Key derivation method and device applicable to digital currency
A digital currency and key technology, applied in the field of information security, can solve problems such as difficult management, large key backup volume, and digital currency can no longer be consumed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
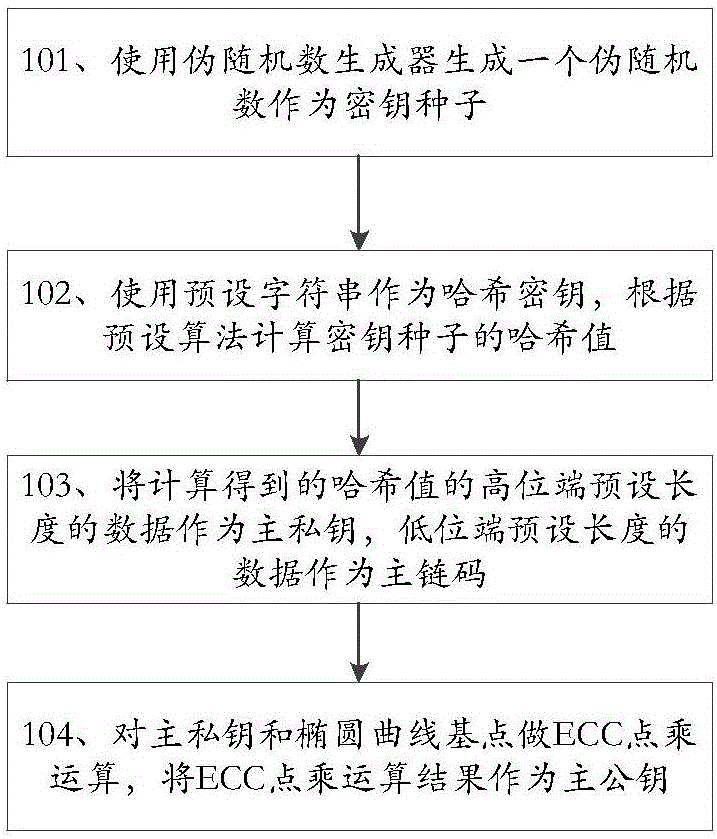
[0174] This embodiment provides a key derivation method suitable for digital currency. The key derived by the method provided by this embodiment has a tree structure. The root of the tree is the master key and the master chain code, and the master key is the The parent key and the main chain code are the child key and the child chain code generated by the parent chain code are the first-level key and the first-level chain code of the tree, and the first-level key is the parent key and the first-level chain code The child key and child chaincode generated for the parent chaincode are the second-level key and second-level chaincode of the tree, and so on.
[0175] A subkey index is introduced when generating a subkey according to a parent key, and different subkeys are generated according to different subkey indexes, and the subkey index and the subkey are in one-to-one correspondence.
[0176] Described method specifically comprises:
[0177] 1. The derivation process of maste...
Embodiment 2
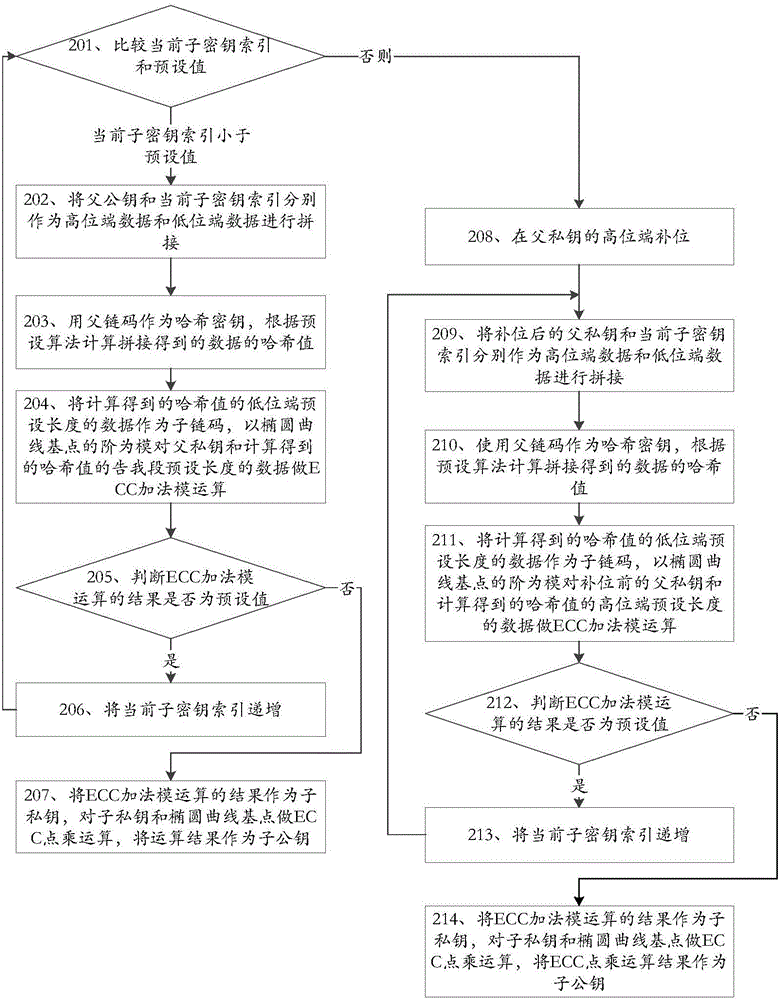
[0326] This embodiment provides a key derivation device suitable for digital currency. The key derived by the device provided by this embodiment is in a tree structure. The root of the tree is the master key and the master chain code, and the master key is the The parent key and the main chain code are the child key and the child chain code generated by the parent chain code are the first-level key and the first-level chain code of the tree, and the first-level key is the parent key and the first-level chain code The child key and child chaincode generated for the parent chaincode are the second-level key and second-level chaincode of the tree, and so on.
[0327] A subkey index is introduced when generating a subkey according to a parent key, and different subkeys are generated according to different subkey indexes, and the subkey index and the subkey are in one-to-one correspondence.
[0328] The device provided by this embodiment is as Figure 6 shown, including:
[0329]...
Embodiment 3
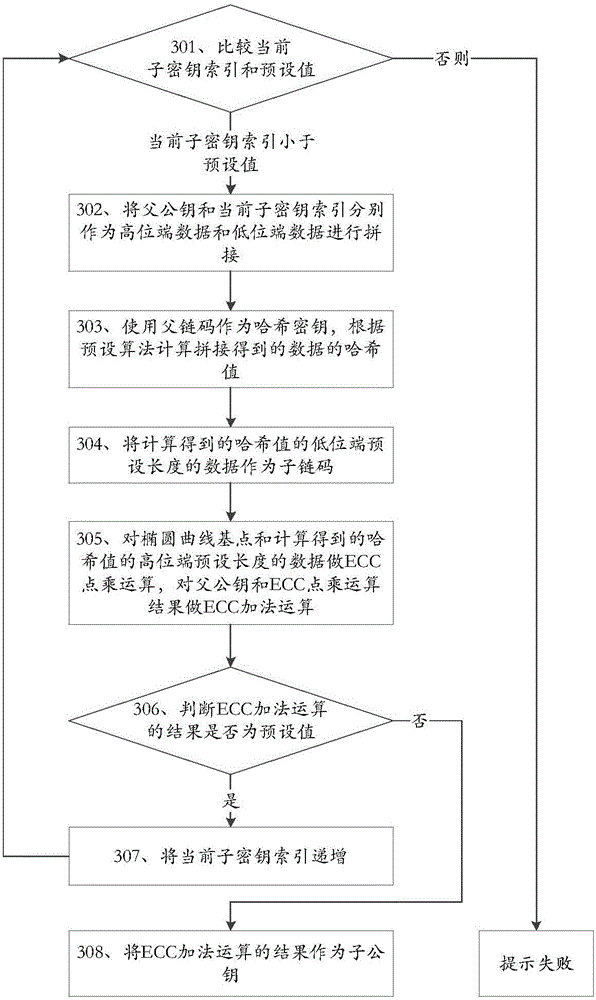
[0374] This embodiment provides a key derivation device suitable for digital currency, such as Figure 7 shown, including:
[0375] The first acquisition module 91 is used to use the master private key, master public key and master chain code of the digital currency wallet as the parent private key, parent public key and parent chain code respectively, and use the first child key index as the child key index ;
[0376] The first derivation module 92 is used to derive the child private key, child public key and child chain code according to the parent private key, parent public key, parent chain code and child key index obtained by the first acquisition module 91;
[0377] The account key generation module 93 is used to use the sub-private key, sub-public key and sub-chain code derived by the first derivation module 92 as the master private key, master public key and master chain code of the digital currency account respectively.
[0378] In one aspect, the first derivation m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com