Secure steganography method and device based on generative adversarial networks
A network and security technology, applied in the information field, can solve the problems of insecure steganography method, poor network discrimination effect, and insignificant network effect of steganalysis, so as to achieve good steganalysis effect, fast training speed, and training time. reduced effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0044] Example 1 Secure Steganography Method Based on Generative Adversarial Networks
[0045] Take the CelebA face dataset as an example:
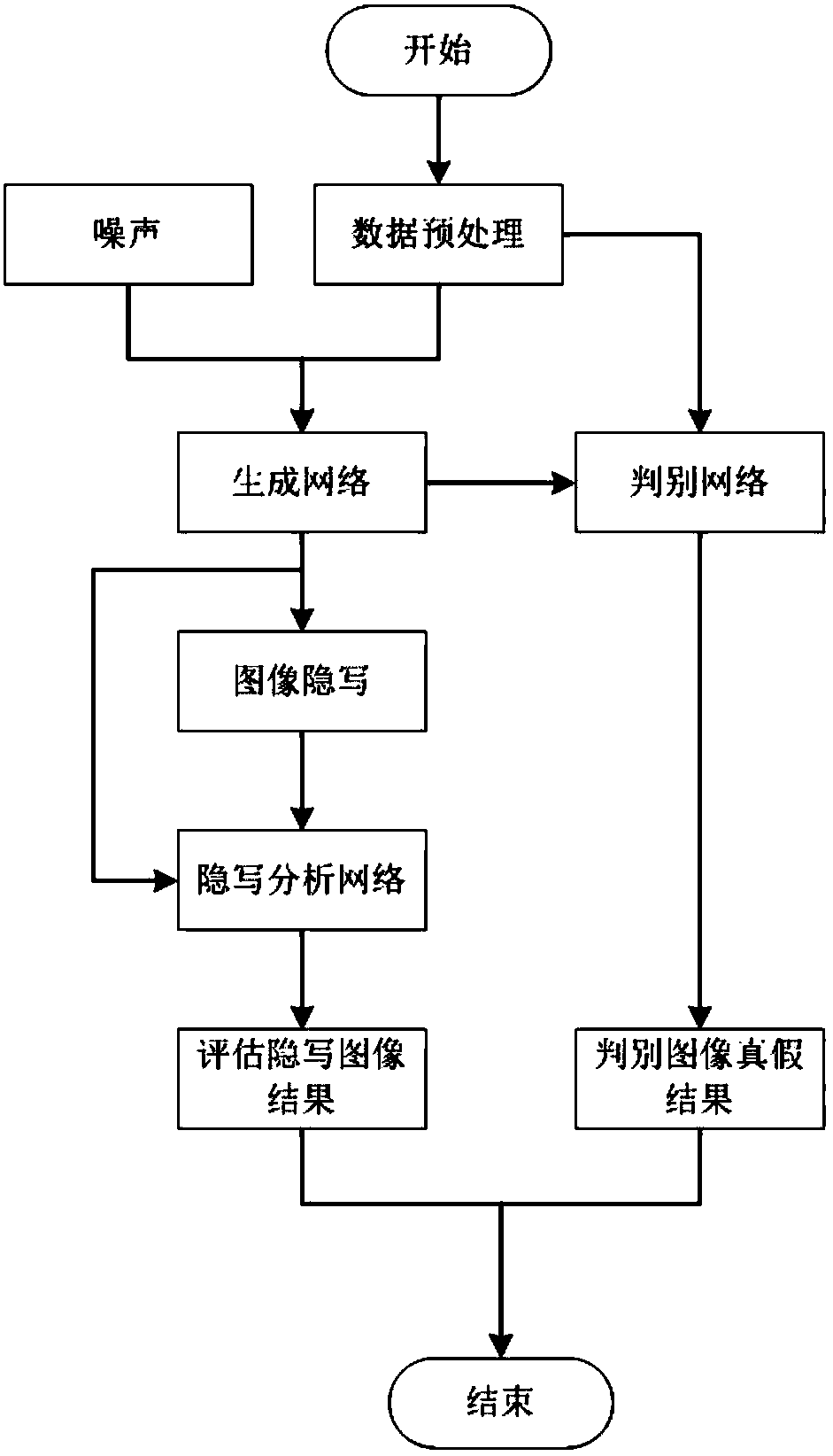
[0046] 1) Under the framework of WGAN (Wasserstein Generative Adversarial Networks, Wasserstein Generative Adversarial Networks), the noise signal z is input to the generation network G, and the carrier image I is generated by the generation network G;
[0047] 2) The discrimination network D and the generation network G compete with each other, so that the carrier image I generated by G is closer to the real image;
[0048] 3) The discriminant network D performs discriminant analysis on the carrier image I generated by G, and obtains the probability of judging it as a real picture or a fake picture;
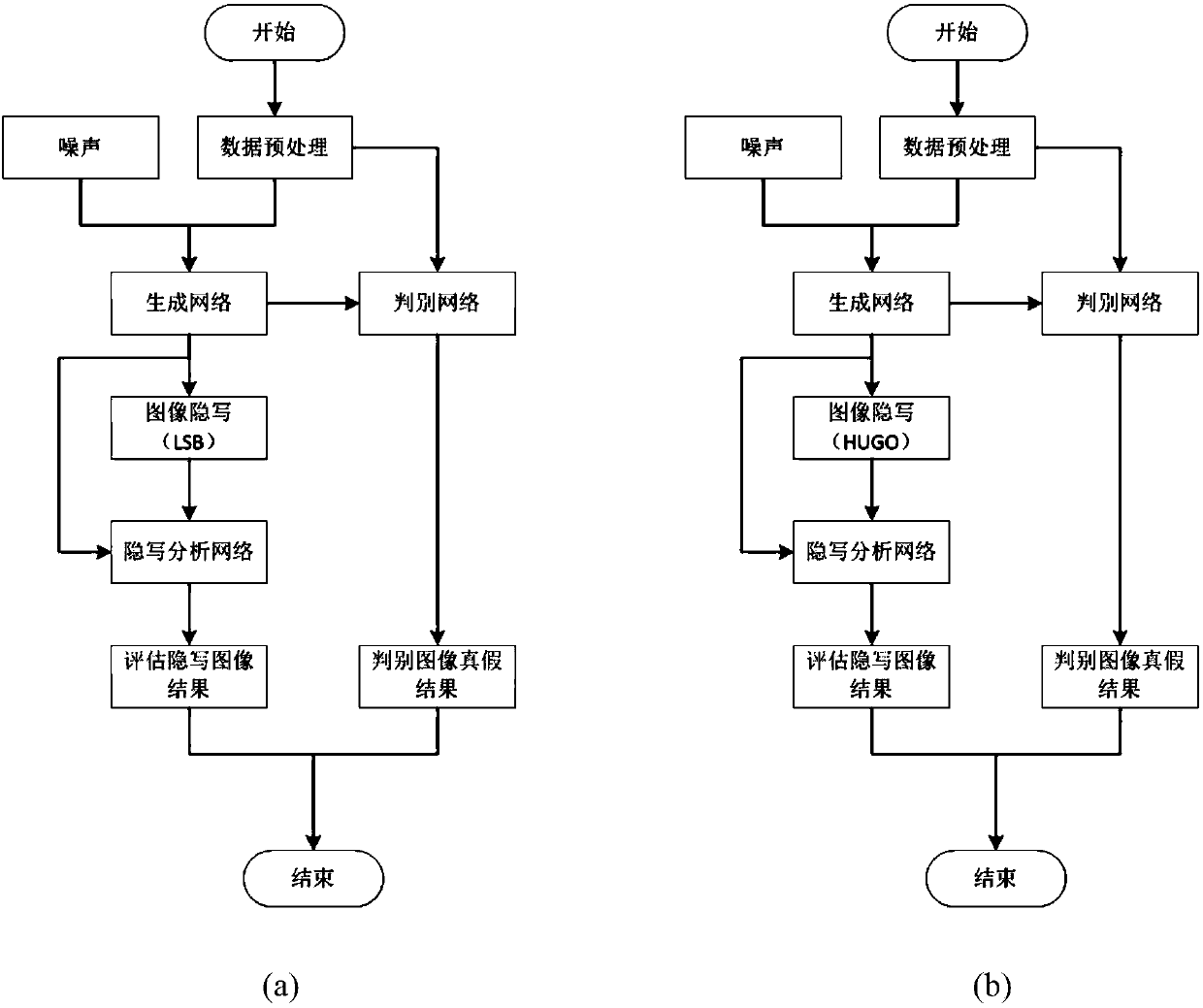
[0049] 4) Embed the generated carrier image I into information off-line, first use the LSB fixed key to embed to obtain the steganographic image I', input I and I' to the steganalysis network S at the same time, and judge whether it is the...
example 2
[0056] Example 2 Secure Steganography Method Based on Generative Adversarial Networks
[0057] Taking the CelebA face dataset as an example, in this experiment, by setting different seed values, we compare the deceptiveness of the generated images to the steganalysis network after information embedding under different parameters. The seed value refers to controlling the repeatability of the experiment under the condition of a certain random number, which is reflected in the present invention as controlling the randomness of the generated image.
[0058] 1) Under the WGAN framework, the noise signal z is input to the generation network G, and the carrier image I is generated by the generation network G;
[0059] 2) The discrimination network D and the generation network G compete with each other to generate a carrier image I that is closer to the real image;
[0060] 3) The discriminant network D performs discriminant analysis on the generated carrier image I, and obtains the ...
example 3
[0069] Example 3 Secure Steganographic Device Based on Generative Adversarial Networks
[0070] The secure steganography device based on the generative confrontation network includes: a generation network unit, used to generate a carrier image to embed information under the framework of the generative confrontation network; a discriminant network unit, used to judge the authenticity of the generated carrier image , and through the dynamic game process with the generating network unit, the carrier image generated by the generating network unit is close to the real image; the steganographic unit is used to embed information on the carrier image generated by the generating network unit. Further, the device also includes a steganalysis network unit, which is used to perform binary classification on the input carrier image and the steganographic image, and obtain the accuracy rate of classification into the original image and the steganographic image.
[0071] The present invention...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com