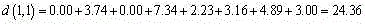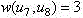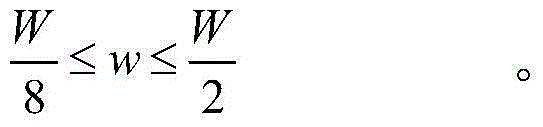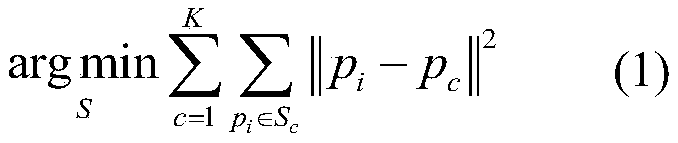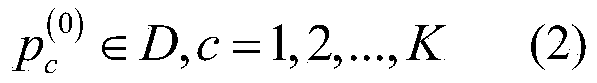Patents
Literature
1181 results about "K-means clustering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
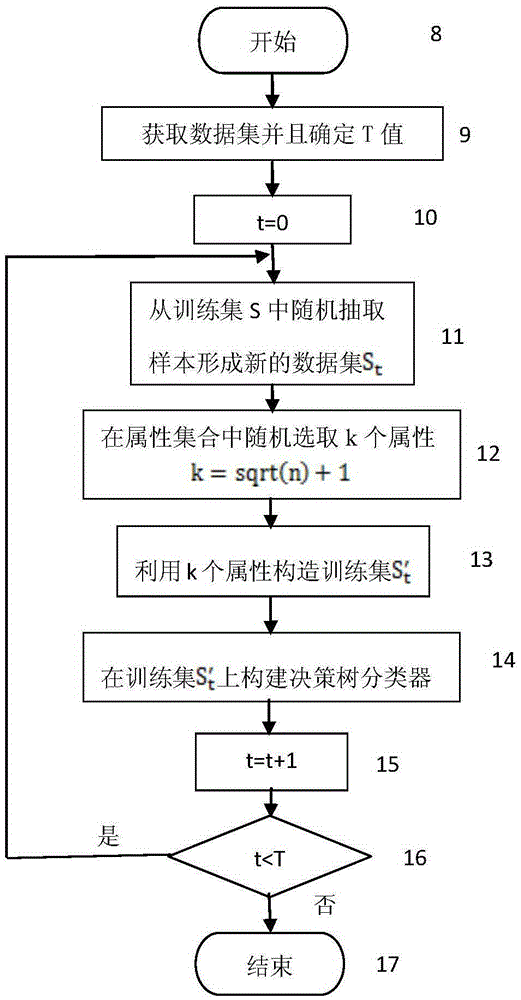
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
K-means clustering is a method of vector quantization, originally from signal processing, that is popular for cluster analysis in data mining. k-means clustering aims to partition n observations into k clusters in which each observation belongs to the cluster with the nearest mean, serving as a prototype of the cluster. This results in a partitioning of the data space into Voronoi cells. k-Means minimizes within-cluster variances (squared Euclidean distances), but not regular Euclidean distances, which would be the more difficult Weber problem: the mean optimizes squared errors, whereas only the geometric median minimizes Euclidean distances. Better Euclidean solutions can for example be found using k-medians and k-medoids.
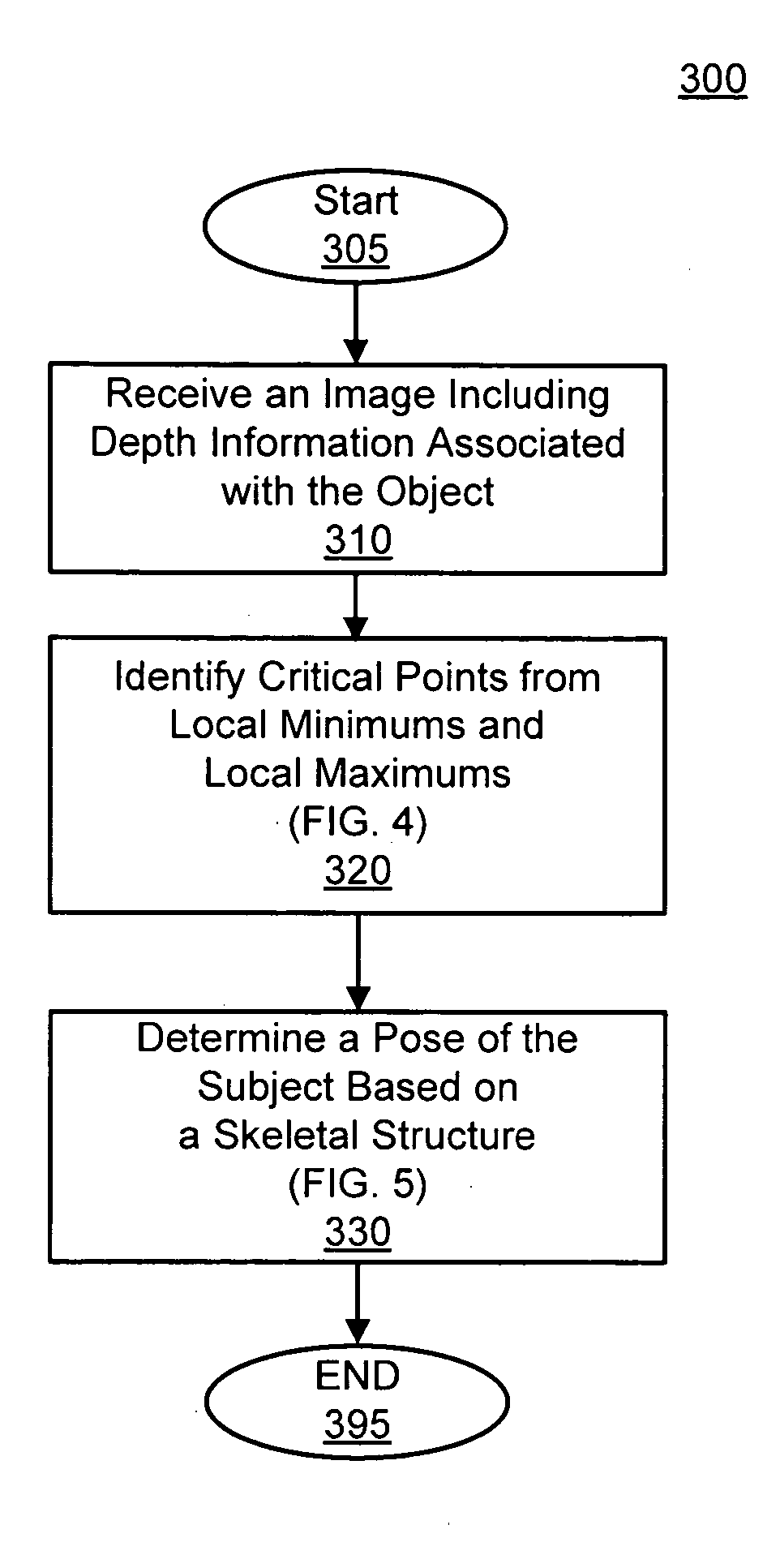
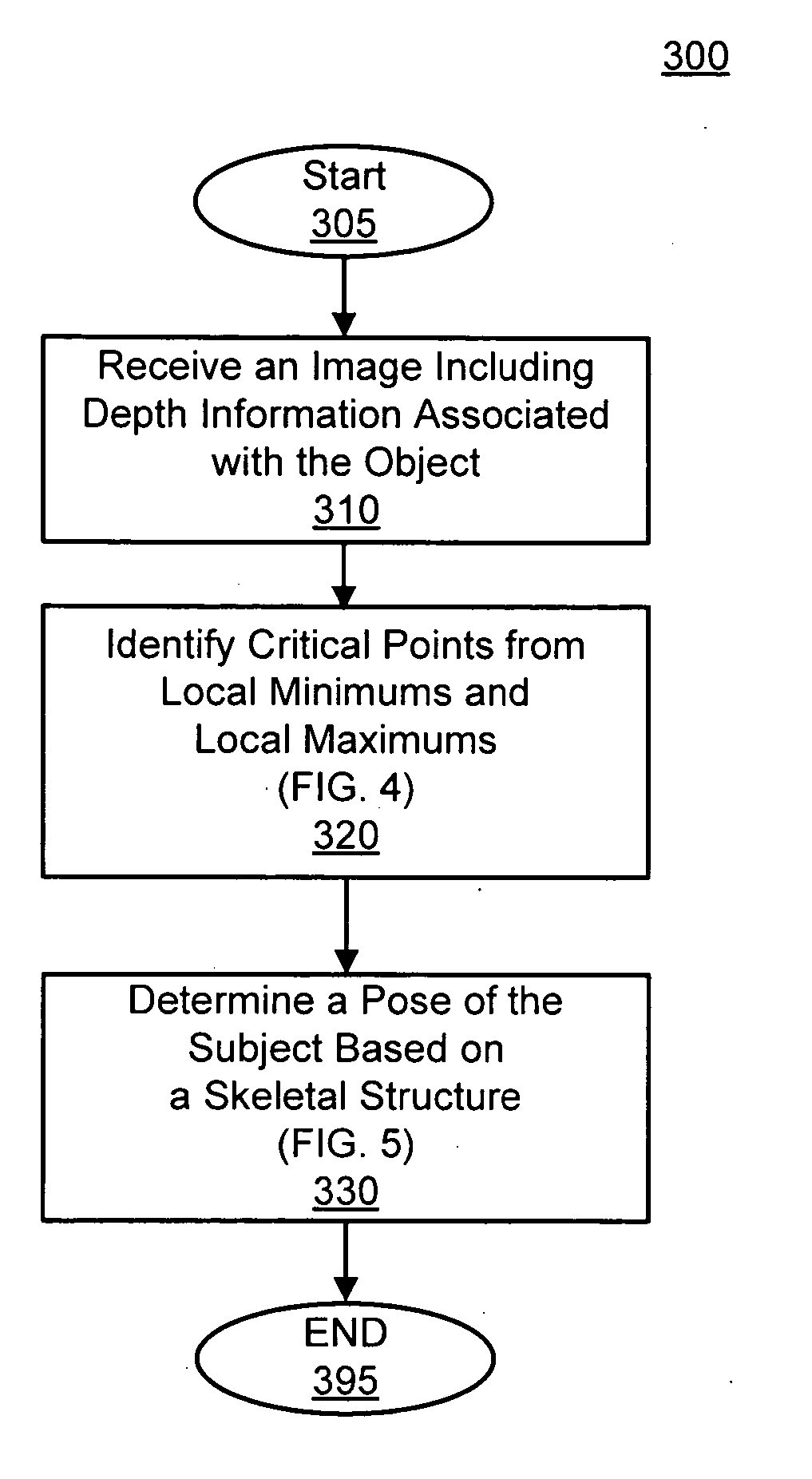
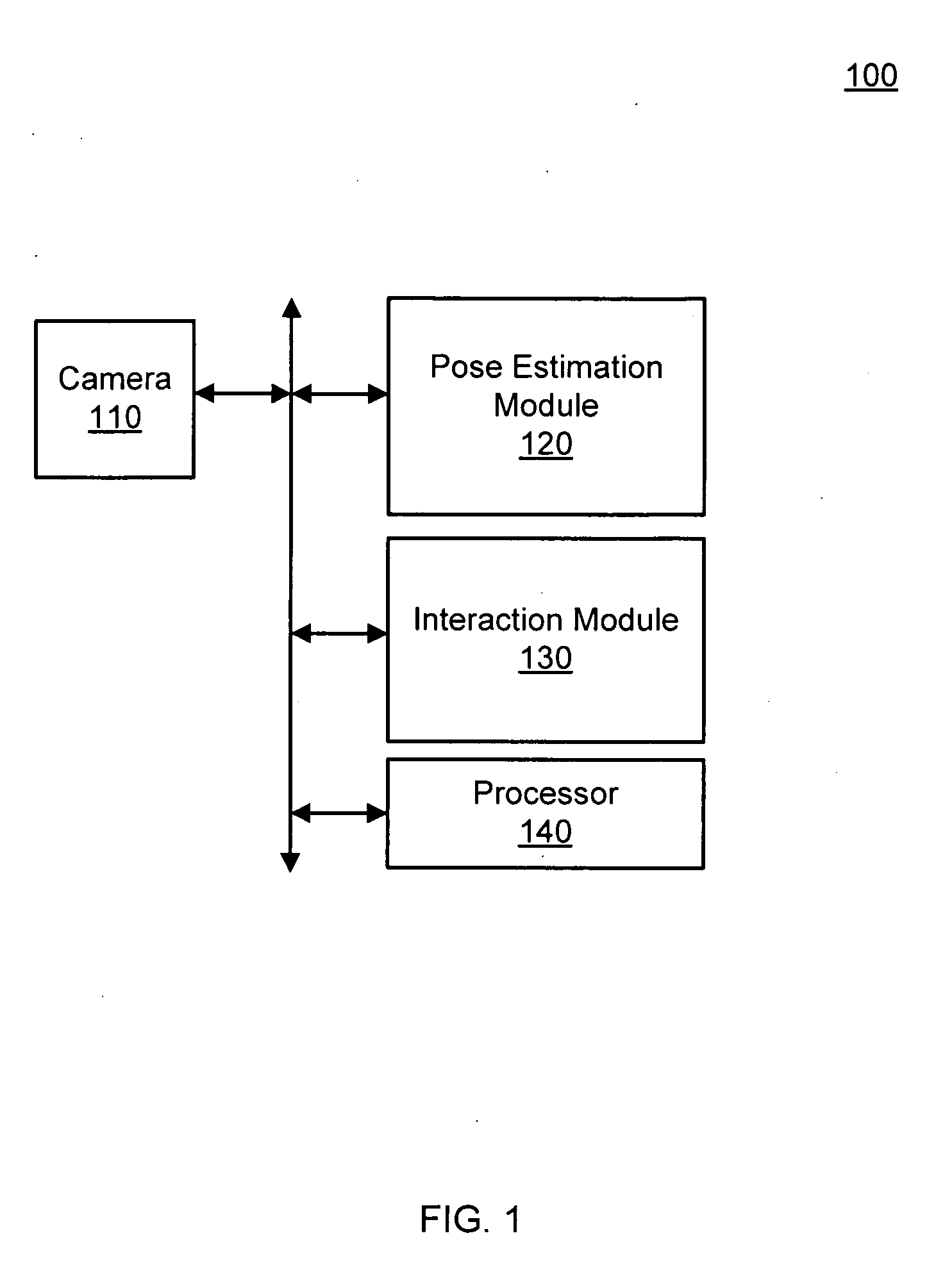
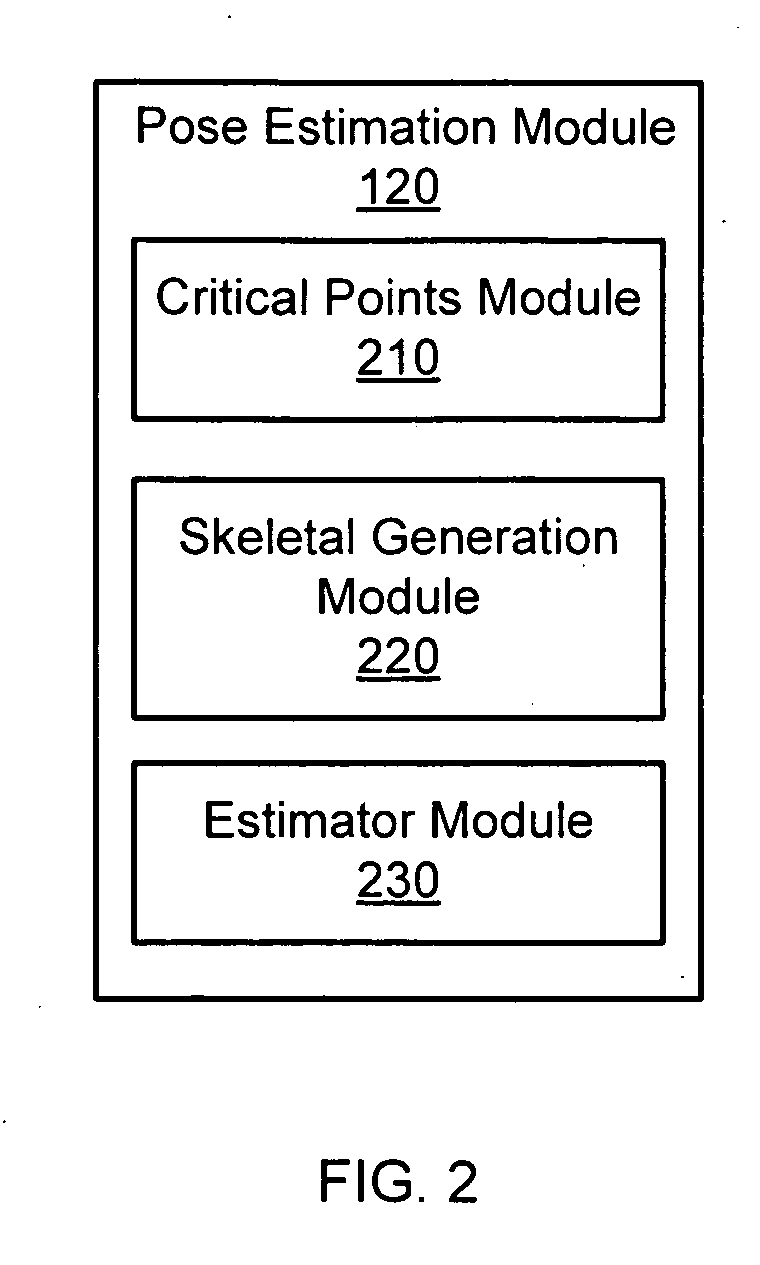
Pose estimation based on critical point analysis
Owner:THE OHIO STATE UNIV RES FOUND +1
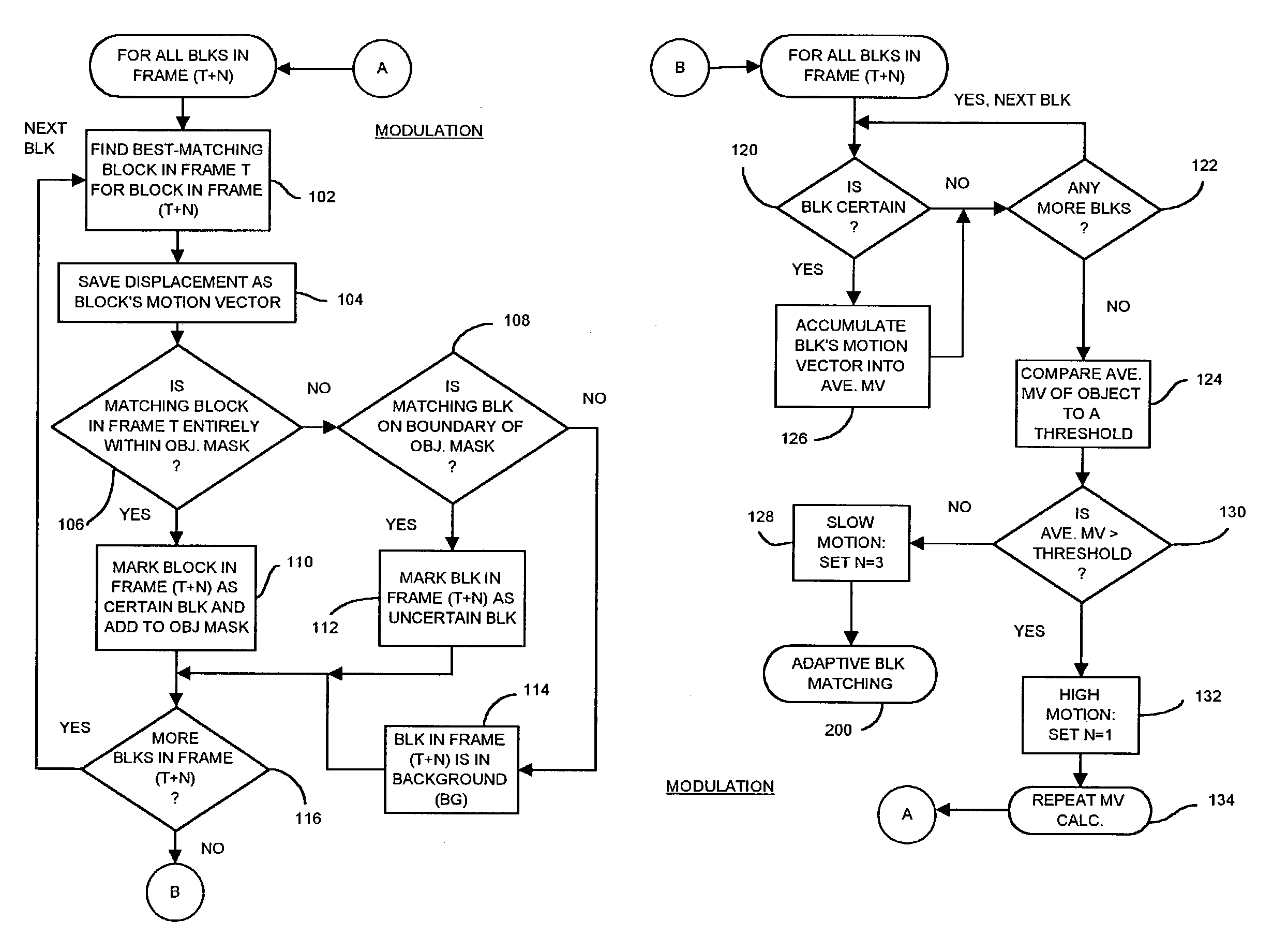
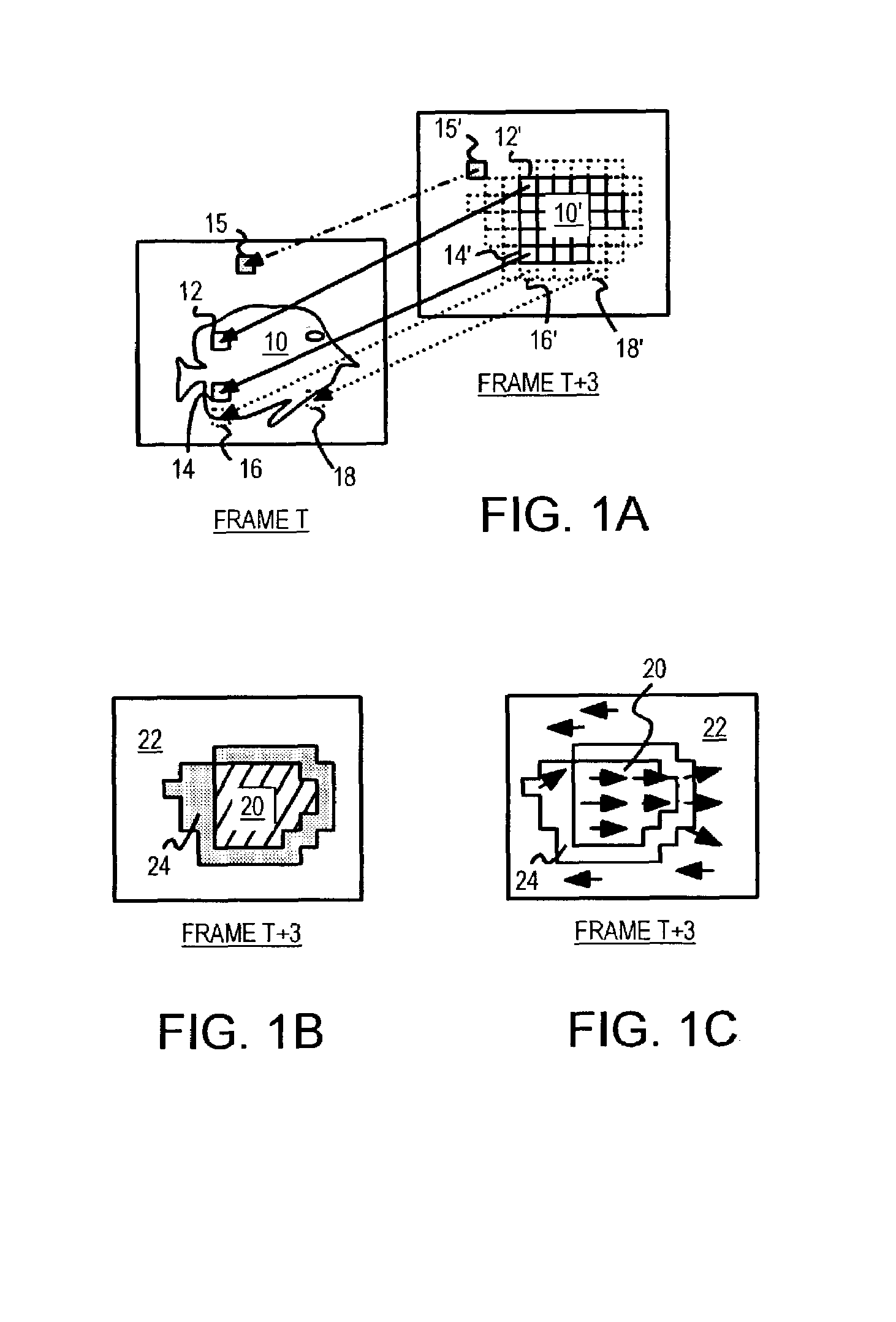
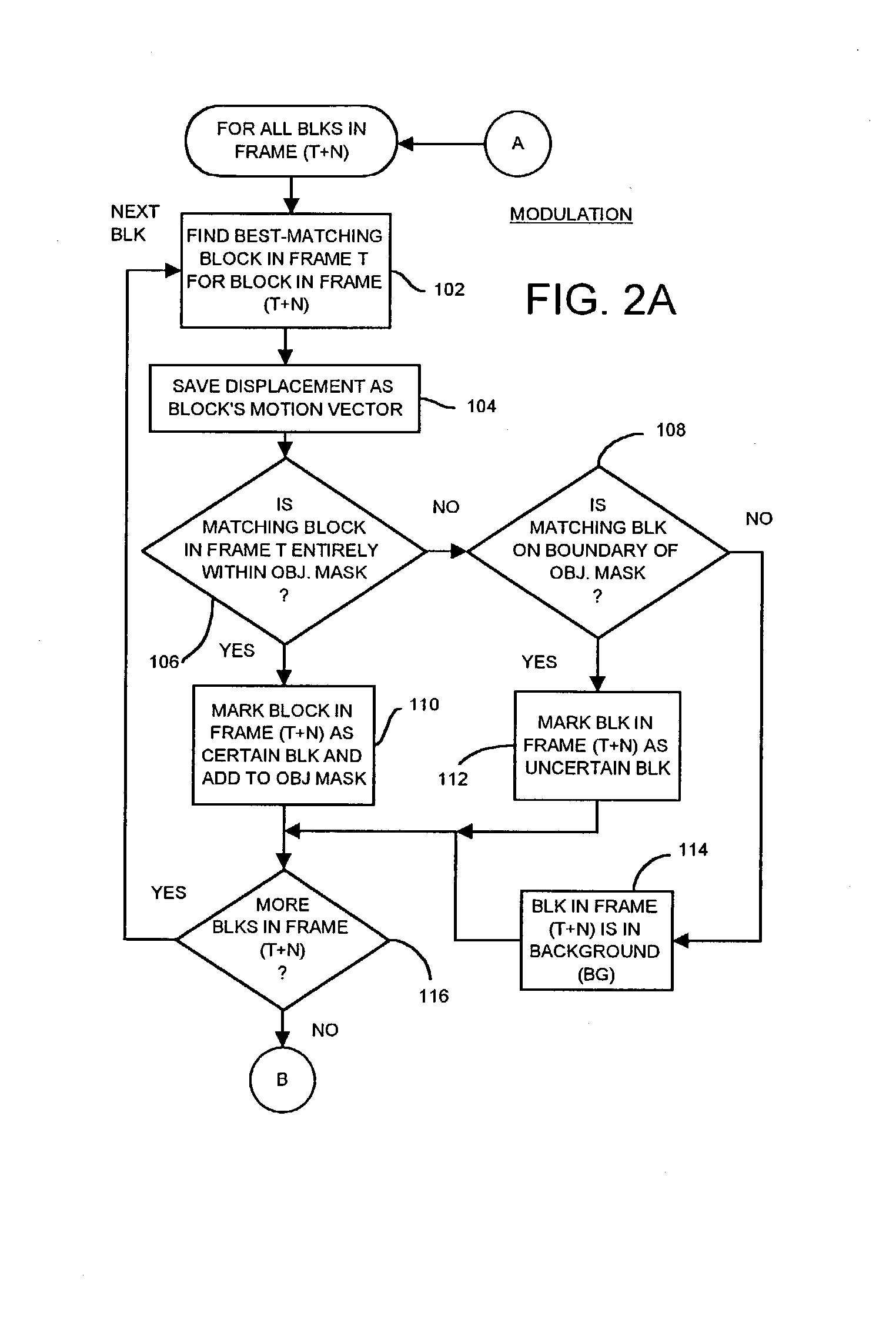
Occlusion/disocclusion detection using K-means clustering near object boundary with comparison of average motion of clusters to object and background motions
ActiveUS7142600B1Reduce varianceAccurate representationColor television with pulse code modulationImage analysisMotion vectorVideo sequence
An object in a video sequence is tracked by object masks generated for frames in the sequence. Macroblocks are motion compensated to predict the new object mask. Large differences between the next frame and the current frame detect suspect regions that may be obscured in the next frame. The motion vectors in the object are clustered using a K-means algorithm. The cluster centroid motion vectors are compared to an average motion vector of each suspect region. When the motion differences are small, the suspect region is considered part of the object and removed from the object mask as an occlusion. Large differences between the prior frame and the current frame detect suspected newly-uncovered regions. The average motion vector of each suspect region is compared to cluster centroid motion vectors. When the motion differences are small, the suspect region is added to the object mask as a disocclusion.
Owner:INTELLECTUAL VENTURES I LLC
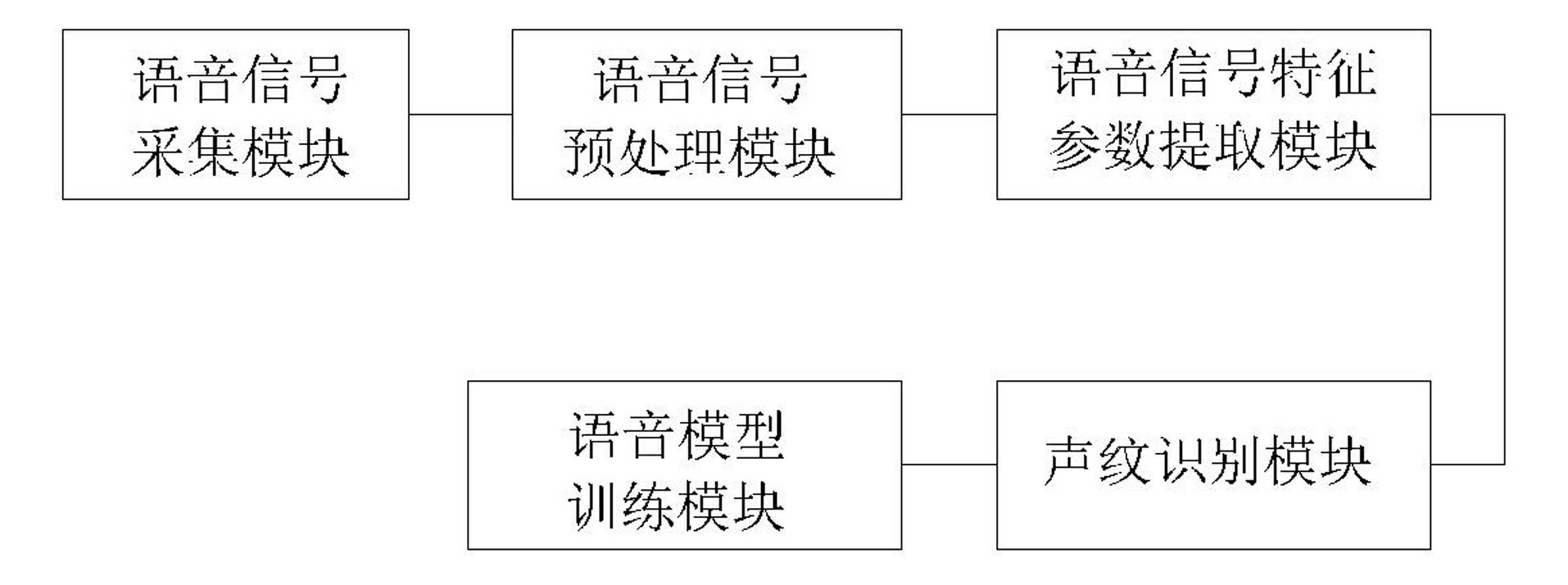
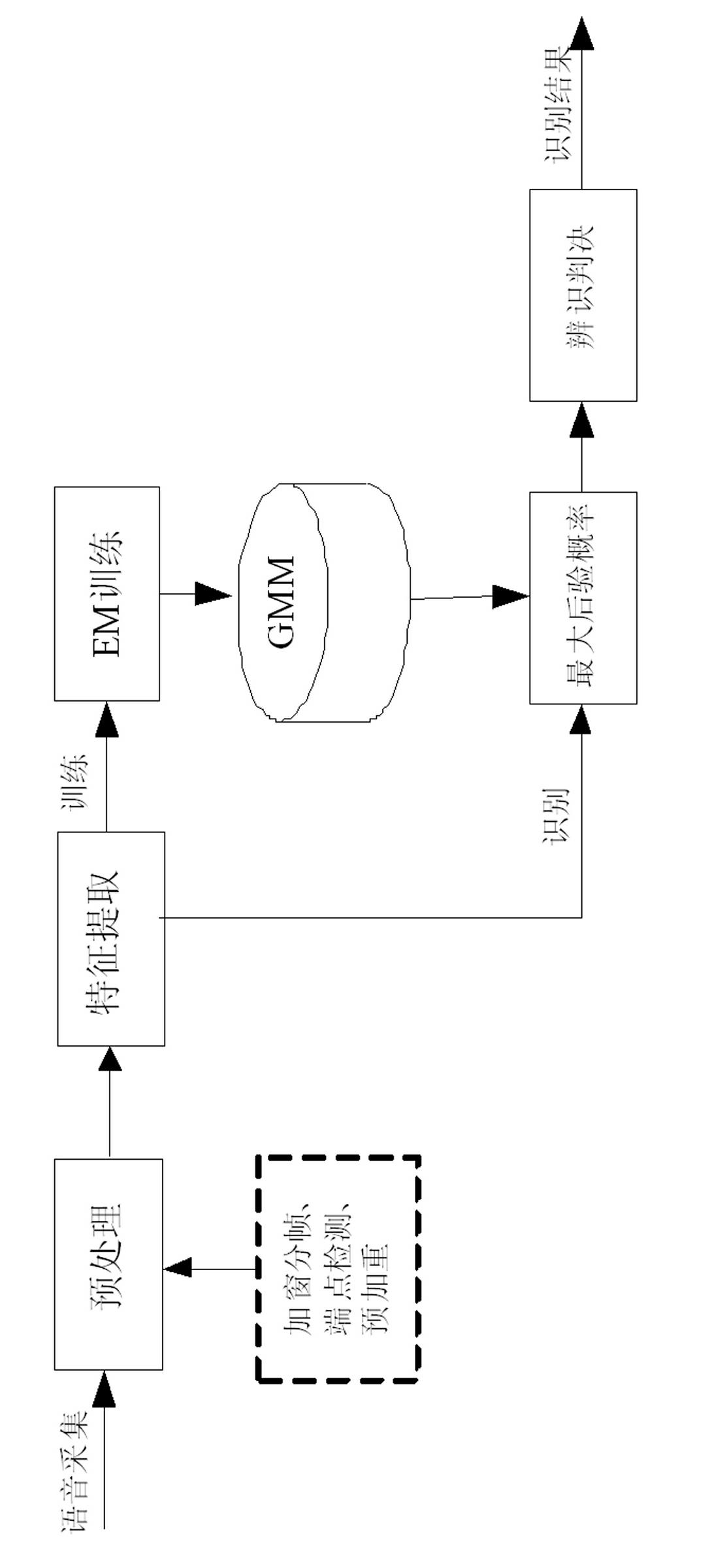
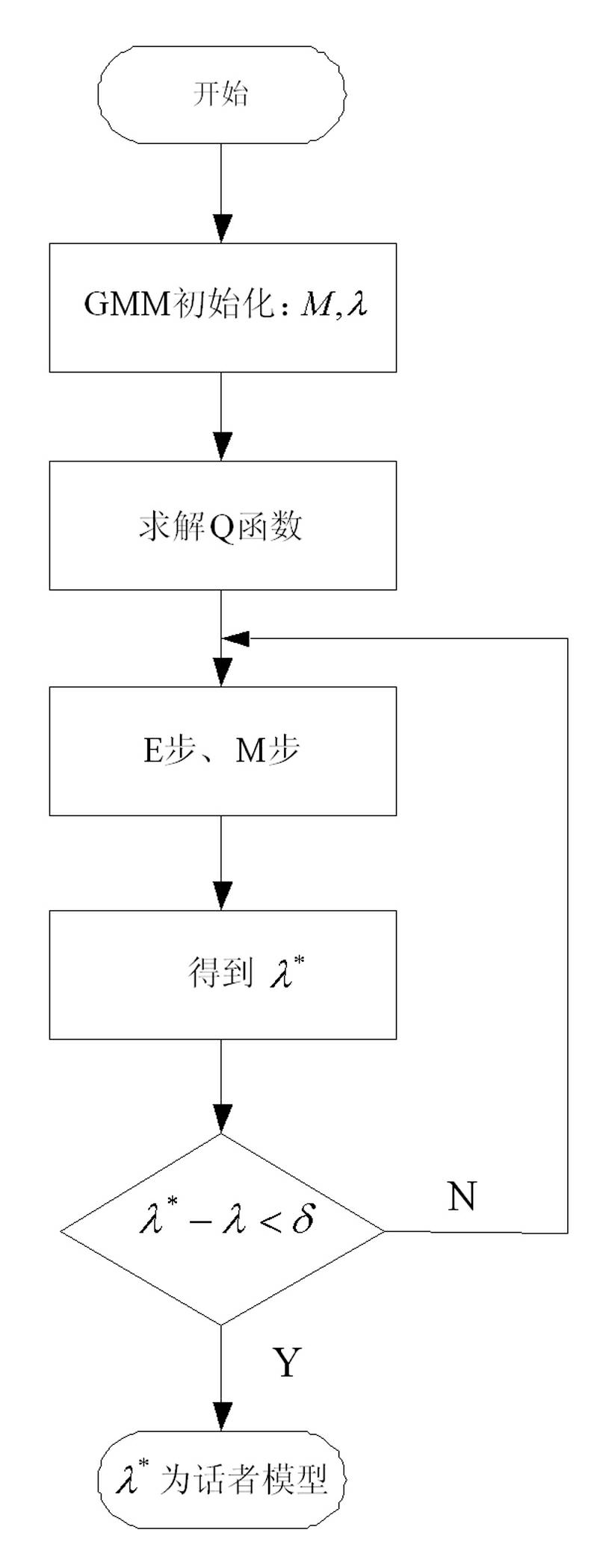
Voiceprint identification method based on Gauss mixing model and system thereof
InactiveCN102324232AGood estimateEasy to trainSpeech recognitionMel-frequency cepstrumNormal density
The invention provides a voiceprint identification method based on a Gauss mixing model and a system thereof. The method comprises the following steps: voice signal acquisition; voice signal pretreatment; voice signal characteristic parameter extraction: employing a Mel Frequency Cepstrum Coefficient (MFCC), wherein an order number of the MFCC usually is 12-16; model training: employing an EM algorithm to train a Gauss mixing model (GMM) for a voice signal characteristic parameter of a speaker, wherein a k-means algorithm is selected as a parameter initialization method of the model; voiceprint identification: comparing a collected voice signal characteristic parameter to be identified with an established speaker voice model, carrying out determination according to a maximum posterior probability method, and if a corresponding speaker model enables a speaker voice characteristic vector X to be identified to has maximum posterior probability, identifying the speaker. According to the method, the Gauss mixing model based on probability statistics is employed, characteristic distribution of the speaker in characteristic space can be reflected well, a probability density function is common, a parameter in the model is easy to estimate and train, and the method has good identification performance and anti-noise capability.
Owner:LIAONING UNIVERSITY OF TECHNOLOGY
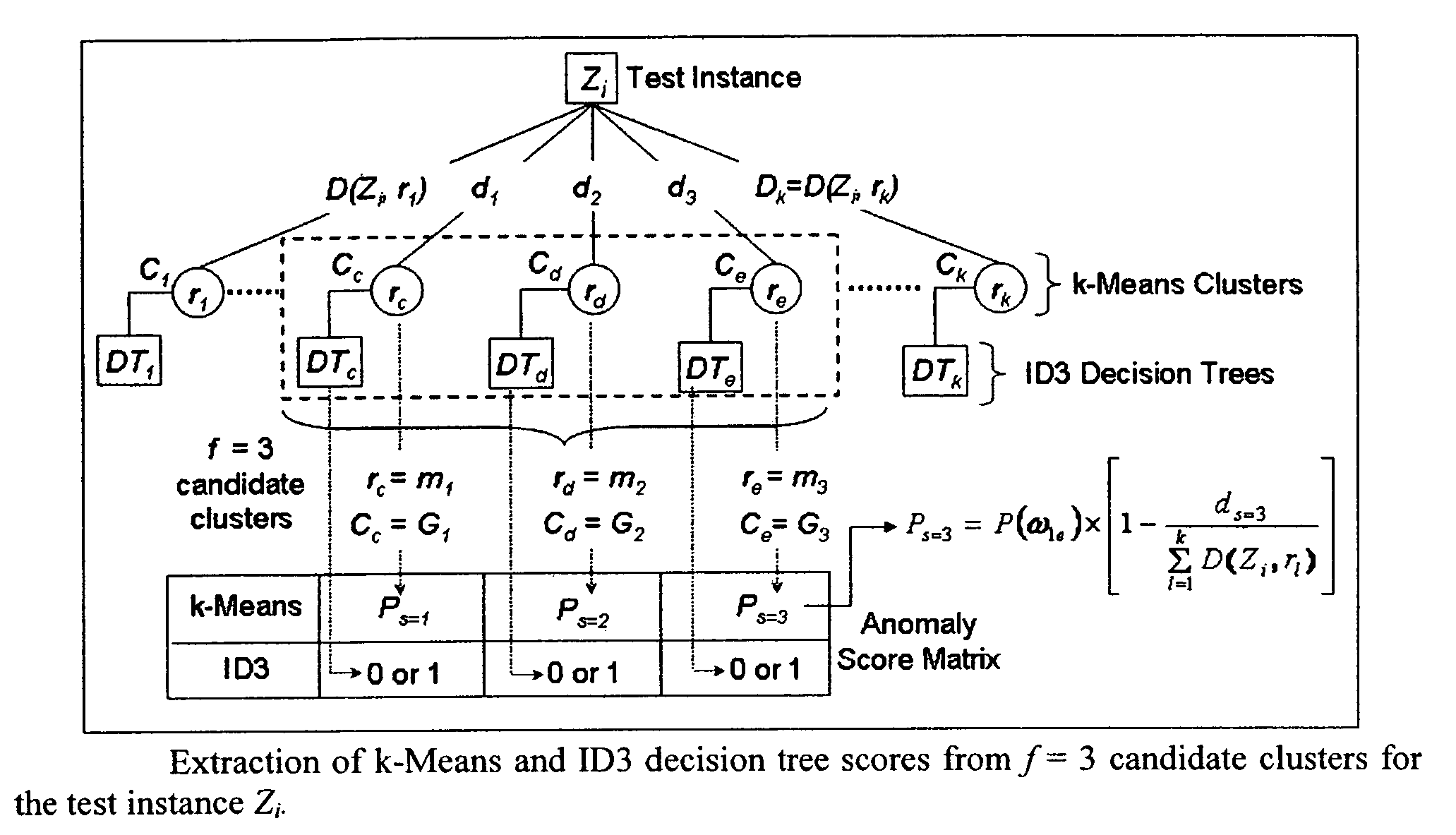
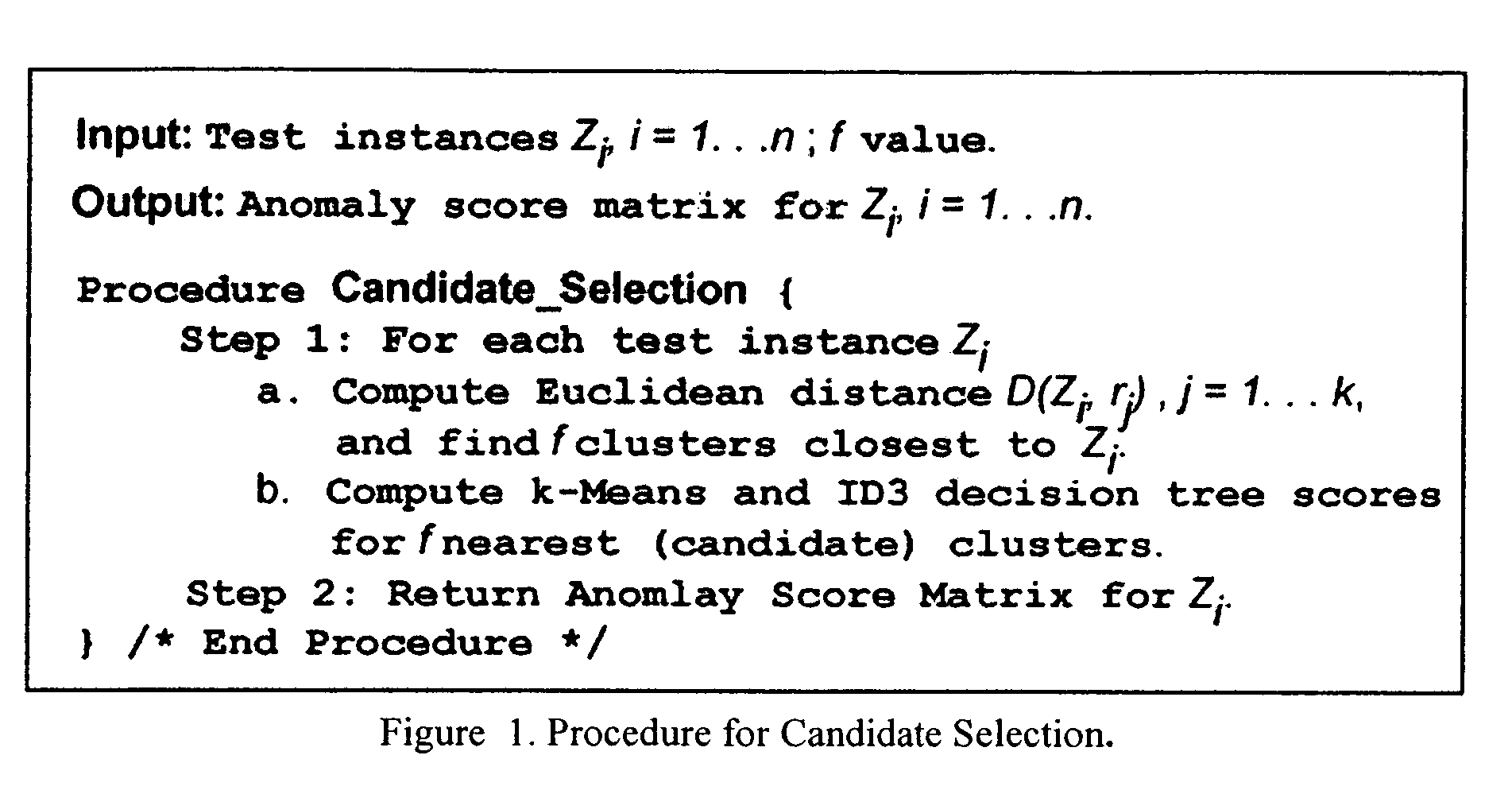
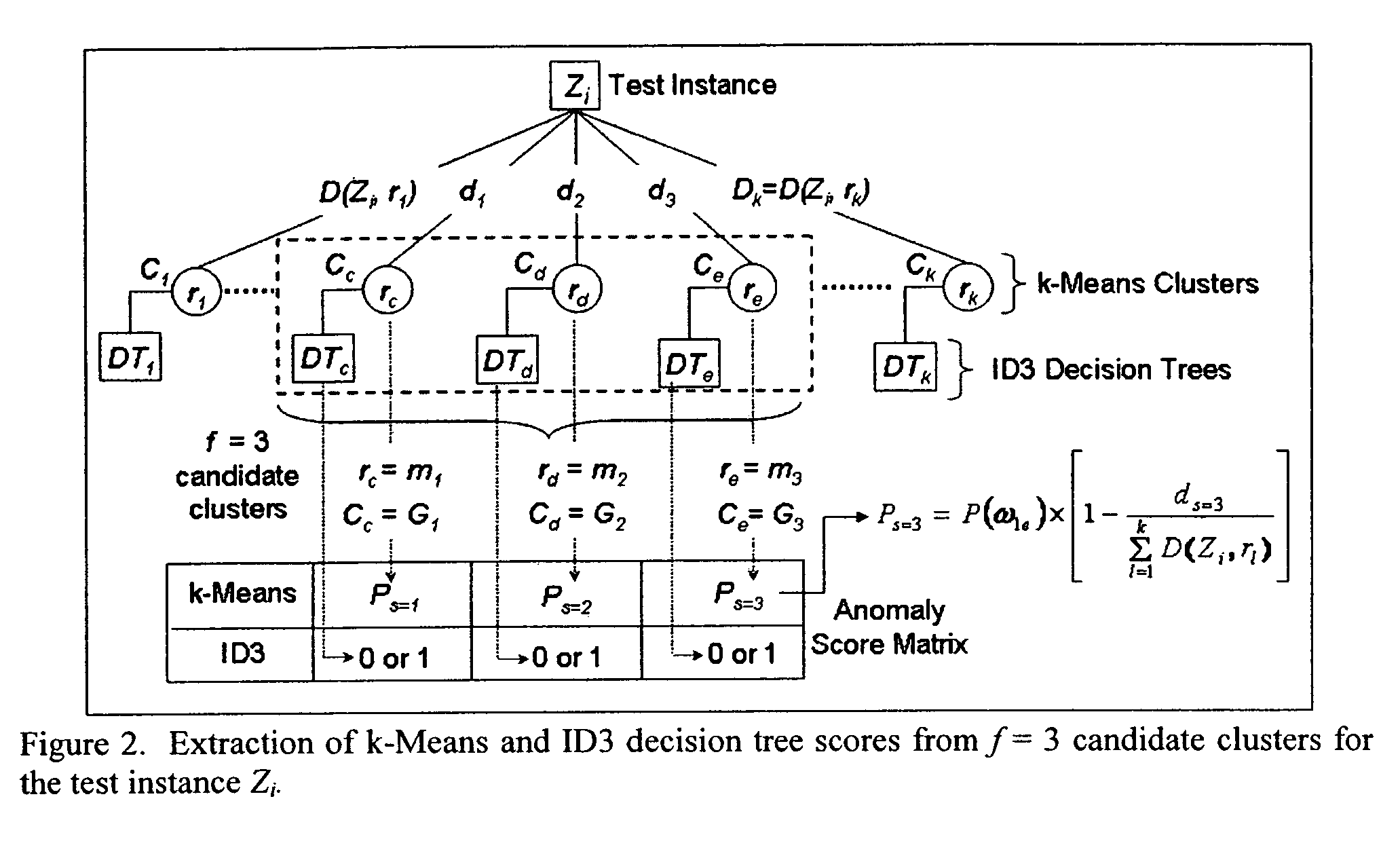
Method to indentify anomalous data using cascaded K-Means clustering and an ID3 decision tree
The invention is a computer implemented technique for id entifying anomalous data in a data set. The method uses cascaded k-Means clustering and the ID3 decision tree learning methods to characterize a training data set having data points with known characterization. The k-Means clustering method first partitions the training instances into k clusters using Euclidean distance similarity. On each training cluster, representing a density region of normal or anomaly instances, the invention builds an ID3 decision tree. The decision tree on each cluster refines the decision boundaries by learning the sub-groups within the cluster. A test data point is then subjected to the clustering and decision trees constructed form the training instances. To obtain a final decision on classification, the decisions of the k-Means and ID3 methods are combined using rules: (1) the Nearest-neighbor rule, and (2) the Nearest-consensus rule.
Owner:LOUISIANA TECH RES CORP
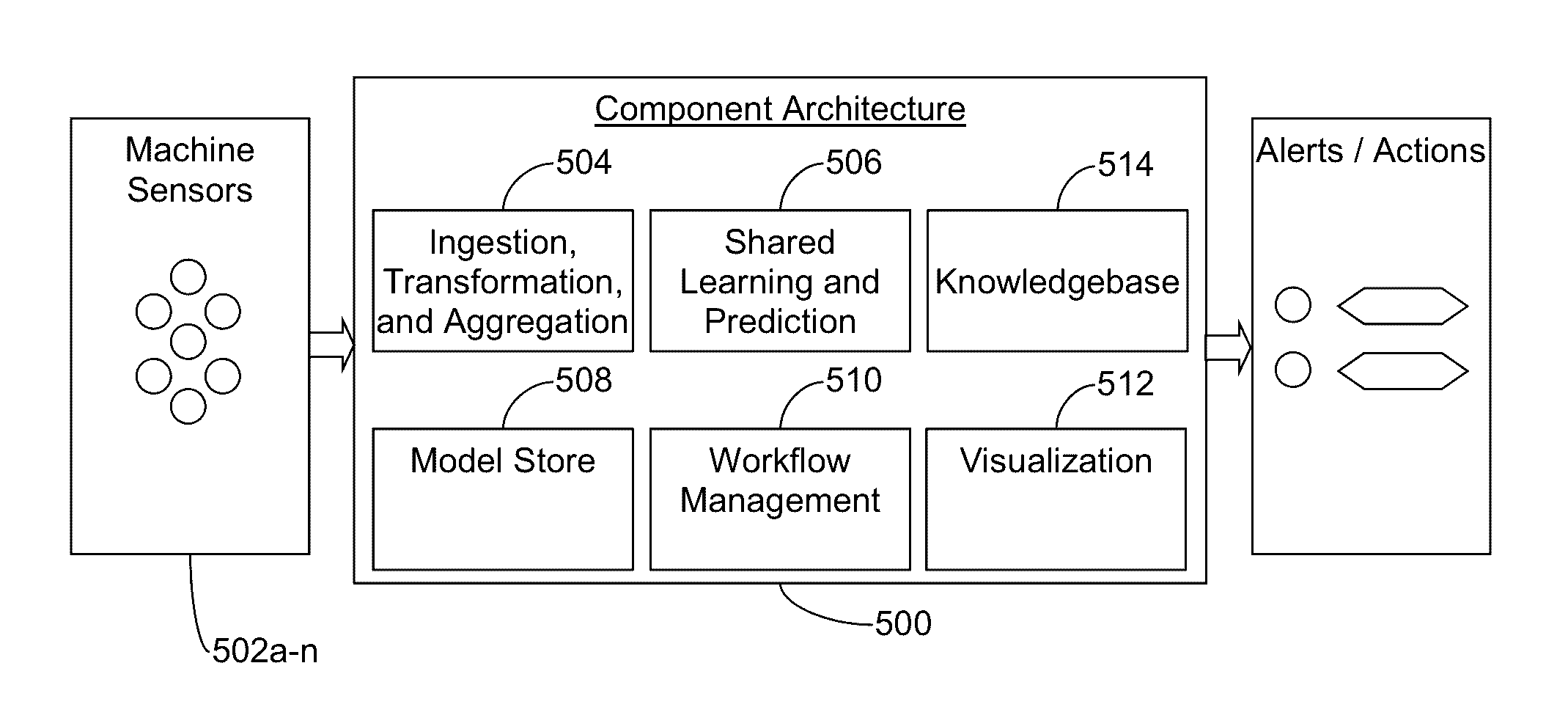
Systems and/or methods for dynamic anomaly detection in machine sensor data
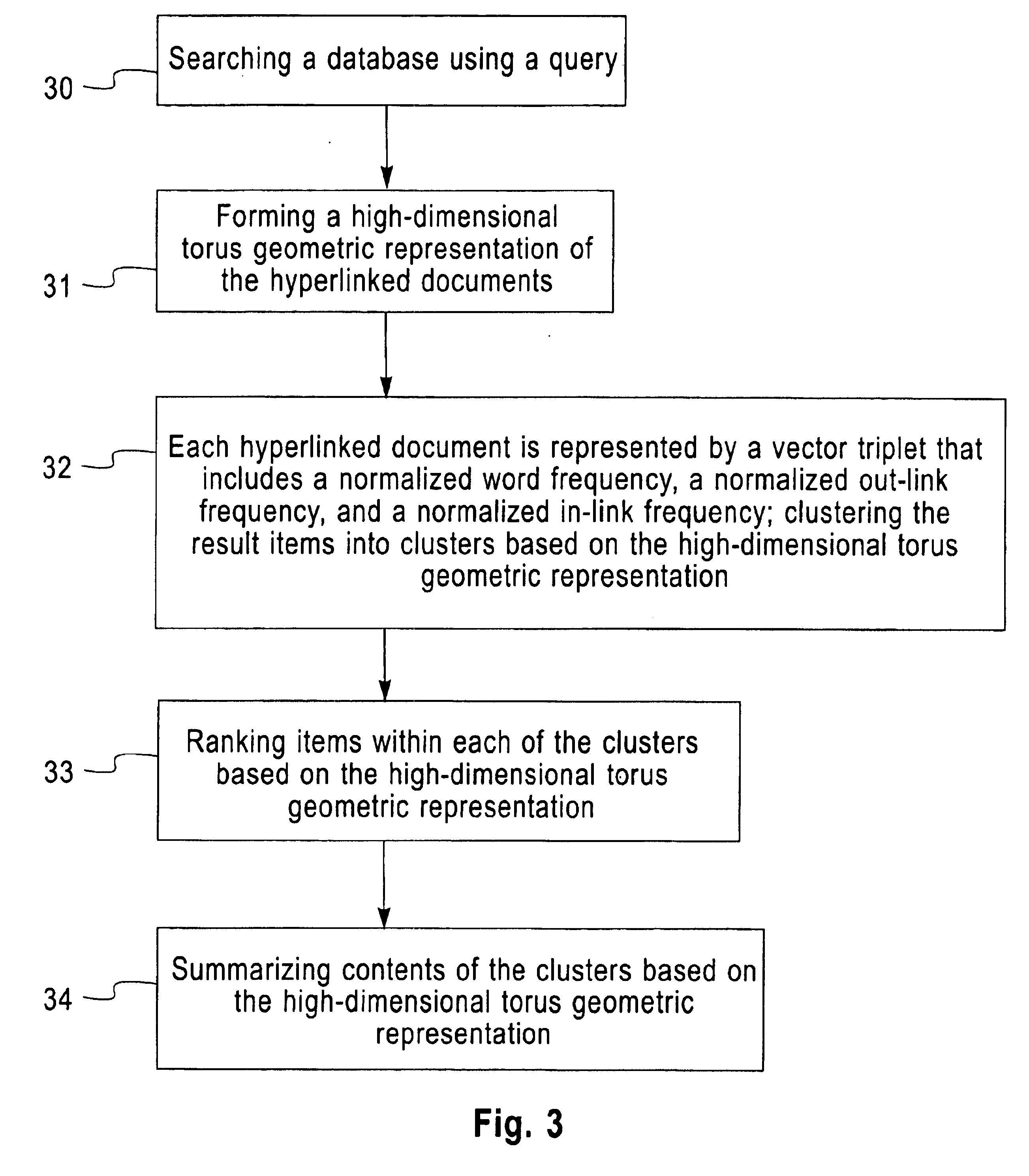
ActiveUS20160342903A1Reduce the possibilityQuickly and in large amountFault responseReliability/availability analysisIndefinite timeCluster algorithm
Certain example embodiments relate to techniques for detecting anomalies in streaming data. More particularly, certain example embodiments use an approach that combines both unsupervised and supervised machine learning techniques to create a shared anomaly detection model in connection with a modified k-means clustering algorithm and advantageously also enables concept drift to be taken into account. The number of clusters k need not be known in advance, and it may vary over time. Models are continually trainable as a result of the dynamic reception of data over an unknown and potentially indefinite time period, and clusters can be built incrementally and in connection with an updatable distance threshold that indicates when a new cluster is to be created. Distance thresholds also are dynamic and adjustable over time.
Owner:SOFTWARE AG USA
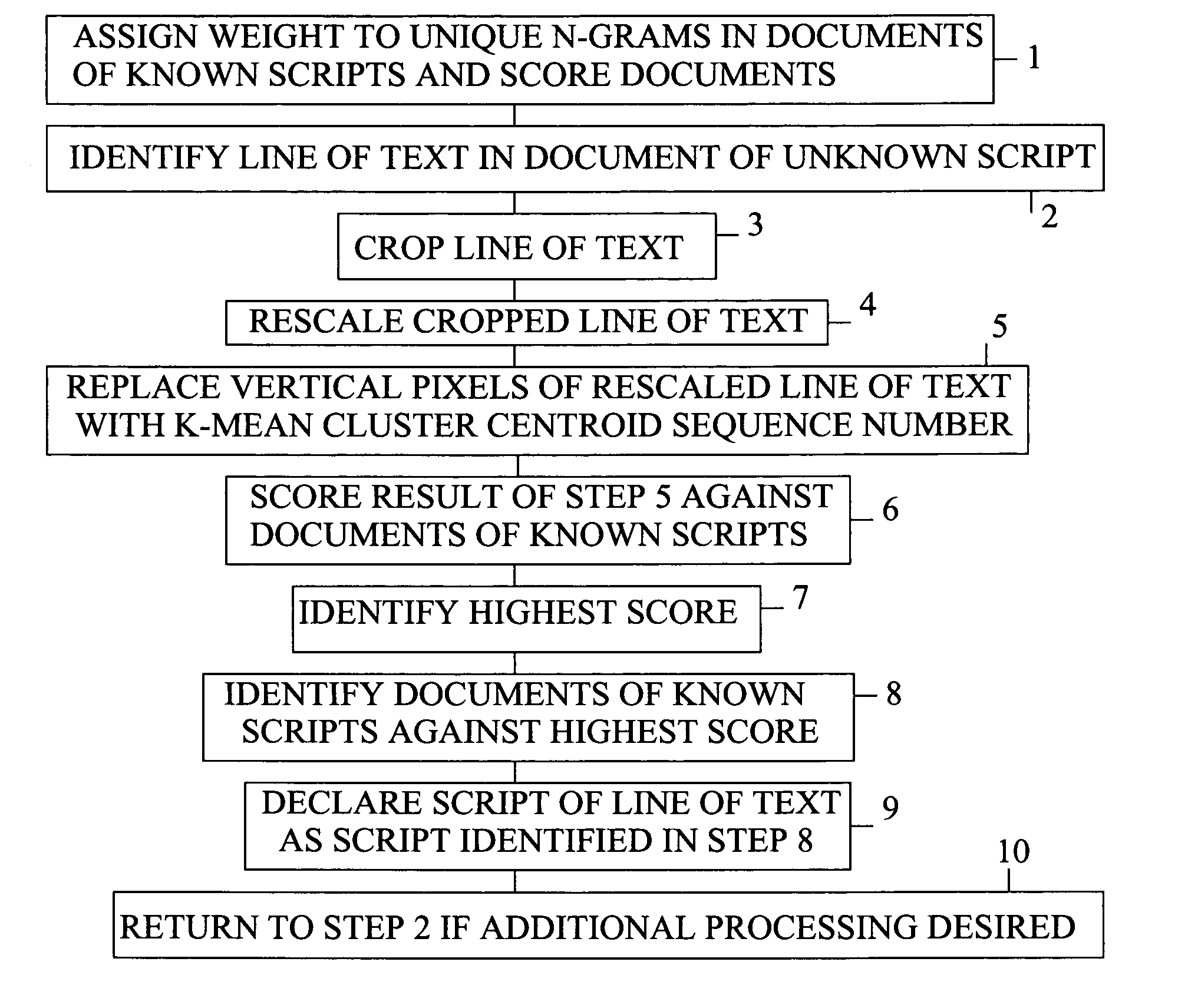
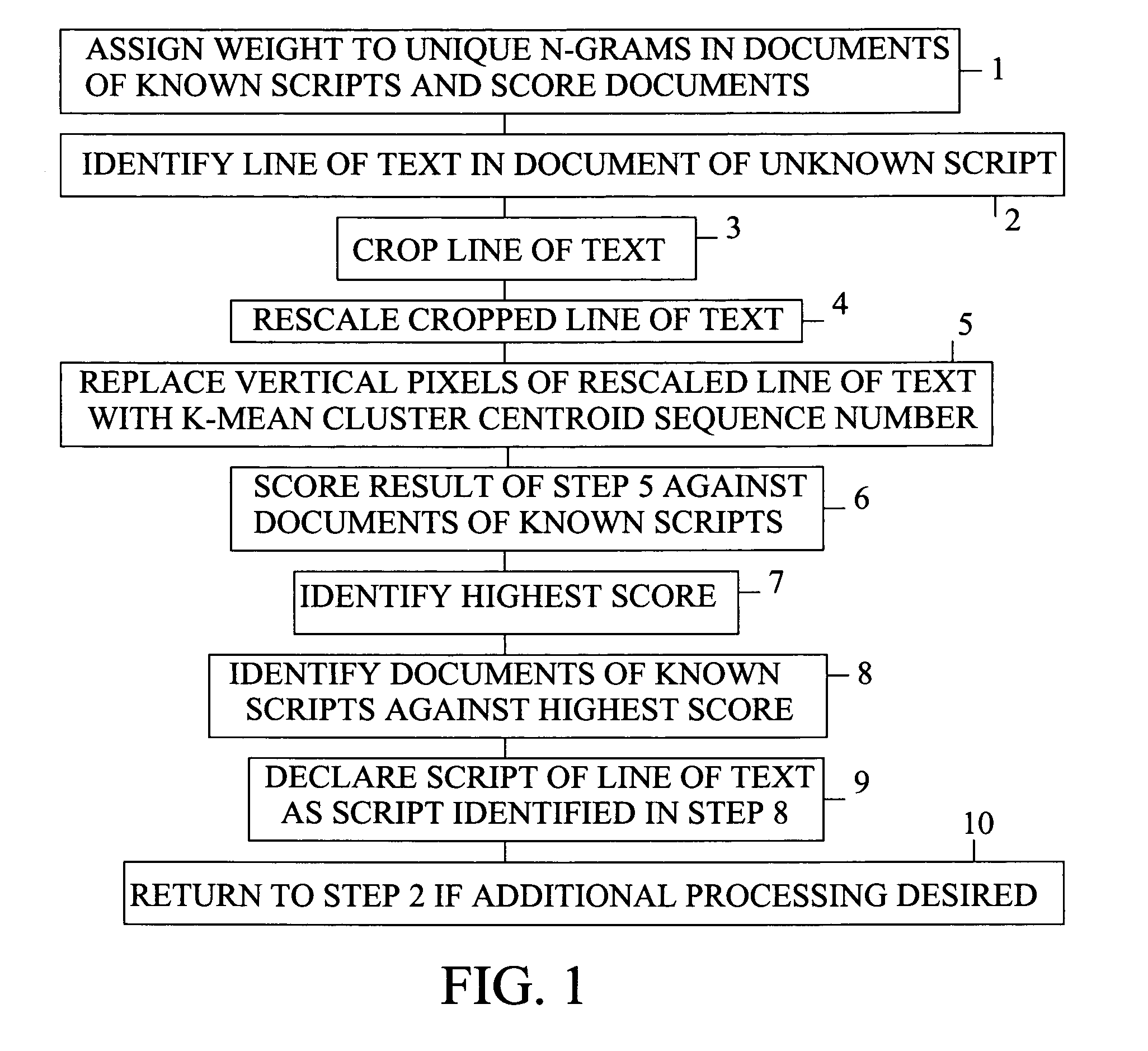
Method of identifying script of line of text
InactiveUS7020338B1Character and pattern recognitionNatural language data processingPattern recognitionDocument preparation
A method of identifying the script of a line of text by first assigning a weight to each n-gram in a group of documents of known scripts, where each n-gram is a sequence of numbers representing k-mean cluster centroids of a known script to which character segments in the documents of known scripts most closely match. A line of text is identified, where the line of text is made up of pixels. The identified line of text is cropped so that only a percentage of the pixels remain. The cropped line is vertically and horizontally rescaled into gray-scale pixels. The vertical gray-scale pixels are replaced with the sequence number of a k-means cluster centroid of a known script to which it most closely matches. The n-grams of the number sequence that represents the line of text is scored against the n-gram weights of the documents of known text. The highest score of the line of text is identified and compared to the scores of the documents of known scripts. The script of the line of text is determined to be the script of the document against which the line of text scores the highest.
Owner:NATIONAL SECURITY AGENCY
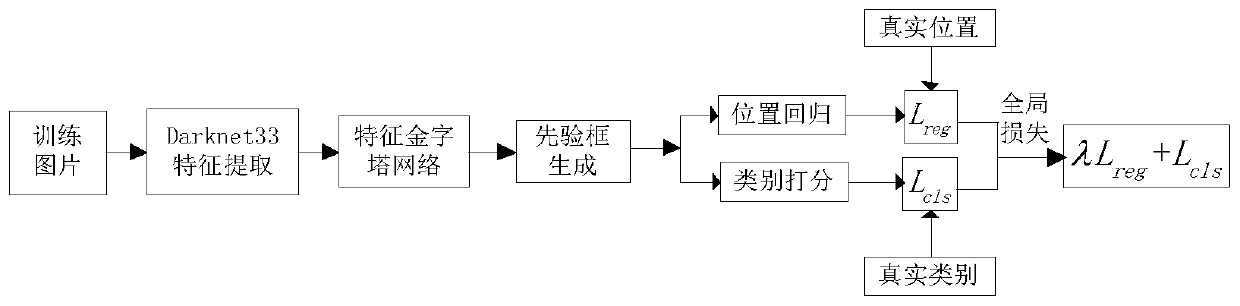
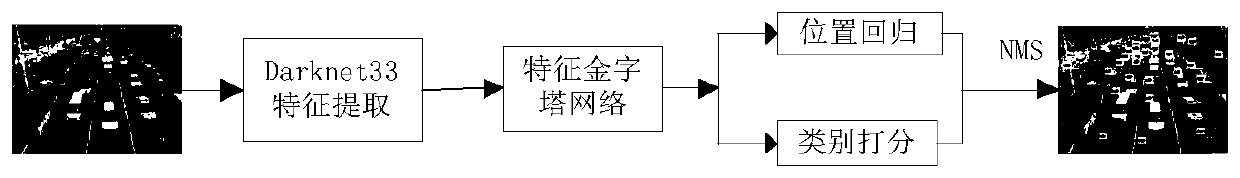
A pedestrian and vehicle detection method and system based on improved YOLOv3
ActiveCN109815886ADetection matchHigh speedCharacter and pattern recognitionNeural architecturesMulti-label classificationVehicle detection
The invention discloses a pedestrian and vehicle detection method and system based on improved YOLOv3. According to the method, an improved YOLOv3 network based on Darknet-33 is adopted as a main network to extract features; the cross-layer fusion and reuse of multi-scale features in the backbone network are carried out by adopting a transmittable feature map scale reduction method; and then a feature pyramid network is constructed by adopting a scale amplification method. In the training stage, a K-means clustering method is used for clustering the training set, and the cross-to-parallel ratio of a prediction frame to a real frame is used as a similarity standard to select a priori frame; and then the BBox regression and the multi-label classification are performed according to the loss function. And in the detection stage, for all the detection frames, a non-maximum suppression method is adopted to remove redundant detection frames according to confidence scores and IOU values, and an optimal target object is predicted. According to the method, a feature extraction network Darknet-33 of feature map scale reduction fusion is adopted, a feature pyramid is constructed through feature map scale amplification migration fusion, and a priori frame is selected through clustering, so that the speed and precision of the pedestrian and vehicle detection can be improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
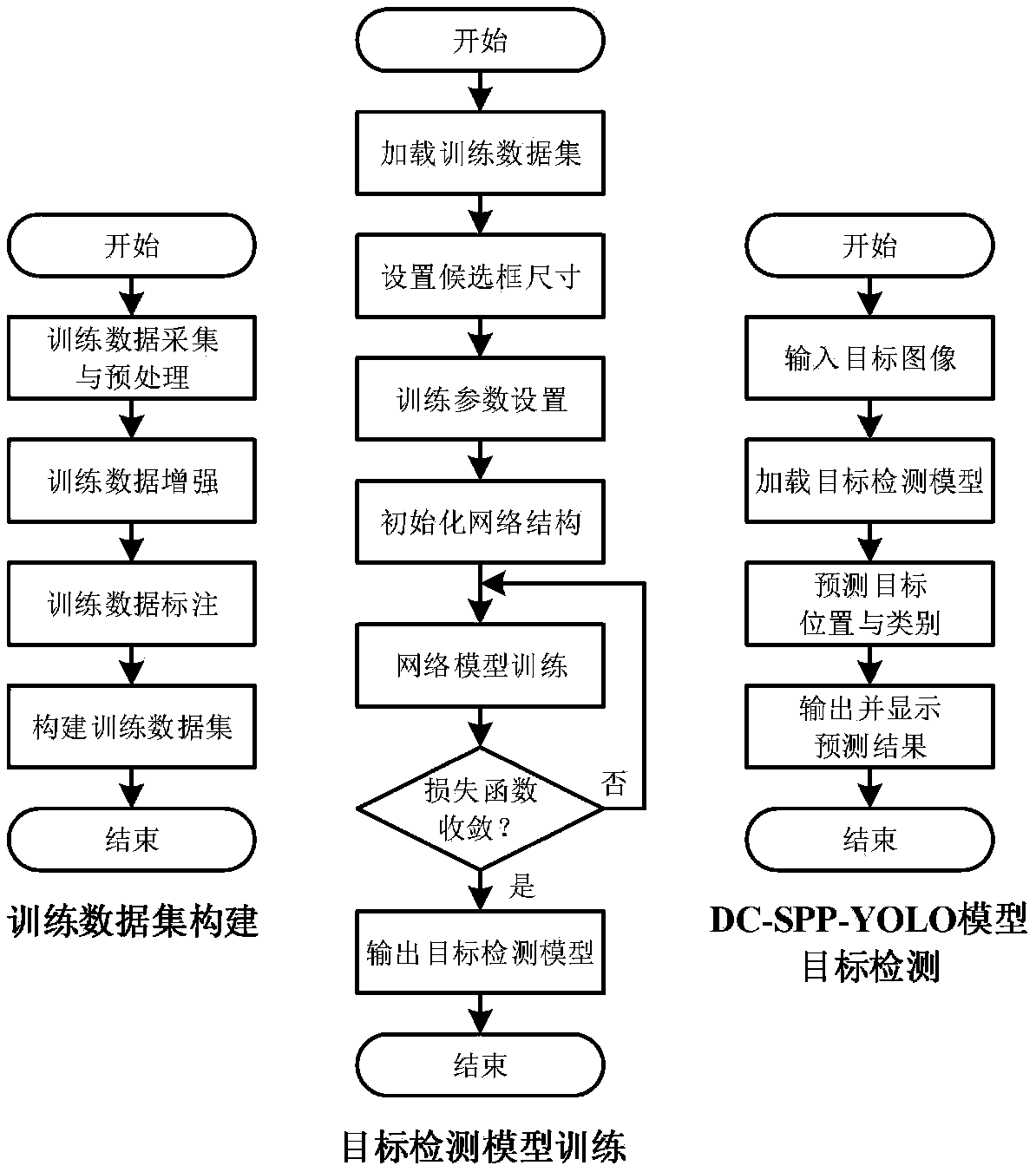
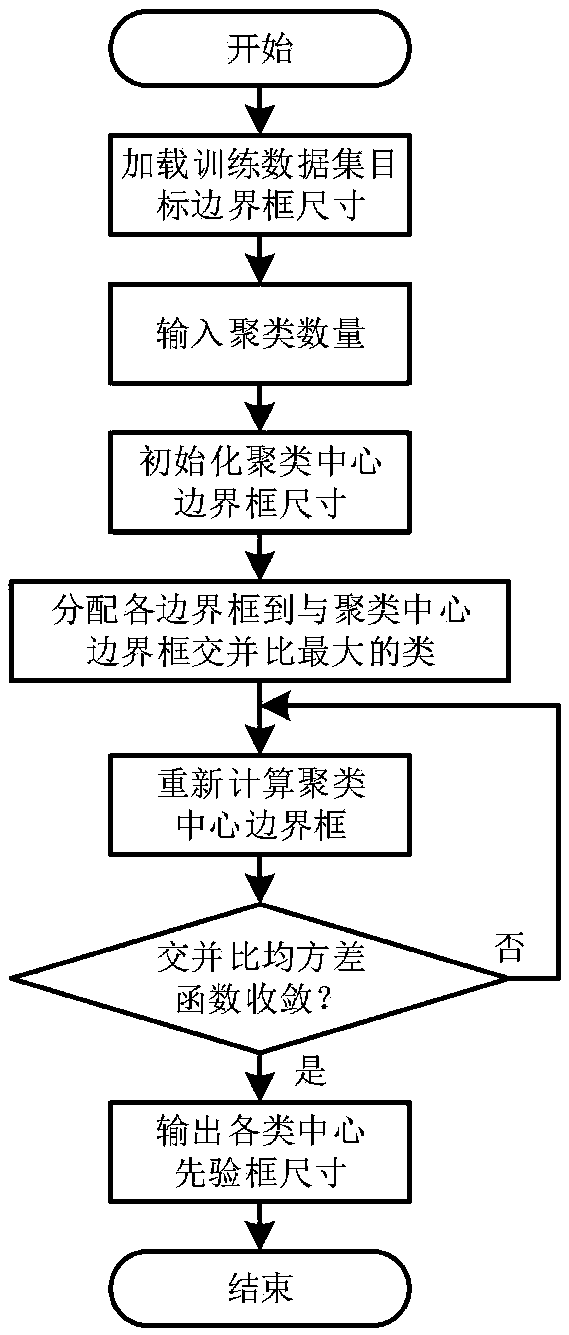
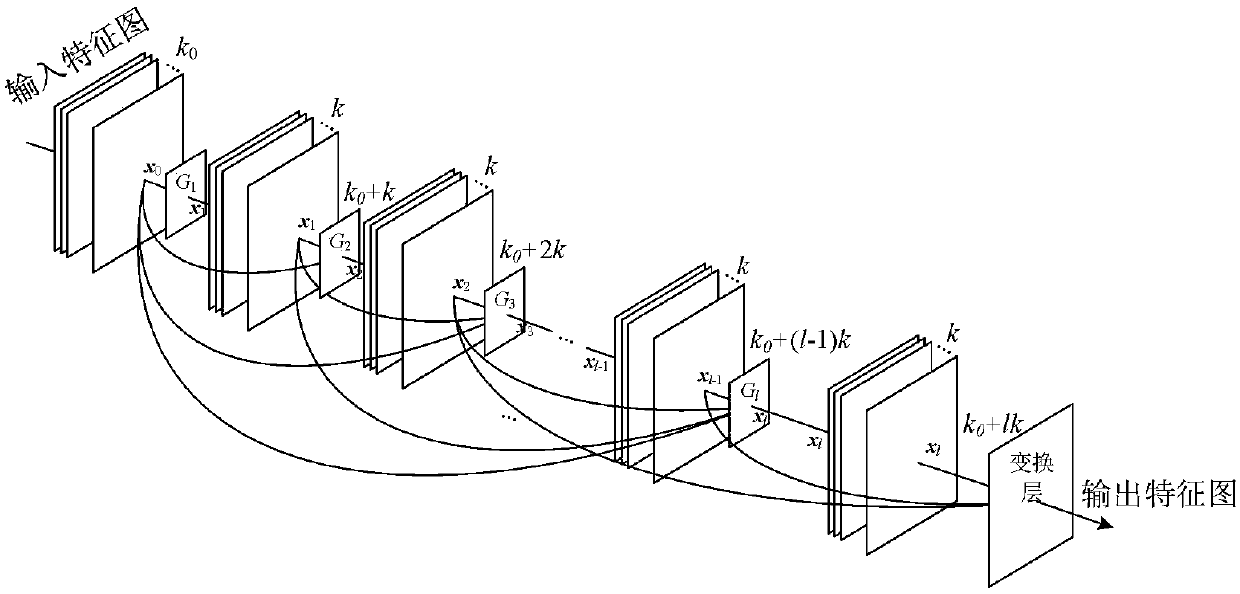
An image target detection method based on DC-SPP-YOLO
ActiveCN109685152AEnhancing feature propagationHigh precisionCharacter and pattern recognitionPattern recognitionPyramid
The invention discloses an image target detection method based on DC-SPP-YOLO, which comprises the following steps: firstly, preprocessing a training image sample by using a data enhancement method,constructing a training sample set, aSelecting a prior candidate box for target boundary box prediction by using a k-means clustering algorithm; Then, improving the convolutional layer connection modeof the YOLOv2 model from layer-by-layer connection to dense connection, introducing a space pyramid pooling between the convolutional module and a target detection layer, and establishing DC-SPP-YOLOtarget detection model; And finally, constructing a loss function by using an error quadratic sum between the predicted value and the real value, and iteratively updating model weight parameters to converge the loss function to obtain the DC-SPP-YOLO model for target detection. The invention considers the gradient disappearance caused by deepening convolution network and the insufficient use of multi-scale local region features of YOLOv2 model, and constructs a DC-SPP-YOLO target detection model based on improved convolution layer dense connection and spatial pyramid pooling. the target detection accuracy is improved.
Owner:BEIJING UNIV OF CHEM TECH
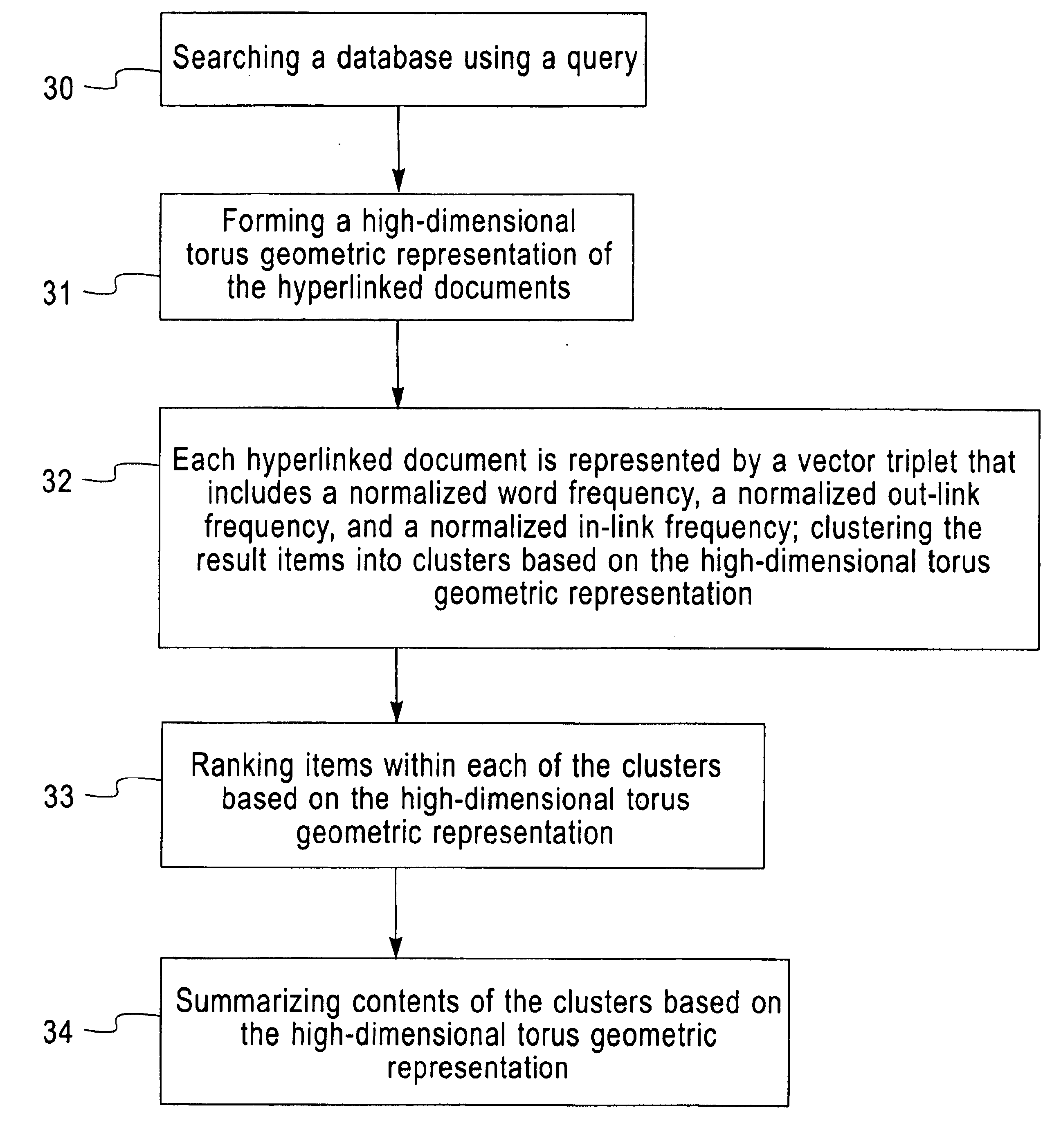
Searching databases that identifying group documents forming high-dimensional torus geometric k-means clustering, ranking, summarizing based on vector triplets
InactiveUS6862586B1Data processing applicationsDigital data information retrievalHigh dimensionalDocumentation
Owner:IBM CORP
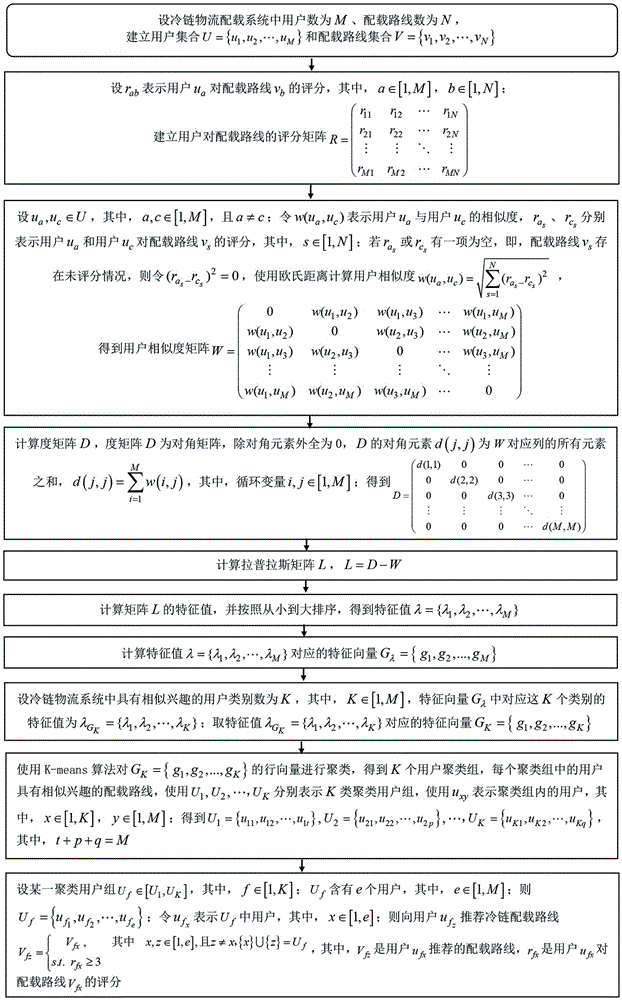
Cold-chain logistic stowage intelligent recommendation method based on spectral cl9ustering
InactiveCN105654267AReduce the no-load ratioIncrease profit marginsCharacter and pattern recognitionLogisticsCold chainRating matrix
The invention discloses a cold-chain logistic stowage intelligent recommendation method based on spectral clustering. Scores of users for a stowage line are conveyed through a cold chain for cold-chain logistic stowage intelligent recommending, a score matrix is built, the Euclidean distance is used for calculating the user similarity, a degree matrix is used for calculating a Laplacian matrix, feature vectors are obtained by calculating feature values of the orderly Laplacian matrix, a K-means algorithm is used for clustering the feature values to obtain a user group with the similar interesting stowage line, and a stowage line is recommended inside the user group with the similar interesting stowage line, so that cold-chain logistic stowage intelligent recommending is achieved, the cold-chain logistic vehicle non-load ratio is lowered, and the profit rate of cold-chain logistic transport vehicles is increased.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
Hard disk failure prediction method for cloud computing platform
InactiveCN104503874AHigh fault recall rateImprove performanceDetecting faulty computer hardwareHardware monitoringDensity basedSupport vector machine classifier
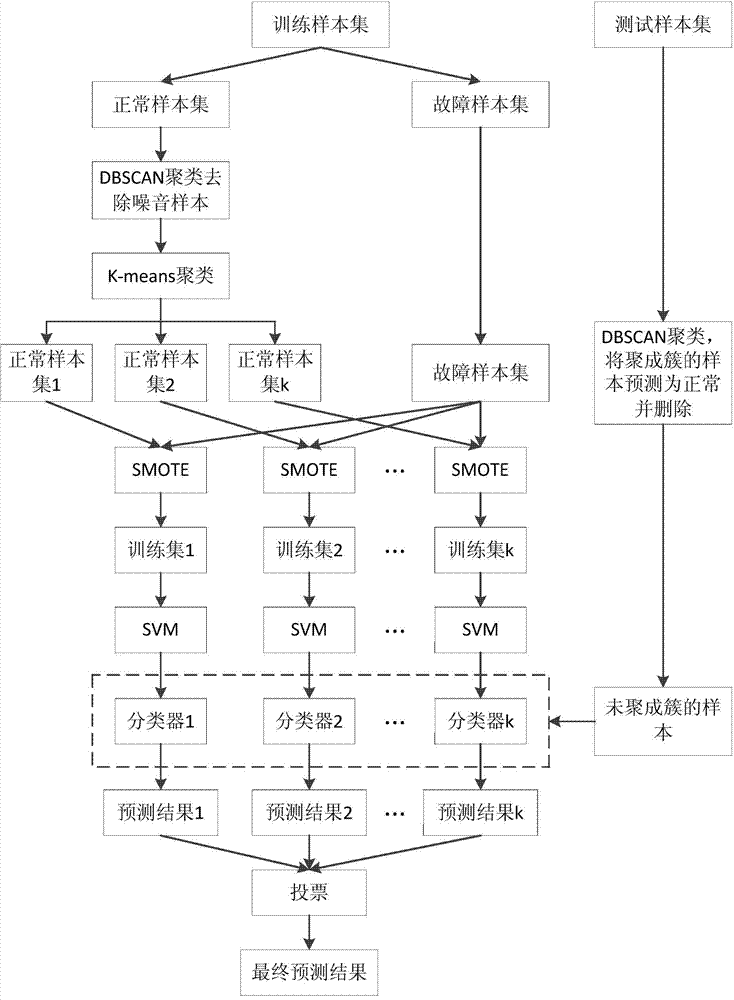
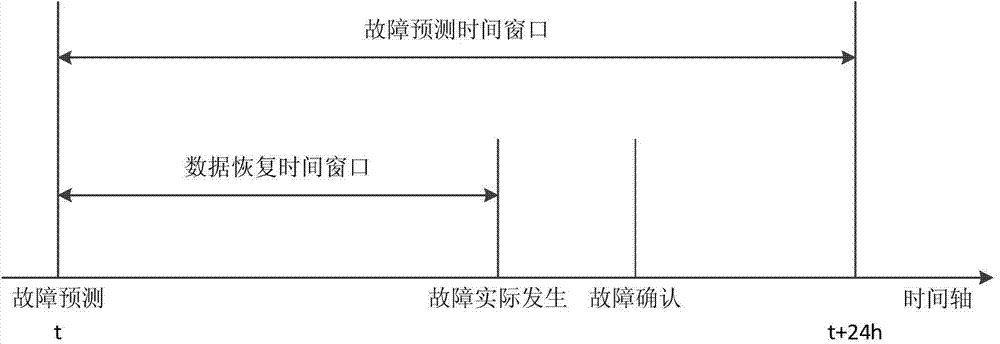
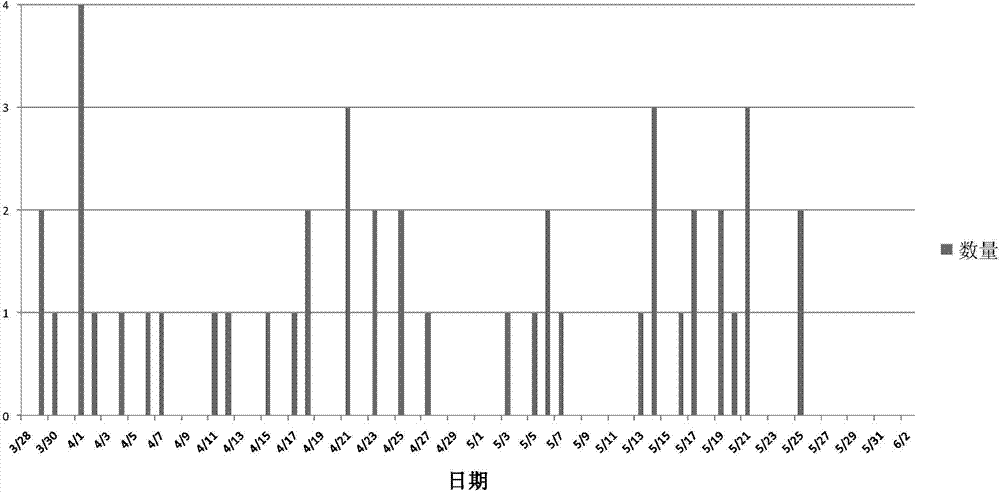
The invention discloses a hard disk failure prediction method for a cloud computing platform. The hard disk failure predication method comprises the following steps: marking SMART log data of a hard disk as a normal hard disk sample and a faulted hard disk sample according to a hard disk maintenance record in a prediction time window; then, dividing the denoised normal hard disk sample into k non-intersected subsets by adopting a K-means clustering algorithm; combining the k non-intersected subsets with the faulted hard disk sample respectively; generating k groups of balance training sets according to an SMOTE (Synthetic Minority Oversampling Technique) so as to obtain k support vector machine classifiers for predicting the faulted hard disk. In the prediction stage, test sets can be clustered by using a DBSCAN (Density-based Spatial Clustering Of Applications With Noise), a sample in a clustered cluster is predicted as the normal hard disk sample, a noise sample is predicted by each classifier obtained by training, and further a final prediction result is obtained by voting. According to the method disclosed by the invention, hard disk fault prediction is carried out by using the SMART data of the hard disk, and relatively high fault recall ratio and overall performance can be obtained.
Owner:NANJING UNIV
Screening grouping method of echelon utilization type lithium batteries
ActiveCN103785629AImprove group consistencyGuaranteed Capacity UtilizationSortingPower batteryBattery degradation
The invention relates to a screening grouping method of echelon utilization type lithium batteries, and belongs to the technical field of determination of parameters of the lithium batteries. According to the technical scheme, the screening grouping method of the echelon utilization type lithium batteries comprises the following steps: testing and calculating so as to obtain a battery dQ / dV-V curve, analyzing ageing reasons of return power batteries by adopting an ICA (Incremental Capacity Analysis) method, and firstly rejecting the return power batteries, negative active materials of which are lost; testing to obtain the capacities, ohmic internal resistance, polarization internal resistancs and self-discharge values of the echelon utilization type lithium batteries, and screening the batteries according to indexes; and regrouping the screened batteries. The screening grouping method of the echelon utilization type lithium batteries has the beneficial effects that serious declining batteries are rejected by screening the echelon utilization type lithium batteries so as to ensure that the echelon utilization grouping property of the batteries is not affected by individual damaged battery; the batteries which are similar in terms of capacity, ohmic internal resistance and polarization internal resistance are clustered together by using a weighting k-means clustering method, and due to the setting of weights, the capacity utilization rate of a battery group is ensured; the forming consistency of the echelon utilization type lithium batteries can be improved, and the service life of the echelon utilization type lithium batteries is prolonged.
Owner:STATE GRID CORP OF CHINA +1
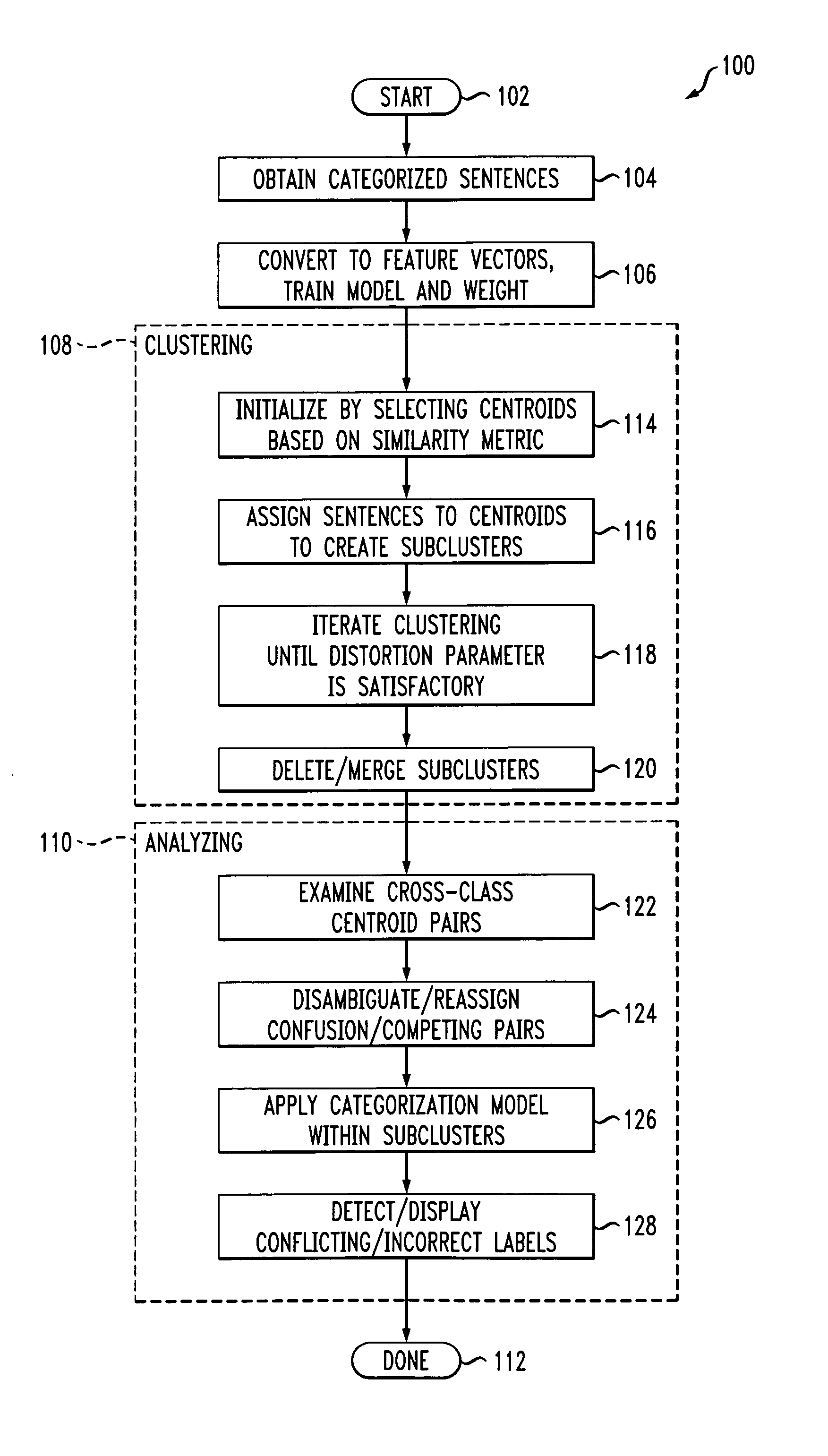
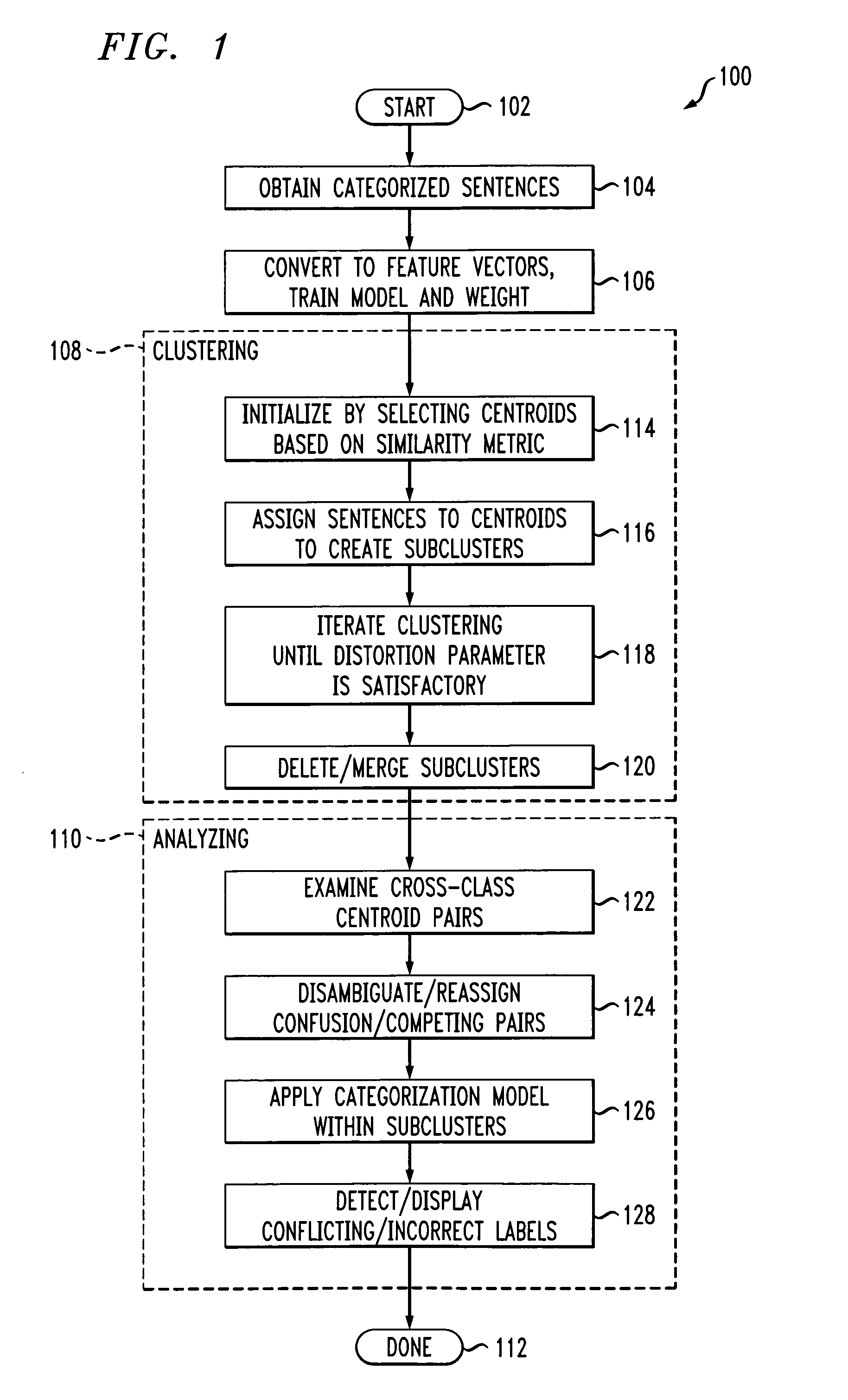
Method and apparatus for detecting data anomalies in statistical natural language applications
InactiveUS20070016399A1Natural language translationCharacter and pattern recognitionCluster algorithmLanguage understanding
Techniques for detecting data anomalies in a natural language understanding (NLU) system are provided. A number of categorized sentences, categorized into a number of categories, are obtained. Sentences within a given one of the categories are clustered into a number of sub clusters, and the sub clusters are analyzed to identify data anomalies. The clustering can be based on surface forms of the sentences. The anomalies can be, for example, ambiguities or inconsistencies. The clustering can be performed, for example, with a K-means clustering algorithm.
Owner:IBM CORP
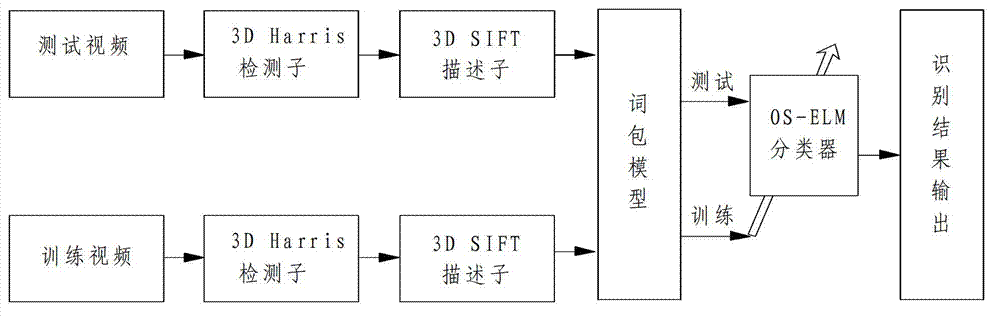
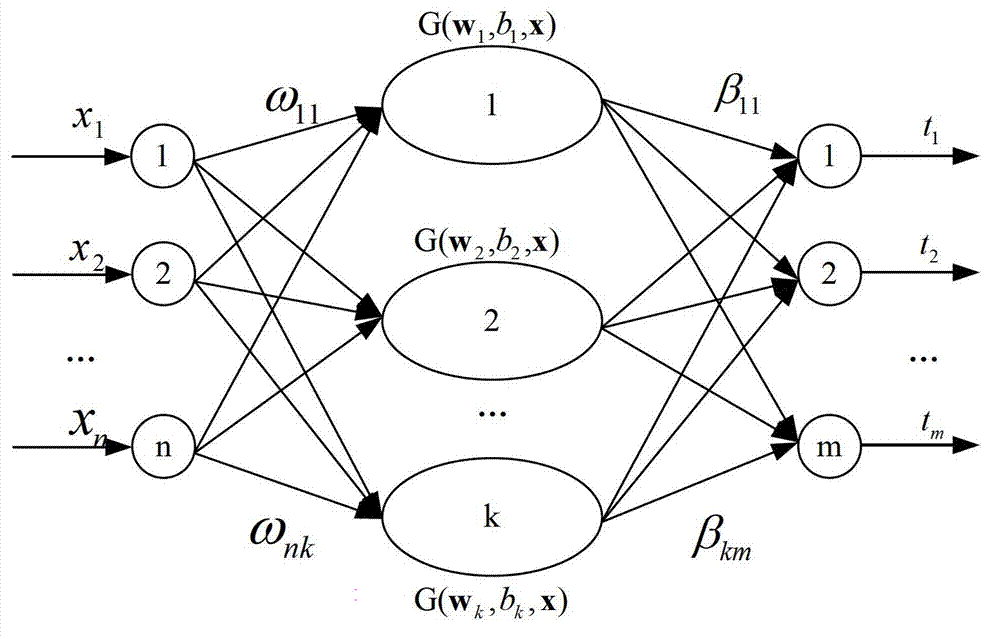
On-line sequential extreme learning machine-based incremental human behavior recognition method
InactiveCN102930302AImprove recognition accuracyAdaptableCharacter and pattern recognitionHuman bodyLearning machine
The invention discloses an on-line sequential extreme learning machine-based incremental human behavior recognition method. According to the method, a human body can be captured by a video camera on the basis of an activity range of everyone. The method comprises the following steps of: (1) extracting a spatio-temporal interest point in a video by adopting a third-dimensional (3D) Harris corner point detector; (2) calculating a descriptor of the detected spatio-temporal interest point by utilizing a 3D SIFT descriptor; (3) generating a video dictionary by adopting a K-means clustering algorithm, and establishing a bag-of-words model of a video image; (4) training an on-line sequential extreme learning machine classifier by using the obtained bag-of-words model of the video image; and (5) performing human behavior recognition by utilizing the on-line sequential extreme learning machine classifier, and performing on-line learning. According to the method, an accurate human behavior recognition result can be obtained within a short training time under the condition of a few training samples, and the method is insensitive to environmental scenario changes, environmental lighting changes, detection object changes and human form changes to a certain extent.
Owner:SHANDONG UNIV
Power equipment current-carrying fault trend prediction method based on least squares support vector machine
InactiveCN102663412AHigh precisionImprove reliabilityCharacter and pattern recognitionLeast squares support vector machinePower equipment
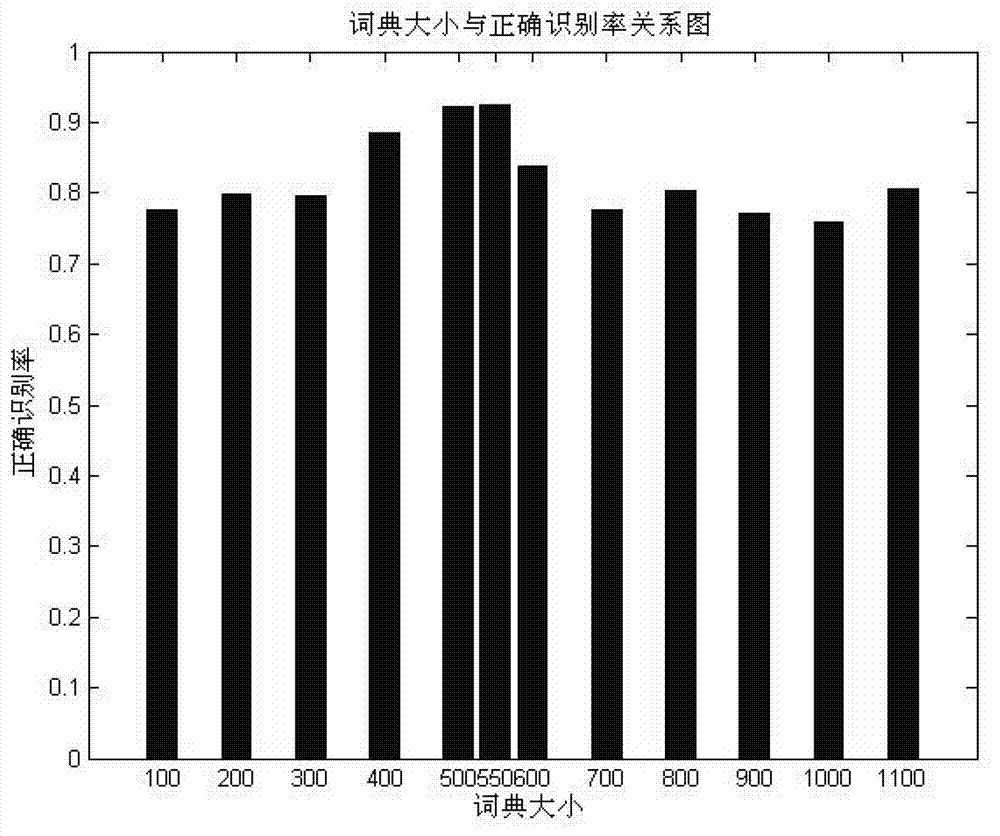
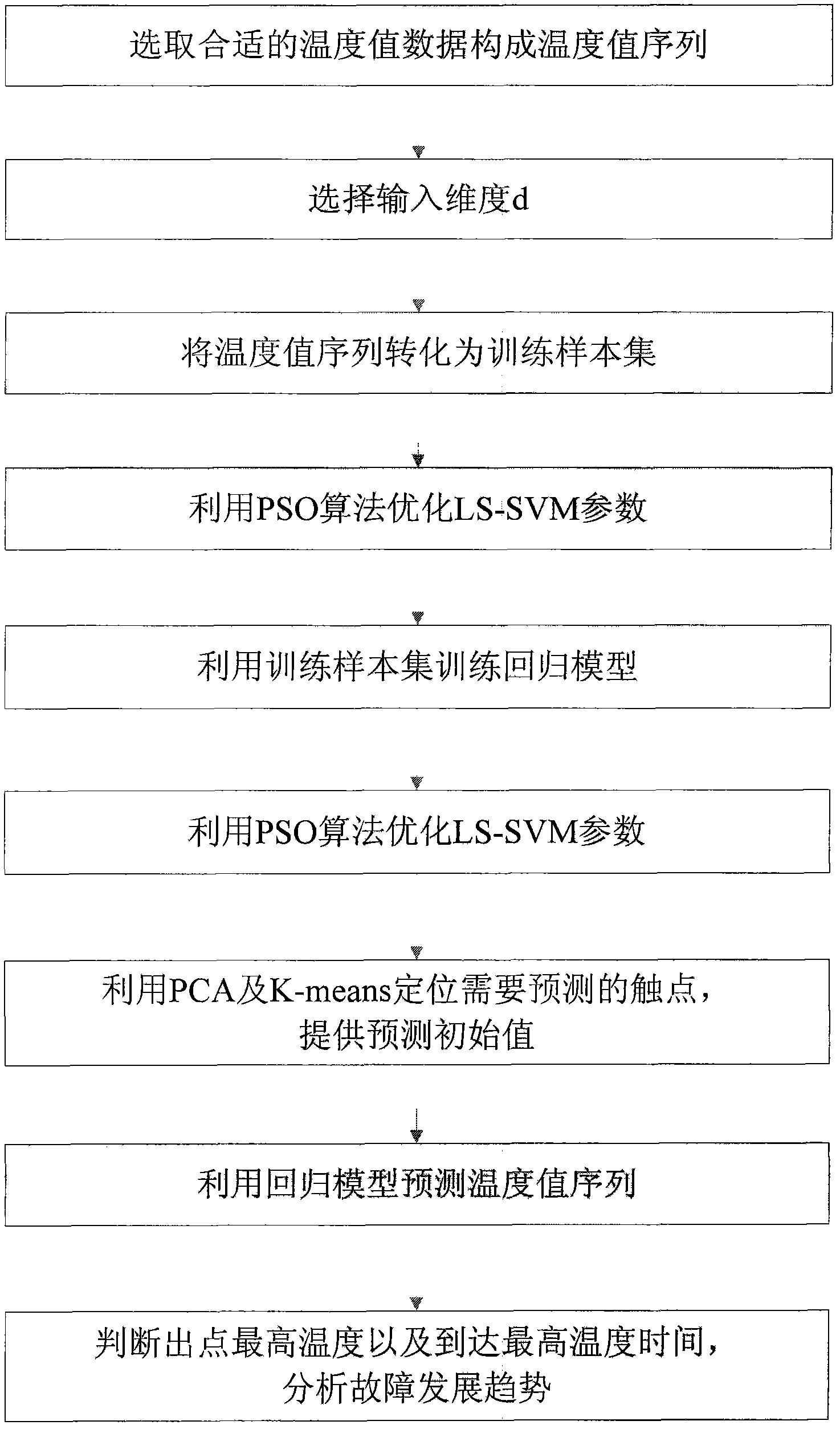
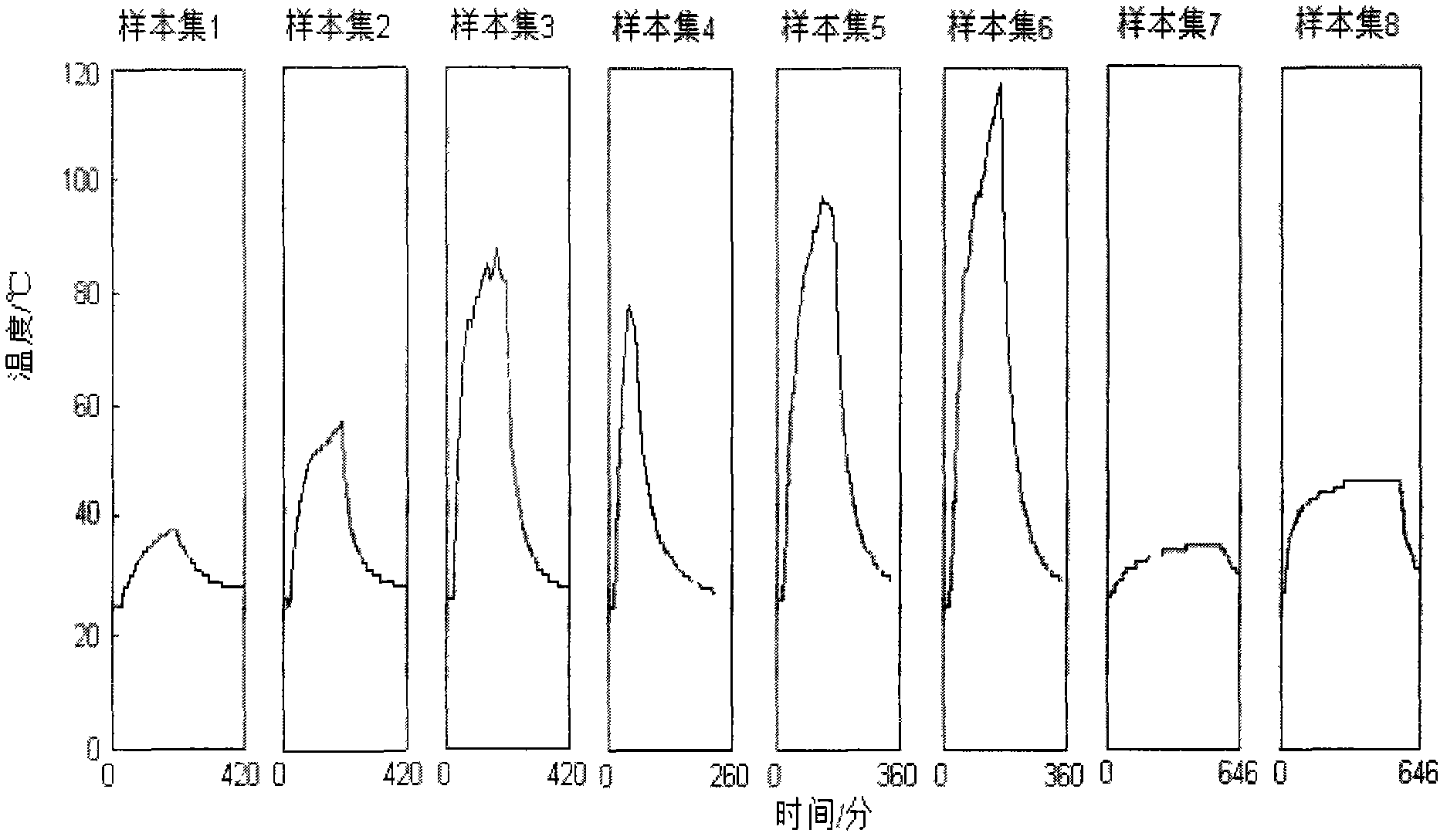
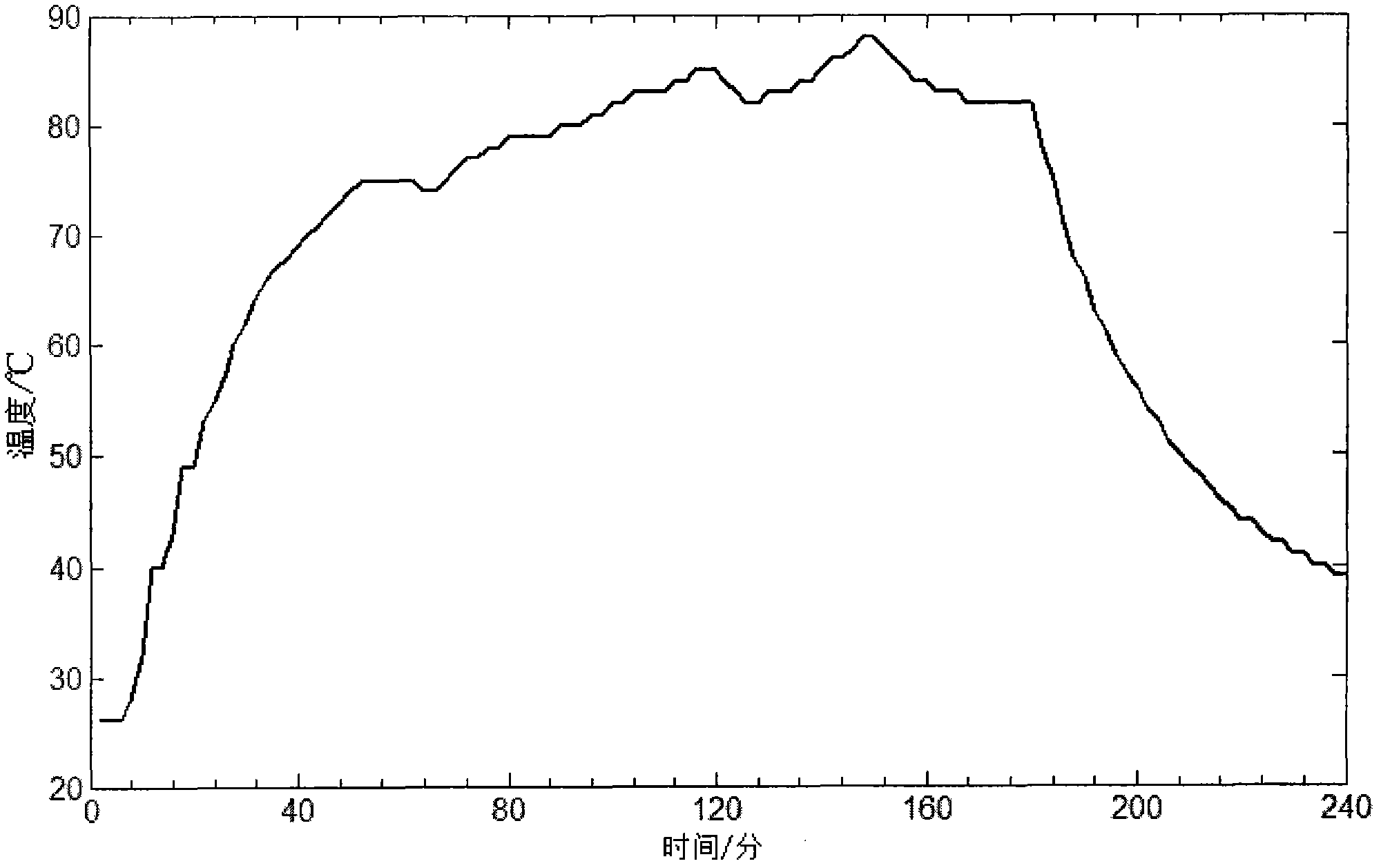
The invention discloses a power equipment current-carrying fault trend prediction method based ona least squares support vector machine. The method provided by the invention comprises the steps of employing historical temperature data to train an LS-SVM regression model, and employing a PSO optimization algorithm to adjust two parameters of the model, namely nucleus width sigma and punishment parameter gamma; employing a PCA algorithm and a K-means clustering algorithm to real-time analyze the temperature of equipment contacts to find contacts with abnormal temperature rising, and using the temperature value asan initial value sequence of prediction;and finally employing the regression model obtained by training to predict the temperature value of the initial value for a long term and for a short term, and analyzing the highest point the contact temperature may reach and the time when the contact temperature reaches the highest point. Through predictive analysis based on PSO-LSSVM, fault development trend of equipment contacts is actively controlled, so the time for timely measures and ensuring the safe operation of power grid is bought. The method provided by the invention can be widely used in the field of power equipment forecast alarm protection.
Owner:ZHEJIANG UNIV +1
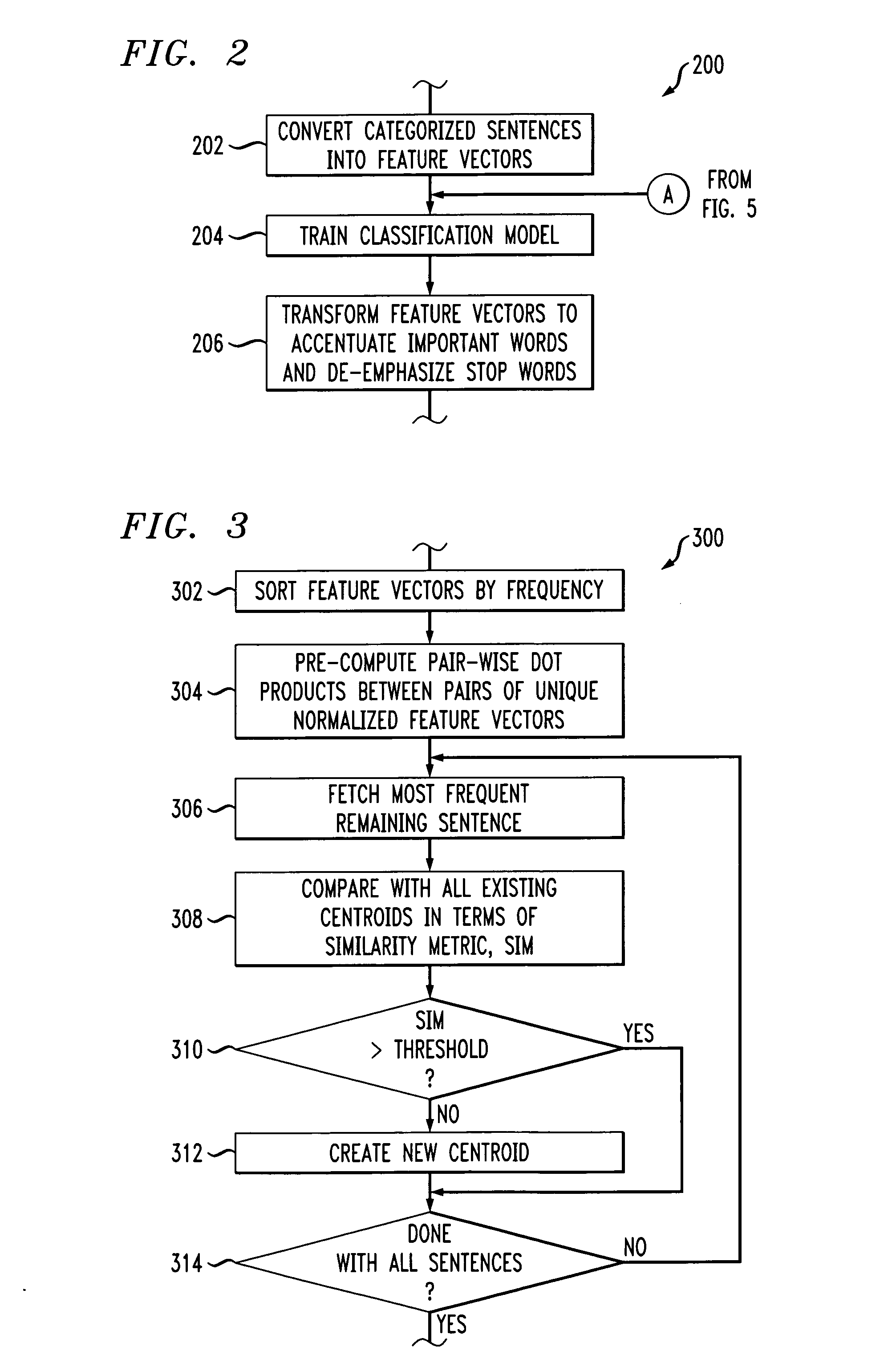
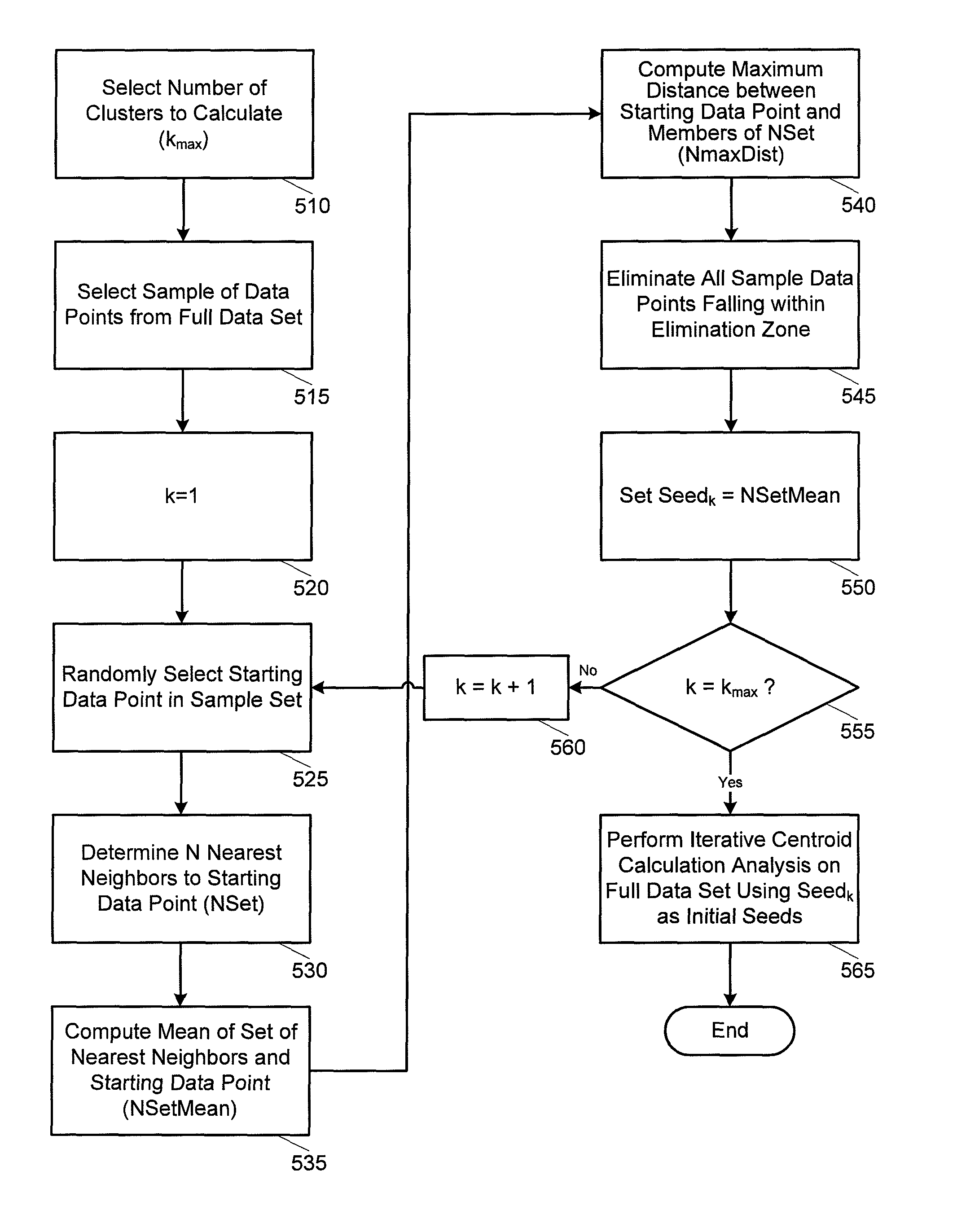
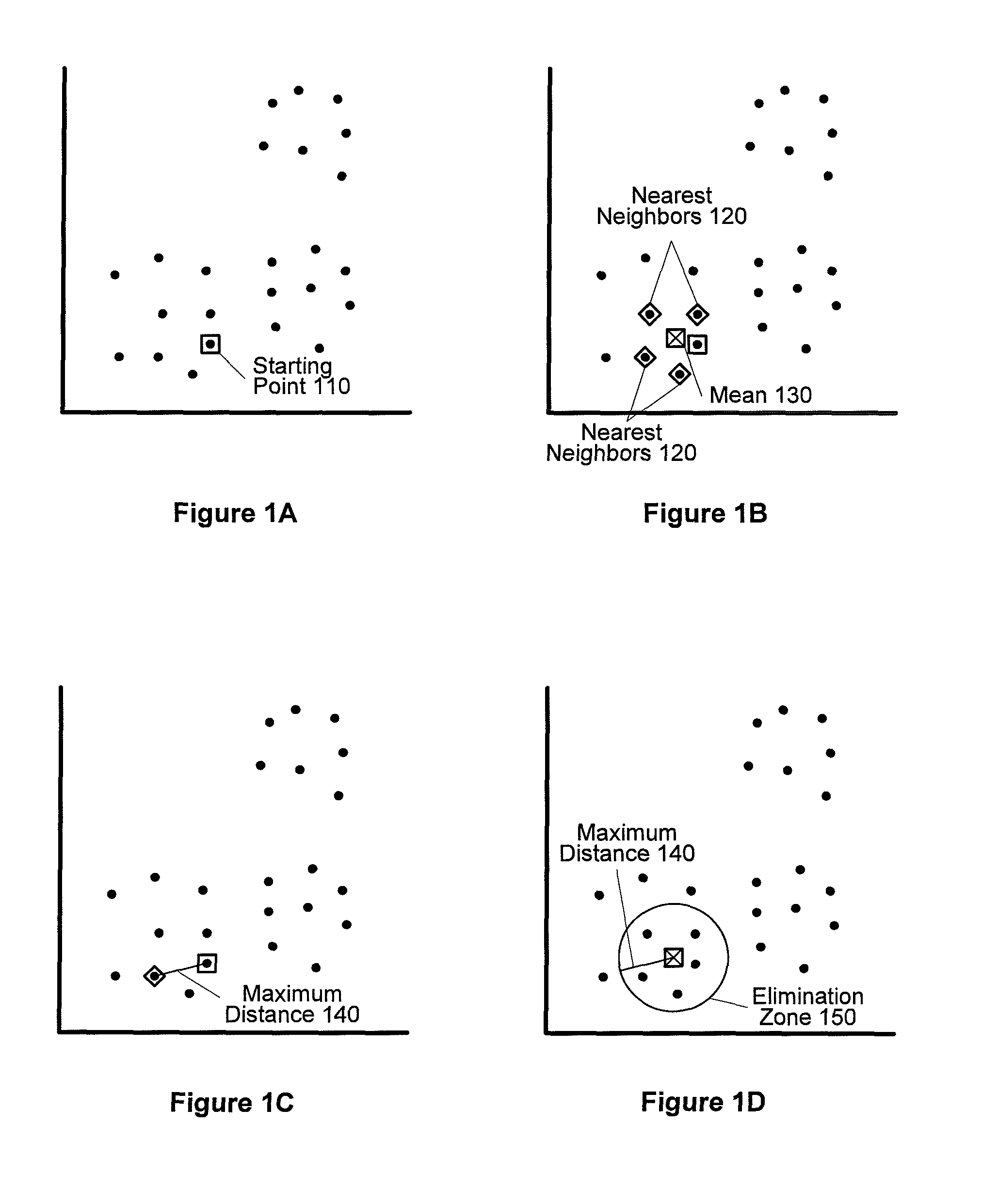
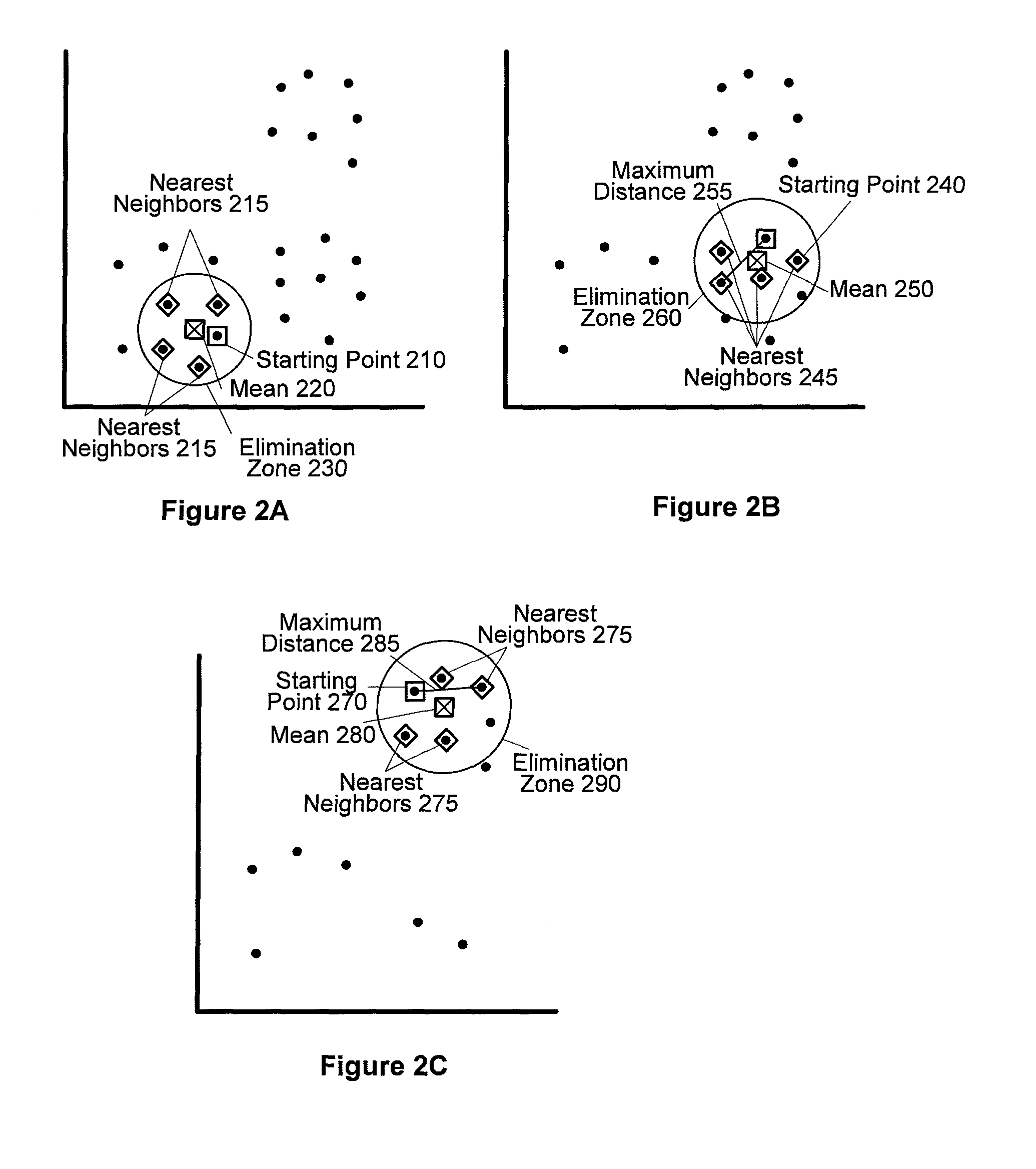
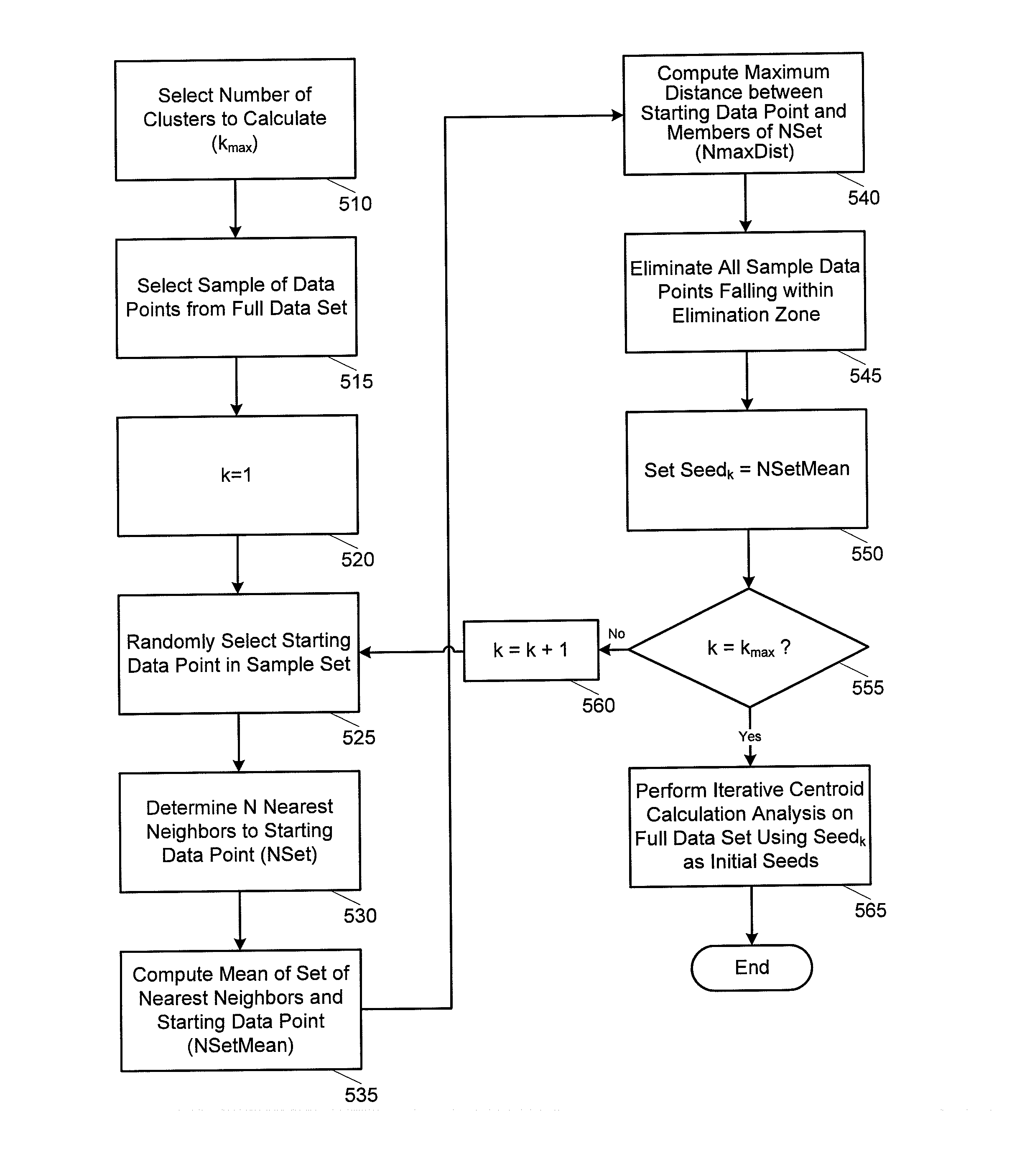
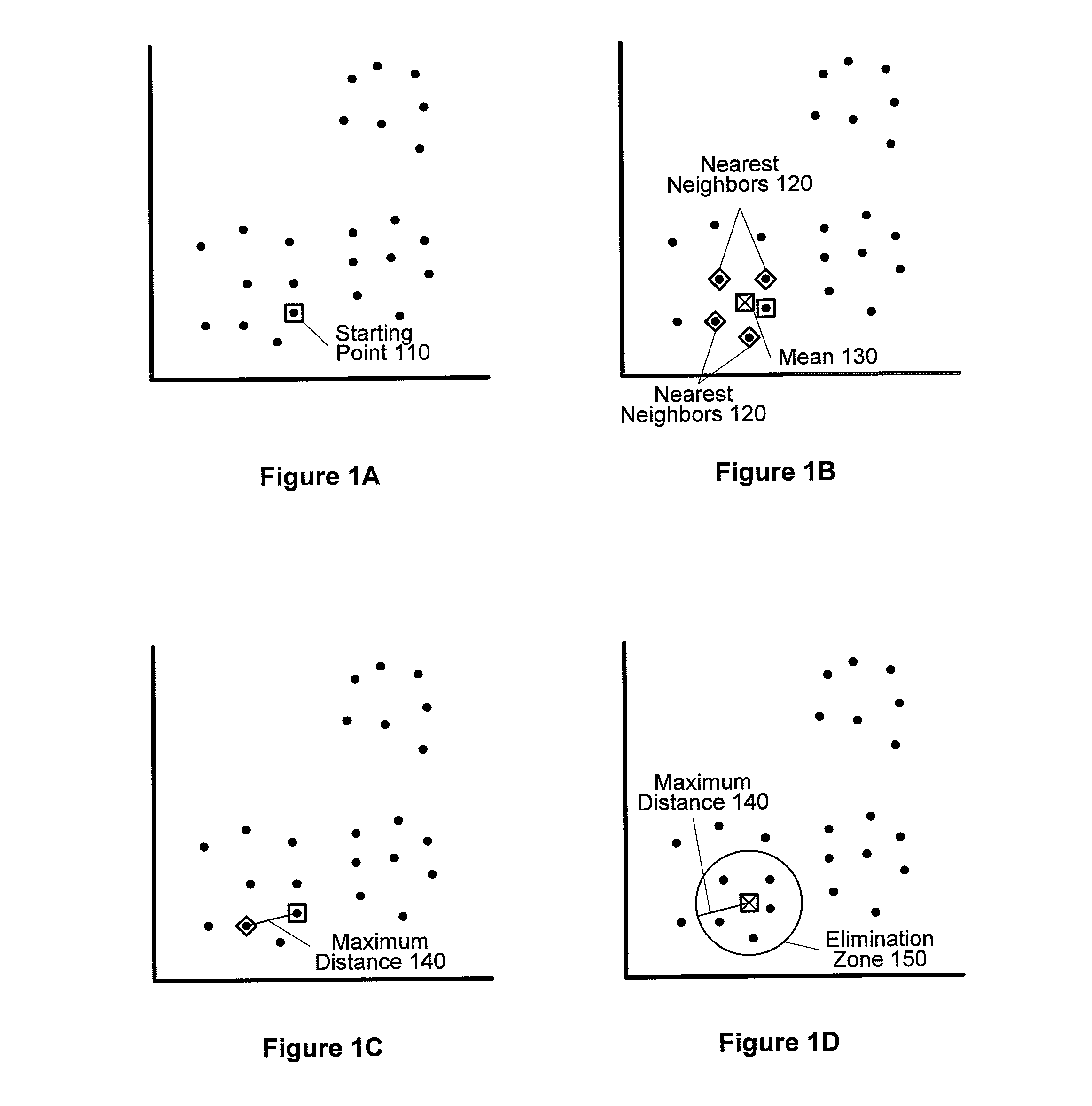
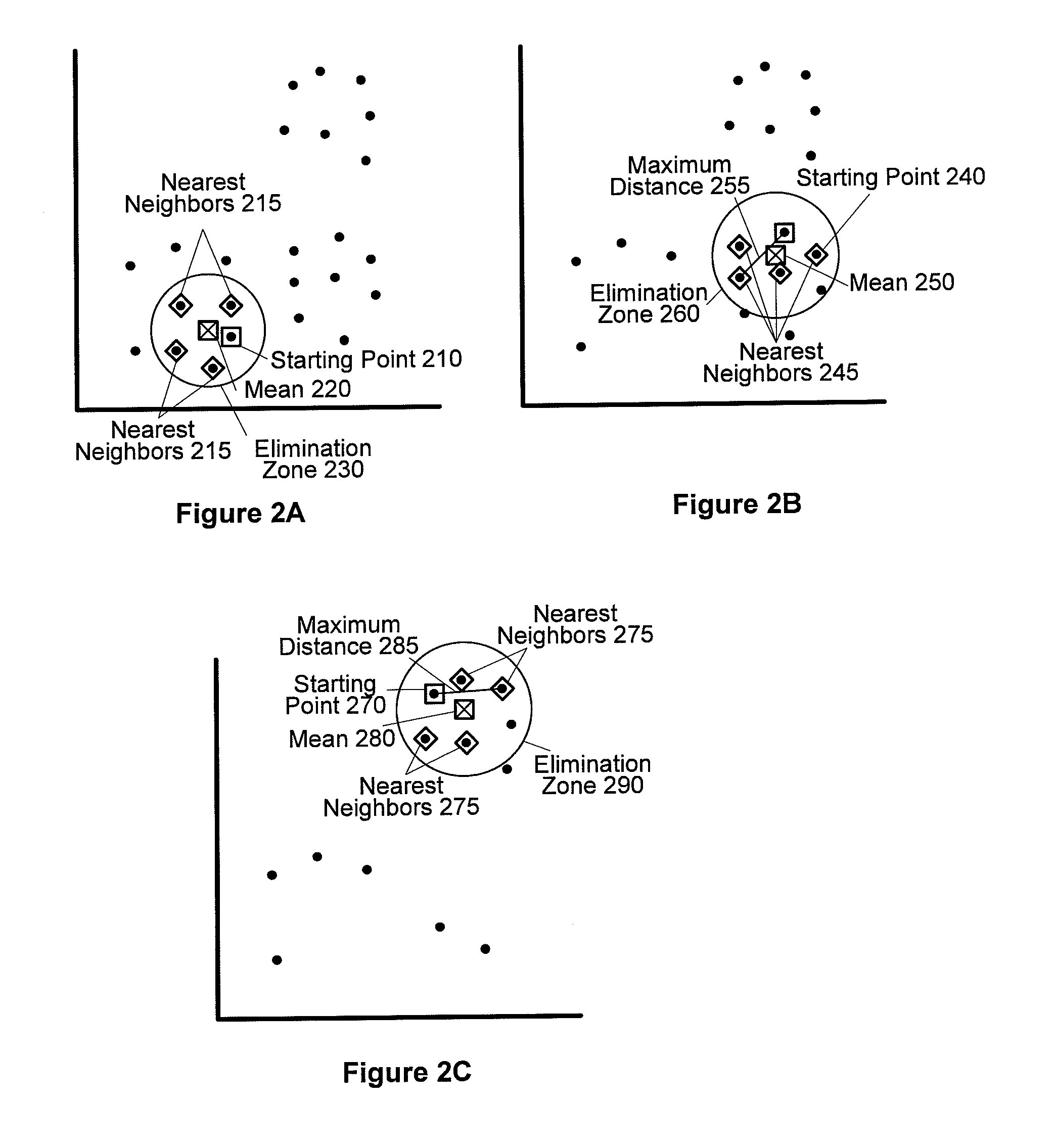
Expediting K-means cluster analysis data mining using subsample elimination preprocessing
Improved efficiencies of data mining clustering techniques are provided by preprocessing a sample set of data points taken from a complete data set to provide seeds for centroid calculations of the complete data set. Such seeds are generated by selecting a uniform sample set of data points from a set of multi-dimensional data and then seed values for the cluster determination calculation are determined using a centroid analysis on the sample set of data points. The number of seeds calculated corresponds to a number of data clusters expected in the set of multi-dimensional data points. Seed values are determined using subsample elimination techniques.
Owner:ORACLE INT CORP
Expediting k-means cluster analysis data mining using subsample elimination preprocessing
ActiveUS20110055140A1Character and pattern recognitionFuzzy logic based systemsComplete dataData set
Improved efficiencies of data mining clustering techniques are provided by preprocessing a sample set of data points taken from a complete data set to provide seeds for centroid calculations of the complete data set. Such seeds are generated by selecting a uniform sample set of data points from a set of multi-dimensional data and then seed values for the cluster determination calculation are determined using a centroid analysis on the sample set of data points. The number of seeds calculated corresponds to a number of data clusters expected in the set of multi-dimensional data points. Seed values are determined using subsample elimination techniques.
Owner:ORACLE INT CORP
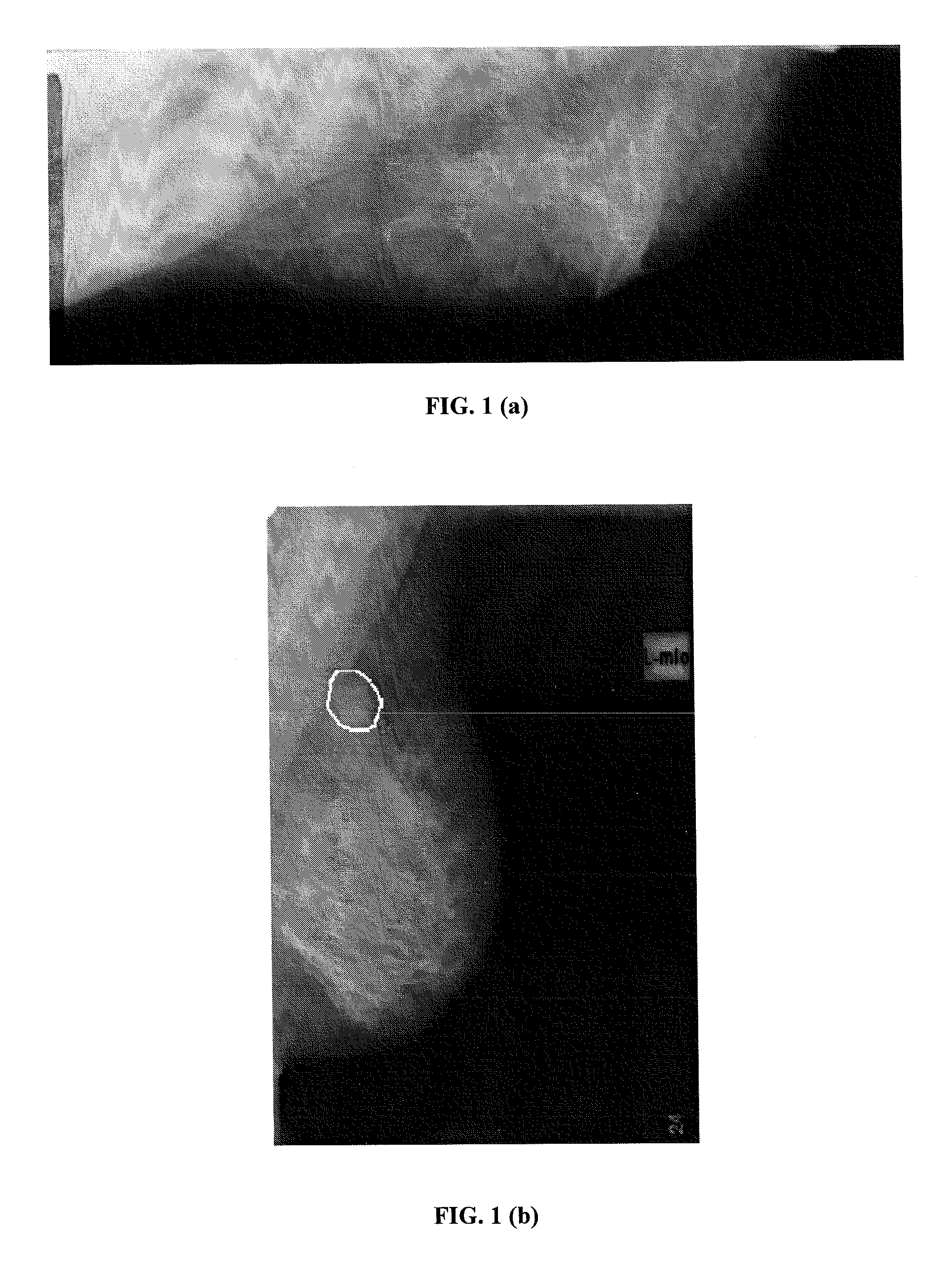
Method for Segmenting Digital Medical Image
ActiveUS20080101678A1Promote resultsImage enhancementImage analysisStatistical classificationCategorical models
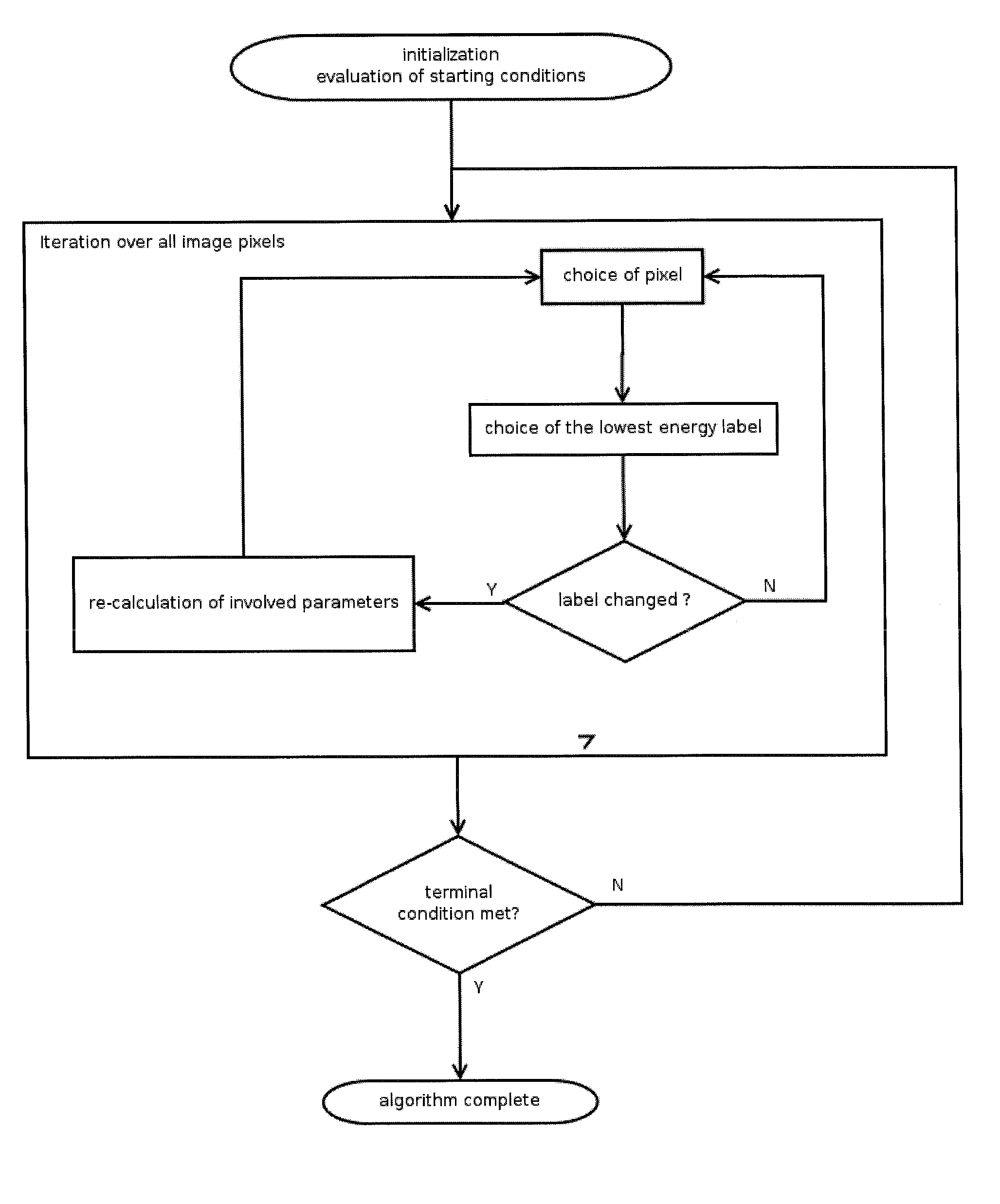
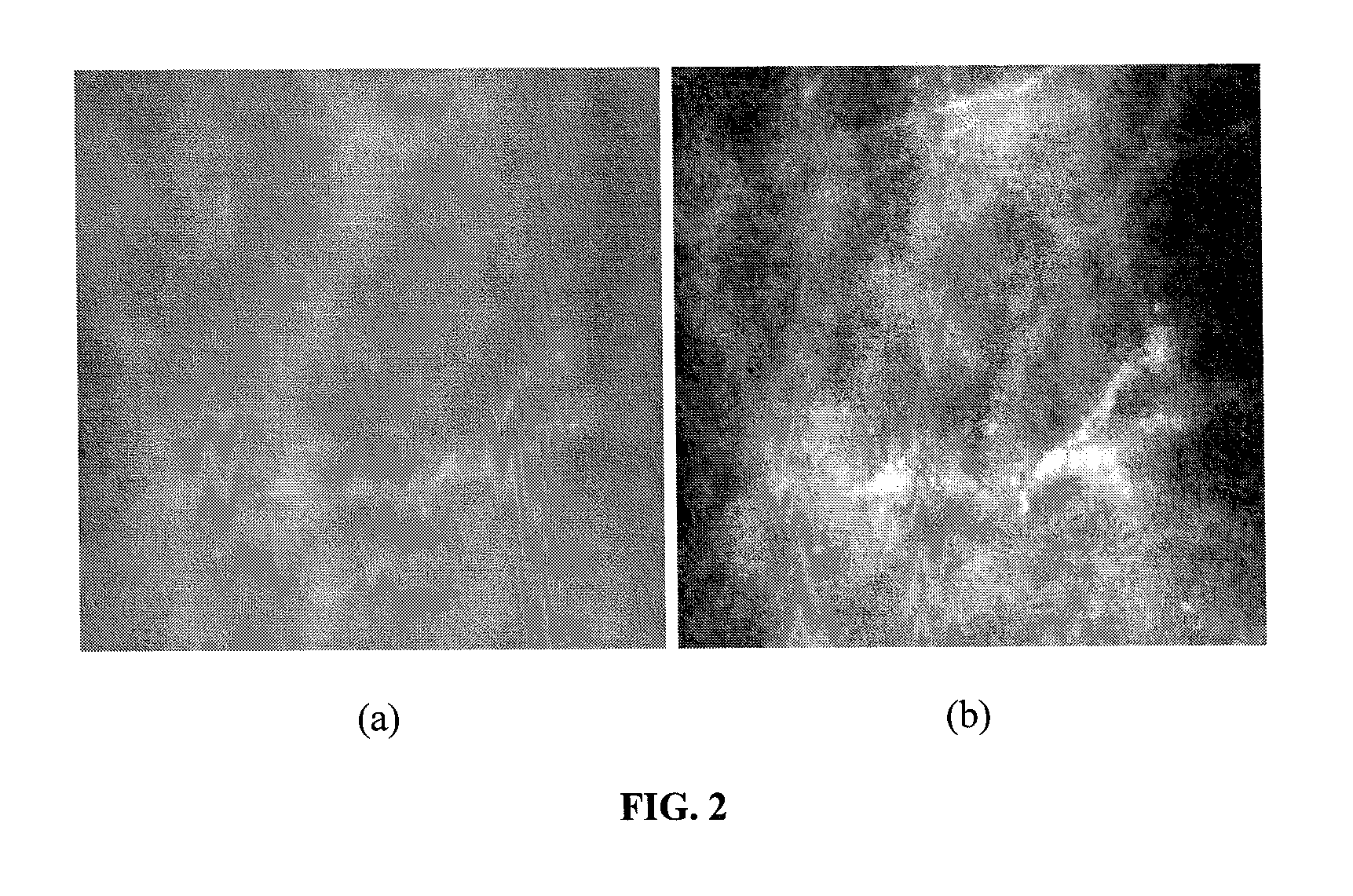
A Markov Random Field (MRF)-based technique is described for performing clustering of images characterized by poor or limited data. The proposed method is a statistical classification model that labels the image pixels based on the description of their statistical and contextual information. Apart from evaluating the pixel statistics that originate from the definition of the K-means clustering scheme, the model expands the analysis by the description of the spatial dependence between pixels and their labels (context), hence leading to the reduction of the inhomogeneity of the segmentation output with respect to the result of pure K-means clustering.
Owner:AGFA NV
Anomaly detection with k-means clustering and artificial outlier injection
ActiveUS20170124478A1Reduce in quantityRelational databasesMachine learningData setAnomaly detection
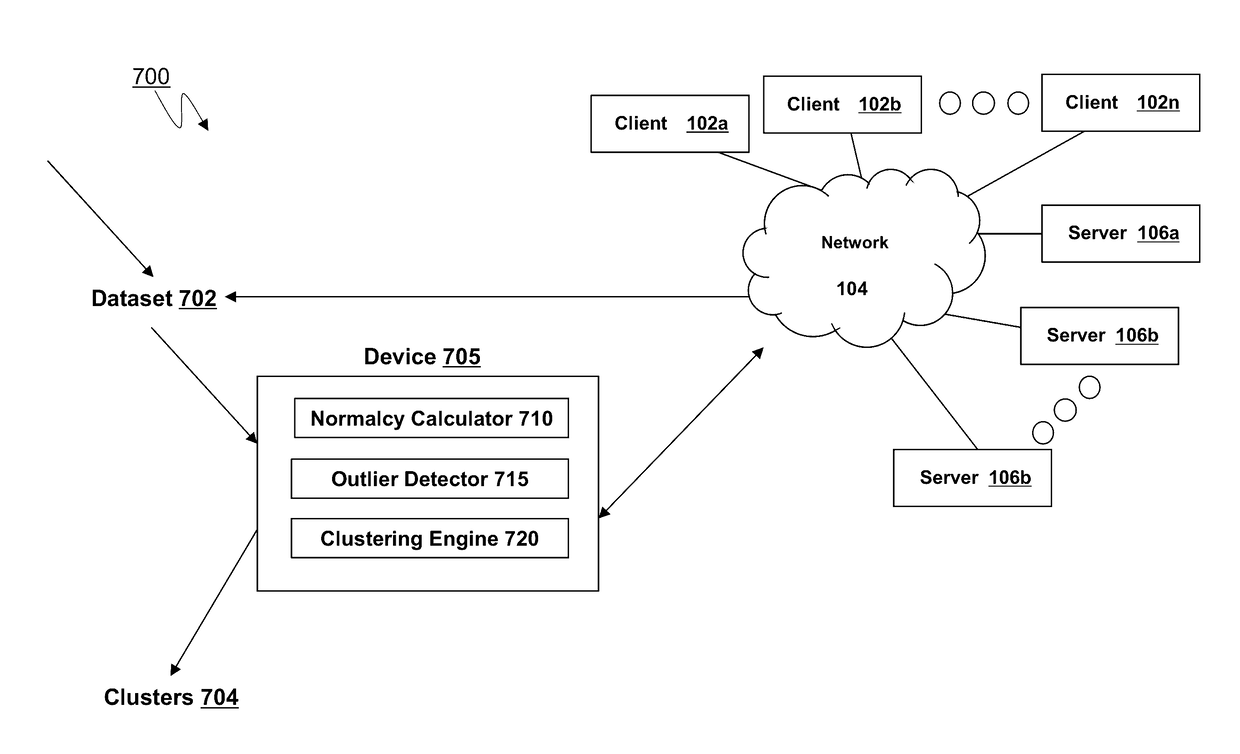
The present disclosure is directed towards systems and methods for improving anomaly detection using injected outliers. A normalcy calculator of a device may include a set of outliers into a training dataset of data points. The normalcy calculator, using a K-means clustering algorithm applied on the training dataset, identify at least a first cluster of data points. The normalcy calculator of the device may determine a region with a center and an outer radius that covers at least a spatial extent of the first cluster of data points. The normalcy calculator may determine a first normalcy radius for the first cluster by reducing the region around the center until a point at which all artificial outliers are excluded from a region defined by the first normalcy radius. An outlier detector of the device may use the region defined by the first normalcy radius to determine whether a new data point is normal or abnormal.
Owner:CITRIX SYST INC
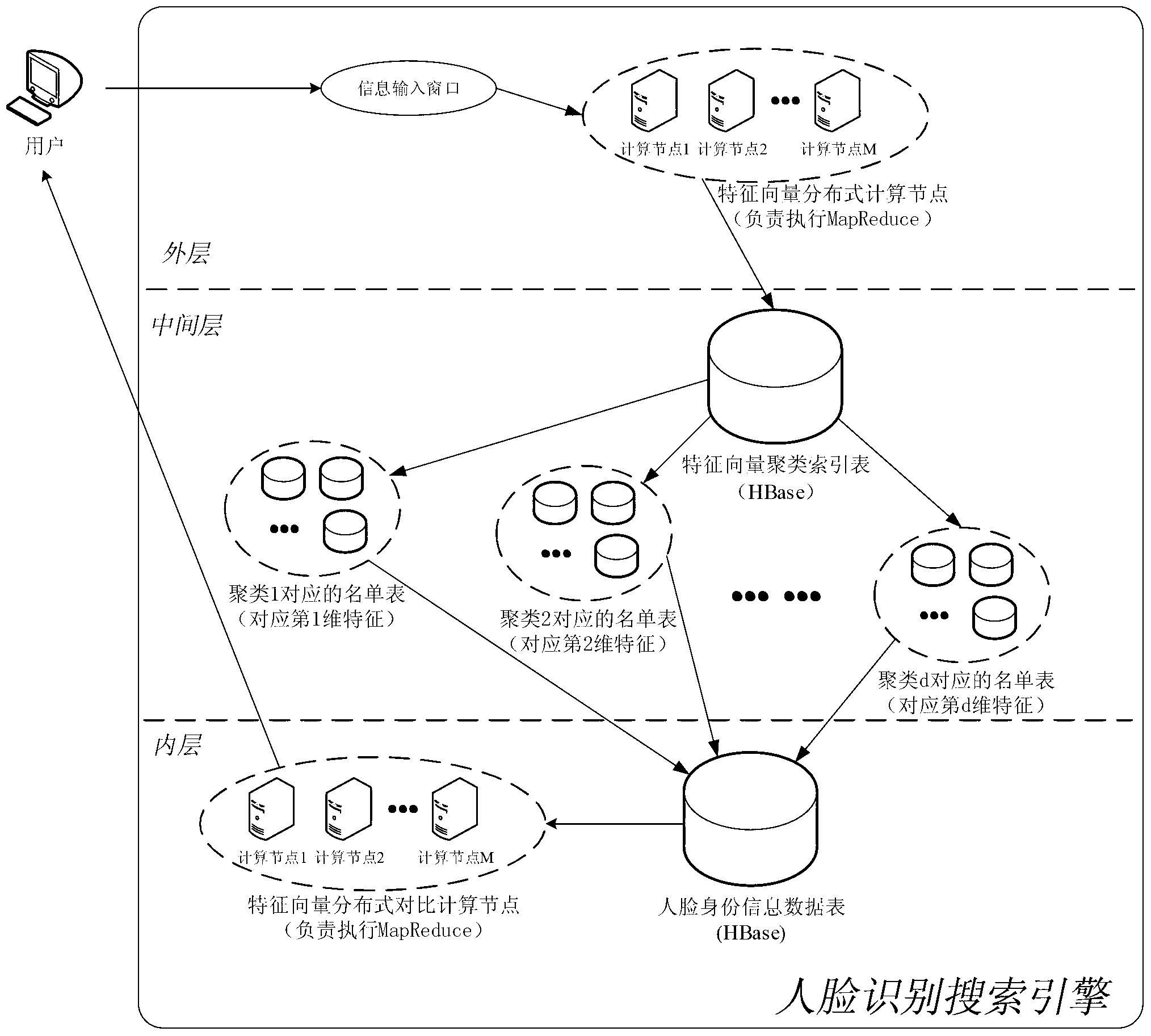
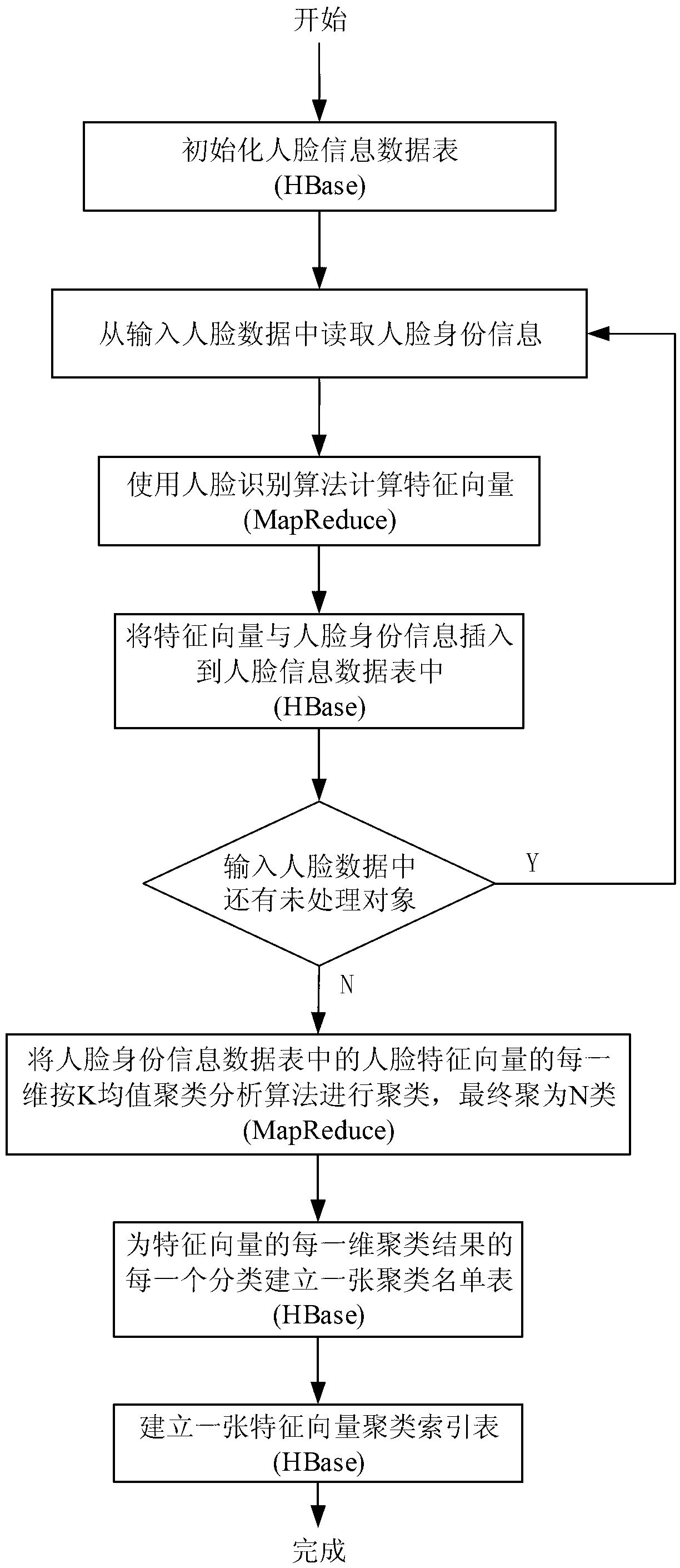
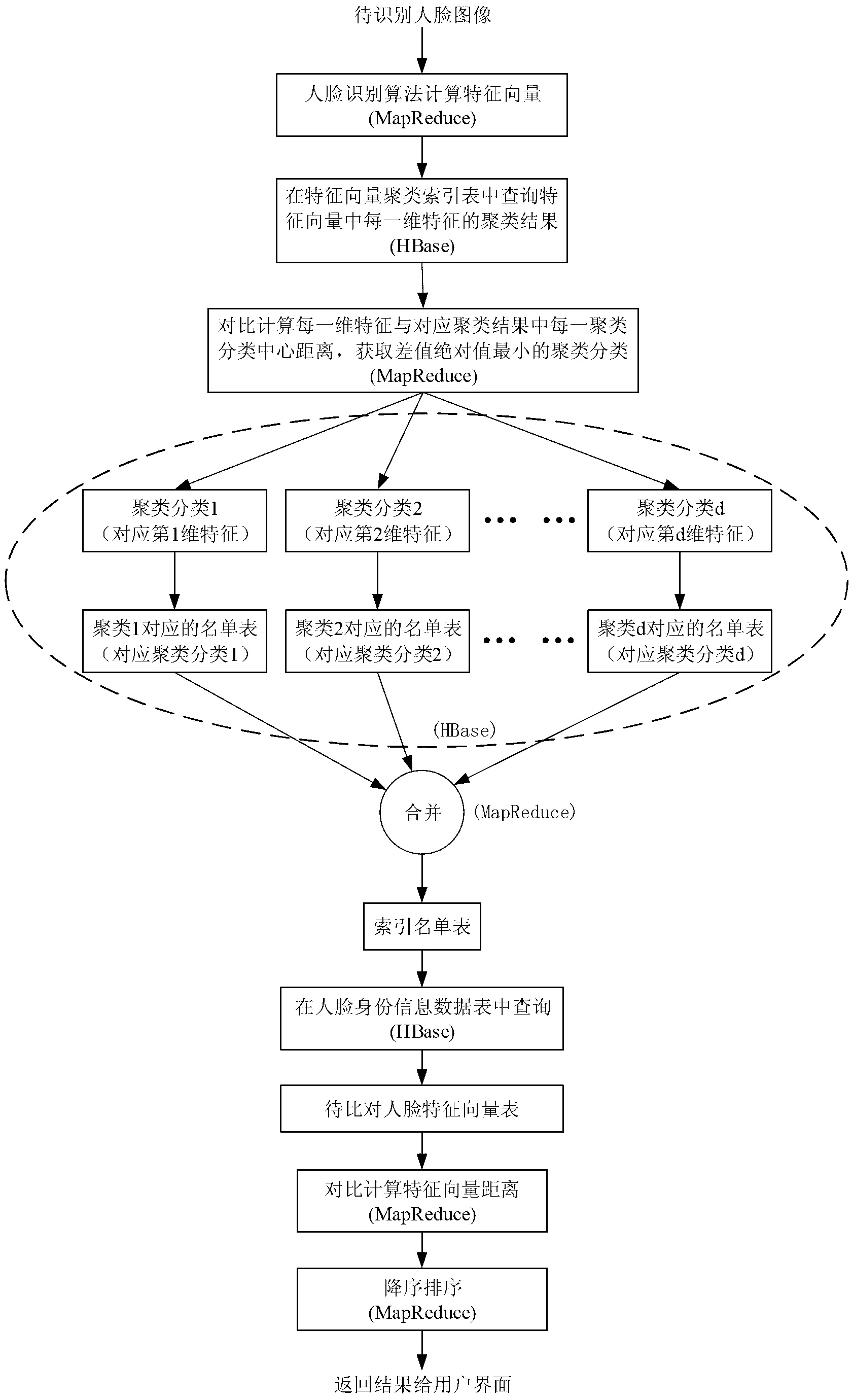
Method used for designing large-quantity face recognition search engine and based on Hadoop cloud computing frame
ActiveCN103235825AGuaranteed real-timeGuaranteed reliabilityCharacter and pattern recognitionSpecial data processing applicationsFeature vectorMachine learning
A method used for designing a large-quantity face recognition search engine and based on a Hadoop cloud computing frame belongs to the field of cloud computing and mode recognition. Based on the Hadoop cloud computing frame, the search engineis formed by an inner layer, a middle layer and an outer layer. The inner layer is used for storing a large quantity of face images and identity information and providing distributed computing resources. The middle layer is used for building and maintaining an index table of the search engine, and the outer layer is used for receiving tasks and distributing tasks. In order to increase searching speed of the face images in a data base while the precision is guaranteed, a K-means clustering algorithm is used in the middle layer to build a face feature vector cluster index table to be combined with a clustering list table. By means of the method, cheap common server groups can be used for building the large-quantity face recognition search engine, and the method is achieved based on the Hadoop cloud computing frame proved by a large amount of practice, has good stability and is simple and easy to implement.
Owner:CHONGQING UNIV
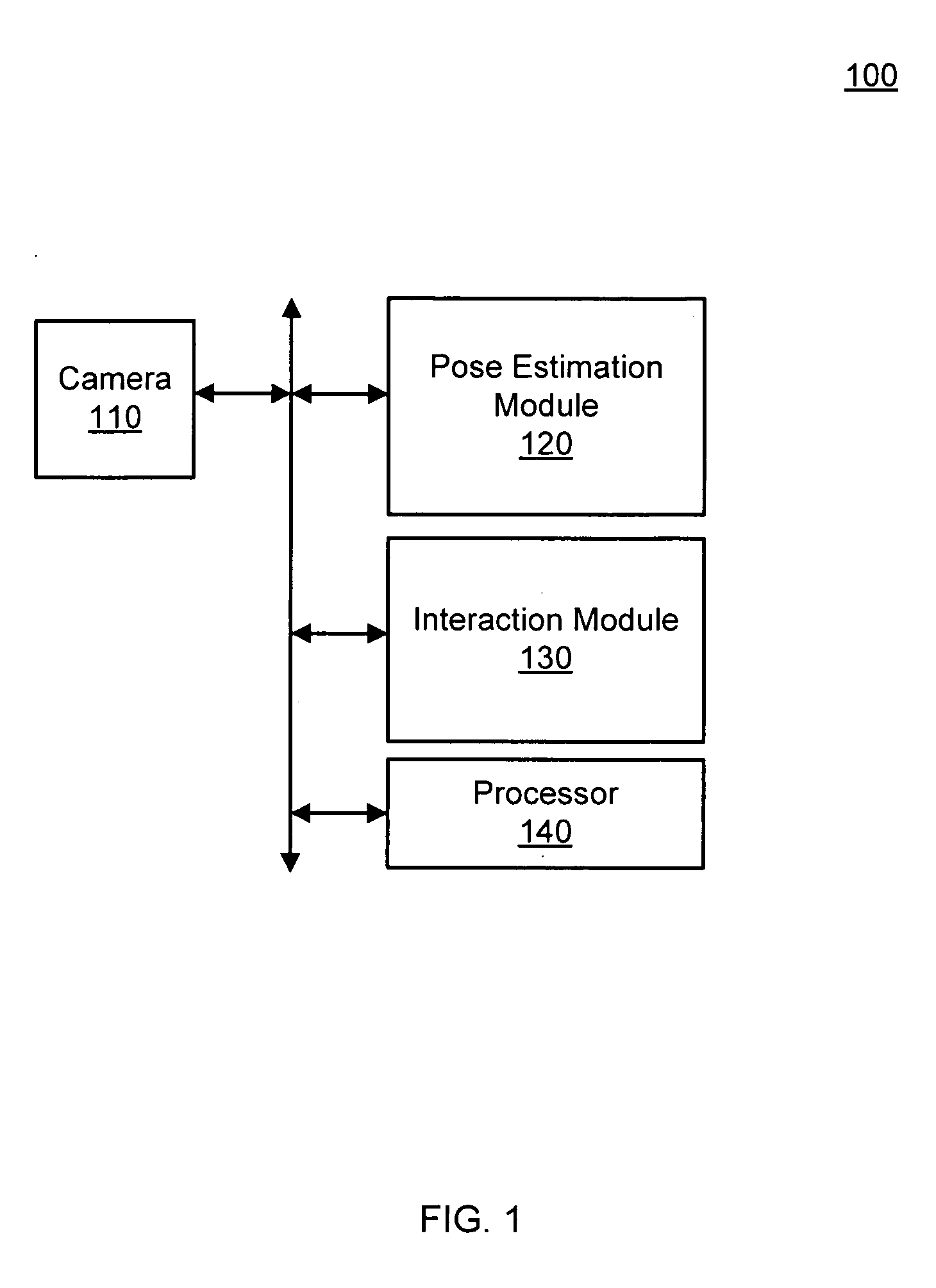
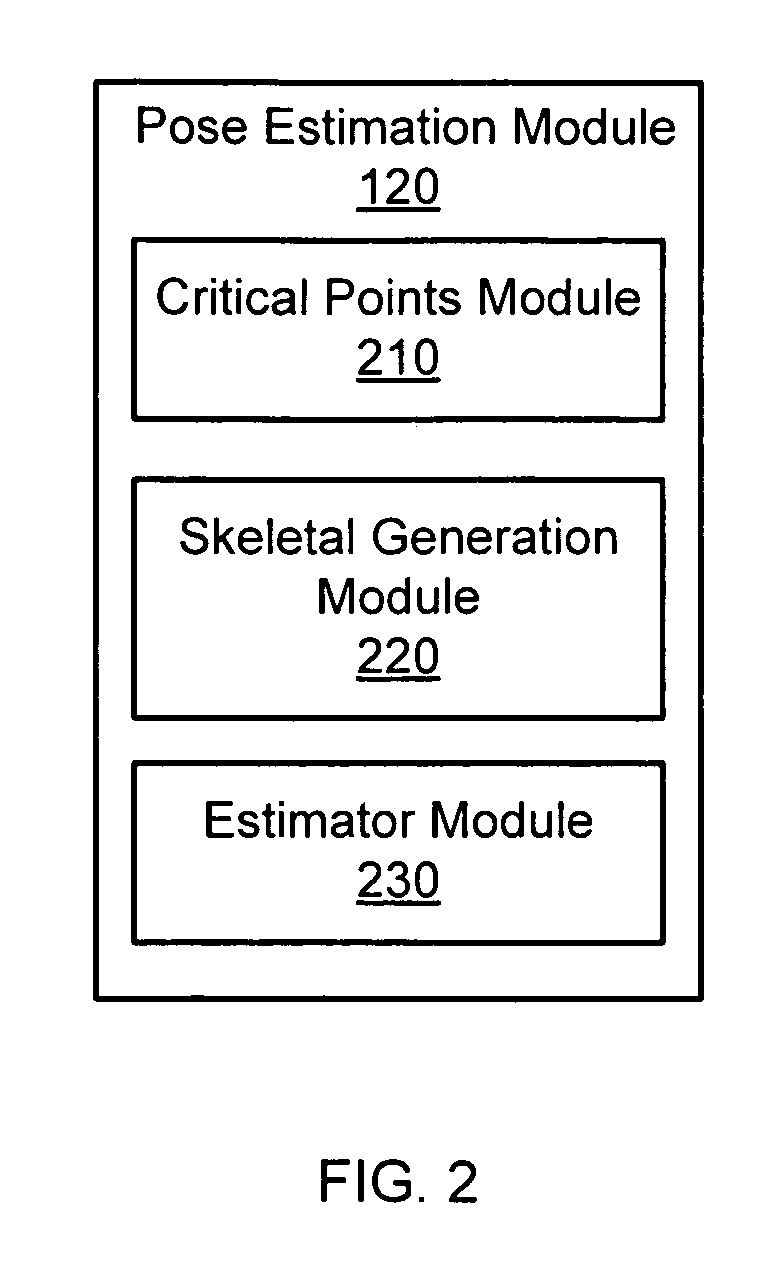
Pose estimation based on critical point analysis
Methods and systems for estimating a pose of a subject. The subject can be a human, an animal, a robot, or the like. A camera receives depth information associated with a subject, a pose estimation module to determine a pose or action of the subject from images, and an interaction module to output a response to the perceived pose or action. The pose estimation module separates portions of the image containing the subject into classified and unclassified portions. The portions can be segmented using k-means clustering. The classified portions can be known objects, such as a head and a torso, that are tracked across the images. The unclassified portions are swept across an x and y axis to identify local minimums and local maximums. The critical points are derived from the local minimums and local maximums. Potential joint sections are identified by connecting various critical points, and the joint sections having sufficient probability of corresponding to an object on the subject are selected.
Owner:THE OHIO STATE UNIV RES FOUND +1
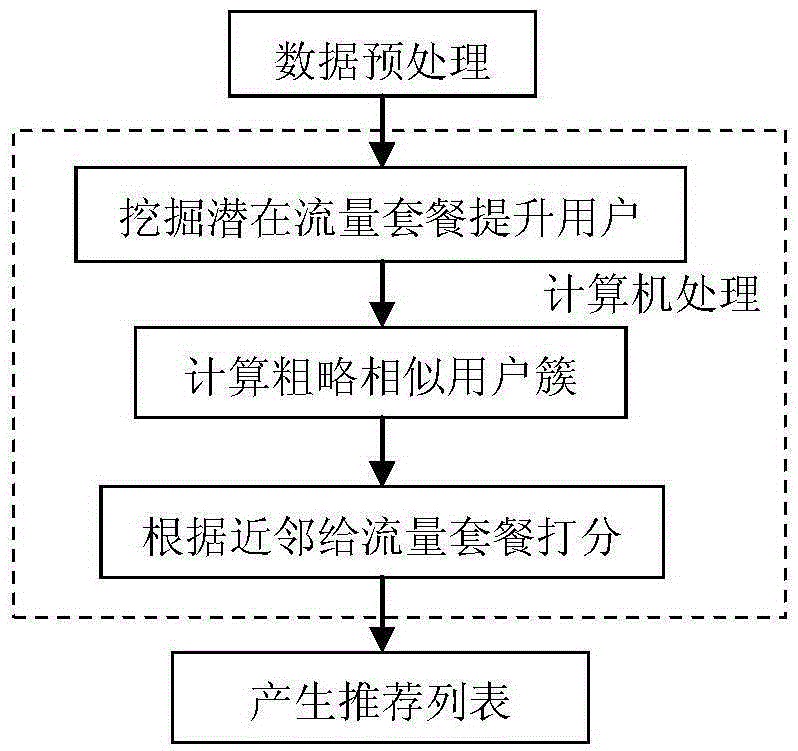
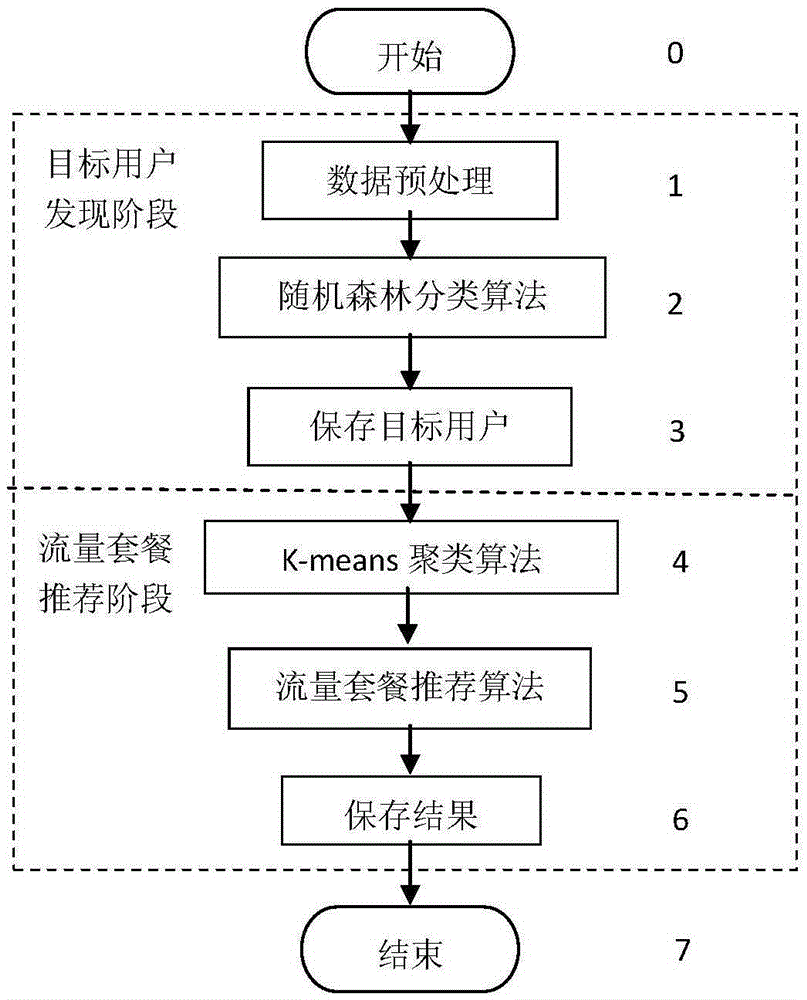
Mobile data traffic package recommendation algorithm based on user historical data
InactiveCN105389713AAccurate discoveryReduce computational complexityCharacter and pattern recognitionMarketingData dredgingData set
The invention provides a mobile data traffic package recommendation algorithm based on user historical data according to data mining analysis technology. The mobile data traffic package recommendation algorithm comprises the following steps of: 1) a target user finding period comprising the processes of a, acquiring a processed generated data set which comprises a training set and a prediction set, b, executing a random forest classification algorithm for finding a latent data traffic package improving user as a target user, and c, ending; 2), a data traffic package recommendation period comprising the process of a, acquiring a processed generated prediction set, b, executing a K-means clustering algorithm for obtaining a slightly similar user cluster, c, obtaining the target user obtained in the process 1)-b, d, executing a TopN recommendation algorithm on the target user in a same cluster according to a similarity function of the user, and e, ending. The mobile data traffic package recommendation algorithm is used for finding the latent user with a latent data traffic improvement requirement according to data mining technology and executing a recommended plan on the user. Compared with a traditional method, the mobile data traffic package recommendation algorithm has advantages of higher accuracy, higher efficiency, simple realization, low cost, etc.
Owner:NANJING UNIV
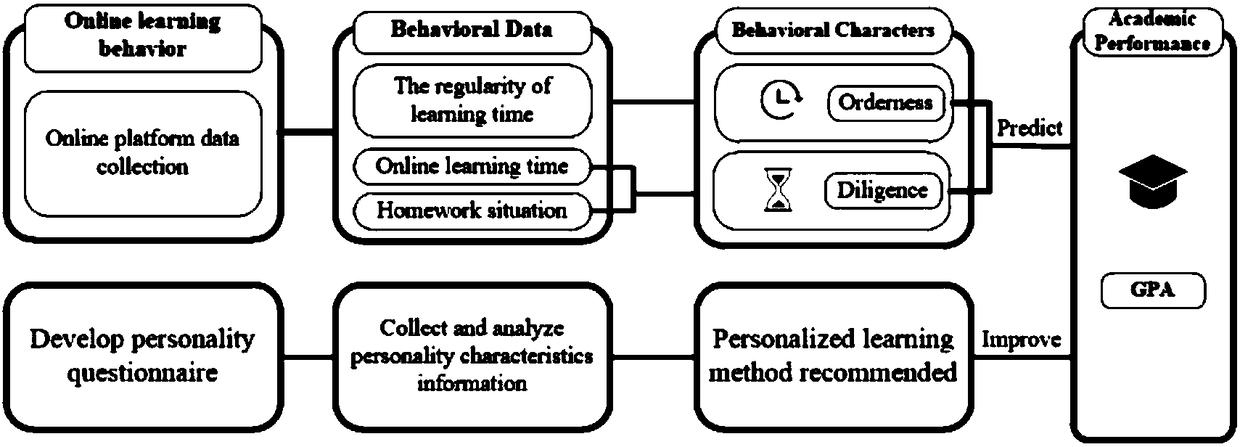
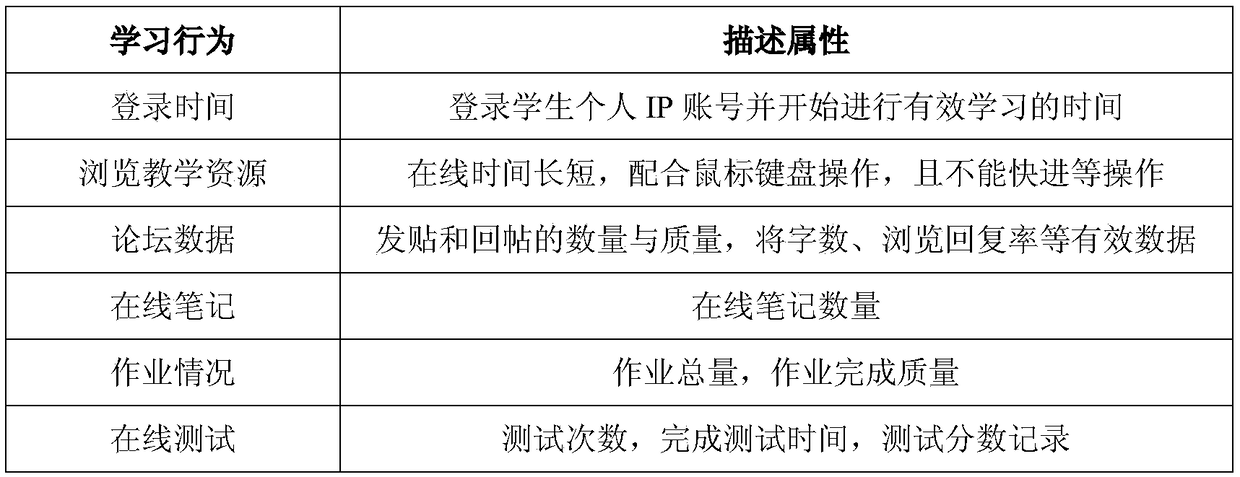
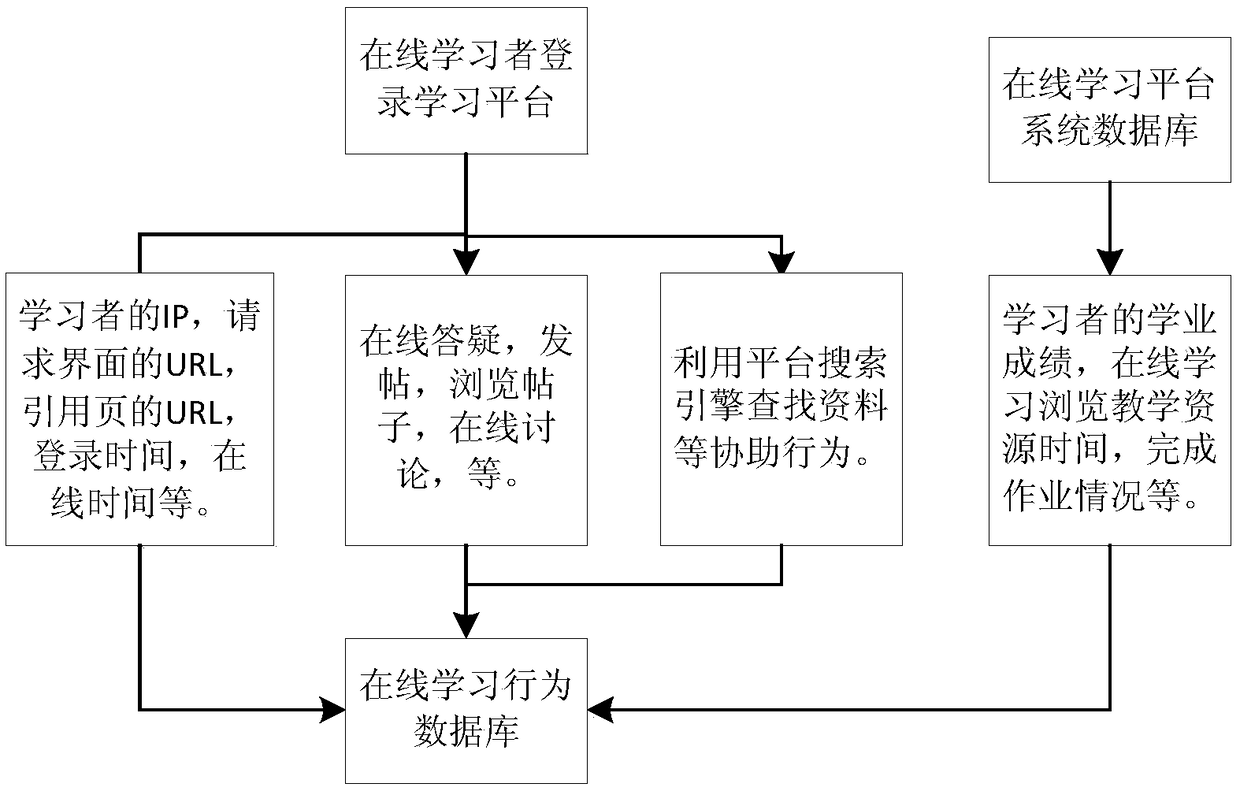
Online learning behavior analysis-based individualized learning recommending method
ActiveCN108182489AImprove forecast accuracyEasy to understandForecastingResourcesPersonalizationData set
An online learning behavior analysis-based individualized learning recommending method comprises the following steps of 1 collecting the data, and obtaining the learner log data, the student score data and the student character data of an online learning platform; 2 extracting and mining the features; 3 preparing a dataset to train a BP neural network and testing the accuracy of a model; 4 utilizing the trained model to predict the scores of the new learners; 5 issuing the questionnaires to the learners, and collecting the questionnaire data; 6 carrying out the k-means clustering analysis on the questionnaire data; 7 combining the character features of the different learners to recommend the individualized learning methods. The present invention provides a BP neural network prediction method that is higher in prediction precision and can analyze the online learning time regularity of the learners more comprehensively. According to the present invention, the characters of the learners can be analyzed, and the individualized learning methods can be recommended to the learners.
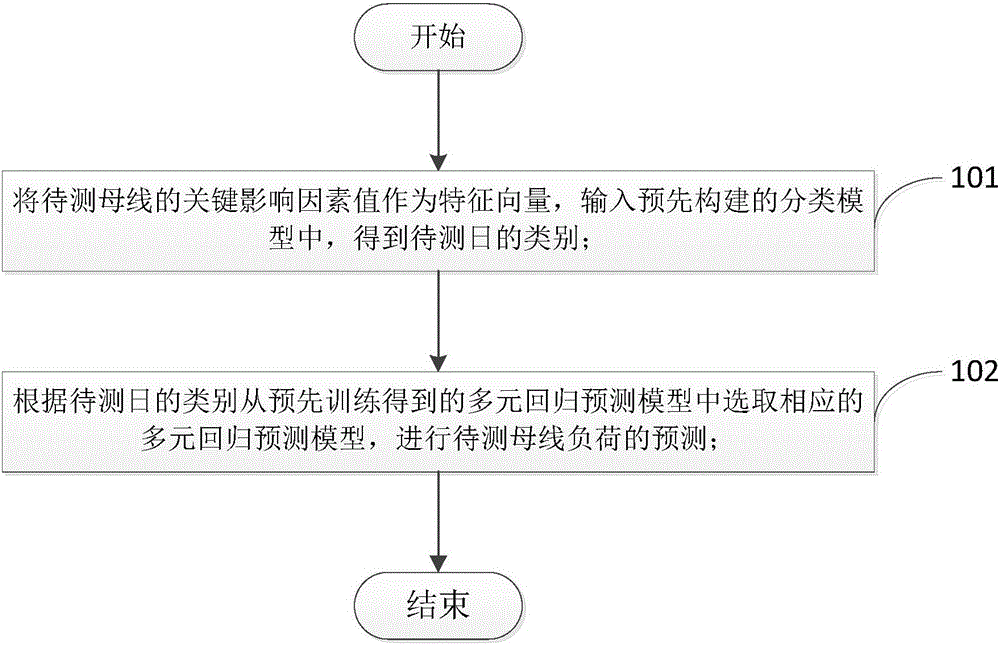
Owner:深圳市优课再学教育科技有限公司
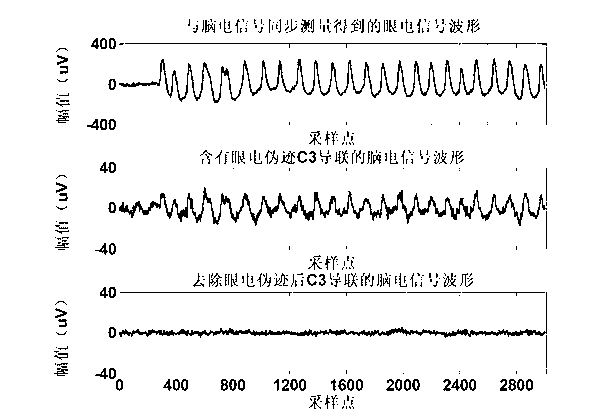
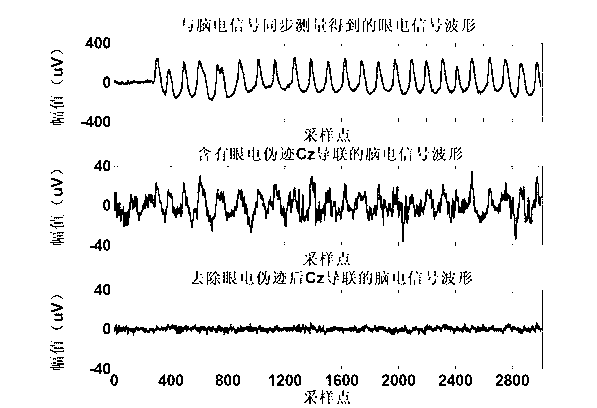
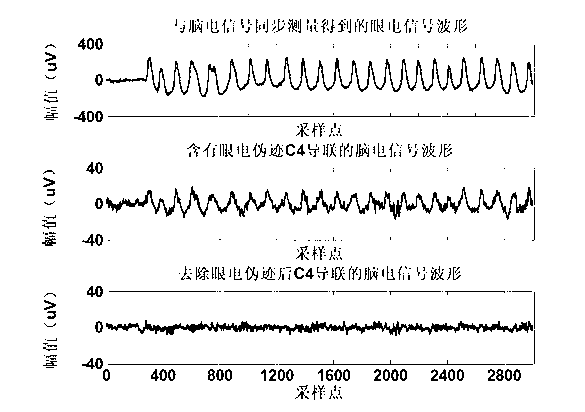
Method of automatically removing ocular artifacts from electroencephalogram signal without setting threshold value
The invention provides a method of automatically removing ocular artifacts from an electroencephalogram signal without setting a threshold value, belongs to the field of biological information technology, and is mainly applied to the preprocessing process of the electroencephalogram signal. The method particularly comprises the following steps: performing an independent component decomposition to a captured electroencephalogram signal containing the ocular artifacts; gaining the kurtosis, the sequence renyi entropy and the sample entropy of each independent component as feature vectors, so as to automatically recognize an independent component containing the ocular artifacts by k-means cluster analysis, and setting the independent component to be zero and other components to be constant, reconstructing the signal, and obtaining a pure electroencephalogram signal. The method provided by the invention solves the problems that the artifacts are identified by means of manual work during the traditional process for removing the ocular artifacts, so that time and labors are wasted and the workload is heavy. In addition, the method provided by the invention can realize the purposes of automatically identifying and removing the ocular artifacts without setting the threshold value by manual work, so that the shortcoming in the existing method that a researcher is required to have definite future knowledges and strong subjectivity during the setting of the the threshold value is overcame.
Owner:BEIJING UNIV OF TECH
Method for recognizing diseases of crop leaves
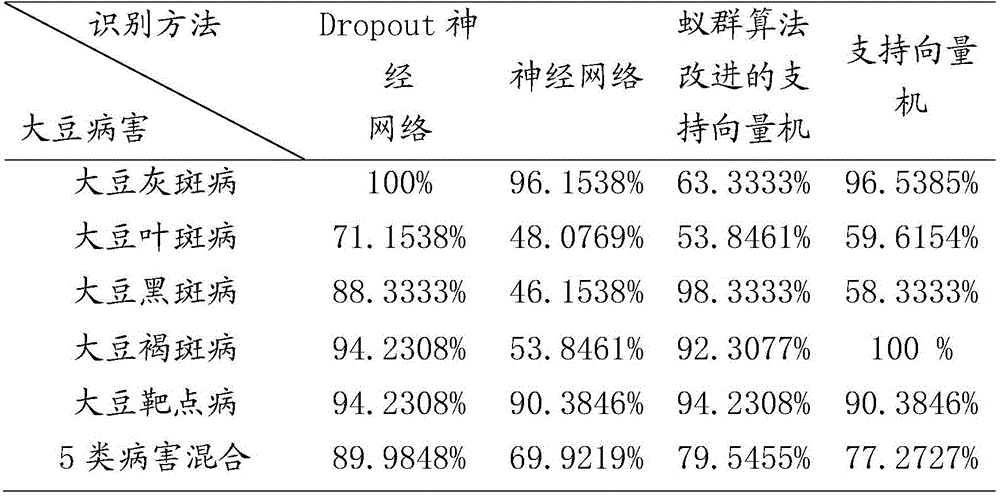
InactiveCN104598908AGuaranteed accuracyEasy and Accurate AcquisitionCharacter and pattern recognitionNeural learning methodsPattern recognitionDisease
The invention discloses a method for recognizing diseases of crop leaves. The method comprises the steps of converting acquired images into CIELab colored space images; calculating the saliency of each pixel point according to a multi-scale neighborhood to obtain a final salient image; cutting the final salient image into K areas by the K means clustering method; extracting the area of which the average value of the saliency of the pixel points is more than a set threshold as a salient area; adjusting the extracted salient area to obtain a scab image; extracting the color and local texture feature parameters of the scab image; inputting the obtained color and local texture feature parameters into the neural network for recognizing and classifying the diseases. With the adoption of the method, the extracted scab image is free of color distortion, and the diseases recognition accuracy is high.
Owner:ZHEJIANG SCI-TECH UNIV
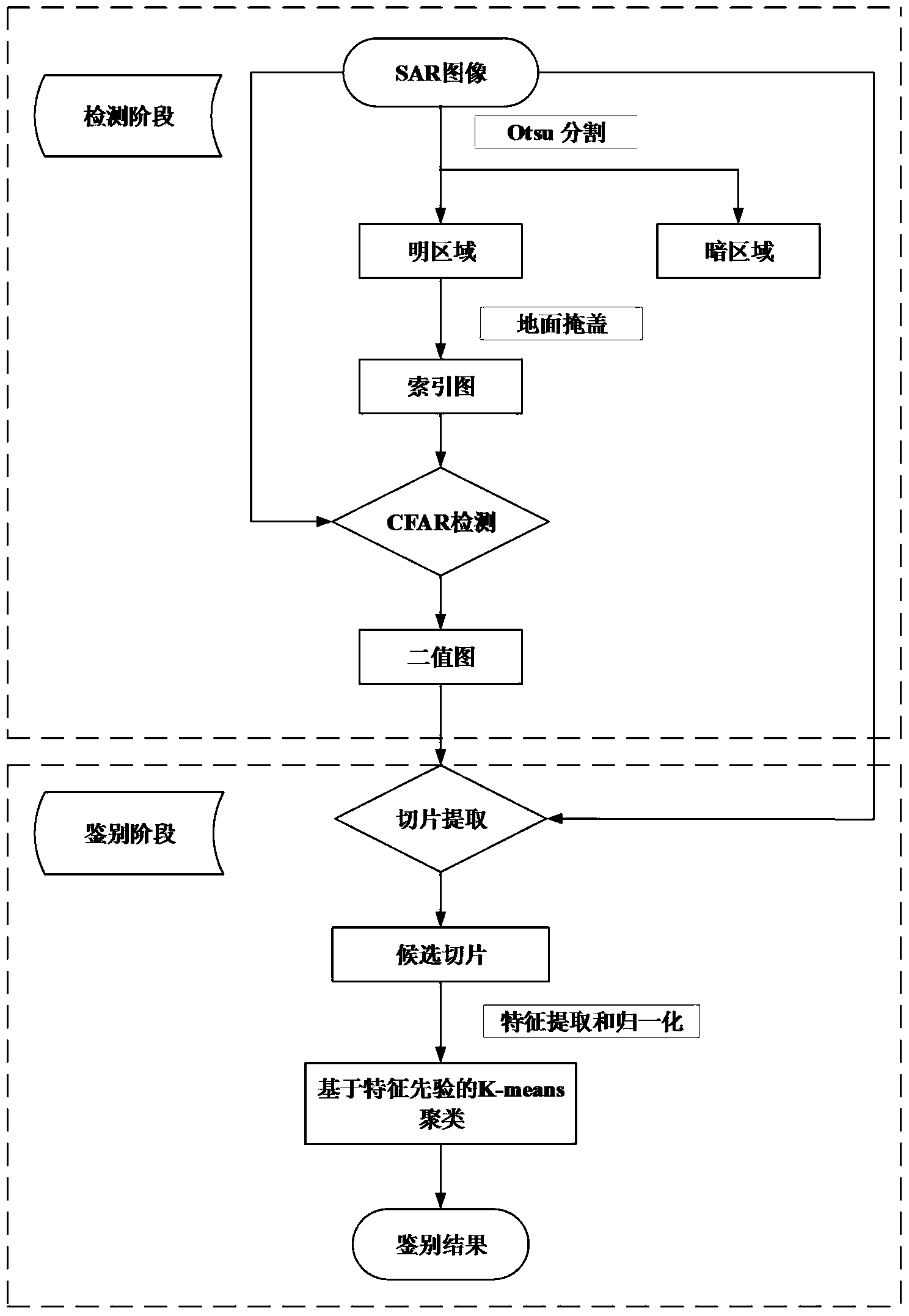
Fast high-resolution SAR (synthetic aperture radar) image ship detection method based on feature fusion and clustering
ActiveCN104036239ANarrow searchDetection speedCharacter and pattern recognitionSynthetic aperture radarInverse synthetic aperture radar
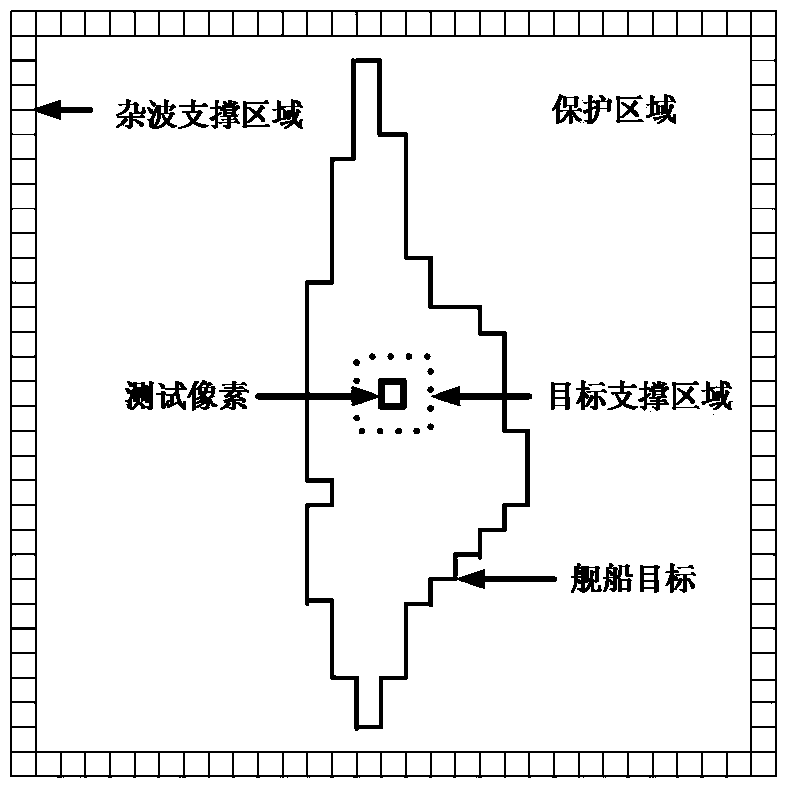
The invention discloses a fast high-resolution SAR (synthetic aperture radar) image ship detection method based on feature fusion and clustering. The fast high-resolution SAR image ship detection method comprises the following steps: on the basis of the back scattering characteristics of each ground object and the prior information of a ship target in an SAR image, positioning a target potential position index map by an Otsu algorithm and range constraint; on the index map, pre-screening to obtain a detection binary segmentation map by a CFAR (constant false alarm rate) algorithm based on a local contrast; carrying out morphological processing to a detection result, and extracting a potential target slice from the SAR image and a detected binary segmentation map according to a processing result; and carrying out K-means clustering to the extracted slice by a designed identification feature to obtain a final identification result. According to the fast high-resolution SAR image ship detection method based on feature fusion and clustering, the data volume of a detection stage is effectively reduced by pre-processing, and point-to-point detection is not needed / the time of point-to-point detection is saved. Meanwhile, a target identification problem under the condition of insufficient training samples at present can be solved by the designed characteristic and a non-supervision clustering method, the target can be effectively positioned, and the size of the target can be estimated.
Owner:西安维恩智联数据科技有限公司
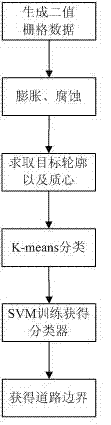
A method of combining svm and lidar to detect unstructured road boundaries
ActiveCN102270301AImprove robustnessImprove accuracyCharacter and pattern recognitionSupport vector machineRadar
The invention discloses a method for detecting an unstructured road boundary on which an intelligent vehicle runs. The method comprises the following steps of: analyzing and processing frame data of a vehicle-mounted 64 line laser radar to obtain frame two-value raster data, expanding and corroding the frame two-value raster data to fill small space between data of barriers on the same side of a road and keeping the whole outline unchanged; solving the outline of each barrier target, storing in a chain code mode and solving the mass center of the outline; performing K means clustering on the barrier targets, wherein a sample is the solved mass center, the targets comprise barrier targets on the left side of the road and barrier targets on the right side of the road; and training by using a support vector machine (SVM), wherein the sample is the outline points of the classified barrier targets, thus obtaining a classifier, and finally solving a straight line section which describes theroad boundary according to the classifier, the maximum interval conditions and the raster data. In the method, data involved in calculation is reduced as much as possible; and the method is high in real-time property, and the solved road boundary accuracy rate is high.
Owner:NANJING UNIV OF SCI & TECH
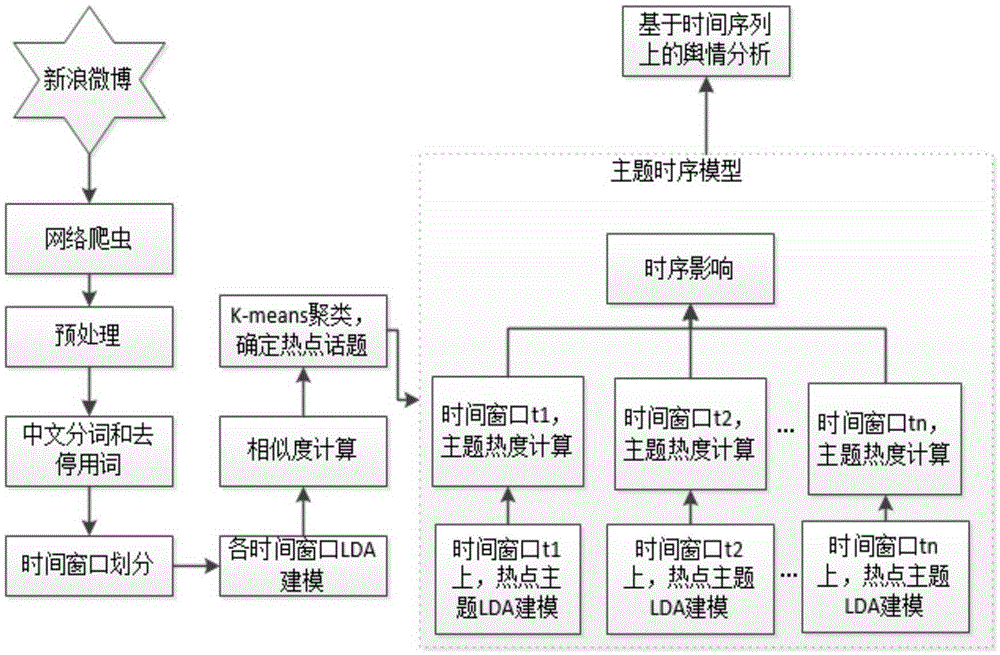
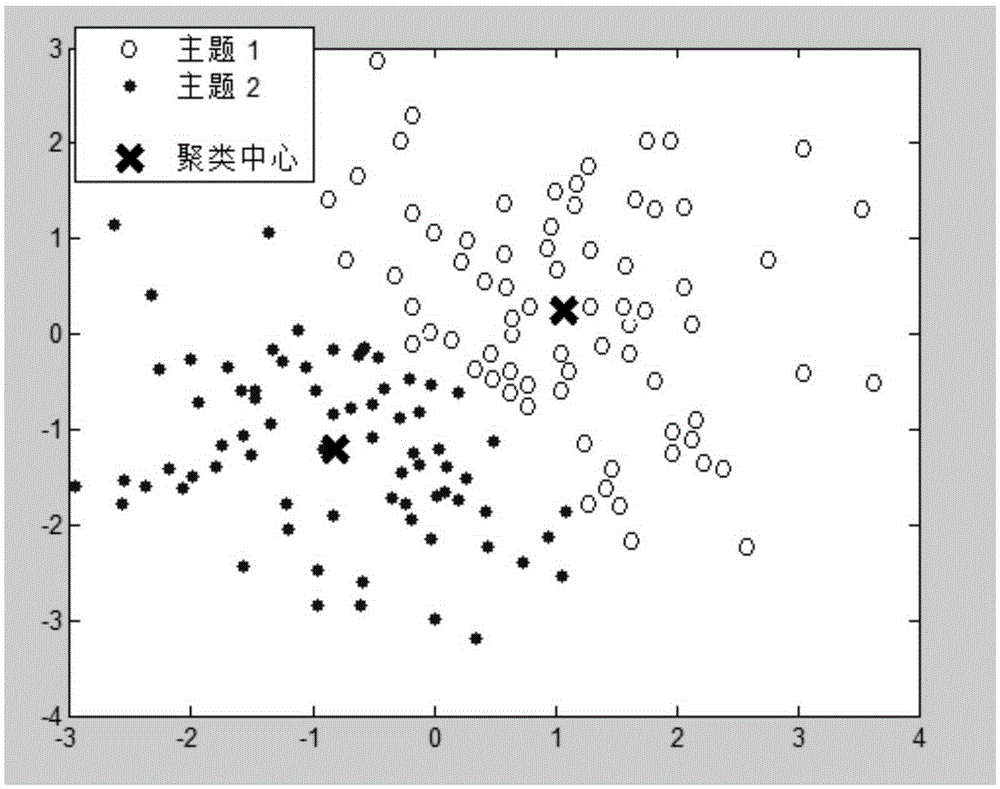
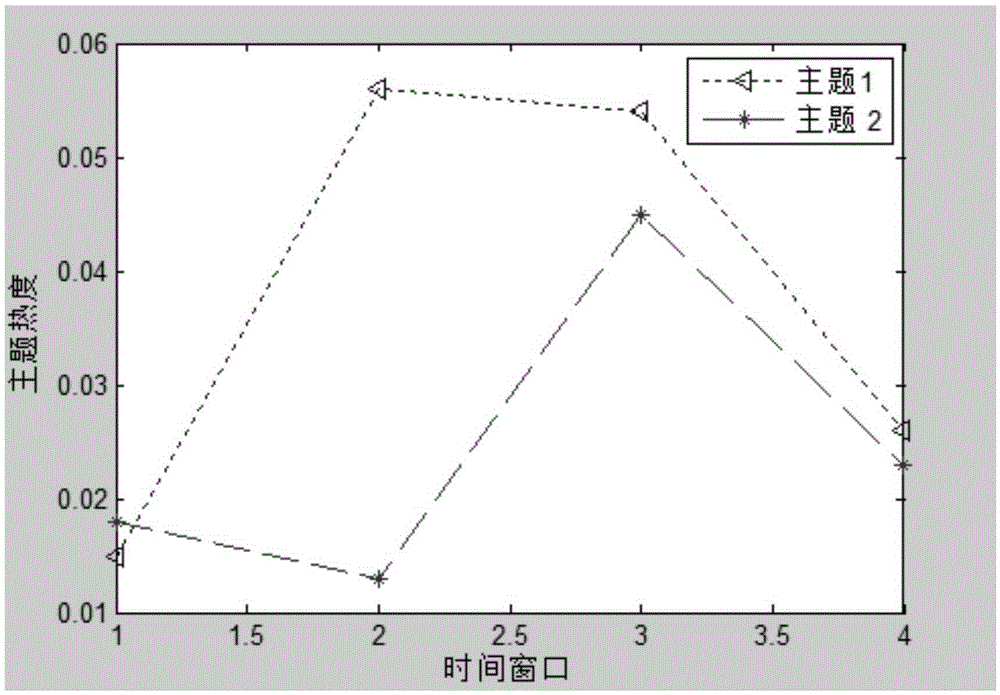
Time window based LDA microblog topic trend detection method and apparatus
The invention discloses a time window based LDA microblog topic trend detection method and apparatus. The method comprises: extracting a topic word from a word set by utilizing an LDA model in each time window, and obtaining global topics; performing similarity computing on the global topics, and performing K-means clustering to obtain hot topics conforming to public opinion analysis; extracting feature words of each hot topic in each time window in sequence in combination with the hot topic through the LDA topic model; and in combination with results of the feature words, computing a popular value of the hot topic in each time window, and drawing a trend graph of the hot topic. The apparatus comprises a first acquisition module, a second acquisition module, an extraction module and a drawing module. According to the detection method and apparatus, the precision of microblog topic detection is improved, so that a trend index is more expressive, and a more accurate basis is provided for analyzing a hot topic trend.
Owner:TIANJIN UNIV
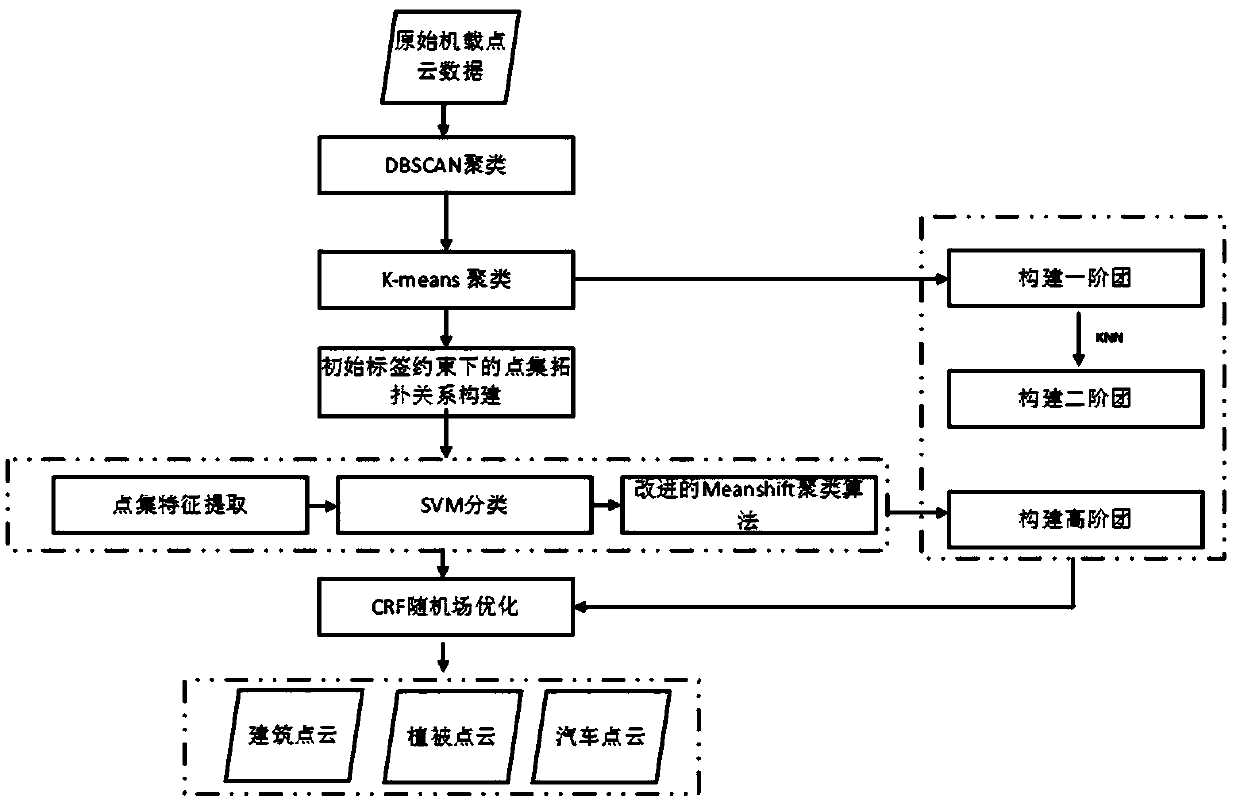
Airborne laser point cloud classification method based on high-order conditional random field
ActiveCN110110802ABuild accuratelyAccurate classificationCharacter and pattern recognitionConditional random fieldClassification methods
The invention provides an airborne laser point cloud classification method based on a high-order conditional random field. The airborne laser point cloud classification method specifically comprises the following steps: (1) point cloud segmentation based on DBSCAN clustering; (2) point cloud over-segmentation based on the K-means cluster; (3) construction of a point set adjacency relation based onthe Meanshift clustering; and (4) construction of a point cloud classification method of a high-order conditional random field based on the multi-level point set. The method has the advantages that:(1) a multi-layer clustering point set structure construction method is provided, and a connection relation between point sets is constructed by introducing a Meanshift point set cluster constrained by category labels, so that the categories of the point sets can be classified more accurately; (2) a multi-level point set of the non-linear point cloud number can be adaptively constructed, and information such as the structure and the shape of a point cloud target can be more completely represented; and (3) a CRF model is constructed by taking the point set as a first-order item, and higher efficiency and a classification effect are achieved, so that a higher framework is integrated, and a better effect is obtained.
Owner:NANJING FORESTRY UNIV
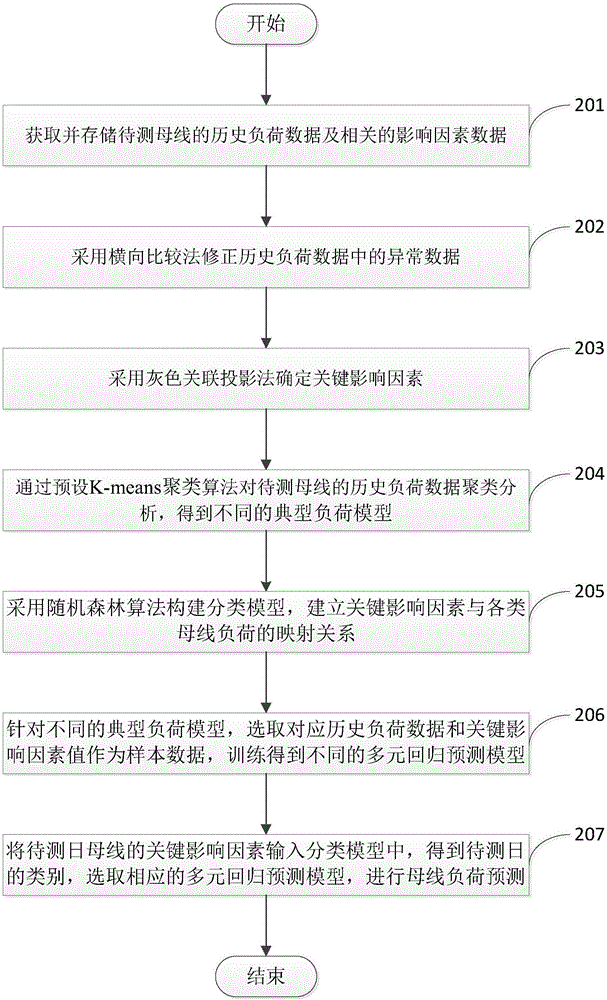
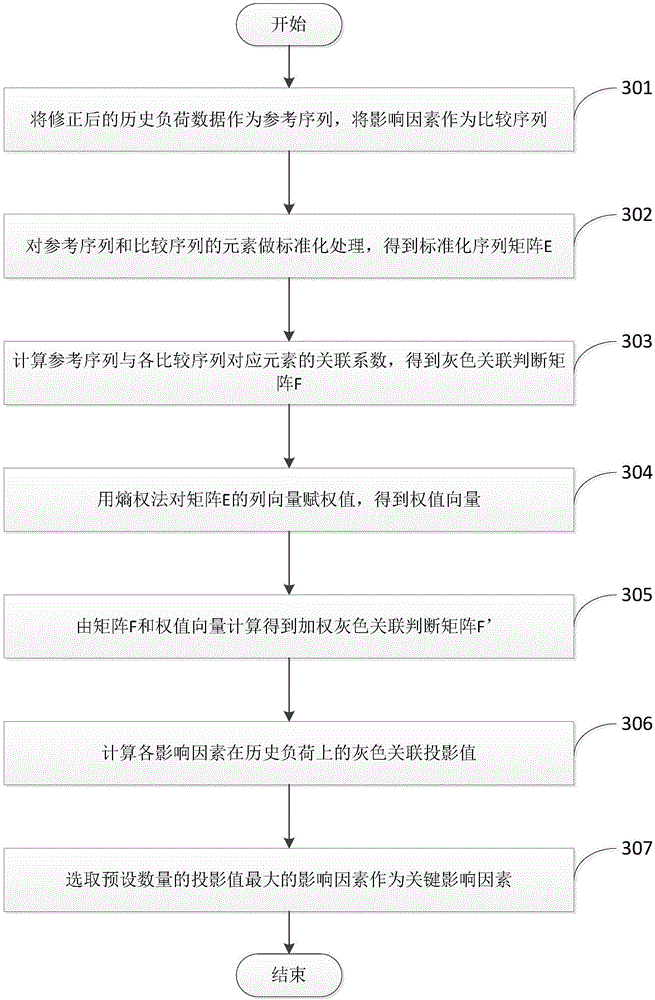
Bus load prediction method
ActiveCN106485262AHigh precisionMeet real-time requirementsCharacter and pattern recognitionEnsemble learningData dredgingDecision taking
The invention discloses a bus load prediction method. The method comprises the following steps: correcting abnormal values in historical load data by use of a transverse comparison method, and determining key influence factors of bus load by use of a grey relation projection method; putting load curves with similar features in the same category by use of an improved K-Means clustering method to get a plurality of typical load patterns, building a random forest classification model, and establishing the mapping relationship between influence factors and clustering results; for each load pattern, training a plurality of prediction models by use of a multivariate linear regression method; and determining the category of a day under test, and selecting a matching regression model to realize load prediction. A data mining method is introduced to analyze the changing rules of bus load, and a prediction model library is built. Model matching is realized based on the category of a day under test. The accuracy and real-time performance of short-term bus load prediction are improved. More accurate decision support is provided for power grid planning and real-time dispatching.
Owner:JINCHENG POWER SUPPLY COMPANY OF STATE GRID SHANXI ELECTRIC POWER +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com