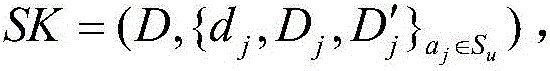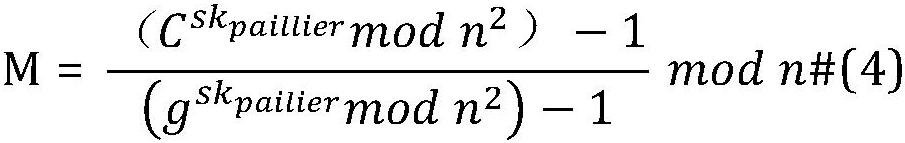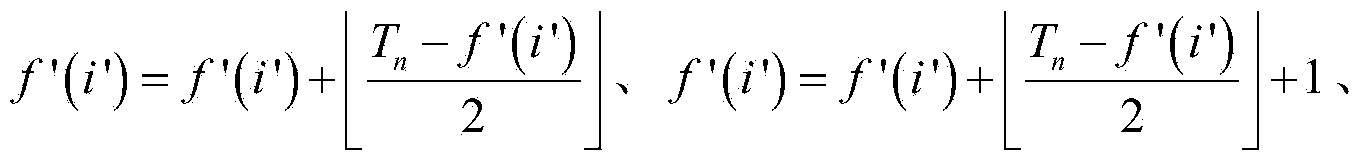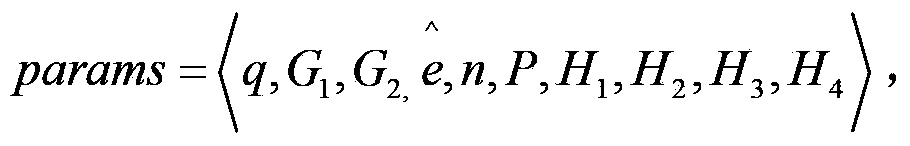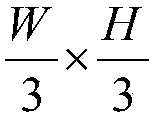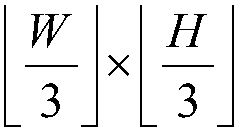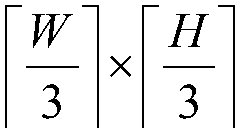Patents
Literature
125results about How to "Address privacy breaches" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
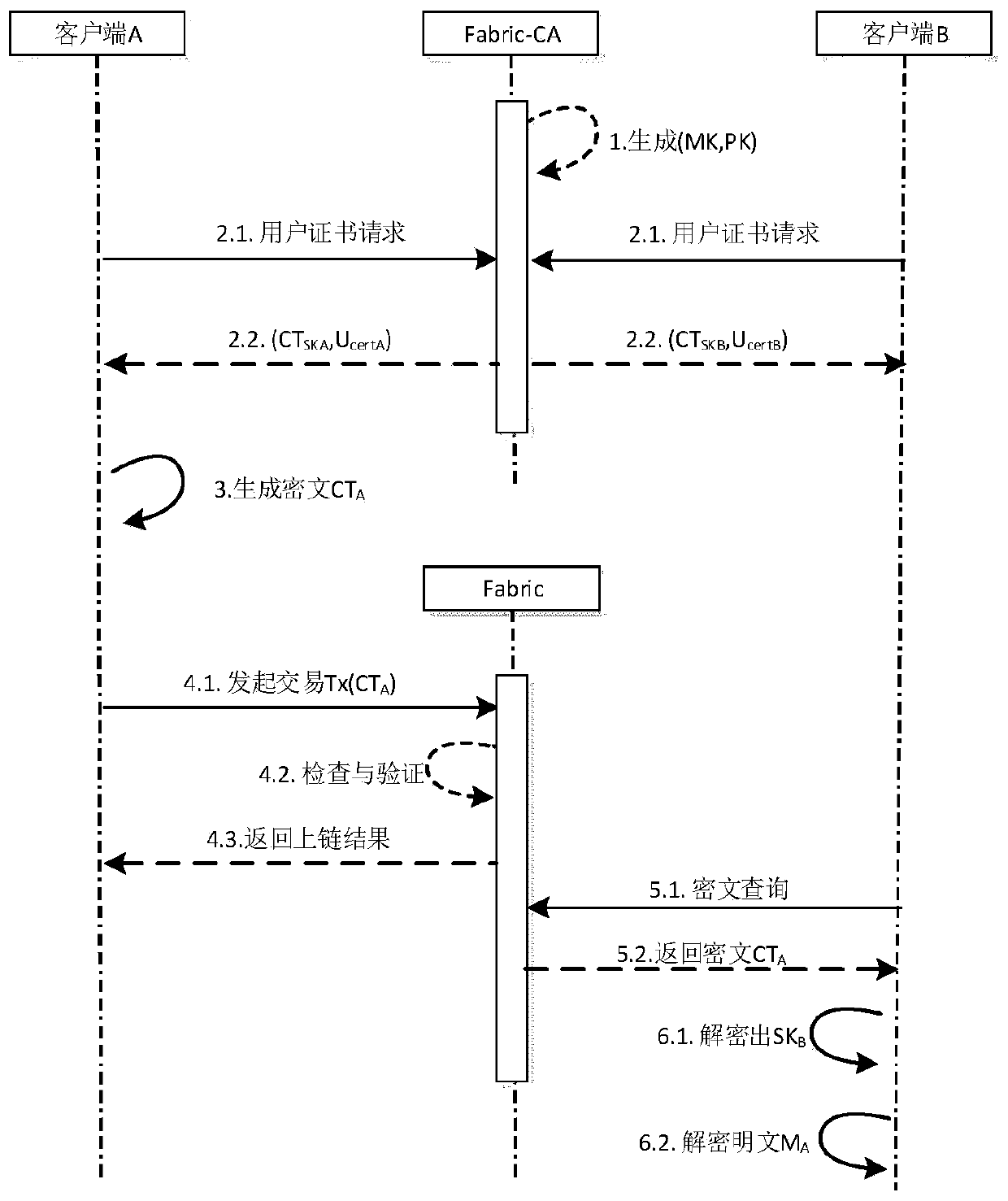
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
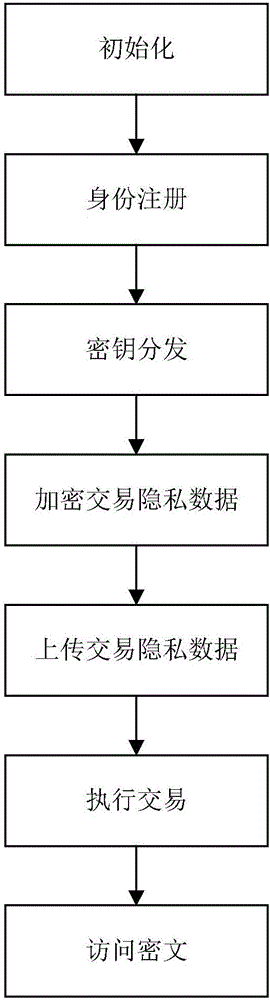
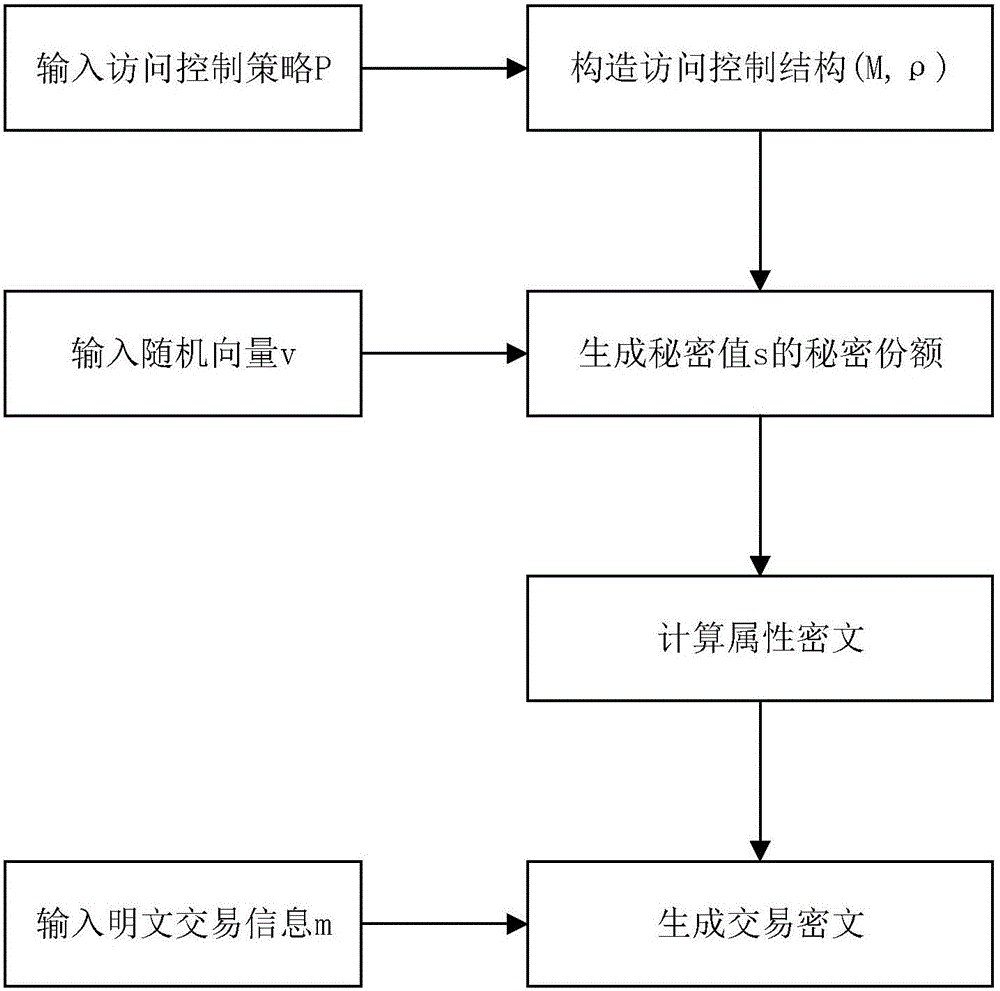
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
A malicious traffic detection implementation method and device based on deep learning
ActiveCN108985361ASolve the characteristicsAddress privacy breachesCharacter and pattern recognitionNeural architecturesFeature extractionManual extraction
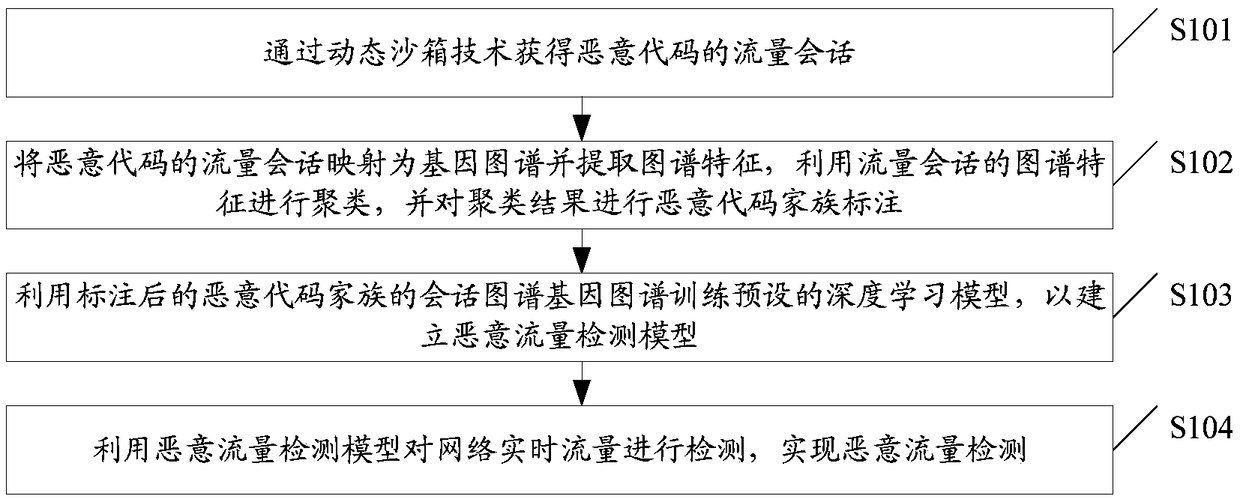
The embodiment of the invention discloses a malicious traffic detection implementation method and device based on deep learning. The method can include: obtaining the flow session of malicious code through dynamic sandbox technology; mapping the traffic session of malicious code to a gene map and extracting the map features; using the map features of traffic session for clustering and marking theclustering results by a malicious code family; training the preset depth learning model by using the tagged gene map of the malicious code family to establish the malicious traffic detection model; using the malicious traffic detection model to detect real-time network traffic, and realizing malicious traffic detection. Through the embodiment, many problems existing in the conventional detection technology such as artificial feature extraction difficulty, privacy disclosure, encryption and confusion difficult to identify, machine learning feature manual extraction and the like are solved to acertain extent, and the method has the characteristics of high robustness, high speed, high accuracy, low false alarm rate, cross-platform detection and the like.
Owner:北京金睛云华科技有限公司
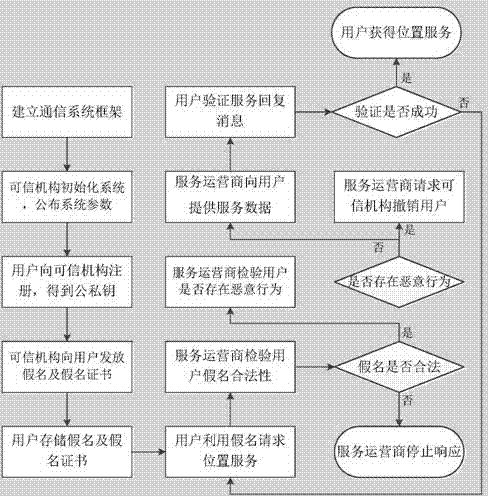
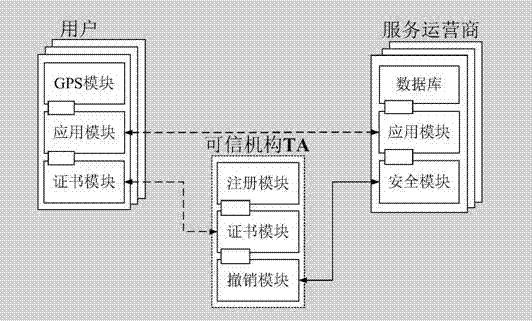
Position privacy protection method based on dynamic pseudonyms
ActiveCN103618995AAddress privacy breachesIncreased level of privacyLocation information based serviceSecurity arrangementCommunications systemSide information
The invention discloses a position privacy protection method based on dynamic pseudonyms. The position privacy protection method mainly overcomes the defect that the position privacy protection degree in an existing position pseudonym method based on position services is too low. The position privacy protection method comprises the steps that a communication system composed of users, a credible mechanism and a service provider is built; the system is initialized through the credible mechanism; the users sign in the credible mechanism on line to obtain public and private keys; the credible mechanism updates the pseudonyms and pseudonym certificates of the users regularly; the users use the dynamic pseudonyms to request position services from the service provider; the service provider provides service data for legal users and requests the credible mechanism to revoke malicious users; the legal users obtain the position service data. According to the position privacy protection method, identity anonymity is achieved by using the dynamic pseudonyms, the relation between identity information and spatiotemporal information is cut off, and therefore it is difficult for the service provider to speculate position information of the specific users by means of side information, position privacy of the users is protected effectively, and the position privacy protection method can be used for position privacy protection based on the position services in social networking services.
Owner:XIDIAN UNIV
Data sharing method, computer equipment applying same and readable storage medium
ActiveCN111931242AAddress privacy breachesSafe and reliableEnsemble learningDigital data protectionData informationSoftware engineering
The invention discloses a data sharing method, computer equipment applying the same and a readable storage medium, and belongs to the technical field of data information security. According to the method, a blockchain technology and a federated learning technology are combined, a data security sharing model based on the blockchain and federated learning is constructed, and a data sharing basic process is designed; a working node selection algorithm based on a block chain and node working quality is designed by taking reliable federated learning as a target; a consensus method of a block chainis modified, an excitation mechanism consensus algorithm based on model training quality is designed, and the purposes of encouraging excellent work nodes to work, simplifying the consensus process and reducing the consensus cost are achieved. The differential privacy algorithm suitable for federated learning is selected by taking balance data security and model practicability as targets. According to the invention, the problem of privacy leakage in a data sharing process can be solved; the blockchain technology is combined into data sharing, so that the security and credibility of data are guaranteed; meanwhile, the efficiency of federated learning tasks is improved.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
Cloud data security protection method
InactiveCN104767745AImprove securitySolve user privacy leakageTransmissionAuthorizationSecurity enhancement
The invention discloses a cloud data security protection method, and belongs to the field of data security. The cloud data security protection method comprises the steps that the leakage protection to cloud data is achieved through data leakage protection; through cloud multi-tenant data security isolation, the leakage prevention of multi-tenant data is achieved, and the problem that a service provider manager views, interpolates and deletes user sensitive data without being authorized is solved; the self-security of a server host is promoted through cloud host security enhancement measures; malicious attack detection, service unified authorization and access control, service request identification and service parameter security check of data services are conducted through a service firewall suite, the security protection to big data is achieved, and the problem of user privacy leakage is solved. Compared with the prior art, according to the cloud data security protection method, all-dimensional security protection to the cloud data can be achieved from four levels, namely, the operation system level, the logical storage level, the data level and the data service level, and the cloud data security protection method has good application and popularization value.
Owner:INSPUR GROUP CO LTD
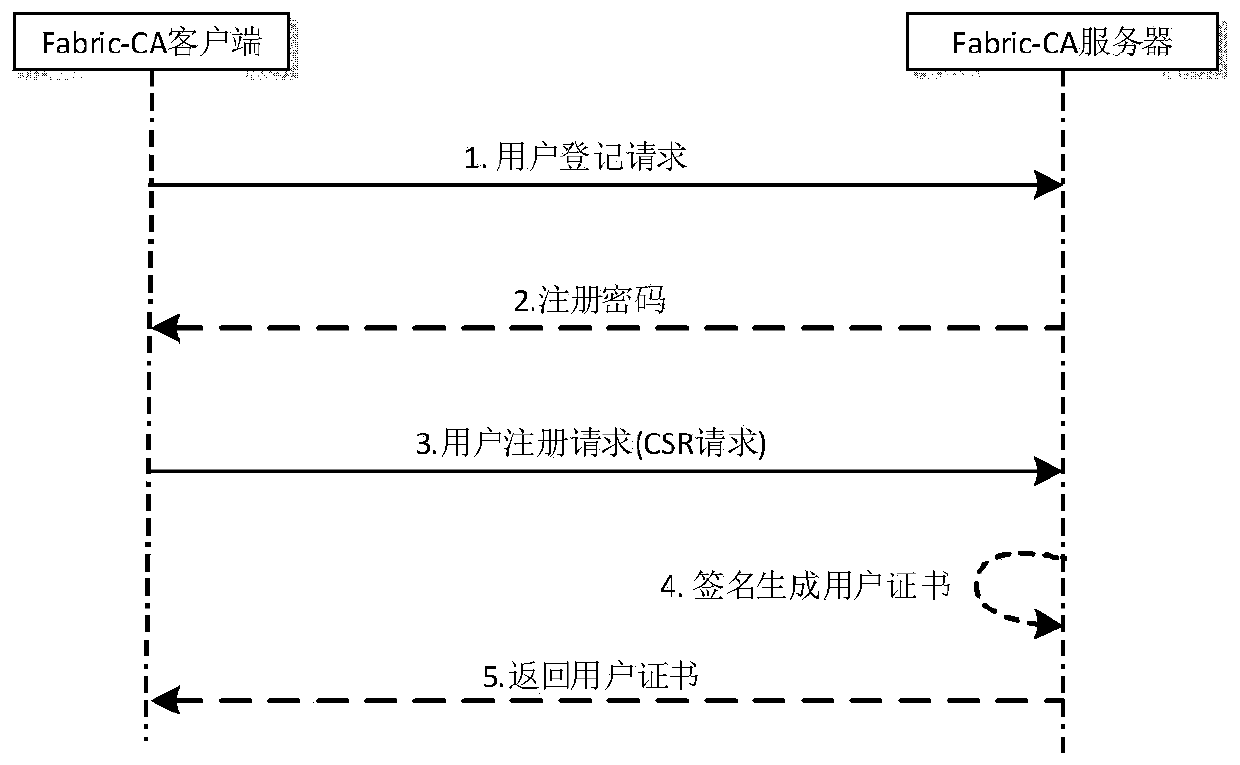
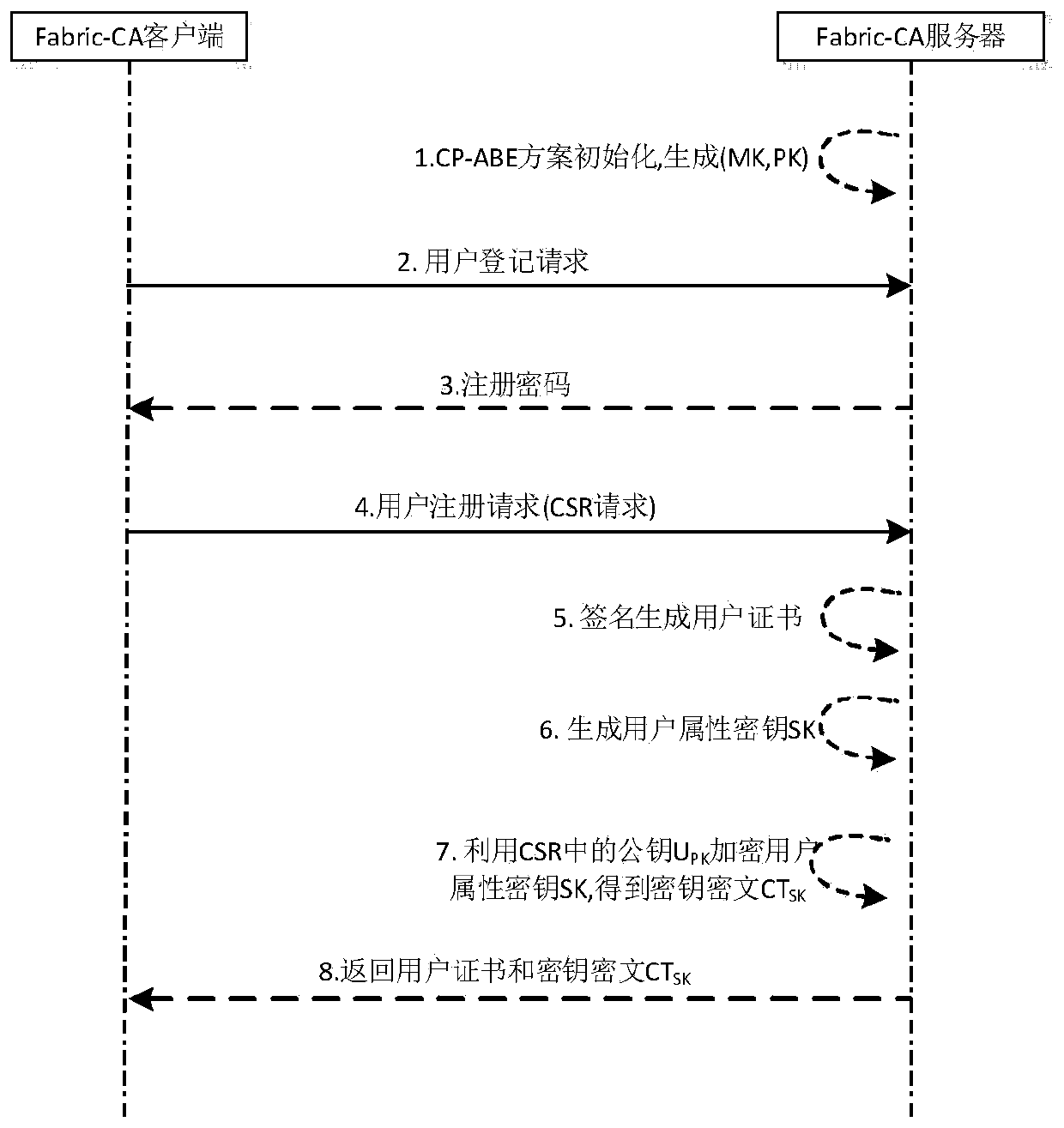
Alliance block chain data access control method based on CP-ABE algorithm
ActiveCN111371561AAddress privacy breachesRealize fine-grained encryption access control functionKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The invention discloses an alliance blockchain data access control method based on a CP-ABE algorithm, which comprises the following steps: (1) a key generation stage: generating a master key MK and apublic parameter PK in a CP-ABE scheme in the stage, generating a user certificate and an attribute key ciphertext according to a user certificate request, and returning the user certificate and theattribute key ciphertext to a client; (2) a data encryption and chaining stage: in the stage, encrypting private data into a ciphertext by using a CP-ABE scheme, and performing chaining operation on the ciphertext; and (3) an access control stage: after the ciphertext transaction information is requested, the client firstly decrypts the attribute key ciphertext to obtain the attribute key, and further decrypts the ciphertext according to the attribute key to obtain plaintext private data. On the premise of ensuring safe distribution of the user attribute key, the method can be used for effectively realizing privacy protection and encryption access control functions of the uplink data of the super account book block chain.
Owner:HUAXIN CONSULTATING CO LTD
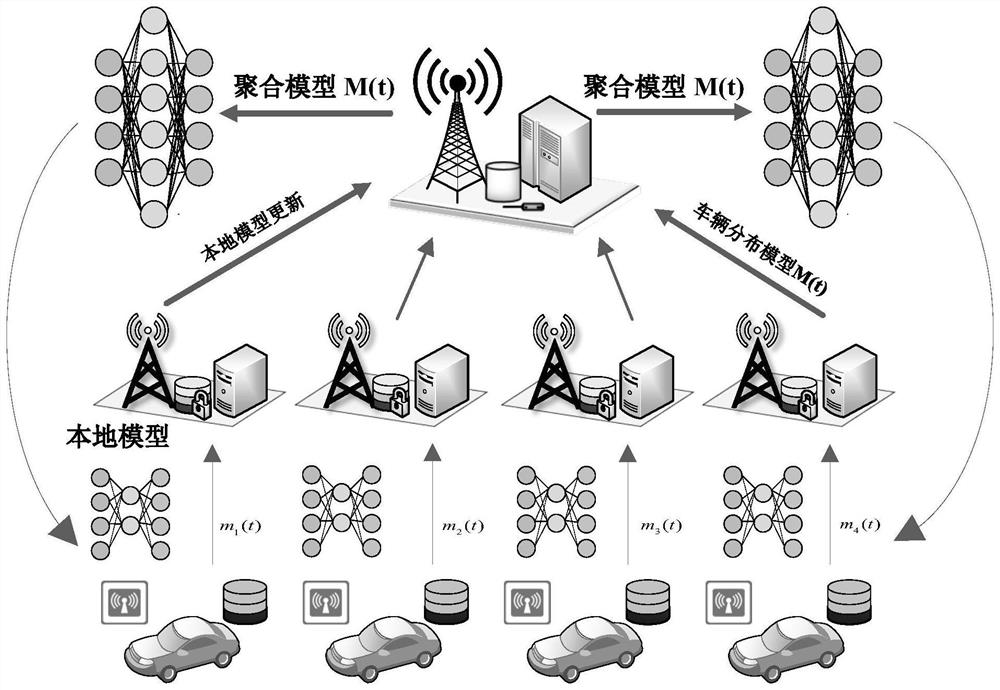
Federated learning privacy protection method based on homomorphic encryption in Internet of Vehicles
ActiveCN112583575AFully homomorphic encryptionNo need to exposeKey distribution for secure communicationEnsemble learningAlgorithmAttack
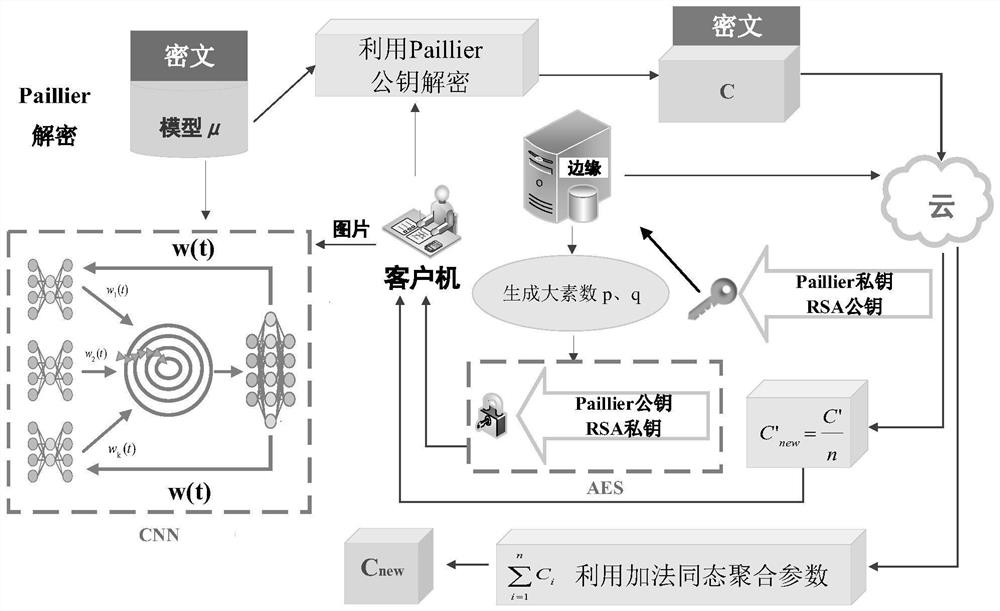
The invention provides a federated learning privacy protection method based on homomorphic encryption in the Internet of Vehicles, which introduces federated learning based on homomorphic encryption into the Internet of Vehicles, improves a Paillier algorithm with addition homomorphic lines and an RSA algorithm with multiplication homomorphism, combines an AES algorithm and a step size confusion mode, and adopts a hierarchical encryption technology at the same time. According to the method, the addition homomorphism is completed at the edge end, and the multiplication homomorphism is completedat the cloud end to improve the encryption efficiency, so that federated learning malicious attacks are effectively prevented, and the delay caused by encryption is effectively reduced. The method can be applied to privacy protection in the Internet of Vehicles to introduce federated learning into the IoV so as to solve the problem of user privacy leakage. In order to further enhance the data safety, efficient homomorphic encryption is introduced into federated learning; moreover, a Paillier algorithm with addition homogeneity and an RSA algorithm with multiplication homogeneity are improved,and a federated learning architecture with full homomorphic encryption is constructed in combination with an AES algorithm and a step length confusion mode.
Owner:HUAQIAO UNIVERSITY +1
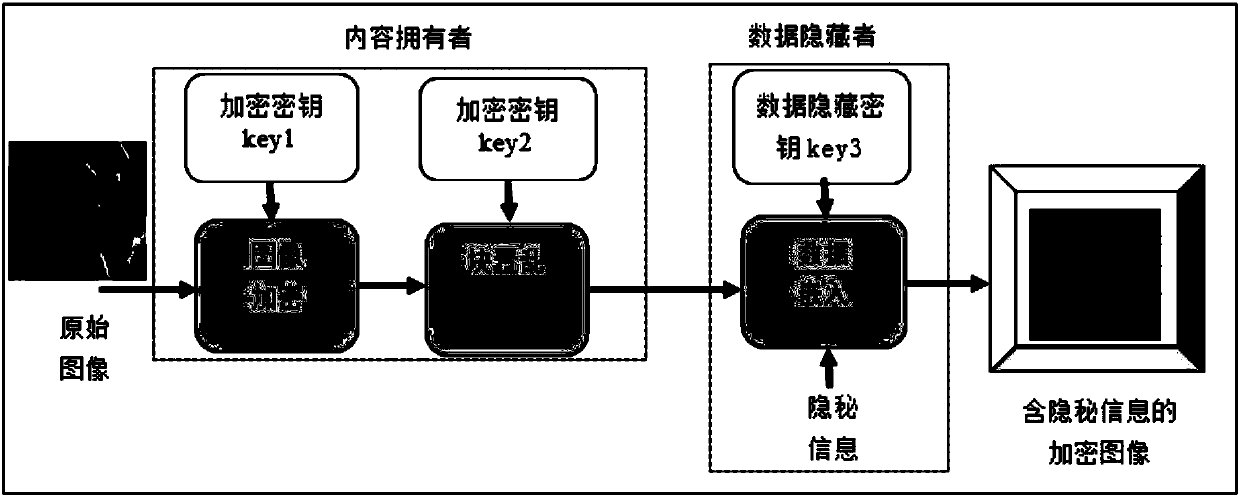
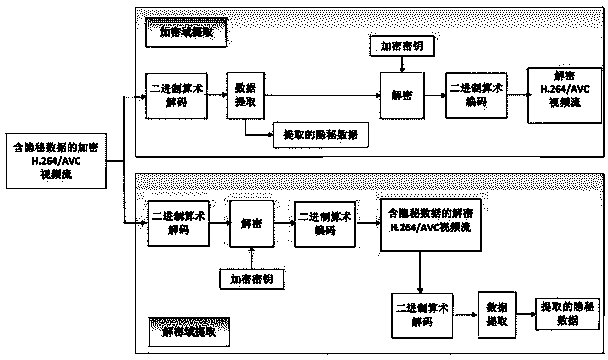
Encryption domain H.264/AVC video reversible data hiding method
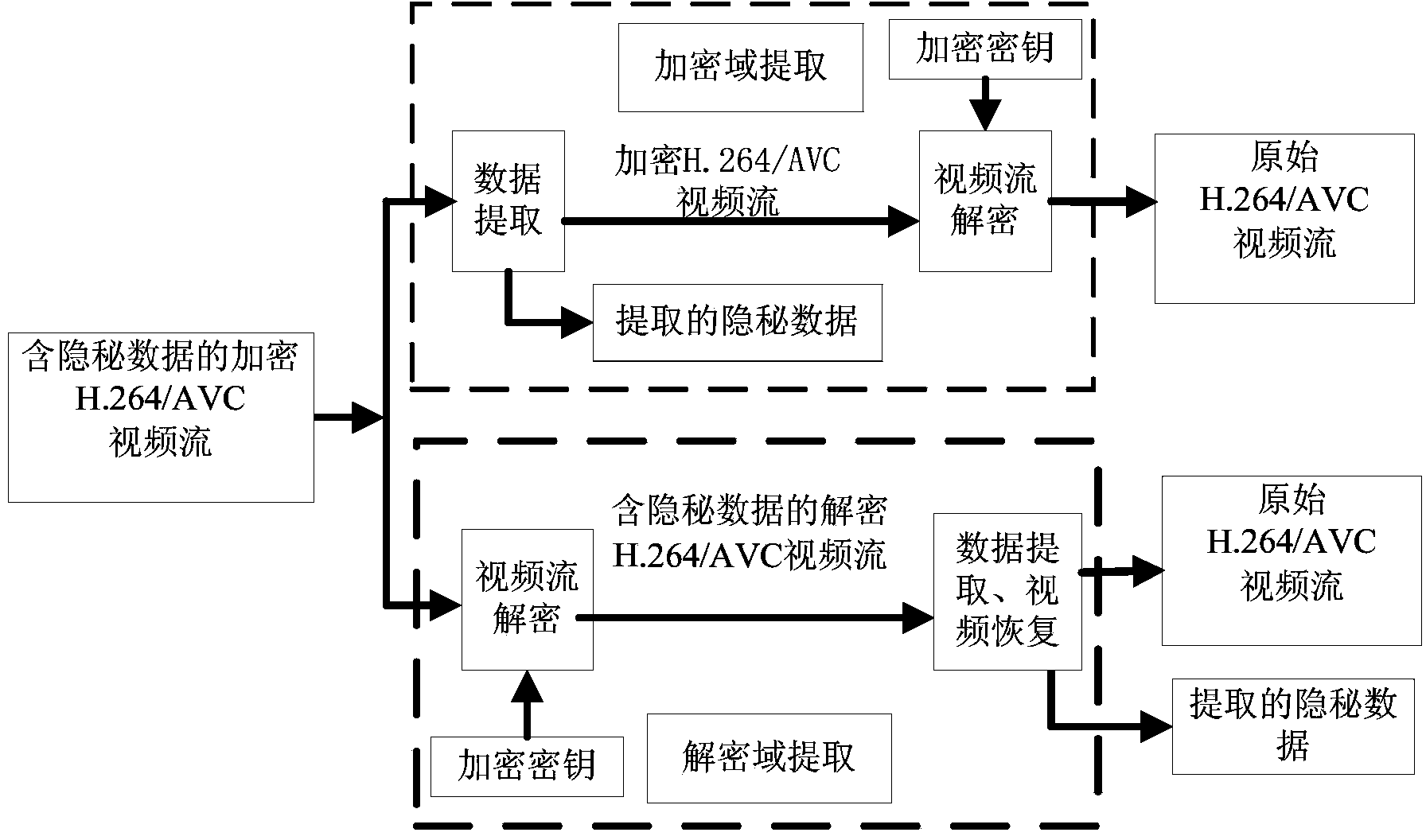
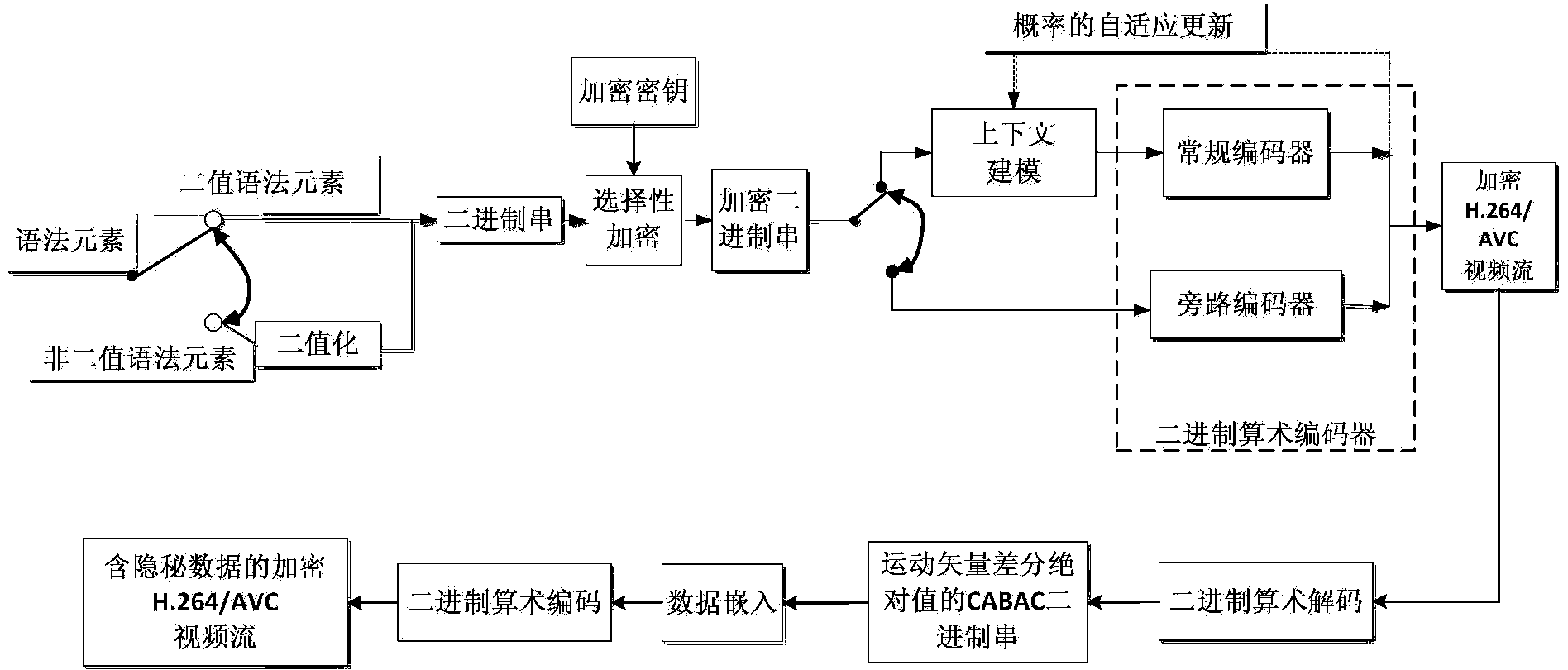
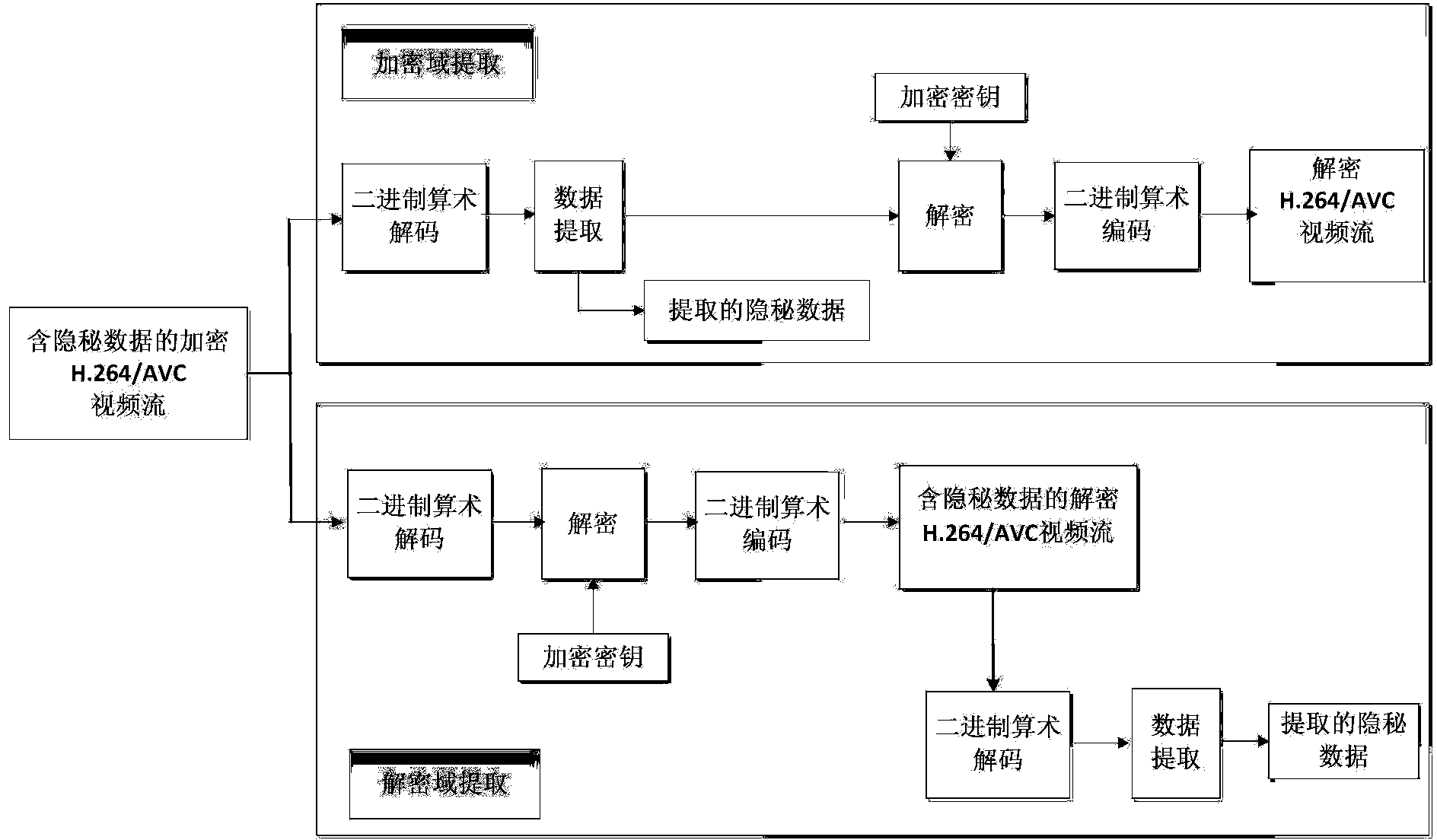
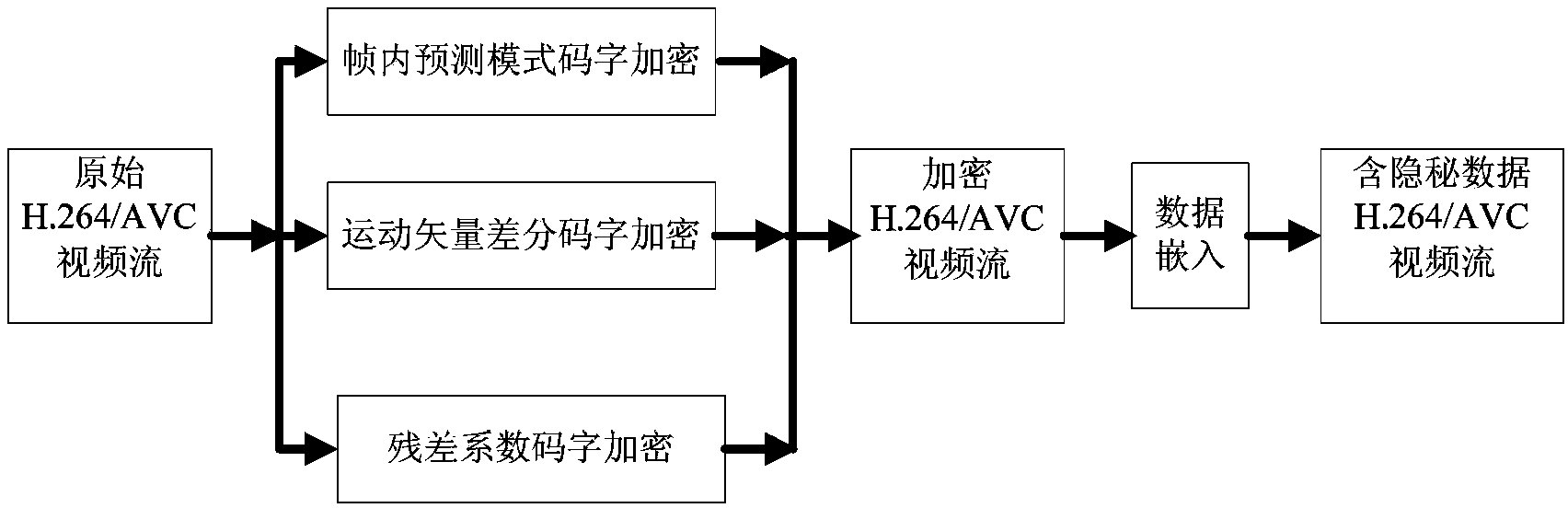
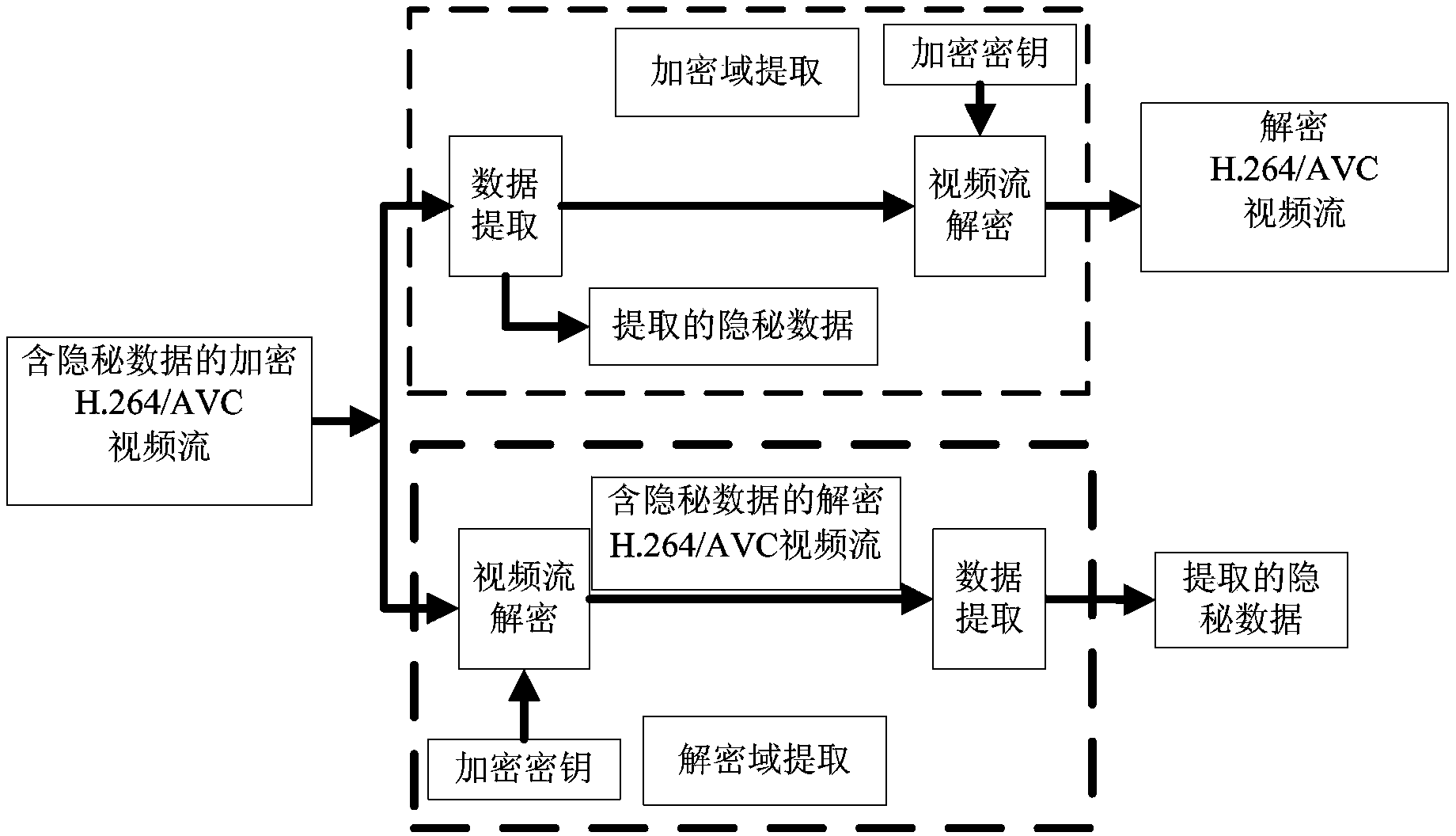
ActiveCN103826128AMeet application needsLittle impact on code rateDigital video signal modificationComputation complexityData expansion
The invention discloses an encryption domain H.264 / AVC video reversible data hiding method. Under the premise that the encryption domain H.264 / AVC video reversible data hiding method is compatible with an H.264 / AVC video compressed encoding standard, code words of prediction modes, Exp-Golomb code words of motion vector difference and sign bits of residual error coefficients are selected to be encrypted, computation complexity is low, the application demands of real-time videos are met, and encryption safety is high. Meanwhile, influences of encryption on the code rate of code streams of H.264 / AVC videos are quite small, and the problem of data expansion in the video encryption process is solved. A data hiding person can embed private information in the H.264 / AVC videos of an encryption domain directly, and thus the problems of video content safety and privacy disclosure can be solved effectively. The hidden data can be extracted effectively from the encryption domain and can also be extracted effectively from a decryption domain, namely, data extraction and data decryption are separated completely, and practicality is high. In addition, the encryption domain H.264 / AVC video reversible data hiding method is completely revisable, and original videos can be restored without damage after the hidden information is decrypted and extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Encrypted domain H.264/AVC video data hiding method based on CABAC binary string mapping
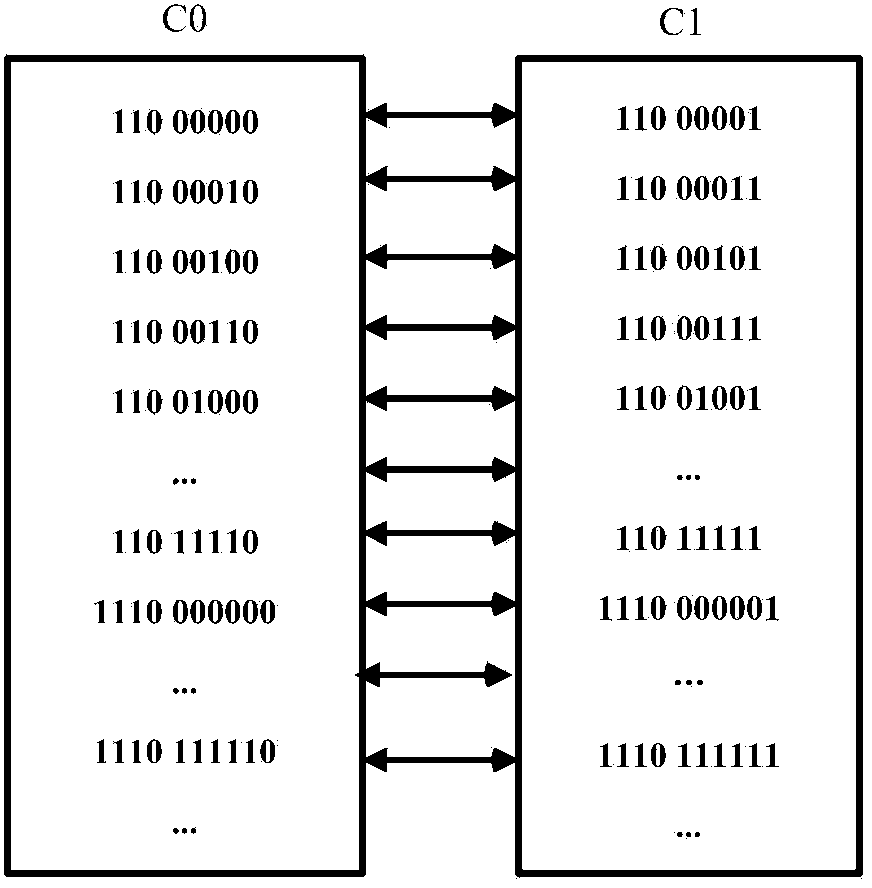
ActiveCN104038761ASolve the problem of data expansionFix security issuesDigital video signal modificationComputer hardwareMotion vector
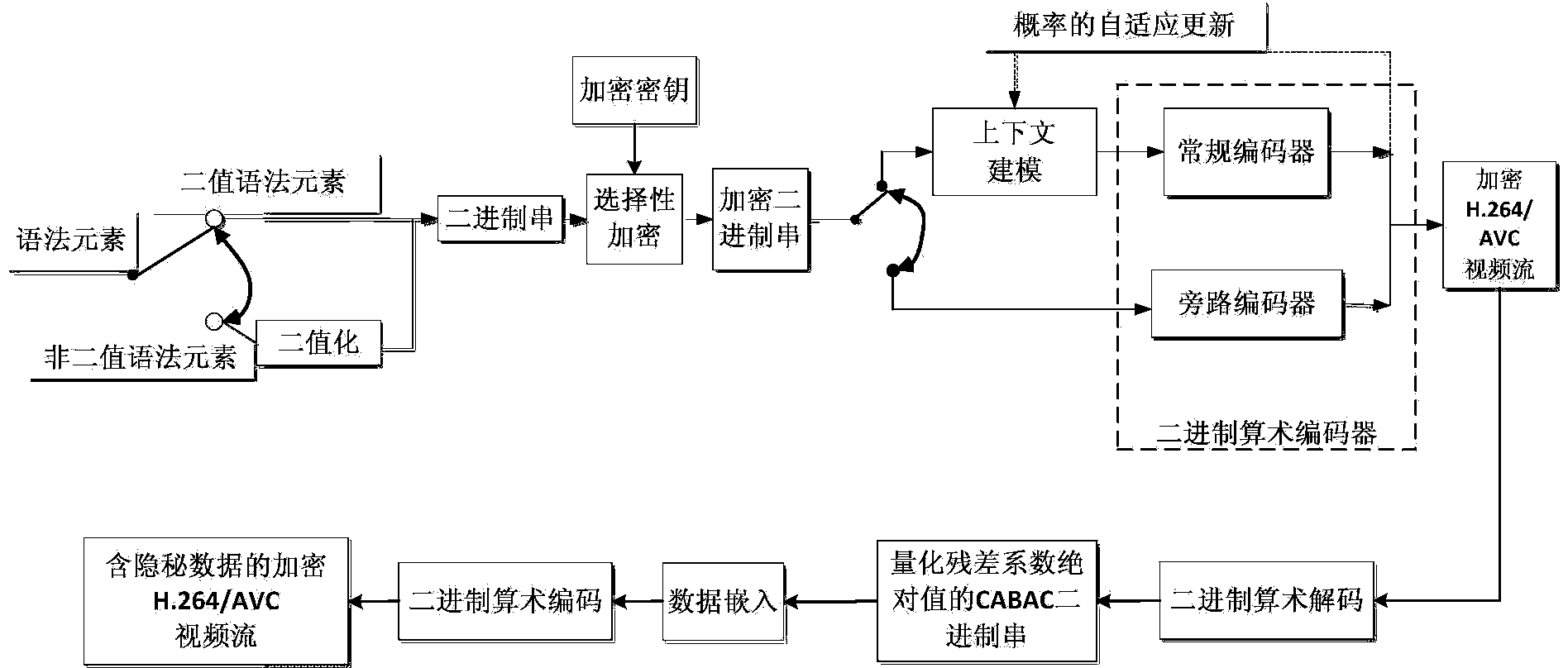
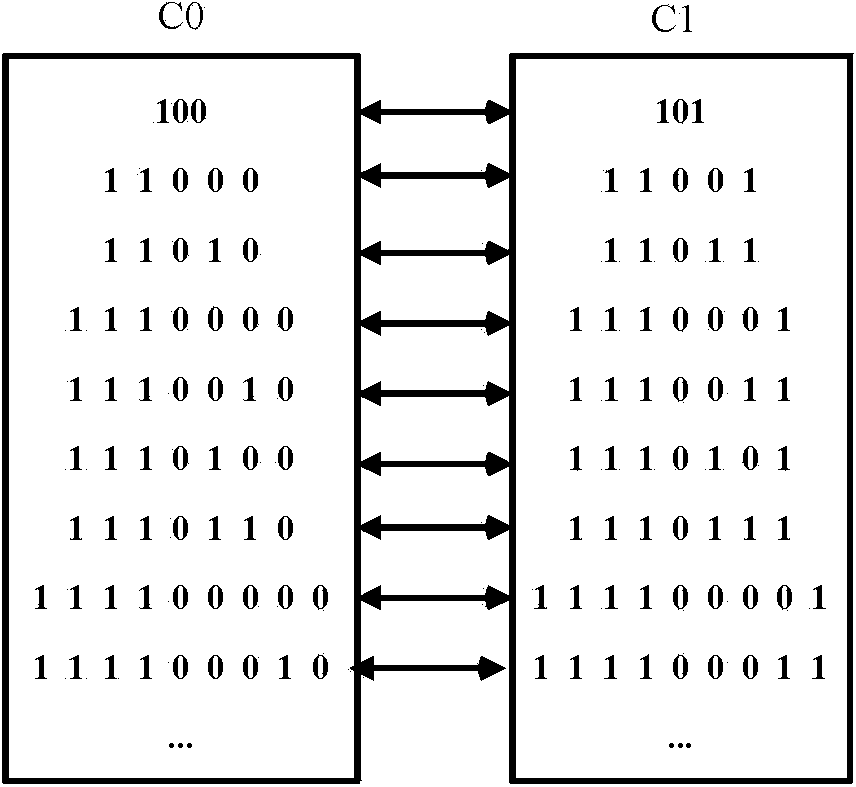
The invention discloses an encrypted domain H.264 / AVC video data hiding method based on CABAC binary string mapping. The encrypted domain H.264 / AVC video data hiding method based on the CABAC binary string mapping includes H.264 / AVC video encryption, encrypted domain H.264 / AVC video data hiding and hidden data extracting, to be specific, using syntax elements of a bypass coding mode in a CABAC to carry out equal-length binary string substitution to encrypt a video, hiding data through a CABAC binary string mapping method for an absolute value of a motion vector difference, wherein both the encryption and data hiding do not change the code rate of a H.264 / AVC video streaming. Both the encryption and the data hiding are finished under CABAC entropy coding and are completely compatible with the CABAC entropy coding, and the encrypted video streaming with hidden data can be decoded through a standard H.264 / AVC video decoder; a person who hides the data can directly embed secrete information in the H.264 / AVC video, even if the person who hides the data does not know the original video content, the person can effectively guarantee the video content safety and avoid the privacy disclosure problem; and in addition, the encrypted domain H.264 / AVC video data hiding method based on the CABAC binary string mapping can effectively extract the hidden data from the encrypted domain and decryption domain.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Method for hiding H. 264/AVC video data of encrypted domain
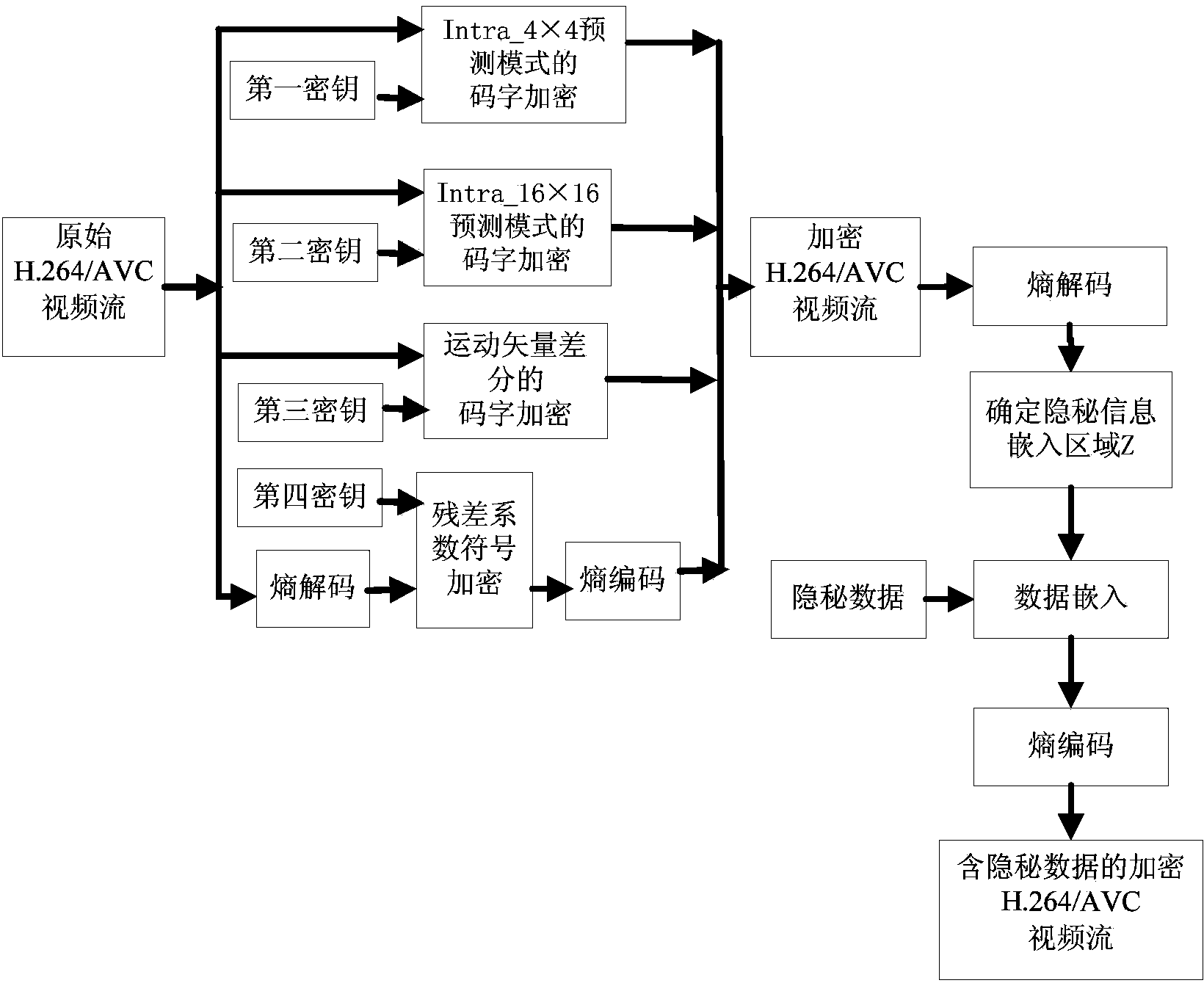
ActiveCN103442253AMeet application needsSolve the problem of data expansionTelevision systemsSelective content distributionHidden dataData expansion
The invention discloses a method for hiding H. 264 / AVC video data of an encrypted domain. The method comprises the process of encrypting H. 264 / AVC videos, the process of hiding the H. 264 / AVC video data of the encrypted domain, and the process of extracting hidden data. In the encryption process, code words of an Intra_4*4 prediction mode, code words of an Intra_16*16 prediction mode, code words with the non-zero motion vector difference and code words with a residual coefficient are encrypted. In the process of hiding the video data, a code word mapping method is adopted. The method has the advantages that video encryption and data hiding are conducted directly in an H. 264 / AVC code stream domain, the videos do not need to be decoded or partially decoded, and application demands of real-time videos are met. The operation of equal-length code word replacement is conducted in the encryption and data hiding processes, code rate of an H. 264 / AVC video stream is not increased, and accordingly the problem of data expansion in the encryption and data hiding processes is solved. Meanwhile, the encrypted video stream with the hidden data is completely compatible with an H. 264 / AVC standard and can be decoded by a standard H. 264 / AVC video decoder. The data extraction and decoding are conducted in a completely separated mode, and the practicability is higher.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
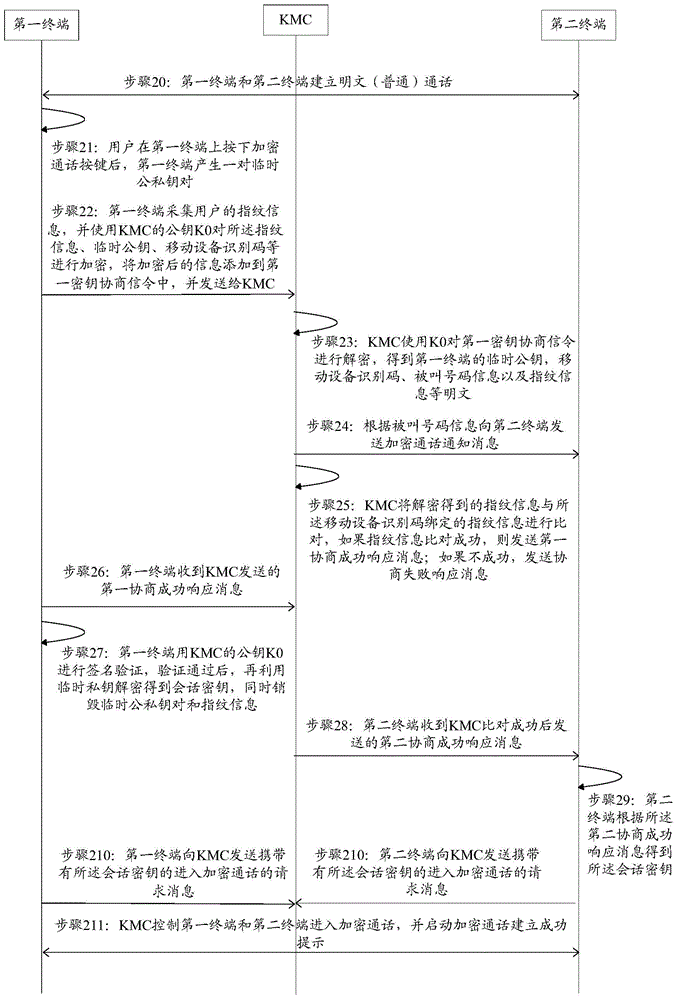
Processing method and apparatus of encrypted call, terminal, and KMC
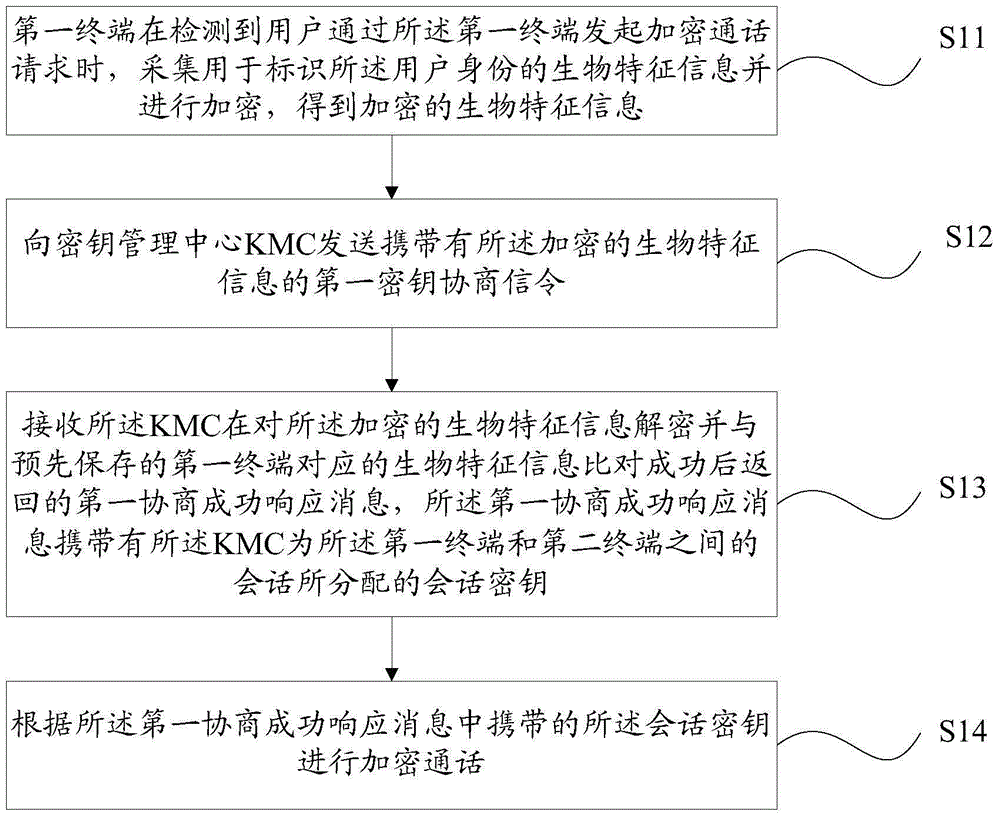
ActiveCN106301767AAddress privacy breachesKey distribution for secure communicationEngineeringSession key
The invention provides a processing method and apparatus of an encrypted call, a terminal, and a KMC. The problems that in the conventional encryption call technology, malicious usage of the telephone of an owner cannot be prevented, and the voice of the owner is imitated for an encrypted call so that the privacy of the owner is leaked are solved. The method includes steps: acquiring biological feature information used for identifying the identity of a user and encrypting the biological feature information when a first terminal detects an encrypted call request initiated by the user, and obtaining encrypted biological feature information; sending a first key negotiation signaling carrying the encrypted biological feature information to the key management center (KMC); receiving a first negotiation success response message returned by the KMC after successful comparison of the decrypted encryption biological feature information and prestored biological feature information corresponding to the first terminal, wherein the first negotiation success response message carries a session key distributed for the session between the first terminal and a second terminal by the KMC; and performing an encrypted call according to the session key carried in the first negotiation success response message.
Owner:ZTE CORP
Dual encryption type reversible data hiding method of encryption domain image
ActiveCN107809644AImprove securityFix security issuesDigital video signal modificationSelective content distributionDistortionXML Encryption
The invention discloses a dual encryption type reversible data hiding method of an encryption domain image. The method comprises three parts, namely, image encryption, reversible data hiding of the encryption domain image, secrete data extraction and original image lossless restoration; a double encryption mechanism is adopted in the image encryption part to enhance the security; secret information can be directly embedded in the encrypted images, even if the data hider knows nothing about the original image contents, the image content security and privacy leakage problems can still be effectively solved, no complex protocol is needed between the image encipherer and the secret information embedding person, and the encryption and data embedding generate no expansion of image data; the practicability is high, if only a data hiding key is present, the hidden secret information can be directly extracted from a ciphertext domain image; if only an encryption key is present, an approximate original image can be obtained by direct decryption; and if the data hiding key and the encryption key are present, it can be guaranteed that the original image can be restored without distortion afterthe hidden secret information is extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
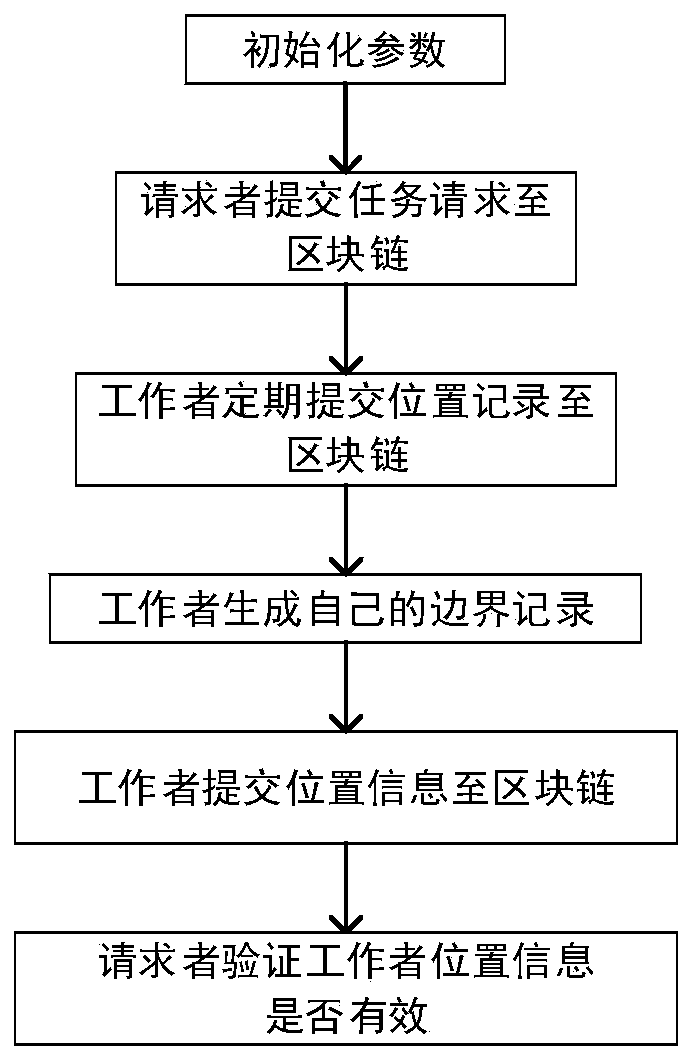
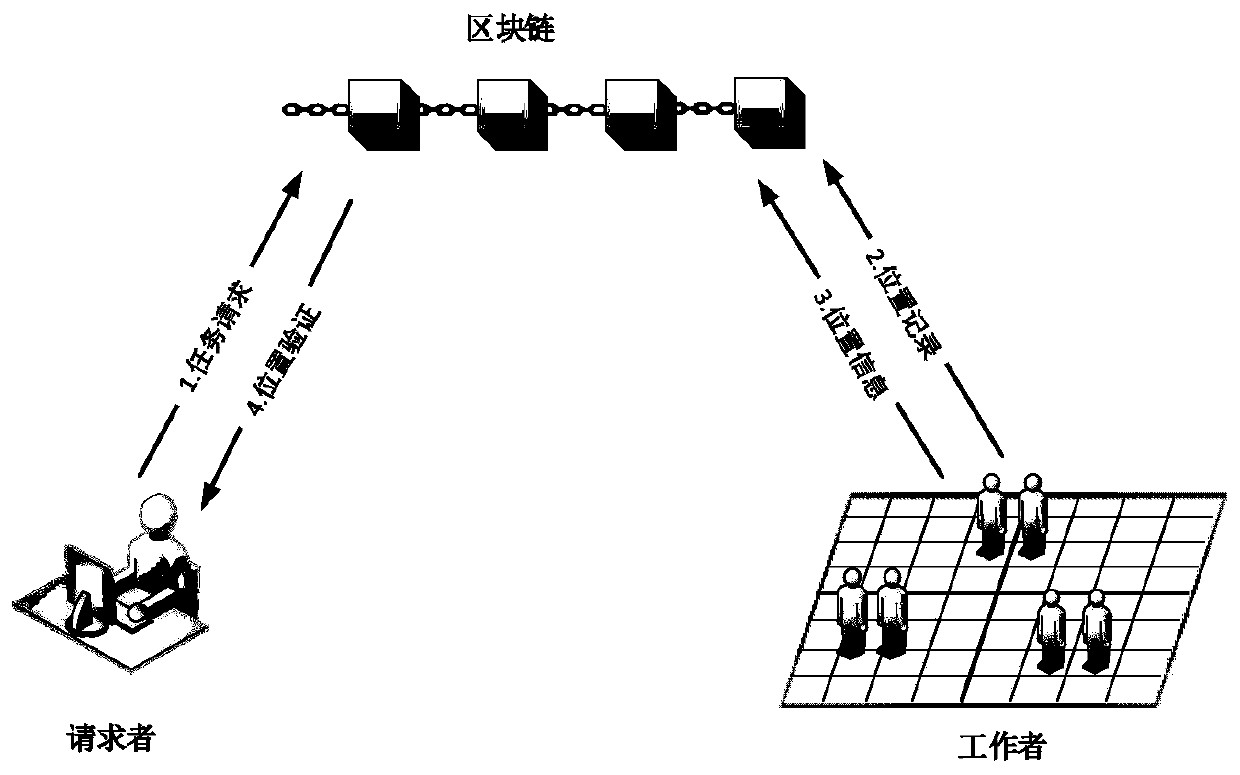
Spatial crowdsourcing multistage position privacy protection method based on block chain
ActiveCN110620772AEliminate controlsEnsure consistencyKey distribution for secure communicationState of artCiphertext
The invention provides a spatial crowdsourcing multistage position privacy protection method based on a block chain, and mainly solves the technical problem of low safety of worker position information data in spatial crowdsourcing in the prior art. The method comprises the following steps: initializing parameters; the requester submits a task request to the block chain; a worker periodically uploads a position record to the block chain; the worker divides the area according to the selected privacy level, and submits the combination of the position coordinate ciphertext and the boundary recordas position information to the blockchain; and the requester verifies the position information submitted by the worker according to the position record on the block chain and the position informationsubmitted by the worker. According to the invention, multi-level privacy protection of worker position information is effectively realized, and the safety of space crowdsourcing is improved.
Owner:XIDIAN UNIV
Encryption domain H.264/AVC (Advanced Video Coding) video data hiding method compatible with CABAC (Context-based Adaptive Binary Arithmetic Coding)
ActiveCN104038767ASolve the problem of data expansionFix security issuesDigital video signal modificationData expansionHidden data
The invention discloses an encryption domain H.264 / AVC (Advanced Video Coding) video data hiding method compatible with CABAC (Context-based Adaptive Binary Arithmetic Coding). The method comprises the three parts of H.264 / AVC video encryption, H.264 / AVC video data hiding of an encryption domain and extraction of hidden data, equal-length binary string substitution operation is performed by selecting syntax elements in a bypass coding mode in CABAC to realize video encryption, data hiding is performed by adopting a CABAC binary string mapping method for quantifying the absolute value of a residual coefficient, and the code rate of H.264 / AVC video stream is not changed by encryption or data hiding, thereby solving the problem of data expansion in video encryption and data hiding. Both encryption and data hiding are completed under CABAC entropy coding, and are completely compatible with CABAC entropy coding. A data hider can embed hidden information directly into encrypted H.264 / AVC videos, and the problems of video content security and privacy disclosure can be solved effectively even the data hider does not know original video contents. Moreover, by adopting the method, hidden data can be extracted effectively on an encryption domain and can be extracted effectively on a decryption domain.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Ciphertext domain high-capacity image reversible data hiding method
ActiveCN109348230AFix security issuesAddress privacy breachesDigital video signal modificationNon destructiveCryptographic key generation
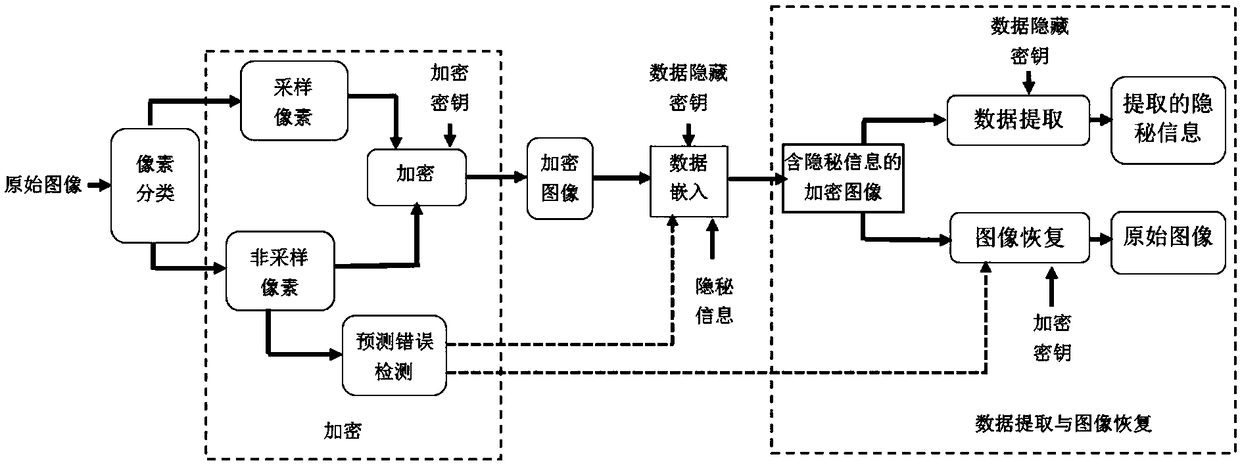
The invention discloses a ciphertext domain high-capacity image reversible data hiding method, including prediction error detection, image encryption, ciphertext domain image reversible data hiding, secret information extraction and original image non-destructive recovery, wherein in the first part, all pixel points in a grayscale image are first divided into two categories that are sampling pixelpoints and non-sampling pixel points, and then all non-sampling pixel points are marked as prediction errors and accurate predictions respectively; in the second part, the marked grayscale image is encrypted by using a binary pseudo-random sequence generated by an encryption key; in the third part, the secret information is encrypted by using a binary pseudo-random sequence generated by a data hiding key, and then the encrypted secret information is used to embed data into each non-sampling pixel point that is marked as the accurate prediction in a ciphertext domain image; and in the fourth part, only the secret information is extracted, or only the original grayscale image is recovered, or the secret information is extracted first and then the original grayscale image is recovered. The method has the advantages that information can be embedded in the ciphertext domain image, and the embedding capacity is high.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
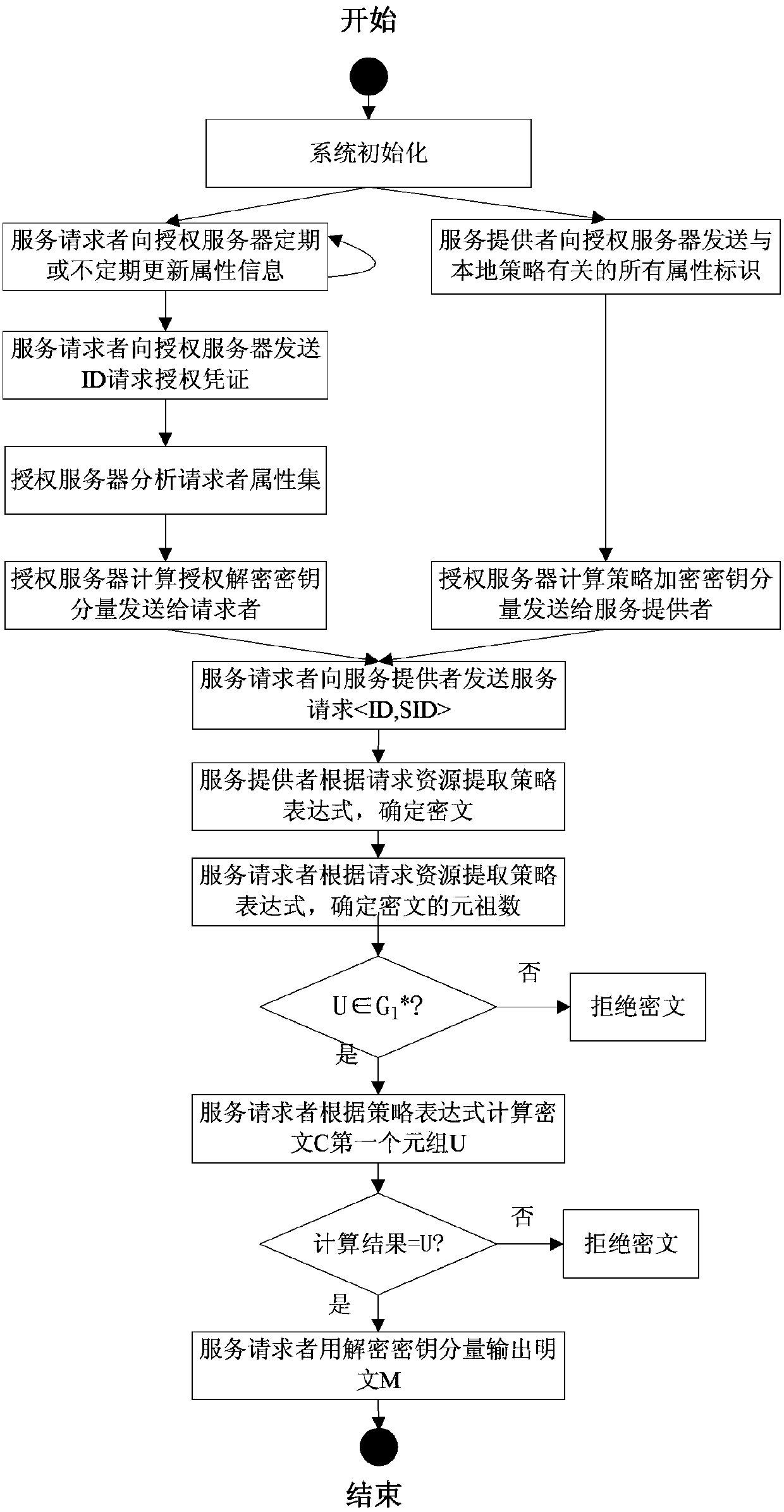
Cross-safety-domain access control system and method based on privacy protection
ActiveCN103391192AAddress privacy breachesRealize privacy protectionPublic key for secure communicationControl systemPrivacy protection
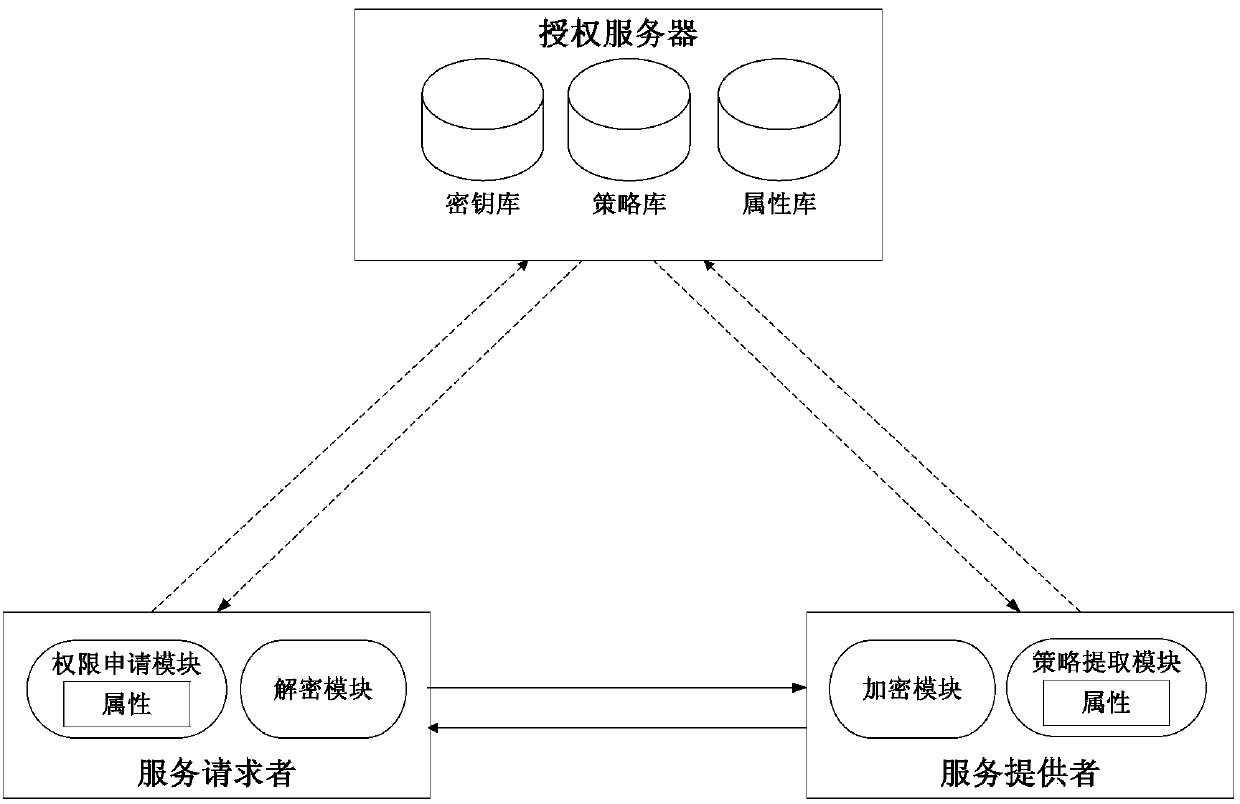
The invention relates to a control system and method in the field of information safety, in particular to a cross-safety-domain access control system and method based on privacy protection. The control system comprises an authorization server, a service provider and a service requester. The control method includes that a privacy protection mechanism is adopted, fusion of cross-safety-domain access control and a privacy protection mechanism is finished in the processes of system initialization, authorization and assignment, strategy making, encryption processing and message recovery and verification, protection of privacy information of the requester is achieved, and the problem of privacy leakage of the service requester in the cross-safety-domain access control is solved. By means of the control system and method, privacy protection of the service requester can be achieved, information disclosure degree is reduced, sensitive information leakage is avoided, and privacy safety of the service requester is achieved.
Owner:STATE GRID CORP OF CHINA +2
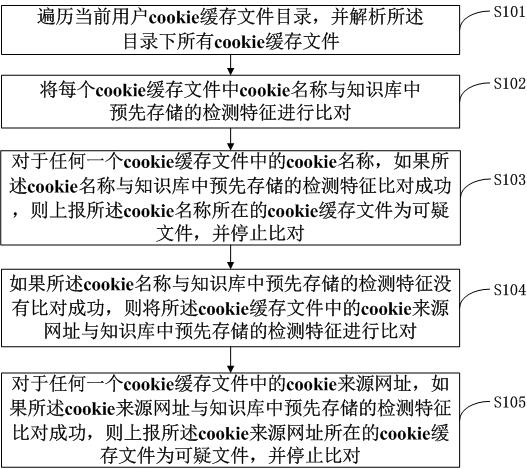
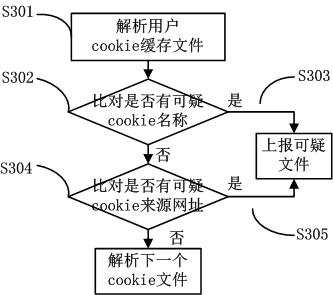
Method and system for detecting and tracking cookie cache files
InactiveCN102043840AAddress privacy breachesEasy to cleanTransmissionSpecial data processing applicationsOperating systemKnowledge base
The invention discloses a method and system for detecting and tracking cookie cache files. The method comprises the steps of: traversing a cookie cache file catalog of a current user, and analyzing all the cookie cache files of the catalog; comparing the cookie name of each cookie cache file with suspicious cookie names pre-stored in a knowledge base; if the comparison succeeds, reporting that the cookie cache files of the cookie name are suspicious files, and stopping comparison; and if the comparison fails, comparing the cookie source universal resource locators (URLs) of the cookie cache files with suspicious URLs pre-stored in the knowledge base; and if the comparison succeeds, reporting that the cookie cache files of the cookie source URLs are suspicious files, and stopping comparing. The problem of privacy leak for users can be solved.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
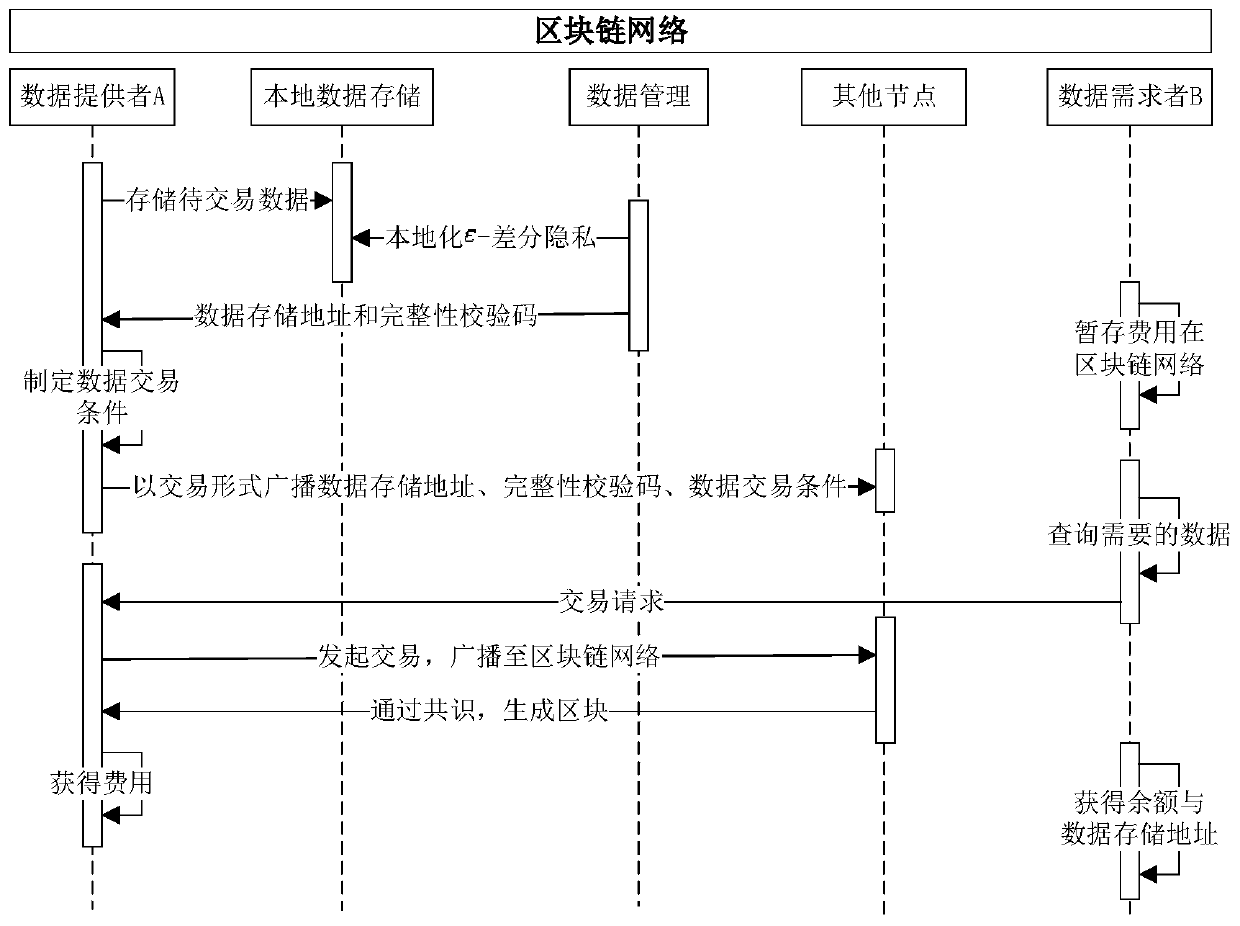
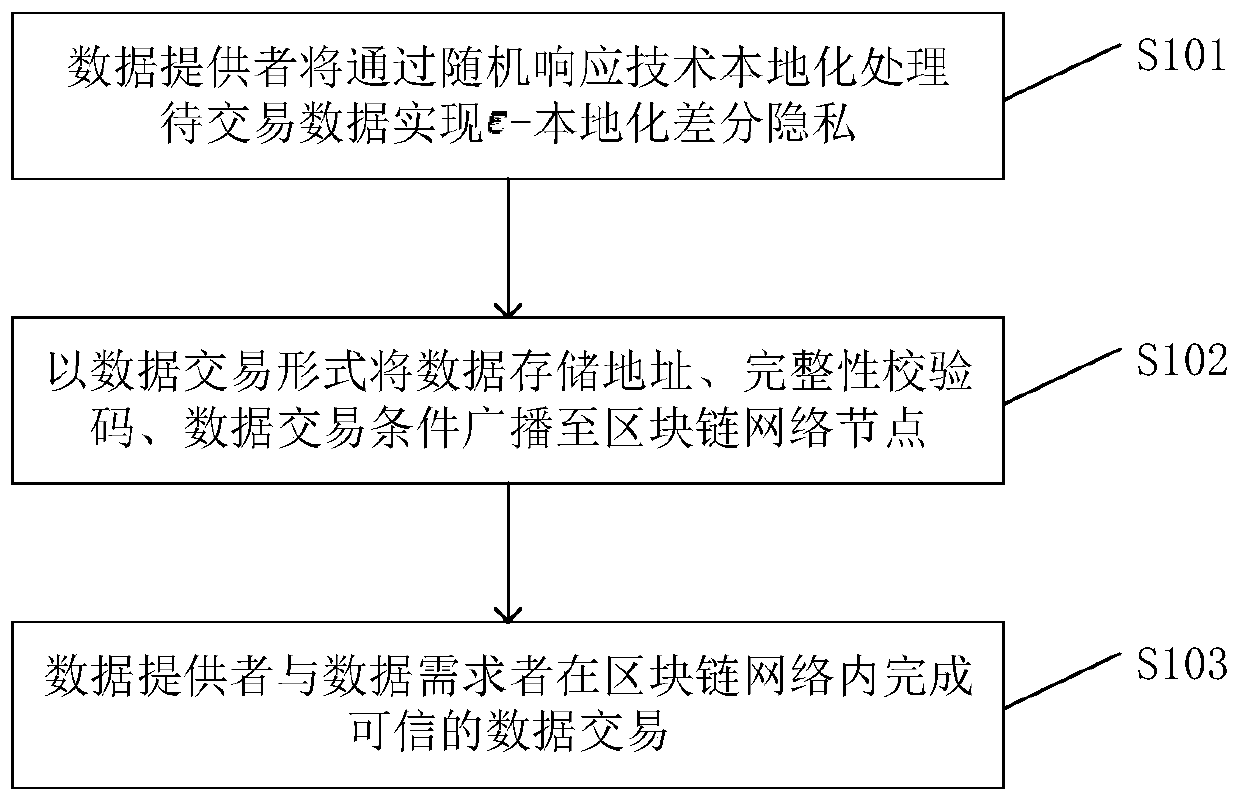
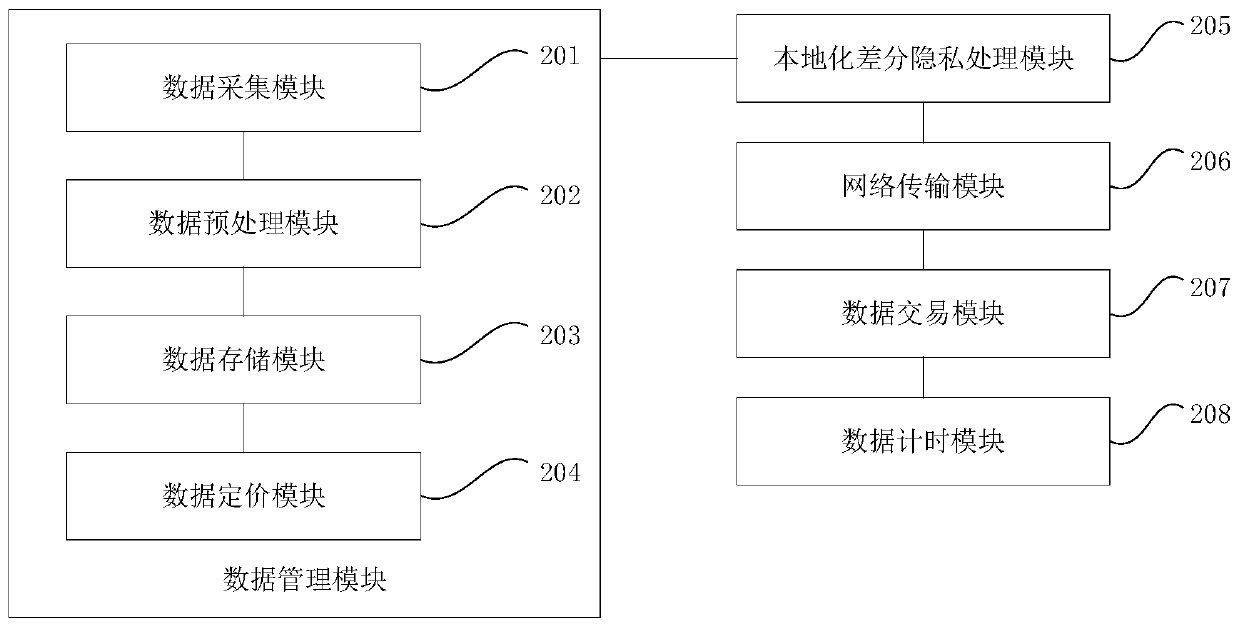
Data transaction localized differential privacy protection method and device based on block chain
InactiveCN110147996ATiming cannot be tampered withAddress privacy breachesPayment protocolsData providerTransaction data
The invention discloses a data transaction localized differential privacy protection method and device based on a block chain, and mainly solves the problem of privacy leakage of an existing centralized data transaction platform. The method comprises the steps that a data provider locally processes to-be-transacted data through a random response technology to achieve Epsilon-local differential privacy; the data storage address, the integrity check code and the data transaction condition are broadcasted to a block chain network node in a data transaction form; and the data provider and the datademander complete credible data transactions in the blockchain network. The privacy disclosure problem in a large number of data transaction scenes with high relevance and various requirements can besolved, and meanwhile the defects that an existing block chain-based data transaction method is poor in flexibility, high in calculation expenditure, low in practicability and the like are overcome.
Owner:CENTRAL UNIVERSITY OF FINANCE AND ECONOMICS
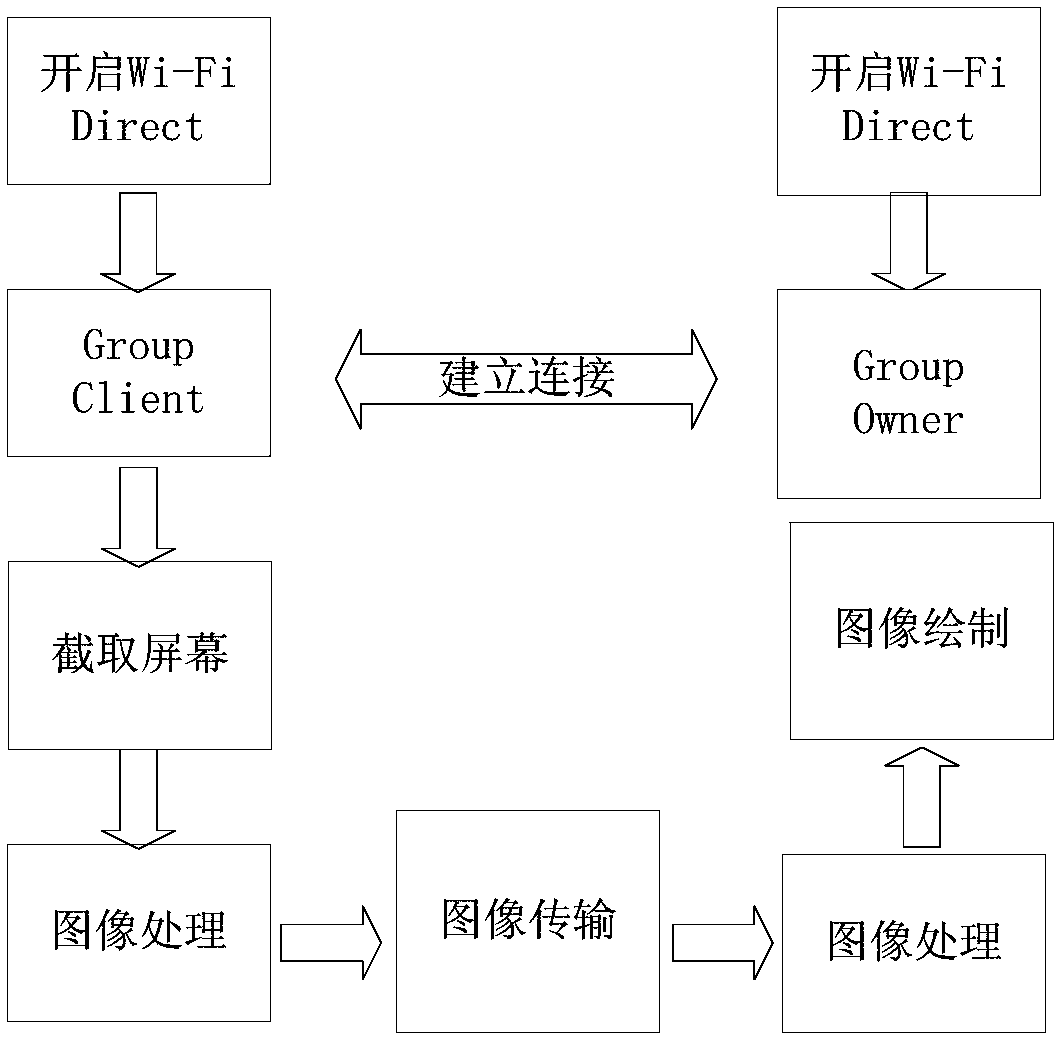
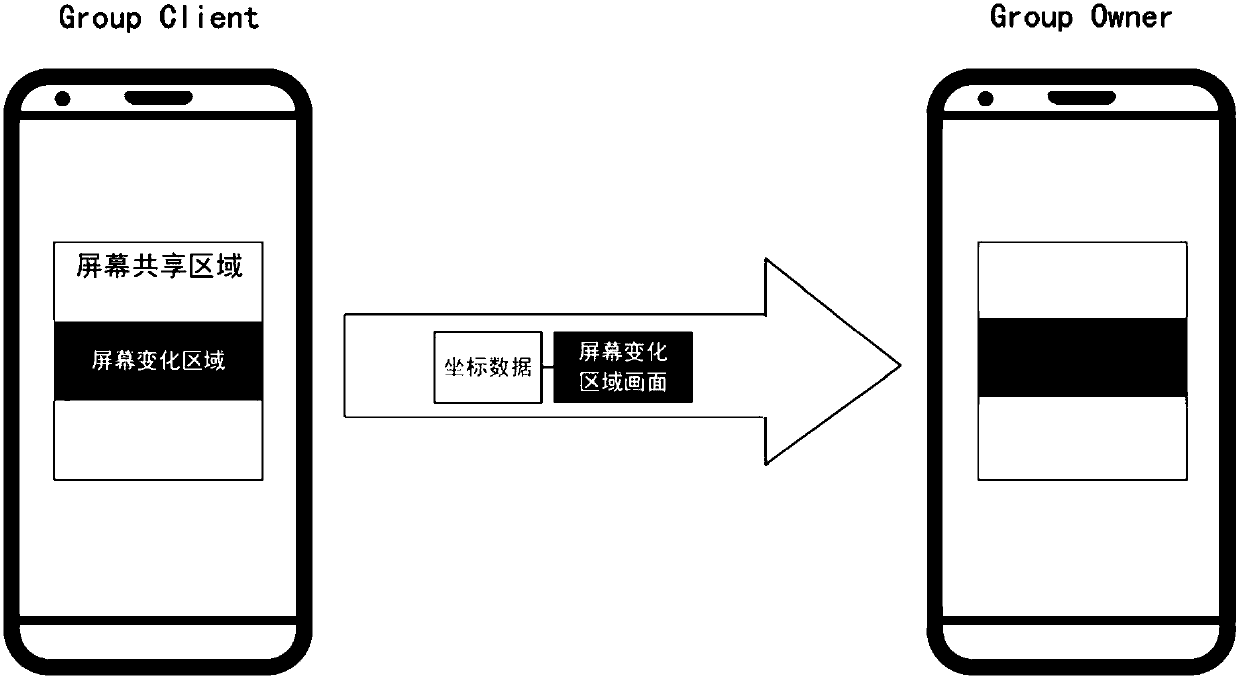
Android terminal screen sharing method
InactiveCN108021347AGuaranteed real-timeAddress privacy breachesDigital data protectionDigital output to display deviceScreen sharingWireless data
The invention discloses an Android terminal screen sharing method, and relates to the technical field of wireless data sharing at close range. The method establishes a data transmission channel between Android terminals through connection established by Wi-Fi Direct and achieves real-time transmission of data by means of a wireless direct connection technology; in the first time, only the screen information of a user-specified area is sent to a server; from the second time, only the area image which has changes for once in a shared area and starting point coordinates thereof are sent to the server at a time, so that the amount of shared transmission is reduced, transmission speed of shared data is accelerated, and real time performance of shared information is ensured; meanwhile, only theuser-specified area is shared, so that the problem of privacy leakage when an Android terminal screen is shared is solved, and security of user personal information is ensured.
Owner:航天科工智慧产业发展有限公司
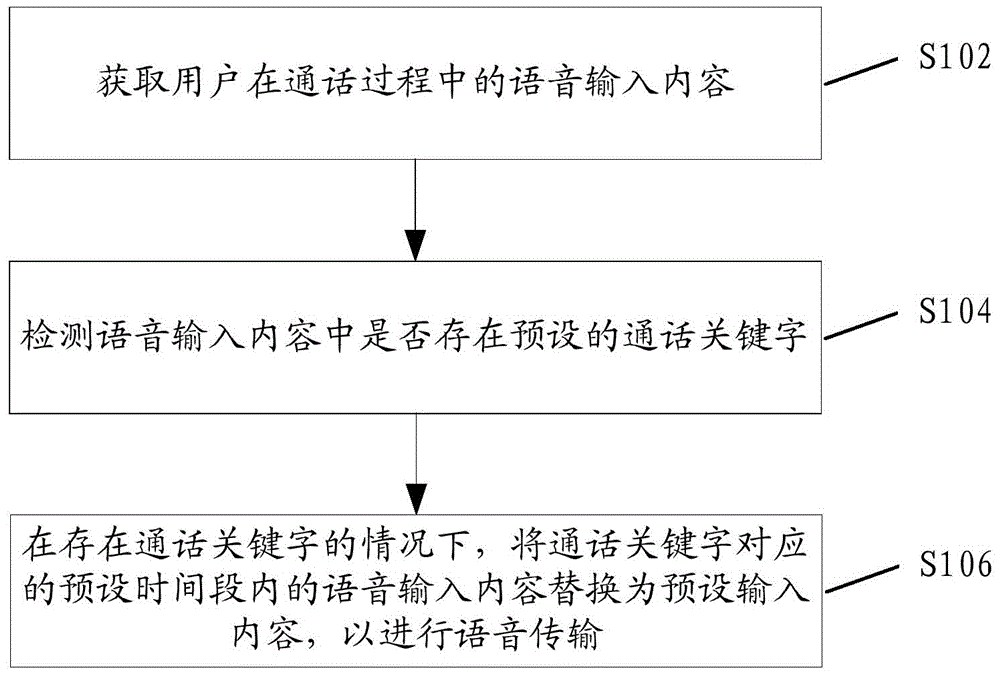
Method and apparatus for protecting privacy in conversation process and mobile terminal
InactiveCN106162624APrivacy protectionImprove experienceSecurity arrangementComputer networkPrivacy protection
The invention discloses a method and an apparatus for protecting privacy in the conversation process and a mobile terminal. The method comprises the steps of: acquiring voice input contents of a user in the conversation process; detecting whether preset conversation keywords exist in the voice input contents; and in the case that the conversation keywords exist, replacing the voice input contents corresponding to the conversation keywords in a preset time period with preset input contents so as to carry out voice transmission. By applying the method, the apparatus and the mobile terminal which are disclosed by the invention, a user can be prevented from leaking important information to other people, privacy of the user is protected, user experience is relatively good, and the problem of privacy leakage in the conversation process of the user, which is caused by the case that no any one method relates to privacy protection in the conversation process of the user in the prior art, is solved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method with privacy protection function for validating creditability of public terminal
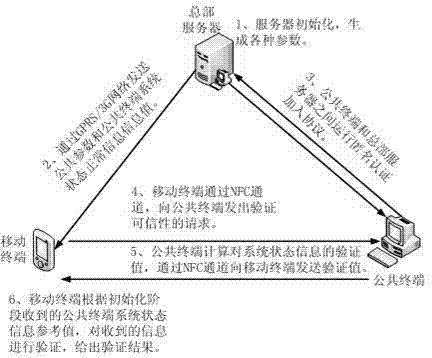
InactiveCN102761544AAddress privacy breachesPublic key for secure communicationUser identity/authority verificationValidation methodsServices computing
The invention relates to a method with a privacy protection function for validating the creditability of a public terminal, which can validate the creditability of the public terminal and can protect the privacy of the public terminal. A dependable computing module and a near-field wireless communication module (NFC) are arranged in a key service computing device, a common user holds a mobile terminal with the NFC communication module, before a public computer is used for carrying out a business transaction, the user holding the mobile terminal is close to the computer and sends a validating request through an NFC channel, the dependable computing module in the computer carries out Hash operation on several key content information in a system, then carries out signing on Hash values by directly using an anonymous attestation protocol, and sends signature data to the mobile terminal of the user through the NFC channel, the mobile terminal of the user carries out validation on signatures, and validation results are displayed through a screen of the mobile terminal. Through the method, a user extremely intuitively judges whether a computer for carrying out transactions is credible, thereby determining subsequent transaction actions; and because a direct anonymous authentication technology is adopted, the identity privacy of an authentication computer also can be protected.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
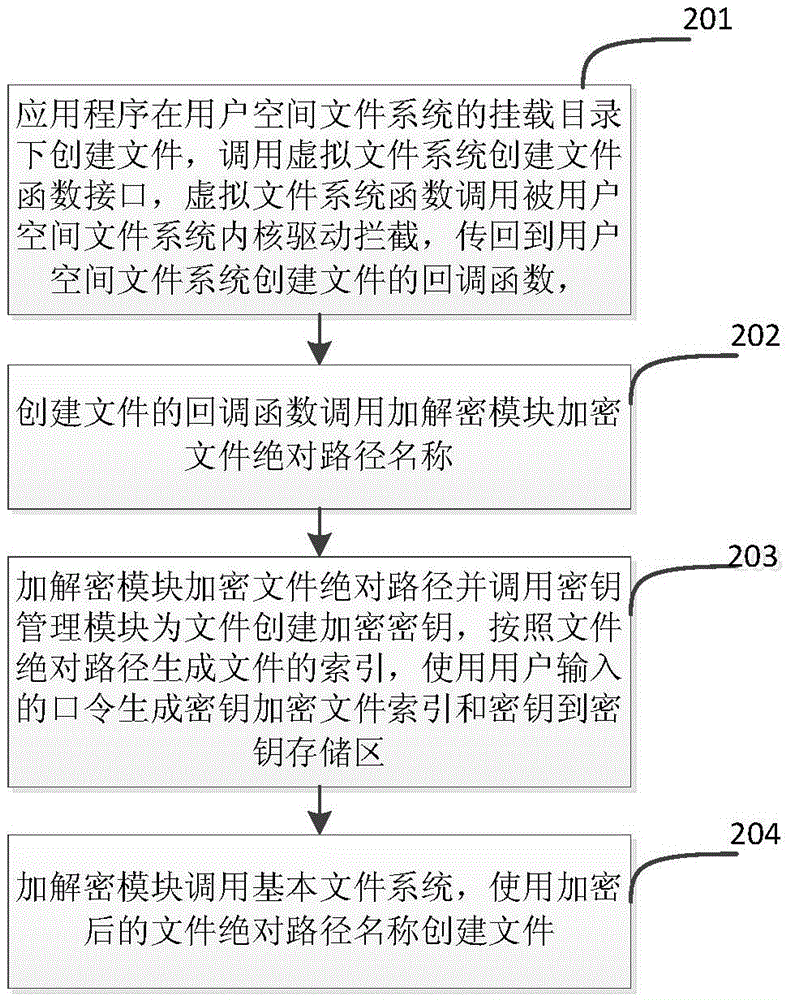
System and method for securely deleting file from user space on mobile terminal flash medium
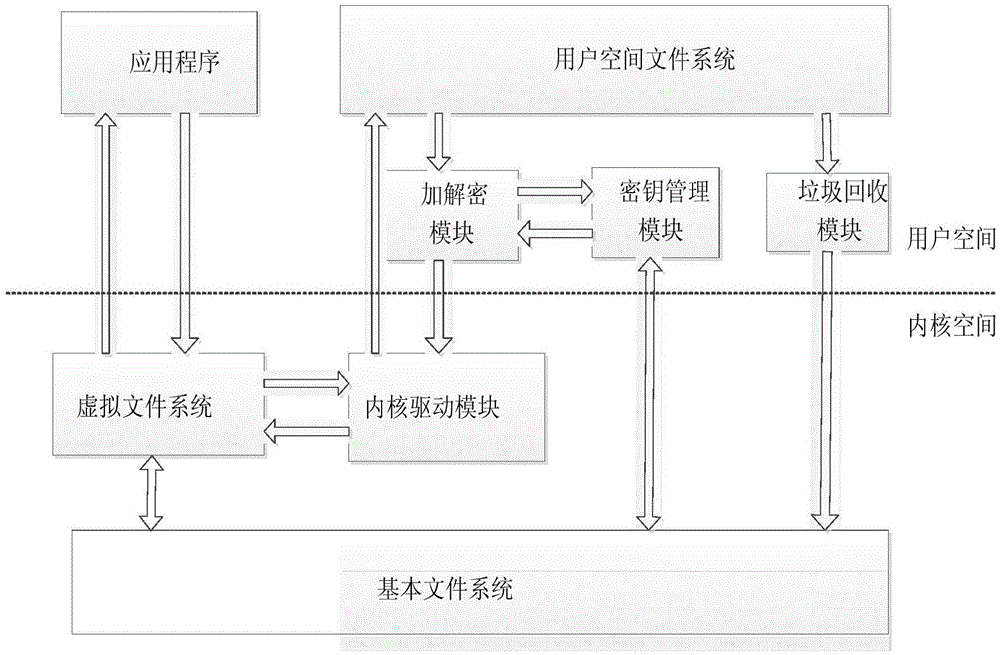
ActiveCN105630965ASafe deleteRemove completelyDigital data protectionSpecial data processing applicationsVirtual file systemFile system
The invention discloses a system and method for securely deleting a file from a user space on a mobile terminal flash medium. The system comprises the user space and a kernel space, wherein the user space comprises an application program, a user space file system module, an encryption and decryption module, a key management module and a garbage recovery module; and the kernel space comprises a virtual file system module, a kernel driving module and a basic file system. According to the method, an application program operation file function is transmitted to a virtual file system module; a virtual file system function is routed to a user space file system; the user space file system encrypts and decrypts an operation file; the encryption and decryption module calls a key management module to obtain a key; and a basic file system method is called for completing the file operation of the application program on the user space file system. The file is securely deleted in a file key deleting way; ciphertexts of the file key and file ciphertexts in the user space file system are thoroughly deleted from the flash medium in a garbage recovery way, so that the goal of securely detecting the file from the mobile terminal flash medium is realized.
Owner:XIDIAN UNIV
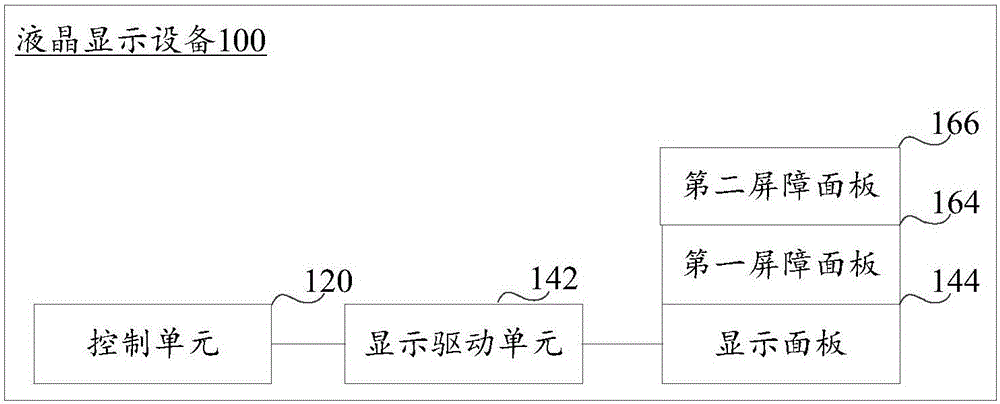
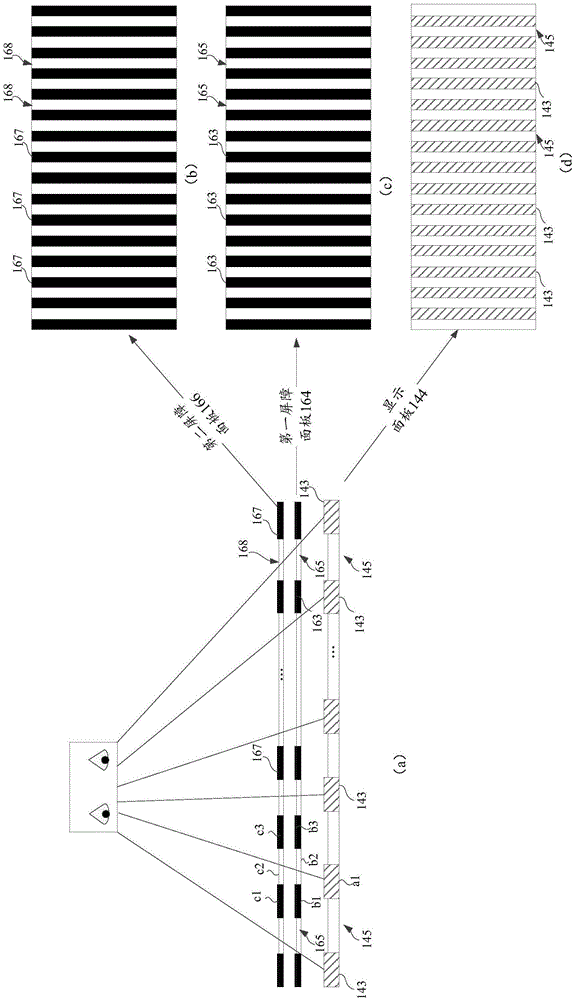
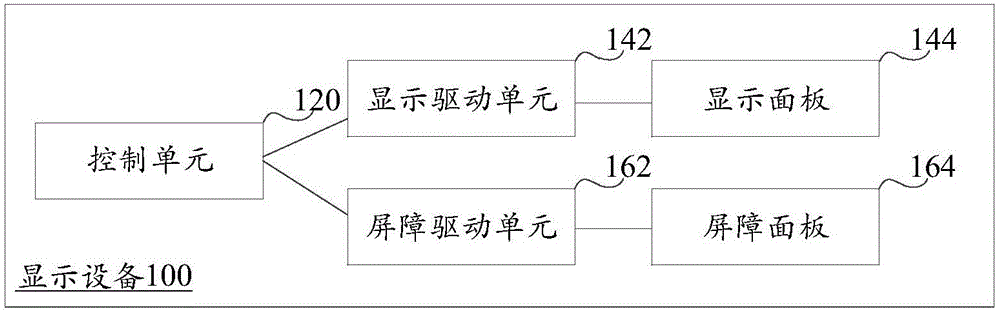
Display device and display method
InactiveCN106353916AAddress privacy breachesFix the leakTelevision system detailsStatic indicating devicesDisplay deviceComputer science
The invention relates to a display device and a display method, and belongs to the technical field of image displaying. The displaying device comprises a control unit, a display driving unit connected with the control unit, a display panel connected with the display driving unit, a first barrier panel located on the display panel and a second barrier panel located on the first barrier panel. A plurality of first barriers which are paratactic and distributed at intervals are distributed on the first barrier panel; a plurality of second barriers which are paratactic and distributed at intervals are distributed on the second barrier panel; the control unit is used for sending image frames to the display driving unit; the display driving unit is used for driving the display panel to display the image frames on a plurality of display areas which are paratactic and distributed at intervals, and all display areas are used for a part of displaying content of display image frames of all the all display areas. The display device provides the narrow-visual-angle visual range.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Full separable encryption domain image reversible data hiding method
ActiveCN105872305AFix security issuesAddress privacy breachesPictoral communicationImage segmentationBit numbering
The invention discloses a full separable encryption domain image reversible data hiding method. According to the full separable encryption domain image reversible data hiding method, in an image encryption part, firstly, an image is partitioned into image blocks; and then after a pixel value of each pixel point in each image block is added with one element in a random sequence for encryption, an absolute value of 256 is calculated so as to implement encryption. In the encryption mode, a difference value of a pixel value of each non-center pixel point in each image block and a pixel value of a center pixel point can be kept consistent before and after encryption; not only can data hiding be guaranteed to be carried out in an encrypted image, but also full separation of data extraction and image decryption is ensured; secret data can be effectively extracted in a encryption domain or a decryption domain; meanwhile, an original image can be guaranteed to be recovered in a distortionless manner after secret information is extracted; in the encryption domain image reversible data hiding part, the secret information is embedded in a combining manner, and the combined embedded secret information with a high occurrence frequency has a great bit number, so that data embedding capacity is effectively improved.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
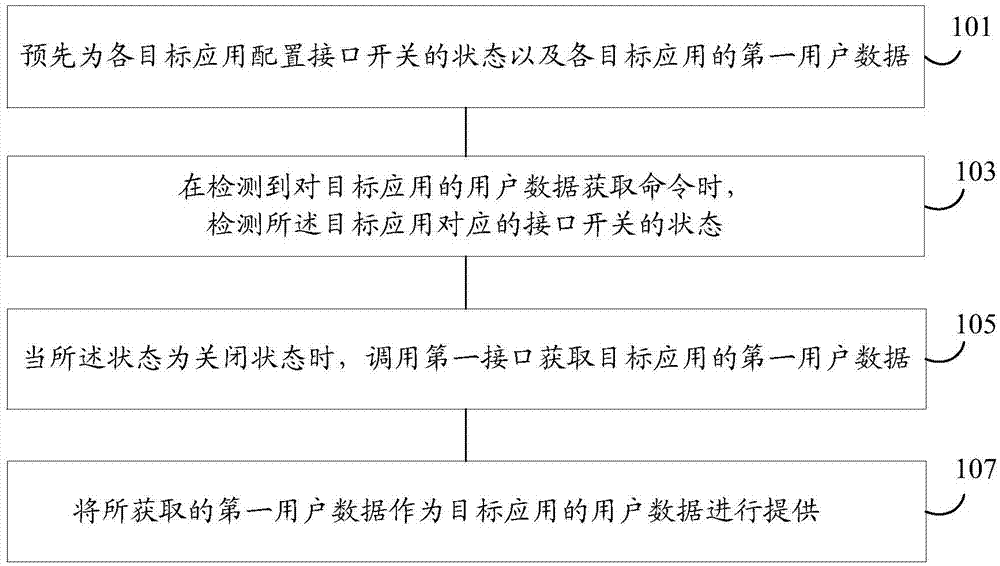
Device and method for providing user data
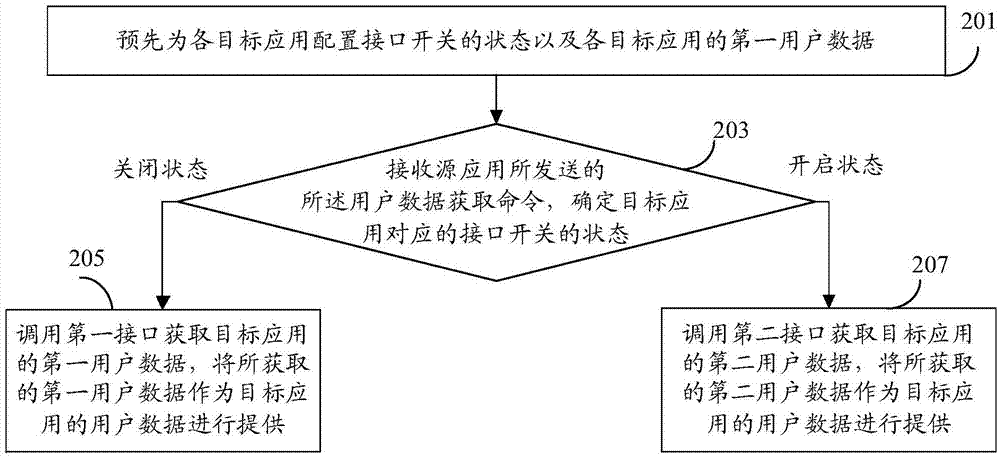
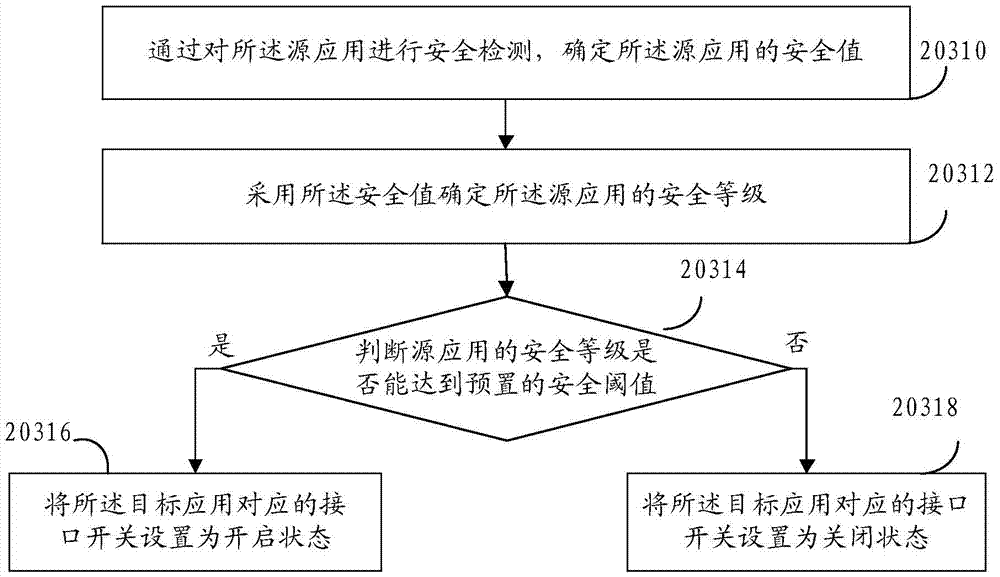
InactiveCN106874748AAddress privacy breachesGuaranteed privacy and securityDigital data protectionPlatform integrity maintainanceThird partyInternet privacy
An embodiment of the invention provides a device and a method for providing user data. The method includes: pre-configuring interface switch states and first user data for each target application; when detecting instructions for acquiring the user data of the target applications, detecting the corresponding interface switch states of the target applications; if the interface switch states are closed states, calling first interfaces to acquire the first user data of the target applications; providing the acquired first user data as the user data of the target applications. Mobile terminals can acquire the preset first user data through the first interfaces, and the first user data can be provided as the user data of the target applications, so that the problem of user privacy disclosure caused by acquisition of real user data by third-party software is solved, user data protection is enhanced, and user privacy security is guaranteed.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Data differential privacy protection sharing platform based on block chain
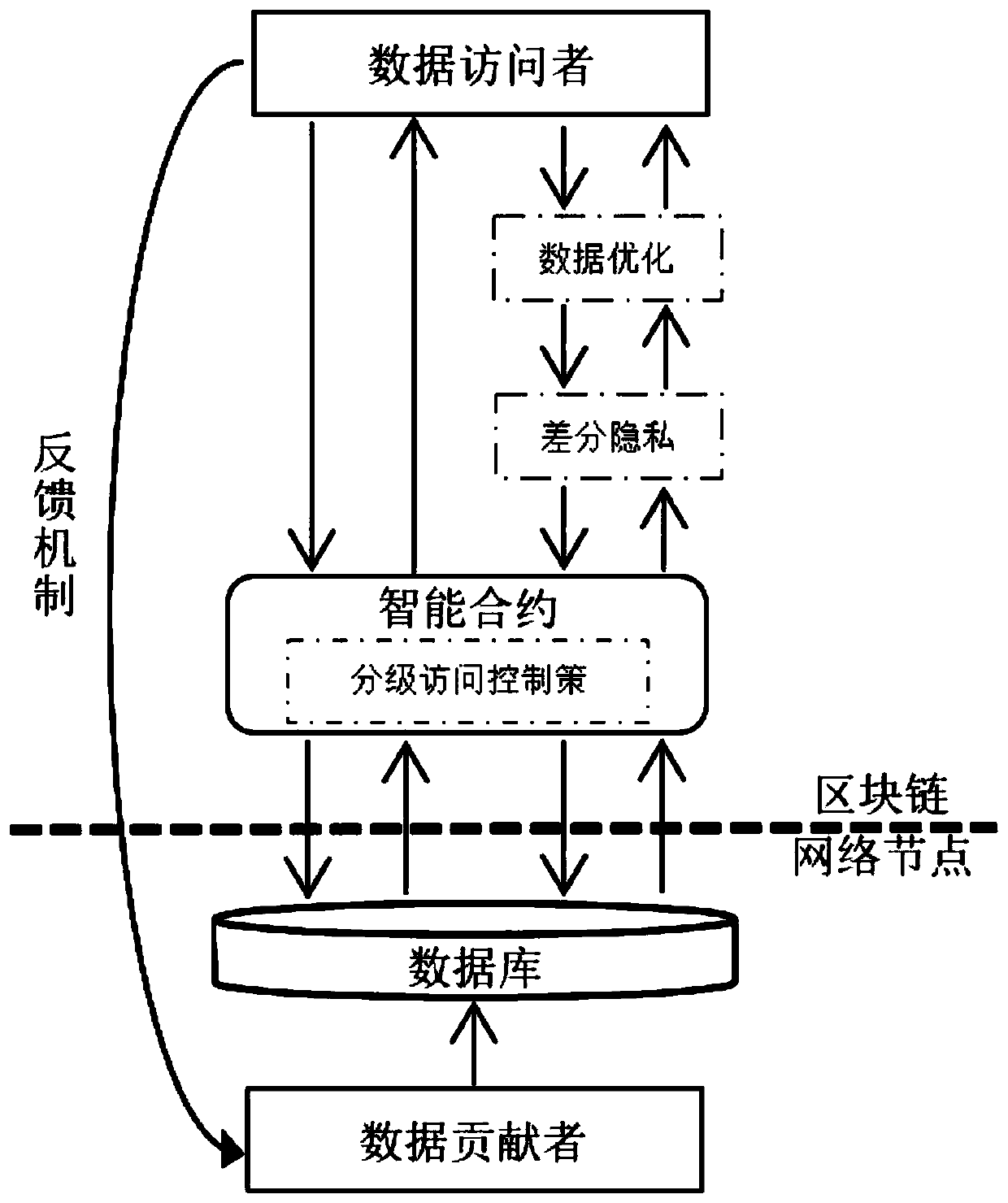
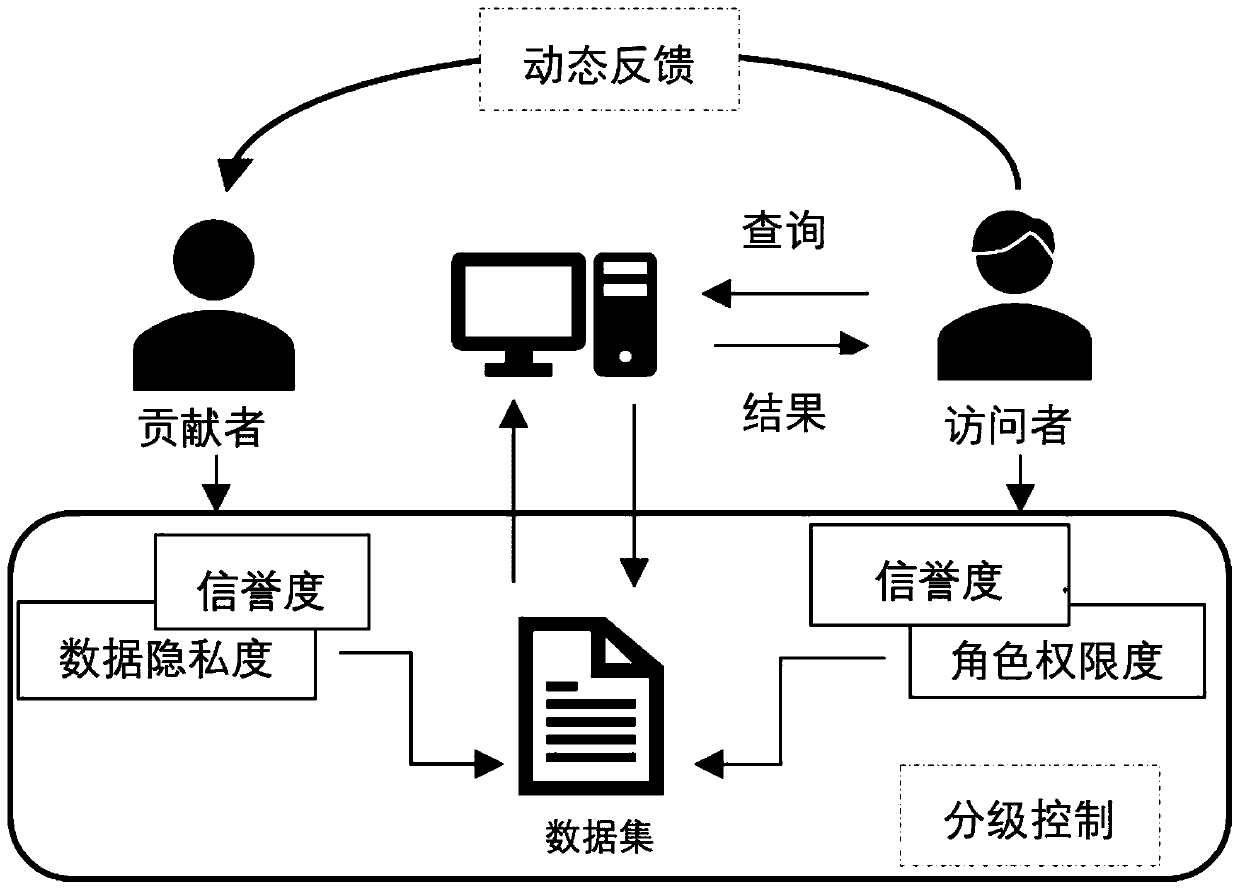
PendingCN110941856ARealize data sharing functionRealize a reasonable distributionFinanceDigital data protectionData providerPrivacy protection
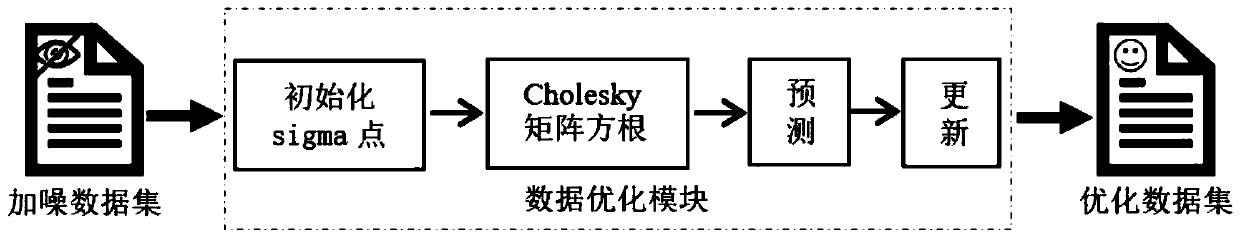
The invention discloses a data differential privacy protection sharing platform based on a block chain. The data differential privacy protection sharing platform based on the block chain comprises a data uploading module, a data access module, a data processing module and an intelligent contract module, and the data processing module comprises a hierarchical access control module, a data optimization module, a data query component and a credibility evaluation feedback module. The data differential privacy protection sharing platform is used for solving the problem of privacy leakage caused bya transaction process between a data provider and a data visitor in the prior art, and by realizing de-intermediation operation, the provider can obtain corresponding value income while sharing own health data for scientific research institutions and the like.
Owner:GUANGXI UNIV FOR NATITIES
Dredging and blocking combined privacy protection method and system
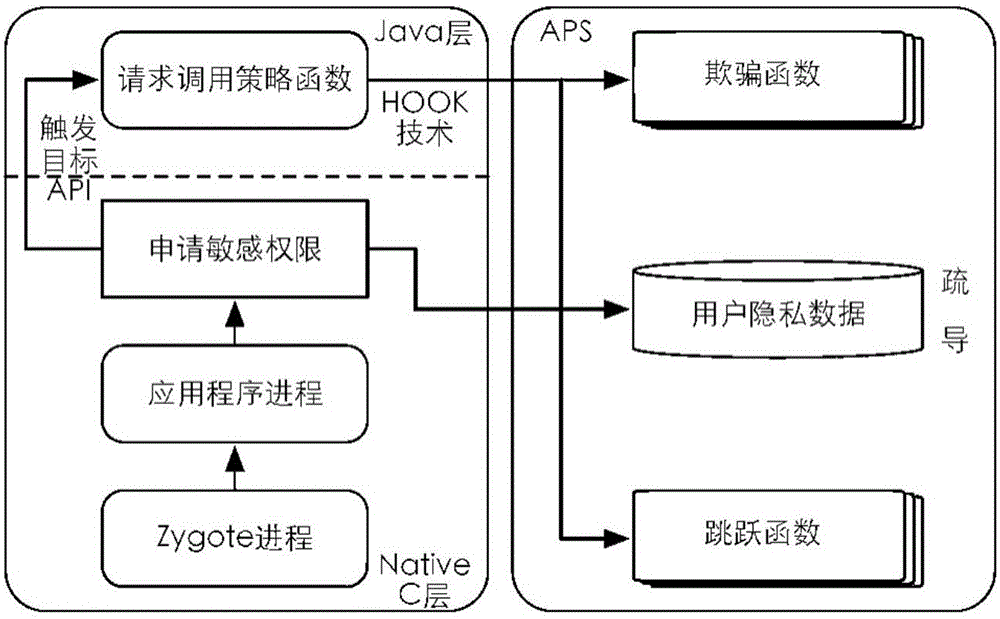
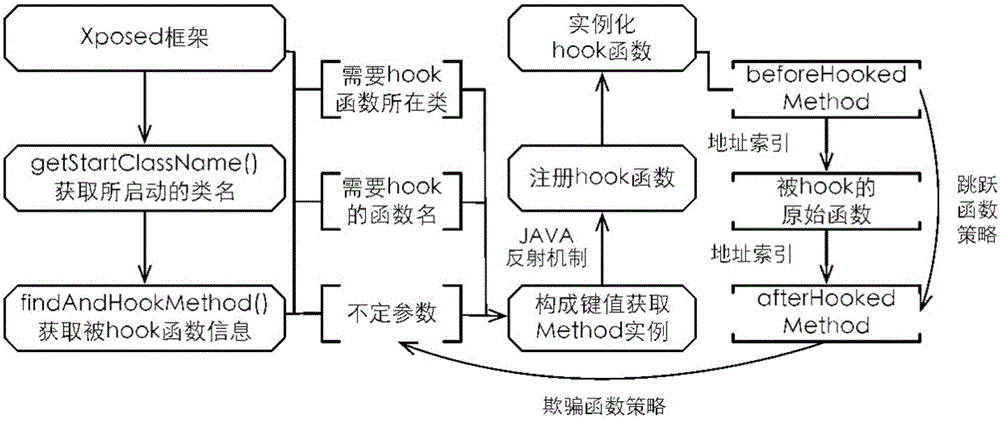
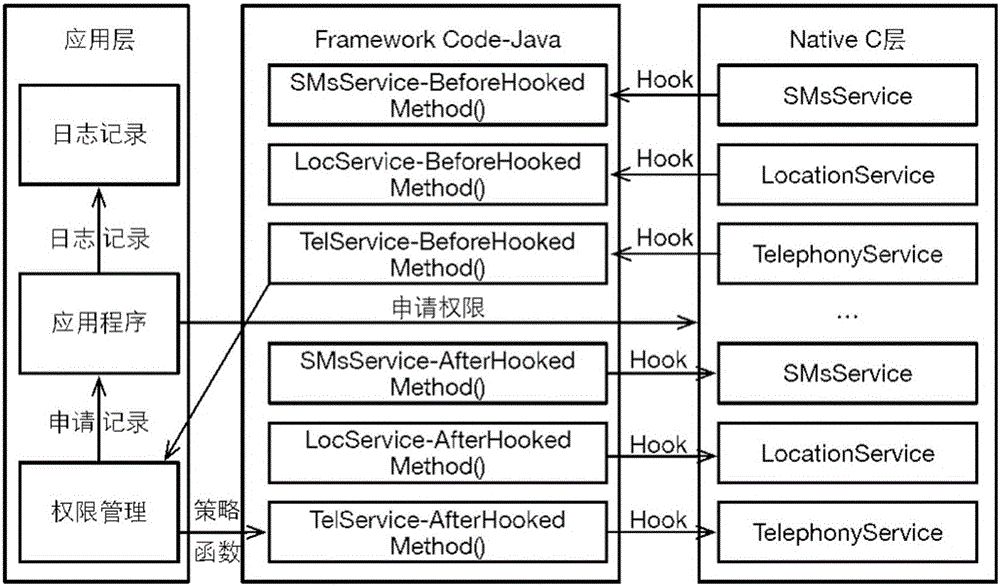
ActiveCN106203162AAddress privacy breachesFix security issuesDigital data protectionJumping functionPrivacy protection
The invention discloses a dredging and blocking combined privacy protection method and system. The method comprises steps as follows: 1) an application is scanned, all permissions of the application are listed, and whether the installed application is involved with a sensitive permission is judged; 2) as for the application involved with the sensitive permission, a user is reminded to use a cheat function strategy or a jump function strategy; the cheat function strategy specifically comprises steps as follows: the sensitive permission involved by an application program is hooked, a cheating function is implanted in the hooked function, and when the sensitive permission of application access is monitored, a false value is returned for the application; the jump function strategy specifically comprises steps as follows: a permission involved with a malicious application is extracted, and calling of the malicious application permission is bypassed by modifying an entry address of a permission function; 3) according to the strategy selected by a user, when the sensitive permission applies data, the false value is returned to the sensitive permission or permission calling is directly jumped. The security problems of privacy disclosure, permission abuse and the like of an existing application of a mobile phone can be effectively solved.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Big data privacy retrieval method based on edge computing
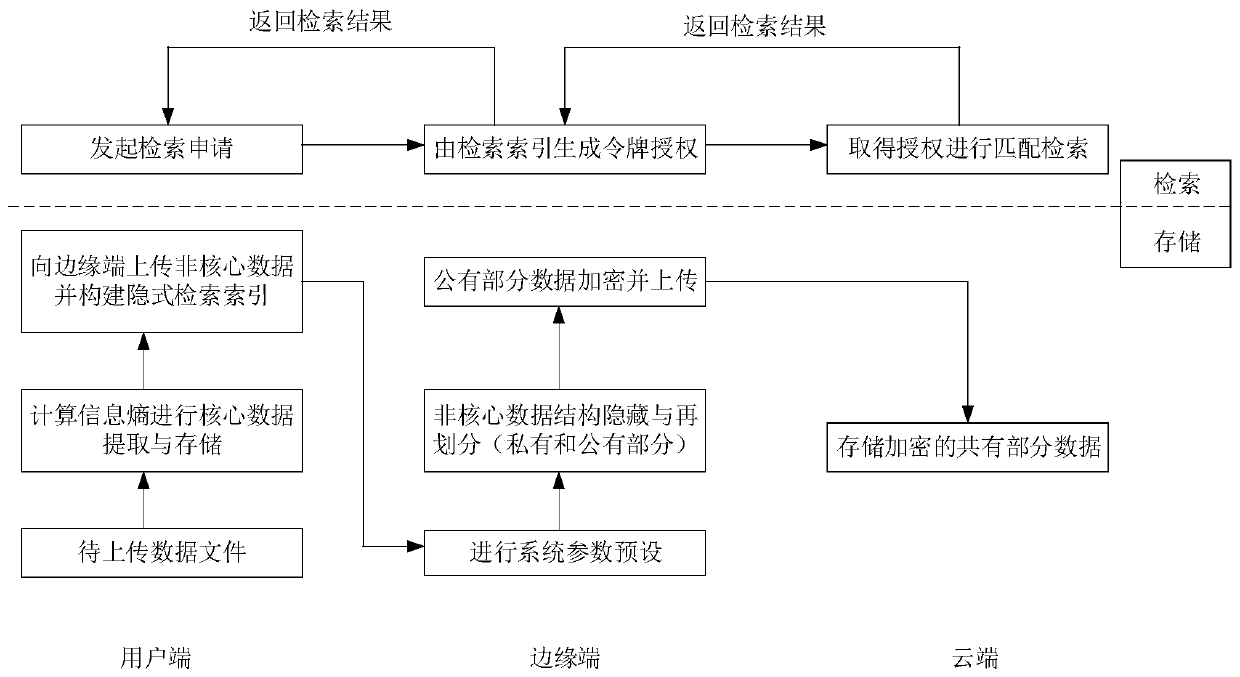
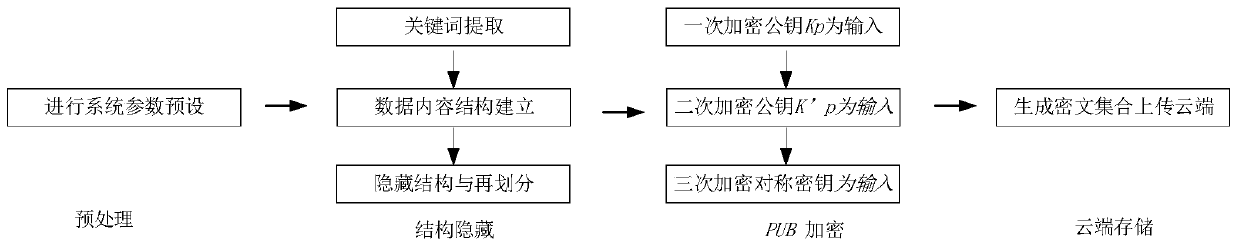
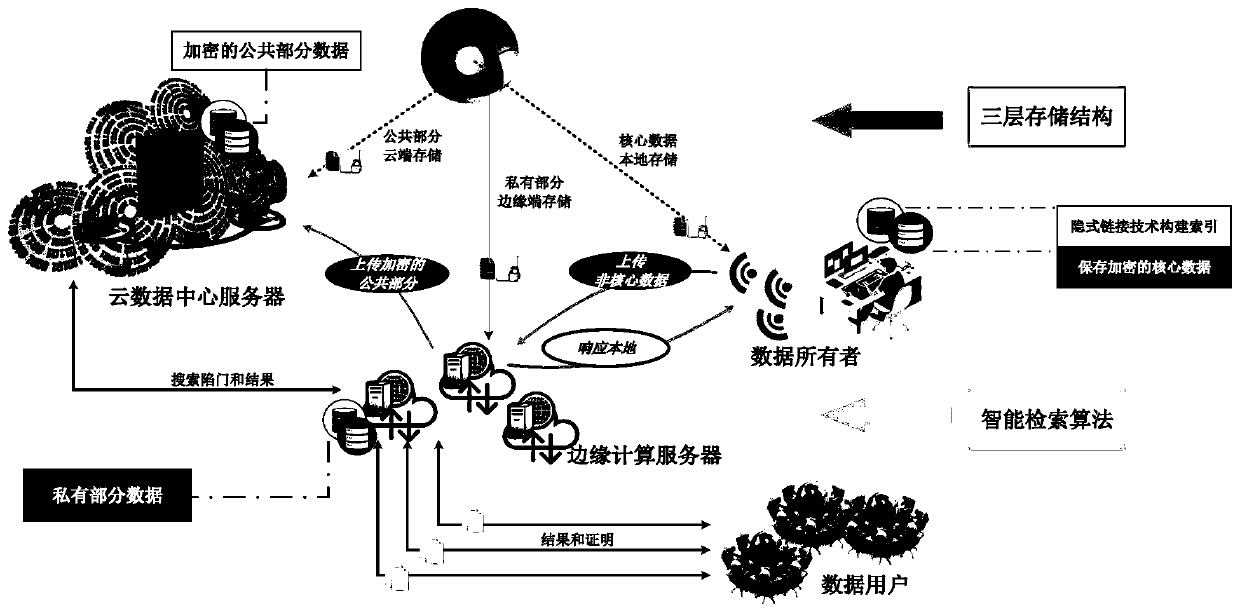
ActiveCN110413652AGuaranteed privacyAvoid safety hazardsDigital data protectionSpecial data processing applicationsEdge computingData retrieval
A big data privacy retrieval method based on edge computing comprises the steps that (1) enabling a user side to calculate information entropy of a to-be-uploaded data file, and carrying out core dataextraction and storage; 2) uploading the non-core data to an edge end and constructing an implicit retrieval index; 3) presetting system parameters at the edge end, and performing structure hiding and re-division on the non-core data to obtain public part data and private part data; 4) encrypting the public part of data and uploading the encrypted public part of data to a cloud, wherein the cloudstores the encrypted public part of data; and 5) enabling the user side to initiate a retrieval application according to the keyword, enabling the edge side to generate a retrieval token according tothe keyword and the implicit retrieval index, enabling the cloud side to perform keyword matching retrieval after acquiring the retrieval token, returning a retrieval result to the edge side, and enabling the edge side to return the retrieval result to the user side. According to the method, the effectiveness, reliability and flexibility of the system in the storage and retrieval process can be ensured, and efficient and private data retrieval is achieved.
Owner:HUAQIAO UNIVERSITY
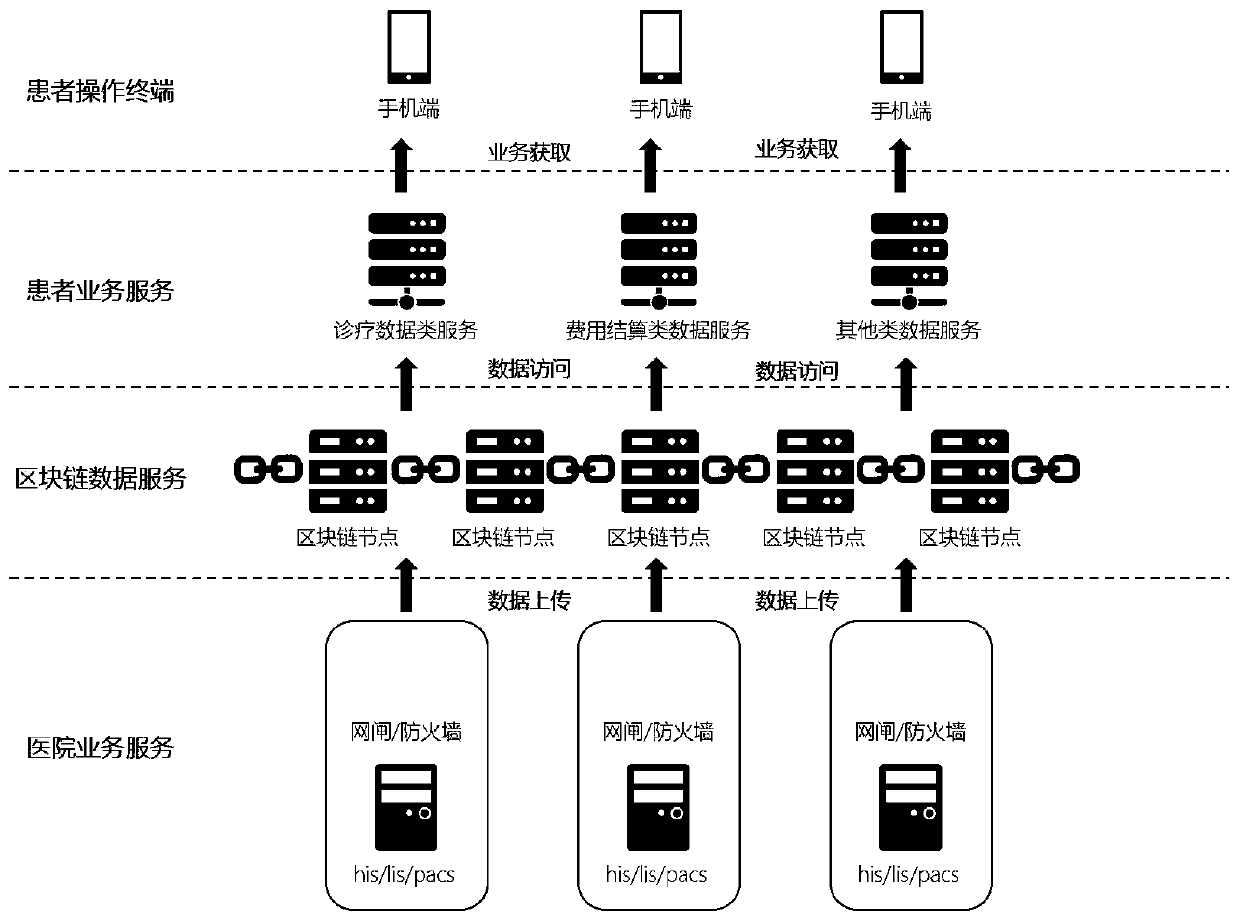
Medical data intranet and extranet interaction safety protection method based on a block chain technology
PendingCN109741800AMaintain data two-way communicationImprove data securityDigital data protectionPatient-specific dataTamper resistanceData access
A medical data intranet and extranet interaction safety protection method based on a block chain technology comprises the following steps that step 1, data is uploaded, and a client creates a transaction proposal and sends the transaction proposal to an endorsement node; the endorsement node executes the chain code, and generates a read-write operation set based on the read and written Key; the endorsement node returns a proposal result to the client; the client submits a transaction proposal to the sorting node, wherein the transaction content comprises a read-write operation set from a proposal result; the sequencing node encapsulates the sequenced transaction proposal into a block; wherein the block is to be sent to an acknowledgement node; and step 2 data access is carried out: 1) personal medical data: the user selectively opens part of private data to a specified doctor or a specified medical institution for access as required, and 2) institution data: the institution selectivelyopens part of private data to a specified institution or a specified person for access, so that the method has the advantages of data security and tamper resistance.
Owner:李秦豫
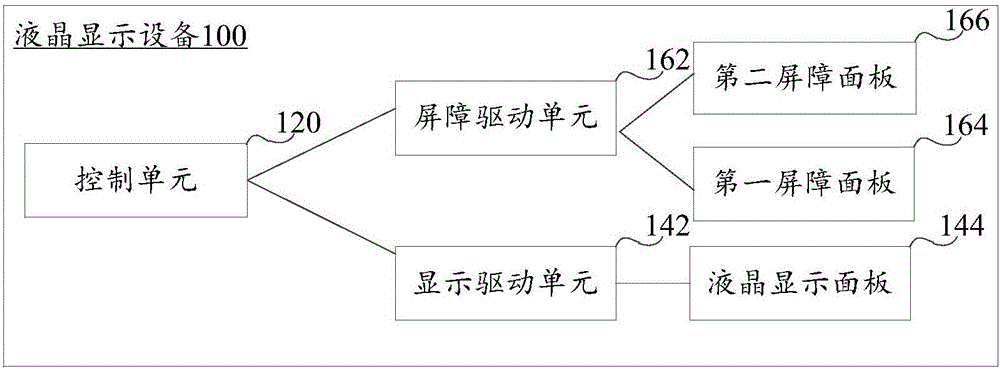
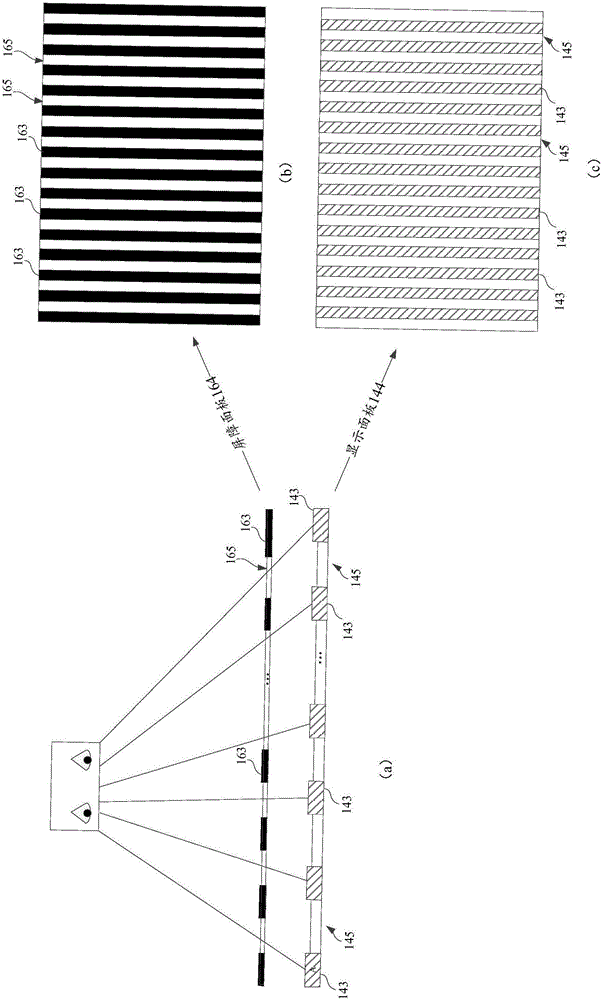
Display equipment and display method
ActiveCN106557710AAddress privacy breachesAcquiring/recognising eyesCathode-ray tube indicatorsComputer scienceControl unit
The invention provides display equipment and a display method, and belongs to the technical field of image display. The display equipment provided by the invention comprises a control unit, a display drive unit and a barrier drive unit which are connected with the control unit, a display panel connected with the display drive unit, and a barrier panel which is connected with the barrier drive unit and is positioned on the display panel, wherein the control unit is used for sending display image frames to the display drive unit and sending a first command to the barrier drive unit; the display drive unit is used for driving the display panel to display the display image frames on a plurality of parallel display areas arranged at intervals, and each display area is used for displaying the contents of a part of the display image frames respectively; and the barrier drive unit is used for controlling electrodes of display barriers arranged at the positions of odd numbers or even numbers on the barrier panel in on state according to the first command. According to the display equipment provided by the invention, the visual range of a narrow visual angle is provided.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com