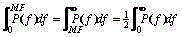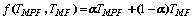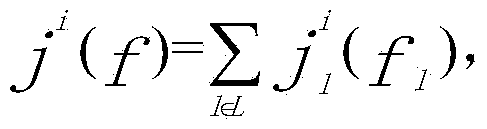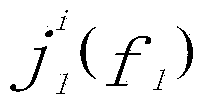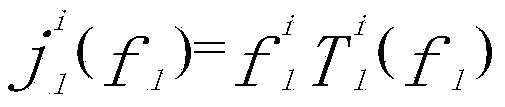Patents
Literature
701results about How to "Will not affect operation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
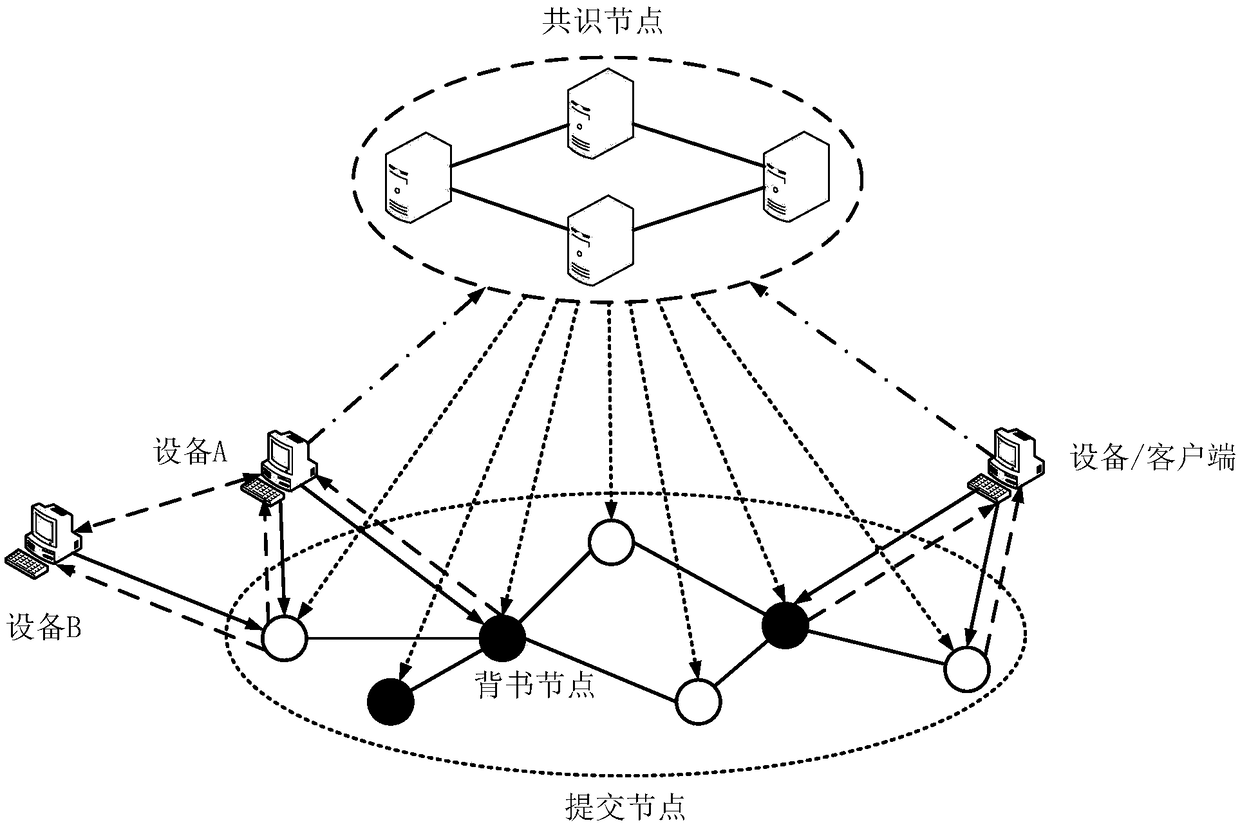
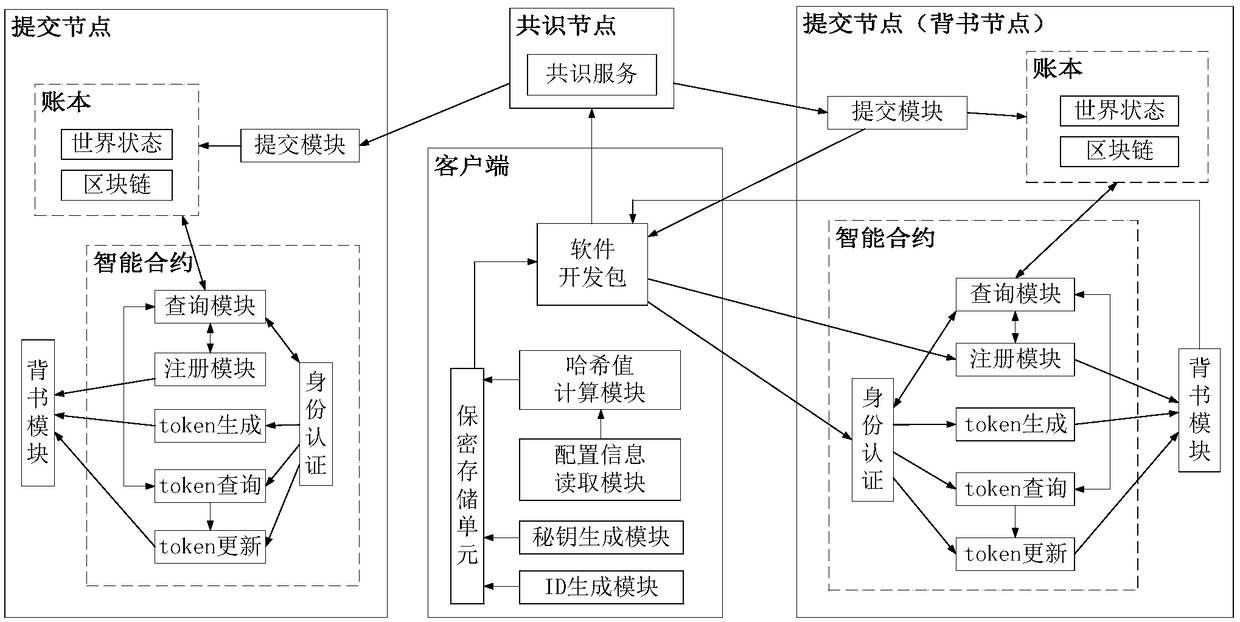
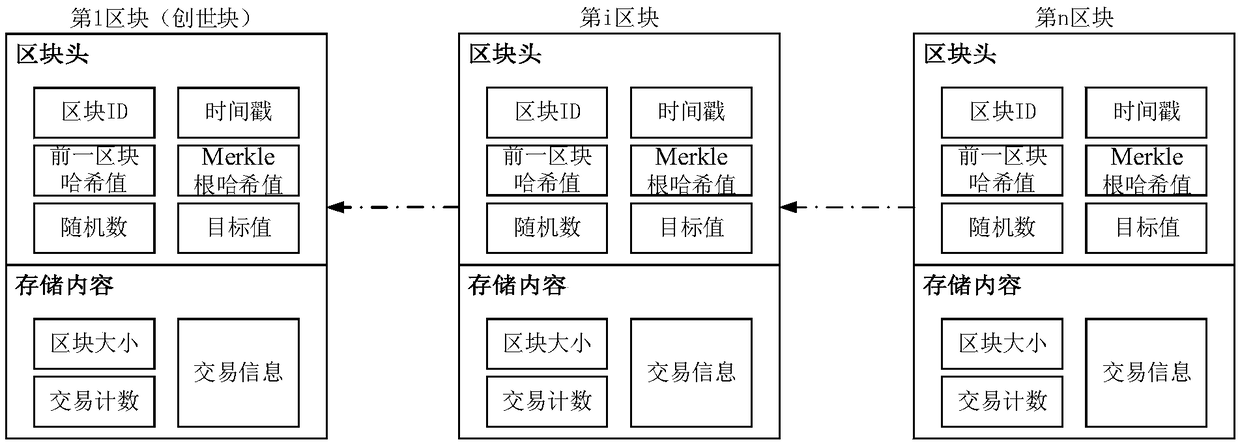
Device networking authentication method based on blockchain
ActiveCN108833081AGuaranteed legalityWill not affect operationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTimestampSmart contract
The invention discloses a device networking authentication method based on a blockchain for solving the single point failure problem existing in the current networking authentication method. The technical scheme is to deploy a blockchain network comprising a client, a submission node and a consensus node. By means of the non-tampering property of the blockchain, a device firstly registers on the blockchain before accessing the network, when the device A needs to access the network, the device sends a networking request of a device B that has accessed to the network, the device B compares the information of the device A in the networking request with the information of the device A stored in the blockchain to judge whether the identity of the device A is legal, a smart contract issues a token to the device A, a timestamp in the token ensures that the device A is valid within a certain period of time, and after the token expires, the device A needs to pass the identity authentication toaccess the network again. By adoption of the device networking authentication method disclosed by the invention, the single point failure problem existing in the traditional networking authenticationmethod can be avoided, the legality of the identity of the device is ensured, and the security of the network is improved.
Owner:NAT UNIV OF DEFENSE TECH
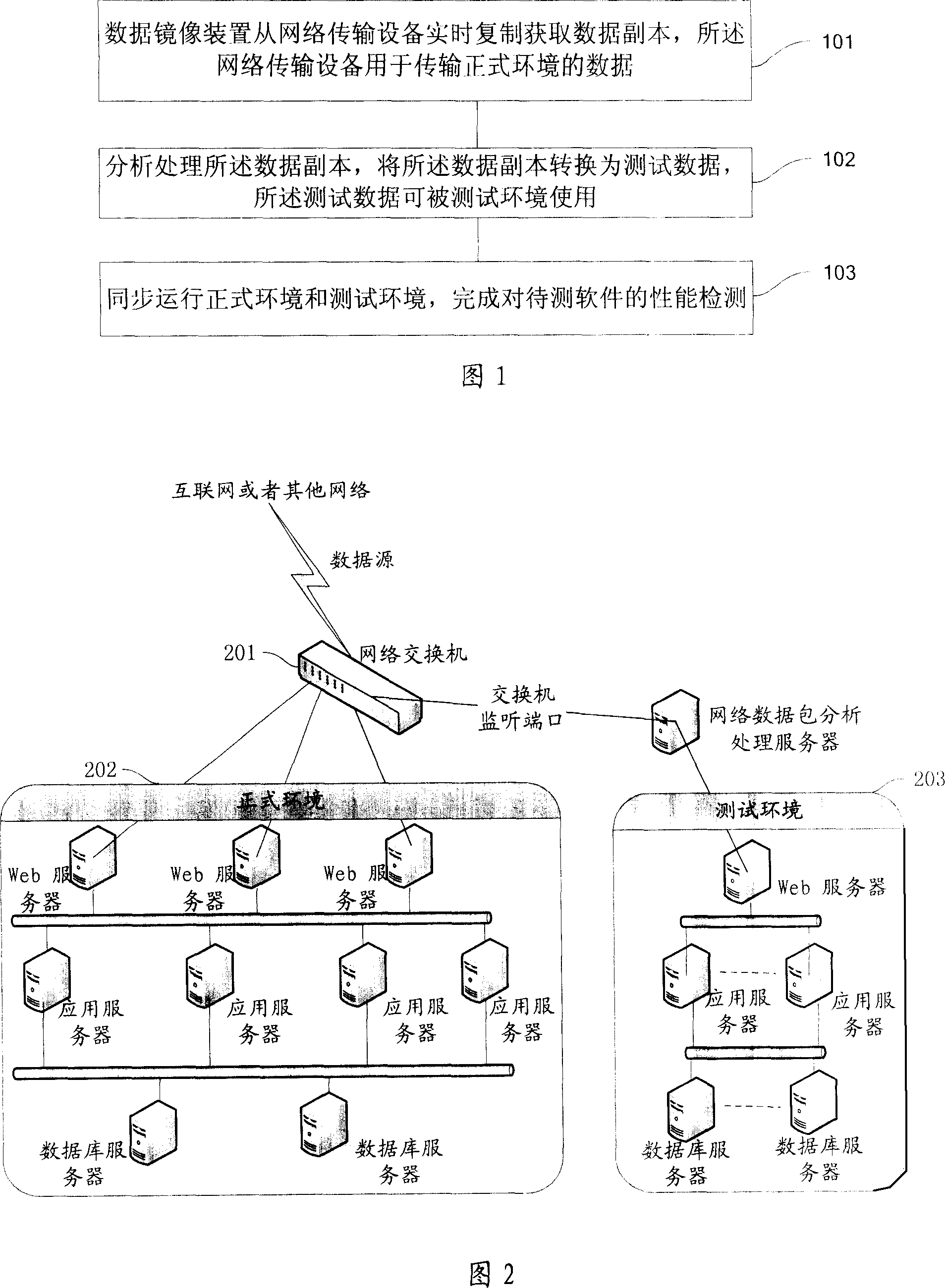
Test method and system for network application software
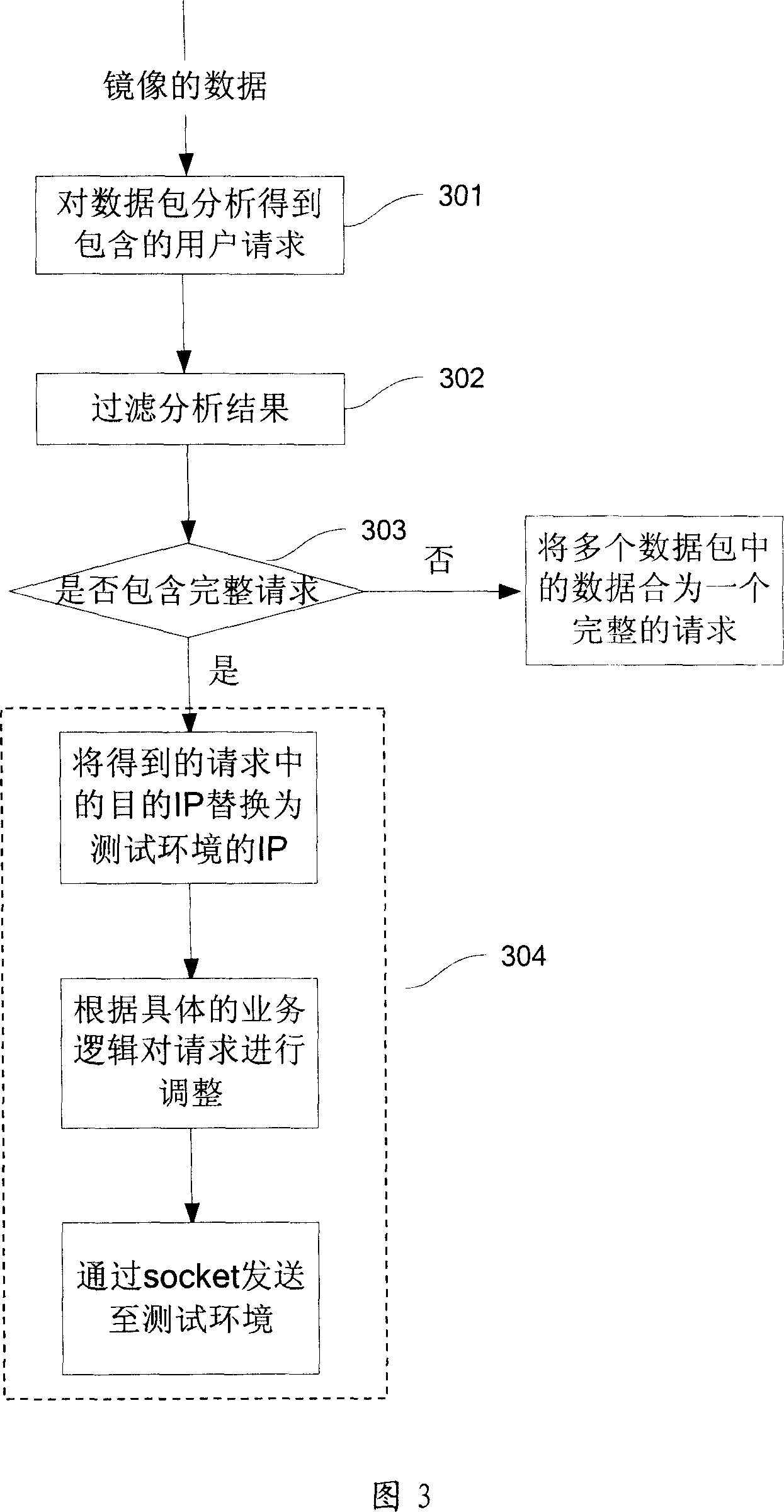
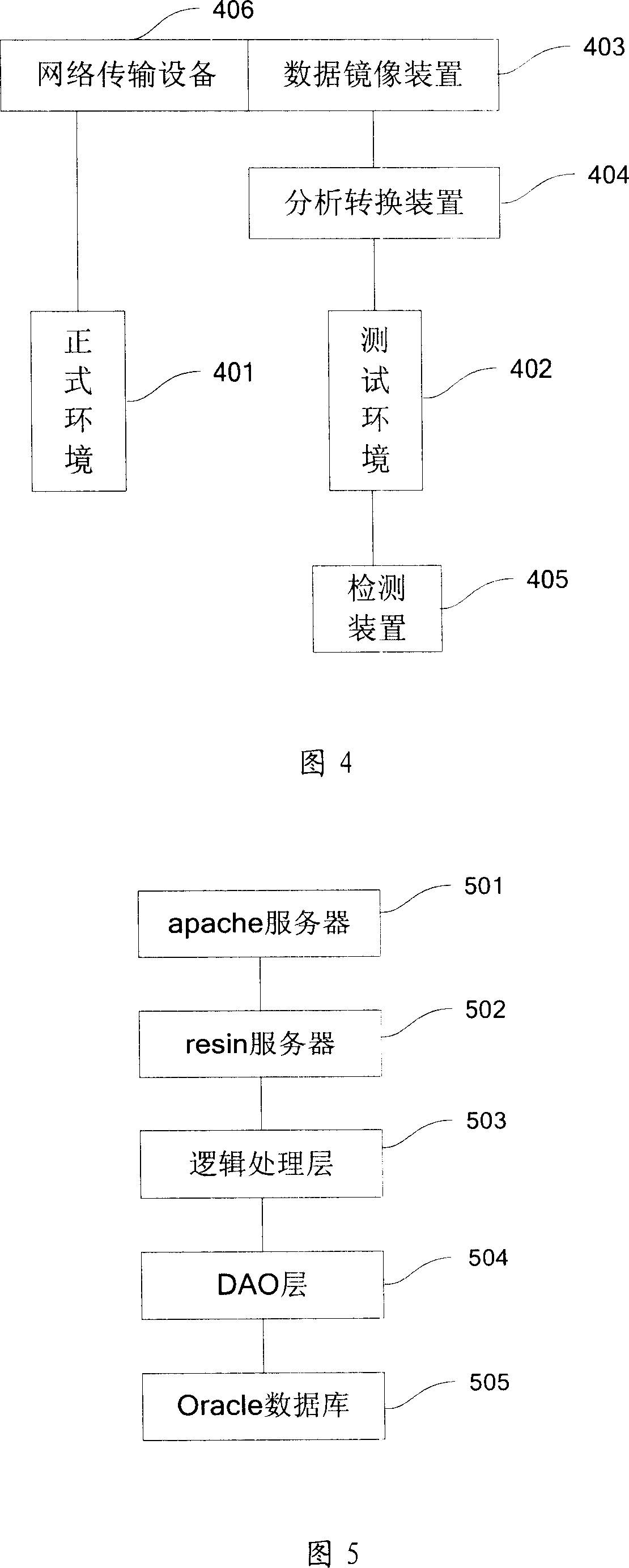
InactiveCN101001183AThe test is complete and relatively accurateAchieve replicationSoftware testing/debuggingData switching networksComputer hardwareGeneration process
This invention provides a test method and a system for network applied software, in which, the method includes: a data imaging device copies timely from a network transmission device to get a data copy, said network transmission device is used in transmitting data of normal environment, analyzing and processing said data copy to convert it to test data, which can be used by the test environment, operating the normal environment and test environment synchronously to finish the performance test to being tested software. The hardware part finishes the copy of the lowest bottom data in the network protocol and the software part re-processes data to input the processed data to the test environment to generate and produce operation scene in the same environment.
Owner:NETEASE INFORMATION TECH(BEIJING) CO LTD
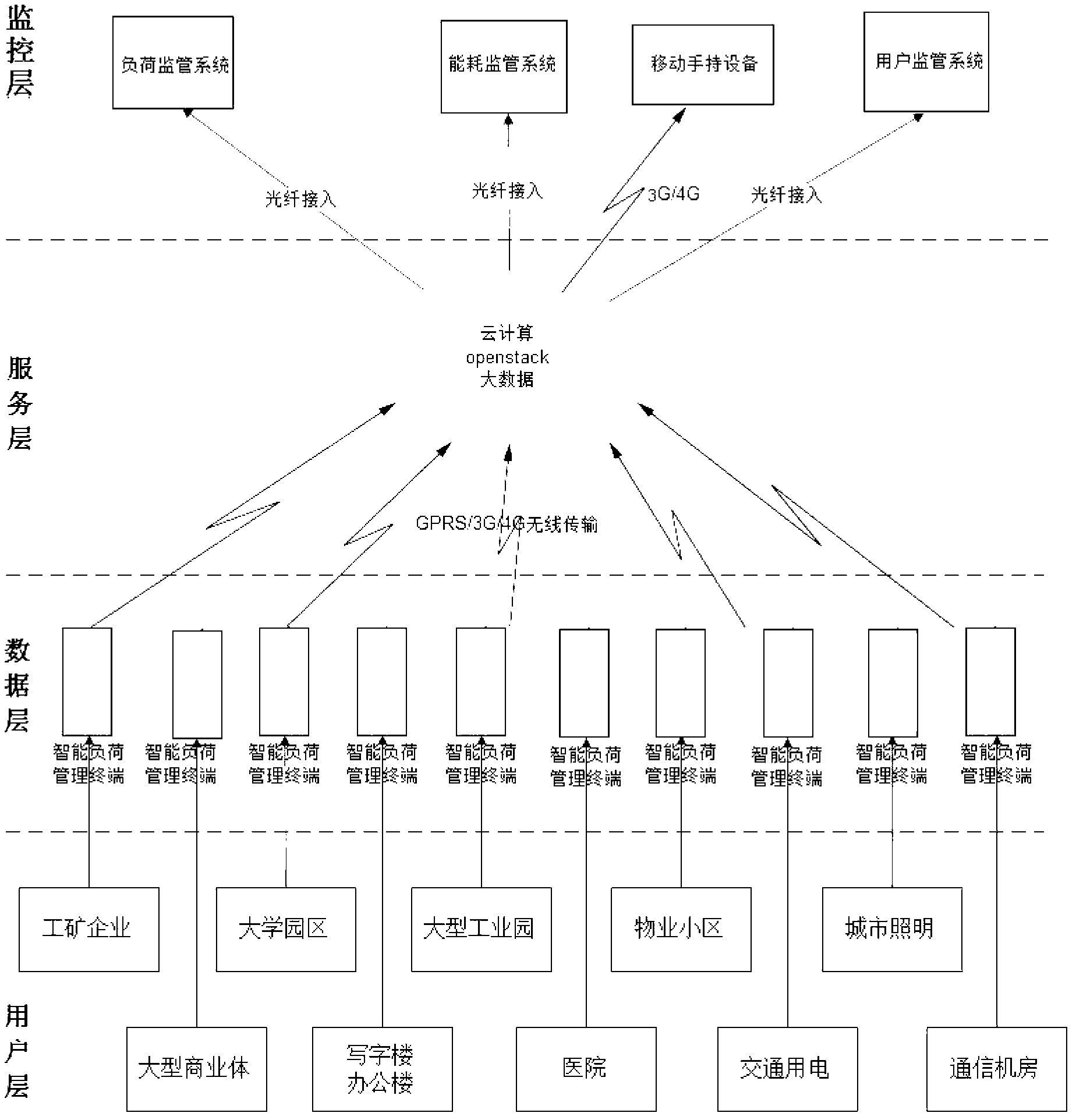
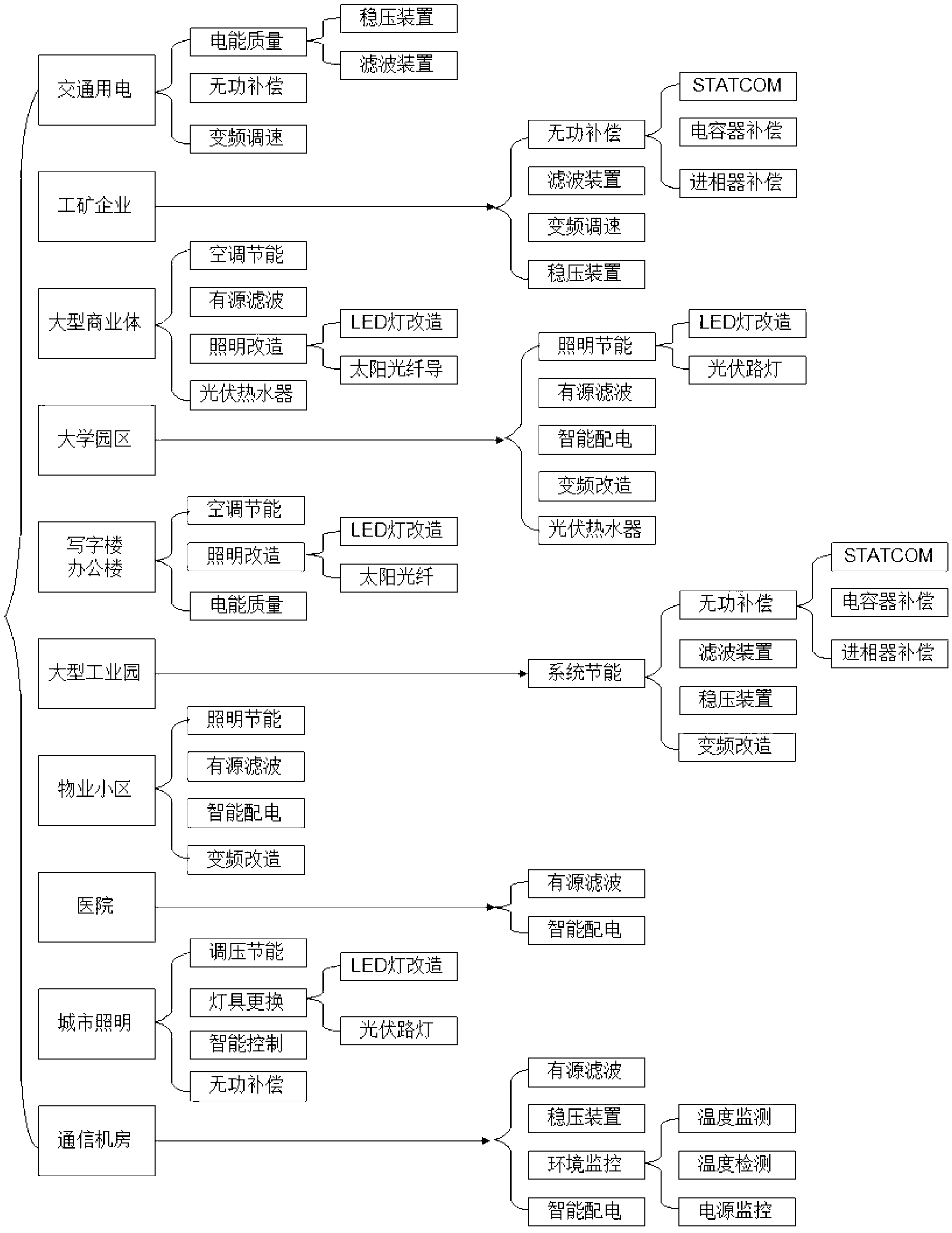
Power demand side monitoring system and method
ActiveCN103268115AWide range of industriesEasy to useEnergy industryTotal factory controlInformation resourceDistribution power system
The invention discloses a power demand side monitoring system and method. A cloud computing technology is used, power consumption information forms a large power information resource pool, the power load is accurately predicted, the energy-saving potential is accurately mined, and a powerful guarantee is provided for reasonable, ordered, high-efficiency and safe power utilization, so that the aim of continuously utilizing the power is fulfilled. The system comprises a user layer, a data layer, a service layer and a monitoring layer, wherein the user layer is used for dividing the energy-saving method of the whole distribution system according to the industry difference; the data layer is used for acquiring power user data of the user layer by employing an intelligent load control terminal; the service layer is used for processing the data acquired from the data layer by employing the cloud computing and big data technology; and the monitoring layer is connected to the cloud of the service layer and is used for monitoring a power load in real time, counting the power consumption, checking and managing the power service condition and checking the energy-saving potential, so that the service type of the energy-saving equipment is determined.
Owner:LU SHANDONG ELECTRIC POWER GRP CO LTD
Light-emitting keyboard
InactiveCN103839722AImprove efficiencyImprove the defects of non-luminous functionElectric switchesDirect illuminationLight beam
The invention provides a light-emitting keyboard comprising multiple direct illumination-type light-emitting elements, an induction circuit layer, multiple keys and a light-transmitting supporting plate. When the keys are close to the induction circuit layer, the induction circuit layer correspondingly generates a non-contact type key signal. Besides, each direct illumination-type light-emitting element is corresponding to one key and arranged below the corresponding key. The light-transmitting supporting plate is arranged between the multiple direct illumination-type light-emitting elements and the multiple keys. Light beams of each direct illumination-type light-emitting element penetrate through the light-transmitting supporting plate and then are projected to the corresponding key. Use efficiency of light can be effectively enhanced by the light-emitting keyboard.
Owner:PRIMAX ELECTRONICS LTD
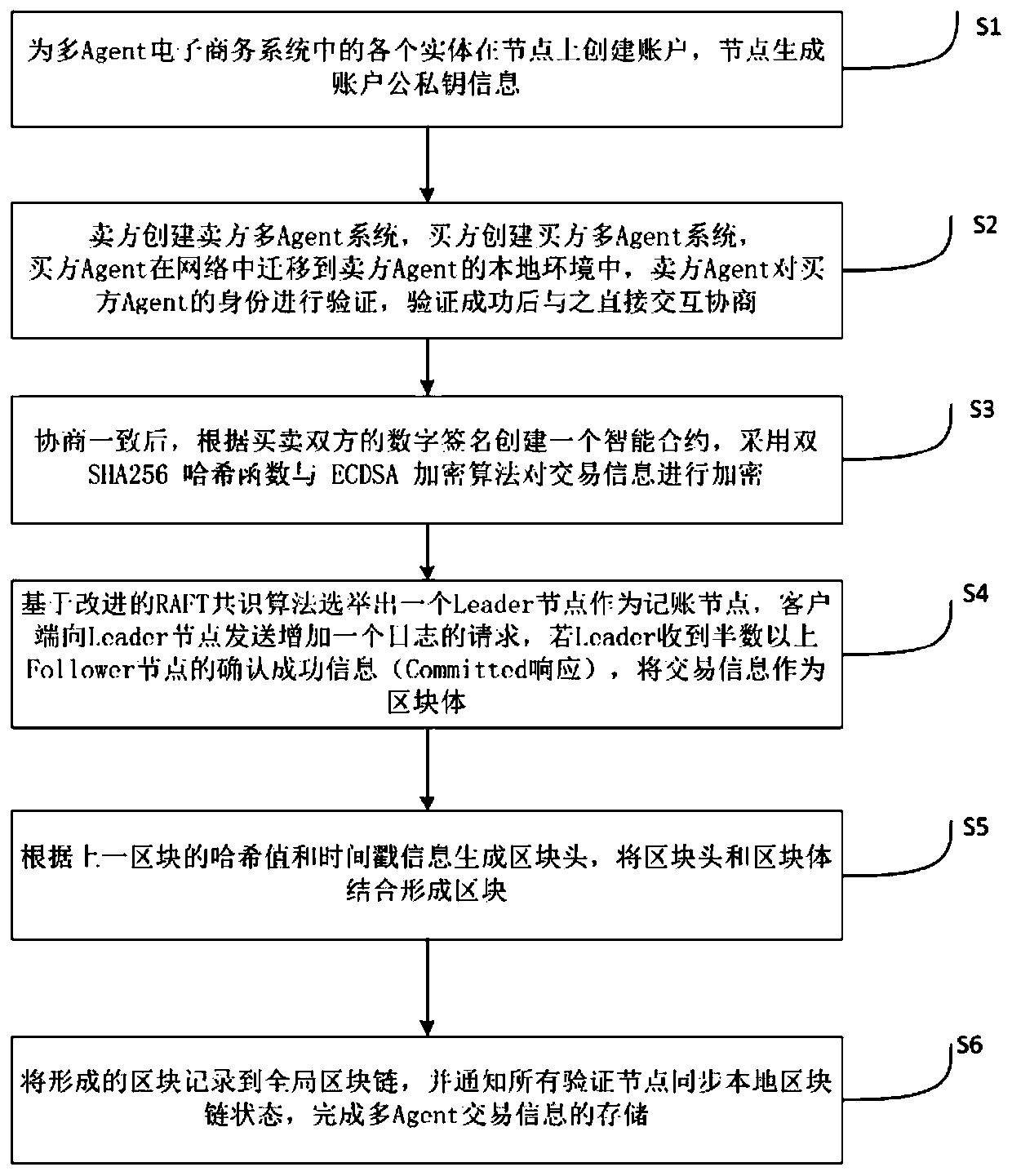
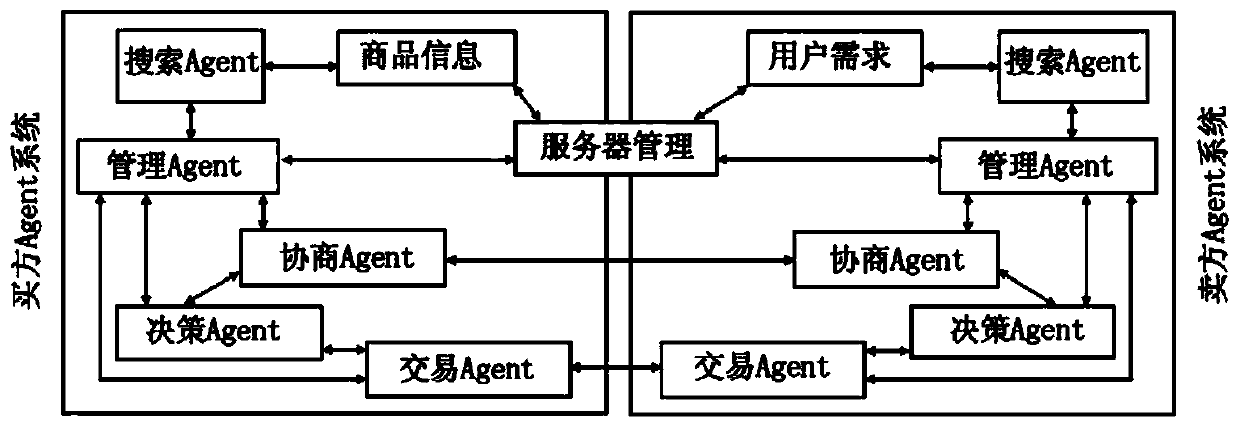
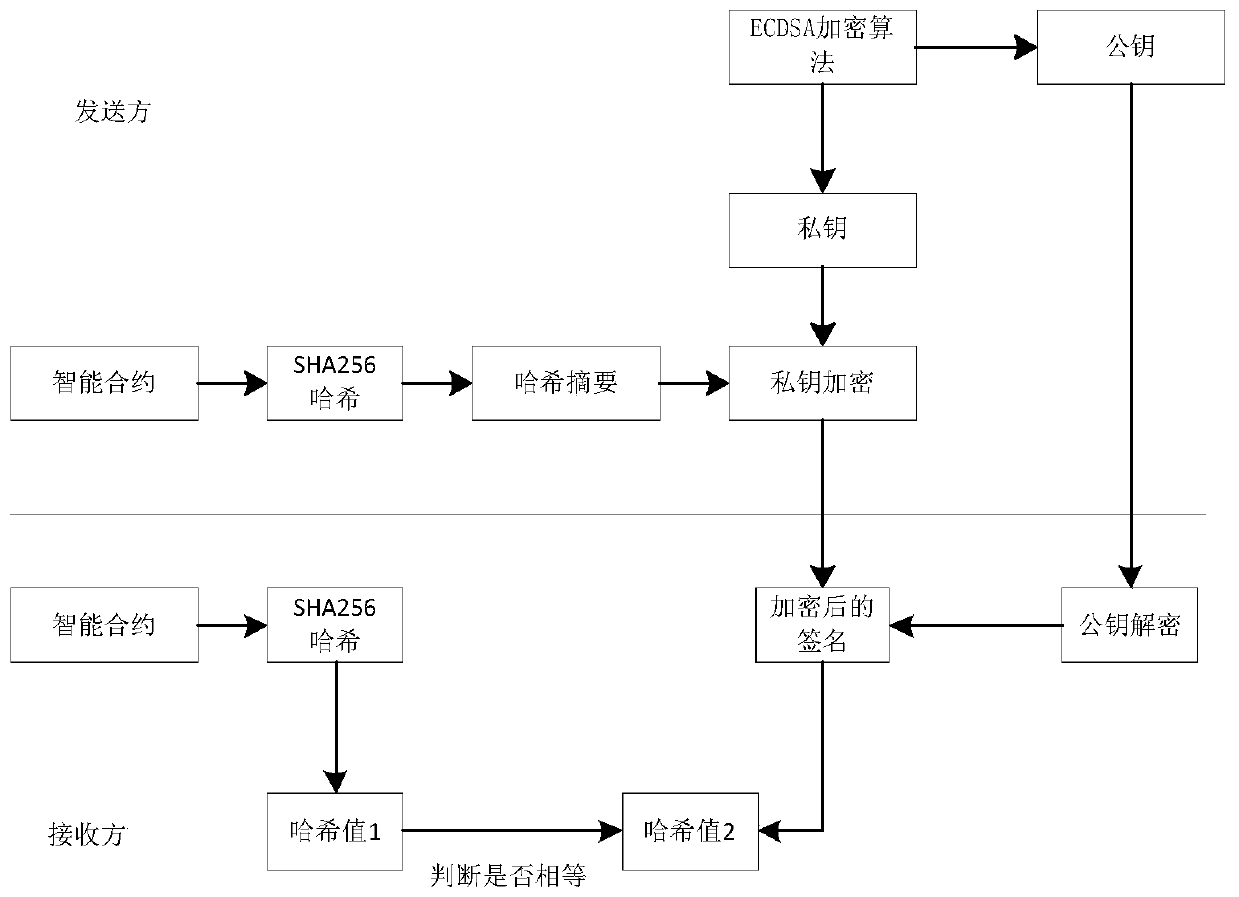
Multi-Agent transaction information protection method based on block chain technology
ActiveCN110569675AReduce in quantitySolve the consensus problemFinanceDigital data protectionByzantine fault toleranceDigital signature
The invention discloses a multi-Agent transaction information protection method based on a block chain technology. According to the method, a transaction execution platform which only has credible andsafe transaction information protection execution environment is established by utilizing a block chain. A transaction process between the buyer and the seller is realized by using the transaction execution platform. Besides, a BFT-Raft consensus algorithm based on Byzantine fault tolerance is adopted, and the method has the advantages that due to the establishment of a multi-Agent e-commerce system, the transaction cost and the user time can be remarkably reduced, and illegal authorization acquisition, use and leakage of transaction information are effectively prevented. The BFT-Raft consensus algorithm ensures that the log is not tampered by applying a digital signature technology and incremental hash in a log replication link. Through a Committed proving mechanism, it is ensured that aselected Leader node must have all log items reaching consensus, the BFT-Raft consensus algorithm can solve the consensus problem in a Byzantine fault-tolerant environment, the number of nodes participating in verification and accounting is greatly reduced, and second-level consensus verification can be achieved.
Owner:SHANGHAI MARITIME UNIVERSITY
Distributed system and automatic maintaining method for same
ActiveCN103051551AImprove scalabilityEasy to deleteData switching networksSystem maintenanceNetwork structure
The invention discloses a distributed system and an automatic maintaining method for the same. The method comprises the following steps that after a node starts a service, a service registration request is sent to a service registry at regular time; and the service registry maintains local information according to the received service registration request and provides an information service for the node or a node related to the node. The scale of the distributed system disclosed by the invention can be dynamically shrunk; after the node starts the service, service registration can be automatically initiated without manual configuration; a network relation can be automatically formed between the nodes by a calling relation and can be dynamically regulated; and the network structure does not need to be planned in advance. Moreover, the system disclosed by the invention is simple to maintain and is low in construction cost.
Owner:ZTE CORP
Wireless ad hoc network communication method and device
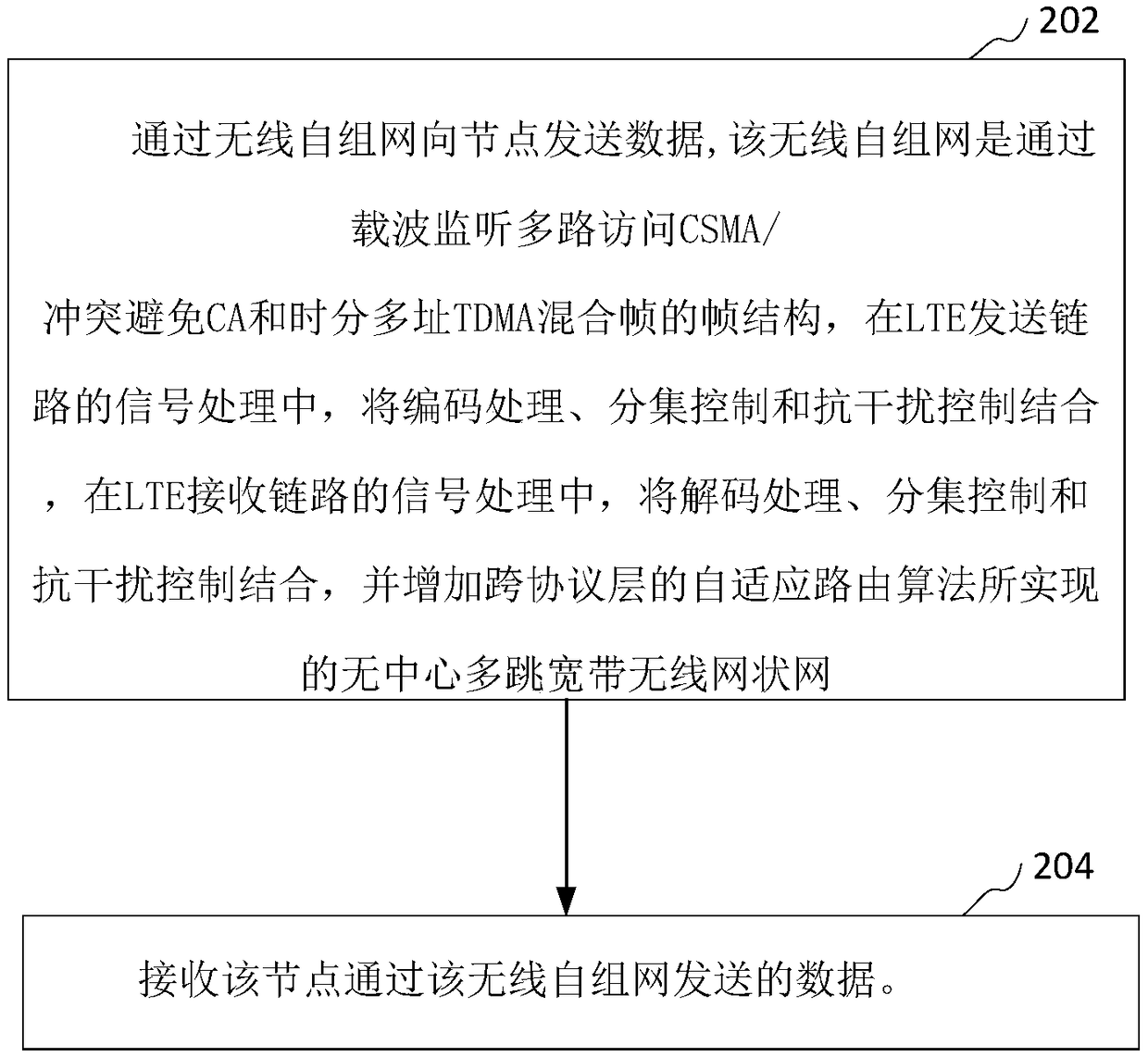
ActiveCN109275171AWill not affect operationImprove survivabilityError preventionNetwork topologiesAnti jammingWireless mesh network
The invention relates to a wireless ad hoc network communication method and device. The method sends data to a node through a wireless ad hoc network and receives the data sent by the node through thewireless ad hoc network. Wherein the wireless ad hoc network is a frame structure of a mixed frame of a CSMA / collision avoidance CA and a time division multiple access TDMA through a carrier sense multiple access, In signal processing of LTE transmission link, encoding, diversity control and anti-jamming control are combined. In signal processing of LTE reception link, decoding, diversity controland anti-jamming control are combined, andAdaptive routing algorithm across protocol layer is added to realize centerless multi-hop wideband wireless mesh network. The wireless ad hoc network is a peer-to-peer network, all nodes in the network are equal in status, nodes can join and leave the network at any time, the failure of any node will not affect the operation of the whole network, and theinvulnerability of the network is improved.
Owner:ZHUHAI YUNZHOU INTELLIGENCE TECH COMPANY
Fixed building rubbish treatment device
InactiveCN101927257AHigh-quality mechanized productionEnsure quality and puritySievingGas current separationReinforced concreteEngineering
The invention provides a fixed building rubbish treatment device adopting a crushing core technique (hammer crusher) and a double-quality vibration screening core technique, wherein the rushing core technique can be used for crushing reinforced concrete containing reinforcing steel bars, braking and separating the reinforcing steel bars from equipment and generating high-quality recycled building aggregates, and the double-quality vibration screening core technique has favorable vibration track, can be used for precise screening and ensure the screening precision (other types of screening machines can not achieve the advantages). The fixed building rubbish treatment device can decompose and treat abandoned building rubbish, such as the reinforced concrete containing reinforcing steel bars and the like, to generate the high-quality recycled building aggregates; and the fixed building rubbish treatment device can break the reinforcing steel bars in the reinforced concrete so that the reinforcing steel bars are conveniently recovered without blocking and winding the equipment, thereby the whole recycling and treatment system realizes favorable mechanical production.
Owner:CHANGSHU RIXIN MACHINERY
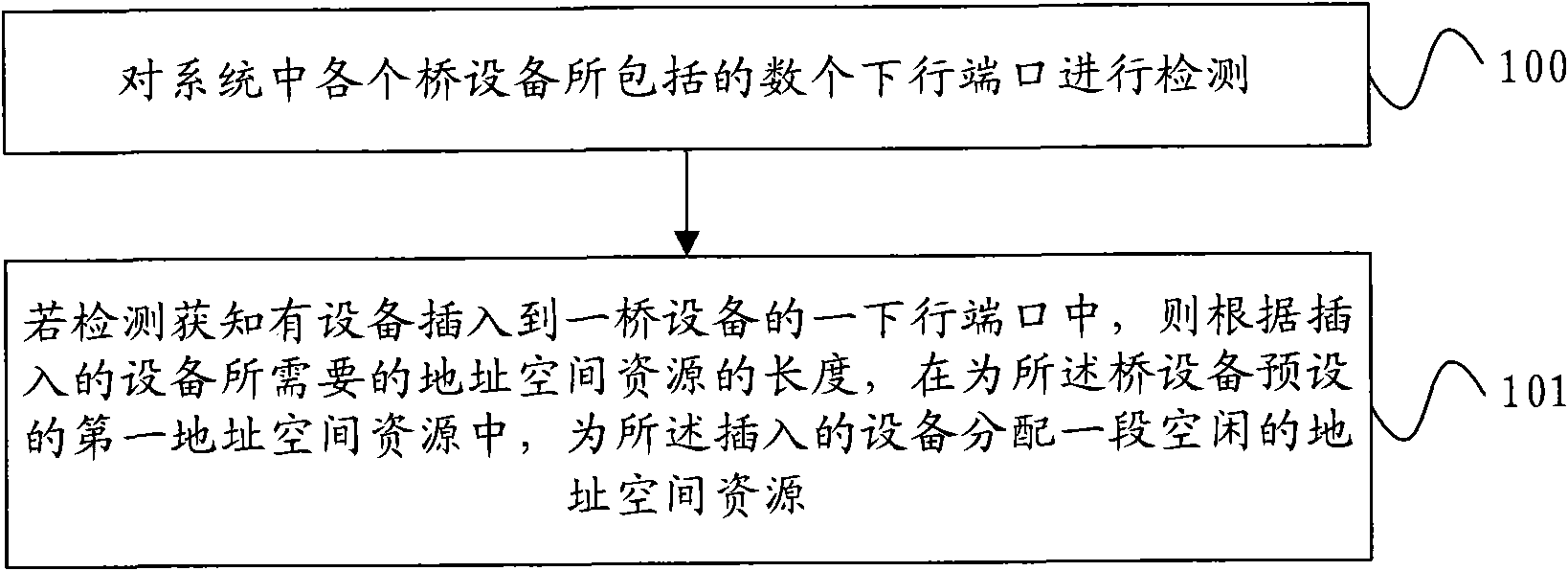
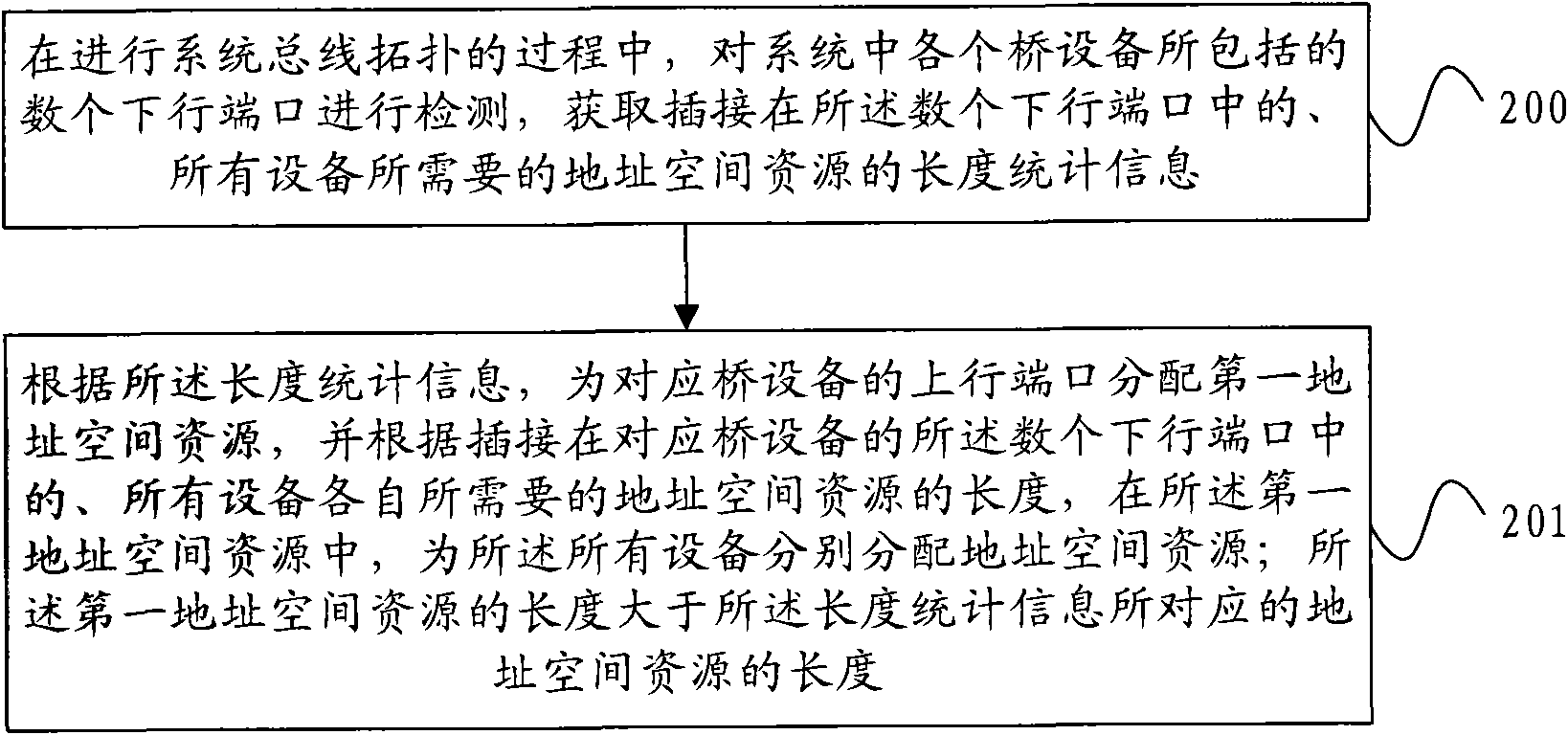
Method and device for allocating and processing address space resource
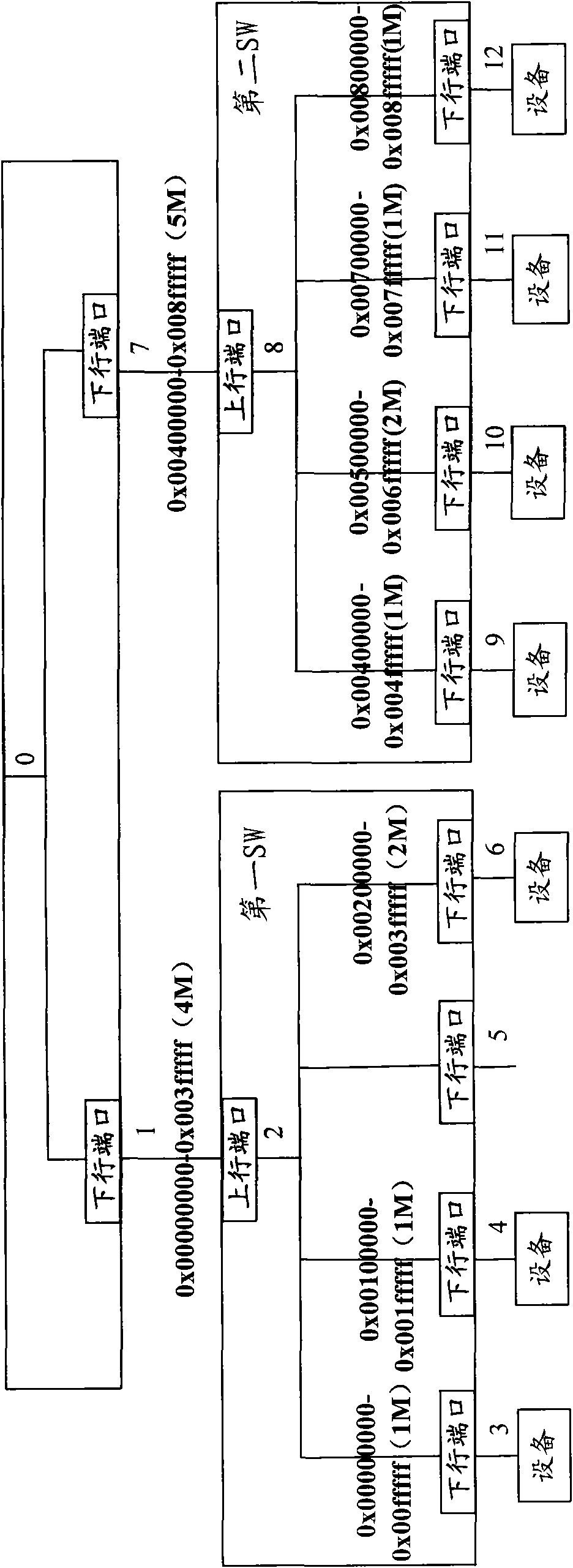
ActiveCN102117259AWill not affect operationEnhanced hot-plug functionElectric digital data processingLow resourceAddress space
The embodiment of the invention provides a method and a device for allocating and processing an address space resource. The method comprises the following steps: detecting a plurality of downlink ports of each bridge device in a system, and if confirming that a device is inserted into one downlink port of one bridge device, allocating a section of spare address space resource to the inserted device in a preset first address space resource of the bridge device according to the length of the address space resource required by the inserted device. In the embodiment of the invention, through previously reserving certain address space resources on the uplink ports of all the bridge devices in the system, the required address space resources are dynamically allocated to the device when a device is inserted in the normal working process of the system, thereby achieving dynamically allocating resource according to the address space required by the device, avoiding influencing the running of the device by insufficient resource and enhancing the hot plug function of the device.
Owner:CHENGDU HUAWEI TECH
Pipe logistics conveying device
InactiveCN101117118AImprove reliabilityEase traffic congestionRailway tunnelsRailway componentsLogistics managementControl room
The invention relates to a logistics transportation device by pipelines. The system comprises a plurality of pipelines and a master control room. The pipelines form a through network. A plurality of freight transportation vehicles are arranged inside the pipelines and the master control room is used to control the transportation vehicles to transport the goods loaded to a designated location. The invention is highly efficient and space-saving, can reduce traffic jam and transport goods conveniently and rapidly.
Owner:李荣生
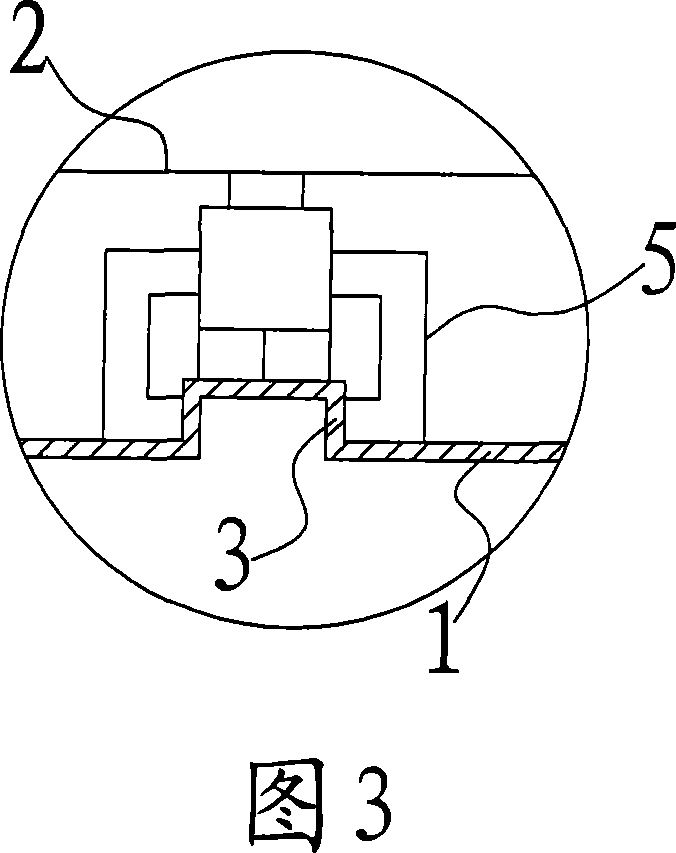
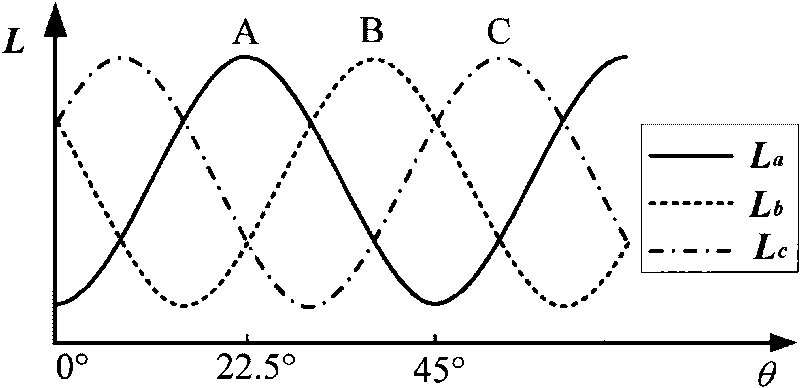
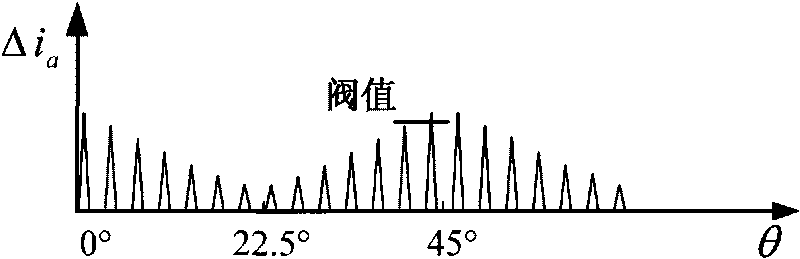
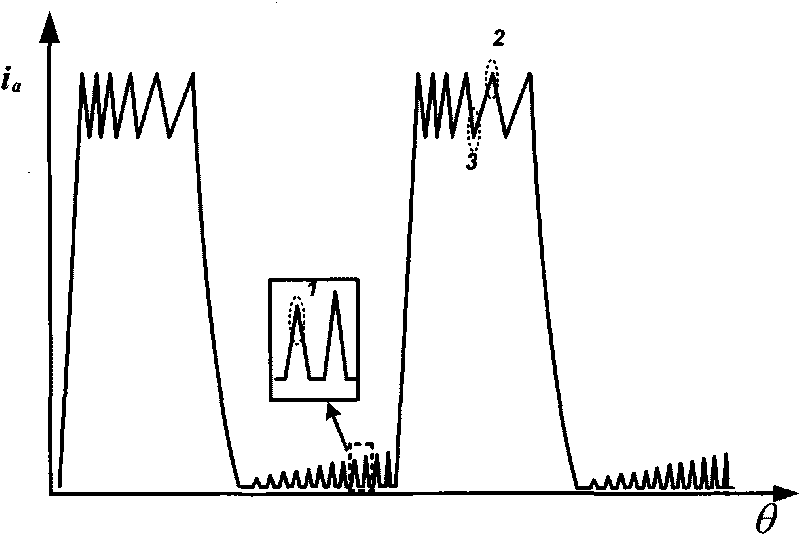
Method suitable for low-speed switched reluctance motor without position sensor
The invention discloses a method suitable for a low-speed switched reluctance motor without a position sensor, which belongs to the technical field of control of the switched reluctance motors. The method is as follows: taking the switched reluctance motor as a control object, injecting high frequency pulses into a non-conduction phase, detecting the differences between rising slopes and descending slopes of three-phase current during the whole period, filtering the discrete differences, and then forming three envelope lines respectively, thereby being capable of determining the position of a rotor according to cross points of the envelope lines due to the special relationship between the envelope lines and inductance, calculating other positions according to the rotational speed and further realizing the normal running of the motor and the adjustable control of a turn-on angle and a turn-off angle. The method has simple algorithm and flexible control, only the phase current needs to be detected, and the affects of counter potential are simultaneously eliminated, thereby improving the accuracy of position estimation to a greater extent.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
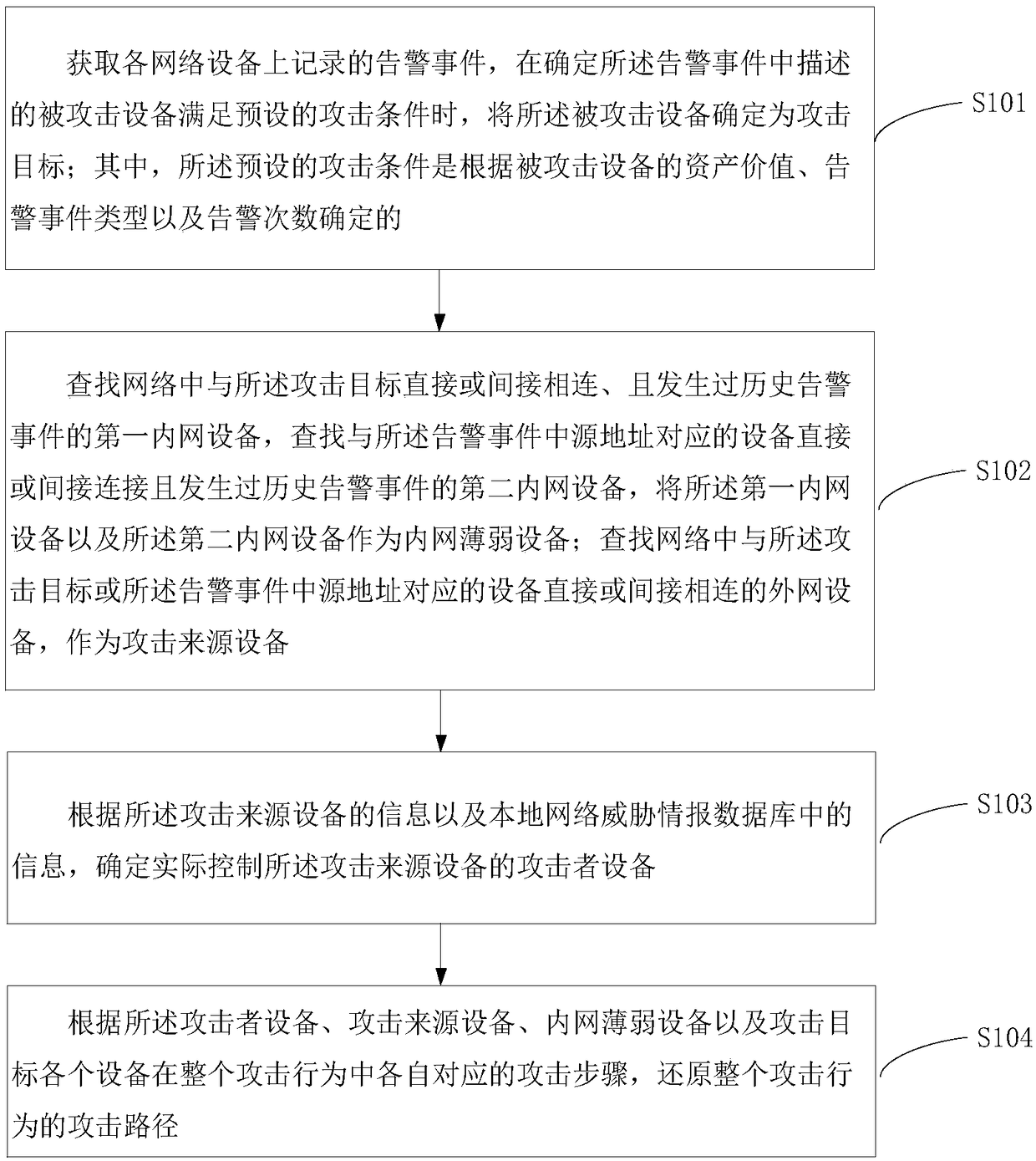
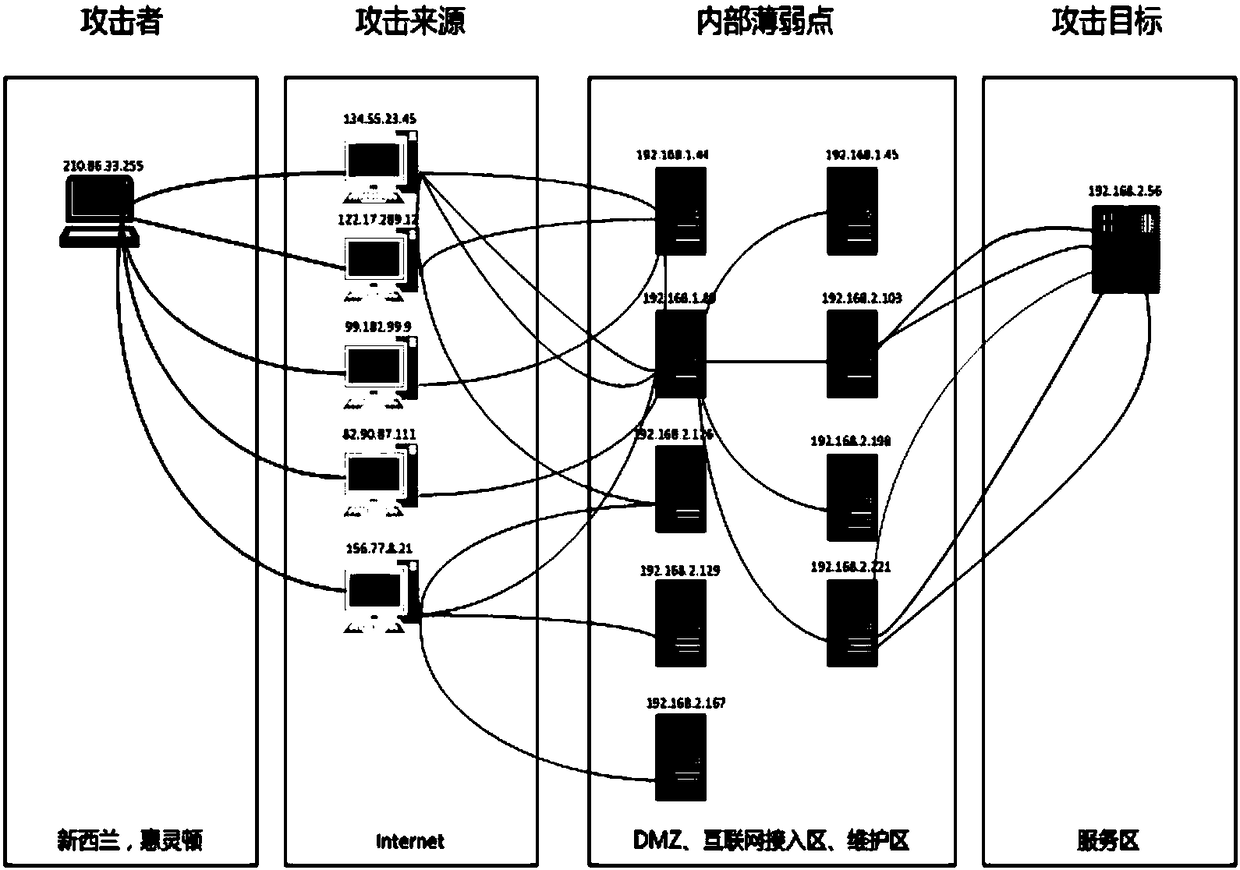
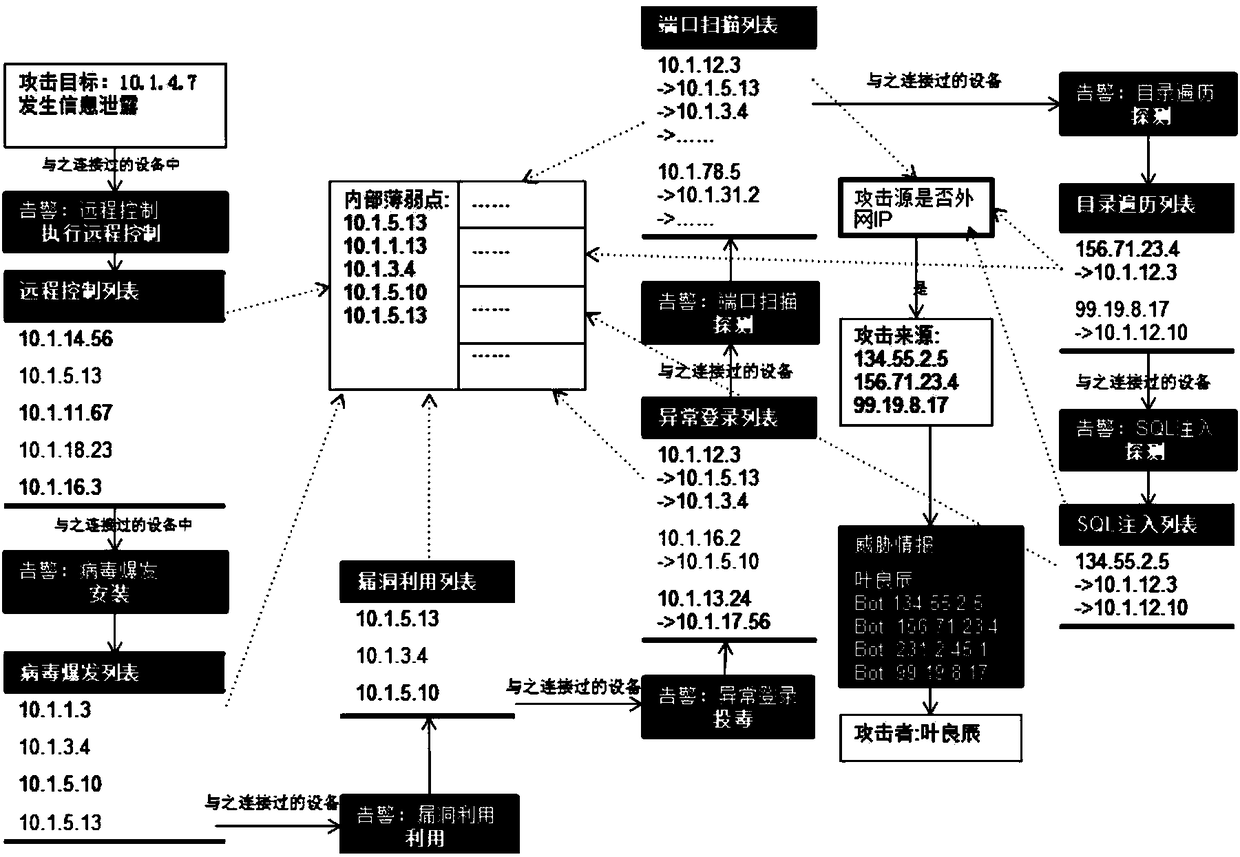
Attack path restoration method and apparatus
ActiveCN108696473ANoise shieldingWill not affect operationTransmissionRestoration methodNormal functioning
The invention relates to an attack path restoration method and apparatus. According to the method, through comprehensive analysis on a security event alarm, and a connection relationship of each device in a network topology, a connection relationship between each of respective lists of an attacker, an internal network weak point, an attack source and the attacker and each set of device is obtained, thereby finishing restoration of an attack process. Compared with the existing path restoration method, the method provided by the embodiment of the invention can go deep into an internal network todiscover a security weak point in internal network protection, so that an attack path is traced to the source and thus the method is more effective to improve the enterprise security and improves theanalysis efficiency; and meanwhile, a noise of an uncritical connection in massive security events can further be shielded and only an attack path coming into effect is traced to the source; moreover, all attacks can be restored, so the restoration capacity is improved; and in addition, according to the method provided by the invention, while the attack path is restored, an operating service is not affect and thus the normal operation of the service can be kept.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
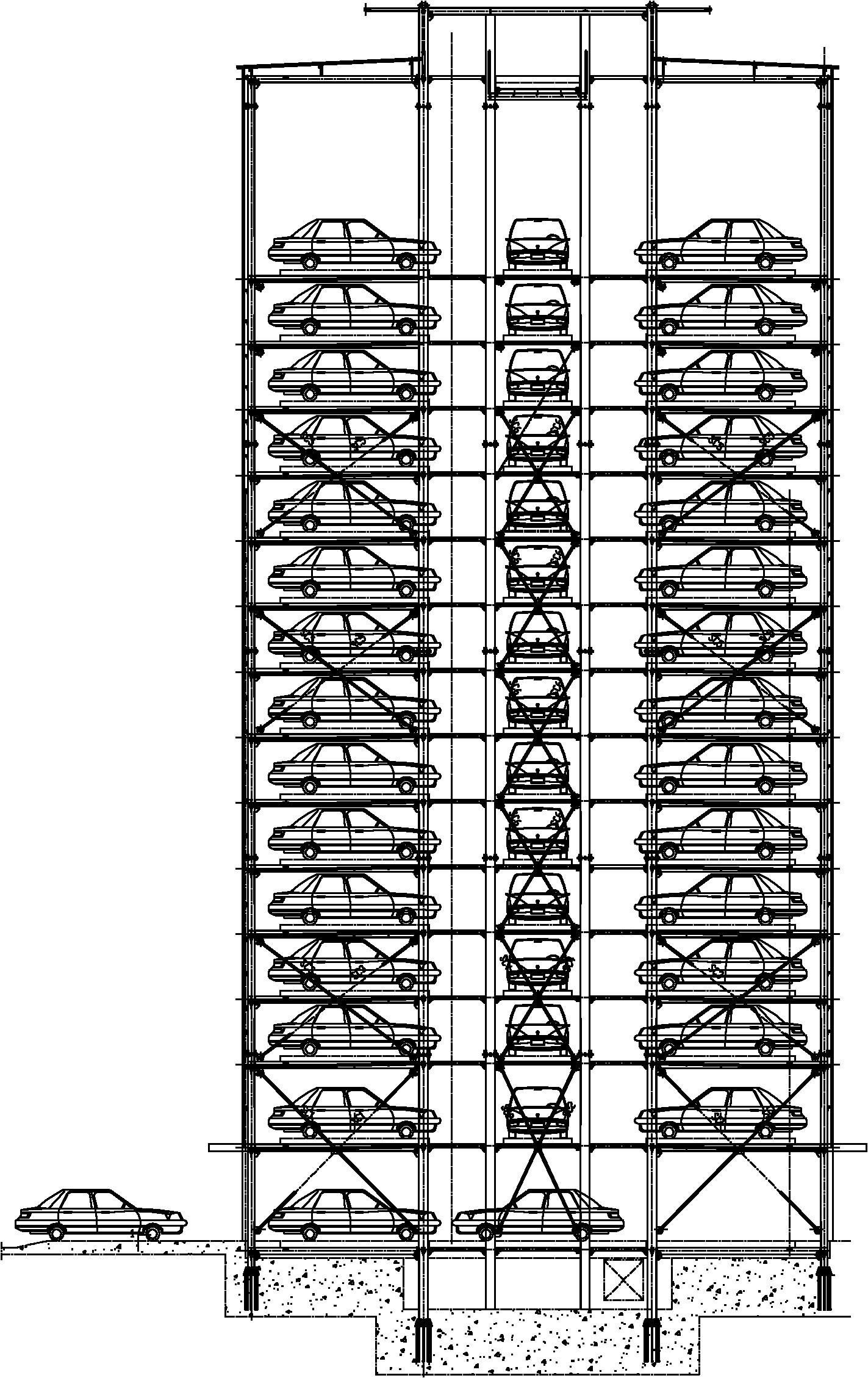
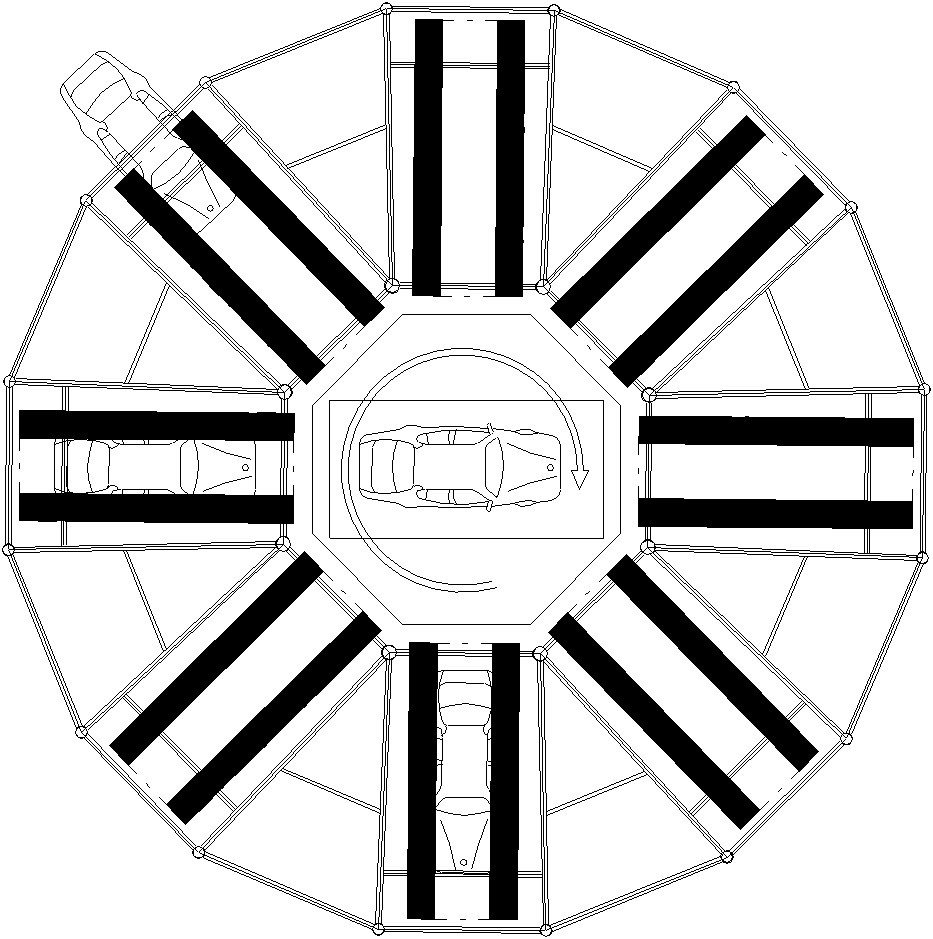
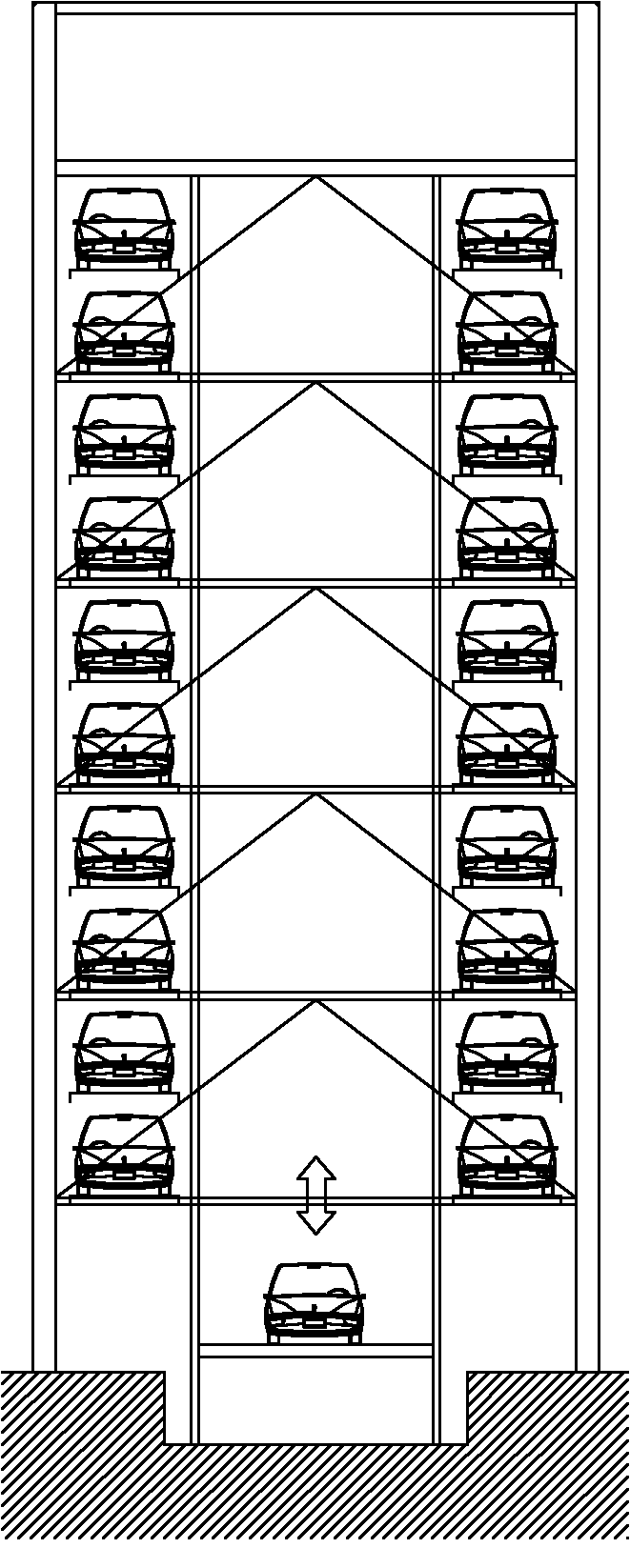
Tower type three-dimensional garage and lifting system thereof
The invention discloses a tower type three-dimensional garage and a lifting system thereof. The tower type three-dimensional garage comprises a lifting cage, lifting power equipment of the lifting cage, multiple layers of parking space platforms and a carrier, wherein the lifting cage is arranged in the lifting well of the garage; the plane of the lifting cage is a rectangle, and the length of the rectangle in the transverse direction of a vehicle is at least equal to the width of carriages of two parking spaces; the multiple layers of the parking space platforms are positioned on the rectangle of the lifting cage at the front side and the back side of the vehicle, each layer of the parking space platform at least comprises four parking spaces, the multiple layers of the parking space platforms are provided with passage layers, and each passage layer is provided with at least two passages; and the carrier is arranged in the lifting cage, and is used for moving transversely along the rectangle in the transverse direction of the vehicle and horizontally moving the vehicle between the lifting cage and each of the parking spaces. The invention can realize the effects of higher moving speed, low energy consumption and high vehicle parking and withdrawing efficiency on the basis of low cost.
Owner:SHENZHEN ZHONGKE LIHENG PARKING EQUIP
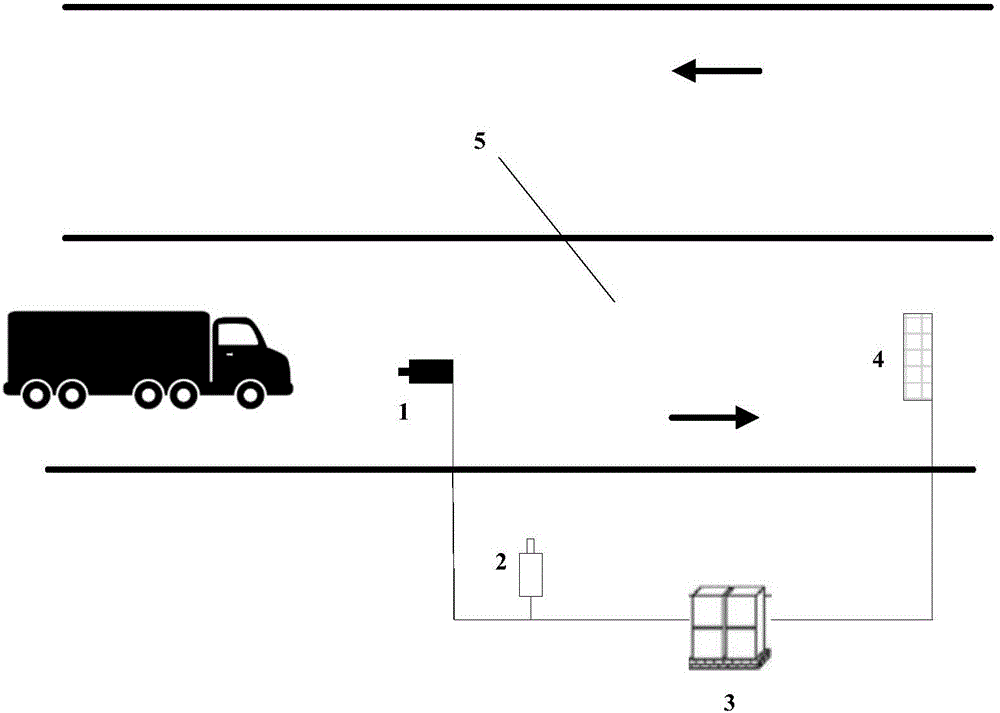
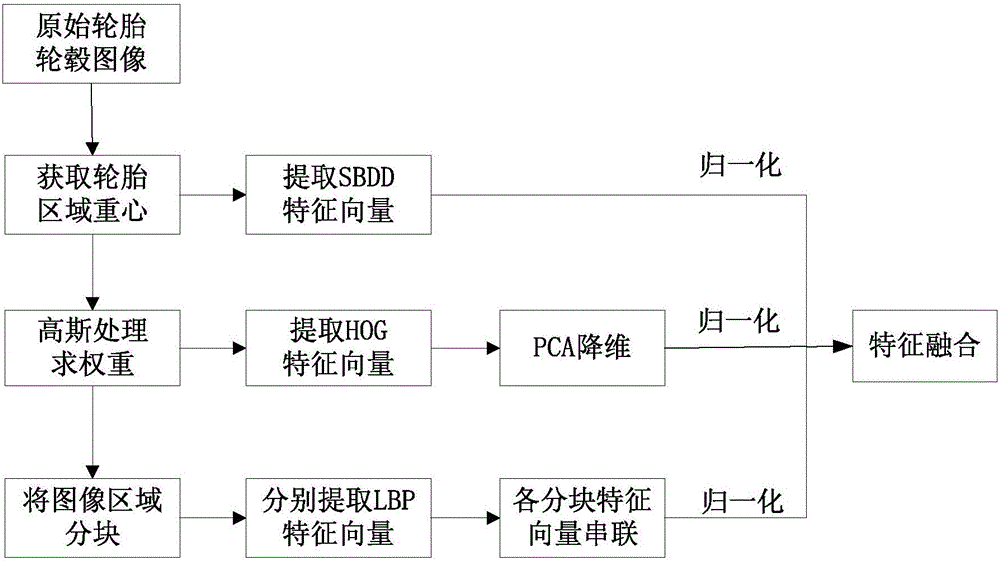
Hub temperature anomaly detection and early warning method and system
ActiveCN105869408AIncrease temperatureAvoid brake failureRoad vehicles traffic controlSensing radiation from moving bodiesAnomaly detectionTraffic accident
The invention relates to an automobile hub temperature anomaly detection and early warning method and system. The system comprises a surveillance camera, a thermal infrared imager, a control host and a variable information board. The surveillance camera is installed above a road, the thermal infrared imager is installed on the road side, and the variable information board is arranged on the downstream of the surveillance camera. When a vehicle arrives at a detection area, the surveillance camera and the thermal infrared imager collect images of the vehicle and send the images to the control host; the control host carries out vehicle license plate recognition on the image shot by the surveillance camera; the control host extracts and fuses the SBDD, HOG and LBP features of a hub in the thermal imaging image and then judges whether the temperature of the hub is abnormal or not in a classified mode through an incremental support vector machine; when it is found that the temperature of the hub is abnormal, vehicle information is sent to the variable information board for early warning reminding. By means of the automobile hub temperature anomaly detection and early warning method and system, whether the temperature of the hub of an automobile is abnormal or not can be effectively detected, and early warning can be effectively carried out, so that traffic accidents caused by brake failure, fire breakout, tire burst and the like are avoided.
Owner:CHANGAN UNIV
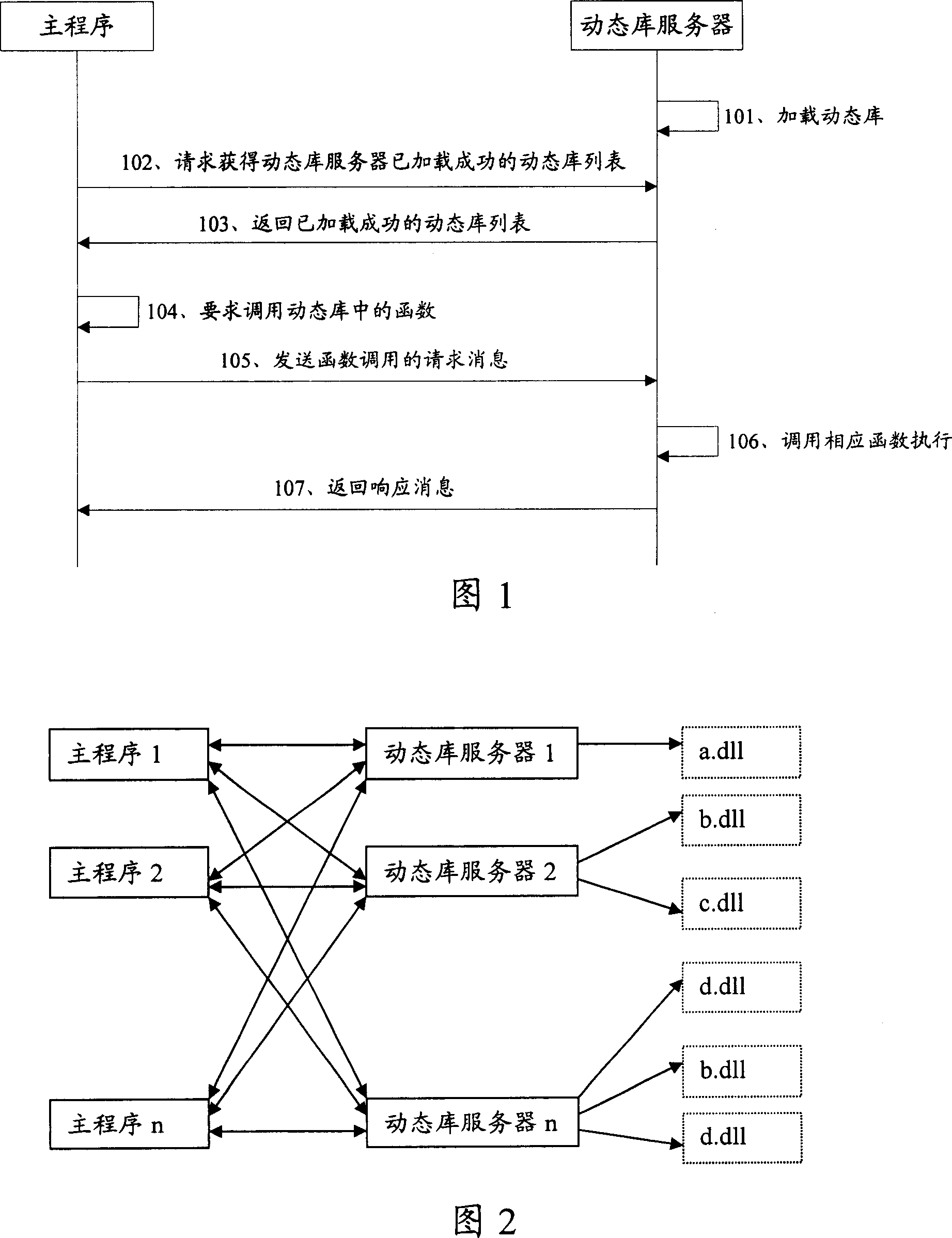
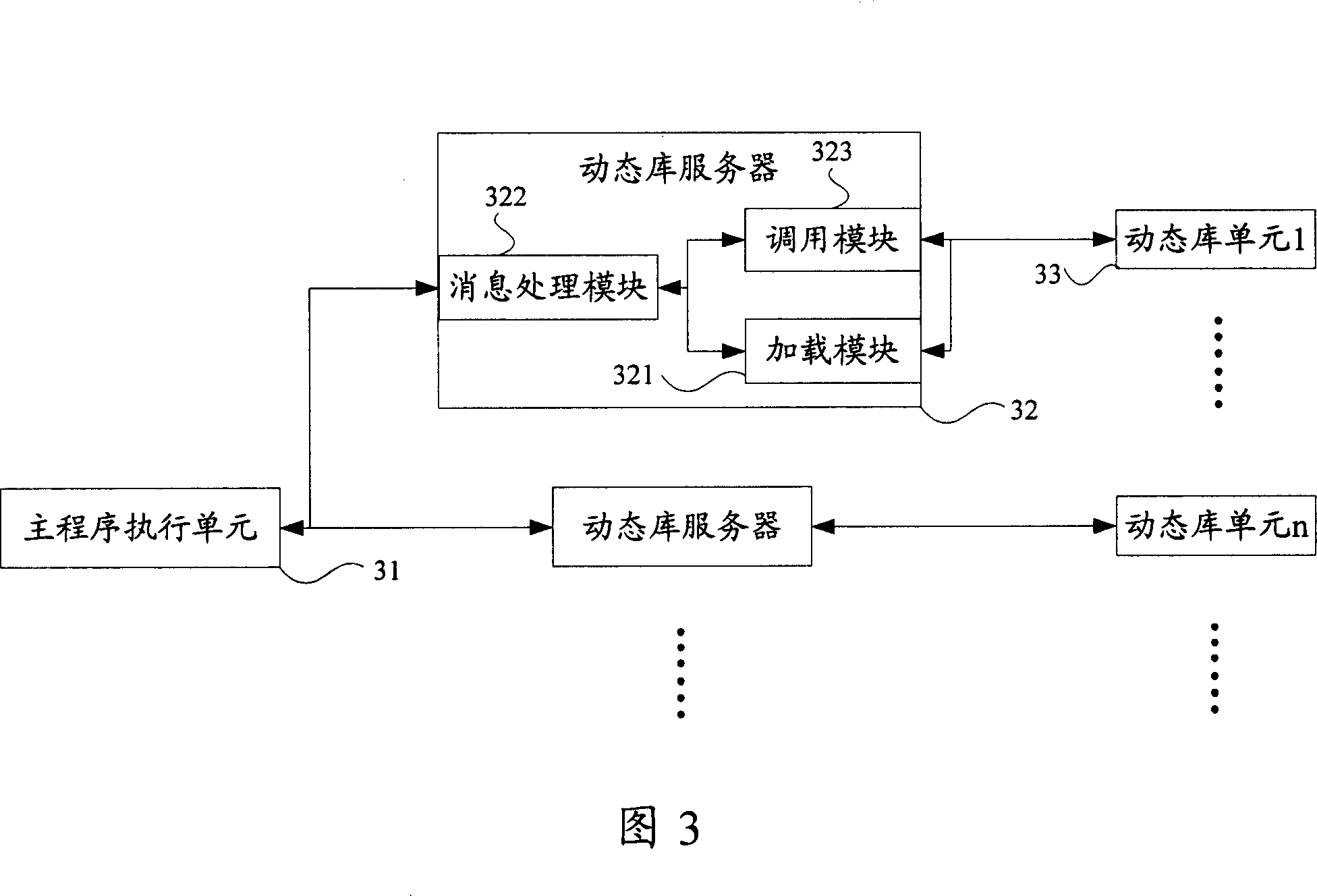
Method and apparatus for calling dynamic library and dynamic library server
InactiveCN101021804AWill not affect operationImprove portabilityProgram initiation/switchingOperating system
The invention discloses a method for calling a dynamic library, including: the main program sends a request for DLL functions to the DLL server, and described request carries the parameters for calling the functions. The DLL server calls the functions according to the parameters and returns the functions' result to the main program via the response news. The invention also discloses a device for calling a dynamic library, including: a main program module is used to send requests for calling the DLL function, and a DLL server is used to call the functions according to the parameters and return the functions' results to the main program via the response news, and a DLL module is used to run functions according to the DLL server and submit the results of functions.
Owner:HUAWEI TECH CO LTD
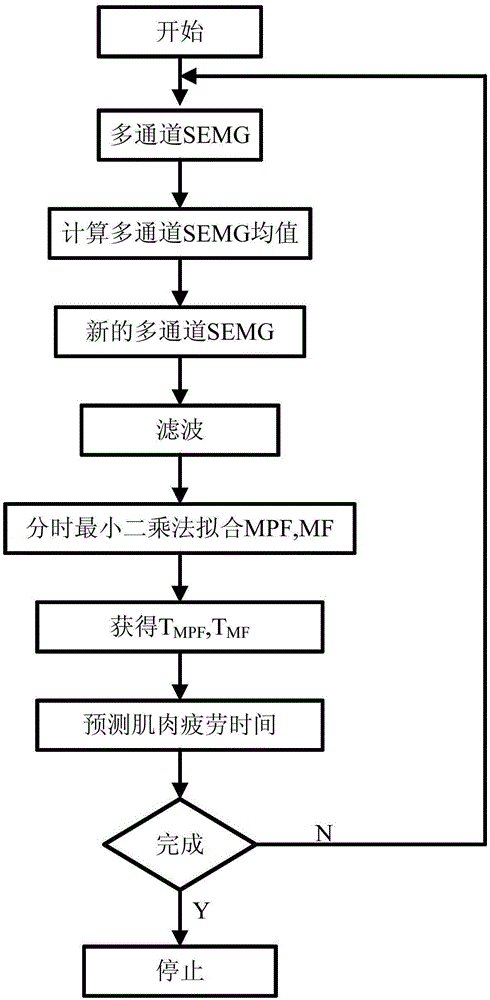
Muscle fatigue dynamic prediction method based on multi-channel sEMG
InactiveCN105147251AAvoid instabilityPrediction is accurate and fastDiagnostic recording/measuringSensorsInstabilityLeast squares
The invention provides a muscle fatigue dynamic prediction method based on multi-channel sEMG. An sEMG signal is susceptible to external interference, so an average value of all channels is selected to be a reference value; a difference is made between the new reference value and the original multi-channel sEMG, so external interference can be effectively reduced; a time-scale least square method is translated according to time reference to achieve dynamic update and predict muscle fatigue time; MPF and MF parameters are important parameters reflecting muscle fatigue, so reliability is provided for muscle fatigue prediction; the MPF and the MF two parameters are employed for prediction of muscle fatigue time, so instability of single parameter prediction can be avoided and prediction robustness can be enhanced; and the muscle fatigue dynamic prediction method based on multi-channel sEMG has high accuracy, fast calculation speed, simplicity and important application values.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Wireless network optimization method for intelligent meter reading system
InactiveCN104010343ASolve problems such as non-correlation cannot be guaranteedAvoid breakingNetwork traffic/resource managementTransmission congestionData transmission
The invention discloses a wireless network optimization method for an intelligent meter reading system. The method is an improved dynamic routing allocation optimization algorithm. The method mainly solves the routing optimization problem of a wireless network layer, DSR is preliminarily optimized, the unrelated routing number in the DSR is increased, and the enhanced DSR optimization algorithm is provided. In order to solve the route selection problem in the enhanced DSR optimization algorithm, the minimum spanning tree thought is introduced into the DSR, a DSR optimization protocol based on a minimum spanning tree is provided, factors in multiple aspects of bandwidth, transmission congestion, network throughput and the like are comprehensively considered, simulation software NS-2 is used for simulation, and the result shows that the method can effectively shorten delay and improve data transmission efficiency and other indexes.
Owner:MICROCYBER CORP
Detection method for configuration of programmable logic device
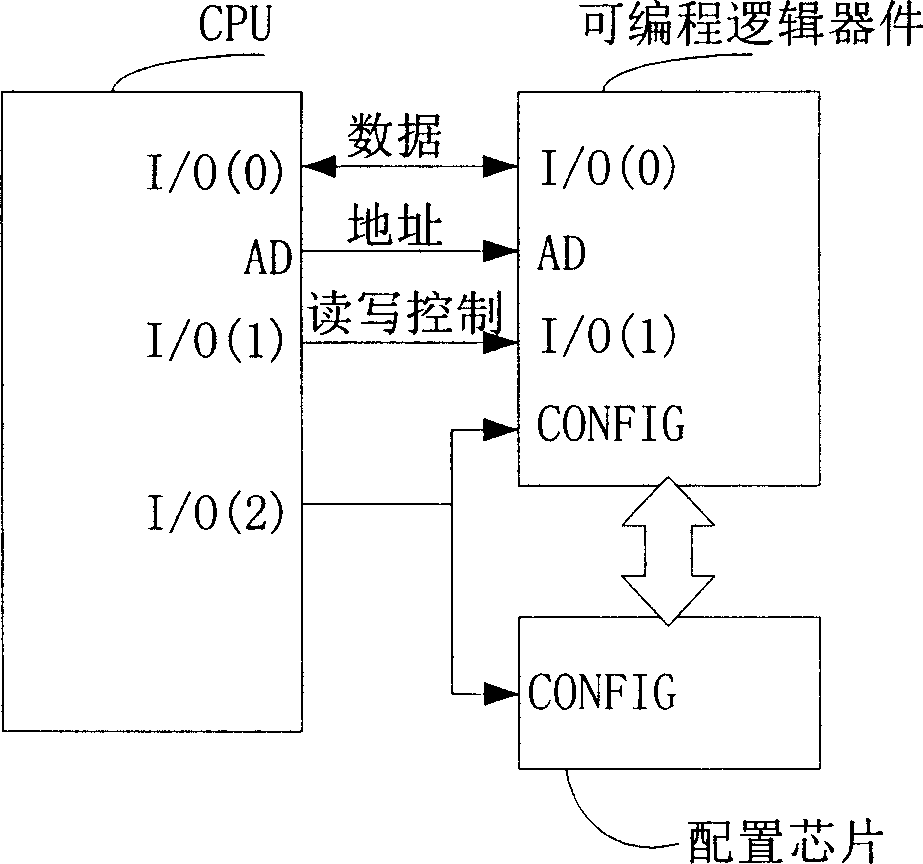
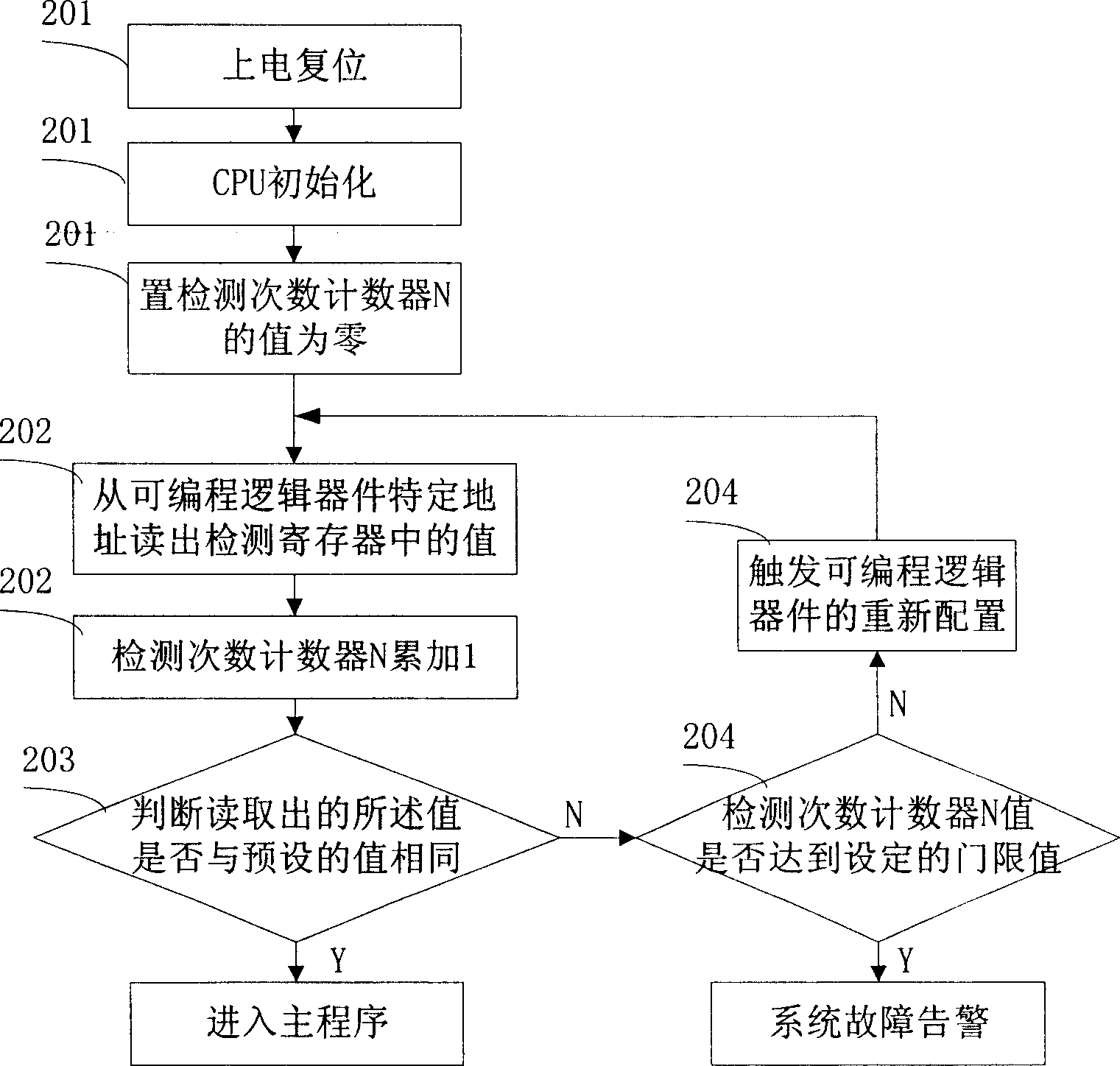
ActiveCN1841079AMeet the requirements for configuration to detectNo external electrical interferenceDigital circuit testingElectricityCollocation
The invention provides a programmable logic device collocation test method. When initializing the programmable logic device, the employed collocation information includes of allocating a specified address and storing a specified value. After system electrifying, this method includes: A. reading the value of the specified address; B. confirming the correction by comparing the reading and the specified value, if wrong, springing the initializing collocation and return to A. With this invention, the collocation correctness can be tested, and the test is not be disturbed by outside.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Distributed real-time database management system and implementation method applicable to electric system
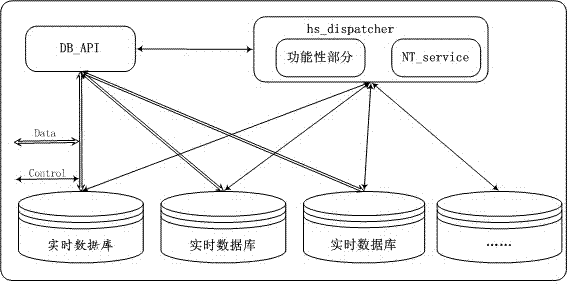
InactiveCN103886104AEfficient managementSolve code requirementsData processing applicationsSpecial data processing applicationsMap database managementElectric power system
The invention discloses a distributed real-time database management system and an implementation method applicable to an electric system and belongs to the field of database technologies. The real-time database management system comprises a server side, a real-time database side and a client side. The distributed management of real-time databases can be achieved through mechanisms such as file mapping, instance IDs, version numbers and client side caching. Through the distributed real-time database management system and the implementation method applicable to the electric system, transparency of multiple database instances is achieved, access of clients to the multiple database instances equals to access to a single database instance, the province-wide centralized deployment of the databases are facilitated, the province-wide unified data schema, data models and data standards are facilitated, and the access requirements of existing data and future data can be met.
Owner:CHINA REALTIME DATABASE
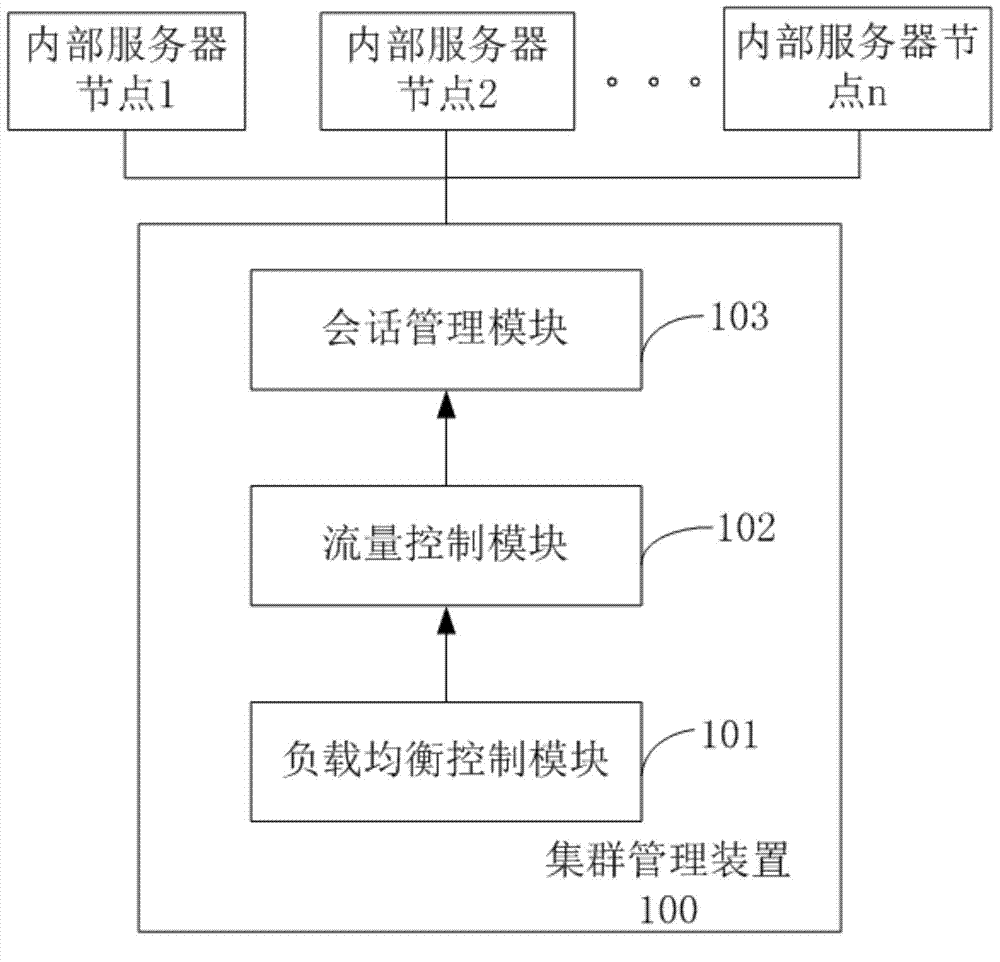
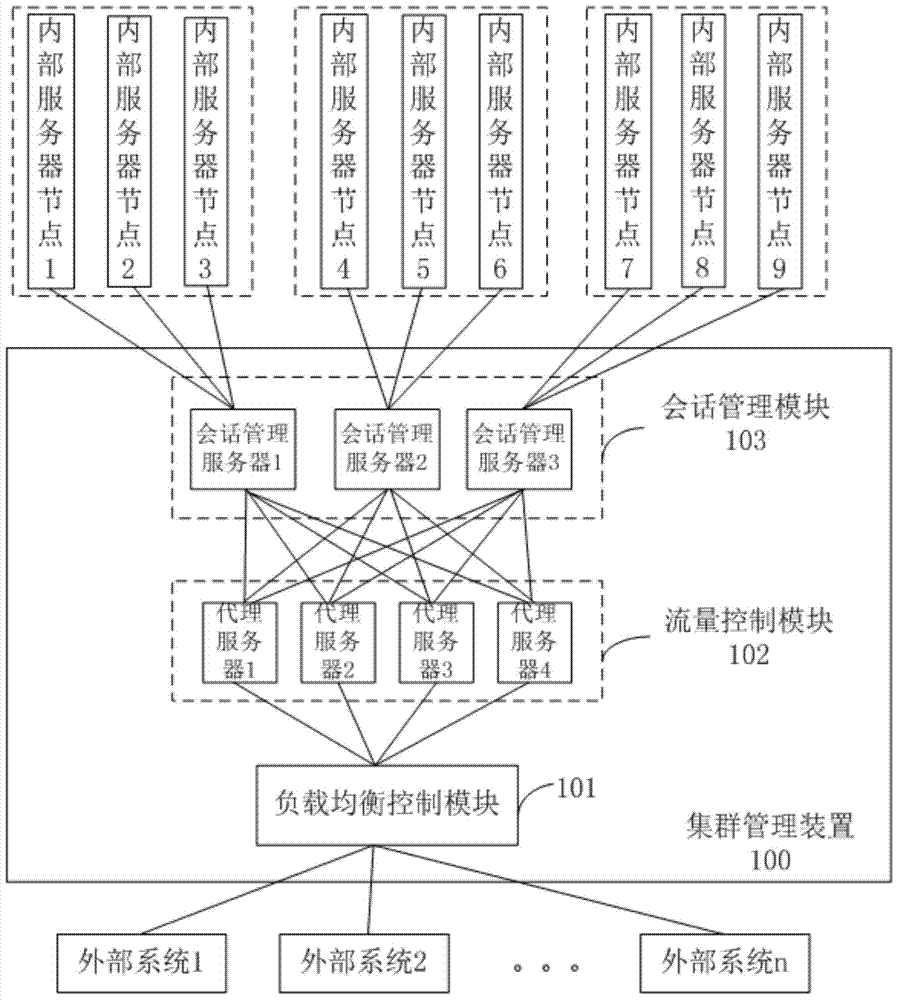
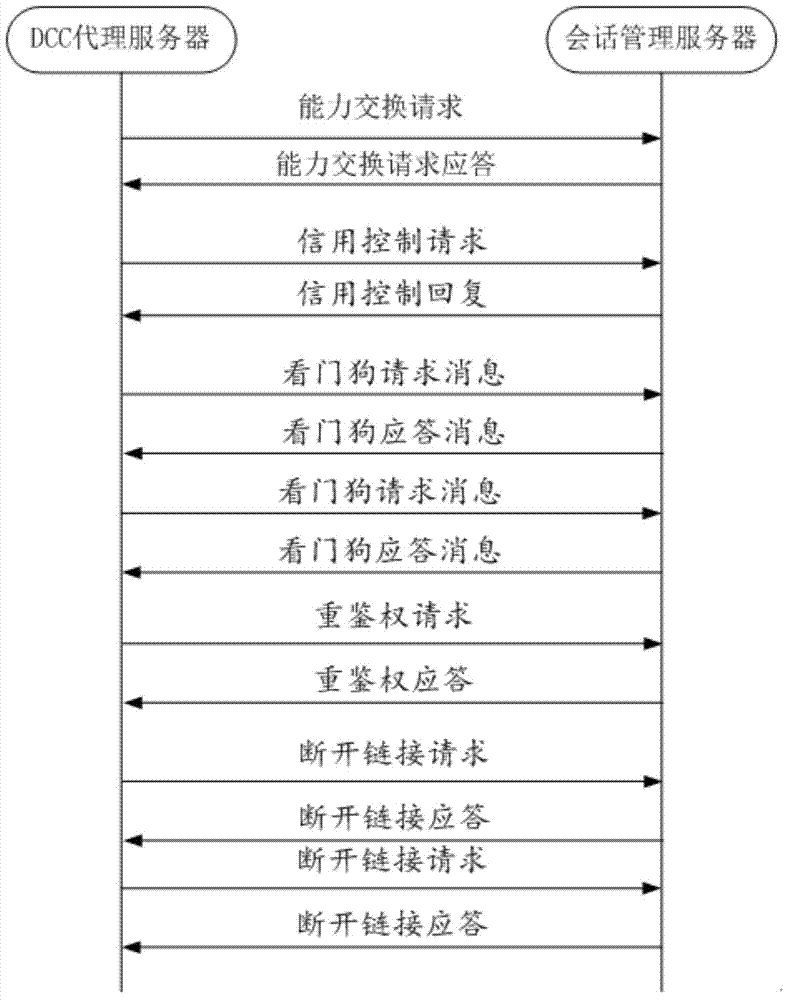
Cluster management device, system and method
InactiveCN103685461AWill not affect operationReduce wasteData switching networksSession managementManagement system
The invention discloses a cluster management device, system and method. The cluster management device employs a server cluster manner, wherein according to the types of request messages and performance of server nodes, a conversation management module selects internal server nodes for issuing the request messages of external systems, thereby realizing dynamic load balance. Thus, the number of cluster server nodes is increased at peak time and decreased at normal time, thereby saving the investment cost, reducing the resource waste, and not influencing service operation.
Owner:TELEFON AB LM ERICSSON (PUBL)
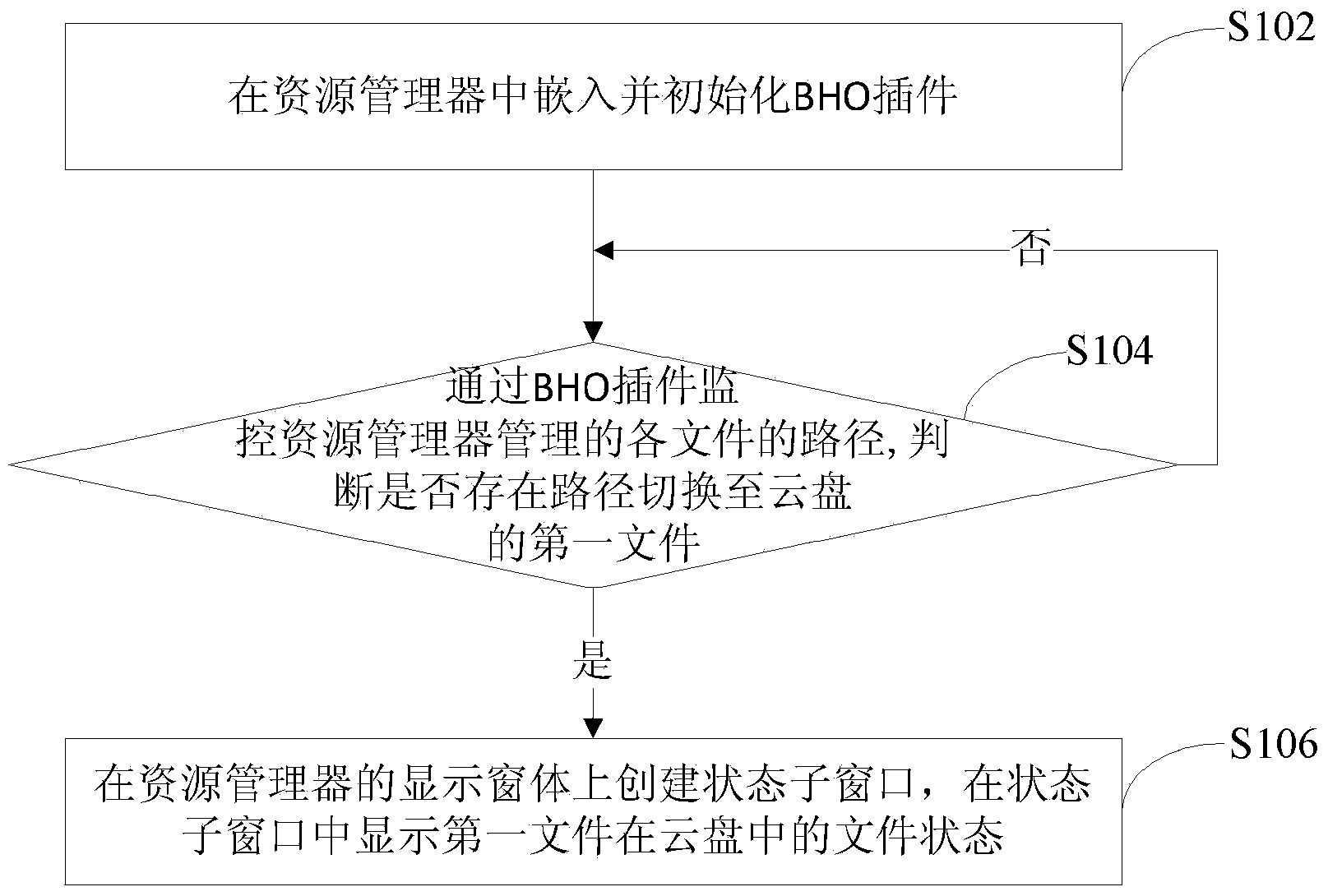
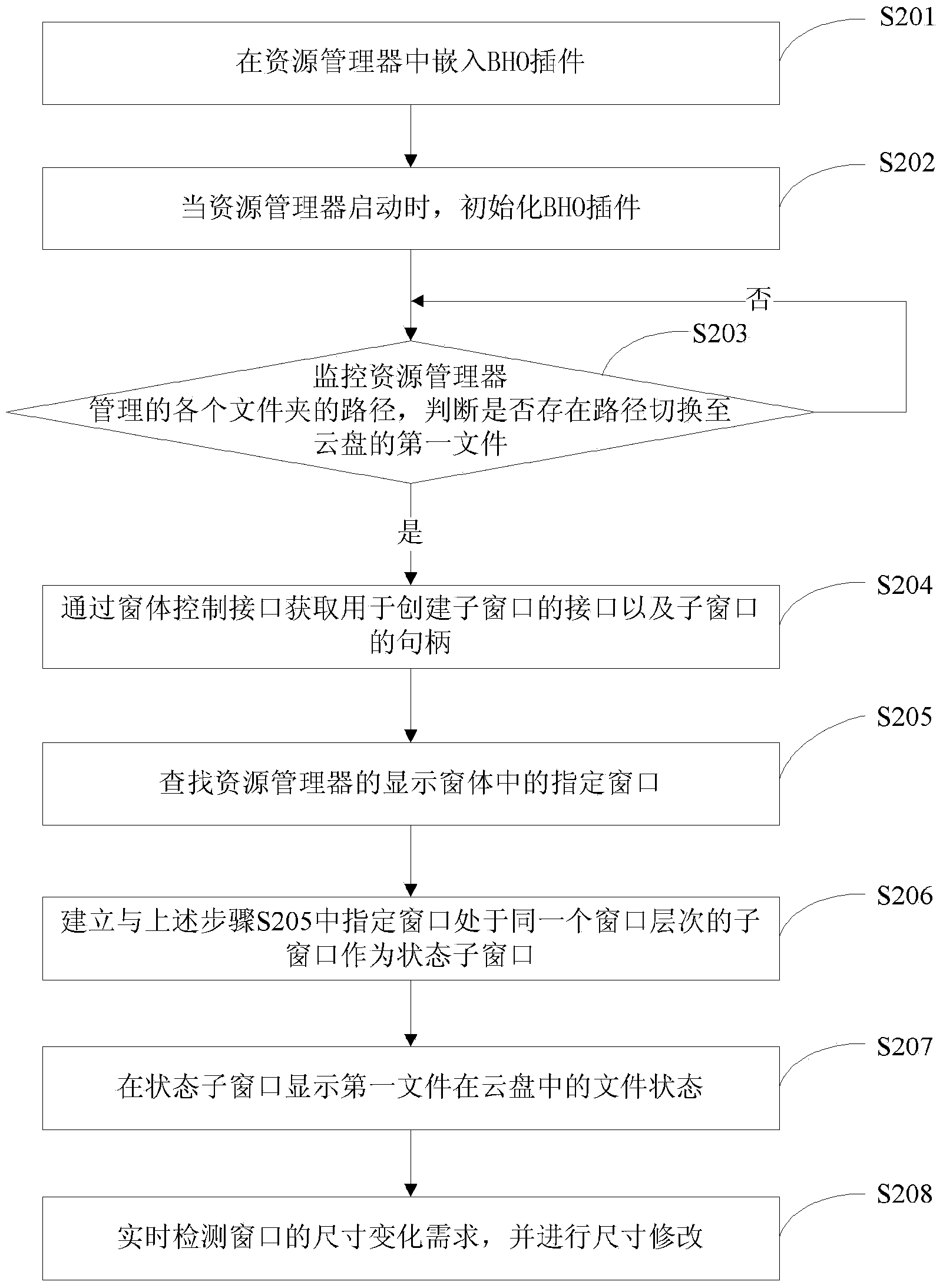
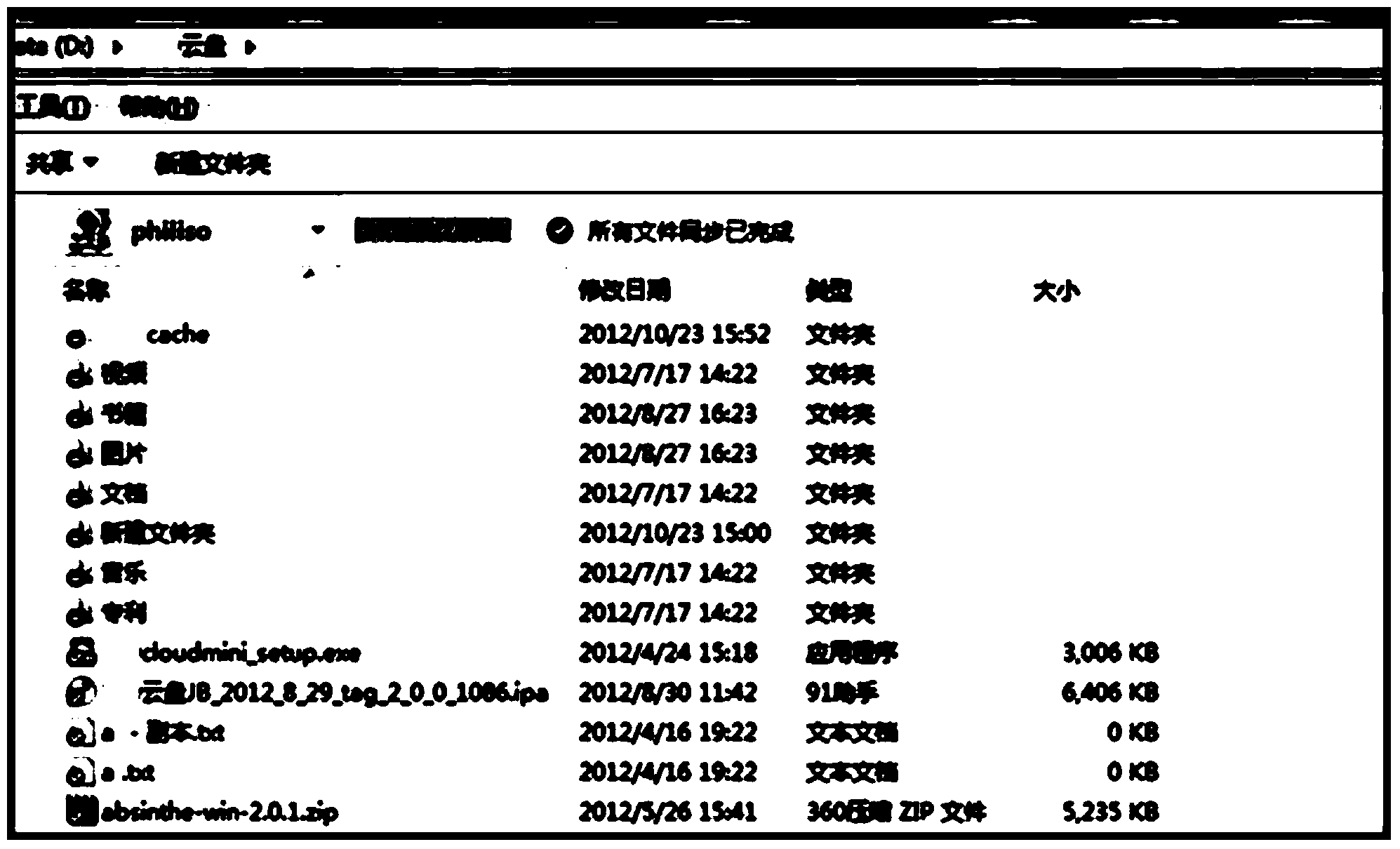
Method and device for displaying cloud disk file statuses
InactiveCN103559029AReal-time monitoring pathImprove experienceSpecific program execution arrangementsSpecial data processing applicationsExtensibilityDocument Status
Owner:BEIJING QIHOO TECH CO LTD +1
Touch screen and manufacturing method thereof as well as display device
ActiveCN104090676AWill not affect operationReduce power consumptionInput/output processes for data processingDisplay deviceComputer science
The invention provides a touch screen and a manufacturing method thereof as well as a display device, relates to the technical field of display, and solves the problems that existing touch screens are power-consuming and limited to operate. The touch screen comprises opposite first and second base plates, wherein the first base plate comprises a first substrate and a nano piezoelectric unit layer formed on the first substrate, and the nano piezoelectric unit layer comprises linear nano piezoelectric materials growing perpendicularly along the first substrate; the second base plate comprises a second substrate as well as first electrodes and second electrodes, the first electrodes and the second electrodes are formed on the second substrate and not contacted with one another, multiple rows of the first electrodes are formed in a first direction, multiple rows of the second electrodes are formed in a second direction, and the first direction is different from the second direction.
Owner:BOE TECH GRP CO LTD
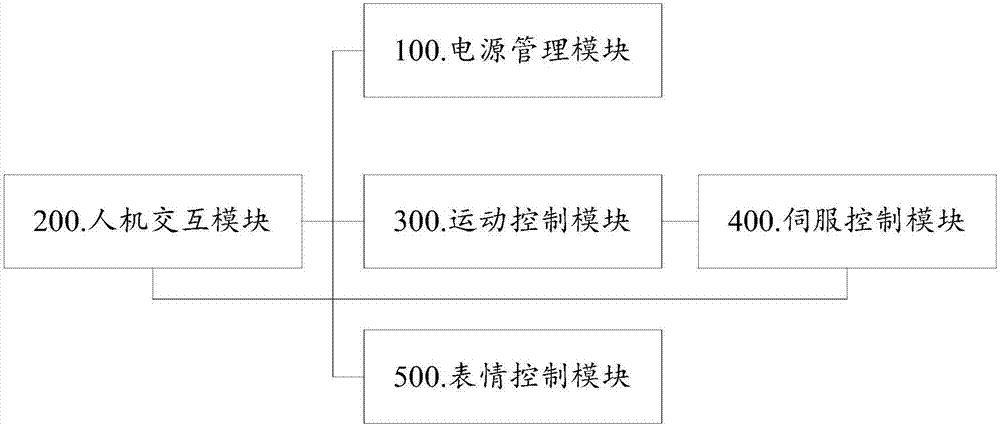
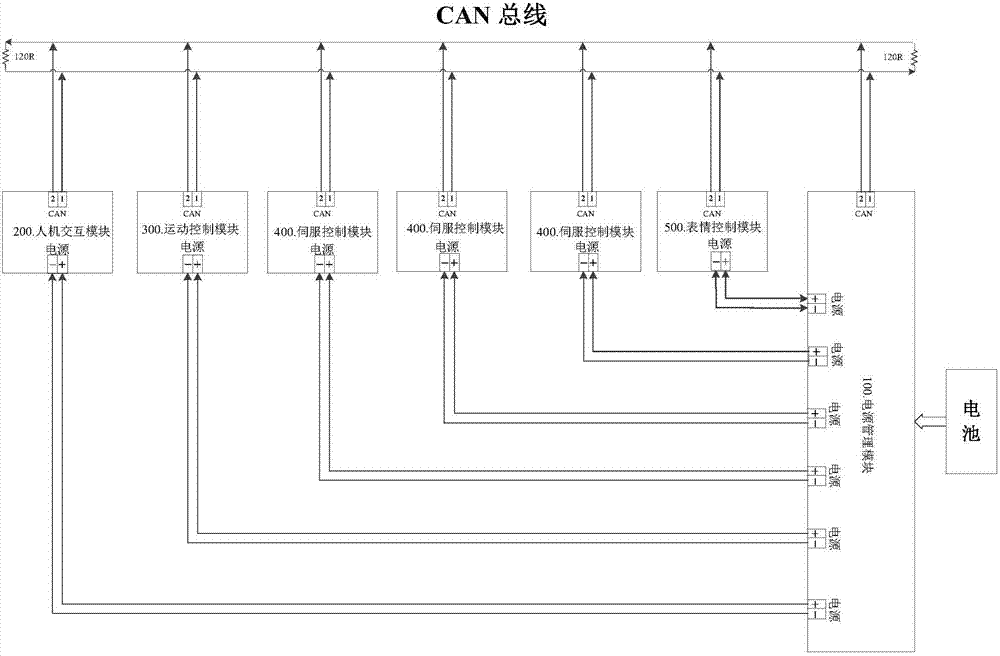
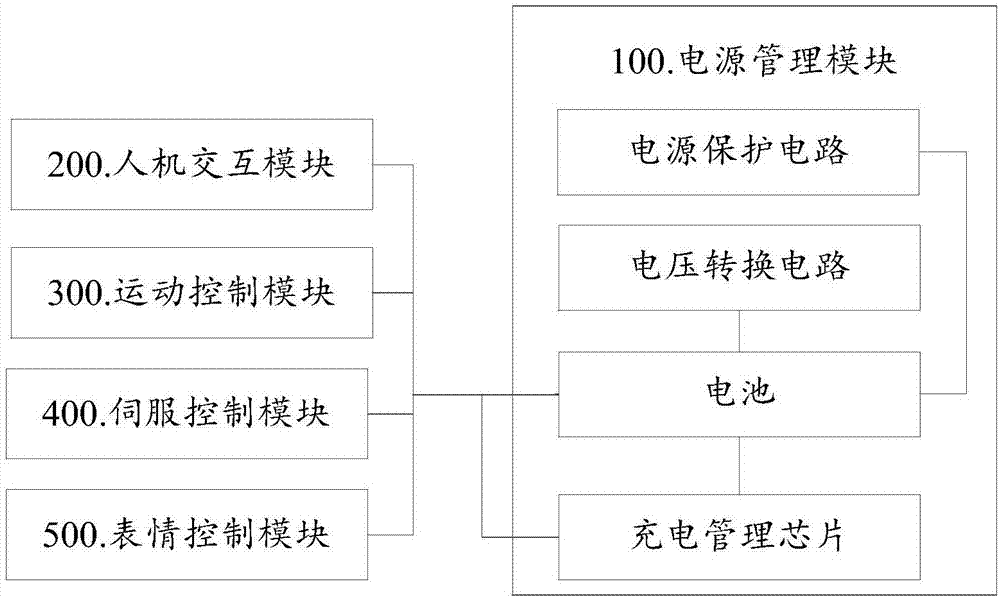
Intelligent robot control system
PendingCN107378971AWill not affect operationAddress reliabilityProgramme-controlled manipulatorControl signalWork task
The invention discloses an intelligent robot control system. The intelligent robot control system comprises a man-machine interaction module, a movement control module, a servo control module and an expression control module, wherein the man-machine interaction module is used for receiving voice information input by a user, analyzing the received voice information and classifying the analyzed voice information, the movement control module is used for adjusting postures of all joints of a robot according to movement command information received by the man-machine interaction module and generating drive command information, the servo control module is used for generating PWM control signals according to the drive command information generated by the movement control module and specifically driving the robot to execute corresponding working tasks according to the PWM control signals, the expression control module is used for executing different expression movements according to expression command information received by the man-machine interaction module, and the man-machine interaction module is in communication with a power management module, the movement control module, the servo control module and the expression control module through a CAN bus.
Owner:NANJING AVATARMIND ROBOT TECH CO LTD
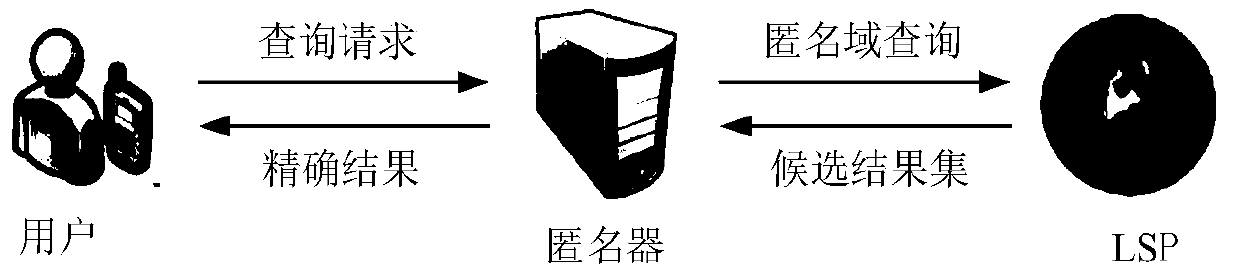
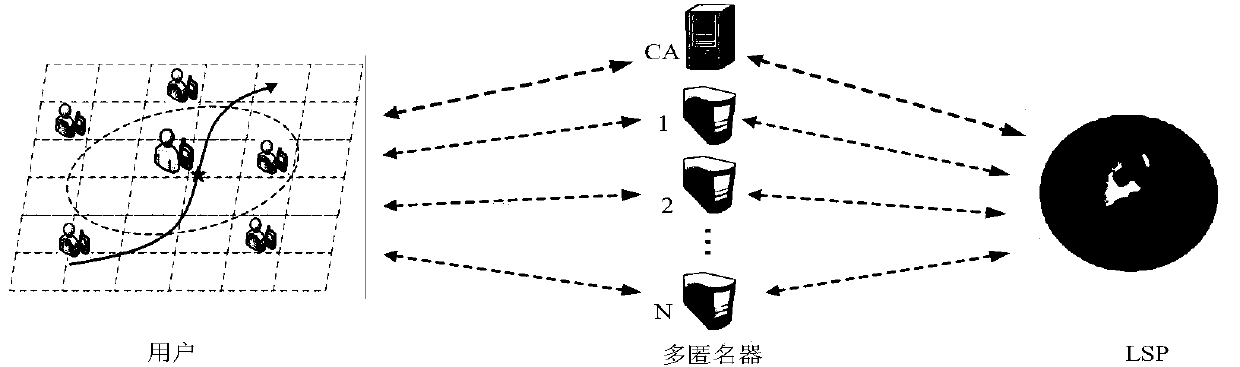
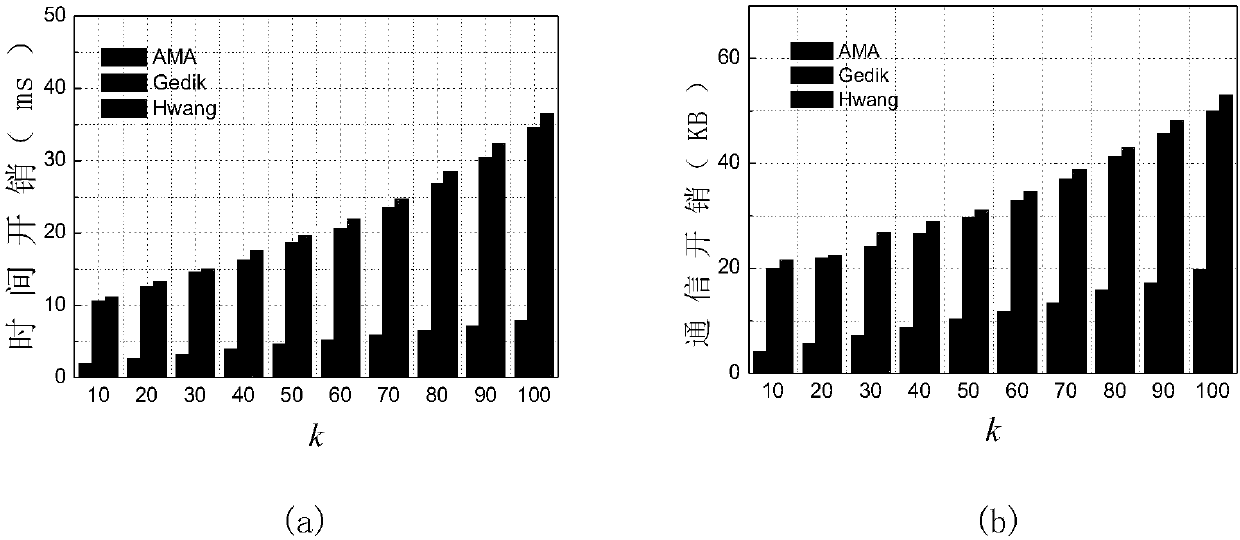
Anonymity based on multi-anonymizer (AMA) location service method
InactiveCN108632237AImprove privacy protectionResist Privacy AttacksKey distribution for secure communicationUser identity/authority verificationPrivacy protectionComputer terminal
The invention discloses an Anonymity Based on Multi-Anonymizer (AMA) location service method. The AMA location service method comprises the steps that: step 1, a mobile terminal conducts identity authentication in a CA to obtain a pseudonym, and user query content is divided into n pieces of sub-information by using a Shamir threshold scheme; step 2, the mobile terminal selects n different anonymizers to anonymize the user, and transmits the n pieces of sub-information to an LBS server by means of the anonymizers; step 3, the LBS server aggregates t pieces of information received from the n anonymizers at first, restores the user query content according to the Shamir threshold scheme, and then queries POIs contained in an anonymous region in an LBS database according to the query content;step 4, the LBS server randomly selects w different anonymizers to forward an encrypted candidate result set to the mobile terminal; step 5, and the mobile terminal obtains a precise query result through filtering and refinement. The AMA location service method strengthens the trajectory privacy protection of the user, and effectively solves the single point failure risk of a single anonymizer.
Owner:HUNAN UNIV OF SCI & TECH
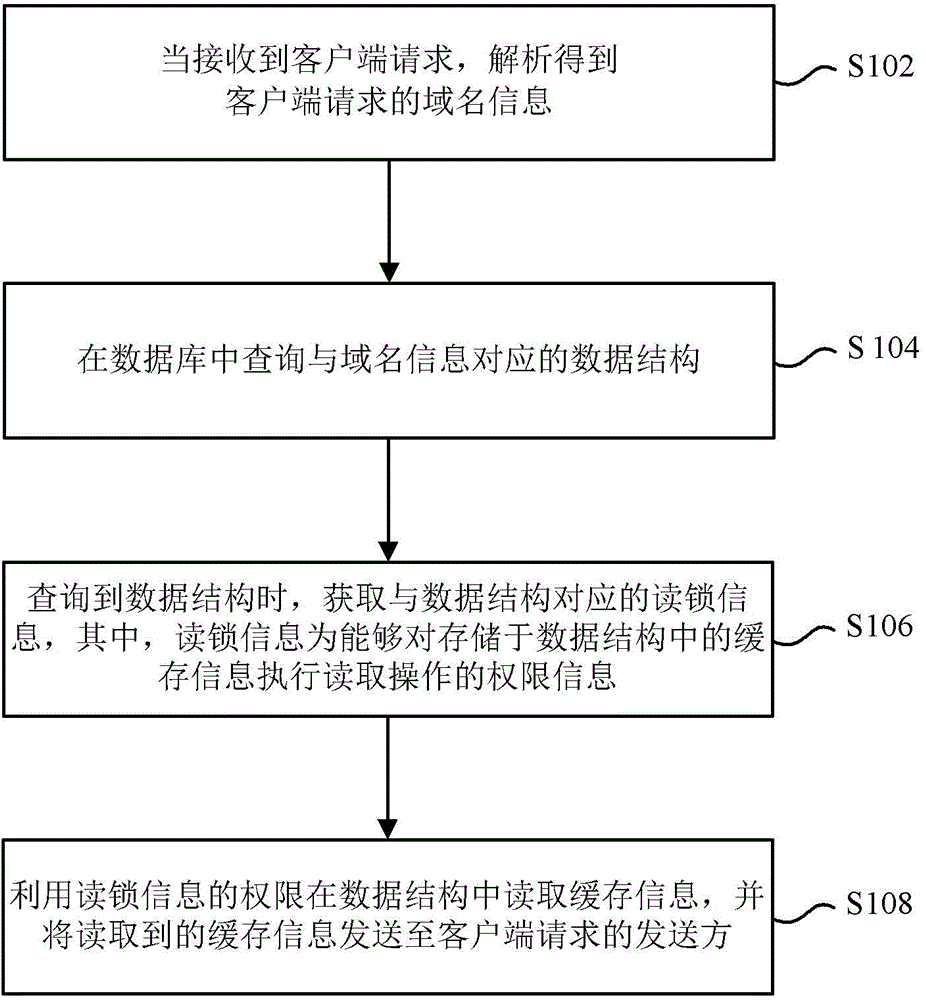
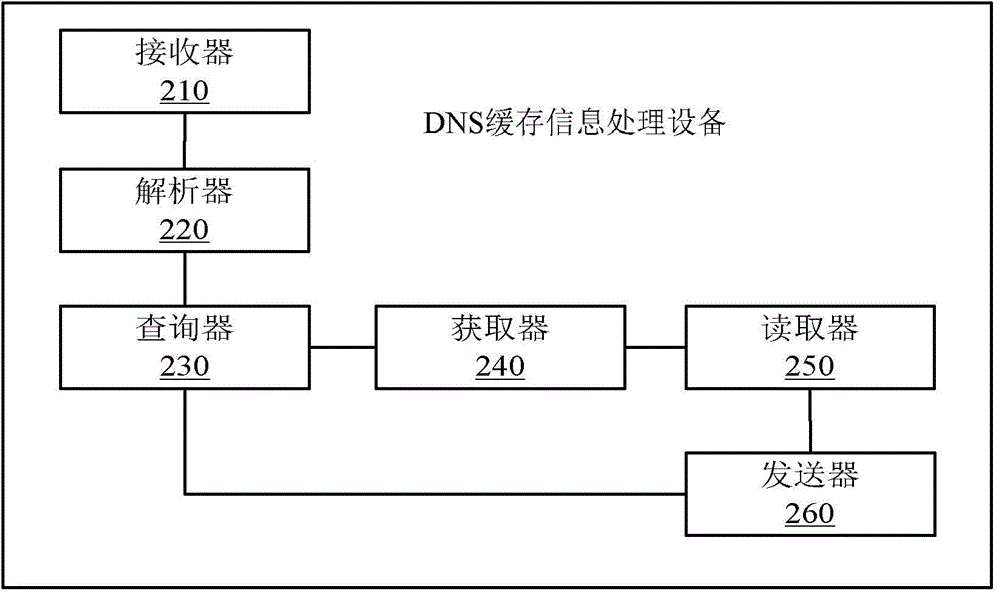
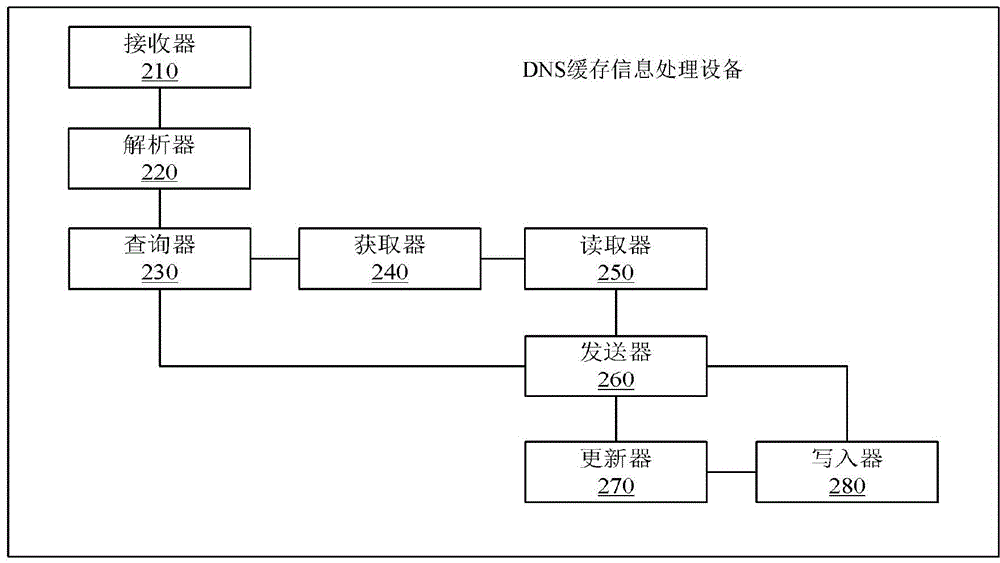
DNS cache information processing method, device and system
ActiveCN103957239AAccurate and fast executionQuality improvementTransmissionSpecial data processing applicationsInformation processingDomain name
The invention provides a DNS cache information processing method, device and system. The method includes the steps that when a request of a client side is received, domain name information requested by the client side is analyzed; a data structure corresponding to the domain name information is inquired in a database; when the data structure is inquired, read lock information corresponding to the data structure is obtained, wherein the read lock information is authority information which can execute read operation on cache information stored in the data structure; the authority of the read lock information is used for reading the cache information in the data structure, and the read cache information is sent to a sender of the request of the client side. The DNS cache information processing method, device and system have the advantages of being capable of increasing corresponding speed and the throughout of the cache information, improving flexibility of the cache information and promoting quality of stored information.
Owner:BEIJING QIHOO TECH CO LTD +2
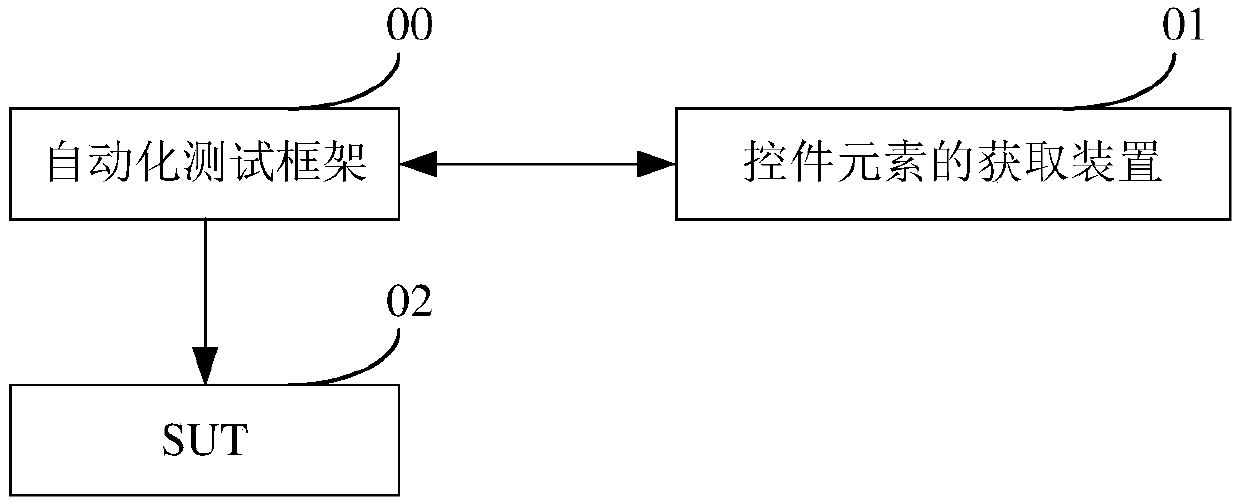
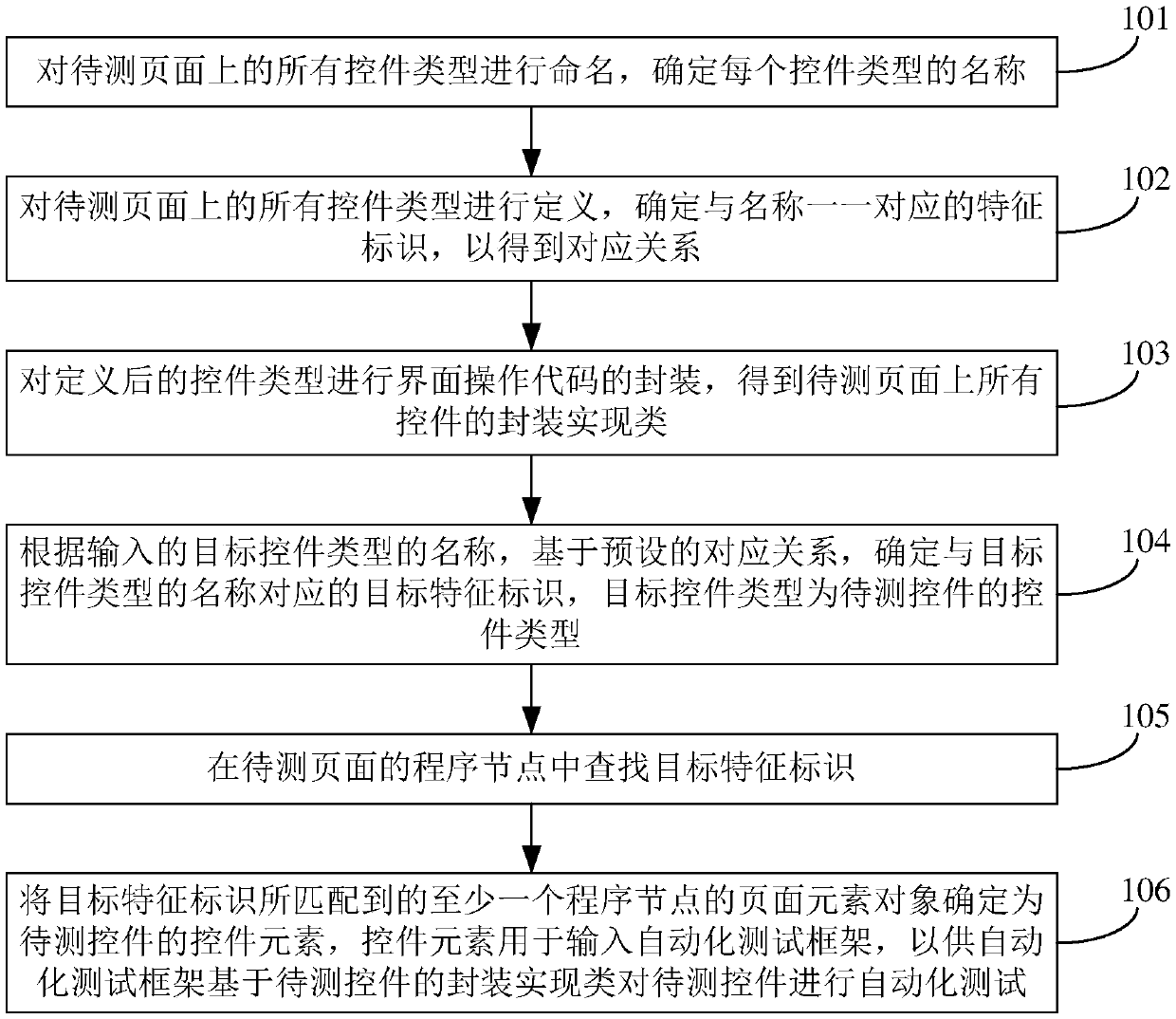
Acquisition method and device of control element, automatic testing system and storage medium
InactiveCN110297752AImprove accuracyImprove reliabilitySoftware testing/debuggingTarget controlAutomatic testing
The invention discloses an acquisition method and device of a control element, an automatic testing system and a storage medium, and belongs to the field of automatic testing. The acquisition method comprises the steps: according to an input name of a target control type, determining target feature identifiers corresponding to the name of the target control type based on a preset corresponding relation, wherein the corresponding relation comprises names of all control types on a page to be tested and feature identifiers in one-to-one correspondence with the names; searching a target feature identifier in a program node of the to-be-tested page; and determining a page element object of at least one program node matched with the target feature identifier as a control element of the to-be-measured and controlled piece, and inputting the control element into an automatic test framework so as to enable the automatic test framework to automatically test the to-be-measured and controlled piece based on the packaging implementation class of the to-be-measured and controlled piece. According to the acquisition method and device, the problems of low development efficiency of automatic test cases and low reliability of automatic test in related technologies are solved. This acquisition method is used for automated testing.
Owner:HUAWEI TECH CO LTD
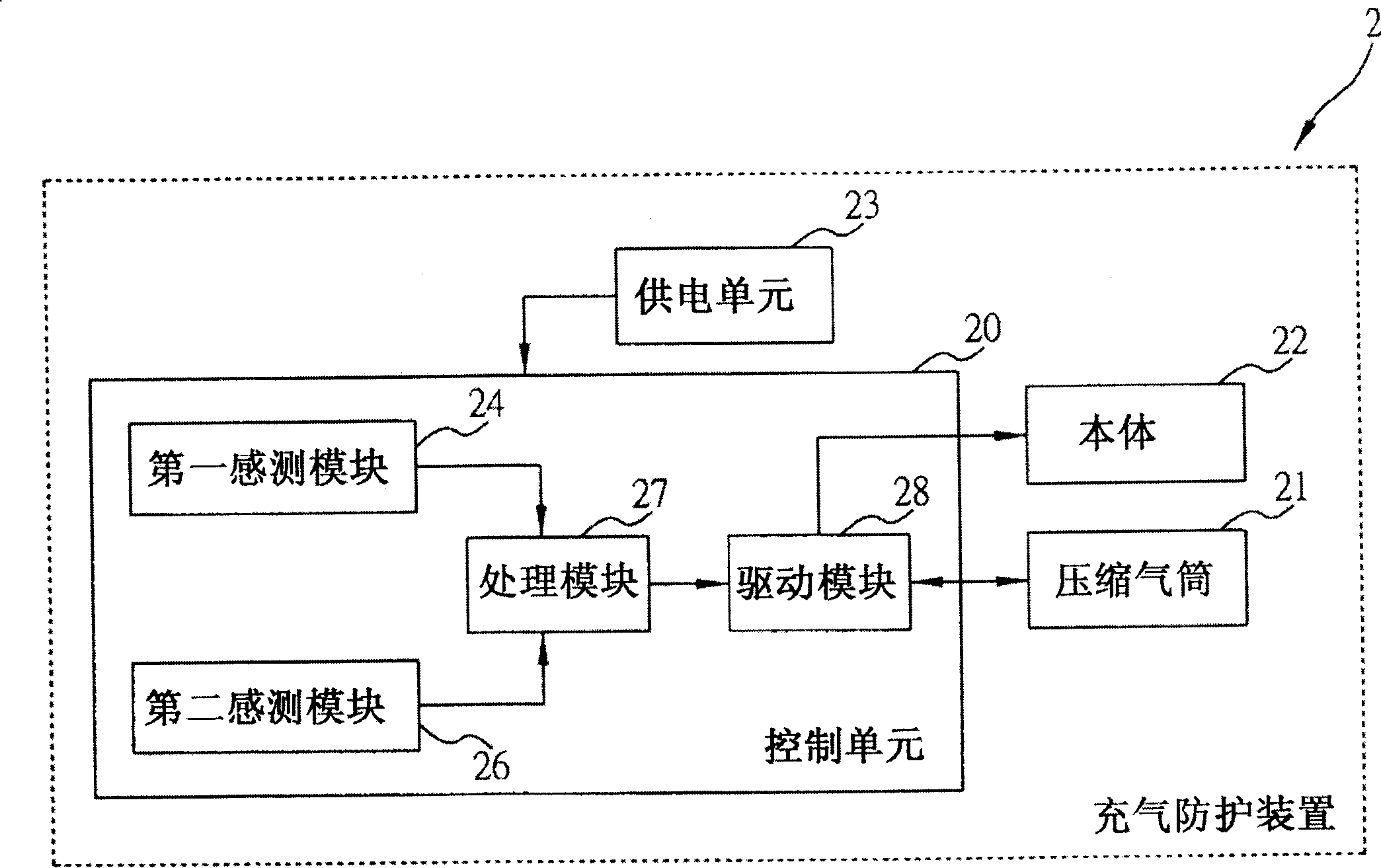
Inflation protection device and method
ActiveCN1913754AWill not affect operationNo compromise on convenienceCasings/cabinets/drawers detailsElectrical apparatus contructional detailsEmbedded systemControl unit
An inflatable protection device and method are used for the portable electronic equipment, which includes the body that is the equipment shell covered by several inflatable hollow closed balloons, an air-container for storing the air which is connected with the body, and a control unit connected with the body and the air-container which is used to sense whether the equipment is falling or not. In the invention, the inflatable balloons of the body protective device usually flatly affixed to the portable electronic equipment, they do not take up additional space, and the protective device can be activated automatically when it is sensing the fall of the portable electronic equipment.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO
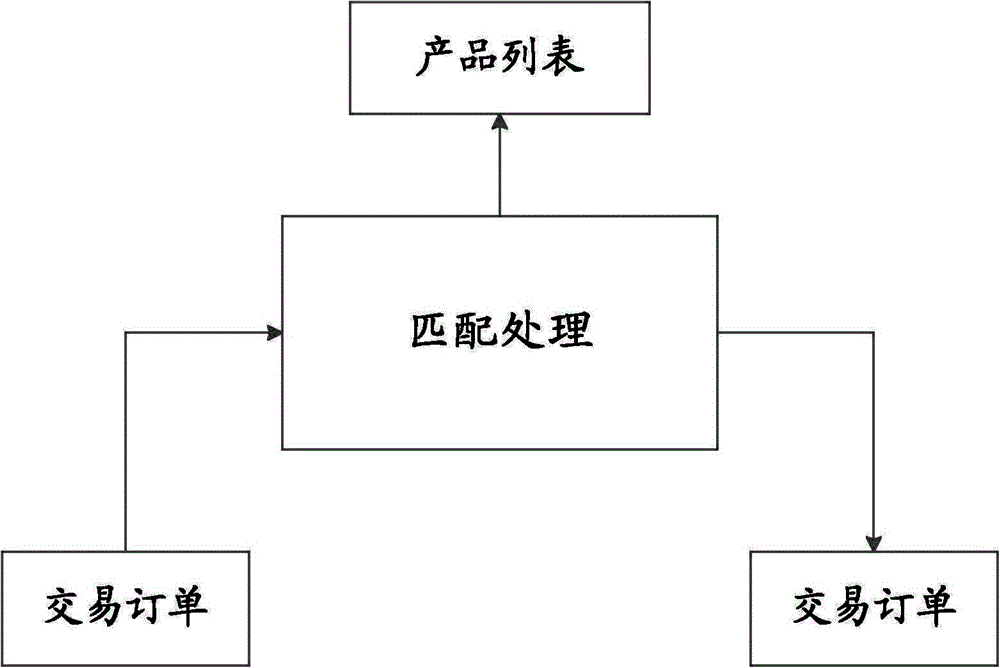
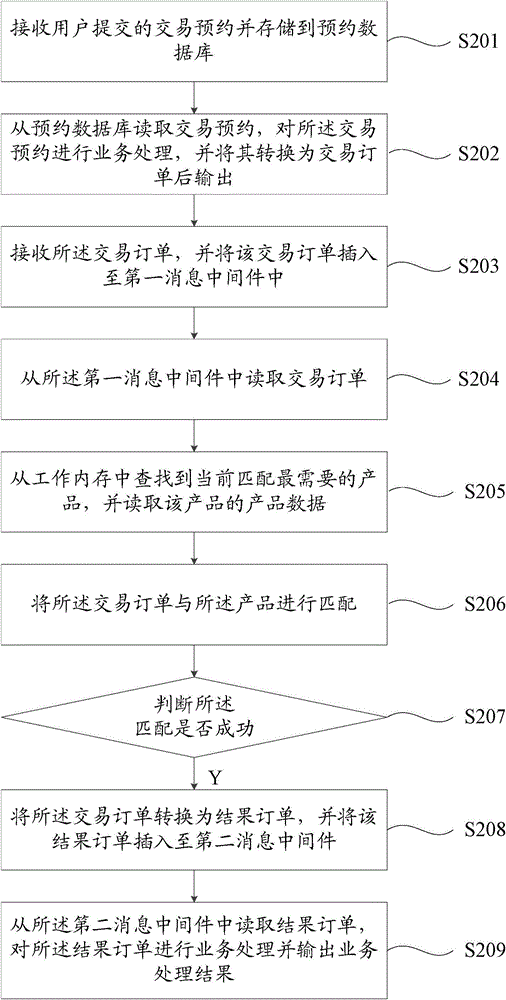
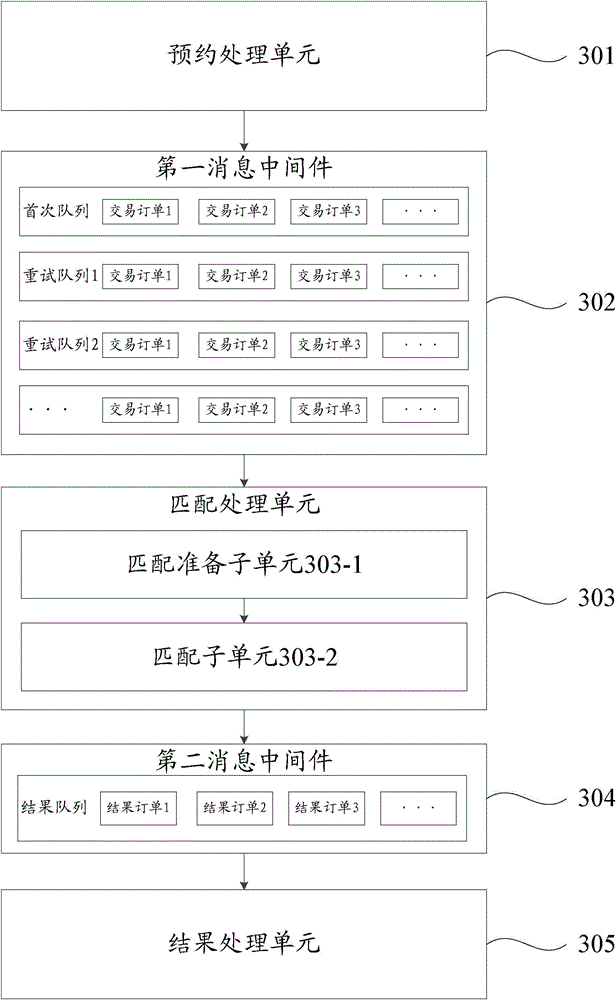
Transaction matching method and transaction matching system
InactiveCN105096174AAvoid serious wasteAddress riskBuying/selling/leasing transactionsSpecial data processing applicationsProgramming languageMatching methods
The invention discloses a transaction matching method and a transaction matching system. The transaction matching method comprises the steps of carrying out service processing on a transaction appointment submitted by a user and generating a transaction order; regarding the transaction order as a message so as to be transmitted in a first message-oriented middleware; reading the transaction order transmitted in the first message-oriented middleware based on any one server in a matching processing cluster formed by a plurality of servers, matching the transaction order with on-sale products, and generating a result order; and carrying out service processing on the result order. The transaction matching method disclosed by the invention adopts cluster processing, and problems caused by increase in service quantity are processed smoothly through a distributed framework. In addition, overall operations of the transaction matching system are not affected if any one server in the cluster breaks down, and normal operations of the transaction matching system are ensured by only removing the failure server from the cluster, thereby reducing the risk of the transaction matching system.
Owner:ALIBABA GRP HLDG LTD
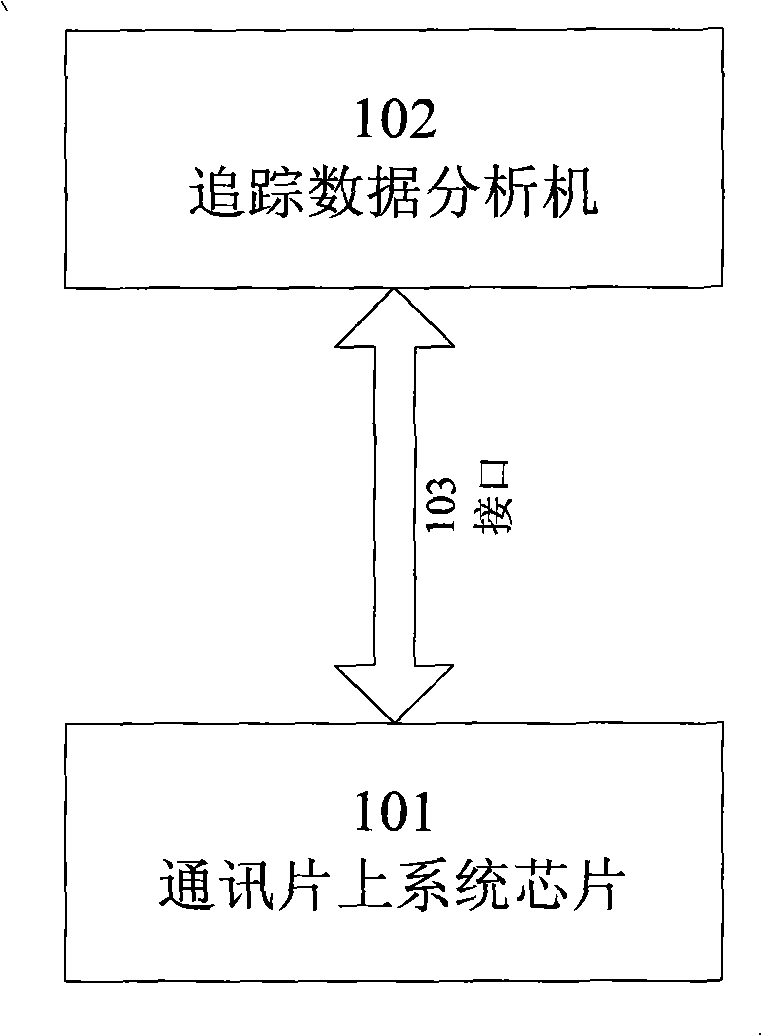
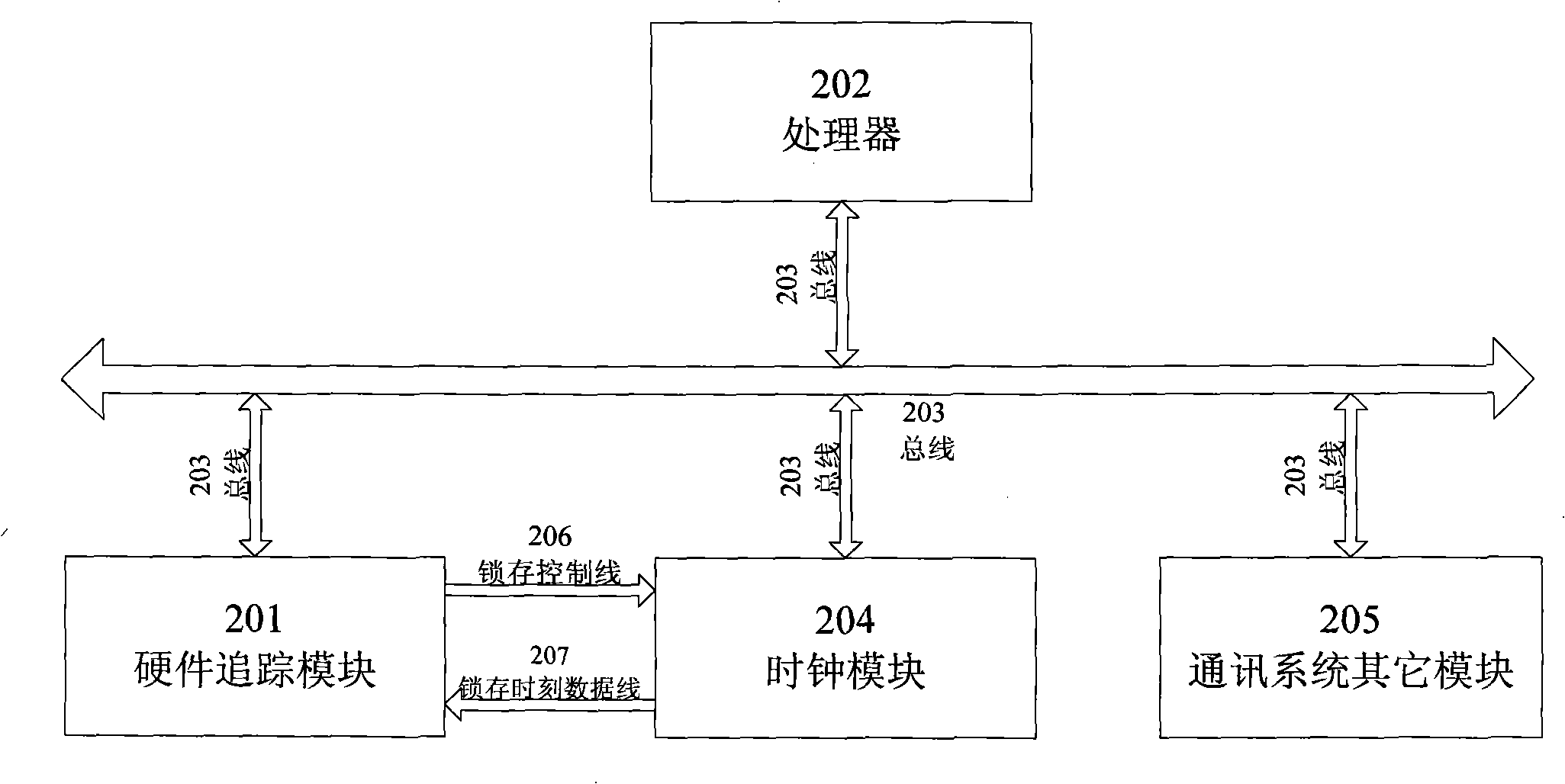
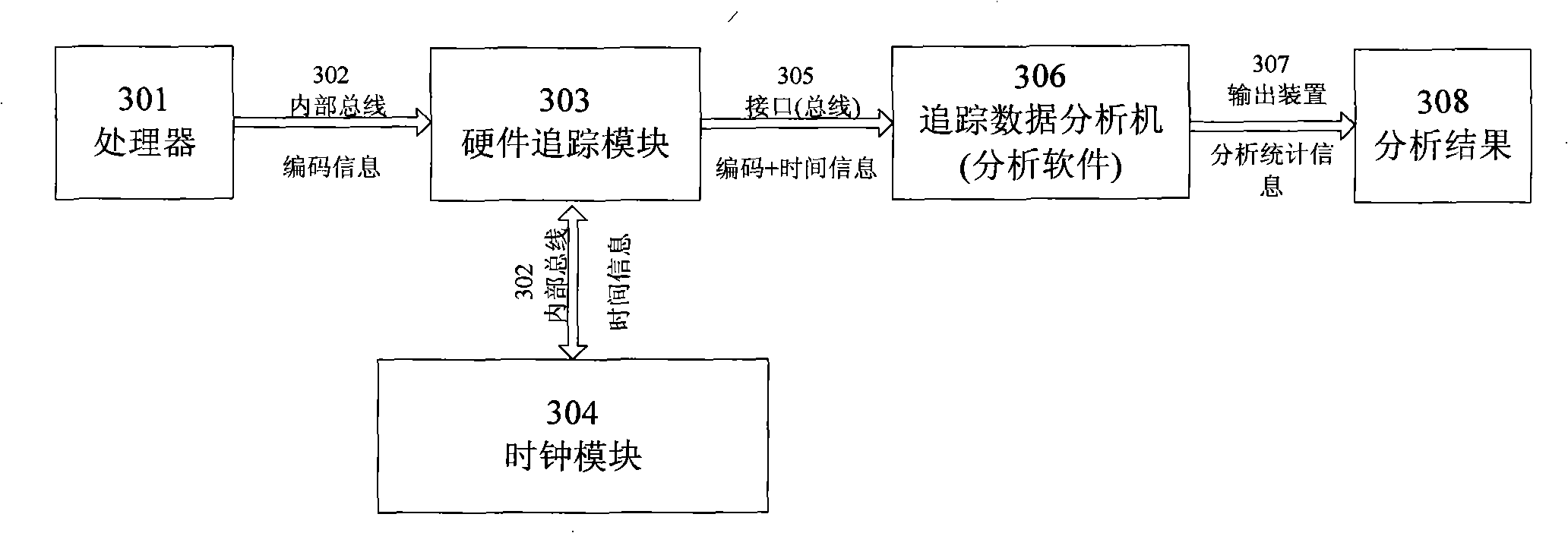
Communication chip system chip tracing and debugging method and apparatus
InactiveCN101493847AReduce overheadWill not affect operationSoftware testing/debuggingSpecial data processing applicationsReal systemsCommunications system
The invention discloses a method and a device for tracing and debugging a system chip of a communication chip, wherein, the system chip of the communication chip comprises a hardware tracking module. The method has the following steps: firstly, the trace and debug data is written and stored in the hardware tracking module, and then output to a track data analysis machine which stores the track and debug data and then analyses and processes the track and debug data to determine the problem of the system. The method and the device collects the data in debugging in batch according to the demand of design, reduces the cost of software of the original system, is more similar to the real system, can automatically sore the very important system time information in the communication system while in the process of recording the track and debug date, help the designer to effectively understand and analyze the integral process of the system by automatic software analysis, determine the problem more rapidly, save workload of the design staff, and improve the work efficiency.
Owner:ZTE CORP
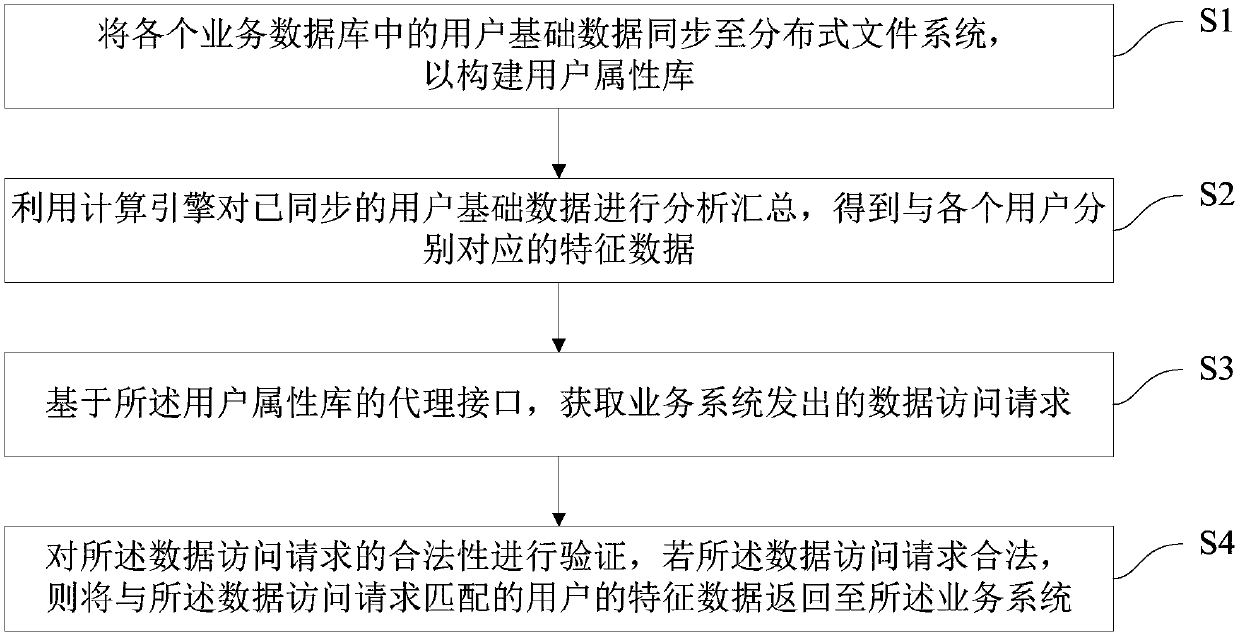
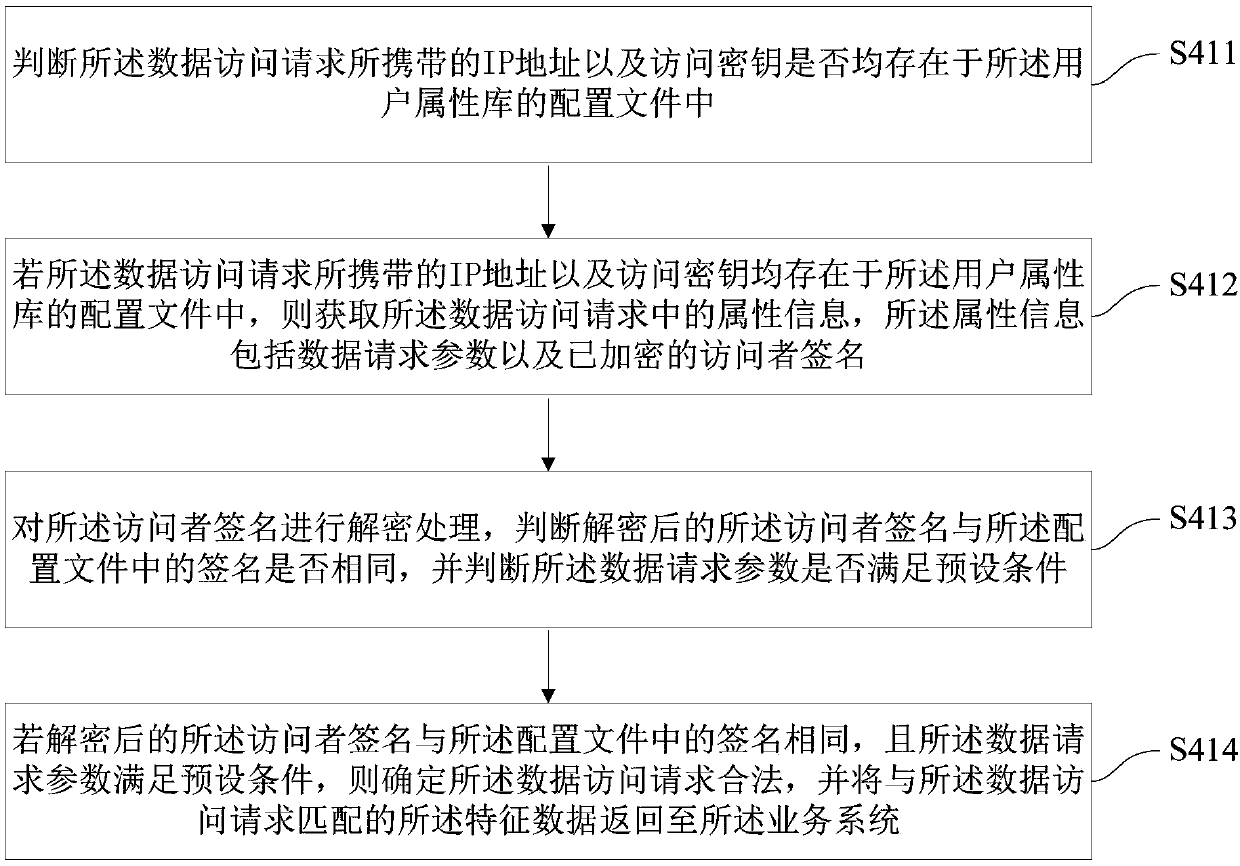
Method for obtaining user feature data, and server
InactiveCN107798037AImprove acquisition efficiencyRealize evaluationDatabase management systemsSpecial data processing applicationsBusiness dataDistributed File System
The invention provides a method for obtaining user feature data, and a server, and is suitable for the technical field of Internet. The method comprises the following steps that: synchronizing user basic data in each business data to a distributed file system to construct a user attribute base; utilizing a calculation engine to analyze and gather the synchronized user basic data to obtain featuredata independently corresponding to each user; on the basis of the interface of the user attribute base, obtaining a data access request emitted from a business system; and verifying the validity of the data access request, and if the data access request is legal, returning the feature data of the user matched with the data access request to the business system. By use of the method, under a situation that multiple business databases are separated, the feature data independently corresponding to each user can be quickly analyzed, the feature data of the user is comprehensively evaluated, the operation of an existing business system is not affected, and accurate data support is provided for functions including the personalized business customization of the user, business recommendation andthe like.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com