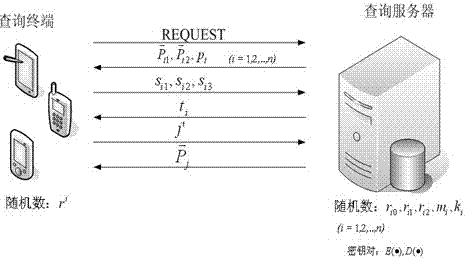
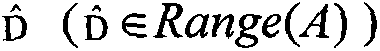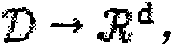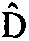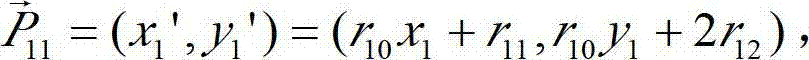Patents
Literature
329results about How to "Guaranteed privacy and security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic game system, method of managing and regulating said system
InactiveUS6117011AImprove securityAvoid possibilityComputer controlSimulator controlSecure communicationAutomatic control
PCT No. PCT / RU95 / 00241 Sec. 371 Date Jan. 27, 1998 Sec. 102(e) Date Jan. 27, 1998 PCT Filed Nov. 10, 1995 PCT Pub. No. WO97 / 05557 PCT Pub. Date Feb. 13, 1997An electronic gaming system is disclosed that includes a central computer station, a plurality of peripheral computer stations, and a data exchange network for coupling the peripheral computer stations to the central computer station. The central computer station includes an administrative subsystem, a player's registration subsystem, a game accounts managing subsystem, an information tabulating, storing and searching subsystem, a game recording subsystem, a scoring subsystem, a wagering and betting subsystem, an executive gaming subsystem, an electronic payment subsystem, an information protection subsystem, a secure communications subsystem, and a game selection subsystem. Each of the peripheral computer stations include a subsystem for admitting and registering players with the central computer station and a gaming interface subsystem. To ensure security of the electronic gaming system, a player seeking to enter the system transmits an encoded message from their peripheral computer station to the central computer station that includes a set of key attributes associated with the player. The central computer station decodes and compares the transmitted set of key attributes with individual information previously stored in the information protection subsystem in order to identify each player during registration based upon the set of key attributes transmitted by each player. The system may automatically control money transactions with each player's bank accounts based upon the player's scoring and wagers in each selected game.
Owner:LYDIA VLADIMIROVNA NESTERENKO
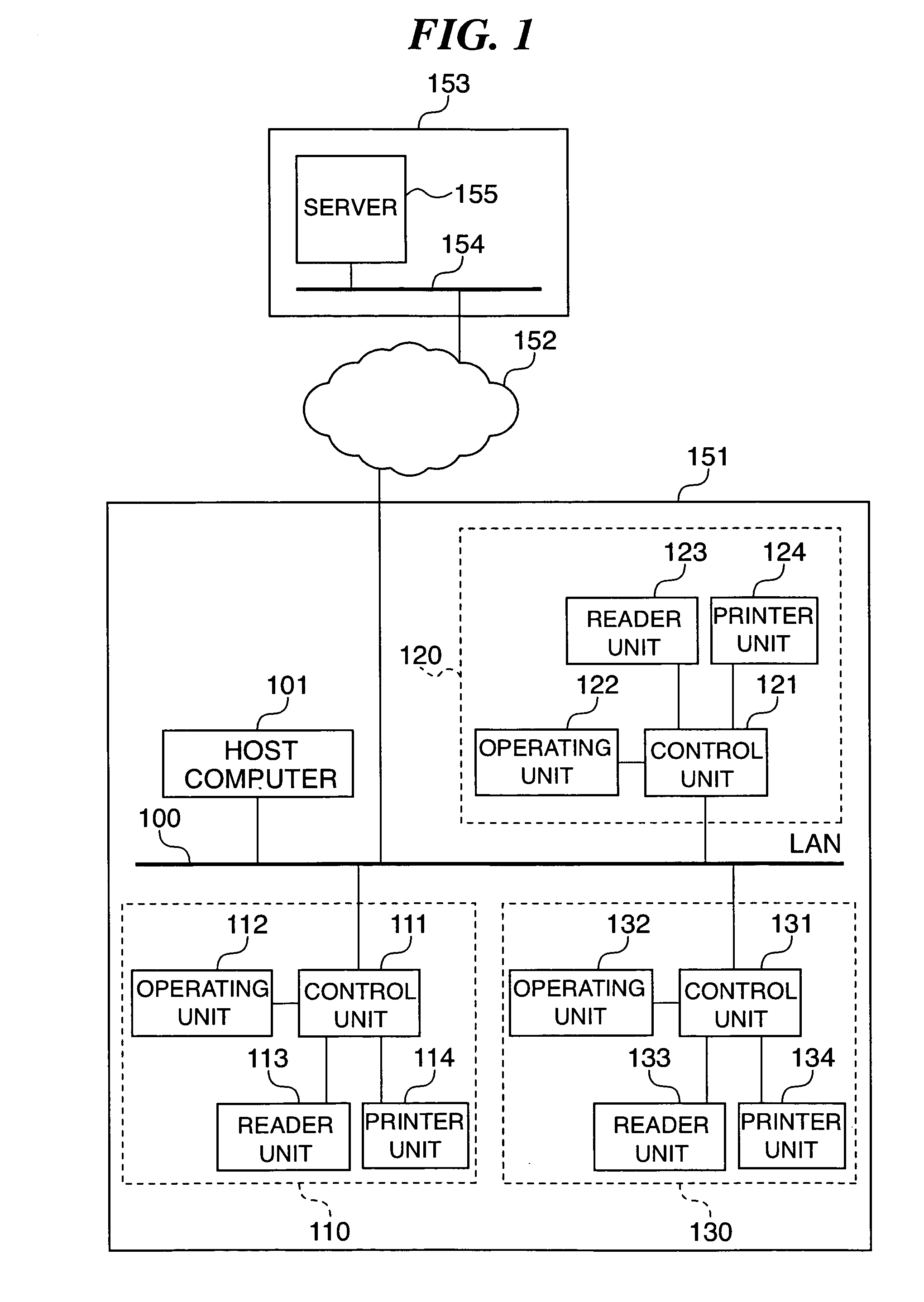
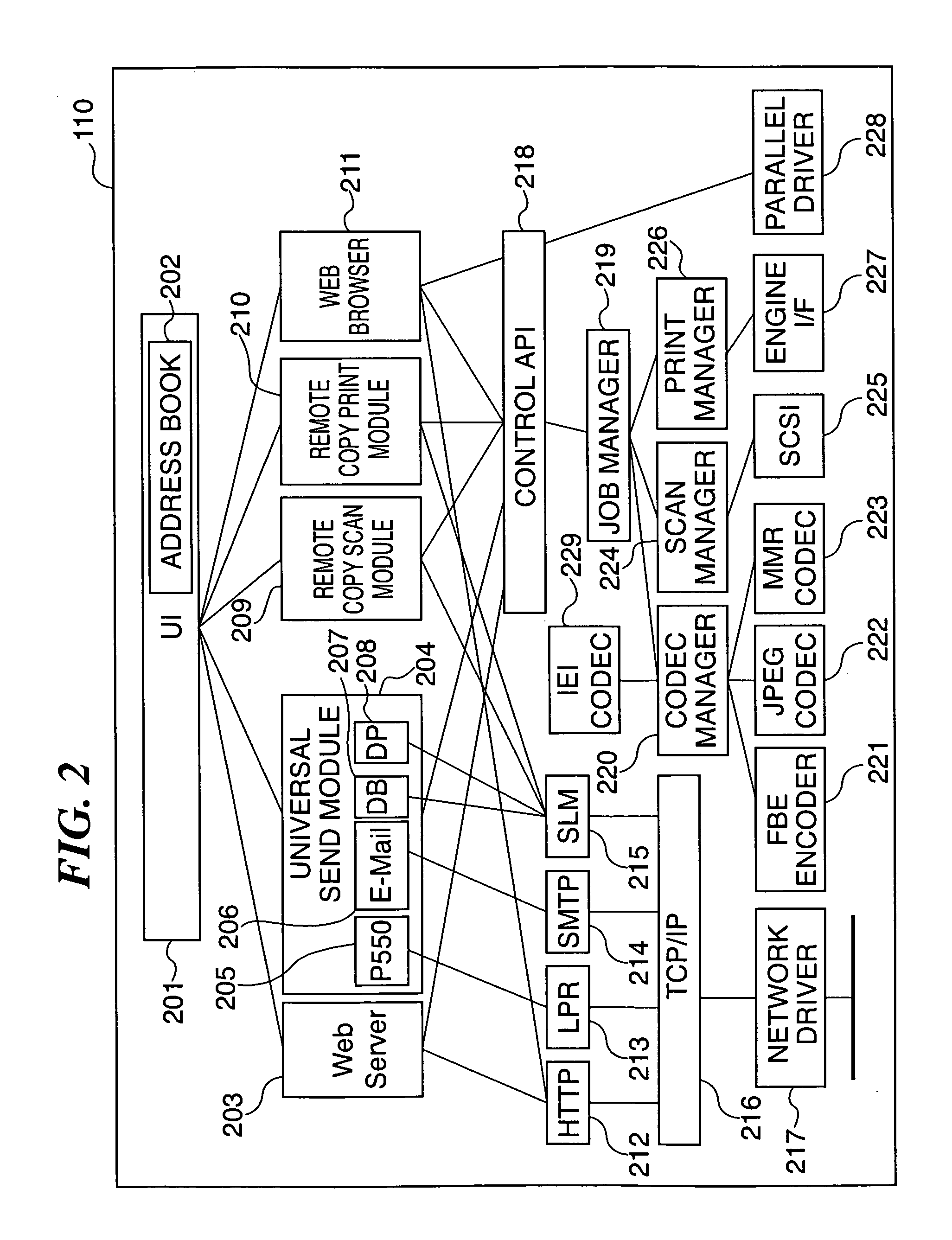
Embedded device, control method therefor, program for implementing the control method, and storage medium storing the program
InactiveUS20060059462A1Easily and flexibly expandableSecuring privacy and securityWeb data retrievalNatural language data processingImaging processingWeb browser
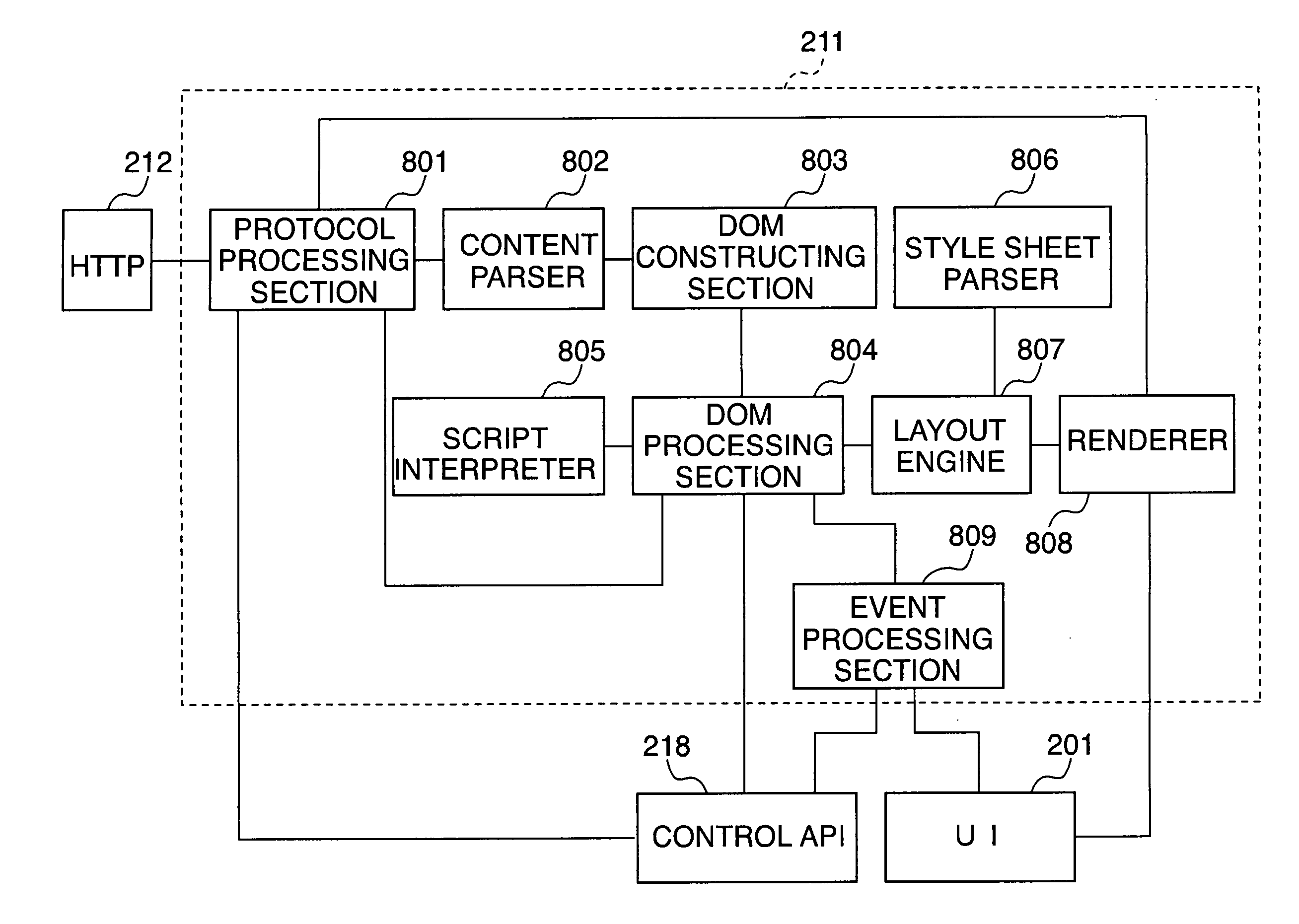
An embedded device incorporating a Web browser, which enables a server to provide a dynamic content adapted and linked to a function specific to the embedded device and a status of the same, as an easily and flexibly expandable service in response to access from the embedded browser, and enables securing privacy and security of information on a client. In an image processing apparatus (110) implementing the embedded device, a Web browser module (211) loads Web content data containing at least document data which is described in a markup language and has a script or information for reference to a script embedded therein, and performs presentation based on the loaded Web content data. A controller unit (111) controls information and operation of the image processing apparatus. A script interpreter (805) incorporated in the Web browser module interprets the document data contained in the loaded Web content data and processes the script or the information for reference to a script embedded in the document data. A control API module (218) provides an interface via which the script interpreter gains access, based on the processing of the script, to a DOM managed in the Web browser module. Further, the control API module provides an interface via which the script interpreter gains access, based on the processing of the script, to the information and operation of the embedded device, controlled by the controller unit.
Owner:CANON KK
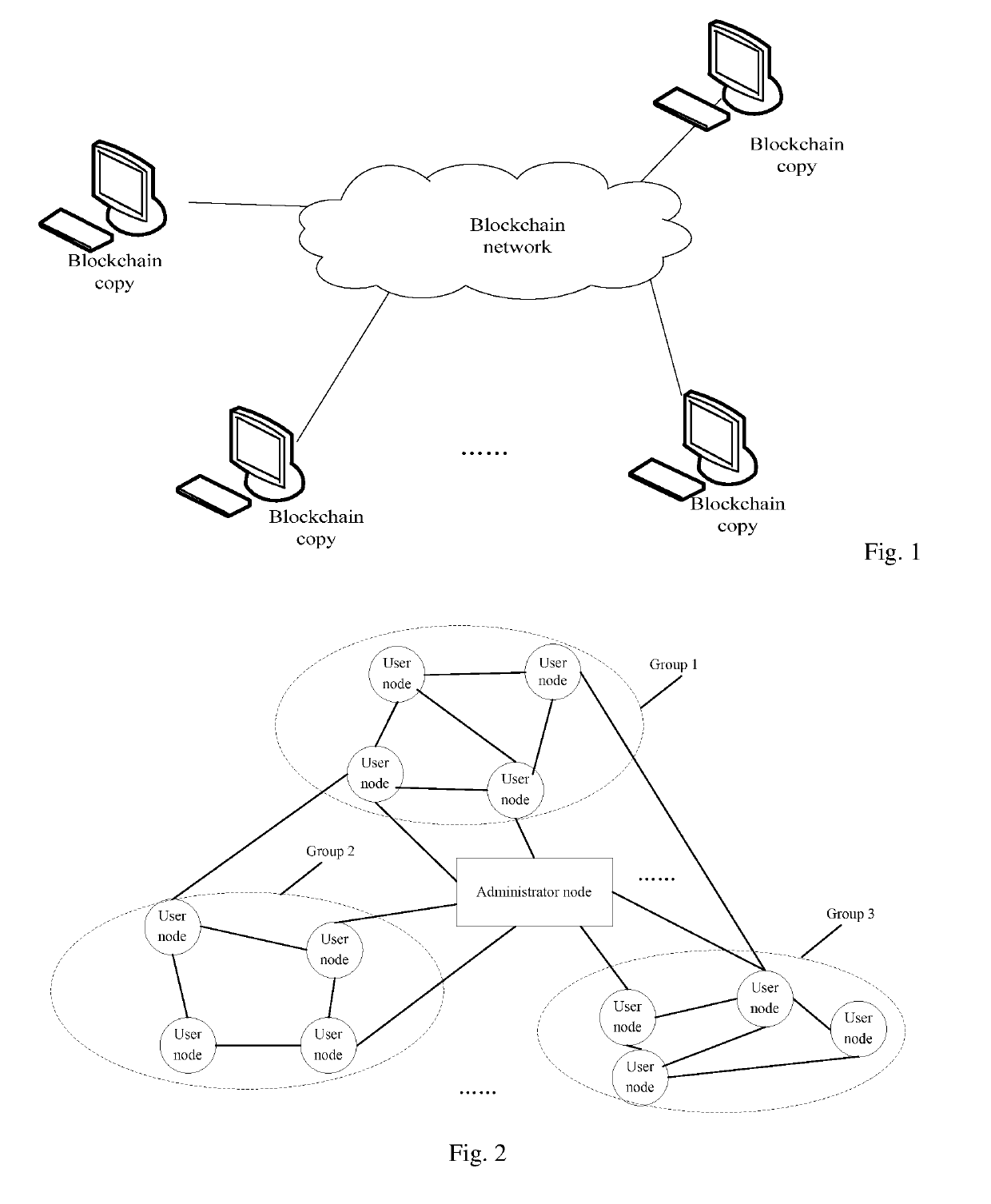
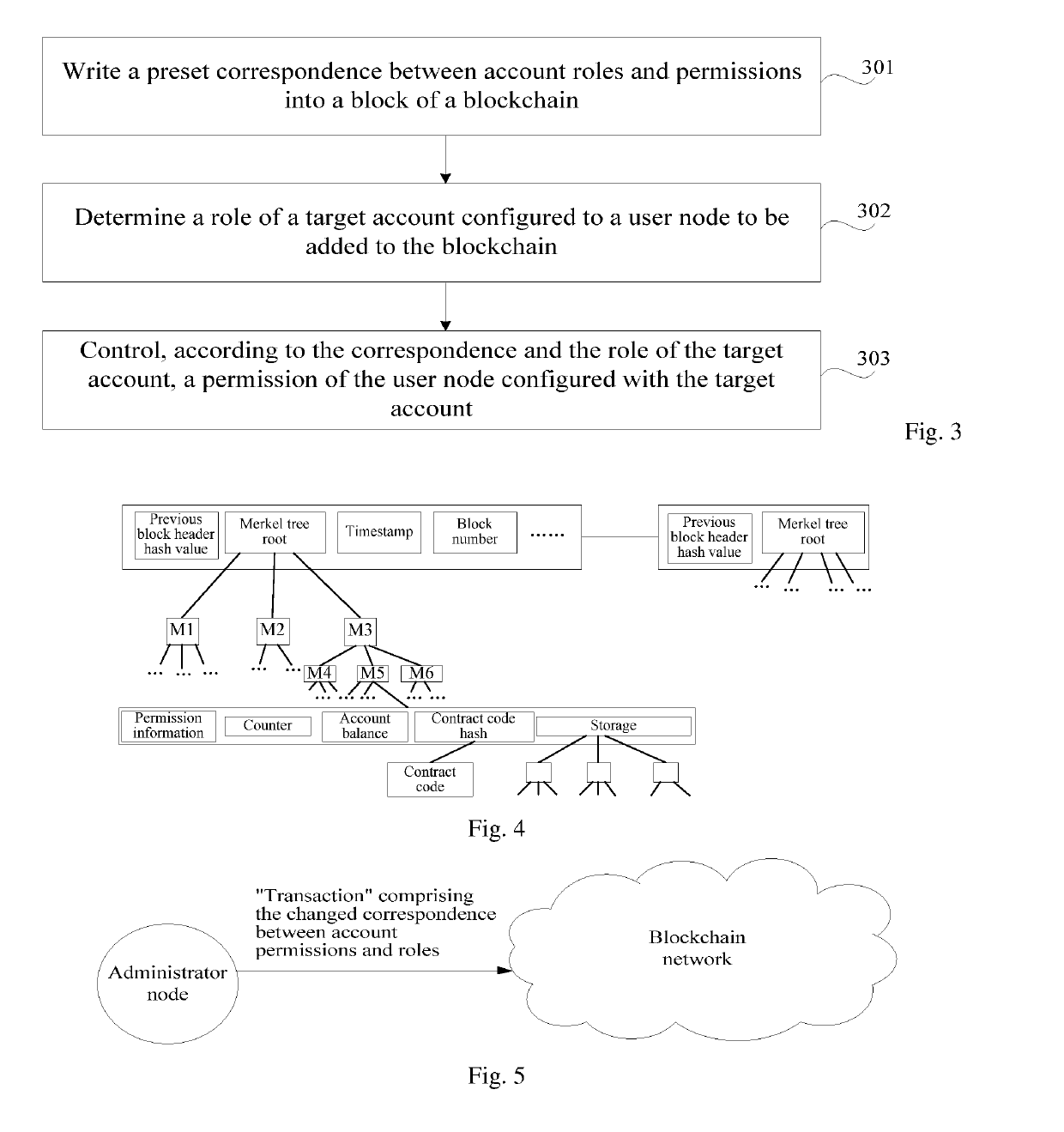
Permission control method, apparatus and system for block chain, and node device
InactiveUS20190238550A1Guaranteed privacy and securityEncryption apparatus with shift registers/memoriesBlockchain
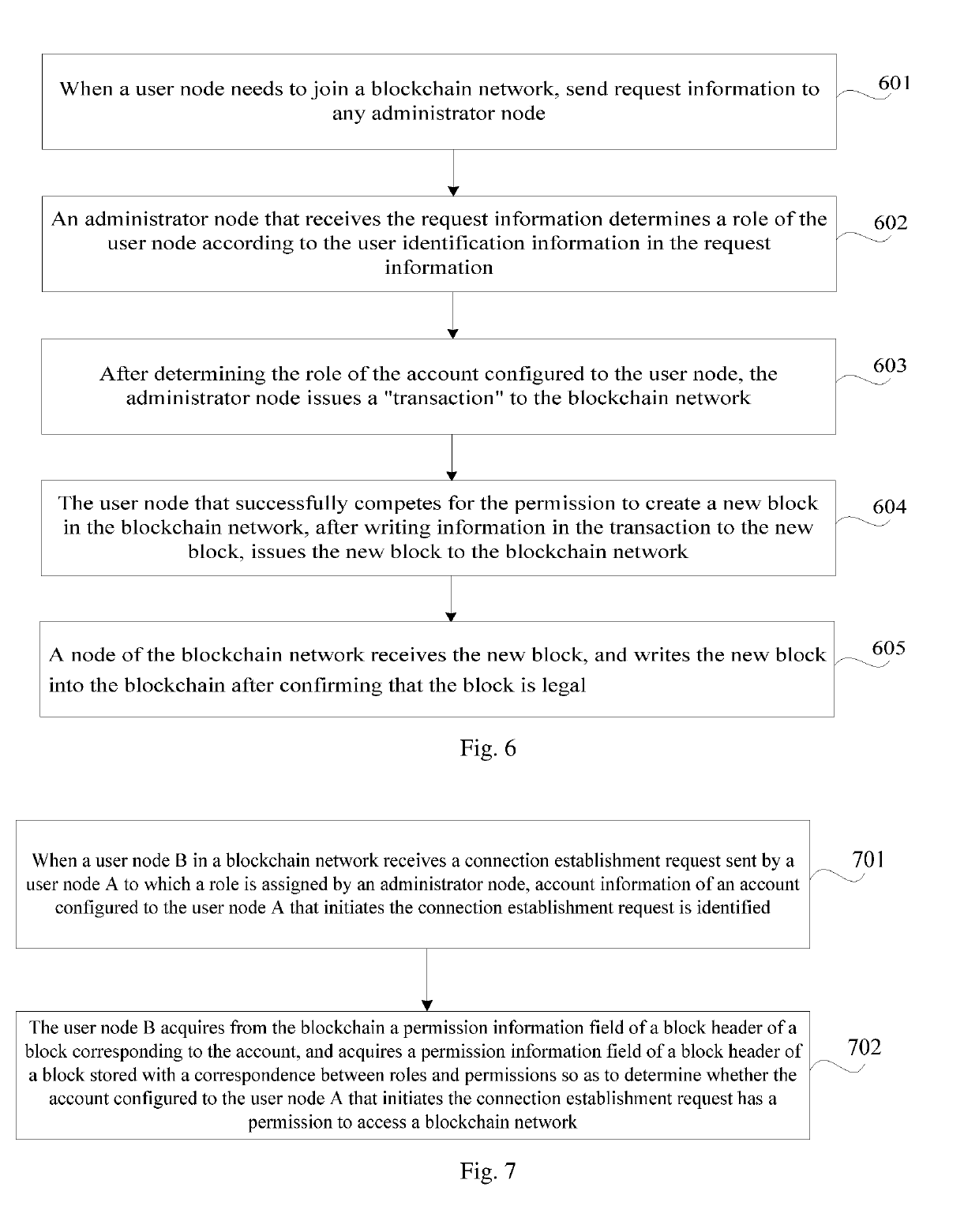
A permission control method, apparatus and system for a blockchain, and a node device. The method comprises: writing a preset correspondence between account roles and permissions into a block of a blockchain; determining a role of a target account configured to a user node to be added to the blockchain; and controlling, according to the correspondence and the role of the target account, a permission of the user node configured with the target account. In the method, by setting roles and permissions of blockchain accounts, user nodes configured with different accounts perform corresponding operations according to roles and permissions of the user nodes, so that only accounts having corresponding permissions can access a blockchain network, synchronize data on a blockchain and acquire data within a permission range; blockchain data is protected, and the security and privacy of the blockchain data are ensured.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Network and domain-creating method thereof
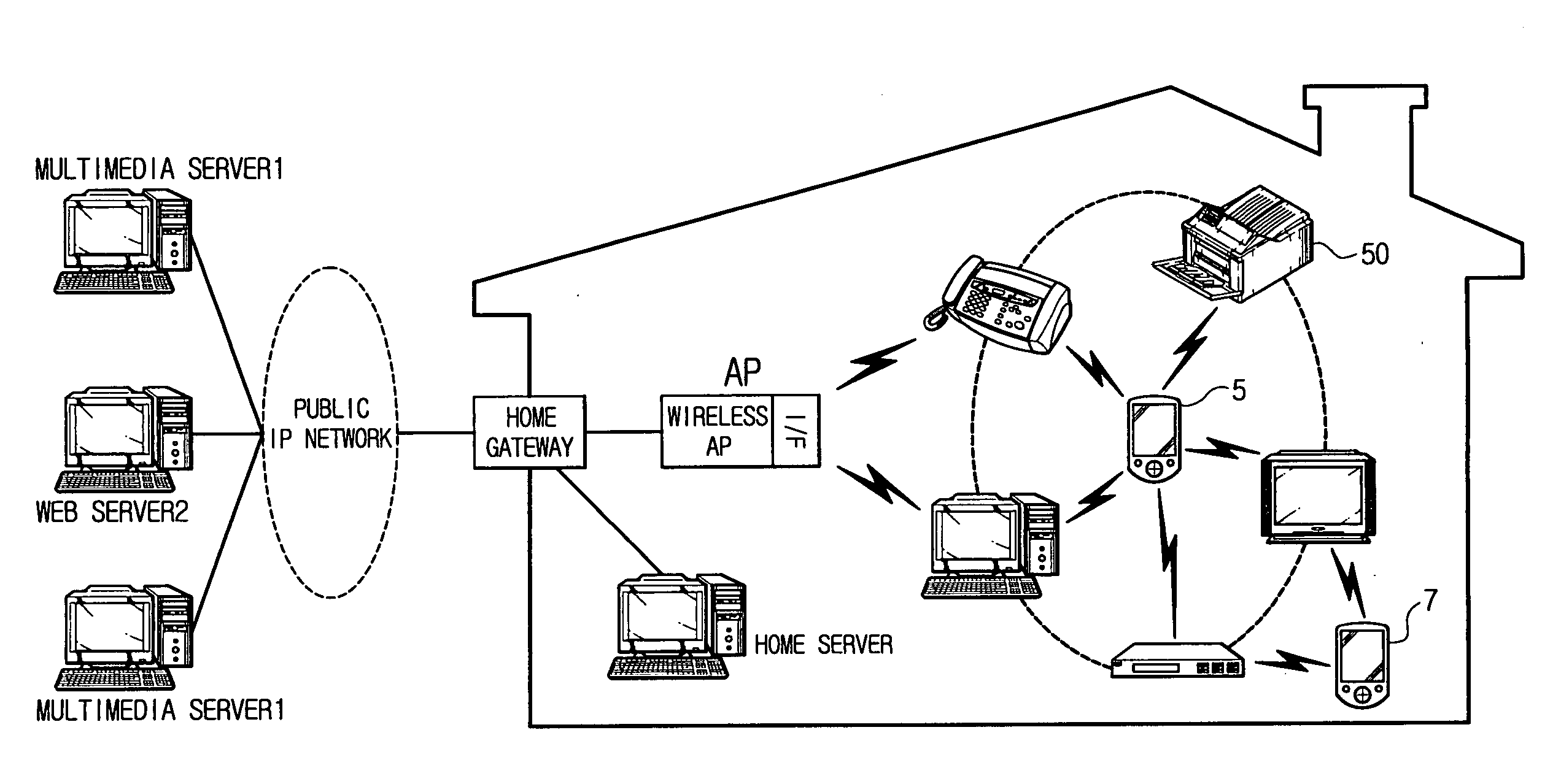
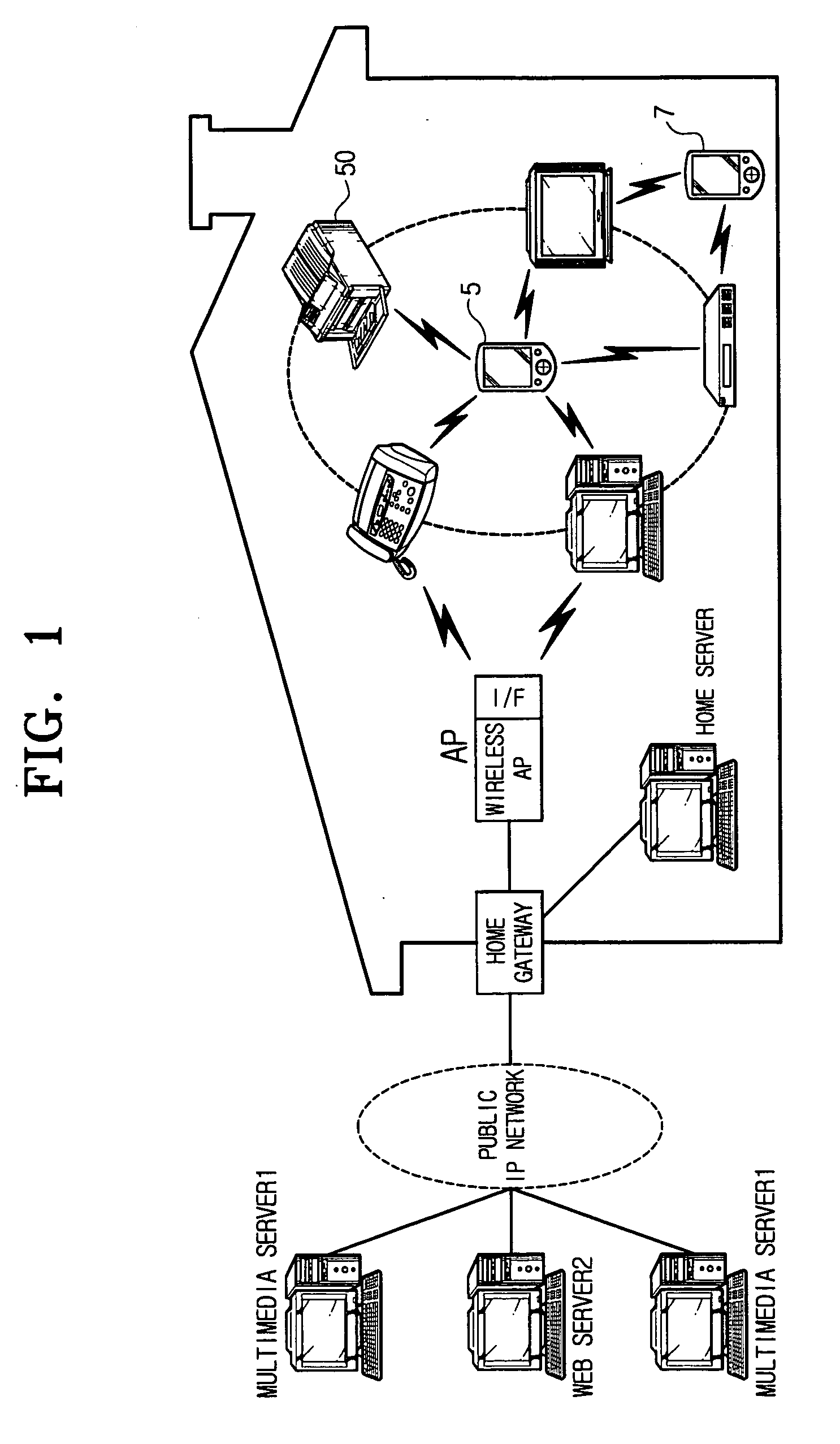
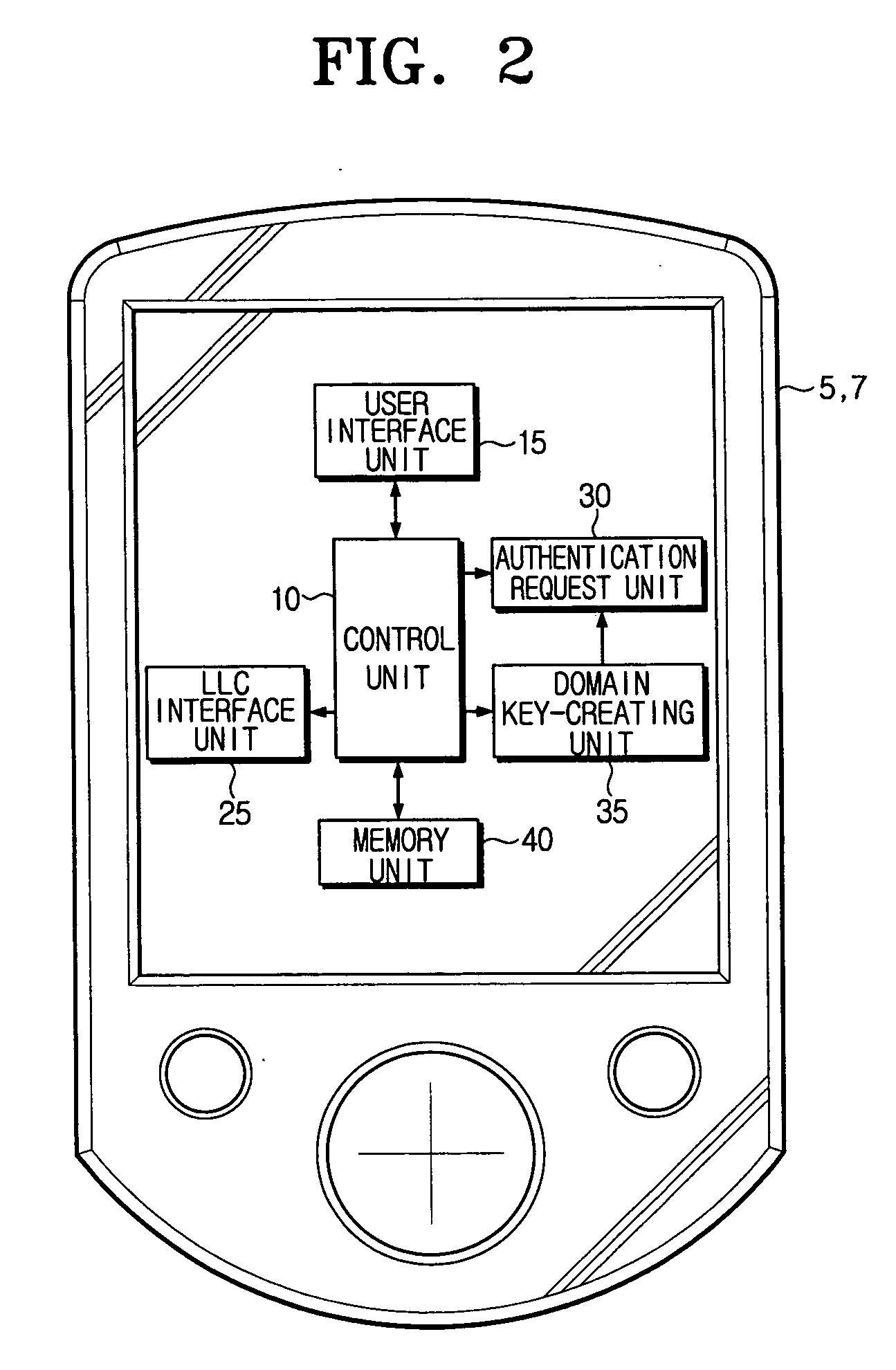
ActiveUS20070177737A1Efficient managementSecurity and Privacy GuaranteedSpectales/gogglesDigital data processing detailsA domainAuthorization
A network capable of communicating with foreign networks and having a plurality of devices capable of mutually communicating with one another and a domain setup method thereof. The network includes at least one main remote controller for, out of the devices, setting up authorization to use the respective devices belonging to at least one main domain having at least one of the devices; and at least one subsidiary remote controller for receiving authentication for authorization to use the respective device belonging to a domain having the respective devices authorized to at least one user by the respective main remote controllers. Thus, the present network enables each user to efficiently administer whether to use the home devices as well as enables the home devices authorized to each user to be set up in one domain in order to keep security and privacy from foreign domains.
Owner:SAMSUNG ELECTRONICS CO LTD
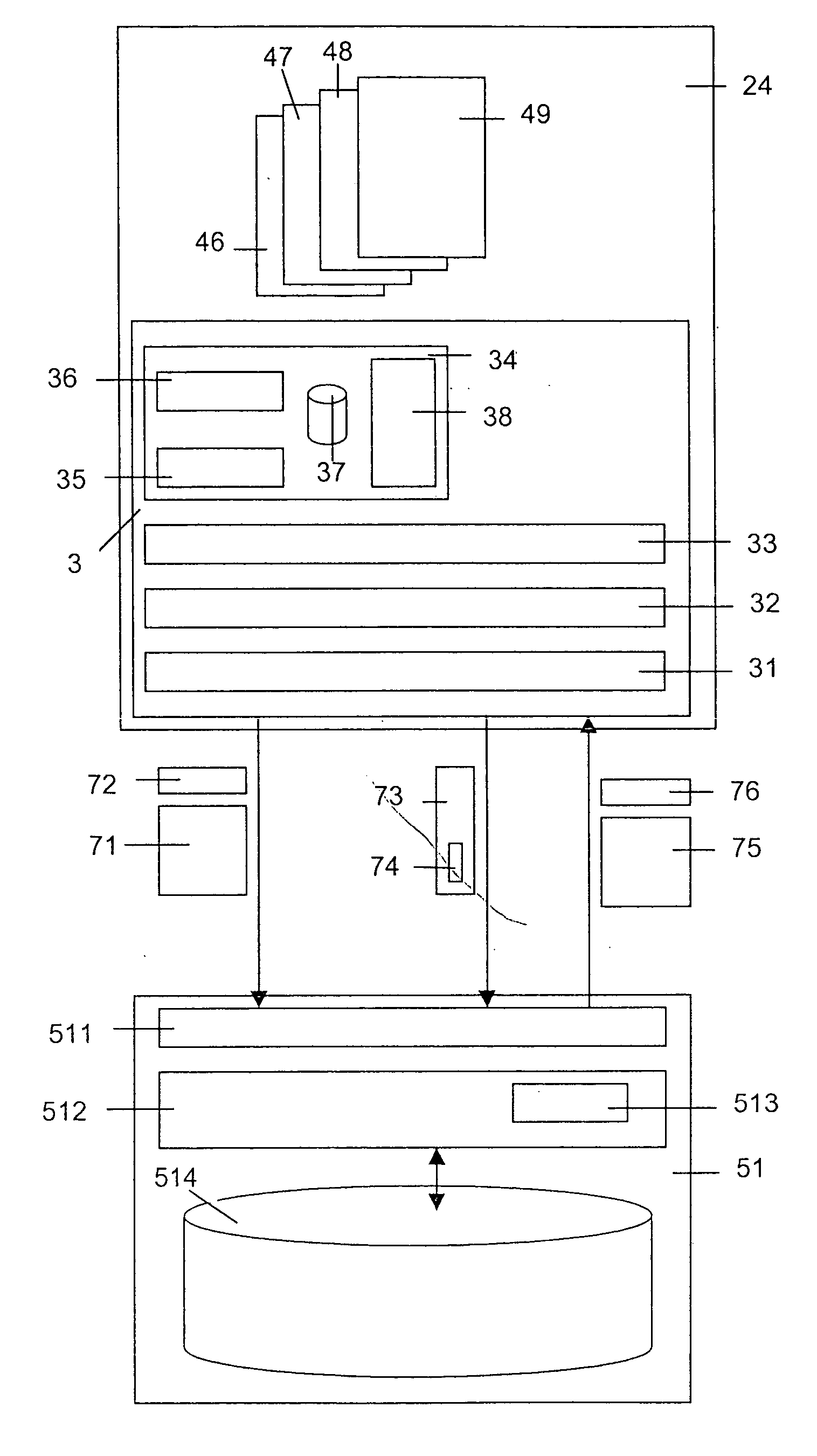
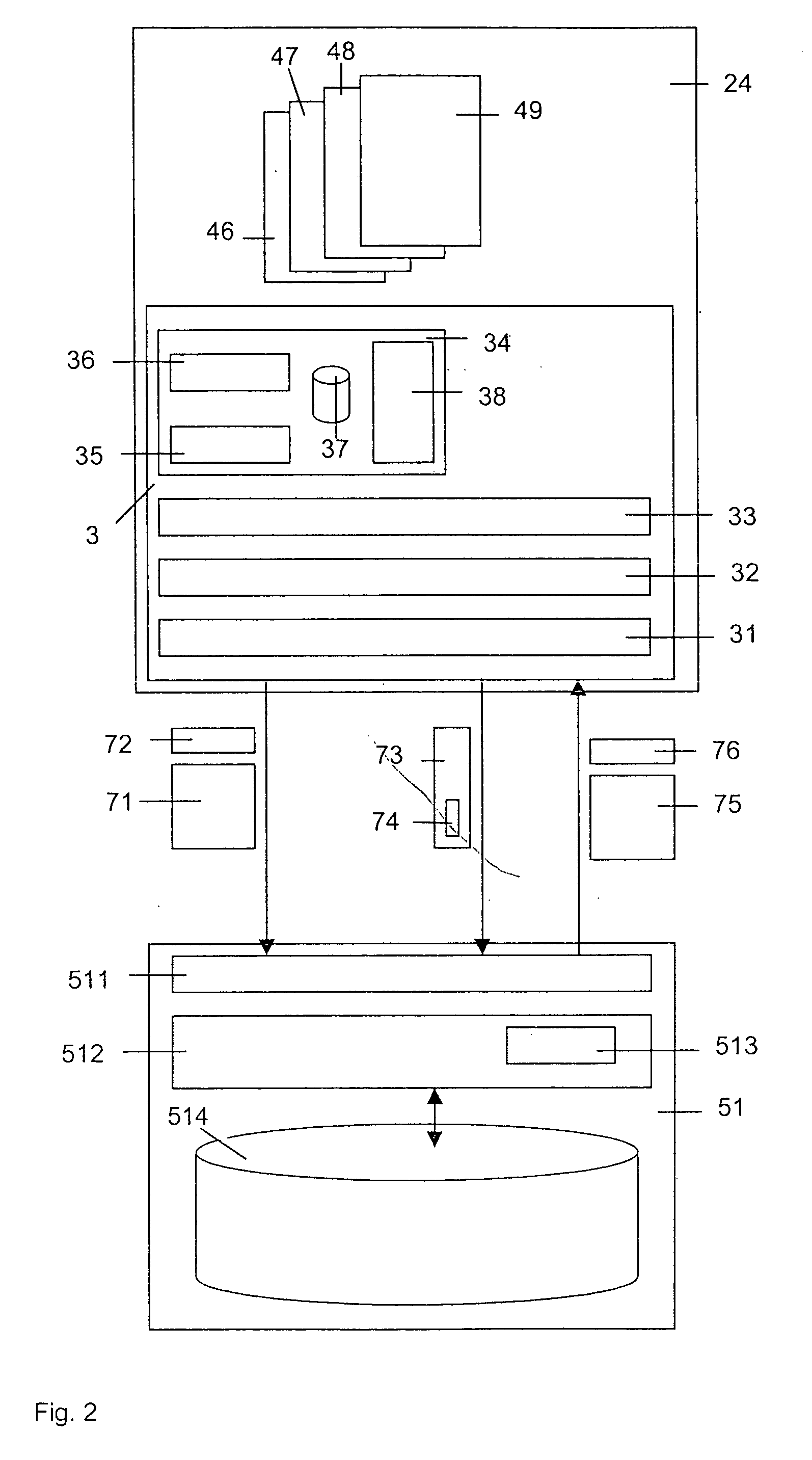
Storage service
InactiveUS20050138404A1High degree of securityReduce bandwidth requirementsDigital data processing detailsUnauthorized memory use protectionOperating system
The invention concerns a method of providing a client (21, 22, 23, 24) transparent access to storage space administrated by a storage service, as well as a client (21, 22, 23, 24) and a storage system for performing this method. Data are exchanged between the client (21, 22, 23, 24) and the storage system (5) providing the storage service via a communication network (1). A client (24) invokes the storage service for providing the storage space. The storage space associated with the client (24) is located within the storage system (5). A secure connection is established between the client (24) and a storage device (51) of the storage system (5) dedicated to store data assigned to said storage space. Data assigned to the storage space is stored in encrypted form in said storage device (51).
Owner:IDPA HLDG
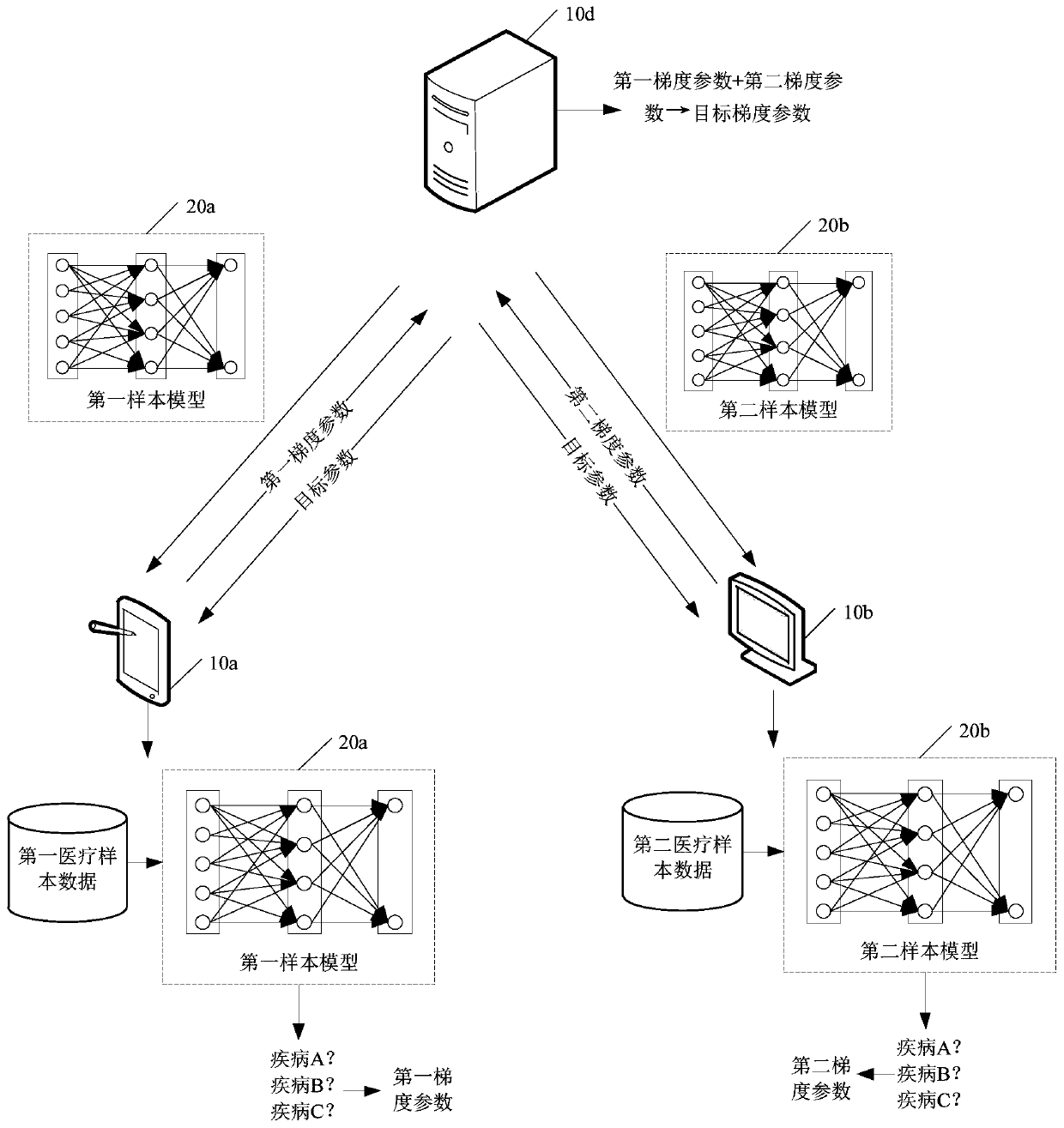
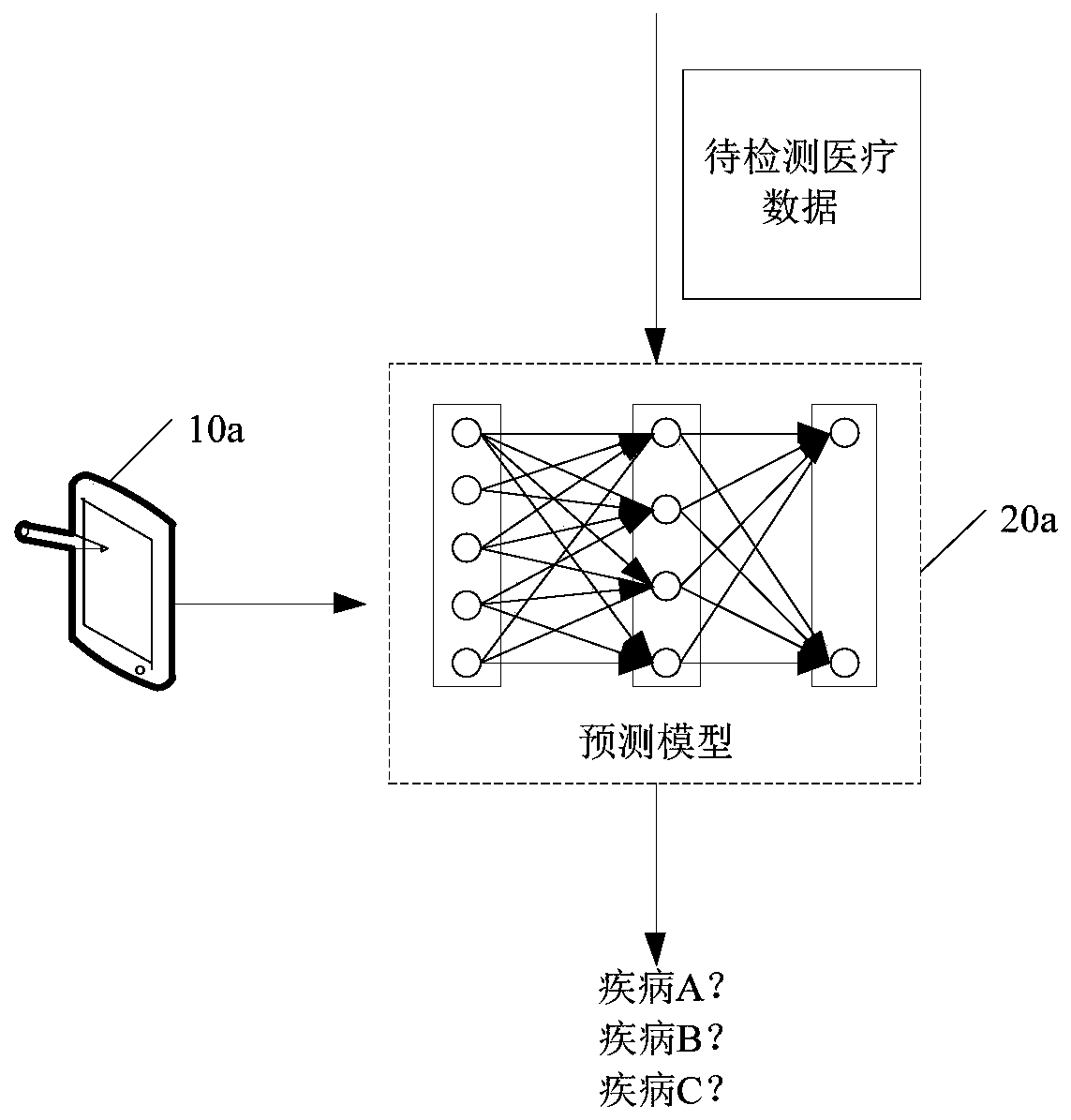
Model multi-terminal collaborative training method and medical risk prediction method and device
PendingCN110797124AGuaranteed privacy and securityIncrease the number ofMedical data miningResourcesPrediction methodsData processing
The embodiment of the invention discloses a model multi-terminal collaborative training method and a medical risk prediction method and device. The method comprises the steps: a first sample model issent to a first terminal and a second sample model is sent to a second terminal; an encrypted first to-be-updated parameter sent by the first terminal and an encrypted second to-be-updated parameter sent by the second terminal are received; the encrypted first to-be-updated parameter and the encrypted second to-be-updated parameter are fused into a target parameter according to a preset encrypteddata processing mode, and the target parameter is sent to the first terminal and the second terminal, wherein the target parameter is used for updating the first sample model and the second sample model; the updated first sample model and the updated second sample model are determined as prediction models, wherein the prediction model is used for predicting a medical risk prediction trend matchedwith the target medical data of the target user. By adopting the methods and the device disclosed in the invention, the prediction accuracy of the prediction model can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
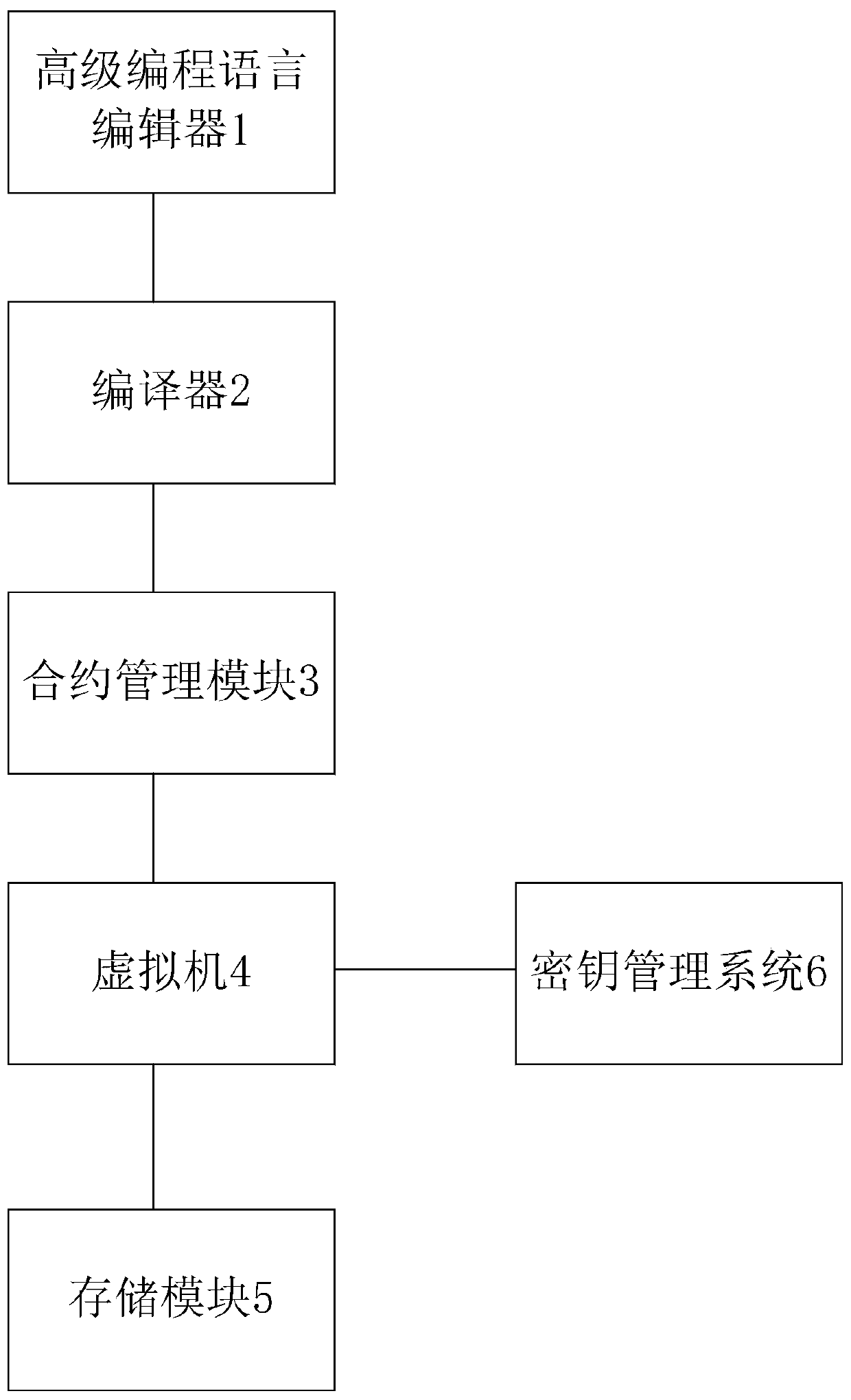
Method and a system for constructing a smart contract in a block chain
ActiveCN109766722APerformance bottleneckLow execution efficiencyDigital data protectionCode compilationData privacy protectionSmart contract
The invention relates to a method and a system for constructing an intelligent contract in a block chain. The method comprises the steps of 1, constructing an intelligent contract core system in the block chain; Step 2, contract upgrading based on the intelligent contract core system; Step 3, contract execution based on the intelligent contract core system; And step 4, performing data privacy protection based on the intelligent contract core system. The characteristics of data isolation, contract upgradable and data privacy protection are provided, and the requirements of enterprise organizations for service iterative upgrade, data governance and data security are better met.
Owner:梧桐链数字科技研究院(苏州)有限公司
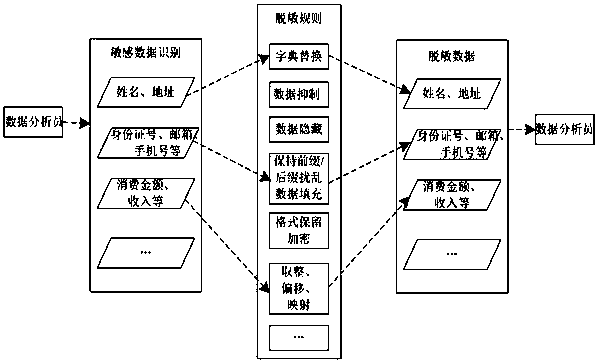
Data desensitization method based on authority
InactiveCN108418676AGuaranteed availabilityImprove access efficiencyEncryption apparatus with shift registers/memoriesInternet privacyOriginal data
The invention relates to a data desensitization method based on an authority. The method comprises the following steps of 1, performing sensitive data recognition on original data, and building desensitization rules for the sensitive data; 2, defining a corresponding strategy between authorities and the desensitization rules: according to the access authority of a user, controlling access authorities of sensitive information, privacy information and secret information, and according to requirements of the different authorities on the sensitive data, making desensitization strategies corresponding to the authorities; 3, positioning desensitization data: positioning and recognizing desensitization data according to features of the sensitive data during a process of accessing the informationin the original data; and 4, dynamically generating the sensitive data: when the original data is output for displaying, desensitizing and outputting the data according to the desensitization strategycorresponding to the access authority of the user.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
User privacy protection method in personalized information retrieval
ActiveCN103279499AGuaranteed privacy and securityDoes not affect calculation resultsDigital data protectionSpecial data processing applicationsStatistical databasePersonalized search
The invention discloses a user privacy protection method in personalized information retrieval. The user privacy protection method in personalized information retrieval is a user interest model anonymization method based on difference privacy and aims to remove contradiction between user privacy protection and improvement of personalized information retrieval performance. The user privacy protection method in personalized information retrieval aims to conduct anonymization after identifiers of a user interest model are concealed, and namely after the identifiers (including the ID, the name, the ID number, the SSN and the like of a user) are eliminated, related technologies of the difference privacy are mainly used for anonymizing standard identifiers of the user interest model. Namely, generalization is conducted on the standard identifiers of the user, Laplace noise is added so as to enable difference privacy protection requirements to be met, the inquiry precision of a statistical database is maximized, and the probability of identification of an entity and attributes is minimized. The user privacy protection method in personalized information retrieval can be widely applied to service systems, such as a personalized retrieval service system and a personalized recommendation service system. The invention belongs to the technical field of information and computers.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Method and device for multi-party joint training of graph neural network
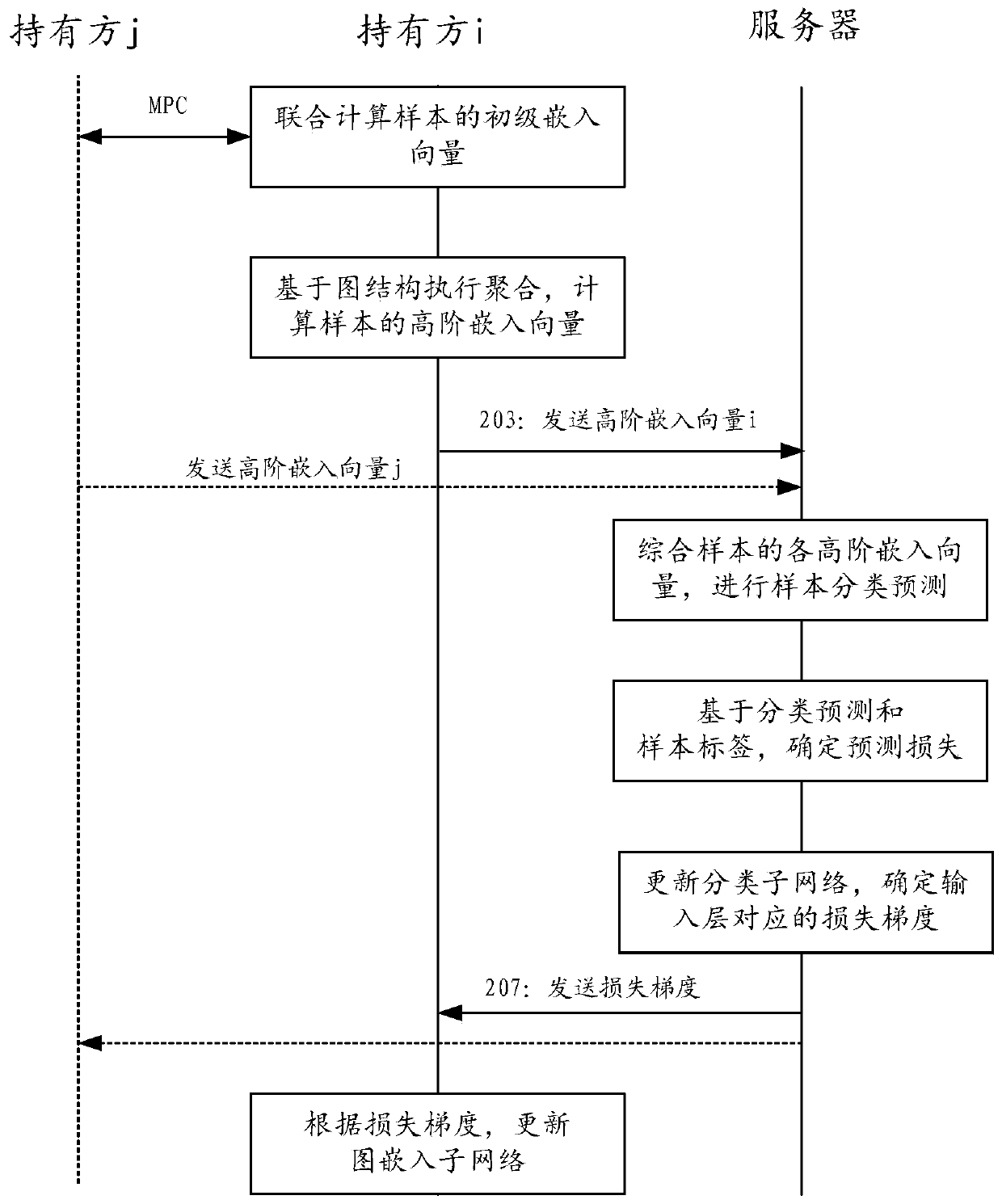
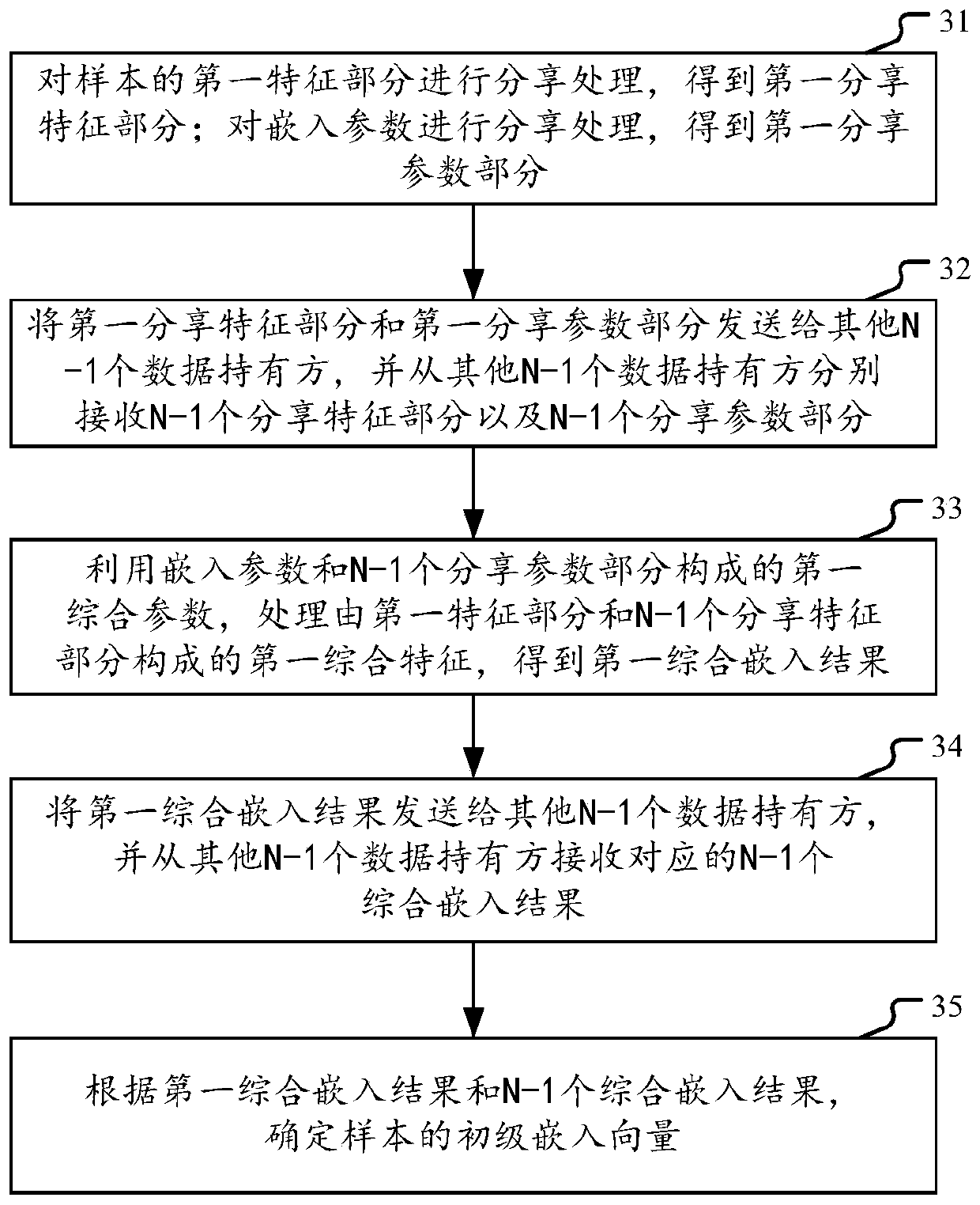
PendingCN110782044AJoint training implementationImprove computing efficiencyEnsemble learningCharacter and pattern recognitionMachine learningEngineering
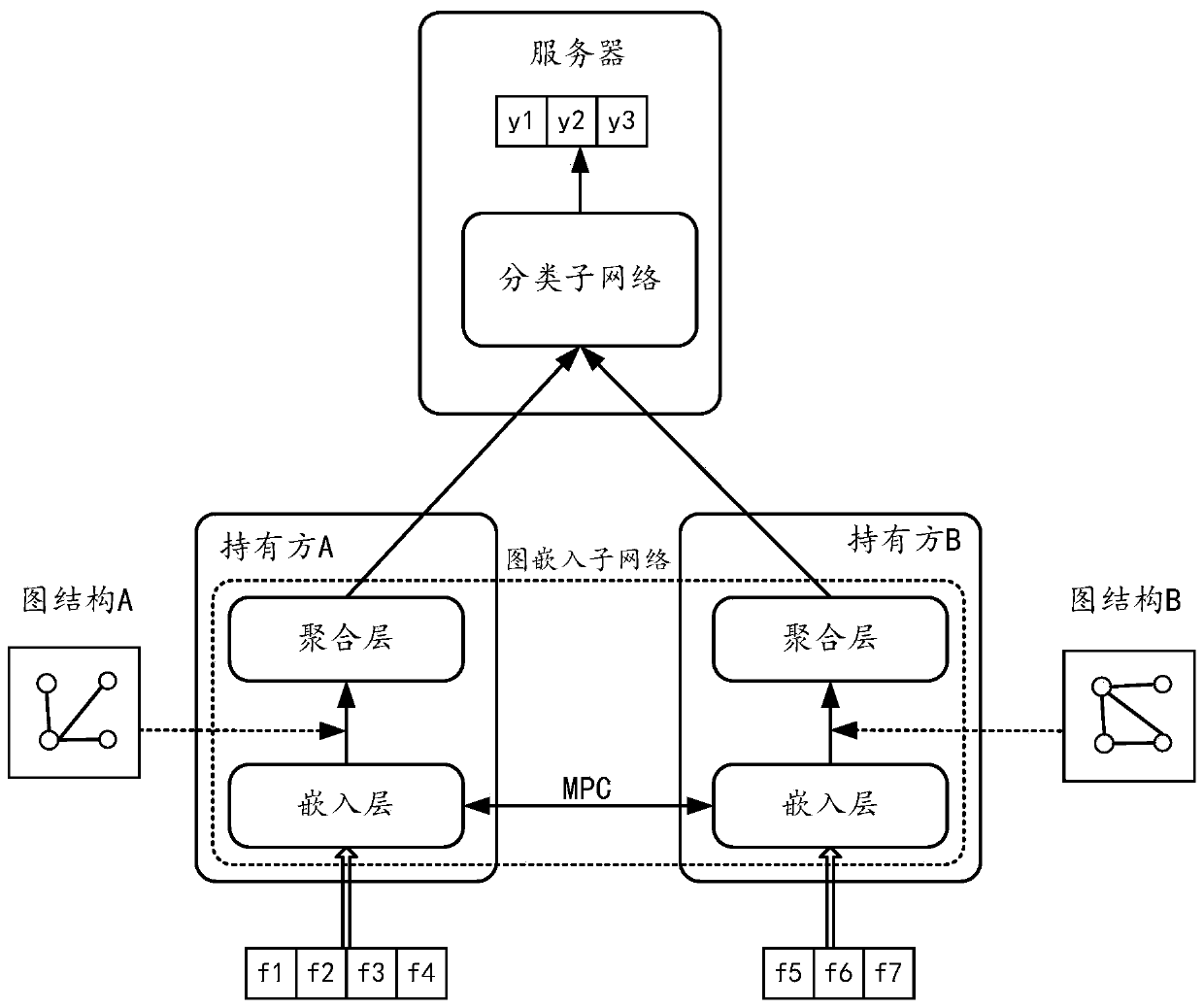
The embodiment of the invention provides a method and device for multi-party joint training of a graph neural network. The multiple parties comprise a plurality of data owners and a server; the graphneural network comprises a graph embedding sub-network and a classification sub-network. And each data owner maintains a part of the graph embedding sub-network, and the server maintains the classification sub-network. Any data owner calculates a primary embedding vector of a sample in a graph embedding sub-network maintained by the data holder through multi-party security calculation MPC, and performs multi-level neighbor aggregation on nodes according to a local graph structure to obtain a high-order embedding vector of the nodes, and sends the high-order embedding vector to a server. And the server synthesizes the high-order embedded vectors from the data owners by using the classification sub-network, and performs classification prediction according to the high-order embedded vectors to determine the loss. And the loss gradient is transmitted back to the graph embedding sub-network in the data holder from the classification sub-network in the server, so that the joint training of the whole graph neural network is realized. According to the embodiment of the invention, the data privacy of each party is protected.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Mobile equipment voiceprint registration and authentication method and system
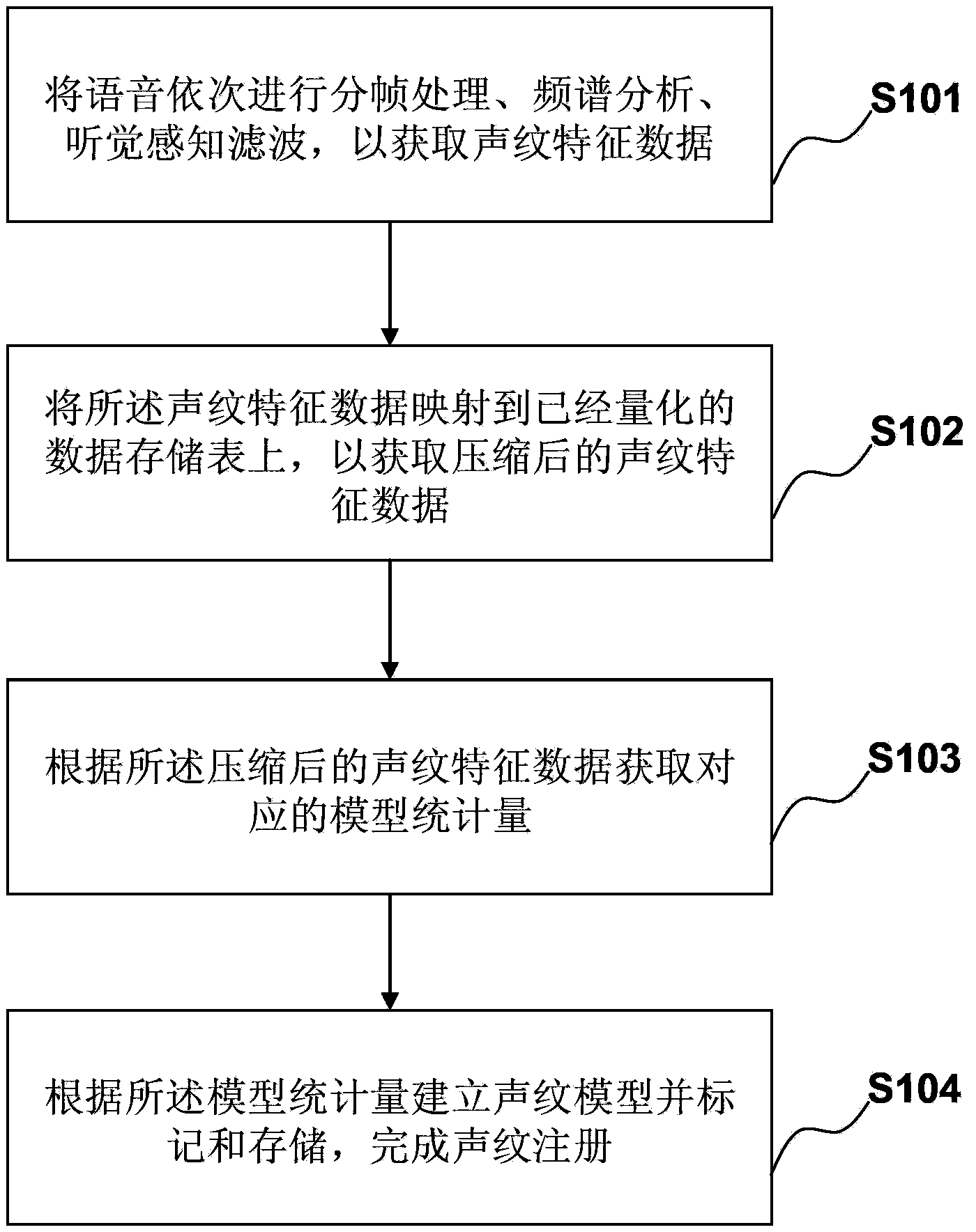
ActiveCN103685185ASave storage spaceSmall amount of calculationSpeech analysisTransmissionUser privacyMobile device
The invention discloses a mobile equipment voiceprint registration and authentication method and system. The voiceprint registration method comprises the following steps: processing voices to framing treatment, spectral analysis and auditory perception filtering to obtain voiceprint characteristic data; mapping the voiceprint characteristic data to a quantified data storage list to obtain compressed voiceprint characteristic data; acquiring a corresponding a model statistic quantity according to the compressed voiceprint characteristic data; establishing a voiceprint model according to the voiceprint statistic quantity, and marking and storing to complete voiceprint registration. In the voiceprint registration stage, the voiceprint model is registered according to the model statistic quantity. In the authentication stage, the model statistic quantity is compared with a stored voiceprint model. The method provided by the invention can reduce the calculation amount of the voiceprint model, reduce the storage space of voiceprint characteristics, and resolve the requirement of the mobile equipment for real-time performance of an algorithm, and can improve the use experience and ensure user privacy security without networking for registration and authentication or uploading the user's voiceprint data to a server.
Owner:SHANGHAI GUOKE ELECTRONICS
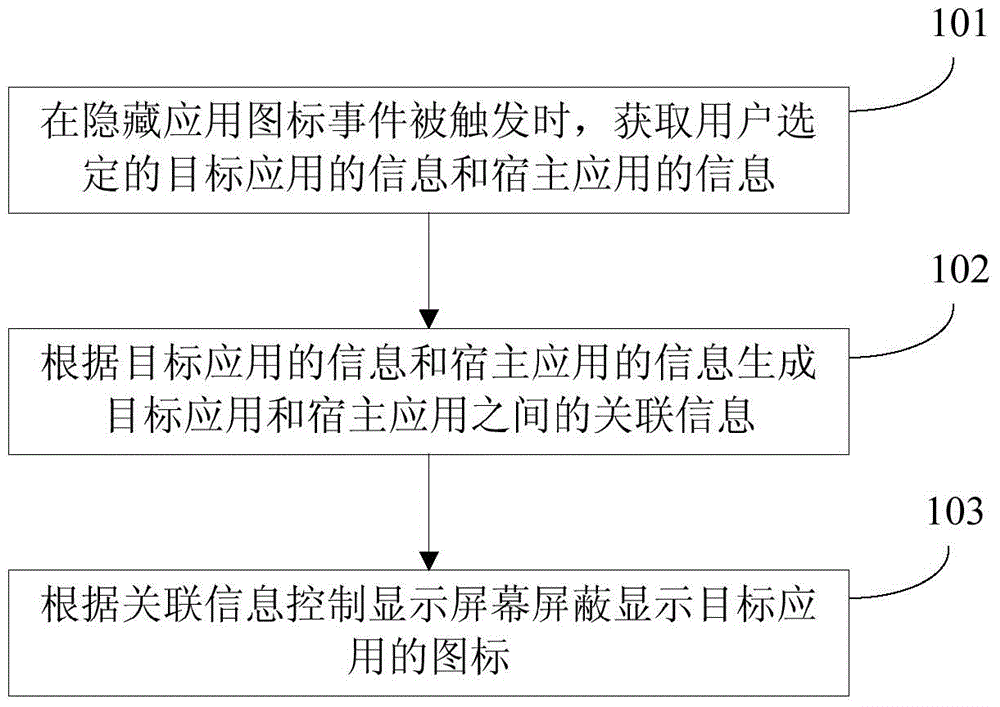
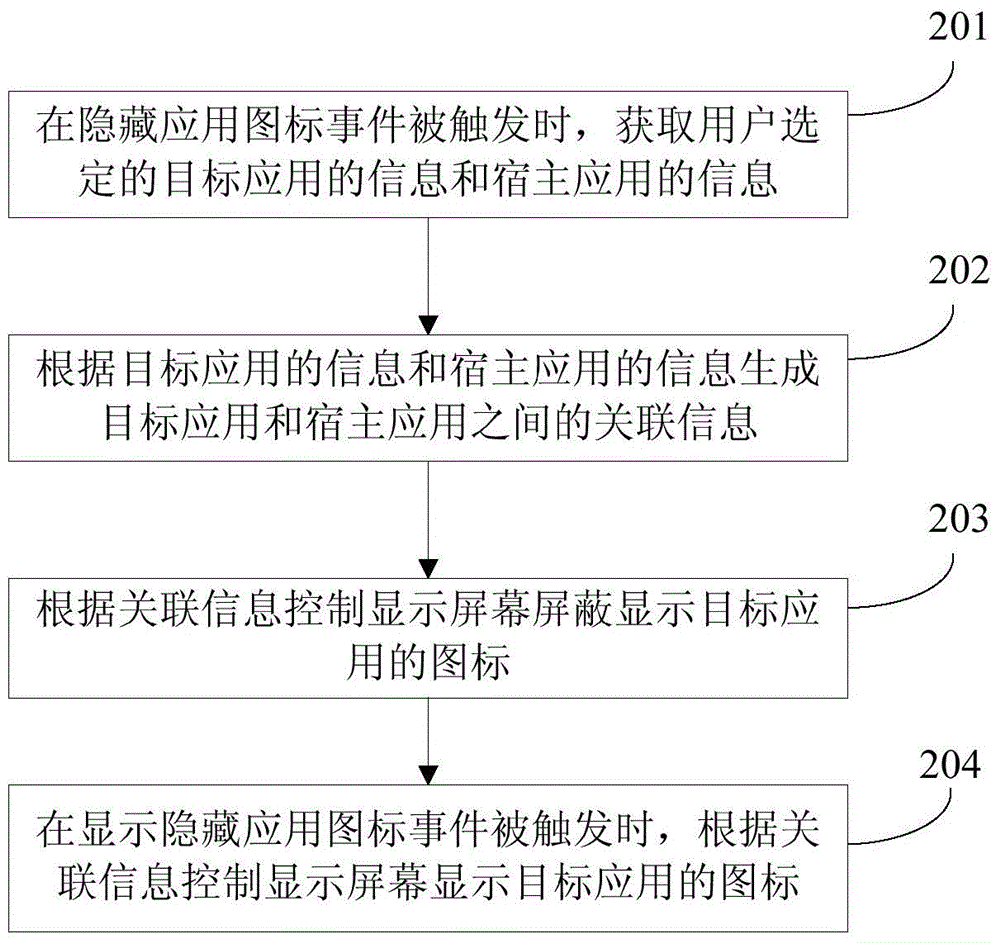
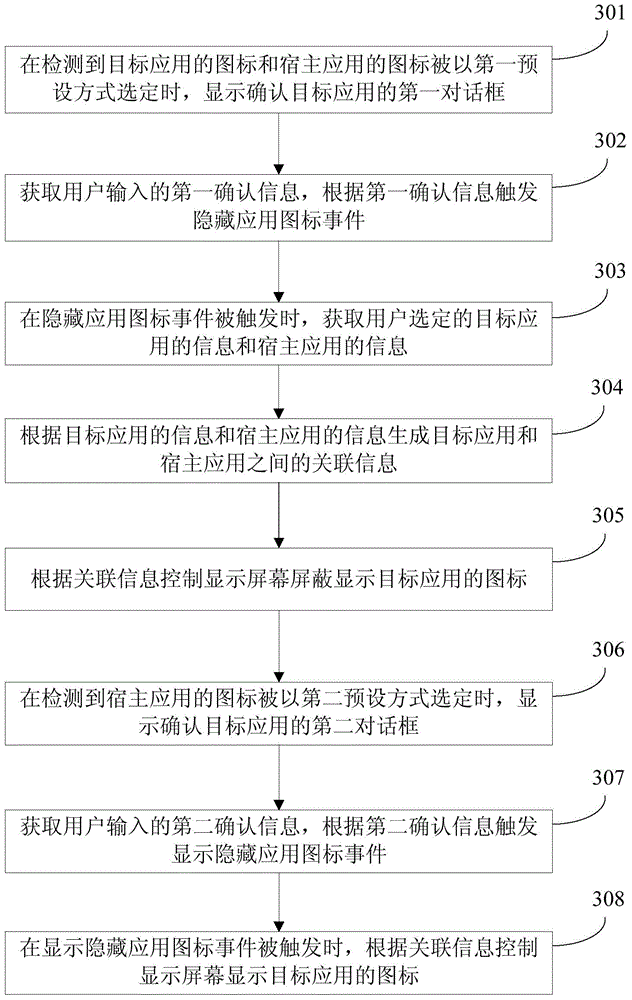
Method and device for hiding application icons
ActiveCN104573552AHide thoroughlySolve the imperfect functionDigital data protectionInput/output processes for data processingMobile deviceInformation control
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Electronic accounting method and device and terminal equipment
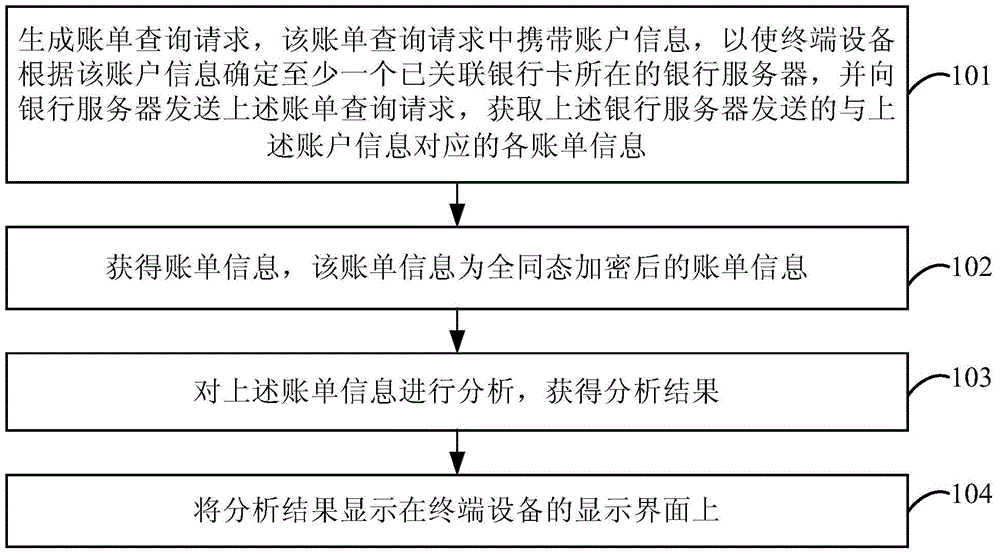
InactiveCN104700277AImprove protectionGuaranteed privacy and securityCash registersCommerceTerminal equipmentComputer terminal
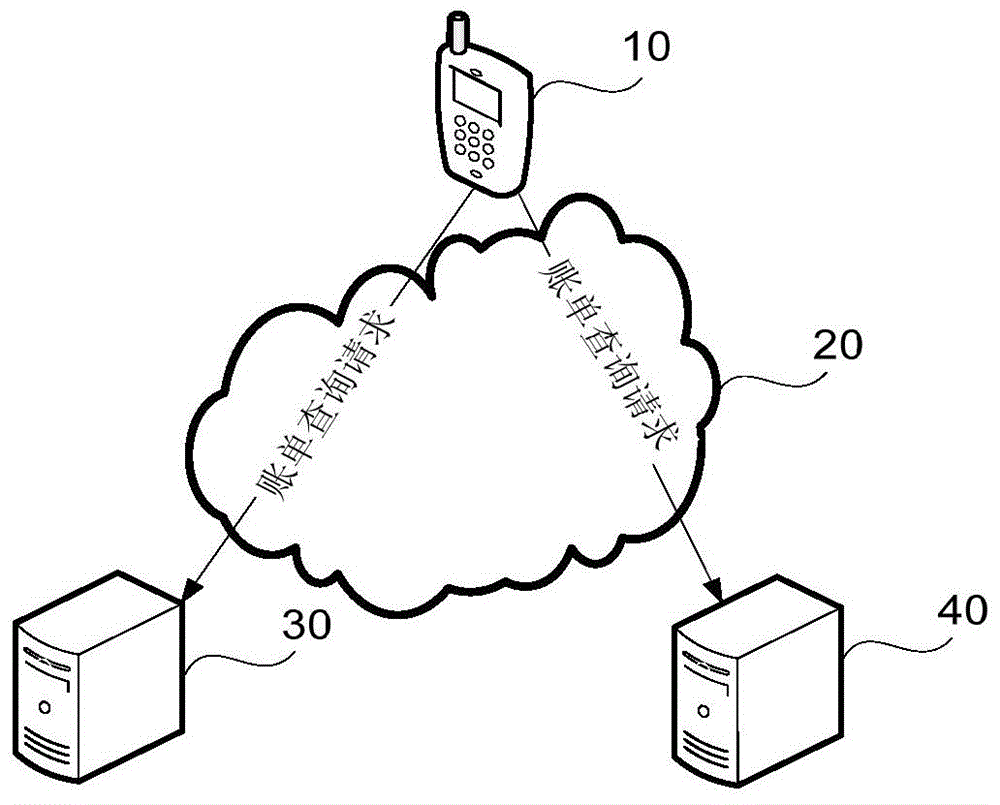
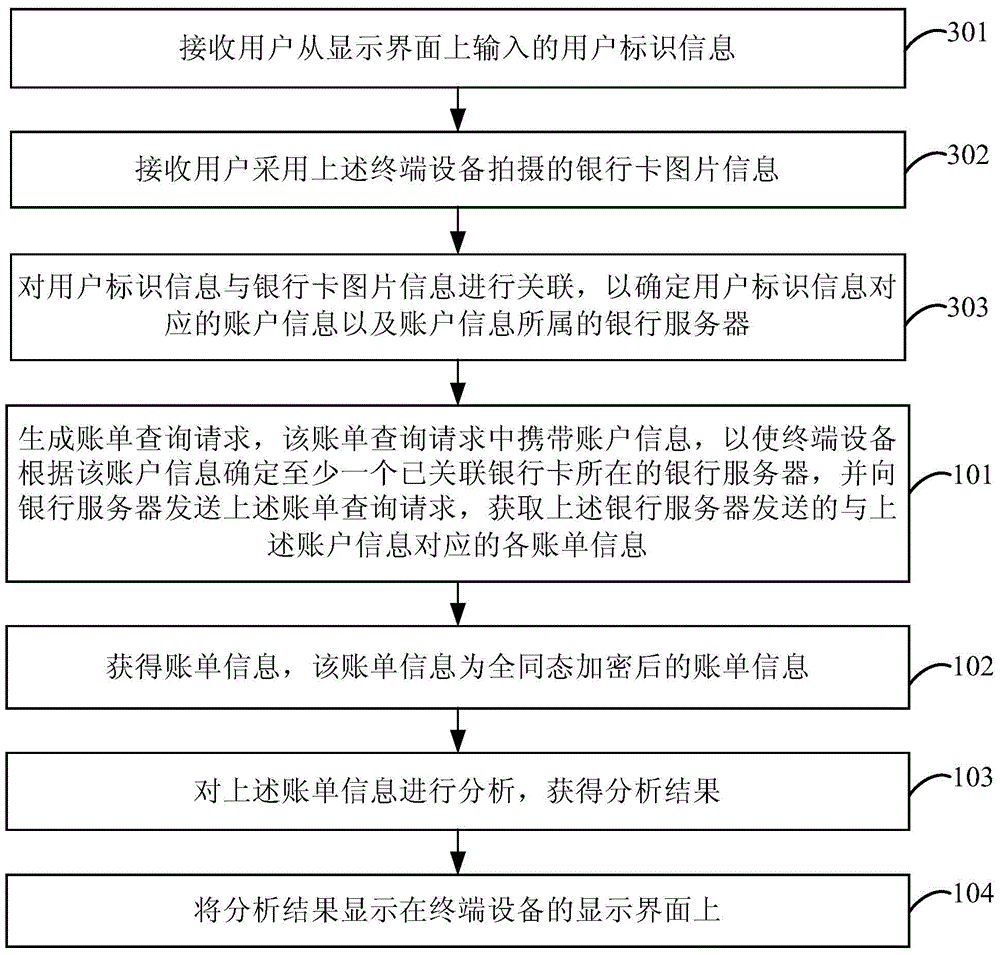
An embodiment of the invention provides an electronic accounting method and device and terminal equipment. The electronic accounting method includes generating a bill query request containing account information, accordingly allowing the terminal equipment, based on the account information, to determine a bank server of at least one bank card associated and send the bill query request to the bank server so as to obtain variable bill information, corresponding to the account information, sent from the bank server; acquiring the bill information which is subjected to fully homomorphic encryption; analyzing the bill information to obtain an analysis result; displaying the analysis result on a display interface of the terminal equipment. According to the embodiment, interaction of the terminal equipment supporting the electronic accounting function and the bank server is achieved, and bill records of the user are automatically collected and analyzed to increase accounting efficiency, accordingly allowing the user to learn individual financial state conveniently; the bill information subjected to fully homomorphic encryption is adopted to improve safety guarantee of the user information.
Owner:HUAWEI TECH CO LTD
Privacy protection method based on location service in scene of Internet of Things (IOT)
ActiveCN103037306AGuaranteed privacy and securityReduce security risksPayment architectureTransmissionProtocol for Carrying Authentication for Network AccessInternet of Things
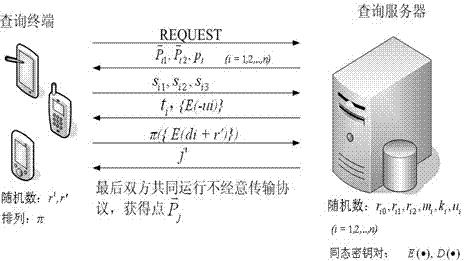
Provided is a privacy protection method based on location service in a scene of the Internet of Things (IOT). The privacy protection method based on the location service in the scene of the IOT comprises two privacy protection schemes according to the characteristics on the basis of the location service and the privacy protection level, namely an absolute privacy query scheme for a quite high security level and a query privacy scheme for a quite low security level. Through analysis of application scenes, the secure multi-party computation technology is integrated into IOT location privacy protection, by utilization of technologies such as adding random numbers, using dot product properties, and carrying out homomorphic encryption and oblivious transfer protocols, a dot which is nearest to a query input location in a database to be queried is calculated and found out, different levels of protection measures are taken according to the different application scenes, and therefore the effect that the privacy of query input, query results and contents of the database to be queried is protected is achieved in the absolute privacy protection scheme, and the privacy of the query input and the query results is protected in the query privacy protection scheme.
Owner:NANJING UNIV OF POSTS & TELECOMM
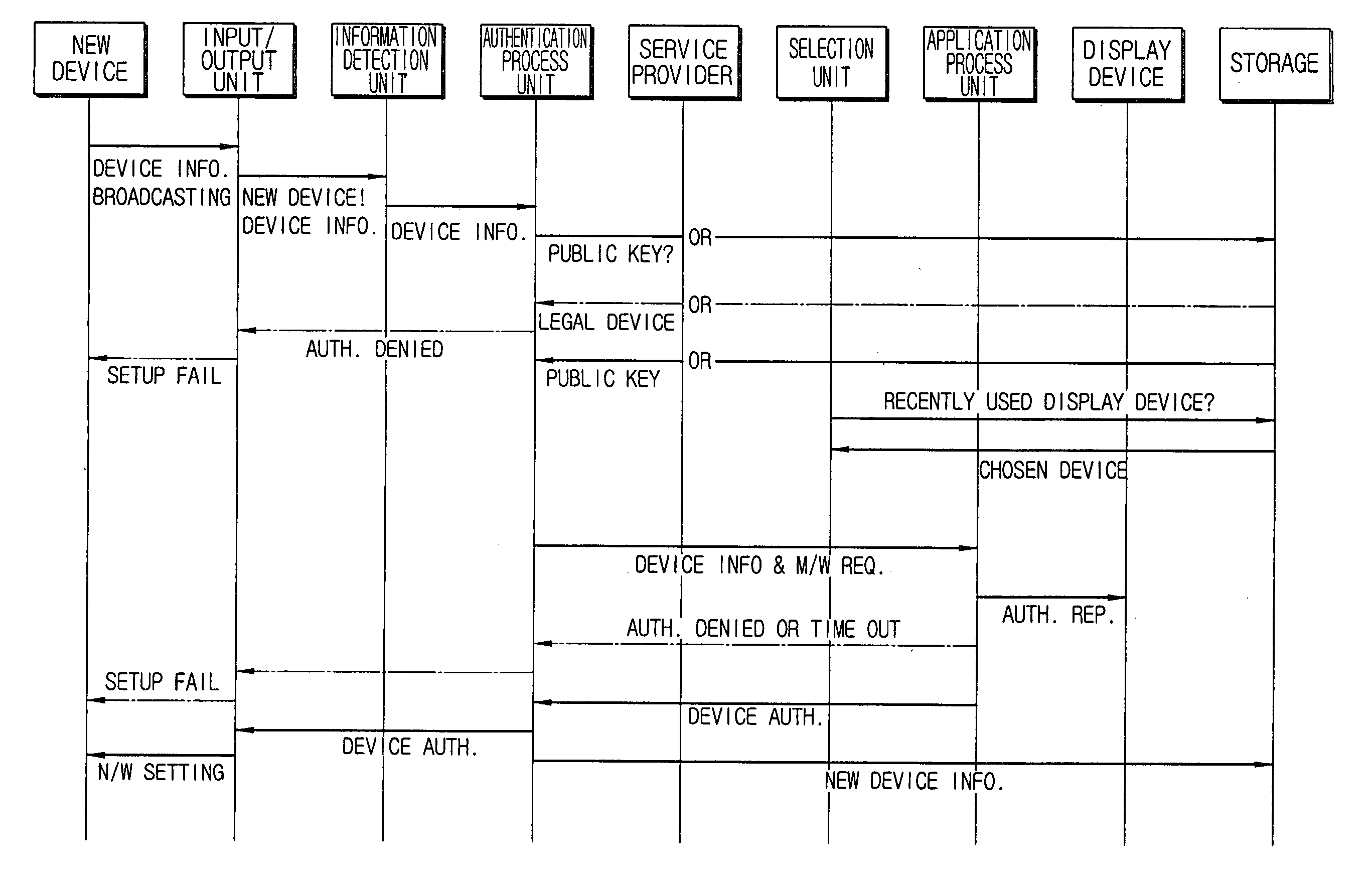
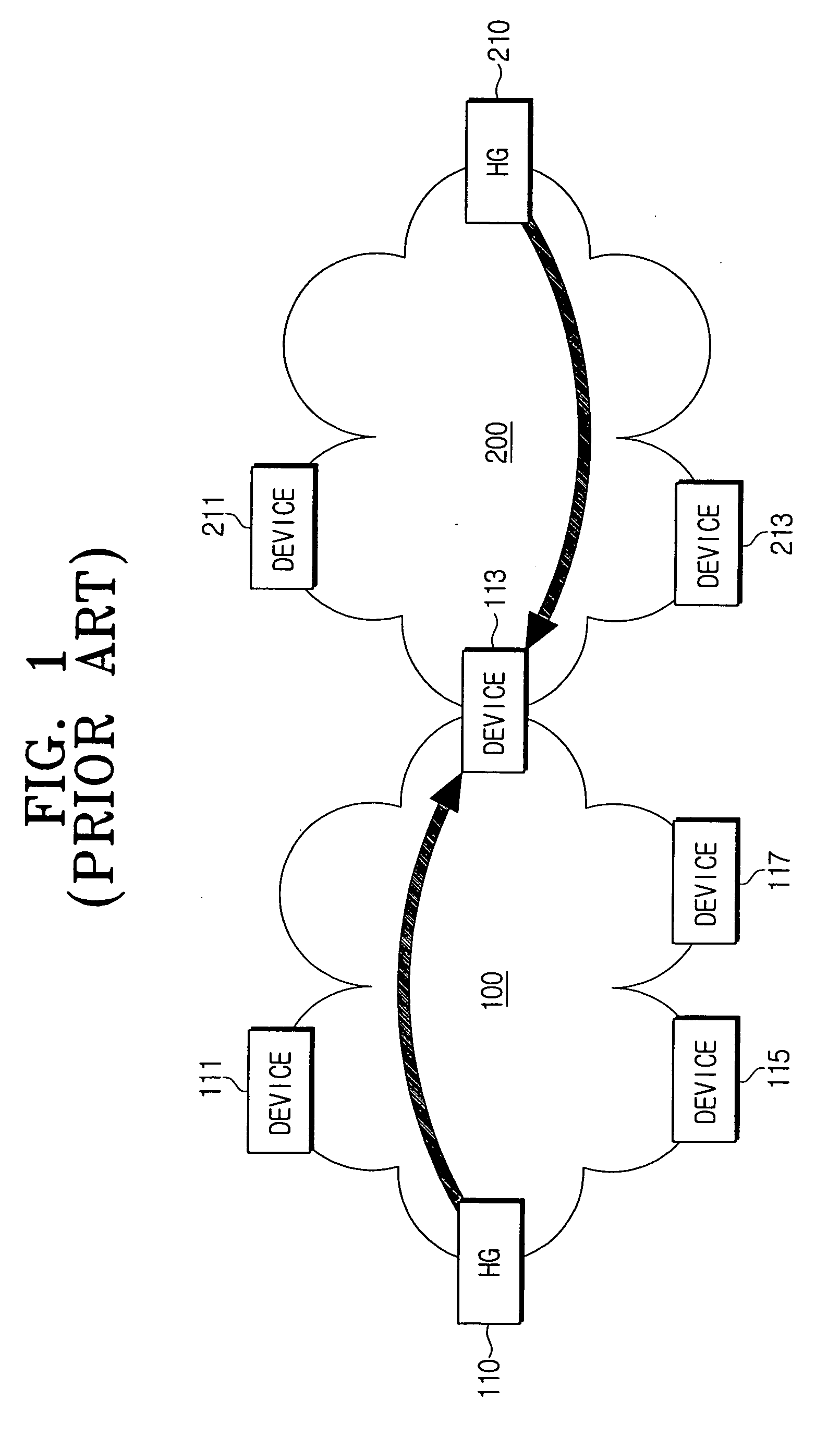
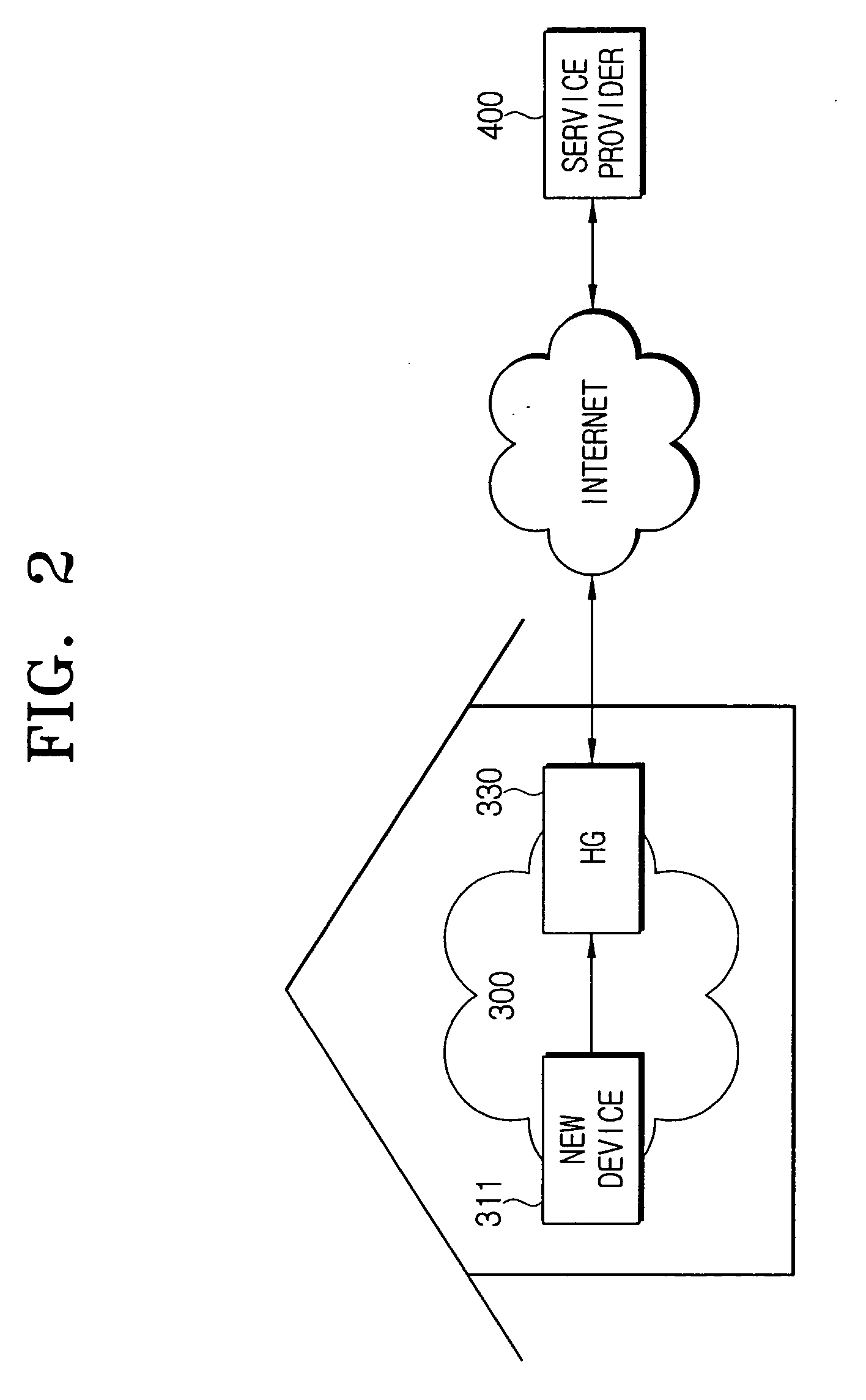
Home device authentication system and method
ActiveUS20040205335A1Security networkGuaranteed privacy and securityKey distribution for secure communicationBroadband local area networksAuthentication systemService provider
A home device authentication system and method, wherein the home device authentication system includes one or more home devices each having device information including coding information for authentication and information on a service provider providing authentication services; and a home gateway including decoding information corresponding to the coding information of the home devices, and for authenticating the home devices by using the decoding information. Further, if there exists no decoding information in the home gateway, the home gateway requests the decoding information from the service provider. Accordingly, privacy and security for the home network is secured.
Owner:SAMSUNG ELECTRONICS CO LTD
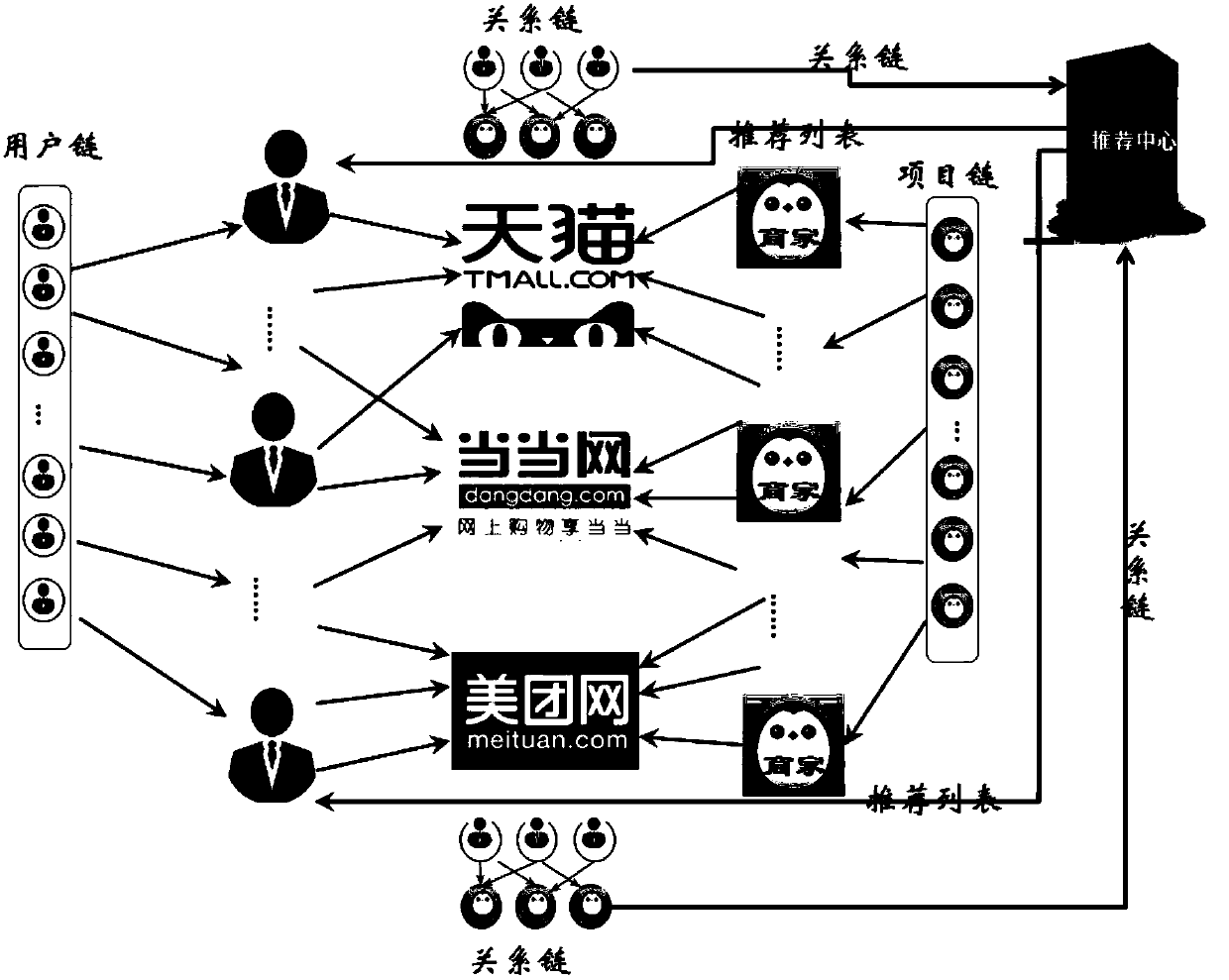
Anonymous Cross-domain Recommendation Based on Block Chain Technology
ActiveCN109523341AGuaranteed privacy and securityReduce storage pressureBuying/selling/leasing transactionsDatabase indexingTransaction dataData aggregator
The invention discloses an anonymous cross-domain recommendation method based on block chain technology, A technology base on block chain adopts heterogeneous multi-link data structure to carry out data storage, Users, merchandise and transaction relationship data are stored on users, merchants and platforms respectively. Transaction relationship does not store specific user and commodity information. Recommendation center can only obtain the relationship chain stored by each platform to ensure that an attacker cannot associate a user with a commodity. Aiming at the cold start problem caused by data sparseness, the invention performs data aggregation and similarity calculation based on accurate transaction data, and adopts a mixed recommendation strategy based on users and commodities to perform cross-platform recommendation, so as to achieve a safe and accurate win-win recommendation effect.
Owner:GUANGXI NORMAL UNIV
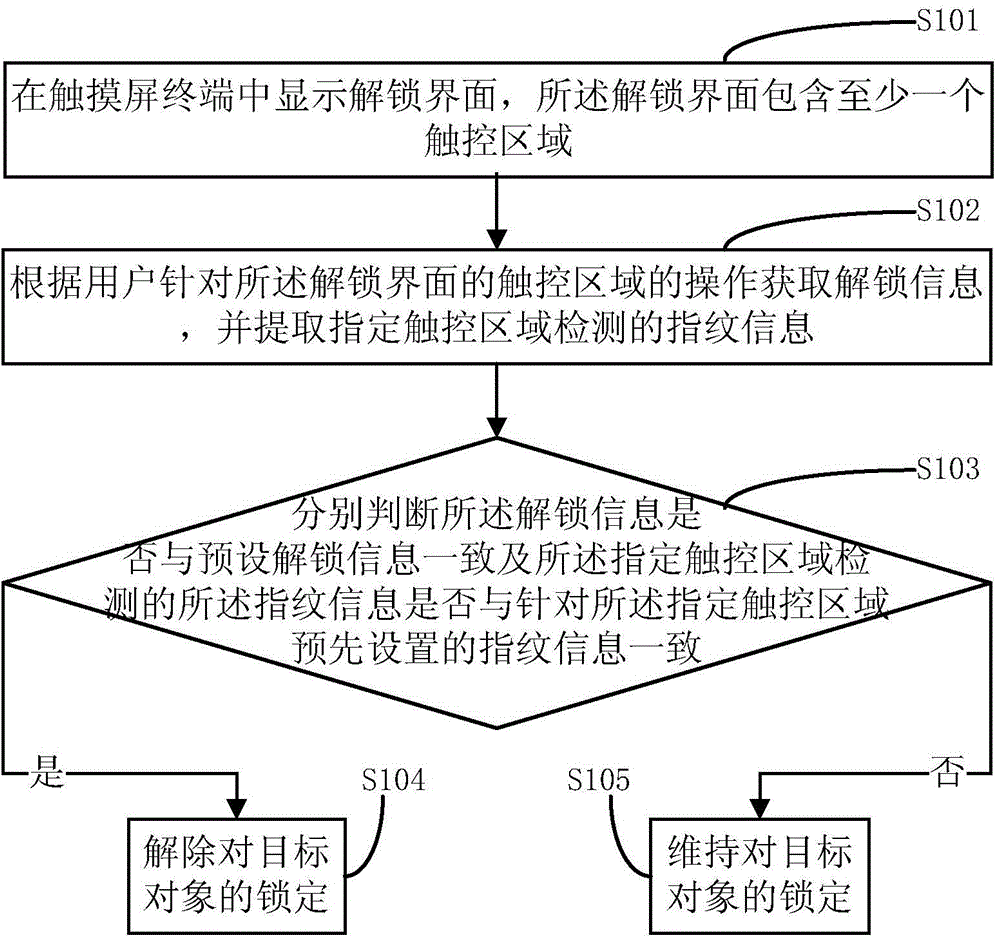
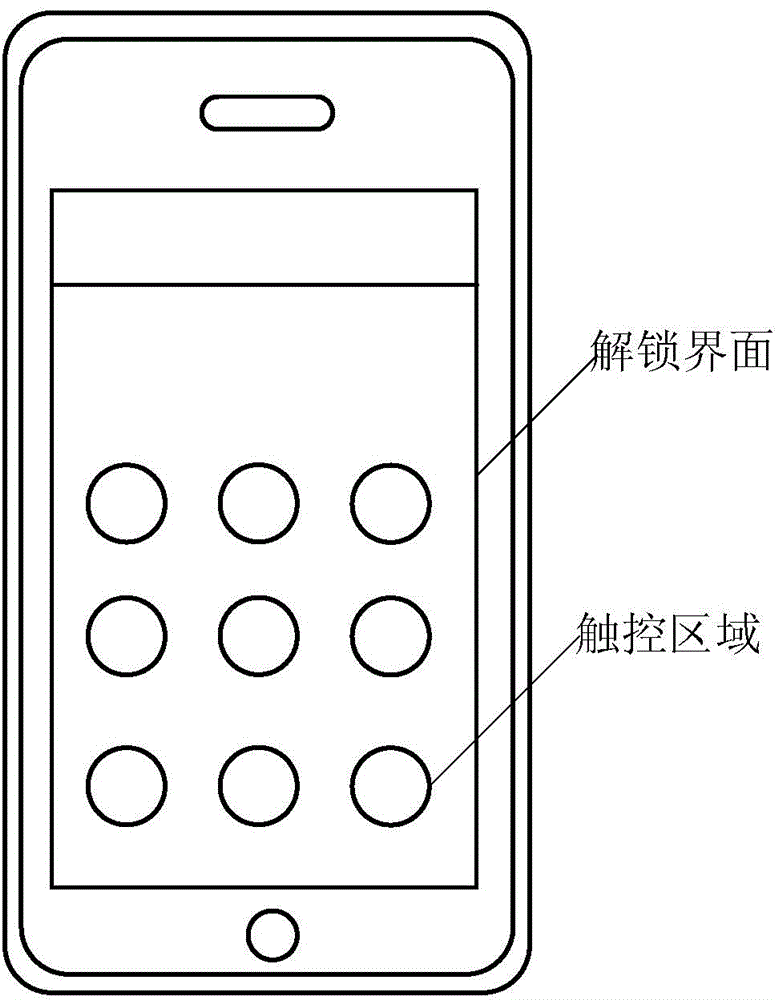
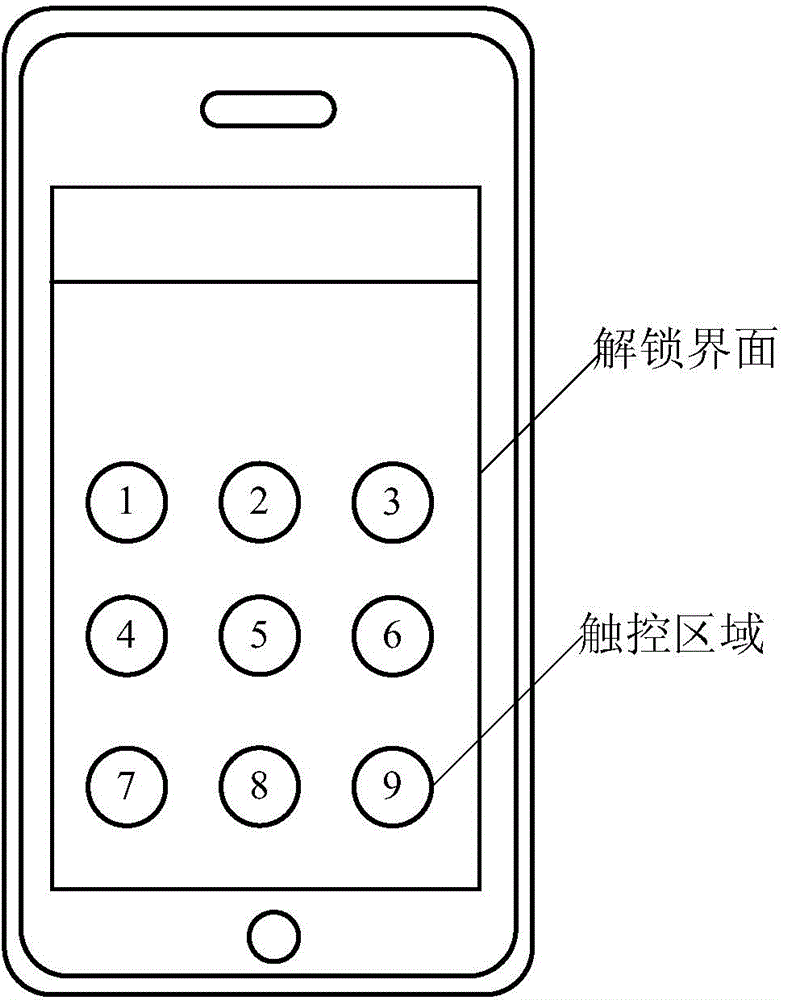
Touch screen terminal based unlocking method and apparatus and touch screen terminal
ActiveCN105574388AGuaranteed privacy and securityImprove security levelInternal/peripheral component protectionDigital data authenticationUser privacyTouchscreen
The invention discloses a touch screen terminal based unlocking method. The method comprises the steps of displaying an unlocking interface in a touch screen terminal, wherein the unlocking interface comprises at least one touch region; according to the operation of a user for the touch region of the unlocking interface, obtaining unlocking information and extracting fingerprint information detected in a specified touch region; judging whether the unlocking information is consistent with preset unlocking information or not and whether the fingerprint information detected in the specified touch region is consistent with fingerprint information preset for the specified touch region or not; and if the unlocking information is consistent with the preset unlocking information and the fingerprint information detected in the specified touch region is consistent with the fingerprint information preset for the specified touch region, unlocking a target object. Correspondingly, the invention furthermore discloses a touch screen terminal based unlocking apparatus and the touch screen terminal. With the adoption of the method and the touch screen terminal, the information security level can be improved, thereby ensuring user privacy to be secure.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for creating virtual service connections to provide a secure network
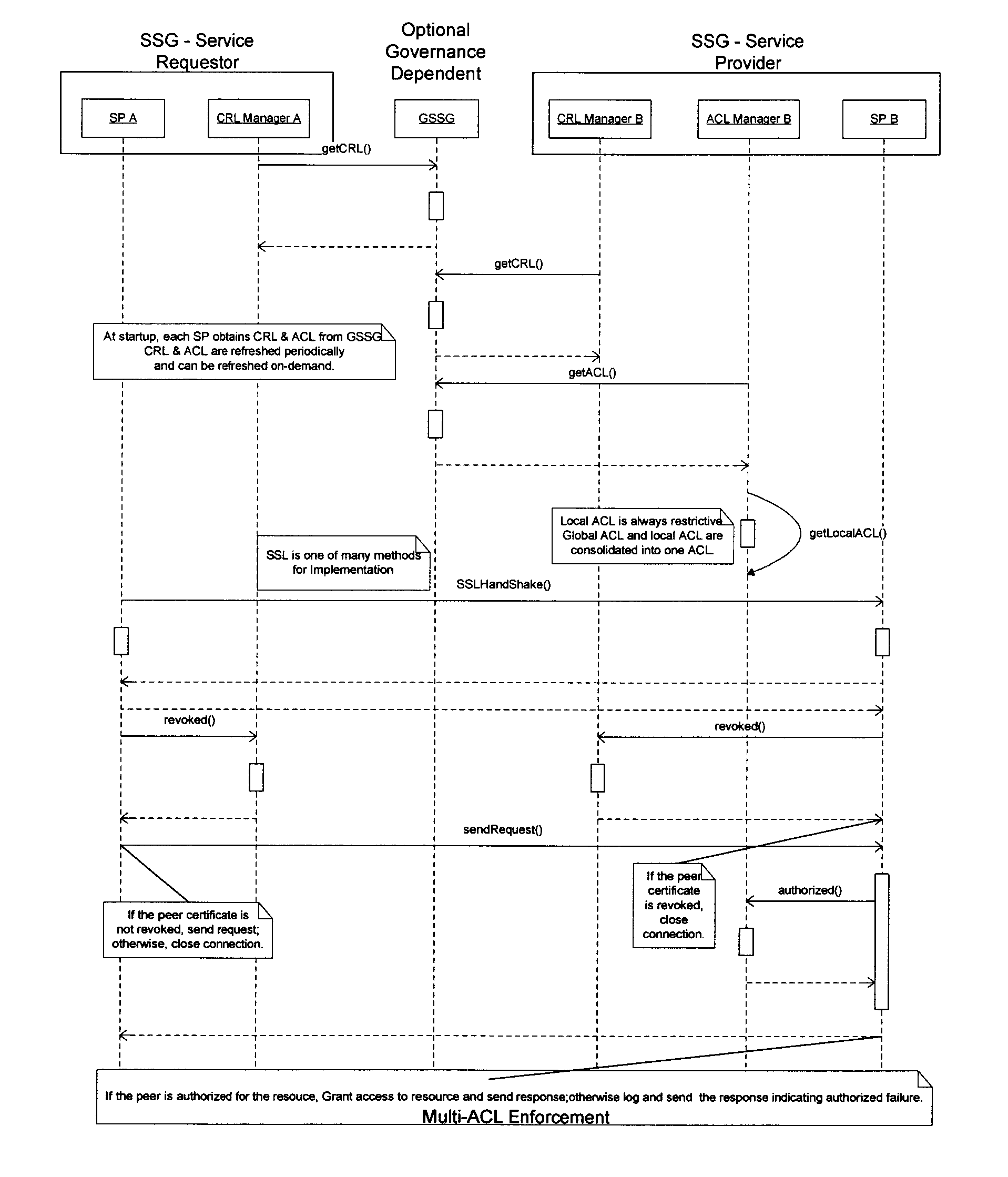
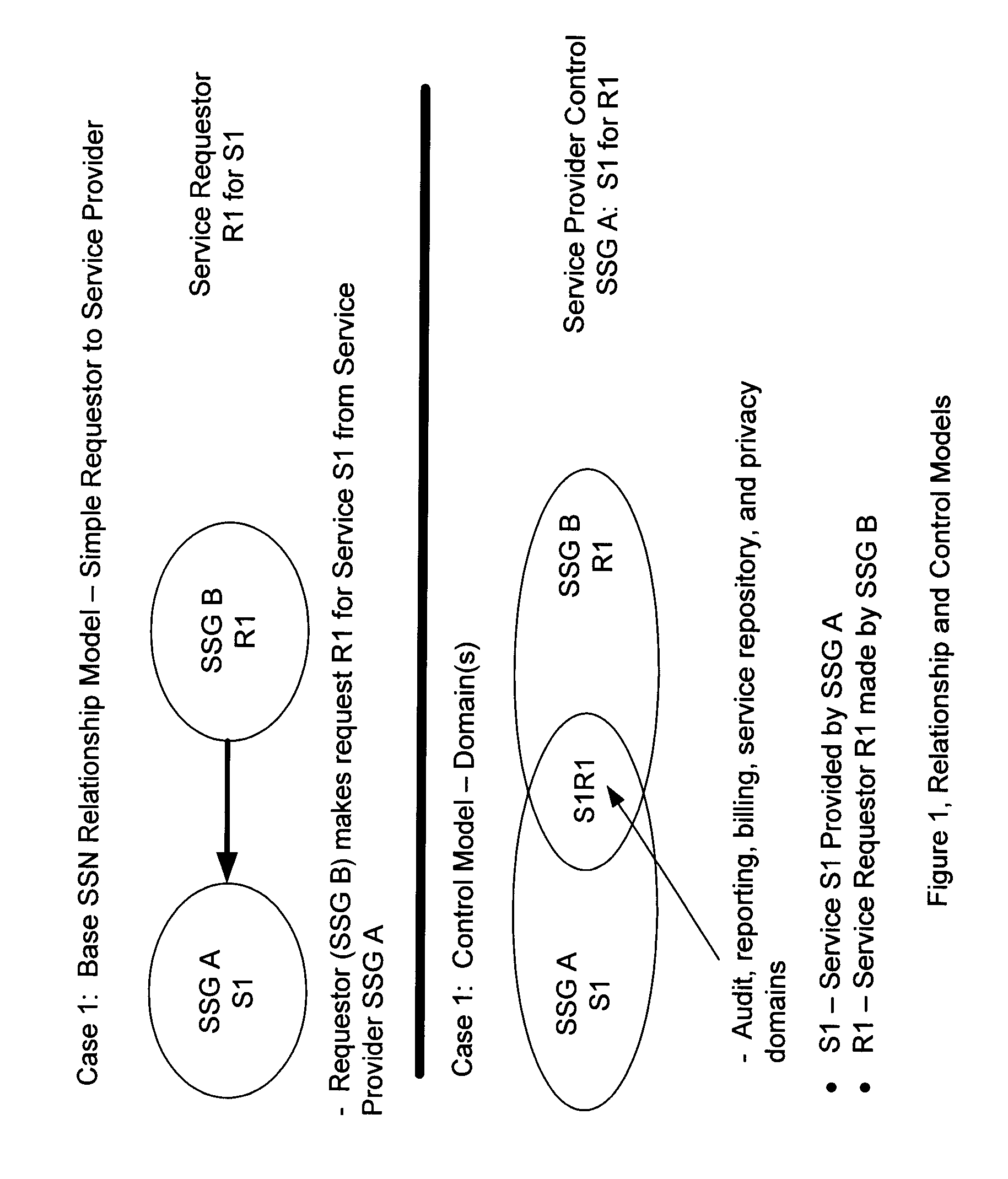
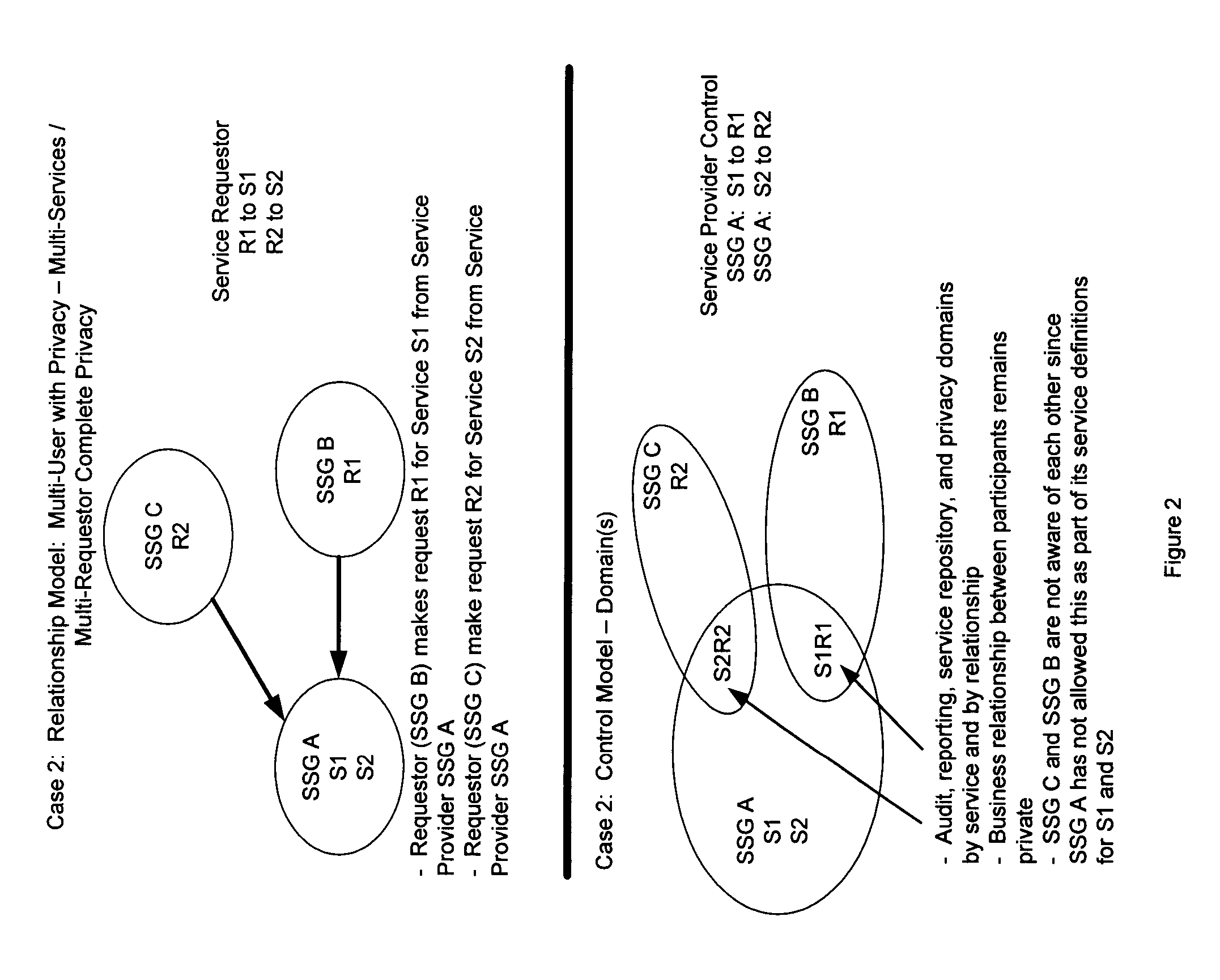
InactiveUS7949871B2Communication securityGood serviceMultiple digital computer combinationsTransmissionVirtual network topologyWeb service
A Secure Service Network (SSN) in which at least two participants having a relationship are connected to a physical network by way of Secure Service Gateways and share information defined by one or more Service Definitions allowing for the creation of a secure Virtual Service Connection (VSC) between the participants in which the VSC is specific to the activity being performed and the participants provisioned for that activity. SSN enables the creation of a secure virtual network topology on any network transport that allows participants to exchange documents and transact business over the network real time, where all activity inherits a business and security infrastructure that is independent and in addition to the applications, devices, web services, users using the network.
Owner:RANDLE WILLIAM M +1
Differential privacy data publishing method and system based on dependency removal
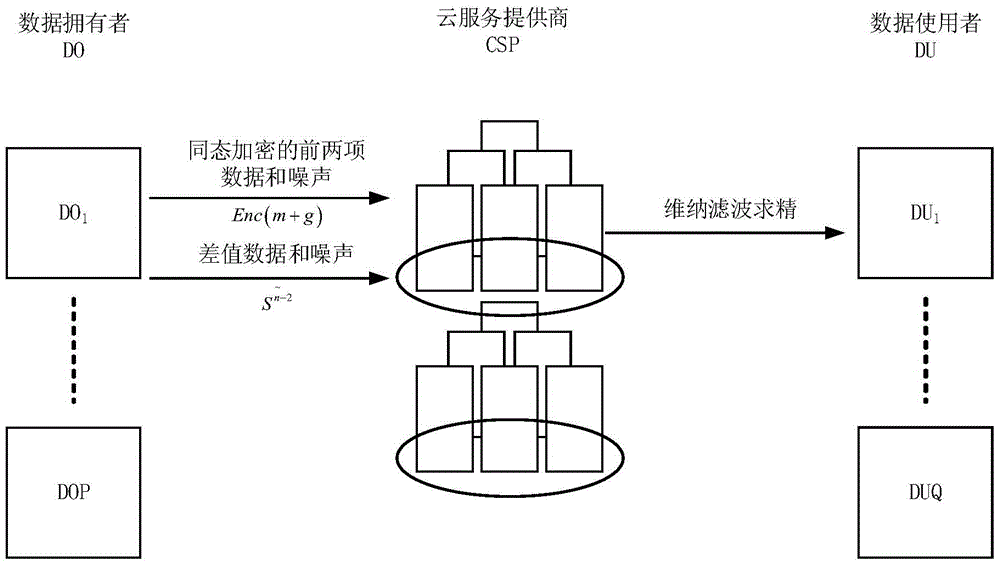
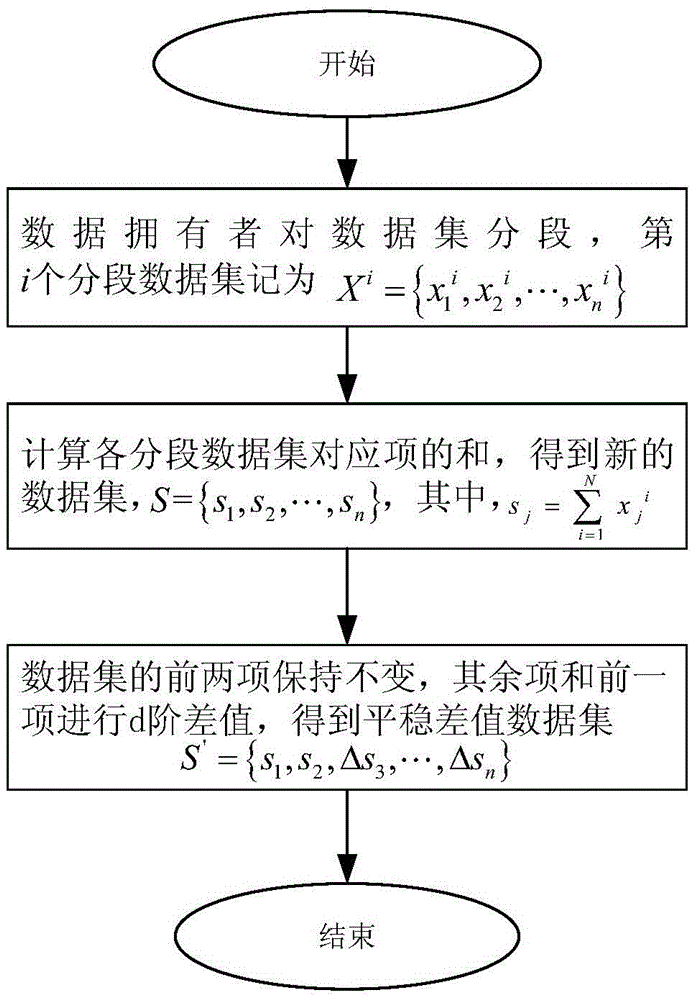
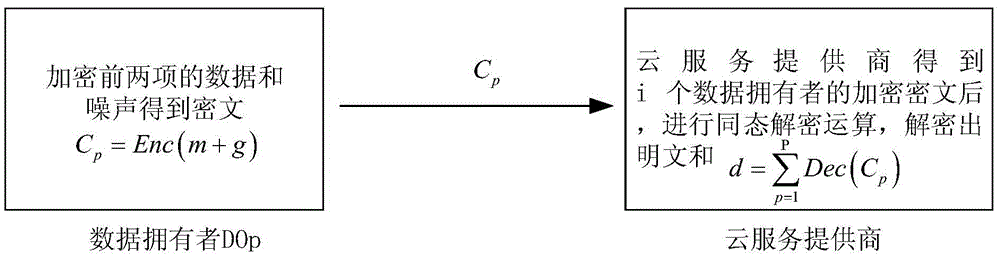
ActiveCN105608388AGuaranteed privacy and securityReduce computational complexityDigital data protectionTransmissionData setOriginal data
The invention discloses a differential privacy data publishing method and system based on dependency removal. Each data owner independently sections an own original data set and obtains a differential value data set, the first two items of the differential value data set are subjected to summation and noise adding, then, the obtained value is uploaded to a cloud service provider after the obtained value is subjected to homomorphic encryption, and the cloud service provider carries out homomorphic decryption operation; each data owner transforms the differential value data set item to obtain a transformation coefficient, and stable noise consisting of white noise which is mutually independent and complies with Gaussian distribution is added; the data owner carries out inverse wavelet transform to obtain a scrambled data set, and the data set is uploaded to the cloud service provider; and the cloud service provider utilizes Wiener filtering to carry out filtering, and the cloud service provider carries out inverse transformation on a refined data set and publishes the refined data set to the data item of a third-party data user when the data user requests the data set. The differential privacy data publishing method and system effectively reduces the data calculation amount and interaction amount and improves a resource use ratio and data availability.
Owner:WUHAN UNIV
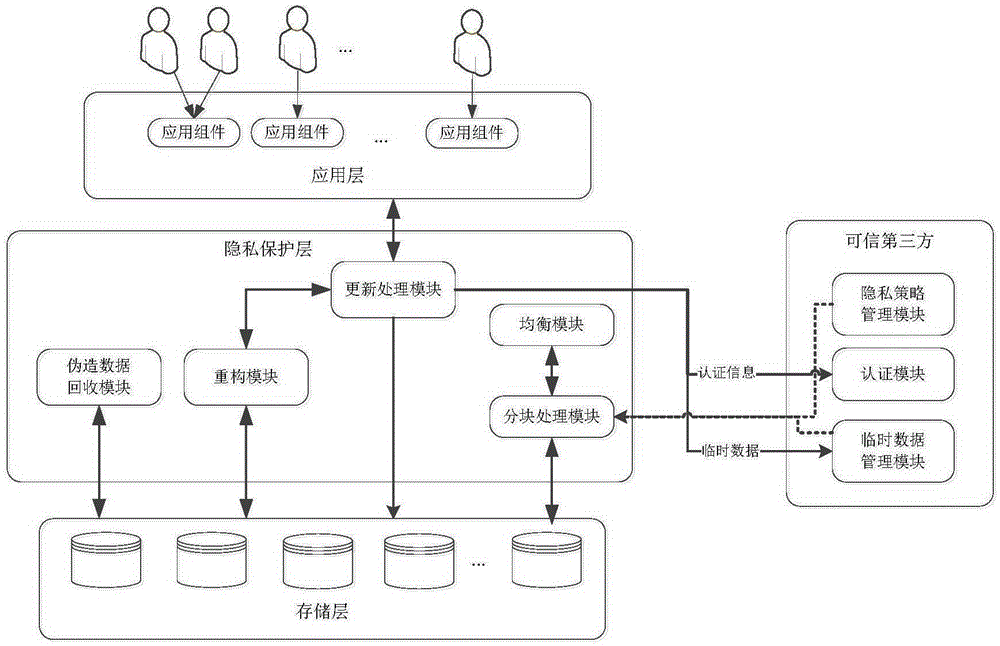
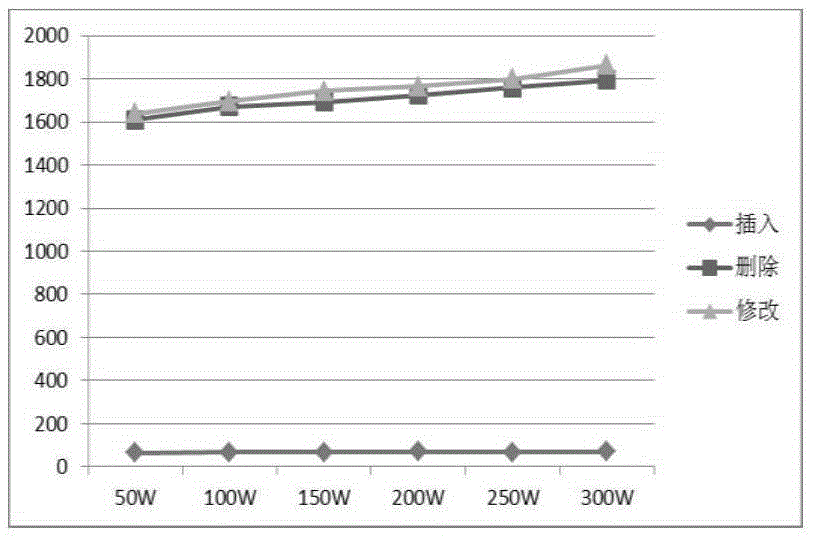
Blocking confusion based dynamic data privacy protection system and method
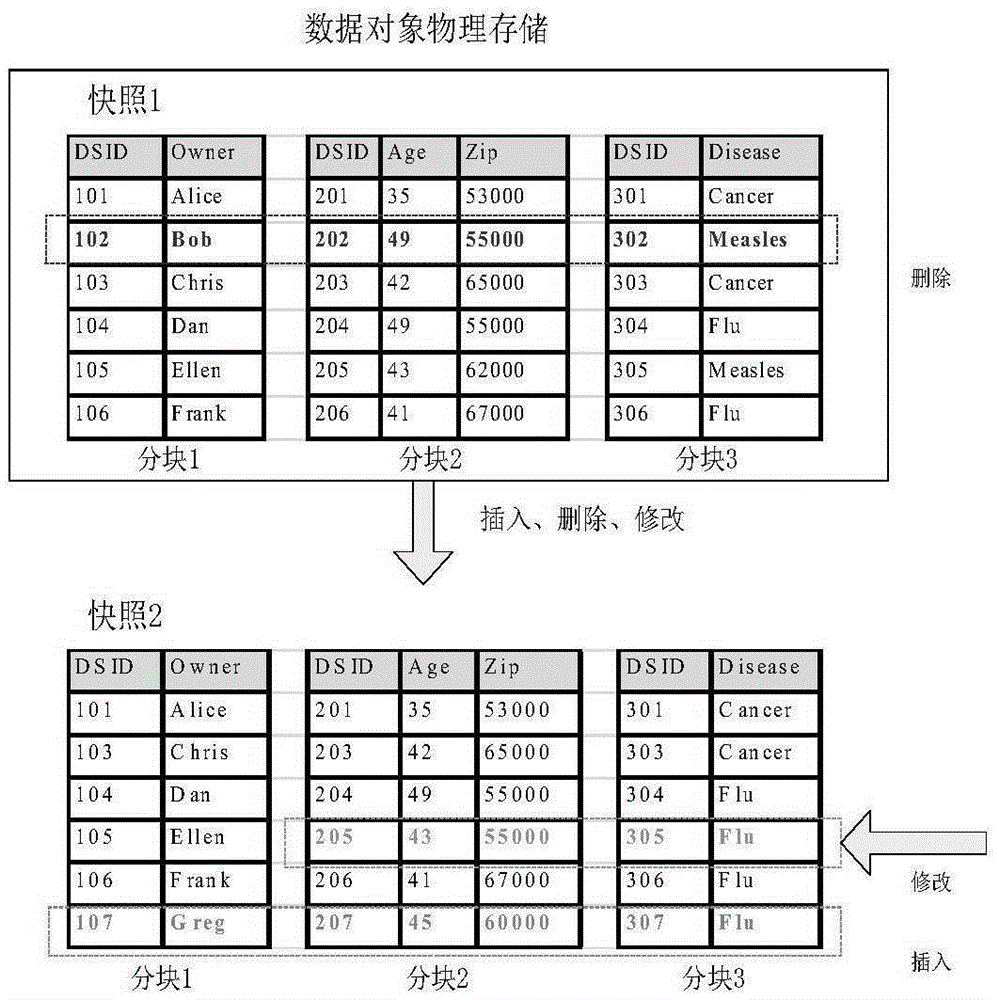
InactiveCN105303123AGuaranteed privacy and securityReduce consumptionDigital data protectionProtection mechanismResource consumption
The invention discloses a blocking confusion based dynamic data privacy protection system and method. Newly inserted and modified data is cached through a trusted third party, and the data is grouped and stored when conditions are met; the privacy security of deleted data and residual data in a delete operation is ensured by keeping key fragmentations; and the reduction of storage resource consumption and the optimization of the application performance are realized by falsification of a data recycling mechanism. Experiments prove that the proposed dynamic data privacy protection mechanism is higher in feasibility and practicability.
Owner:SHANDONG UNIV +1
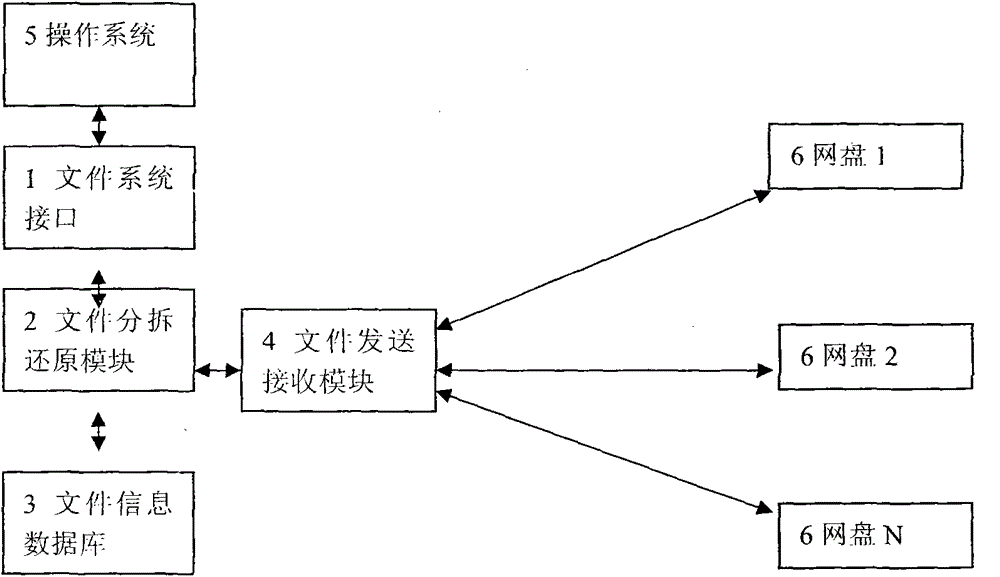
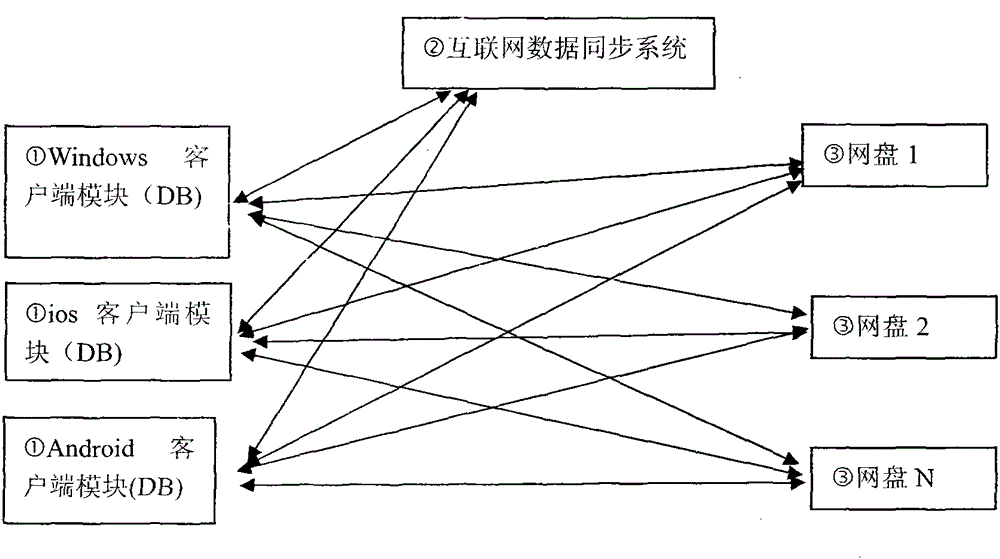
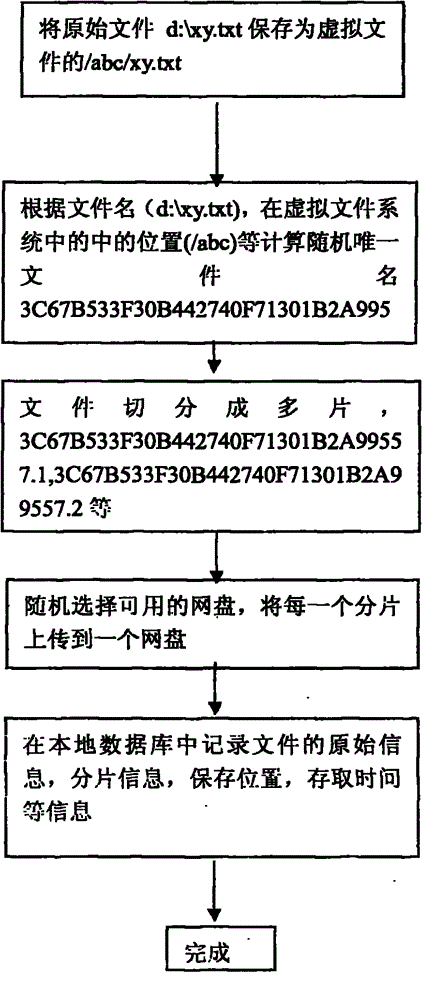
Virtual file system achieving reliability through multi-network-disk redundant storage
InactiveCN104156377AImprove access performanceGuaranteed privacy and securityTransmissionRedundant operation error correctionData reliabilityComplete data
Owner:孙良茵
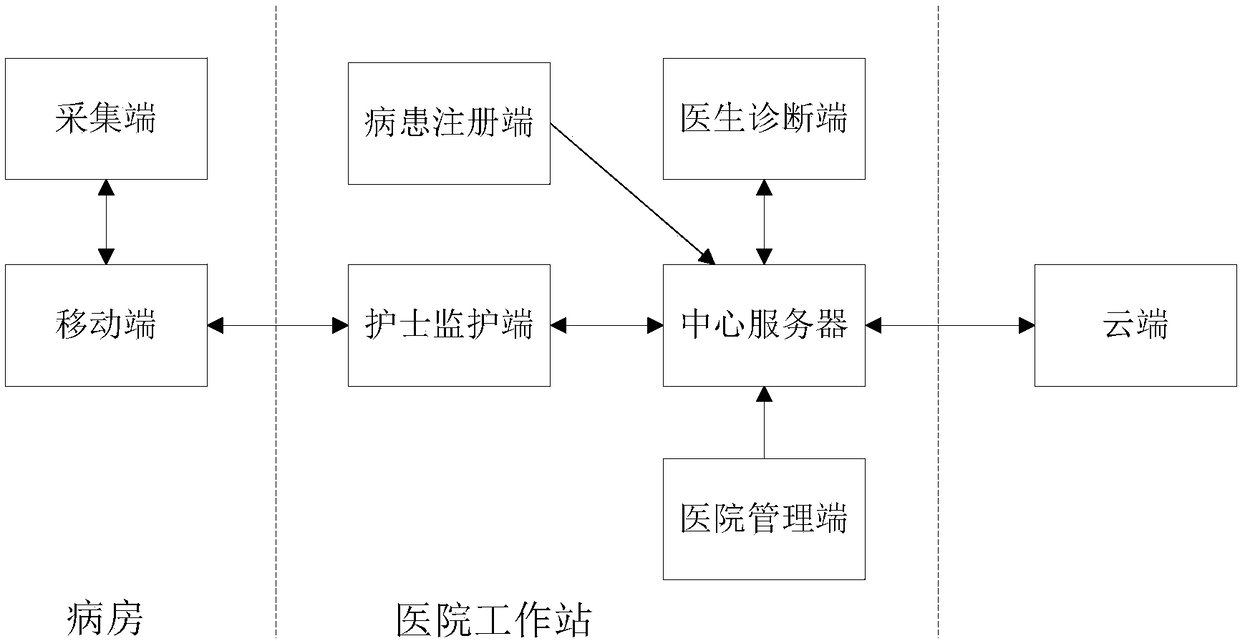
Remote hospital monitoring system and method
InactiveCN108852282AReal-time acquisition of physiological dataAvoid the need for one-by-one roundsData processing applicationsDiagnostic recording/measuringReal time analysisMonitoring system
The invention discloses a remote hospital monitoring system and method. The system comprises a collecting end, a mobile end, a patient registration end, a nurse monitoring end, a central server, a doctor diagnosis end and a hospital management end; the patient registration end obtains personal information of a patient and writes the information into the central server; the collection end collectsphysiological data of the patient and uploads the data to the nurse monitoring end through the mobile end; the nurse monitoring end performs real-time analysis and intelligent monitoring on the physiological data and uploads the data to the central server; the doctor diagnosis end requests real-time or history data from the central server, performs comprehensive diagnosis, generates a diagnostic report and uploads the report to the central server; the hospital management end manages personal information and permission of medical personnel. By taking a server as the center, working end and dataflow are arranged reasonably, effective transmission, storage and management of the data are kept; on the one hand, a nurse remotely and centrally monitors the patient, and the workload of ward roundis relieved; on the other hand, a doctor remotely obtains the patient data conveniently, and the diagnostic process is assisted.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV +1
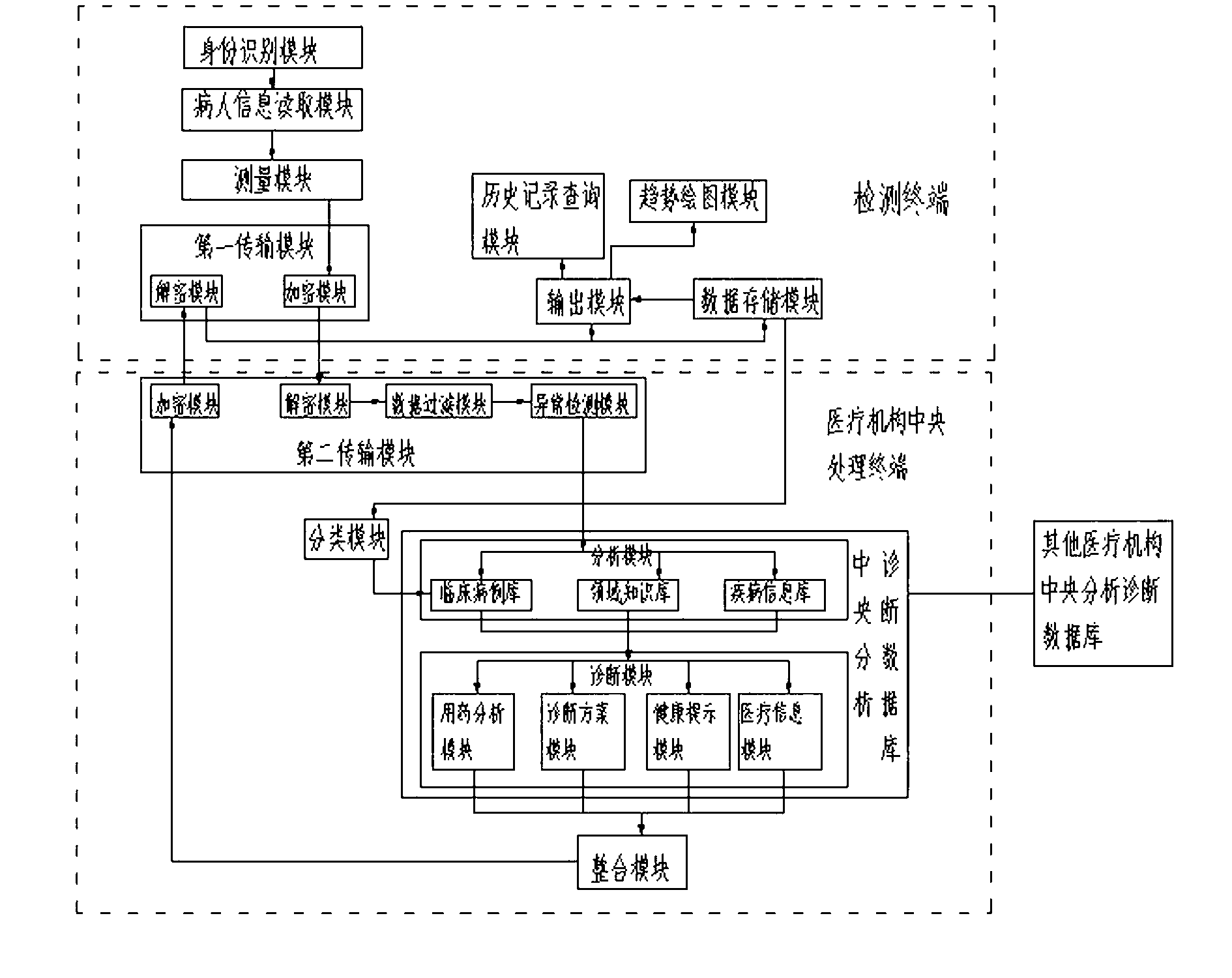
Multi-user multi-parameter wireless detection, diagnosis, service and monitoring system
InactiveCN103268422AConvenient to enjoyFlexible timeSpecial data processing applicationsDiagnostic dataNetwork connection
The invention relates to a multi-user multi-parameter wireless detection, diagnosis, service and monitoring system which comprises a detection terminal and a medical establishment central processing terminal connected to the detection terminal through a network, wherein the detection terminal comprises a patient information reading module, a measuring module and a first transmission module. The first transmission module transmits patient physiological data measured by the measurement module to the medical establishment central processing terminal through the network. The medical establishment central processing terminal comprises a central analysis and diagnosis database and a second transmission module, and the second transmission module transmits data between the first transmission module and the central analysis and diagnosis database. The detection terminal further comprises an output module which is at least used for outputting inspection reports. According to the multi-user multi-parameter wireless detection, diagnosis, service and monitoring system, data transmission between the detection terminal and the medical establishment central processing terminal is utilized to achieve remote medical service, so people can more conveniently enjoy the medical service, and time and places for the medical service are more flexible.
Owner:MAYHAP IND SUZHOU
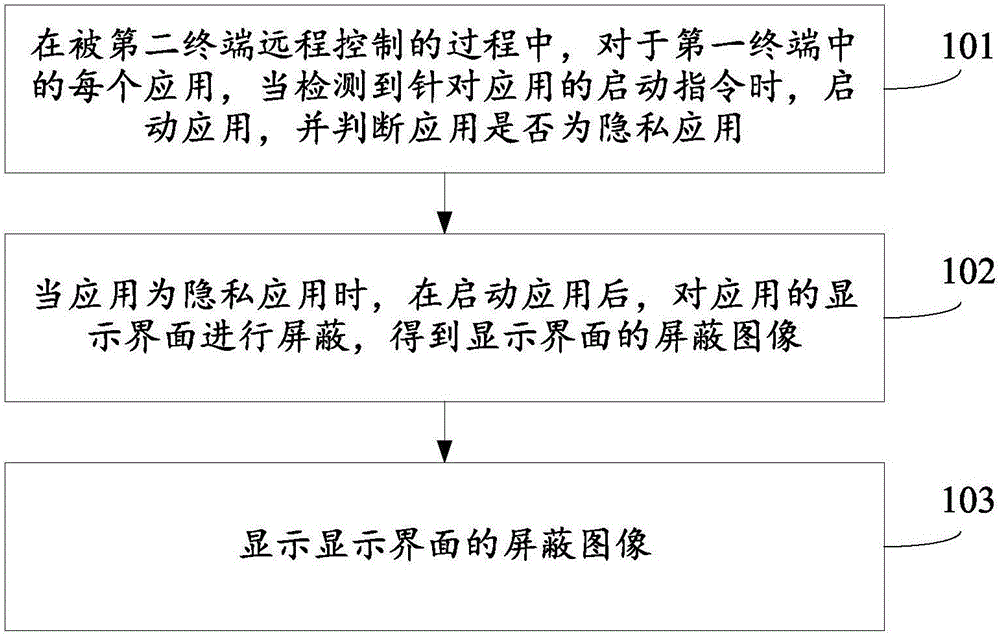
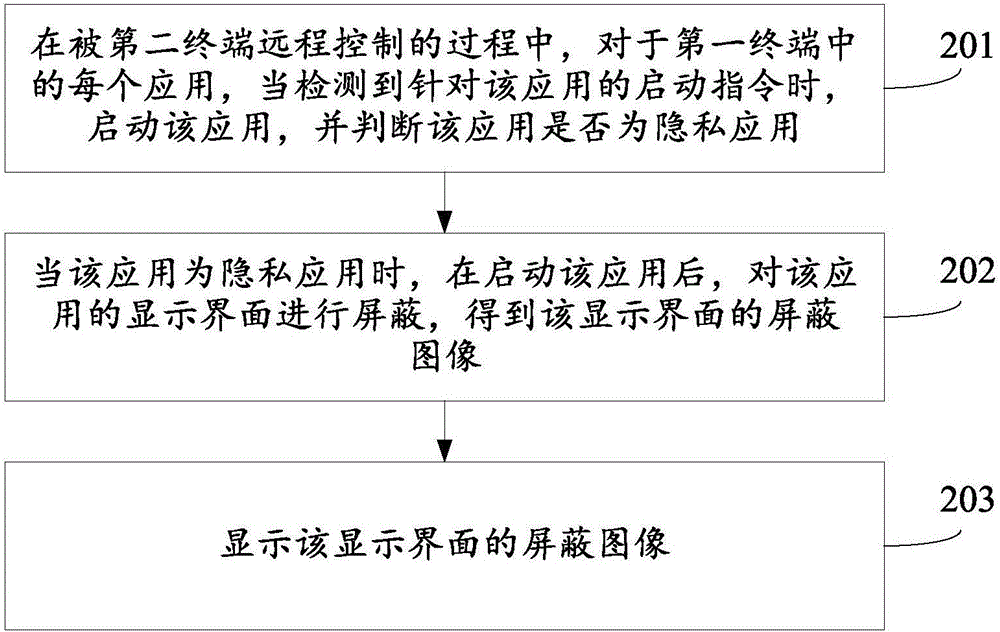
Remote control method and apparatus
ActiveCN105956486AAvoid Privacy LeakageGuaranteed privacy and securityDigital data protectionRemote controlThe Internet
The invention relates to a remote control method and apparatus, and belongs to the technical field of internet. The method is applied to a first terminal. The method comprises the steps of starting an application when a starting instruction for the application is detected for each application in the first terminal in a process of remote control by a second terminal, and judging whether the application is a private application or not; when the application is the private application, hiding a display interface of the application after starting the application to obtain a hided image of the display interface; and displaying the hided image of the display interface. According to the method and apparatus, the privacy leakage of the first terminal can be effectively prevented to ensure privacy security of the first terminal.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
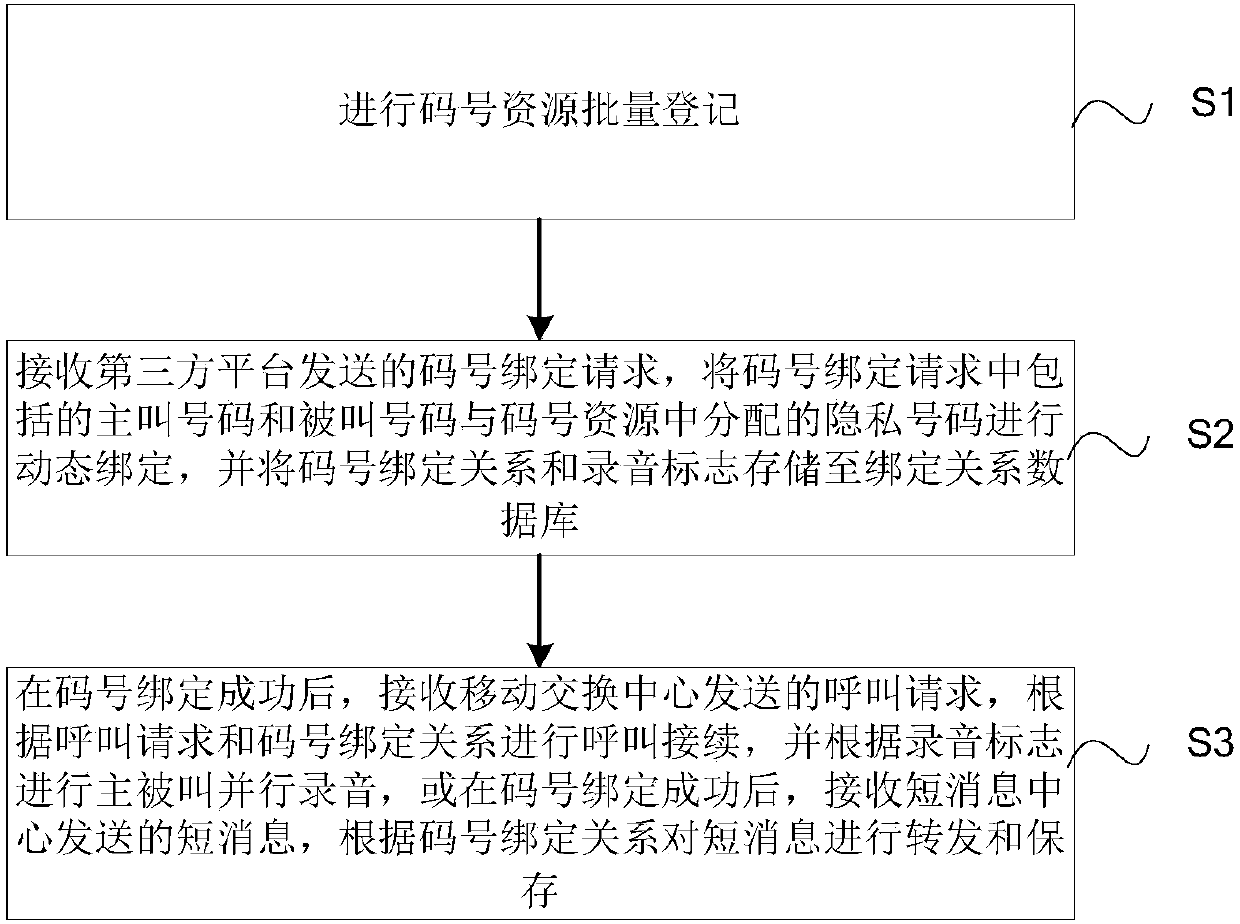
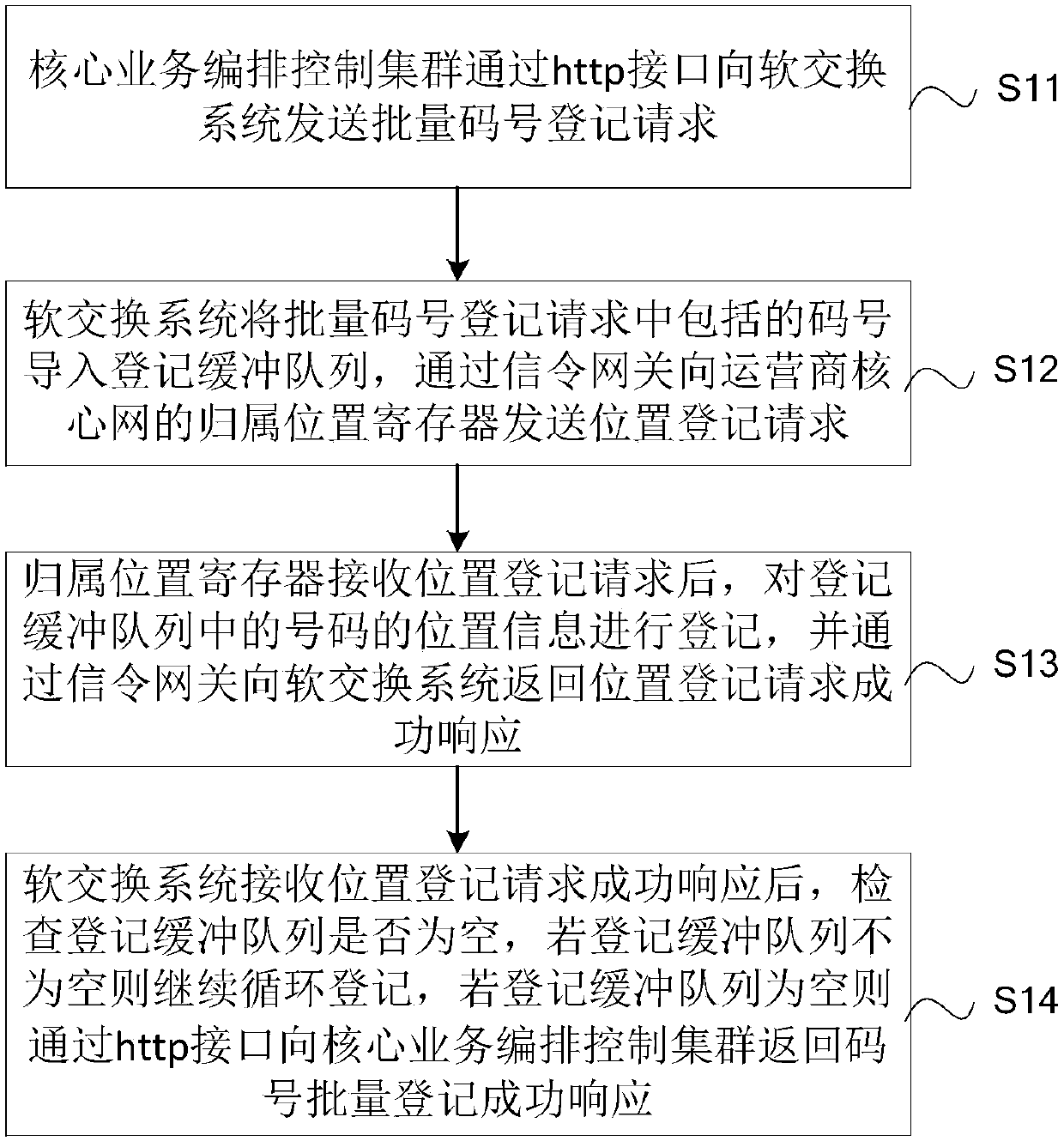
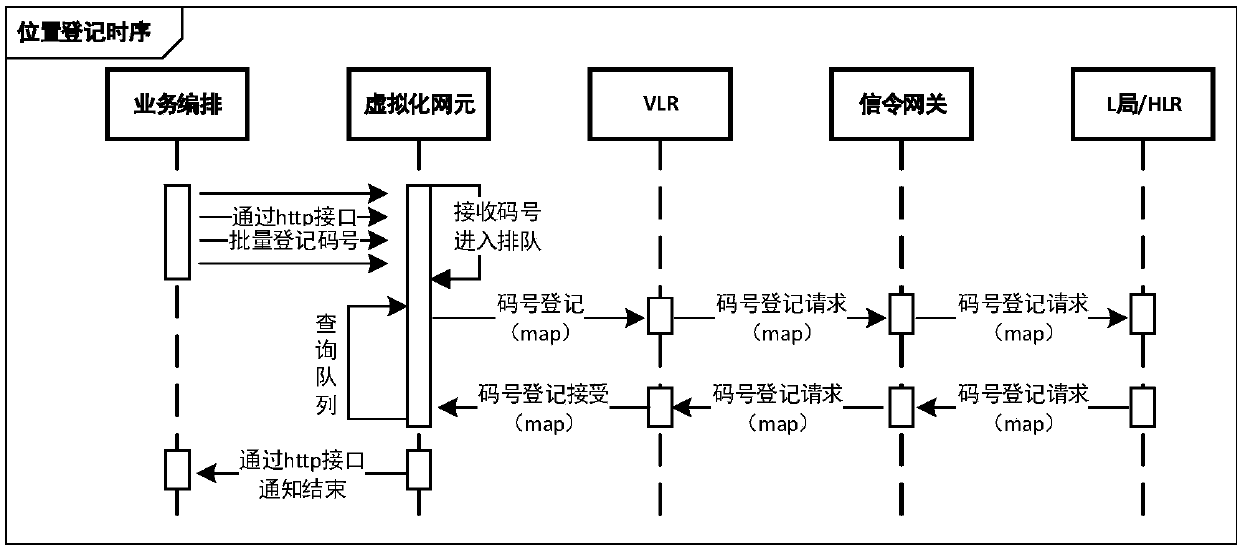
Mobile phone number security privacy protection method and platform based on mobile Internet
ActiveCN107809749AGuaranteed privacy and securityRelational databasesCommmunication supplementary servicesThird partyThird platform
The invention discloses a mobile phone number security privacy protection method and platform based on the mobile Internet. The method comprises the steps of S1, carrying out code number resource batch registration; S2, receiving a code number binding request sent by a third platform, carrying out code number binding according to the code number binding request, and storing a code number binding relationship and a recording mark to a binding relationship database; and S3, after the code number binding is successful, receiving a call request sent by a mobile switching center, carrying out callconnection according to the call request, and carrying out calling and called parallel recording, or receiving a short message sent by a short message center, and forwarding and storing the short message. The method and the platform have the beneficial effects that private numbers and true numbers of two parties are bound, the binding relationship is stored, and a called true number is queried indirectly according to the private numbers and the binding relationship, so the privacy security of a mobile phone number of the a user is ensured.
Owner:中国东盟信息港股份有限公司
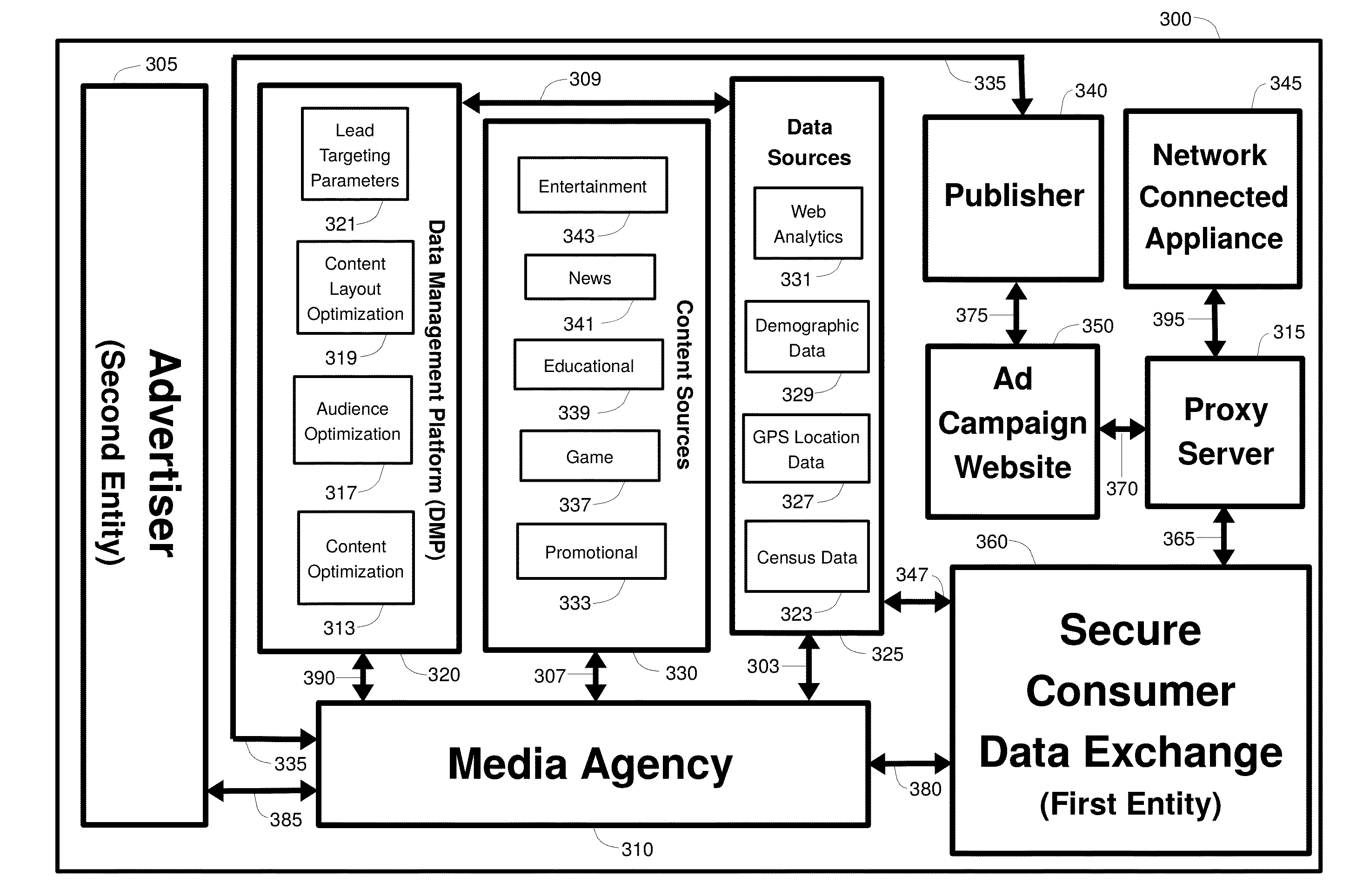
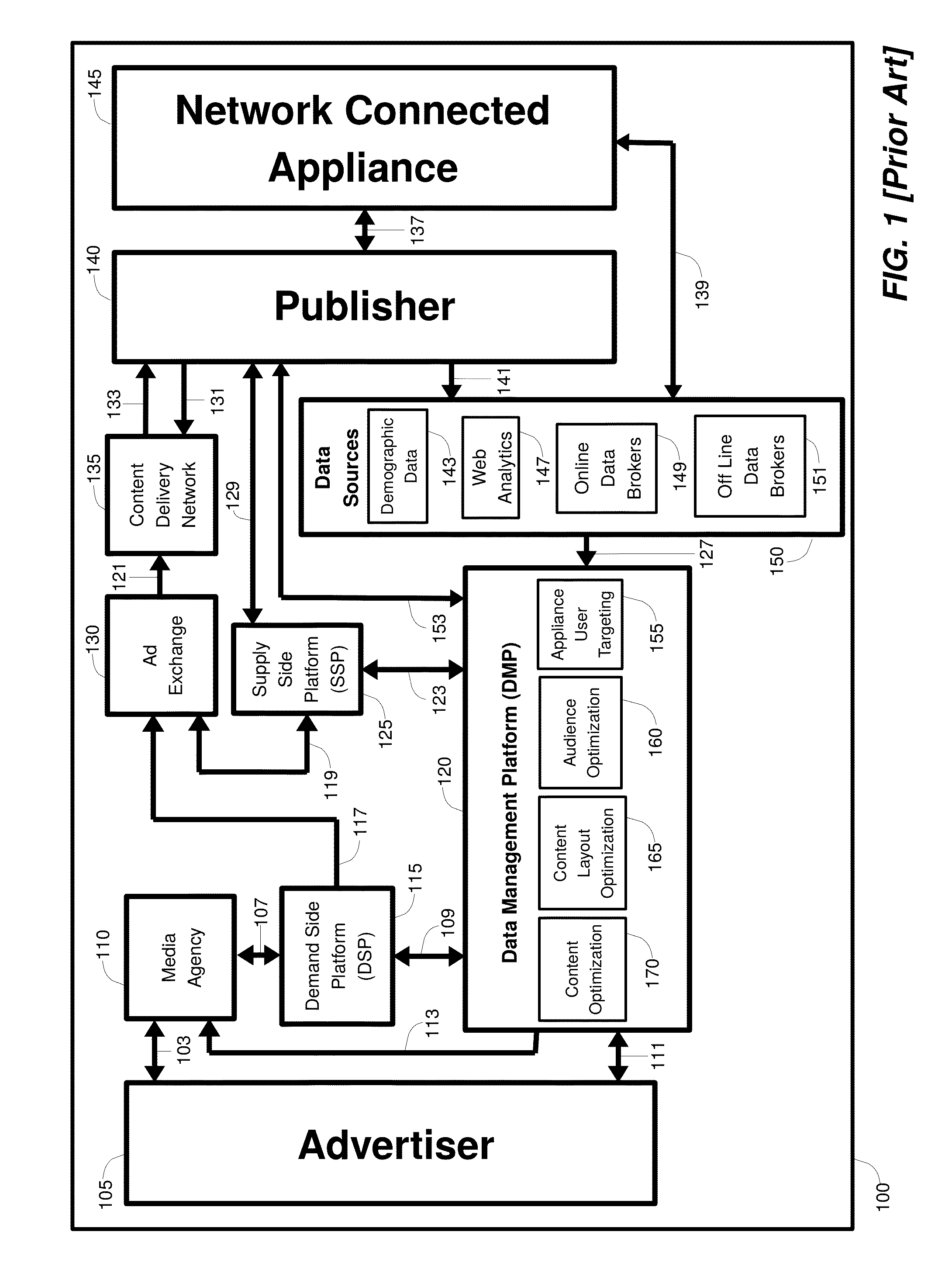
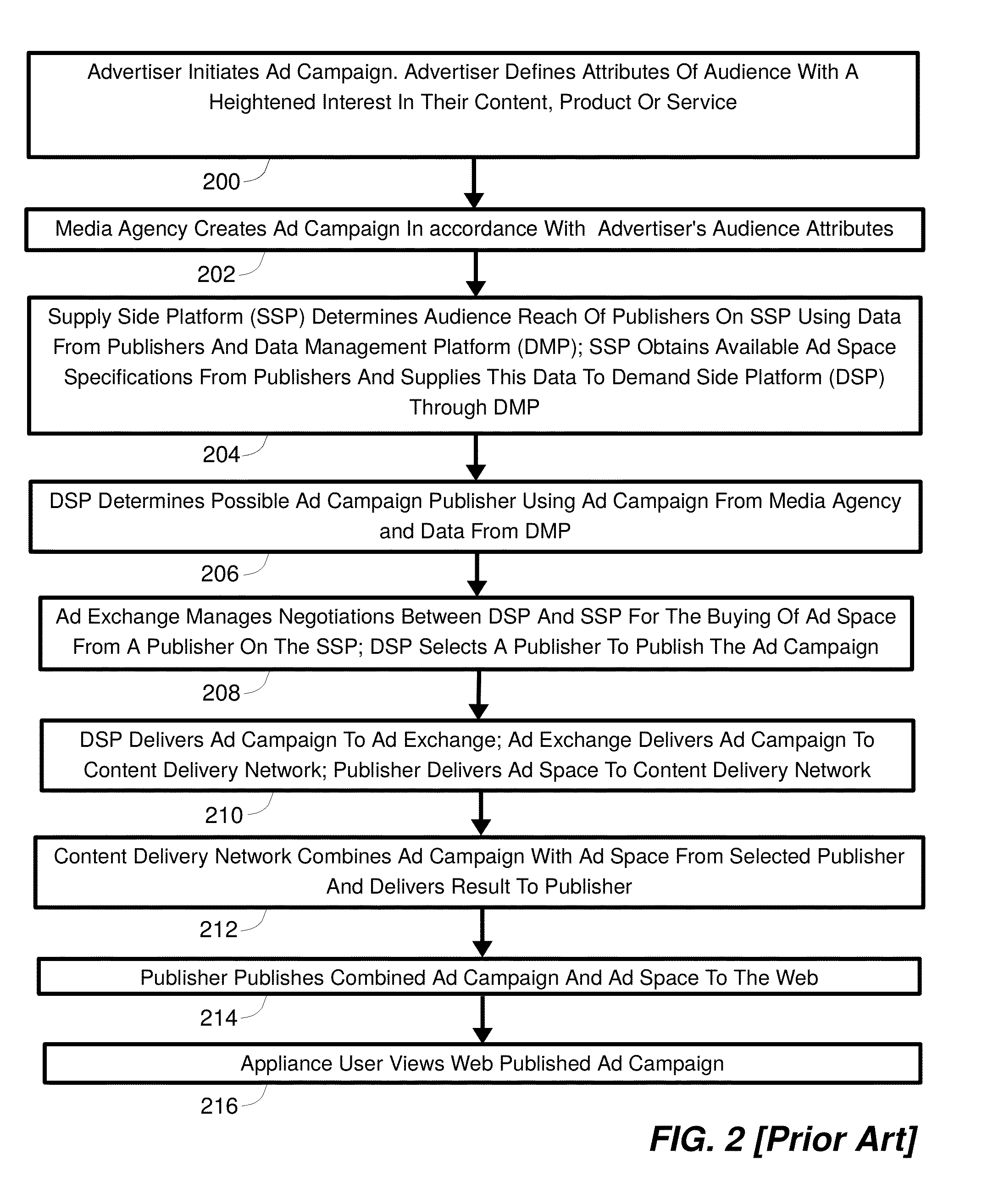
Method, system and apparatus for effecting targeted access to anonymous users of a network
InactiveUS20150095104A1Guaranteed privacy and securityComputer security arrangementsMarket data gatheringNetwork connectionWorld Wide Web
A method, system, and apparatus for effecting targeted access to anonymous users of a network is provided. A second entity delineates parameters of an audience with heightened interest in an offering, and a first entity provides the second entity with access to an audience accordant with these parameters. Consumer data collected by a network connected appliance used by an appliance user is linked with an appliance user anonymous identifier, and communicated to the first entity. Using the parameters, the first entity analyzes the collected consumer data and aggregates the appliance user's anonymous identifier with anonymous identifiers of other appliance users, thereby generating an aggregate set of anonymous identifiers that point to members of the audience. This set is marked with an identification code that is communicated to the second entity that can be used by the second entity to gain access to the audience through the first entity.
Owner:GOLDBERG PAUL R
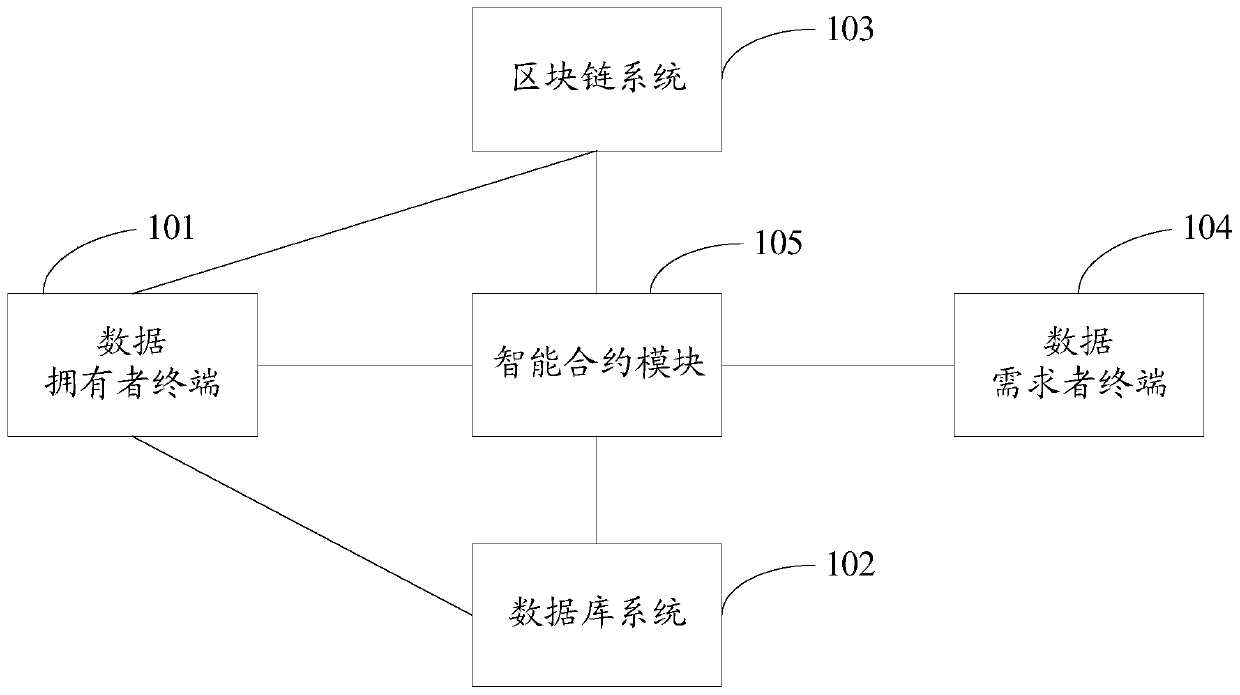
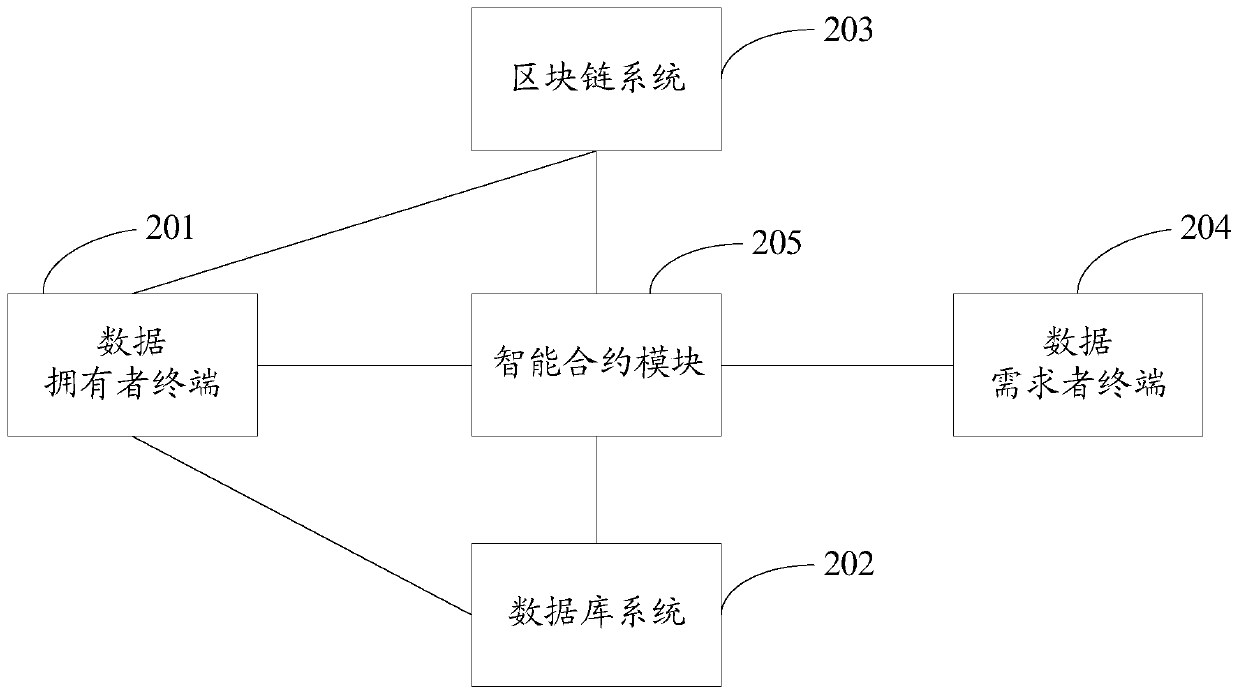
Blockchain data transaction system and method based on proxy re-encryption and smart contract
ActiveCN110430186AGuaranteed privacy and securityRealize economic valueKey distribution for secure communicationFinanceTransaction dataData needs
The invention discloses a blockchain data transaction system and a blockchain data transaction method based on proxy re-encryption and an intelligent contract. The system comprises a data owner terminal, a database system, a blockchain system, a data demander terminal and an intelligent contract module. According to the method, the security privacy of the transaction data can be ensured by using the proxy re-encryption technology, and the efficient and automatic execution of the data transaction can be realized by using the smart contract, so that the security privacy and efficiency problems of the blockchain data transaction are solved. The economic value of the data is realized, and the application value of the data is brought into full play.
Owner:STATE GRID E COMMERCE CO LTD +2
Multi-user searchable encryption method and encryption system in Internet of Vehicles environment
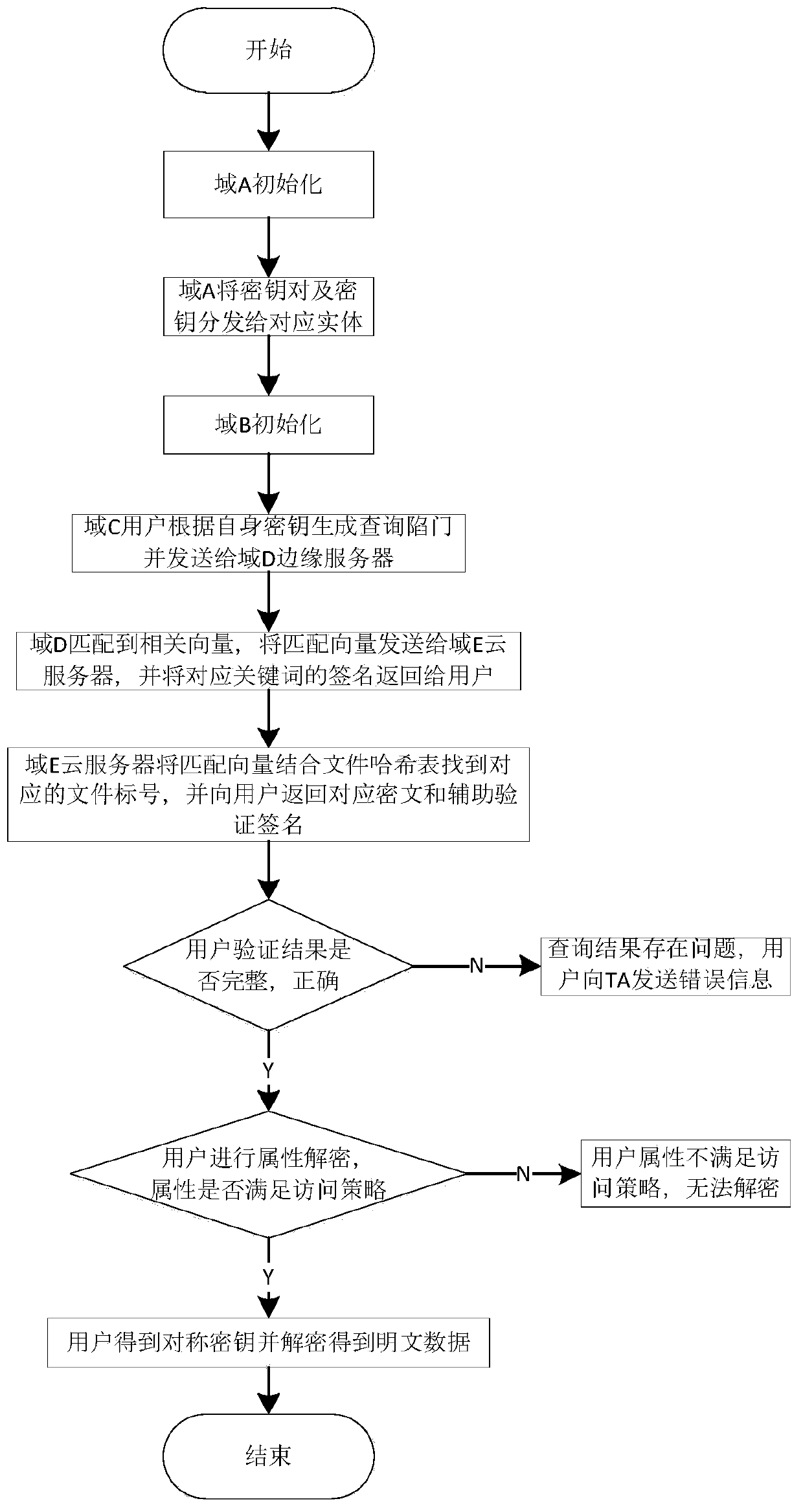
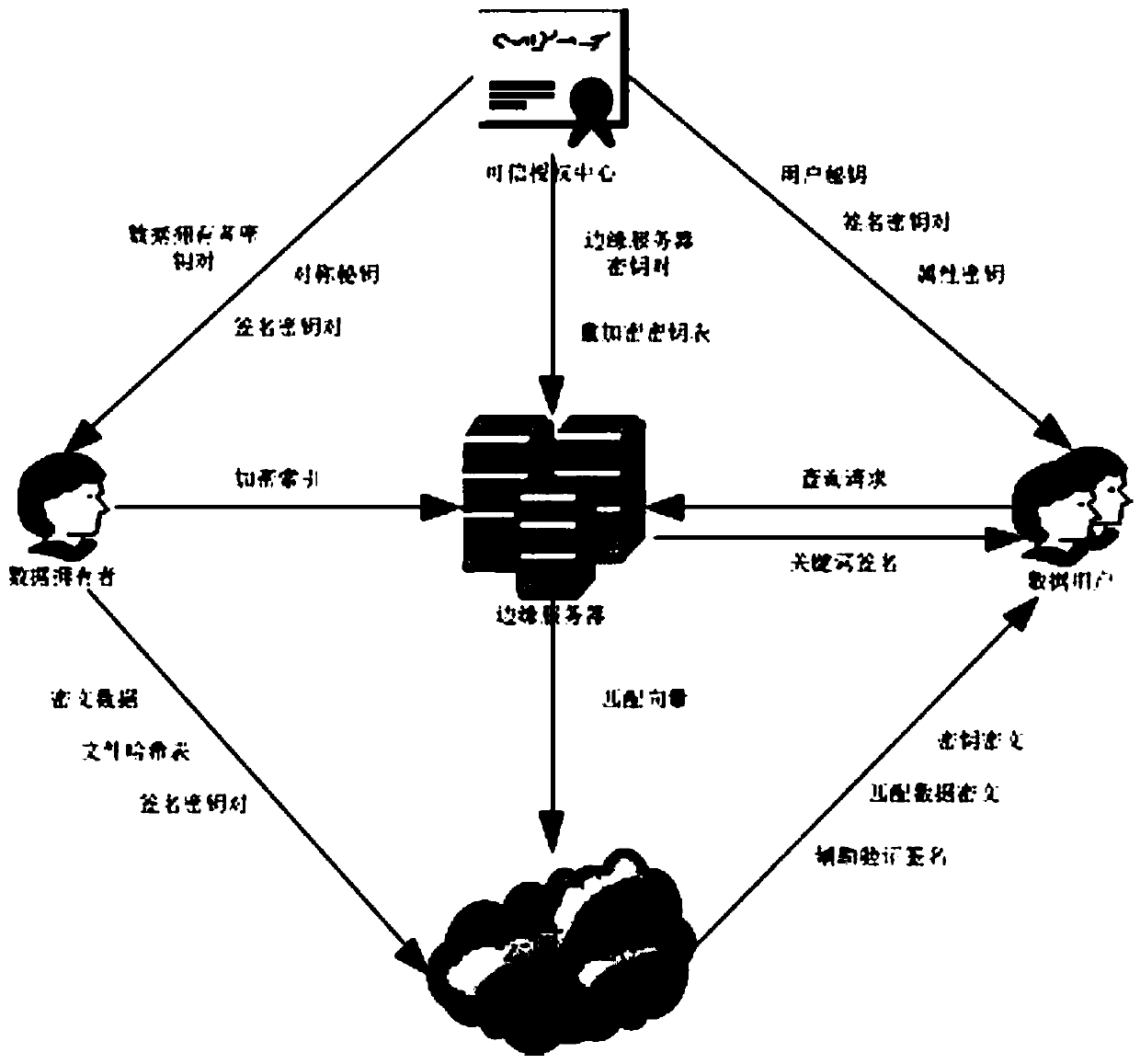
ActiveCN111556495AGuaranteed privacy and securityReduce communication delayEncryption apparatus with shift registers/memoriesPublic key for secure communicationPlaintextData privacy protection
The invention belongs to the technical field of wireless communication networks. The invention discloses a multi-user searchable encryption method and encryption system in an Internet of Vehicles environment, and the method comprises the steps: a trusted authorization mechanism transfers a calculation burden on a cloud server to an edge server of each edge node, and a data end generates a query trap door through a private key, and transmits the query trap door to the edge server on the edge node; after receiving the request, the edge server matches a corresponding vector according to an indexand a trap door sent by the data end and sends the vector to the cloud server, and the cloud server obtains a matched file label and ciphertext data according to the vector and the hash table, searches for a signature of a keyword and returns the signature to the data end; and after verifying that the signature is correct by using the signature public key, the data end decrypts the ciphertext databy using the attribute key to obtain a data plaintext. Data privacy protection is achieved in the Internet of Vehicles environment with high requirements for communication time delay and calculationoverhead, and fine-grained control over the access permission of multiple users is achieved.
Owner:XIDIAN UNIV
Distributed data processing method and device, computer equipment and storage medium
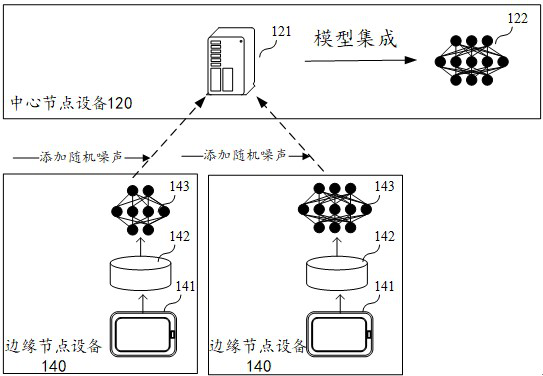
ActiveCN112329073AImprove integrationEasy to integrateEnsemble learningDigital data protectionEdge nodeDifferential privacy
The invention relates to a distributed data processing method and device, computer equipment and a storage medium, and relates to the technical field of artificial intelligence. The method comprises the steps that model training information sent by at least two edge node devices is acquired, wherein the model training information is transmitted in a plaintext form, and the model training information is obtained by training a sub-model by the edge node equipment in a differential privacy mode; on the basis of the model training information sent by the at least two pieces of edge node equipmentrespectively, sub-models obtained by training the at least two pieces of edge node equipment respectively are obtained; and on the basis of a specified model integration strategy, model integration iscarried out on the sub-models obtained by training the at least two pieces of edge node equipment to obtain a global model. By means of the scheme, on the premise that data privacy safety is guaranteed, the model integration mode is expanded, and the model integration effect is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Anonymous bidirectional authentication method in mobile social network based on single hash function and false identity
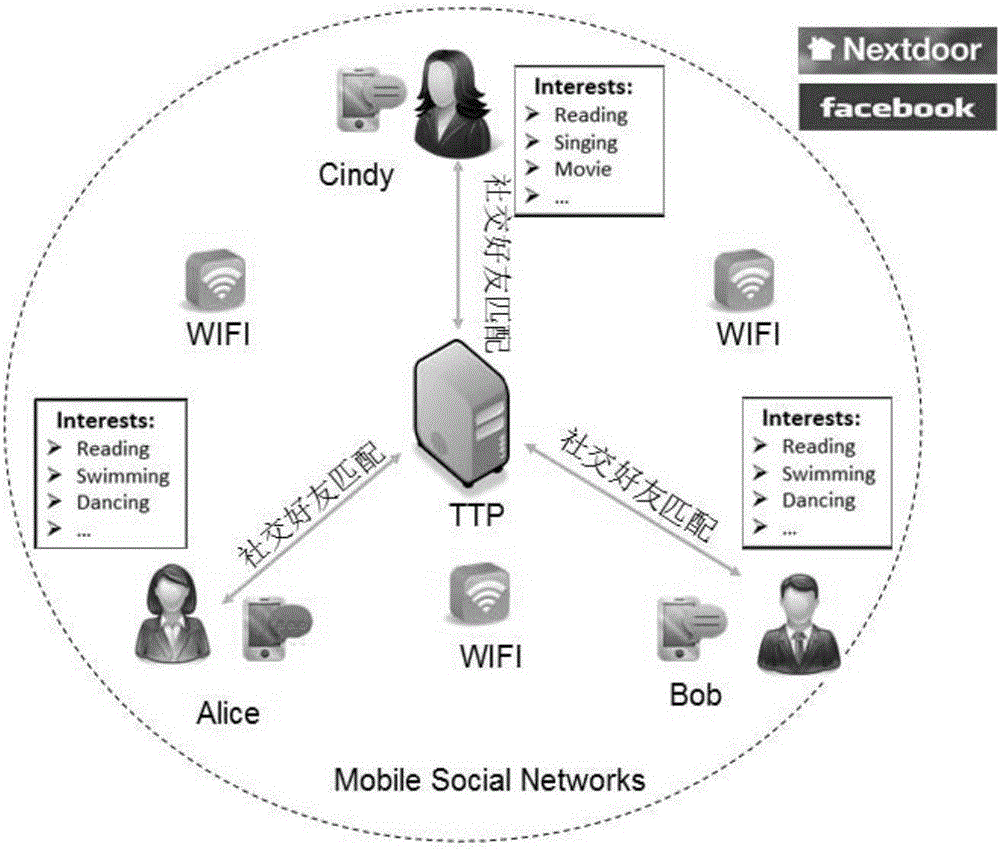
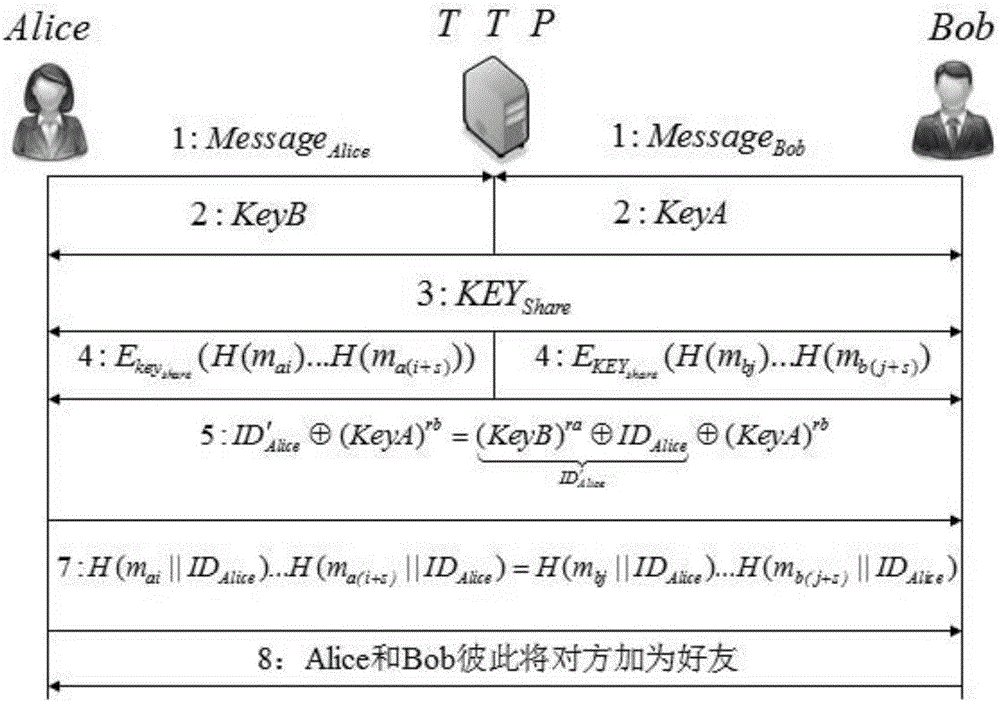
InactiveCN105871869AAvoid non-repudiation authenticationPrevent Forgery AttacksUser identity/authority verificationHash functionDual identity
The invention discloses an anonymous bidirectional authentication method in a mobile social network based on the single hash function and the false identity. The self characteristic attributes of users are subjected to hash through the function characteristic of the single hash function, the hash result and the identifiers of the users are encrypted and sent to a TTP through a public key. After the TTP authenticates the permission of the users, the hash results of different users are compared, and therefore the similarity of the attributes of the users is obtained. In the process, the TTP sends the respective identifiers to the matched users to help the user to establish an identical shared key, then the TTP encrypts the matched attribute set through the key negotiated by the users and sends the matched attribute set to the users participating in friend making. The access permission of the users is controlled through an identity authentication and key negotiation dual-authentication mechanism, and the calculating and storage loads of an intelligent user terminal are relieved through the strong calculating and storage capacity of the TTP.
Owner:HUNAN UNIV OF SCI & ENG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com