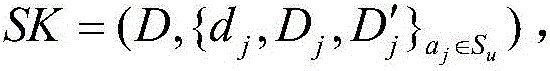Block chain privacy data access control method based on attribute encryption
A technology for access control and privacy data, applied in the field of cryptography, can solve the problem of not being detailed enough to consider attribute correlation, and achieve the effect of privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
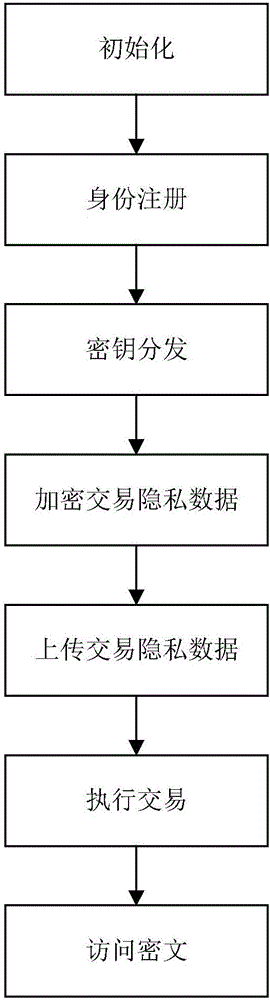
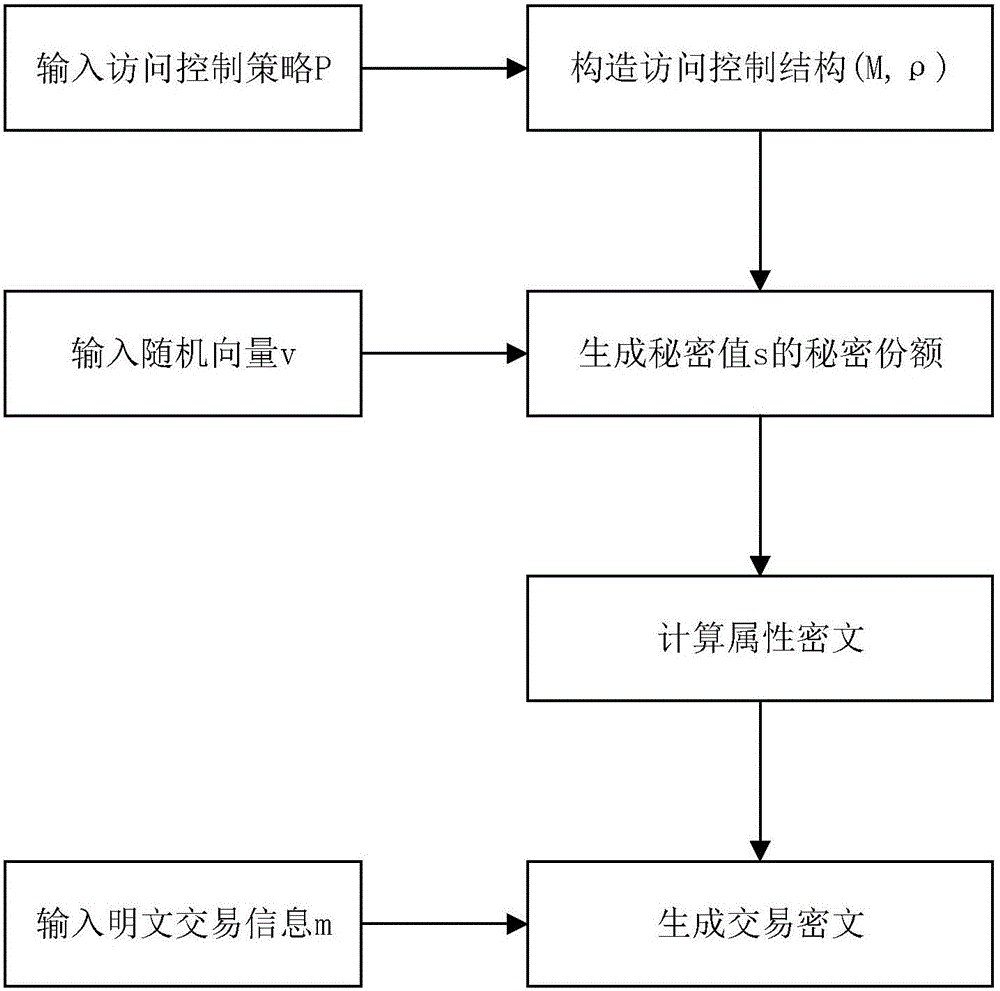
[0048] The present invention will be further described below in conjunction with the accompanying drawings.
[0049] Refer to attached figure 1 , the realization steps of the present invention are as follows.
[0050] Step 1, initialization.
[0051] Enter system security parameters 1 λ , generating the first multiplicative cyclic group G of prime number p 0 , the second multiplicative cyclic group G 1 and the finite field Z p , randomly select the first multiplicative cyclic group G 0 The generator g of , defines a bilinear map e:G 0 ×G 0 →G 1 ;
[0052] From the finite field Z p Select N elements as system attributes to form a system attribute set S, divide the attributes in S into n trees according to the correlation between attributes, and set the depth of the i-th tree as l i , define l=max{l i} i∈[1,n] Represents the maximum depth of n trees, i∈[1,n];
[0053] Randomly select the first vector U=(u θ ) 1≤θ≤l and the second vector U'=(u' θ′ ) 1≤θ′≤n , whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com