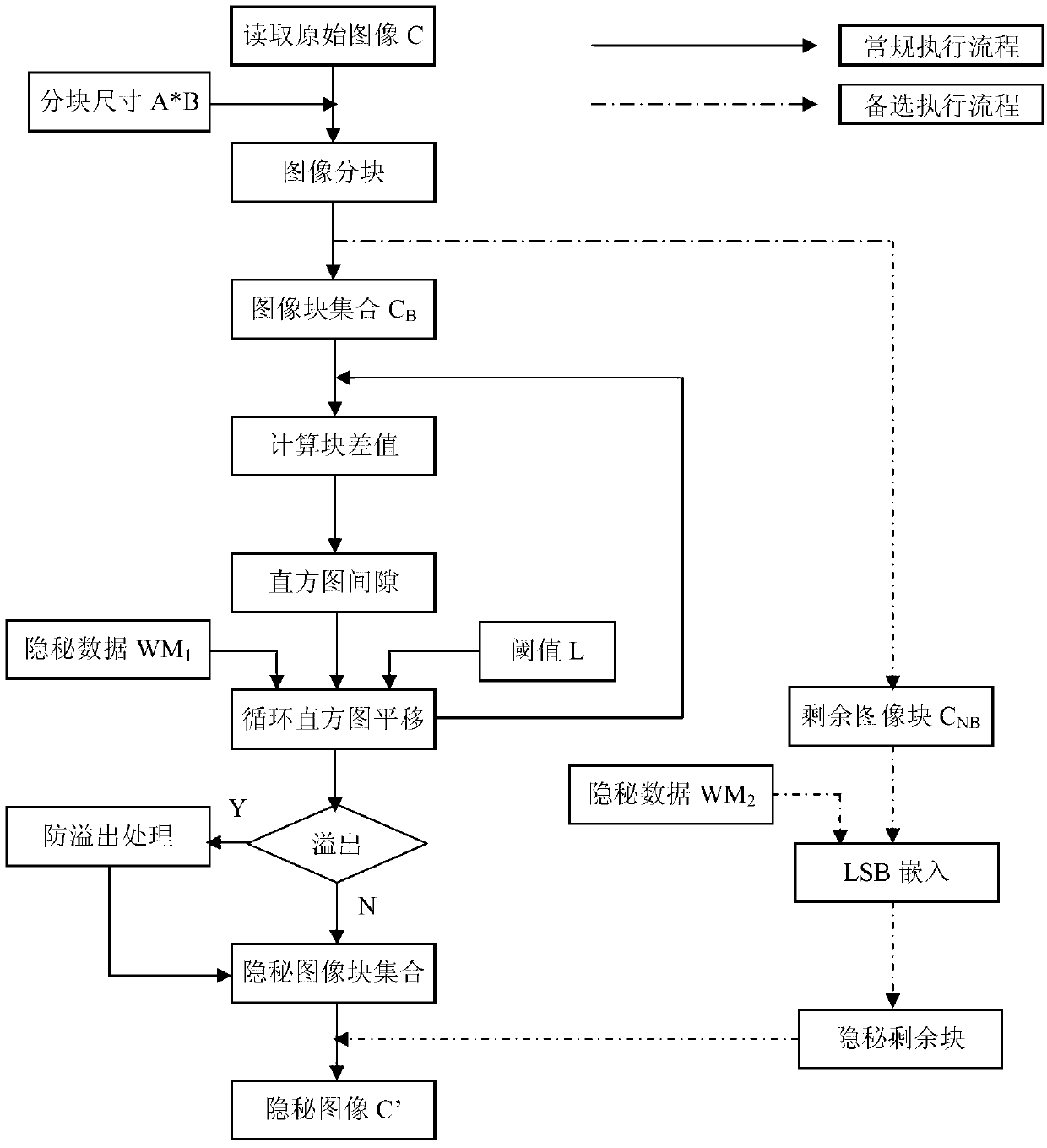
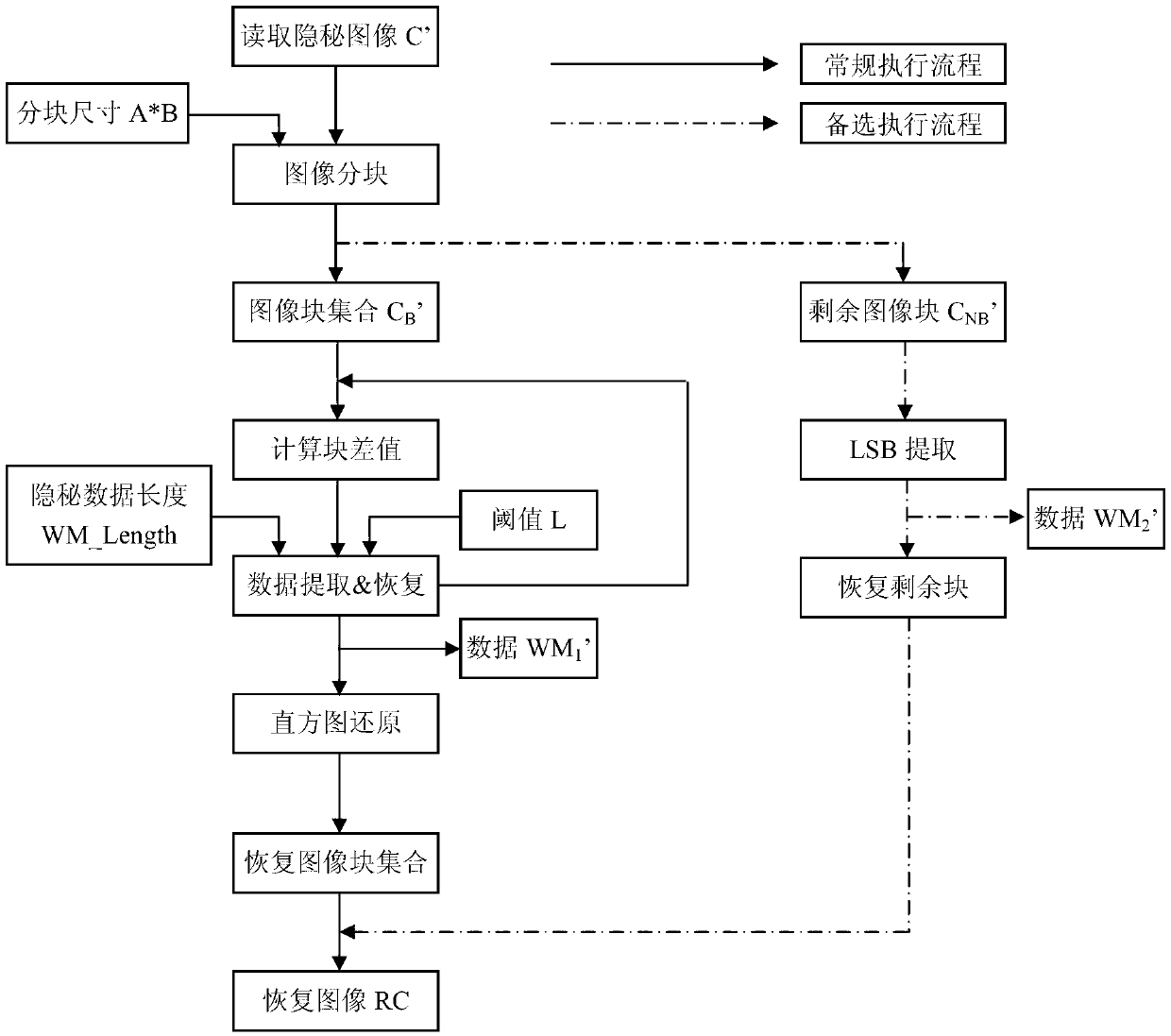
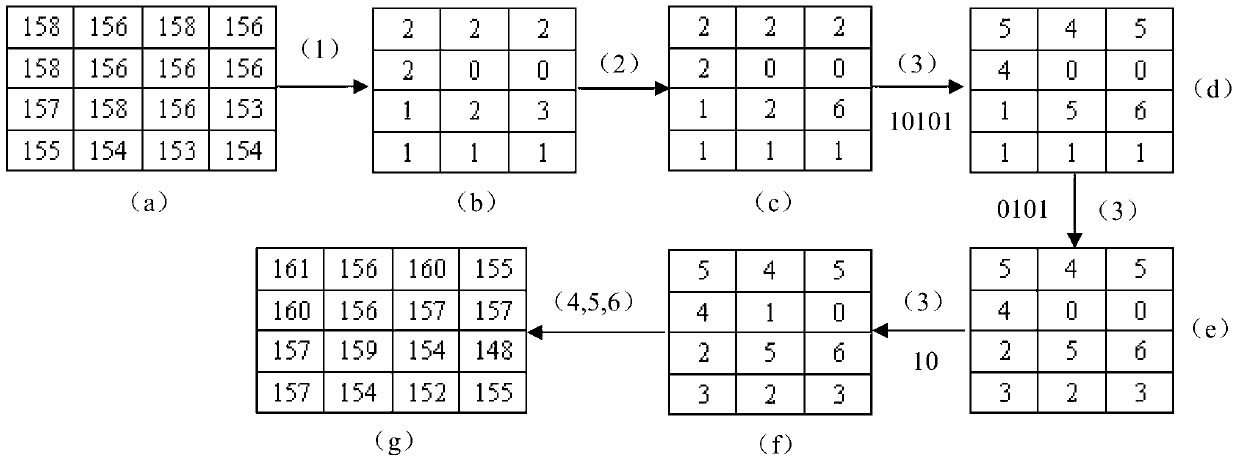
Lossless data hiding method based on difference image histogram cycle spinning
A cyclic translation and data hiding technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of embedding capacity dependence, algorithm embedding capacity is small, affecting hidden data extraction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0096] The present invention will be described in further detail below in conjunction with accompanying drawing and specific embodiment:
[0097] Although the invention has been described with respect to specific embodiments, it is apparent that the principles of the invention, as defined by the appended claims, can be applied beyond the embodiments specifically described herein. Moreover, some details have been left out here in order not to obscure the inventive aspects of the invention. Specific details not described within this application are within the purview of any person of ordinary skill in the art.
[0098] The drawings in this application and their accompanying detailed description are for purposes of illustrating example embodiments of the invention only. In order to maintain brevity, other embodiments of the invention using the principles of the invention are not specifically described in this application and are not specifically illustrated by the present drawin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com