A generative image steganography method based on an adversarial network
A generative, image-based technology, applied in the field of information security systems, can solve the problems of fundamentally resisting detection, staying in theoretical concepts, and poor application effects, etc., to achieve imperceptibility, difficulty in attack, and good imperceptibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
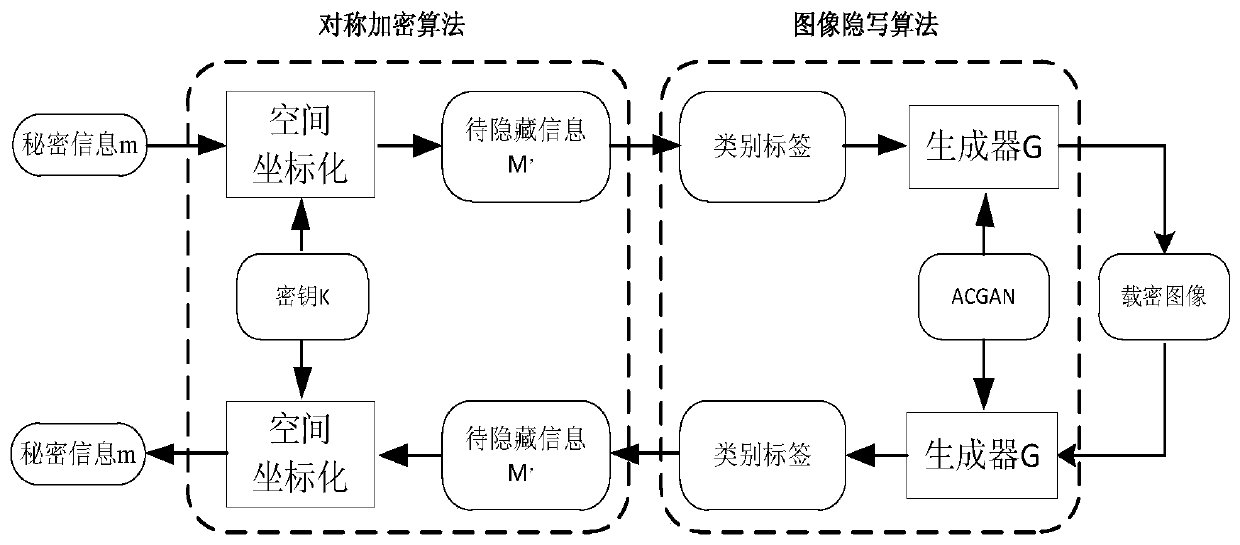
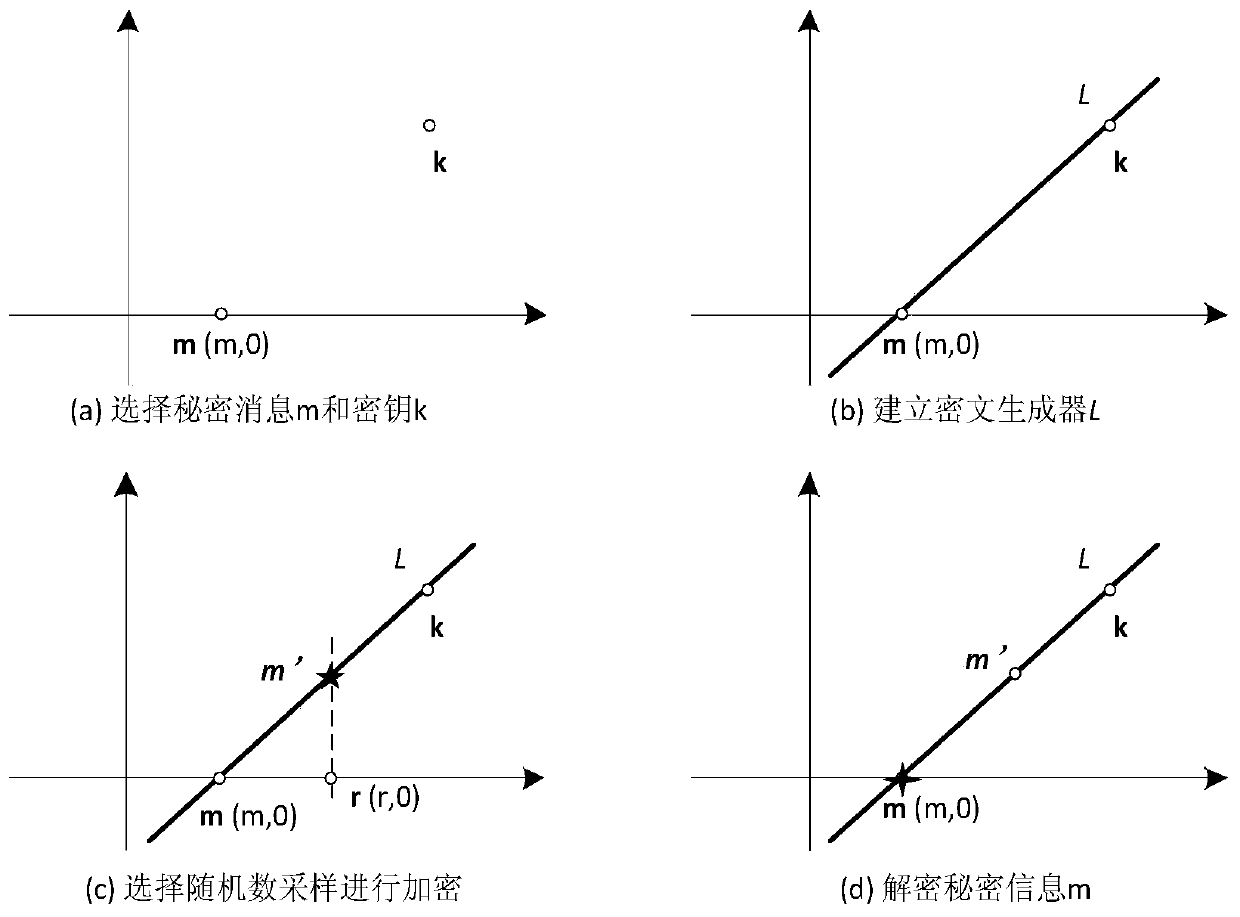
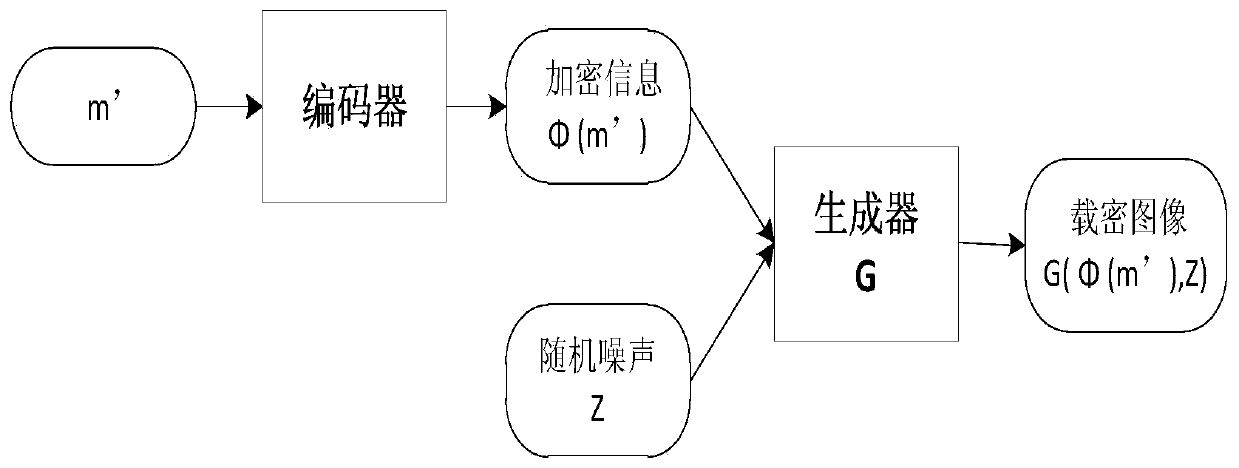
[0041] A generative image steganography method based on an adversarial network of the present invention is composed of a symmetric encryption algorithm and an image steganography algorithm. The symmetric encryption algorithm can carry out spatial coordinates, encrypt and decrypt according to the mathematical principle of "two points and one line", and at the same time expand the spatial dimension according to different encryption levels; the image steganography algorithm is based on the ACGAN model, replacing the category labels in the GAN with the The embedded transmission information is used as a driver to directly generate a encrypted image for transmission, and the receiver extracts the embedded transmission information from the encrypted image through the discriminator to realize generative ima...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com