Big data privacy retrieval method based on edge computing
An edge computing and big data technology, which is applied in the field of big data privacy retrieval based on edge computing, can solve problems such as data-intensive service computing and storage not proposed, inability to apply traditional management models, lack of data security, etc., to achieve Efficient information retrieval, reduced computing scale, and the effects of avoiding potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below through specific embodiments.
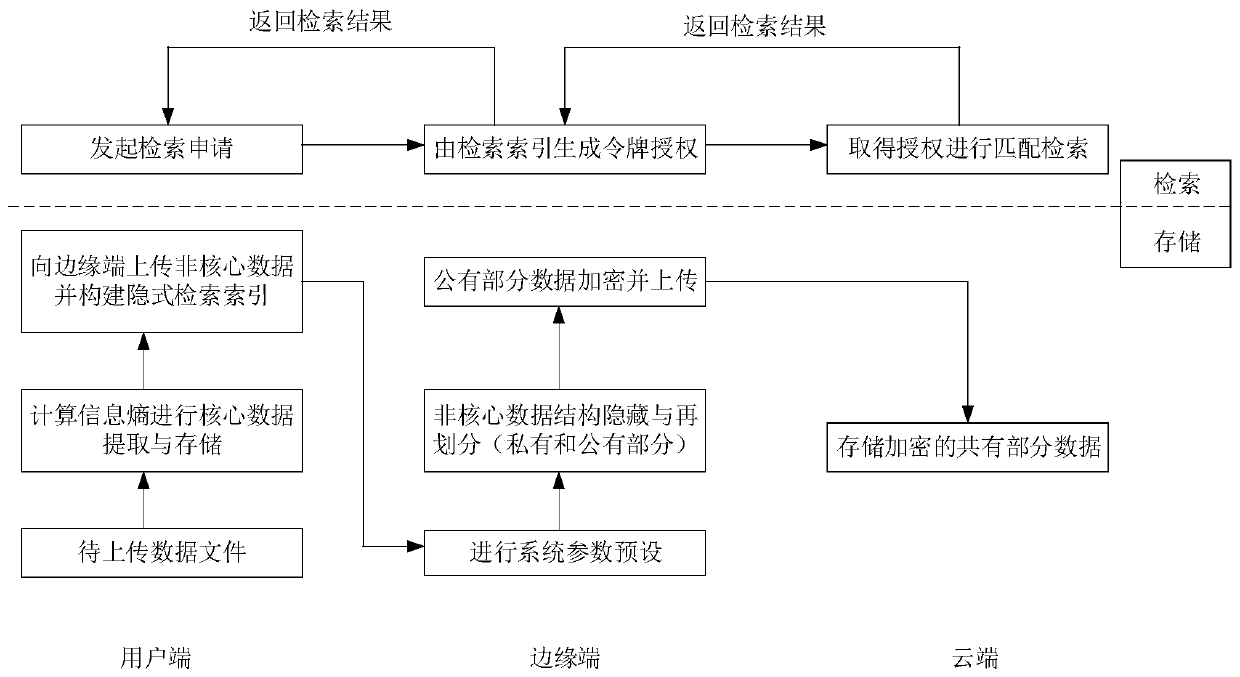
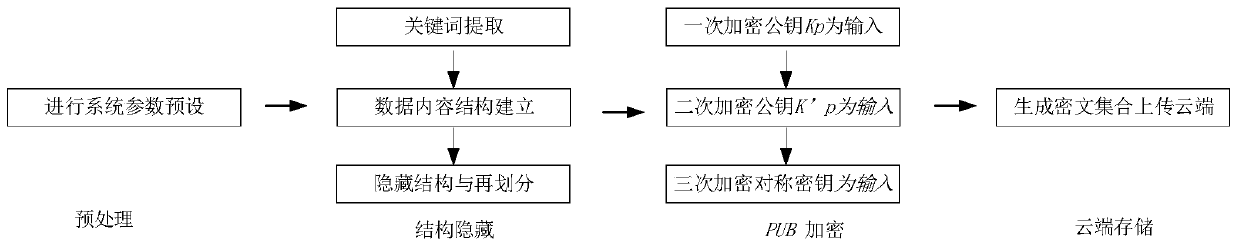
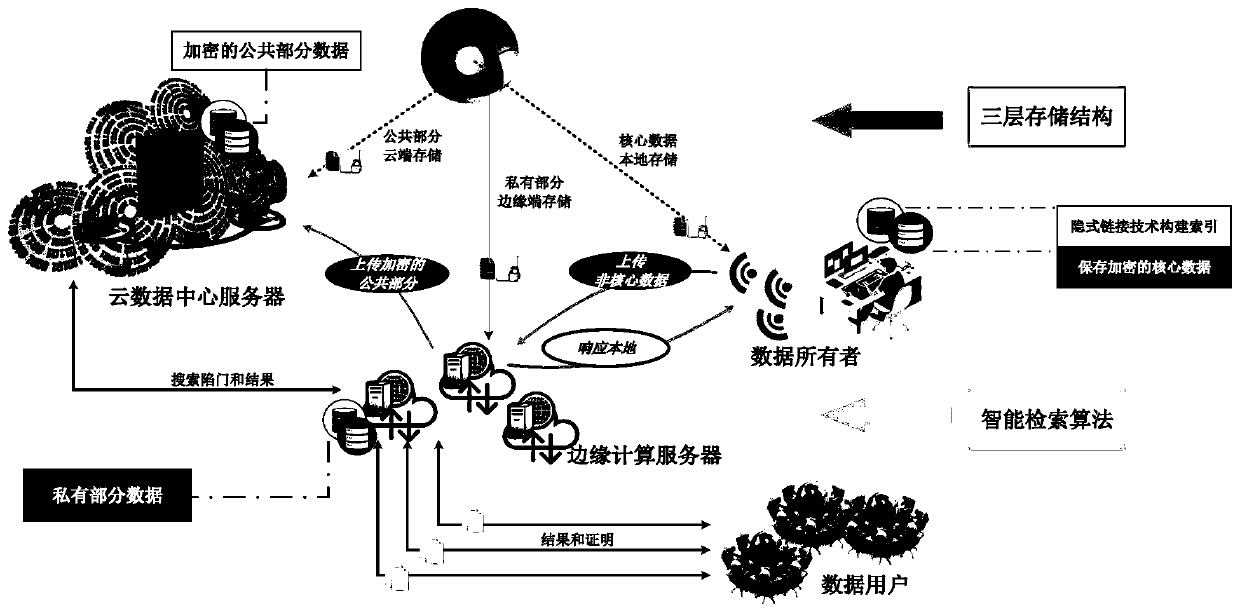
[0034] In order to ensure that users have complete control and management rights of private data, the method of large data privacy retrieval based on edge computing in the present invention makes full use of the advantages of edge and cloud, and constructs a "local-edge-cloud" layered storage and query system. Preprocess the data to be uploaded, that is, divide the data, decide the amount of data to be retained at each level based on semantic protection, and avoid the risk of content leakage by creating an implicit index structure locally and at the edge. By improving the traditional searchable encryption algorithm, a light-computing hybrid encryption mechanism is designed to be suitable for the cloud and edge collaborative work mode. In the process of retrieving data, the actual data content is hidden from the cloud and edge servers, thereby realizing privacy data protection.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com