Method and system for detecting large-scale malicious web pages
A malicious web page and detection method technology, applied in the field of computer security, can solve the problems of not providing continuous operation and low analysis efficiency, and achieve the effect of efficient update, high analysis efficiency, and convenient update
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
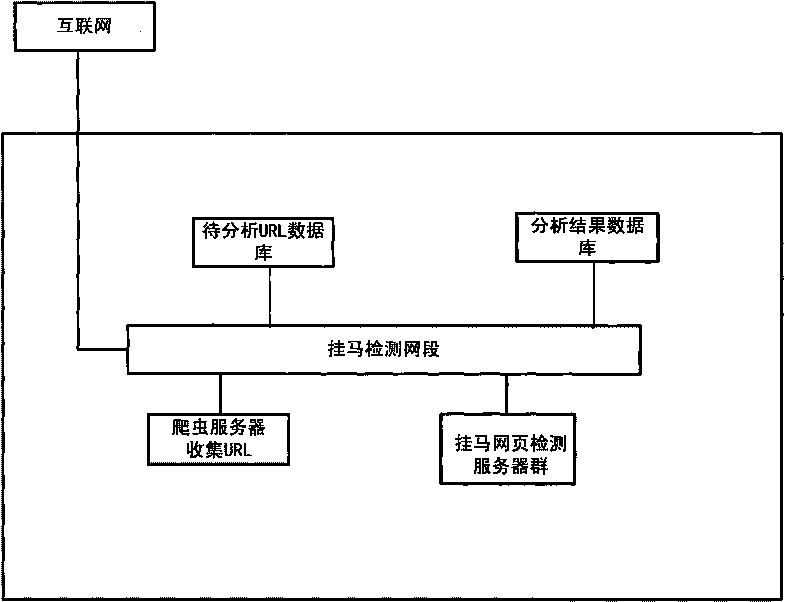
[0076] According to the technical method in the content of the invention, we have implemented a large-scale network horse detection and analysis environment, combined with the accompanying drawings to illustrate our specific implementation as follows:
[0077] 1) Detect the implementation strategy of the server layer:
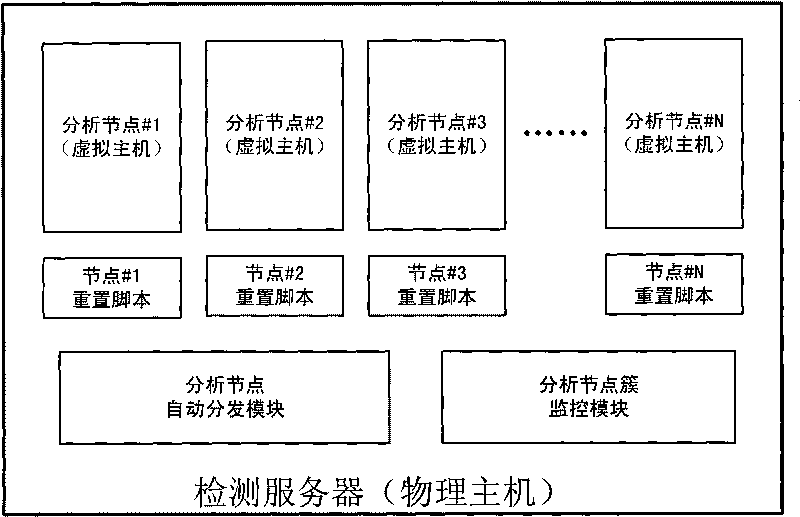
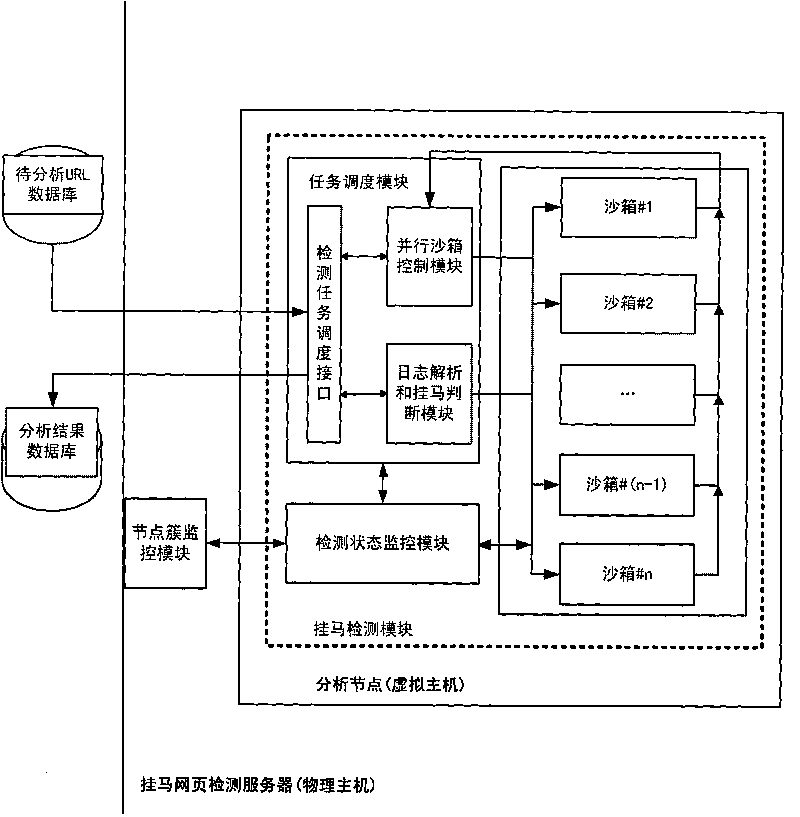
[0078] a) Deployment of analysis node clusters: Currently, our system uses 64-bit servers to build analysis node clusters, deploying 8 virtual host analysis nodes in each server to form an analysis node cluster, and deploying 10 parallel sandboxes in each node box, a single server can simultaneously analyze 80 URLs in parallel;
[0079] b) Distribution of analysis nodes: When the environment of analysis nodes needs to be updated, the distribution module of analysis nodes can be started and run through remote control, the initial image of analysis nodes can be obtained through ftp, and the virtual machine copy written by the API interface provided by the virtual...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com