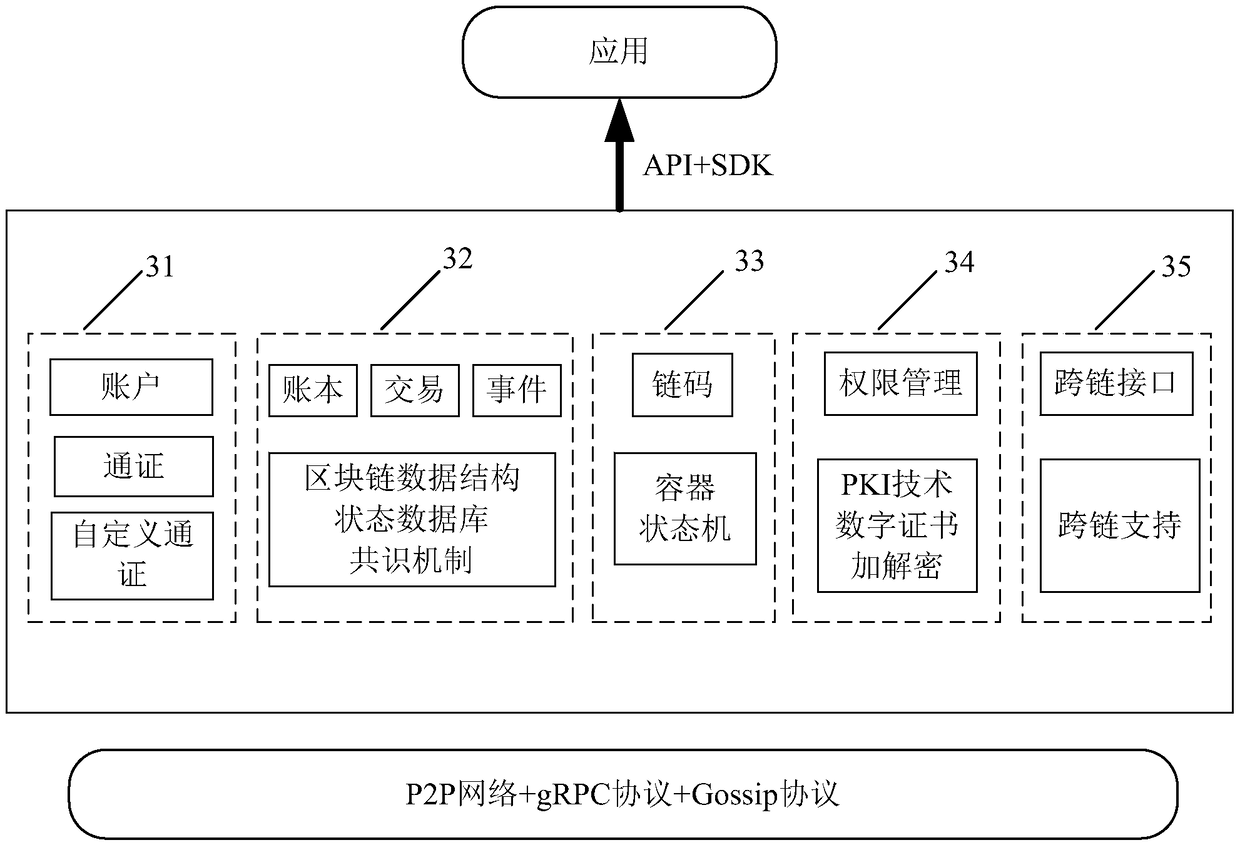
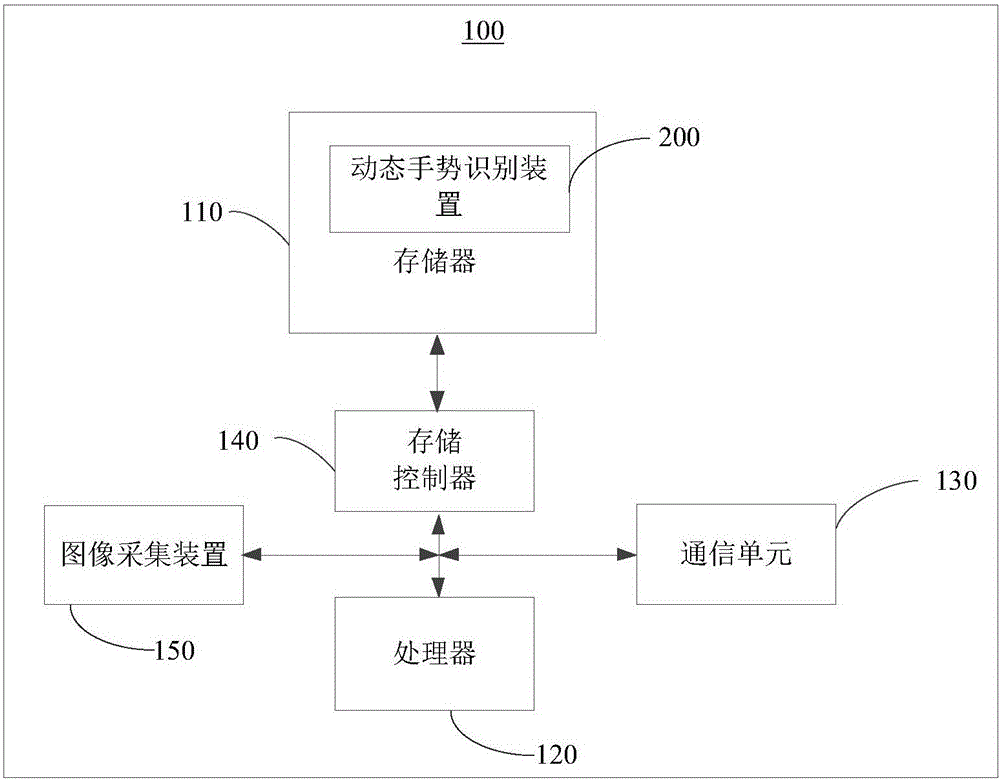
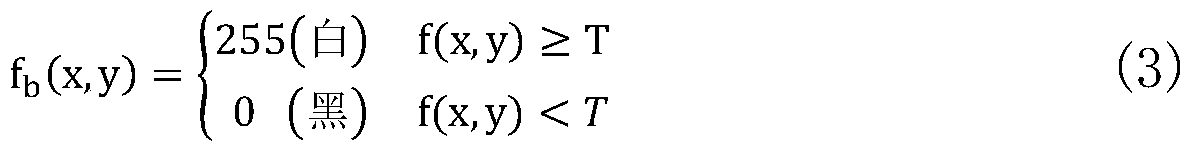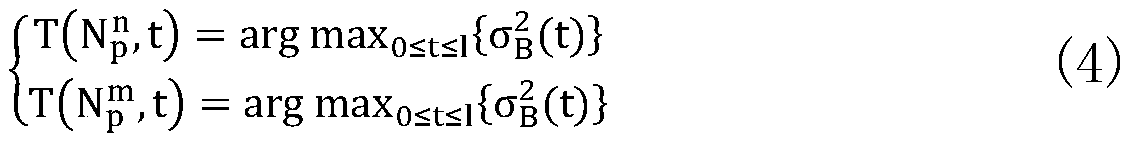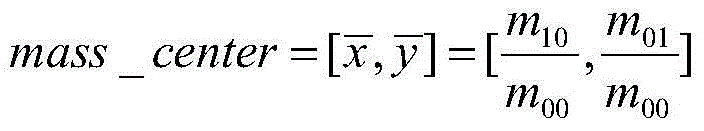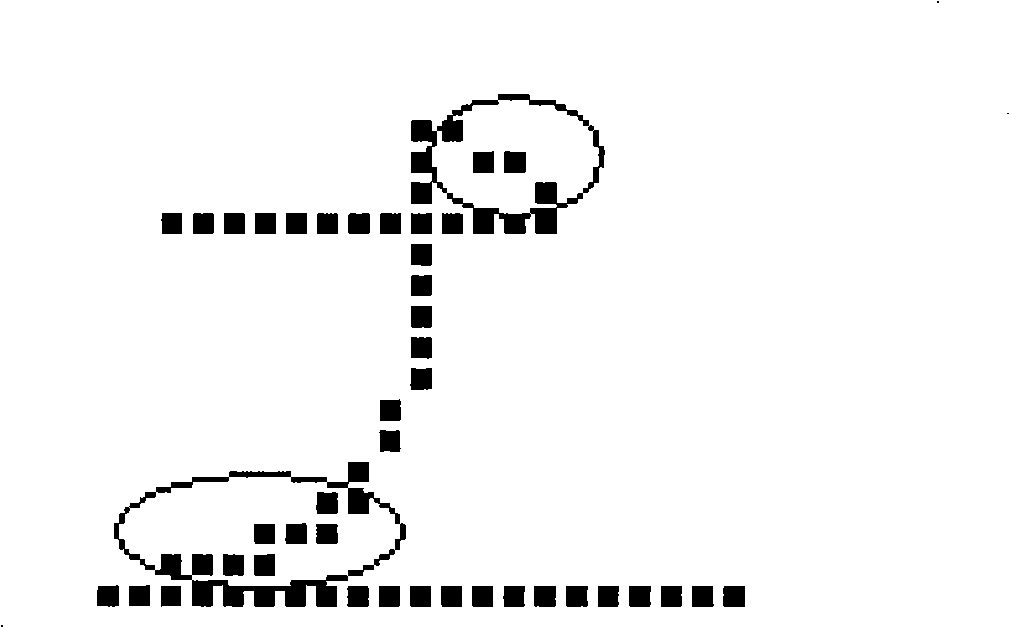Patents
Literature
403 results about "Chain code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
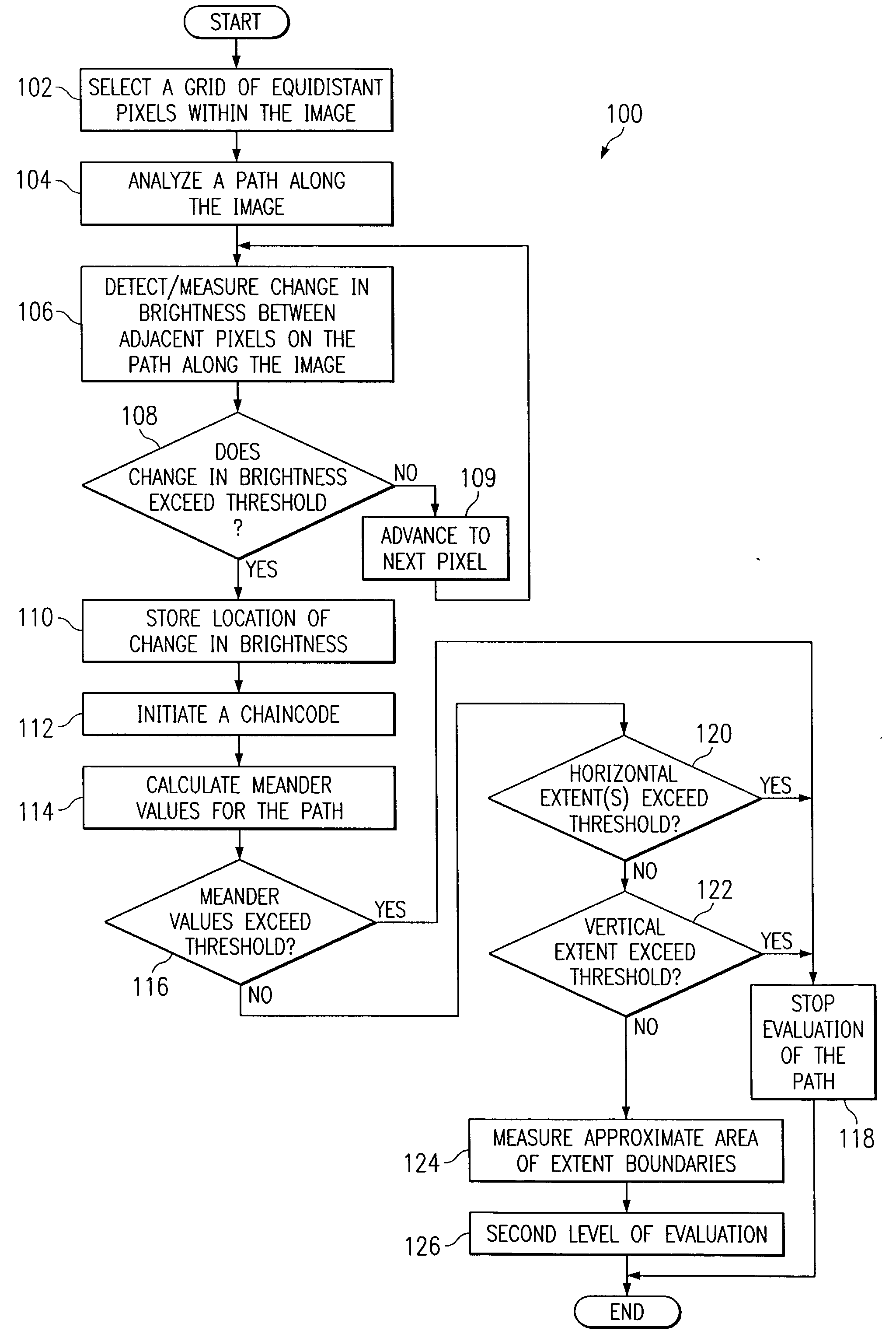
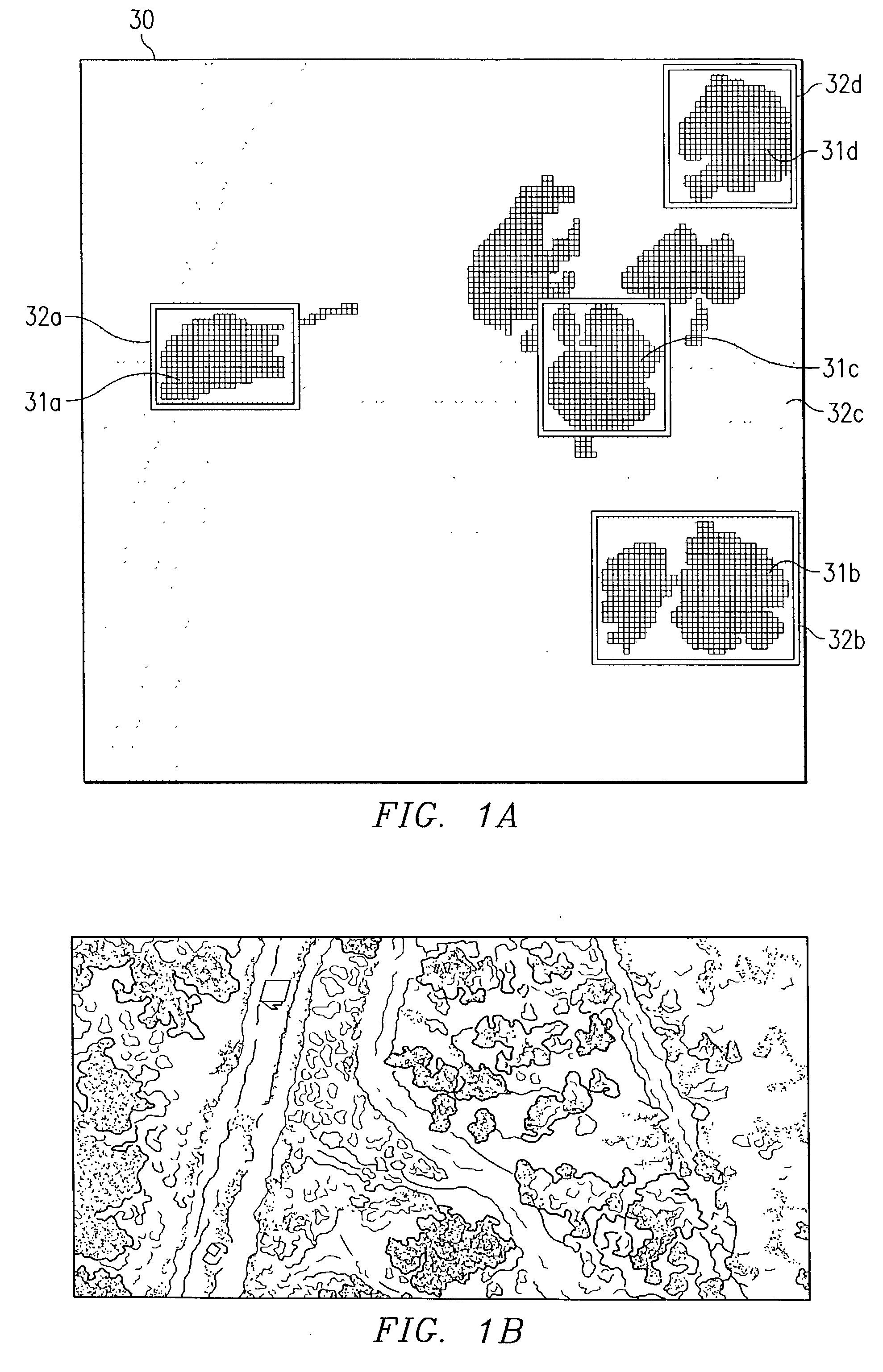
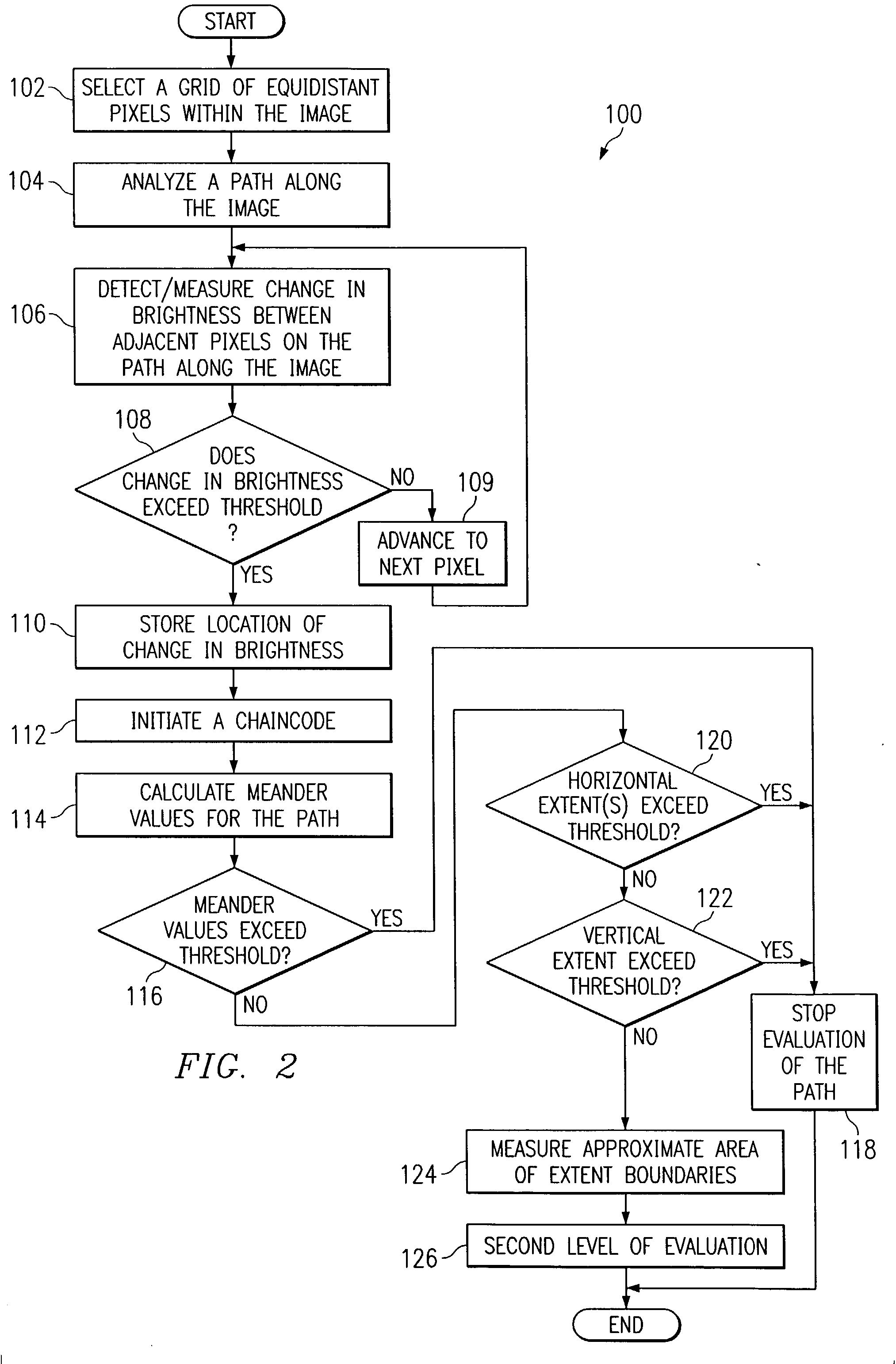
A chain code is a lossless compression algorithm for monochrome images. The basic principle of chain codes is to separately encode each connected component, or "blob", in the image. For each such region, a point on the boundary is selected and its coordinates are transmitted. The encoder then moves along the boundary of the region and, at each step, transmits a symbol representing the direction of this movement.
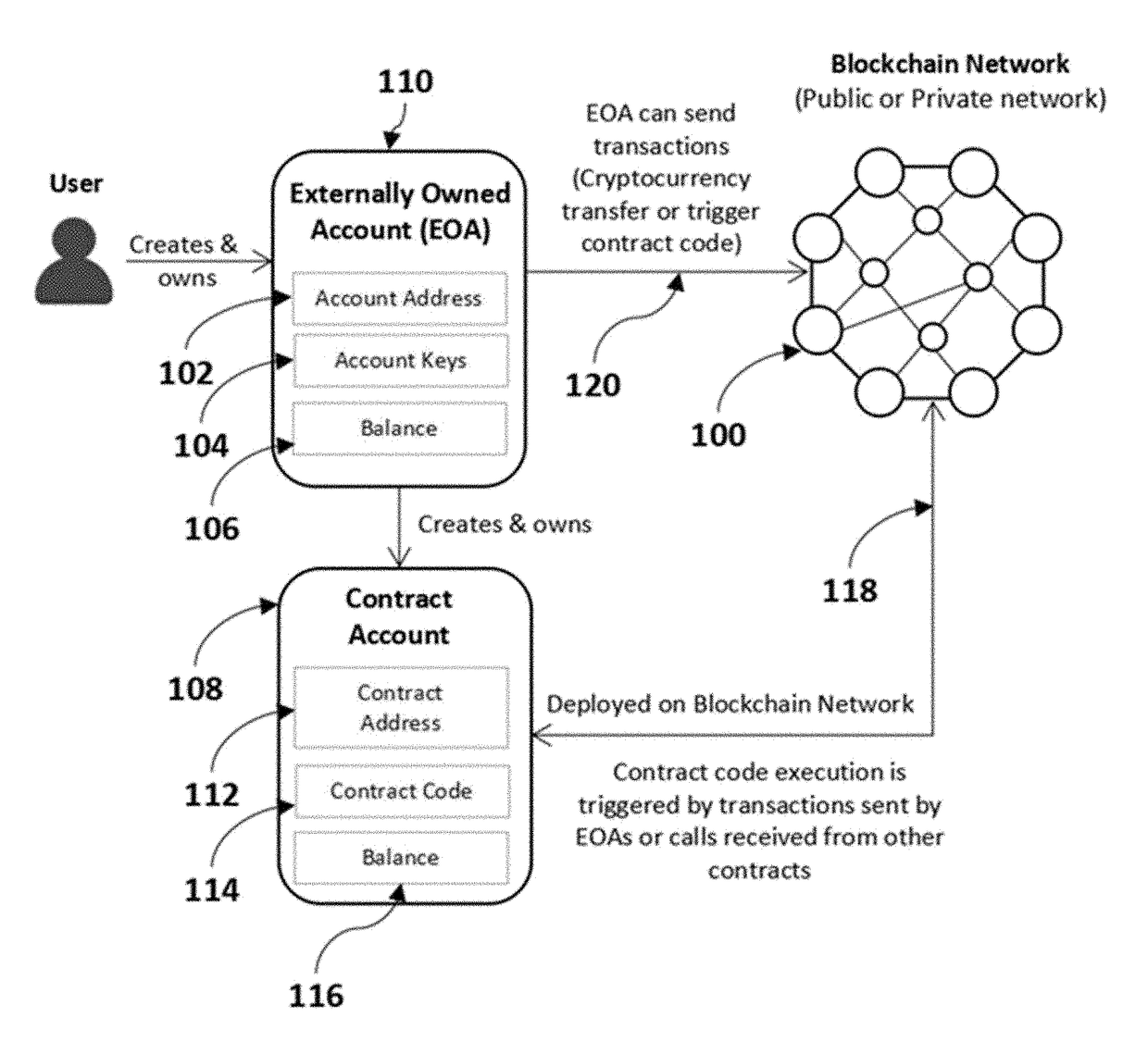
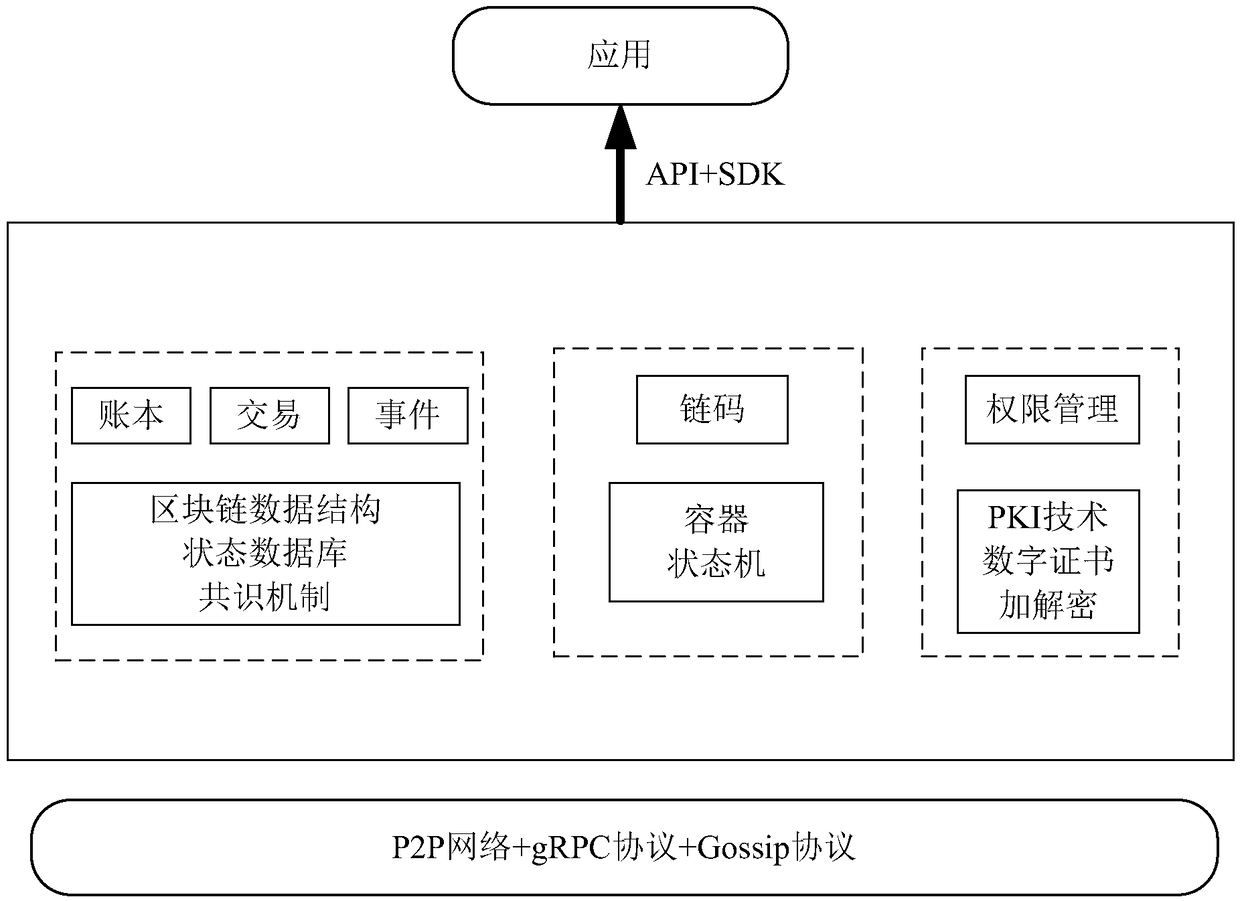
Method and System for Identity and Access Management for Blockchain Interoperability
ActiveUS20180288022A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesAccess managementChain code
A method of generating wallets for discrete blockchain networks comprising receiving a primary and a first secondary seeds, generating an enhanced hierarchical deterministic (HD) wallet, comprising deriving an enhanced parent public key and an enhanced parent private key from the primary seed, generating a first toughened HD wallet, comprising deriving a first toughened parent public and private key pair from the first secondary seed, deriving a first toughened primary child public / private key pair from a function including as inputs the first toughened parent public / private key pair, a first parent chain code, and the enhanced parent public key, and performing an identity registration and certification procedure for both the enhanced and the first toughened HD wallets. An identify of a user associated with each of the enhanced and the first toughened HD wallets is verifiable by an external blockchain network because of the identity registration and certification procedures.
Owner:MADISETTI VIJAY K
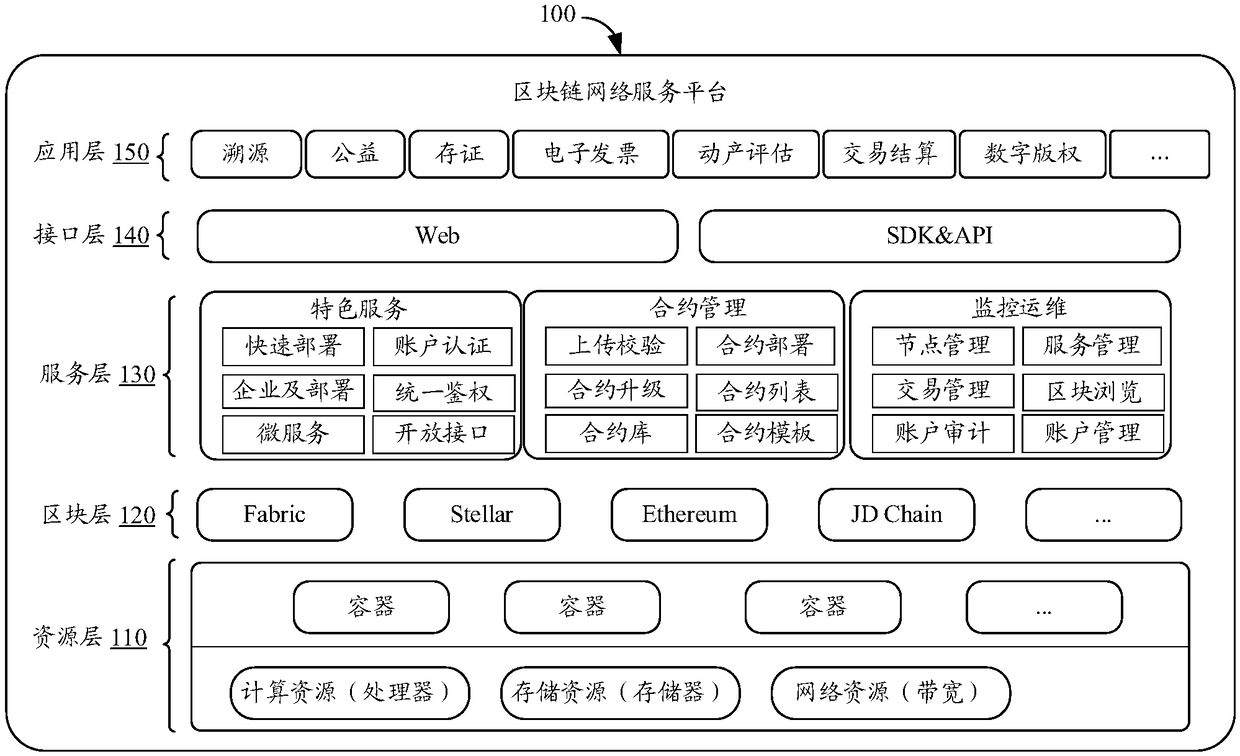
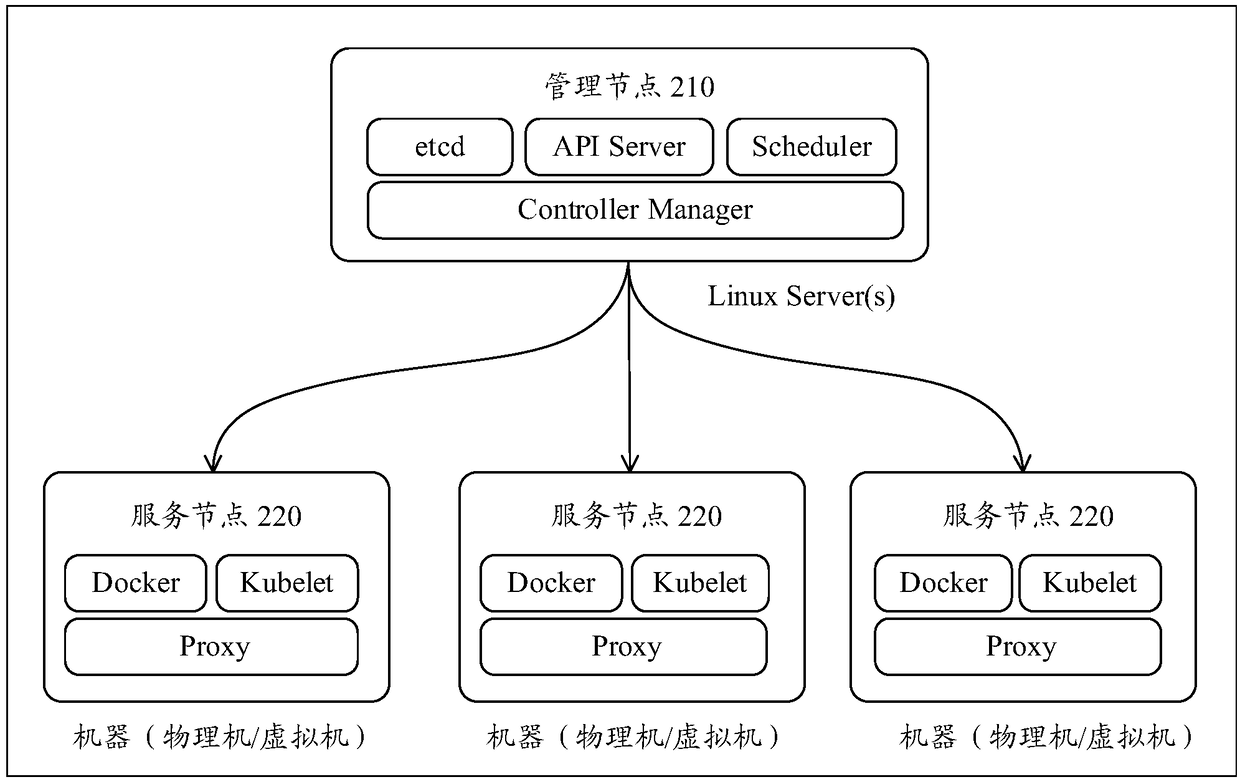
Block chain network service platform and chain code installing method thereof, storage medium
The embodiment of the invention provides a block chain network service platform and a chain code installing method, a storage medium. The method comprises the following steps: storing a chain code mirror image compiled by an endorsement node by calling a container engine, wherein the endorsement node is located at a first service node of a container cluster, and the endorsement node is deployed through a block chain network service platform; when the chain node is installed, calling an application program interface service module of a management node of the container cluster, and requesting the management node to schedule the chain code container through the endorsement node, wherein the chain code container is located at a second service node of the container cluster; and scheduling the chain code mirror image to accomplish the installing of the chain node in response to an operation of requesting to search the chain node mirror image corresponding to the chain node container from a mirror image warehouse.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
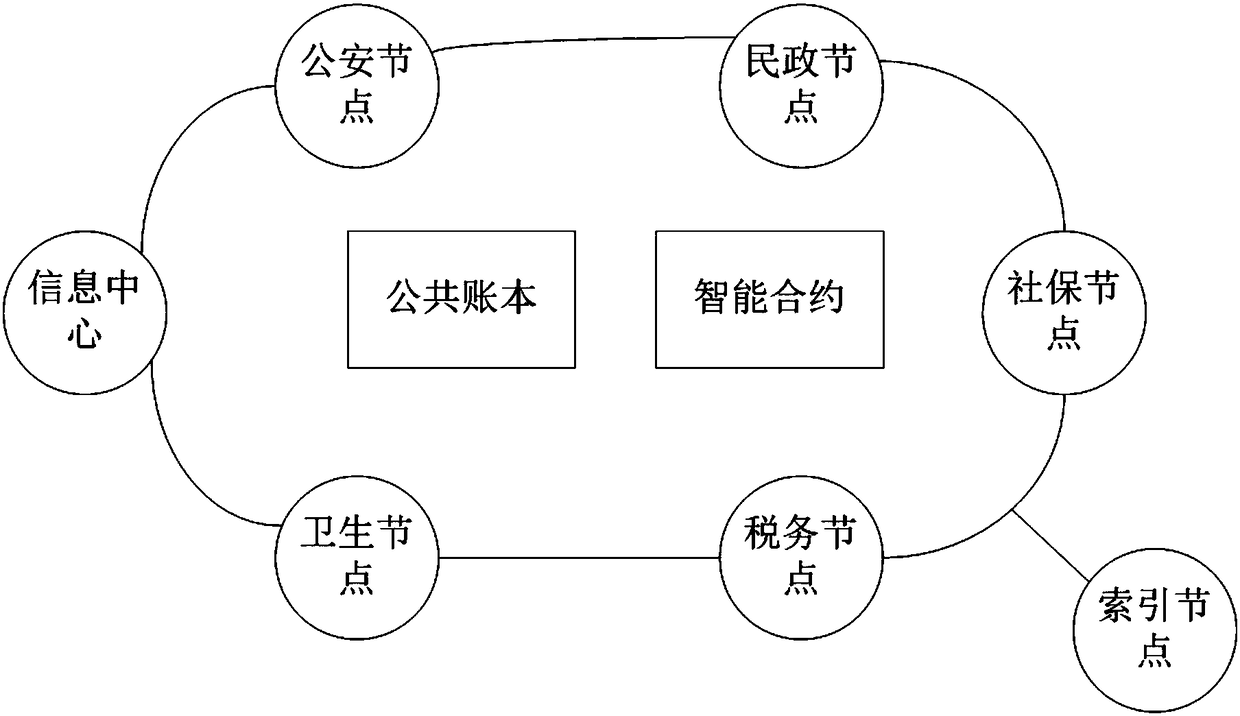
Credible government administration data sharing network system and sharing method based on block chain
InactiveCN108234457AIncrease credibilityAchieve comprehensive imputationData processing applicationsTransmissionPublic accountChain network
The invention provides a credible government administration data sharing network system based on a block chain. The system comprises service departments, an access layer and a block chain network, wherein the service departments perform information interaction with the block chain network via the access layer; the block chain network comprises a plurality of node servers, and the node servers arecorrespondingly connected with the service departments; the block chain network also comprises chain codes and a public account book based on the chain codes, wherein the public account book is used for dispersedly recording and storing the data of the service departments on the corresponding node servers, and each node server comprises the full amount of service data; the node servers are also separately connected with a management application platform used for interacting the data with the outside and a decryption server used for decrypting the data. The system provided by the invention hasthe advantages of high sate security, strong stability and high degree of opening.
Owner:苏州涞泽信息科技有限公司
System and method for analyzing a contour of an image by applying a sobel operator thereto
ActiveUS20050002570A1Accurate analysisImage enhancementImage analysisAngular degreesCharacteristic space
The present invention includes a method for analyzing an image wherein elements defining a path within a two-dimensional image are received from a prescreener. A Sobel operator may be applied to the region around each of the elements of the chain to obtain a corresponding array of gradient directions. An angle correction may be applied to any of the gradient directions that goes beyond the highest value (in radian measure; the Pi −Pi transition), to obtain an array of gradient directions free of any artificial jumps in value. The gradient direction array (Sobel chaincode) can have its bandwidth taken to determine a single number of straightness so as to identify extremely straight edges, (manmade objects) from less straight edges (natural objects). A similar process can be used to analyze contours for straight sections, which are also parallel. These two and other filters applied to the gradient array can be part of a feature suite, for feature space analysis.
Owner:NORTHROP GRUMMAN SYST CORP
A method of combining svm and lidar to detect unstructured road boundaries
ActiveCN102270301AImprove robustnessImprove accuracyCharacter and pattern recognitionSupport vector machineRadar
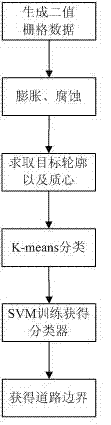
The invention discloses a method for detecting an unstructured road boundary on which an intelligent vehicle runs. The method comprises the following steps of: analyzing and processing frame data of a vehicle-mounted 64 line laser radar to obtain frame two-value raster data, expanding and corroding the frame two-value raster data to fill small space between data of barriers on the same side of a road and keeping the whole outline unchanged; solving the outline of each barrier target, storing in a chain code mode and solving the mass center of the outline; performing K means clustering on the barrier targets, wherein a sample is the solved mass center, the targets comprise barrier targets on the left side of the road and barrier targets on the right side of the road; and training by using a support vector machine (SVM), wherein the sample is the outline points of the classified barrier targets, thus obtaining a classifier, and finally solving a straight line section which describes theroad boundary according to the classifier, the maximum interval conditions and the raster data. In the method, data involved in calculation is reduced as much as possible; and the method is high in real-time property, and the solved road boundary accuracy rate is high.
Owner:NANJING UNIV OF SCI & TECH
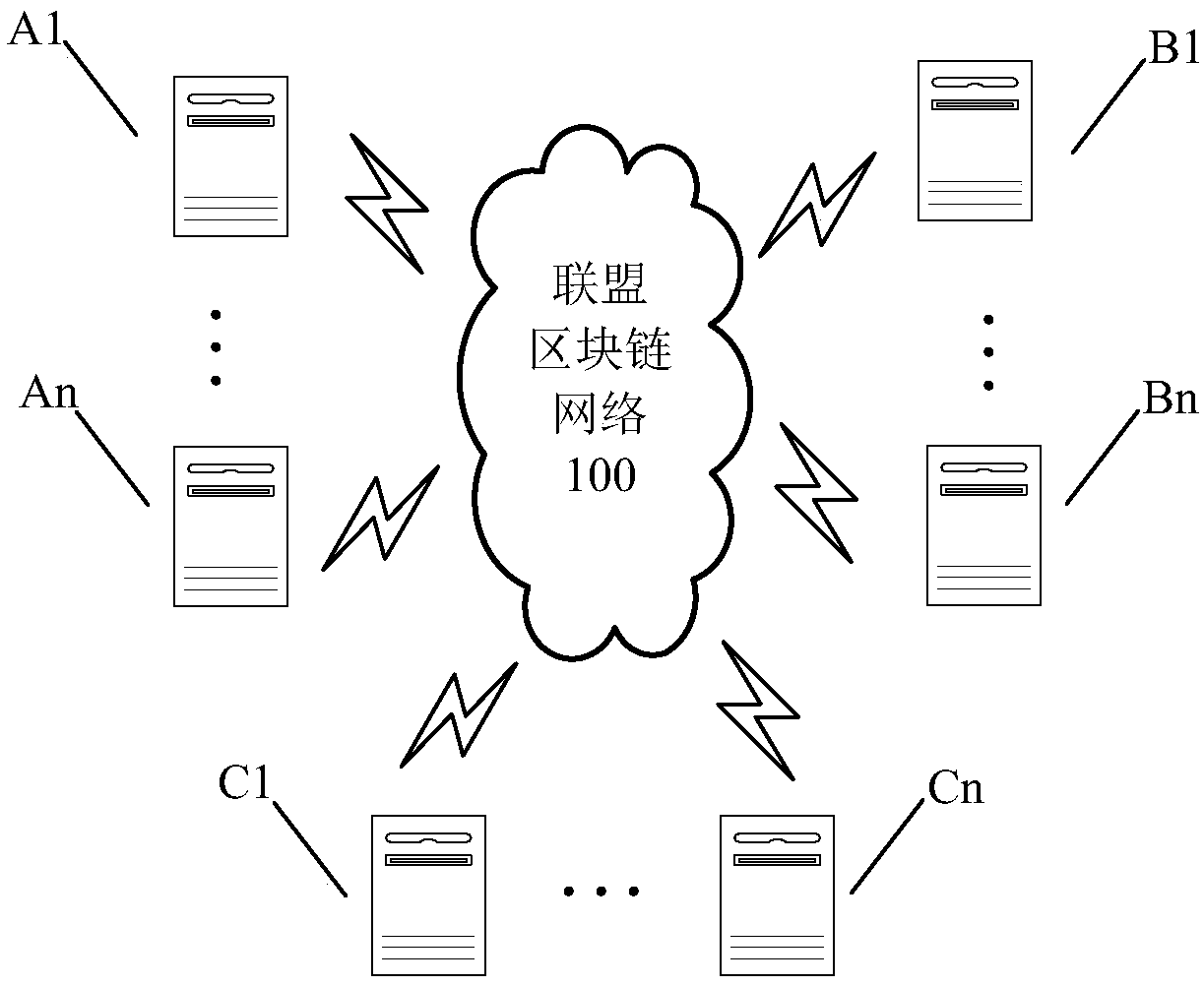
Alliance blockchain system
ActiveCN108810137AGood application requirementsUser identity/authority verificationChain codeBlockchain
The present application discloses an alliance blockchain system. A system asset chain code is added in the chain code deployed via an alliance blockchain system; a pass-through certificate circulationunit is added to maintain accounts having the pass-through certificate and achieve pass-through certificate asset management; through signature of the account, the state related to the pass-through certificate is written to a field in an account book related to the system asset chain code to achieve pass-through certificate circulation, thereby expanding the application requirement of the alliance blockchain system.
Owner:西安纸贵互联网科技有限公司
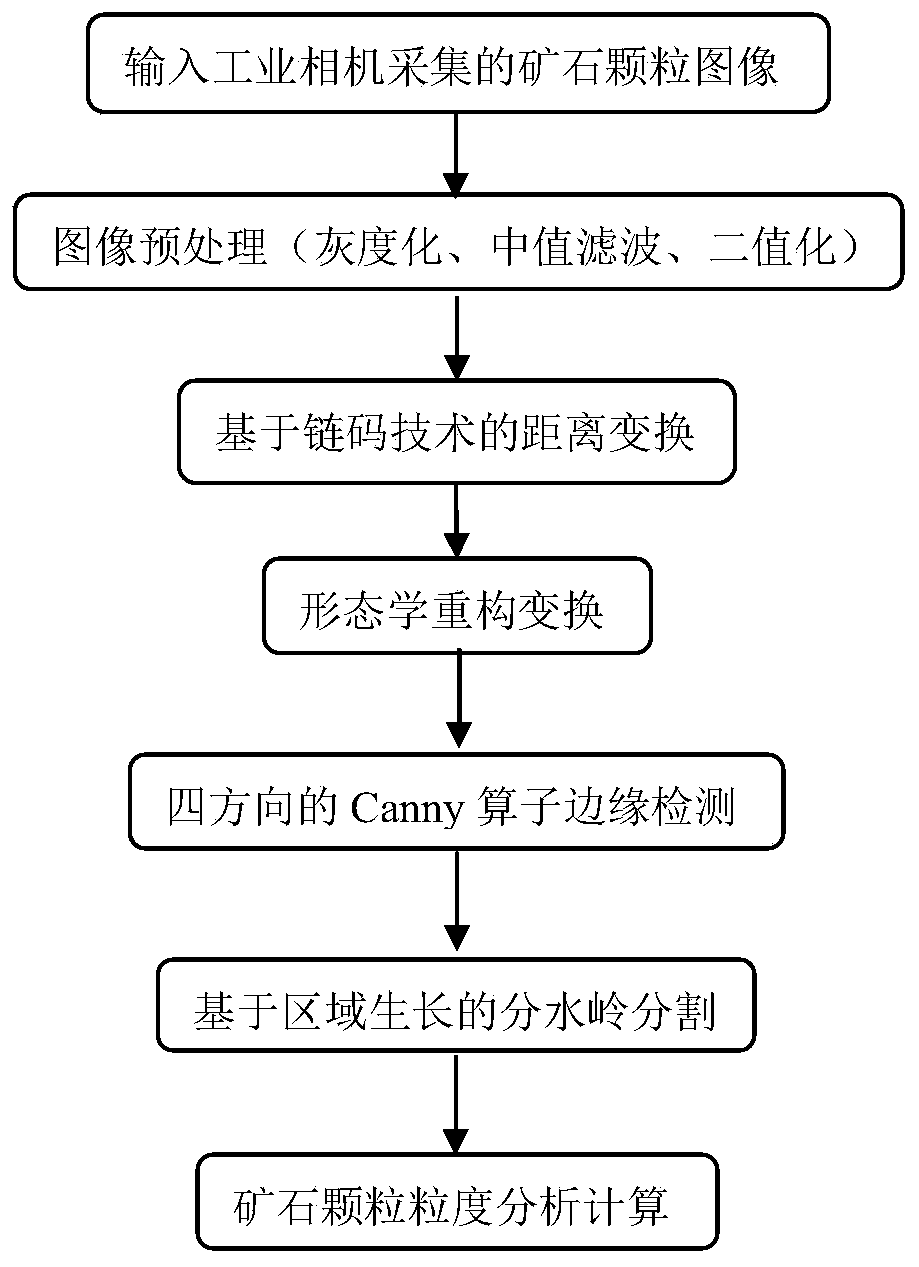
Ore image granularity detection algorithm based on image processing technology
ActiveCN111047555AHigh yieldLow failure rateImage enhancementImage analysisImaging processingImage segmentation algorithm
The invention belongs to the technical field of ore granularity detection and analysis in mine development, and particularly relates to an ore image granularity detection algorithm based on an image processing technology. The algorithm is characterized by comprising the following steps: (1) completing acquisition of an ore image by using an industrial camera; (2) preprocessing the collected ore image, and sequentially performing image graying, median filtering denoising and binarization processing; (3) performing distance transformation and morphological reconstruction on the obtained binarized image by applying a chain code technology; (4) adopting an ore image segmentation algorithm combining Canny operator edge detection and a watershed algorithm based on region growth; and (5) analyzing and calculating the ore granularity by utilizing the obtained ore parameters and the granularity model. According to the invention, high-precision and high-accuracy granularity detection is obtainedthrough accurate ore image segmentation, the failure rate of the crusher is reduced, and the ore yield is increased.
Owner:ANSTEEL GRP MINING CO LTD
Sparse-coding license plate character recognition method based on shape and contour features
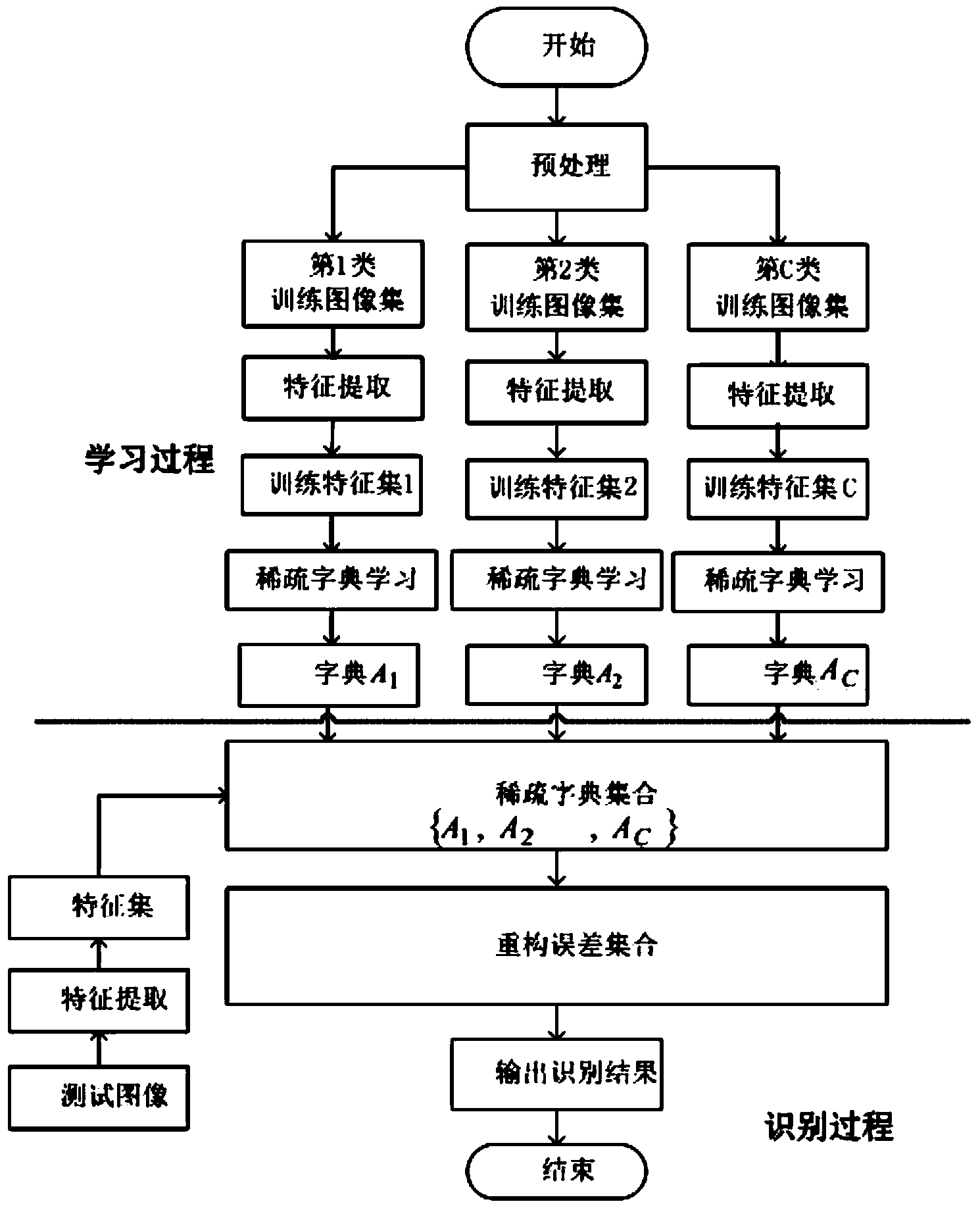
InactiveCN103761531AEasy to identifyImprove scalabilityCharacter and pattern recognitionDictionary learningFeature set
The invention provides a sparse-coding license plate character recognition method based on shape and contour features. The method comprises a sparse dictionary learning process and a dictionary-utilizing character recognition process. The method mainly comprises the following steps: firstly, a training image set is formed by pre-processing standard license plate images; secondly, feature extraction is performed on the training image set, so that a training feature set is formed; thirdly, a sample region feature and a chain code histogram feature of the raining feature set are introduced into an objective function, sparse dictionary learning is performed on license plate character samples off line to obtain dictionaries corresponding to all characters, and a dictionary set is formed by all the dictionaries; fourthly, feature extraction is performed on test sample data; fifthly, test sample features are subjected to sparse representation in each dictionary, and license plate character recognition is performed through reconstruction errors. Since region features and boundary features of character images are considered at the same time, the sparse-coding license plate character recognition method is a fast and robust license plate character recognition method.
Owner:XIAN UNIV OF TECH
Local shape matching method based on outline random sampling
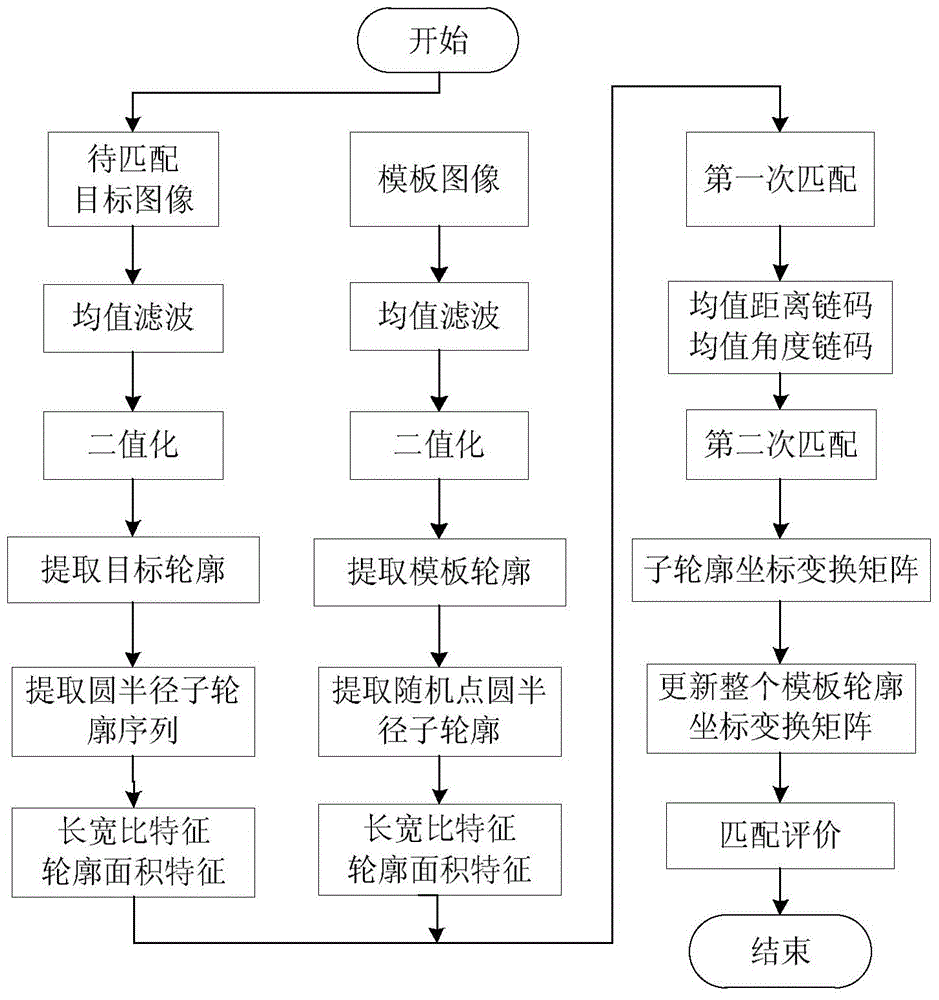
ActiveCN104463866AImprove computing efficiencyFast and reliable matching resultsImage analysisCharacter and pattern recognitionShape matchingMatching methods
The invention discloses a local shape matching method based on outline random sampling. The local shape matching method based on outline random sampling comprises the steps that all sub-outline sequences of a target outline to be matched and random sub-outlines on a template outline are extracted through a geometric round radius method; the length and width ratios of the minimum rotation bounding rectangles and the outline area features of a target sub-outline and the random sub-outlines of the template are extracted, and primary matching is conducted; mean value distance chain code and mean value angle chain code features, based on angle classification, of the sub-outlines of the outline points obtained after primary matching are extracted; secondary matching is conducted between the chain code features obtained through the random sub-outlines of the template and the sub-outlines obtained after primary matching, so that a small number of optimal matched outlines are obtained; a coordinate conversation matrix of the random sub-outlines of the template and the matched sub-outlines are calculated, and the outline of the whole template is projected to the target outline through the conversation matrix; the coordinate conversation matrix of the sub-outlines is updated; and the optimal matched outline is recognized. By the adoption of the local shape matching method, a matched result can be rapidly and reliably provided, the image registration calculation efficiency is high, and the adaptability is high.
Owner:WUXI UNICOMP TECH
Key derivation method and device applicable to digital currency
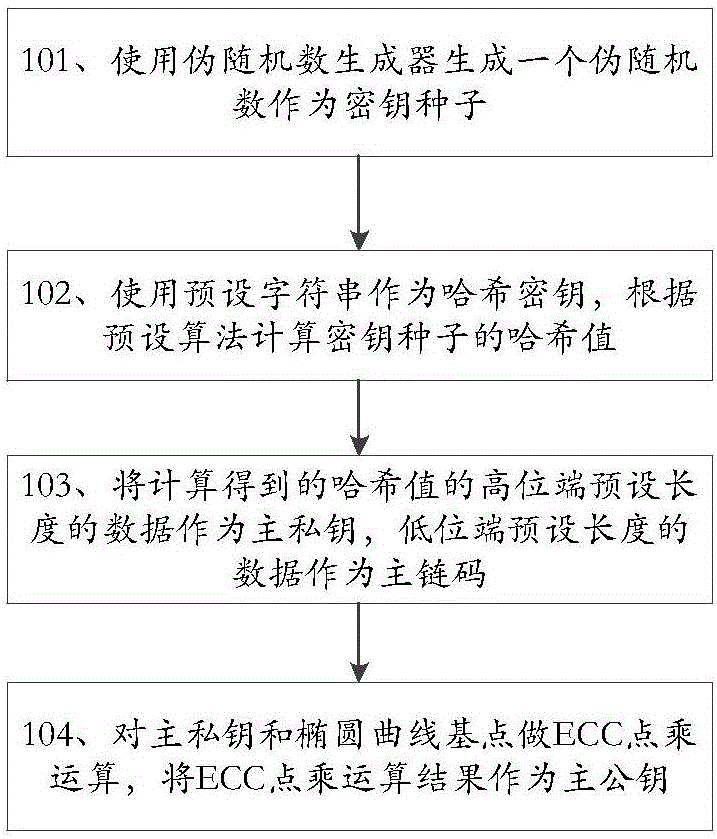
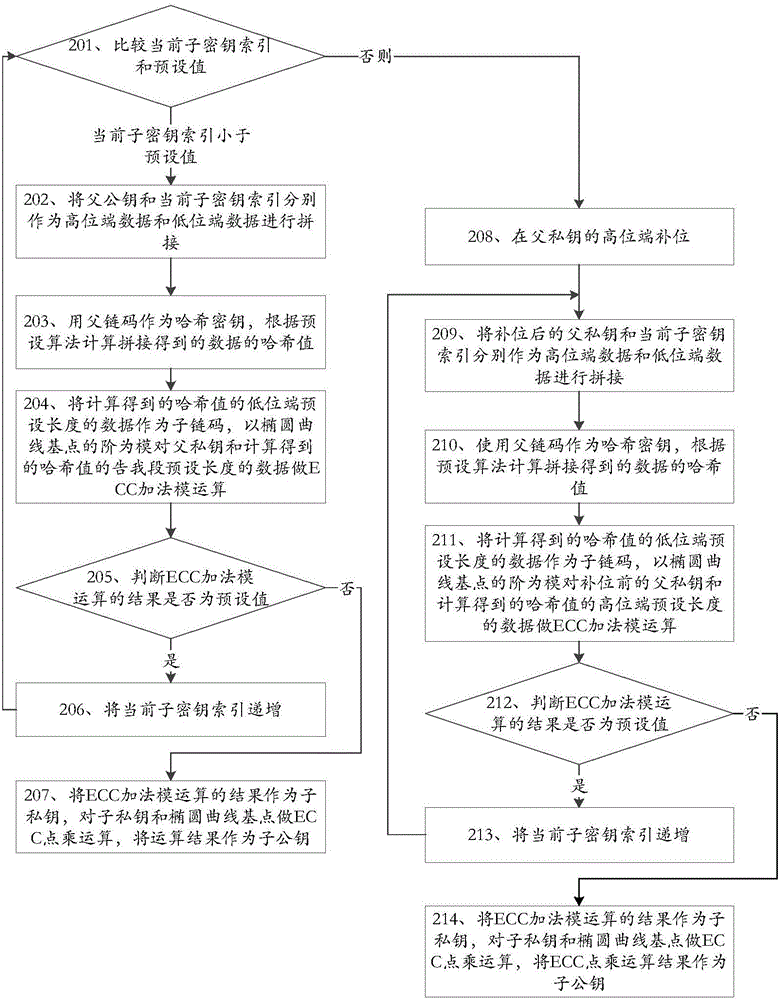
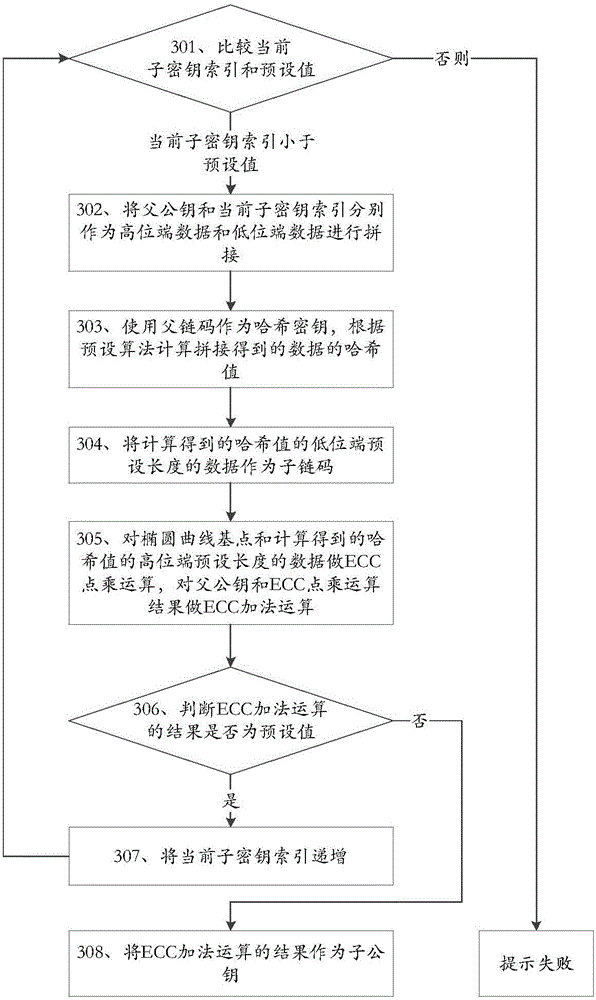
ActiveCN106411506AImprove securityAvoid lostKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital currencyRelationship - Father
The invention discloses a key derivation method and device applicable to digital currency and belongs to the field of information security. The key derivation method applicable to digital currency comprises the steps of splicing indexes of father public keys and sub-key indexes according to a sequence; using father chain codes as Hash keys, and calculating Hash values of spliced data based on a preset algorithm; obtaining sub-chain codes based on the Hash values; performing ECC (Elliptic Curve Cryptography) addition modular operation on captured residual data; if the operation results are not preset values, regarding the operation results as sub-private keys; and performing ECC point multiplication operation on the sub-private keys to obtain sub-public keys. The key derivation method and device applicable to digital currency have the beneficial effects that backup of key seeds rather than all the keys is required as all the keys can be derived based on the key seeds, the backup volume is small, and loss caused by key damage also can be avoided.
Owner:FEITIAN TECHNOLOGIES
Extraction method for dimension shape characteristics of profiled fiber
InactiveCN101487838AAutomatically obtain classification statistics resultsImprove accuracyImage analysisCharacter and pattern recognitionEngineeringImage segmentation
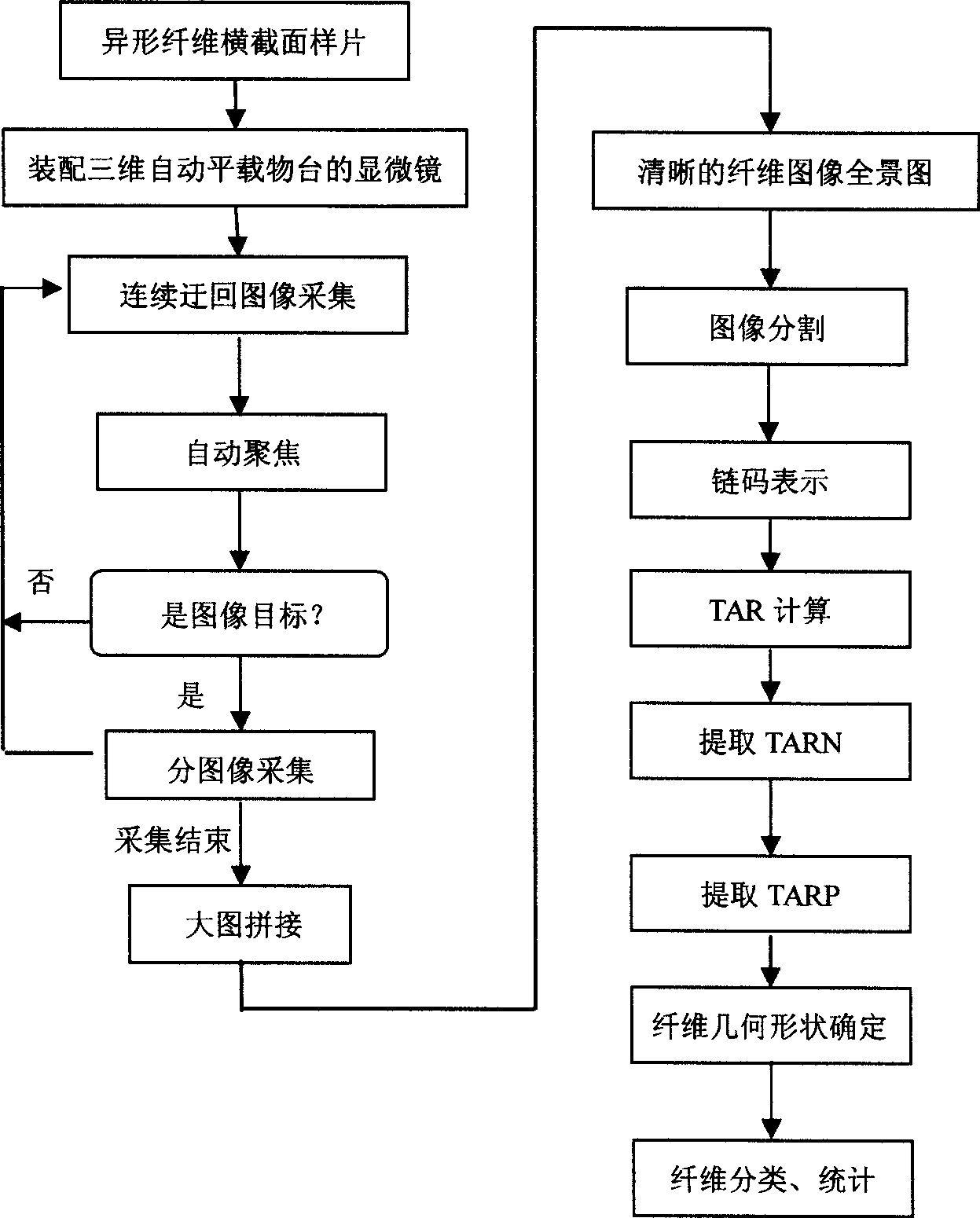
The invention relates to a method for extracting dimensional shape characteristics of profiled fibers; the stepper motor in XYZ direction of an automatic loading table is controlled through a series port to realize the mobile control in horizontal and vertical directions to cause an optical microscope to work in an optimum focusing state. The extracting method comprises the following steps: giving 'cross-sectional samples of the profiled fibers' and 'microscopes for assembling three-dimensional automatic loading table' to judge through 'continuous indirect image acquisition' and 'automatic focusing'; if not, returning to the 'continuous indirect image acquisition'; if yes, going to 'partial image acquisition', then returning to the 'continuous indirect image acquisition' until the partialimage acquisition is ended; going to 'big image splicing'; obtaining 'clear fiber image panoramagram'; carrying out 'image segmentation', 'chain code representation', 'TAR calculation', 'TARN extraction', 'TARP extraction', and 'fiber geometrical shape determination' on the acquired images; and at last, carrying out 'fiber classification and statistics'.
Owner:DONGHUA UNIV
Fast target positioning method and device
InactiveCN107657639AAccurate segmentationHigh precisionImage enhancementImage analysisMathematical morphologyChain code
The invention discloses a fast target positioning method and device. The method comprises the following steps: according to an input original image, obtaining a binary image; according to the binary image, carrying out target boundary tracking to obtain a target contour, and obtaining a bounding rectangle of the target contour; and according to target characteristics, carrying out target screeningand positioning. The binary image is obtained by carrying out multi-threshold segmentation, denoising and hole filling of the original image, wherein the denoising and hole filling processing is finished through expansion, corrosion, opening and closing operation of mathematical morphology; the boundary tracking is realized through 4-neighborhood or 8-neighborhood chain code tracking; the targetscreening is realized based on a plurality of constraint conditions, wherein the plurality of constraint conditions comprise an aspect ratio constraint, a maximum and minimum area constraint, a regiongray average value constraint and a heel landing constraint; and the positioning comprises acquisition of azimuth and distance. The fast target positioning method and device are applied to the infrared image field, is high in operation efficiency and accurate in analysis.
Owner:WUHAN GUIDE SENSMART TECH CO LTD
Automatic separating method for X type overlapping and adhering chromosome
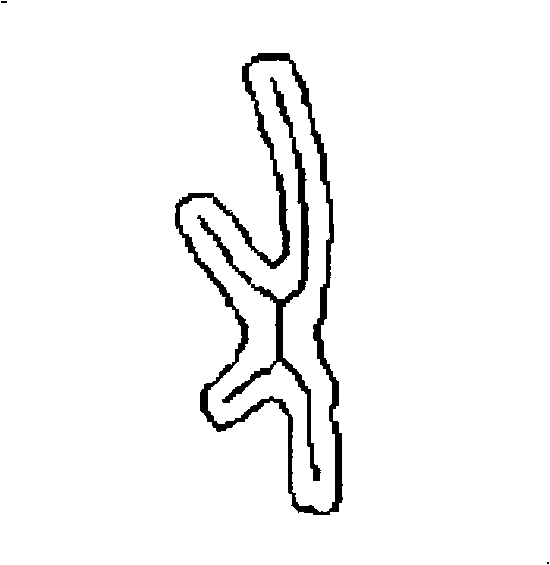
InactiveCN101403743AEffective segmentationHigh degree of automationImage analysisMaterial analysis by optical meansGradient operatorsChain code
The invention provides a method used for automatically cutting X-typed overlapped and conglutinated chromosomes, comprising the steps as follows: step 1: binarization segmentation processing is carried out to a chromosome image so as to obtain a binarization template; step 2: the X-typed overlapped chromosome image is extracted from the template, the chromosome profile is obtained by a gradient operator and treated with Freeman chain coding so as to obtain a boundary chain code; step 3: the overlapped chromosome is processed by thinning algorithm so as to extract a single-pixel framework and determine the central point of an overlapping area; and step 4: the distance from the profile pixel point to the central point of the overlapping area after the Freeman chain code is calculated; four profile concave points which are not adjacent to each other are selected as cutting points so as to divide the profile into two profile sets; and the segmented chromosome profile sets are used for automatically completing the operation of segmenting the chromosome grey images, thus obtaining the automatic segmenting result of the X-typed overlapped and conglutinated chromosome. The method has quick and effective cutting operation and greatly reduces the working quantity and difficulty of manpower segmentation.
Owner:GUANGDONG VTRON TECH CO LTD
Hand gesture recognition method based on switching Kalman filtering model
InactiveCN104050488AThe recognition result is accurateReduce recognition errorsImage enhancementCharacter and pattern recognitionPattern recognitionSkin color
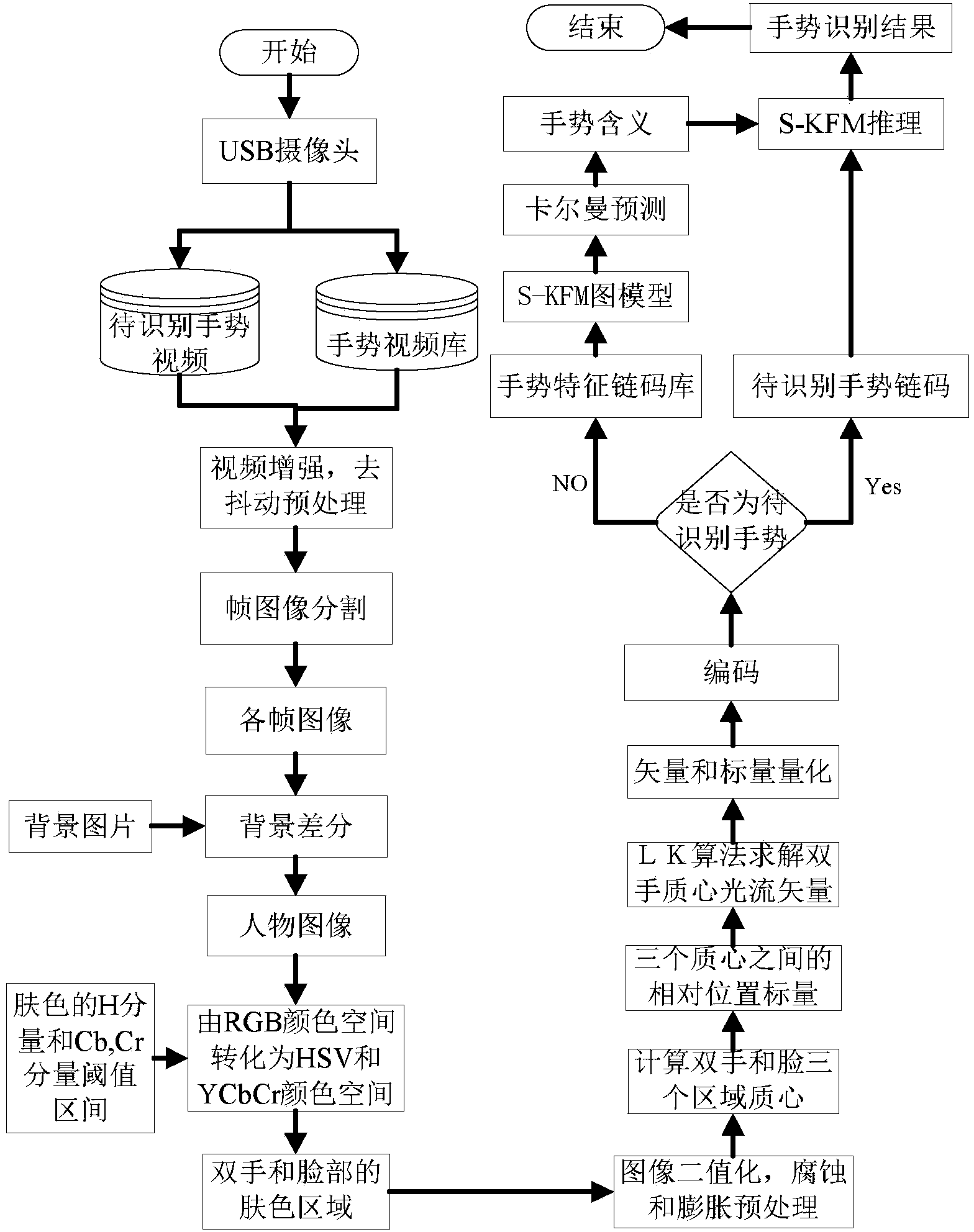
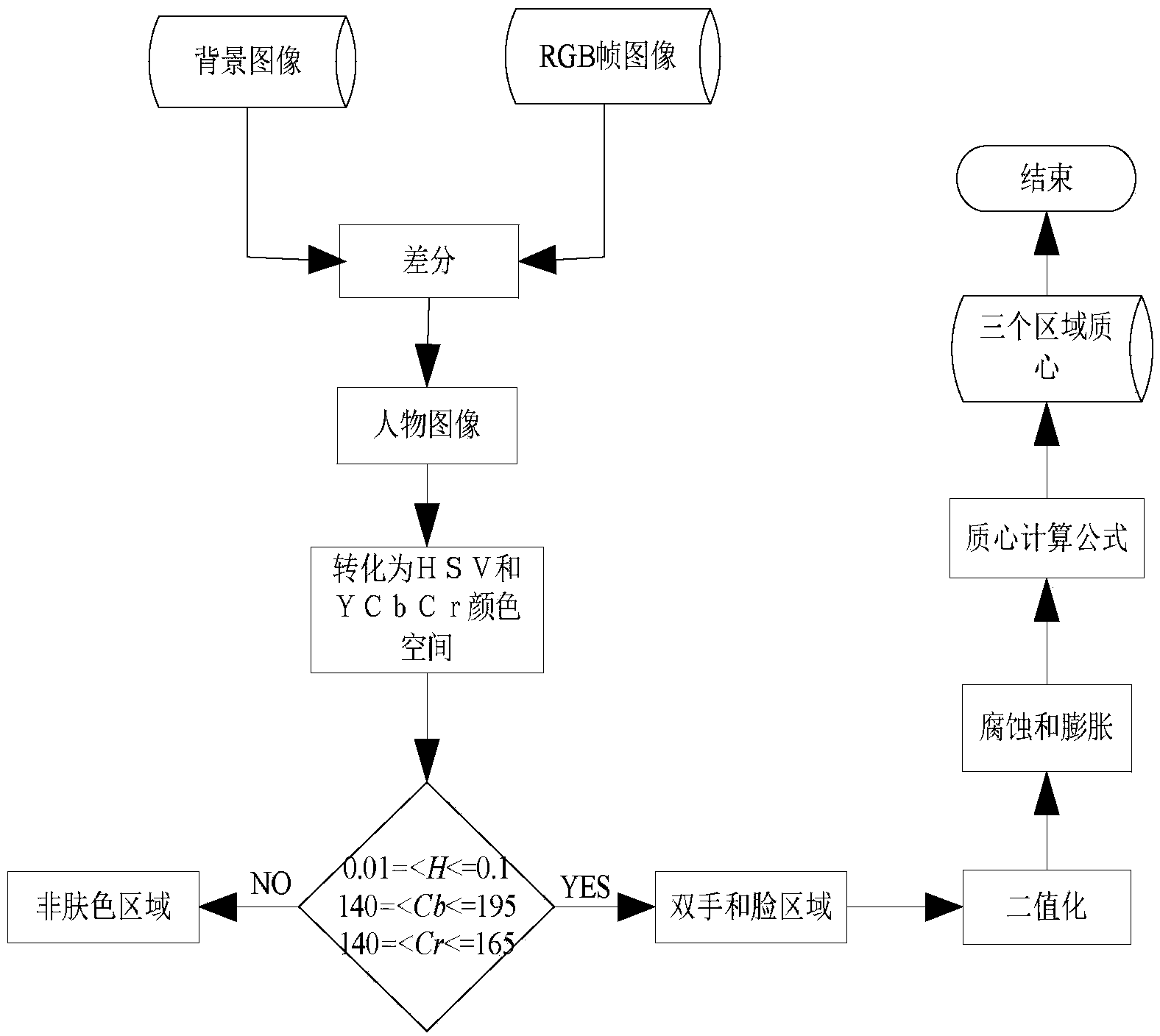
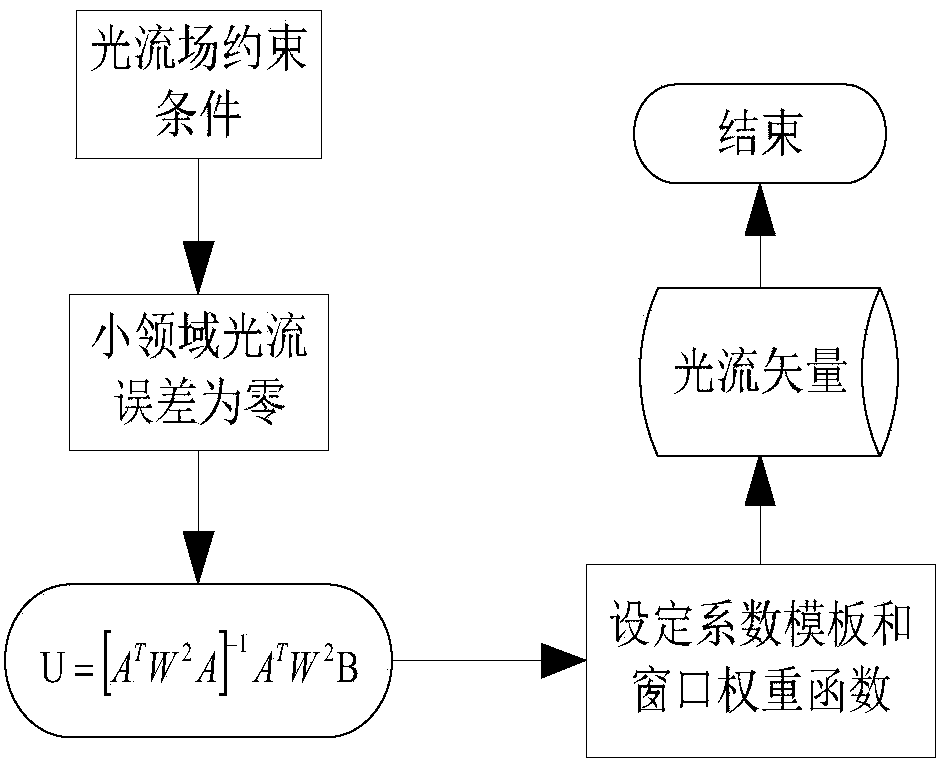
The invention discloses a hand gesture recognition method based on a switching Kalman filtering model. The hand gesture recognition method based on a switching Kalman filtering model comprises the steps that a hand gesture video database is established, and the hand gesture video database is pre-processed; image backgrounds of video frames are removed, and two hand regions and a face region are separated out based on a skin color model; morphological operation is conducted on the three areas, mass centers are calculated respectively, and the position vectors of the face and the two hands and the position vector between the two hands are obtained; an optical flow field is calculated, and the optical flow vectors of the mass centers of the two hands are obtained; a coding rule is defined, the two optical flow vectors and the three position vectors of each frame of image are coded, so that a hand gesture characteristic chain code library is obtained; an S-KFM graph model is established, wherein a characteristic chain code sequence serves as an observation signal of the S-KFM graph model, and a hand gesture posture meaning sequence serves as an output signal of the S-KFM graph model; optimal parameters are obtained by conducting learning with the characteristic chain code library as a training sample of the S-KFM; relevant steps are executed again for a hand gesture video to be recognized, so that a corresponding characteristic chain code is obtained, reasoning is conducted with the corresponding characteristic chain code serving as input of the S-KFM, and finally a hand gesture recognition result is obtained.
Owner:XIAN TECHNOLOGICAL UNIV
Hand-written recognition method based on assembled classifier
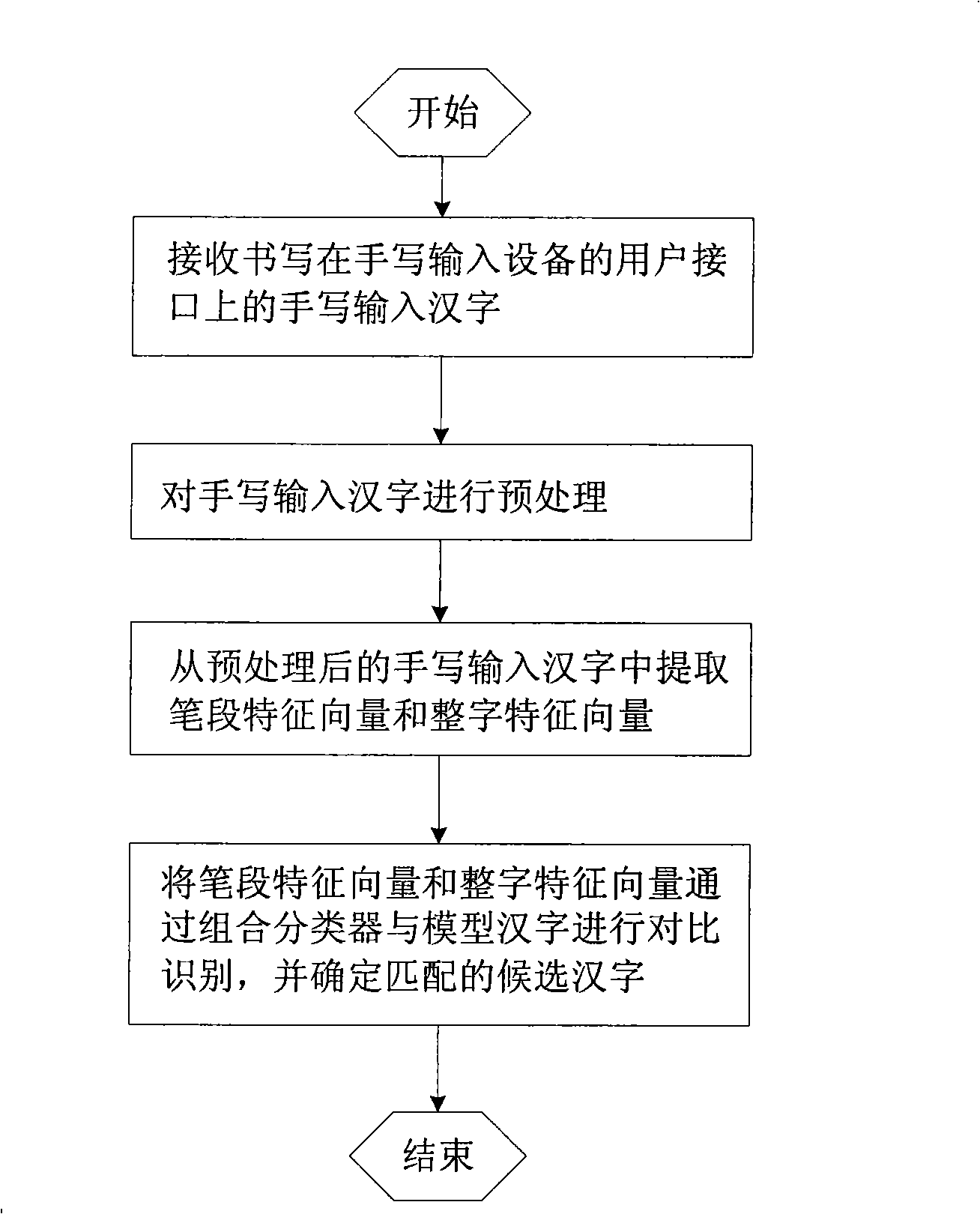
InactiveCN101290659AAvoid errorsEasy to identifyCharacter and pattern recognitionChinese charactersNoise removal
The invention discloses a method for identifying handwritten Chinese characters based on a combination classifier, which has the advantages that after hand-inputted Chinese characters collected undergo treatments of smoothed filter, noise removal, resampling and data linear normalization, the characters undergo the peeling-off points removal treatment, which removes points of stroke segments which deviate from hand-inputted Chinese characters, which exceed the set threshold value, thereby facilitating the extraction of turning points of strokes and the correct input of stroke segments; setting up basic stroke segment types and corresponding parameter characteristics is to define separating points for separation according to time intervals of sampling points of hand-inputted Chinese characters while sampling; when the directional deviation of a stroke segment is in the range of the set angle threshold, the stroke segment is automatically corrected; a separating connection relation is built, and as for stroke segments which are connected in fact, but separated due to writing habits, the stroke segments are treated as connected stroke segments after being identified, thereby better differentiating a plurality of similar Chinese characters; by calculating Freeman chain codes, hand-inputted Chinese characters can be conveniently identified by using the whole character identification classifier.
Owner:NINGBO SUNRUN ELEC & INFO ST&D
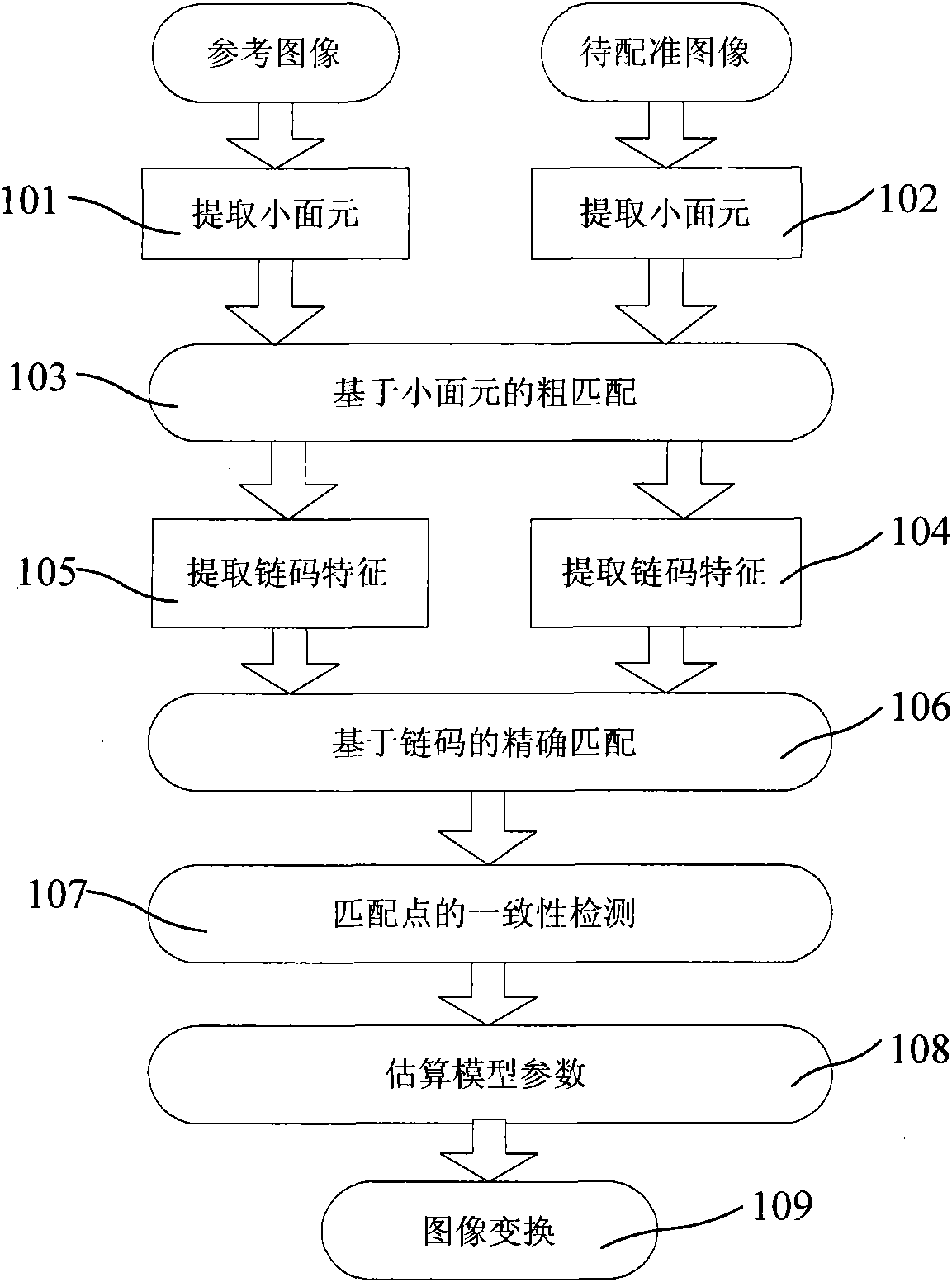
Optical remote sensing image registration method
InactiveCN101847258AReduce complexityEnhance matching strengthWave based measurement systemsImage analysisTransformation parameterChain code
The invention discloses an optical remote sensing image registration method which is characterized by the following steps that: first a small surface element is extracted, pretreated and matched at one step so as to more effectively extract a closed border and reduce the algorithm complexity simultaneously; second, boundary correspondence relationship is established according to the similar function of a closed border chain code and a region invariant moment matching strategy; and finally the center of mass of a matched area, i.e. a matching point is extracted for consistency detection, and an affine transformation parameter is estimated for image registration. The optical remote sensing image registration method improves the defect that the prior art is based on a chain code registration method, improves the registration precision and time efficiency, and can meet the automatic registration requirements of optical remote sensing images.
Owner:陈贤巧 +2
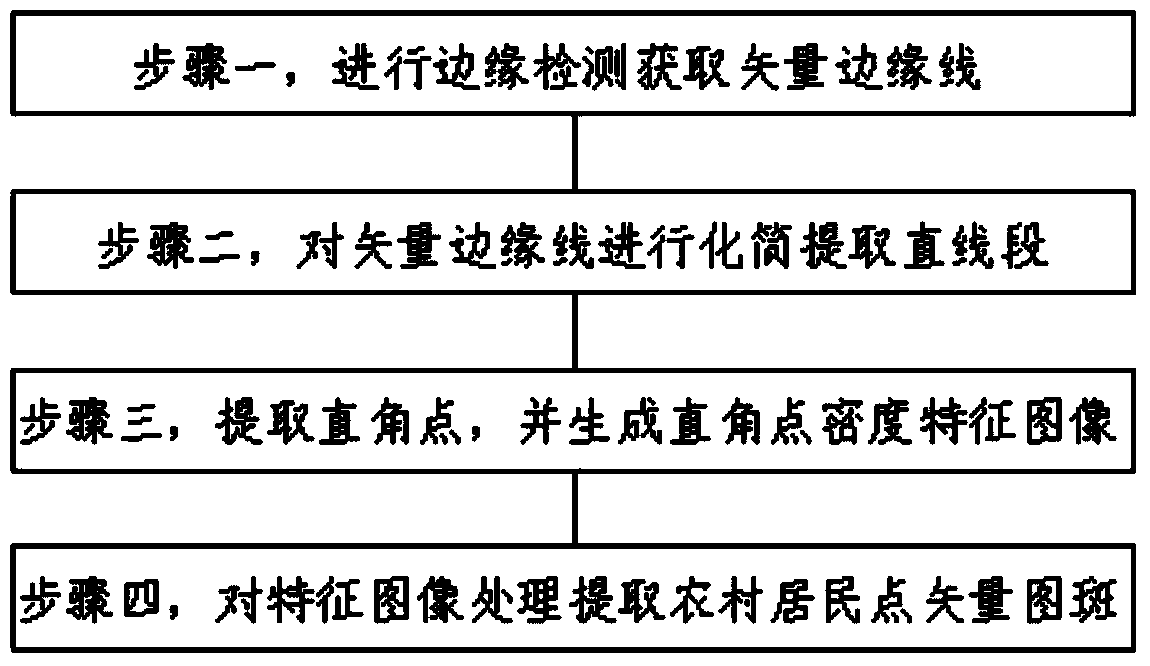
Rural resident point information extraction method based on high-resolution remote-sensing image
InactiveCN104182754AEasy extractionSimple extraction methodCharacter and pattern recognitionOtsu's methodRural settlement
The invention discloses a rural resident point information extraction method based on a high-resolution remote-sensing image. The rural resident point information extraction method comprises the following steps: firstly, carrying out Canny edge detection on the high-resolution remote-sensing image, and obtaining a vector edge line through chain code tracking; then, carrying out Douglas-Peucker abbreviation on a vector edge to extract straight-line segments, and rejecting shorter straight-line segments and keeping longer straight-line segments according to length constraints; secondly, according to adjacency relation between the straight-line segments and included angle constraints, extracting straight angle points, calculating the density characteristics of the straight angle points within a certain space region range, and generating a straight angle point density characteristic image, wherein the characteristic image and the input high-resolution remote-sensing image have same spatial range and spatial resolution; and finally, carrying out binarization processing on the density characteristic image by utilizing Otsu, extracting rural resident point vector pattern spots through connected component analysis so as to extract rural resident point information. Precision and effects are improved, and robustness and universality are better.
Owner:SHANDONG LINYI TOBACCO
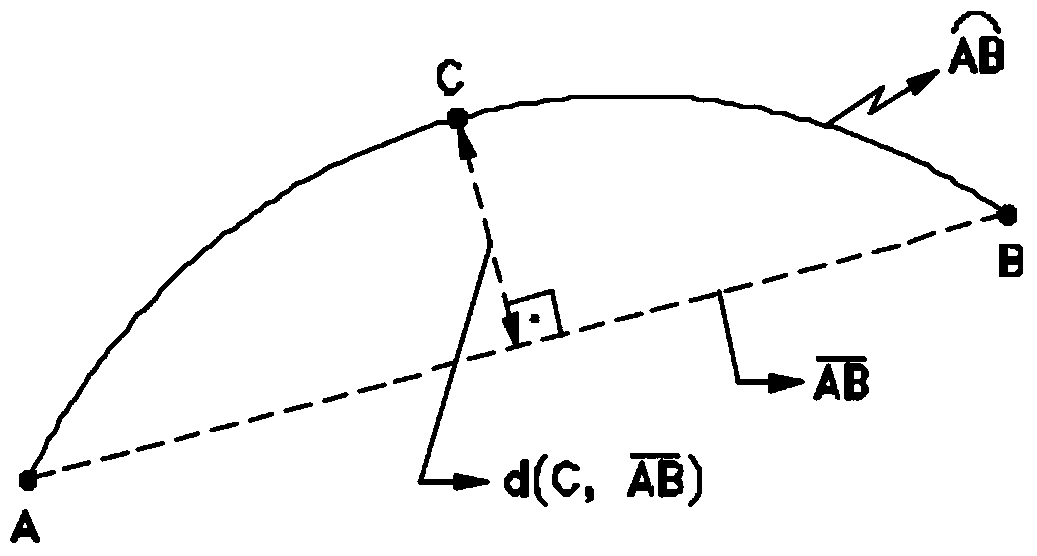
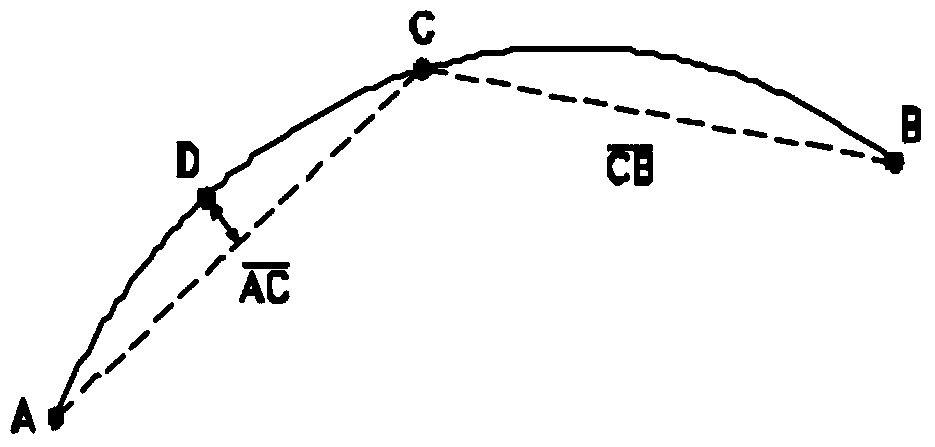
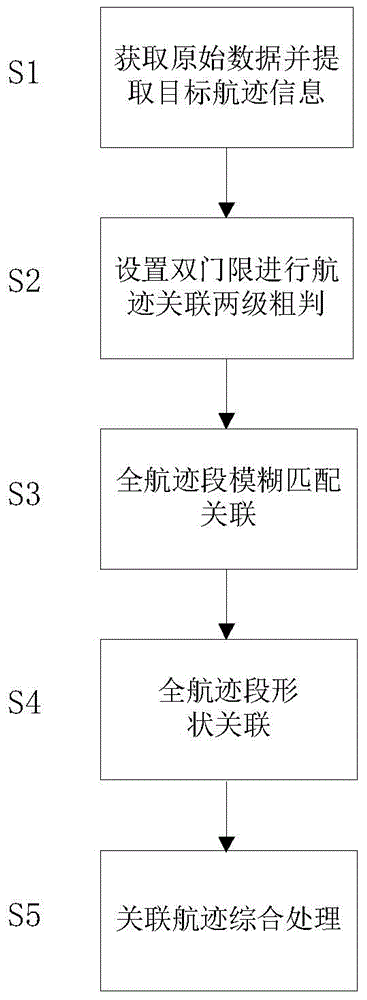
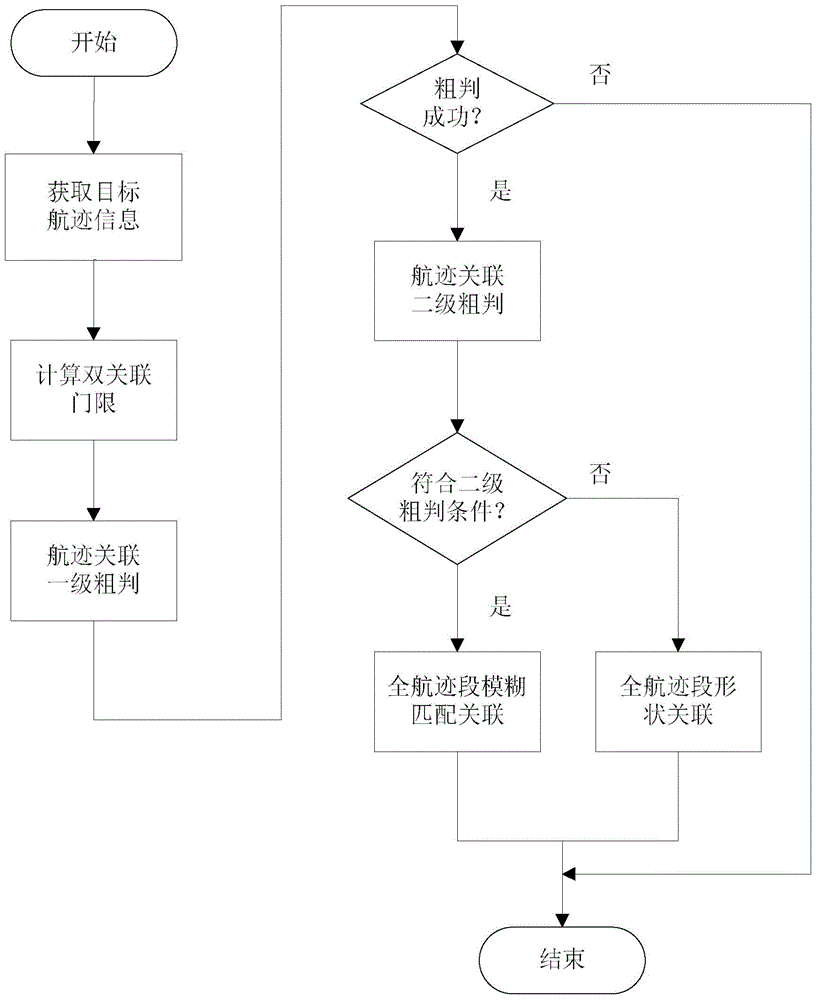
Trend message and radar target state information whole-track data correlation method
ActiveCN104931960AExpress uncertaintyAvoid noise and other disturbancesNavigation instrumentsRadio wave reradiation/reflectionPaired DataRadar
The invention discloses a trend message and radar target state information whole-track data association method comprising the following steps: extracting track information from trend message and radar target state information; using a double-association threshold rule including a fuzzy association threshold and a shape association threshold to make coarse association judgment on whole-track data, forming a target association track pair of the trend message and radar target state information, and determining the mode of subsequent track data association processing according to the result of coarse judgment; for track pair data in line with the fuzzy association threshold, constructing a fuzzy factor according to information corresponding to the target track point location, and then allocating a weight according to the degree of importance of the fuzzy factor, and carrying out fuzzy comprehensive treatment to realize whole-track association; for track pair data in line with the shape association threshold, using a chain code to describe the track shape, and completing whole-track shape association through chain code matching; and finally, carrying out comprehensive association track processing to realize association of trend message and radar target state information whole-track data.
Owner:10TH RES INST OF CETC
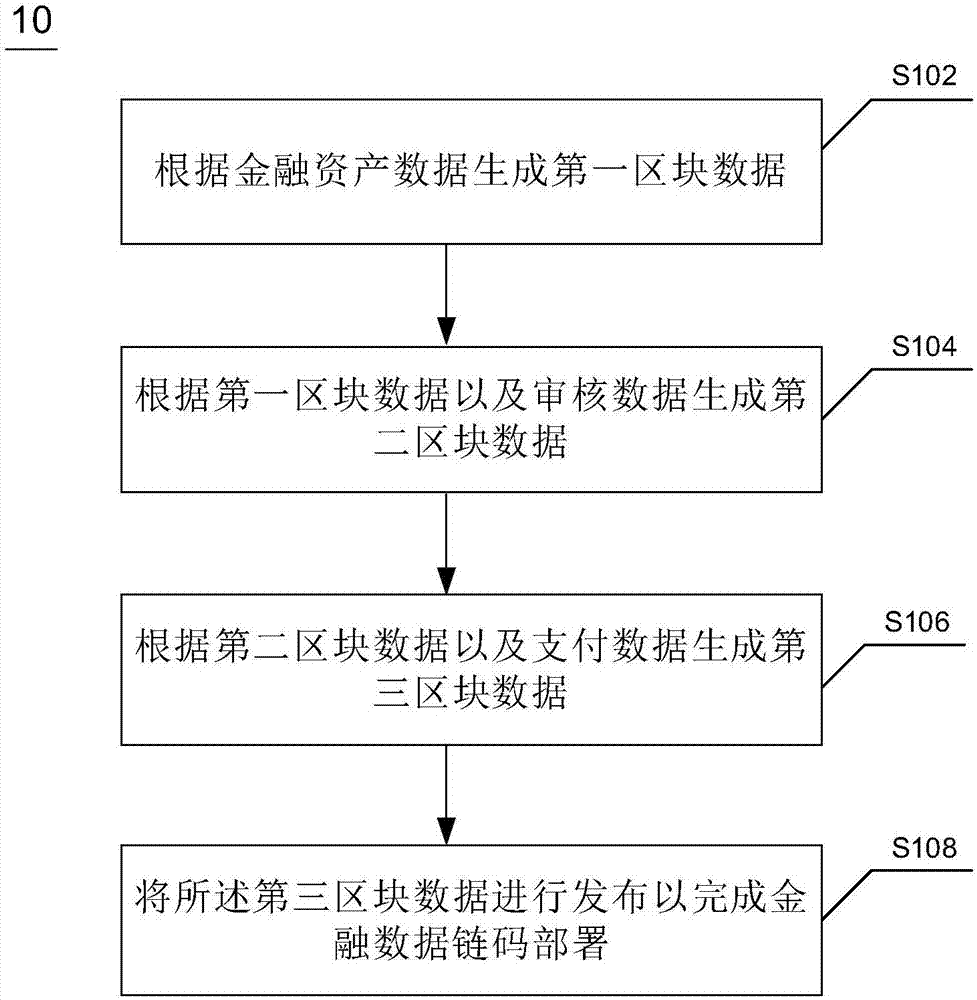
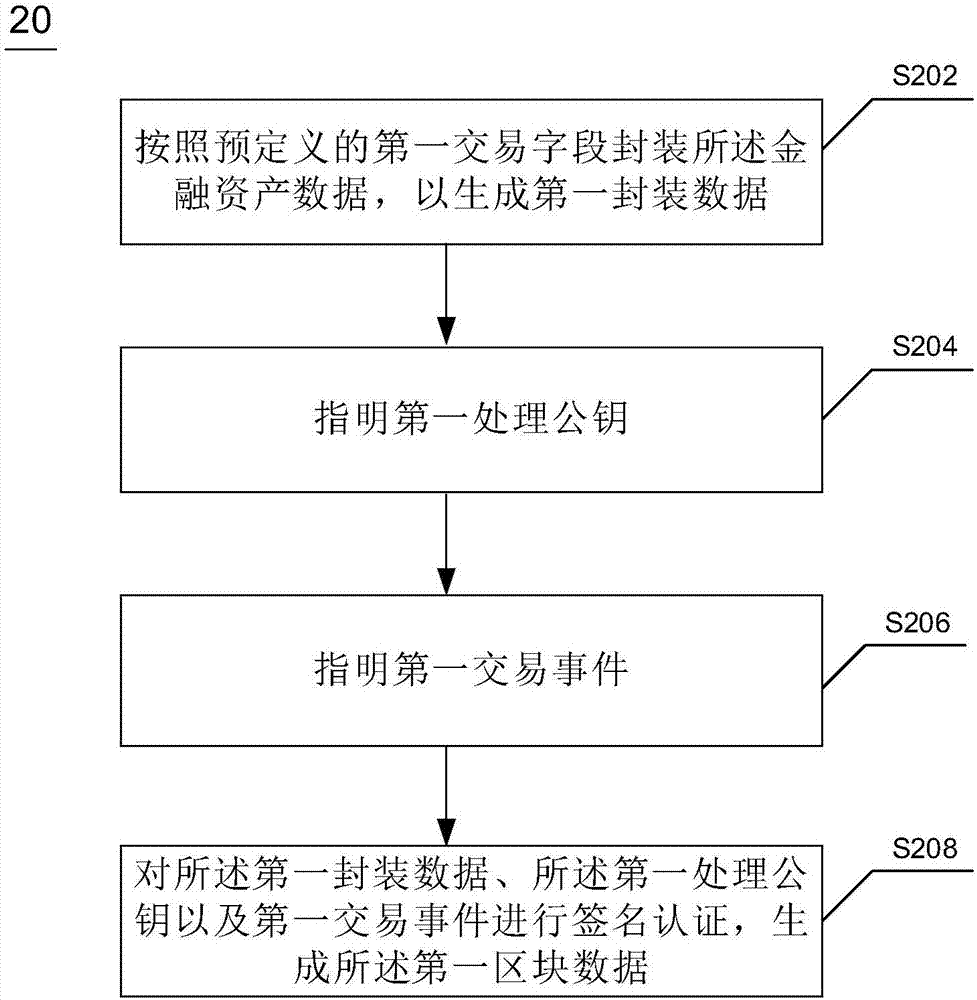
Method used for financial data sharing, device used for financial data sharing and electronic device
The application discloses a method used for the financial data sharing, a device used for the financial data sharing and an electronic device. The method comprises the steps of generating the first block data according to the financial asset data; according to the first block data and the audit data, generating the second block data; according to the second block data and the payment data, generating the third block data; issuing the third block data to finish the financial data chain code deployment. The method used for the financial data sharing, the device used for the financial data sharing and the electronic device which are disclosed by the application can guarantee the authenticity of the underlying data of the asset securitization service providers.
Owner:JINGDONG TECH HLDG CO LTD
Improved Zernike moment edge detection method
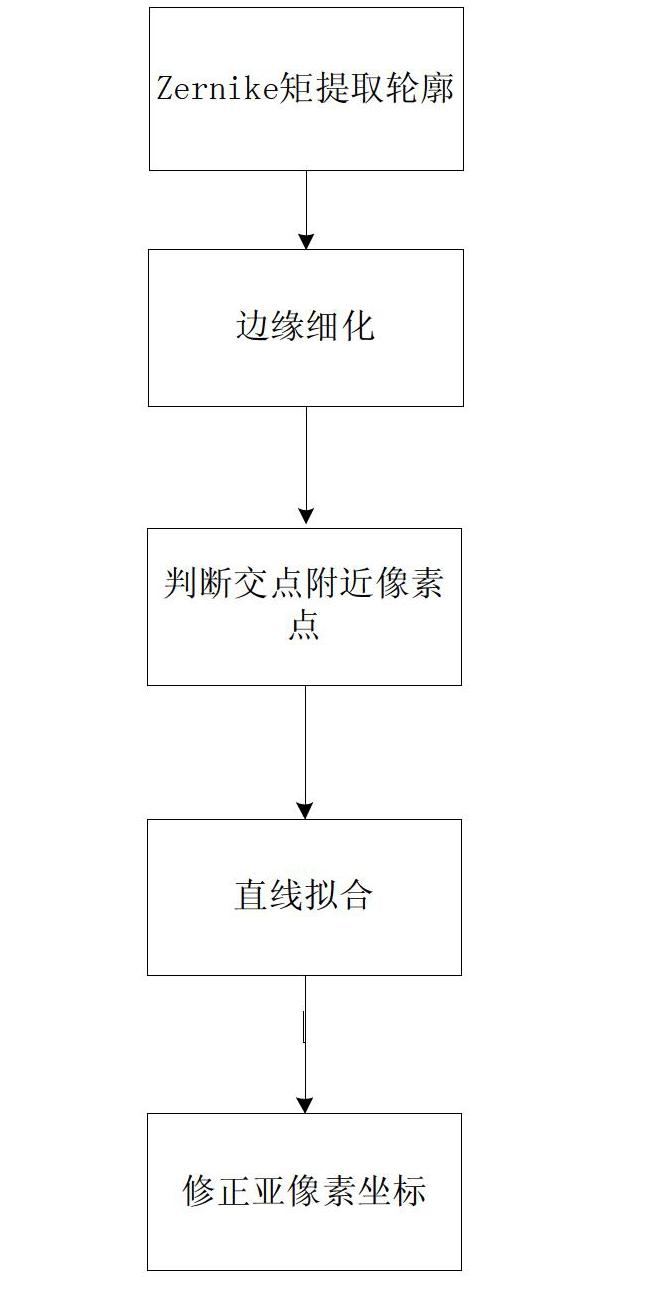
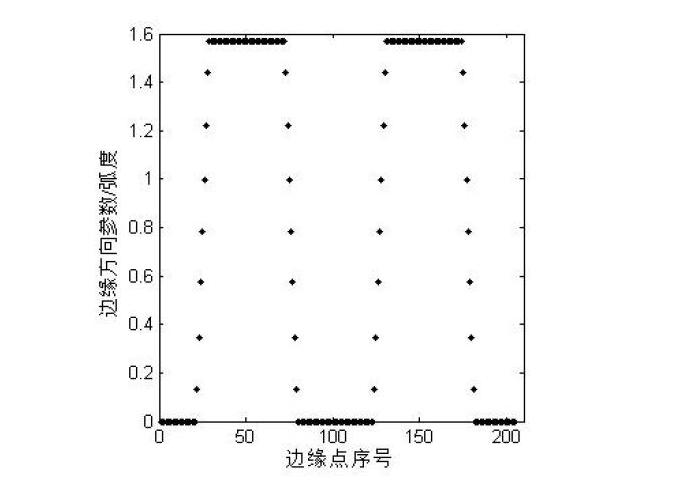
The invention discloses an improved Zernike moment edge detection method, which relates to an image processing method. The invention provides an improved Zernike moment edge detection method, which aims to the sub-pixel positioning of pixel points near an intersection point. The method comprises the following steps: carrying out sub-pixel edge extraction on an industrial CT (computed tomography) image by using a Zernike moment method, and refining an edge; then, obtaining the distribution of an edge direction parameter phi by using a 8-chain code tracing method, and calculating a difference value delta phi of the edge direction parameter phi; selecting a threshold T; judging whether an edge point is the pixel point near the intersection point; if the edge point is not the pixel point near the intersection point, carrying out least square fit on the edge point so as to obtain a linear equation; and calculating the sub-pixel coordinates of a to-be-corrected edge point near the intersection point by using the linear equation. The improved Zernike moment edge detection method well makes up for a shortage that the positioning error of a pixel point near an intersection point in a Ghosal algorithm is large, and has an important significance for high-precision area measurement and high-precision three-dimensional measurement.
Owner:CHONGQING UNIV
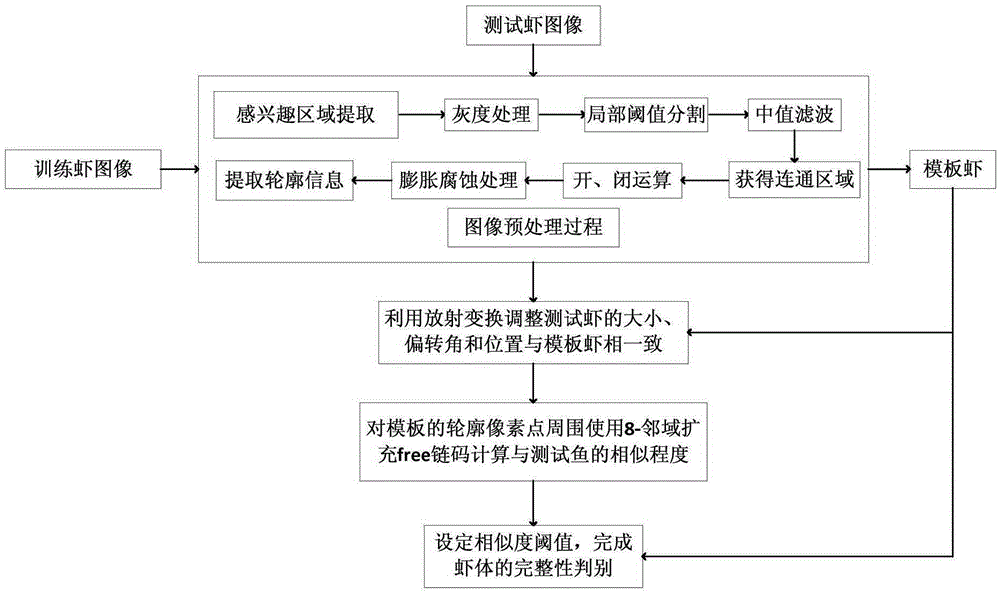
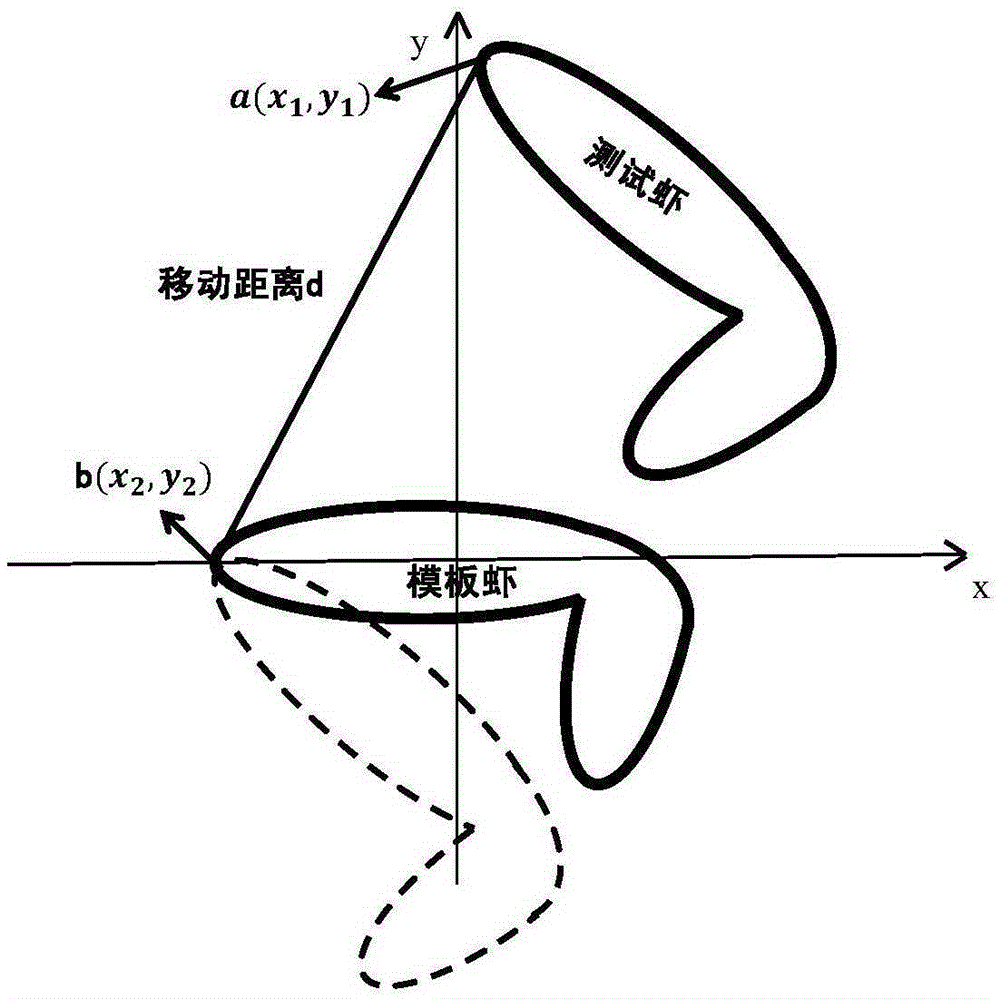
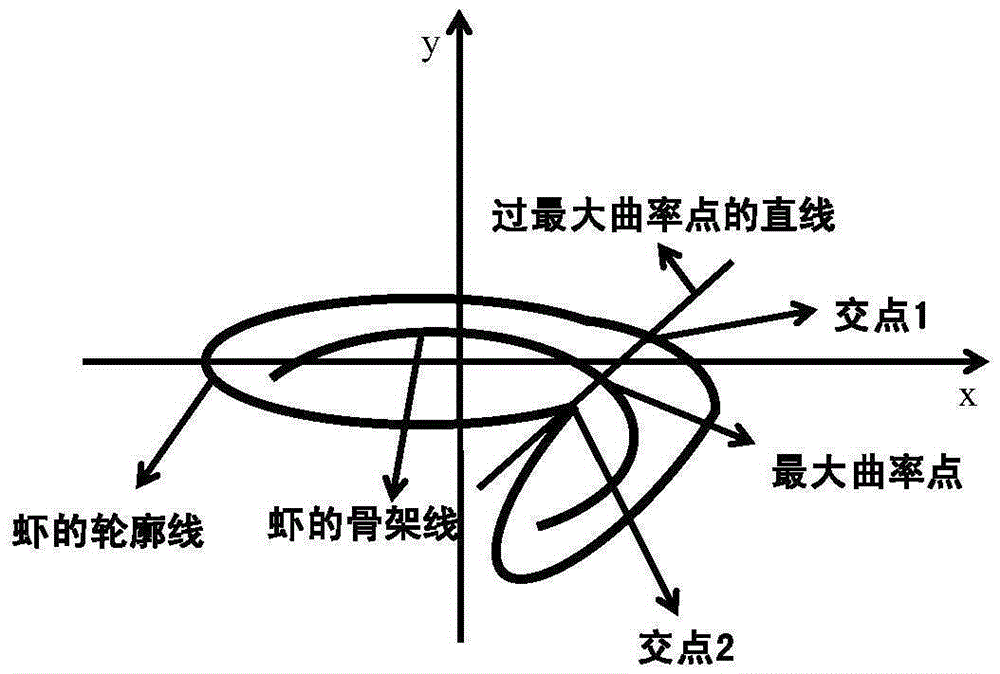
Method for automatically detecting integrity of shrimp body based on computer vision
The invention discloses a method for automatically detecting integrity of a shrimp body based on computer vision. The method comprises the steps of: 1) regarding an integral shrimp body as a template shrimp, and extracting an outline image of the template shrimp as an outline template; 2) extracting an outline image of a tested shrimp, and correcting a morphological position of the outline of the tested shrimp by adopting an affine transformation method according to the outline template; 3) extracting a main skeleton curve of the tested shrimp in the outline image, taking an obtained maximum curvature point of the shrimp body as a supporting point for abdominal rotation, and correcting an abdominal deviation angle of the tested shrimp; 4) and calculating similarity of the outline image of the template shrimp and the outline image of the tested shrimp by adopting an 8-neighbourhood free chain code method based on template traversal; 5) and setting a similarity threshold value, and completing the integrity judgment of the shrimp body. The method can be directly applied to a sample preprocessing link of a prawn aquaculture and processing plant, removes the non-integral shrimps, and meets the requirement of product culling classification during product processing.
Owner:ZHEJIANG UNIV
Multi-source image registering method on the basis of contour under rigid body transformation
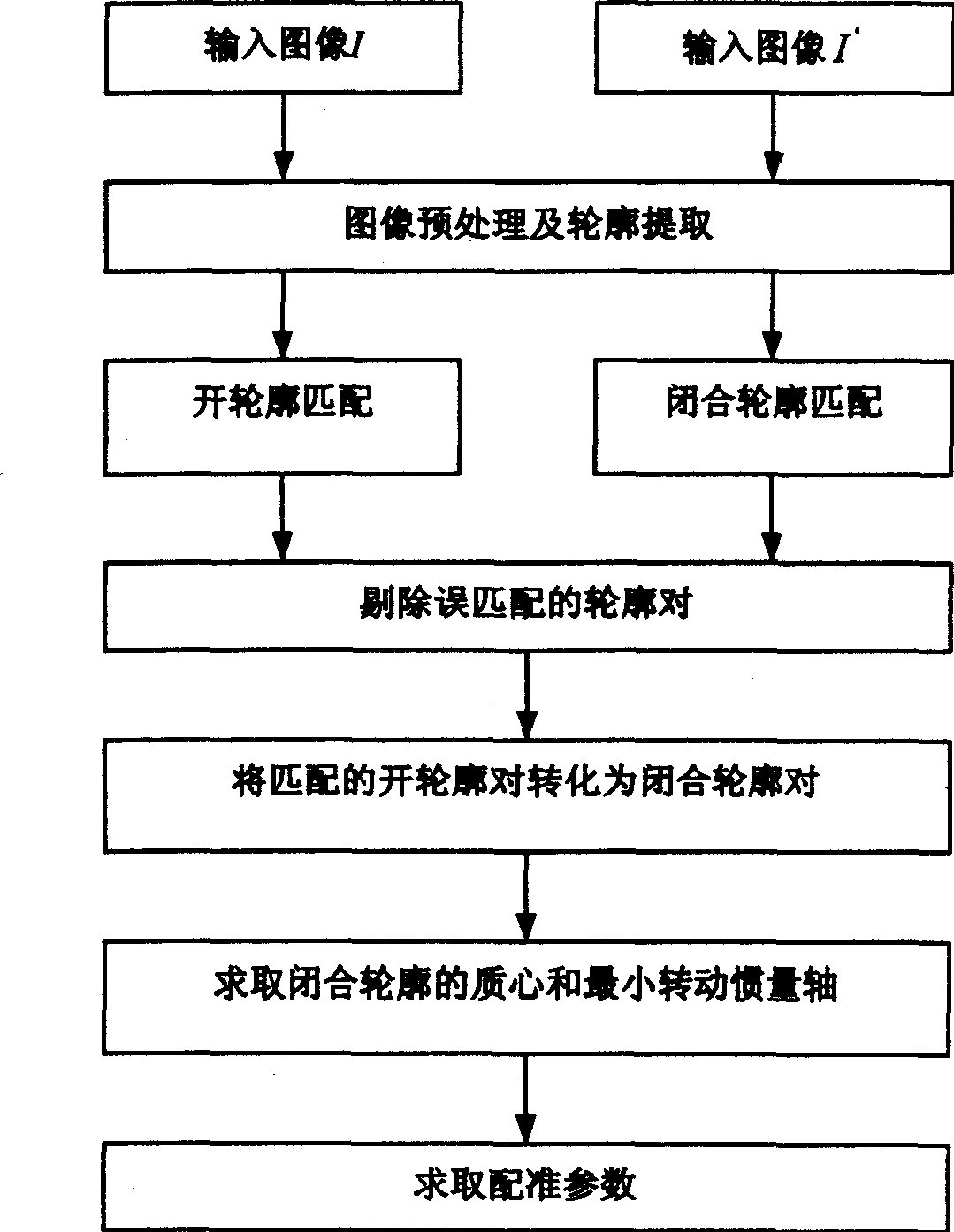
InactiveCN1545061AReduce computationAvoid registration errorsGeometric image transformationImage codingAngular pointMoment of inertia
The invention relates to an outline-based multi-source image aligning method under a rigid-body transformation, performing noise filter pretreatment on input multi-source images, respectively and then edge detection, linking their respective edges to obtain the closed or open outlines, matching the closed ones by partial variables and the open ones by chain codes, then converting the open outline pairs into the closed outline pairs, and finally finding the centers of mass and minimum moment of inertia axes of all the closed outlines, and according to this, obtaining the rotation and translation quantities between two images to be aligned and implementing the alignment. It can be applied to remote sensing, safety monitoring, airborne multi-source image fusion, image tracking, and other civil or military fields.
Owner:SHANGHAI JIAO TONG UNIV
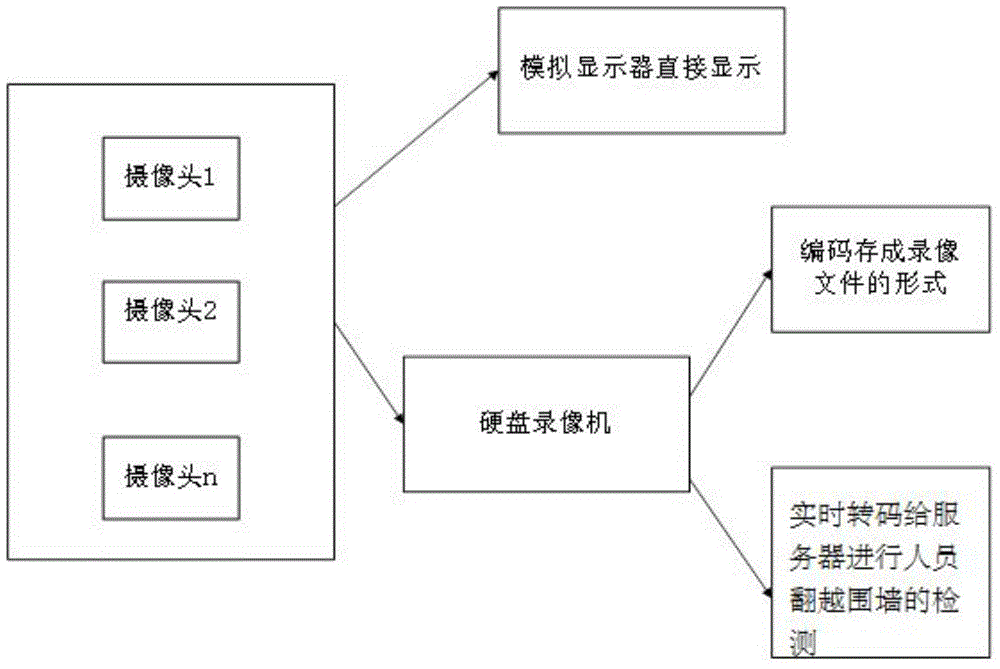
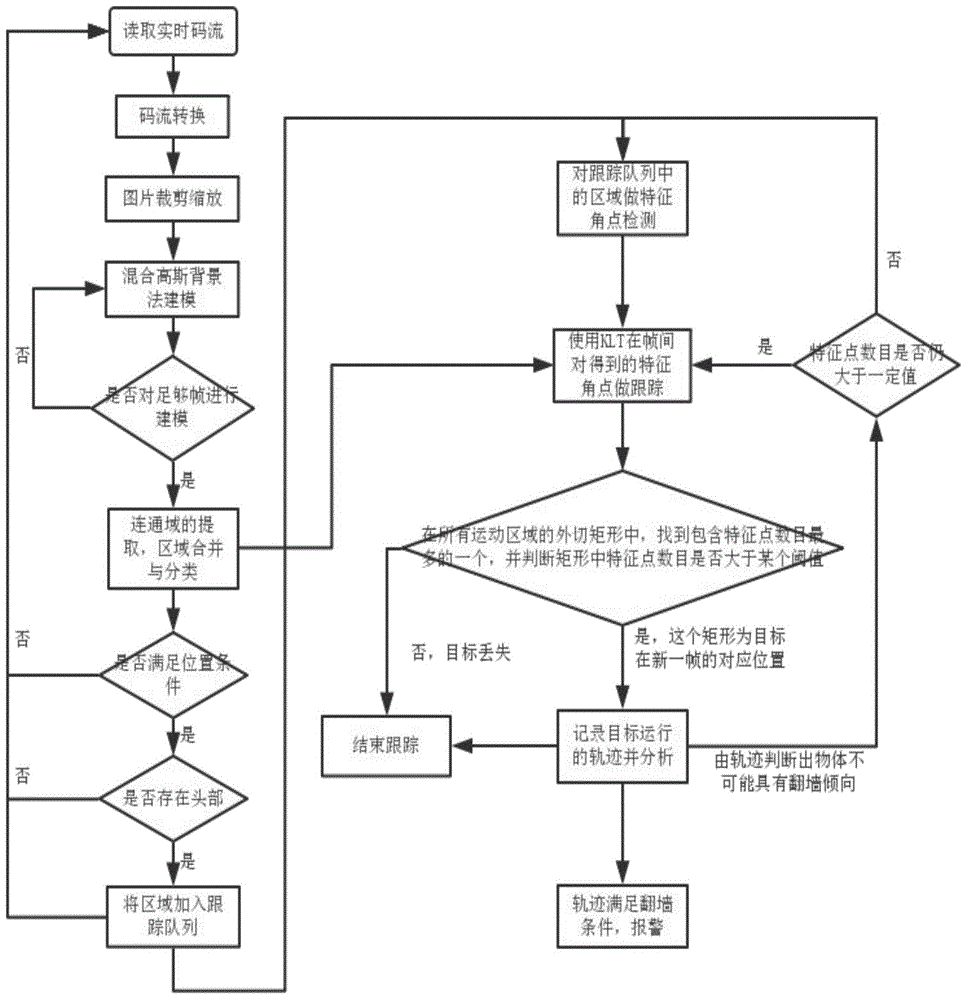
Method for detecting people crossing behavior based on video monitoring platform
InactiveCN104866827AReduce configurationImprove computing efficiencyCharacter and pattern recognitionBurglar alarmHuman bodyVideo monitoring
The invention relates to a method for detecting people crossing behaviors based on a video monitoring platform. The method includes inputting video frames, marking a wall position with a straight line which is a warning line, editing the video frame according to the marked wall position for each frame of an image, extracting motion foreground images, carrying out binary processing and morphological filtering on foreground images, extracting connected domain by employing a boundary chain code extraction method to obtain a series of rectangular areas which may have human bodies, sorting out the rectangular areas which satisfy the position conditions, tracking images, and recording the top positions of the rectangles tracked for each frame to obtain a motion track. The method does not rely on color information in images, especially suitable of detection during the night. (Enclosure wall crossing events usually occur during the night) The calculating efficiency is high, server configuration can be saved, and the use cost is lowered.
Owner:TIANJIN UNIV
Fault diagnosis method of sucker-rod pump well
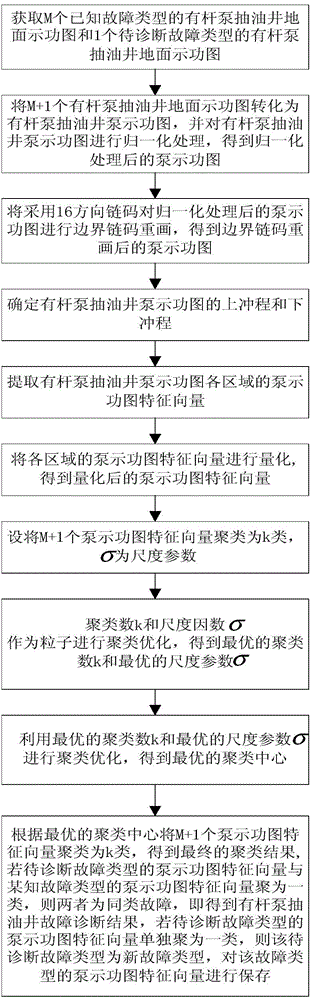
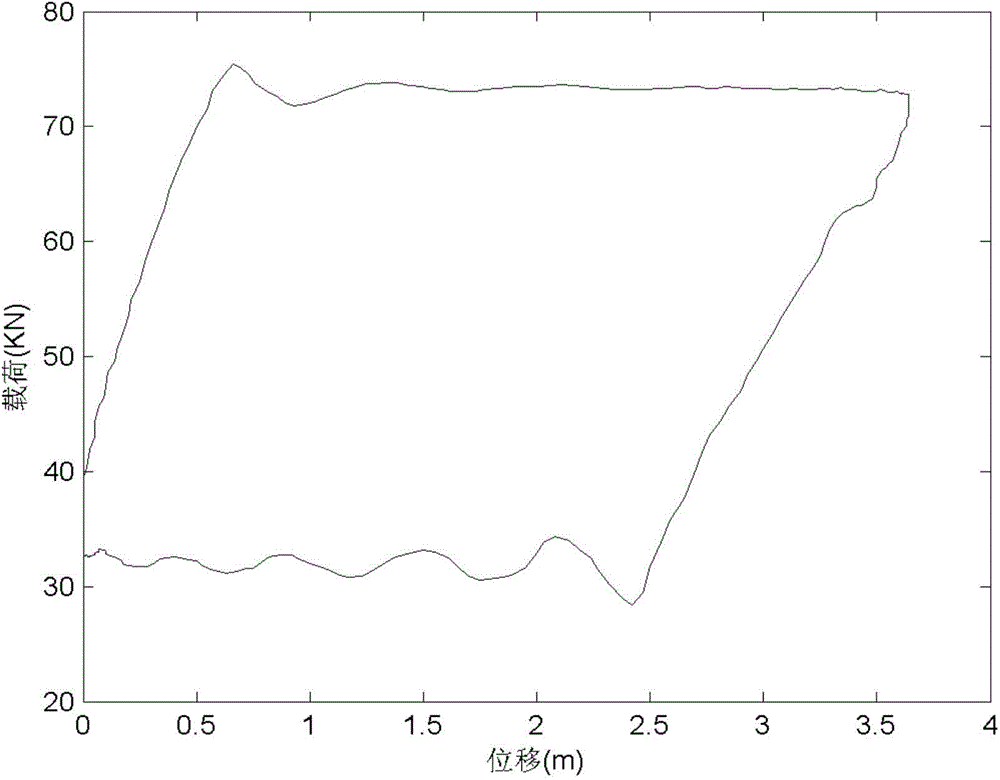
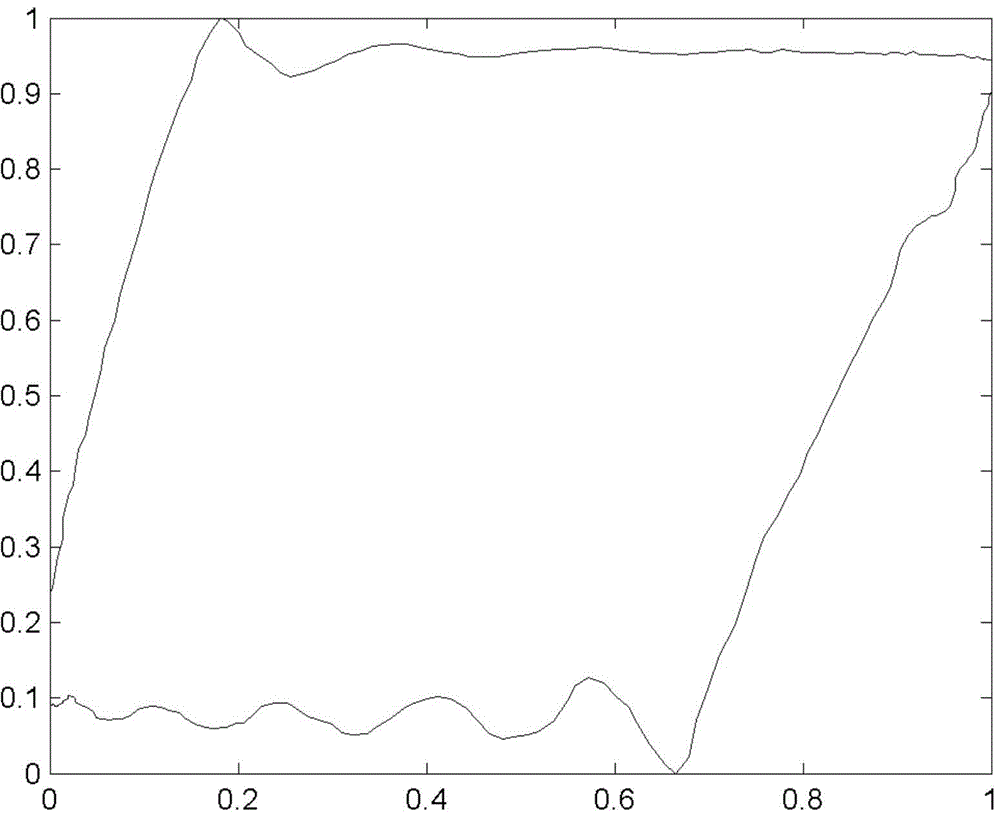
InactiveCN104481496AImprove recognition accuracyDescribe wellConstructionsAutomatic control for drillingFeature vectorGraphics
The invention relates to a fault diagnosis method of sucker-rod pump well; the method comprises the following steps: acquiring ground dynamometer cards of the known and to-be-diagnosed sucker-rod pump wells; converting the ground dynamometer card of the suck-rod pump well into a suck-rod pump well dynamometer card; redrawing a boundary chain code of a normalization processed pump dynamometer card by 16-direction chain codes; zoning the pump dynamometer card which is redrawn with the boundary chain code, and extracting the characteristic vector of each zone; clustering the characteristic vectors of the quantified pump dynamometer card by spectral clustering algorithm based on particle swarm optimization, so as to finish the fault diagnosis of the suck-rod pump well; the fault diagnosis method of sucker-rod pump well uses the number of the 16-direction chain codes to quantify the characteristic vectors of each pump dynamometer card, so as to effectively and precisely describe the pattern characteristics; the fault diagnosis is achieved by clustering the quantified pump dynamometer card characteristic vectors with spectral clustering algorithm based on particle swarm optimization, without depending one training samples, thus increasing the performance of the diagnosis.
Owner:BOHAI UNIV
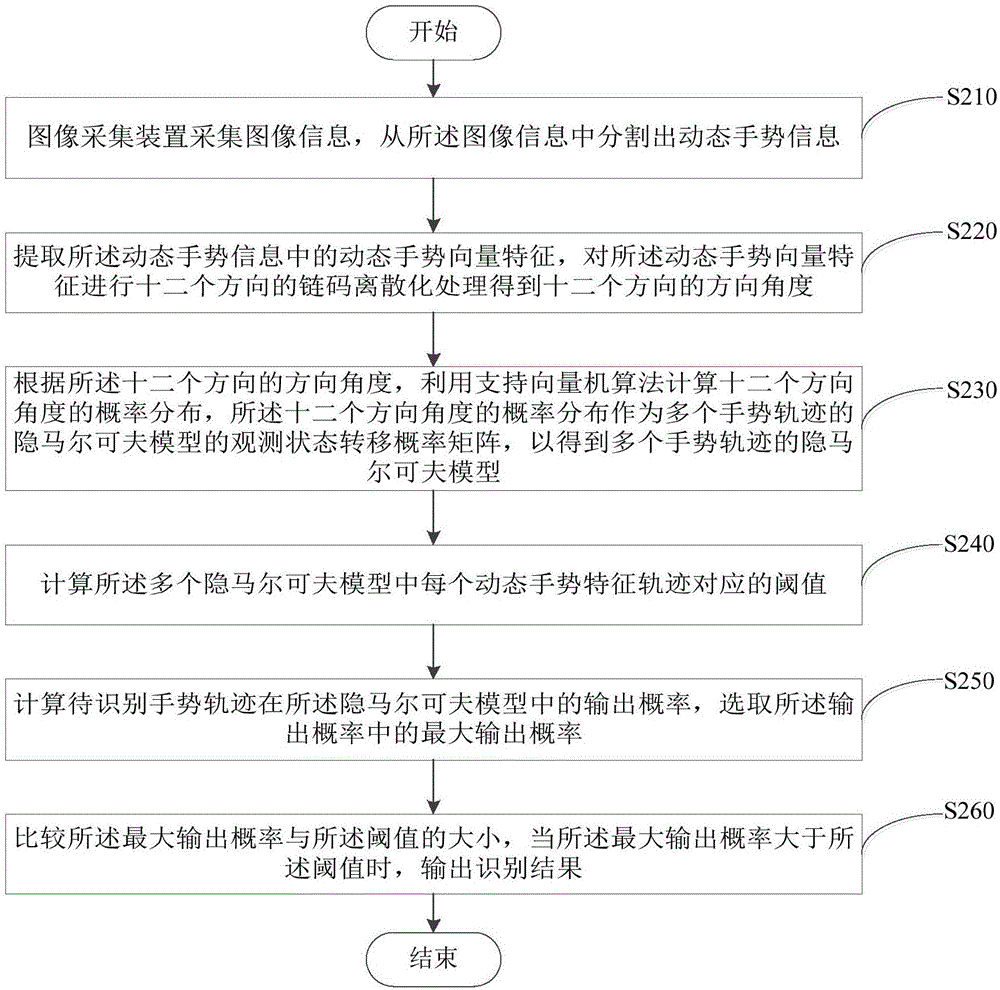
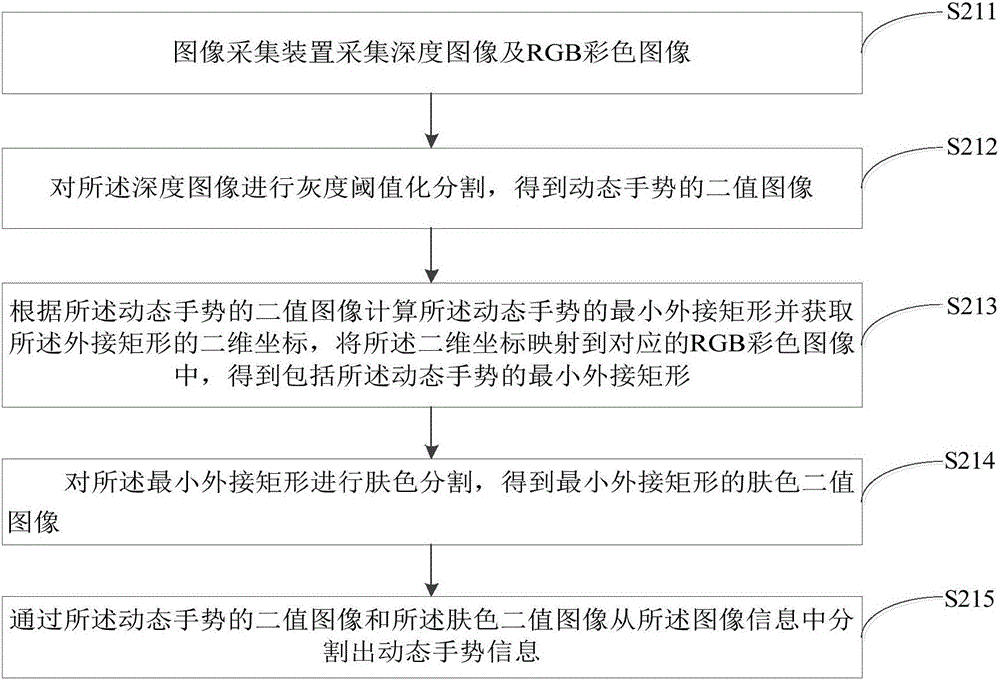
Dynamic gesture recognition method and device
InactiveCN106557173AImprove dynamic gesture recognition rateInput/output for user-computer interactionCharacter and pattern recognitionHide markov modelDiscretization
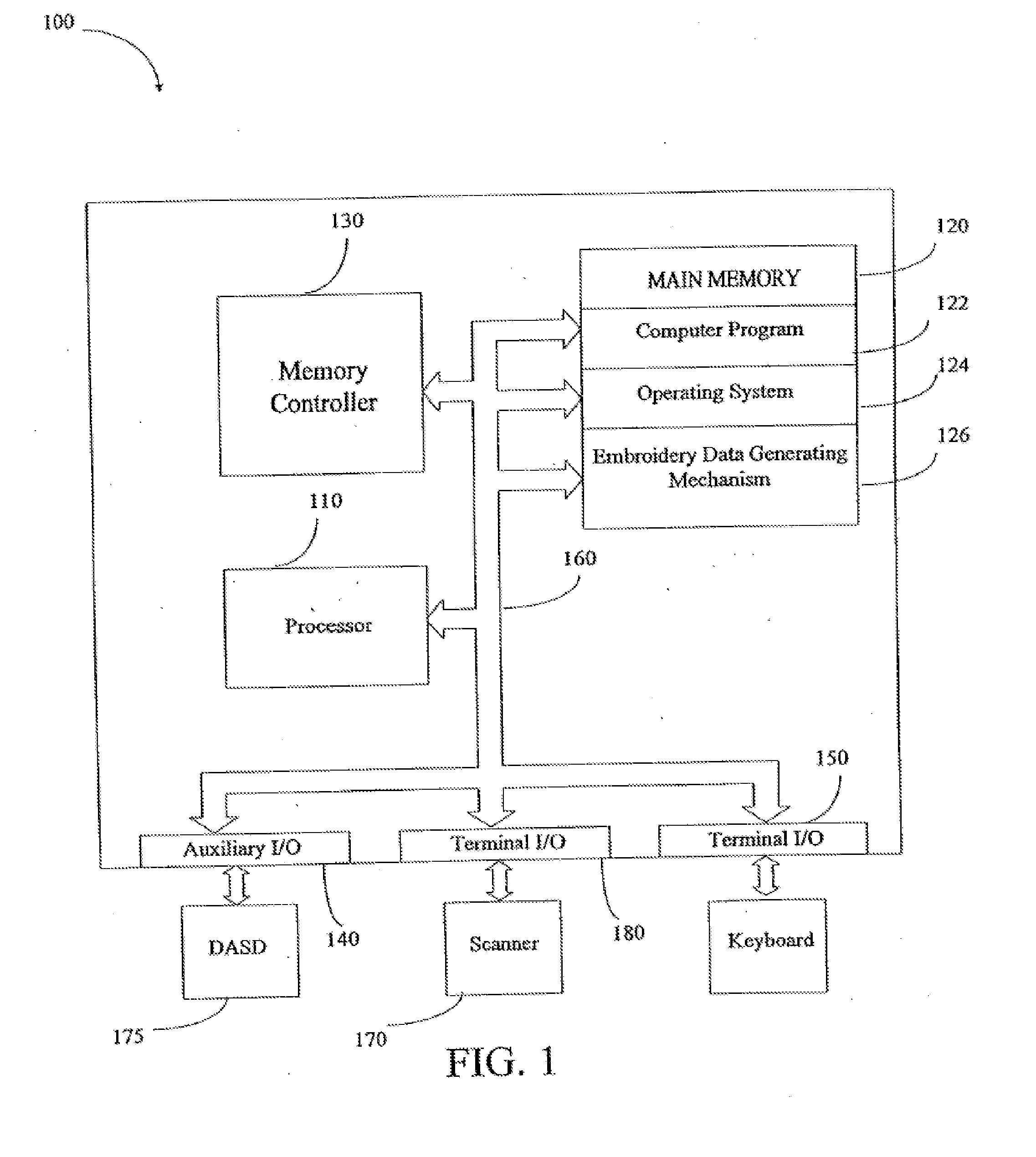
The invention provides a dynamic gesture recognition method and device. The method comprises the following steps of: acquiring image information by an image acquisition device, and segmenting dynamic gesture information from the image information; extracting dynamic gesture vector characteristics in the dynamic gesture information, and performing chain code discretization of the dynamic gesture vector characteristics in twelve directions; calculating probability distribution in the twelve directional angles by utilizing a support vector machine algorithm, and taking the probability distribution as an observation state transition probability matrix of a hidden Markov model having multiple gesture trajectories, so that the hidden Markov model having the multiple gesture trajectories is obtained; calculating a threshold value corresponding to each dynamic gesture characteristic trajectory in the hidden Markov model; calculating the output probabilities of gesture trajectories to be recognized in the hidden Markov model, and selecting the maximum output probability in the output probabilities; and, comparing the maximum output probability with the threshold value, and outputting a recognition result when the maximum output probability is greater than the threshold value. By means of the dynamic gesture recognition method and device provided by the invention, the dynamic gesture recognition rate can be increased.
Owner:重庆重智机器人研究院有限公司
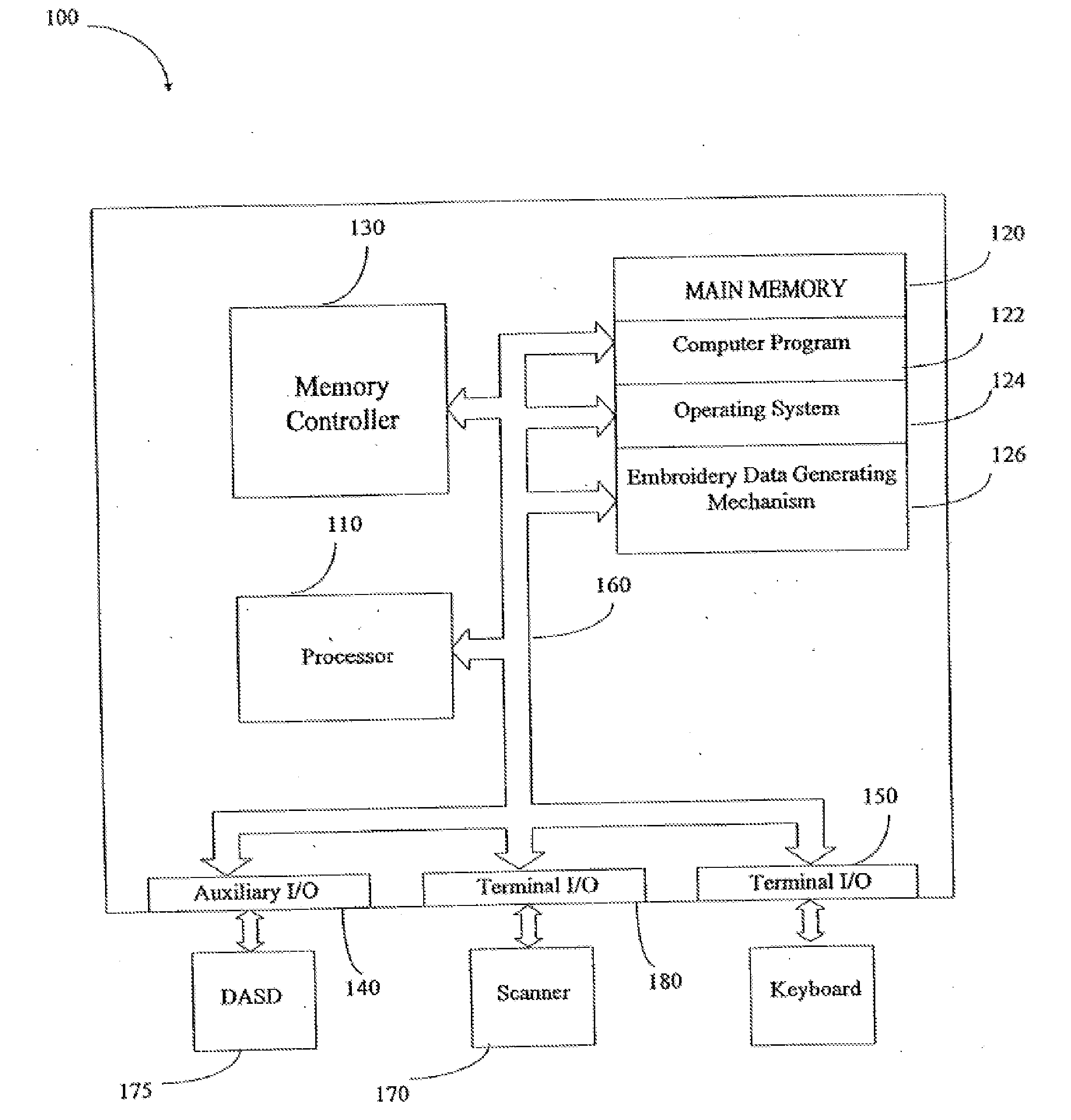
Automatically generating embroidery designs
InactiveUS20140094952A1Efficient and accurateAutomatically and efficiently generates accurate embroidery design dataProgramme-controlled sewing machinesSaving energy measuresChain code
A method and system are disclosed for automatically generating embroidery designs. A described method includes identifying vertices in a set of chain-code points defining an edge of a first object to be embroidered; filtering the vertices by: determining whether a height of a first triangle defined by a first one of the vertices and ones of the vertices that neighbor the first one of the vertices is at least a threshold; and when the height is less than the threshold, eliminating the first one of the vertices from the vertices; and generating embroidery data based on the filtered vertices.
Owner:CIMPRESS SCHWEIZ
Method for recognizing and calculating galloping of transmission conductor based on video image processing
InactiveCN102143354AGuaranteed safe operationFacilitate dance state analysisImage analysisCharacter and pattern recognitionVideo monitoringDigital video
The invention discloses a method for recognizing and calculating galloping of a transmission conductor based on video image processing, belonging to the technical field of remote digital video monitoring and image identification. The method comprises the steps of real-time transmitting a digital video signal collected by a camera to a monitoring centre through a transmission channel in the form of video stream; carrying out remote video monitoring on the field at the monitoring centre; intercepting a monitoring target image from the video stream; and calculating to obtain amplitude information of galloping through a series of image processing and identifications like image gray processing, image segmentation, transmission conductor extraction based on a chain code, Hough transformation and galloping amplitude calculation. Therefore, the galloping amplitude of the transmission conductor can be accurately, intuitively and effectively calculated; meanwhile, long-time galloping data can be saved in a database so as to provide the remote video monitoring and the image identification with original data of the galloping state of the transmission conductor, and thereby, the galloping state of the transmission conductor is convenient to analyze; and the omitted and false reports of accidents are reduced to assure the safe operation of the transmission line.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
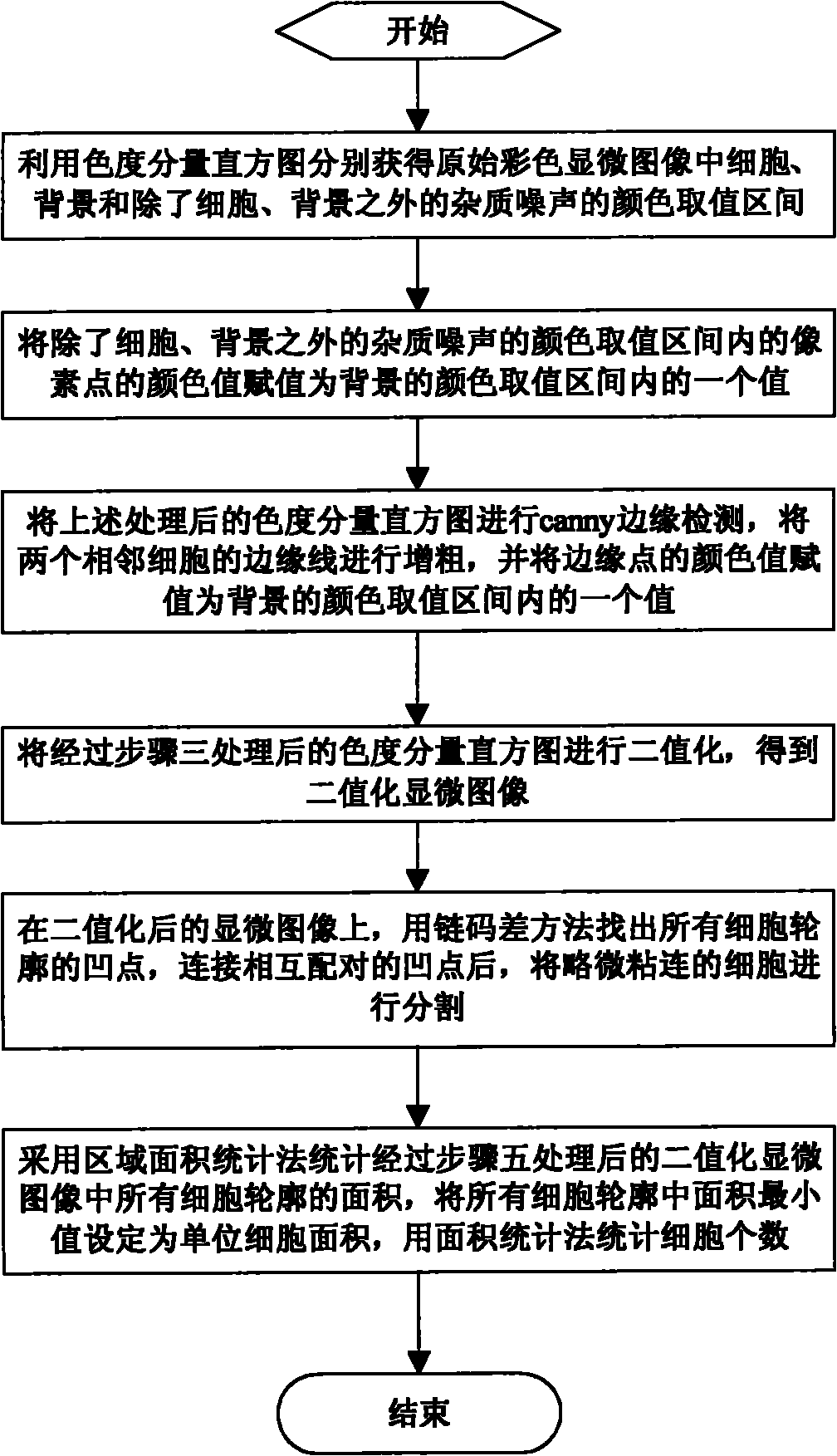
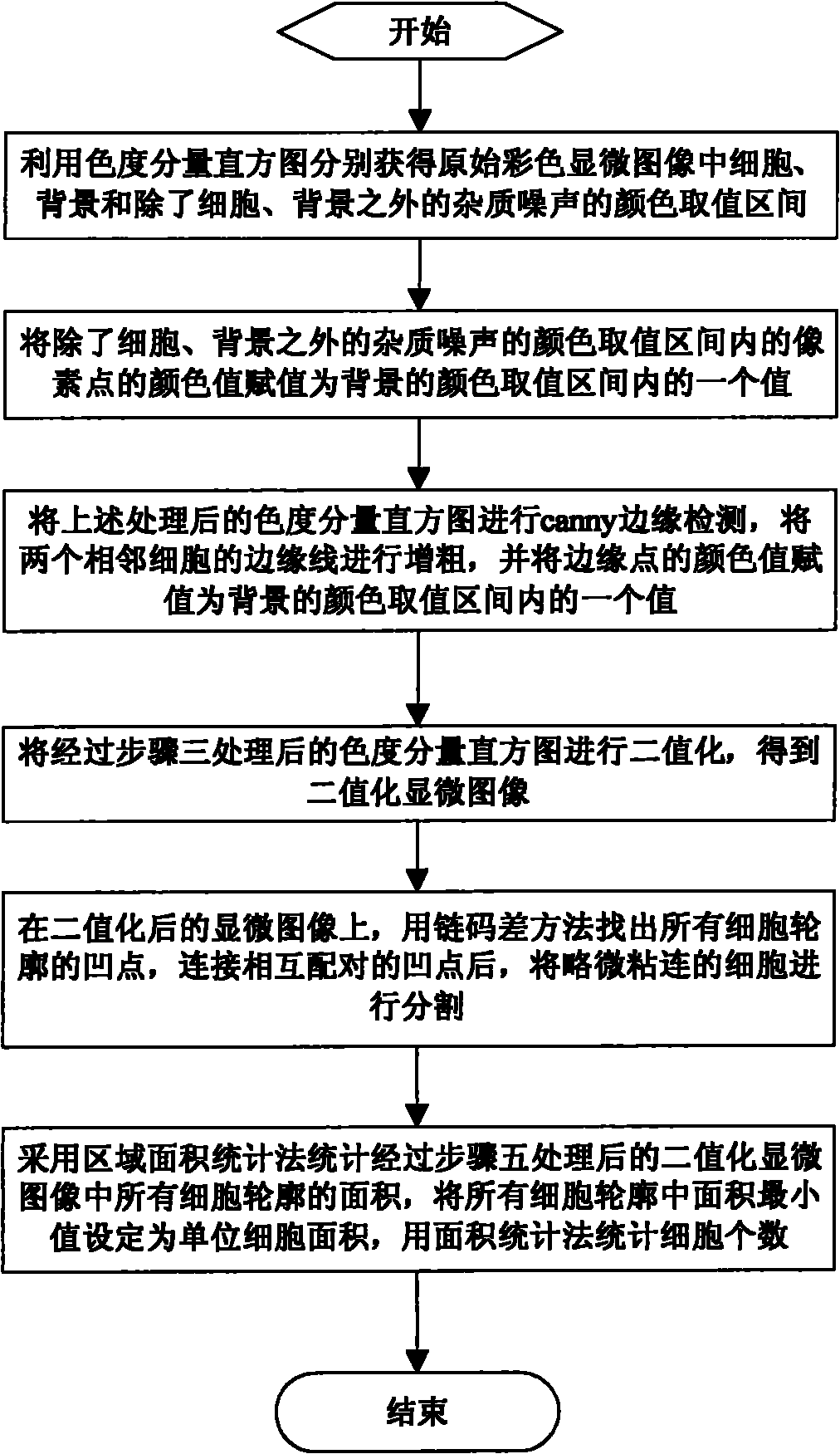
Method for counting number of complex overlapping cells in microscopic image
InactiveCN101777140AReduce mistakesHigh precisionCharacter and pattern recognitionCounting objects with random distributionMicroscopic imageState of art
The invention relates to a method for counting the number of complex overlapping cells in a microscopic image. The method comprises the following steps: pre-processing and further binarizing an original colored microscopic image; locating the concave points in the outline of all the cells by using a chain code difference method, connecting the concave points which are paired with each other, and segmenting the slightly overlapping cells; and finally, counting the number of cells by using a region area statistical method. Compared with the prior art, the invention has the following advantages that: the original colored microscopic image is pre-processed and further binarized according to the color features of the colored microscopic image; the outline of the cells are detected and further segmented by using the chain code difference method because the slightly overlapping cells are characterized in that the concave points of the cells are obvious; and finally, the numbers of the heavily overlapping cells and the single cells are calculated by using the region area statistical method, so the method has small error and high accuracy.
Owner:NINGBO UNIV
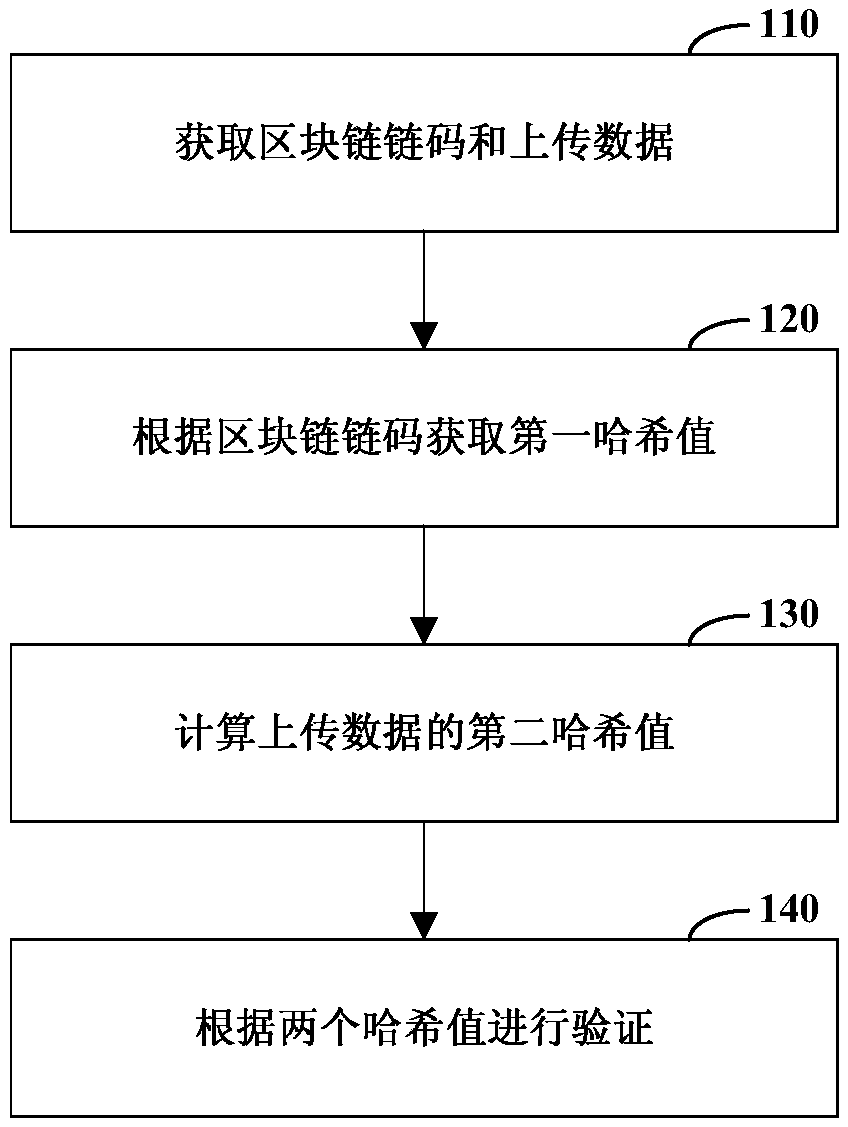
Verification method and device and computer-readable storage medium
InactiveCN108764944AImprove reliabilityUser identity/authority verificationBuying/selling/leasing transactionsValidation methodsInformation security
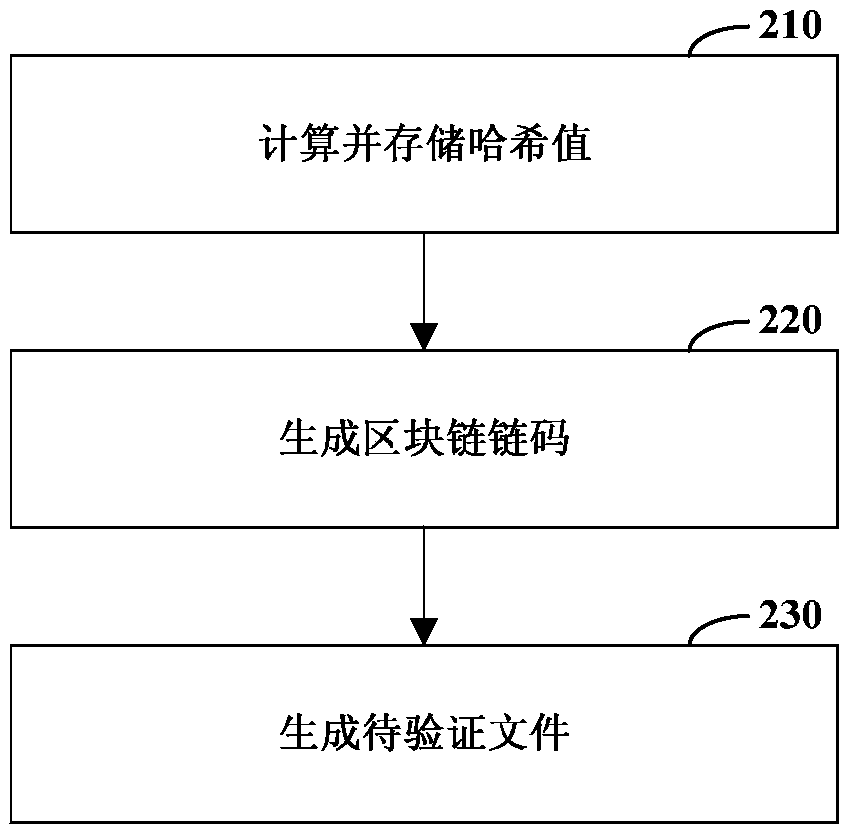
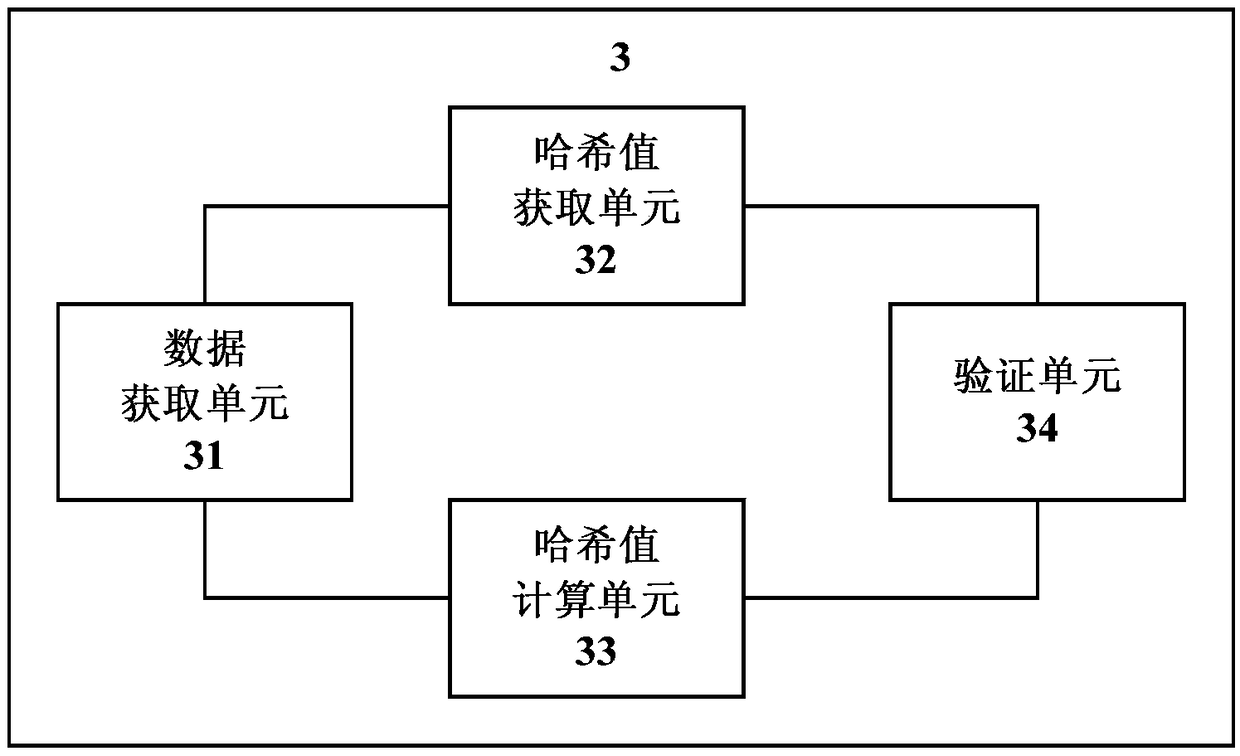
The disclosure relates to a verification method and device and a computer-readable storage medium, and relates to the technical field of information security. The method includes obtaining a block chain code in a file to be verified uploaded by a client and uploading data; obtaining a hash value corresponding to the block chain code from a block chain as a first hash value; performing hash calculation on the uploaded data to obtain a second hash value; and comparing whether the first hash value and the second hash value are consistent to verify whether the file to be verified is tampered. Thetechnical scheme of the disclosure can improve the reliability of information verification.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Digital image active camouflage scheme based on fractal
InactiveCN104835104AImprove visual effectsAchieving Adaptive FusionImage enhancementImage data processing detailsColor imageDigital image
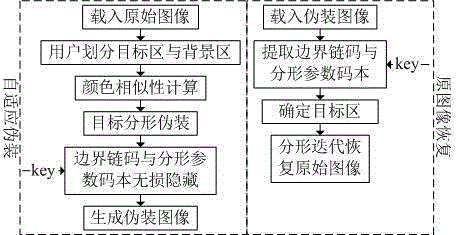
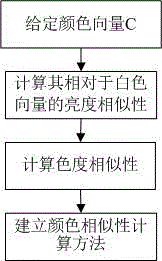
The invention provides a digital image active camouflage scheme based on fractal, comprising two main phases of adaptive camouflage and original image restoration. In the adaptive camouflage phase, fractal camouflage from an object to a background is realized by utilizing fractal mapping based on color similarity, and an original image is converted into another meaningful image to realize object adaptive camouflage. In the original image restoration phase, an authorized user first losslessly extracts target zone boundary chain codes and fractal parameter codes and approximately recovers an original color images through proper fractal iteration. The invention fully combines fractal self-similarity and image color characteristics, realizes full combination between the object and the background, has good camouflage effects, and can be used for guiding military object camouflage in the military field. The digital image active camouflage scheme has good security, and only an authorized user with a correct secret key can effectively recover an original image; in addition, the scheme is low in computing cost, and can be better applied to network environment visual media anonymous communication.
Owner:HUNAN FIRST NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com