Patents
Literature
699 results about "Node clustering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
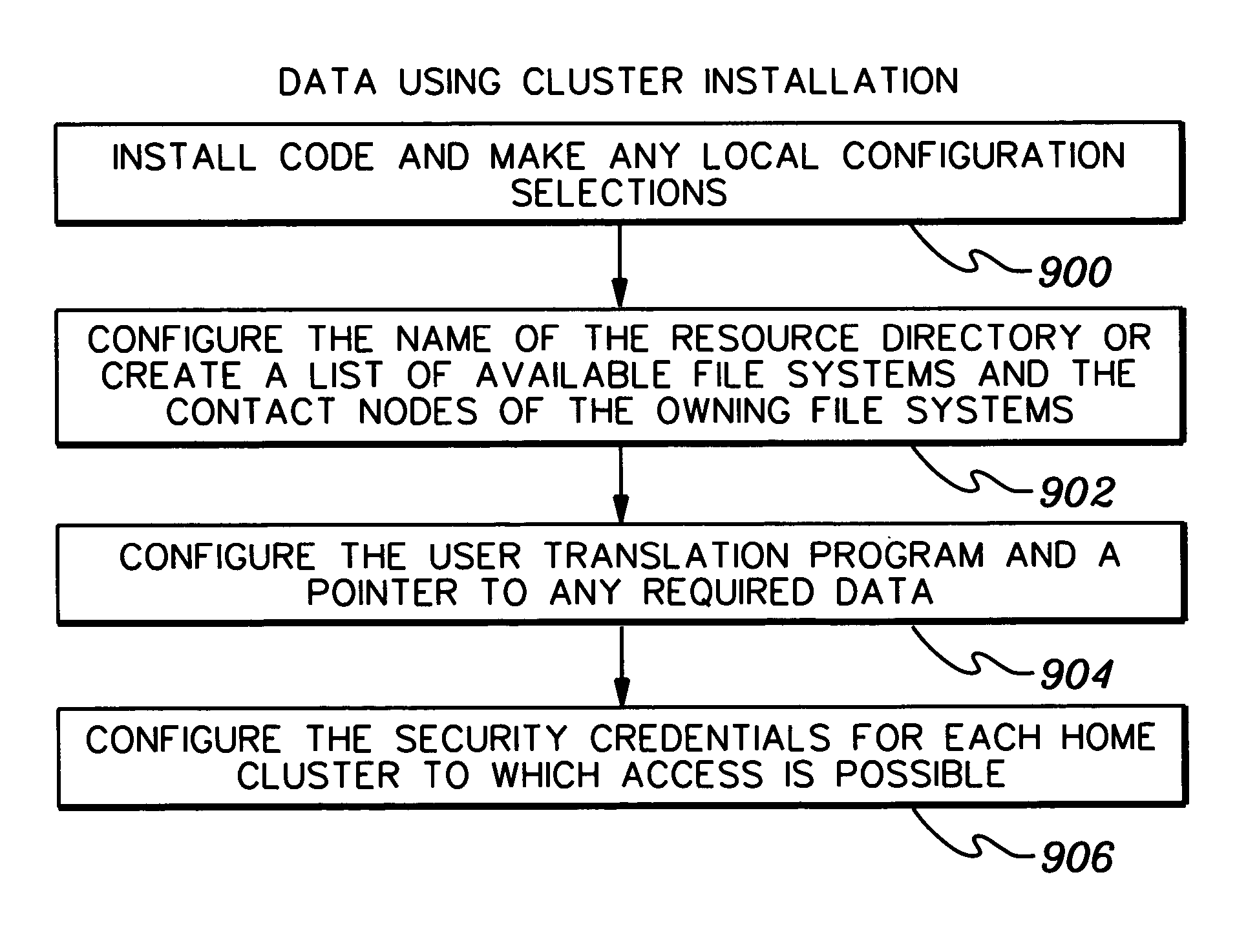
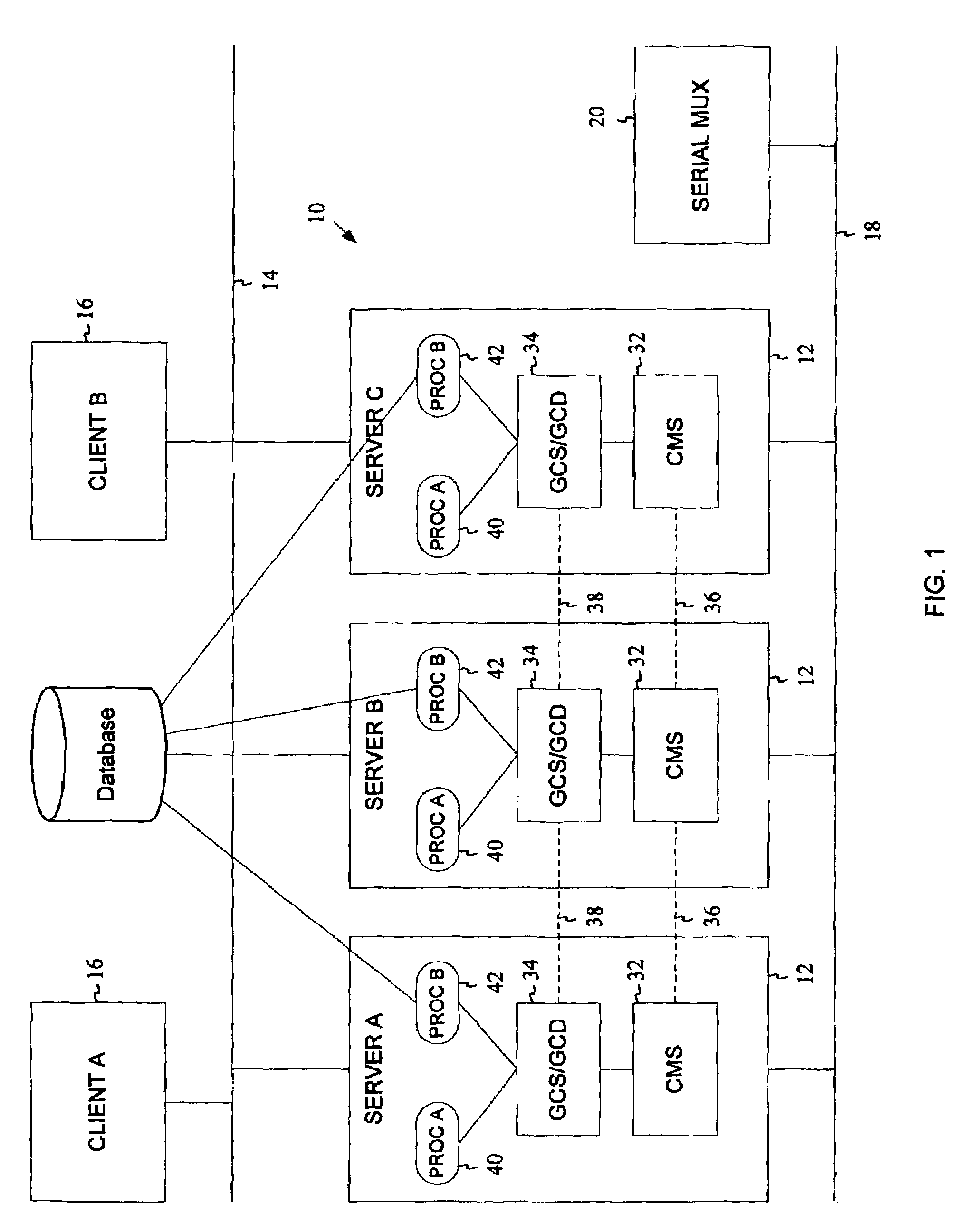
Dynamic management of node clusters to enable data sharing
InactiveUS20060074940A1Digital data information retrievalDigital data processing detailsNode clusteringDynamic management
Owner:IBM CORP
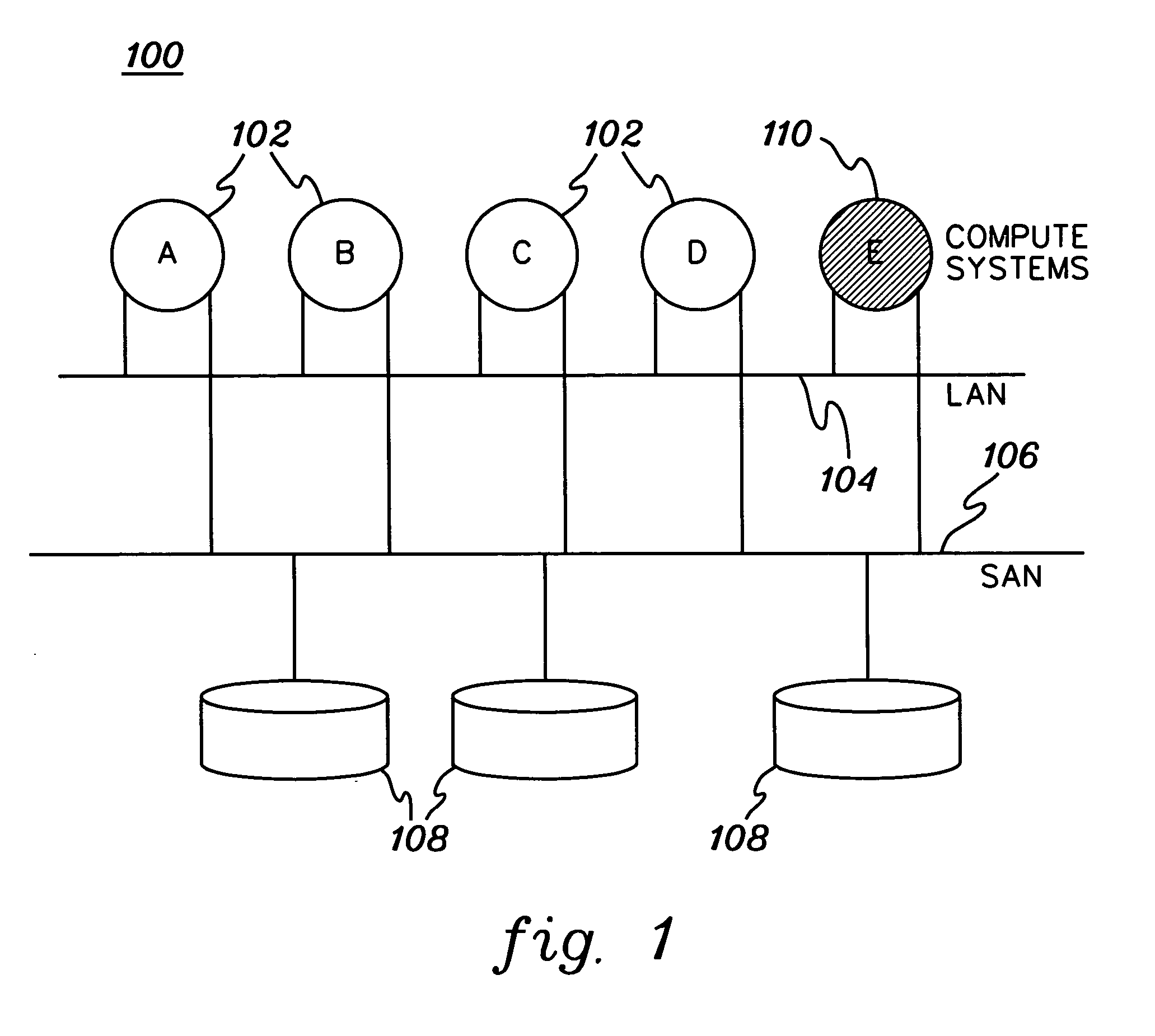
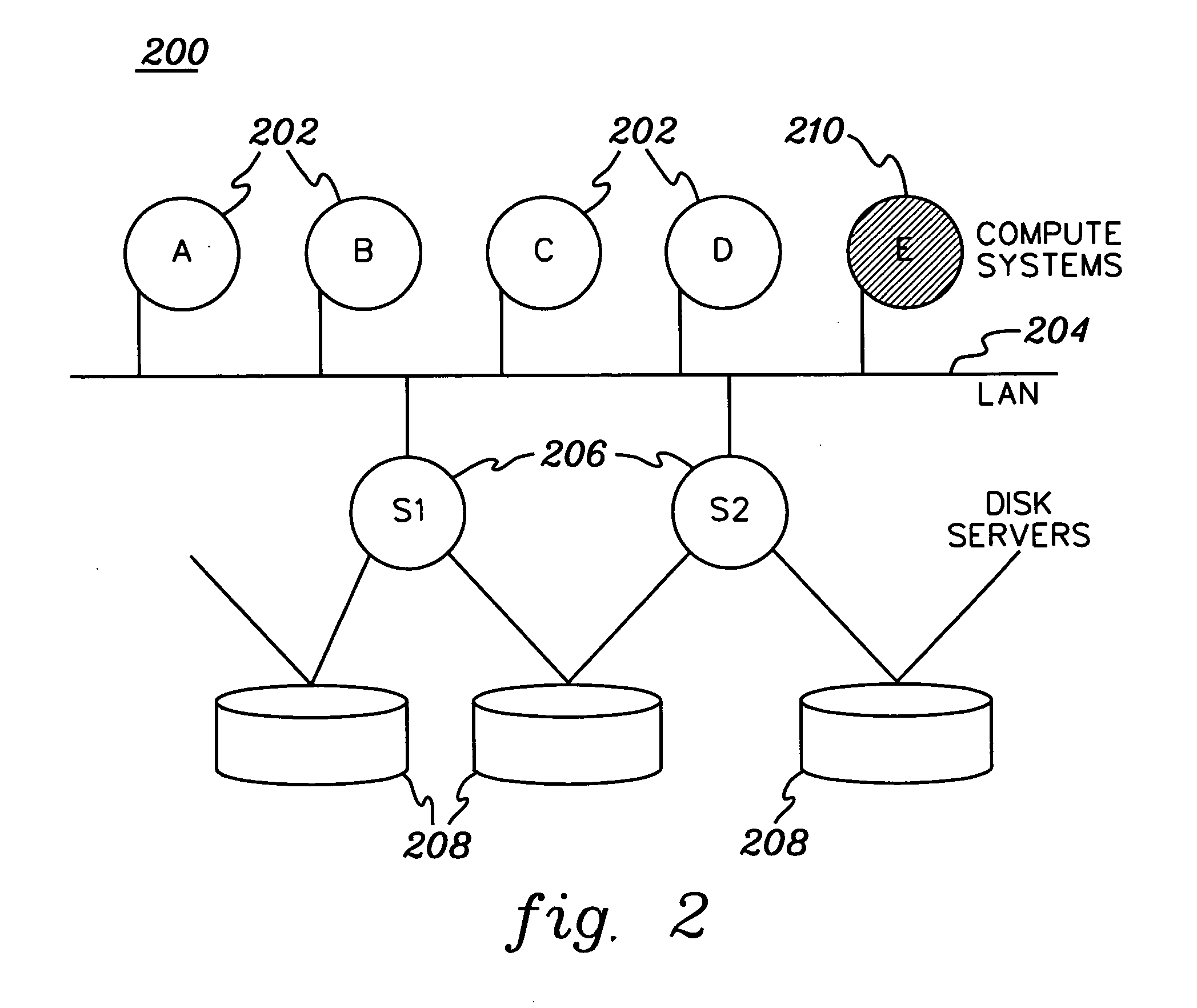
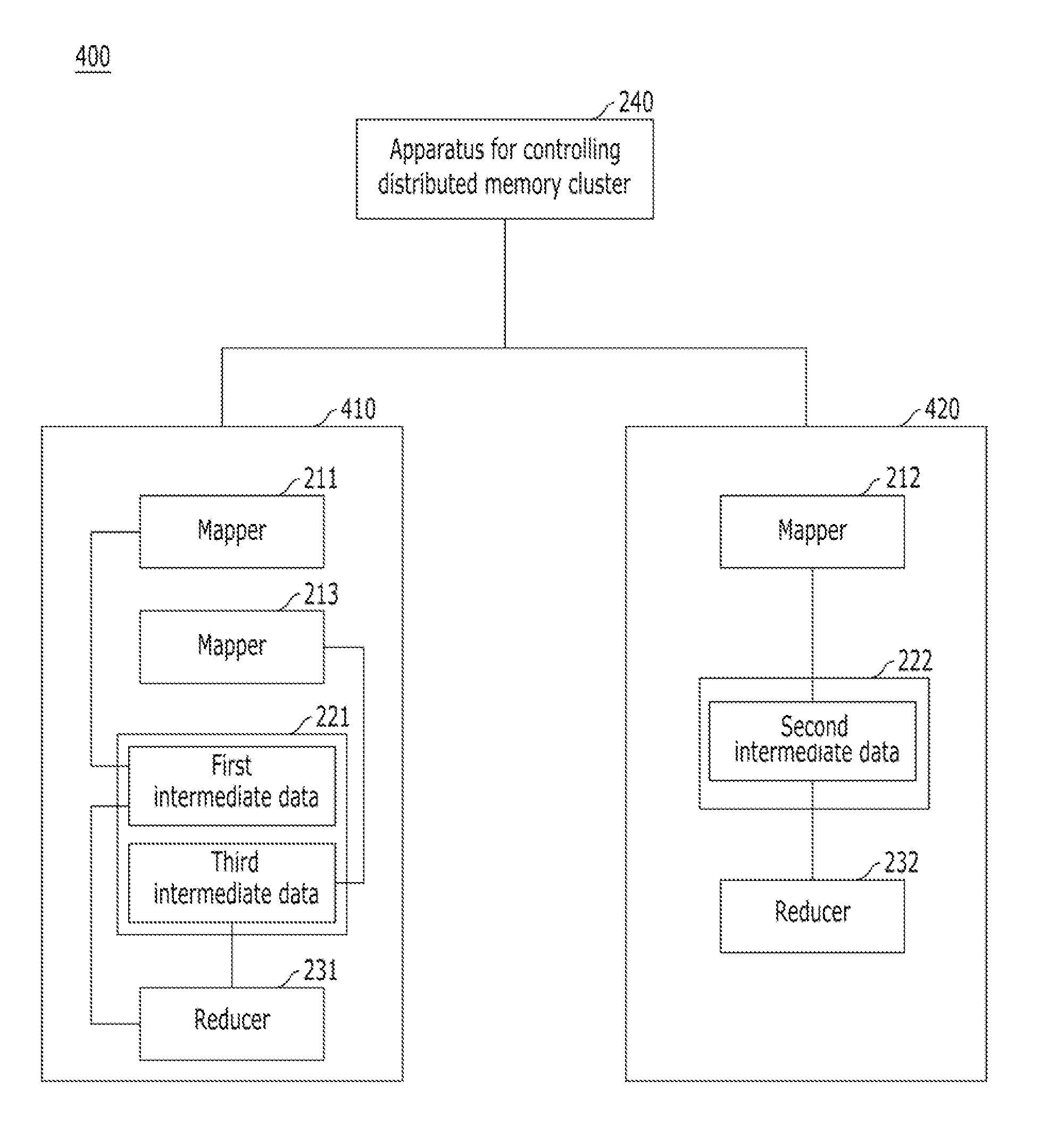
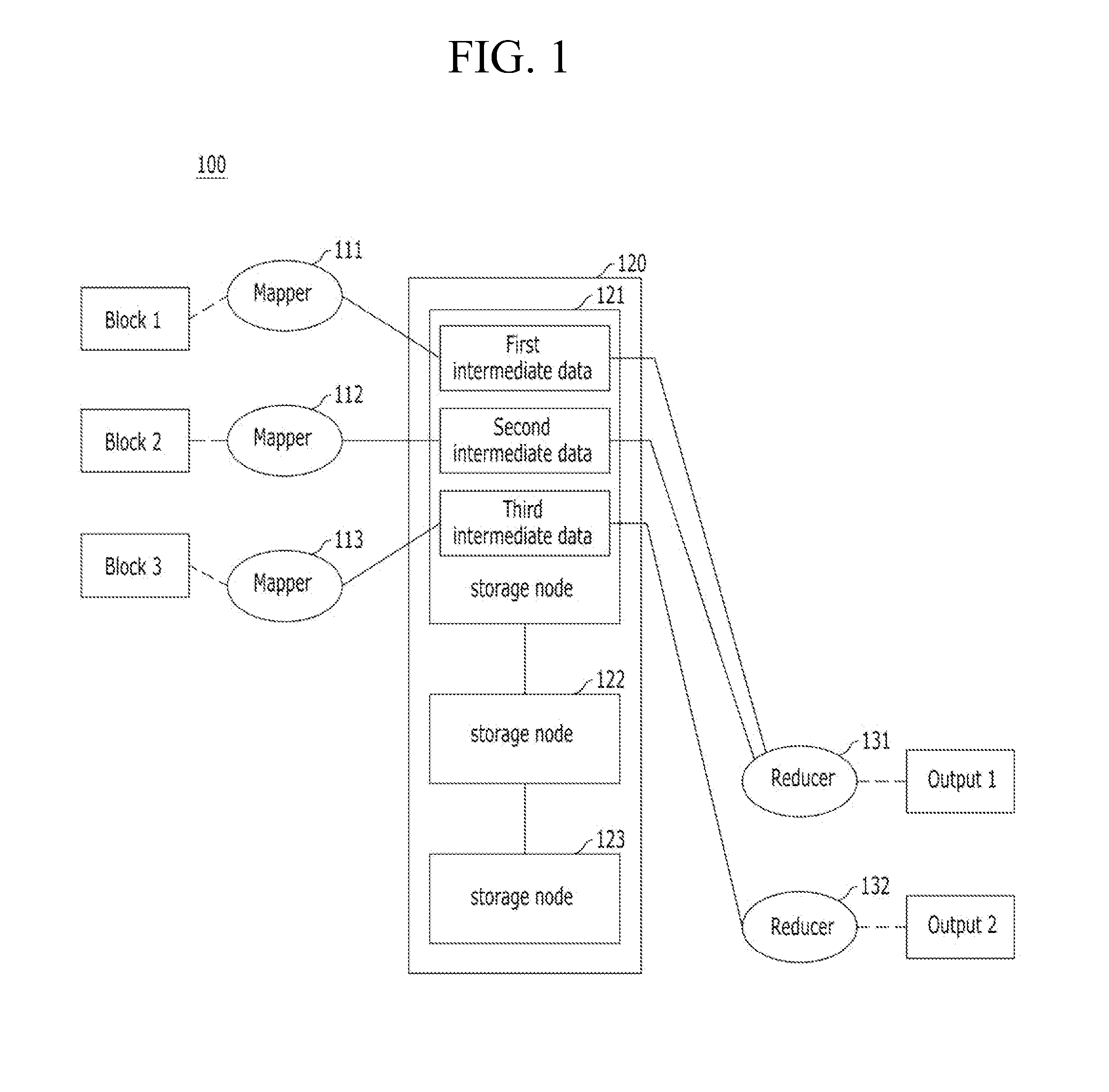
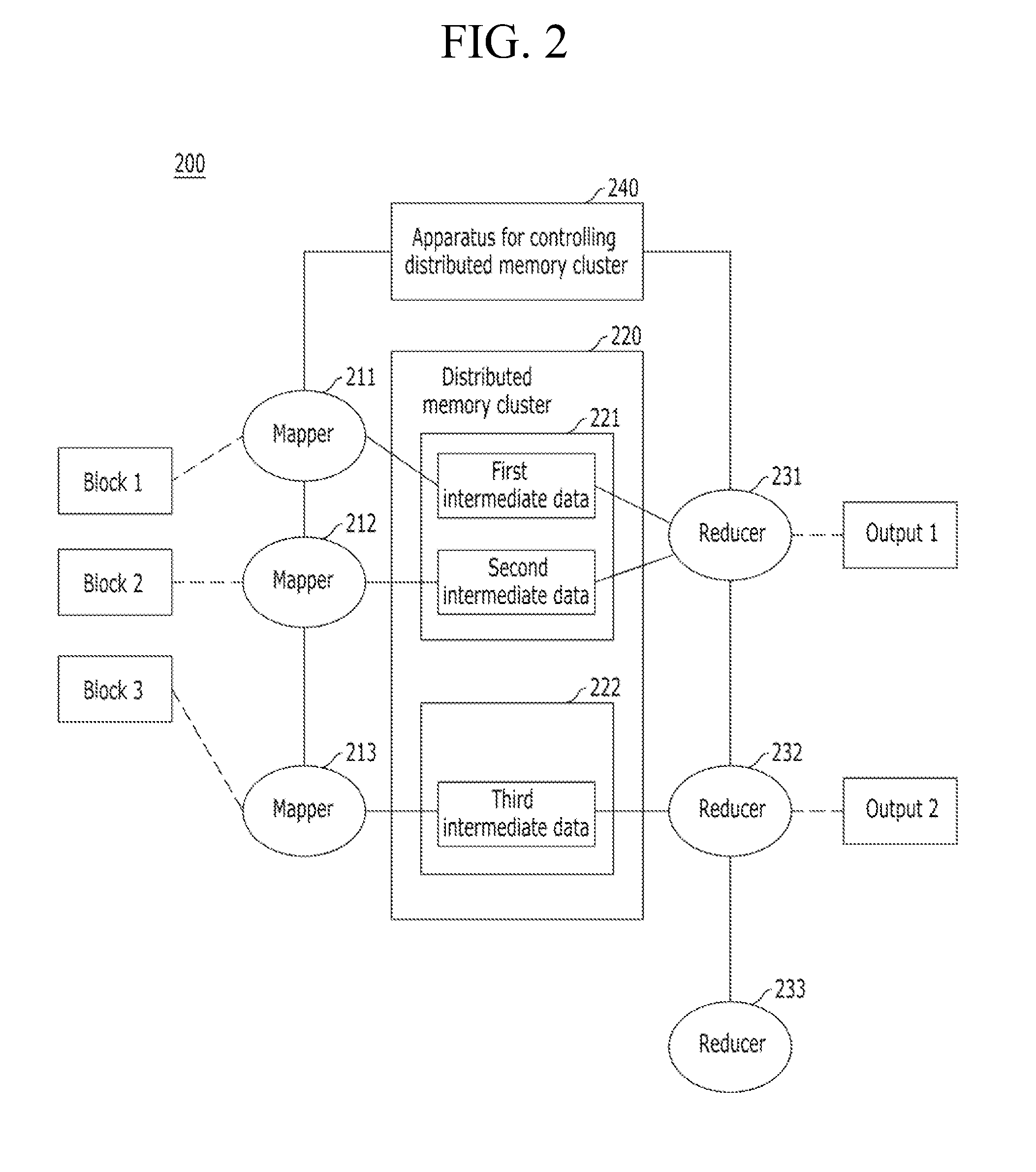
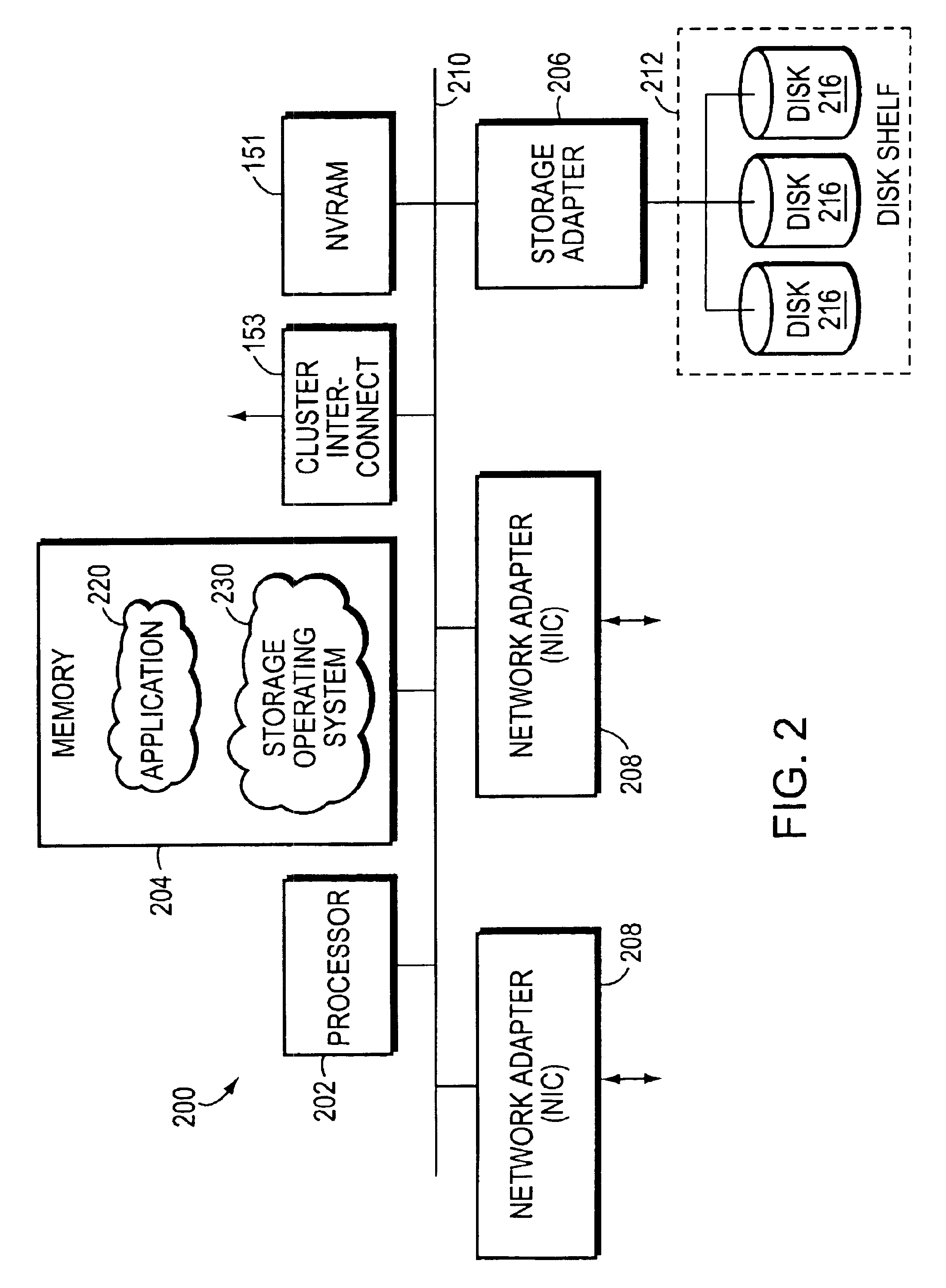
Apparatus and method for controlling distributed memory cluster
ActiveUS20120209943A1Valid choiceMemory adressing/allocation/relocationDigital computer detailsNode clusteringDistributed memory
Provided are an apparatus and method for controlling a distributed memory cluster. A distributed computing system may include a computing node cluster, a distributed memory cluster, and a controlling node. The computing node cluster may include a plurality of computing nodes including first computing nodes that each generates associated data. The distributed memory cluster may be configured to store the associated data of the first computing nodes. The controlling node may be configured to select memory blocks of the associated data for distribution on the distributed memory cluster based on a node selection rule and memory cluster structure information, and to select second computing nodes from the computing node cluster based on a location selection rule and the memory cluster structure information.
Owner:KT CORP
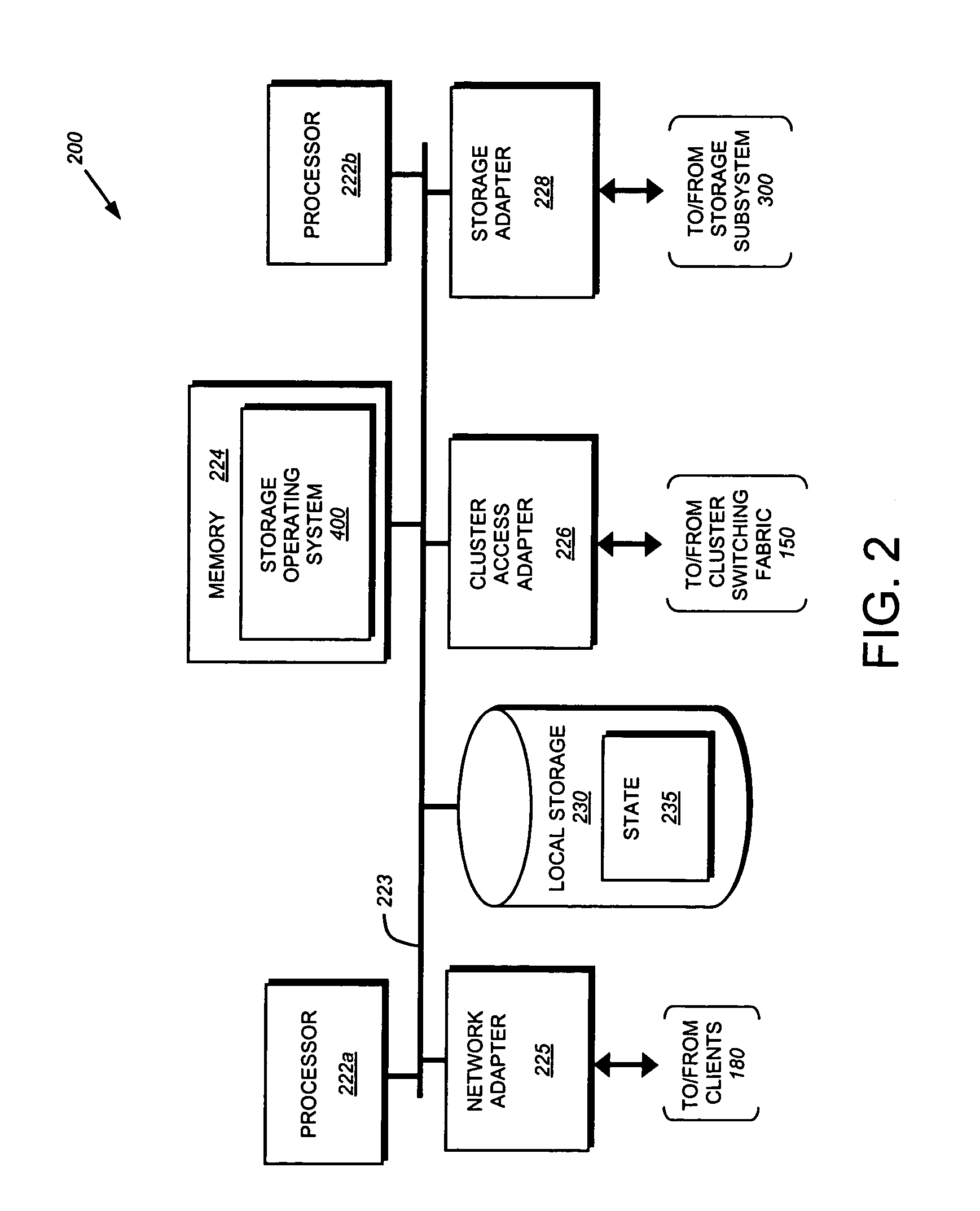
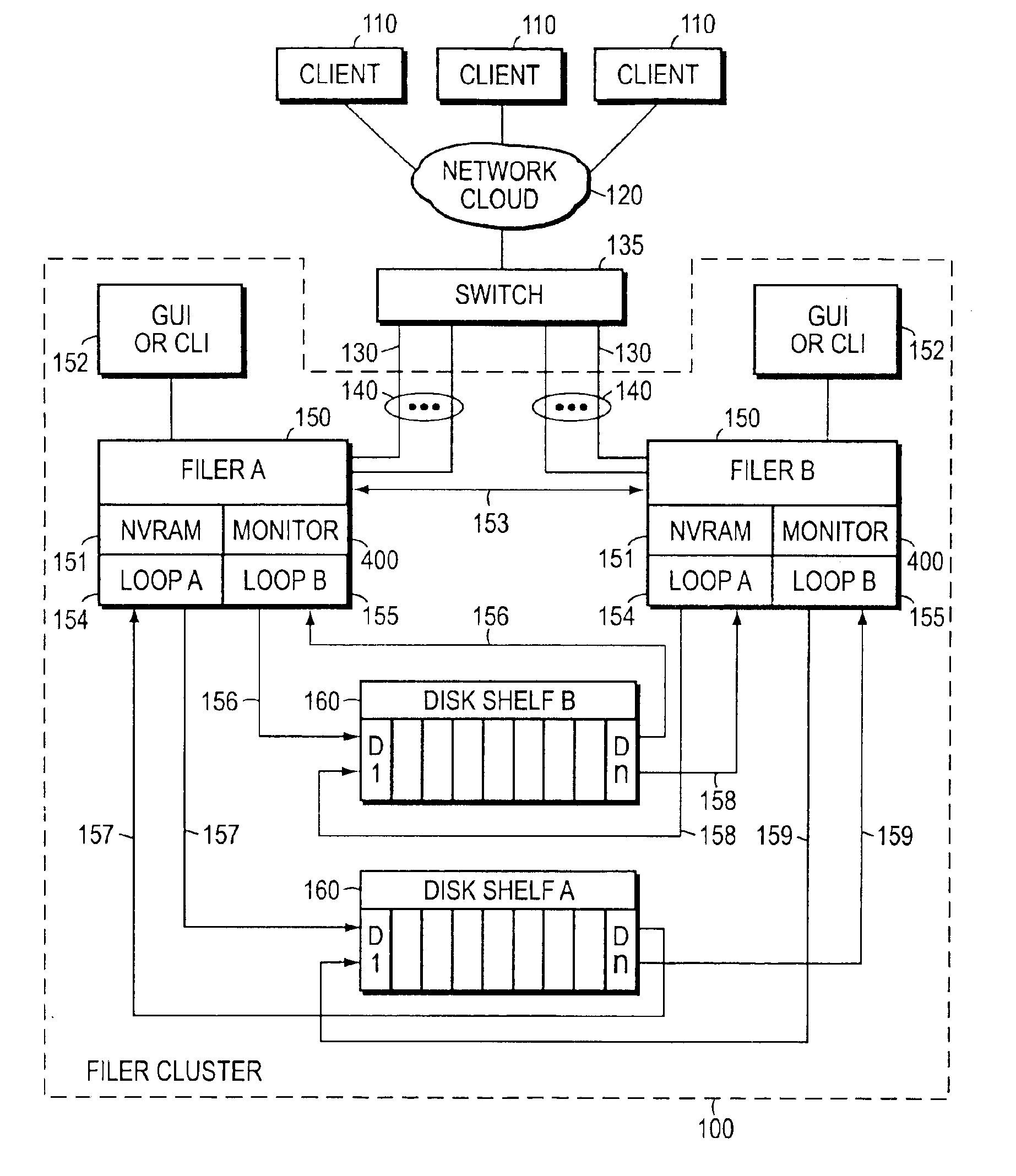
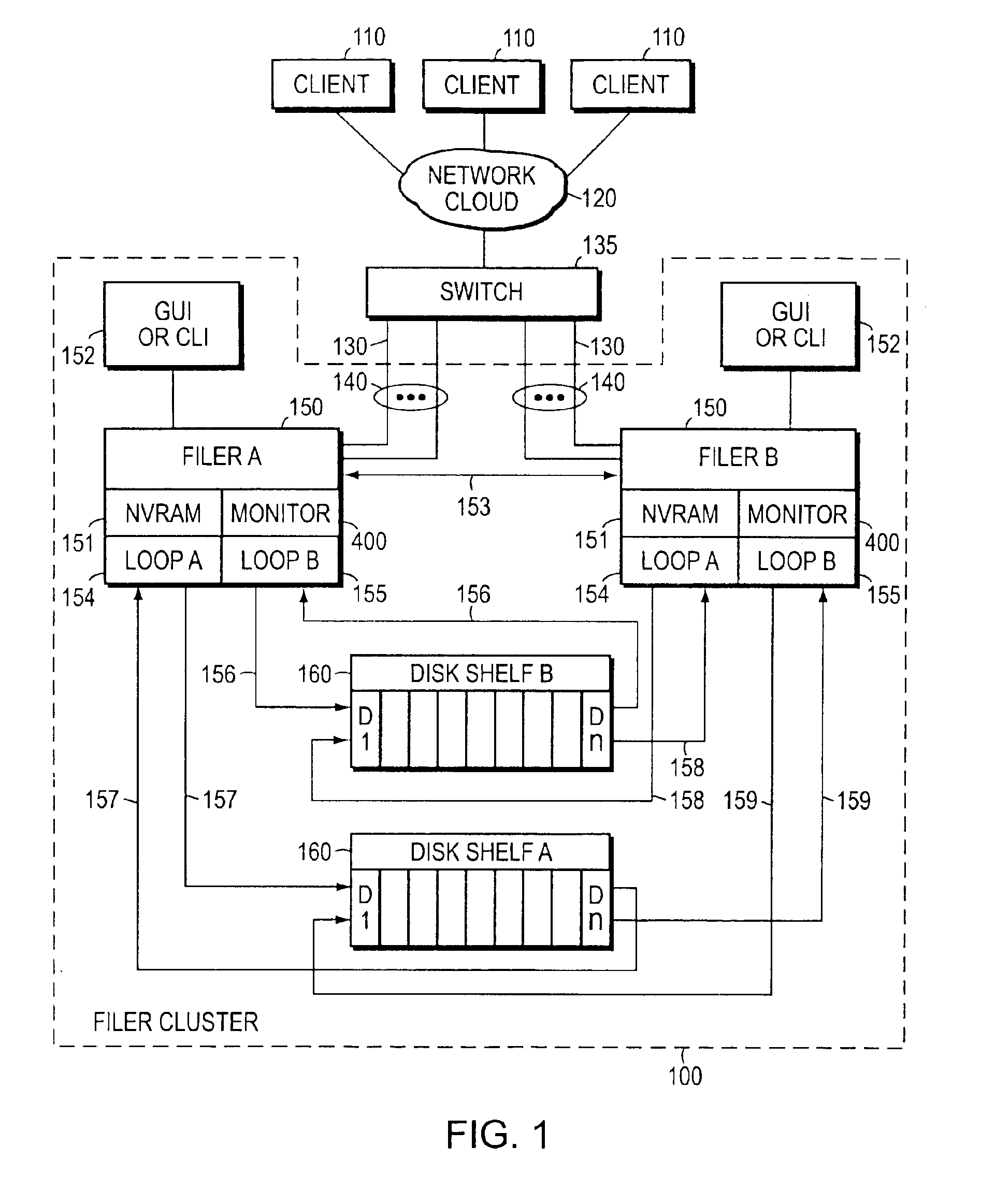
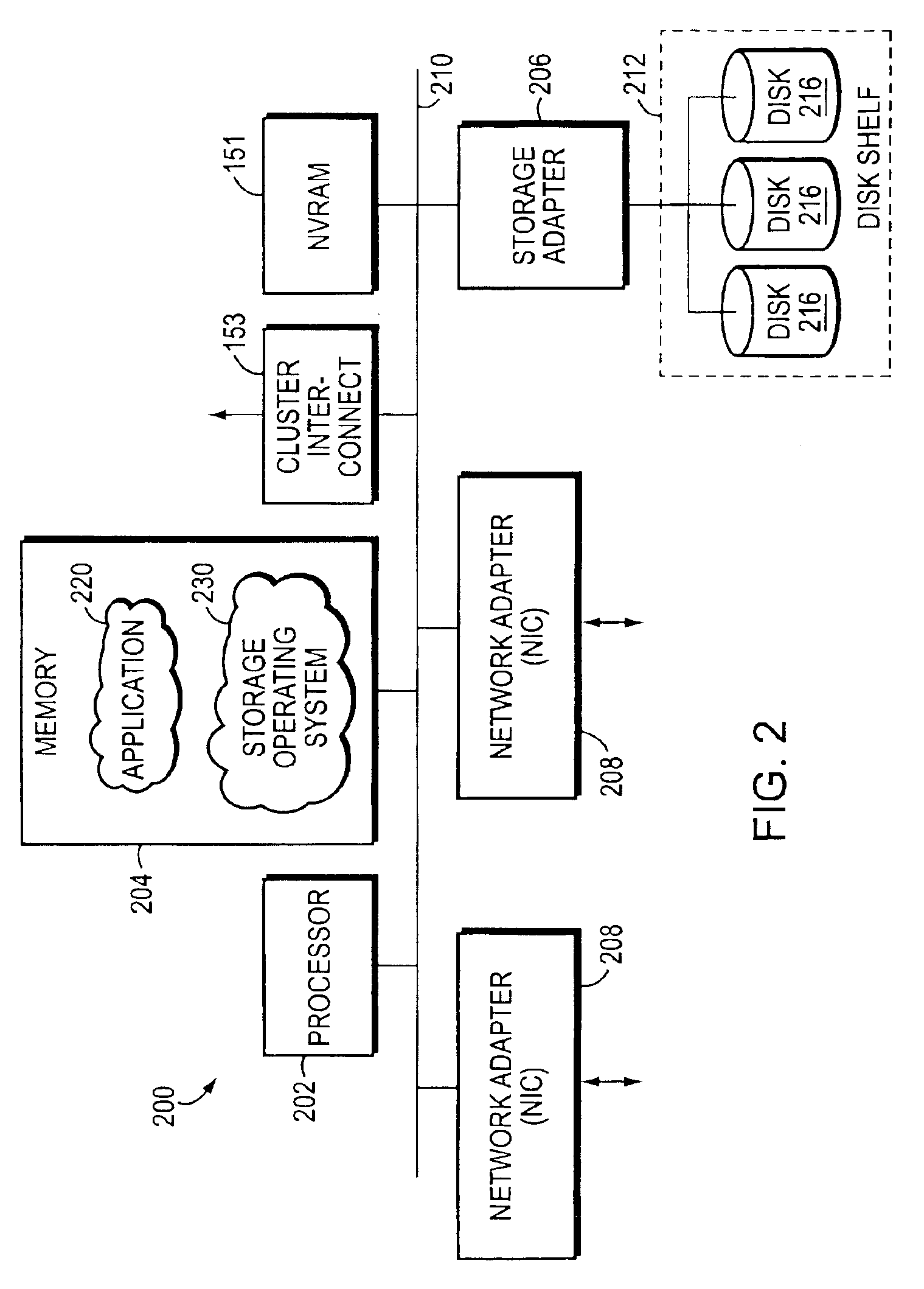
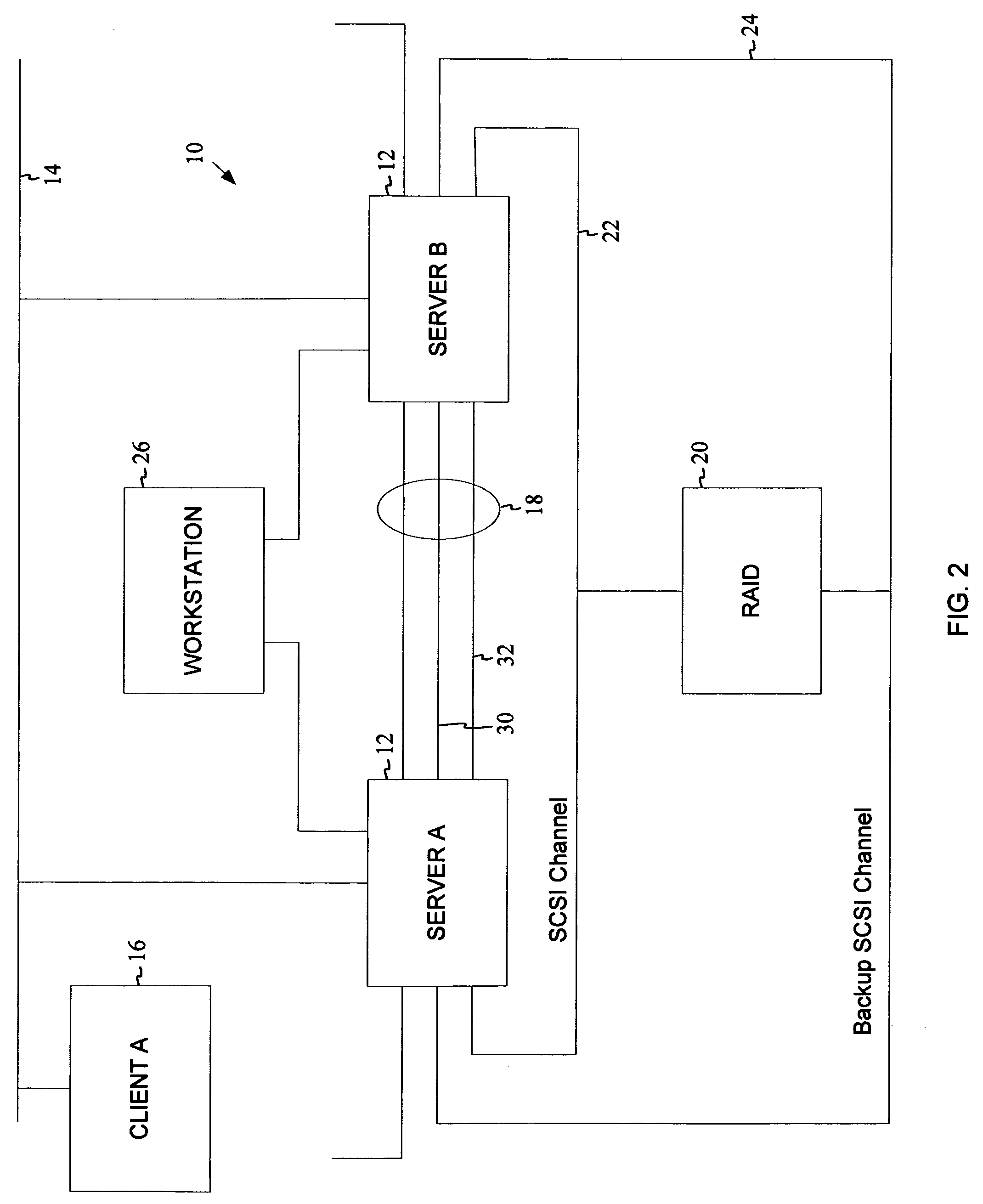
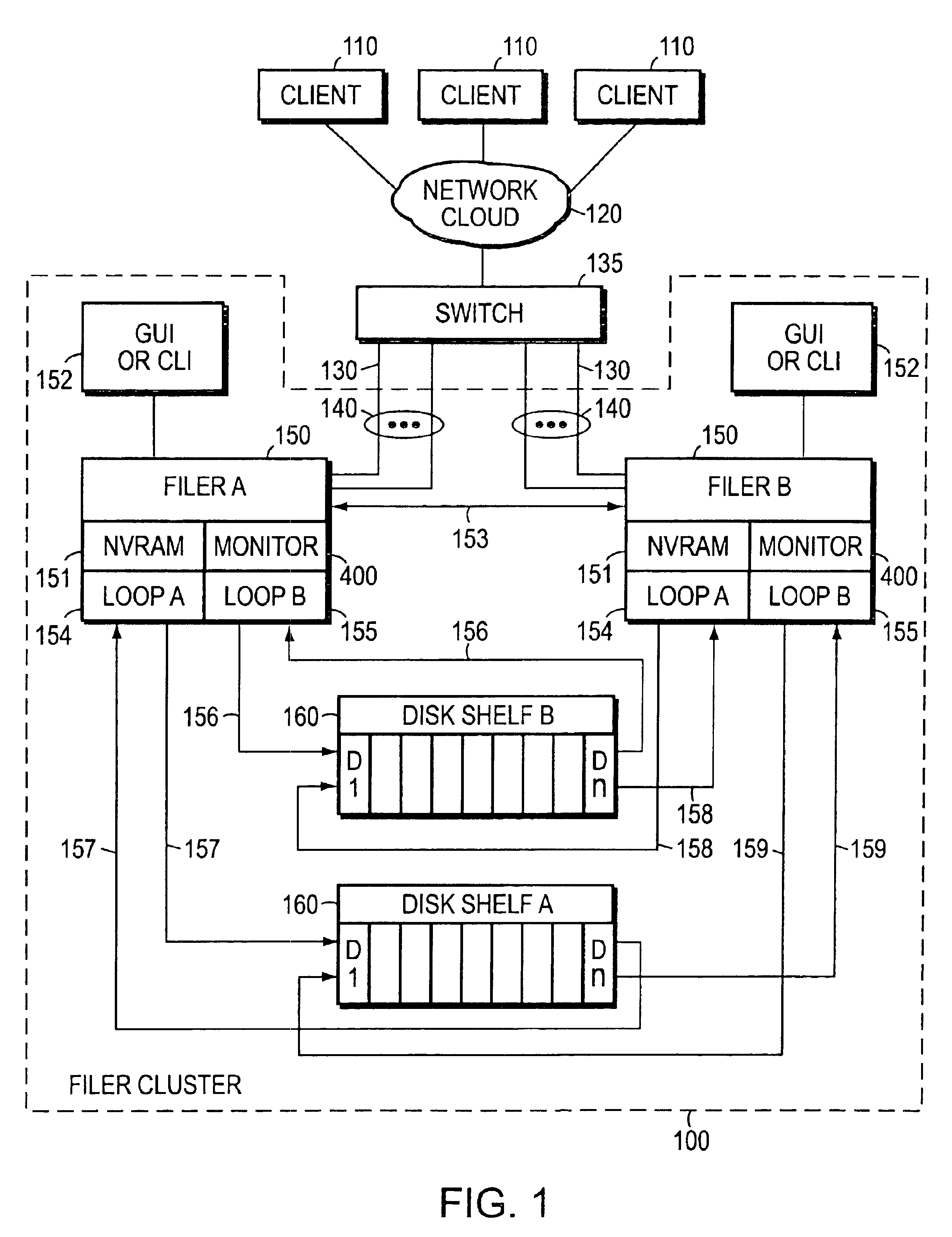
System and method for establishing bi-directional failover in a two node cluster
ActiveUS7478263B1Avoid dataInhibition transitionTransmissionRedundant hardware error correctionNode clusteringFailover
Owner:NETWORK APPLIANCE INC
Negotiated graceful takeover in a node cluster
InactiveUS6920580B1Minimizes problemRedundant hardware error correctionNode clusteringNetwork addressing
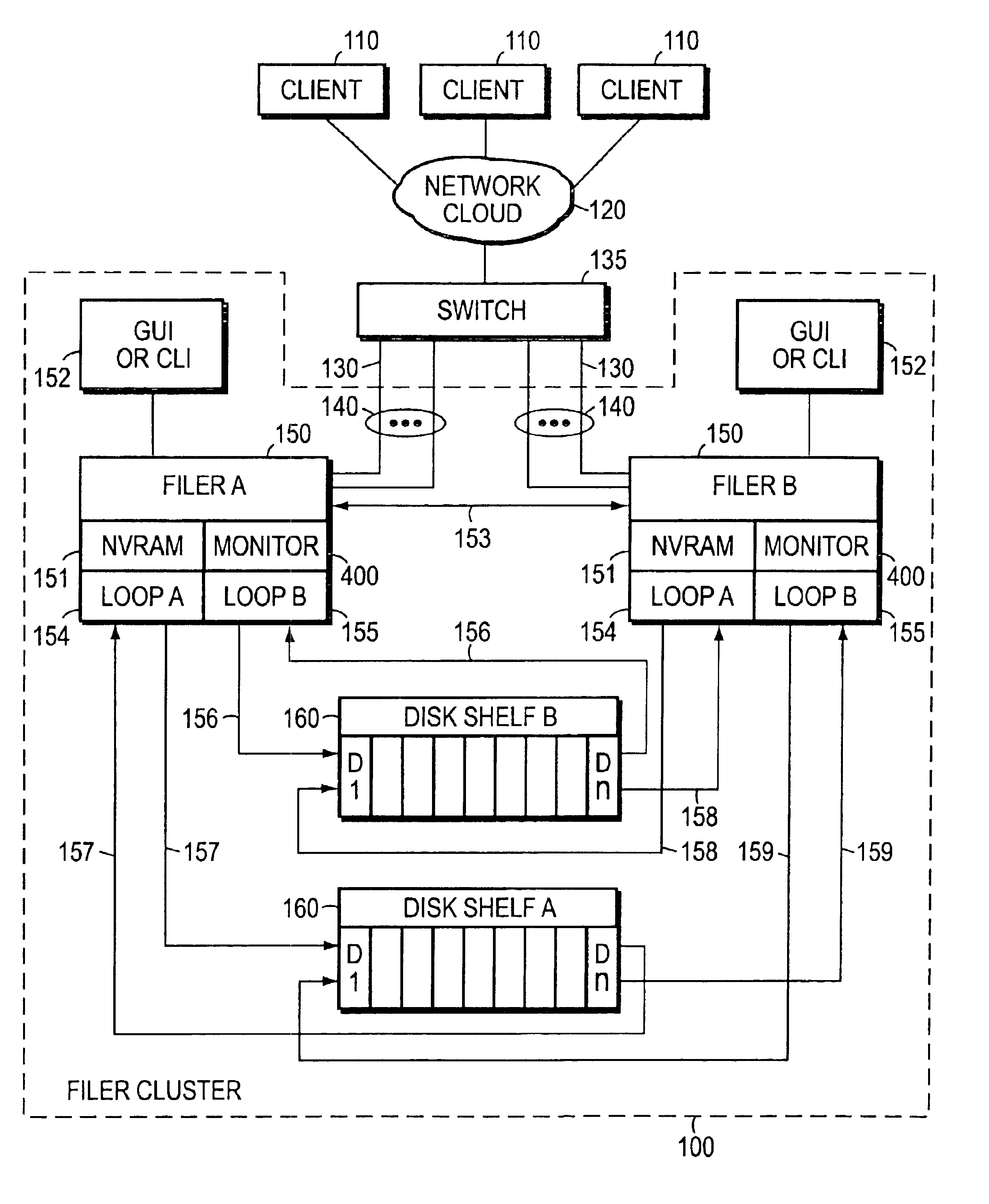
The invention is a method for operating a file server system in a cluster mode that provides for relatively rapid and reliable takeover of a failed file server in the cluster by a partner file server when the failed file server has detected a fault that will cause it to shut down. This is done by the failed file server requesting the one file server to take over its file services after detecting the fault in its operations, the one file server letting the failed file server complete existing file service requests from clients, refusing further file service requests addressed to the failed file server, and the one file server taking over by transferring file service requests to the one file server. As part of this takeover the one file server takes on the identity of the failed filer and activates network interfaces and network addresses that replicate the failed server's network addresses.
Owner:NETWORK APPLIANCE INC
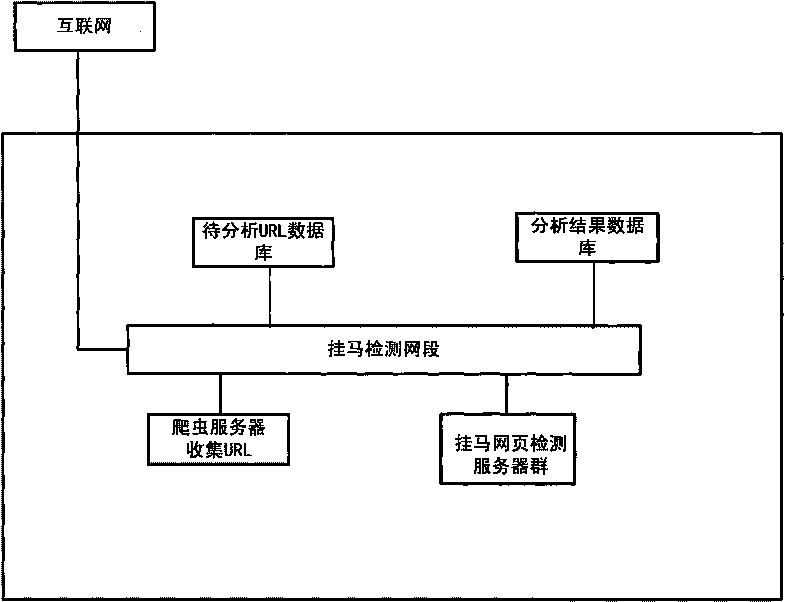
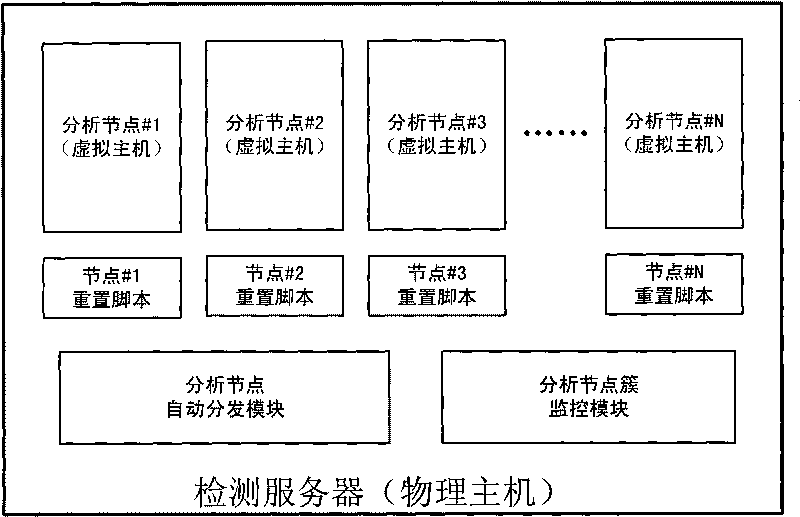
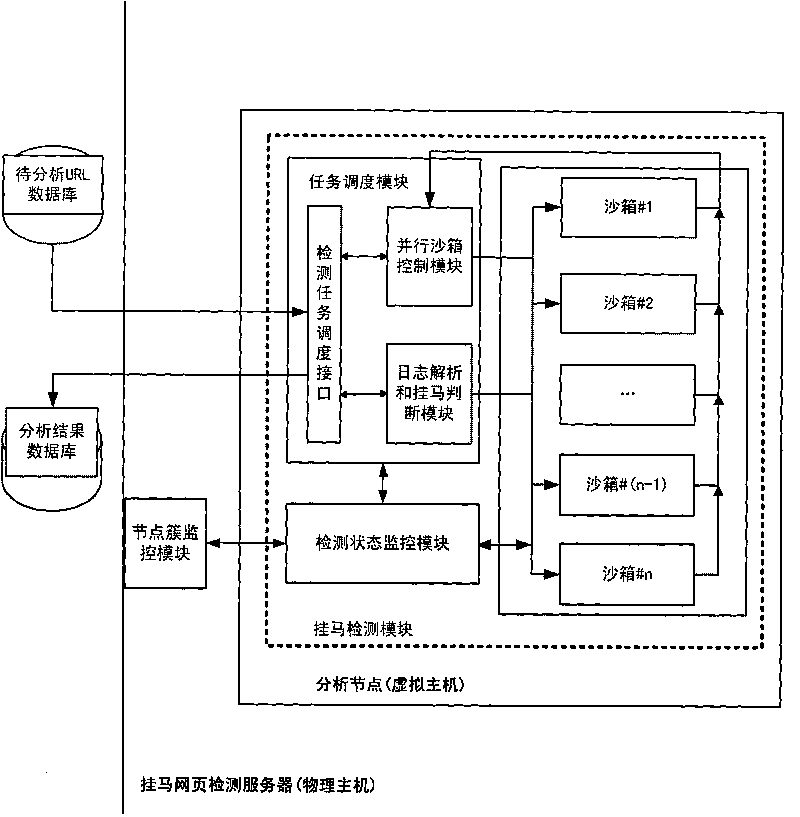
Method and system for detecting large-scale malicious web pages
InactiveCN101692267AWill not affect operationDoes not affect functionalityPlatform integrity maintainanceProgram loading/initiatingSelf maintenanceNode clustering
The invention discloses a method and a system for detecting large-scale malicious web pages by using a three-layer parallel architecture and a layered control guarantee method: in the first layer, a plurality of detection servers interconnected via networks are arranged in parallel, so as to construct a detection server cluster, and a task set to be analyzed is set up on one detection server; in the second layer, a plurality of analysis nodes are arranged in parallel in each detection server, and a node cluster monitoring module is arranged so as to monitor and analyze the operating condition of the nodes; and in the third layer, a sandbox environment is constructed in parallel in each analysis node, so as to achieve the paralleled detection of the task to be analyzed. The architecture of the invention ensures the mutual independence and self-maintenance among the detection servers and among the analysis nodes, the overall operation of the system is free from the dynamic expansion of physical hosts and node numbers, and the overall function thereof is not affected by the invalidity of the single analysis node; and various tasks can be detected in a multi-channel and paralleled manner at the same time in the same node, thereby improving the analysis efficiency of the system.
Owner:PEKING UNIV
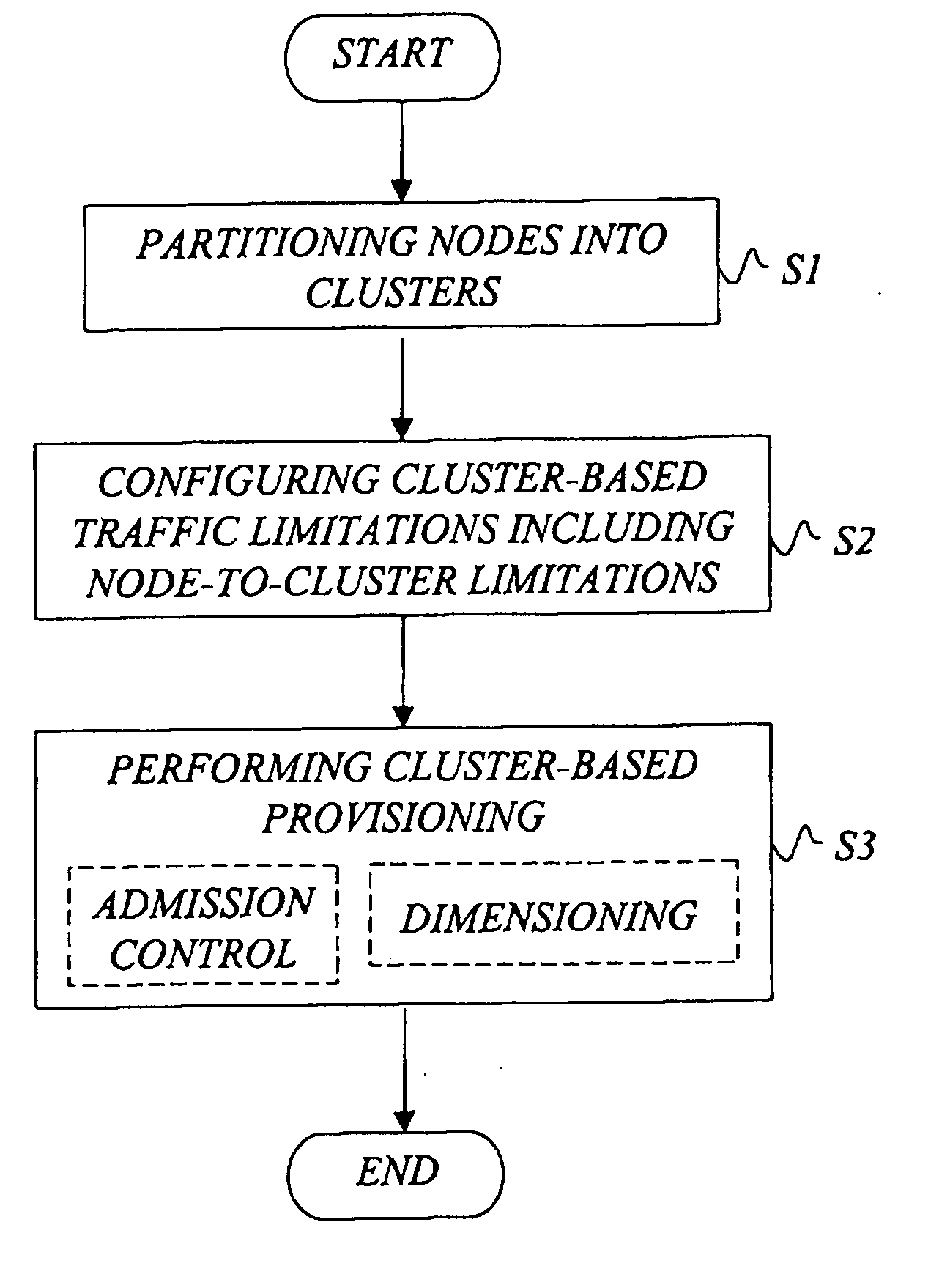
Cluster-based network provisioning
ActiveUS20050169179A1Efficient network operationImprove bandwidth efficiencyError preventionTransmission systemsNode clusteringTrade offs
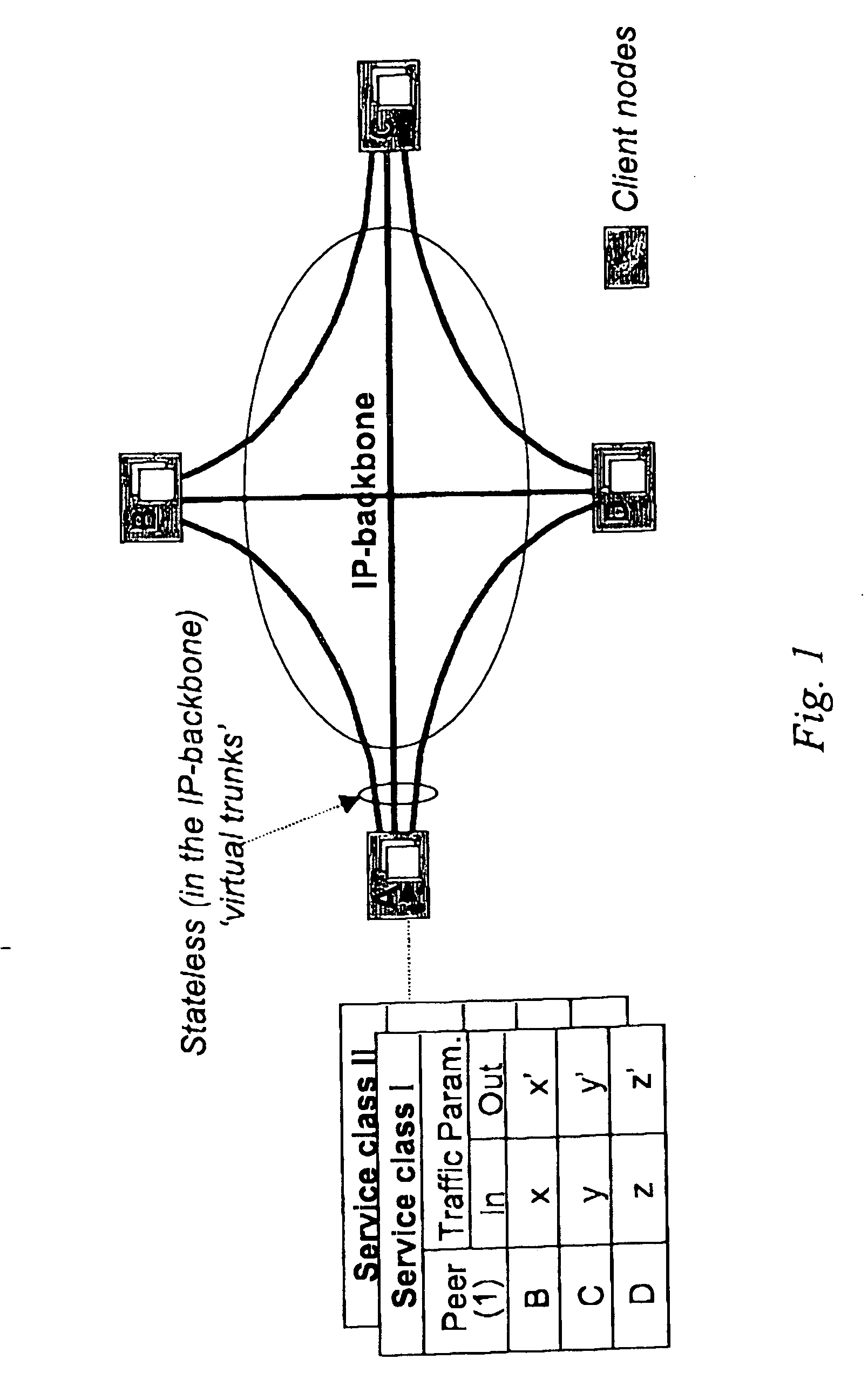
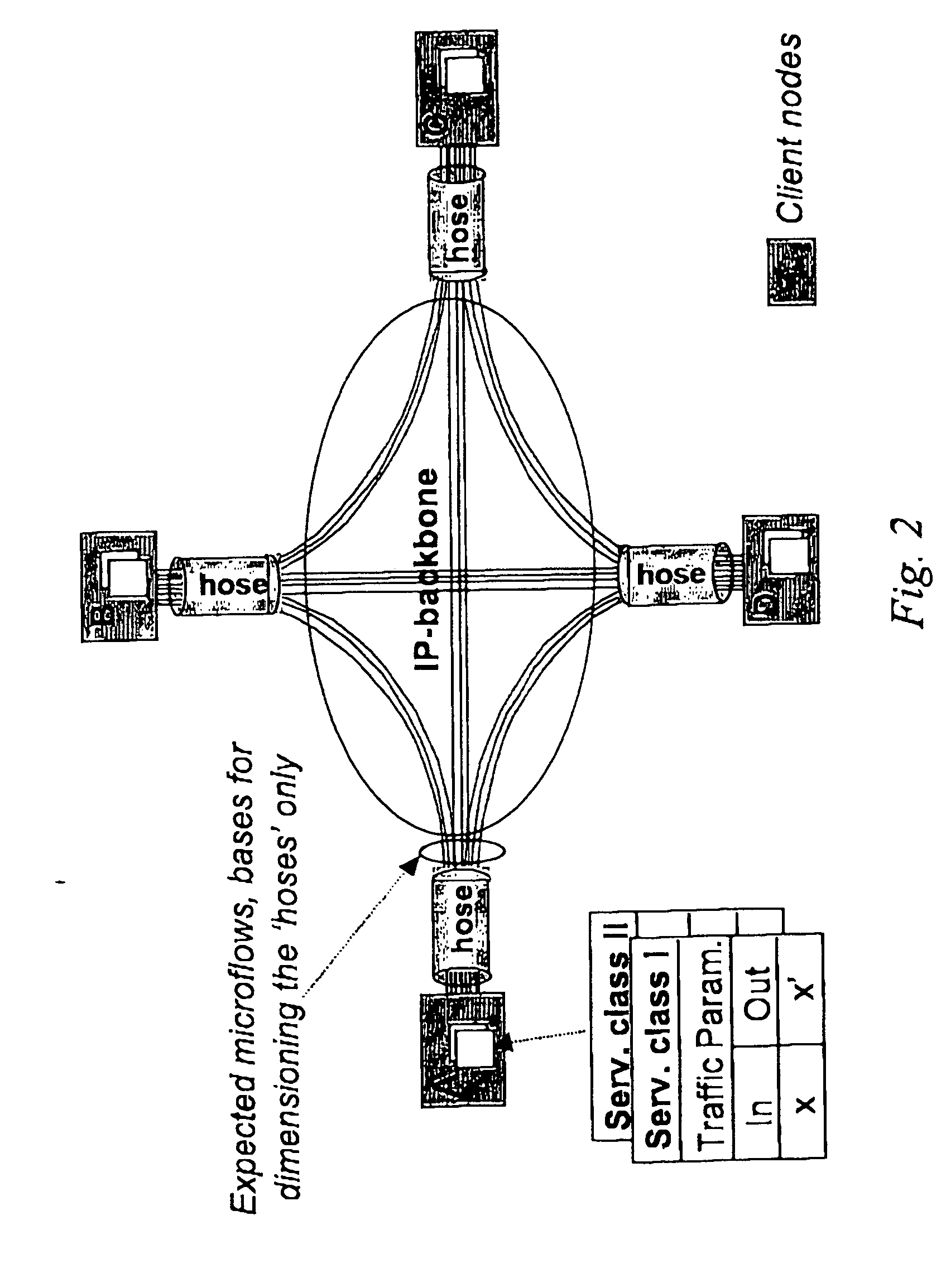
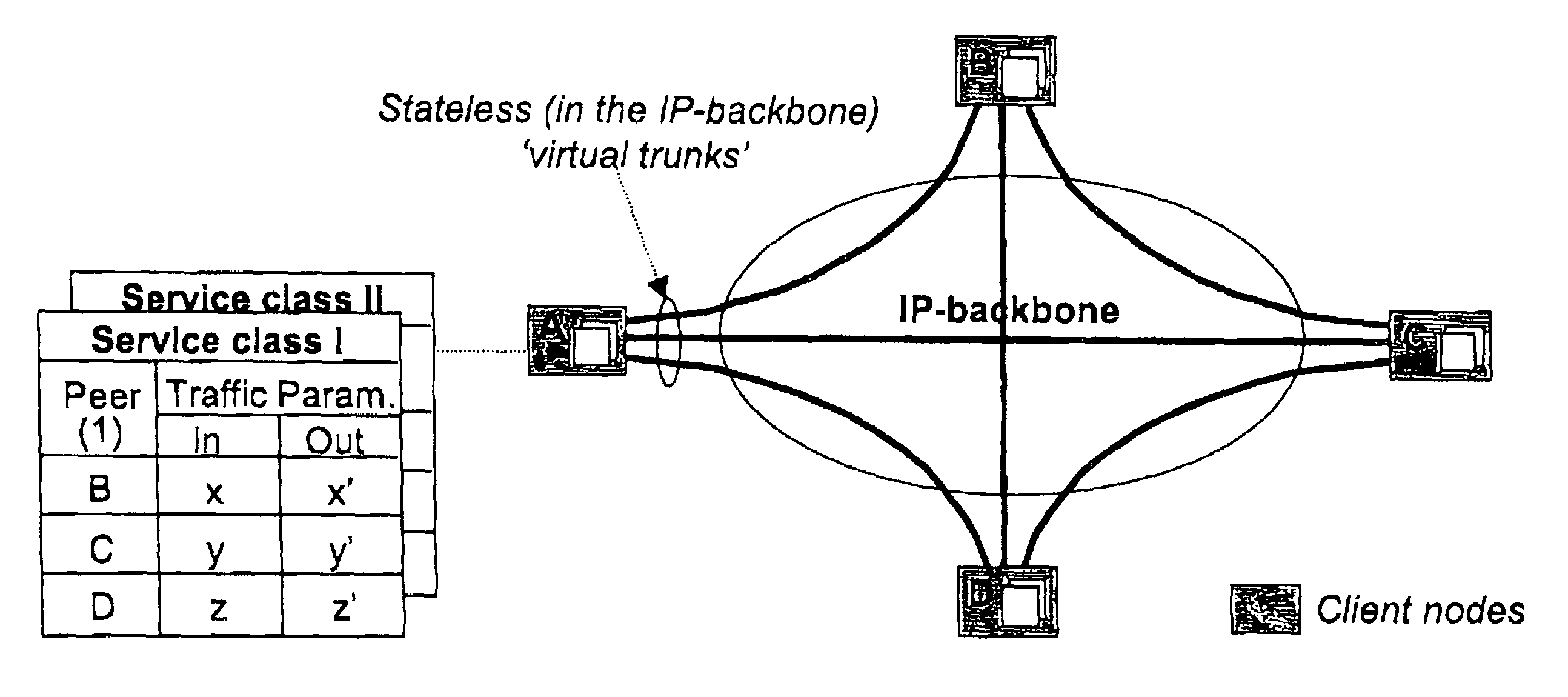
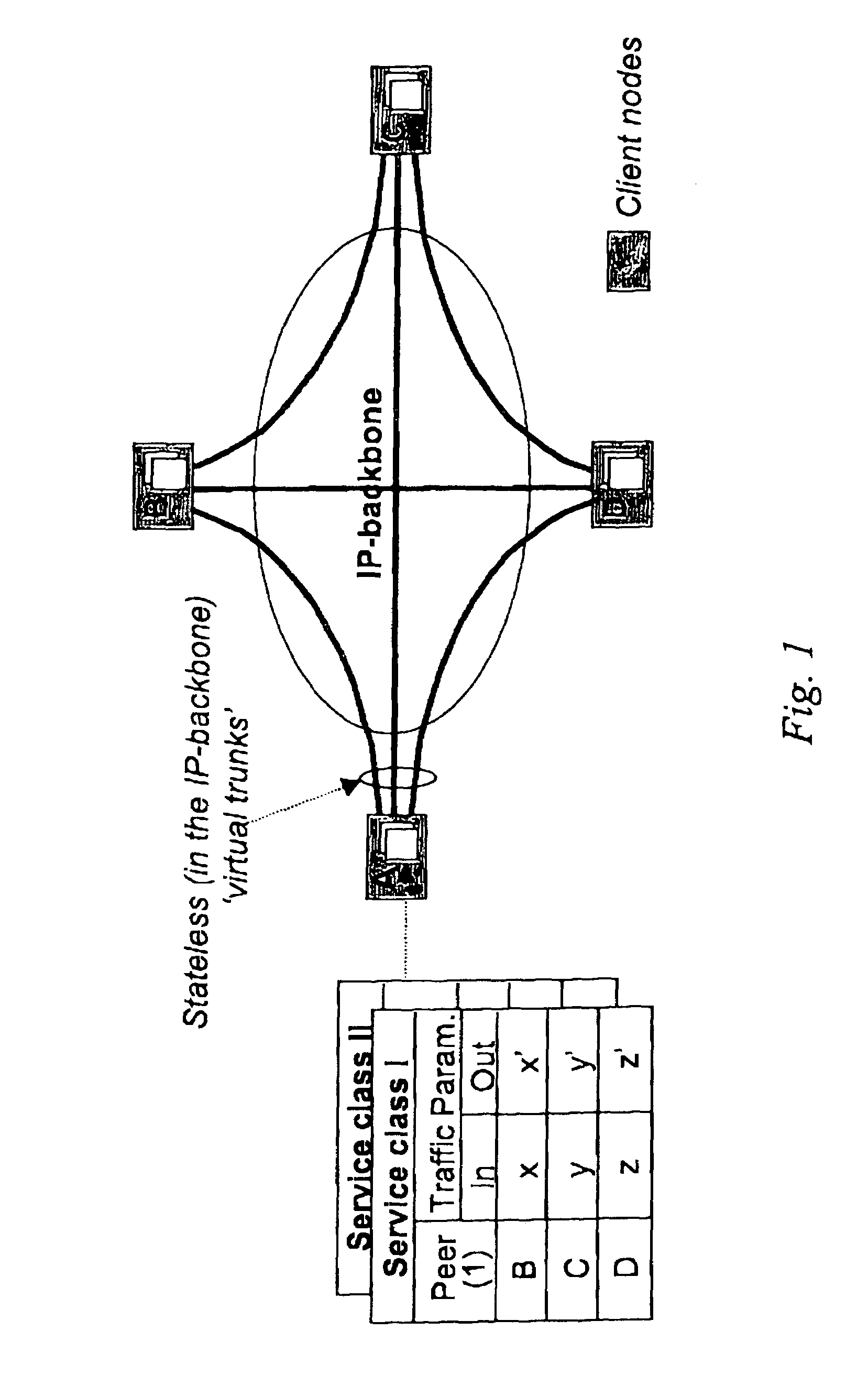
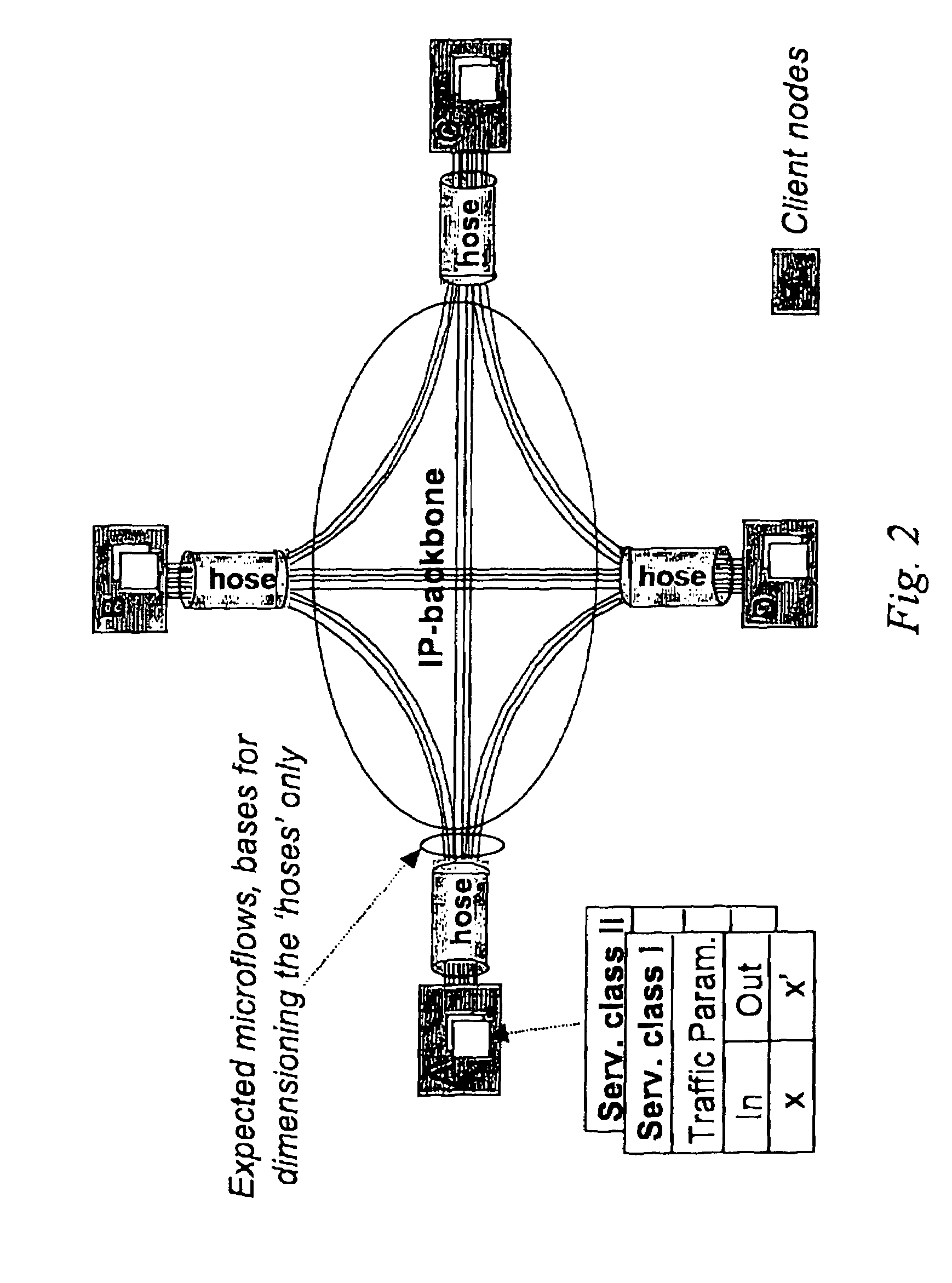
In the area of network provisioning, there is a problem of selecting a suitable traffic-provisioning model for large networks due to the high management complexity of the resource-efficient trunk model and the poor bandwidth efficiency of the easy-to-configure hose model. The invention is based on the idea of partitioning at least part of the network into multi-node clusters, and defining traffic limitations on at least two levels, including the intra-cluster level and the inter-cluster level, where the traffic limitations include one or more node-to-cluster traffic limitations for inter-cluster traffic. Subsequently, cluster-based provisioning of the network is performed based on the traffic limitations. The novel node-to-cluster limitations proposed by the invention are preferably applied in a cluster-based trunk or hose model on the inter-cluster level. In other words, for the description of the inter-cluster traffic (traffic between the clusters) cluster-based trunk or hose models can be used, preferably depending on the available information about the traffic. The cluster-based provisioning makes it possible to find a trade-off between management complexity and overprovisioning.
Owner:TELEFON AB LM ERICSSON (PUBL)
Controller Driven Reconfiguration of a Multi-Layered Application or Service Model
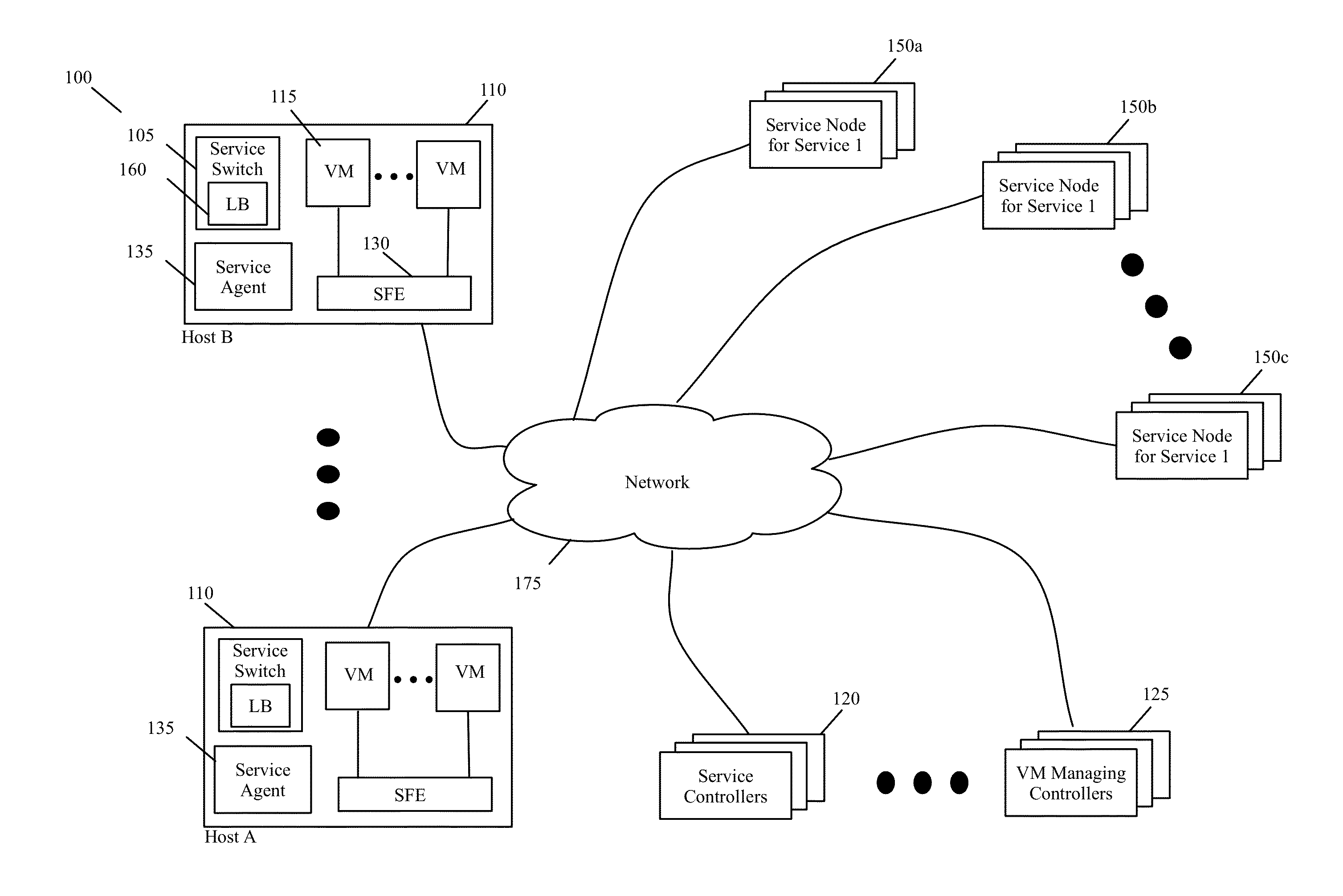
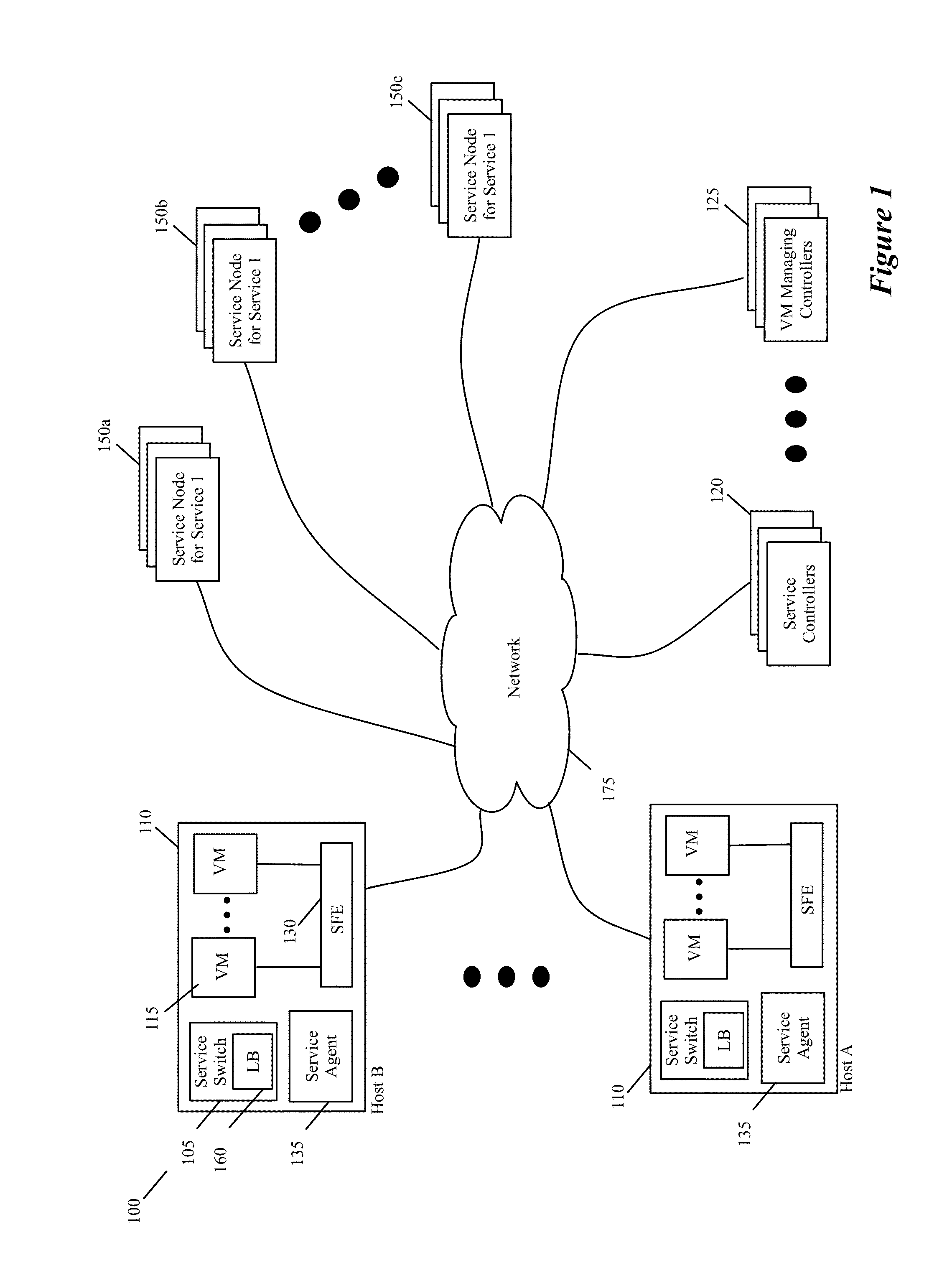
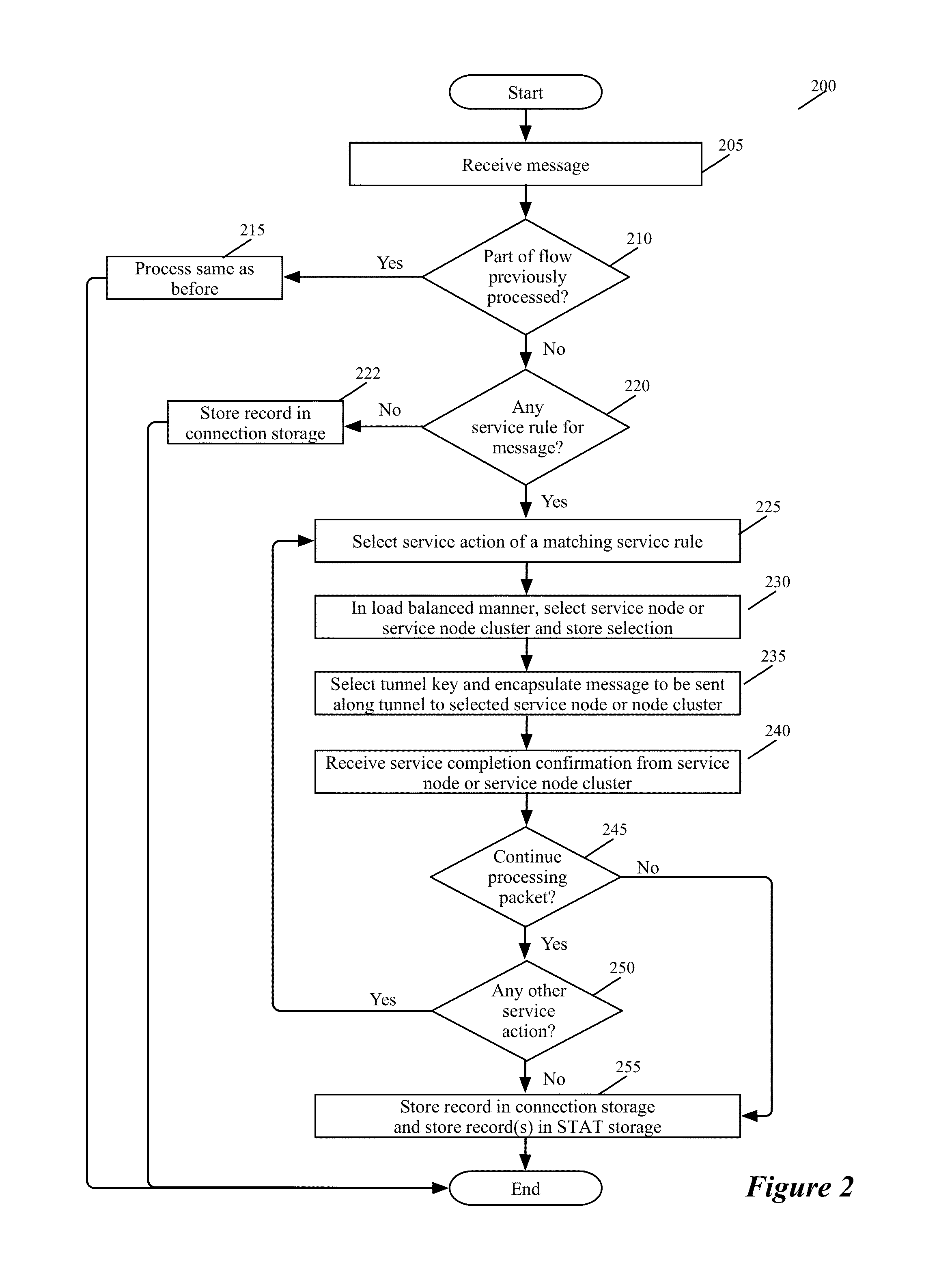
Some embodiments provide novel inline switches that distribute data messages from source compute nodes (SCNs) to different groups of destination service compute nodes (DSCNs). In some embodiments, the inline switches are deployed in the source compute nodes datapaths (e.g., egress datapath). The inline switches in some embodiments are service switches that (1) receive data messages from the SCNs, (2) identify service nodes in a service-node cluster for processing the data messages based on service policies that the switches implement, and (3) use tunnels to send the received data messages to their identified service nodes. Alternatively, or conjunctively, the inline service switches of some embodiments (1) identify service-nodes cluster for processing the data messages based on service policies that the switches implement, and (2) use tunnels to send the received data messages to the identified service-node clusters. The service-node clusters can perform the same service or can perform different services in some embodiments. This tunnel-based approach for distributing data messages to service nodes / clusters is advantageous for seamlessly implementing in a datacenter a cloud-based XaaS model (where XaaS stands for X as a service, and X stands for anything), in which any number of services are provided by service providers in the cloud.
Owner:NICIRA
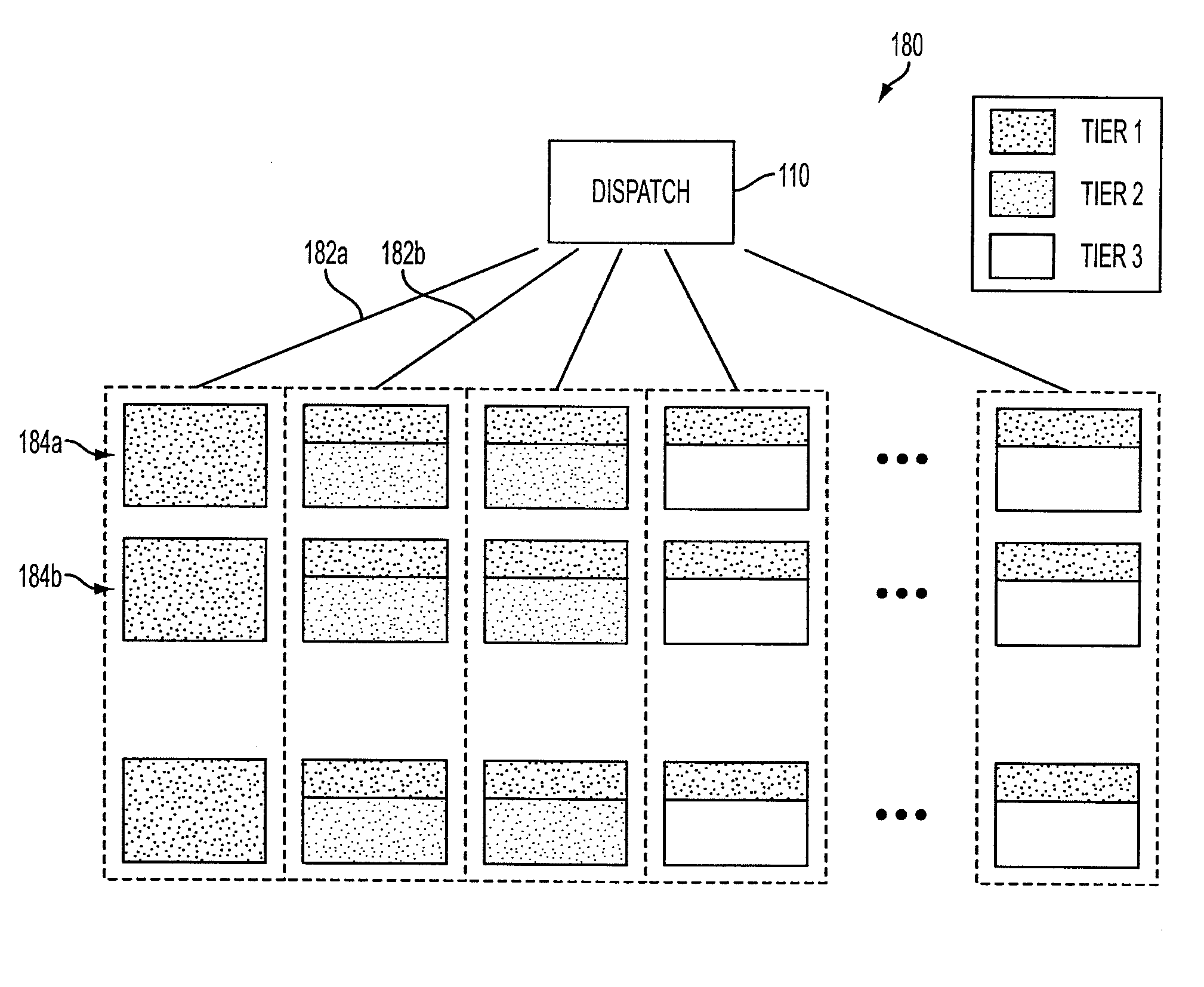
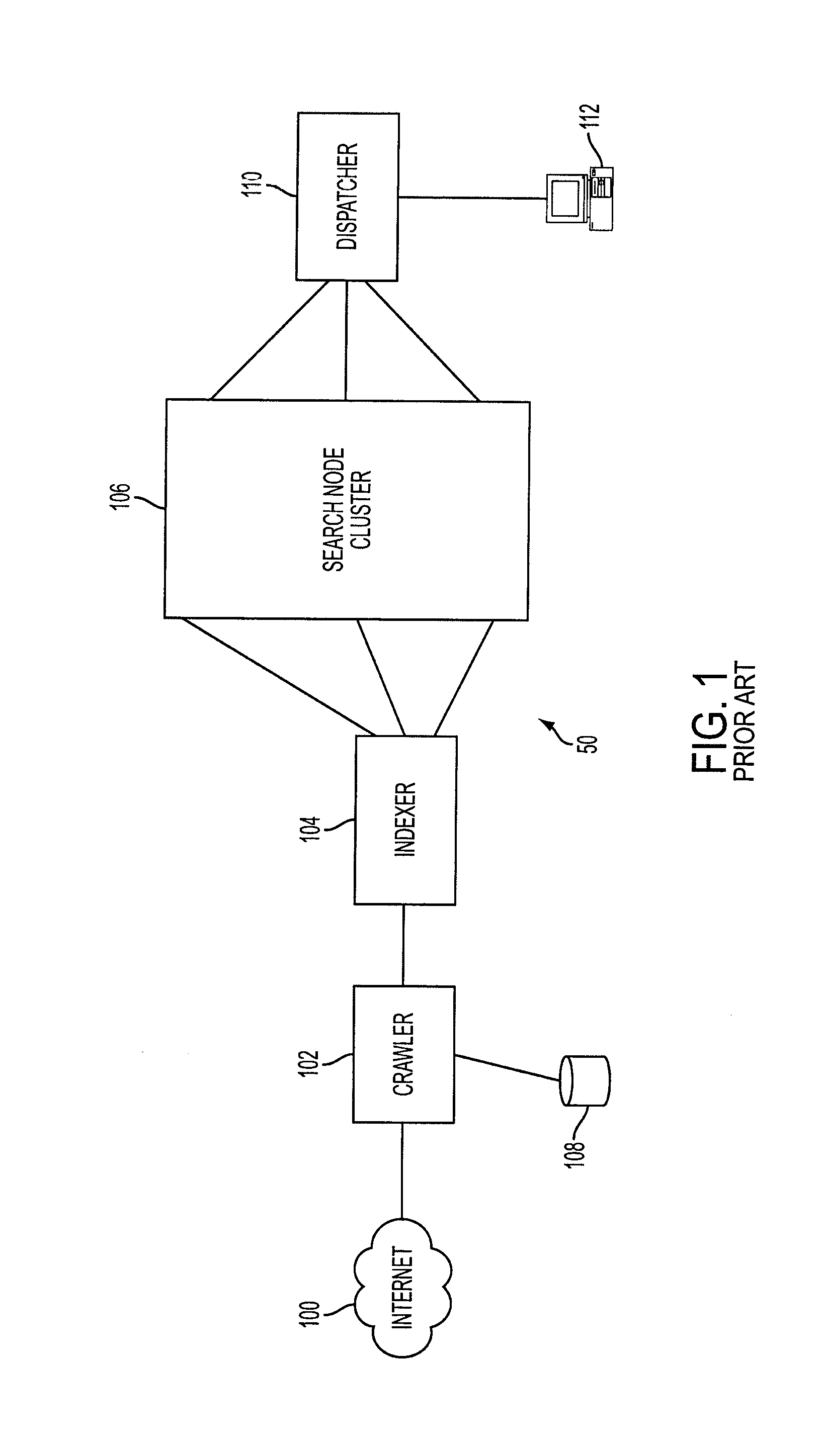
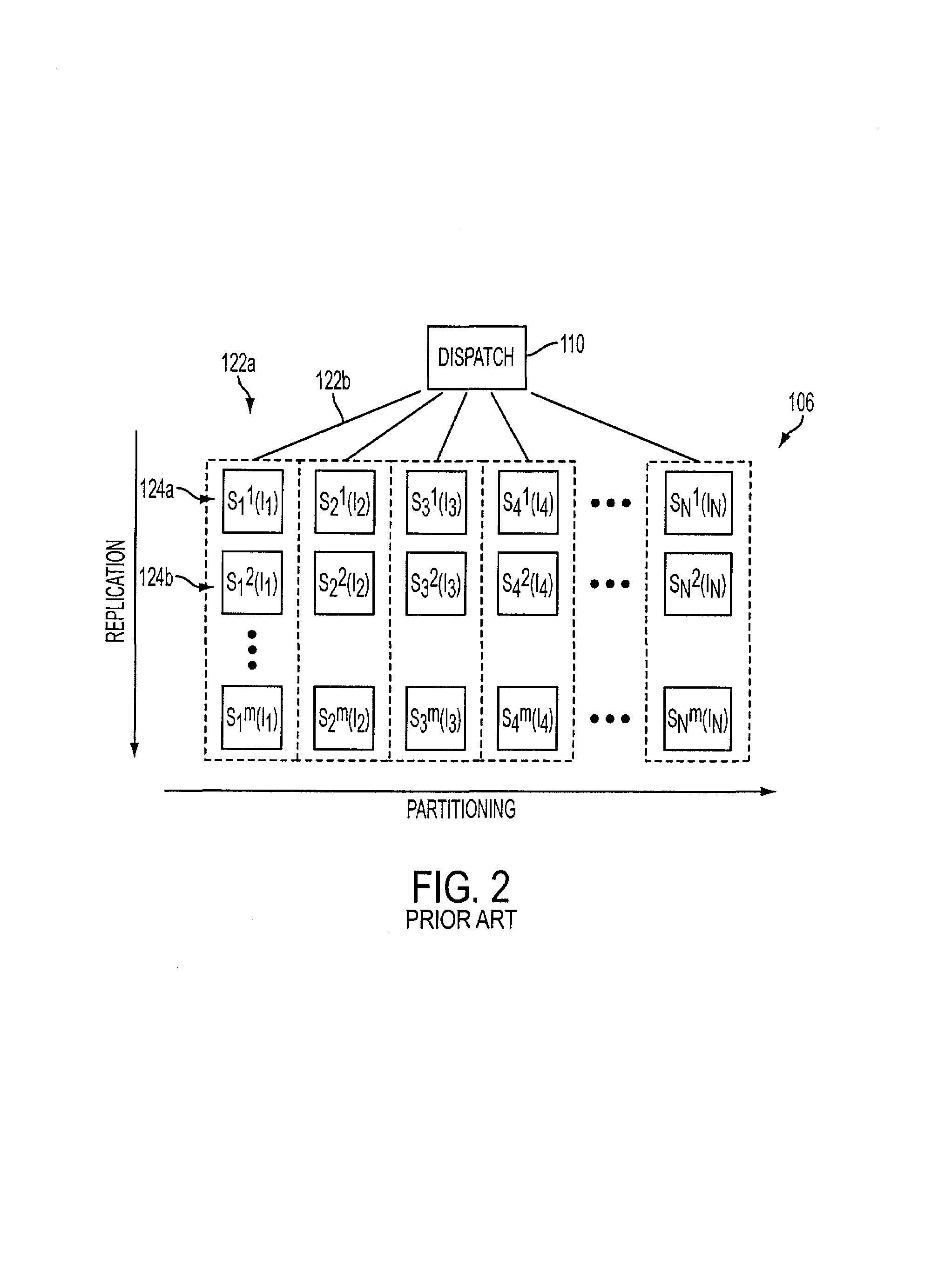
Search engine with hierarchically stored indices
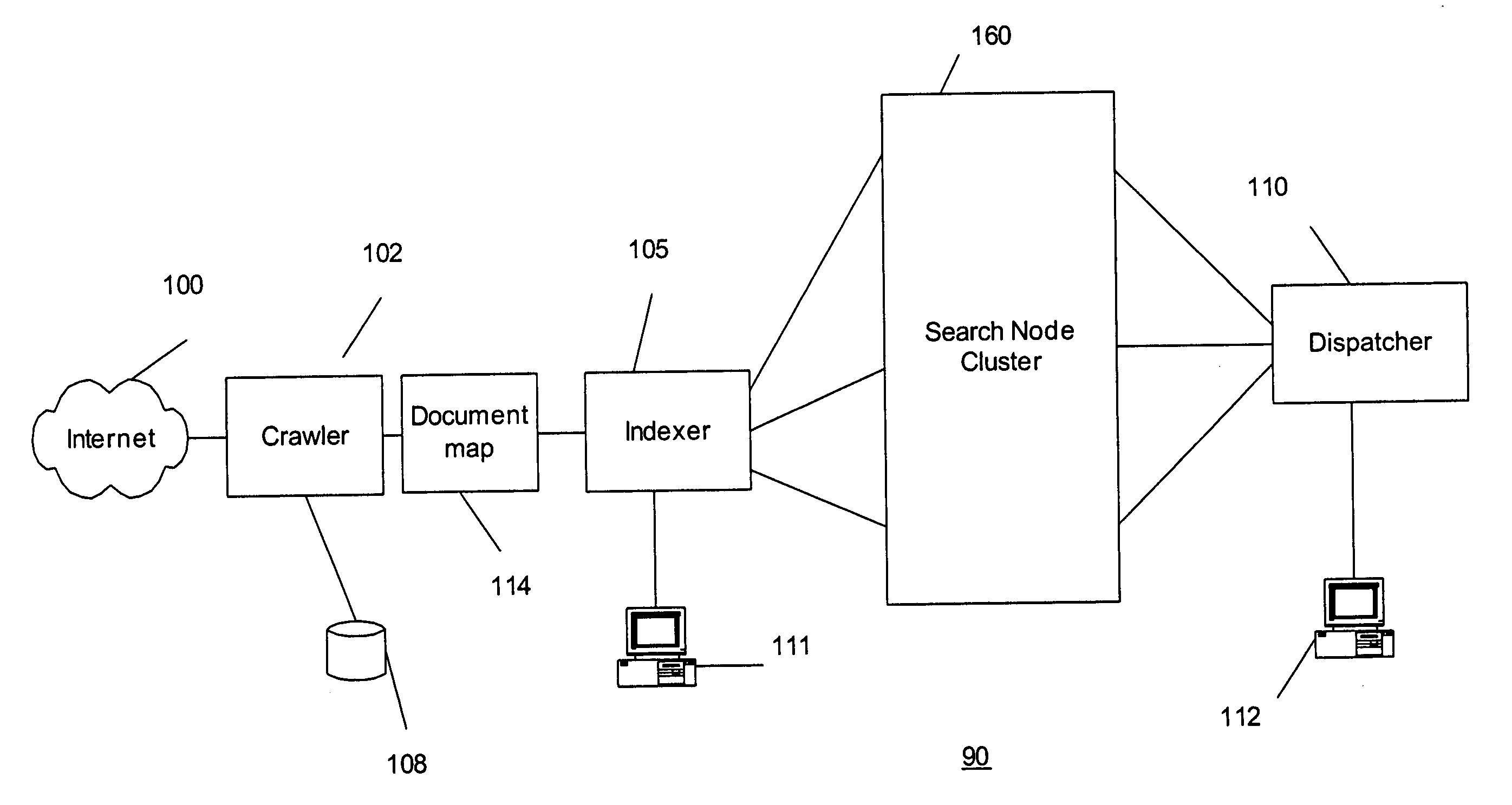
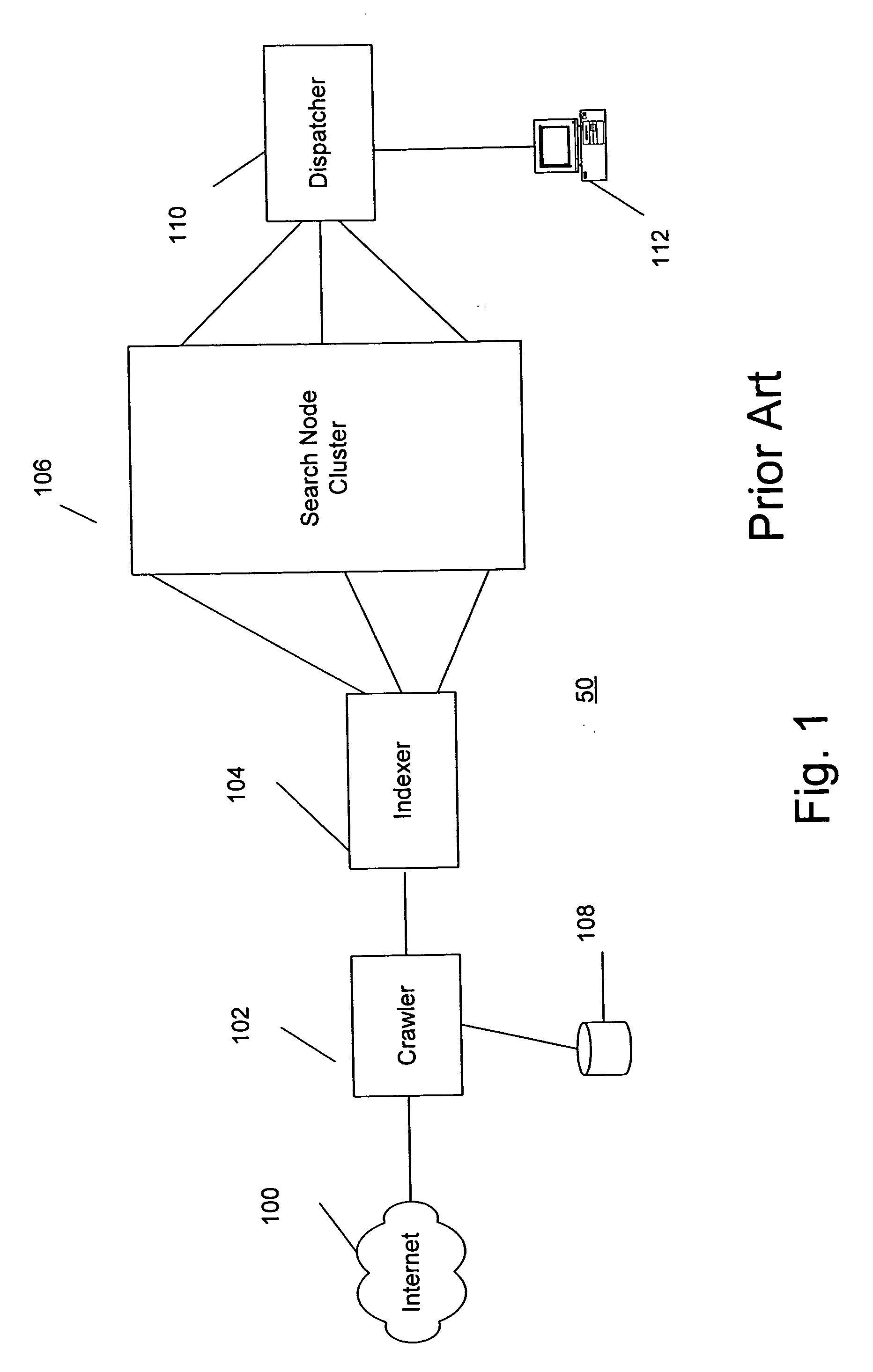
A search engine comprising a crawler which crawls the WWW and stores pages found on the WWW in a database. An indexer indexes the pages in the database to produce a primary index. A document mapping section maps pages in the database into a plurality of tiers based on a ranking of the pages. The ranking may be based on portions of the pages which have a relatively higher value context. A processor produces a plurality of sub-indices from the primary index based on the mapping. The sub-indices are stored in a search node cluster. The cluster is a matrix of search nodes logically arranged in a plurality of rows and columns. Search nodes in the same column include the same sub-index. Search nodes in the same row include distinct sub-indices. A search query received by a user is sent to a dispatcher which, in turn, forwards the query to the first tier of search nodes. A fall through algorithm is disclosed which indicates when the dispatcher should forward the search query to other tiers of search nodes.
Owner:JOLLIFY MANAGEMENT
Search engine with hierarchically stored indices
A search engine comprising a crawler which crawls the WWW and stores pages found on the WWW in a database. An indexer indexes the pages in the database to produce a primary index. A document mapping section maps pages in the database into a plurality of tiers based on a ranking of the pages. The ranking may be based on portions of the pages which have a relatively higher value context. A processor produces a plurality of sub-indices from the primary index based on the mapping. The sub-indices are stored in a search node cluster. The cluster is a matrix of search nodes logically arranged in a plurality of rows and columns. Search nodes in the same column include the same sub-index. Search nodes in the same row include distinct sub-indices. A search query received by a user is sent to a dispatcher which, in turn, forwards the query to the first tier of search nodes. A fall through algorithm is disclosed which indicates when the dispatcher should forward the search query to other tiers of search nodes.
Owner:JOLLIFY MANAGEMENT
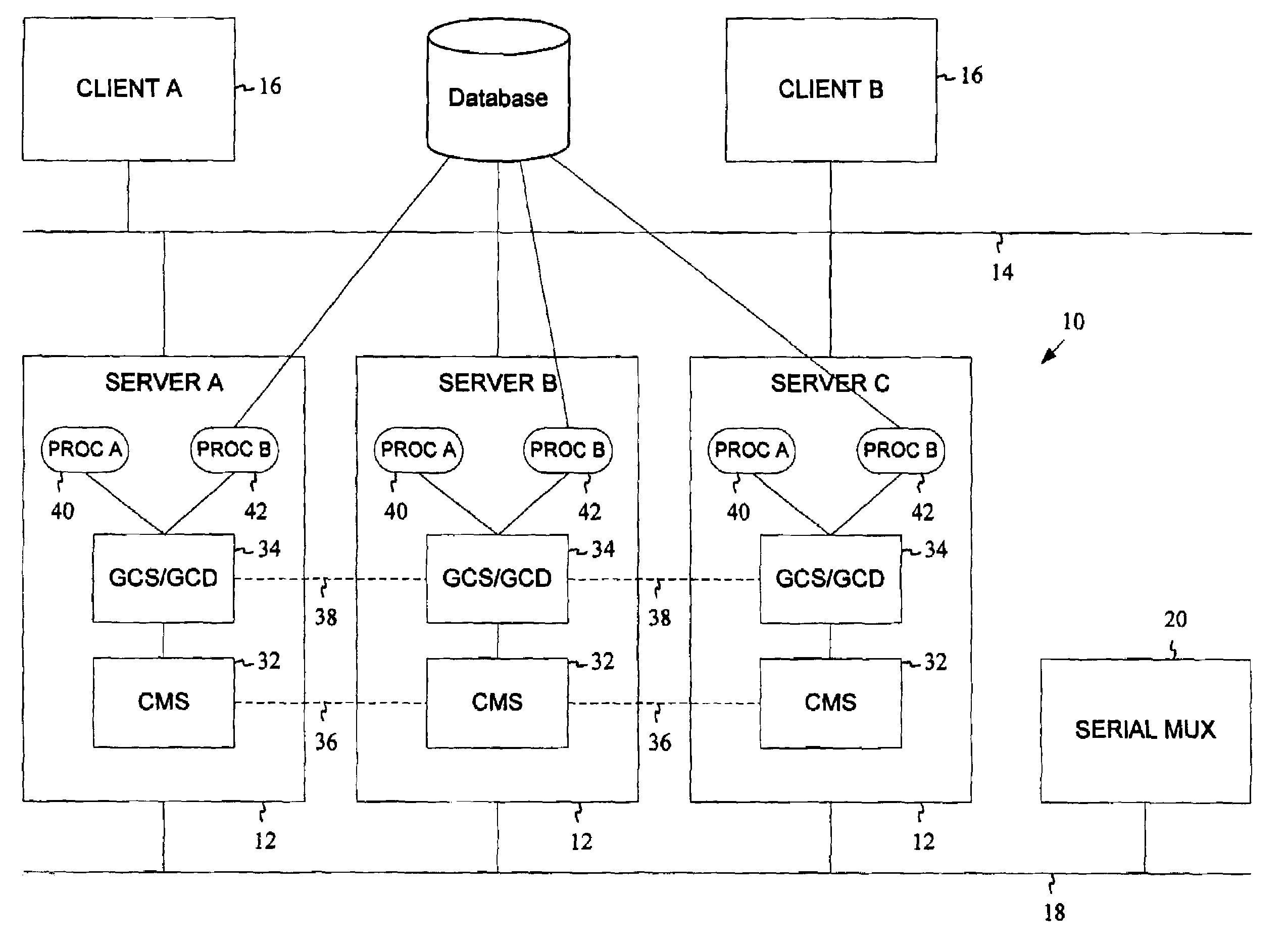
Maintaining process group membership for node clusters in high availability computing systems
InactiveUS7627694B2Improve usabilityMultiple digital computer combinationsTransmissionNode clusteringNetwork connection
A high availability computing system includes a plurality of computer nodes (for example, a server system) connected by a first and a second network, wherein the computer nodes communicate with each other to detect server failure and transfer applications to other computer nodes on detecting server failure. The system incorporates methods of maintaining high availability in a server cluster having a plurality of nodes. A group communications service, a membership service and a system resource manager are instantiated on each node and the group communications service, the membership service and the system resource manager on each node communicate with other nodes to detect node failures and to transfer applications to other nodes on detecting node failure.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
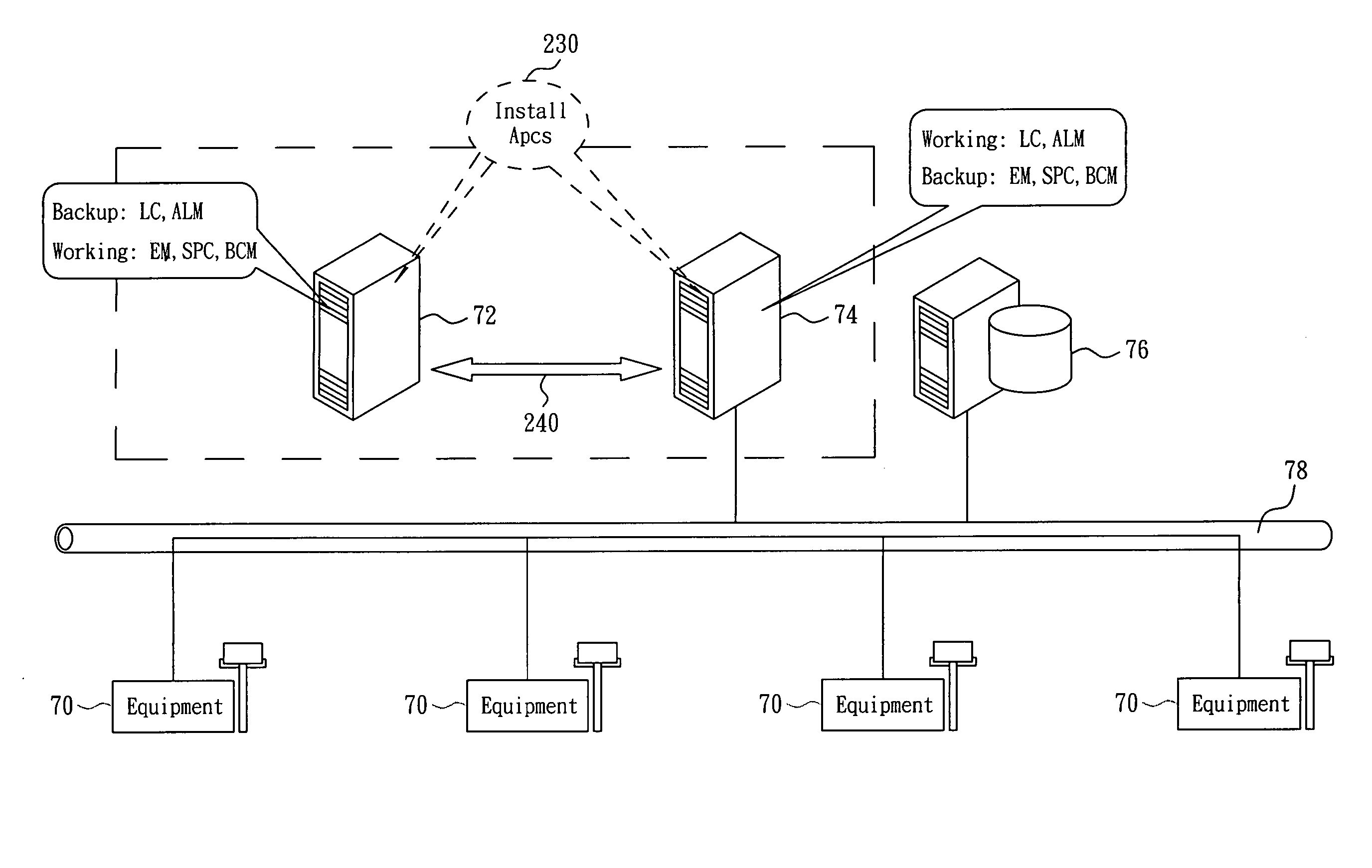
Method for providing fault-tolerant application cluster service
ActiveUS20050237926A1Easy to detectImprove efficiencyError preventionTransmission systemsNode clusteringRecovery function
A method for providing an application cluster service (APCS) with fault-detection and failure-recovery capabilities. This method is composed of the steps of nodes clustering, invoking and detecting applications, fault-recovery of applications, detection of nodes, and node replacement. This method is applicable in a clustered environment to detect if a slave node is failed by sending a heartbeat periodically from a master node; and to detect if the master node still exists by checking if the master node stops sending the heartbeat (i.e. the master node may be failed).
Owner:NAT CHENG KUNG UNIV
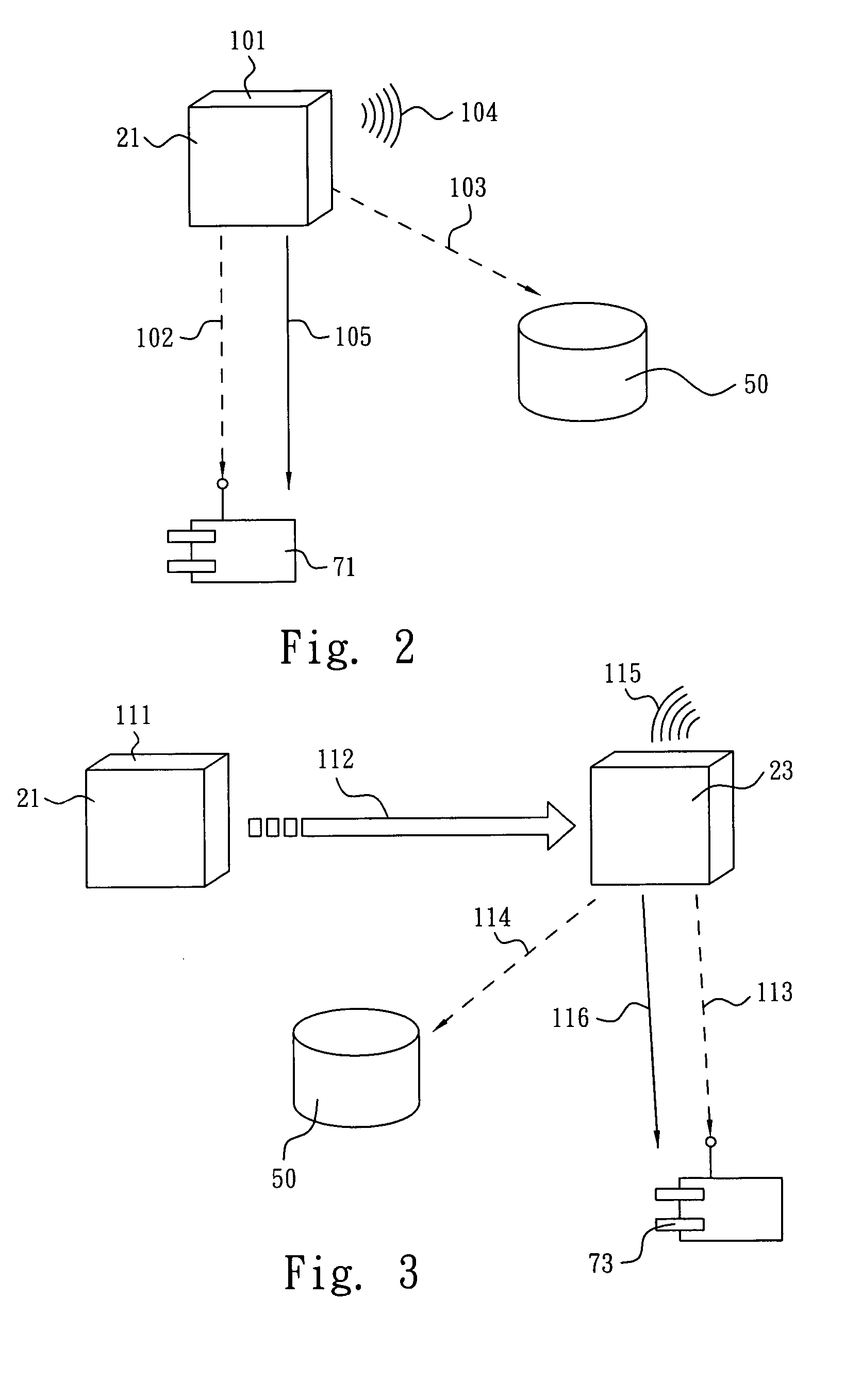
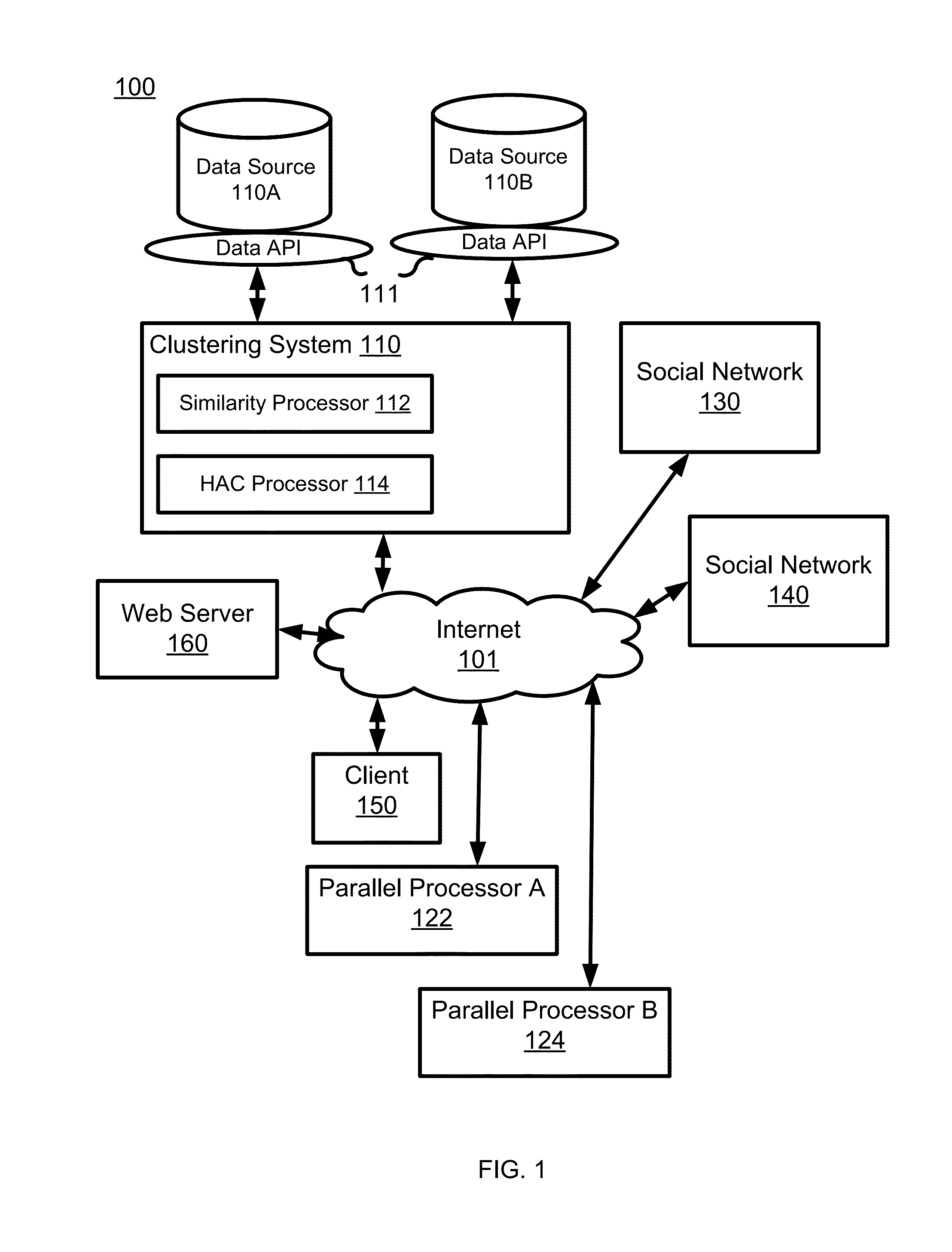
Social network node clustering system and method
InactiveUS8606787B1Improve efficiencyReduce processData processing applicationsDigital data processing detailsNode clusteringCluster based
Users in a social network are represented by nodes on a network graph. A similarity processor generates a similarity matrix of nodes and neighbors. A clustering processor groups select nodes based on similarity. Nodes initially assigned to one cluster are selectively added to other clusters based on similarity. A social network processor provides features and processing based on the clusters of nodes thus produced.
Owner:GOOGLE LLC
Cluster-based network provisioning
ActiveUS7577091B2Improved network provisioning strategyImprove performanceError preventionFrequency-division multiplex detailsNode clusteringTrade offs
Owner:TELEFON AB LM ERICSSON (PUBL)
Method, device and system for backup
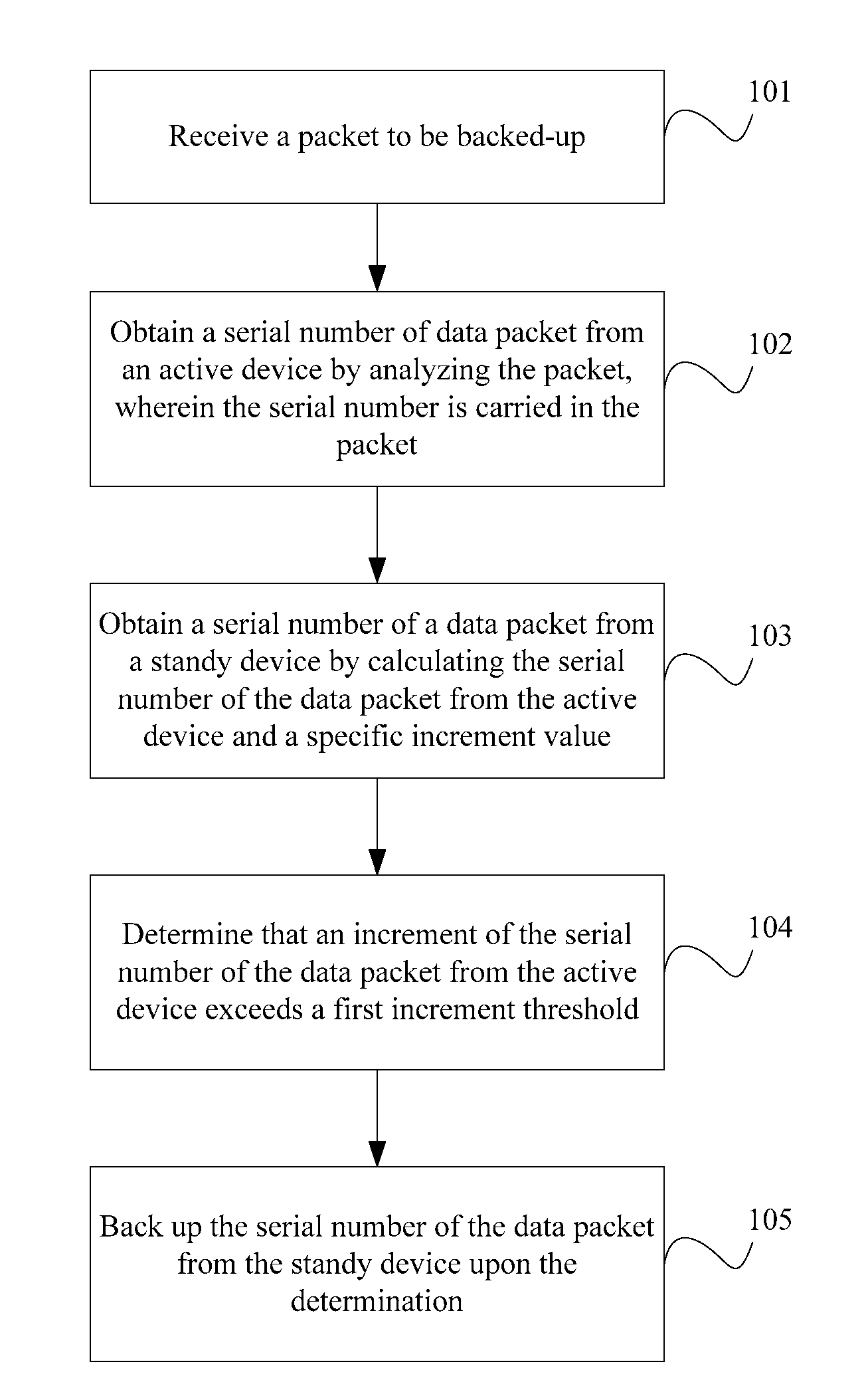
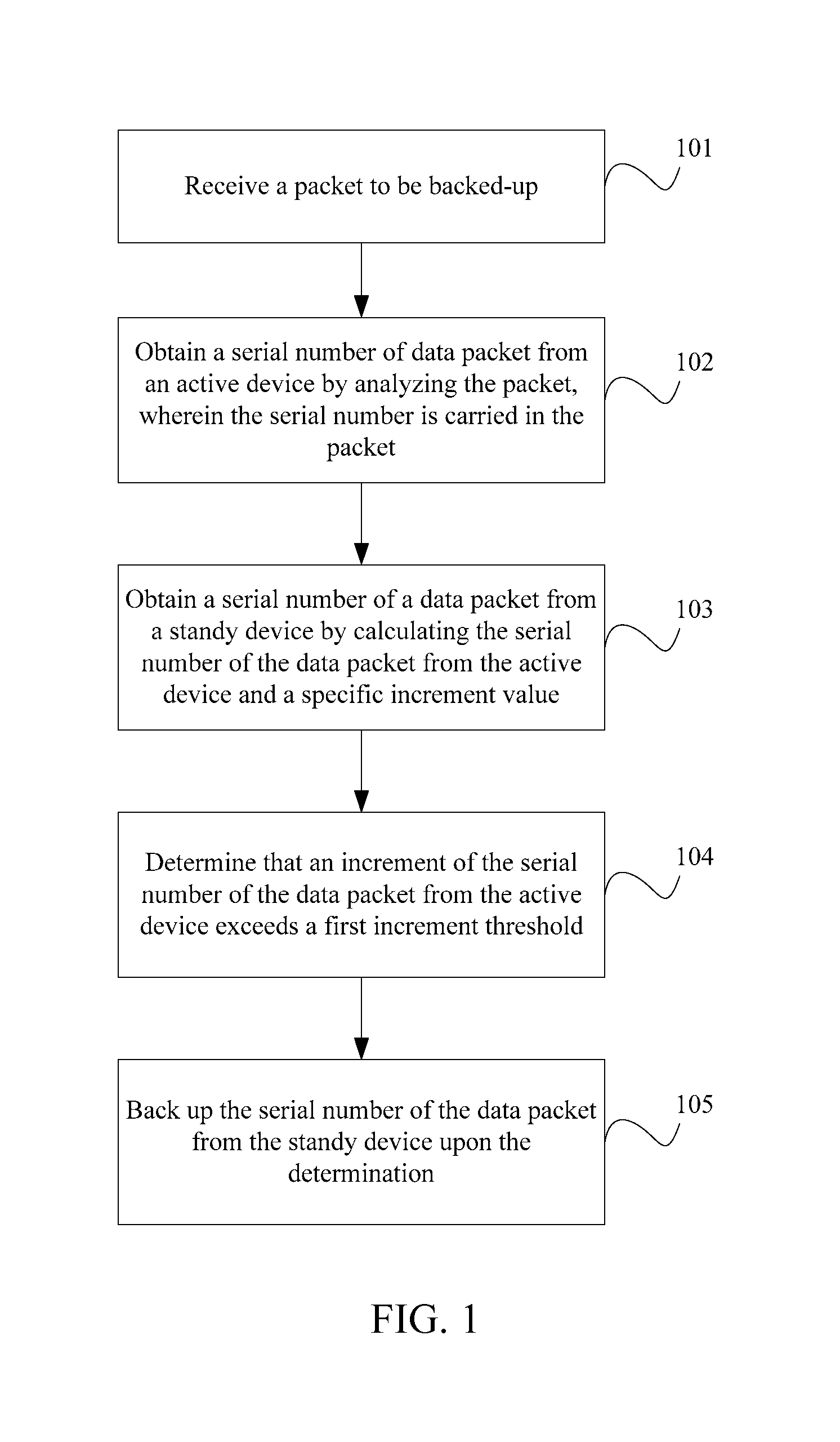
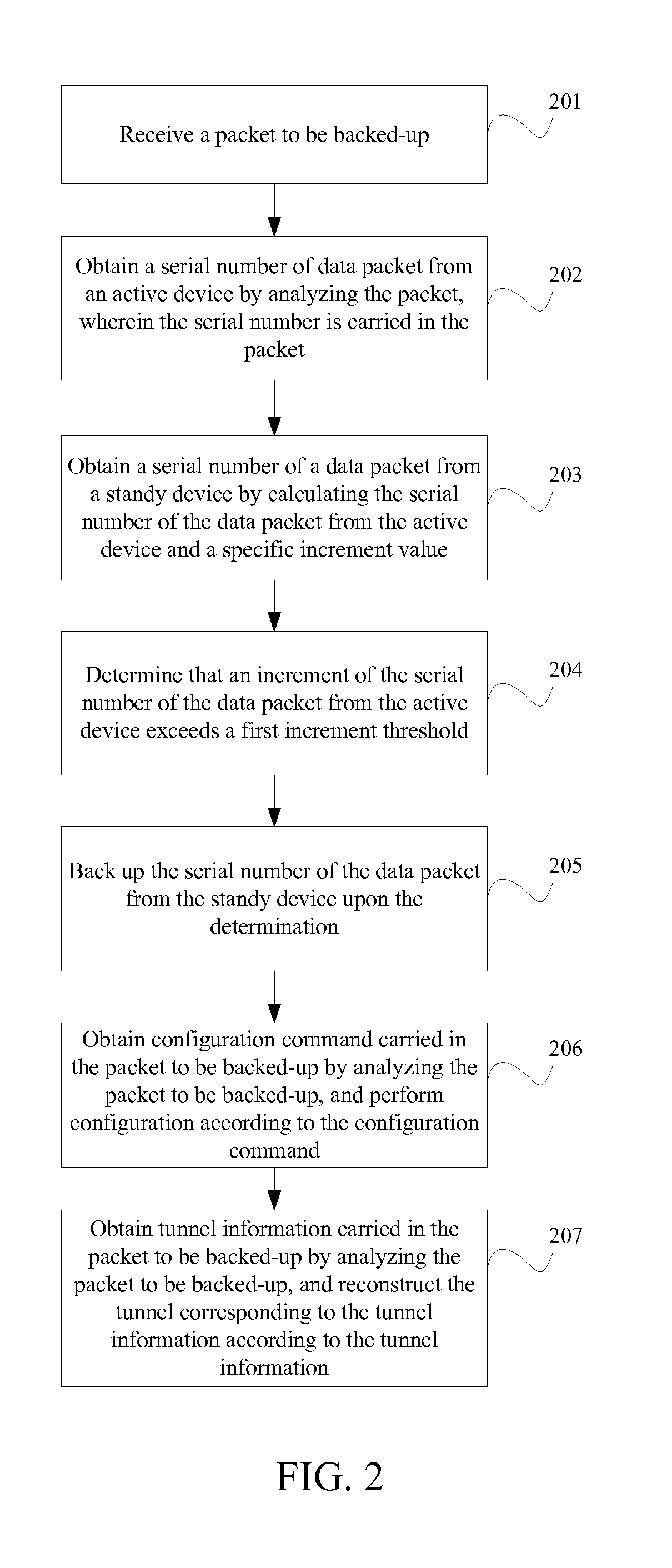
ActiveUS20120239804A1Improve continuityAvoid service interruptionDigital computer detailsTransmissionNode clusteringNetwork packet
A method, a device, and a system for backup are disclosed. The method includes: receiving a backup packet; analyzing the backup packet to obtain a serial number of an active data packet, where the serial number is carried in the backup packet; calculating a sum of the serial number of the active data packet and a specific increment value to obtain a serial number of a standby data packet; and backing up the serial number of the standby data packet. Therefore, after the service is switched over from the active device to the standby device, the active device still regards the data packet sent by the former standby device as a new data packet and receives the data packet, which prevents service interruption caused by the switchover and improves continuity of service processing in the process of two-node cluster hot backup.
Owner:HUAWEI TECH CO LTD
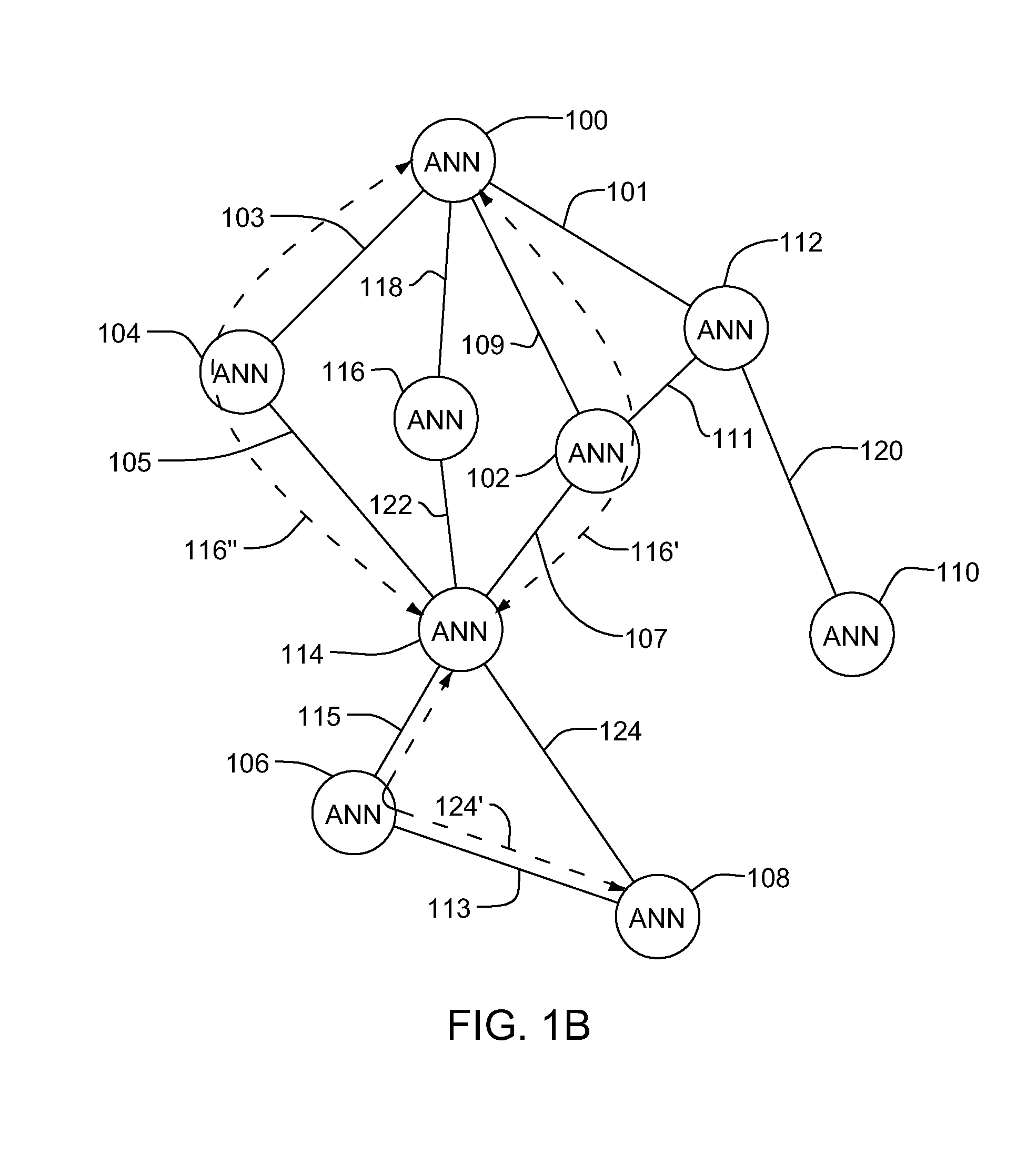
Neural network-based mobility management for mobile ad hoc radio networks
InactiveUS20070299946A1Easy to addEasy to insertError preventionTransmission systemsNode clusteringNerve network
A self managed ad hoc communications network and method of managing the network. The network includes wireless devices or nodes that include a neural network element and the ad hoc network operates as a neural network. One of the nodes is designated as a Network Management System (NMS) that provides overall network management. Clusters of nodes are organized around cluster leaders. Each cluster leader manages a cluster of nodes and communications between node clusters. Each cluster may also have other nodes identified as lower order cluster leaders.
Owner:THE BOEING CO
Network, system and method for distributing digital media
InactiveUS7634076B2Prevent theftCable networksInterconnection arrangementsNode clusteringComputer network
A network, a system and a method distribute digital media from a substation and / or a server to a set-top box of a subscriber. The digital media is requested, is accessed and / or is transferred from the substation and / or the server to the set-top box via one or more nodes and / or one or more node clusters. The subscriber may utilize an interactive means in conjunction with the set-top box to access, to request, to receive and / or to display the digital media via a communication medium and / or a connection line. One or more nodes and / or one or more node clusters connect a central office to the substation. The digital media is stored in a server farm of the central office which is accessed by one or more nodes and / or one or more node clusters. The digital media is transmitted and / or is distributed to the set-top box via the communication medium, the connection line one or more of the nodes and / or one or more of the node clusters. The subscriber access, displays and / or views the digital media via the set-top box, a display monitor, one or more input devices and / or one or more output devices.
Owner:APPLE INC
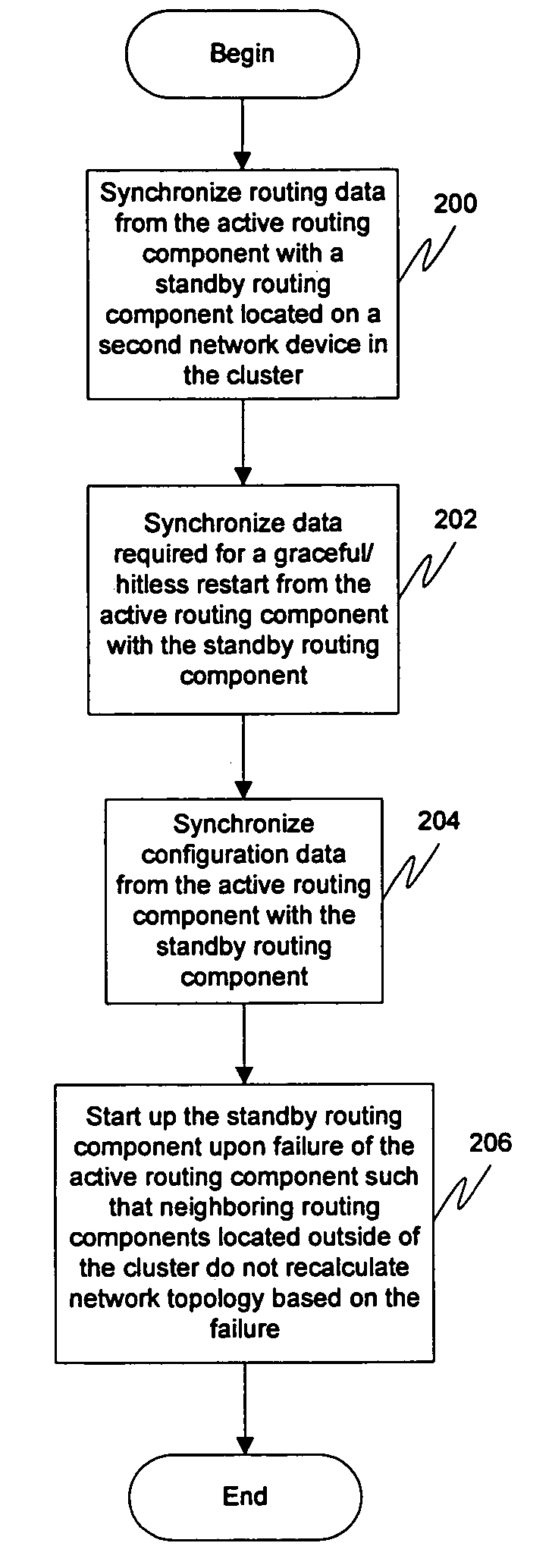
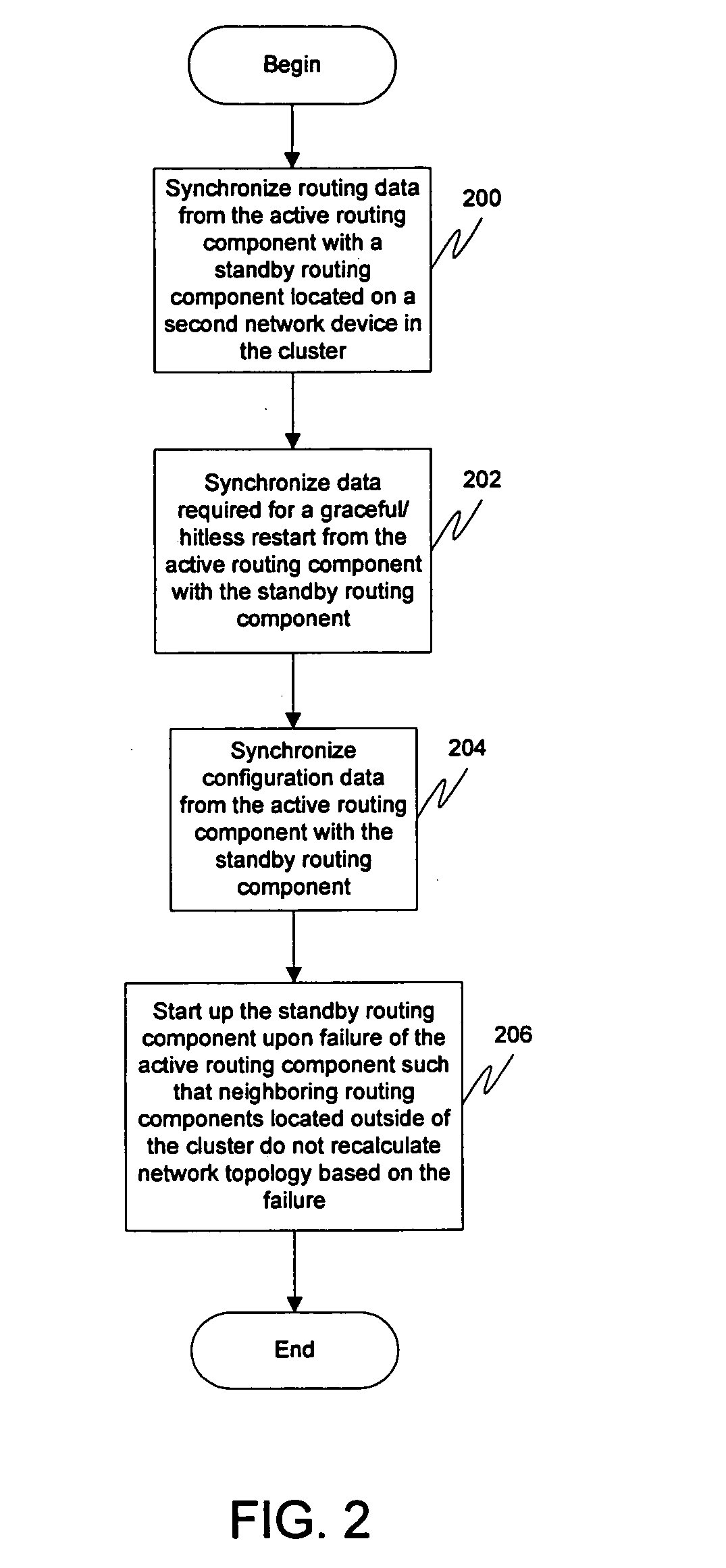
Redundant routing capabilities for a network node cluster
Graceful / hitless restart features from a routing / signaling protocol may be utilized along with synchronization between cluster members in order to provide routing capabilities in a clustering environment. During normal operation, the active cluster member may operate the routing protocol(s) and communicate with the neighboring components using the cluster's address. As the active member learns the routes to the destinations, the routing data may be propagated to the stand-by cluster members across an internal communication mechanism. Configuration information for the routing component may also be propagated to the stand-by cluster members. Upon failure of the active routing component, the standby routing component may be started up such that neighboring routing components located outside of said cluster do not recalculate network topology based on said failure. This allows for failover to occur without affecting neighboring components and unduly burdening the system.
Owner:IP INFUSION INC
Operator initiated graceful takeover in a node cluster
The invention is a method for operating a file server system in a cluster mode that provides for relatively rapid and reliable takeover by one file server of another. This is done by a system operator requesting takeover of file services of a file server, letting the first file server complete existing file service requests from clients, refusing further file service requests addressed to the first file server, and the one file server taking over by transferring file service requests to the one file server. As part of this takeover the one file server takes on the identity of the first filer and activates network interfaces and network addresses that replicate the first server's network addresses.
Owner:NETWORK APPLIANCE INC
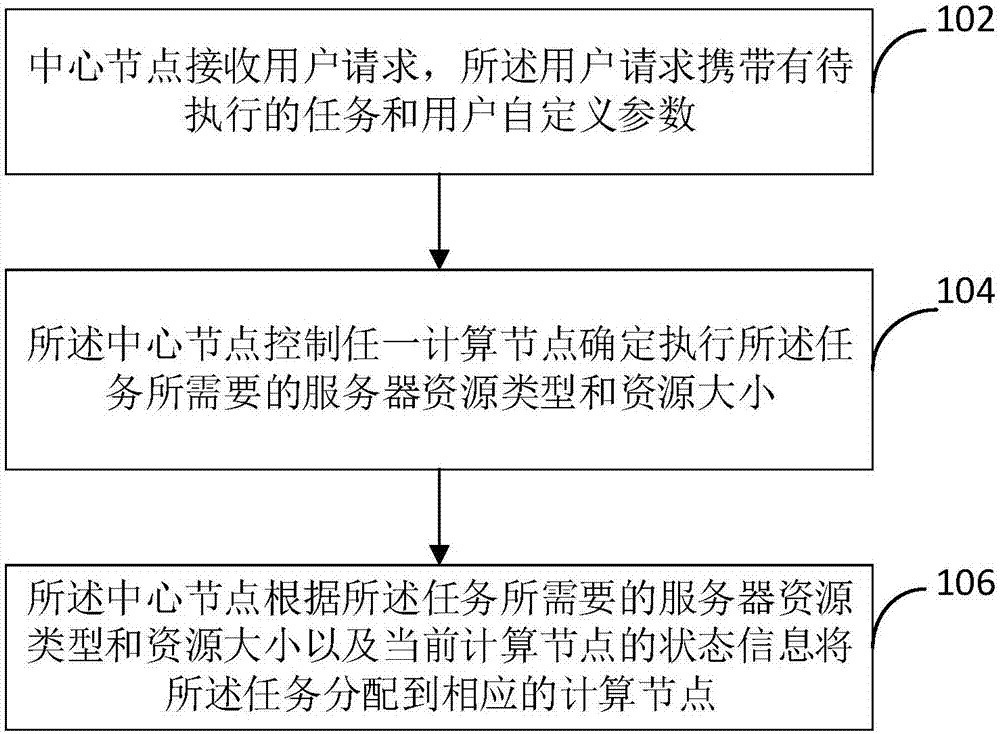
Task allocation method and system in node cluster, and node
InactiveCN107135257AEnable mixed useResource allocationTransmissionNode clusteringDistributed computing
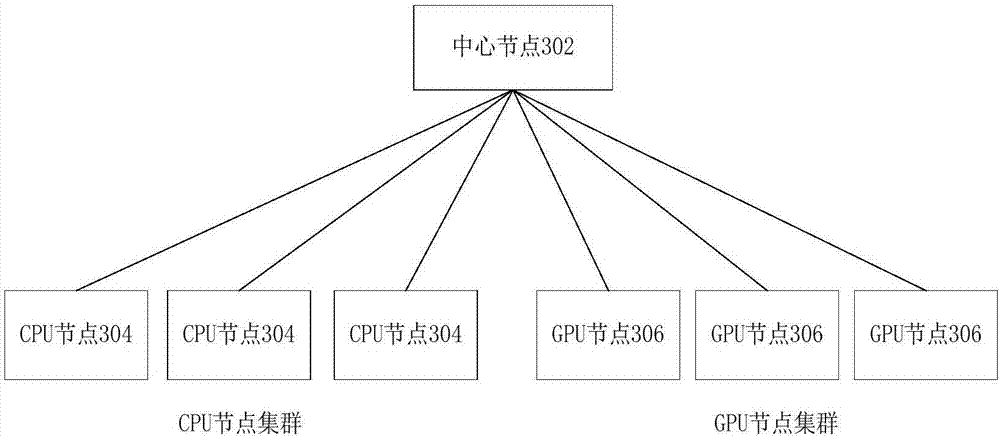
The invention provides a task allocation method and system in a node cluster, and a node. The node cluster comprises a plurality of computing nodes, the plurality of computing nodes comprise GPU nodes and CPU nodes, a plurality of GPU nodes constitute a GPU node cluster, and a plurality of CPU nodes constitute a CPU node cluster. The method comprises the following steps: a center node receives a user request, wherein the user request carries a to-be-executed task and a user-defined parameter; the center node controls any computing node to determine a server resource type and the service magnitude necessary for executing the task; and the center node allocates the task to the corresponding computing node according to the server resource type and the service magnitude necessary for executing the task and the state information of the current computing node. By adoption of the method provided by the embodiment of the invention, unified management and mixed use of the CPU node cluster and the GPU node cluster can be realized.
Owner:NETPOSA TECH
Network attached storage SNMP single system image
ActiveUS7451199B2Simplifying management taskSimple taskMultiple digital computer combinationsData switching networksNode clusteringNetwork-attached storage
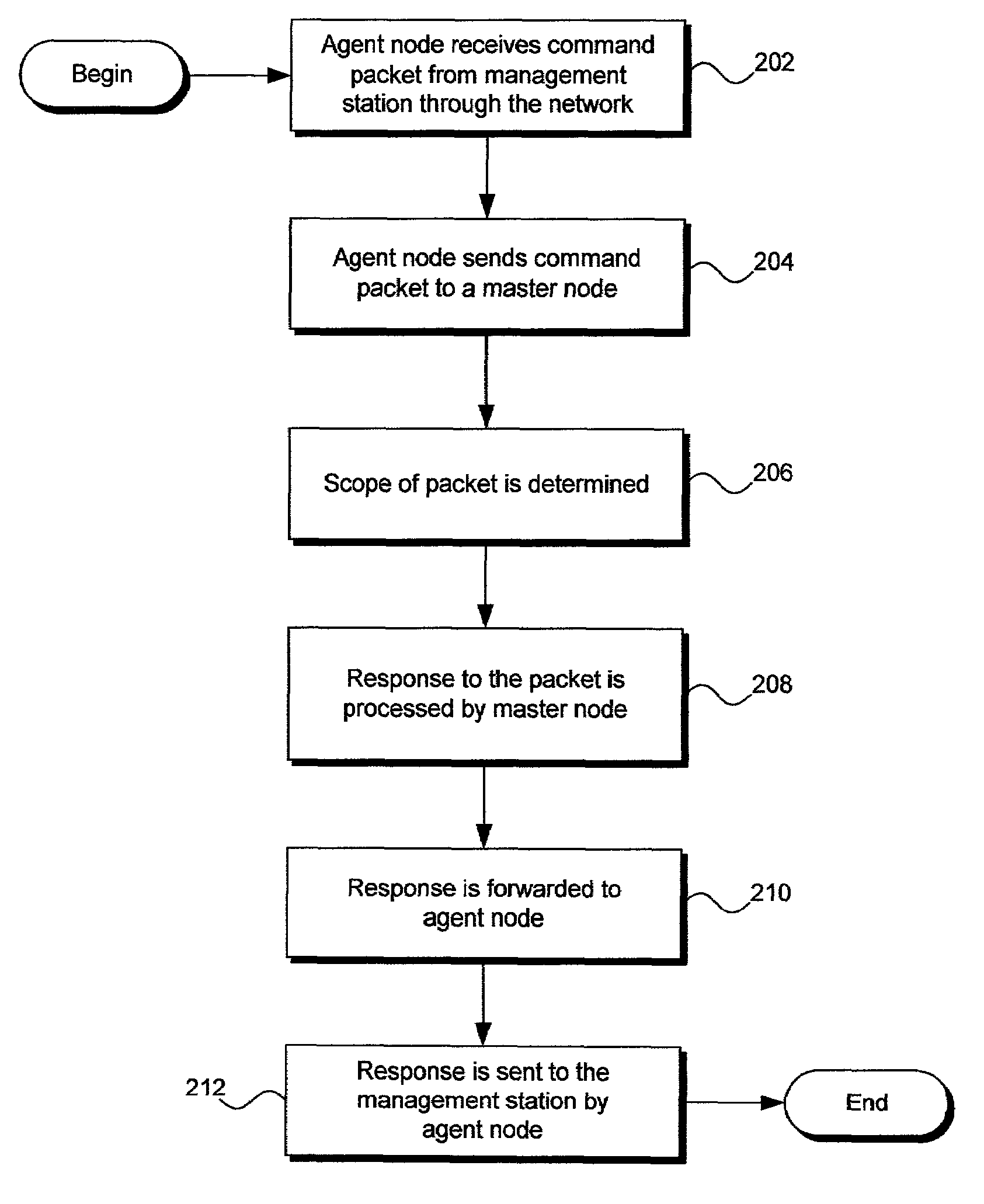
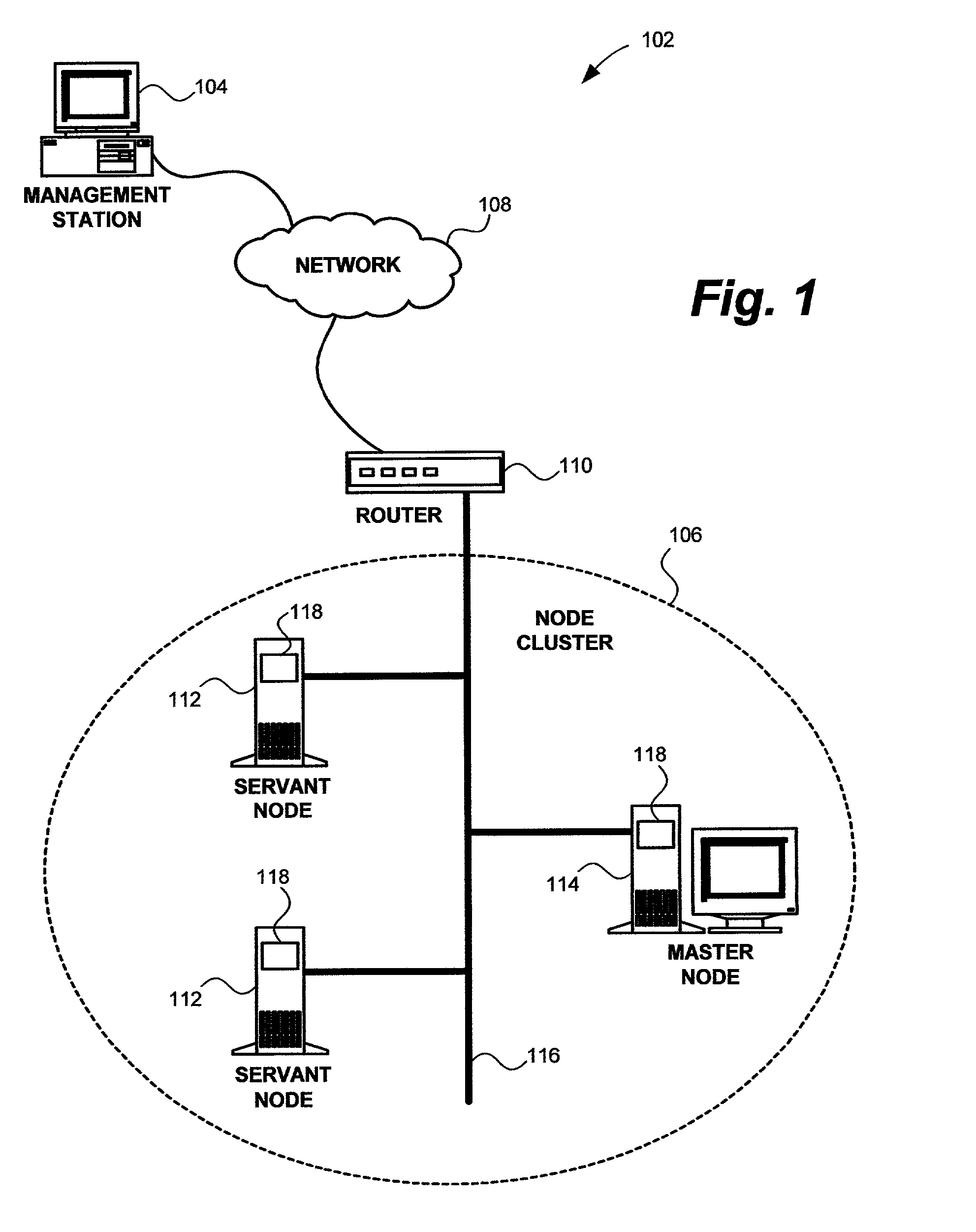
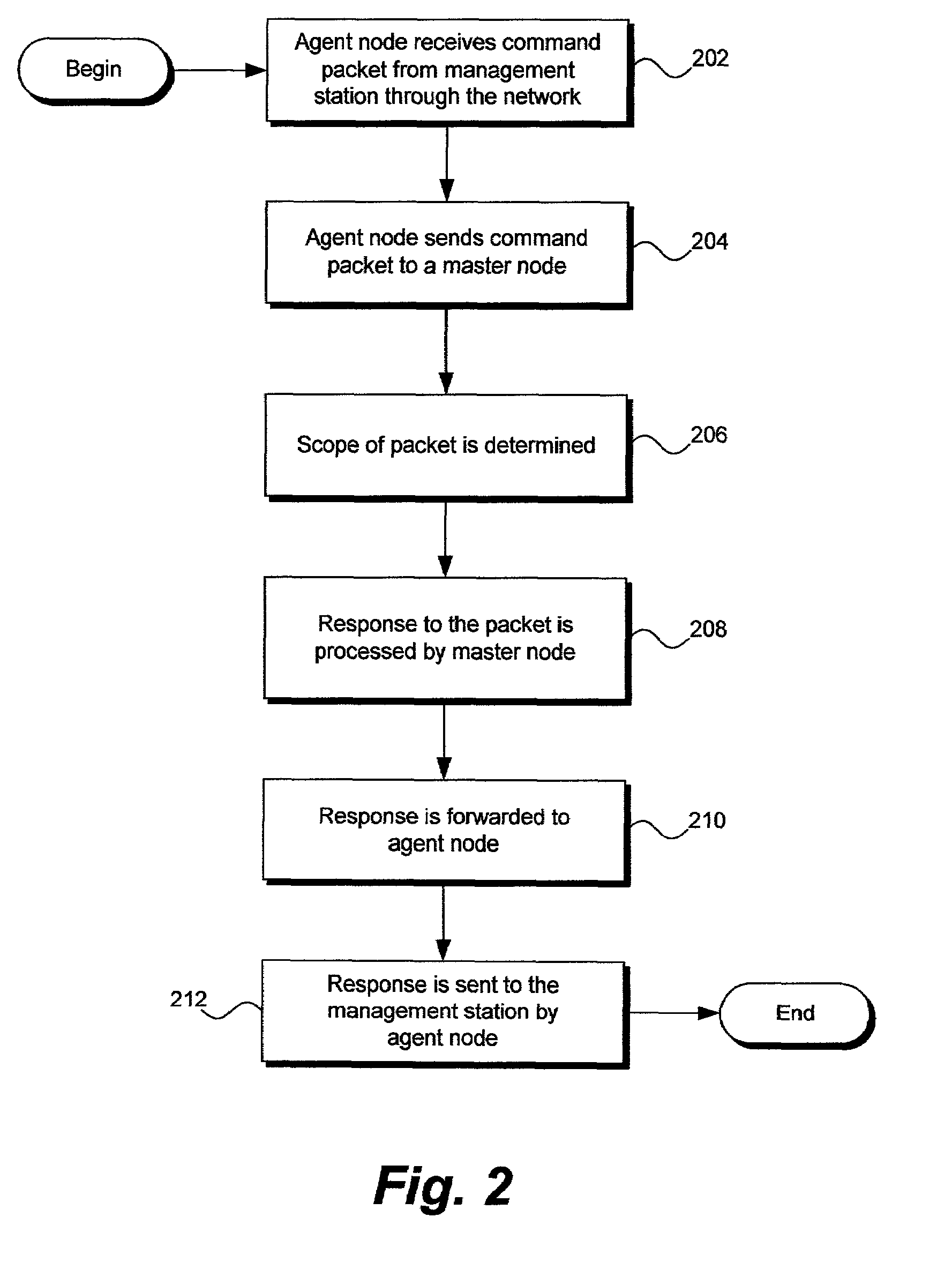
A method, system, and apparatus for a management station to manage a node cluster in a computer network. Regardless which node in the node cluster receives a management command from the management station to the master node, the management command is sent to the master node. The master node prepares a command response and sends the response back to the original node that received the management command. The original node, in turn, forwards the command response to the management station. The invention utilizes management agents executing on a master node and servant nodes to create and process the command response.
Owner:IBM CORP
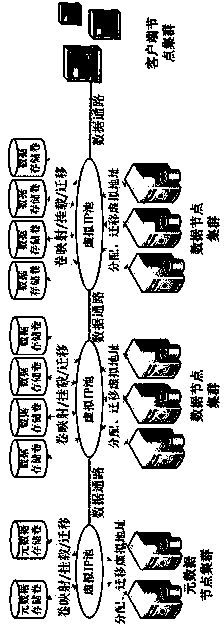
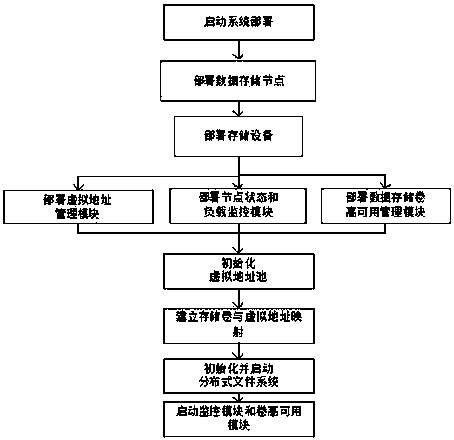
Distributed file system data volume deployment method based on virtual address pool
InactiveCN103475732AFlexible migrationEnsure service continuityTransmissionNode clusteringDistributed File System
The invention provides a distributed file system data volume deployment method based on a virtual address pool. A node cluster or a sub-cluster is built according to different node roles of metadata nodes, data storage nodes and client side nodes in a distributed file system; a data storage volume is deployed in a mode based on the virtual IP address pool on a data node cluster to separate the deployment of a distributed file system data storage volume from physical addresses of data nodes so as to combine the deployment of the data storage volume with virtual addresses of the data node cluster; a monitoring module is deployed on an operating node of the distributed file system so as to realize real-time monitoring of the operating conditions of the node and a load; according to the conditions of the node and the load, a virtual IP borne by any node and the data storage volume mounted on one virtual address are transferred in real time in the data node cluster; meanwhile, a failure of a physical node is also isolated, so that the effect that data services of the data storage volume are not interrupted when the physical node is maintained is ensured.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
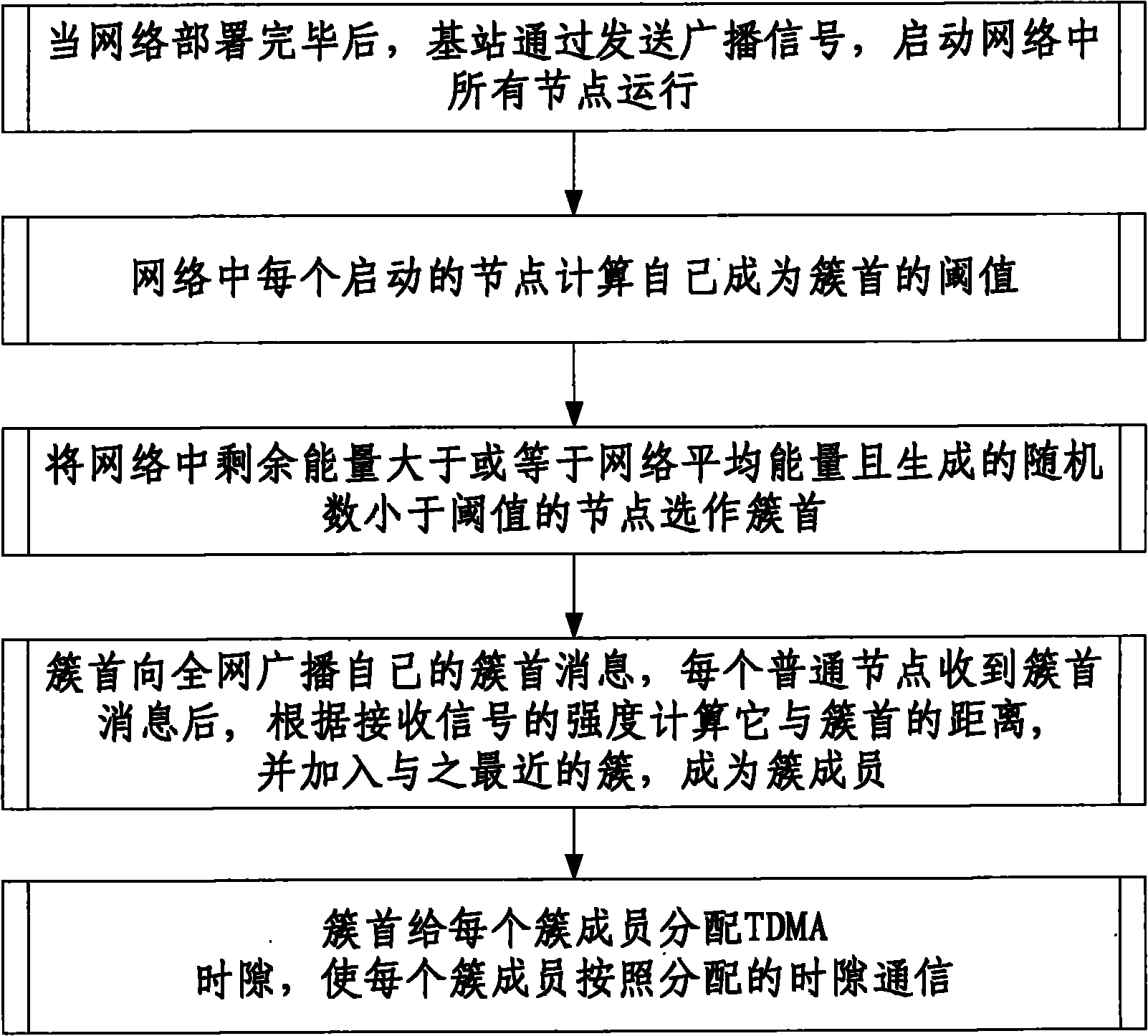
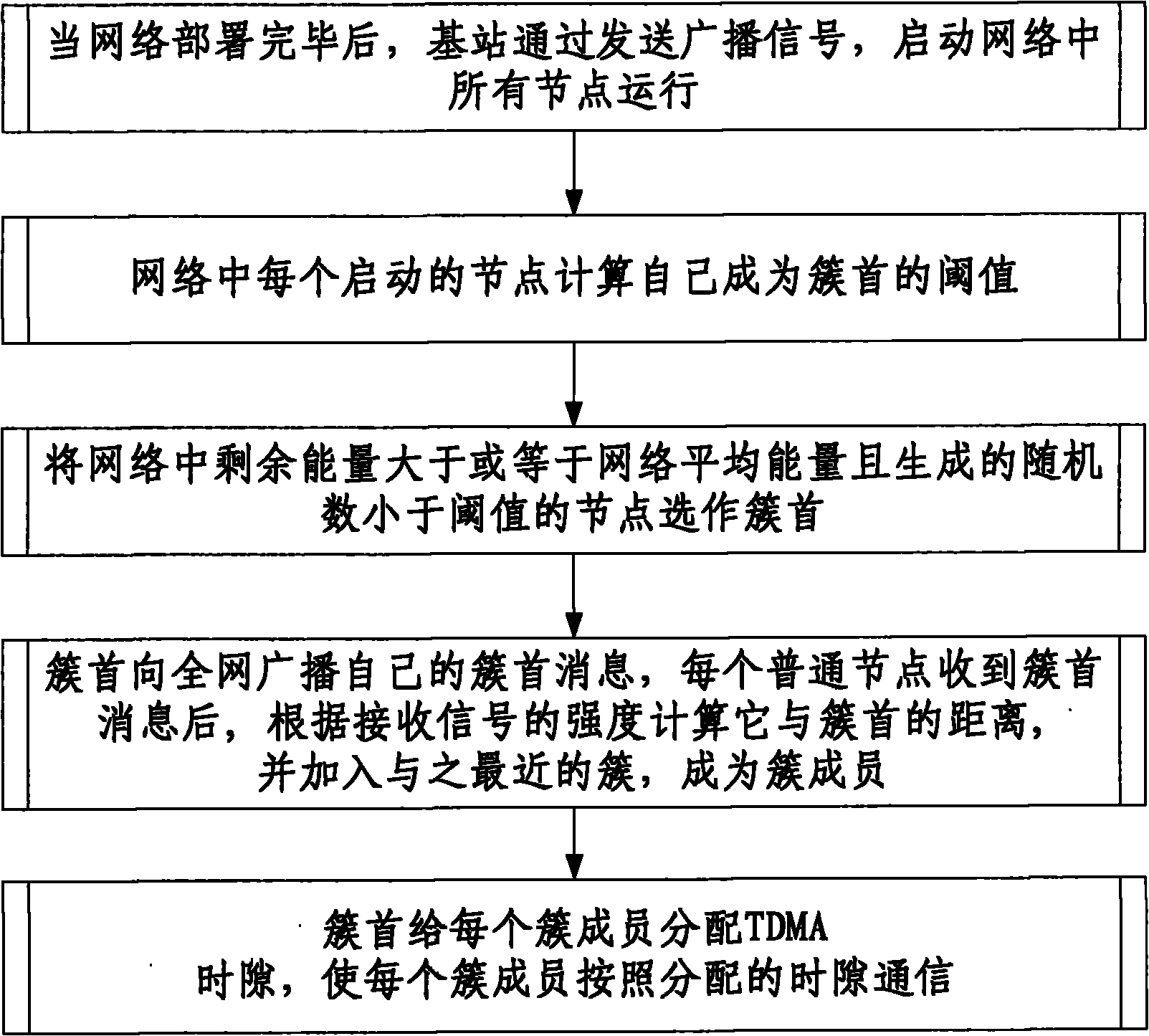
Energy priority node clustering method for wireless sensor network
ActiveCN102256267AProlong survival timeImprove performancePower managementNetwork topologiesNode clusteringRest energy
The invention discloses an energy priority node clustering method for a wireless sensor network. The method comprises the following steps that: after network deployment is finished, a base station starts running all nodes in a network by transmitting a broadcast signal; each started node in the network computes own threshold value for becoming a cluster head; the nodes of which rest energy is more than or equal to the average energy of the network and which generate random numbers lower than the threshold values in the network are selected to be the cluster heads; the cluster heads broadcast own cluster head messages to the whole network, and each ordinary node computes own distances away from the cluster heads according to received signal strength after receiving the cluster head messages, and is added into the closest cluster as a cluster member; and the cluster heads allocate time division multiple access (TDMA) timeslots to each cluster member, so that each cluster member performs communication according to the allocated timeslots. By the method provided by the invention, the time to live of the network can be remarkably prolonged, and performance remarkably higher than that of a low energy adaptive clustering hierarchy (LEACH) protocol is ensured.
Owner:兴科迪科技(泰州)有限公司
Data distributed storage system and method
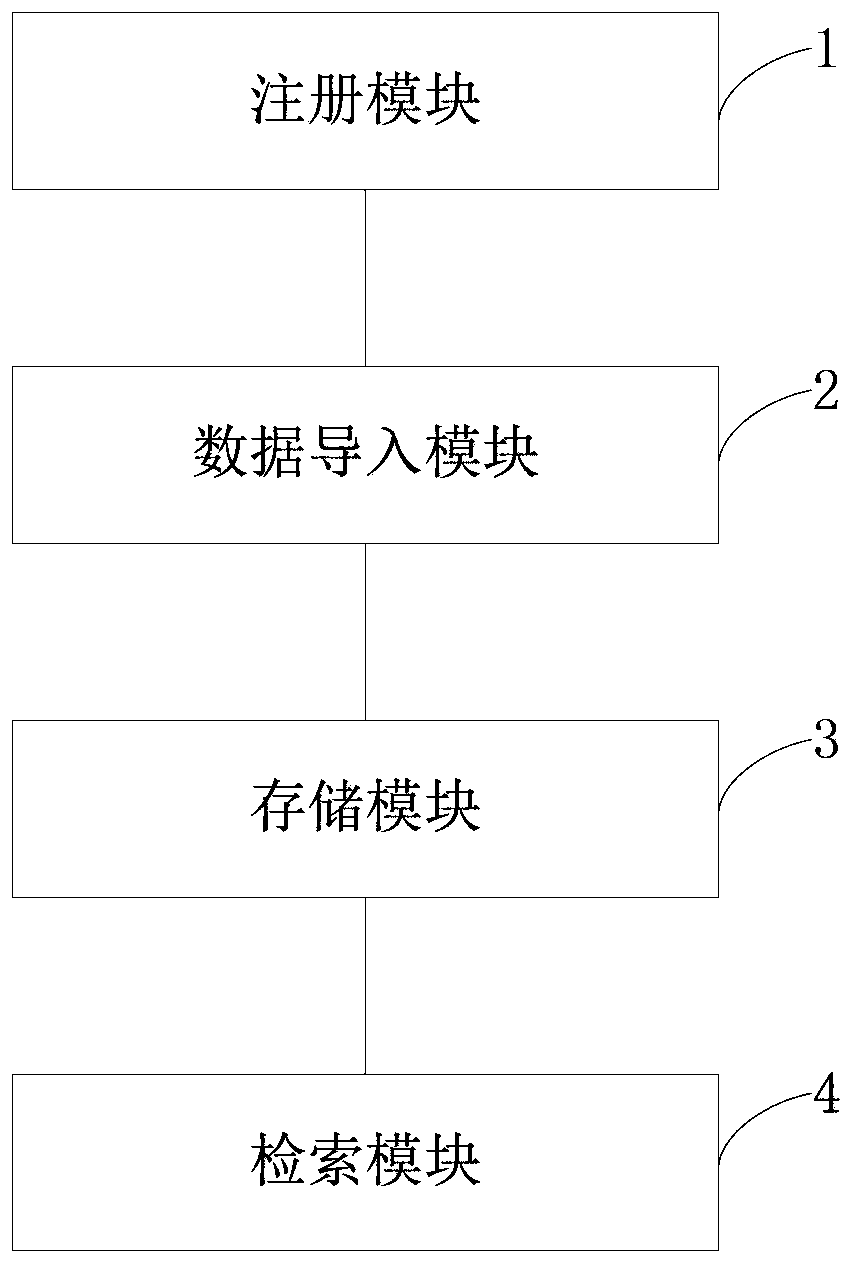
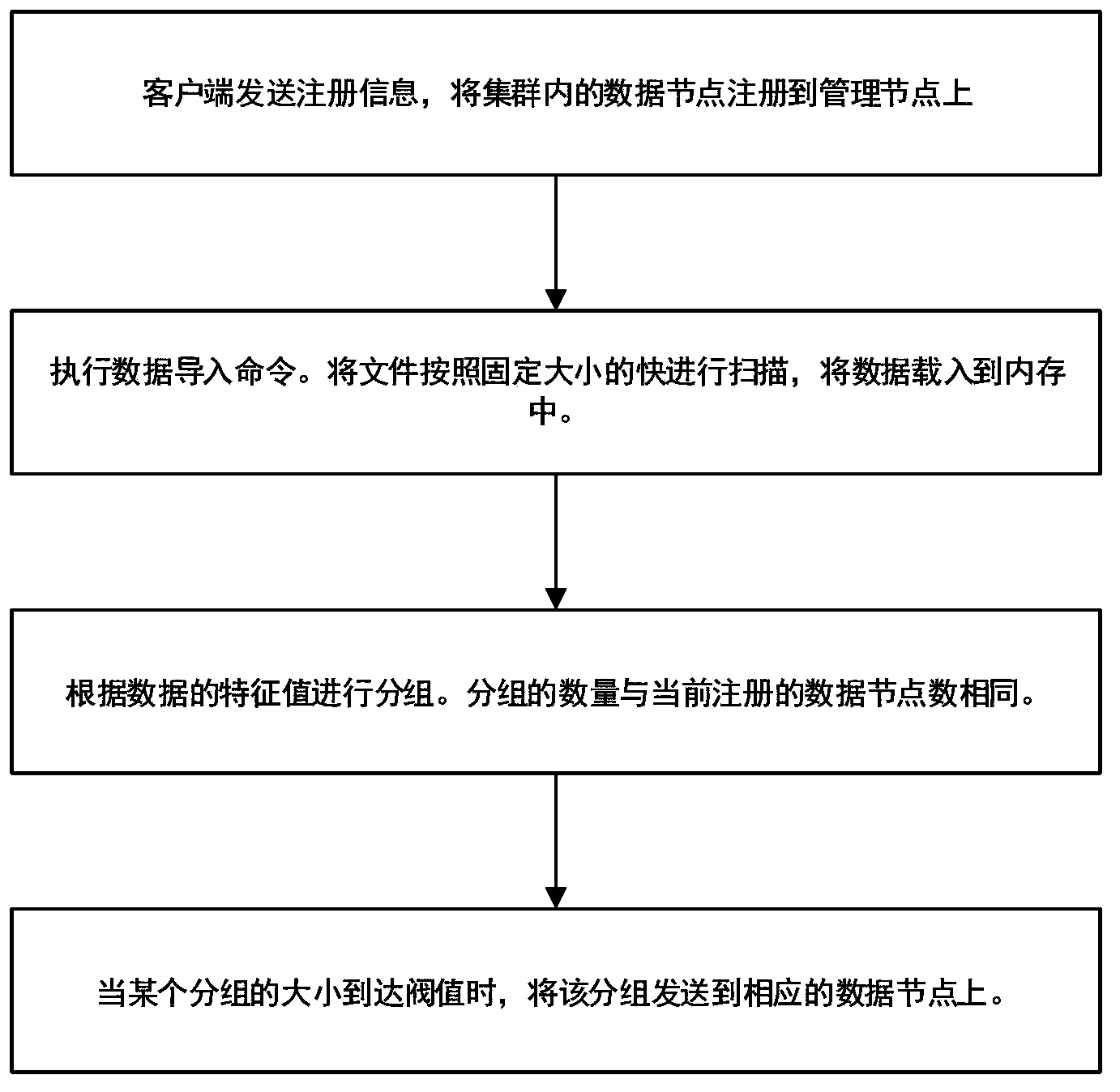
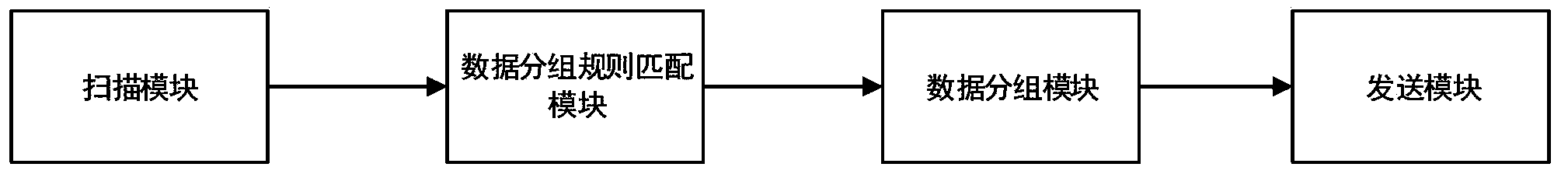
InactiveCN104123300AImplement real-time transaction processingEnsure safetySpecial data processing applicationsNode clusteringComputer module
The invention discloses a data distributed storage system and method. The system comprises a node cluster module, a data import module and a storage module. The node cluster module is used for connecting data nodes in a cluster with corresponding management nodes; the data import module is used for scanning input data according to data blocks with sizes set and loading the input data into a memory, data in the memory are grouped according to characteristic values of the data, and the grouped data are sent to the corresponding data nodes; the storage module is used for storing data fragmentations in the memory after the data nodes receive file fragmentations, and the data nodes output logs to a hard disk; whether the data in the memory exceed a set threshold value or not is judged, if the data in the memory exceed the set threshold value, the data are reorganized and compressed and then written into the hard disk, and corresponding log files restored through user memory data are deleted. According to the system and method, the cluster based on memory computing power can be accelerated; real-time loading and processing capacity for large-scale data can be improved, and response time of the system is shortened.
Owner:SHANGHAI PEOPLEYUN INFORMATION TECH CO LTD
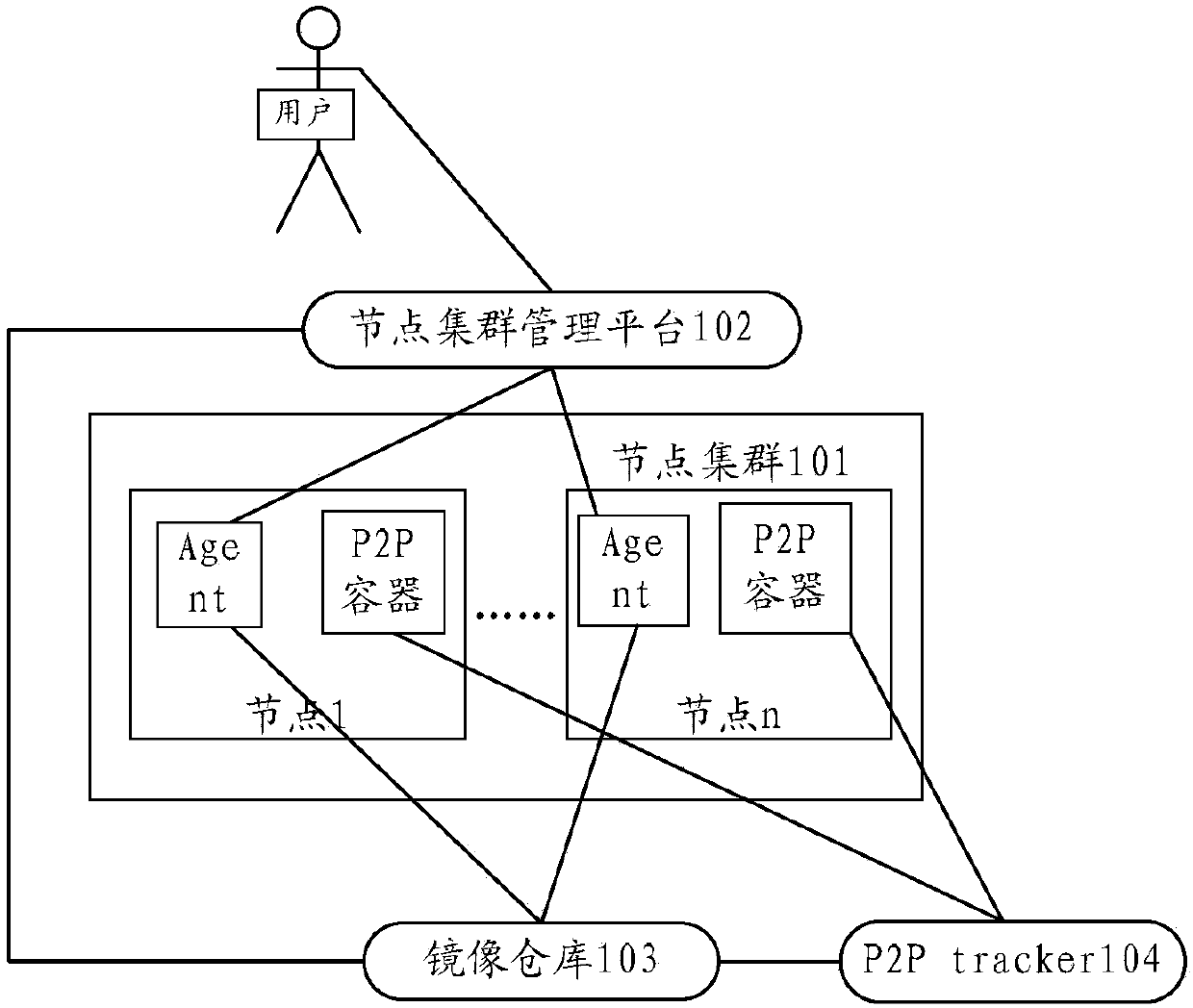
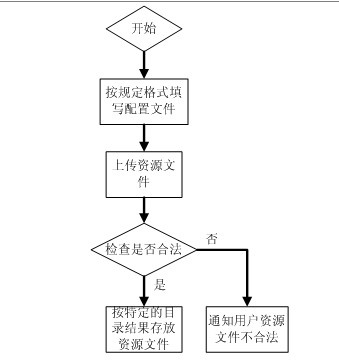
Image acquisition method in node cluster, node equipment and server
The embodiment of the invention provides an image acquisition method in a node cluster, node equipment and a server, and relates to the technical field of the information. The problem that a service container cannot operate as normal since the resource limitation of the existing service container cannot be used as normal under the situation that the used resource is unlimited when the existing cluster node downloads an image through a P2P way by starting a BT client is solved. The method comprises the following steps: a first node receives a service container operation request including an image identifier of the image of a first to-be-operated service container and the resource limitation of the first to-be-operated service container, and requests mirror distribution information corresponding to the mirror identifier from the first server; when an acquisition way of the image layer comprises the P2P acquisition way, the first node creates a P2P container, and sets that the operation resource limitation of the P2P container to be less than and equal to the resource limitation of the first to-be-operated service container, and an image layer compression sack corresponding to the image layer identifier is acquired through the P2P container.
Owner:HUAWEI TECH CO LTD
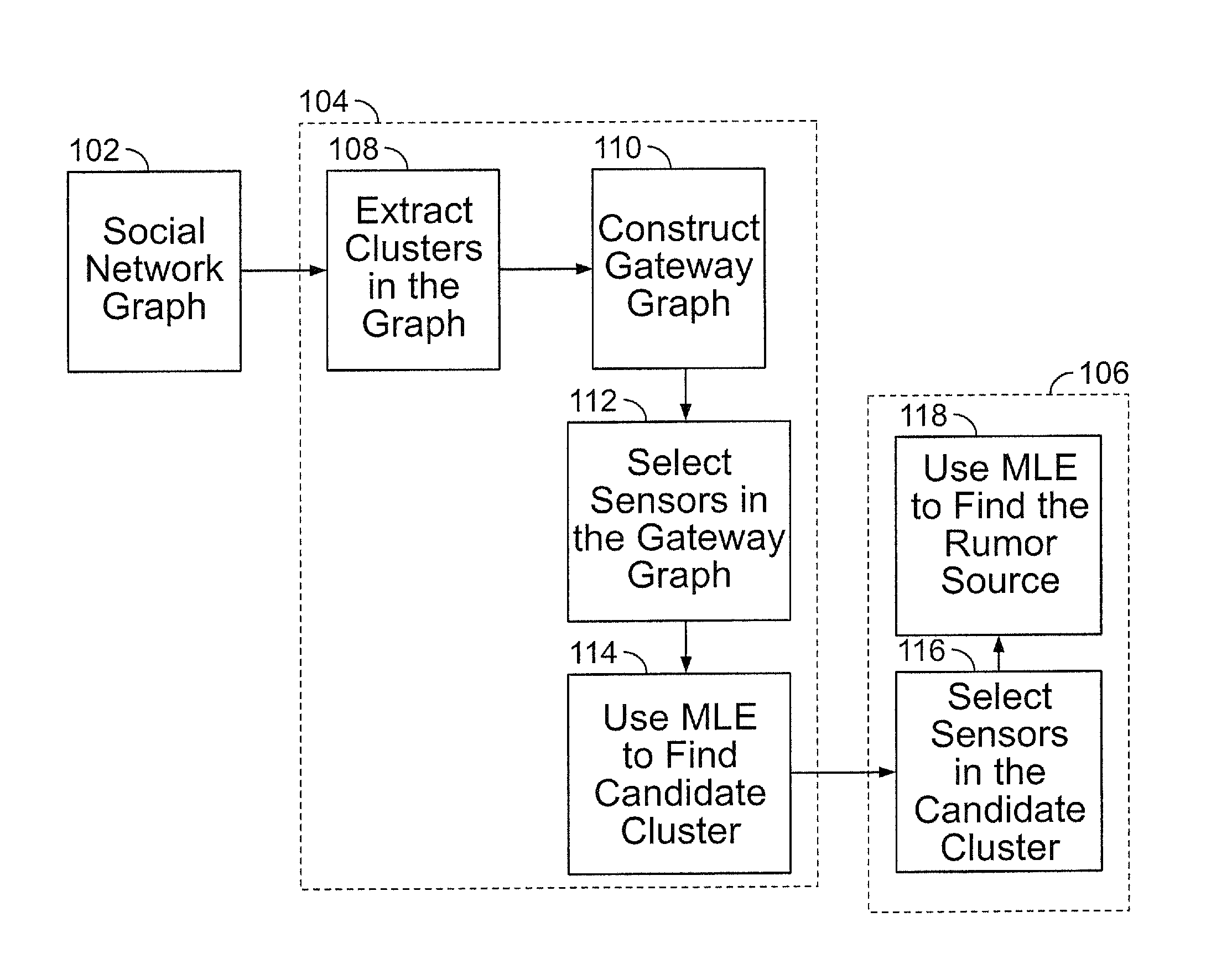
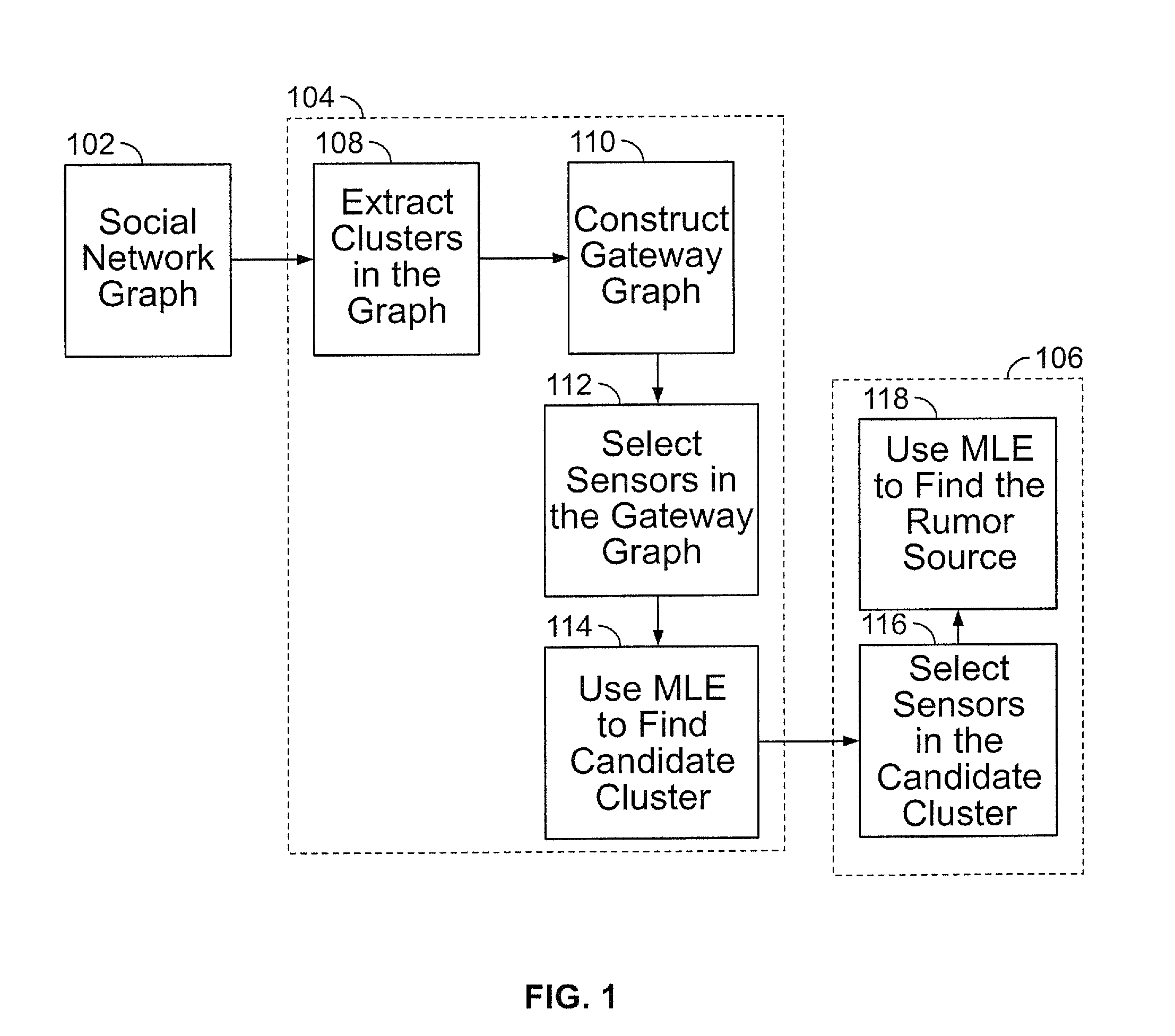
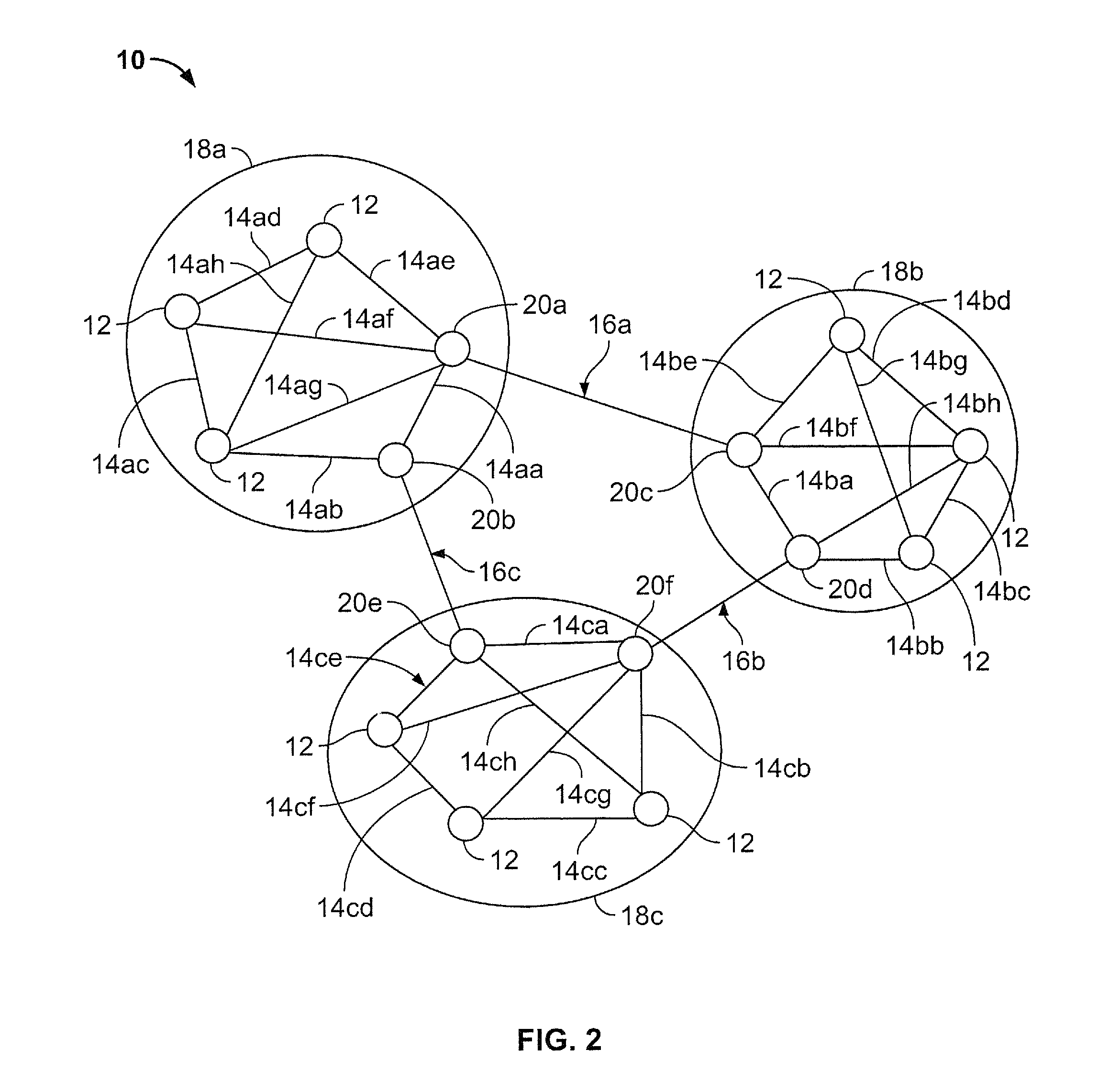
Method and Apparatus to Identify the Source of Information or Misinformation in Large-Scale Social Media Networks
ActiveUS20160212163A1Increase probabilityDigital data information retrievalMemory loss protectionNode clusteringHigh probability
A system and method of detecting a source of a rumor in a social media network is disclosed. The social media network includes a plurality of node clusters, each of the plurality of nodes therein having at least one edge connection to a corresponding number of different nodes in the same cluster. The system identifies a plurality of gateway nodes, each having at least one weak tie connection with a corresponding gateway node from a different node cluster; selects a subset of gateway nodes as sensors to measure arrival times of a rumor; and selects a candidate node cluster based on these arrival times. From there, the system selects a set of nodes in the candidate cluster to measure arrival times of a rumor from a source node, and selects a candidate node from the candidate cluster as having a high probability of being the source node.
Owner:STEVENS INSTITUTE OF TECHNOLOGY
Graph data processing method and graph data calculation task distribution method
ActiveCN108683738AImprove publishing efficiencyImprove processing efficiencyEncryption apparatus with shift registers/memoriesProgram controlNode clusteringDistribution method
Owner:TENCENT TECH (SHENZHEN) CO LTD
Neural network-based mobility management for mobile ad hoc radio networks
InactiveUS7742425B2Easy to addEasy to insertError preventionTransmission systemsNode clusteringRadio networks
A self managed ad hoc communications network and method of managing the network. The network includes wireless devices or nodes that include a neural network element and the ad hoc network operates as a neural network. One of the nodes is designated as a Network Management System (NMS) that provides overall network management. Clusters of nodes are organized around cluster leaders. Each cluster leader manages a cluster of nodes and communications between node clusters. Each cluster may also have other nodes identified as lower order cluster leaders.
Owner:THE BOEING CO
Wireless sensor network, establishing method and communication method
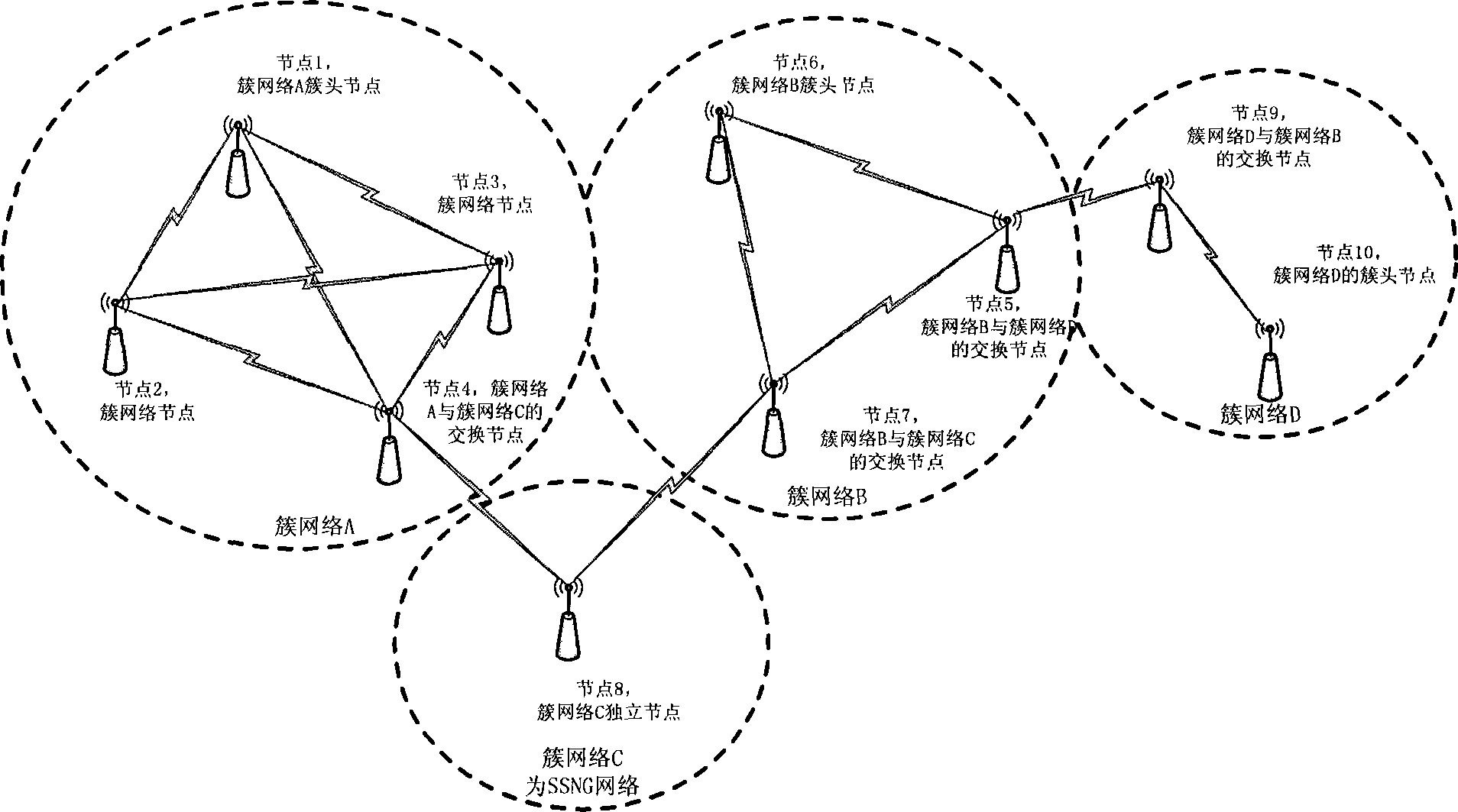
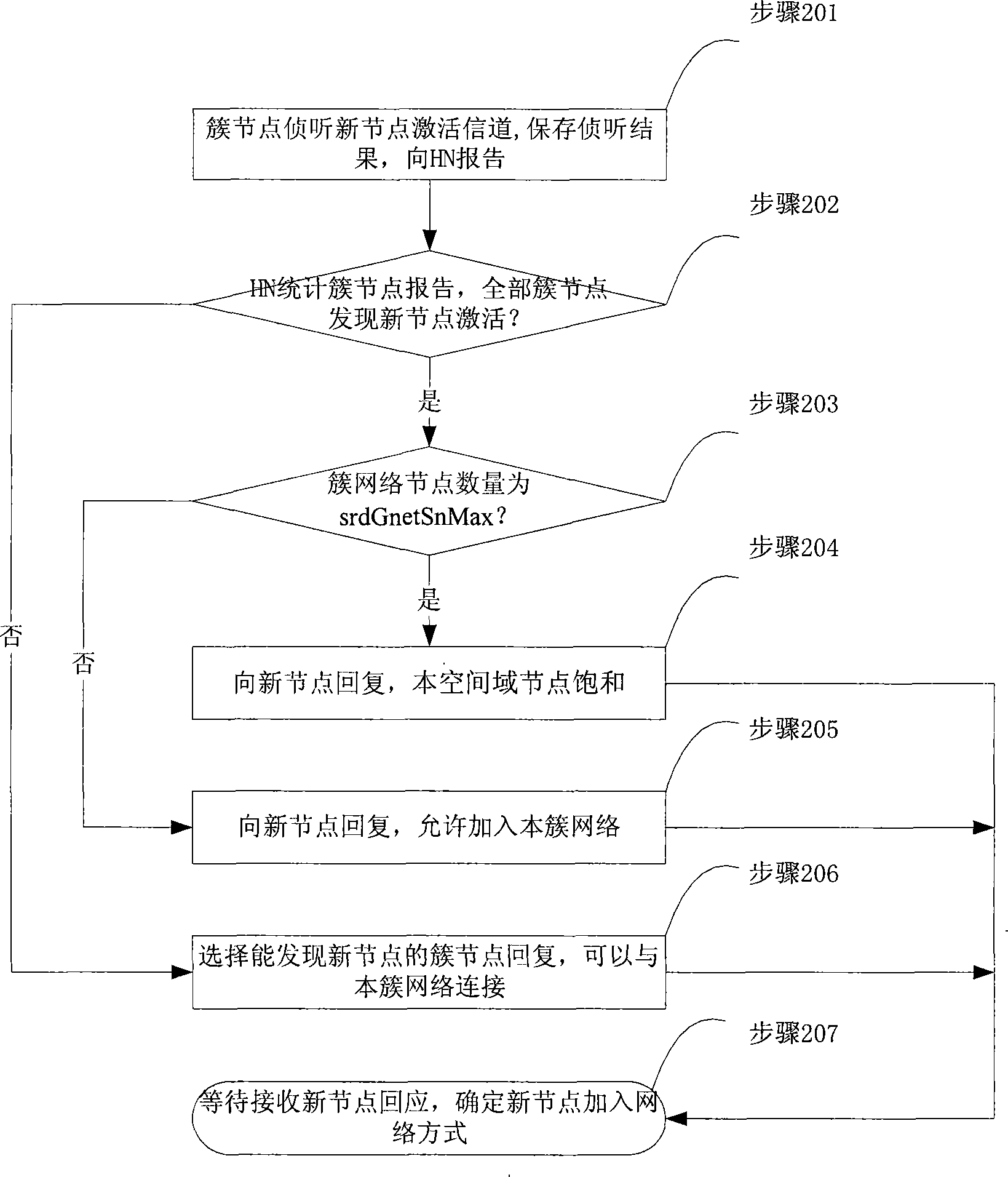
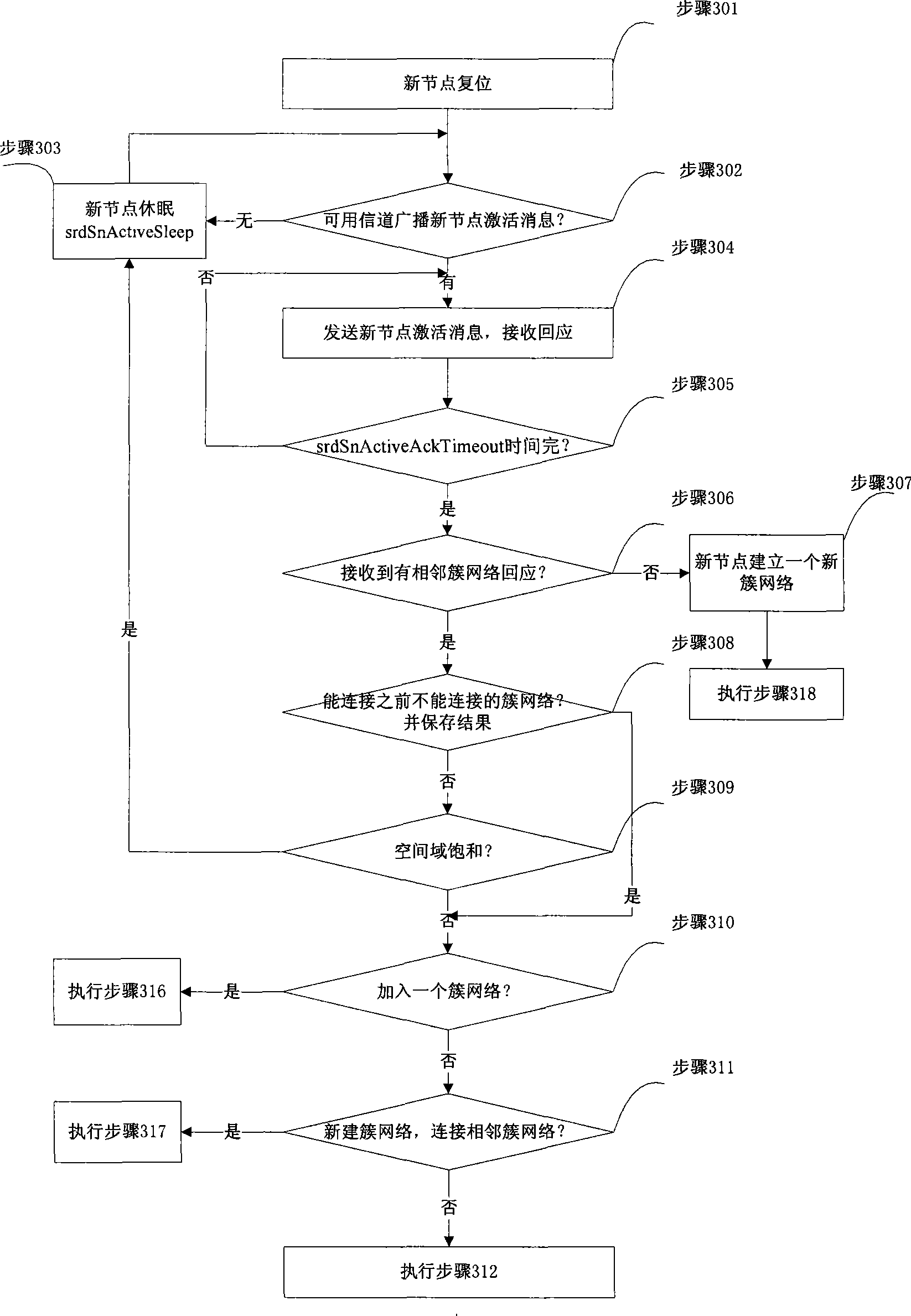
InactiveCN101247342AEasy to deployGuaranteed vandal resistanceData switching by path configurationNode clusteringWireless mesh network
The invention discloses a wireless sensor network and constructing method and communication method capable of self-adapting the web knot according to network structure variation, and variation of service data transferring demand and variation of network management command. The wireless sensor network is isomorphism grouping network structure of node cluster management. Make the knobs which can directly communicate into a cluster, constructing a topological structure of cluster network linking. The communication dispatching of the network nodes can be divided into intra-cluster nodes communication dispatching and inter-cluster nodes communication dispatching. According to the network structure design, set the intra-cluster network nodes constructing cluster network work periods. A cluster network working period comprises cluster resting period, inter-cluster interchanging nodes communicating work period and intra-cluster nodes communication work period. The network nodes is used for self-adapting each working period and the communication time of cluster nodes of each working period, and communication time width to reach the network optimization.
Owner:毛宏伟
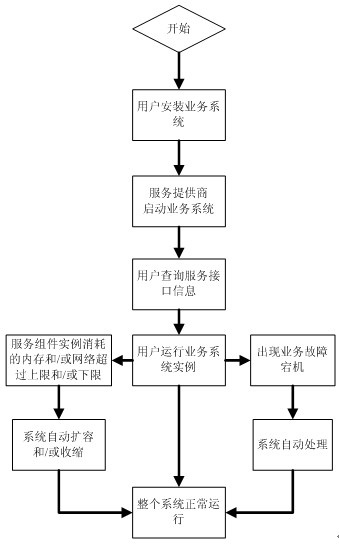
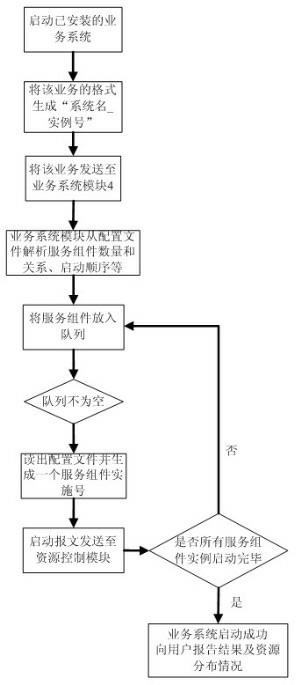
Distributed service integrated system for service-oriented architecture and application method thereof
InactiveCN102624919ARealize dynamic managementImprove availabilityTransmissionNode clusteringService control
The invention discloses a distributed service integrated system for a service-oriented architecture and an application method thereof and belongs to computer application technique. The defects that a present service system cannot perform dynamic management, the automatic expanding and contracting capacities of service component examples are poor and the simultaneous proceeding of large-scale service system examples cannot be supported are overcome. The distributed service integrated system is mainly composed of a deploying node cluster, a service control processor, a resource control server, a Web gateway and a service access point. According to the distributed service integrated system provided by the invention, the operations by a service provider and a user are simplified; a stable operation environment is provided; multiple operation requests of service systems are concurrently processed; when the deploying nodes are subjected to fault crash, the relation thereof is analyzed, and the corresponding examples are informed of registered information and are caused to correspondingly process, so that the service supplied by the service system can be recovered and be reusable within a short period of time and the high applicability of the system is realized; and the distributed service integrated system is suitable for being popularized and applied.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
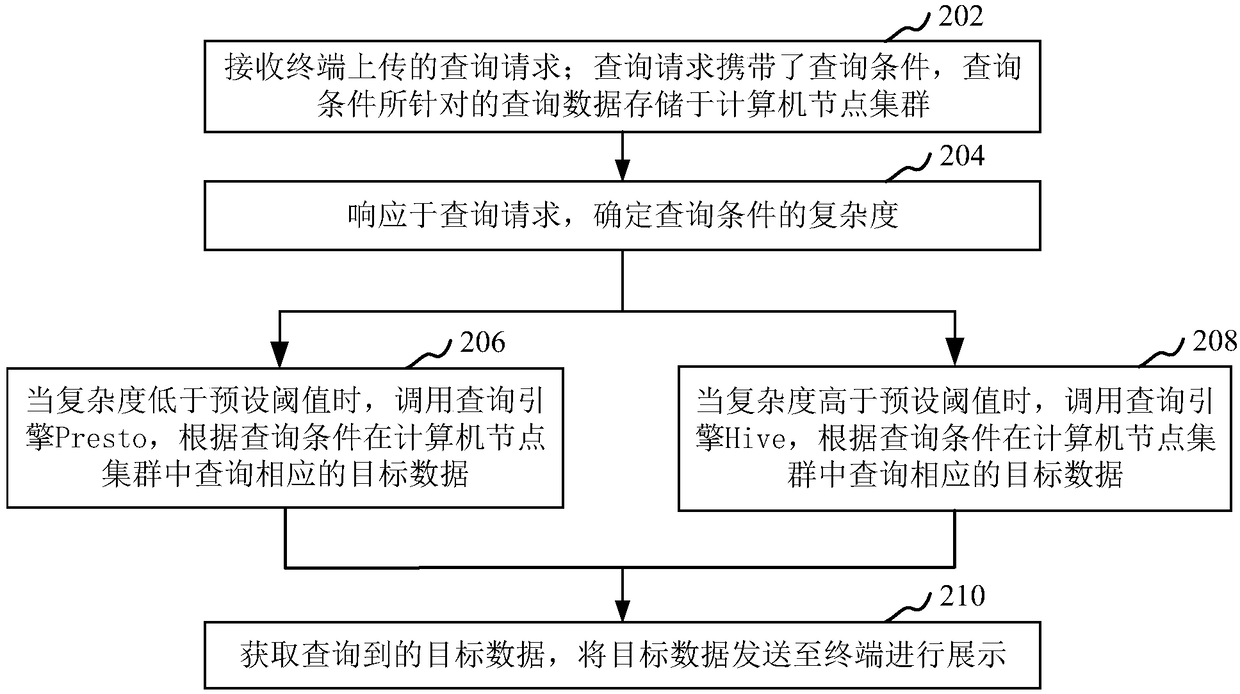
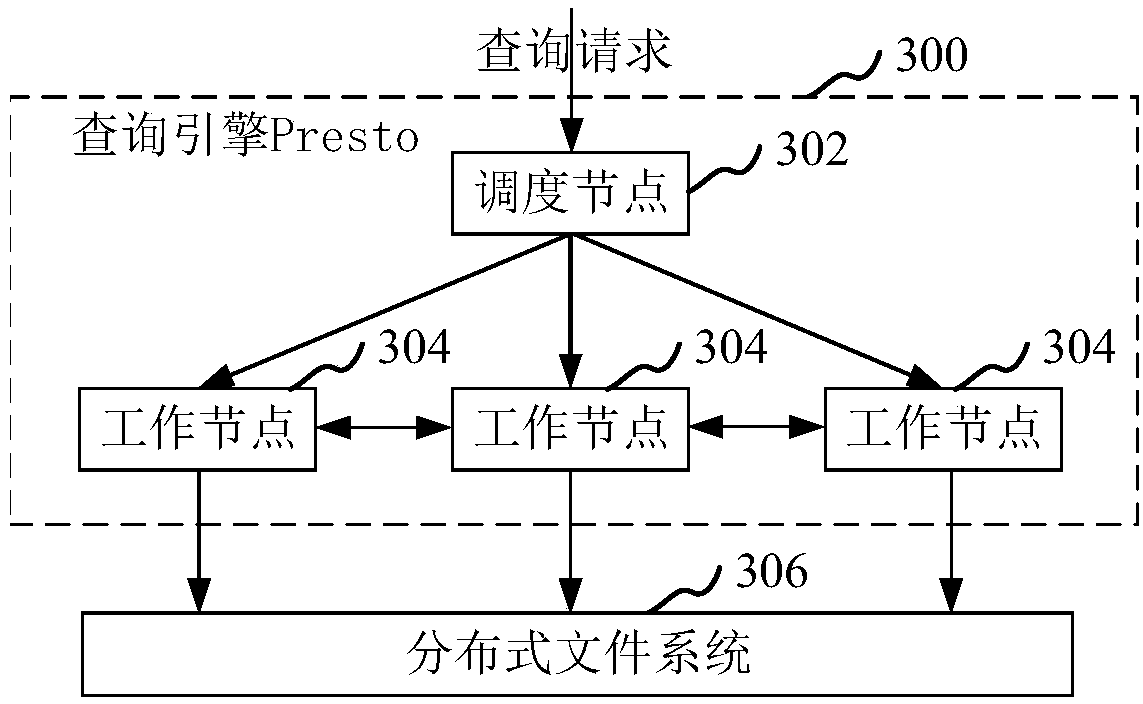
Big-data-based query method and device, computer device and storage medium
ActiveCN109033123AAvoid disadvantagesSpecial data processing applicationsNode clusteringComputer terminal
The present application relates to a big-data-based query method and device, a computer device and a storage medium. The method comprises the following steps of: receiving a query request uploaded bya terminal, wherein query request carries the query criteria, and the query data targeted by the query criteria are stored in the computer node cluster; determining a complexity of a query condition in response to a query request; when the complexity is lower than the preset threshold, calling the query engine Presto to query the corresponding target data in the computer node cluster according tothe query criteria. When the complexity is higher than the preset threshold, the query engine Hive is called to query the corresponding target data in the computer node cluster according to the querycriteria. The queried target data are obtained and sent to the terminal for display. Adopting the method, the corresponding query engine can be adaptively selected in the large data query process.
Owner:KANG JIAN INFORMATION TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com