Patents
Literature
310 results about "Services computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Services Computing has become a cross-discipline that covers the science and technology of bridging the gap between business services and IT services. The underlying technology suite includes Web services and service-oriented architecture (SOA), cloud computing, business consulting methodology and utilities, business process modeling, transformation and integration. This scope of Services Computing covers the whole life-cycle of service provision that includes business componentization, services modeling, services creation, services realization, services annotation, services deployment, services discovery, services composition, services delivery, service-to-service collaboration, services monitoring, services optimization, as well as services management. The goal of Services Computing is to enable IT services and computing technology to perform business services more efficiently and effectively.
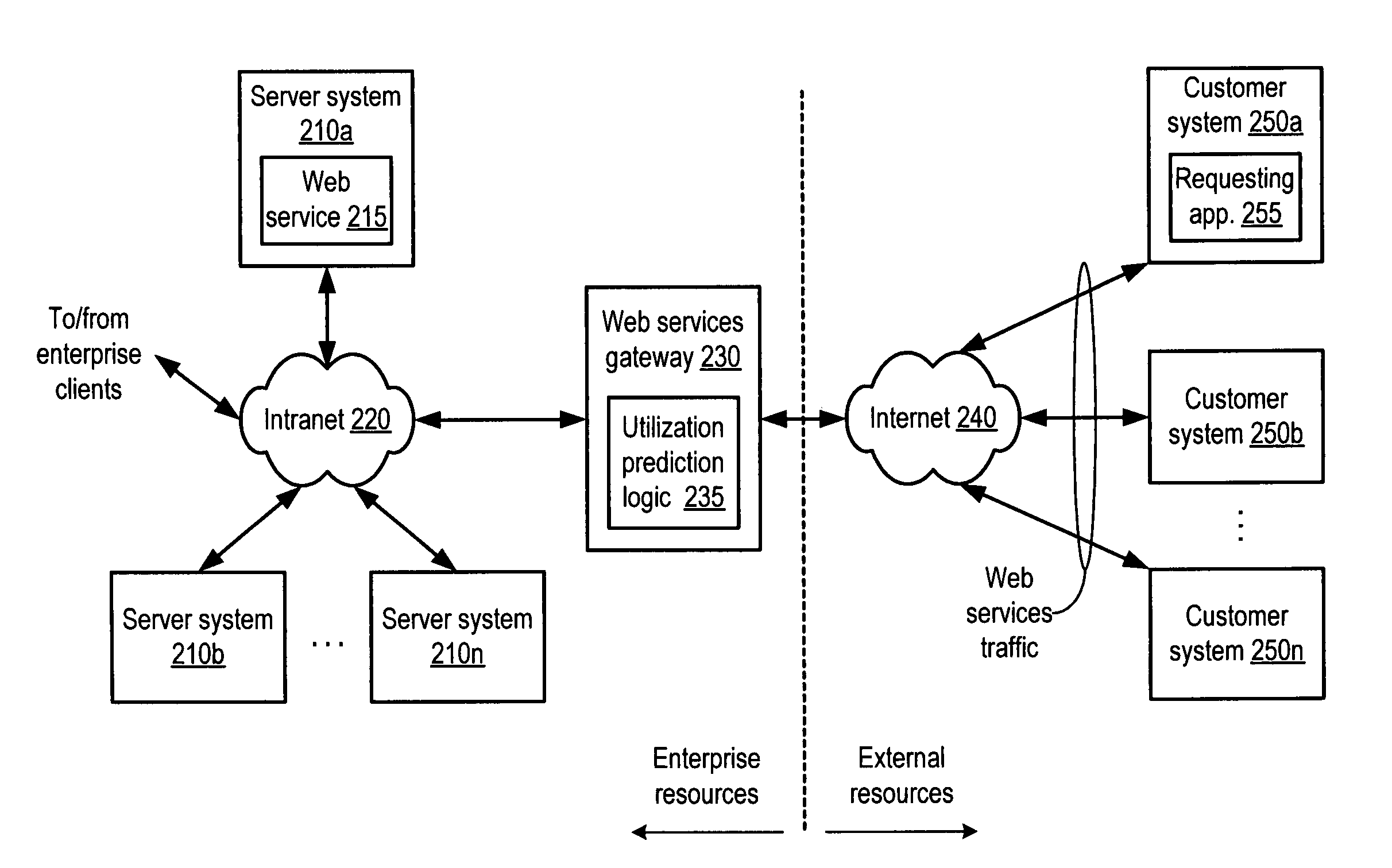
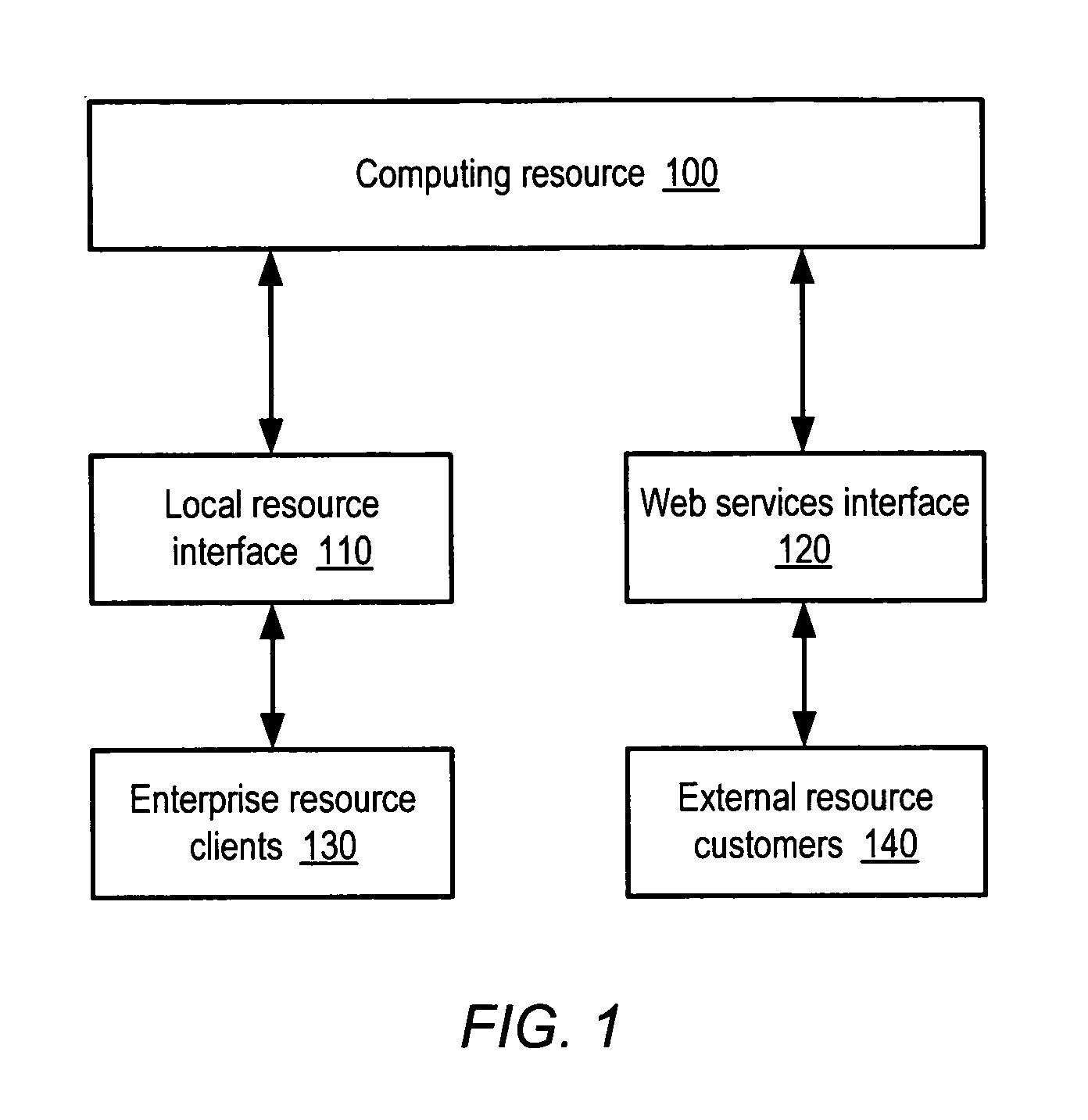
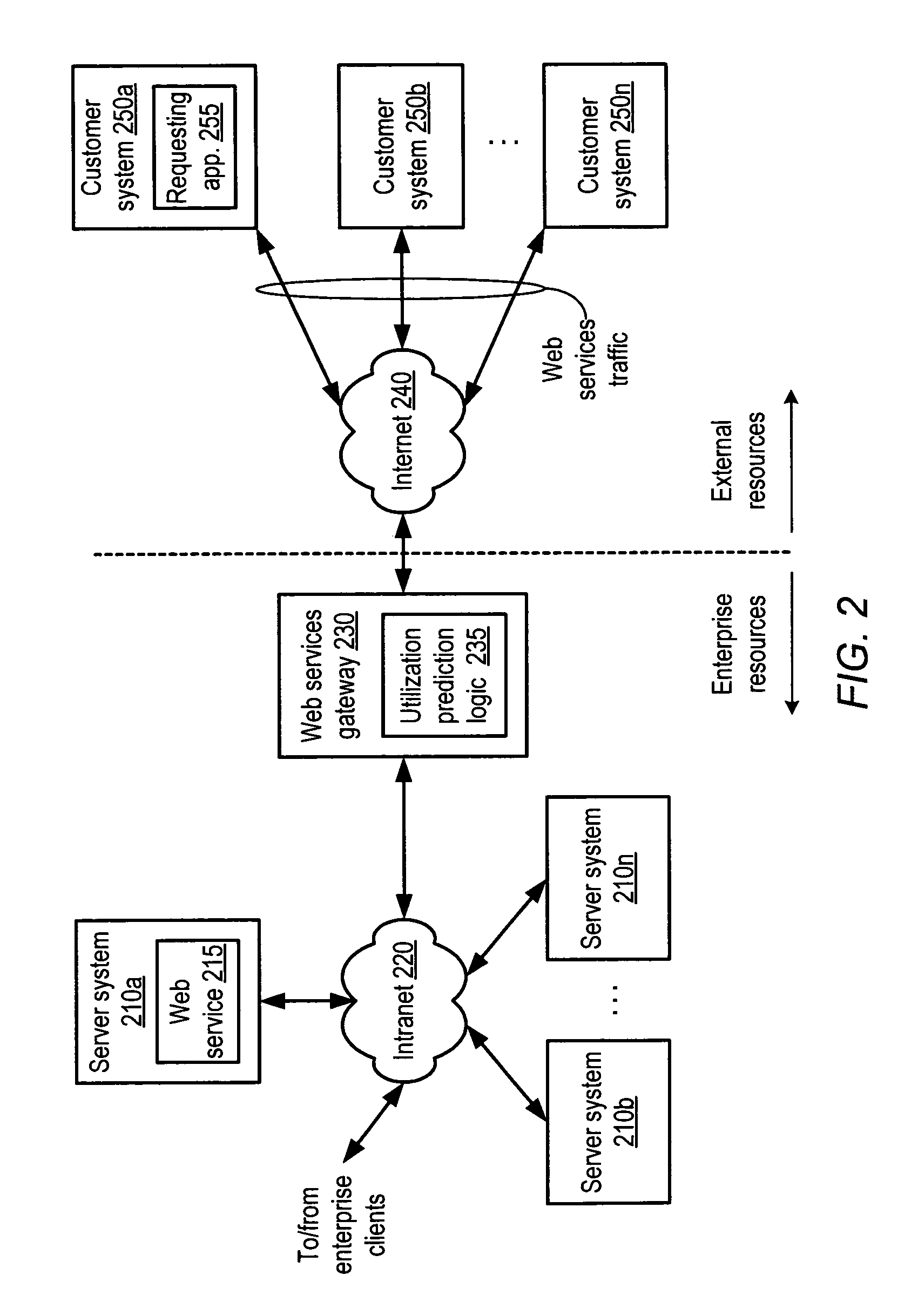
Method and system for dynamic pricing of web services utilization
A method and system for dynamic pricing of web services utilization. According to one embodiment, a method may include dynamically predicting utilization of a web services computing resource that is expected to occur during a given interval of time, and dependent upon the dynamically predicted utilization, setting a price associated with utilization of the web services computing resource occurring during the given interval of time. The method may further include providing the price to a customer.
Owner:AMAZON TECH INC
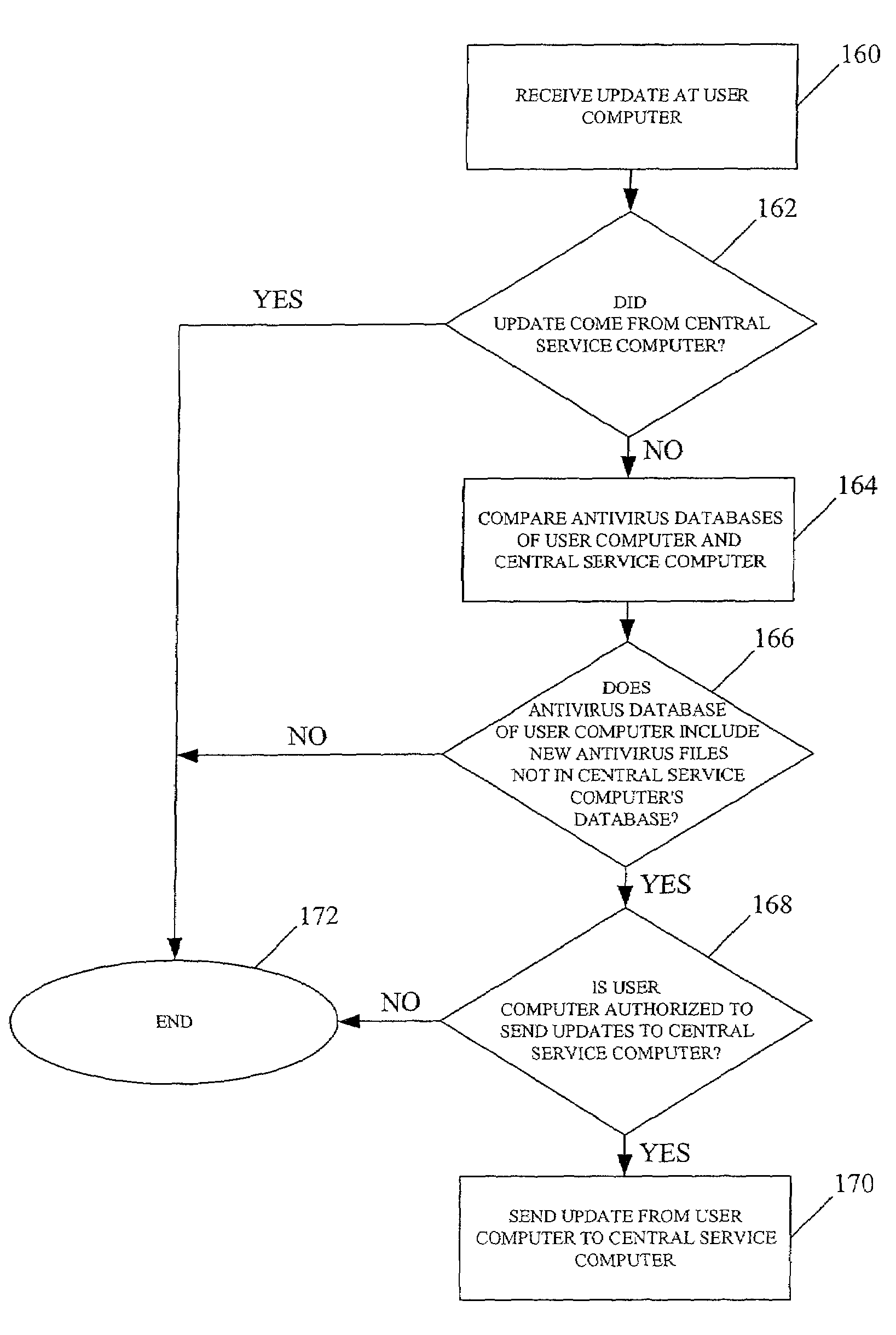
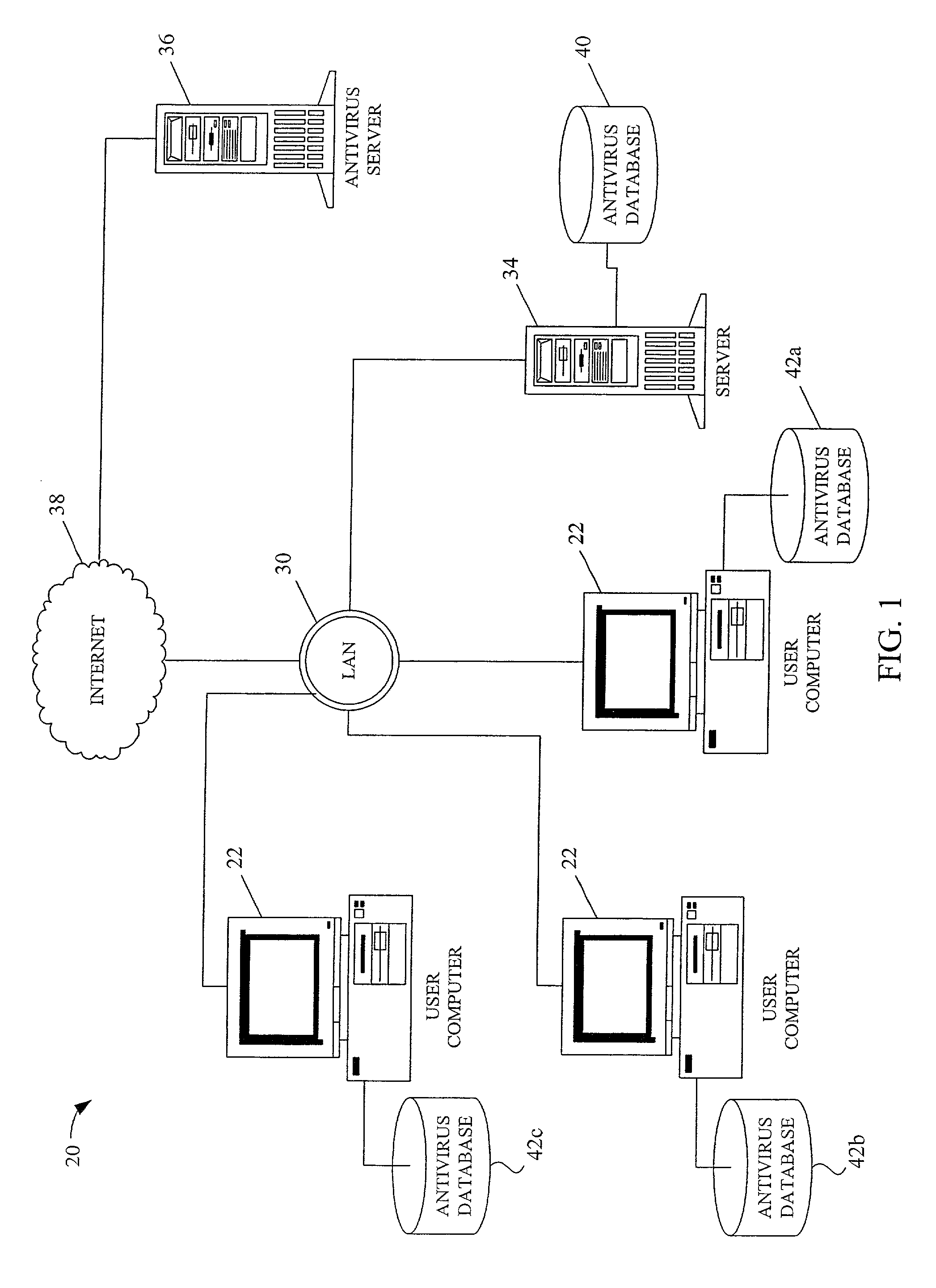
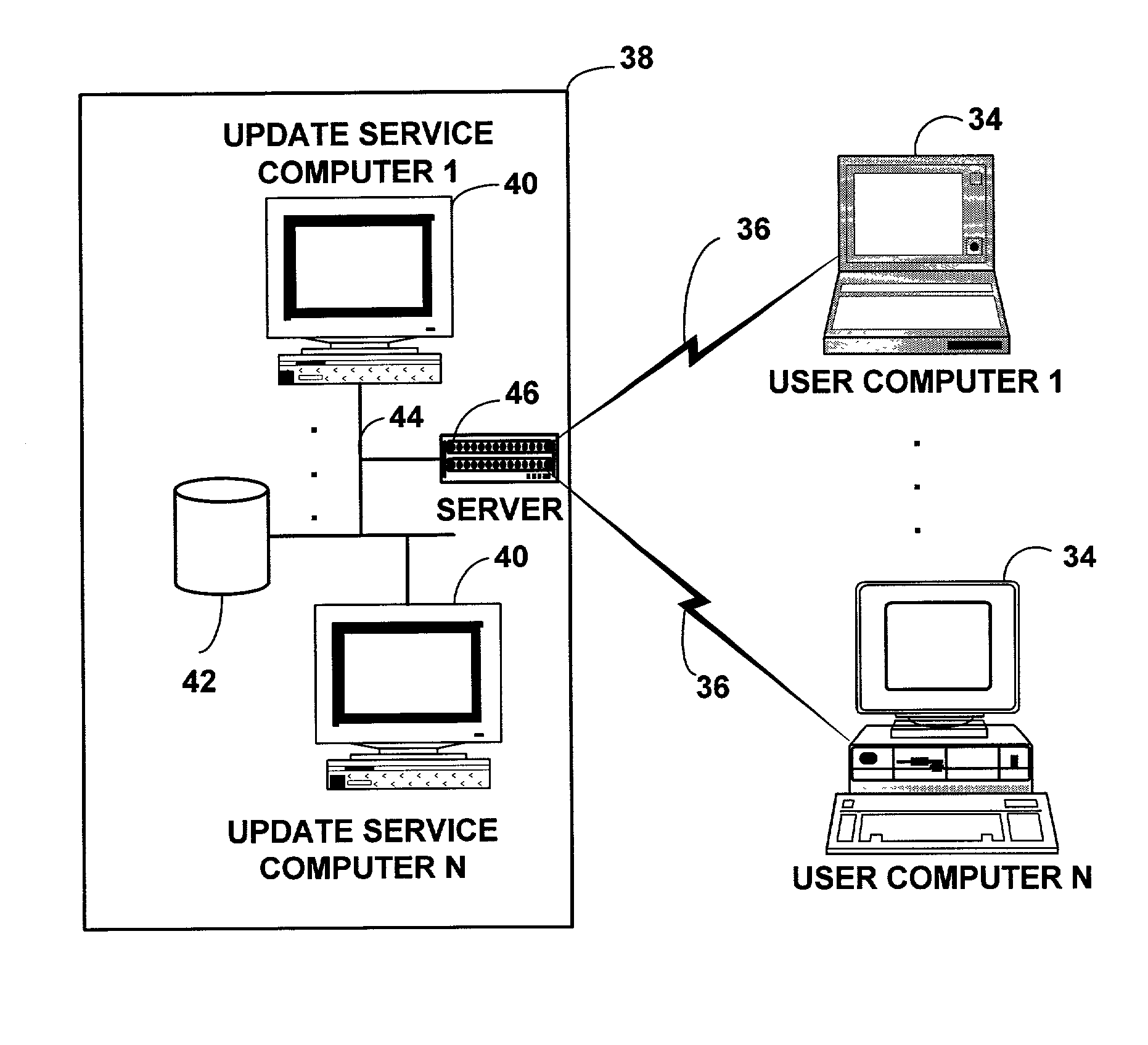
Method and system for bi-directional updating of antivirus database
A method for maintaining updated antivirus files within a computer network comprising at least one user computer and at least one central service computer. Each of the user computer and central service computer has an antivirus database and the network is connected to an antivirus server. The method includes receiving a new antivirus file at one of the user computer and the central service computer and updating the computer's antivirus database. The antivirus databases of the central service computer and the user computer are compared to determine if one of the databases contain new antivirus files not contained within the other database. The central service computer and the user computer are each configured to send the new antivirus files to the other of the central service computer and the user computer to update the antivirus database.
Owner:MCAFEE LLC
Personalized multi-service computer environment
InactiveUS7062475B1Easy to useEasy to identifyGenetic modelsDigital computer detailsPersonalizationHyperlink
A system and method for tracking a user history, for presentation thereof within a browser display. An executable software construct operates at a client machine to trap object references, which are then transmitted to a server. The server analyzes the object references and organizes them into a display structure. The display structure is then displayed within the browser, including hyperlinks to allow the user to select a prior system state to which he seeks to return. Preferably, the software construct also manages objects associated with the object reference, for example cookies associated with URLs, in order to assure full definition of the desired state. The display structure may also be provided to browsers distinct from the originating browser.
Owner:UNWIRED BROADBAND INC
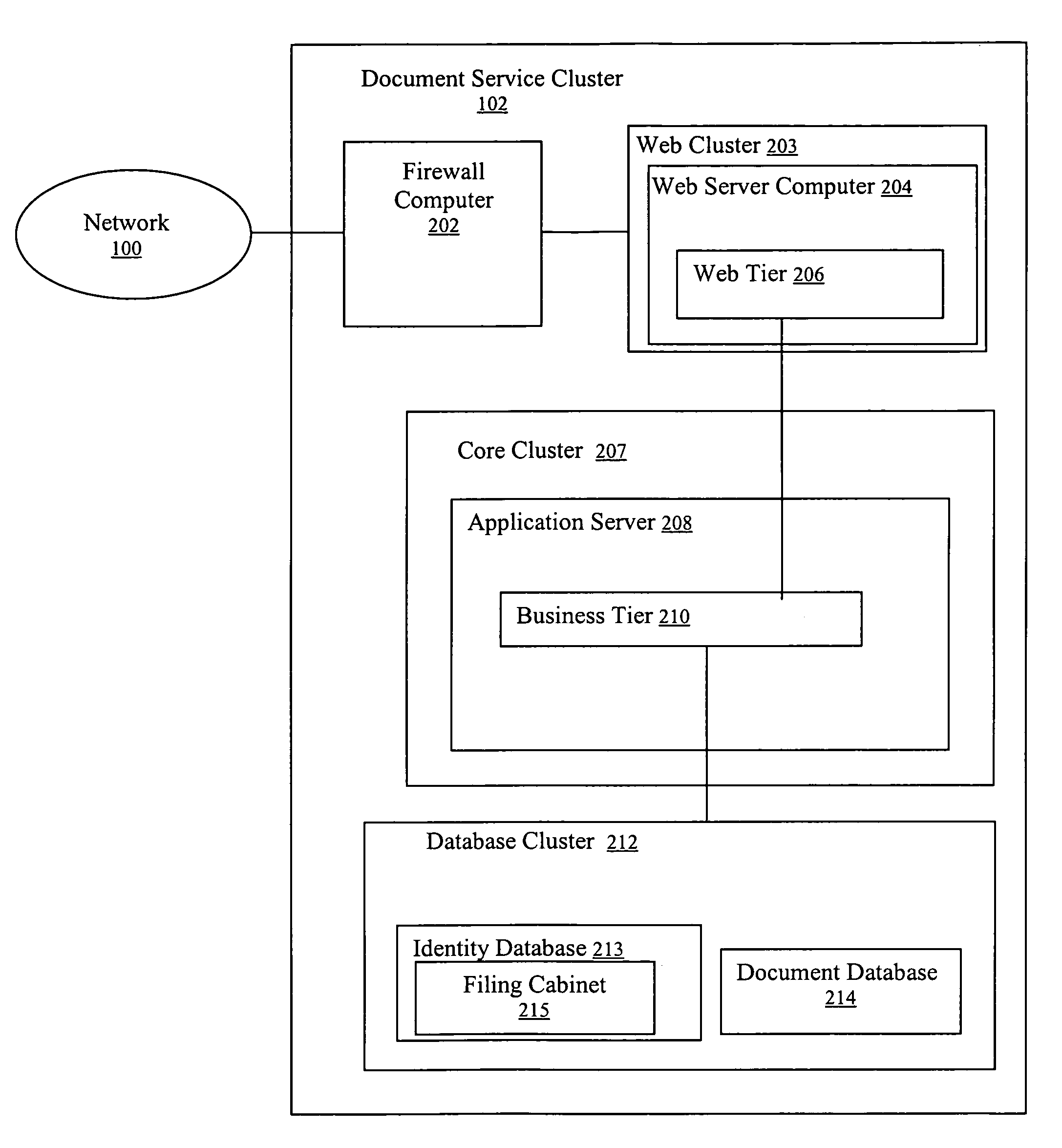
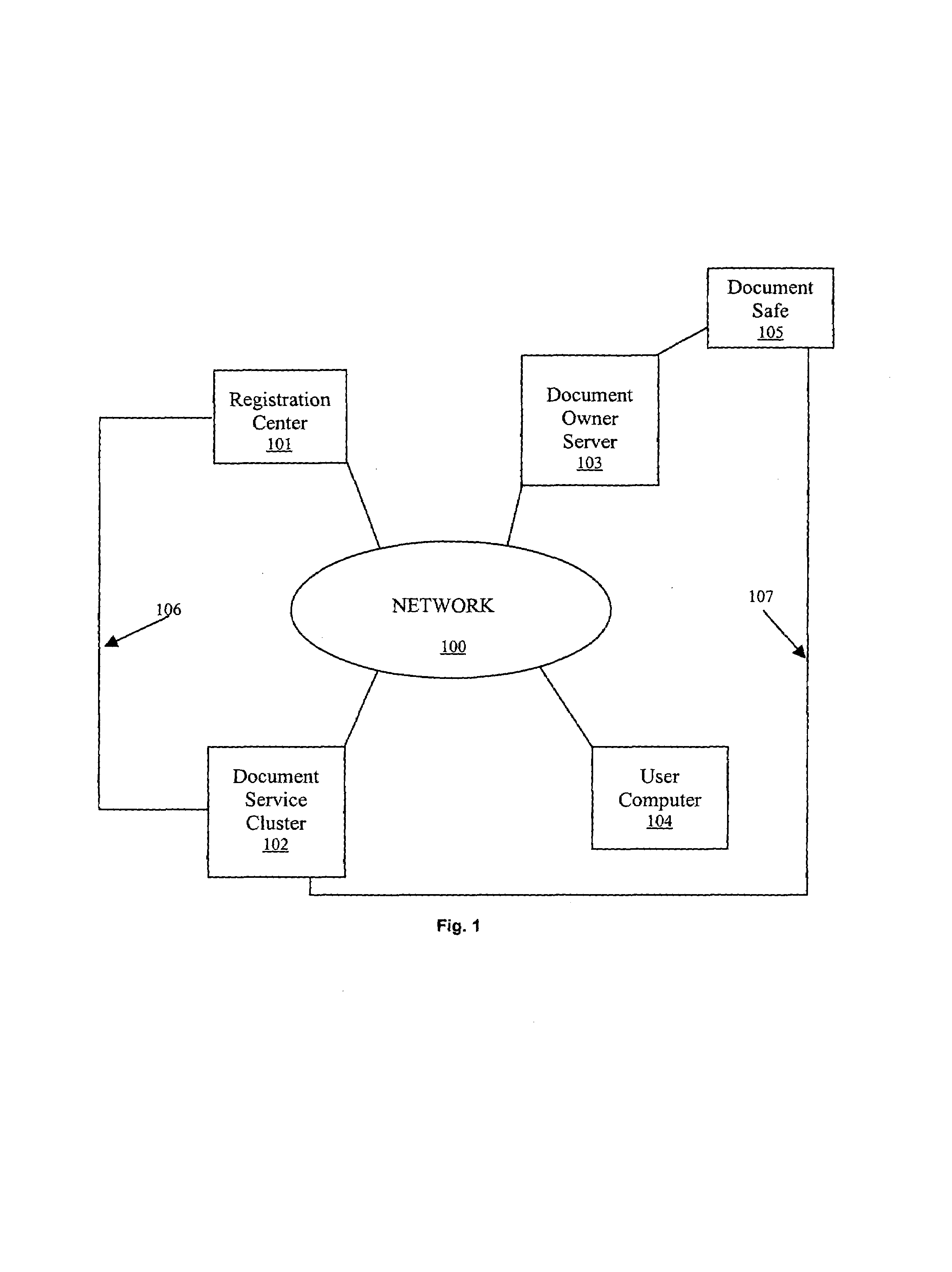
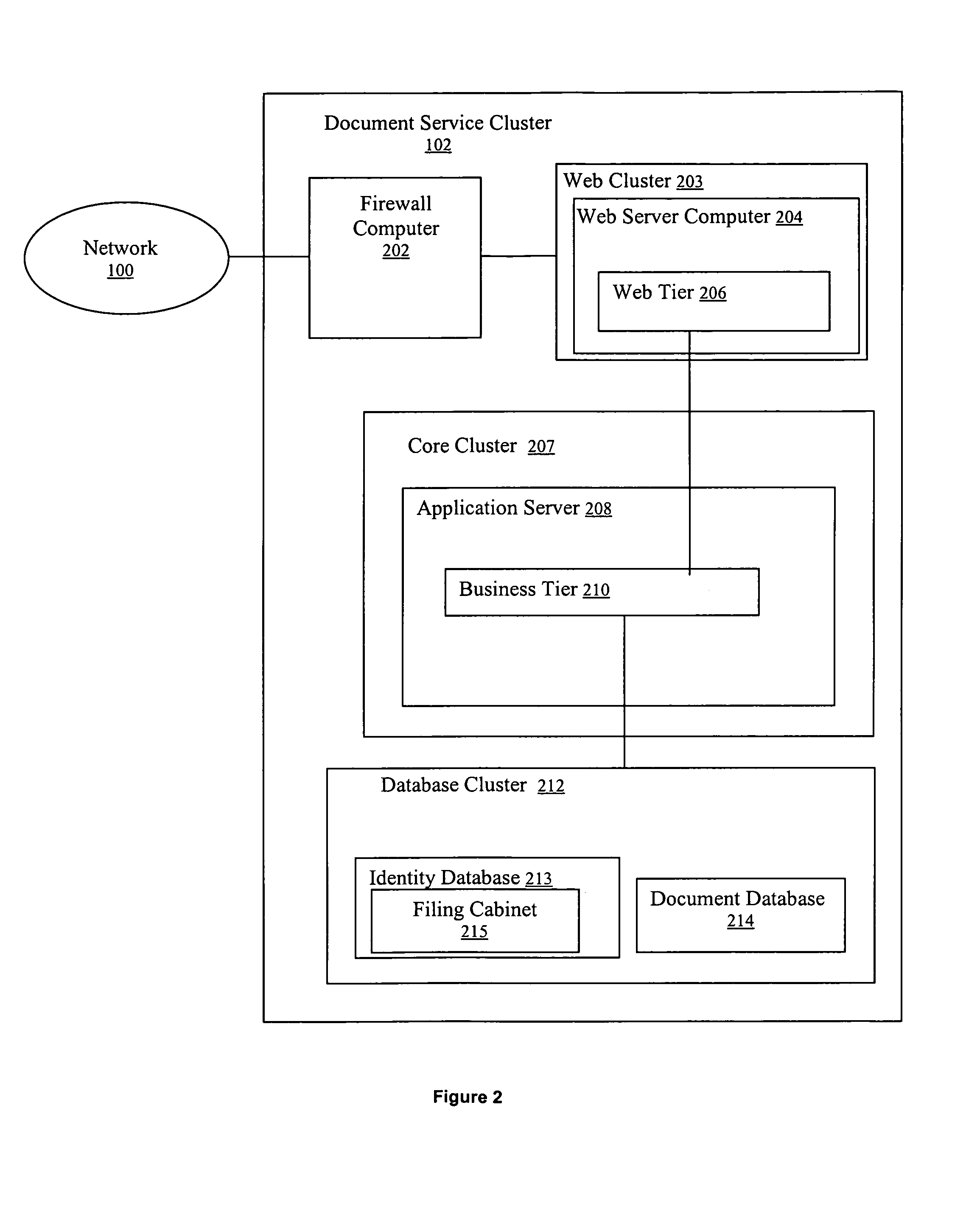
Method and system for signing and authenticating electronic documents
InactiveUS7237114B1Complete private encryption key constructing and reconstructing can be avoidedPrevent steppingUser identity/authority verificationUnauthorized memory use protectionElectronic documentComputer cluster
A system and method for signing, sorting, and authenticating electronic documents using public key cryptography. The system comprises a document service computer cluster connected to user computers, document owner server computers, and registration computers via a network such as for example, the internet or the world wide web. Document owners and system users can store electronic documents in an encrypted database located on the document service computer cluster, or on a document safe connected to the document owner server. Users can sign documents by identifying the document to be signed and sending a signing request to the document service computer cluster. The document service computer cluster retrieves the user's private key, which is located securely in a database on the cluster, and signs the identified document. No dedicated signing software need be installed on the user computer prior to accessing the document service computer cluster.
Owner:SIGNIX
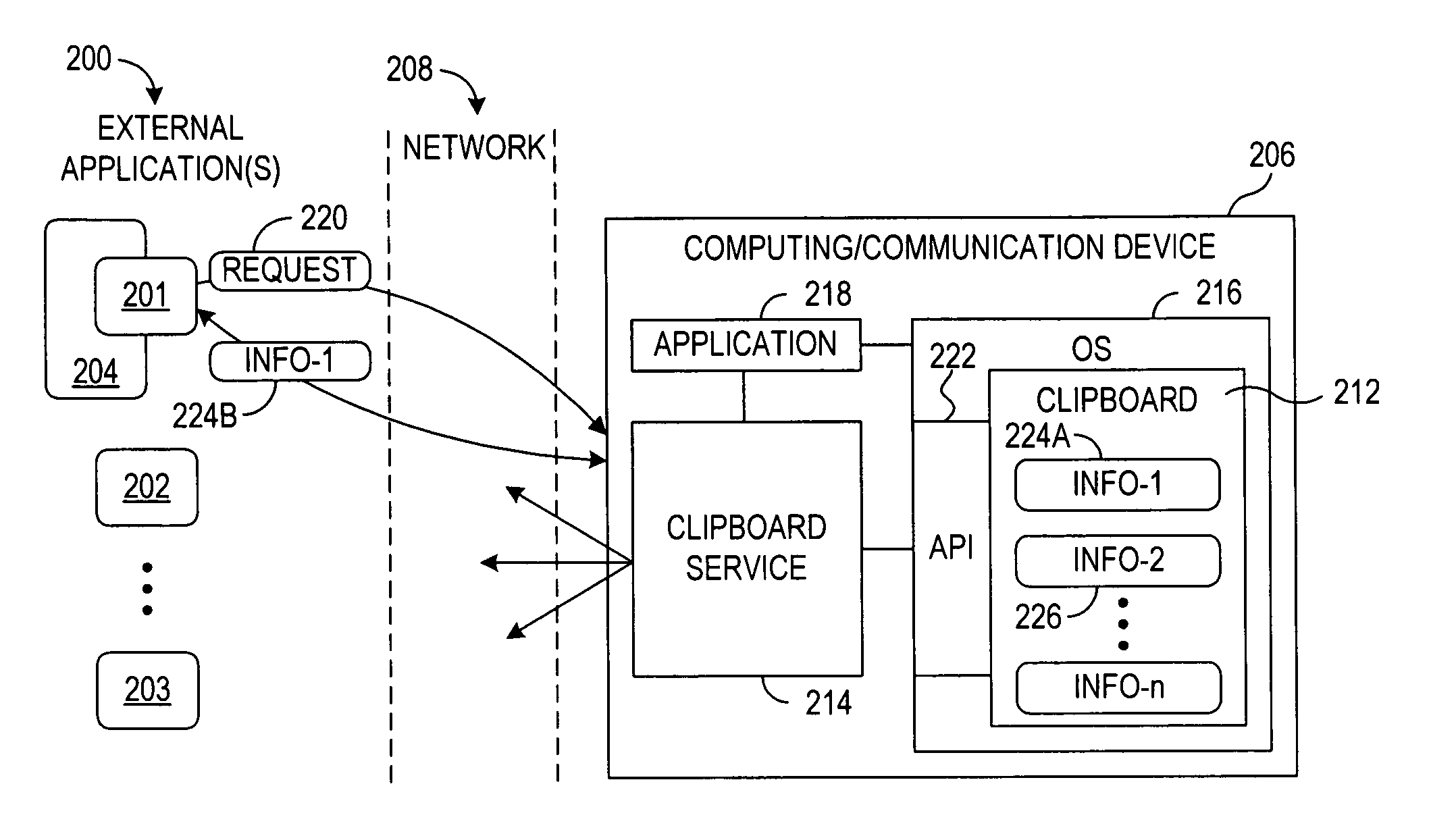
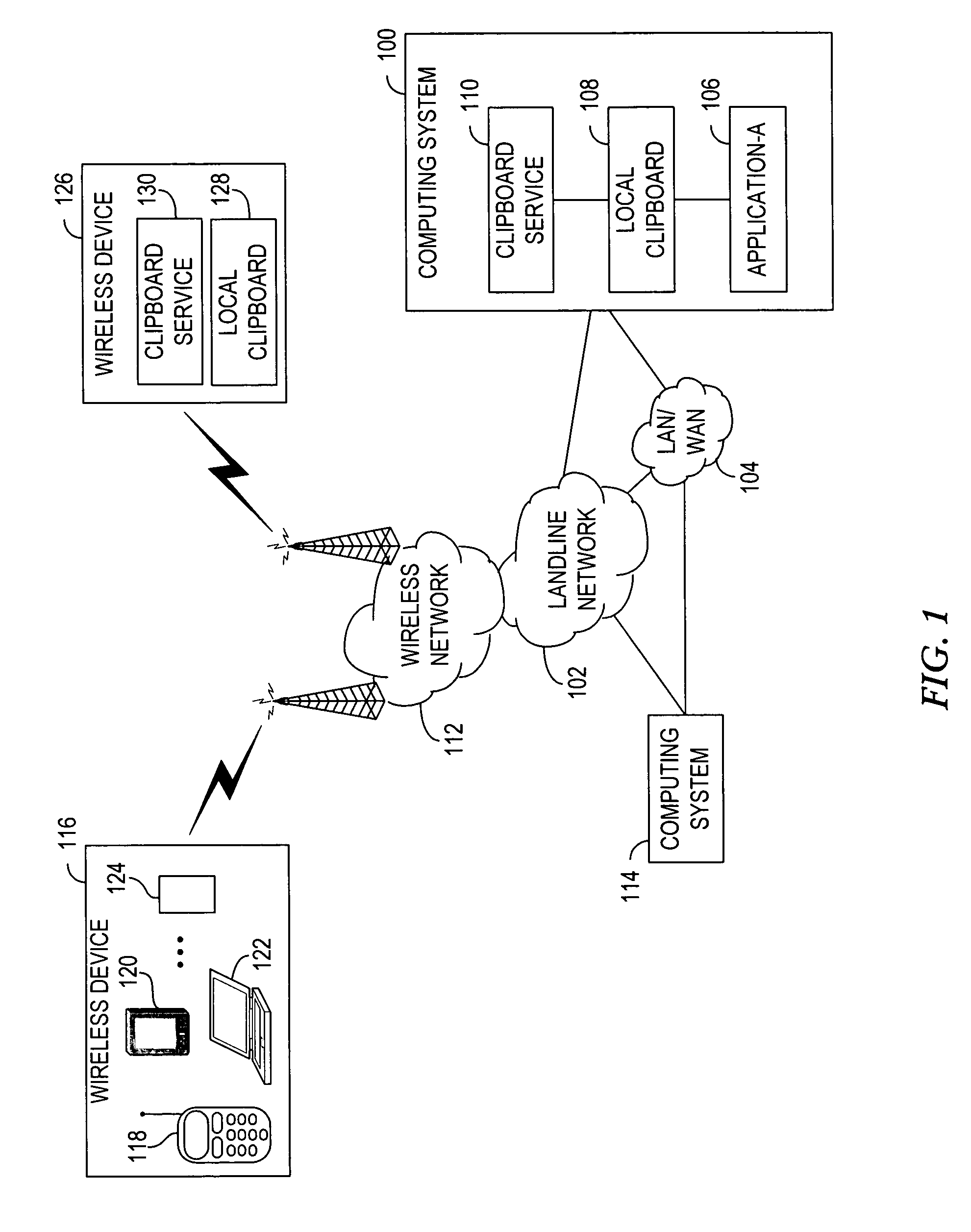
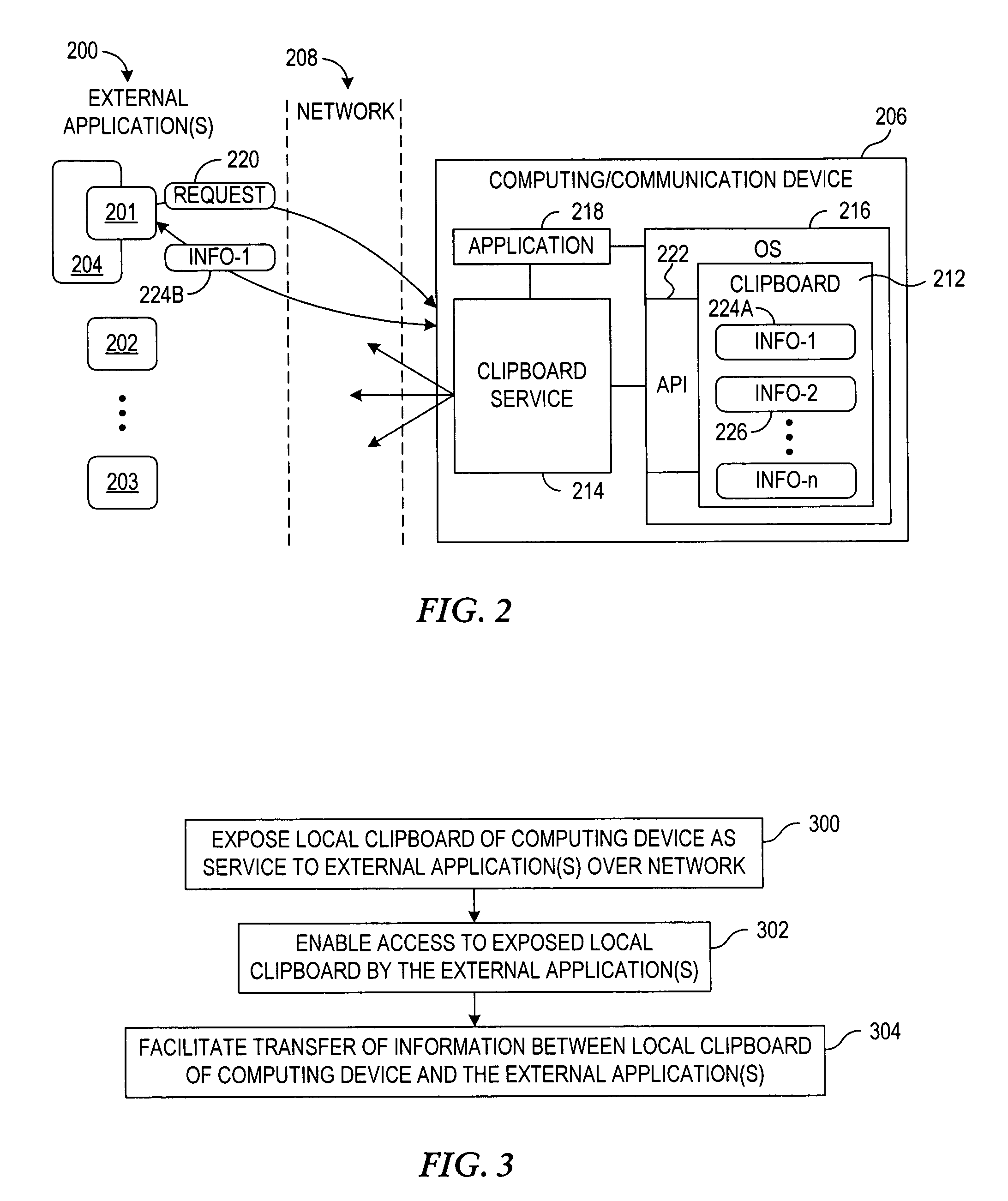
System and method for exposing local clipboard functionality towards external applications
InactiveUS20050066335A1Multiprogramming arrangementsMultiple digital computer combinationsExternal applicationOperating system
A system, apparatus and method for allowing external applications to post information to, and / or retrieve information from, a local clipboard associated with another device that is exposed as a service towards the external applications. The local clipboard of a computing device is exposed towards external applications as a service. A request is received from the external application indicating that a transfer of information between the exposed local clipboard of the computing device and the external application is requested. The information is transferred between the local clipboard of the computing device and the external application in response to the request.
Owner:NOKIA CORP
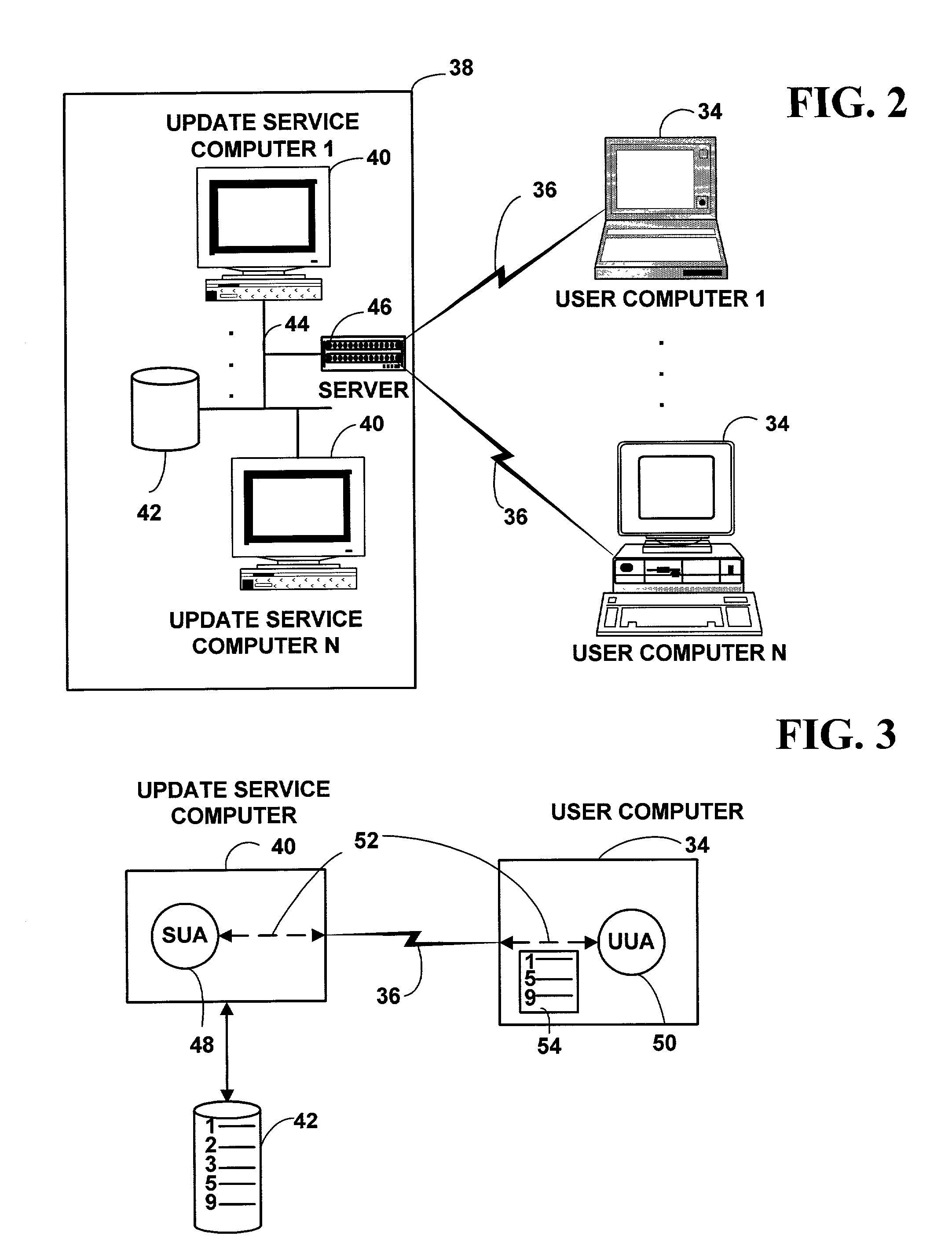
Method and system for identifying and obtaining computer software from a remote computer
InactiveUS20020016956A1Reduce morbidityLess supportingMultiple digital computer combinationsProgram loading/initiatingServices computingRemote computer
Creators of computer software provide the most up-to-date versions of their computer software on an update service. A user who has purchased computer software calls the update service on a periodic basis. The update service automatically inventories the user computer to determine what computer software may be out-of-date, and / or need maintenance updates. If so desired by the user, the update service computer automatically downloads and installs computer software to the user computer. By making periodic calls to the update service, the user always has the most up-to-date computer software immediately available. The update service may also alert the user to new products (i.e. including new help files, etc.), and new and enhanced versions of existing products, which can be purchased electronically by a user from the update service.
Owner:MICROSOFT TECH LICENSING LLC
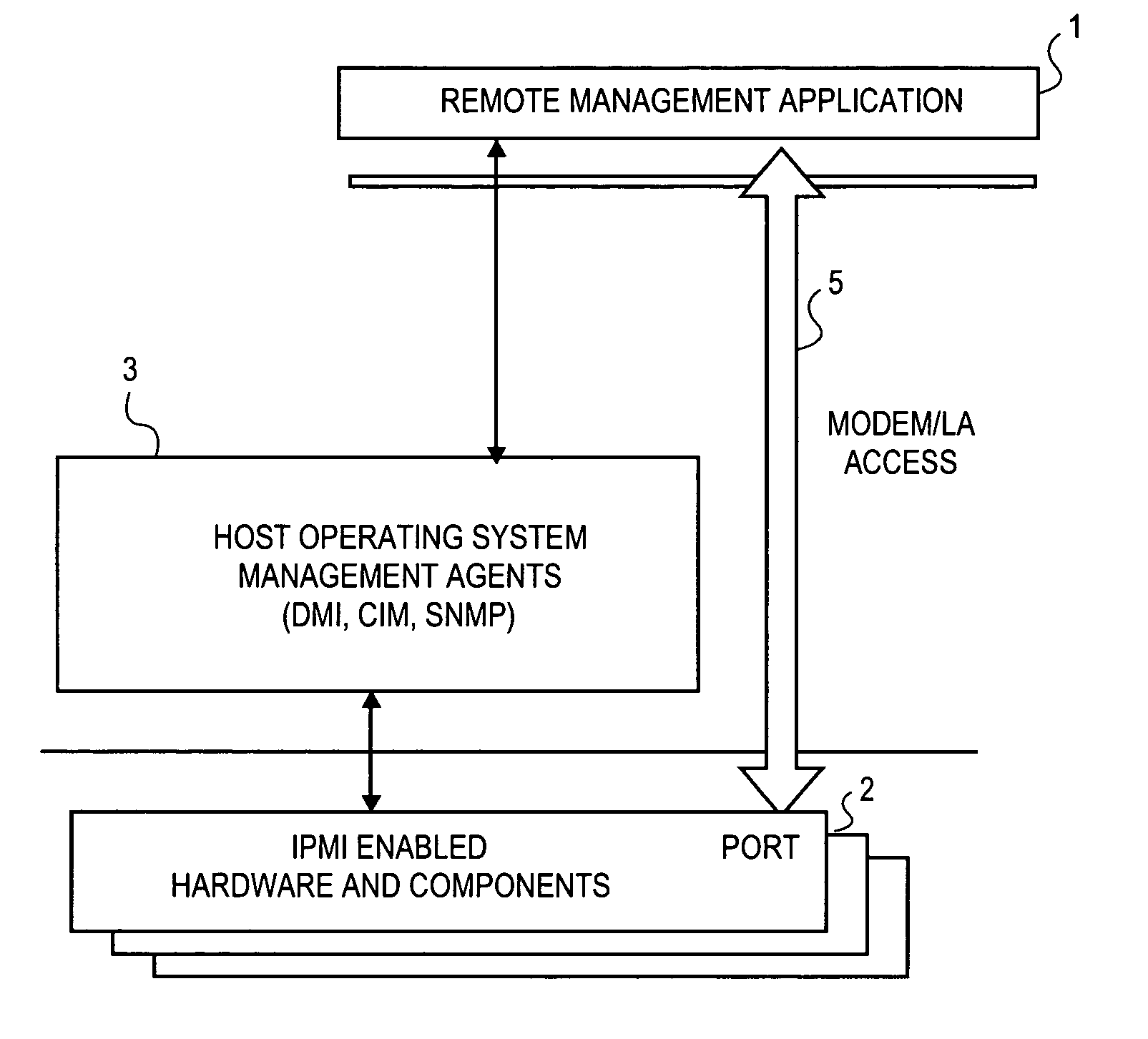
Method and apparatus for secure remote system management
InactiveUS7024695B1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareOperational system
To prevent unauthorized access to hardware management information in an out-of-band mode, i.e., when the operating system of the hardware is not executing, a method and apparatus employ an authentication protocol. Upon receiving a request for hardware component information in a service processor that is disposed in a hardware component, which request is received as an open session request and which request passes external to an operating system controlling the hardware component, the service processor transmits a challenge string to the requesting client application. In response to a challenge response received from the requesting client application, the service processor compares the challenge response to an expected response to the challenge. The expected challenge response is calculated by the service processor. Based on the result of the comparison, the service processor transmits an authentication response to the requesting client application indicating success or failure of the authentication process. On the client side, in response to a challenge string from the service processor, the requesting client application transmits to the service processor a challenge response, which includes an sequence number that increments with every new message from the requesting client application. The challenge response also includes a hash number calculated by the requesting client application, which hash number is a function of the challenge string, session identification number, sequence number and / or a password. Each new packet including data and / or commands from the client application includes a similarly calculated hash number.
Owner:INTEL CORP
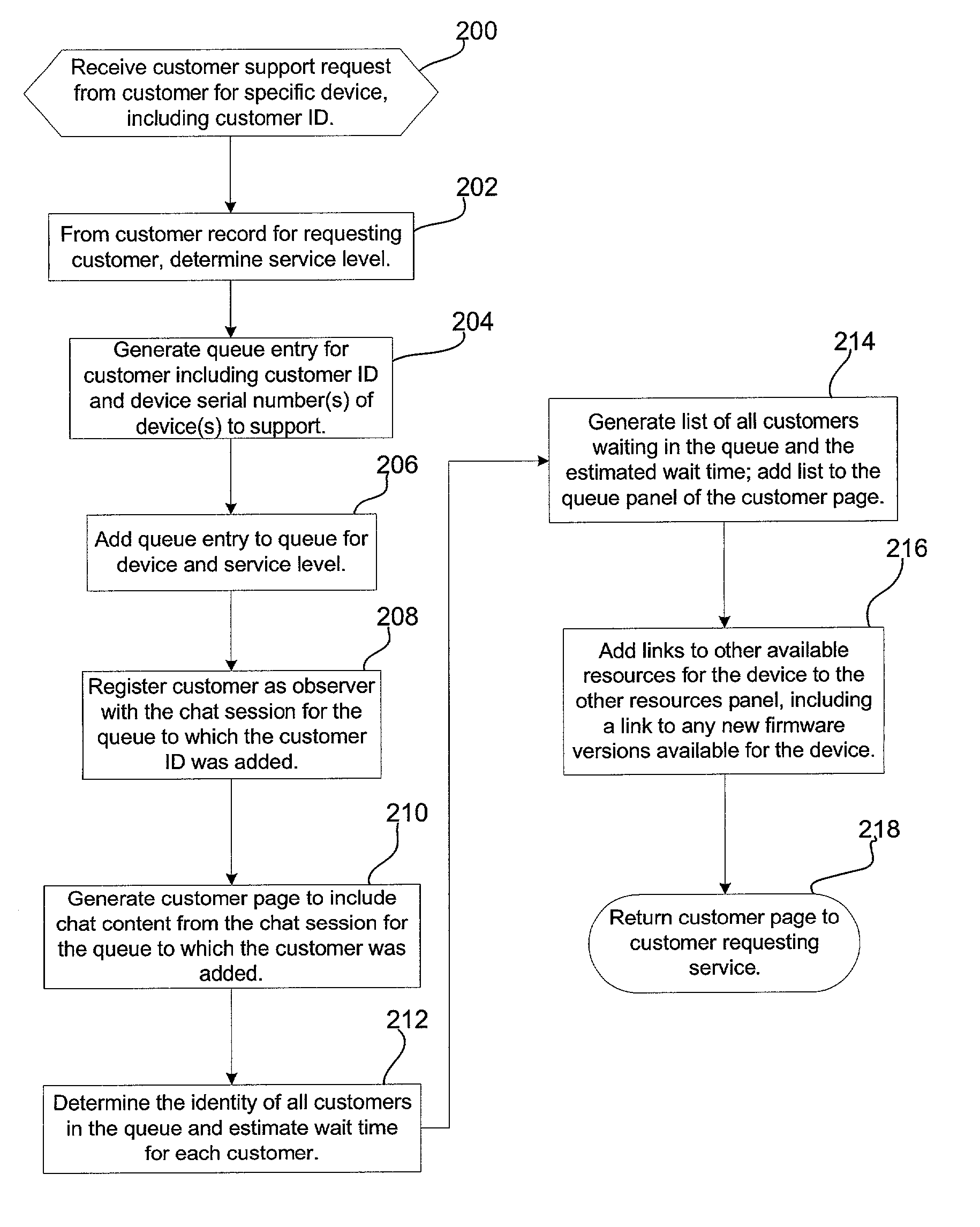
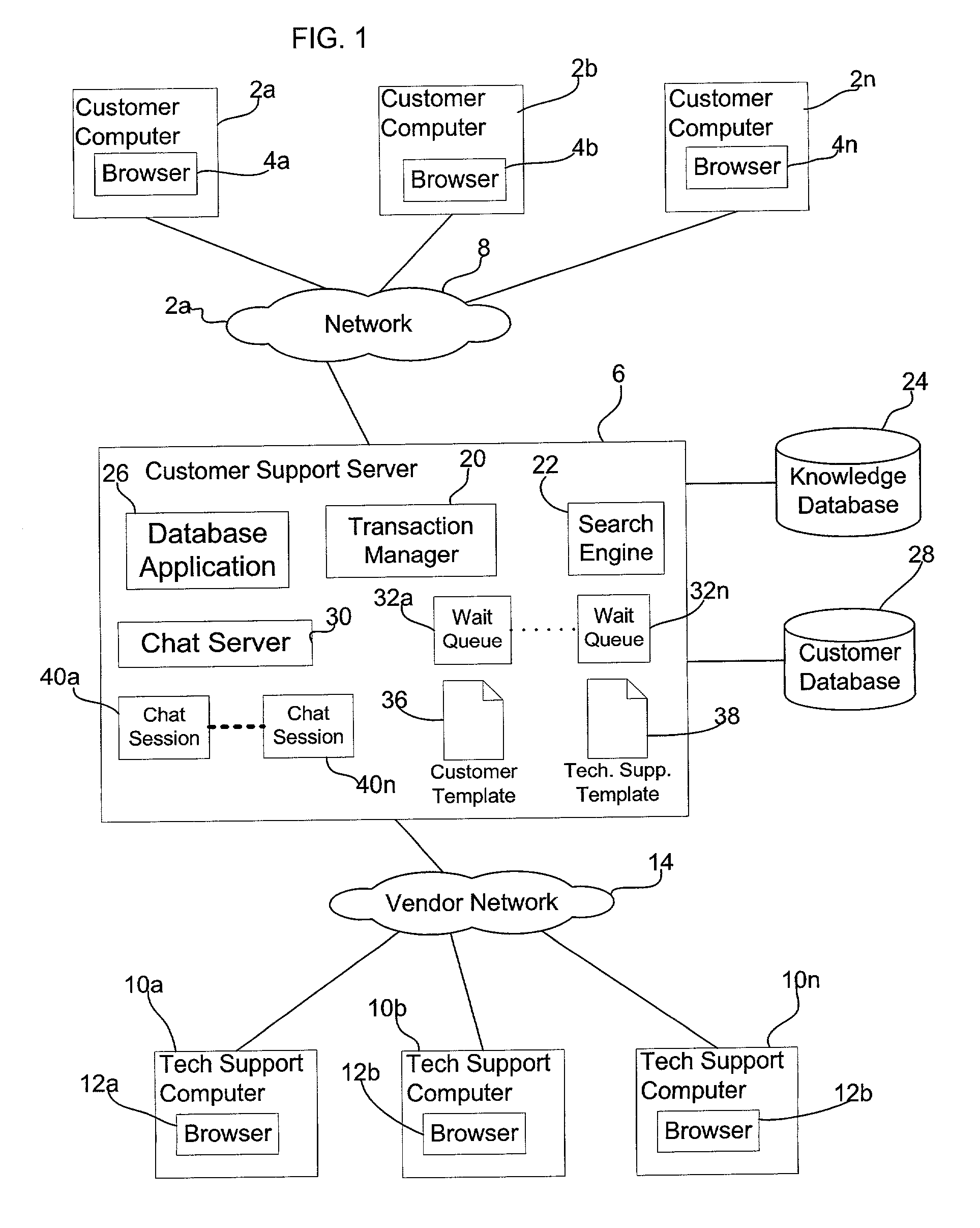
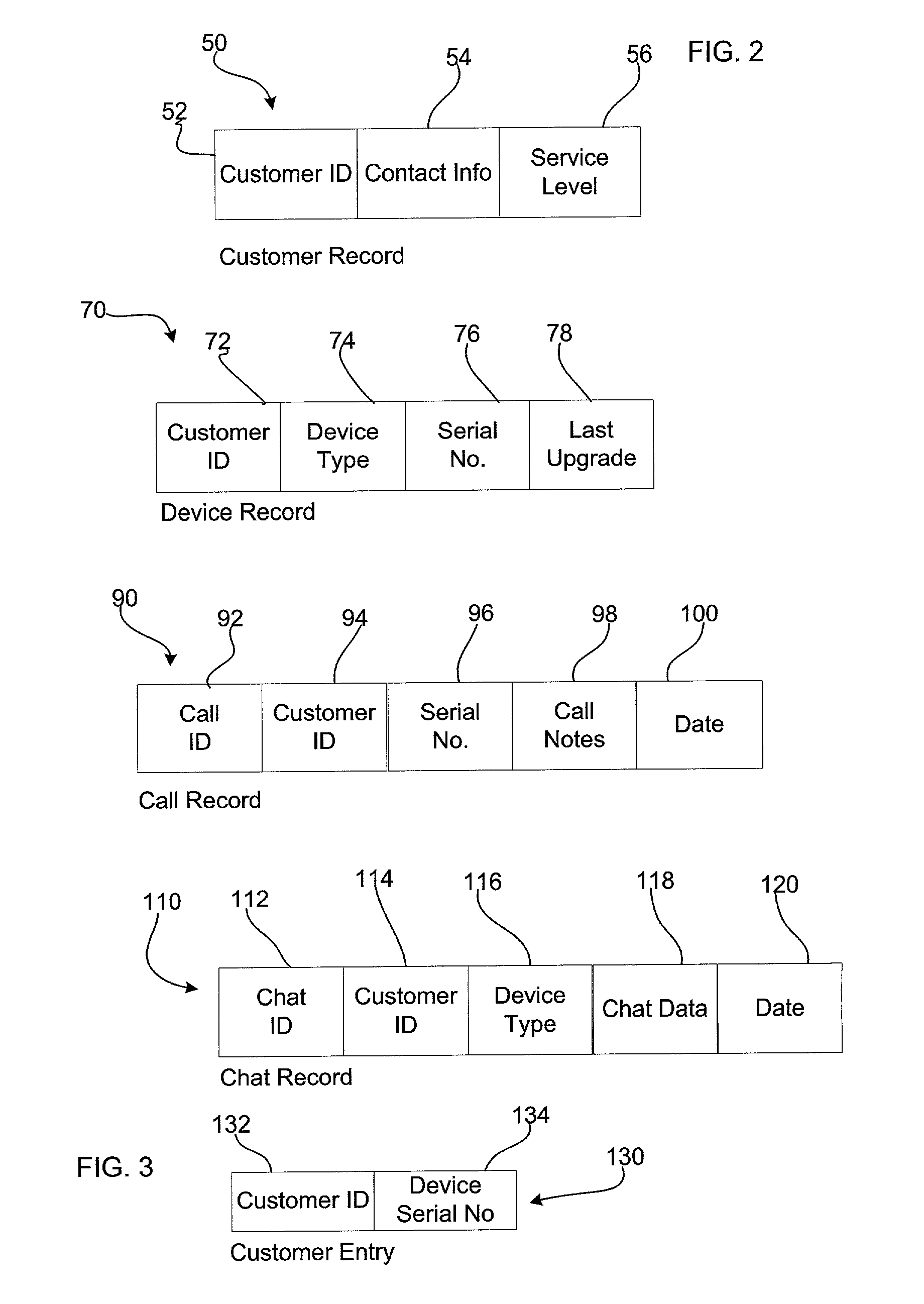
Method, system, and program for servicing customer product support requests
InactiveUS20030187672A1Better ascertainIncrease the number ofSpecial data processing applicationsMarketingServices computingDistributed computing
Provided are a method, system, and program for servicing customer requests for at least one product. At least one queue is maintained in a service computer indicating at least one customer requesting product support for the at least one product. Requests for customer service are received from customer computers used by customers over a network. Transmitted to the customer computers of customers indicated in the queue is chat session content between a technical support agent and one customer indicated in the queue.
Owner:SUN MICROSYSTEMS INC
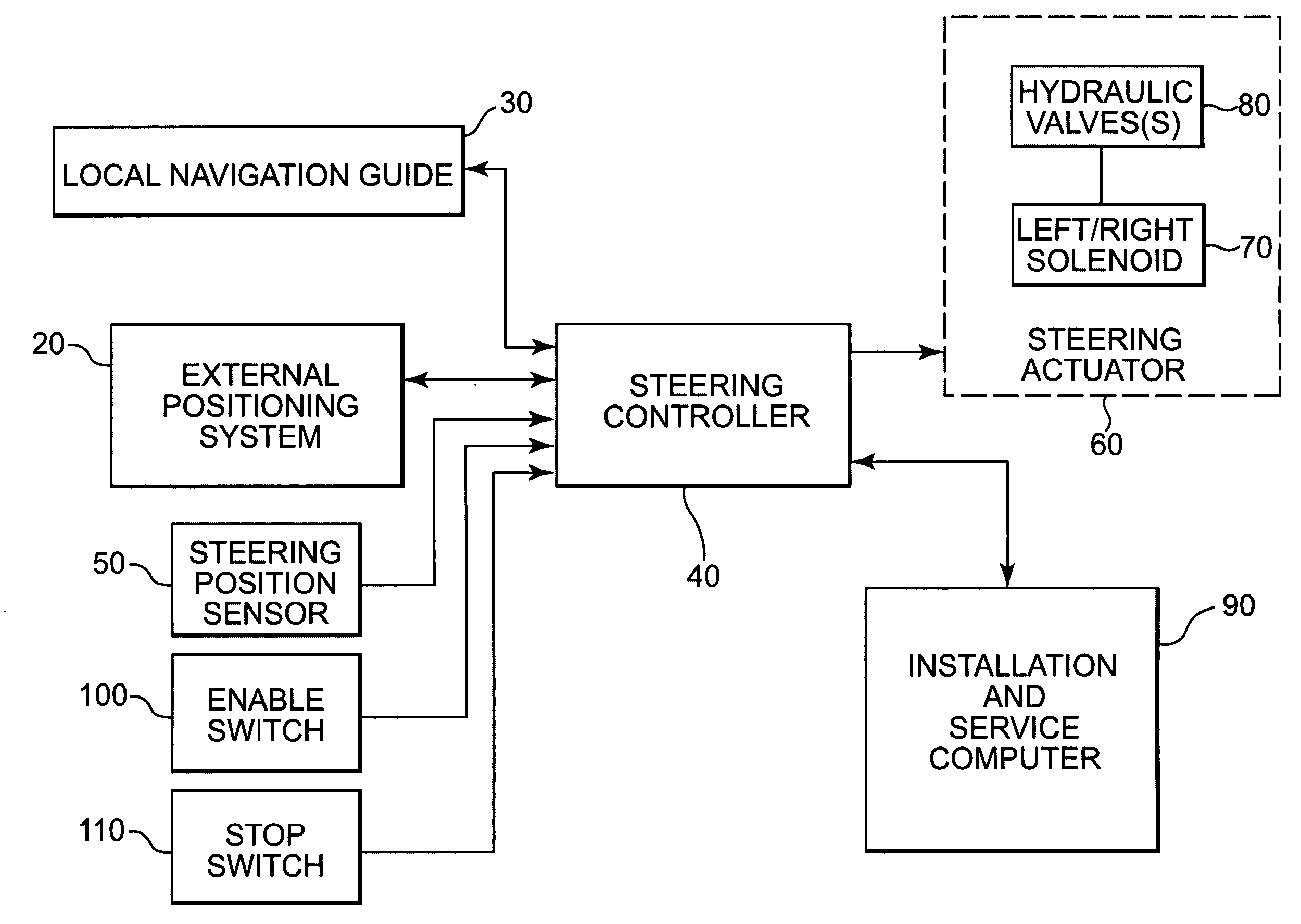
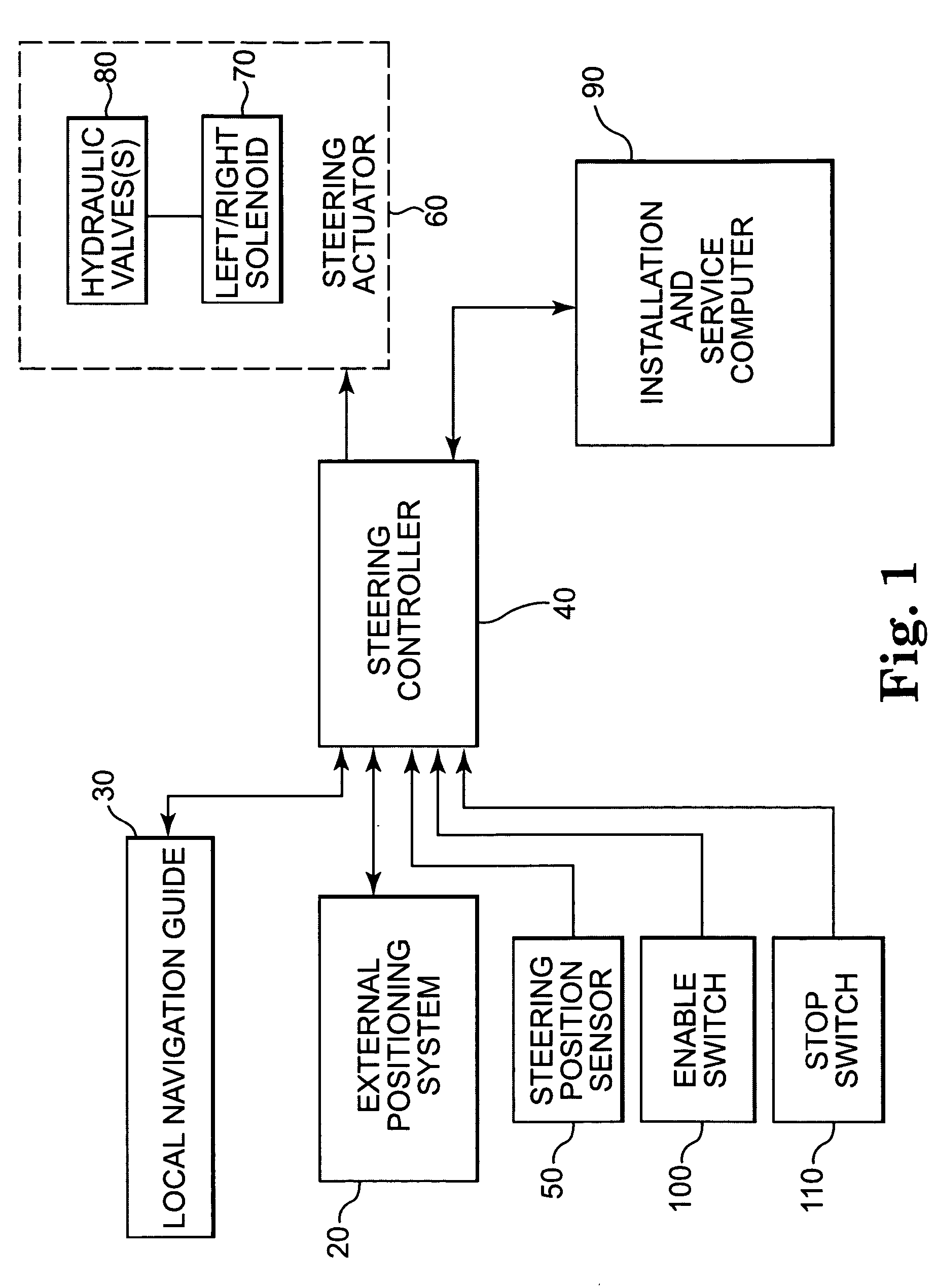
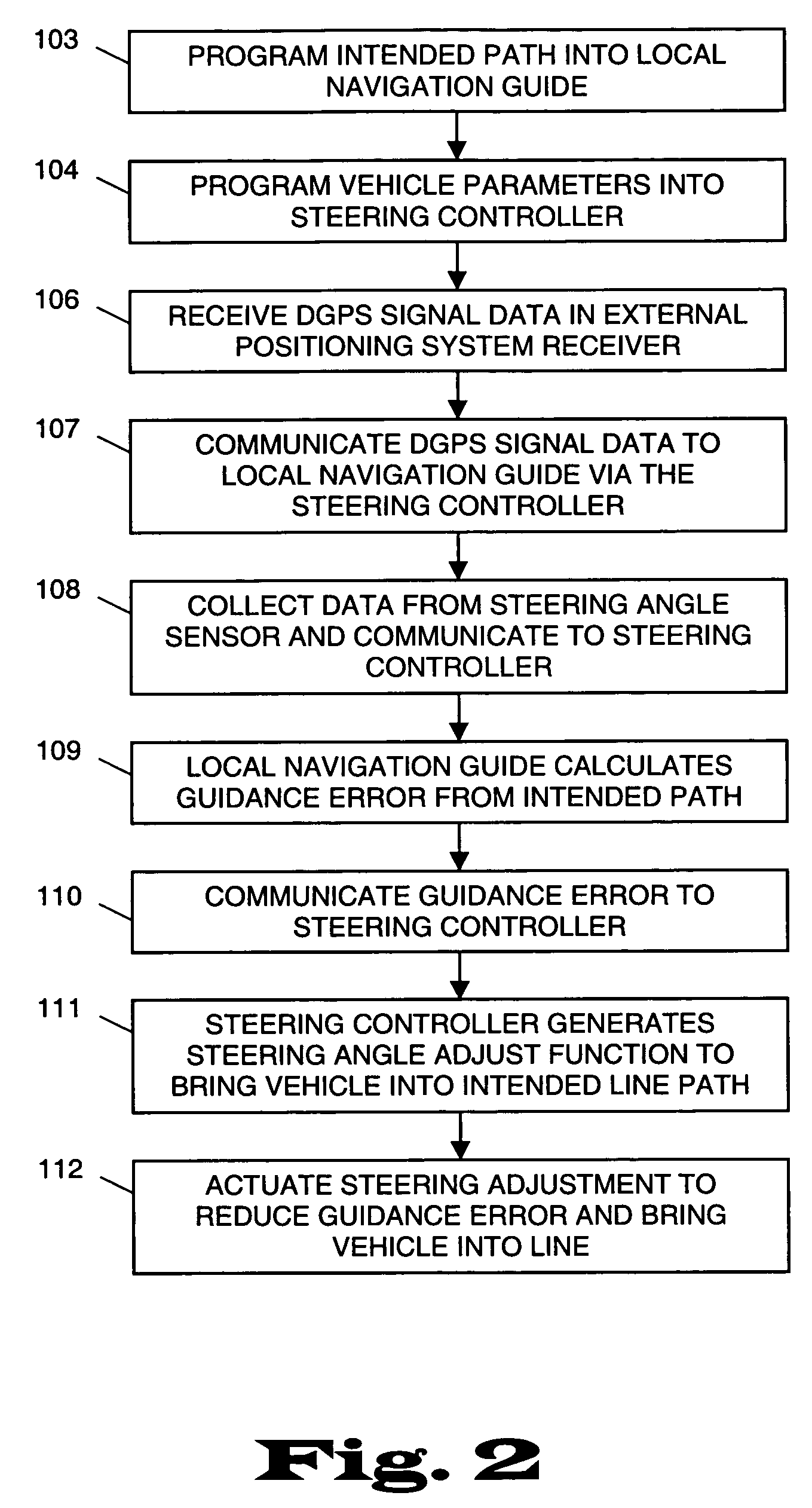
Architecturally partitioned automatic steering system and method
InactiveUS20060167600A1Delay variationMaximum performanceDigital data processing detailsAutomatic steering controlAutomatic steeringSteering angle
A system and method for automatically steering a vehicle along an intended path is provided. The system is architecturally partitioned. The partitioned design allows each of the system elements to be designed and maintained independently while allowing variation and flexibility in system configuration. An embodiment of the system elements may comprise a local navigation guidance unit, an external positioning system, a steering controller, and an installation and service computer. Additional elements of an embodiment of the system may comprise a steering position sensor, and at least one steering actuator. The system allows the operator to enter an intended target path and certain vehicle parameters. The local navigation guidance unit receives positional data from an external positioning system, preferably DGPS, indicative of a navigational path traversed by the vehicle. The guidance unit compares the positional data with the intended target path to obtain guidance error and transmits the guidance error to the steering controller. The system allows for determination of the current steering angle and generation of a steering angle adjustment based upon the intended target, the navigational path traversed by the vehicle, the vehicle parameters, the steering angle and the guidance error. The steering angle adjustment is used to actuate a steering mechanism to smoothly guide the vehicle along the intended target path.
Owner:RAVEN INDUSTRIES INC
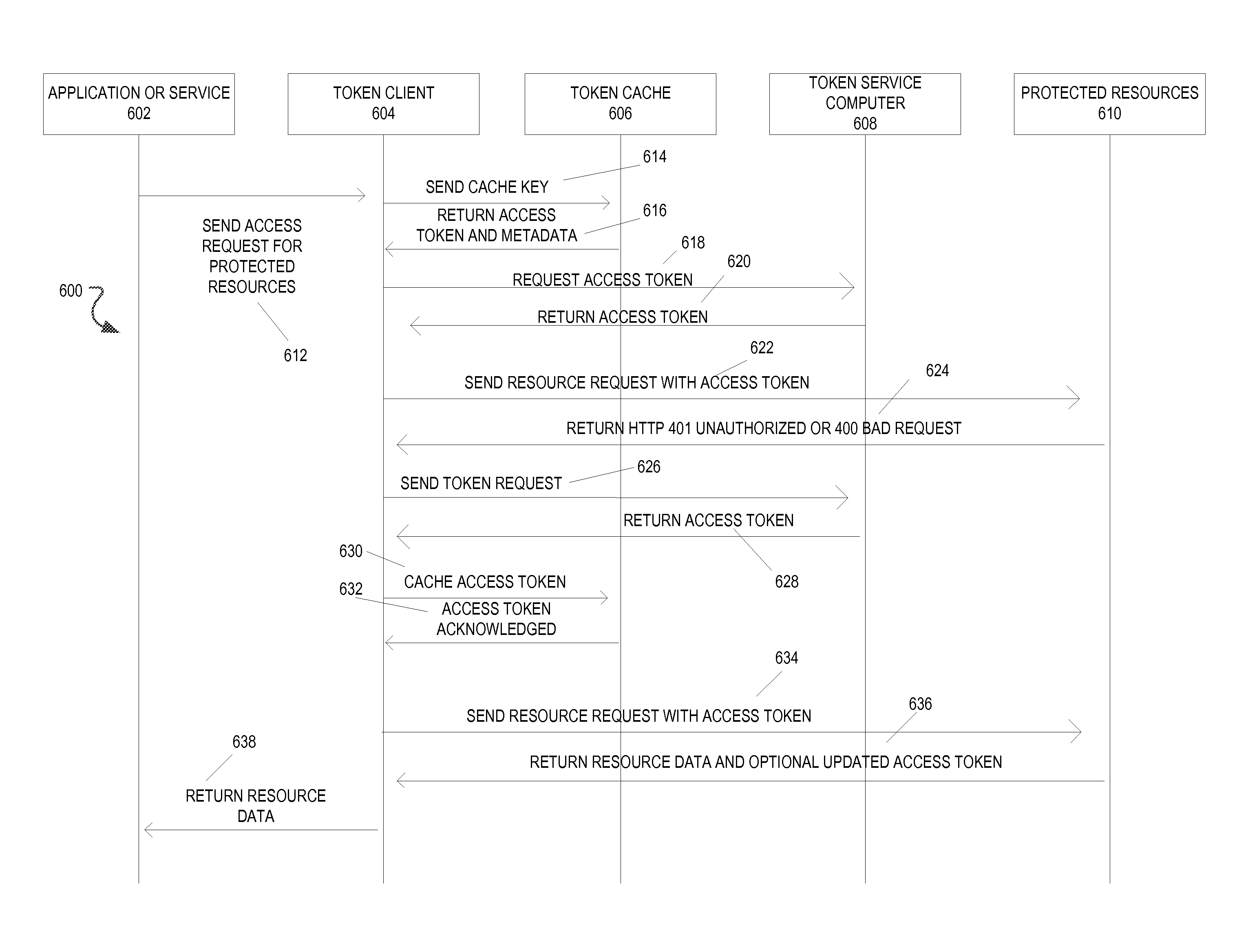
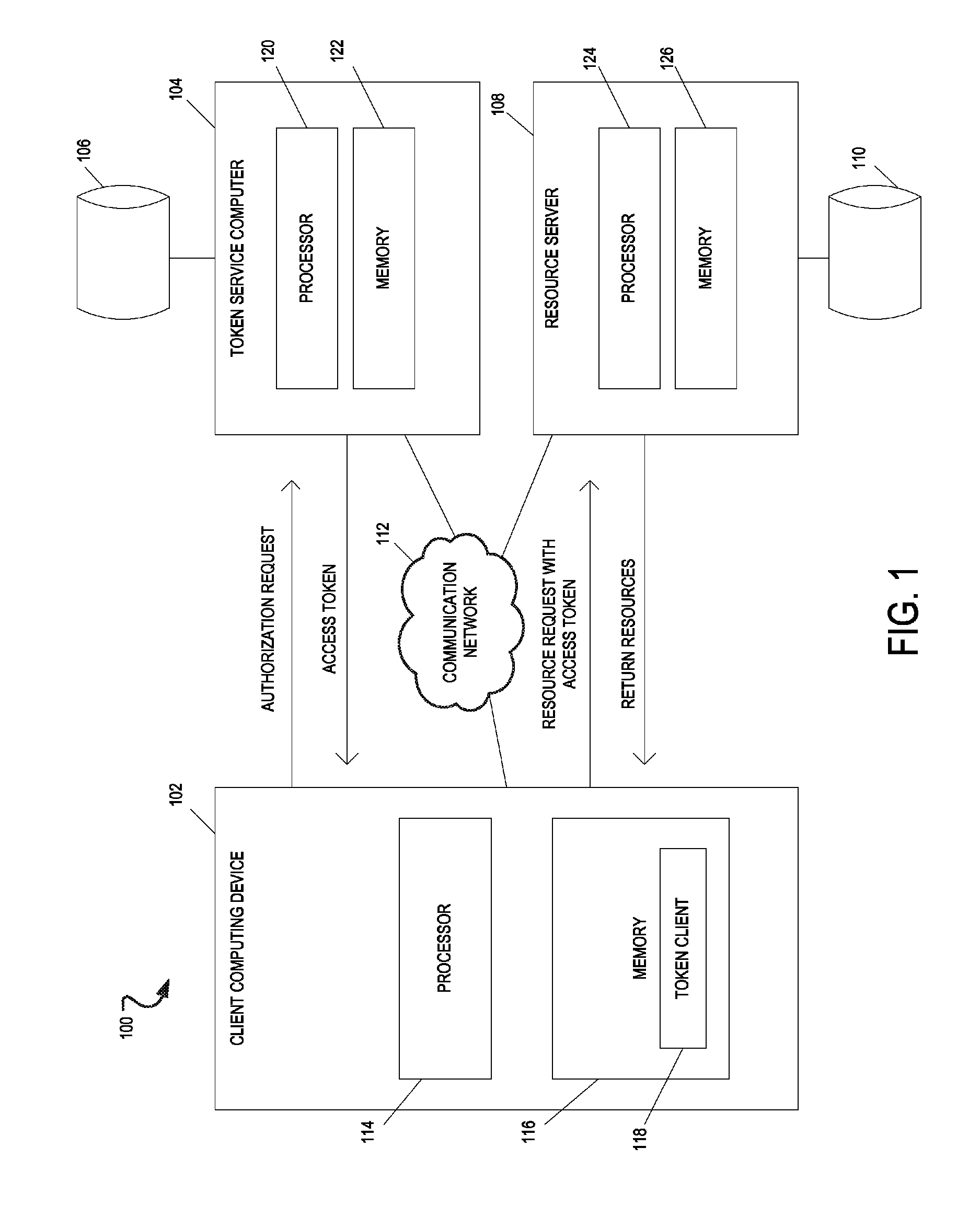
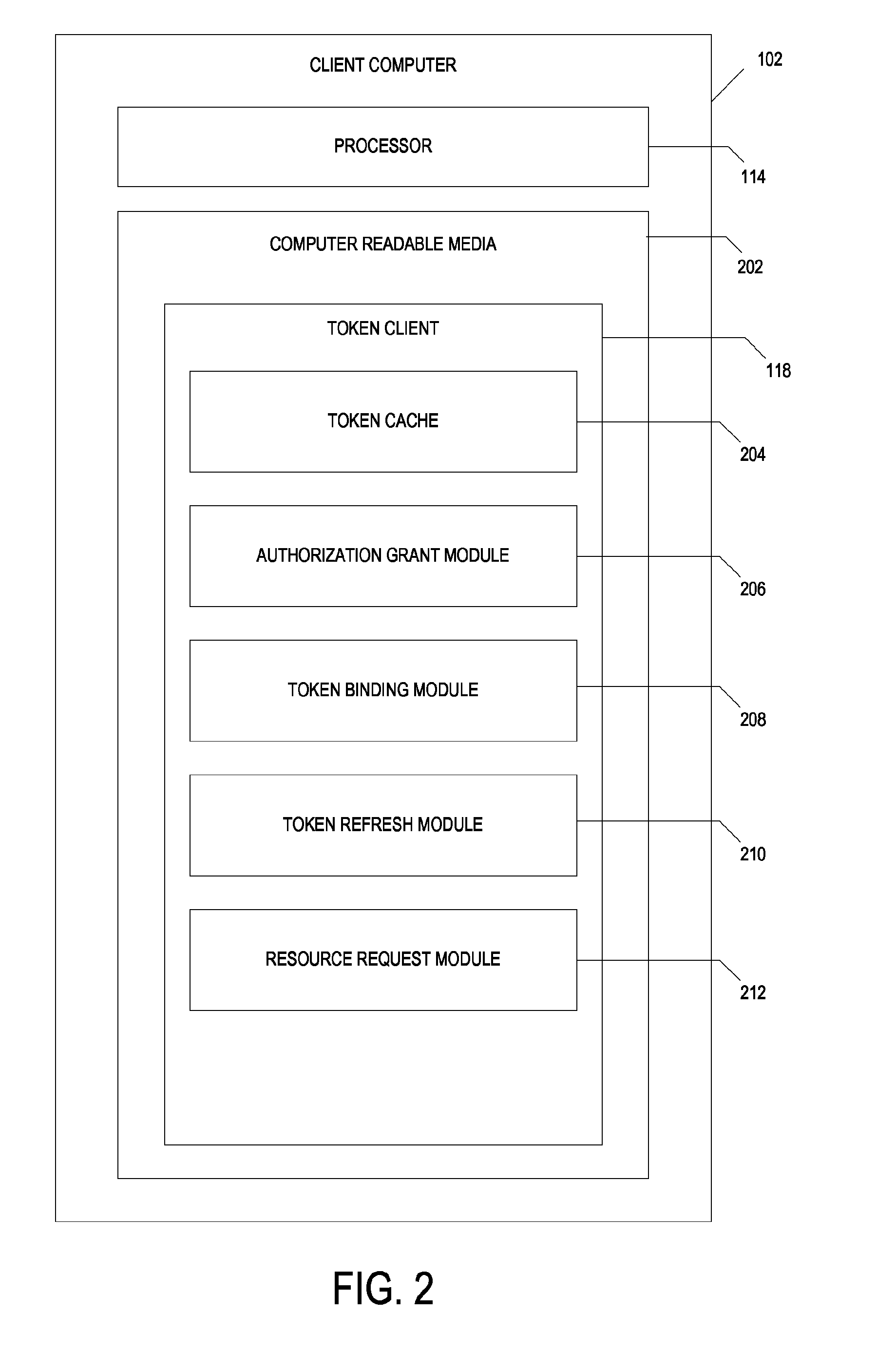
Authorization token cache system and method
A system includes one or more processors to request access tokens from a token service computer, cache the access tokens and related information in a token cache, transmit the access tokens with a resource request to a resource server, and receive requested resources in response to the resource request. The resource server transmits representations of requested resources to computing devices having valid tokens. The access tokens and related information including credentials information and token metadata are stored in the token cache.
Owner:ORACLE INT CORP
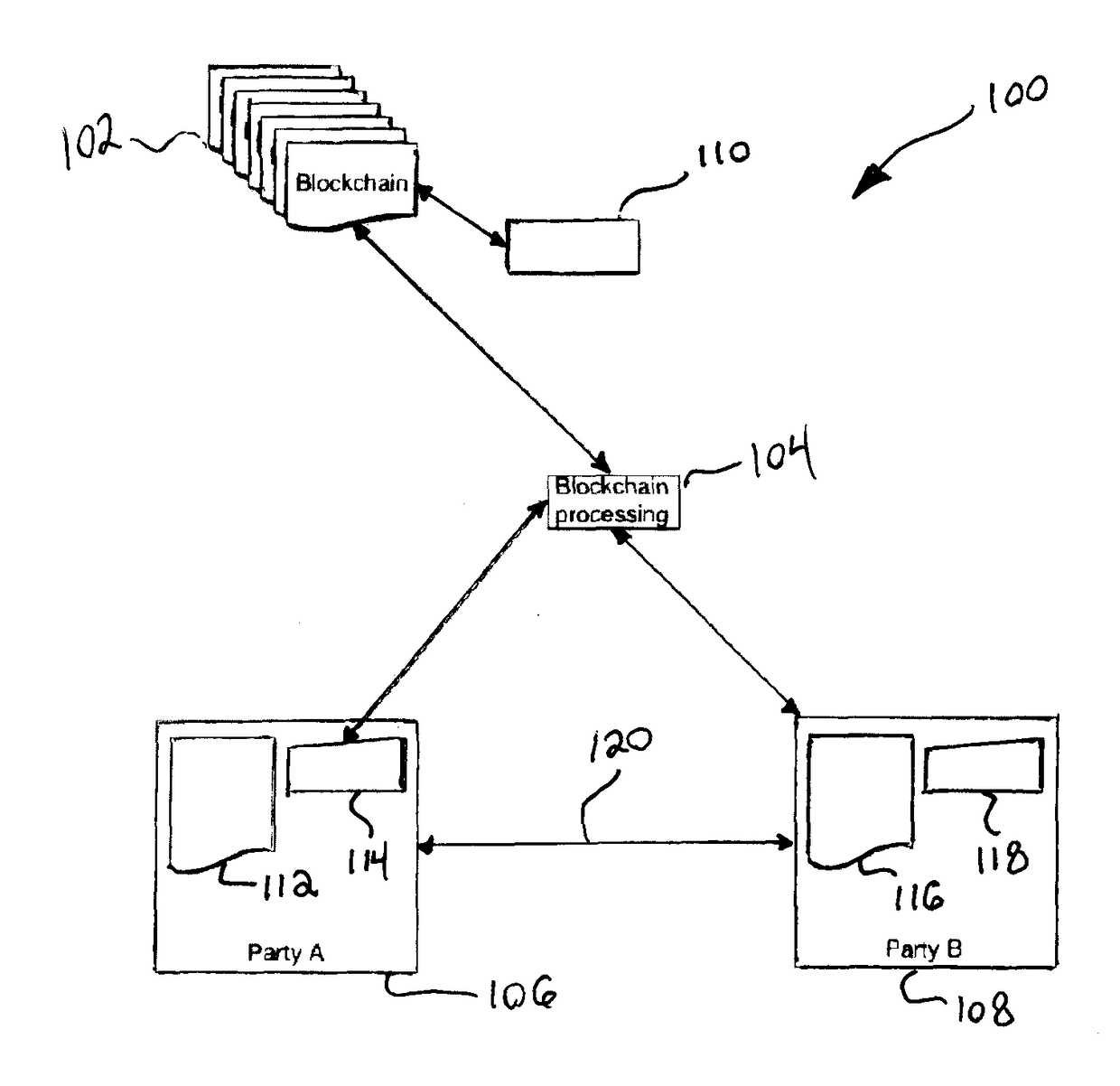
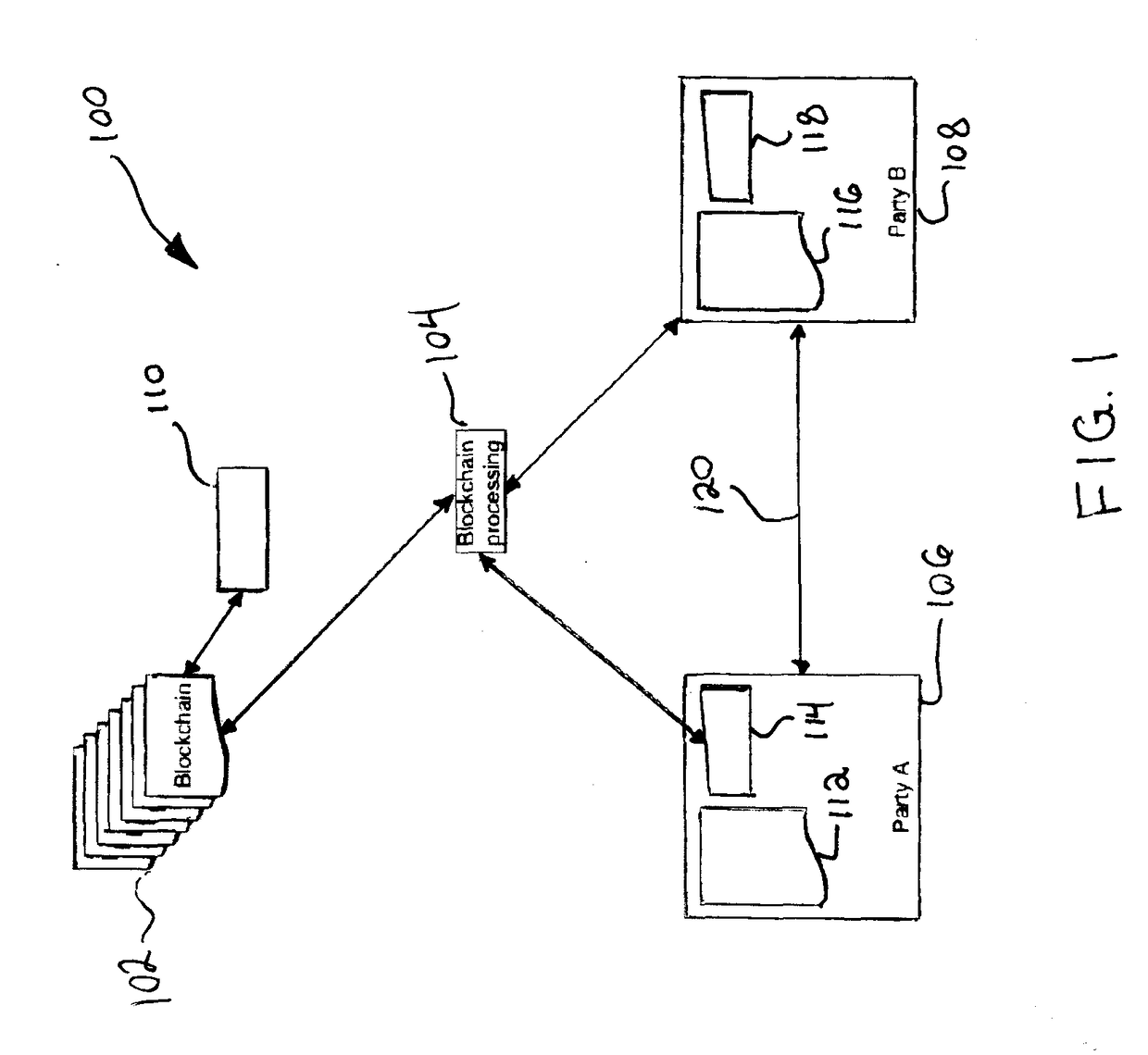
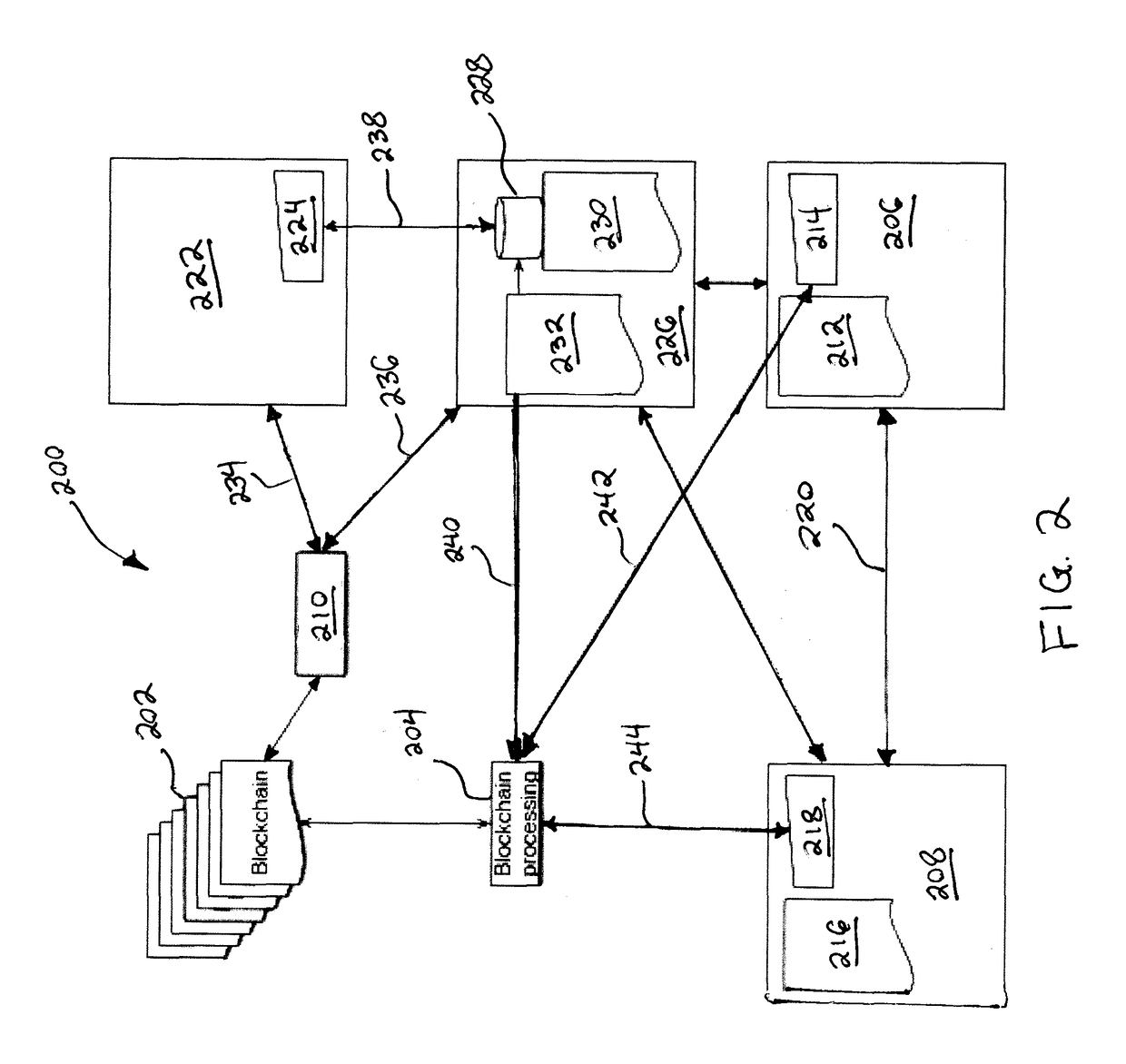
Blockchaining systems and methods for frictionless media
An ecosystem for distributing digital content over an electronic communications network includes a content creator computer system having a processor and a memory configured to store raw digital content. The system further includes computer systems for content service and for a retailer, both in operable communication with the processor. The content service computer system is configured to receive the raw digital content and transmit packaged digital content. The retailer computer system is configured to receive the packaged digital content and display its availability to an electronic device of a user. The ecosystem further includes a blockchain in operable communication with the processor, and the content service and retailer computer systems. The blockchain is configured to verify a transfer of the packaged digital content from the content service system to the user, a payment from the user to the retailer, and an update with information regarding the verified transfer and payment.
Owner:CABLE TELEVISION LAB
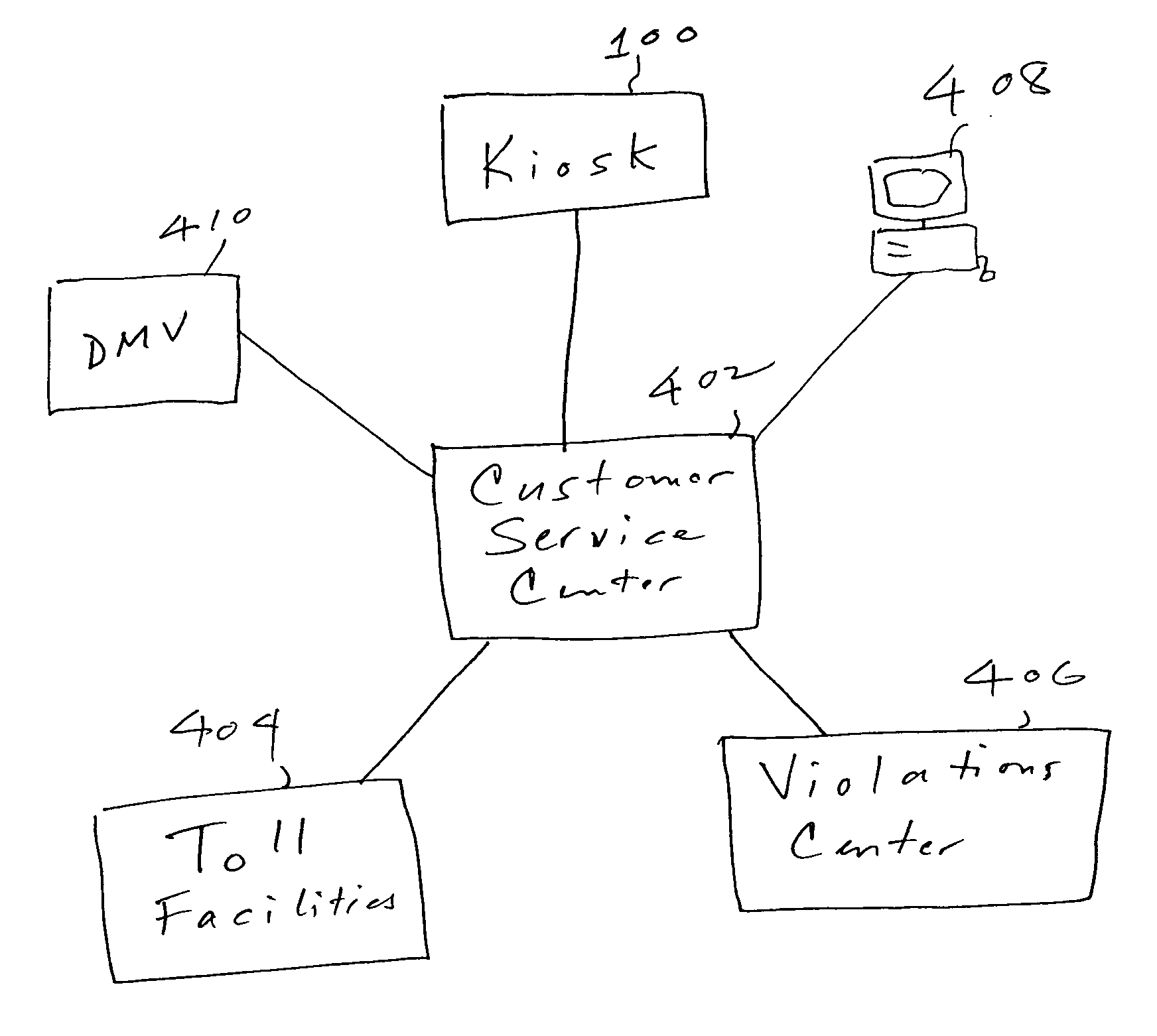
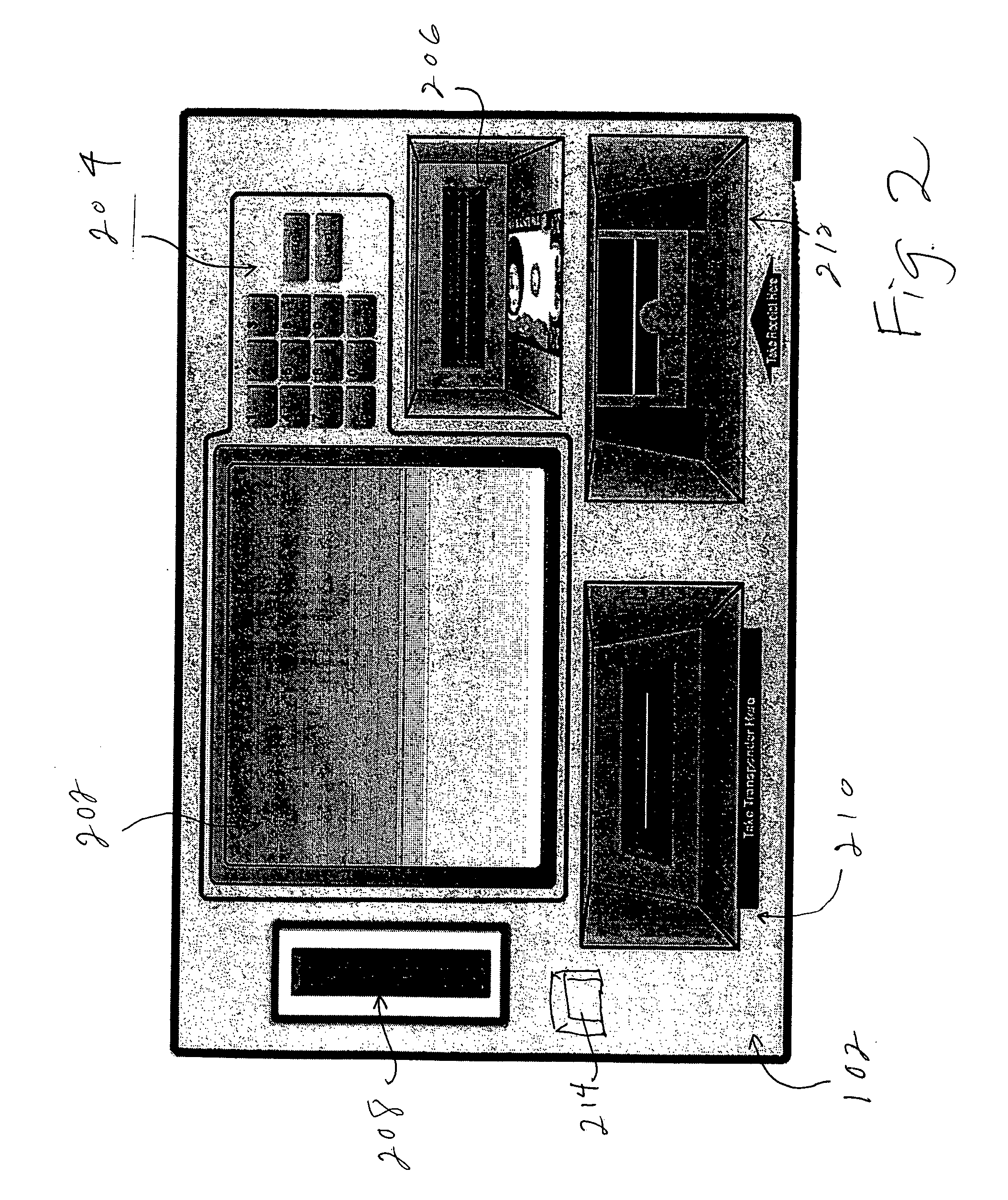
Self-service electronic toll collection unit and system
ActiveUS20050010478A1Efficient formReduce their current operating costTicket-issuing apparatusCredit registering devices actuationServices computingEngineering
A self-service vending unit allows a potential user of a toll transponder to buy the transponder without having to visit a customer-service facility. The vending unit automatically accepts payment, such as cash or a credit or debit card, and issues the transponder with a paid value. The vending unit communicates with a customer-service computer through a TCP / IP connection and allows the user to top off the value on the transponder and otherwise to manage the account.
Owner:AMTECH SYST
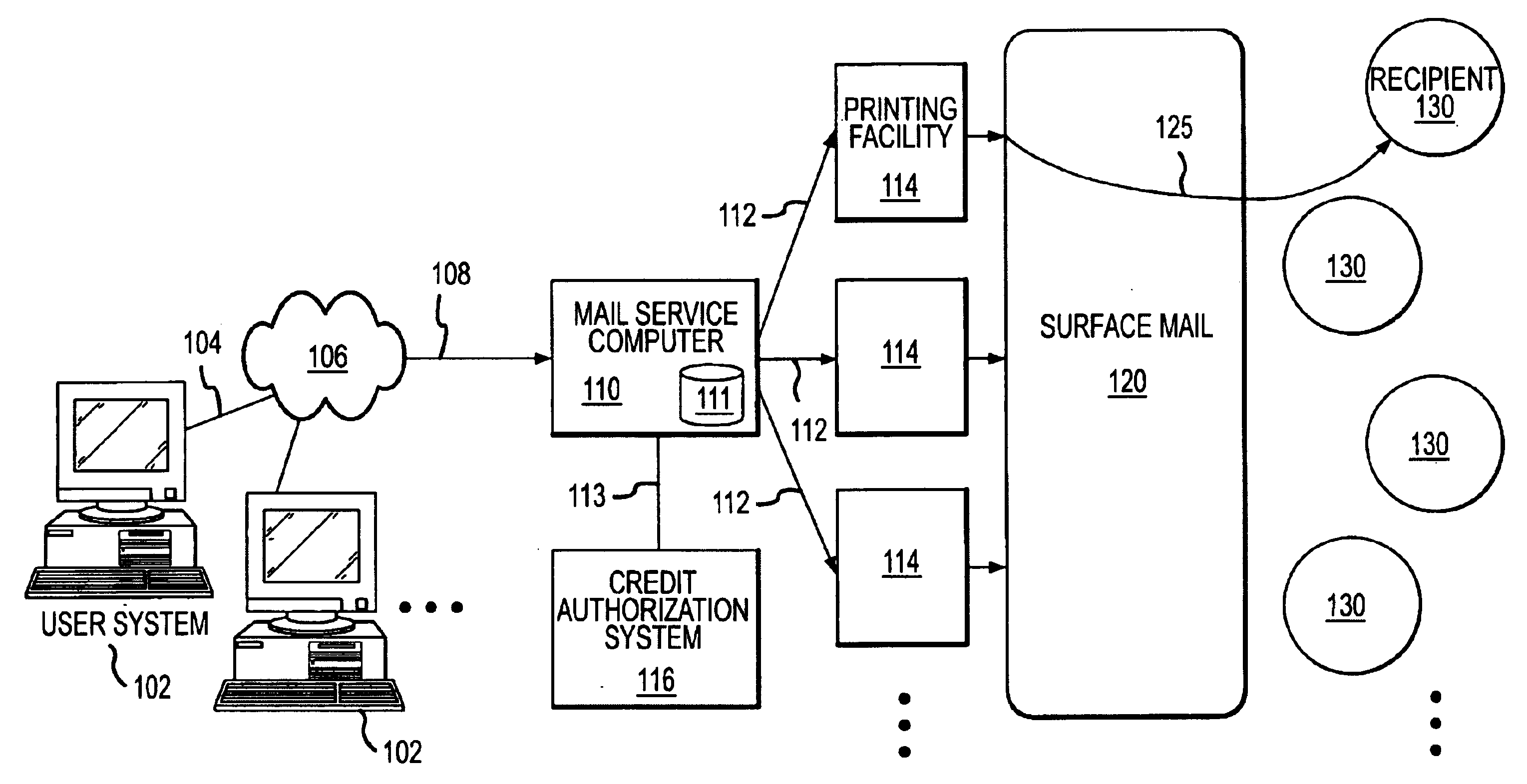
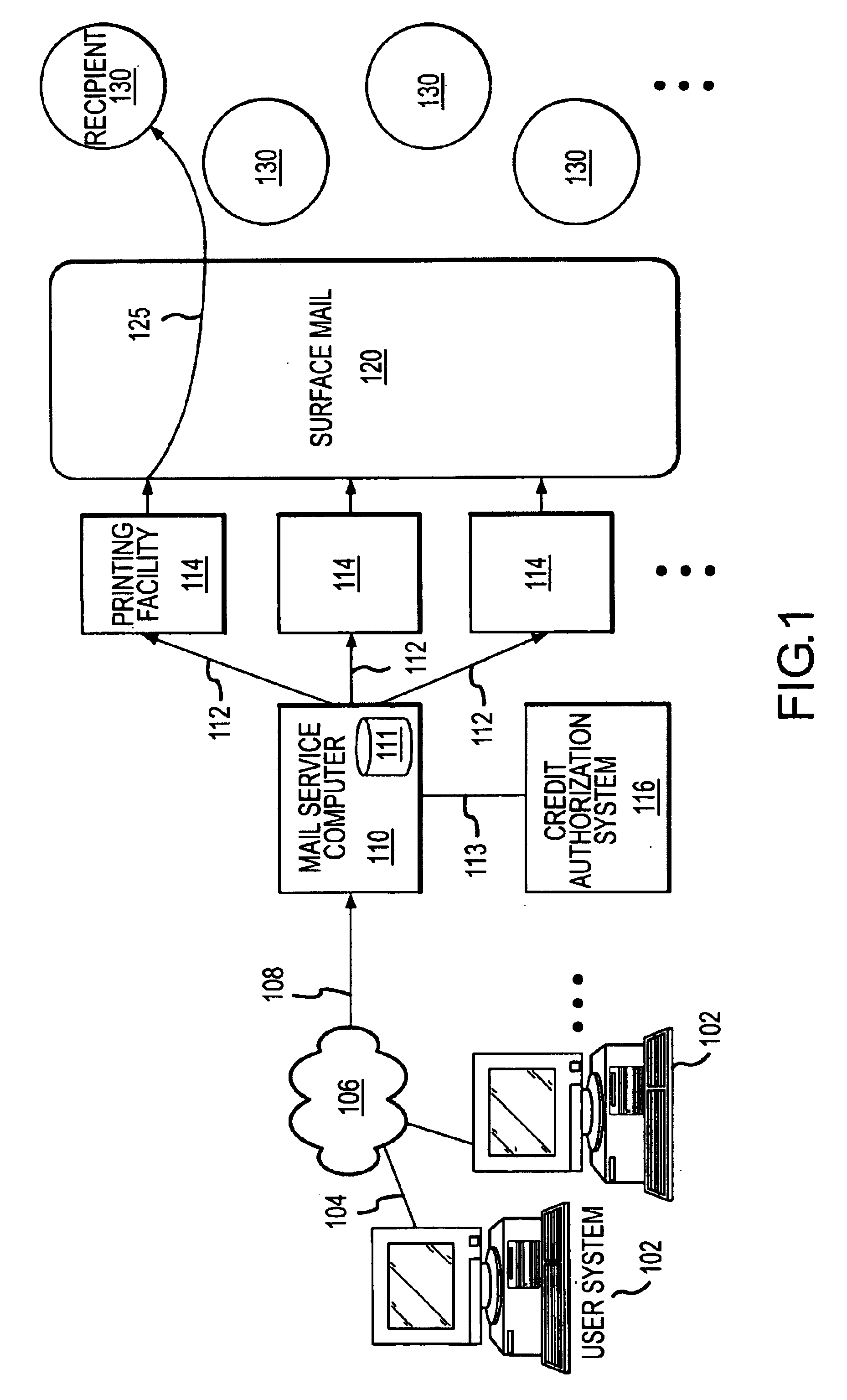
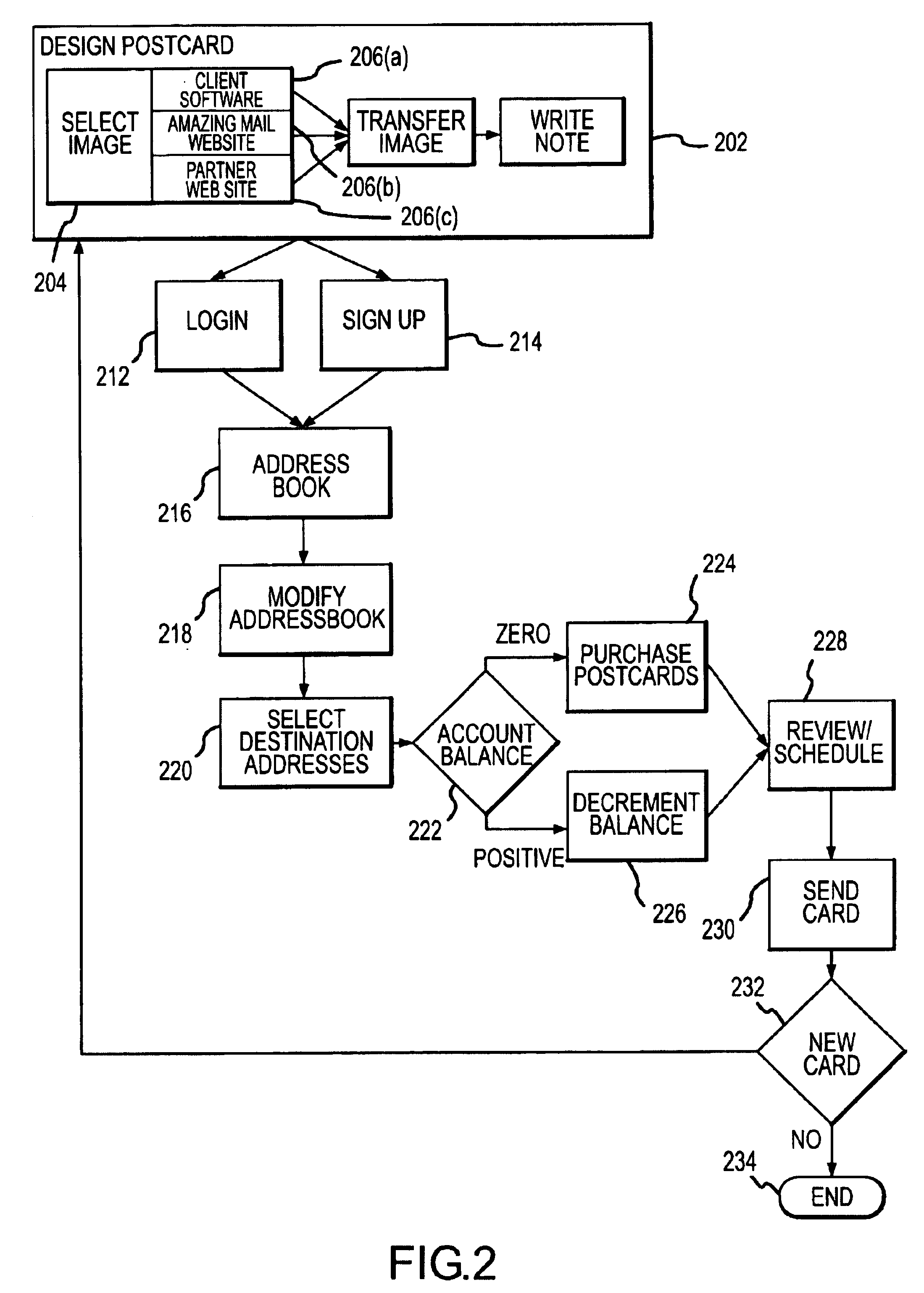
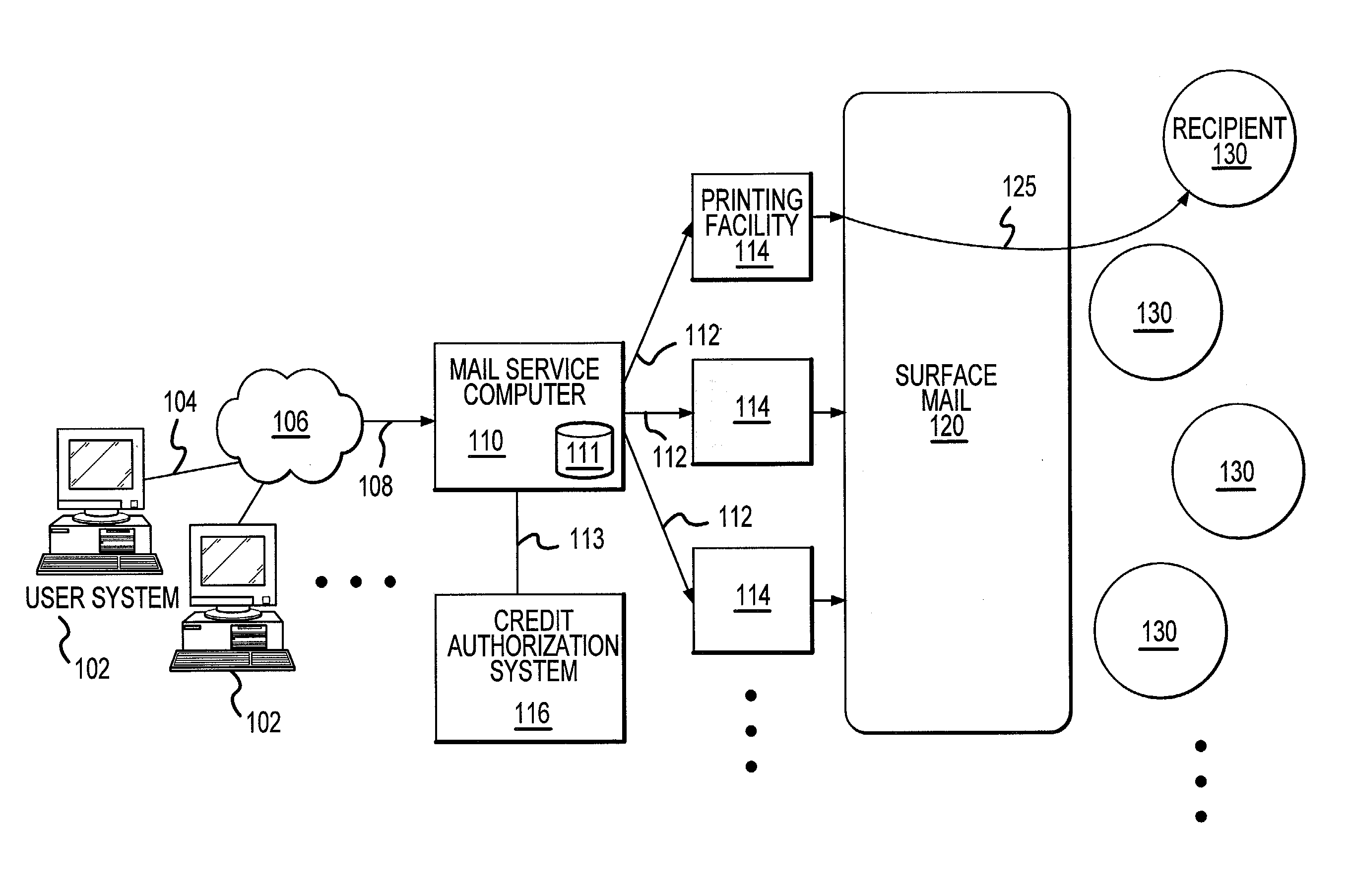
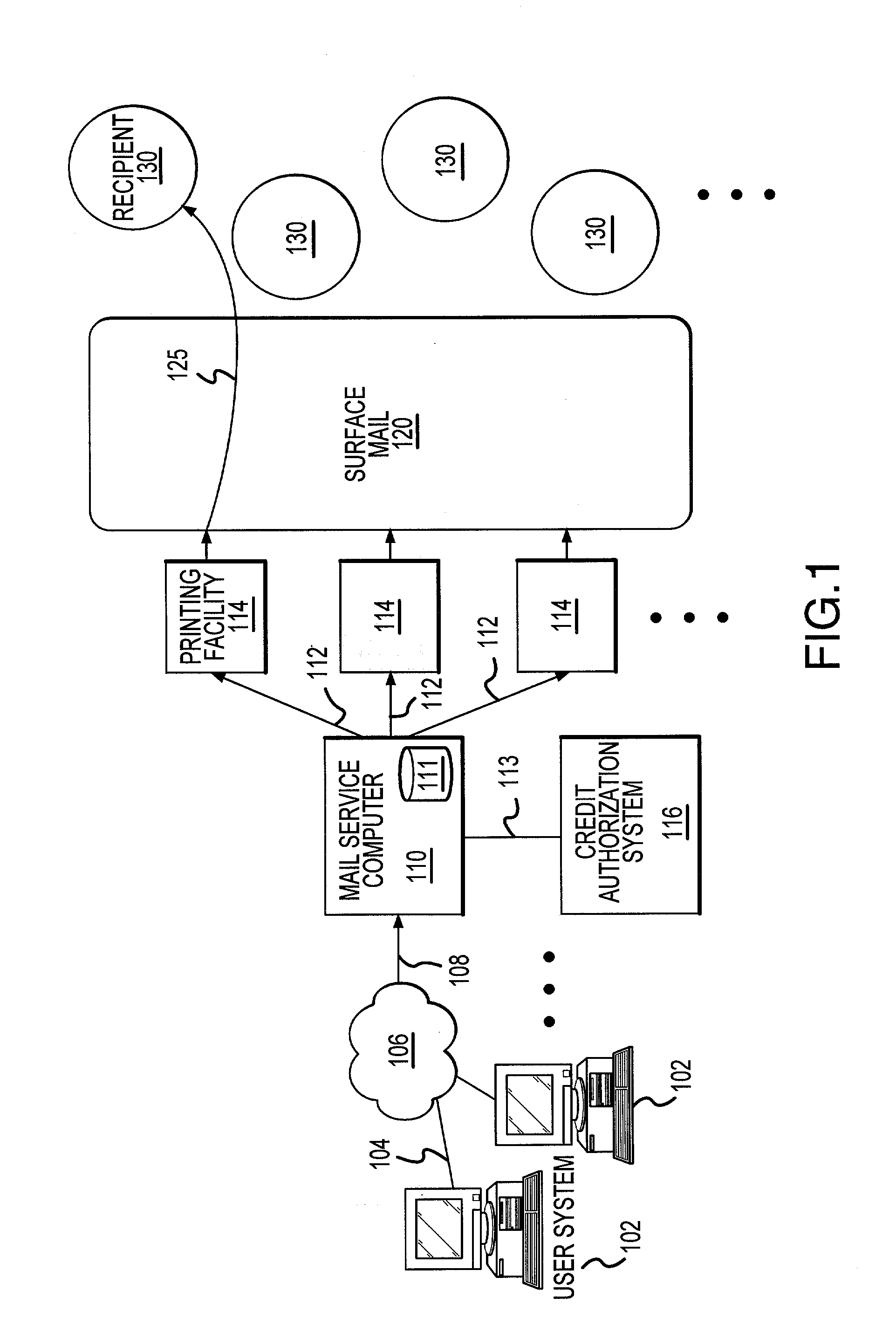
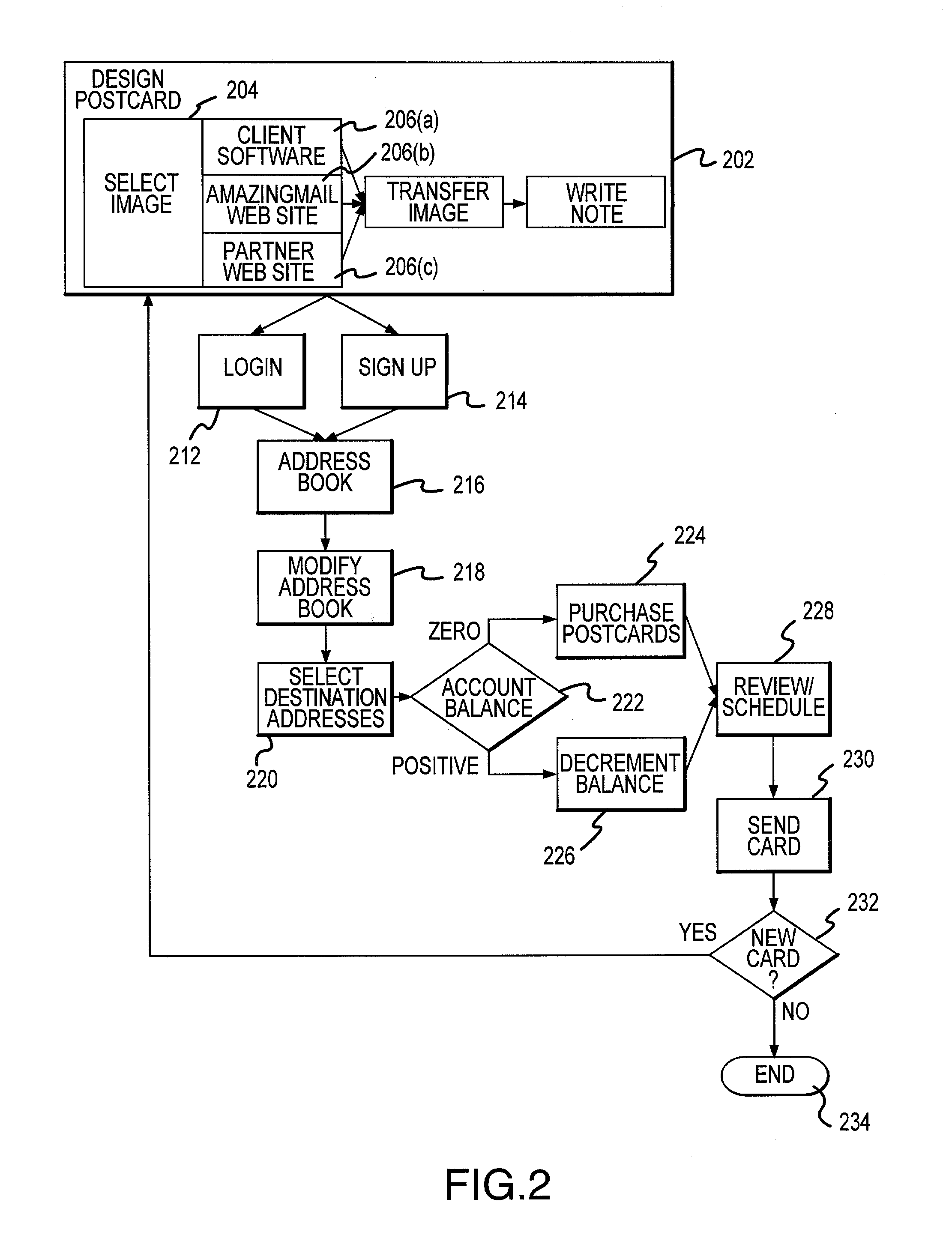
Methods and apparatus for generation and distribution of surface mail objects
A method for generating and distributing mail items includes creating a first and a second mail file, wherein each of the first and second mail files includes recipient address information, and wherein the first mail file is generated by a first user, and the second mail file is generated by a second user. The first and second mail files are then transmitted to a mail service computer over a global computer network and printed, on a single sheet of media, a first mail item in accordance with the first mail file, and a second mail item in accordance with the second mail file. The first and second mail items are then placed into a surface mail system. The first mail item is addressed in accordance with the first recipient address information, and the second mail item is addressed in accordance with the second recipient address information. The mail item is then placed into the surface mail system in such a way as to minimize handling damage, and to leverage available postal technology. The mail items are then delivered to the postal addresses of the intended recipients.
Owner:AMAZINGMAIL COM
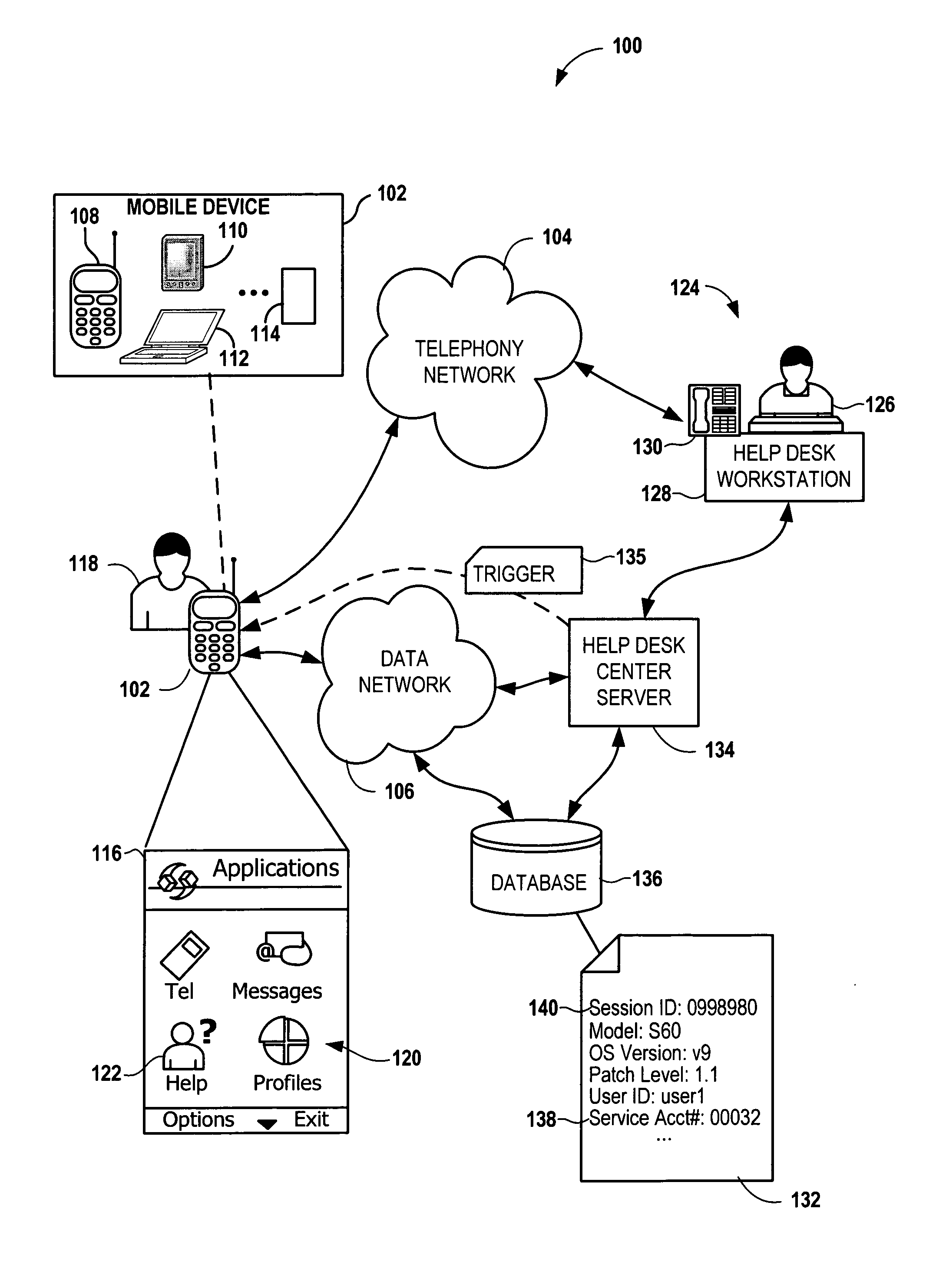
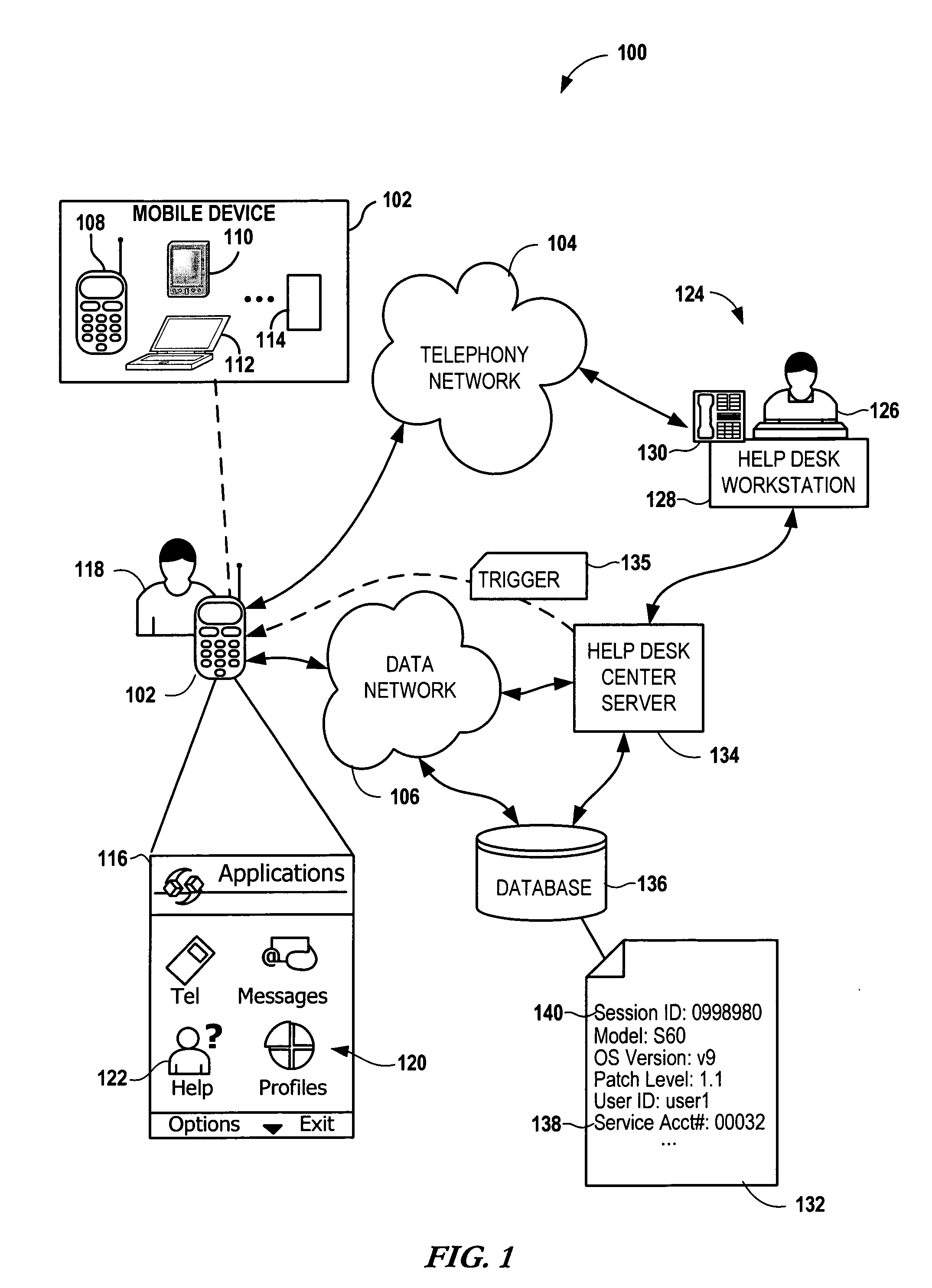
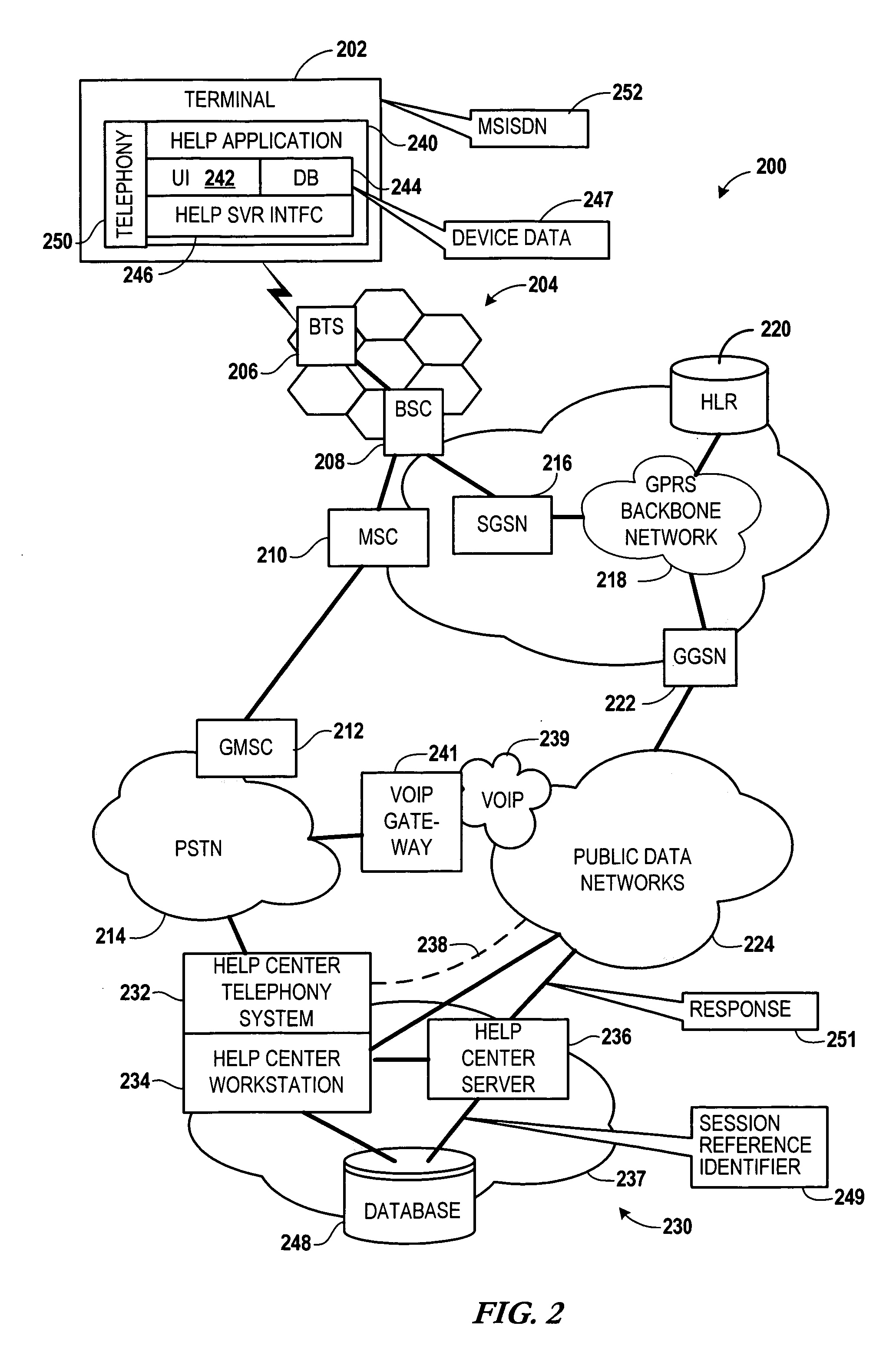
Help desk connect
InactiveUS20060229054A1Easy accessSpecial service for subscribersSubstation equipmentServices computingMobile device
Providing assistance to a user of a mobile device involves sending a signal from the mobile device to a help service computing arrangement via a network to initiate a help session. Device-specific data of the mobile device is sent via the network and targeted for a help database. A session identifier is associated with the device-specific data via the help service computing arrangement. A voice connection between the user and a help agent is established and the session identifier is provided to the help agent. The device-specific data is accessed by the help agent from the help database using the session identifier for purposes of providing the assistance.
Owner:NOKIA CORP
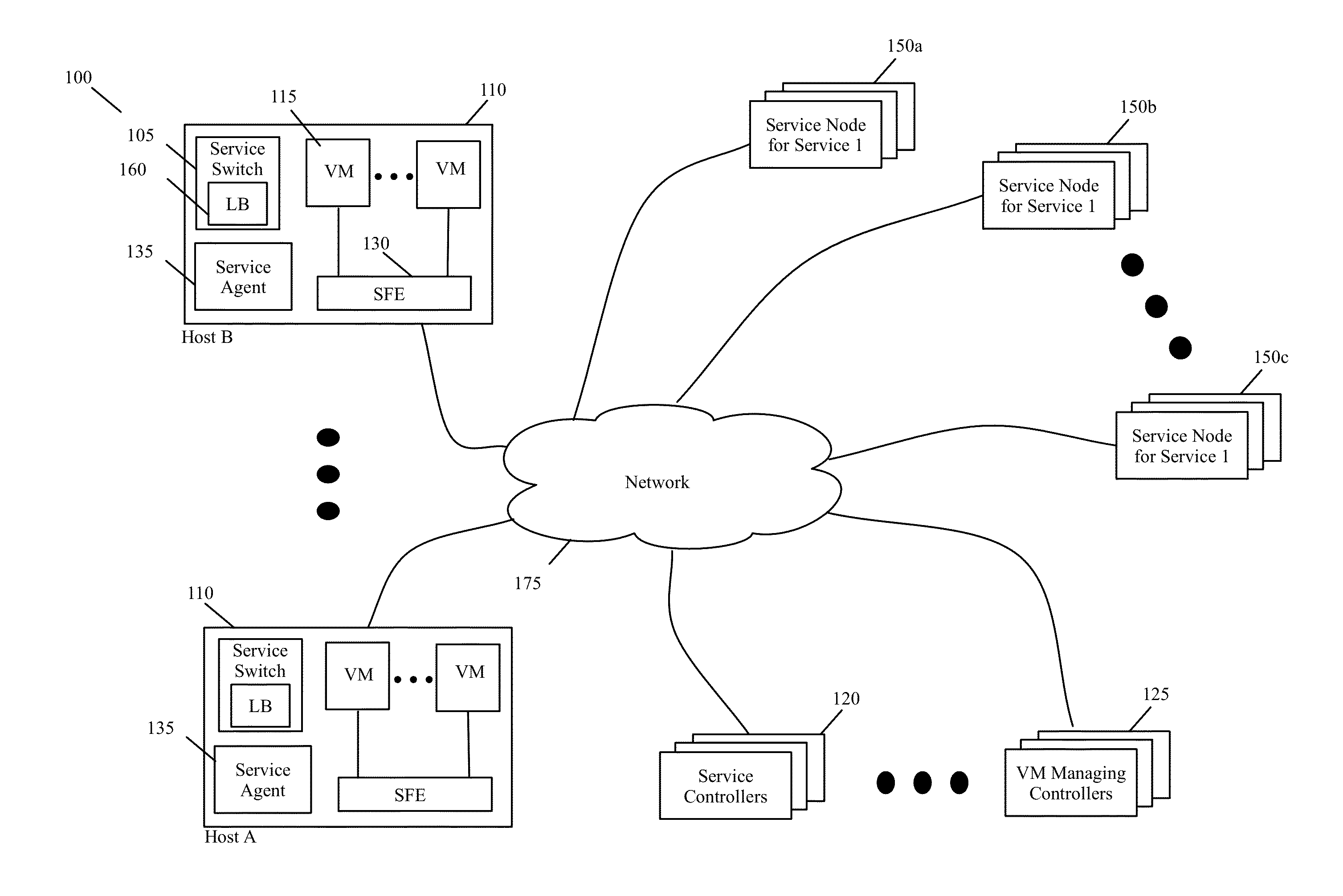
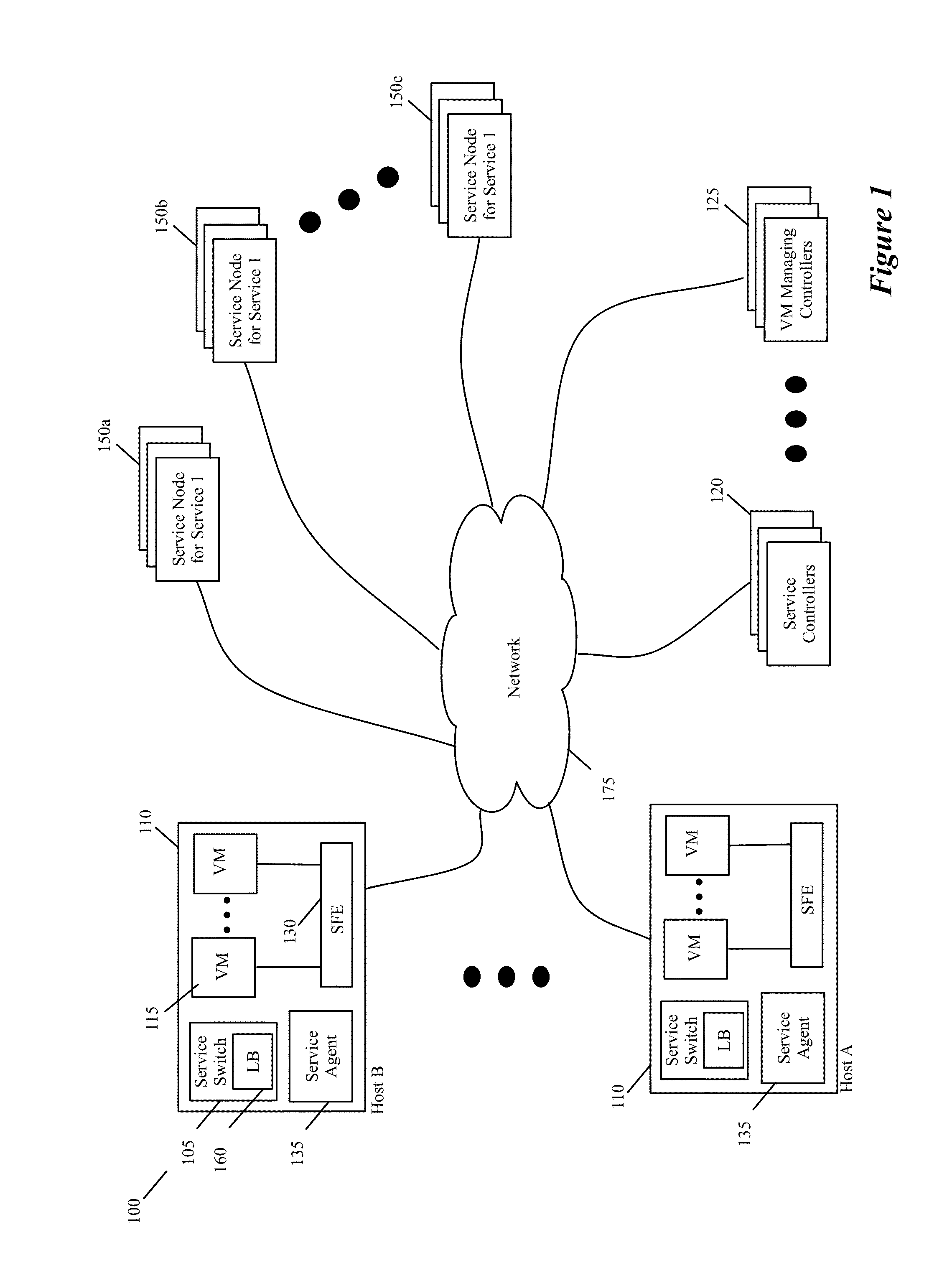
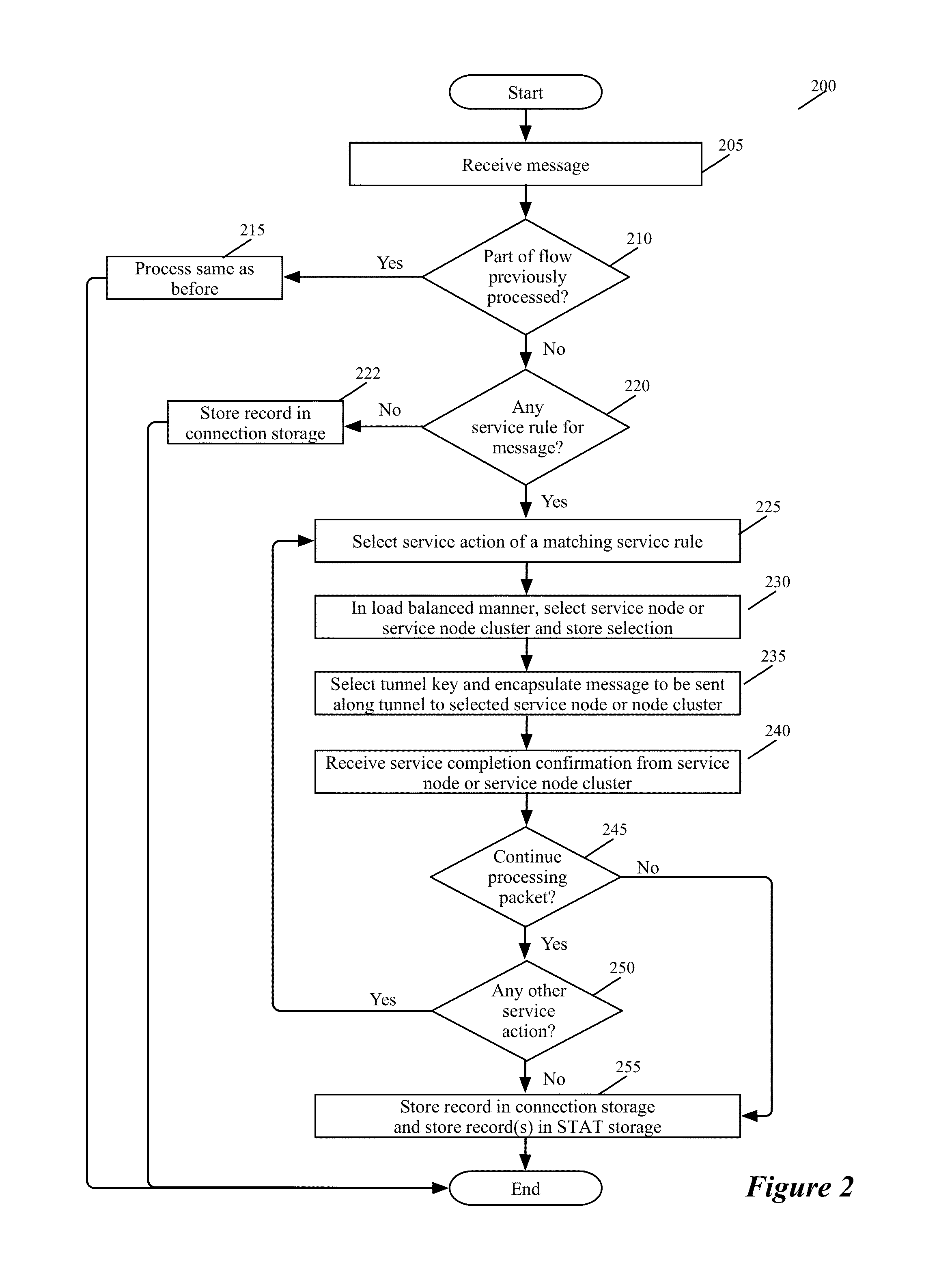
Controller Driven Reconfiguration of a Multi-Layered Application or Service Model
Some embodiments provide novel inline switches that distribute data messages from source compute nodes (SCNs) to different groups of destination service compute nodes (DSCNs). In some embodiments, the inline switches are deployed in the source compute nodes datapaths (e.g., egress datapath). The inline switches in some embodiments are service switches that (1) receive data messages from the SCNs, (2) identify service nodes in a service-node cluster for processing the data messages based on service policies that the switches implement, and (3) use tunnels to send the received data messages to their identified service nodes. Alternatively, or conjunctively, the inline service switches of some embodiments (1) identify service-nodes cluster for processing the data messages based on service policies that the switches implement, and (2) use tunnels to send the received data messages to the identified service-node clusters. The service-node clusters can perform the same service or can perform different services in some embodiments. This tunnel-based approach for distributing data messages to service nodes / clusters is advantageous for seamlessly implementing in a datacenter a cloud-based XaaS model (where XaaS stands for X as a service, and X stands for anything), in which any number of services are provided by service providers in the cloud.
Owner:NICIRA
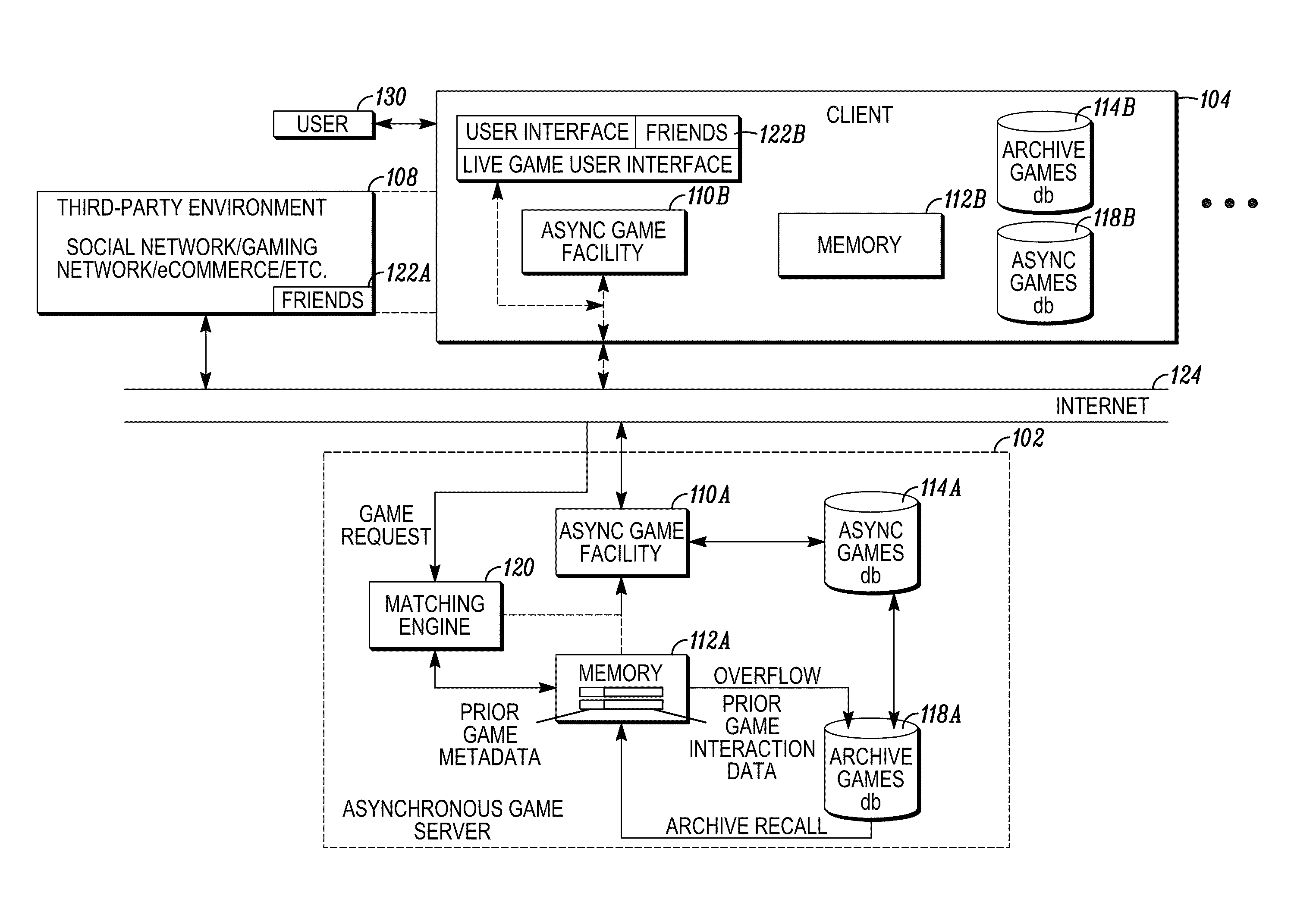
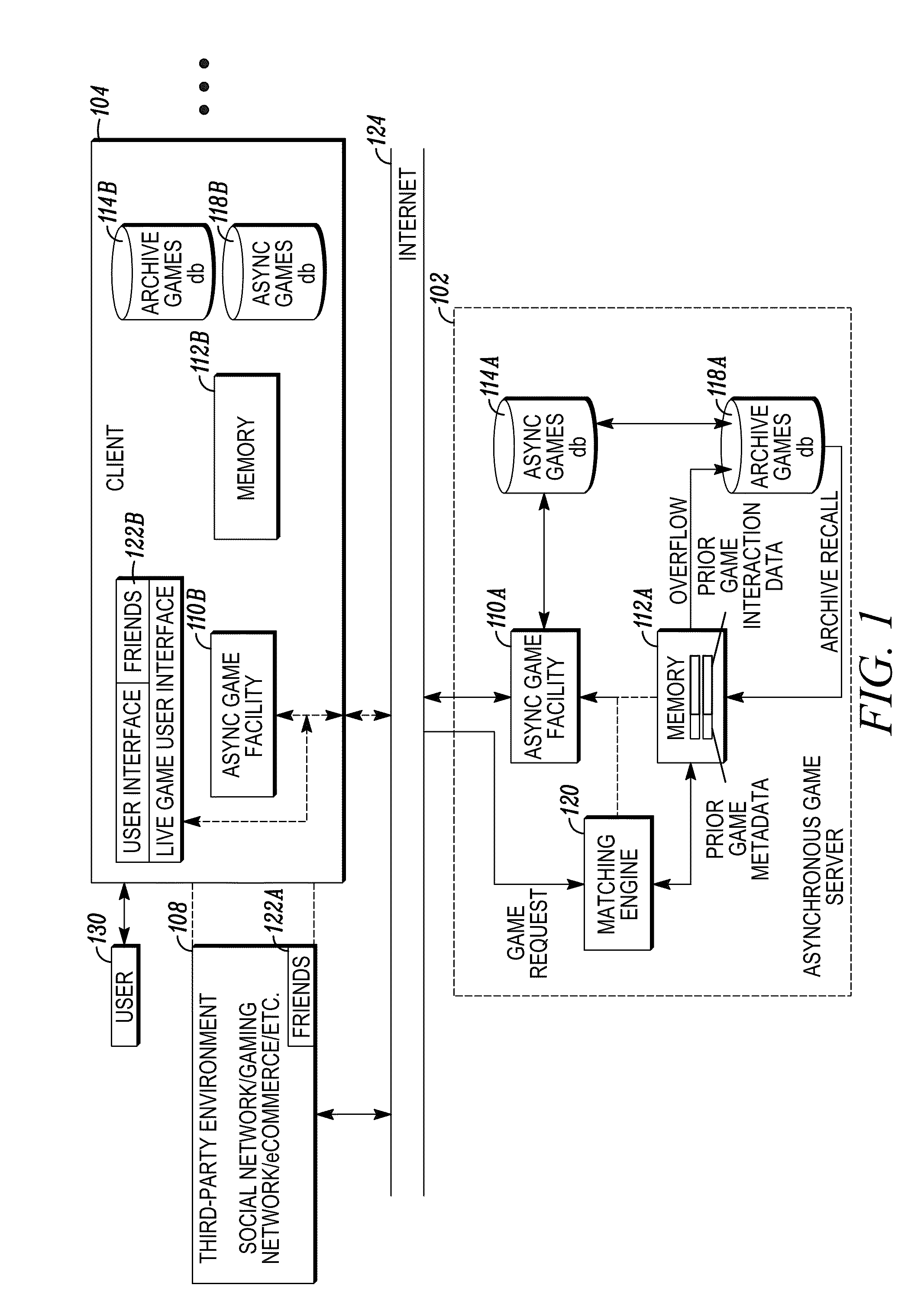
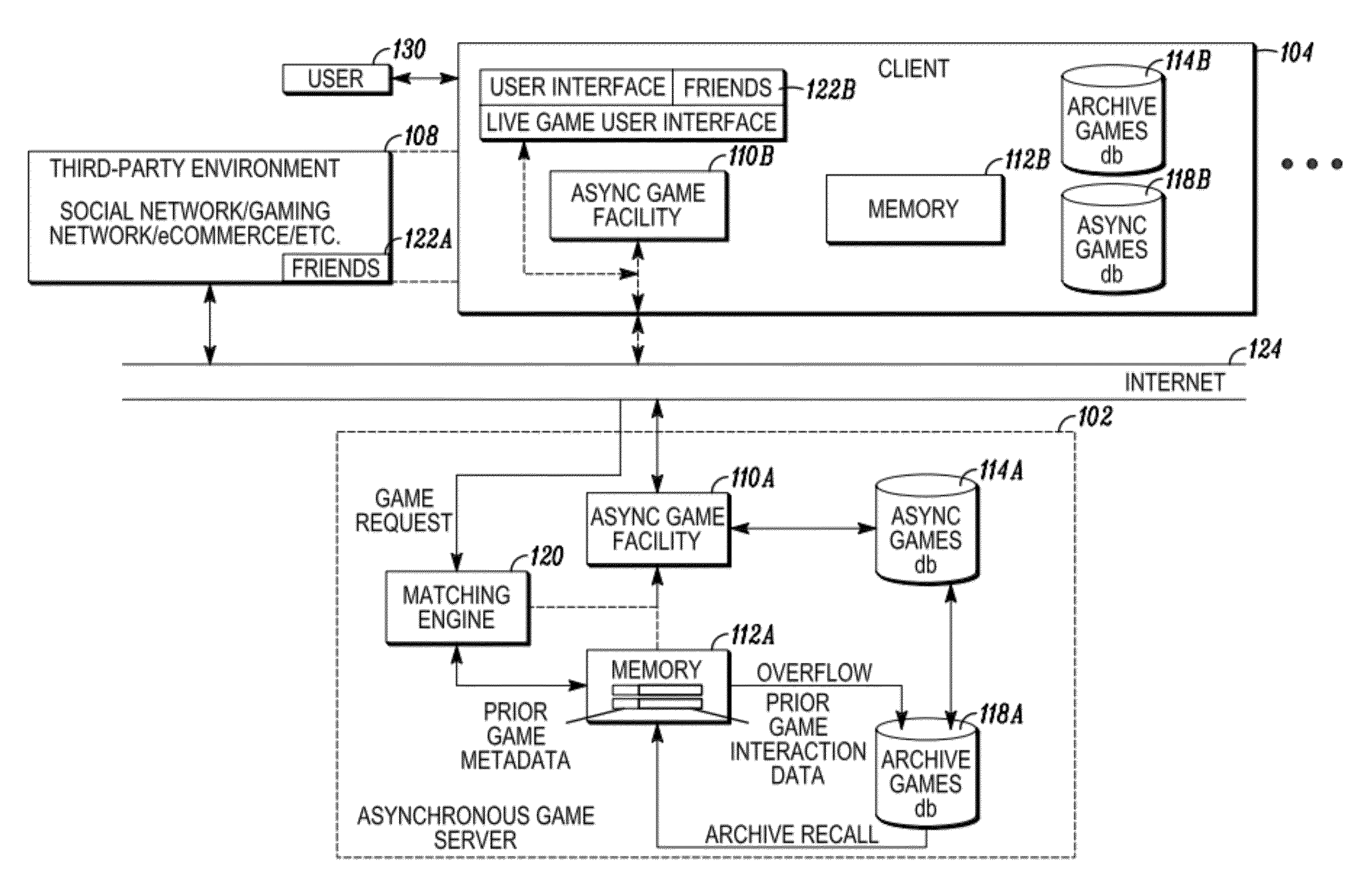
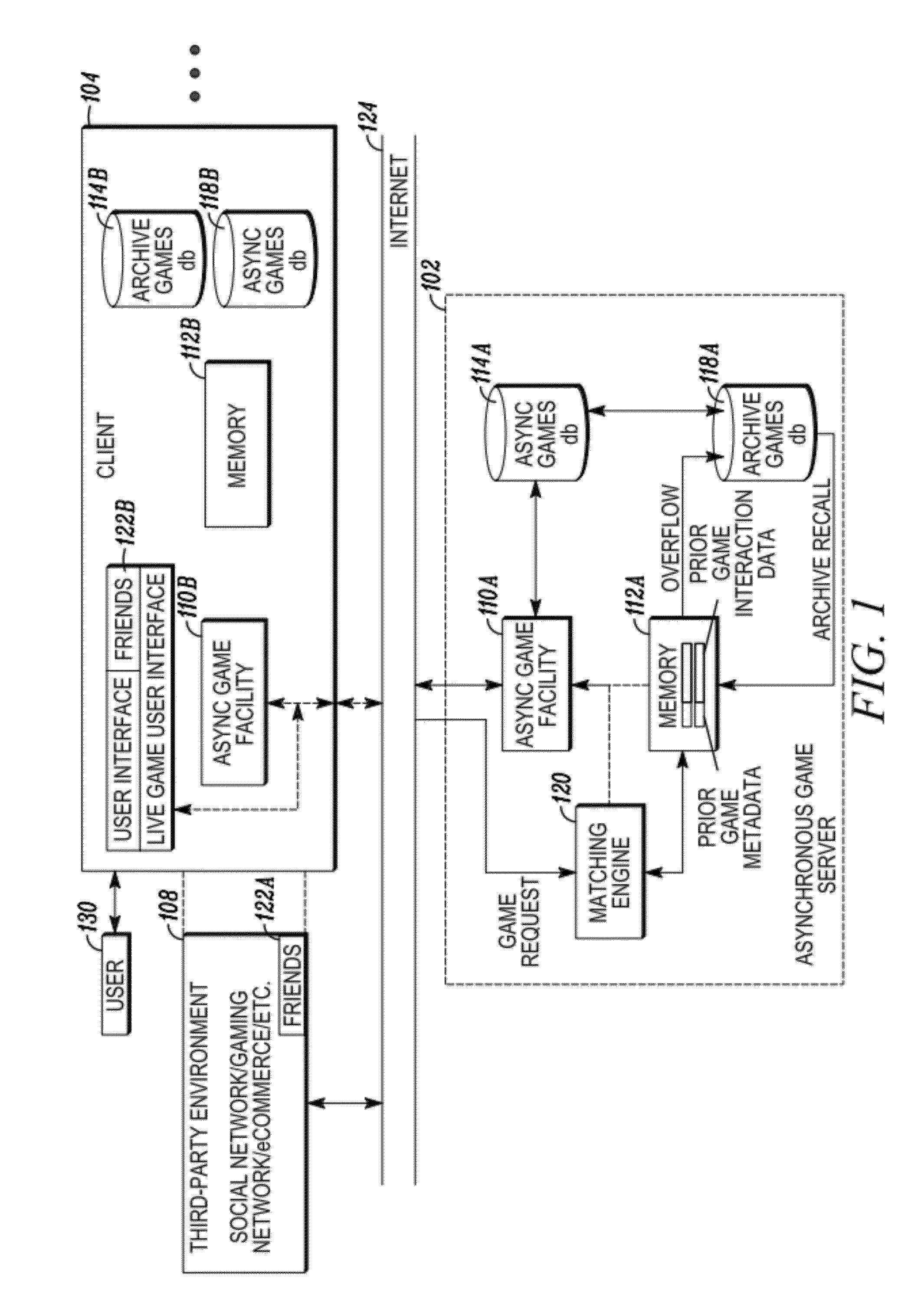
Interactive asynchronous game offline play architecture
InactiveUS20120009997A1Good synchronizationShort incubation periodVideo gamesSpecial data processing applicationsServices computingGame play
In embodiments of the present invention improved capabilities are described for serving a computer game, comprising (a) receiving, at a server, a request from a client for prior game play data relating to another user's prior live game play; (b) retrieving the prior game play data and transmitting the prior game play data to the client; (c) causing the client to store the prior game play data such that the client can retrieve the prior game play data at a later time; and (d) presenting a multi-player game environment where a live gaming participant using the client can play against and have two-way interactions with an apparently live opponent, the apparently live opponent's interaction being based on the prior game play data.
Owner:TETRIS ONLINE INC
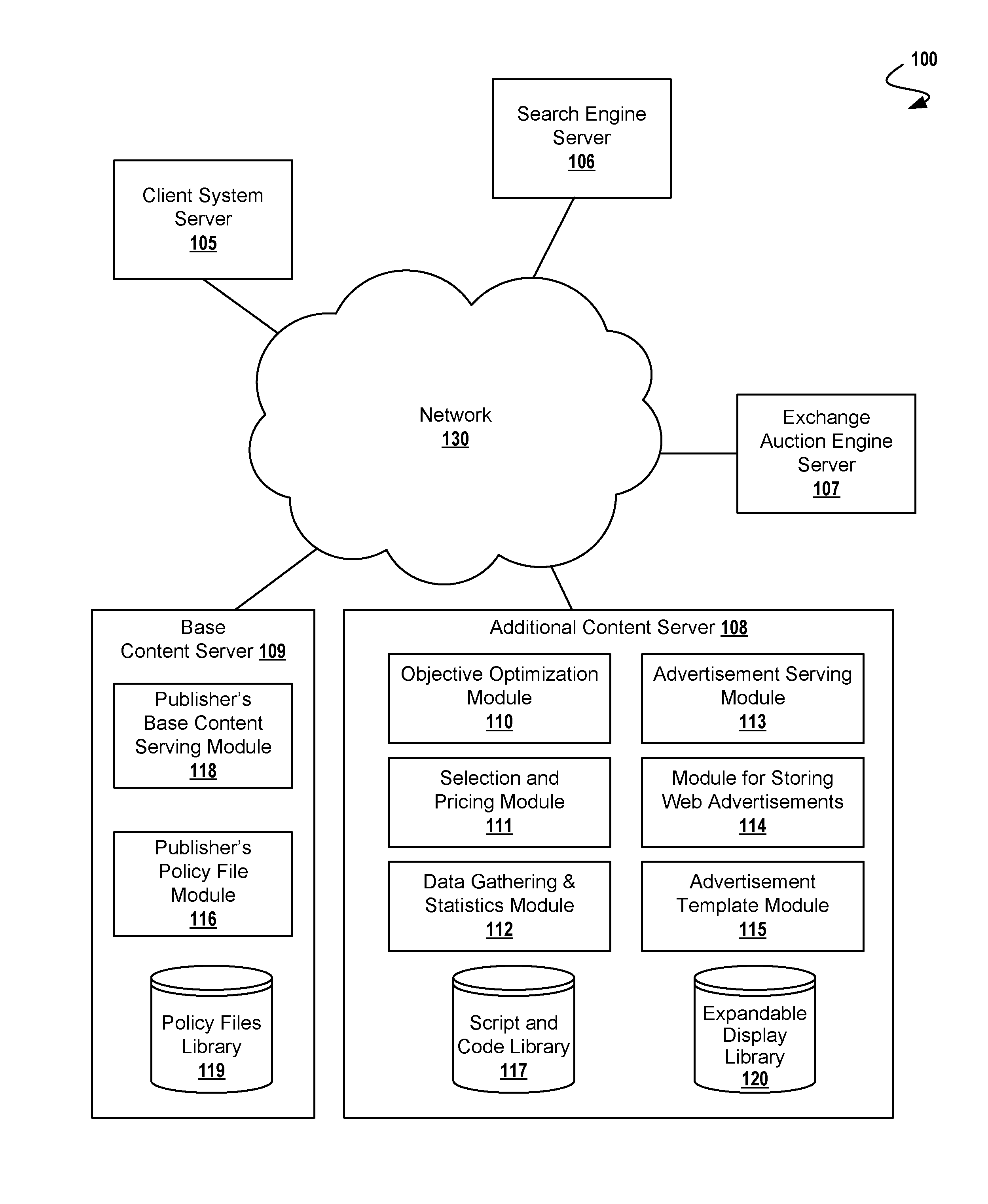
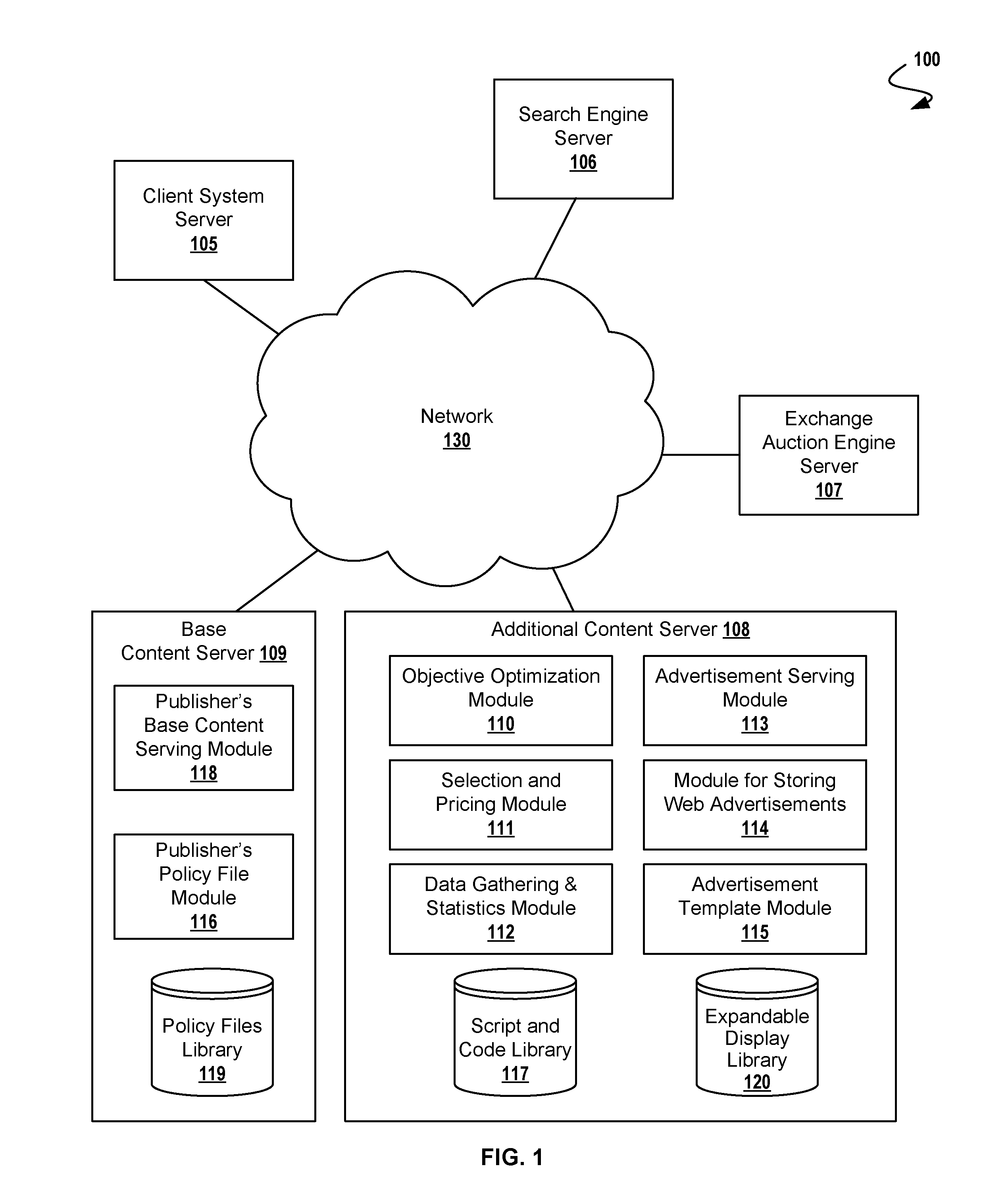
Securing Expandable Display Advertisements in a Display Advertising Environment
A method for securely presenting an HTML expandable display advertisement on a computer display, comprising: storing at a serving computer, an HTML object having an identifier associated with at least one securing computer, registering at the securing computer, the expandable display advertisement, and signaling, from a displaying computer, an expansion event for the expandable display advertisement wherein the expandable display advertisement is for display on the displaying computer. Additional operations for securely presenting an expandable display advertisement on a computer display include expanding, at the displaying computer, the expandable display advertisement; and signaling, from a displaying computer, a restoring event. Using this technique, the serving computer may be within a first domain, and the securing computer within a second domain, the second domain being different from the first domain. In some cases, a registration message received by a securing computer comprises width and height dimensions of the expandable display advertisement.
Owner:R2 SOLUTIONS
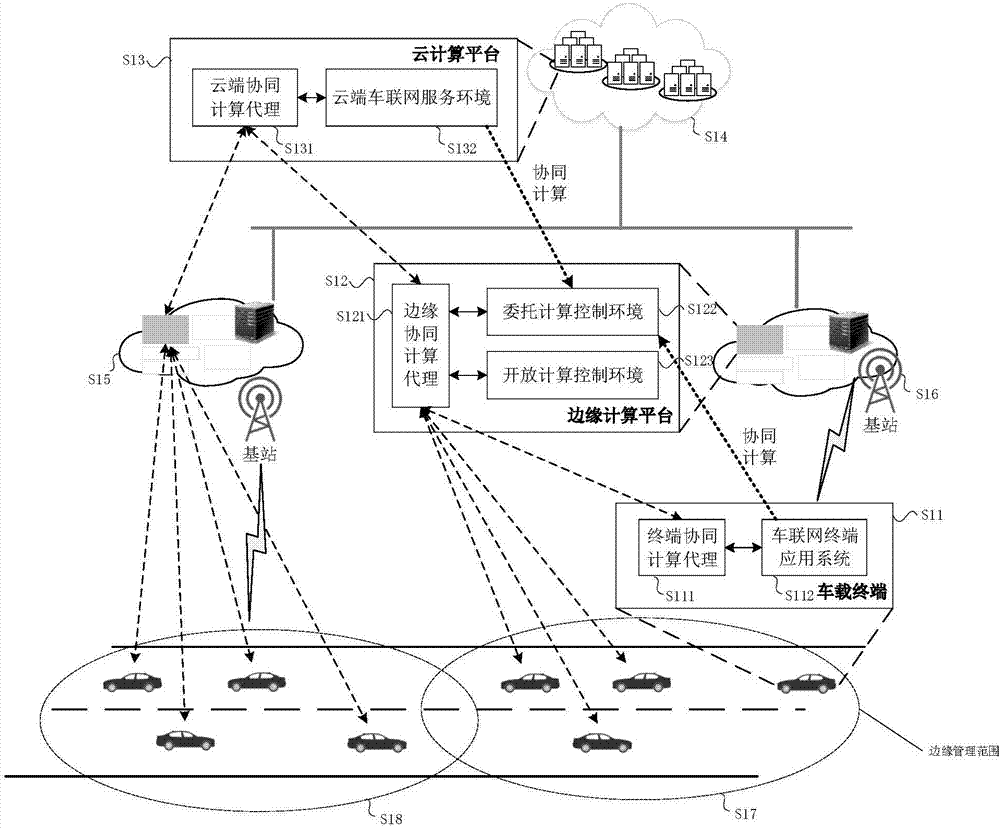
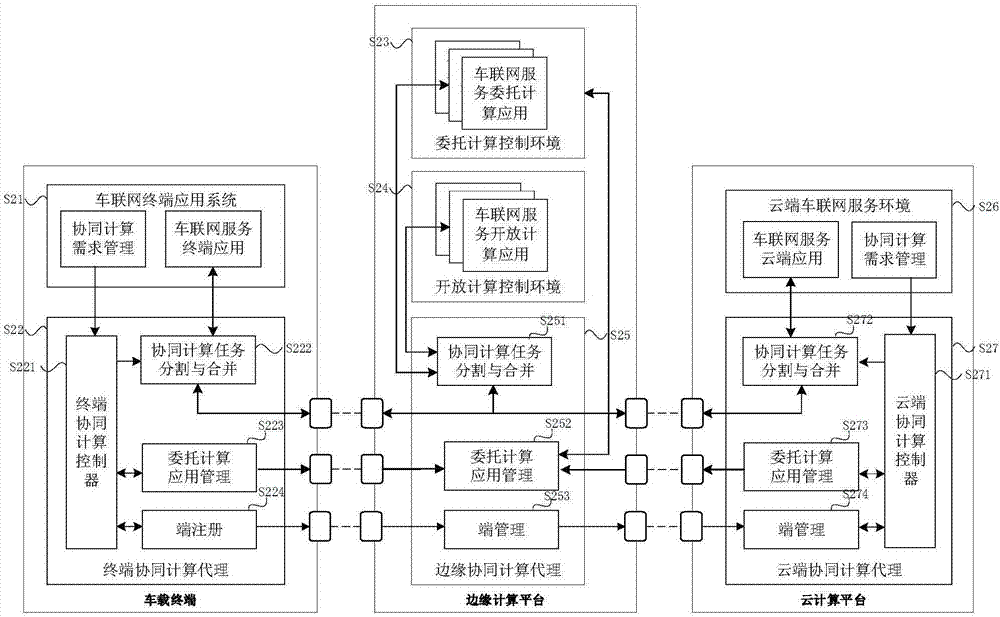
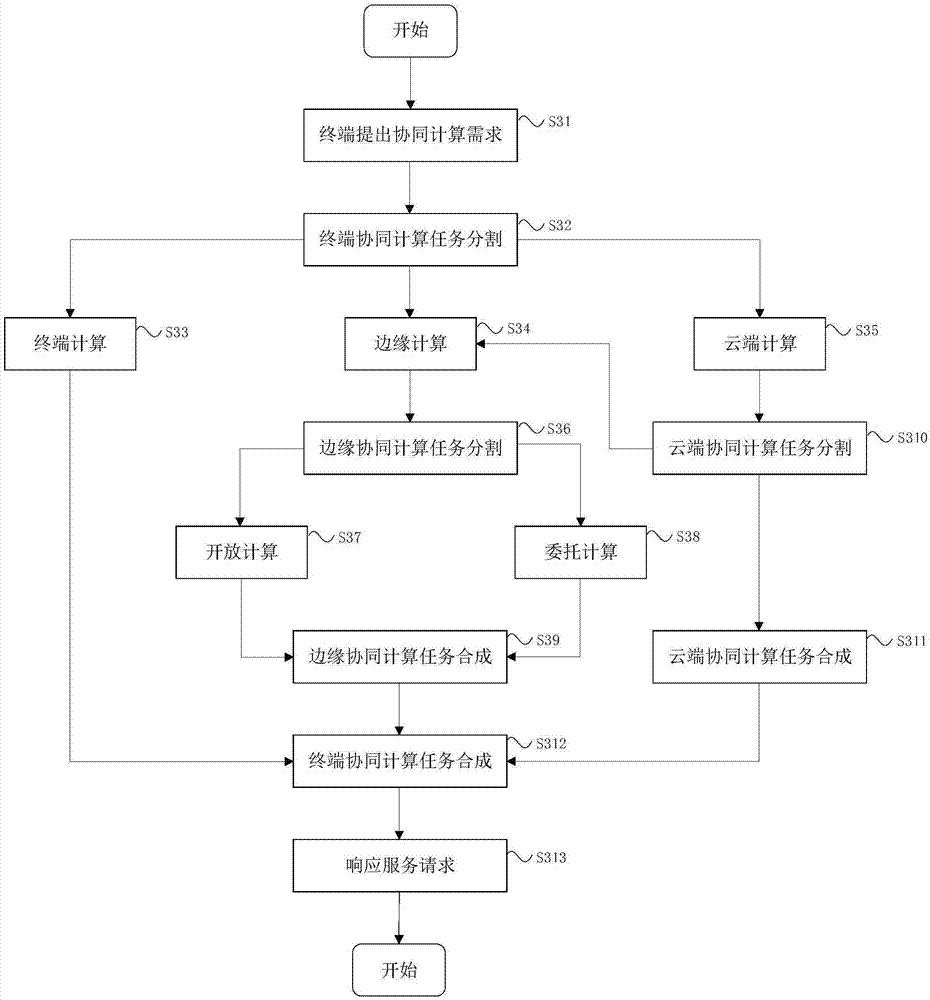
IoV (Internet of Vehicles) service cooperative computation method and system based on cloud end, edge end and vehicle end
ActiveCN107959708AComputing Process SecuritySolve the lack of computing powerTransmissionServices computingThe Internet
The invention discloses an IoV (Internet of Vehicles) service cooperative computation method and system based on a cloud end, an edge end and a vehicle end, and belongs to the field of cloud computation and intelligent driving. According to the computation system and the computation method, firstly, a vehicle-mounted terminal responds to an IoV service request proposed by an IoV terminal application system. A cloud computation platform implements cooperative interactive computation with the vehicle-mounted terminal and an edge computation platform, and provides a service computation resource or a cloud service request by a cloud IoV service environment module. The edge computation platform implements cooperative interactive computation with the vehicle-mounted terminal and the cloud computation platform by an edge cooperative computation agent module, and takes charge of integrating feedback results of a delegation computation control environment module and an open computation controlenvironment module. According to the invention, the unilateral problems of insufficient computation ability of the vehicle end, limited computation resources of the edge end and large data delay of the cloud end are solved, computation efficiency is improved, and user experience is optimized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Methods and apparatus for generating and distribution of surface mail objects
InactiveUS20020103697A1Cost-effectively createEasy to useDigital computer detailsAdvertisingServices computingWorld Wide Web
<heading lvl="0">Abstract of Disclosure< / heading> A method for generating and distributing mail items includes creating a first and a second mail file, wherein each of the first and second mail files includes recipient address information, and wherein the first mail file is generated by a first user, and the second mail file is generated by a second user. The first and second mail files are then transmitted to a mail service computer over a global computer network and printed, on a single sheet of media, a first mail item in accordance with the first mail file, and a second mail item in accordance with the second mail file. The first and second mail items are then placed into a surface mail system. The first mail item is addressed in accordance with the first recipient address information, and the second mail item is addressed in accordance with the second recipient address information. The mail item is then placed into the surface mail system in such a way as to minimize handling damage, and to leverage available postal technology. The mail items are then delivered to the postal addresses of the intended recipients.
Owner:AMAZINGMAIL COM
Multiple redundant services with reputation
InactiveUS20060026123A1Great degree of accuracyGreat of confidenceData processing applicationsProgram controlServices computingClient-side
Multiple copies of web services reside on associated computing devices, each having an associated reputation. A client may desire to access the web service having the highest or best reputation to be ensured of a greater degree of accuracy and confidence. The client does a search, and attaches to whichever web service has the highest reputation. By running multiple copies of the web services, they may vote amongst themselves on the results in the event that one or more of the services starts giving incorrect or otherwise inconsistent results. Combining the voting with reputation data associated with each copy of the web service allows a service's reputation to be dynamically adjusted based upon how faithfully it computes the results of work items sent to it.
Owner:MICROSOFT TECH LICENSING LLC
Interactive asynchronous game play architecture
InactiveUS20120064968A1Good synchronizationShort incubation periodDifferent record carrier formsRecord information storageData retrievalServices computing
In embodiments of the present invention improved capabilities are described for serving a computer game, comprising: (a) providing two separate storage facilities accessible from a server, the first storage facility comprising fast response searchable memory for storage of recently produced game play data, and the second storage facility comprising a structured database for longer term storage of game play data, the first memory having a data search and data retrieval speed that is substantially faster than the second memory; (b) receiving, at the server, a game play request from a live gaming participant with a desired opponent attribute; (c) in response to the game play request, searching the first memory, based on the attribute, to identify prior game play data corresponding to an appropriate opponent; and (d) presenting a multi-player game environment where the live gaming participant can play against and have two-way interactions with an apparently live opponent.
Owner:TETRIS ONLINE INC
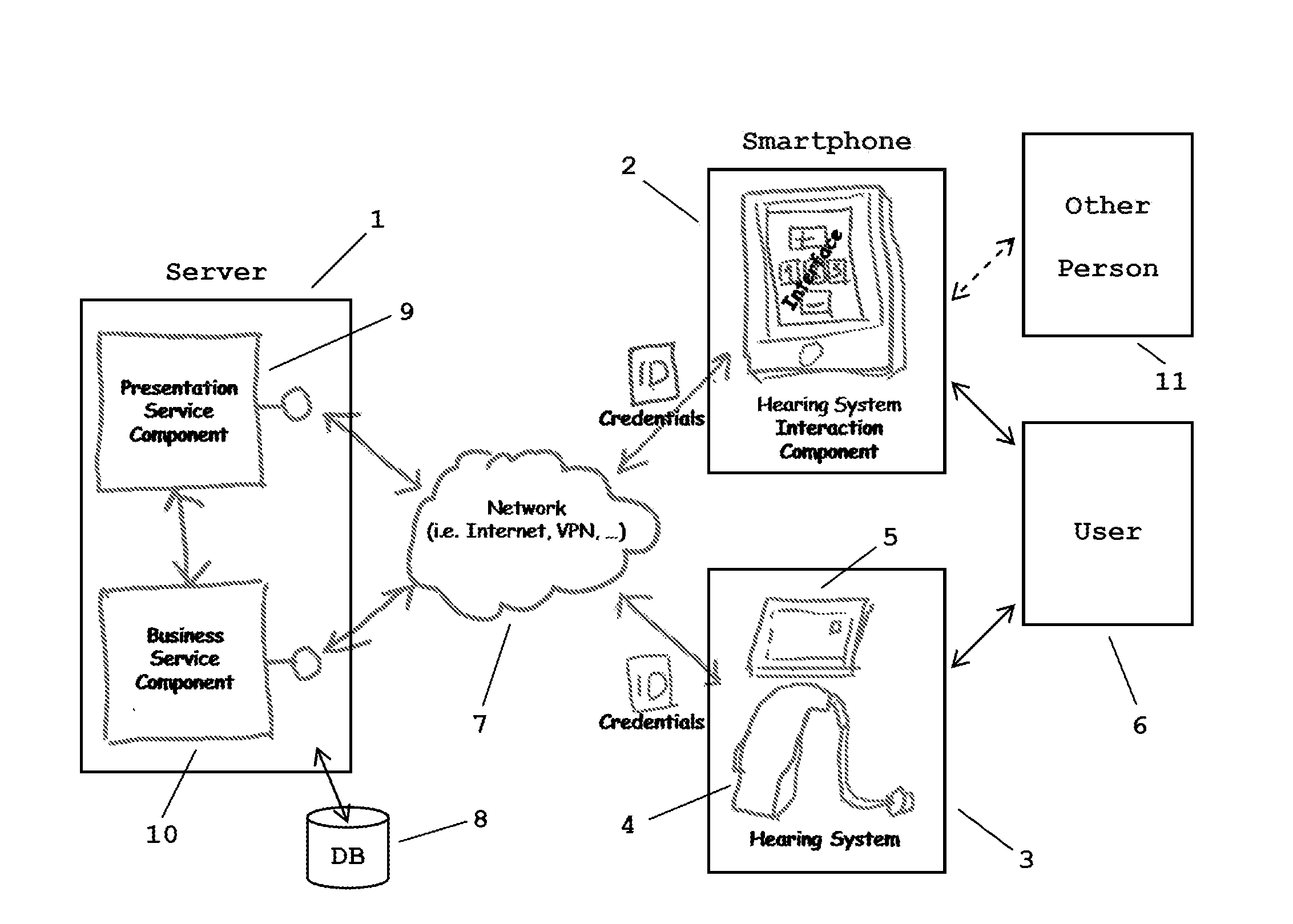
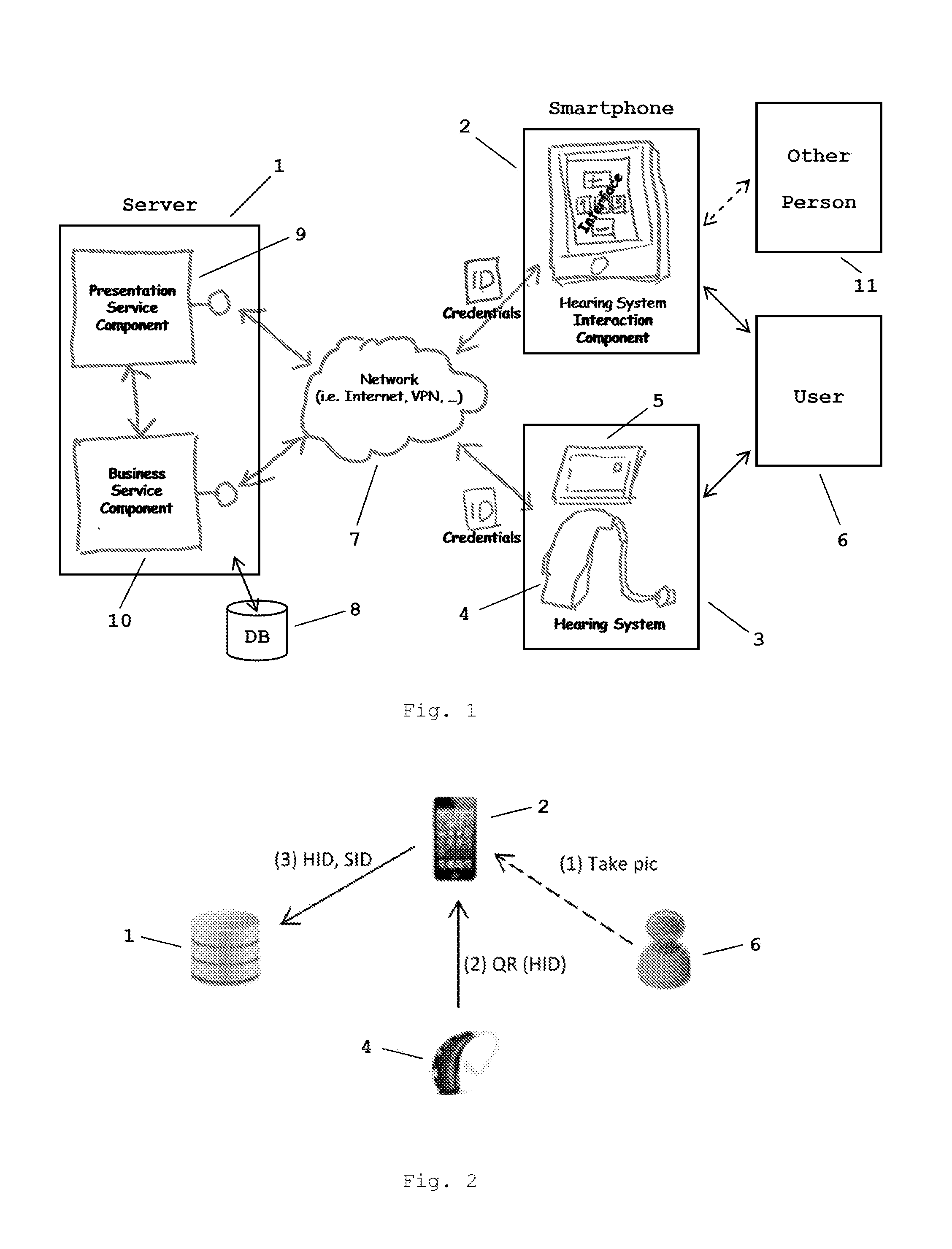
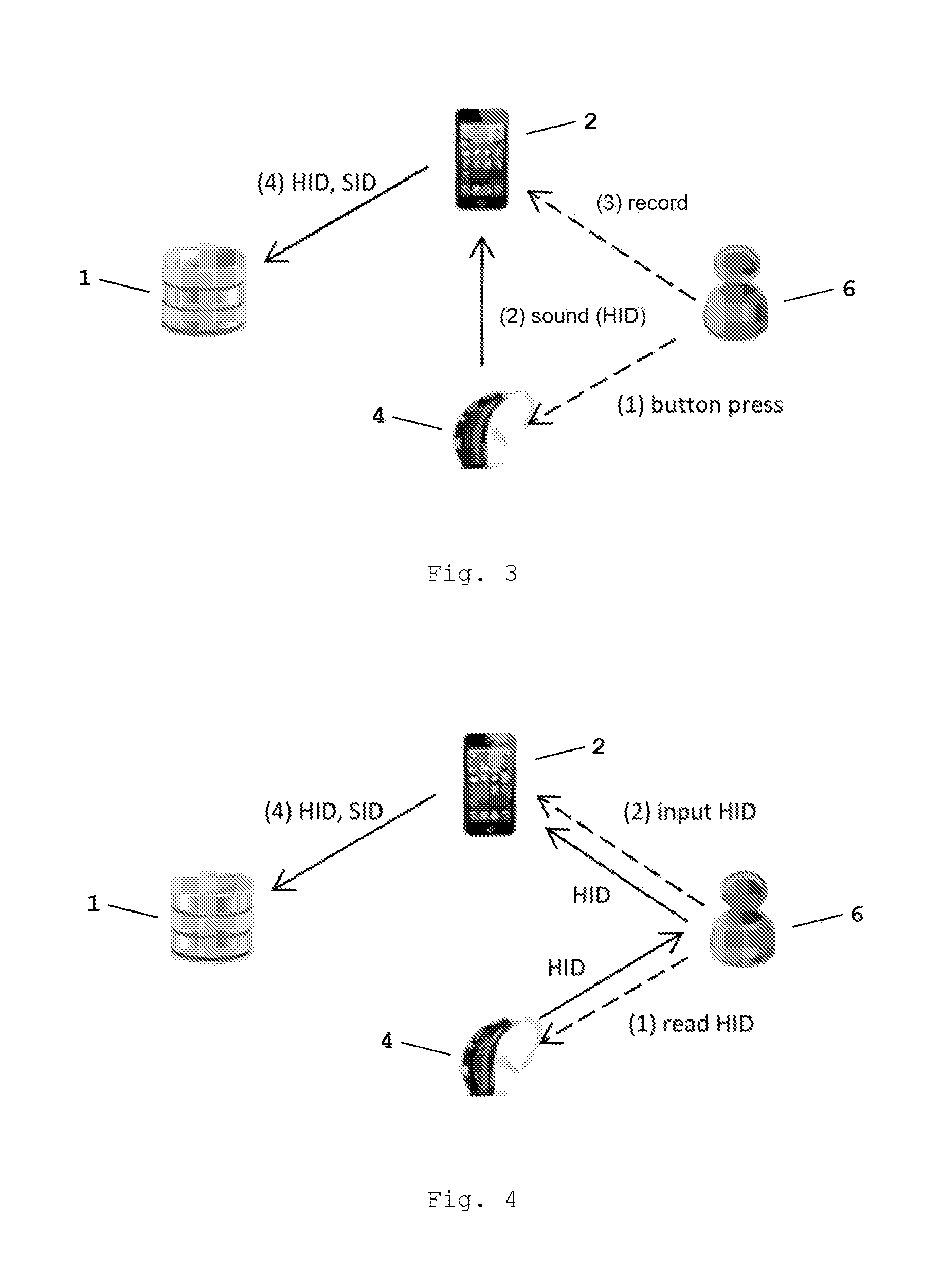
Method for controlling and/or configuring a user-specific hearing system via a communication network
ActiveUS20160212552A1Easy to implementSimple and rapid deploymentPosition data use in hearing devicesTransmissionServices computingControl data
A method for controlling and / or configuring a user-specific hearing system using a computing and / or communication device. The hearing system includes at least one hearing device customisable according to the individual hearing ability and / or preferences of a user of the hearing system. The method includes connecting the hearing system to a server via a network, connecting the computing and / or communication device to the server via the network, providing by the server a hearing system control and / or configuration service tailored to the user-specific hearing system to the computing and / or communication device, determining and / or selecting at the computing and / or communication device control data and / or configuration data using the hearing system control and / or configuration service, sending the control and / or configuration data from the computing and / or communication device to the hearing system, and adjusting the hearing system based on control and / or configuration data received at the hearing system.
Owner:SONOVA AG
Personalized service recommendation system and method based on latent semantic probability models
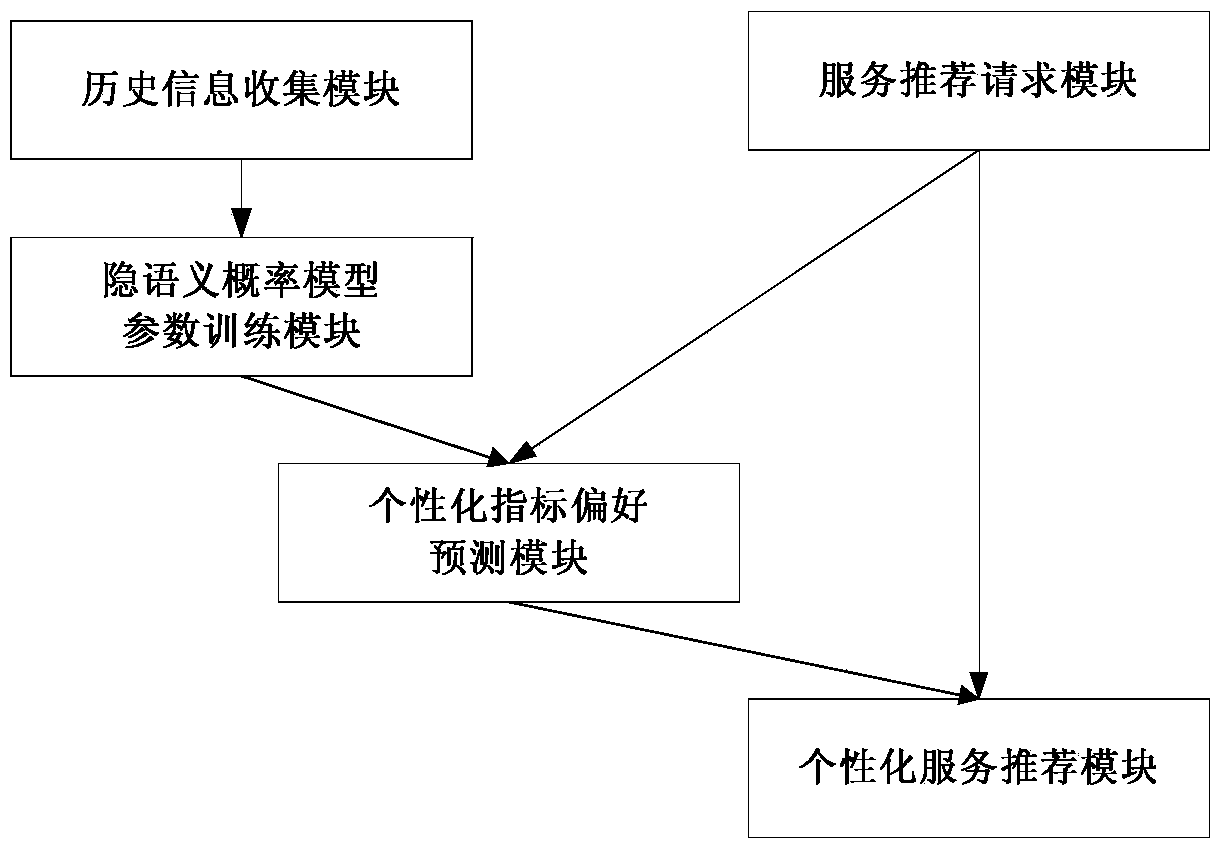
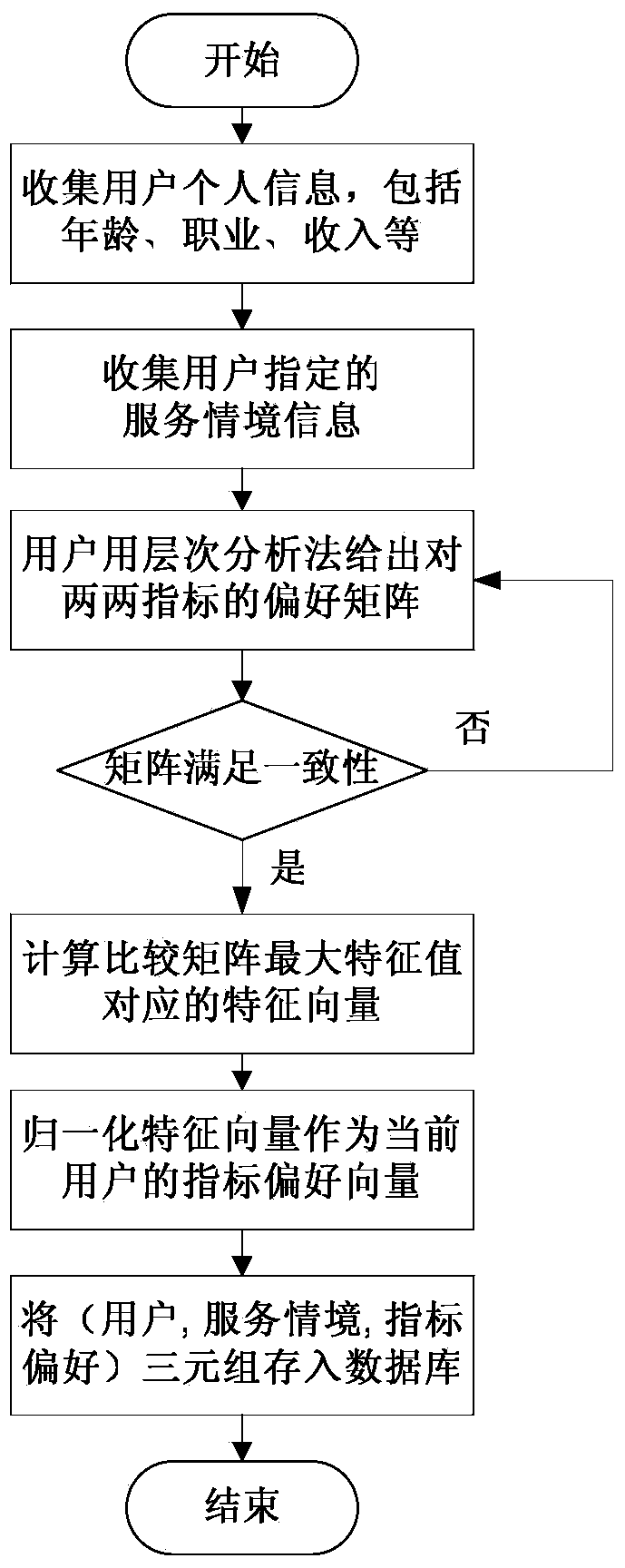
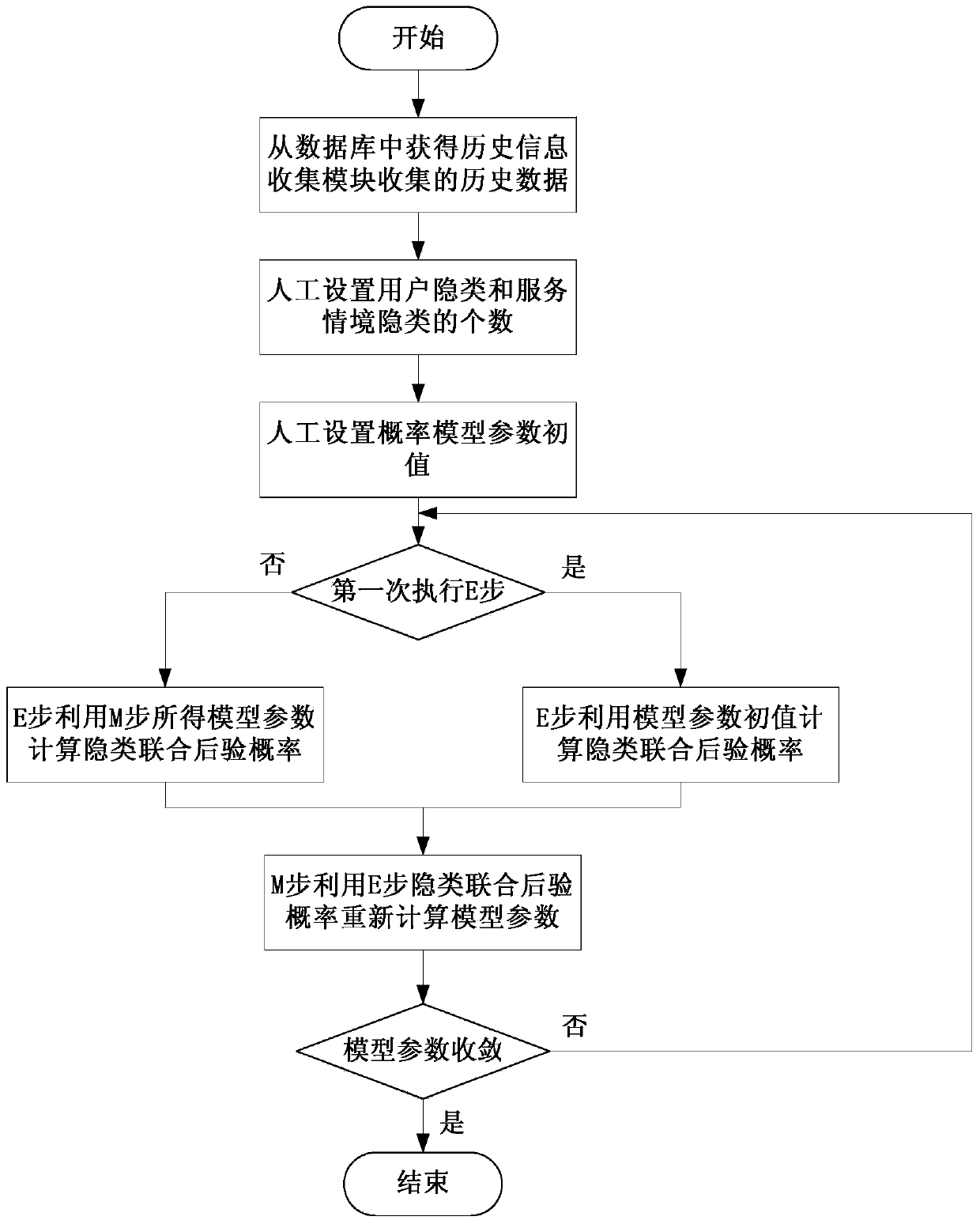
InactiveCN103473291AImproving the Efficiency of Online Service RecommendationsSpecial data processing applicationsServices computingPersonalization service
The invention relates to a personalized service recommendation system and method based on a latent semantic probability models and belongs to the technical field of service computing. The method includes: determining a QoS (quality of service) index system for evaluating performance of a series of services with similar functions; building latent semantic probability models among users, user index preferences and service situations; collecting index preference information provided by user-system interaction when different users use services with different functions under different service situations in a system, and saving the information in a historical experience database; using collected data to train parameters of the latent semantic probability models; when a user is unfamiliar with a certain service situation and needs to call a service with a special function under the service situation, using the trained latent semantic probability models to predict index preference of the user; comprehensively screening candidate services according to the predicted personalized QoS index preference, selecting the service most suitable for the user's requirements, and personalized service recommendation is achieved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
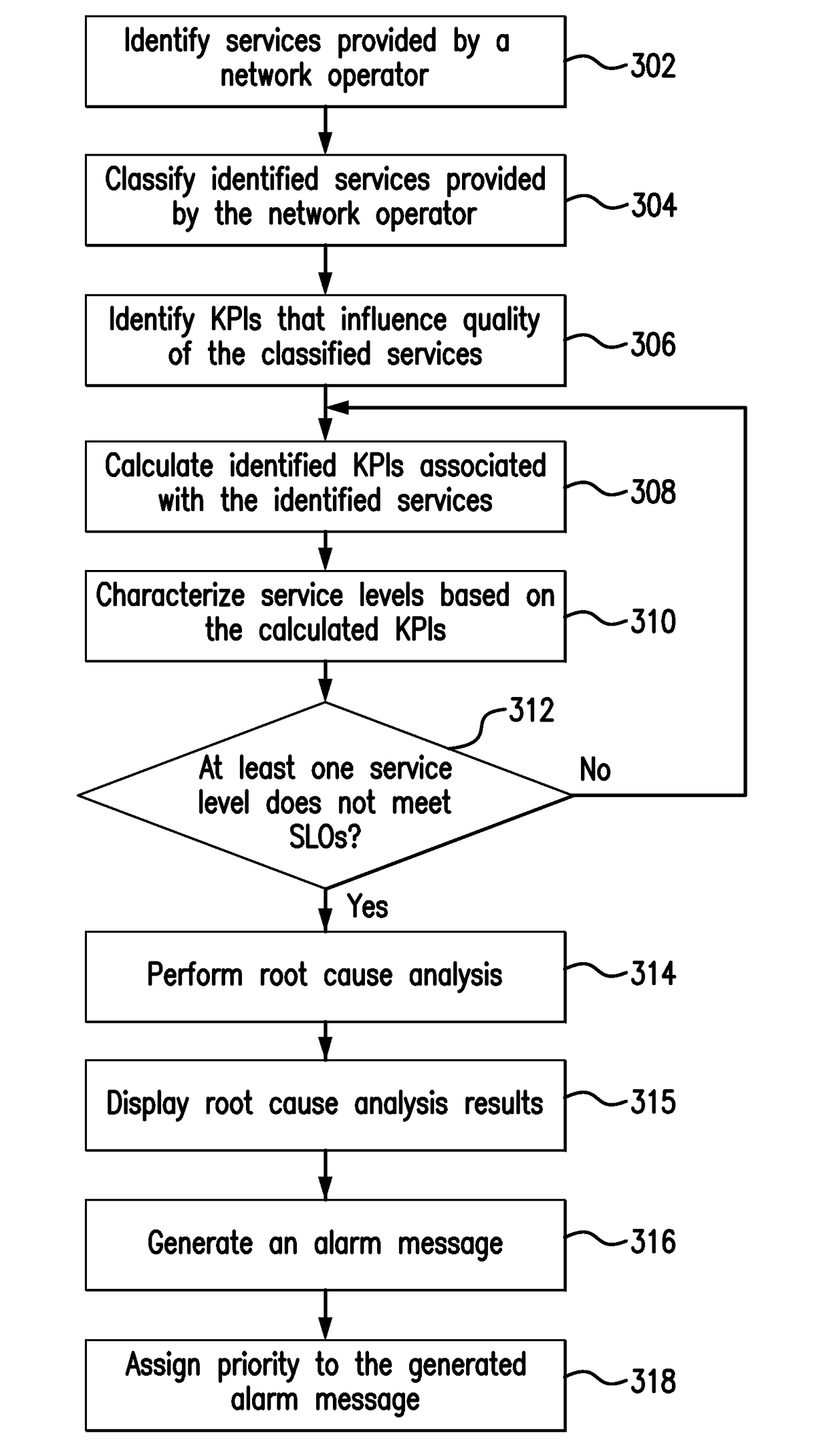
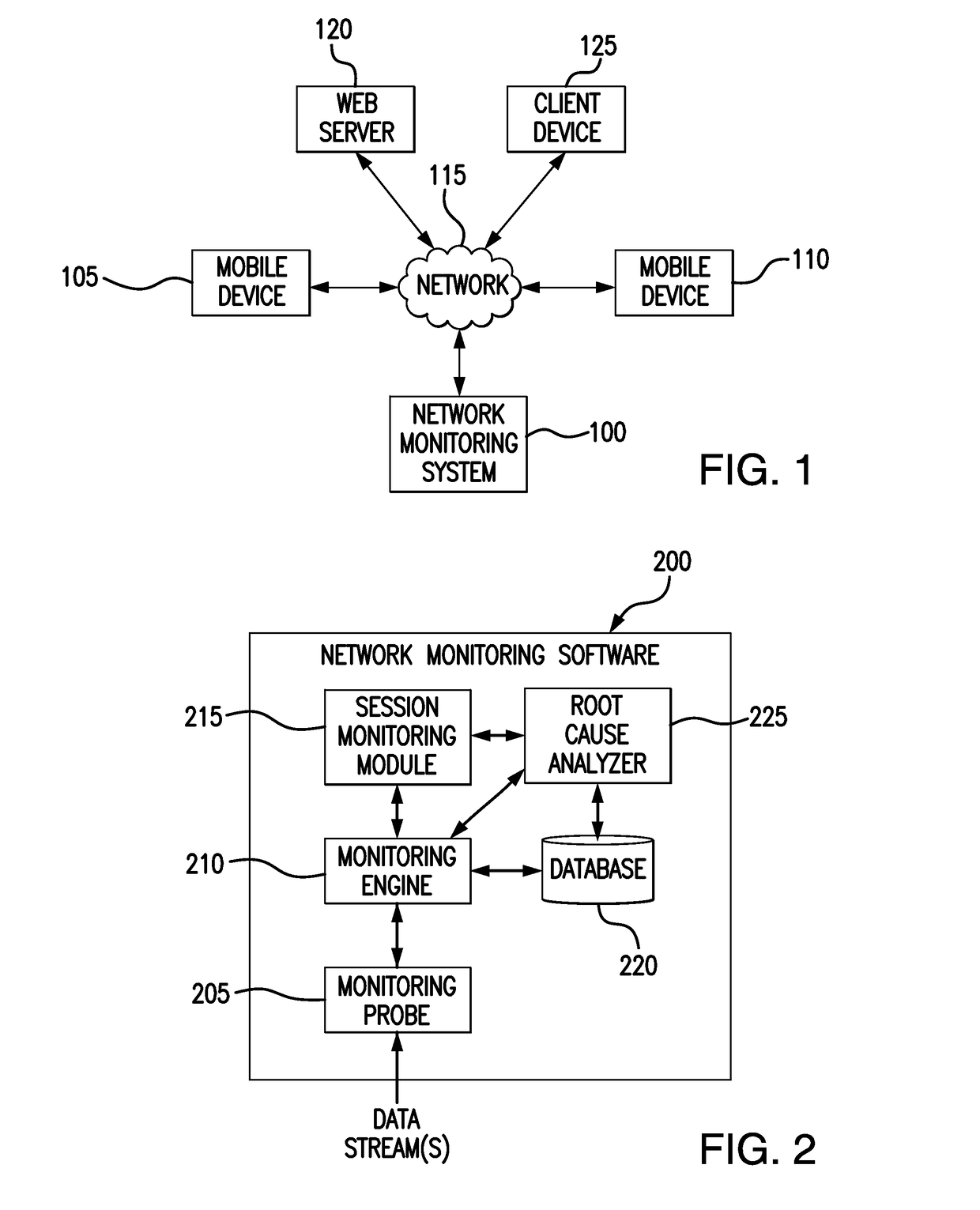
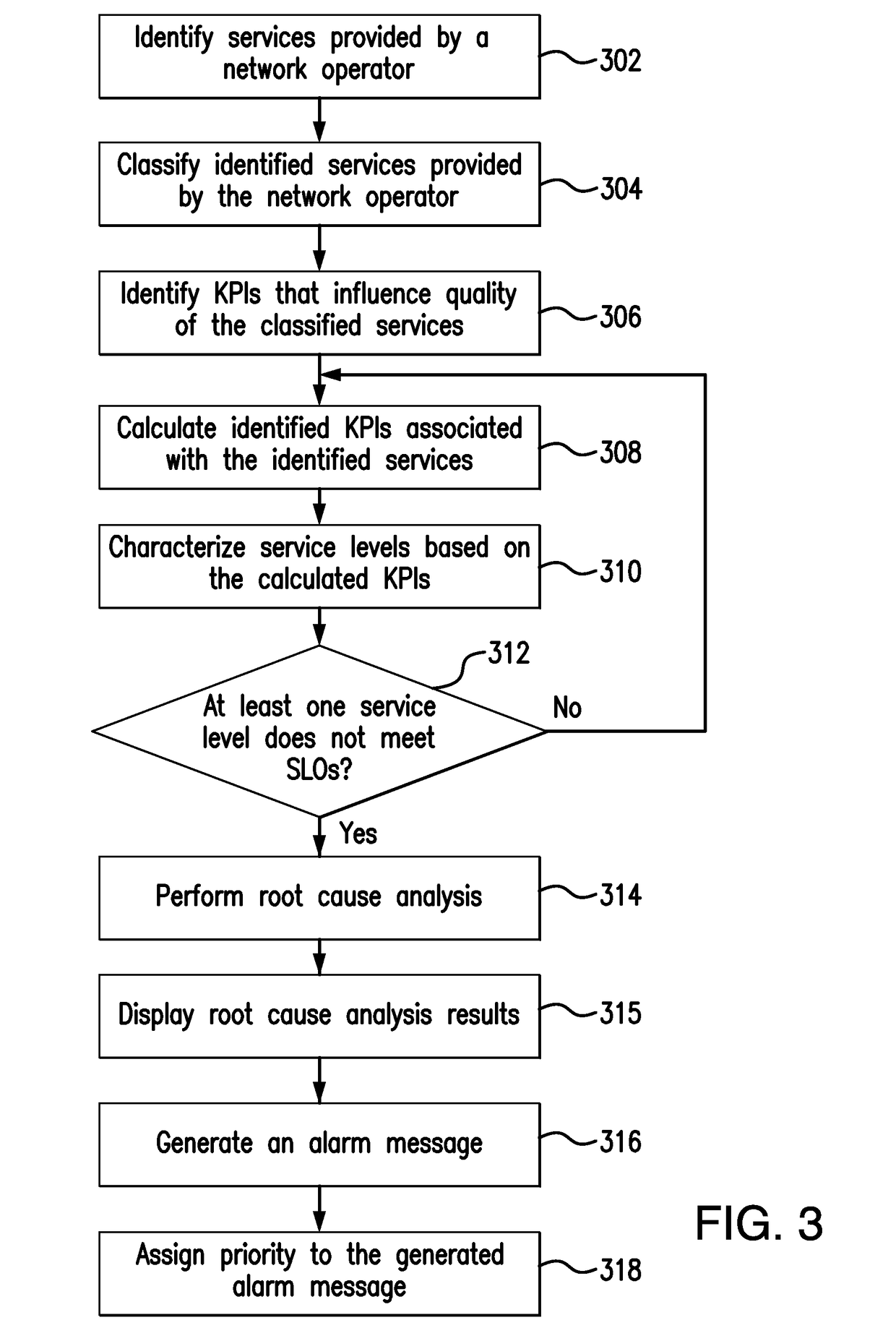
System and method for automatically identifying failure in services deployed by mobile network operators
A network monitoring system is provided that includes a processor and a memory coupled to the processor. A plurality of services provided by a network operator is identified. A plurality of Key Performance Indicators (KPIs) associated with the identified plurality of services is calculated on a per service basis. Individual services provided by the network operator are characterized based on the calculated plurality of KPIs. A root cause of service level failures for one or more of the plurality of services is identified, in response to determining that at least one of the characterized service levels does not meet predefined service level objectives for the one or more of the plurality of services.
Owner:NETSCOUT SYST TEXAS LLC
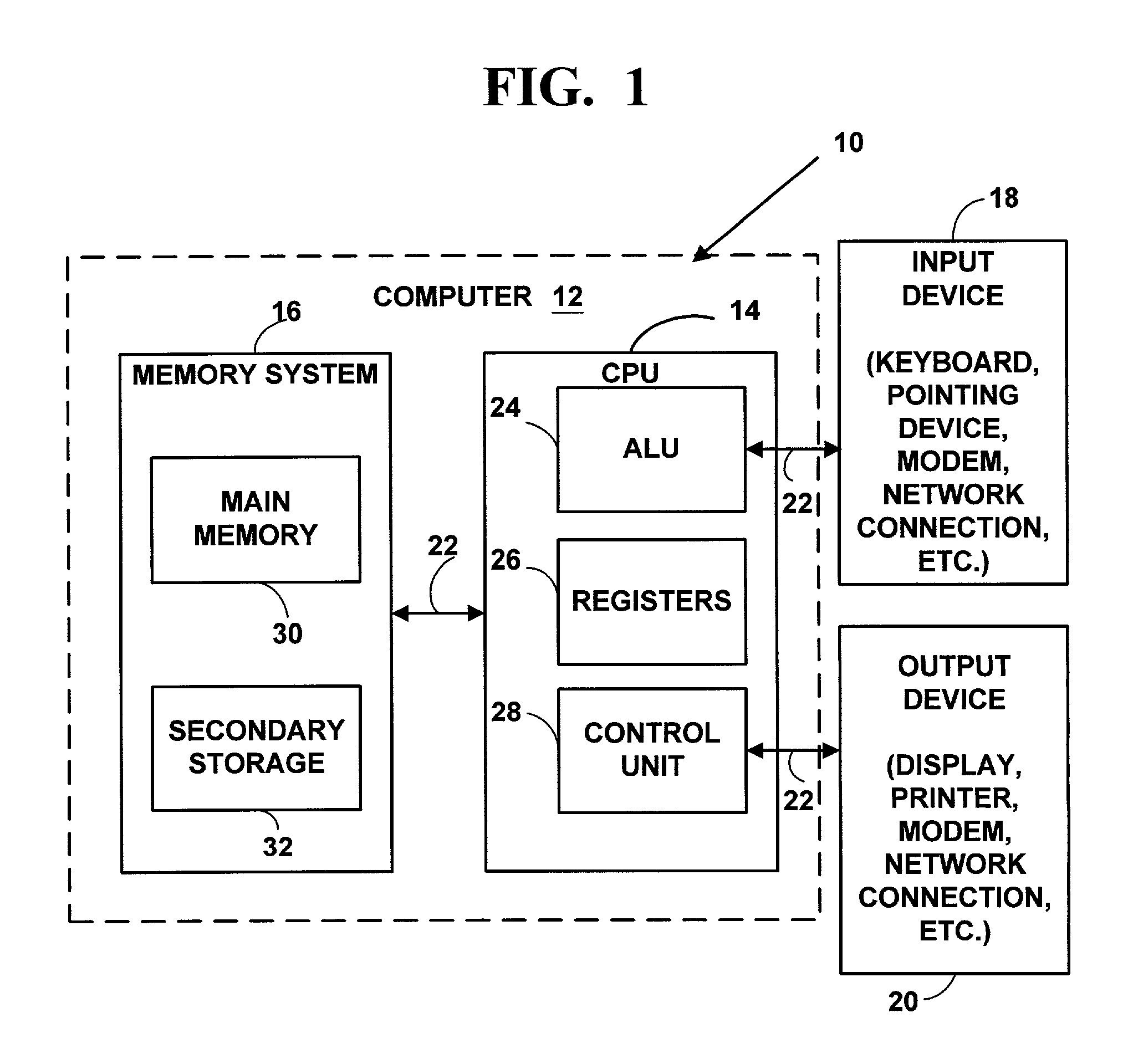
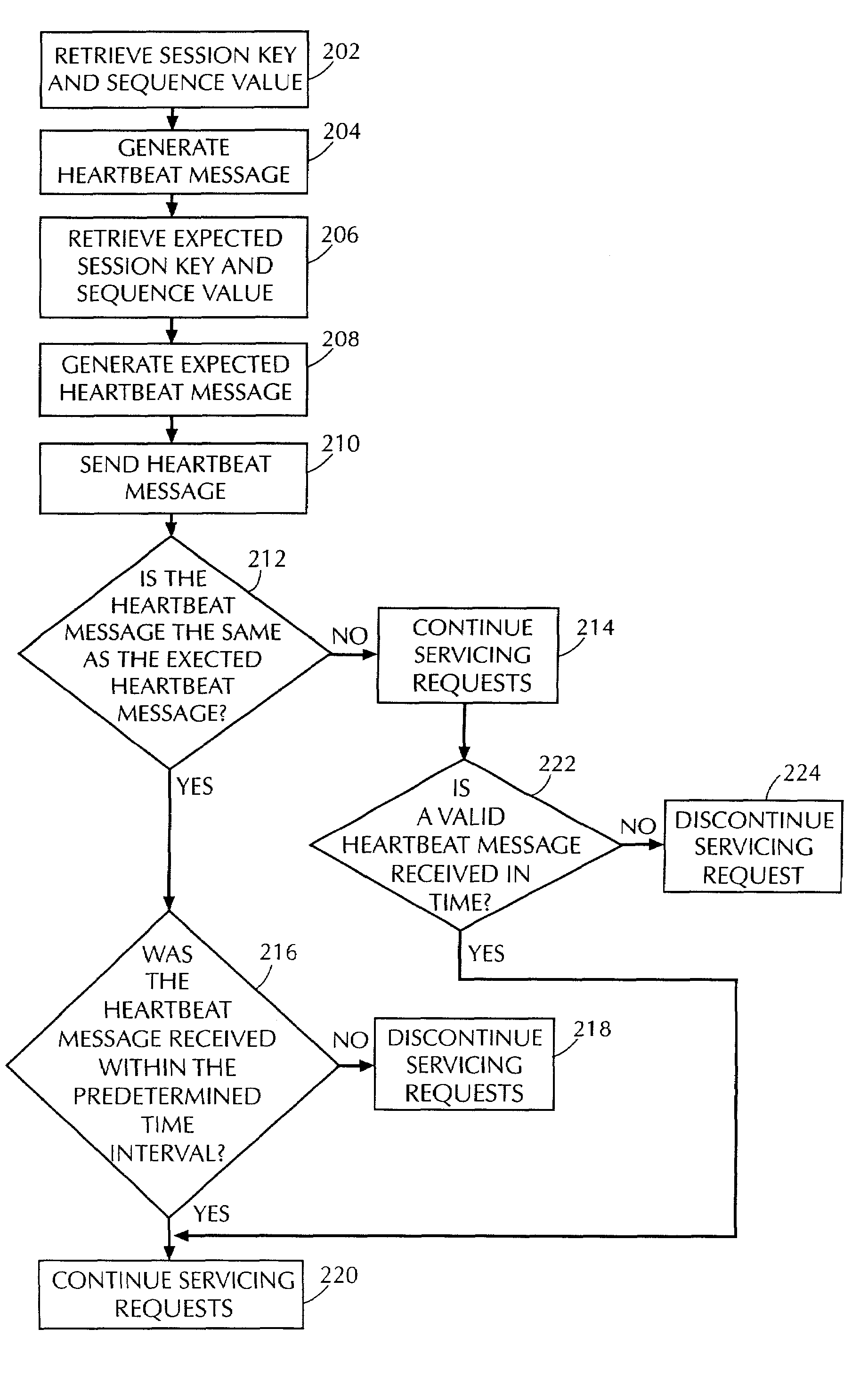
System and method for computer storage security
ActiveUS7093127B2Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwareStorage security
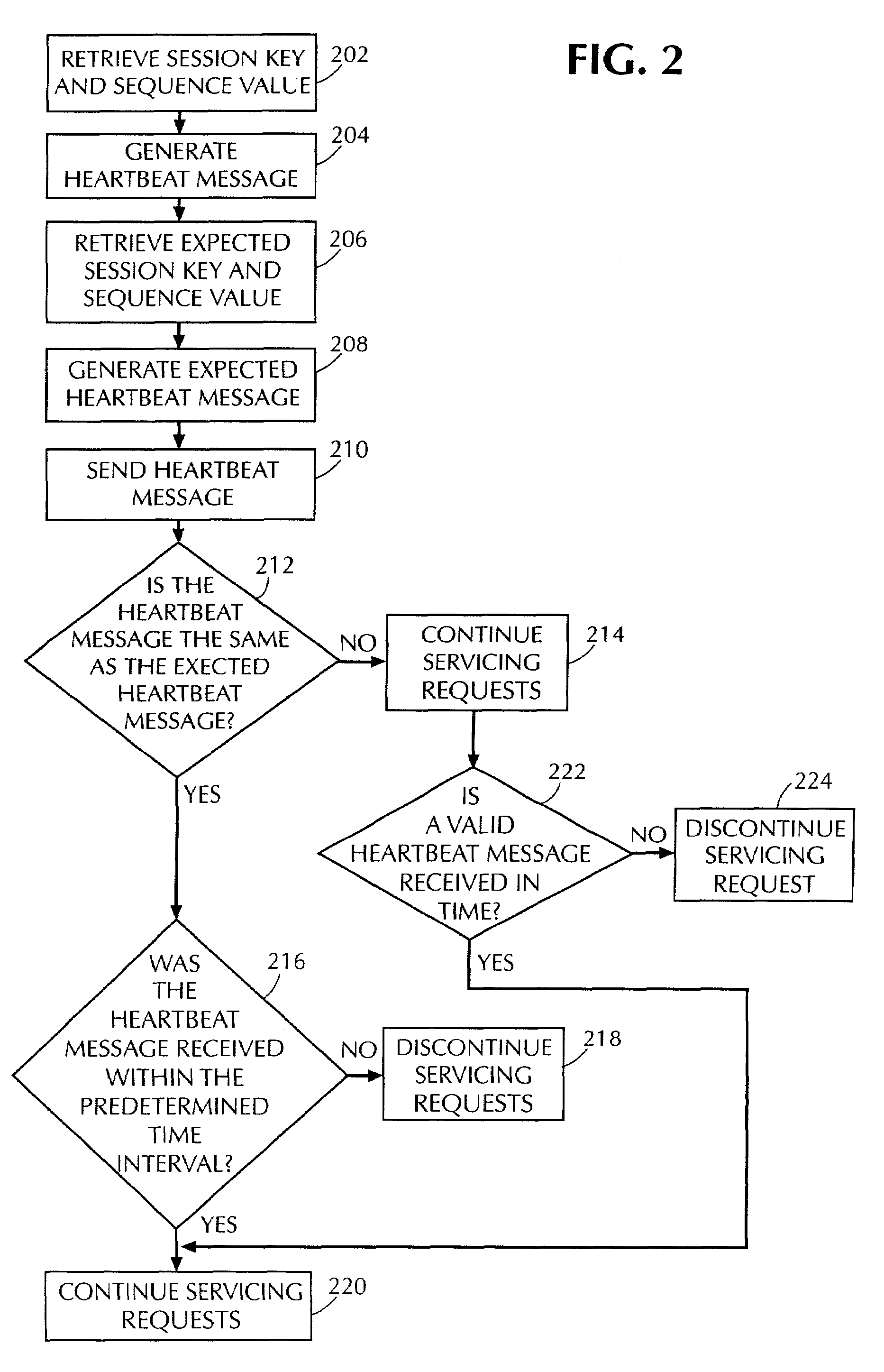
A system and method that improves security of a computer storage system by requiring an initiating computer to periodically reaffirm its identity by transmitting a message to a servicing computer. The message contains a previously established authentication message and a sequence value, established by and known only to the original participants. A message must be received by the servicing computer within a predetermined time interval in order to maintain data communications between the original participants.
Owner:FALCONSTOR
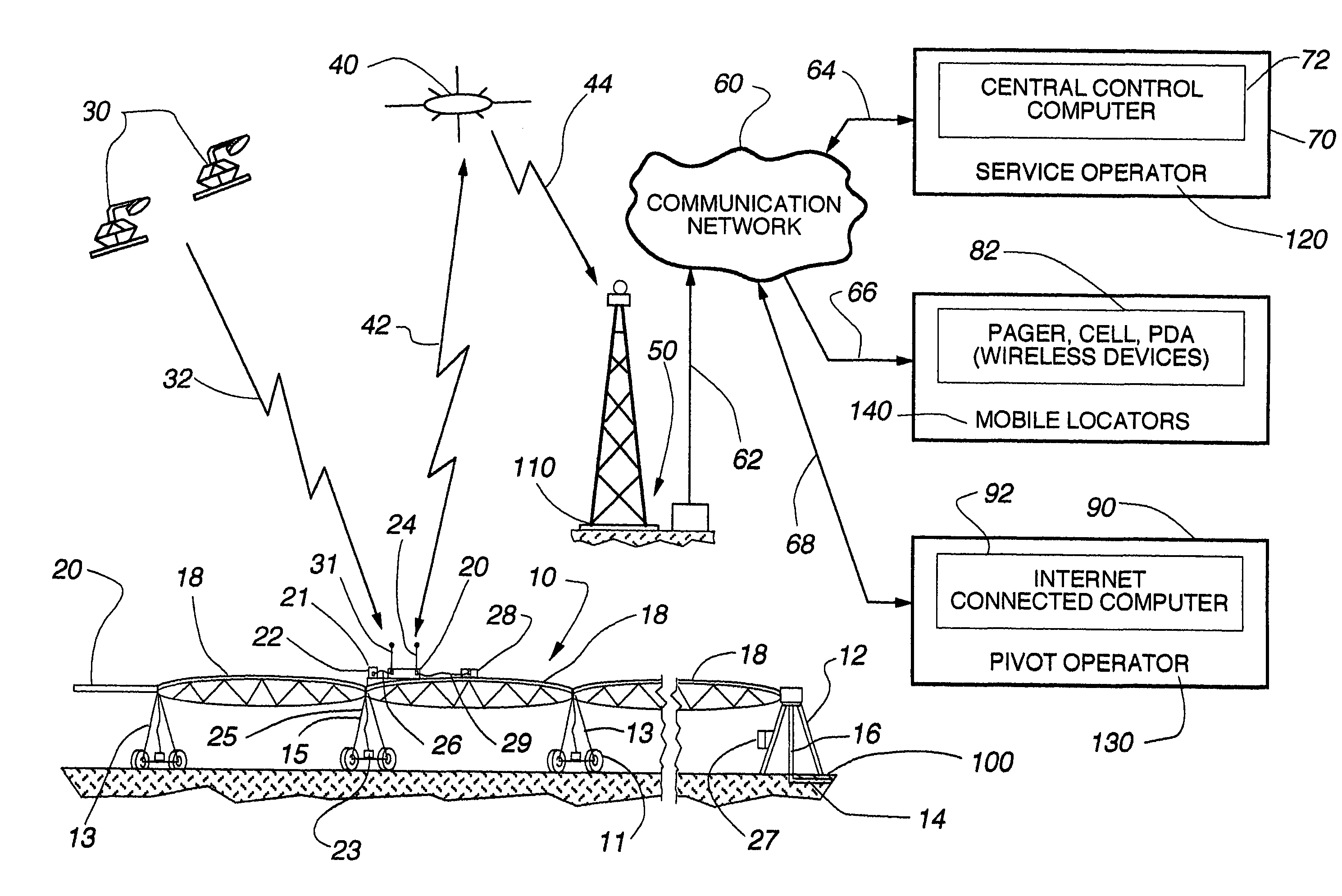
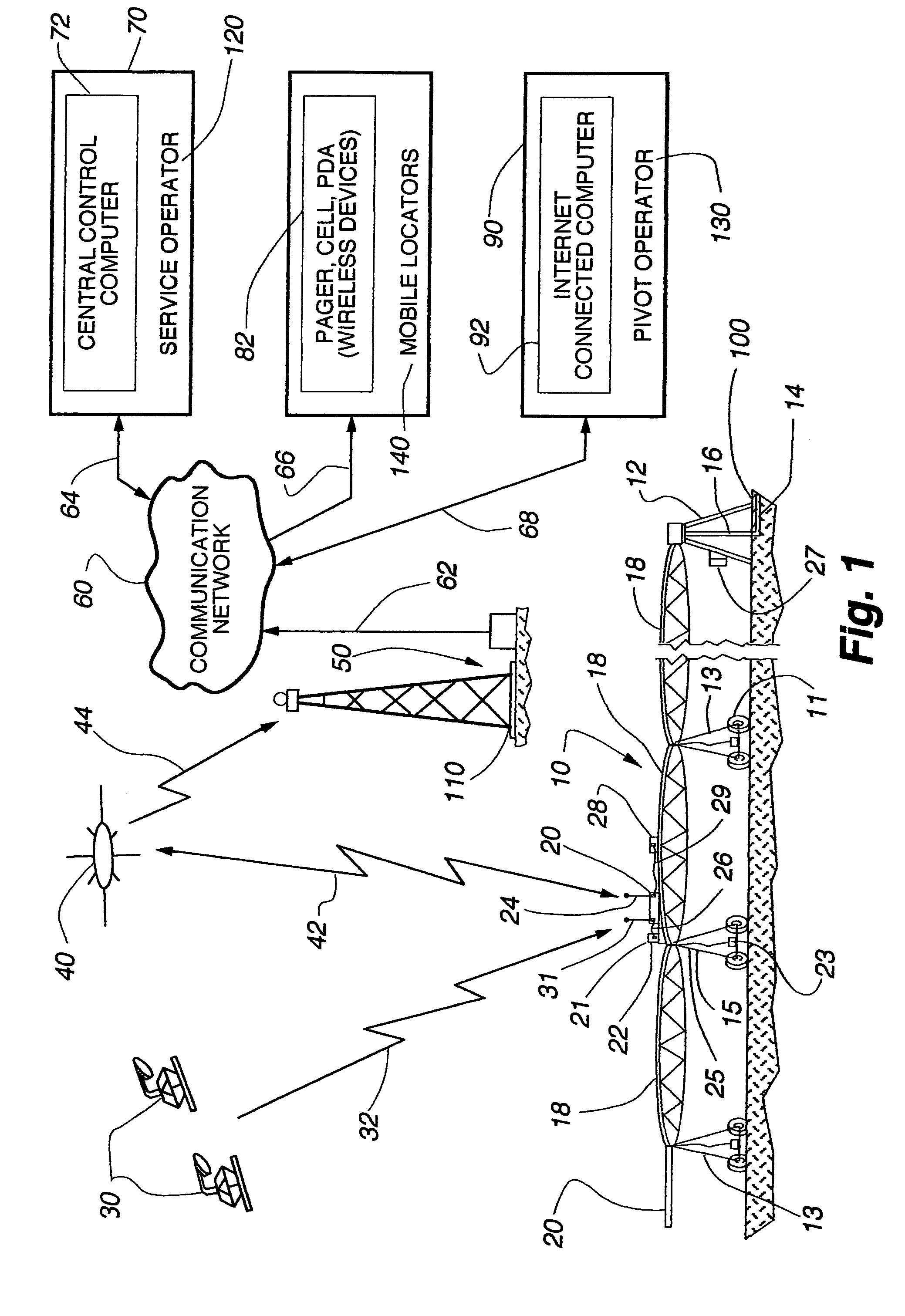
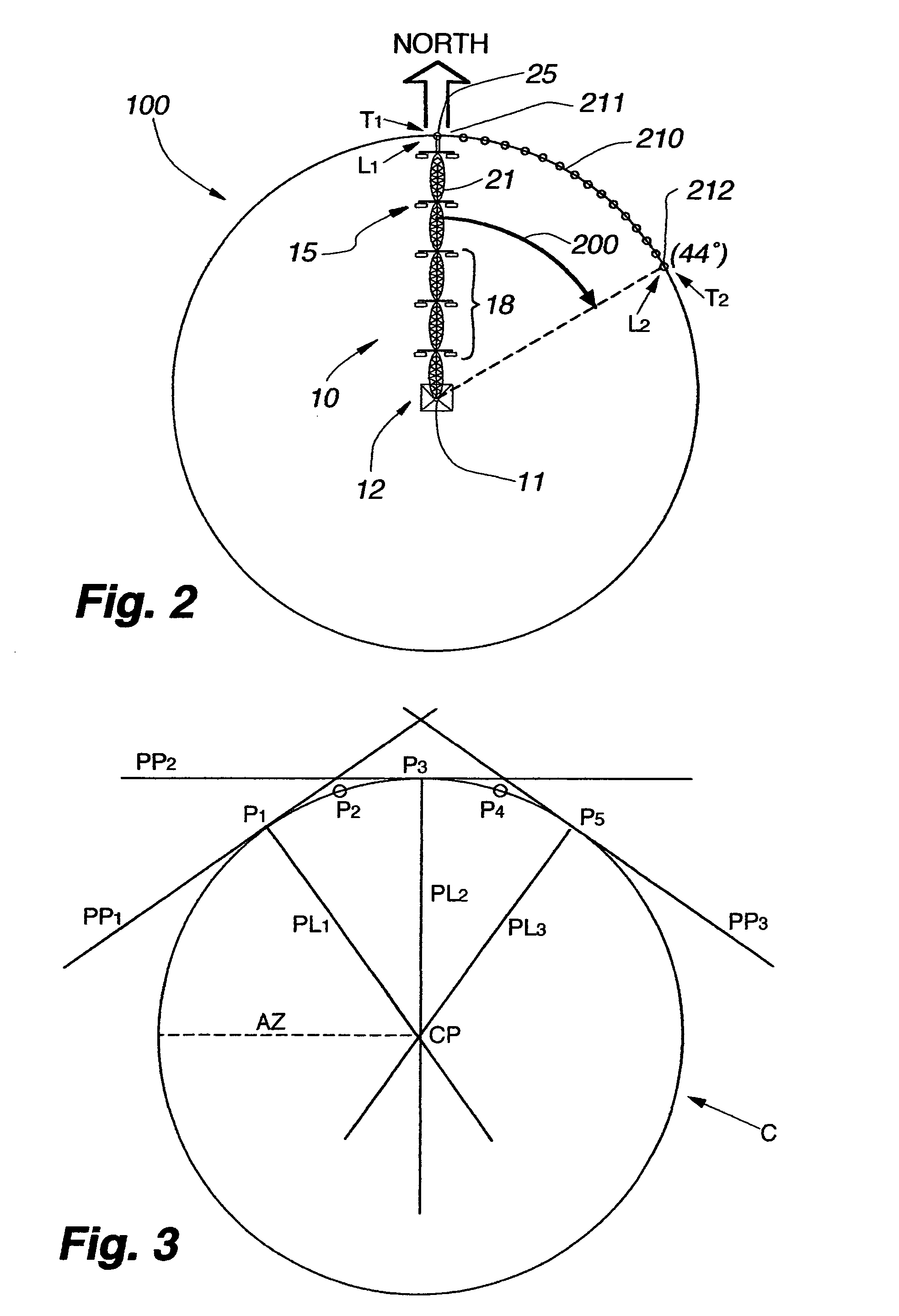
Universal remote terminal unit and method for tracking the position of self-propelled irrigation systems
ActiveUS7584053B2Readily availableEliminate needSelf-acting watering devicesWatering devicesTerminal unitGlobal Positioning System
Owner:HAALAND KARLYLE
Using voice over IP or instant messaging to connect to customer products
ActiveUS7734909B1Minimize blockingEasy to implementDigital data processing detailsMultiple digital computer combinationsServices computingVoice over IP
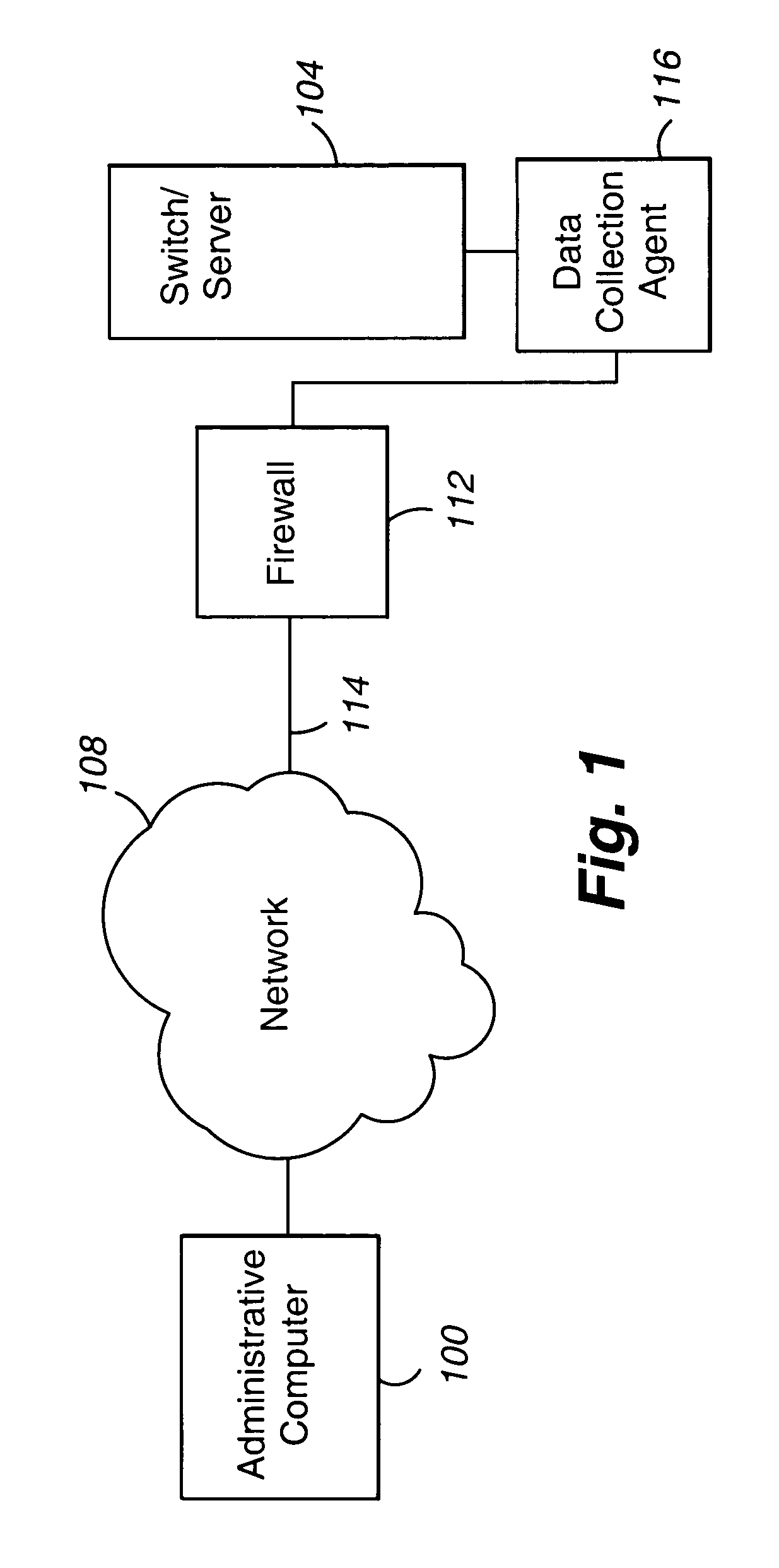
A system for remotely servicing a computational component is provided that includes:(a) a firewall 112; (b) a computational component 104 requiring servicing, the firewall 112 analyzing communications to the computational component 104; (c) a data collection agent 116 operable to (i) establish a session with a servicing computational component 100, packets of the session being analyzed by the firewall 112 and the session being of a type permitted by the firewall 112, (ii) receive a packet associated with the session, the packet comprising a machine executable servicing command for the computational component 104, and (iii) forward the servicing command to the computational component 104.
Owner:AVAYA INC
Method, system and program products for managing thread pools of a computing environment to avoid deadlock situations by dynamically altering eligible thread pools
InactiveUS6898617B2Prevent deadlock situationResource allocationMultiple digital computer combinationsServices computingClient-side
Deadlock situations within a computing environment are avoided by properly managing pools of threads used to service requests of the computing environment. When a server of the computing environment receives a request to be processed and that request is waiting on a response from a client of the computing environment, the set of eligible thread pools for the response is dynamically altered. This dynamic altering allows the response to be serviced by a thread pool different from the thread pool servicing the request, thereby avoiding a deadlock situation.
Owner:DAEDALUS BLUE LLC
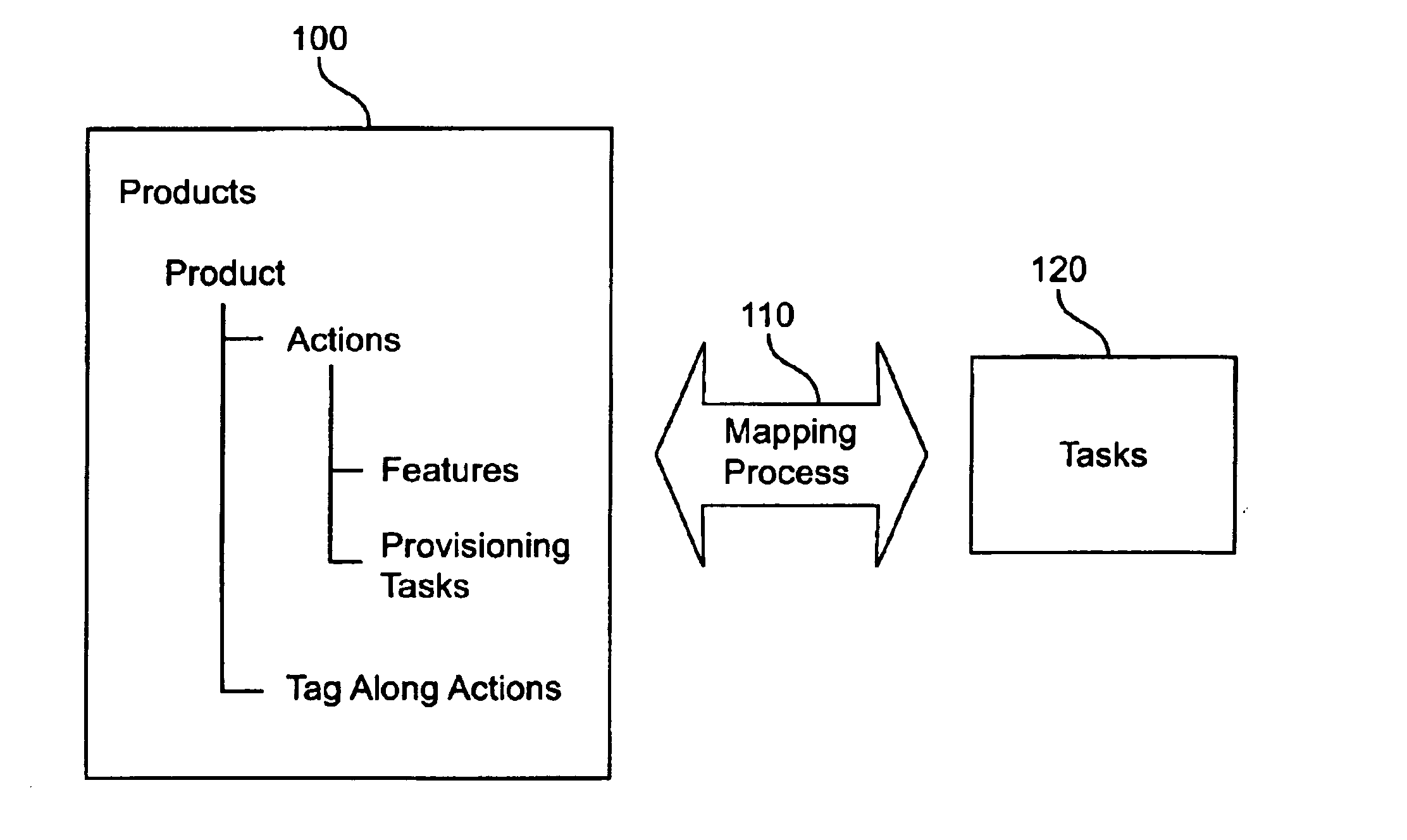
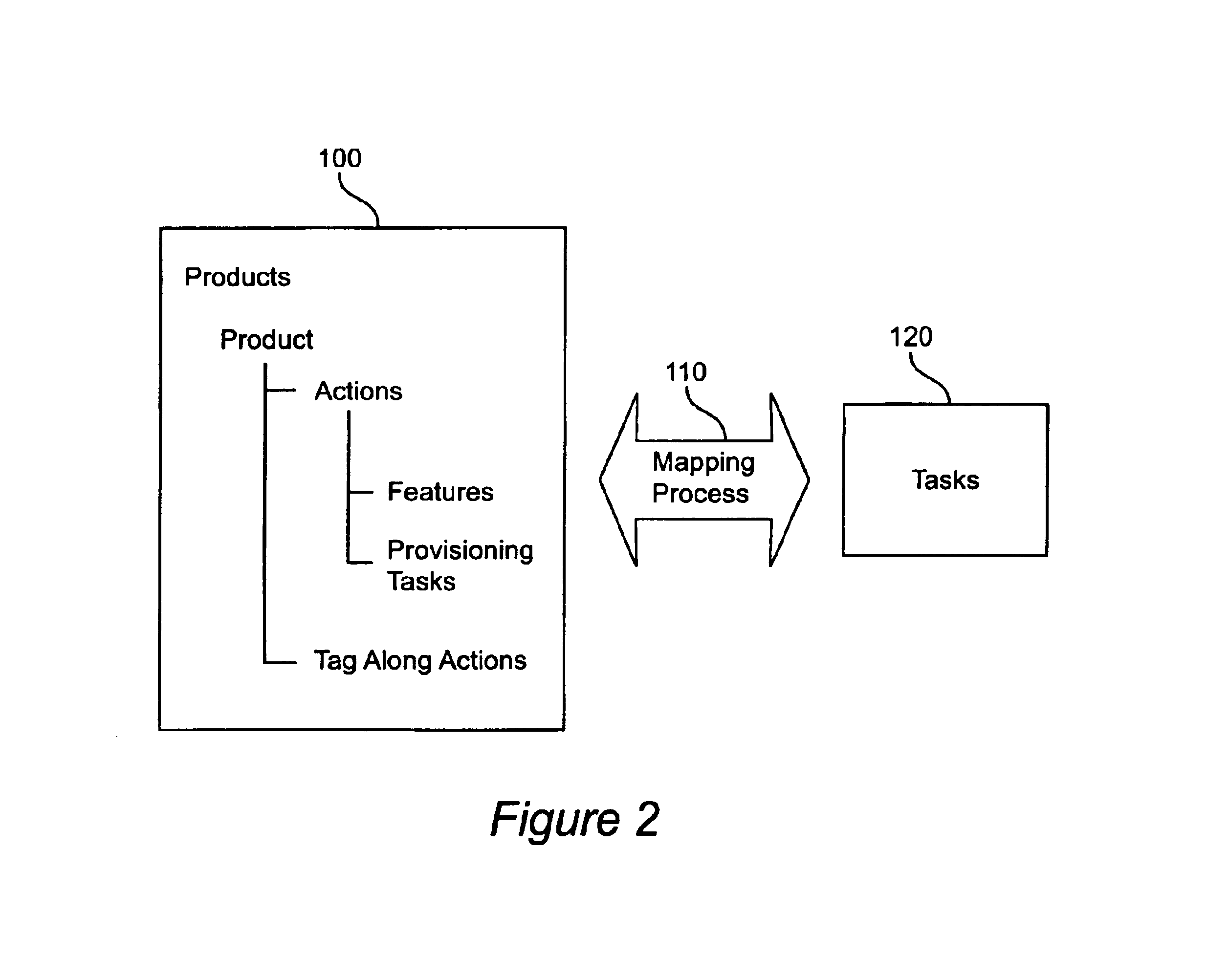
Mapping actions to tasks within customer service processing systems
Methods and apparatus for mapping an action, occurring within a customer servicing computer system, from a meta-level domain to tasks within a system-level domain are described. The actions are defined to have a plurality of data-fields, each of which has attributes. For a subset of the meta-data fields, and for each field within the subset, the mapper key is formed from a portion of the attributes. Each mapper key is compared with a set of task templates. The task templates define a sequence of system-level domain tasks. If there is a match of all the mapper keys with a respective template, then a system-level domain task sequence is formed to give effect to the action as the collective tasks of all task templates.
Owner:IBM CORP
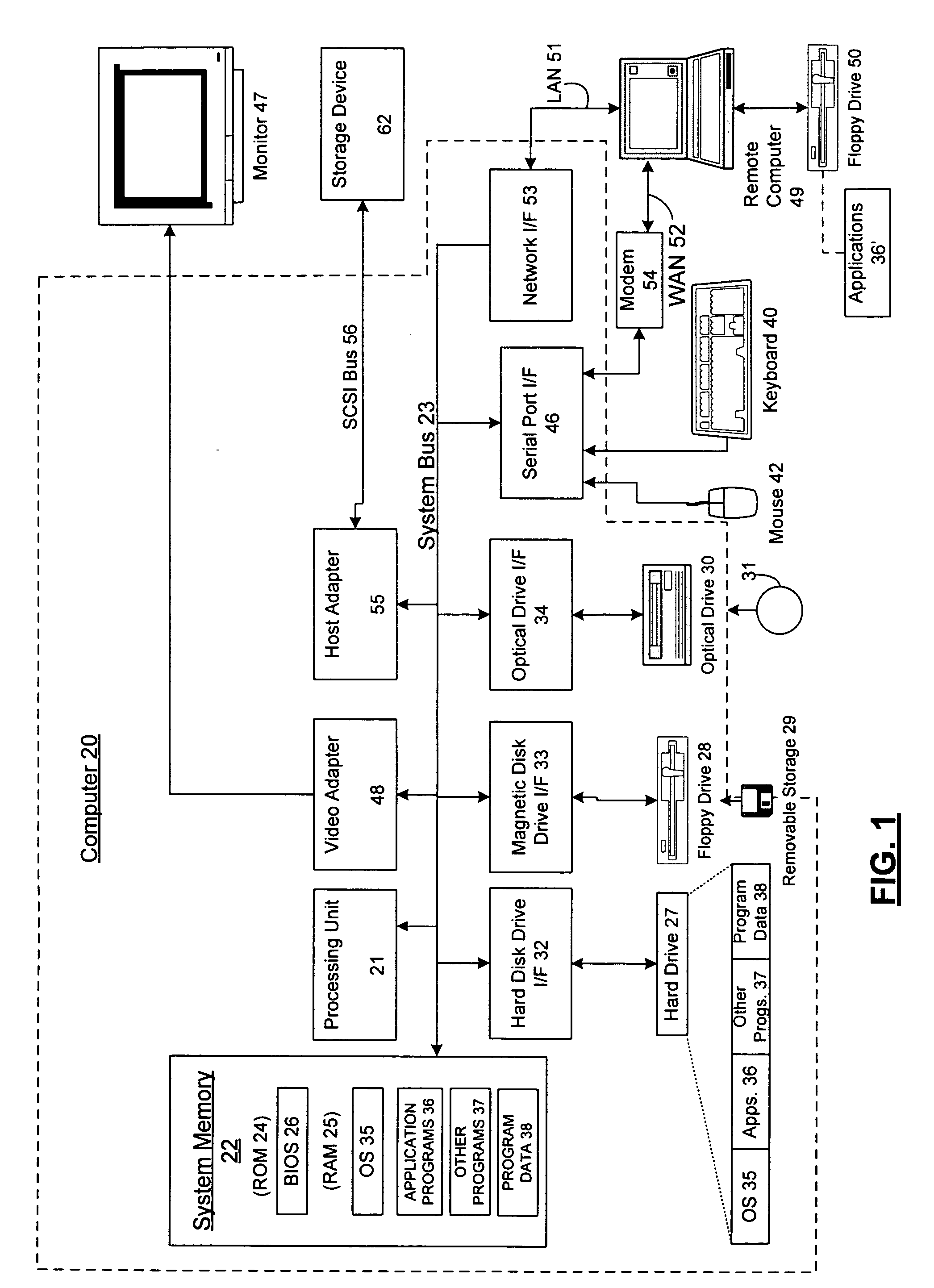
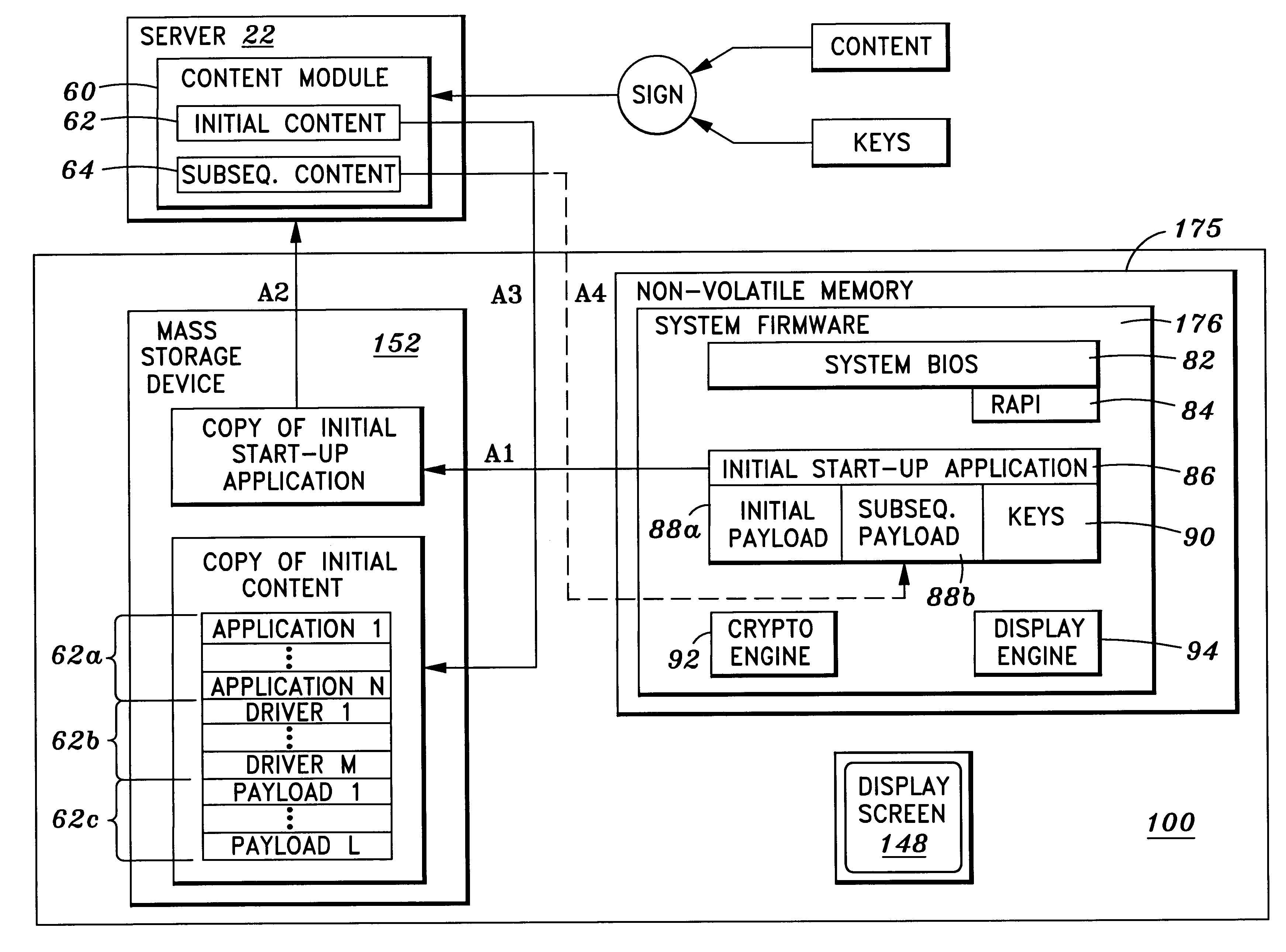
Method and system for transferring an application program from system firmware to a storage device
InactiveUS6519659B1Program control using stored programsDigital computer detailsSequence processingOperational system
One aspect of the invention is a method and system for accessing at least one storage element in a processor-based system. The system comprises a memory for storing instruction sequences by which the processor-based system is processed. The memory has at least one storage element. A processor is coupled to the memory, and a storage device is coupled to the processor. Prior to booting an operating system on the processor-based system, the stored instruction sequences cause the processor to write the contents of the at least one storage element to the storage device. Another aspect of the invention relates to a computer system having a user computer in communication with a remote service computer. The remote service computer has access to a database identifying information available to the service computer. A computer implemented method for transferring information to the user computer, comprises: writing the contents of at least one storage element to a storage device on the user computer prior to booting an operating system on the user computer, establishing a communications link between the user computer and the service computer, and presenting at the user computer, information available to the user computer.
Owner:KINGLITE HLDG INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com