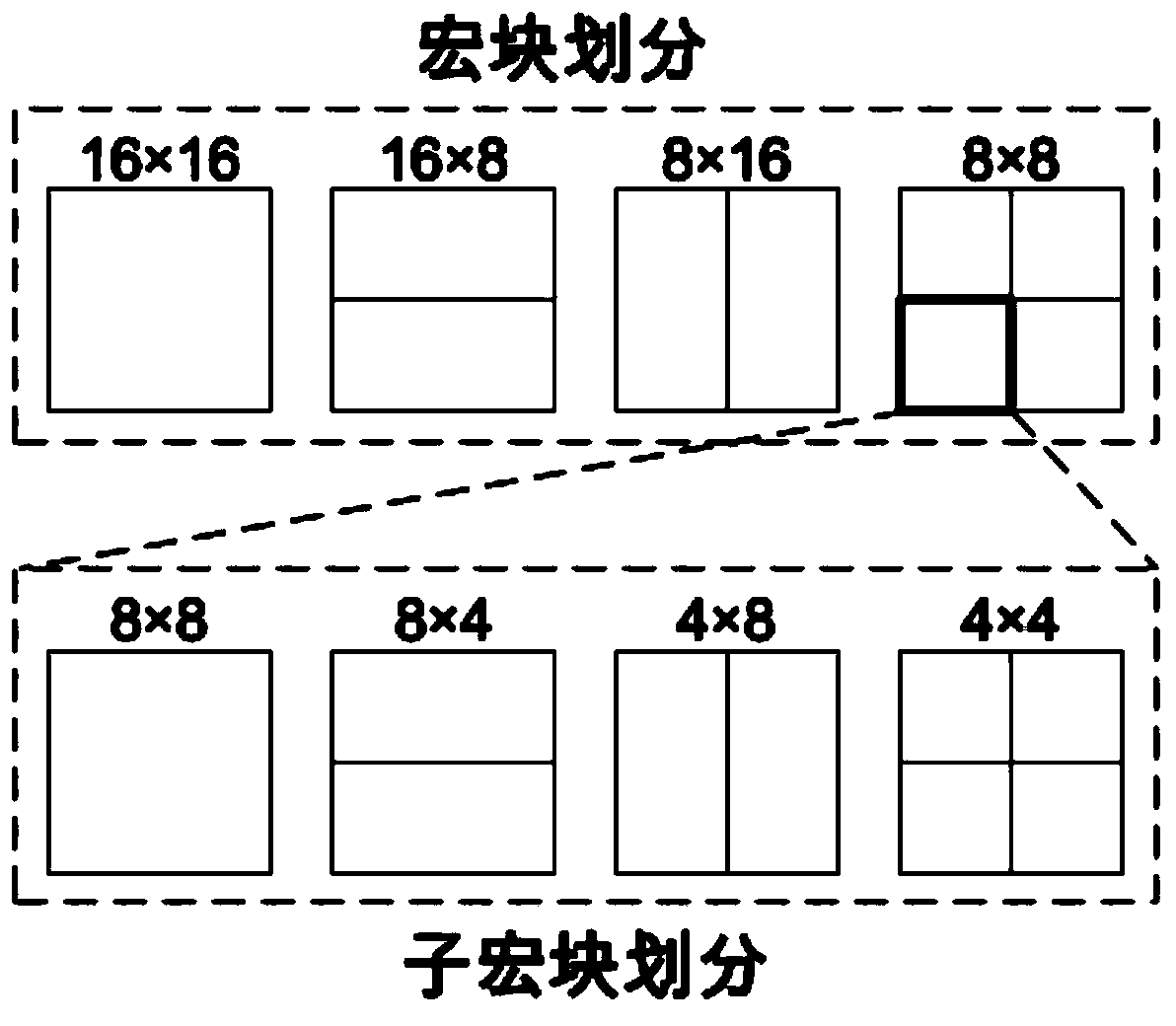
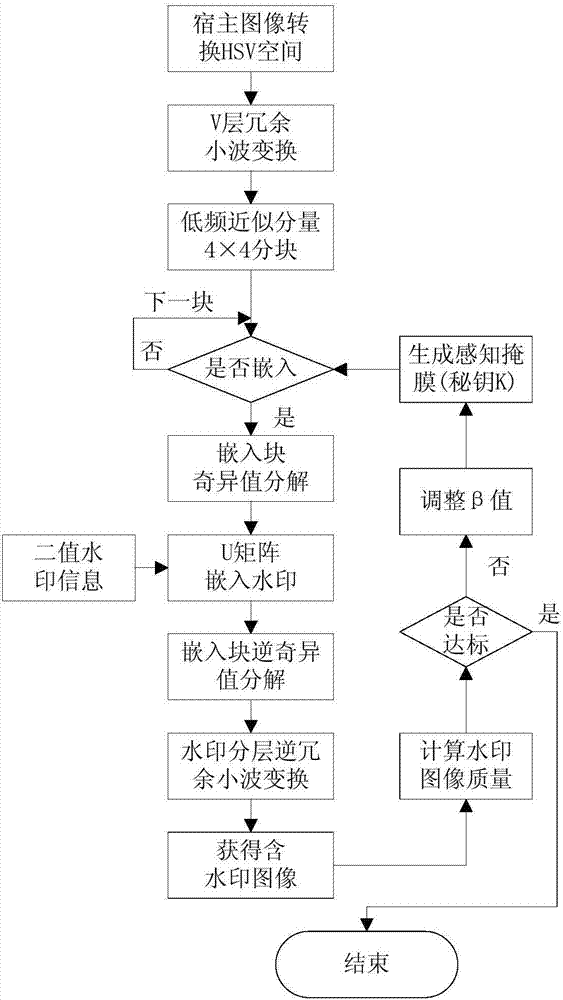
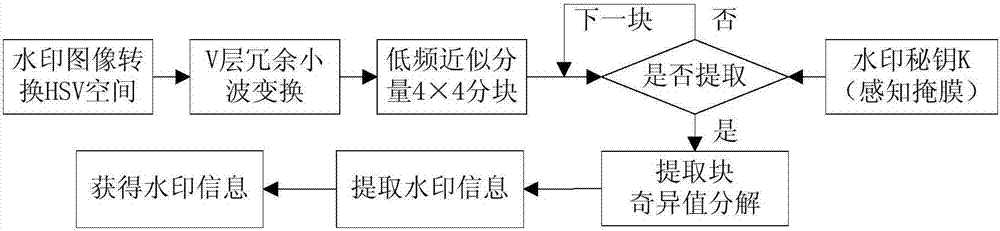
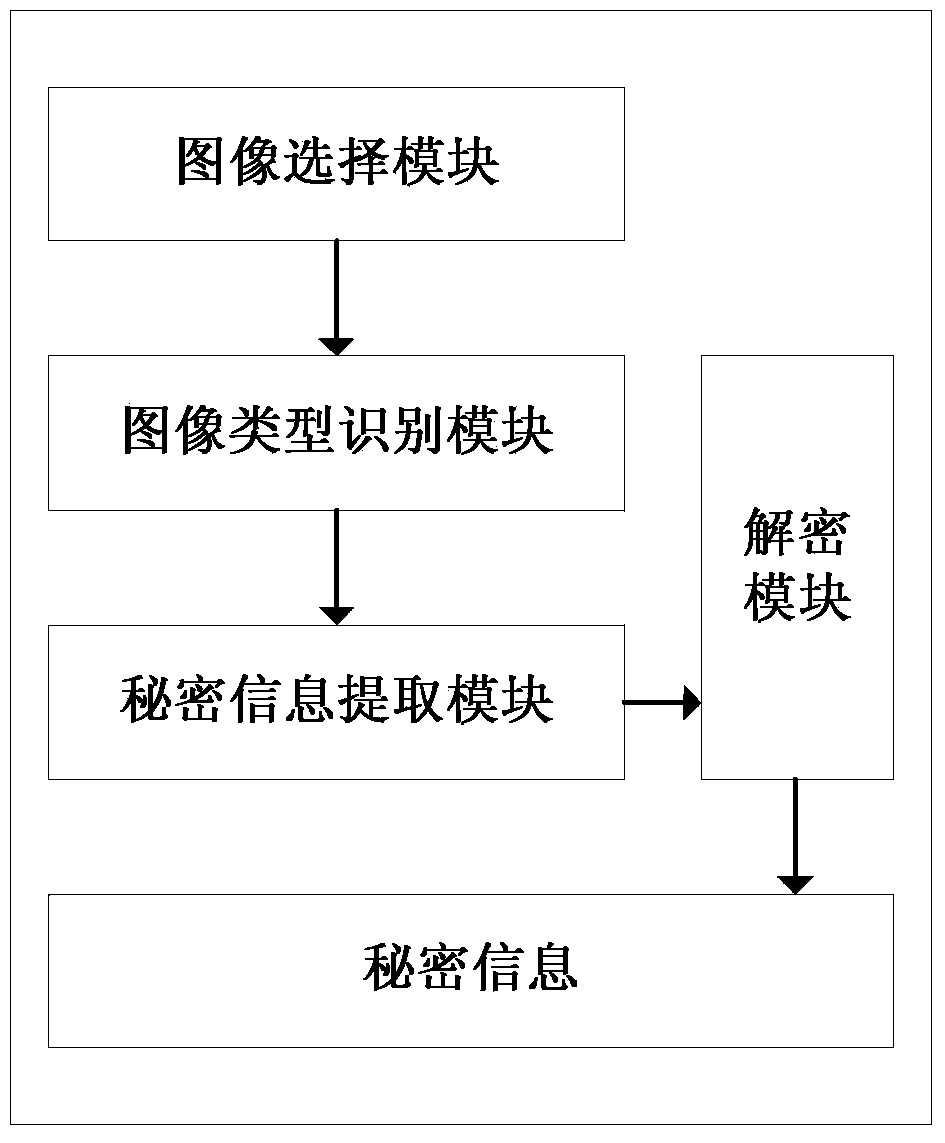
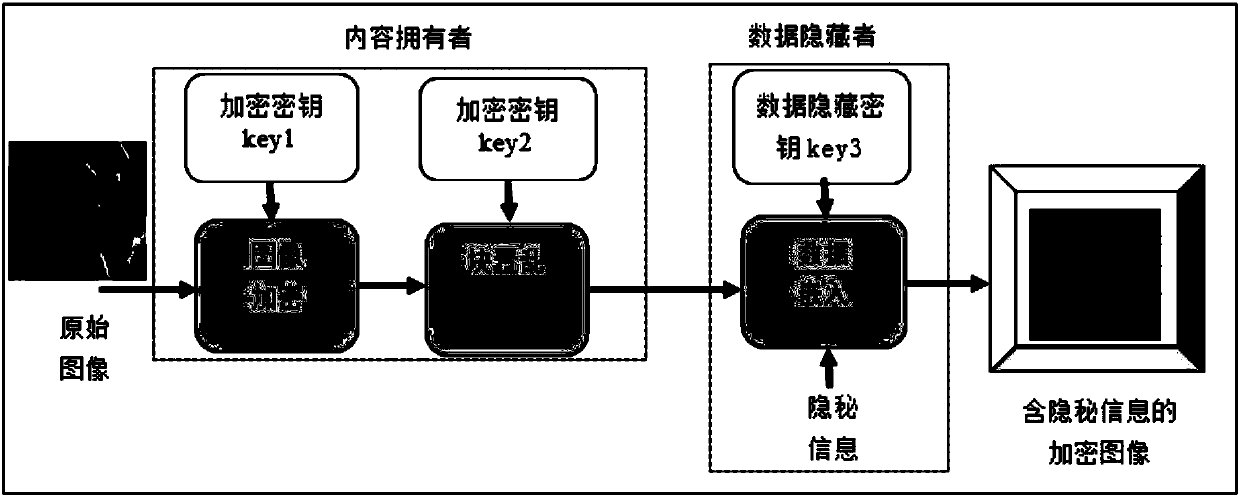
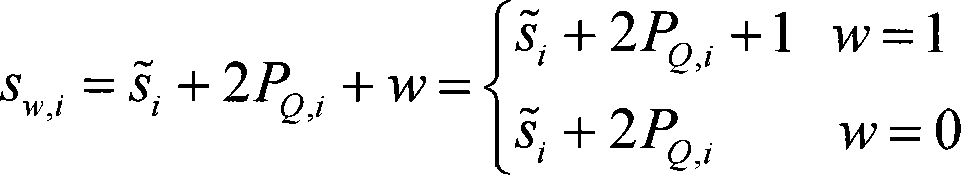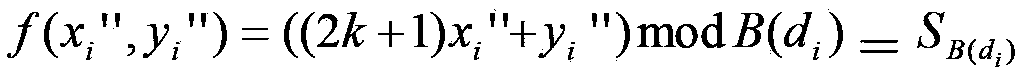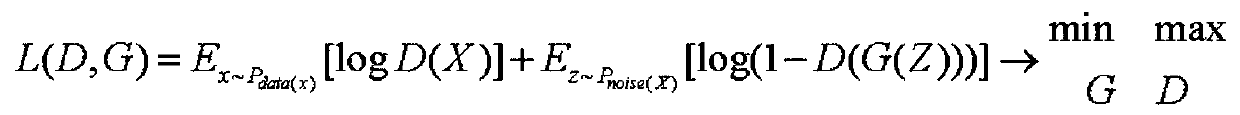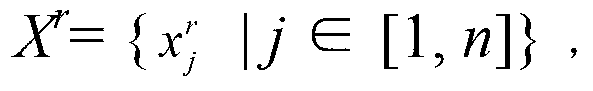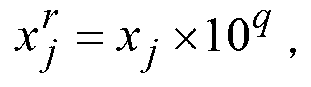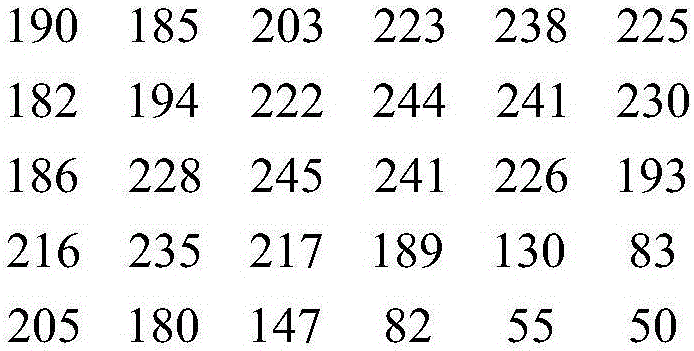Patents
Literature
219results about How to "Increase embedding capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
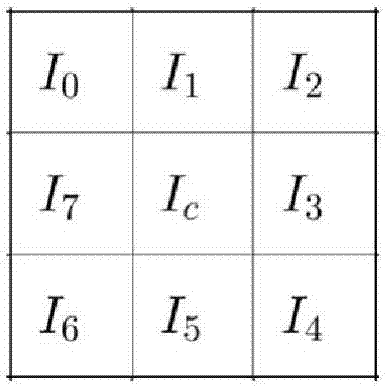
Omni-directional prediction error histogram modification-based reversible image watermarking algorithm
InactiveCN102036079AIncrease embedding capacityImprove forecast accuracyTelevision systemsImage data processing detailsReverse orderOmni directional
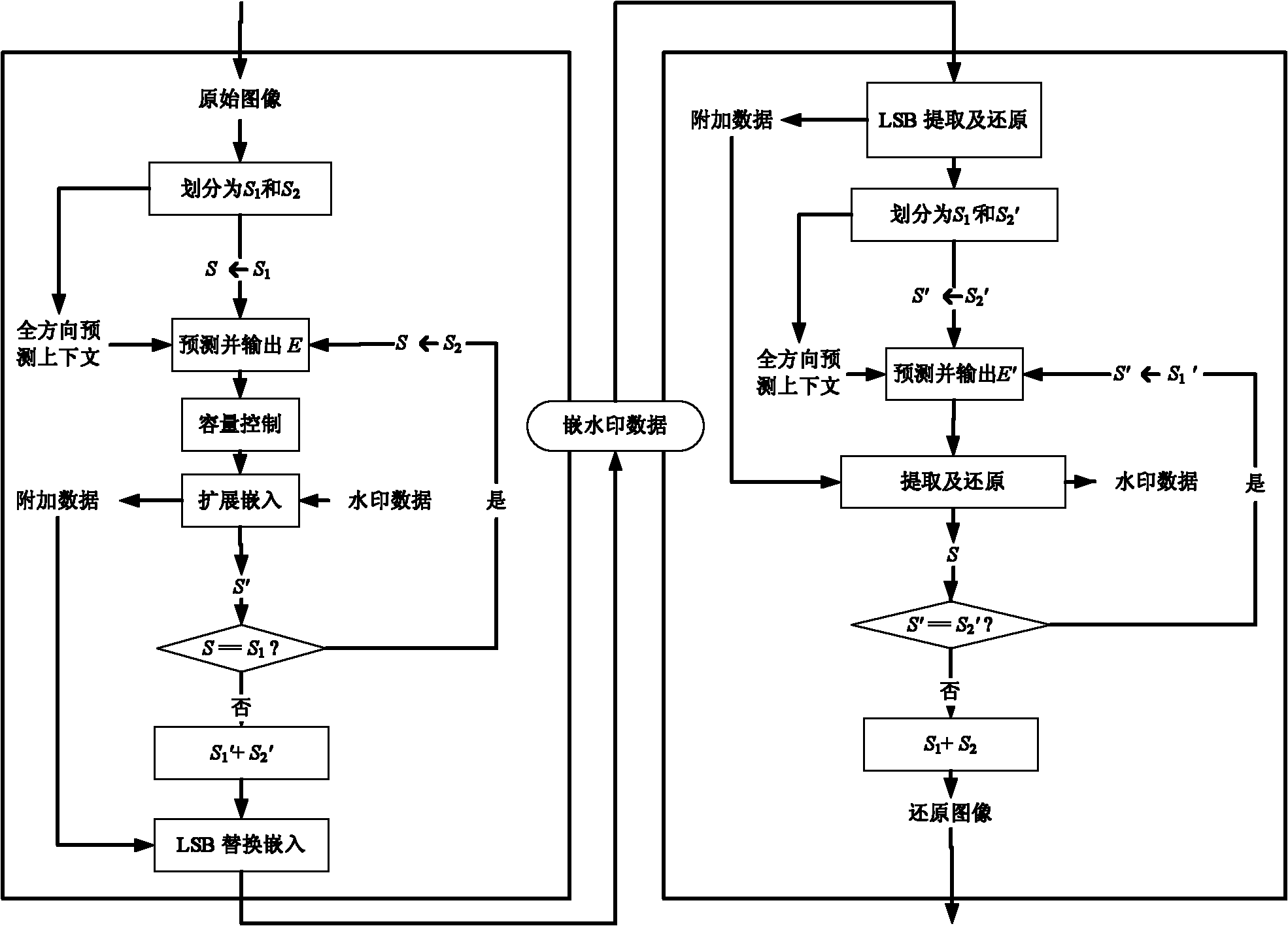
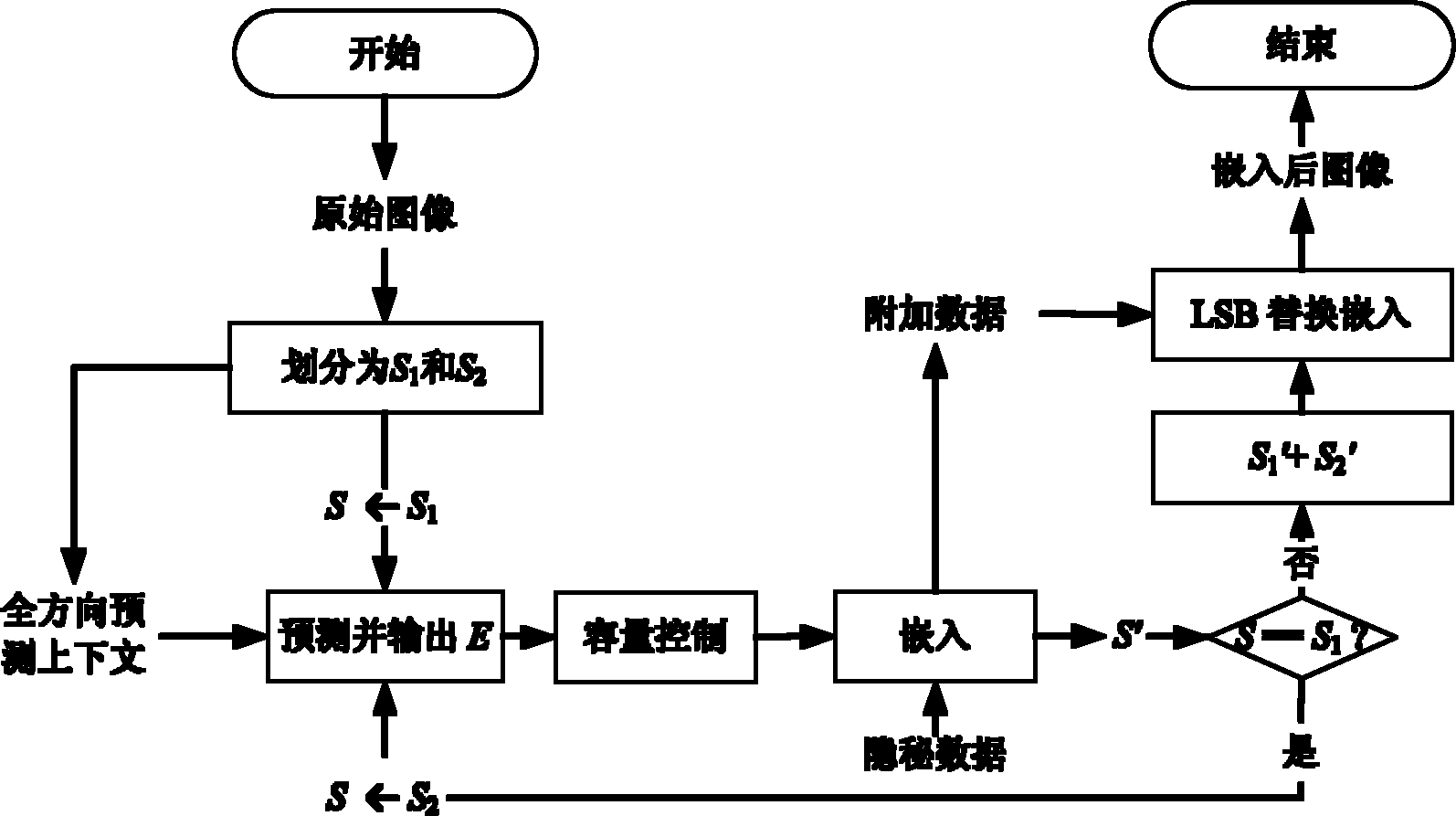
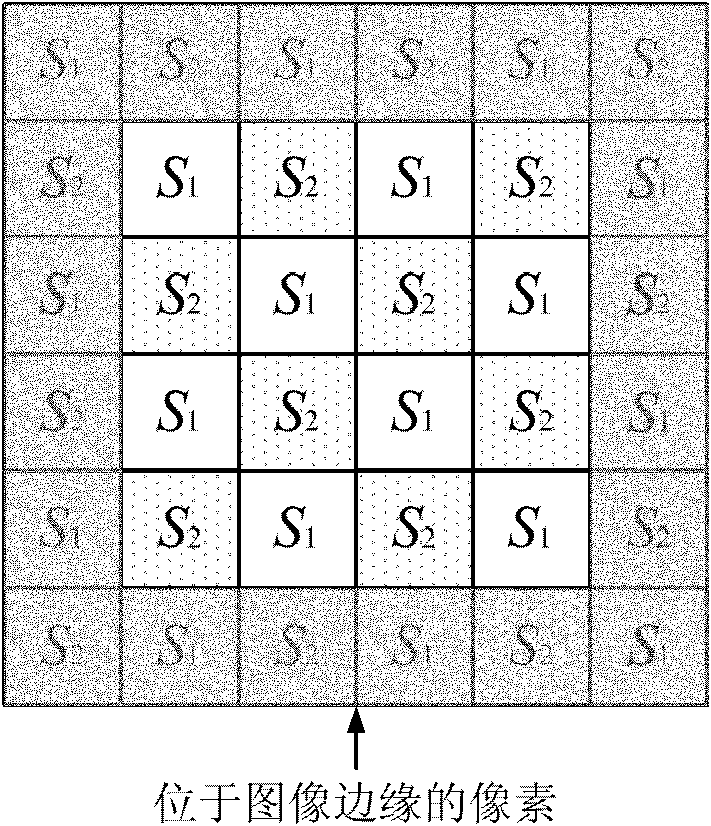
The invention discloses an omni-directional prediction-based reversible image watermarking algorithm comprising the steps of watermark embedding and watermark detection, wherein the watermark embedding process comprises the following steps of: firstly, dividing an image into two mutually-disjointed pixel sets of S1 and S2; secondly, sequentially predicting the pixel sets of S1 and S2 with an omni-directional prediction method to obtain the predication error; and finally, modifying the prediction error histogram to embed the watermark. The watermark extraction process comprises the following steps of: firstly, dividing the image into two mutually-disjointed pixel sets of S1 and S2; secondly, sequentially predicting the pixel sets of S1 and S2 with the omni-directional prediction method according to the sequence opposite to the embedding sequence to obtain the predication error; and finally, extracting the watermark from the predication error, modifying the histogram and restoring the image. According to the invention, by adopting the sequentially-embedded and reversibly-extracting mode, the embedded watermark image can be restored after the watermark is extracted and the reversibility of the watermark of the image can be realized; by adopting the omni-directional prediction method to predict, the prediction error histogram has high centrality and the higher embedded capacity can be realized; and by using the histogram modification in the embedding process, the influence on the image is little and the image embedded with the watermark has favorable visual quality.
Owner:BEIHANG UNIV
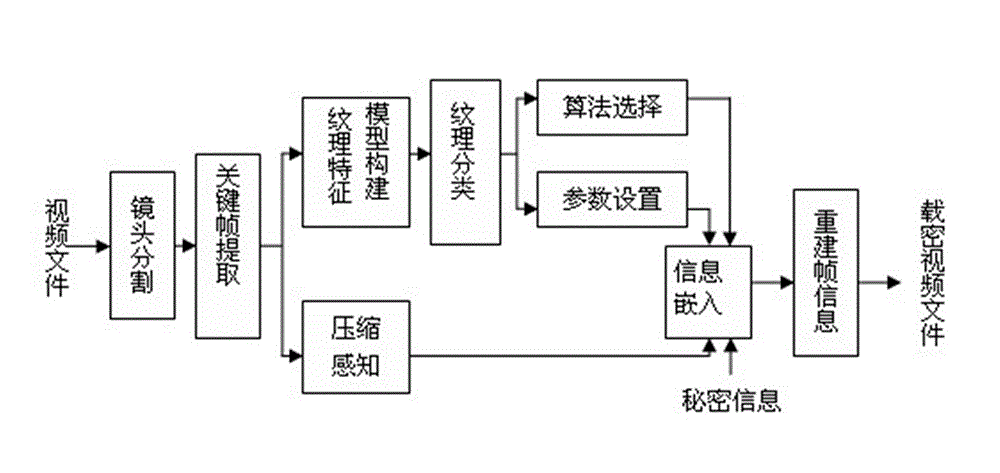
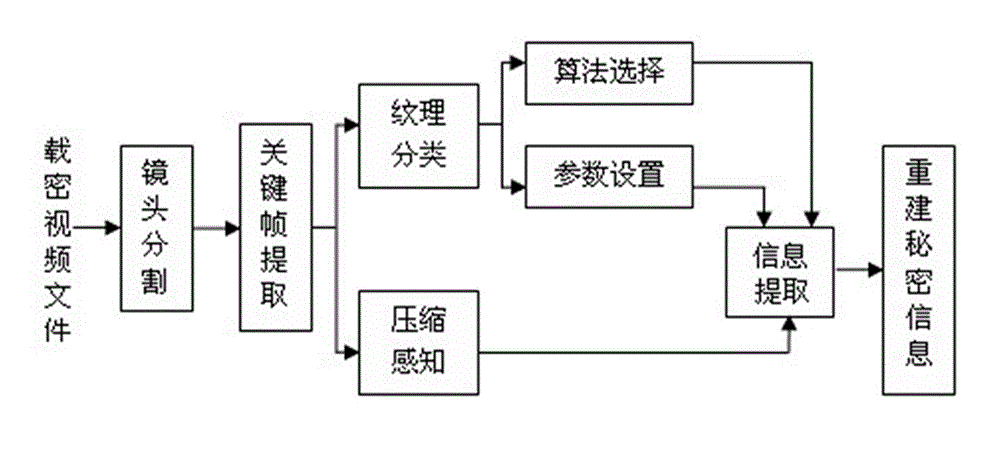
Compressive sensing-based adaptive video information hiding method
InactiveCN102917227AOrnamental effectSmall amount of calculationTelevision systemsDigital video signal modificationPattern recognitionKey frame
The invention discloses a compressive sensing-based adaptive video information hiding method, which is characterized by comprising the following steps of: a, framing a video file by using shot as a unit; b, taking the first frame of each shot as a key frame; c, establishing an image texture classification model to obtain a texture classification model mark of each key frame; d, determining a texture category of each key frame and determining whether the key frame is a texture region, or a smooth region or between the texture region and the smooth region; e, selecting an algorithm and determining insert depth; f, inserting secret information, i.e., inserting the secret information in a coefficient matrix; and g, synthesizing a video file. According to the video information hiding method, the secret information can be adaptively inserted under the condition that the entire video file is not required to be decompressed, so that the ornamental value of the video is not affected, and the method has the advantages of small amount of calculation, high information steganography efficiency, small influence on the video and good secret information safety. The method can be widely applied to various fields such as copyright authentication, pirate tracking and secure communication.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
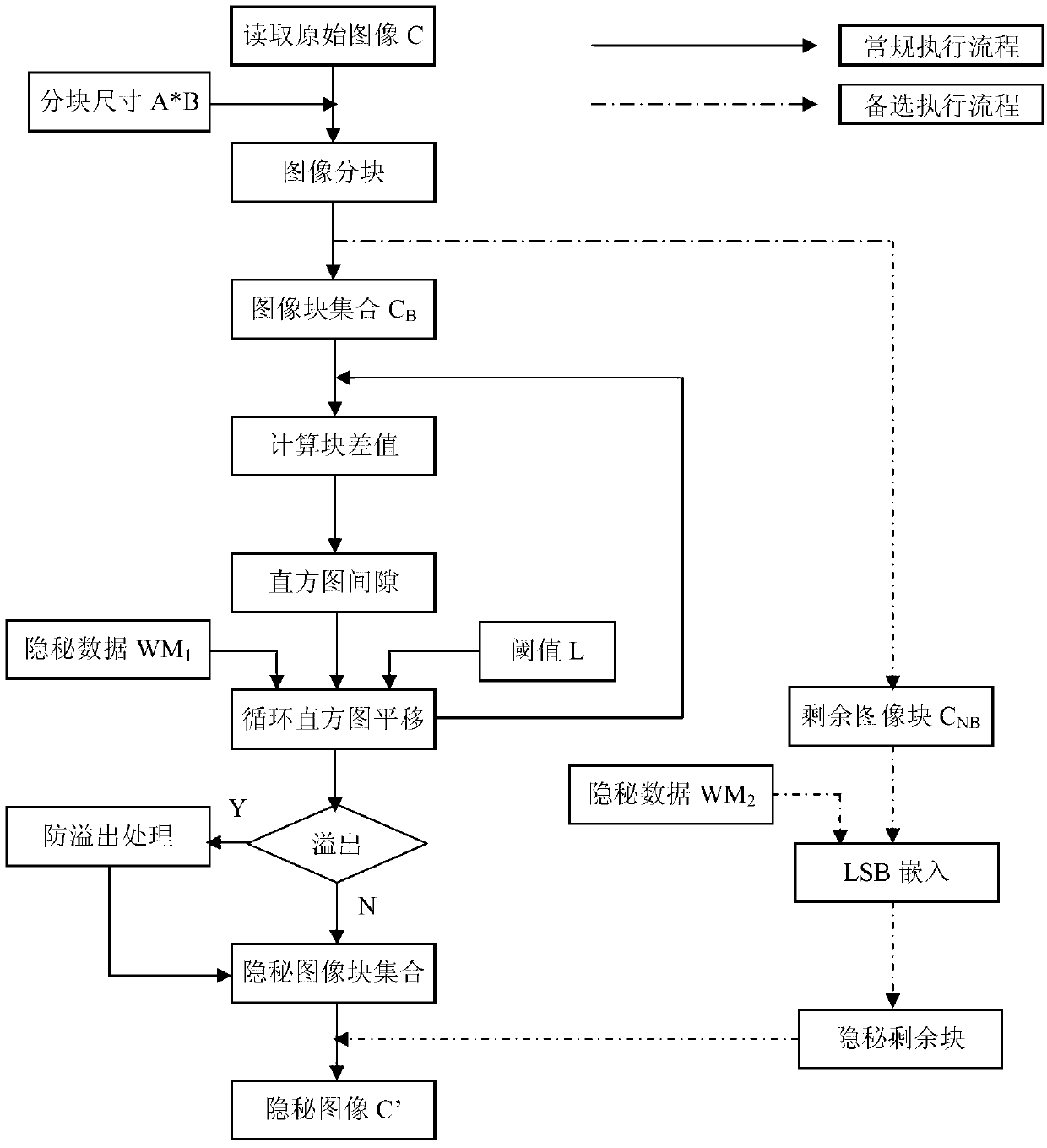
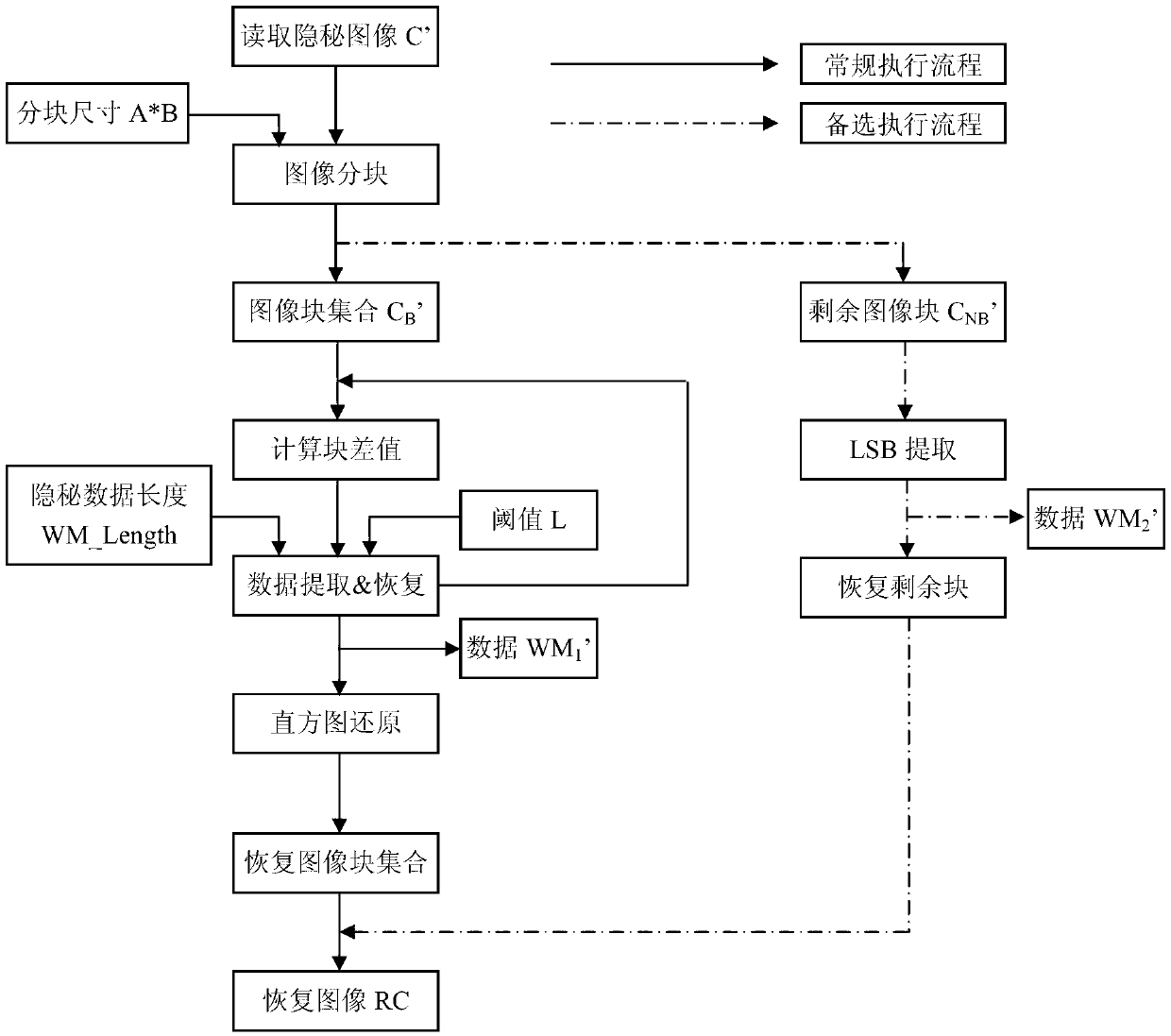
Lossless data hiding method based on difference image histogram cycle spinning
InactiveCN103123720AIncrease capacityLarge capacityImage data processing detailsLow distortionPeak value
The invention discloses a lossless data hiding method based on difference image histogram cycle spinning. The lossless data hiding method includes steps of encrypting, secret key transmitting and data recovery. During encrypting, an original image is divided into a plurality of sub image blocks at the transmitting end, cycle spinning operation is performed by aid of a sub block difference histogram to achieve step-by-step embedding of secret data, a secret image C' is formed and transmitted to the receiving end. During secret key transmitting, the size of sub image blocks, the length of embedded data and the embedding level L serve as a secret key to be distributed to the receiving end. During data recovery, the receiving end extracts the secret data step by step from the secret image C' in an inverse method of the embedding process, block difference and original image data are recovered, and secret data transmission and lossless recovery based on the image carrier are achieved. The lossless data hiding method overcomes the defect that the capacity of the original histogram spinning algorithm depends on a single peak point, and increases the embedding capacity through a cycle embedding method. Experimental results prove that the lossless data hiding method can well meet requirements for high capacity, low distortion and high efficiency.
Owner:CENT SOUTH UNIV
Reversible video frequency watermark method based on interframe forecast error histogram modification
InactiveCN101651837AIncrease embedding capacityImprove forecast accuracyAnalogue secracy/subscription systemsDigital video signal modificationWatermark methodQuality of vision
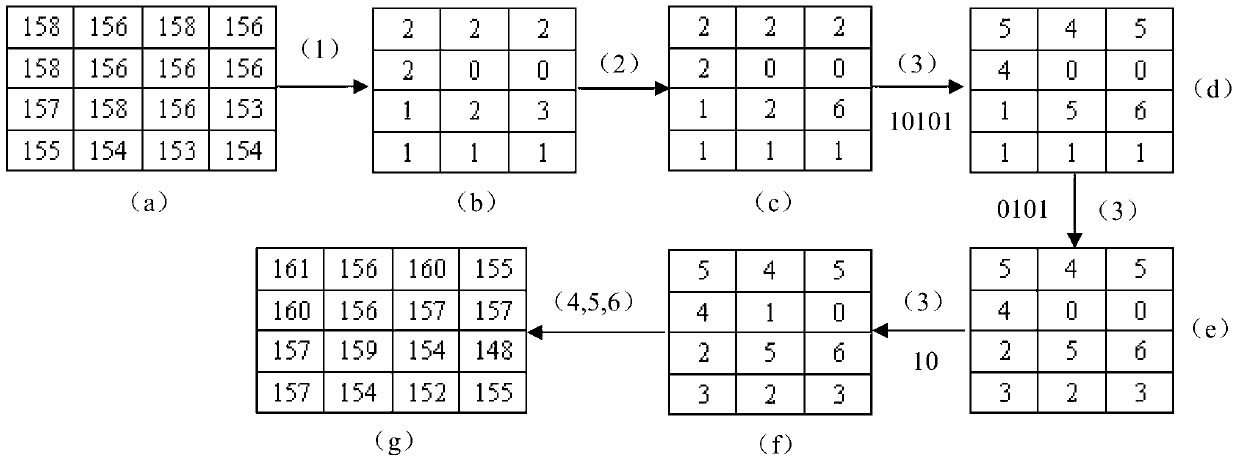
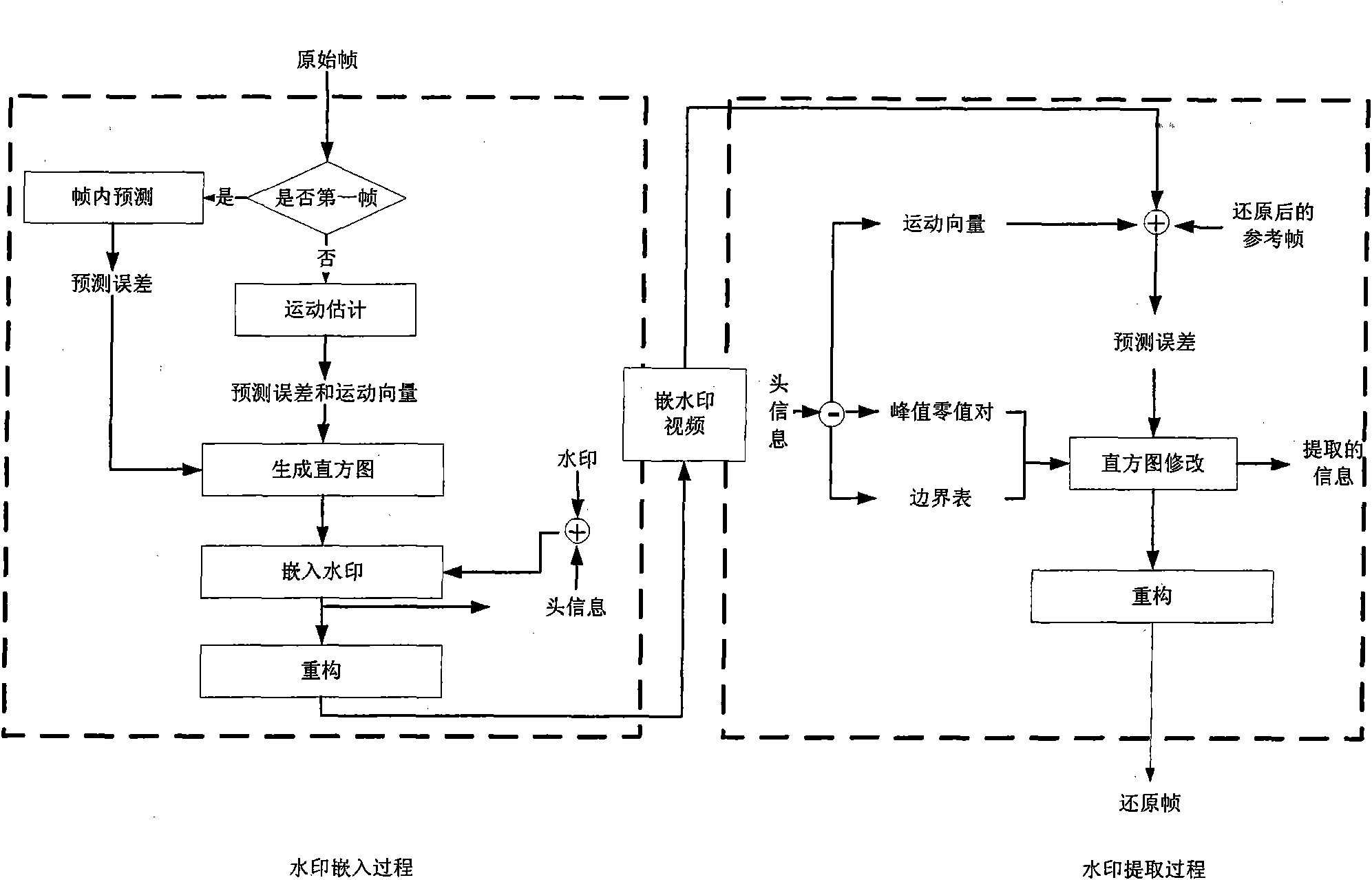
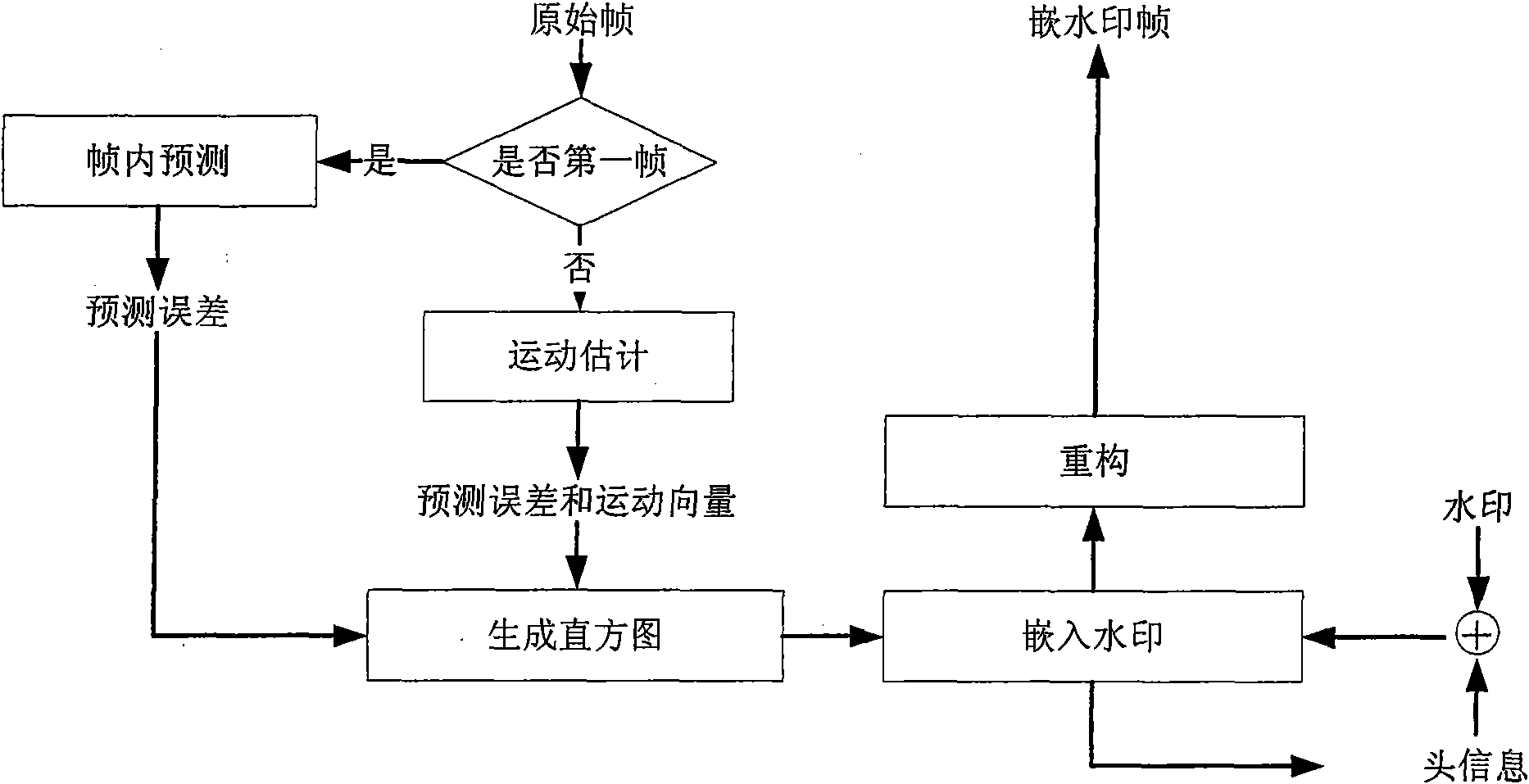
The invention relates to a reversible video frequency watermark method based on interframe forecast error histogram modification, comprising watermark embedding and watermark detection. The watermarkembedding process is carried out according to a video frequency negative sequence: firstly, utilizing the previous frame to carry out motion estimation to obtain an interframe forecast error, and thencarrying out the histogram modification on the interframe forecast error so as to embed a watermark. An extracting process is carried out according to a video frequency sequence mode: similarly, utilizing the previous frame to carry out the motion estimation to obtain a forecast error, and then extracting a watermark from the forecast error, and modifying a histogram to carry out the frame imagerecovery. The invention uses the mode of negative sequence embedding and sequence extracting, thereby an embedded video frequency frame can be recovered after the watermark is extracted, and the reversibility of the video frequency watermark is realized; the motion estimation is used according to the content relation of adjacent interframes to carry out prediction so as to enable the forecast error histogram to have the height centrality, and realize the bigger embedding content; in the embedding process, using the histogram modification enables that the influence on the frame image is small,and a watermark-embedded video frequency has high visual quality.
Owner:BEIHANG UNIV
Zero-watermark embedding and extracting methods and zero-watermark embedding and extracting devices based on DWT and principal component analysis (PCA) compression
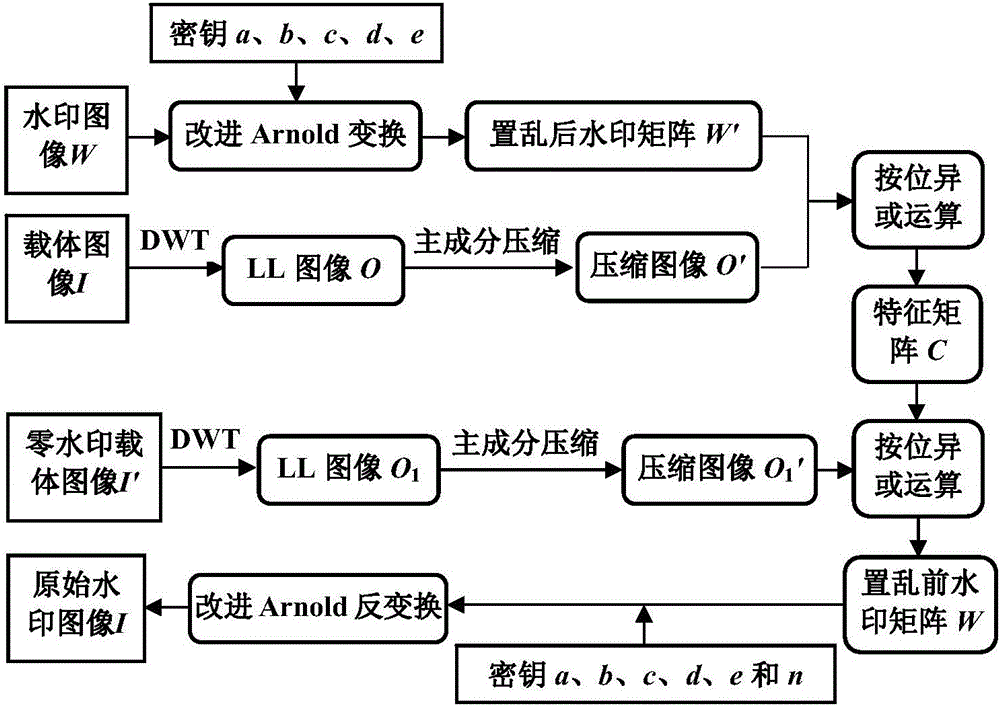
InactiveCN106023056AEasy extractionMeet the requirement of invisibilityImage data processing detailsKernel principal component analysisArnold transformation
The invention relates to zero-watermarking embedding and extracting methods and zero-watermarking embedding and extracting devices based on DWT and PCA compression. When a watermark is embedded, improved Arnold transformation is used to transform an original watermark; a compression image is obtained by using wavelet transformation and PCA compression methods; and XOR operation is carried out on the compression image and a scrambled watermark image to obtain a characteristic matrix. When the watermark is extracted, discrete wavelet transformation is carried out on a carrier image with zero-watermark, the PCA compression method is used to compress a low-frequency sub-band image, XOR operation is carried out on the obtained matrix and the characteristic matrix, the scrambled watermark image is obtained, and a reverse Arnold transformation formula is used to obtain the original watermark image. According to the method and device of the invention, zero watermark is easy to construct and extract, and the safety and anti-attack capability of the watermark are improved effectively.
Owner:HENAN NORMAL UNIV
High capacity reversible water mark method based on predication and companding technology
InactiveCN101105857AExcellent Peak Signal to Noise RatioReduce computational complexityImage data processing detailsSignal-to-noise ratio (imaging)High peak
The invention discloses a high-capacity reversible watermark method based on predication and companding technique. Through the introduction of the companding technique, the invention includes two processes: watermark embedding and watermark extracting. The invention effectively solves the problem of capacity consumption of position drawing in reversible watermark algorithm, and achieves high embedding capacity even in the situation of low threshold value. Meanwhile, due to the operation of data re-embedding after the compression of high predication errors, the invention still can maintain high peak signal to noise ratio (PSNR value).
Owner:BEIJING JIAOTONG UNIV
Image steganography method and secret information extraction method
InactiveCN103413269AIncrease embedding capacityControl distortionImage data processing detailsSteganalysisComputer vision
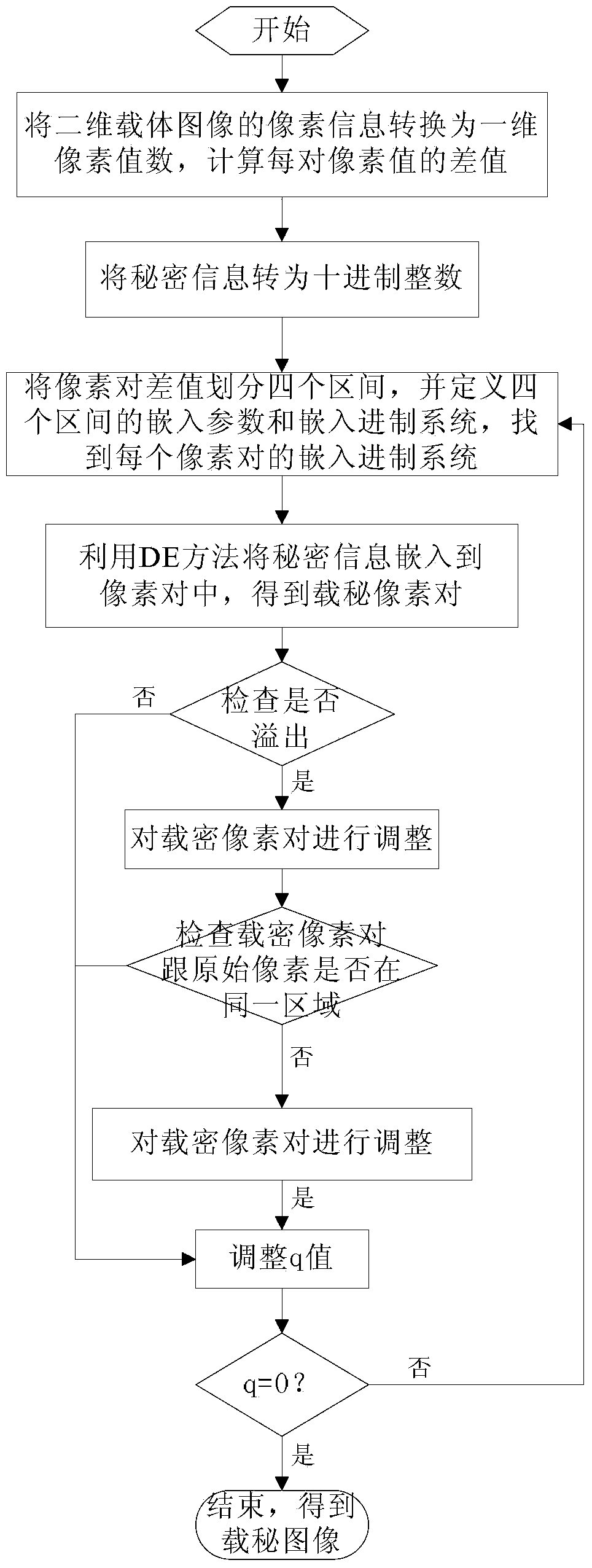
The invention relates to an image steganography method and a secret information extraction method. The image steganography method comprises the steps: (1), converting pixel information of a two-dimensional carrier image I into a set of continuous and non-overlapping one-dimensional pixel value data, and computing a difference value of each pair of pixel values, wherein the size of the two-dimensional carrier image I is N1*N2; (2), performing DES encryption on secret information S, and transferring encrypted secret information S' into a decimal integer q; (3), dividing a di value computed in the step (1) into four sections Tj; (4), obtaining SB(di) according to the equation: SB(di)=qmodB(di), and inserting SB(di) into a pixel pair (xi, yi) through a DE method; (5), detecting whether overflowing occurs or not. Compared with the prior art, the image steganography method has the advantages of being capable of improving insertion capacity of the carrier image remarkably and controlling image distortion effectively. The image steganography method has the steganalysis abilities such as the certain safety performance and resistance to RS attack, and can operate efficiently on mainstream software and hardware platforms of a mobile intelligent terminal.
Owner:NINGBO UNIV
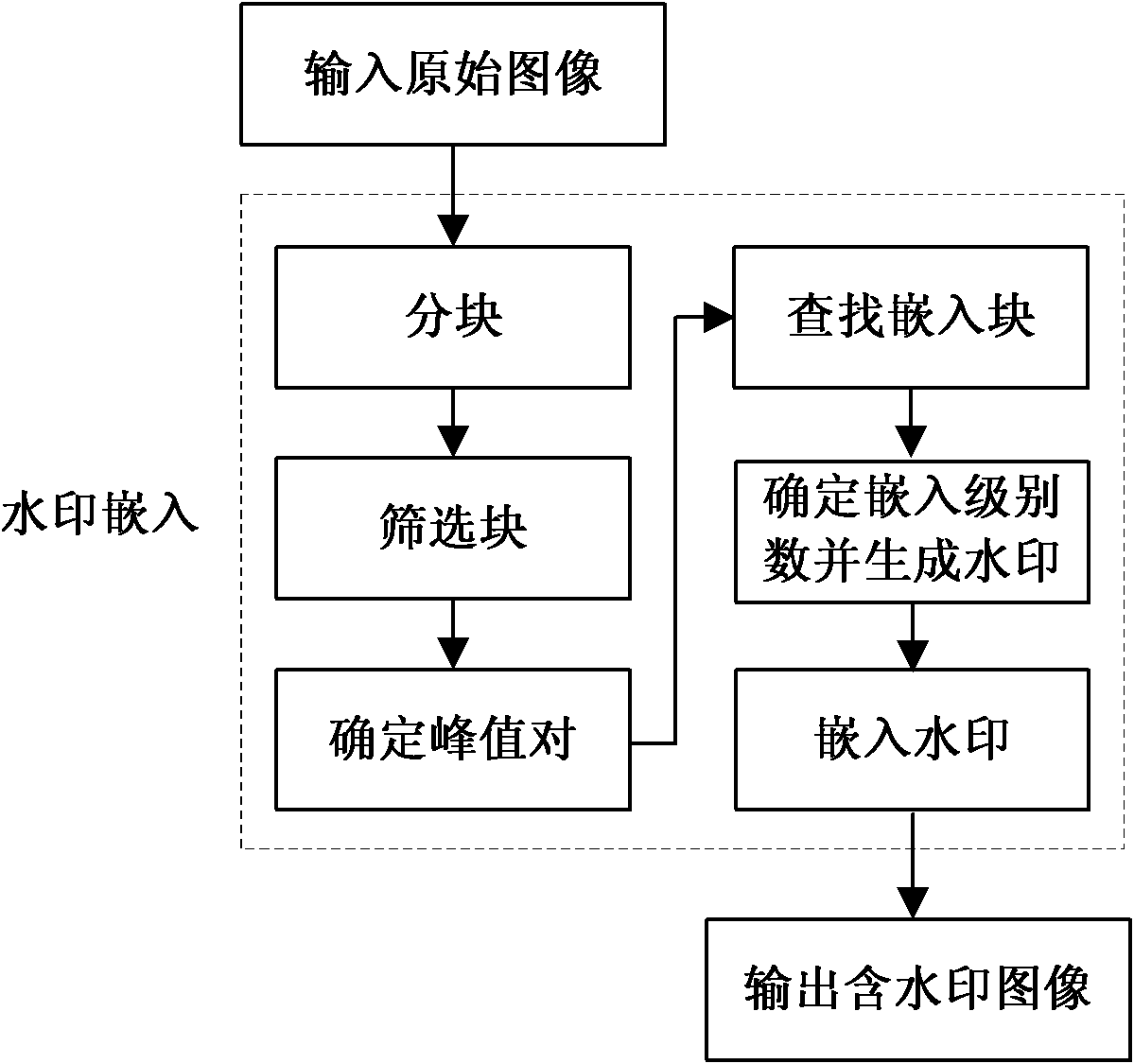
Robust reversible watermark embedding and extracting method based on histogram neighborhood
InactiveCN102156955AIncrease watermark capacityPrevent overflowImage data processing detailsCluster algorithmAlgorithm
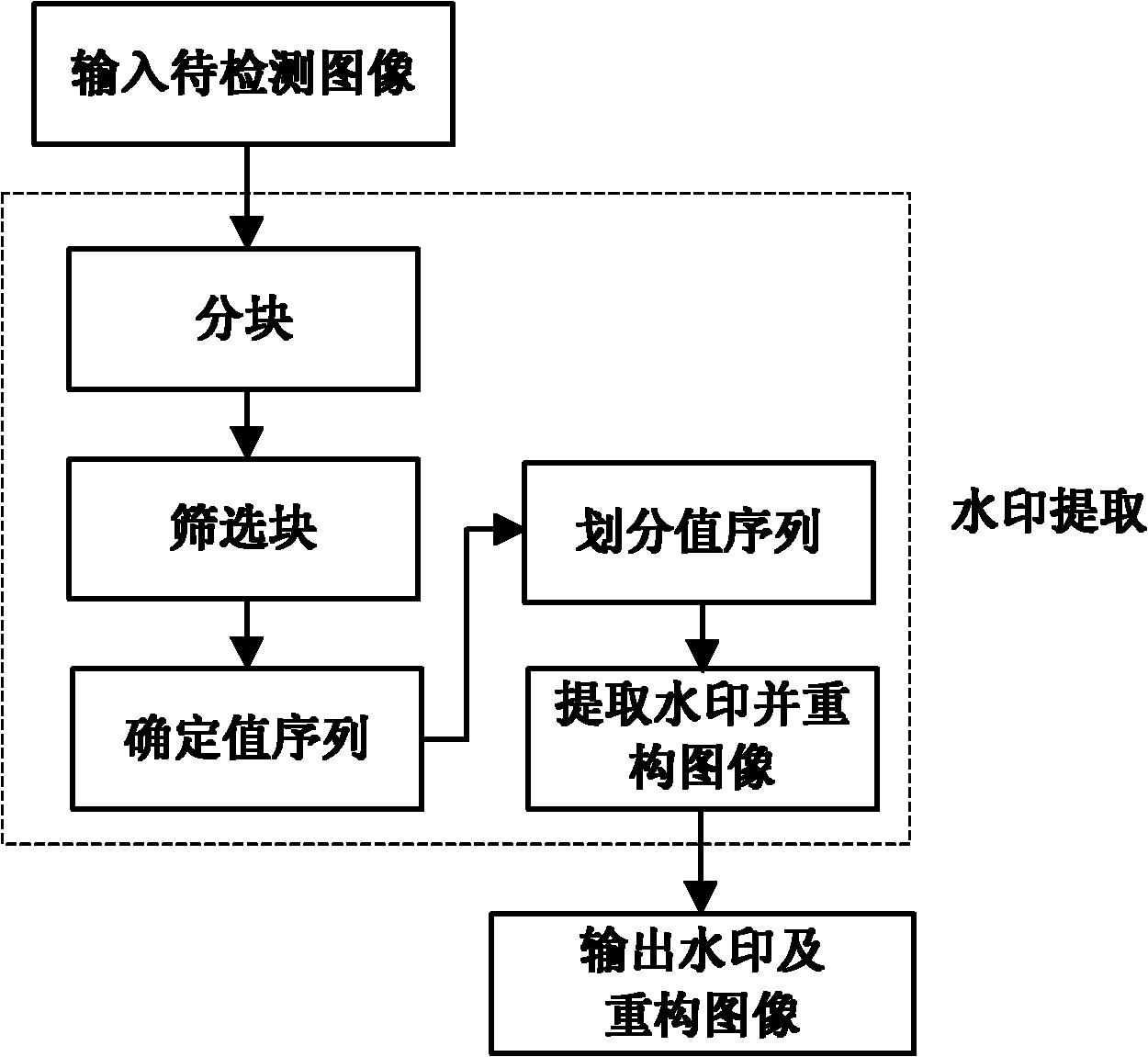
The invention discloses a robust reversible watermark embedding and extracting method based on histogram neighborhood, mainly solves the shortage of poor comprehensive properties of the existing method. The method comprises the following steps of: firstly partitioning an original image, and screening a set of candidate blocks by means of embedding level; then calculating characteristic values of the candidate blocks, determining peak value pair, and obtaining a set of reliable embedding blocks by means of neighborhood selection of the peak value pair; finally, implementing watermark embedding by modifying the characteristic values of the embedding blocks; in the extraction process, the embedding block of an image to be detected is obtained, and the characteristic histogram value sequences of the embedding blocks are sorted by means of a clustering algorithm to obtain a set of sorted sequences, then the watermark is extracted by comparing the characteristic values of the embedding blocks with the sorted sequences, and a reconstructed image is subsequently obtained by modifying the characteristic values of the embedding blocks in the image to be detected. The embedding and extracting method has the advantages the robustness with reliable loss compression attack to JPEG (Joint Photographic Experts Group) and JPEG2000 is provided, the capacity is large, the invisibility is good, the overall performance of the method is superior to that of the similar methods, and the method can be applied to the copyright protection of a digital image.
Owner:XIDIAN UNIV
Video steganographic method based on macro block partition mode disturbance
InactiveCN104010193AImprove securityChange load rateDigital video signal modificationSteganalysisAnalysis method
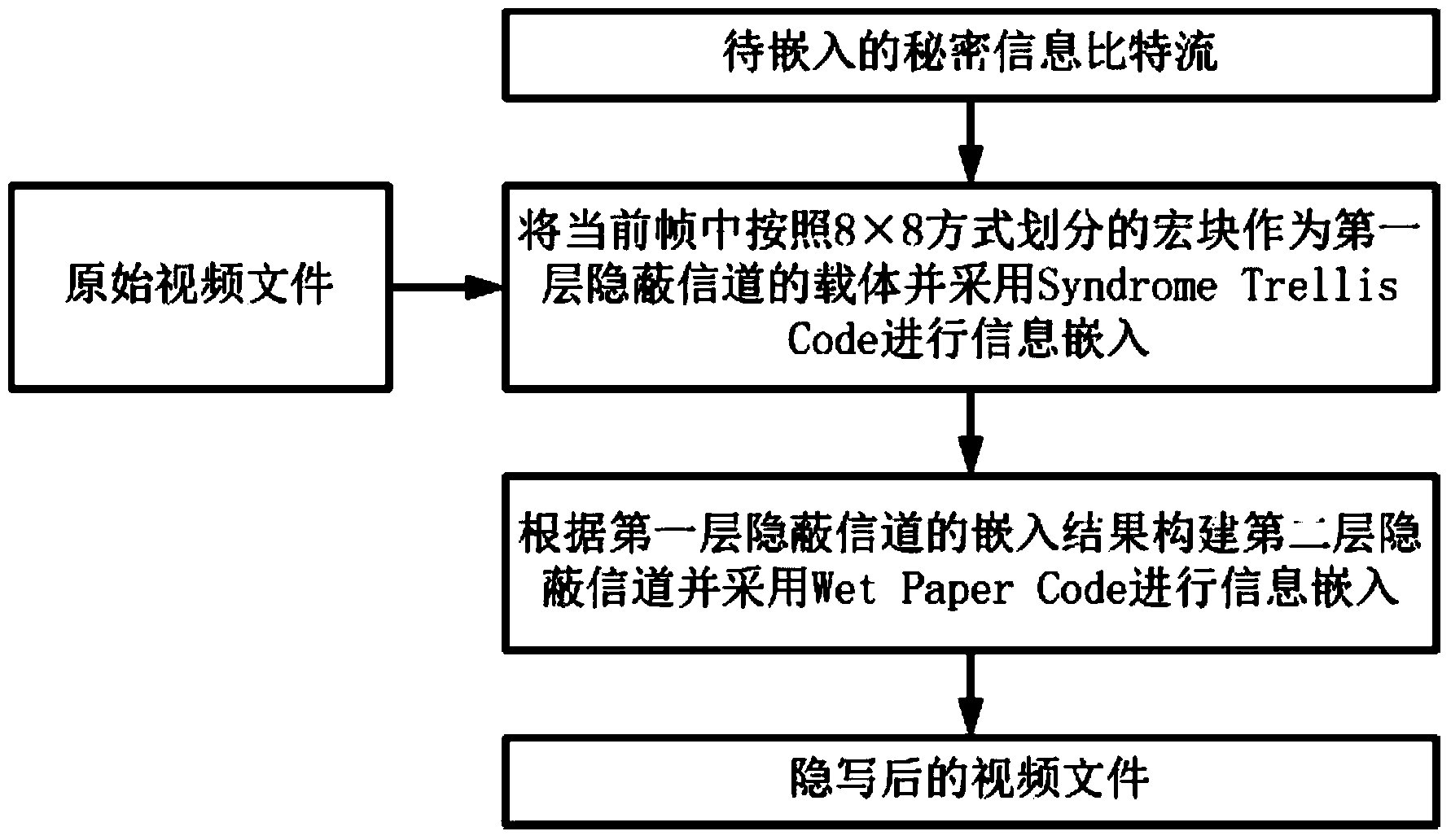
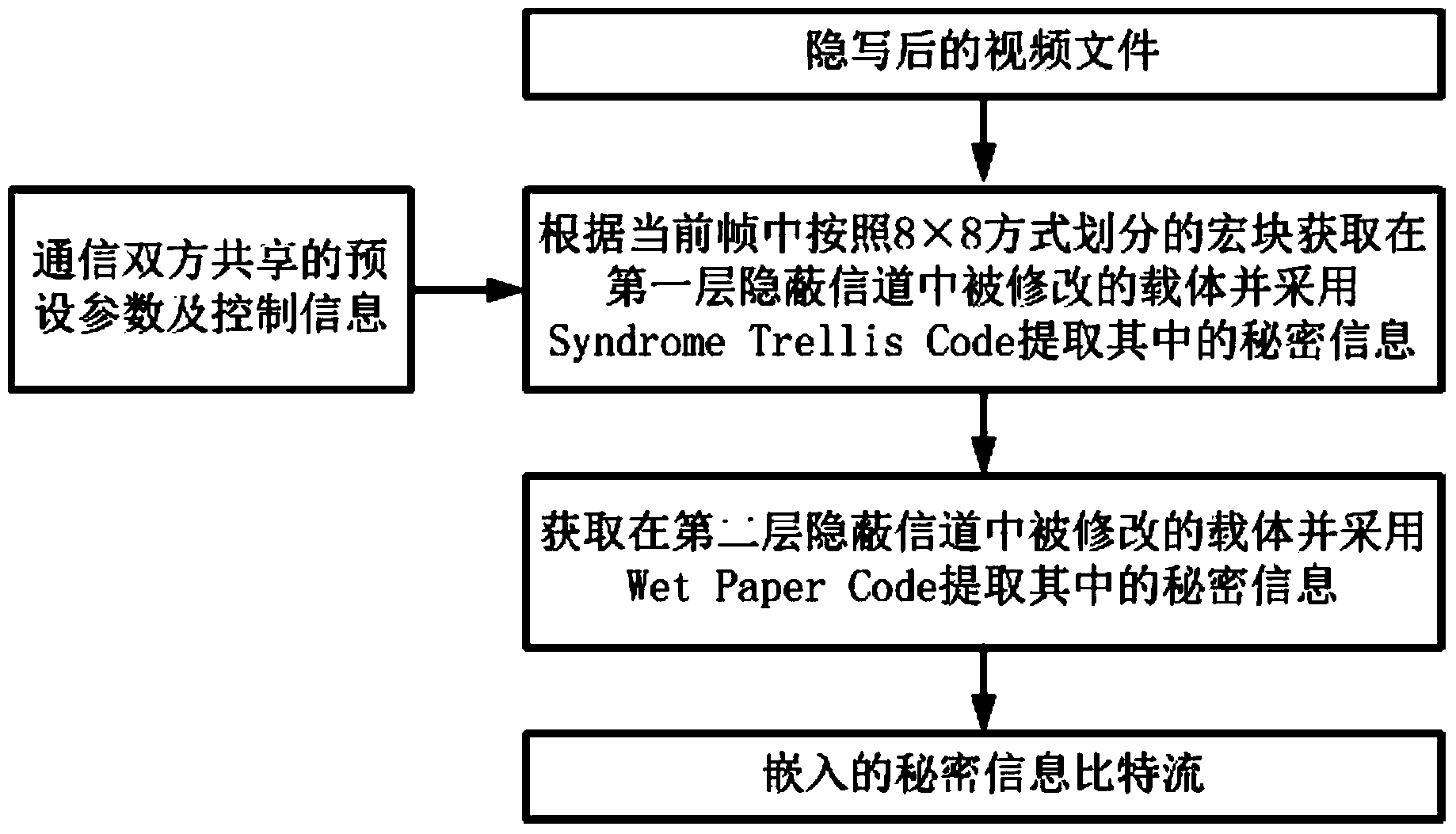
The invention relates to a video steganographic method based on macro block partition mode disturbance. The method includes an embedment process of secrete information and an extraction process of the secrete information. Two hidden channels are built in the embedment process of the secrete information, the secret information is embedded through different steganographic codes, and the secrete information is extracted from the two hidden channels sequentially in the extraction process of the secret information. Preferably, the two hidden channels are built through the steganographic codes including a Syndrome Trellis Code and a Wet Paper Code, and embedment and extraction of the secret information are carried out. Various steganographic codes are used comprehensively to carry out video steganography, high embedment efficiency is achieved, attack of an existing video steganographic analysis method can be resisted effectively, and the video steganographic method is especially suitable for high-safety hidden communication; different macro block division mode disturbance costs can be made according to different application scenes, and high flexibility is achieved.
Owner:INST OF INFORMATION ENG CAS
Large-dynamic-range image watermarking method against tone mapping
ActiveCN107067362AImprove versatilityImprove robustnessImage data processing detailsTone mappingImaging quality
The invention discloses a large-dynamic-range image watermarking method against tone mapping. The method comprises the steps: manually setting the image quality value of a large-dynamic-range image with an embedded watermark relative to an original large-dynamic-range image in a watermark embedding process, so that a user achieves the balance between invisibility and embedding capacity, and the flexibility and practicality are higher; carrying out the effective extraction of watermark information in the extraction process of the watermark from the large-dynamic-range image obtained after a conventional attack of the large-dynamic-range image with the embedded water mark or a small-dynamic-range image after a tone mapping attack, thereby meeting the robustness requirements of the digital watermark of the large-dynamic-range image. Therefore, the method is high in practicality, can resist all tone mapping attacks, is good in robustness, and is low in watermark error rate. The method does not depend on the storage format of the large-dynamic-range image, and is suitable for the large-dynamic-range images at formats of RGBE, OpenEXR or LogLuv.
Owner:NINGBO UNIV
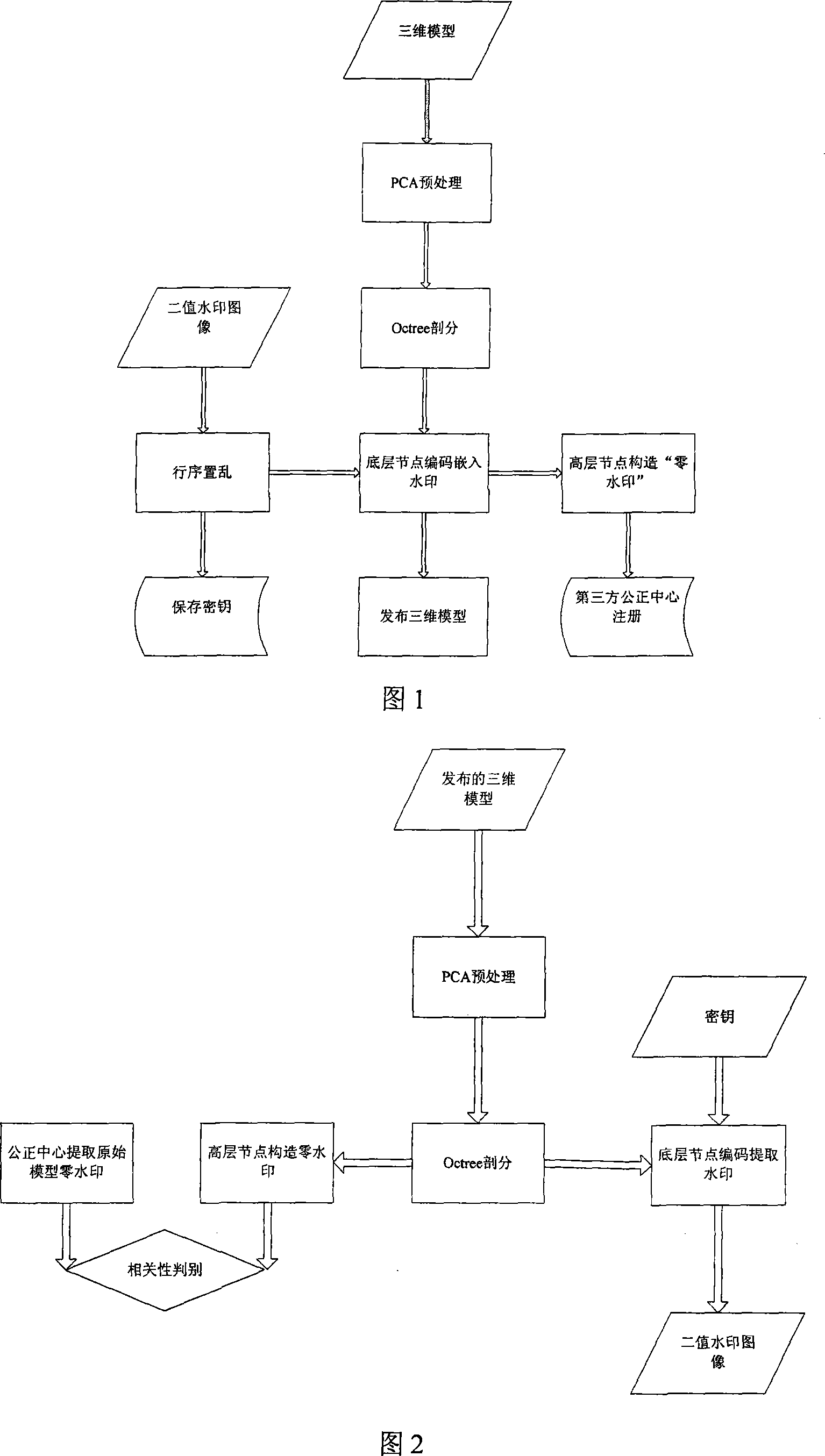
Three-dimensional grid digital blind watermark method based on Octree encode
InactiveCN101178805APracticalImprove robustnessImage codingImage data processing detailsPoint cloudWatermark method
The invention relates to a three-dimension grid number blind watermarking method based on an Octree code, comprising the steps as follows: pretreating a model through principal component analysis to gain a unique gesture direction of the model; carrying out Octree subdivision for the three-dimension model to acquire Octree structure and code data; selecting the code of a specific Octree level and node to be embedded with significant and tremendous watermarking information. The invention does not need the original model data when extracting the watermark and the arithmetic is irrelative to the model topology, allowing watermark inlay of point cloud data. Furthermore, the invention is characterized by large inlay quantity, good resistance against rotation, horizontal movement, zoom and top point reorder attack. According to zero watermark constructed with the Octree high-layer code, the invention having high robustness and university is capable of resisting even simplification, noise and attack from secondary gridding, etc., to some extent.
Owner:BEIHANG UNIV
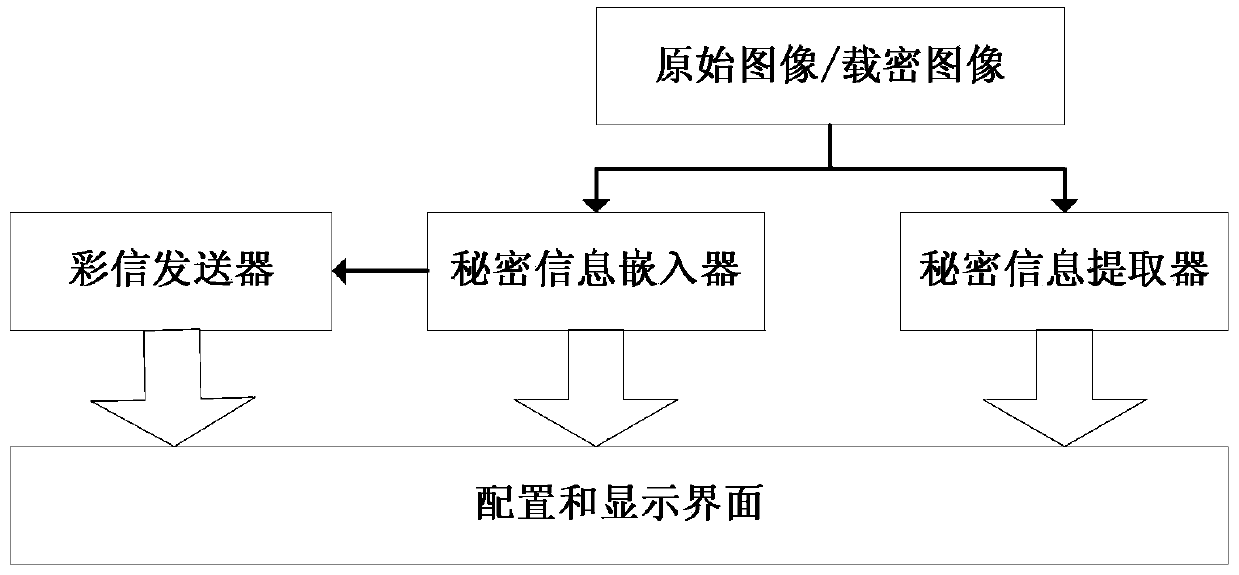
Image steganography and secret information extraction method based on intelligent mobile terminal
InactiveCN103442156AImprove sending efficiencyIncrease embedding capacityMessaging/mailboxes/announcementsPictoral communicationInformation embeddingSystem safety
The invention relates to an image steganography and secret information extraction method based on an intelligent mobile terminal. The intelligent mobile terminal comprises a secret information embedder, a secret information extractor and a multimedia message transmitter, and images are selected by the intelligent mobile terminal for different use purposes. If secret information needs to be embedded, original pictures are selected. If the secret information needs to be extracted, encrypted pictures are selected. The selected original pictures are uploaded into the secret information embedder for the secret information embedding operation, and the encrypted pictures are uploaded into the secret information extractor for the secret information extraction operation. If the current operation is the secret information embedding operation, the encrypted pictures embedded with the secret information are uploaded into the multimedia message transmitter, and are sent to a receiver in a multimedia message mode. Compared with the prior art, the image steganography and secret information extraction method has the advantages that the functions of secret information embedding, multimedia message sending and secret information extraction are achieved in the intelligent mobile terminal, system safety is enhanced, and meanwhile multimedia message sending efficiency is improved.
Owner:NINGBO UNIV
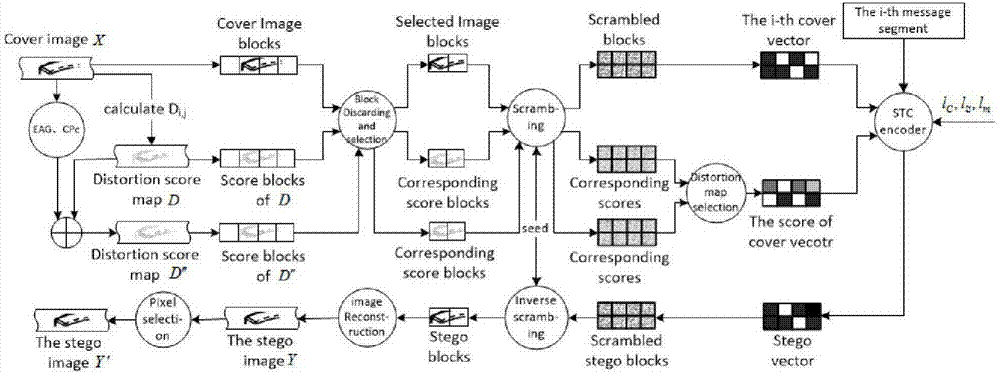
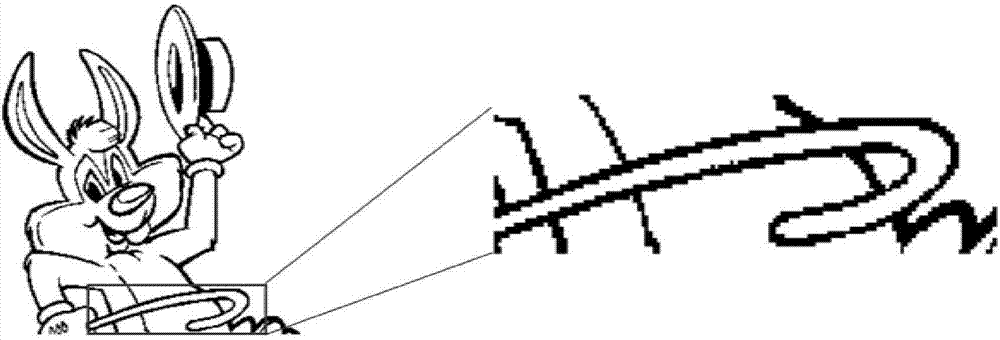
Binary image steganography method based on disturbance distortion and pixel selection
ActiveCN107133991AImprove visual qualityStrong anti-detection abilityImage codingInformation transmissionComputer vision
The invention provides a binary image steganography method based on disturbance distortion and pixel selection, which is characterized in that a distortion condition brought about by pixel overturn of a binary image is calculated according to a more appropriate disturbance measurement method, secret information is embedded through STC encoding, the embedding capacity of the secret information is improved, a secret carrying image is acquired, post-processing is performed on the secret carrying image according to a pixel selection strategy, and a binary steganographic image used for channel transmission is acquired. The binary steganographic image acquired according to the invention is higher in visual quality and higher in safety and anti-detection capacity compared with previous methods. The invention further provides a post-processing strategy for pixel selection in consideration of mutual influences existing between turnover pixels, and a safer binary steganographic image with higher visual quality is acquired. The binary image steganography method can be used for the information security and especially for the aspect of binary image secret information transmission.
Owner:SUN YAT SEN UNIV
H.264/AVC video reversible data hiding method
ActiveCN106817586AMeet application needsLittle impact on code rateDigital video signal modificationHistogramHidden data
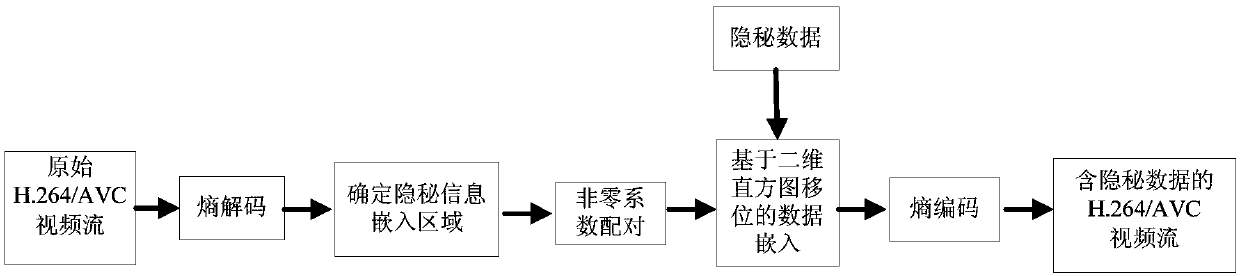
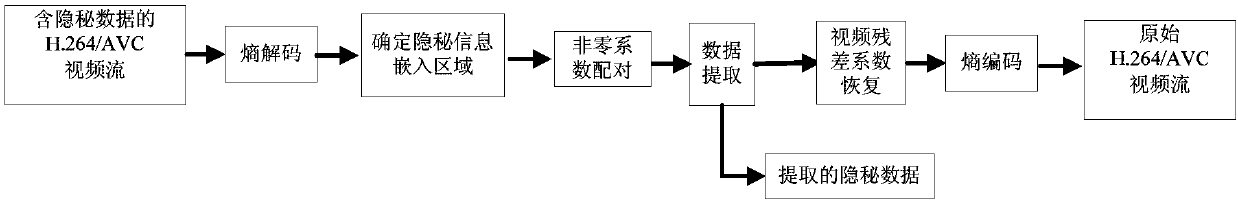
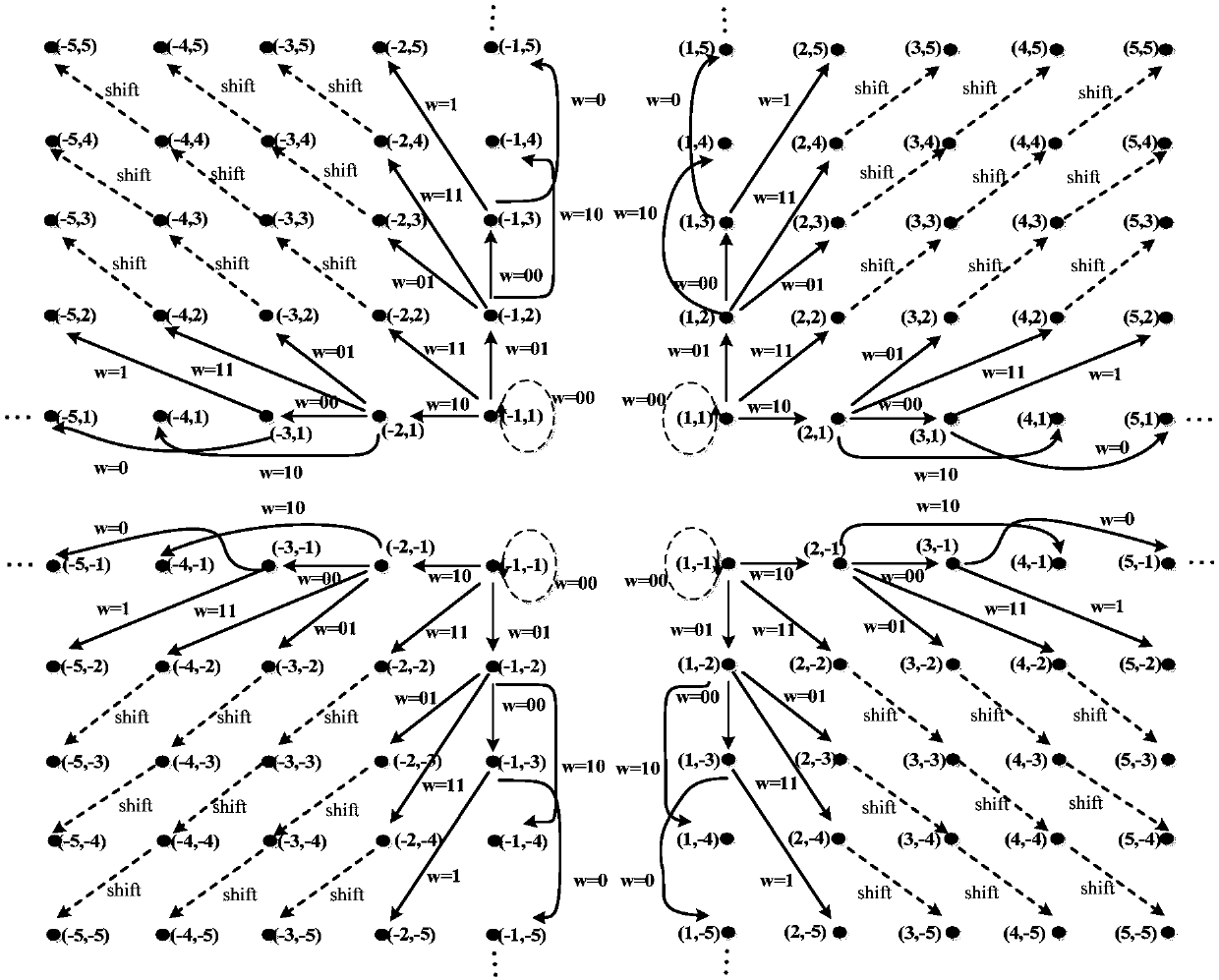
The invention discloses a H.264 / AVC video reversible data hiding method comprising H.264 / AVC video reversible data hiding, hidden data extraction and original video recovery; under the prerequisite of compatible with H.264 / AVC video compression coding standards, the method selects residual error coefficients in a 4*4 sub-block to expand or shift, thus hiding the reversible data; the method is low in calculation complexity, can satisfy real time video application demands, and the hiding data has very little influences on the H.264 / AVC video bitstream code rate; the method pairs two adjacent non-zero residual error coefficients as basic embedding units, can modify a two dimension residual error coefficient histogram to pair the residual error coefficients and to expand or shift, thus embedding the hidden information; the residual error coefficient with big appearance frequency has more bits on the embedded hidden information, thus keeping good perception quality, and providing high embedding capacity; the method can ensure the hidden information to be effectively extracted, thus fully recovering the original video after the hidden information is extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Antistatistical analysis image LSB information hiding method based on chaos system
InactiveCN101022332AIncrease embedding capacityImprove securityImage data processing detailsSecuring communicationPattern recognitionStatistical analysis
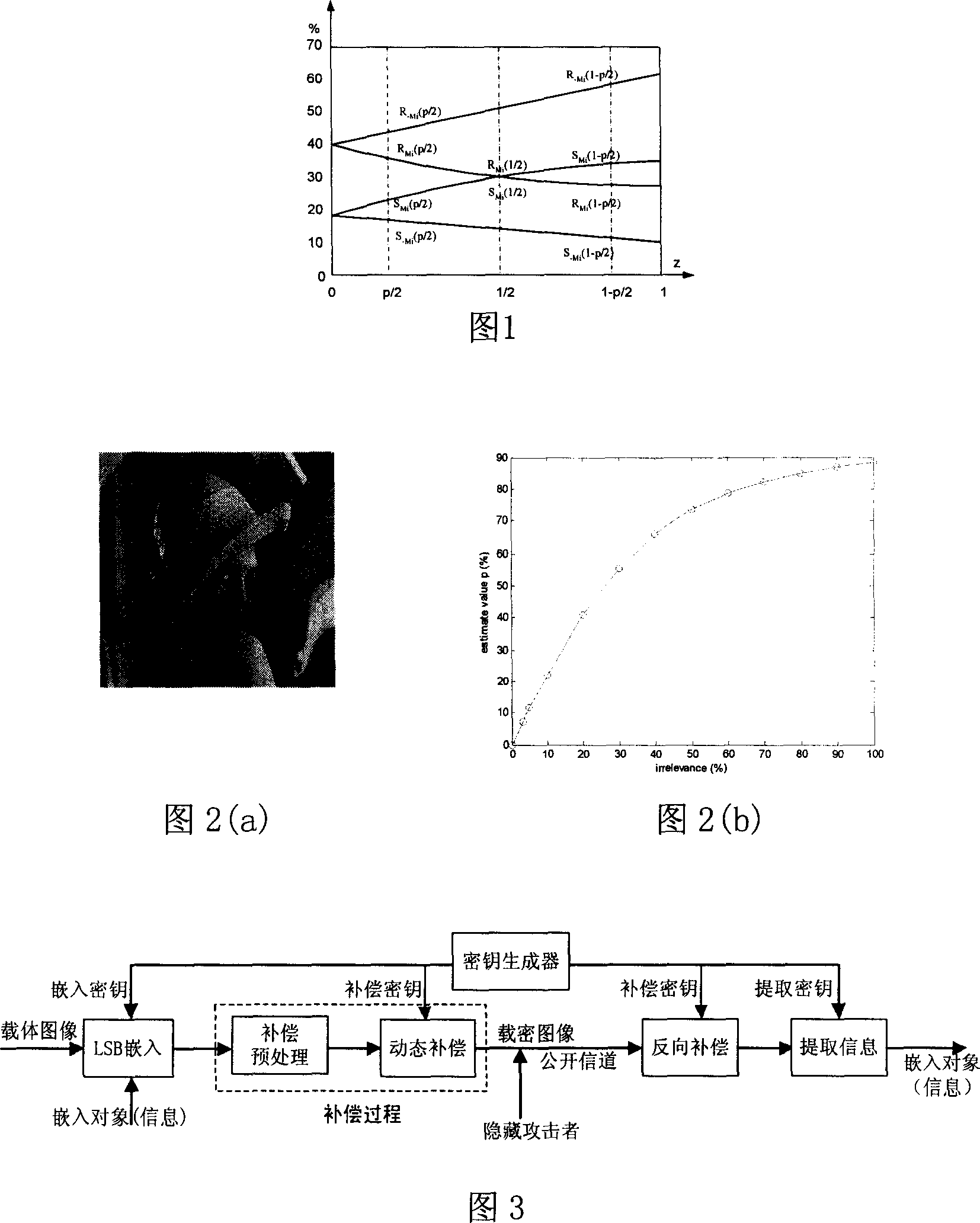
An information-hiding method of anti-statistic analysis image based on chaos system includes selecting embedded-position by random sequence generated on basis of chaos system first then carrying out LSB random-embedding and carrying out dynamic compensation on embedded image.
Owner:刘粉林 +2
Asymmetric prediction error histogram modification-based reversible information hiding method
ActiveCN107944282AQuality improvementIncrease embedding capacityImage enhancementDigital data protectionImaging qualityAlgorithm
The invention discloses an asymmetric prediction error histogram modification-based reversible information hiding method. The method comprises the following steps of performing overflow preprocessing;calculating a peak point and a zero point; embedding secret information; extracting the secret information; and performing overflow recovery processing. A compensation principle can be well utilizedno matter whether an embedded information quantity is maximal or minimal; when the embedded information quantity is relatively small, fewer pixel points can be modified, so that the quality of a secret-carrying image is improved; and meanwhile, by utilizing secondary embedding, the image quality is improved while the embedding capacity is expanded.
Owner:ANHUI UNIVERSITY
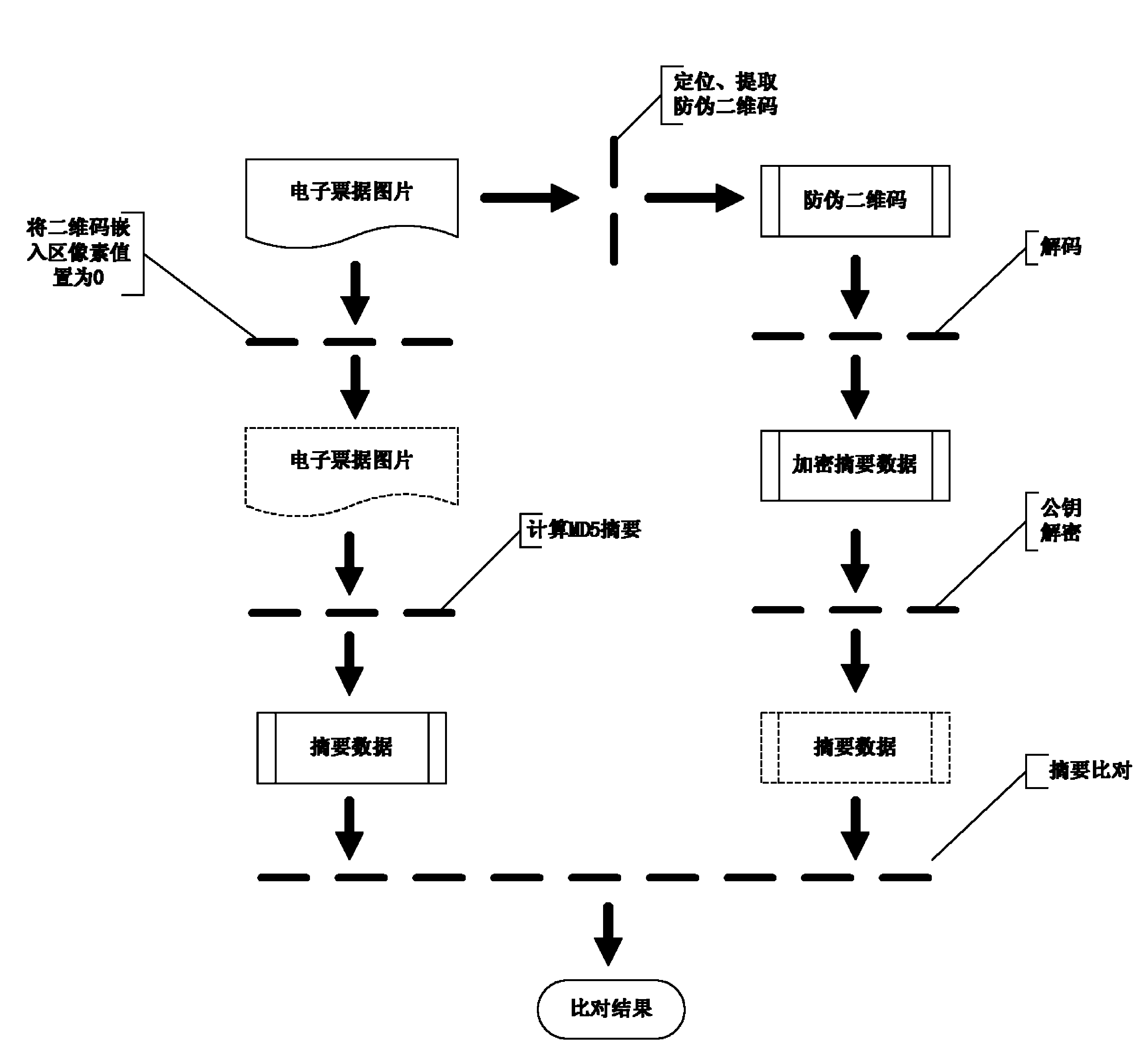
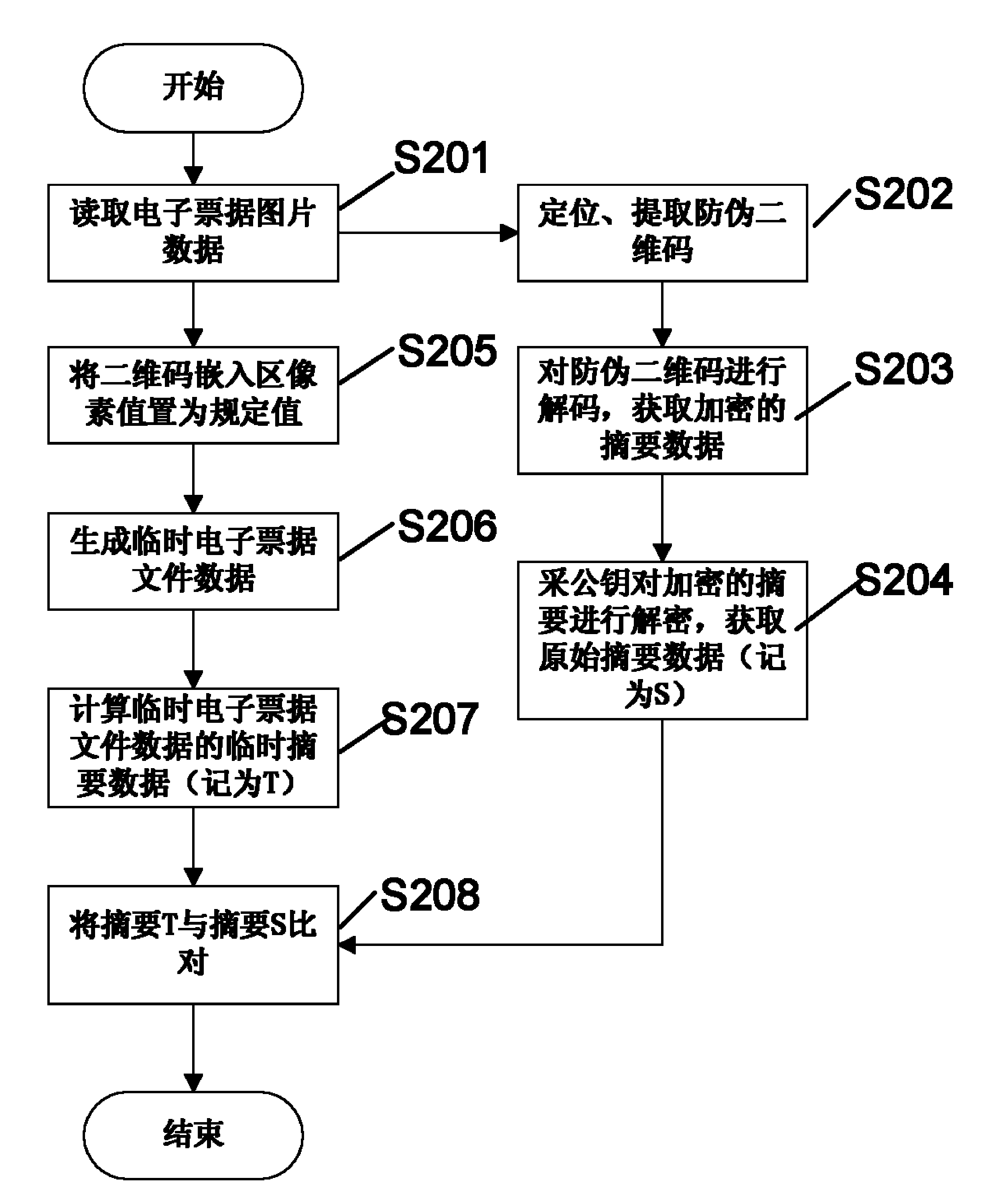
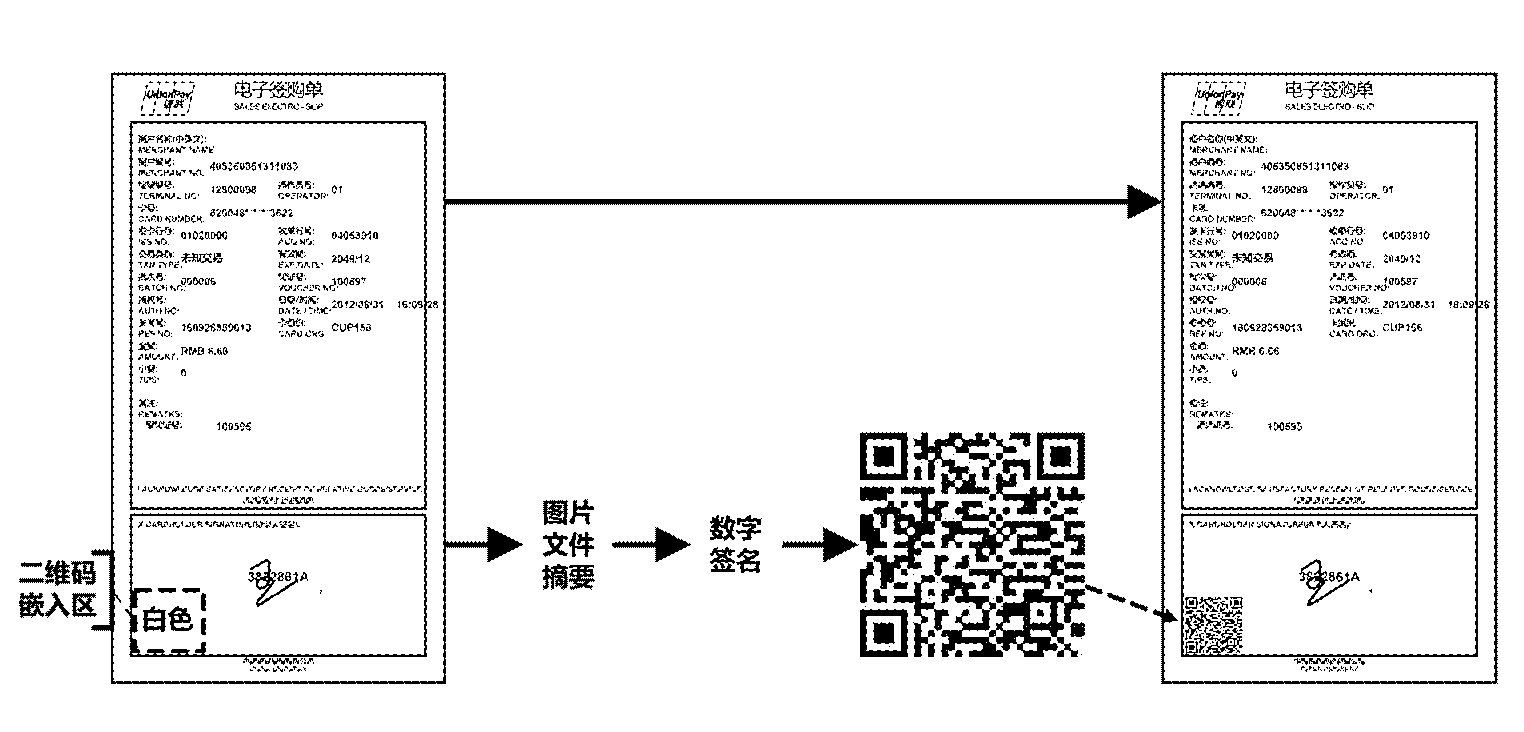
Methods and systems for generating and checking electronic note with anti-counterfeiting two-dimension code
InactiveCN104077624AImprove embedding capacity and recognition rateImprove style diversity and practicalityBilling/invoicingRecord carriers used with machinesAlgorithmTheoretical computer science
The invention relates to methods and systems for generating and checking an electronic note with an anti-counterfeiting two-dimension code. The method for generating the electronic note with the anti-counterfeiting two-dimension code comprises the following steps that: an original electronic note picture is read, and a temporary electronic note picture with a defined two-dimension code embedding region is generated; for the temporary electronic note picture, an information abstract algorithm is utilized for calculating abstract data, and in addition, the obtained abstract data is encrypted for generating the anti-counterfeiting two-dimension code; and the anti-counterfeiting two-dimension code is embedded into the two-dimension code embedding region of the original electronic note picture, and the electronic note with the anti-counterfeiting two-dimension code is obtained. The methods and the systems provided by the invention can be used for effectively preventing the tampering and the counterfeiting of the electronic note, and in addition, the diversity and the practicability of the electronic note can be greatly improved.
Owner:CHINA UNIONPAY
Reversible image watermark method based on quantized DCT coefficient zero values index
InactiveCN101572819AImprove visual qualityIncrease embedding capacityTelevision systemsDigital video signal modificationWatermark methodJPEG
A reversible image watermark method based on quantized DCT coefficient zero values index includes a watermark embedding process, a watermark extraction process and an image recovery process; wherein the watermark embedding can be applied in two modes: embedding is carried out during the process in which pixel image is compressed into JPEG image, or embedding is carried out in coded JPEG image. Specific embedding process aiming at mode I includes: (1) the original image is preprocessed, namely blocking (the size of block is generally 8*8), DCT transforming (discrete cosine transform) and quantization, thus obtaining quantized DCT block; (2) index value of medium-high frequency zero coefficient of the quantized DCT block is used for watermark embedding, and non zero coefficient probably generating ambiguity at extraction end is modified; (3) losses coding, such as run length coding and entropy coding, is carried out on the quantized DCT block embedded with watermark to obtain JPEG image; in the extraction process, the medium-high frequency coefficient index value of the quantized DCT block is utilized to extract watermark and recover the original image without loss by inverse operation of embedding method; the embedding and extraction process of mode II is similar. The invention has reversibility, reduces the ratio of the modified coefficient and embedded watermark digit, and can embed massive watermarks while causing less distortion.
Owner:BEIHANG UNIV
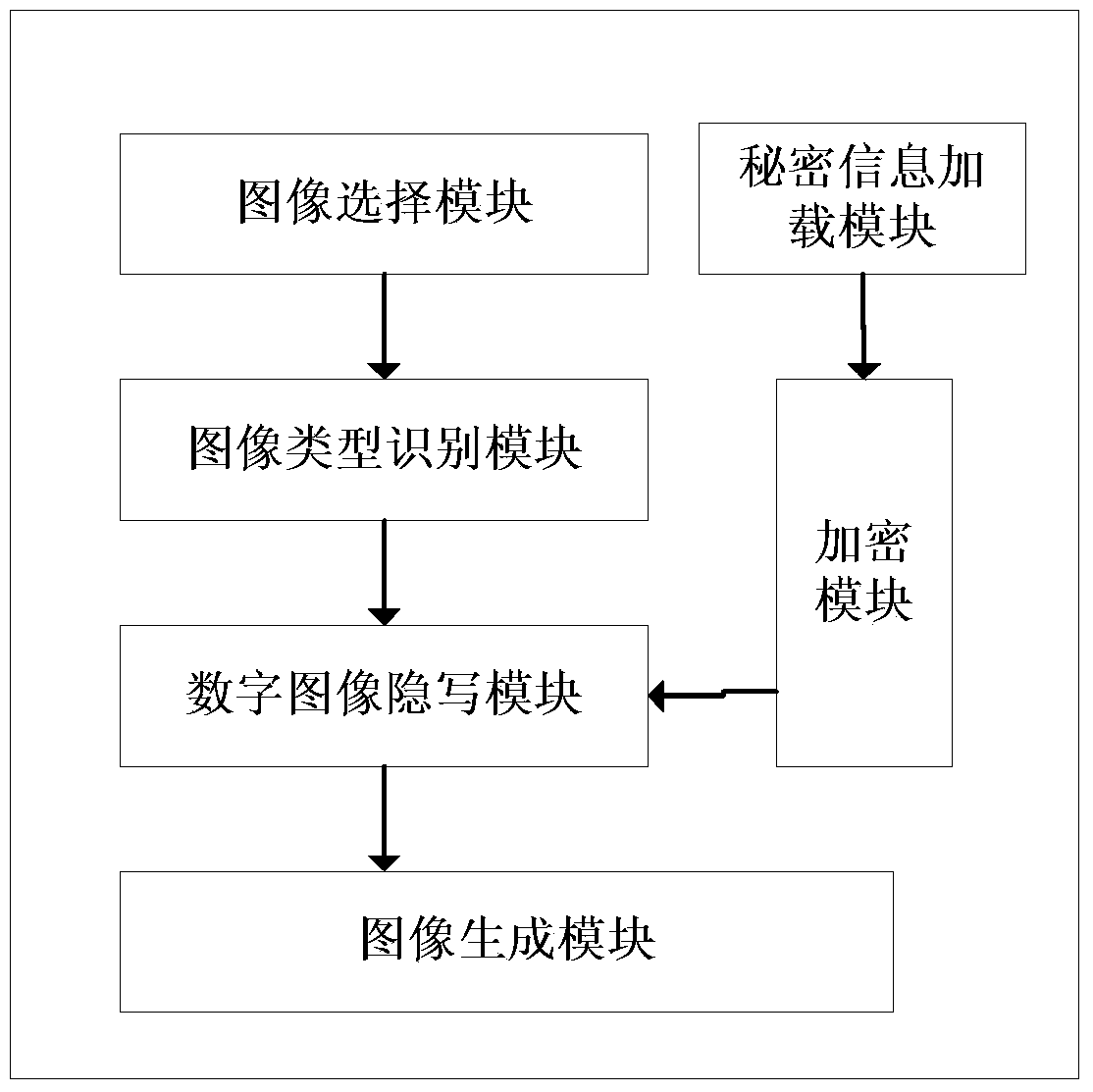
Universal steganography method based on deep learning
PendingCN110533570ACannot be resolved completelyResolve accuracyCharacter and pattern recognitionImage data processing detailsPattern recognitionDiscriminator
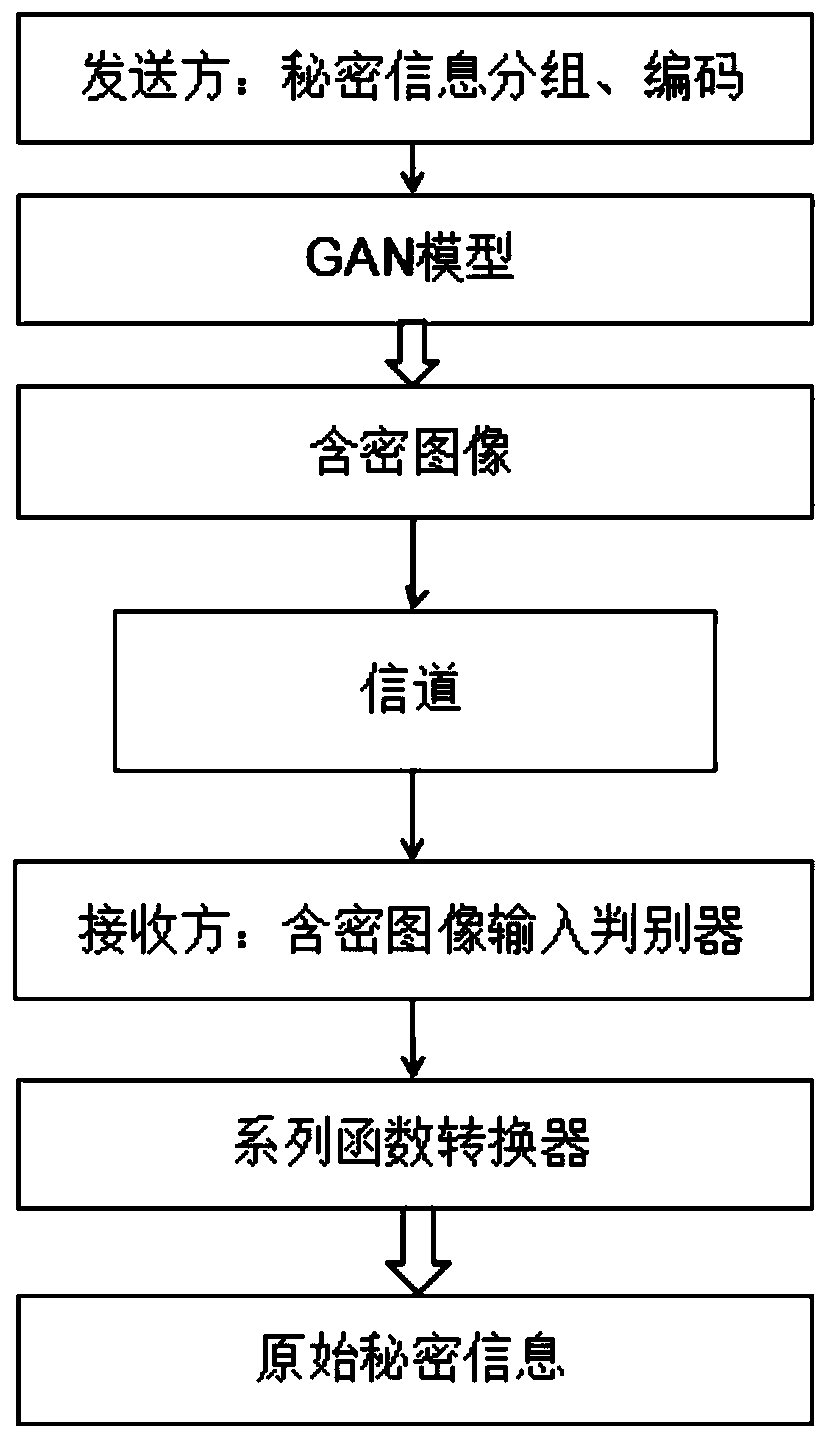
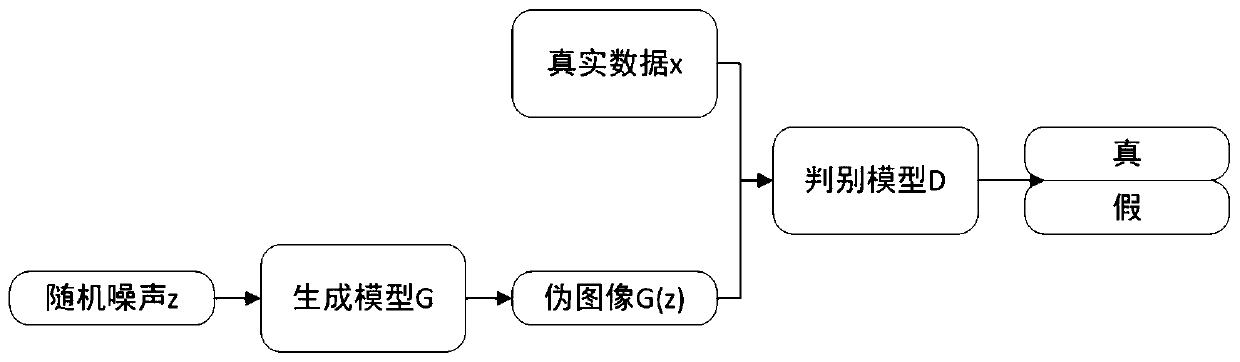
The invention discloses a general steganography method based on deep learning. The method comprises the following steps: S1, carrying out hiding processing on a sender; dividing secret information tobe hidden into n groups of information fragments, wherein each group of information fragments correspond to one category label, a deep learning model is adopted, the category label and random noise are used as drive, a pseudo-natural image of a specified category is generated, and the pseudo-natural image is used as a secret-containing image input channel after hiding processing; and S2, carryingout extraction processing at a receiver: inputting the secret-containing image into a discriminator by the receiver to carry out image authenticity identification and image category judgment, then sending the image category information into a function converter to be processed to obtain a secret information fragment, and decoding the secret information fragment to obtain original secret information. According to the invention, the security and confidentiality of information transmission can be greatly improved.
Owner:NANJING INST OF TECH
Encryption domain image reversible data hiding method based on neighborhood prediction
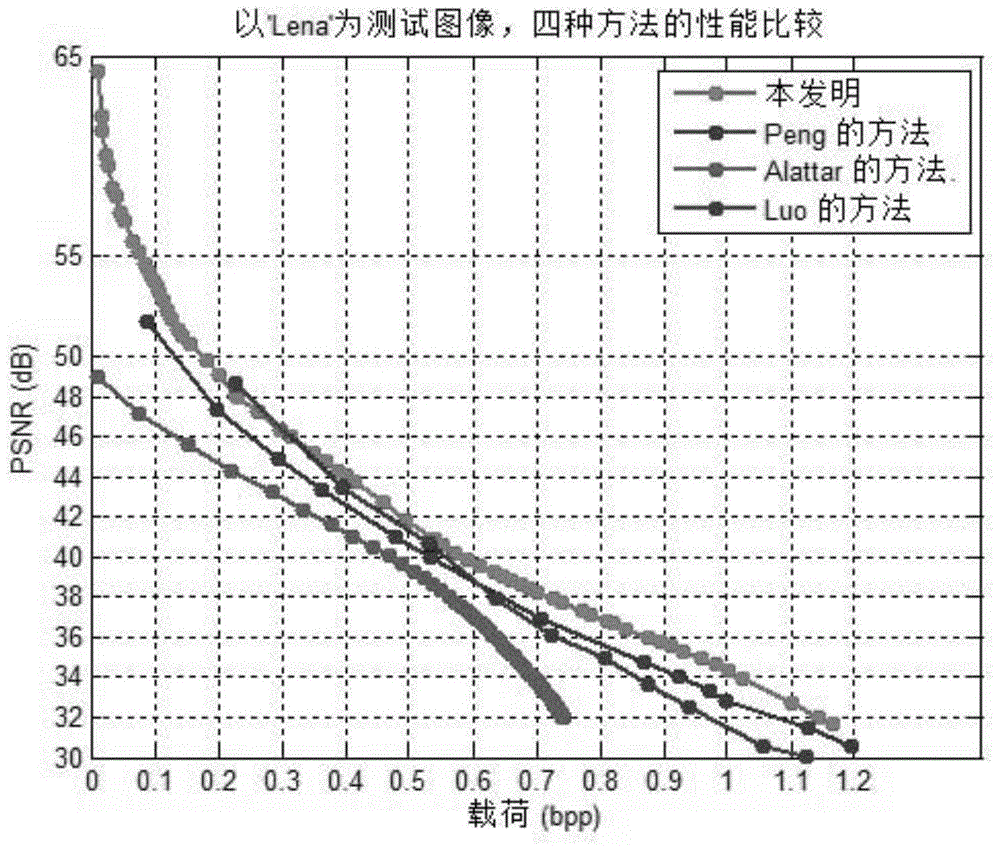
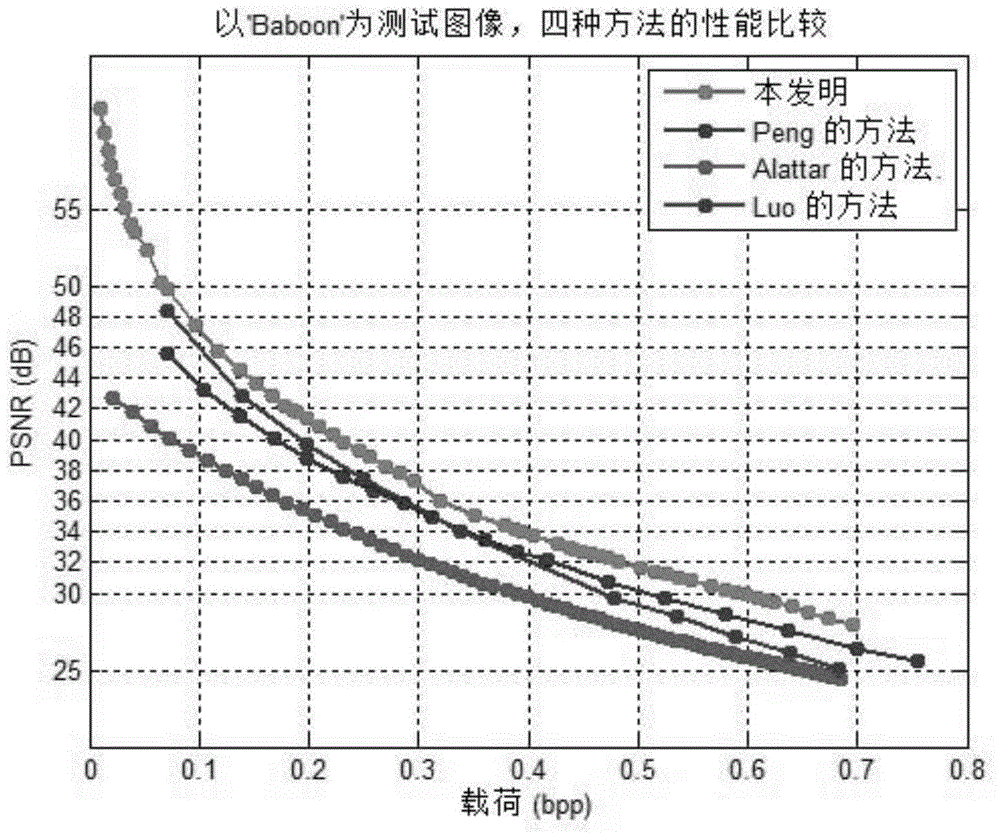
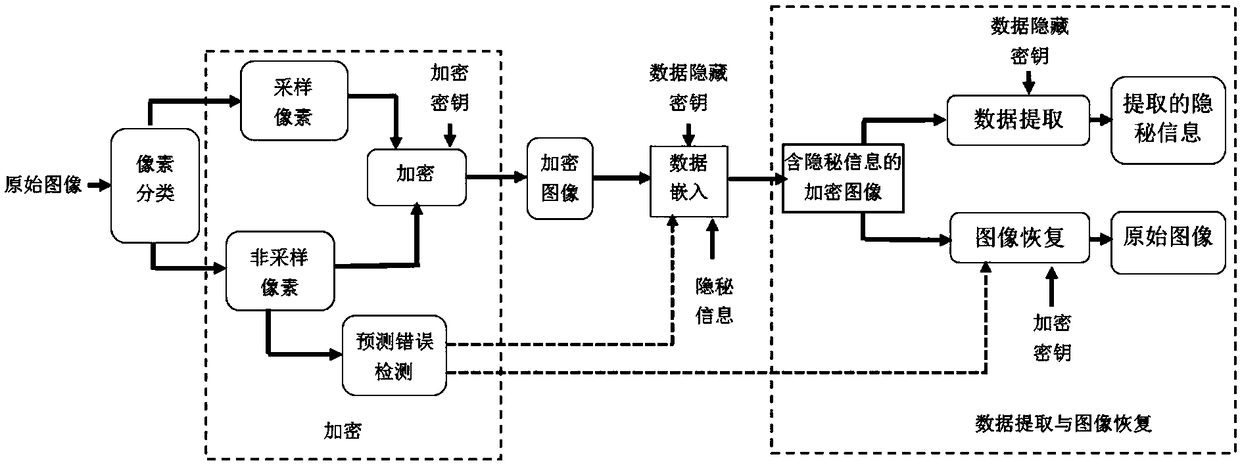
ActiveCN109803142AIncrease embedding capacityImprove forecast accuracyDigital video signal modificationPattern recognitionImage segmentation
The invention discloses an encrypted domain image reversible data hiding method based on neighborhood prediction. The method comprises three steps including Image Encryption reversible data hiding and; secret information extraction; In the image encryption part, an image is segmented into image blocks; the pixel value of each pixel point in each image block and the value of one element in the random sequence are added for encryption, and modulo operation is performed on 256 to realize encryption ; the linear prediction difference values meeting the specific conditions in the image blocks arekept consistent before and after encryption; data hiding in the encrypted image can be ensured; The method has the advantages that hidden information extraction and image decryption are achieved, complete separation of hidden information extraction and image decryption is guaranteed, hidden information can be effectively extracted in an encryption domain, hidden information can also be effectivelyextracted in a decryption domain, the practicability is higher, and meanwhile it can be guaranteed that an original image can be restored without distortion after the hidden information is extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Vector map reversible information hiding method based on LSD planes
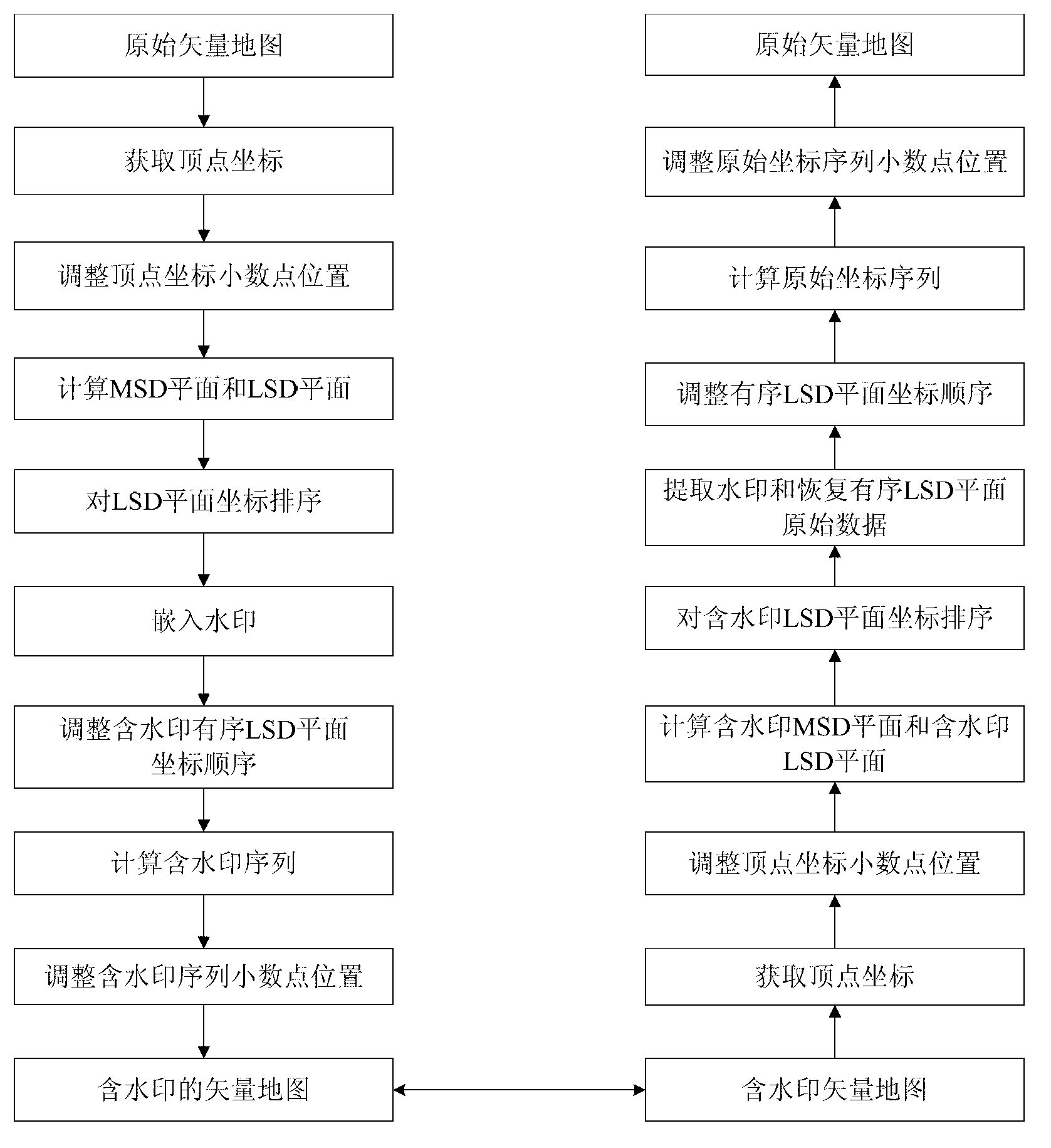
InactiveCN103325082AEasy to useGain invisibilityMaps/plans/chartsImage data processing detailsInformation hidingVector map
The invention relates to a vector map reversible information hiding method based on LSD planes. Top points of a vector map are sequentially scanned to obtain x-coordinate sequences and y-coordinate sequences of the top points; scaling positions of the coordinates are moved towards the right side to obtain new coordinate sequences; MSD planes and the LSD planes are calculated; the LSD planes are sequenced according to the ascending sequence to obtain orderly LSD planes; watermarks are embedded in the orderly LSD planes; the coordinate sequences of the orderly LSD planes containing the watermarks are adjusted to obtain LSD planes containing the watermarks; the coordinate sequences containing the watermarks are obtained through calculating; scaling positions of the coordinates in the coordinate sequences containing the watermarks are adjusted; a vector map containing the watermarks is obtained.
Owner:HARBIN ENG UNIV
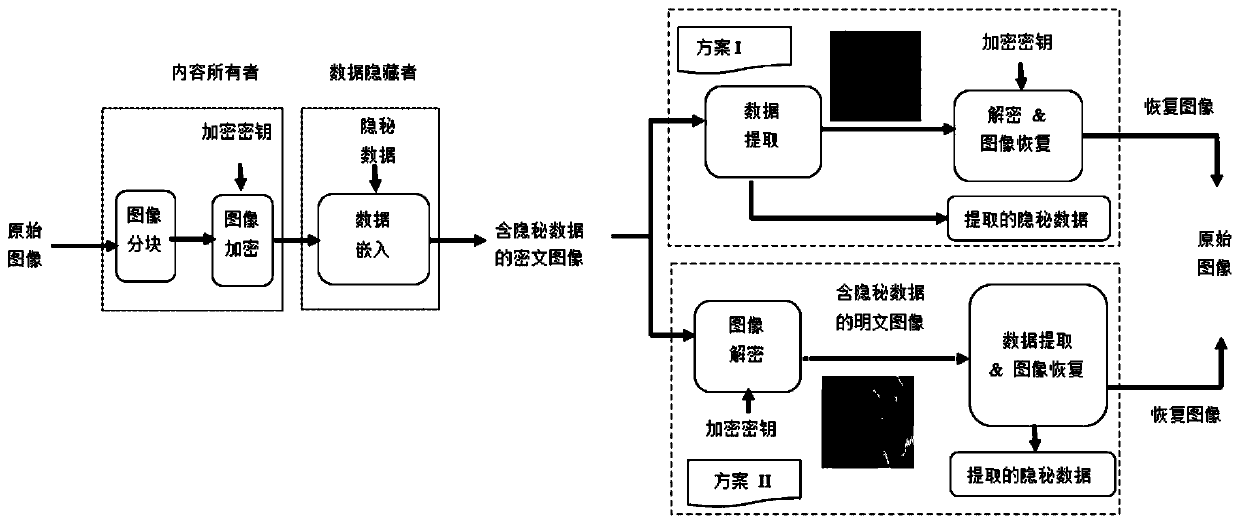
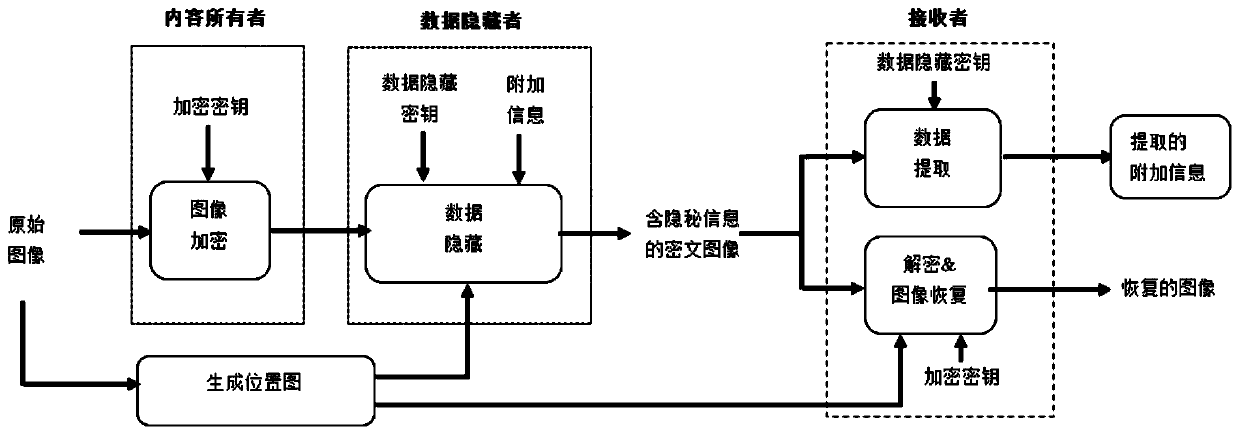
Dual encryption type reversible data hiding method of encryption domain image
ActiveCN107809644AImprove securityFix security issuesDigital video signal modificationSelective content distributionDistortionXML Encryption
The invention discloses a dual encryption type reversible data hiding method of an encryption domain image. The method comprises three parts, namely, image encryption, reversible data hiding of the encryption domain image, secrete data extraction and original image lossless restoration; a double encryption mechanism is adopted in the image encryption part to enhance the security; secret information can be directly embedded in the encrypted images, even if the data hider knows nothing about the original image contents, the image content security and privacy leakage problems can still be effectively solved, no complex protocol is needed between the image encipherer and the secret information embedding person, and the encryption and data embedding generate no expansion of image data; the practicability is high, if only a data hiding key is present, the hidden secret information can be directly extracted from a ciphertext domain image; if only an encryption key is present, an approximate original image can be obtained by direct decryption; and if the data hiding key and the encryption key are present, it can be guaranteed that the original image can be restored without distortion afterthe hidden secret information is extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Self-adaptive reversible information hiding method based on pixel replacement
InactiveCN107818266AAchieve hiddenIncrease embedding capacityImage codingDigital data protectionPattern recognitionInformation hiding
The invention relates to a self-adaptive reversible information hiding method based on pixel replacement. According to the method, a more effective embeddable unit is constructed, differentiation encoding is conducted on the gray level trend of an embeddable region of the embeddable unit according to characteristics of different carrier images, and finally information is embedded through pixel replacement. According to the algorithm, according to embeddable conditions, the embedding capacity is improved while overlarge influences of the steganography process on the visual quality of the imagesare avoided. Besides, the embeddable pixel pair self-adaptive re-encoding process based on the gray level trend characteristics is added, and the algorithm embedding capacity is improved to the largest extent. Finally, the mil is embedded in a pixel replacement mode, so that the algorithm has a gray level histogram stability.
Owner:ZHEJIANG UNIV OF FINANCE & ECONOMICS
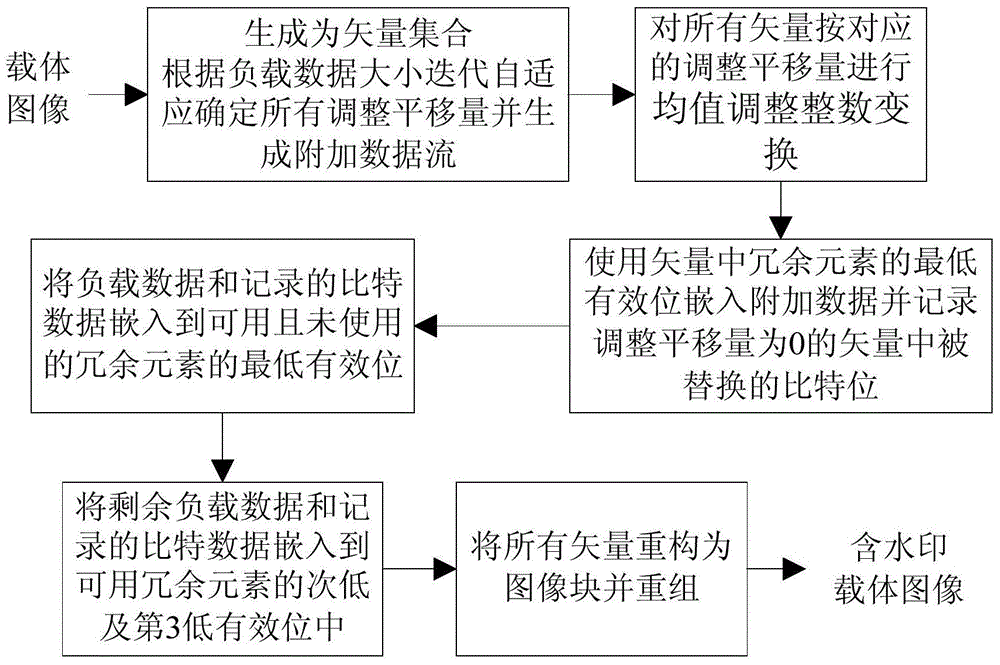
Iterative self-adaptive reversible watermark embedding and extracting method
ActiveCN104835109AIncrease embedding capacityEmbedded Capacity GuaranteeImage data processing detailsAlgorithmWatermark method
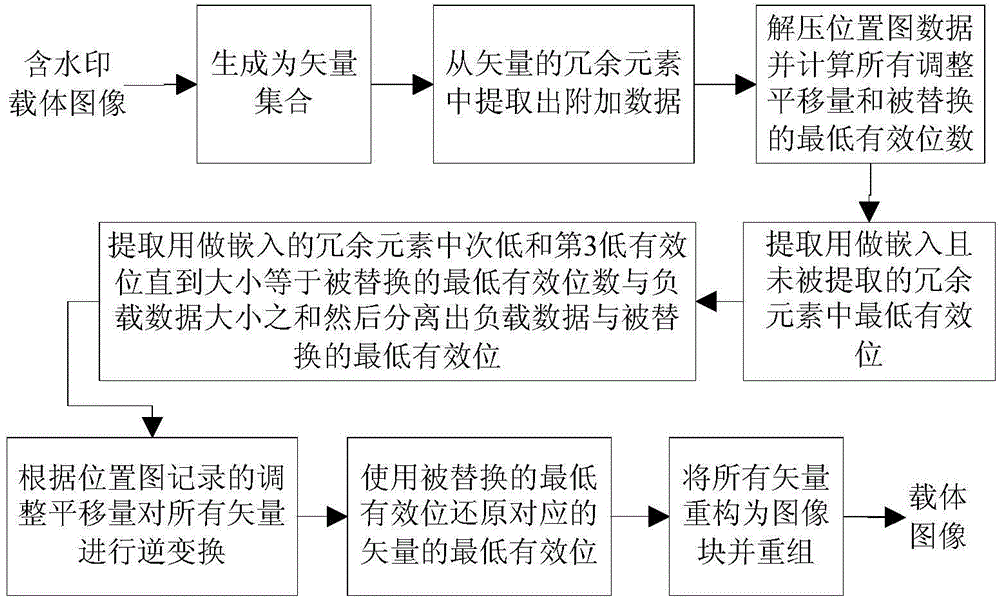
The invention provides an iterative self-adaptive reversible watermark embedding and extracting method. The embedding method firstly adopts an iterative self-adaptive method to select an adjustment translation amount to achieve a balance of watermark embedding capacity and embedding carrier visual quality according to influence of the load data size and an integer vector on a peak signal to noise ratio; then a complete location map generation strategy is given according to a principle that neighboring pixel values are close so as to improve location map compression performance; and finally a layered orderly embedding strategy is adopted to embed load data in the lowest, the second lowest and the third lowest significance bits to avoid a circumstance that the capacity is sufficient but embedding cannot be realized. Compared with a conventional mean value adjustment integer transformation reversible watermark, the method provided by the invention can still maintain a large embedding capacity without setting a threshold value in advance, after a watermark is embedded, visual quality of a shelter is better, performance of the location map generation strategy is better than the conventional mean value adjustment integer transformation reversible watermark method and a compressed location map is smaller, thereby indirectly increasing the embedding capacity.
Owner:SHAANXI NORMAL UNIV
Reversible data hiding method for high-capacity ciphertext domain image
ActiveCN110753226AFast operationPrevent leakageEncryption apparatus with shift registers/memoriesDigital video signal modificationPattern recognitionComplete data
The invention discloses a high-capacity ciphertext domain image reversible data hiding method. The method comprises the steps of binary position map generation, image encryption, ciphertext domain image reversible data hiding, secret information extraction and original image lossless recovery. According to the first part, adjacent pixels are used for predicting a current pixel value, all pixel points in an image are divided into a prediction error type and a prediction accuracy type according to the difference of prediction values, and a binary position map is used for marking; a second part of encrypting the grayscale image by using a binary pseudo-random sequence generated by an encryption key; in the third part, a binary pseudorandom sequence generated by a data hiding key is used for encrypting the hidden information, and three-layer MSB replacement is carried out on pixel points marked as accurate prediction in the ciphertext domain image according to a binary position map so as to complete data embedding; in the fourth part, the original image can be recovered in a lossless manner by using the encryption key, and the secret information can be accurately extracted by using thedigital hidden key; the method has the advantages that information is embedded into three layers of MSB bits of the ciphertext domain image, and the embedding capacity is high.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
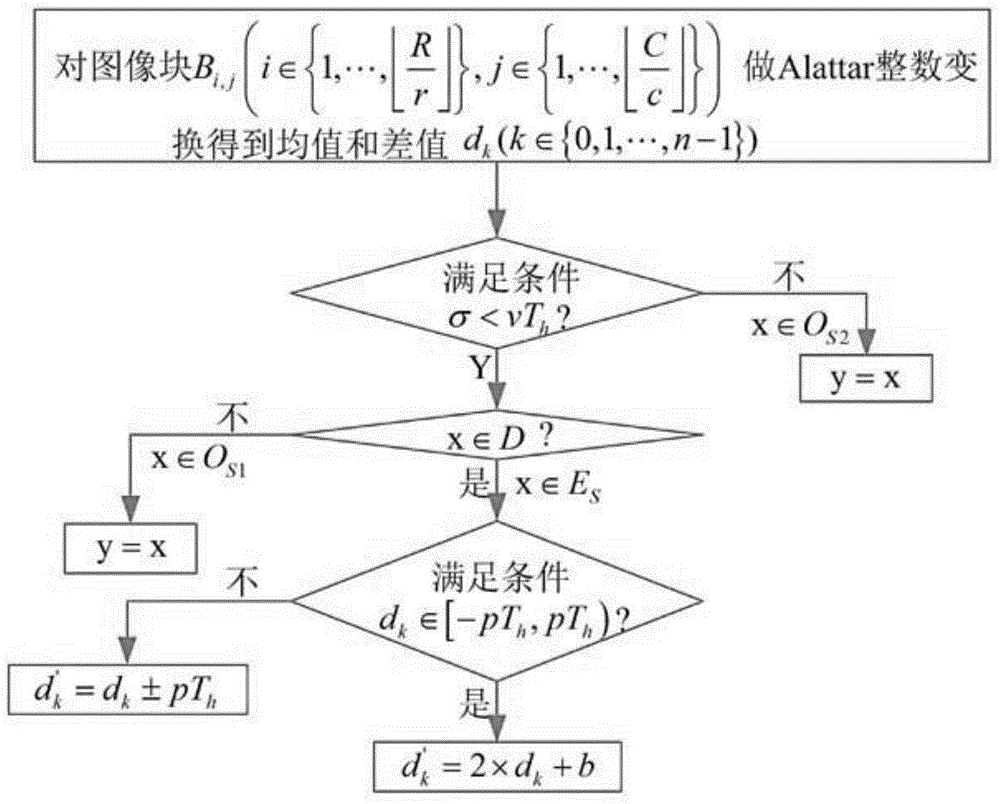
Processing method of reversible watermark on the basis of local positioning and ALattar integer transform
InactiveCN104933668AReduce sizeEfficient compressionImage data processing detailsPattern recognitionEmbedding rate
The invention discloses a processing method of a reversible watermark on the basis of local positioning and Alattar integer transform. The method utilizes the mean value invariance of the Alattar integer transform to evaluate the local texture characteristics of an image block, and specifically, whether the image block is positioned in a smooth area or not is judged through a degree of correlation between the mean value of the certain image block and all pixels surrounding the image block. In order to keep a high visual quality, the image blocks positioned in the smooth area are subjected to watermark embedding, and the image blocks positioned in a texture complicity area are kept constant. A thought that the local texture characteristics of the image blocks are evaluated by the mean value invariance is utilized to solve the problem that a location plan can not be effectively compressed when an embedding rate is low in an Alattar method so as to realize a high PSNR (Power Signal-to-Noise Ratio) value when the embedding rate is low. In a word, the processing method can efficiently compress the location plan through the introduction of the local positioning so as to improve embedding performance.
Owner:GUANGDONG UNIV OF TECH
Ciphertext domain high-capacity image reversible data hiding method
ActiveCN109348230AFix security issuesAddress privacy breachesDigital video signal modificationNon destructiveCryptographic key generation
The invention discloses a ciphertext domain high-capacity image reversible data hiding method, including prediction error detection, image encryption, ciphertext domain image reversible data hiding, secret information extraction and original image non-destructive recovery, wherein in the first part, all pixel points in a grayscale image are first divided into two categories that are sampling pixelpoints and non-sampling pixel points, and then all non-sampling pixel points are marked as prediction errors and accurate predictions respectively; in the second part, the marked grayscale image is encrypted by using a binary pseudo-random sequence generated by an encryption key; in the third part, the secret information is encrypted by using a binary pseudo-random sequence generated by a data hiding key, and then the encrypted secret information is used to embed data into each non-sampling pixel point that is marked as the accurate prediction in a ciphertext domain image; and in the fourth part, only the secret information is extracted, or only the original grayscale image is recovered, or the secret information is extracted first and then the original grayscale image is recovered. The method has the advantages that information can be embedded in the ciphertext domain image, and the embedding capacity is high.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Robust video steganography method for reducing H.264 interframe drift distortions
InactiveCN108769700AQuality improvementReduce drift distortionDigital video signal modificationPattern recognitionVideo quality
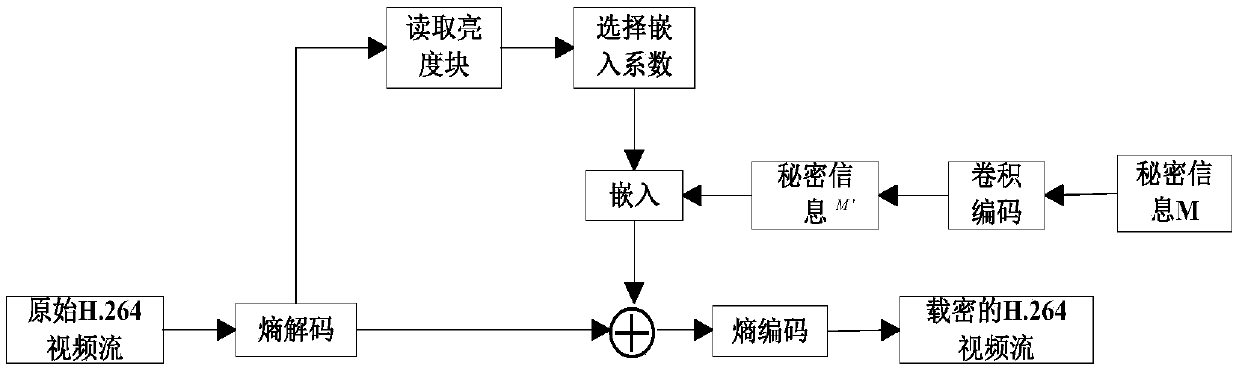
The invention discloses a robust video steganography method for reducing H.264 interframe drift distortions. The method comprises the following steps: step 1, analyzing the interframe drift distortions to obtain the cause of the drift distortions, then classifying the generated drift distortions according to the size, and selecting an embedding position of a DCT brightness coefficient according tothe size of an embedded drift distortion; step 2, carrying out convolutional encoding on an information sequence to be embedded, wherein each input code element corresponds to two output code elements; step 3, embedding an output sequence into the DCT coefficient, after the embedding is completed, performing entropy coding on an H.264 / AVC video stream to form a dense video sequence; and step 4, performing entropy decoding on the H.264 / AVC video stream, extracting an original DCT coefficient, acquiring the output sequence, decoding the output sequence, outputting the information sequence to beembedded, and completing the extraction of the information sequence to be embedded. The robust video steganography method for reducing the H.264 interframe drift distortions provided by the inventionimproves the data embedding capacity, the video quality and the robustness.
Owner:XIAN UNIV OF TECH
Direction changing difference expansion and synchronous embedding reversible watermark embedding and extraction method
ActiveCN106067157AImprove visual qualityHigh computational complexityImage data processing detailsAlgorithmWatermark method
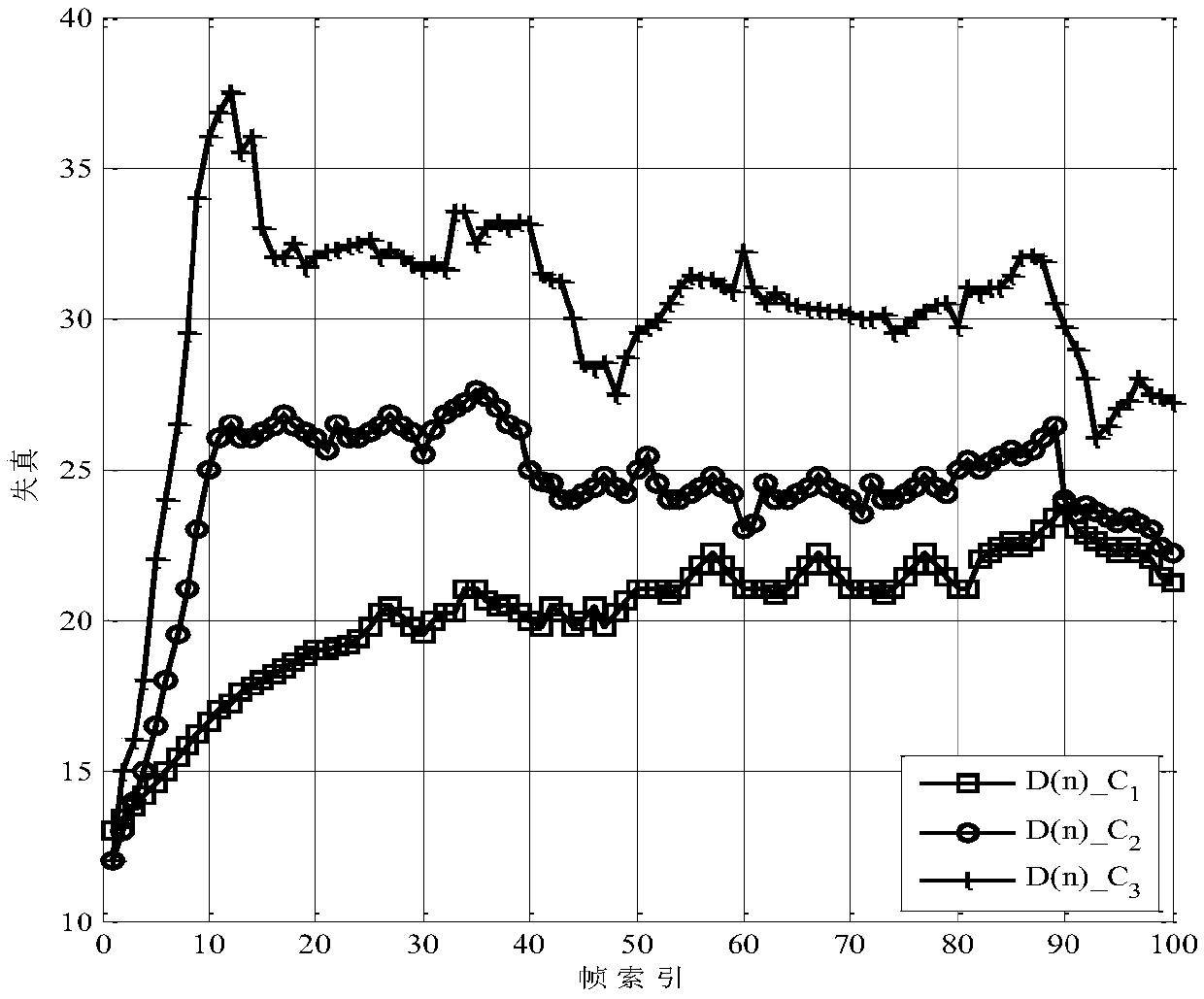
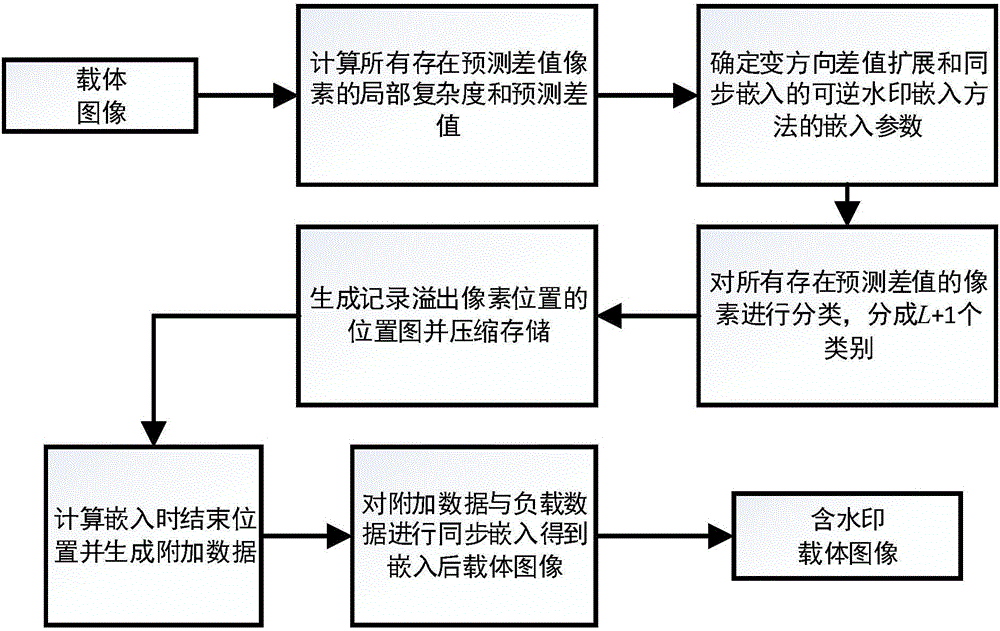
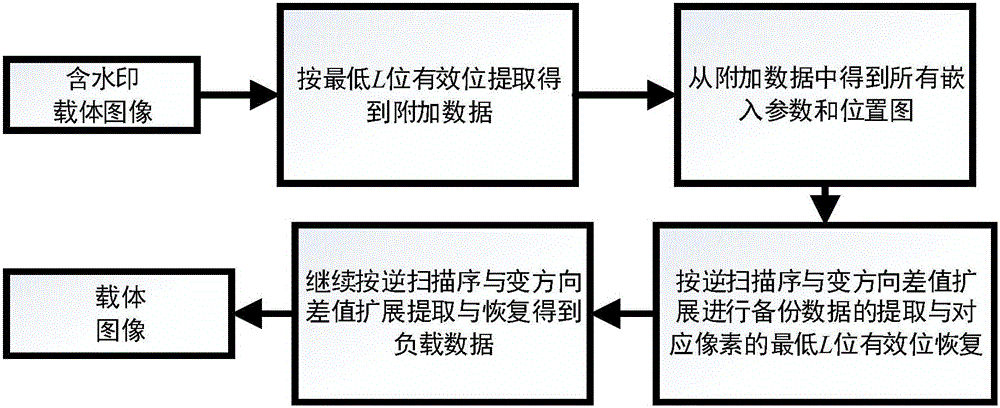
The invention provides a direction changing difference expansion and synchronous embedding reversible watermark embedding and extraction method. Embedding capacity and embedding data are enabled to be unrelated by adopting direction changing difference expansion and the threshold is enabled to select the maximum embedding capacity; and the classification accuracy and the maximum embedding capacity are enhanced by adopting gradient and direct classification for avoiding normalized gradient and reduction of the classification accuracy. A compressed location graph is applied so that large consumption of the embedding capacity and excessive additional data caused by recording overflow pixel location of a generic difference expansion and local complexity reversible watermark method can be avoided. The embedding data are ensured to be completely reversible by giving the embedding strategy of synchronous addition of backup data for avoiding irreversibility caused by direct embedding of the additional data after embedding of load data, and an embedding parameter selection method based on ordering and enumeration is also given so as to reduce computational complexity. Compared with the reversible watermark method based on generic difference expansion and local complexity, the method is completely reversible and parameter selection time is greatly reduced so that the method has larger maximum embedding capacity.
Owner:SHAANXI NORMAL UNIV
A reversible data hiding method based on pixel multi-scale prediction
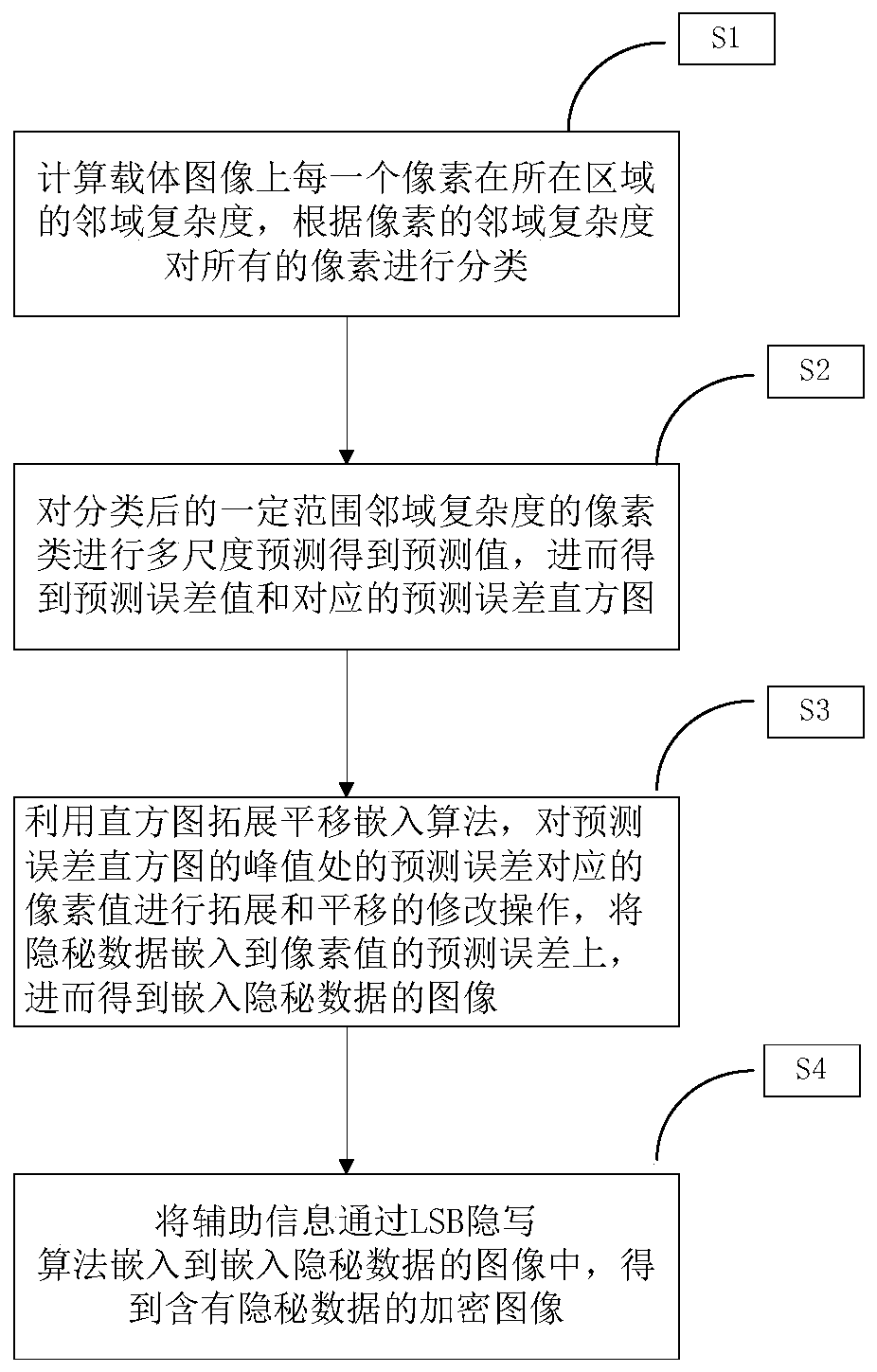
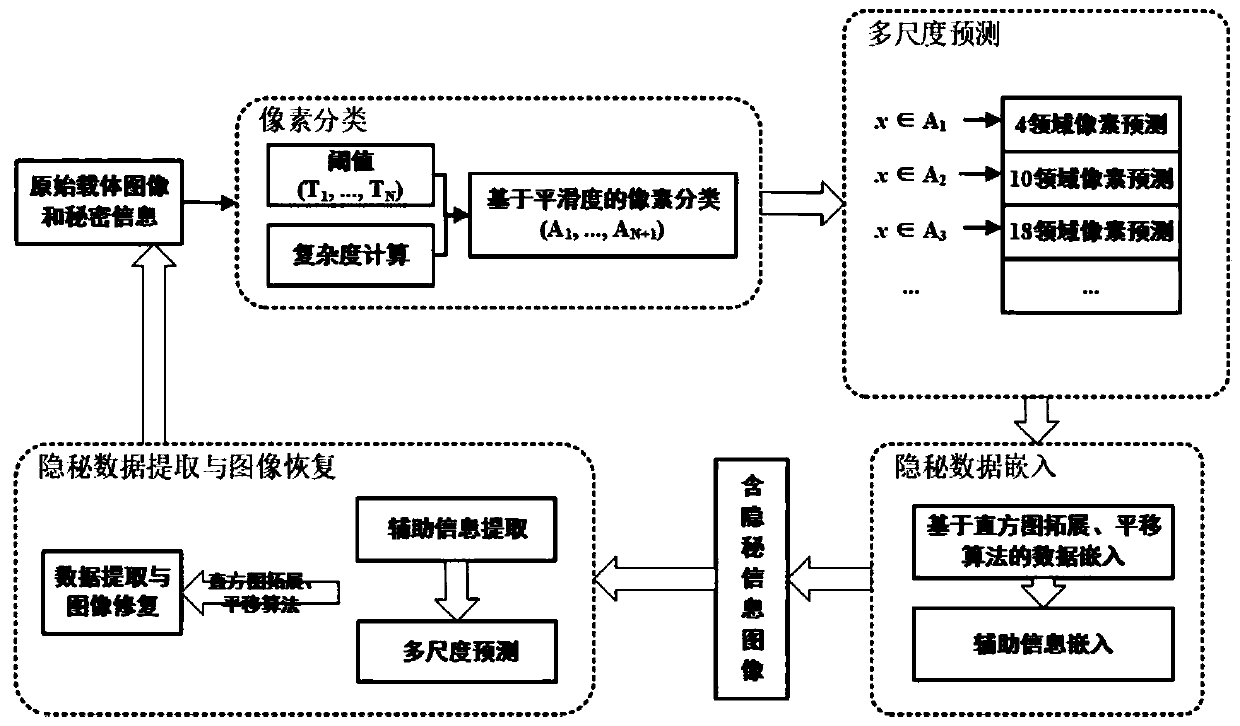
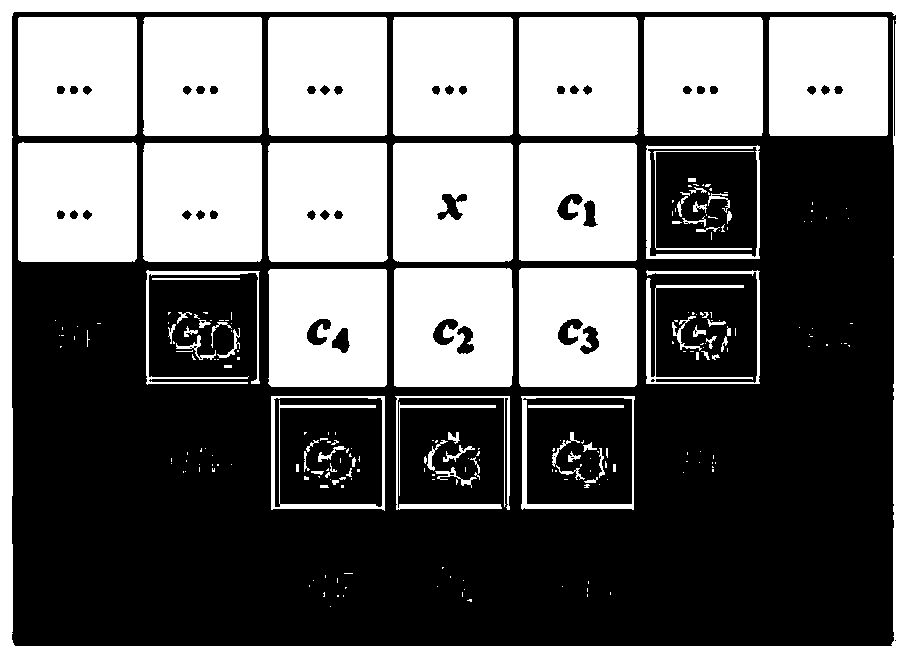
ActiveCN109948307AHigh similarityImprove fidelityProgram/content distribution protectionPictoral communicationLsb steganographyErrors and residuals
The invention provides a reversible data hiding method based on pixel multi-scale prediction, and the method comprises the steps: calculating the neighborhood complexity of each pixel on a carrier image in an area, and carrying out the classification of all pixels according to the neighborhood complexity of the pixels; Performing multi-scale prediction on the classified pixel set with a certain range of neighborhood complexity to obtain a prediction value, and further obtaining a prediction error value and a corresponding prediction error histogram; Using the histogram expansion- translation embedding algorithmto expand and translate the pixel values corresponding to the prediction error at the peak of the prediction error histogram,, and embedding the secret data into the prediction errorof the pixel value so as to obtain an image embedded with the secret data; And embedding the auxiliary information into the image embedded with the secret data through an LSB steganography algorithmto obtain an encrypted image containing the secret data. According to the method, under the condition that a certain embedding capacity is ensured, the embedding distortion of the carrier image is effectively reduced by fully utilizing the information redundancy among the pixels.
Owner:BEIJING JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com