Method with privacy protection function for validating creditability of public terminal
A technology of privacy protection and verification method, which is applied in the field of public terminal credibility verification, and can solve problems that are highly technical and difficult for ordinary users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
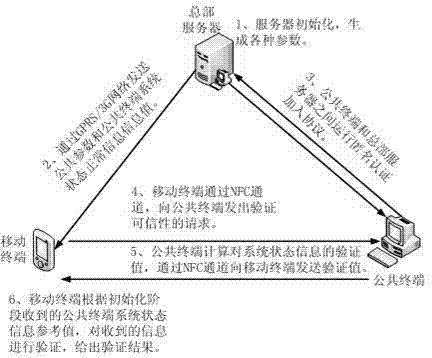
[0040] Such as figure 1 As shown, the described public terminal credibility verification method with privacy protection function, the specific steps are as follows:
[0041] Step 1: The headquarters server to which the public terminal belongs runs the authentication protocol initialization algorithm to generate various necessary parameters:
[0042] 1) Generate commitment parameters . In this step, three groups with sufficiently large prime order are chosen , for the group respectively choose random generators such that , , and also choose a bilinear map: . Next is to choose a random hash function , . . In the present invention, operations on the TPM are strictly limited to group , doing so allows the parameter A subset of TPM parameters allowable Priority was previously set to .
[0043] 2) Generate signature and verification parameters : choose two hash functions, with , the final setting .
[0044] 3) Generate parameters for the publi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com