Patents
Literature
647 results about "Large networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
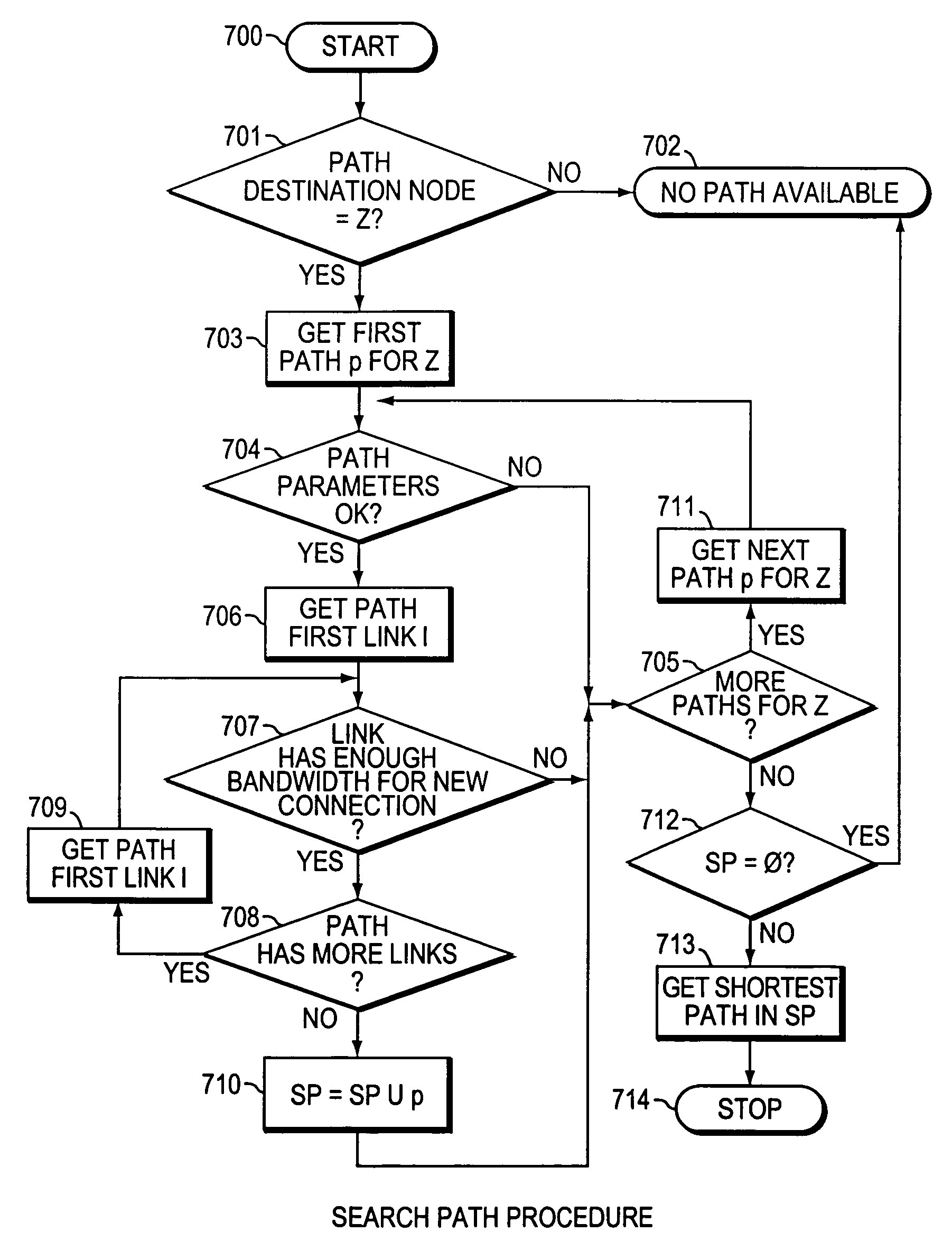
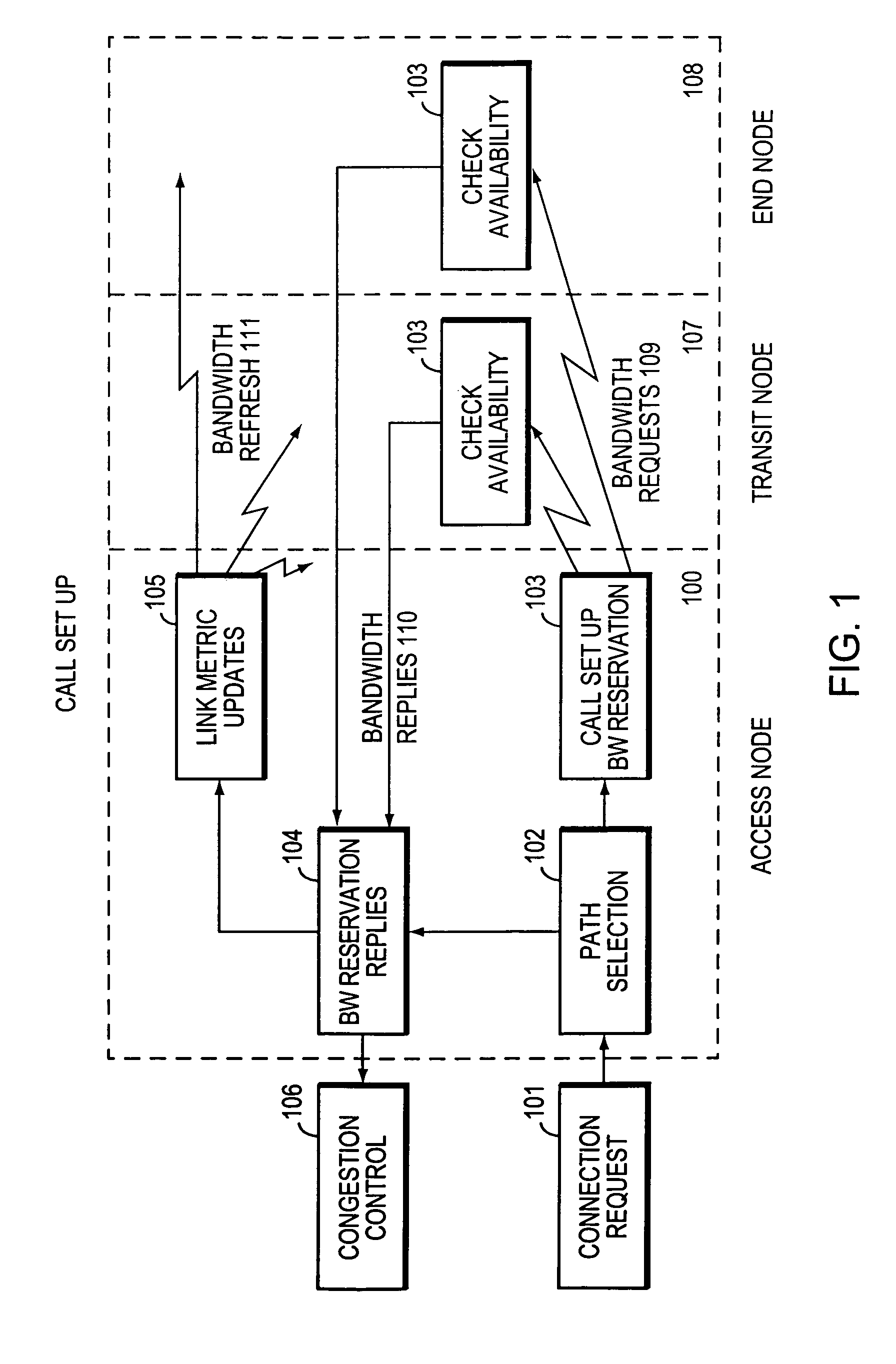
Method and system for minimizing the connection set up time in high speed packet switching networks
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
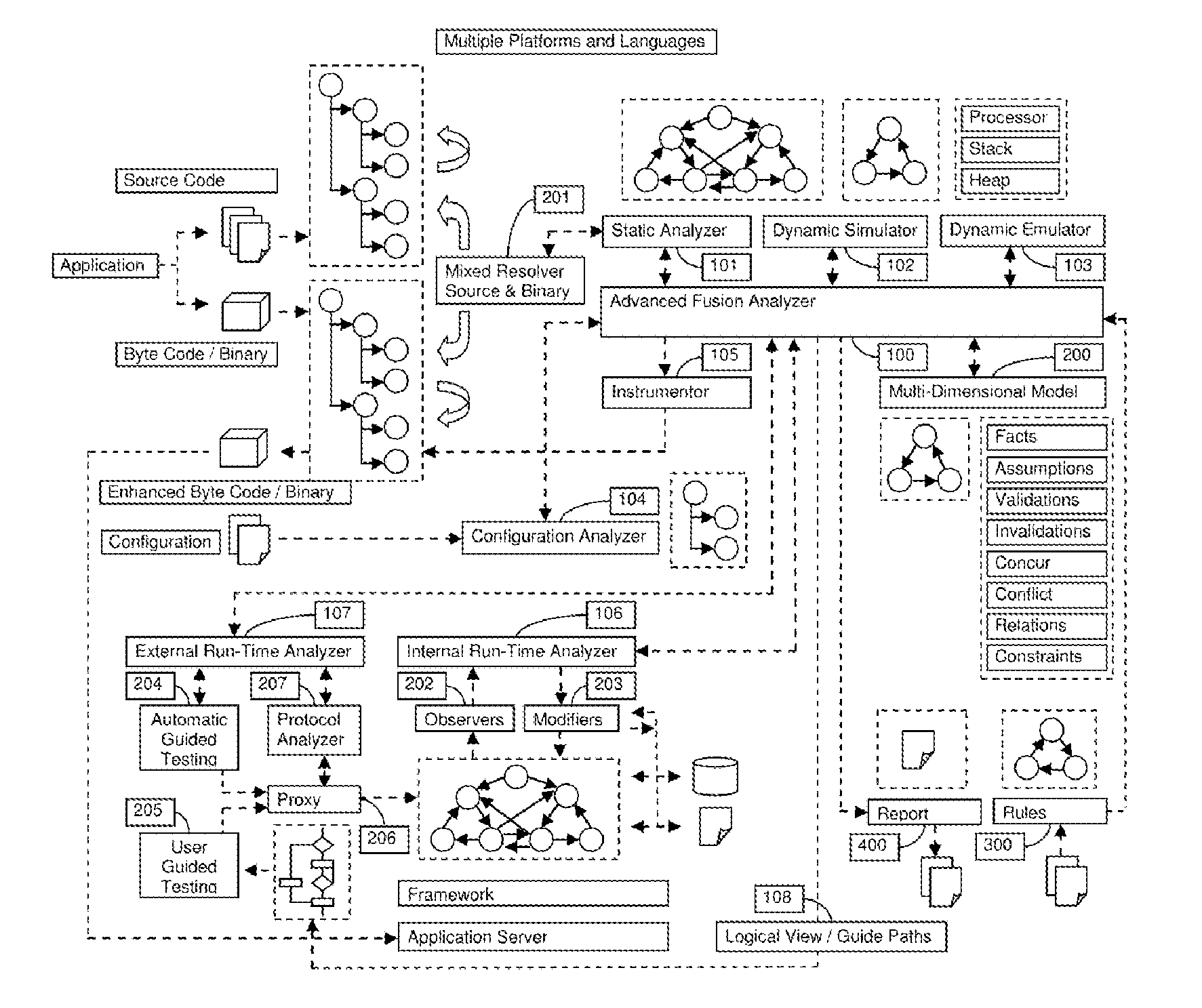
A System for analyzing applications in order to find security and quality issues
InactiveUS20150309813A1Accurate analysisError detection/correctionComputer security arrangementsMachine controlWeb application
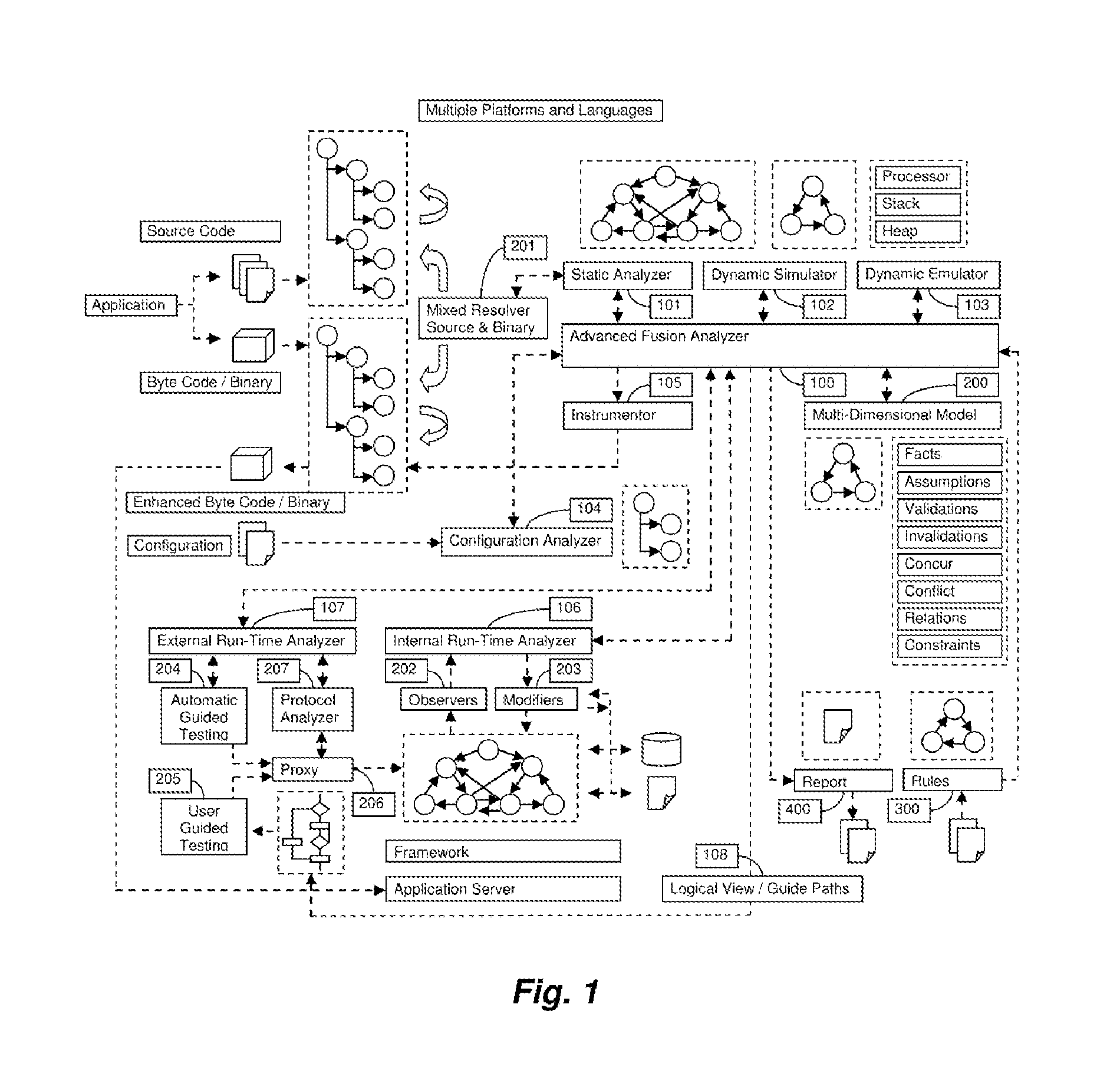
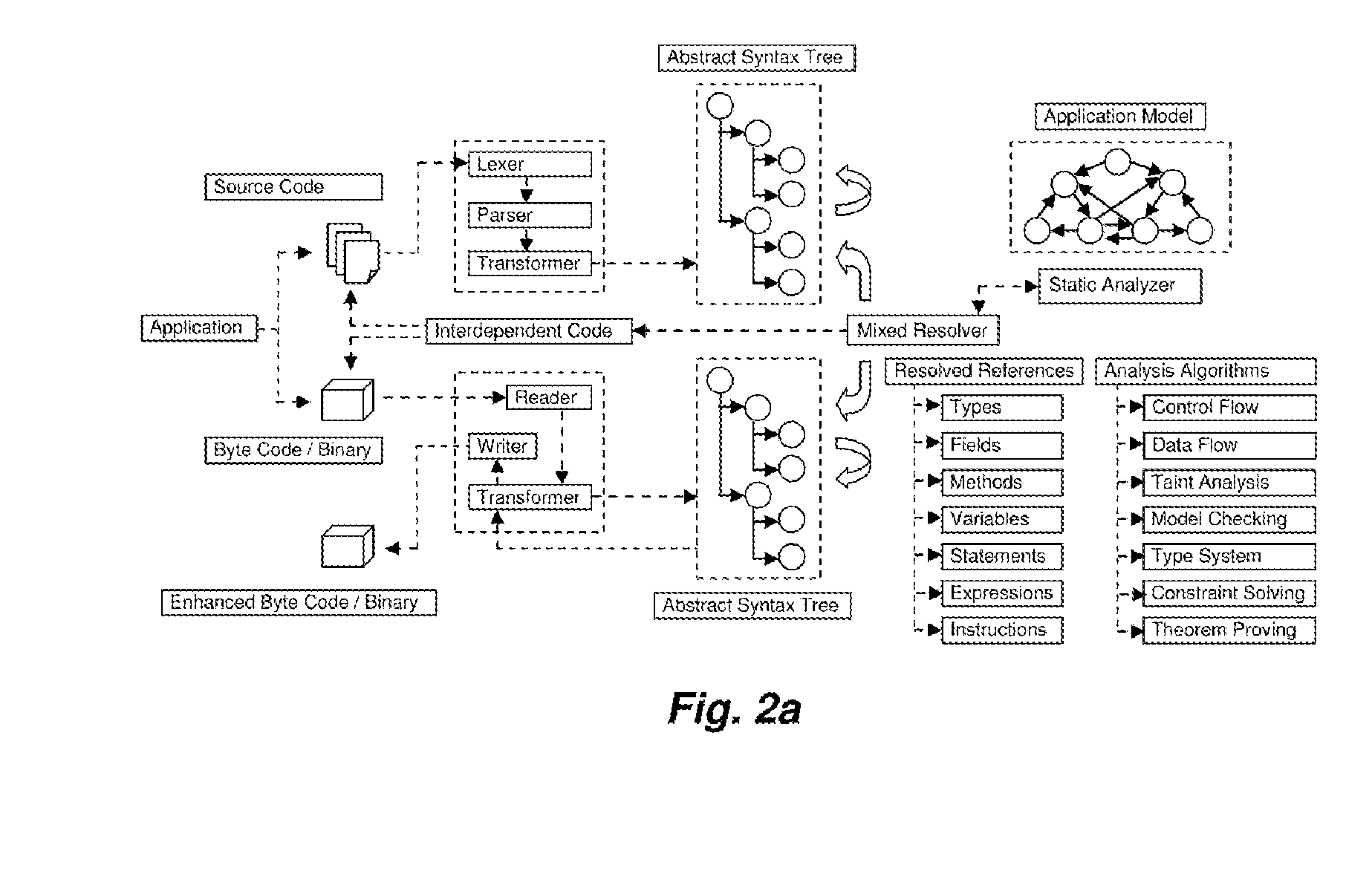
The present invention relates to field of application and more specifically to analysis of applications for determining security and quality issues. The present invention describes an application analysis system providing a platform for analyzing applications which is useful in finding security and quality issues in an application. In particular, the present invention is composed of an advanced fusion analyzer which gains an understanding of the application behavior by using a multi-way coordination and orchestration across components used in the present invention to build an continuously refine a model representing knowledge and behavior of the application as a large network of objects across different dimensions and using reasoning and learning logic on this model along with information and events received from the components to both refine and model further as well as drive the components further by sending information and events to them and again using the information and events received as a result to further trigger the entire process until the system stabilizes. The present invention is useful in analysis of internet / intranet based web applications, desktop applications, mobile applications and also embedded systems as well as for hardware, equipment and machines controlled by software.
Owner:IAPPSECURE SOLUTIONS PVT
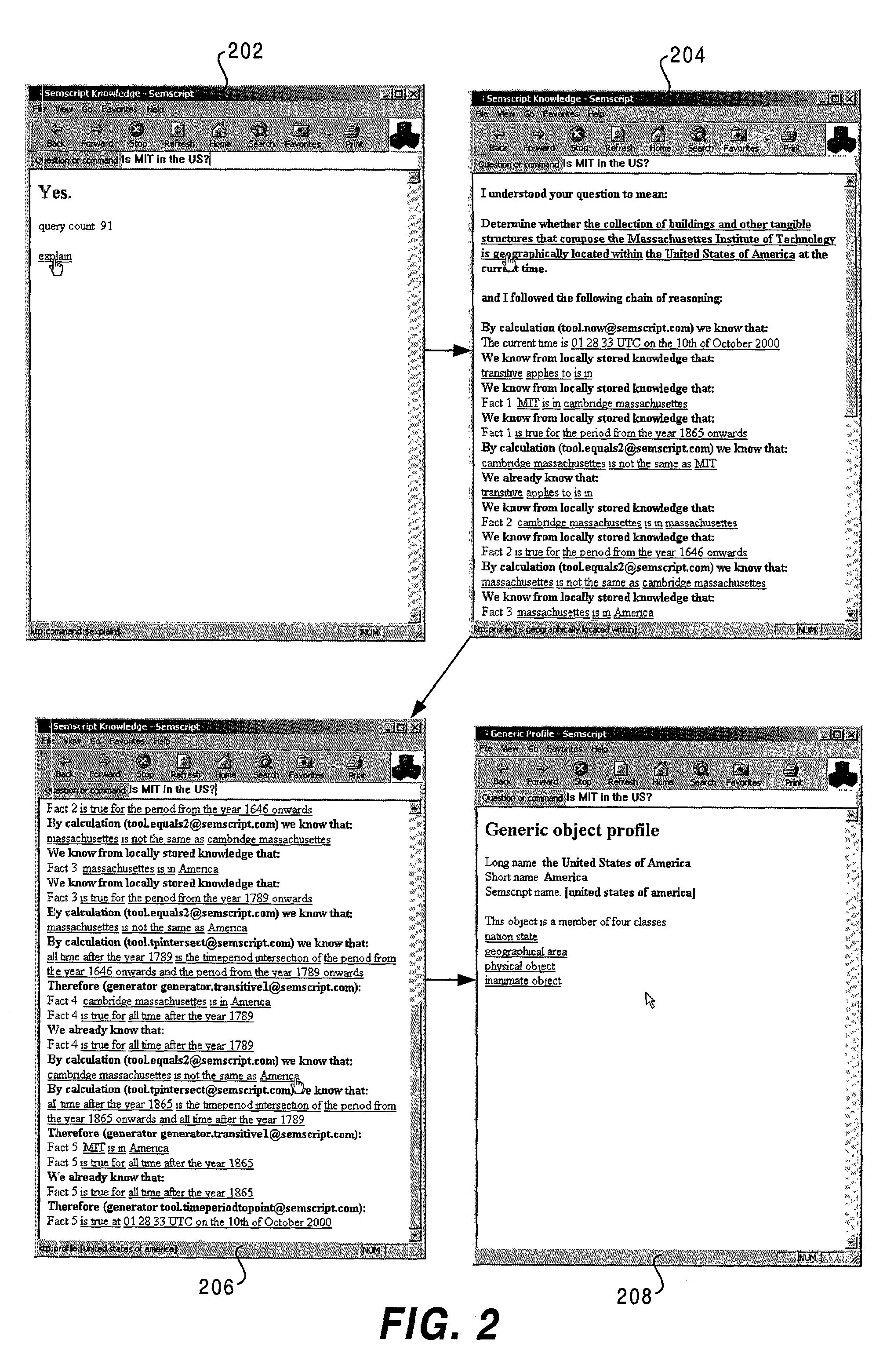
Knowledge storage and retrieval system and method
InactiveUS7013308B1Smooth interfaceSimple processDigital data information retrievalData processing applicationsProgramming languageWeb browser
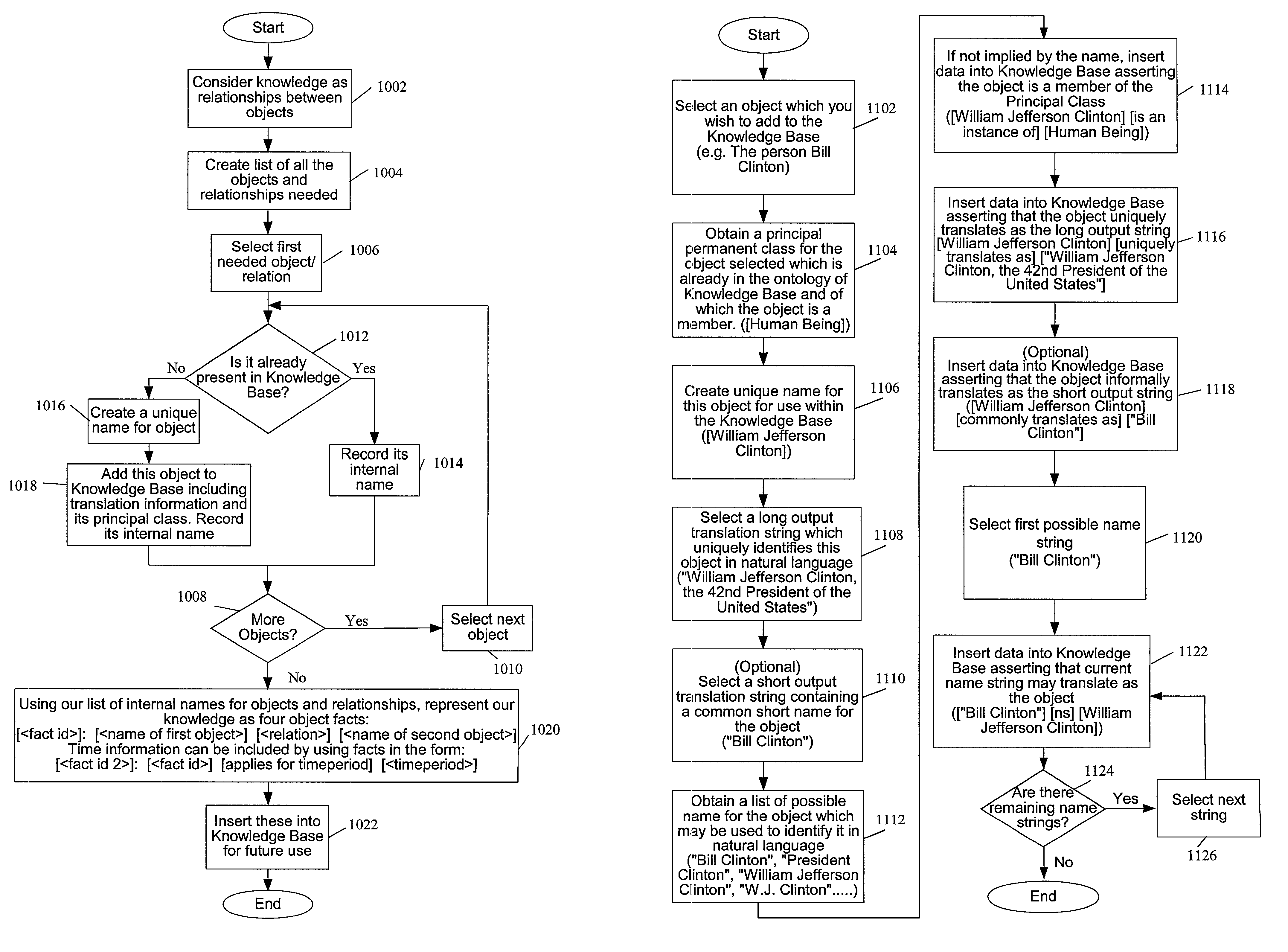
A system and method for representing, storing and retrieving real-world knowledge on a computer or network of computers is disclosed. Knowledge is broken down into permanent atomic “facts” which can be stored in a standard relational database and processed very efficiently. It also provides for the efficient querying of a knowledge base, efficient inference of new knowledge and translation into and out of natural language. Queries can also be processed with full natural language explanations of where the answers came from. The method can also be used in a distributed fashion enabling the system to be a large network of computers and the technology can be integrated into a web browser adding to the browser's functionality.
Owner:AMAZON TECH INC
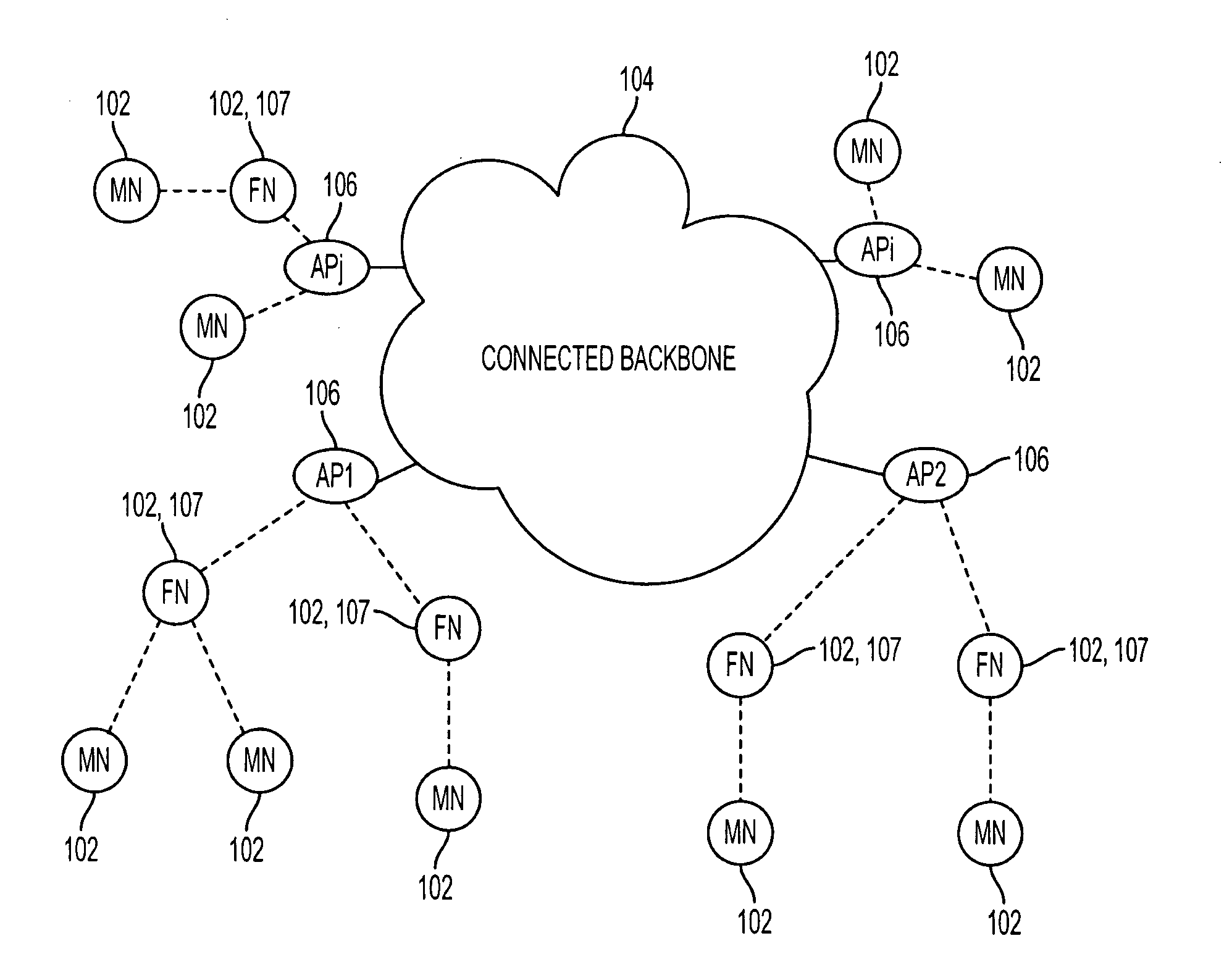
System and method to support multicast routing in large scale wireless mesh networks
ActiveUS20060098607A1Quick changeReduce overheadMultiplex system selection arrangementsNetwork topologiesTree rootWireless mesh network
Provided is a system and method for a multicast routing algorithm to work in infrastructure based mesh networks. It chooses access points, fixed infrastructure gateway nodes connected to each other and / or the global internet via a wired / wireless backbone, as a group of local multicast group leaders to form a multicast group leader cloud. Each local multicast group leader is elected on-demand according to the local multicast group member's request. Each local multicast group leader forms a local multicast tree rooted at this leader connecting all multicast group members associated with the AP. The processes of electing and maintaining local multicast trees rooted at APs enable efficient coordination with underlying unicast routing to exploit the advantages of fixed infrastructure nodes. Therefore, routing overhead and multicast tree convergence time are reduced. The method can support large networks with fast topology change due to fast convergence and reduced routing overhead.
Owner:ARRIS ENTERPRISES LLC
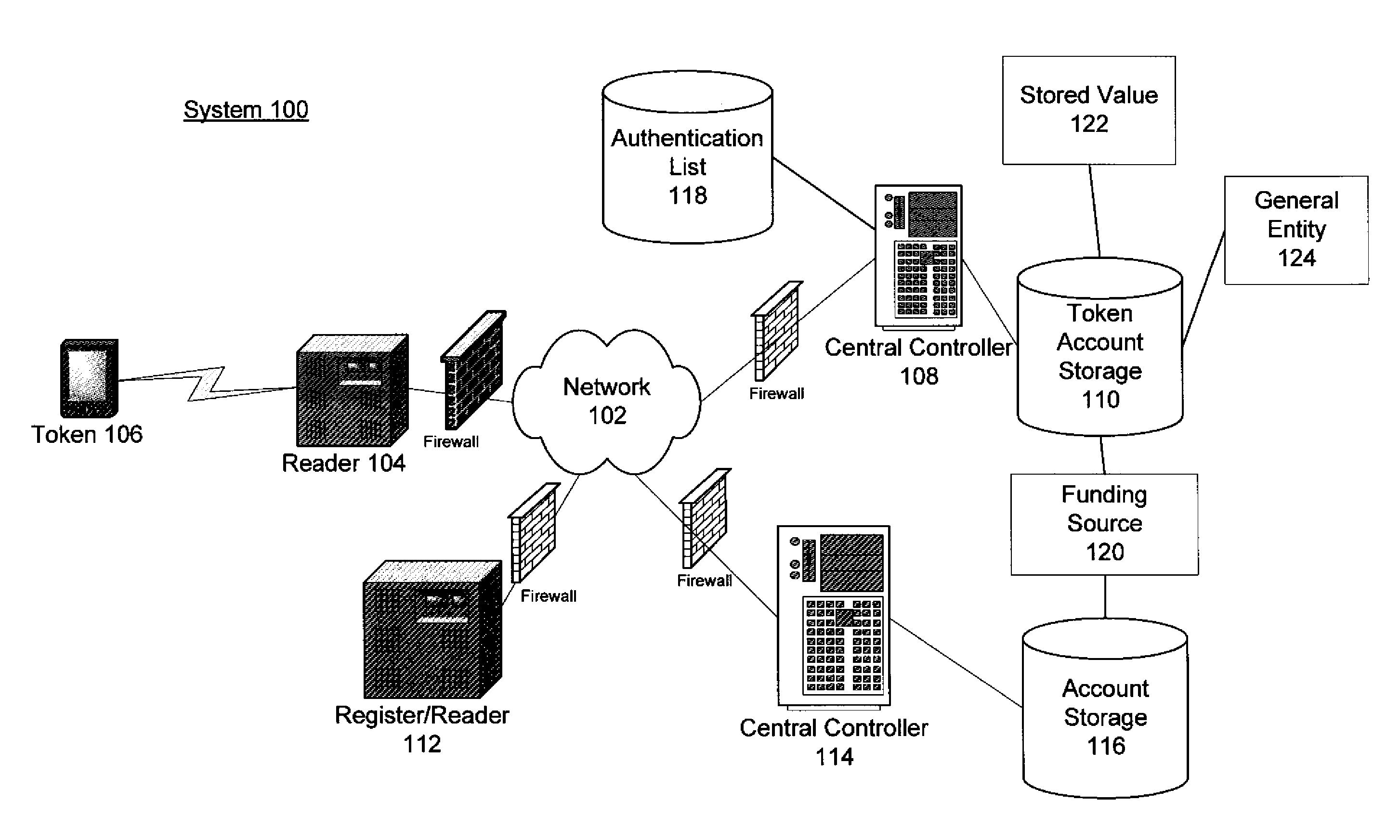
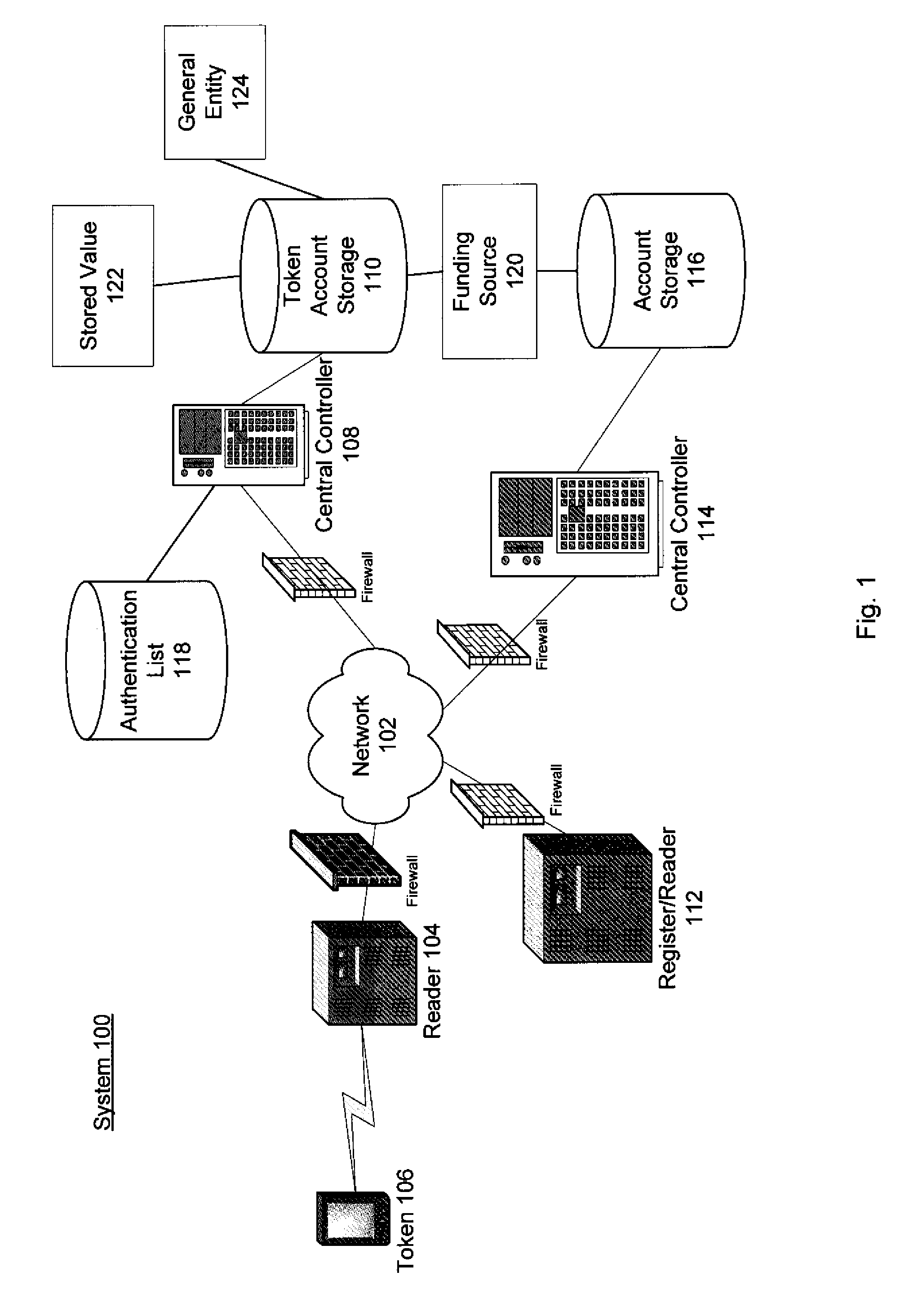
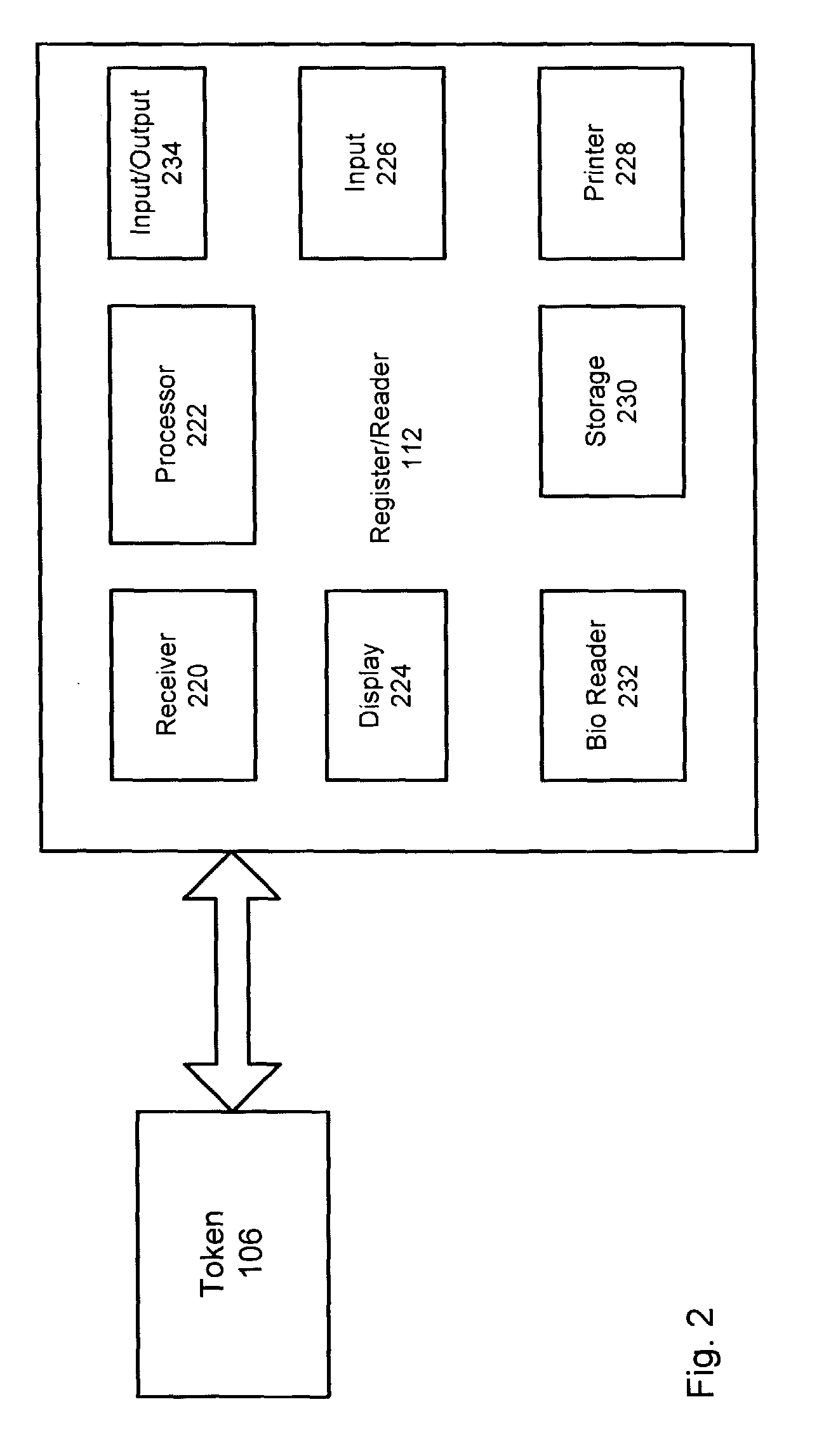
System and process for performing purchase transactions using tokens
The invention relates to a method and process by which an existing and large network of devices can be used by consumers to authenticate themselves, and permits each consumer to apply any of the various payments mechanisms available to him. The existing broadly distributed network is active and passive radio frequency identification (“RFID”) devices held by consumers. Various types of accounts are linked to devices and allow users to perform various purchase transactions, as well as non-financial transactions.
Owner:JPMORGAN CHASE BANK NA +1
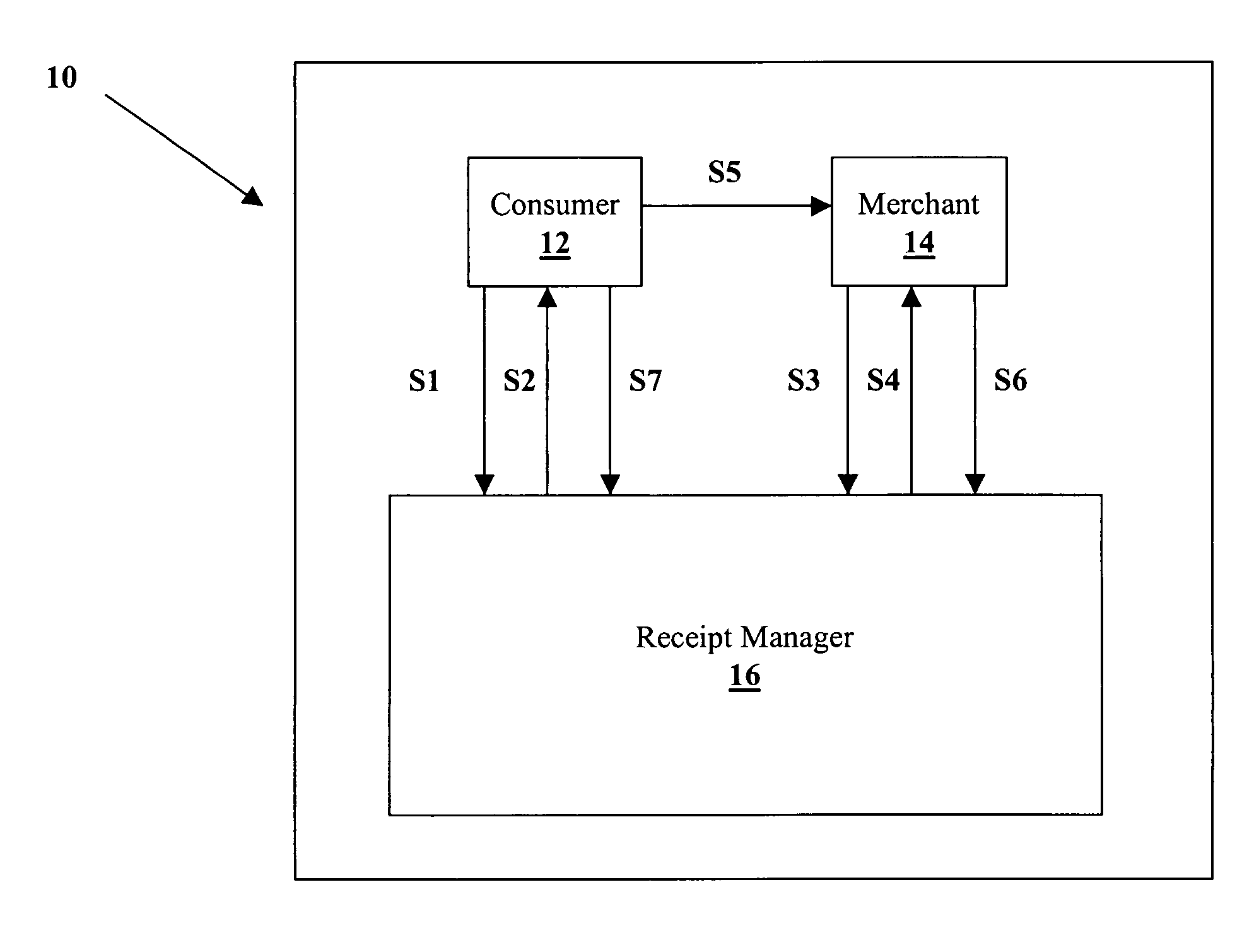
Method and system for associating consumers with purchase transactions
A system and method for associating consumers with their purchases so that consumer transactions can be tied back to a particular consumer is described. More particularly, a central transaction entity as part of a larger network collects, aggregates, manages and mines consumer transaction data from at least consumer and merchant members of the network for the purpose of routing electronic purchase history to consumers and allowing merchant analysis of consumer behavior in order to create consumer profiles to better service consumers and provide more personalized offers.
Owner:CITICORP CREDIT SERVICES INC (USA)
Automated containment of network intruder
InactiveUS20070192862A1Network degradationLow costMemory loss protectionError detection/correctionAutomatic controlVirtual LAN
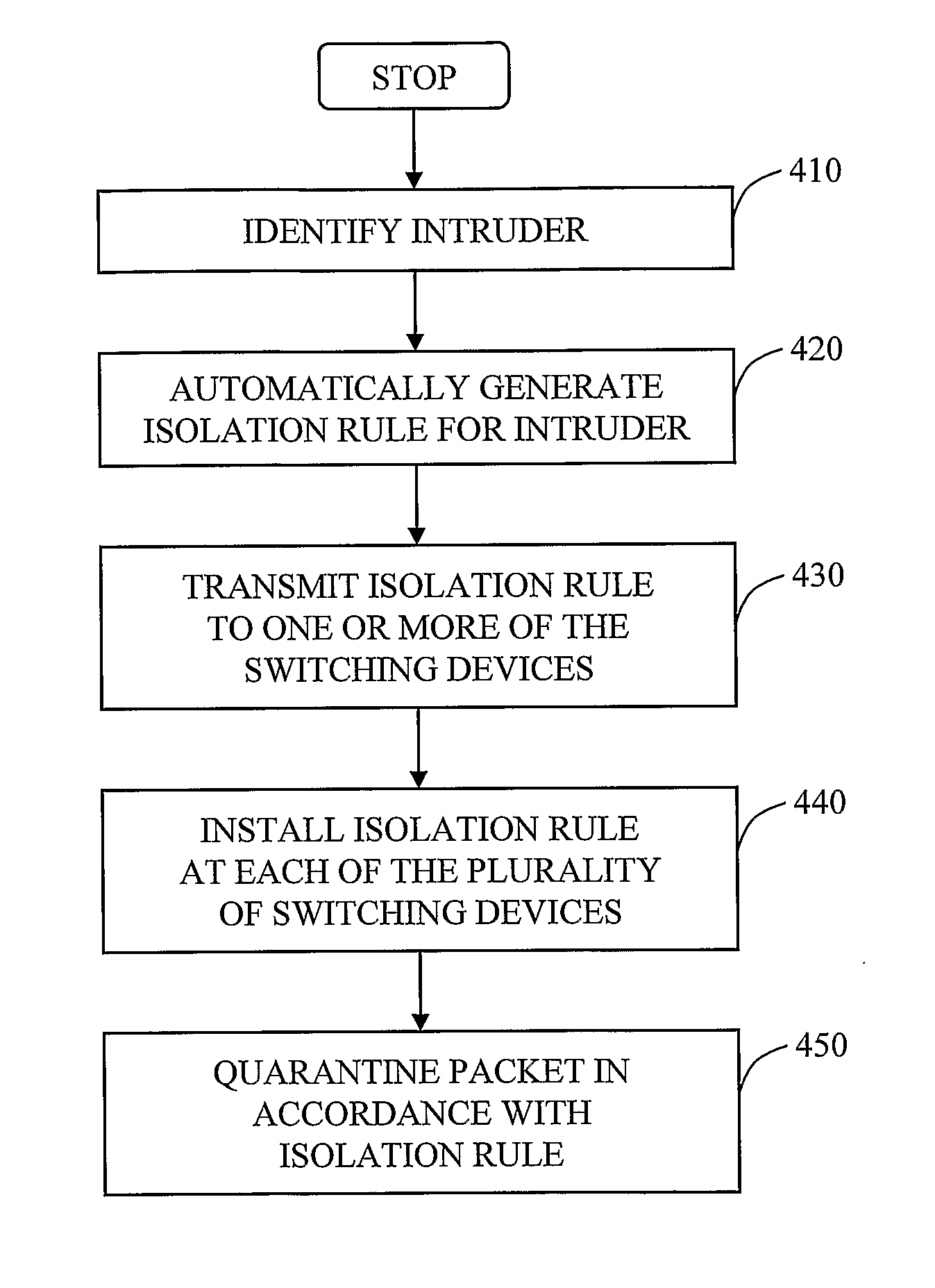
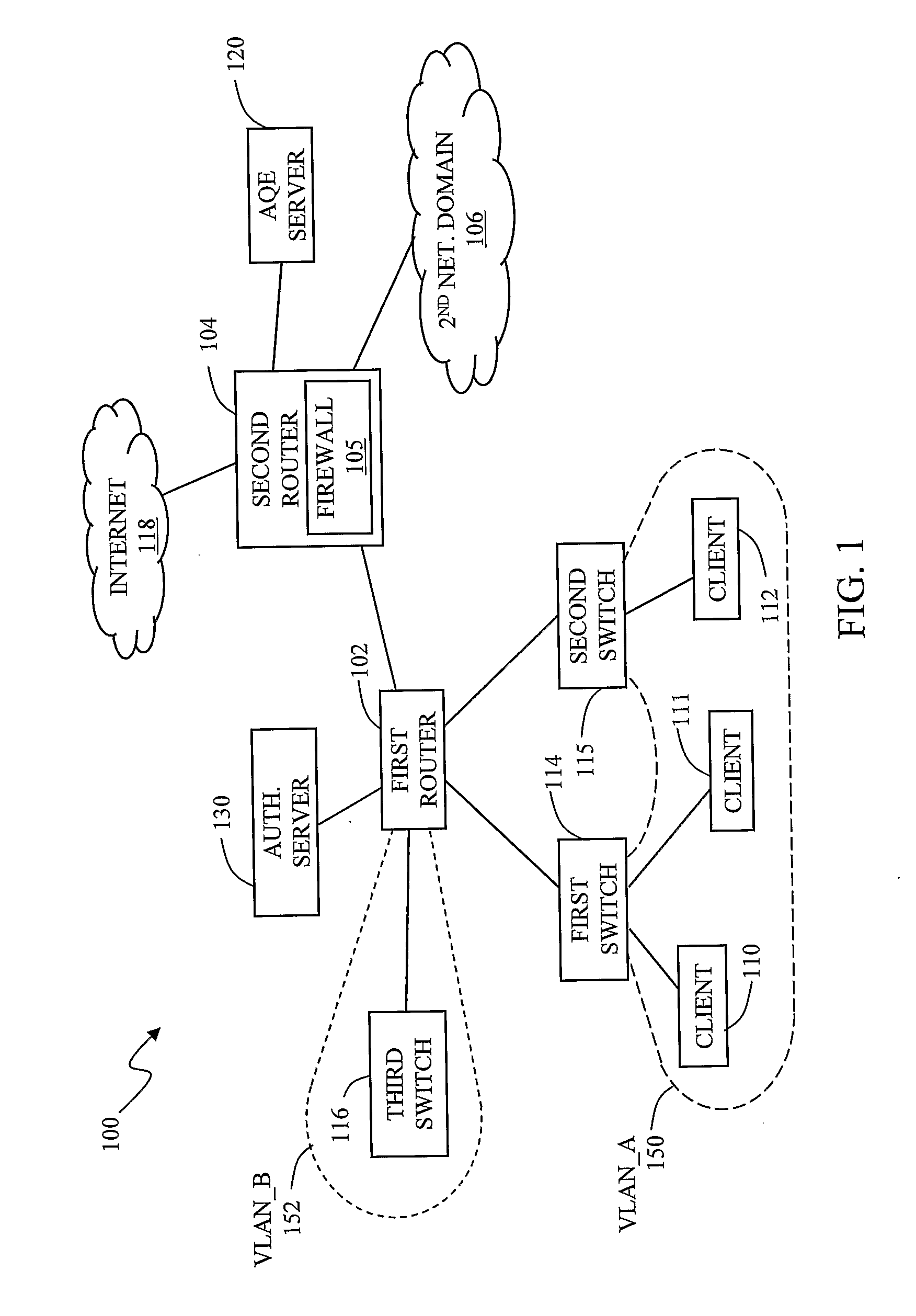
The invention in the preferred embodiment features a system (200) and method for automatically segregating harmful traffic from other traffic at a plurality of network nodes including switches and routers. In the preferred embodiment, the system (200) comprises an intrusion detection system (105) to determine the identity of an intruder and a server (130) adapted to automatically install an isolation rule on the one or more network nodes (114, 115, 116) to quarantine packets from the intruder. The isolation rule in the preferred embodiment is a virtual local area network (VLAN) rule or access control list (ACL) rule that causes the network node to route any packets from the intruder into a quarantine VLAN or otherwise isolate the traffic from other network traffic. In large networks, the isolation rule may be installed on a select plurality of network nodes under the gateway router (104) associated with the node at which the intruder first entered the network (100).
Owner:VERMEULEN VINCENT +1
Autonomous Infrastructure Wireless Networks
InactiveUS20080298275A1Large network capacityLow costNetwork topologiesData switching by path configurationWireless mesh networkData transmission
A method for deploying a cellular wireless communication network is provided. The method consists of: providing one or more micro base stations; autonomously deploying the micro base stations using a network access point linked to a cellular wireless communication network; and enabling configuration of the micro base stations to execute network operation commands from a network controller associated with the wireless communication network. Another aspect consists of enabling cooperation and network connectivity between micro base stations and other base stations, including micro base stations and large network base stations. Network connectivity to one or more cellular communication terminals associated with individuals or businesses subscribing to the cellular wireless communication network is enabled. A wireless network is also provided which is configurable to link a cellular wireless network through a high data transmission connection so as to define at least one access point between the micro base station and the wireless network. The network includes a wireless interface and receives operation commands from a network controller for configuration of micro base stations, to support the linking of cellular wireless terminals to the wireless network via the wireless interface by operation of the micro base station, as an intermediary. A corresponding system and computer readable medium is also provided
Owner:DE SOUSA ELVINO SILVEIRA MEDINA
Apparatus and methods for synaptic update in a pulse-coded network
InactiveUS20130073491A1Reducing memory bus overheadReduce overheadDigital computer detailsDigital dataSynapseSpiking neural network
Apparatus and methods for efficient synaptic update in a network such as a spiking neural network. In one embodiment, the post-synaptic updates, in response to generation of a post-synaptic pulse by a post-synaptic unit, are delayed until a subsequent pre-synaptic pulse is received by the unit. Pre-synaptic updates are performed first following by the post-synaptic update, thus ensuring synaptic connection status is up-to-date. The delay update mechanism is used in conjunction with system “flush” events in order to ensure accurate network operation, and prevent loss of information under a variety of pre-synaptic and post-synaptic unit firing rates. A large network partition mechanism is used in one variant with network processing apparatus in order to enable processing of network signals in a limited functionality embedded hardware environment.
Owner:QUALCOMM INC
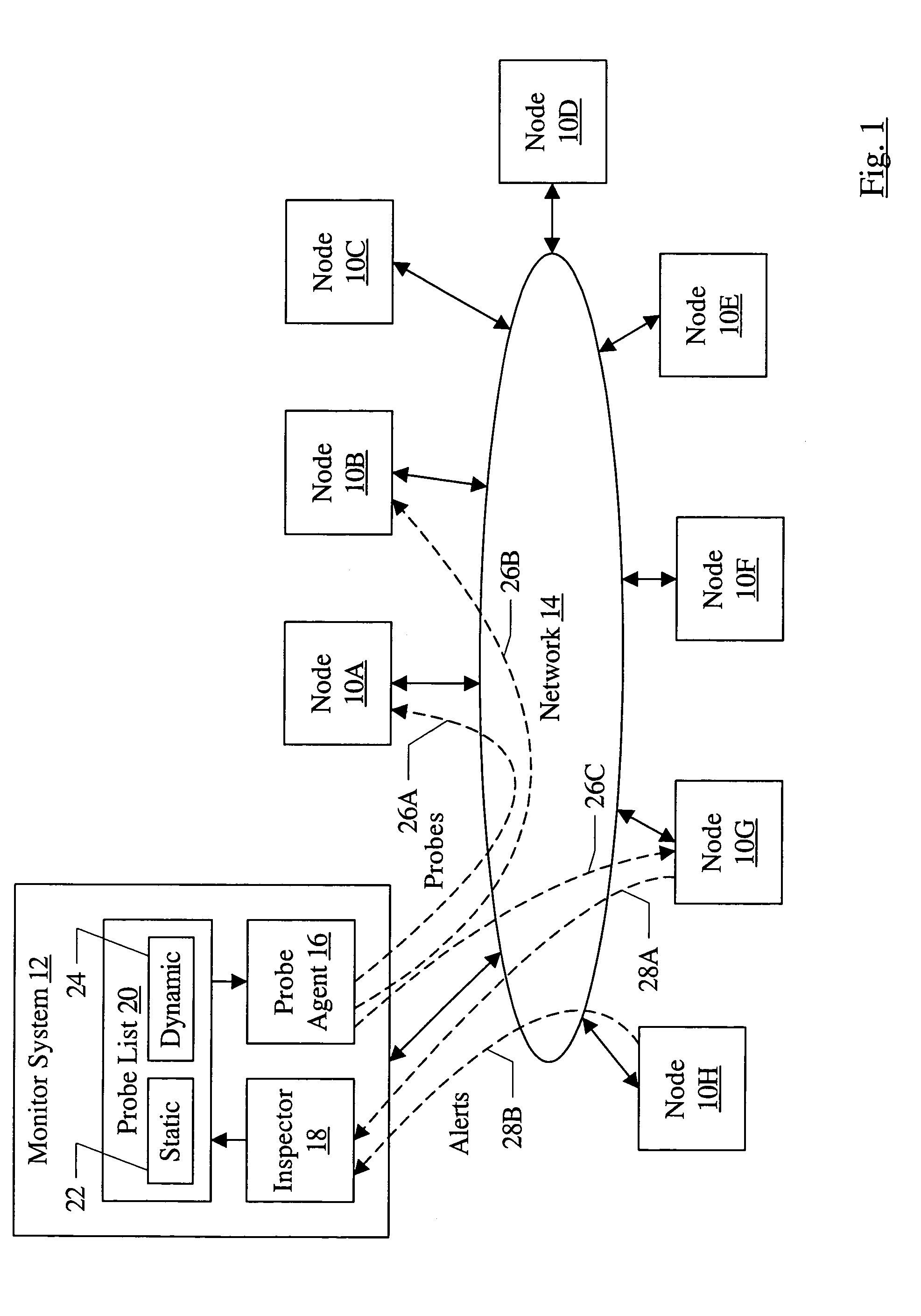
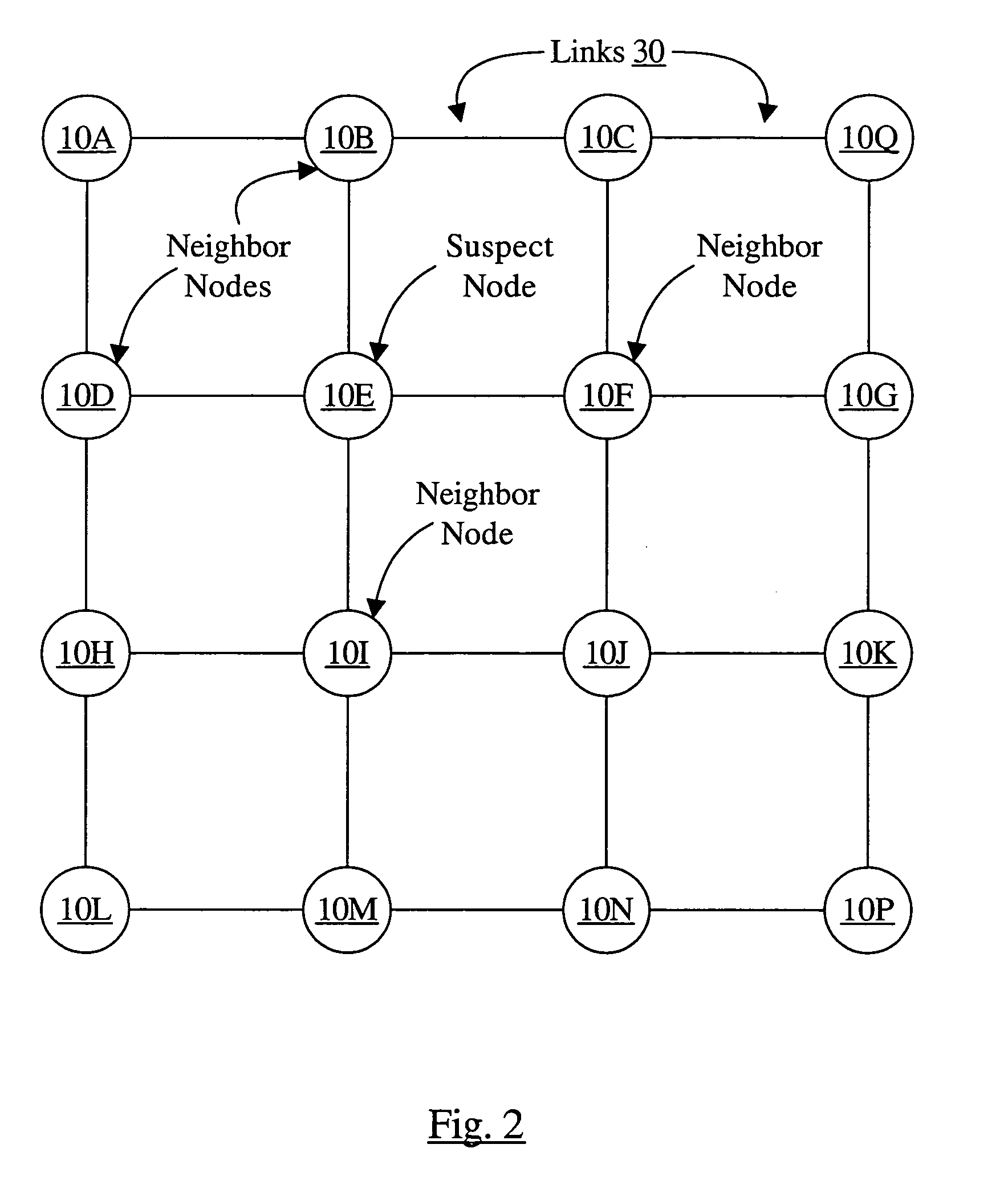
Fault isolation in large networks
Owner:ORACLE INT CORP
System and method for increasing the effective bandwidth of a communications network
InactiveUS7260651B2Increase effective bandwidthIncrease transfer rateDigital data information retrievalCode conversionTelecommunications linkThe Internet
A system and method for increasing the effective bandwidth of a communications network is provided by overlaying a “super” transport and caching structure over the conventional TCP / IP communications network, for example, the Internet, which increases the transfer rate of information in the communications network. The “super” transport and caching structure includes software or hardware or both added to at least two modules separated by a communications link in the communications network. The net result is that the users of the communications network have their time to access and / or retrieve information significantly reduced, and the communications network, particularly a large network, e.g., the Internet, becomes an efficient means of performing commercial transactions by both businesses and individuals.
Owner:ARTERA GRP INC
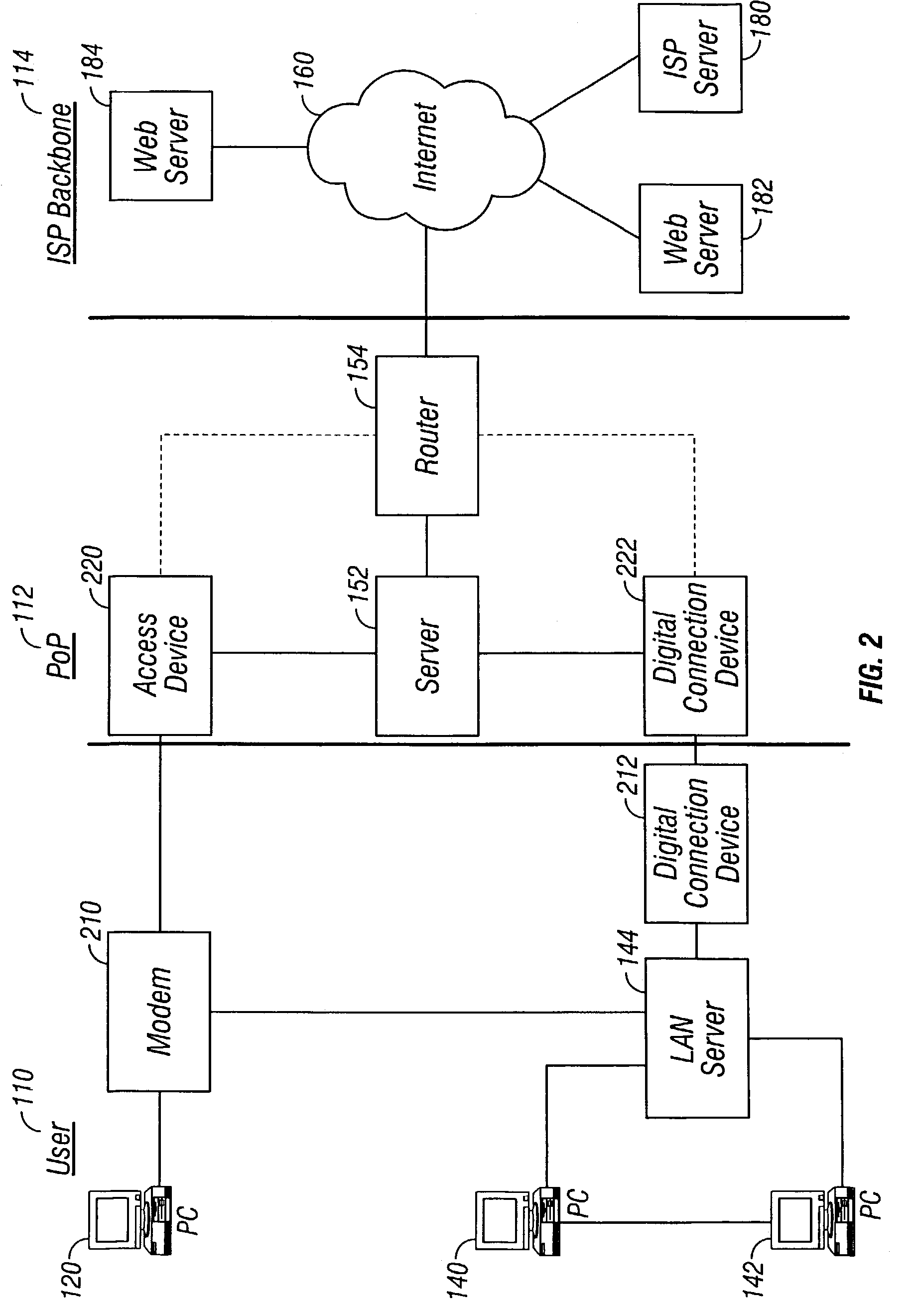
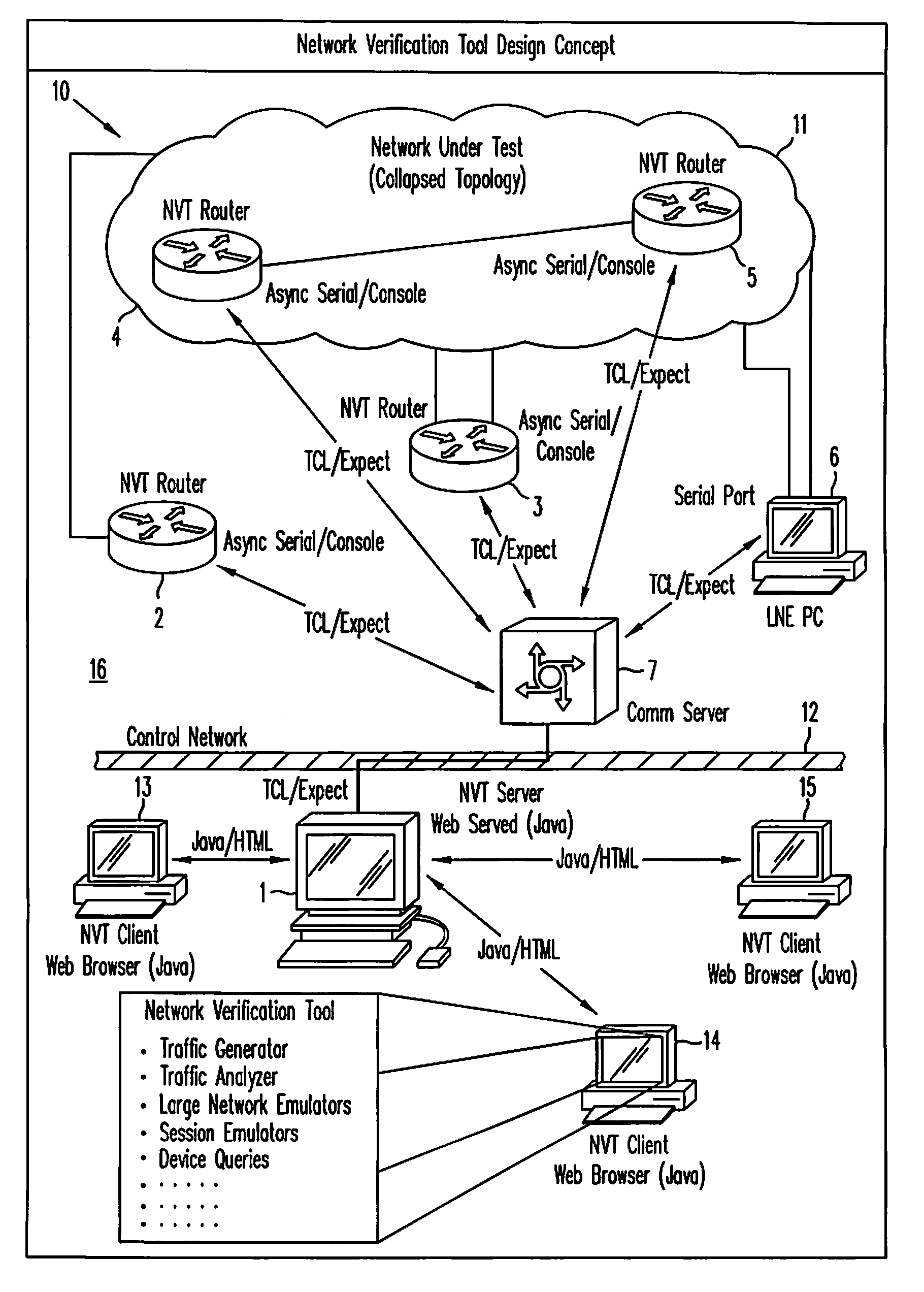
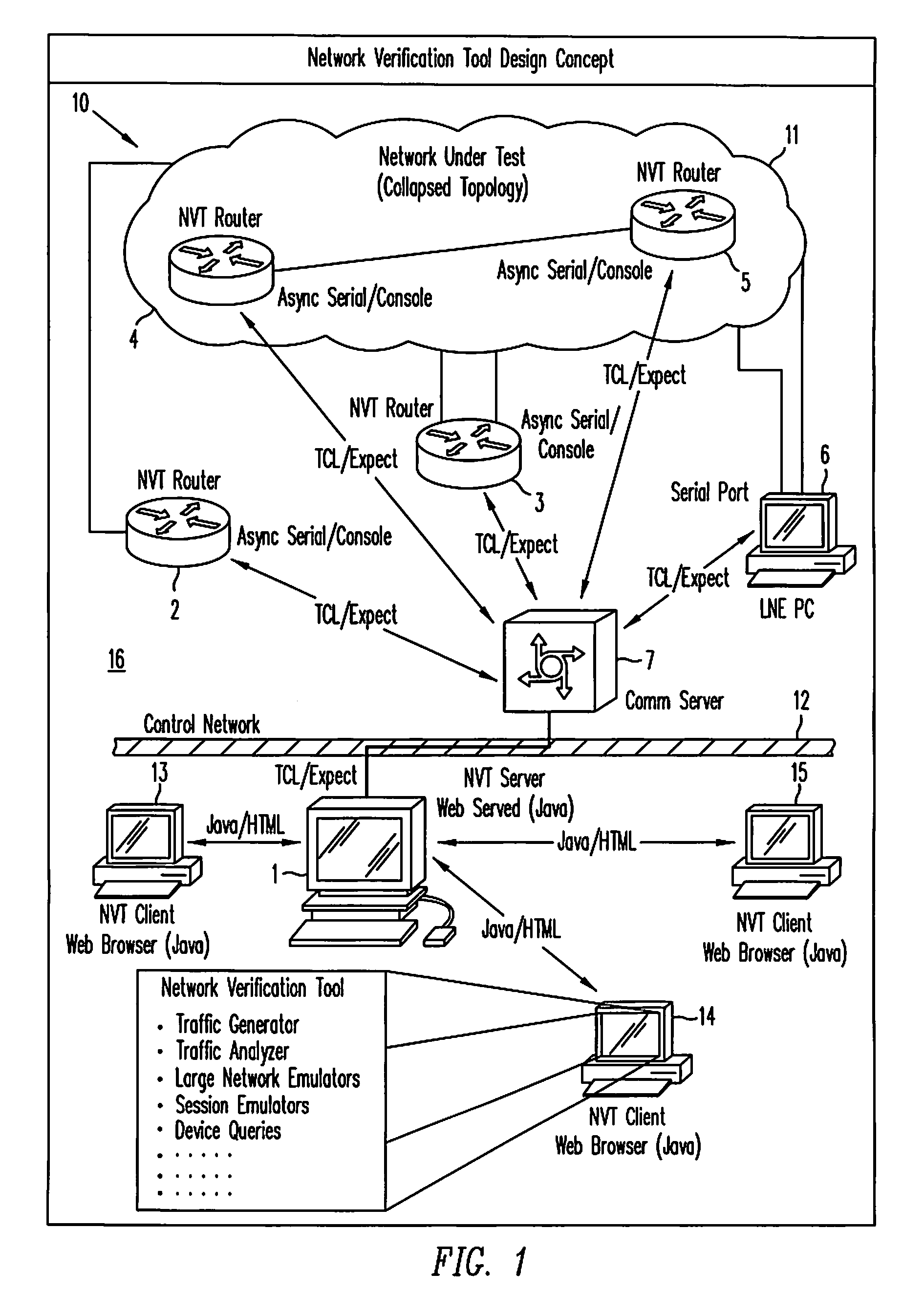
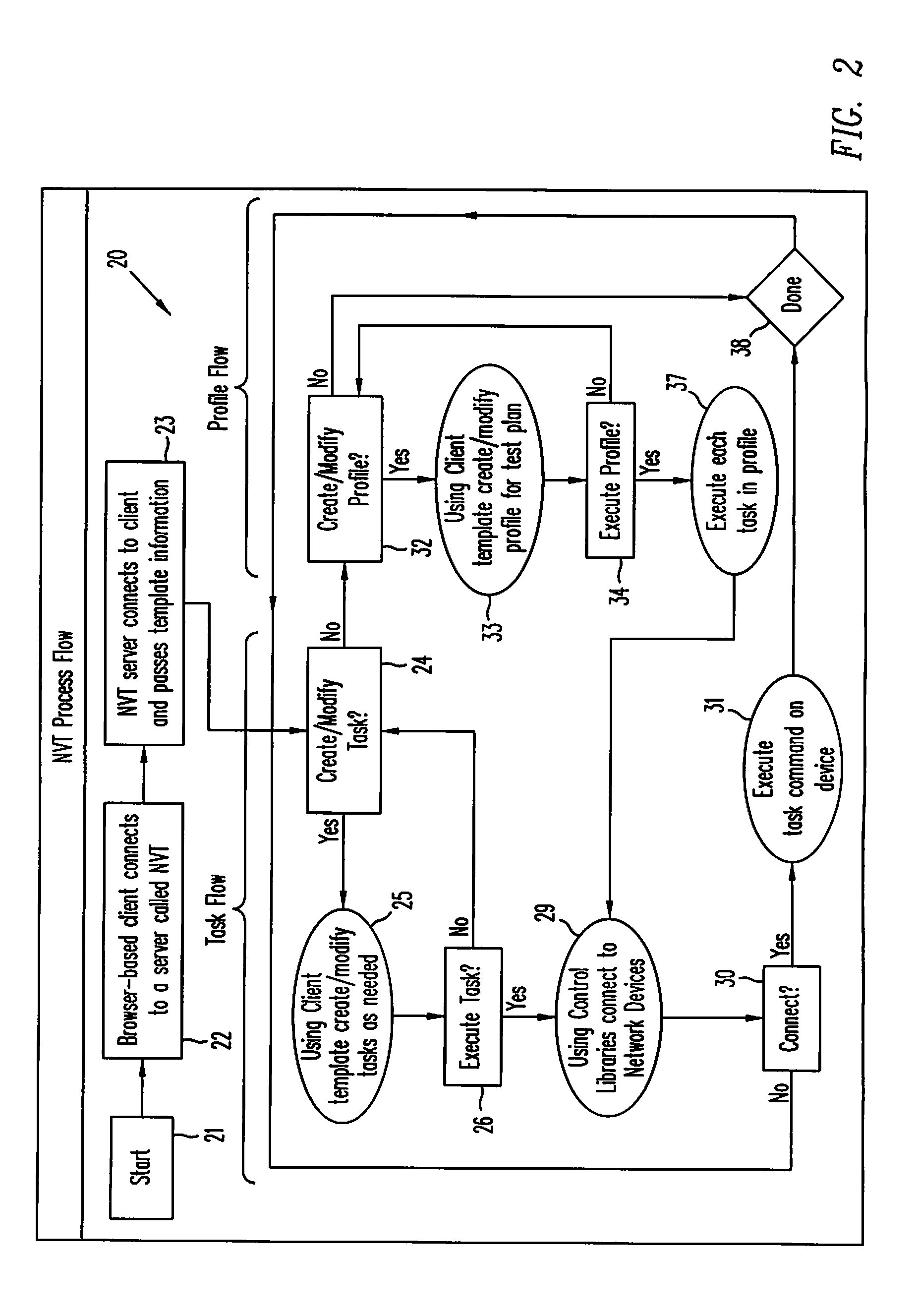
Network verification tool
InactiveUS7342897B1Easily set parameter requiredFacilitate joint resolutionError preventionFrequency-division multiplex detailsTraffic capacityClient-side
A network verification tool is presented that allows a user to easily create tasks for a collection of task types. The collection of task types are hosted by probe network devices that are coupled to a network under test. The network under test includes network devices executing generic network software and particular hardware or software that is being tested. The probe network devices are coupled to an NVT server, which transmits tasks to the task types and interfaces with one or more NVT clients. The NVT clients can create tasks by entering the appropriate parameters within templates supplied by the NVT server. Any collection of task types can be included in the network verification tool, including traffic generators, traffic analyzers, large network emulators, session emulators, device queries and script tasks.
Owner:CISCO SYSTEMS INC
Global network computers
InactiveUS20060177226A1High potential economic savingOptimize networkMultiple digital computer combinationsProgram controlBroadband transmissionThe Internet
This invention generally relates to one or more computer networks having computers like personal computers or network servers with microprocessors linked by broadband transmission means and having hardware, software, firmware, and other means such that at least one parallel processing operation occurs that involve at least two computers in the network. More particularly, this invention relates to one or more large networks composed of smaller networks and large numbers of computers connected, like the Internet, wherein more than one separate parallel processing operation involving more than one different set of computers occurs simultaneously and wherein ongoing processing linkages can be established between virtually any microprocessors of separate computers connected to the network. Still more particularly, this invention relates to business arrangements enabling the shared used of network microprocessors for parallel and other processing, wherein personal computer owners provide microprocessor processing power to a network, preferably for parallel processing, in exchange for network linkage to other personal and other computers supplied by network providers, including linkage to other microprocessors for parallel or other processing; the basis of the exchange between owners and providers being whatever terms to which the parties agree, subject to governing laws, regulations, or rules, including payment from either party to the other based on periodic measurement of net use or provision of processing power.
Owner:ELLIS III FRAMPTON E
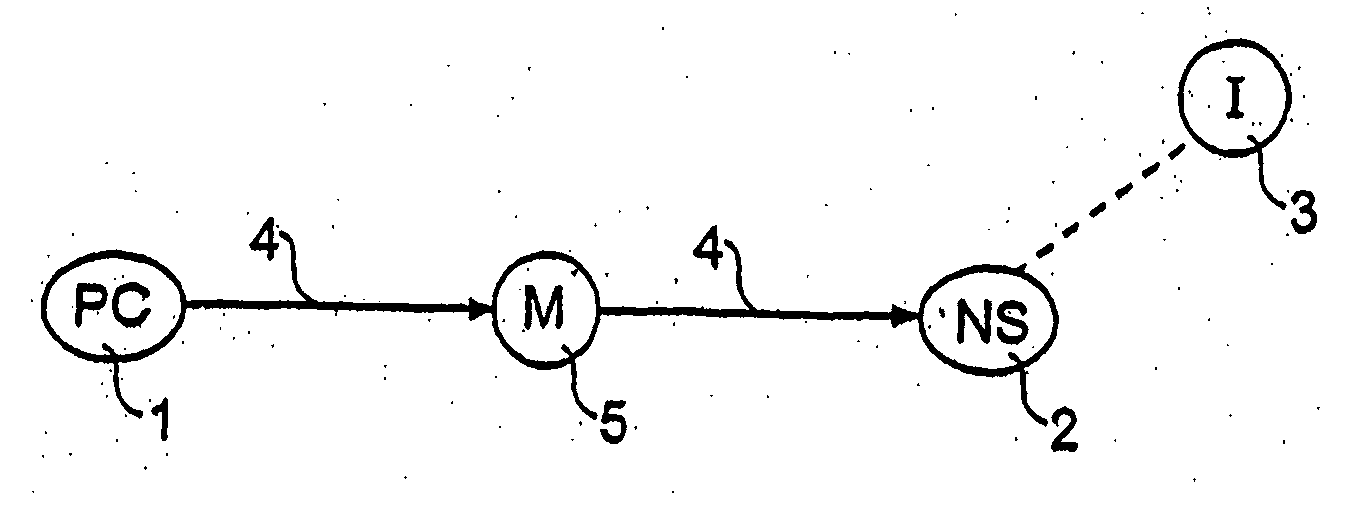
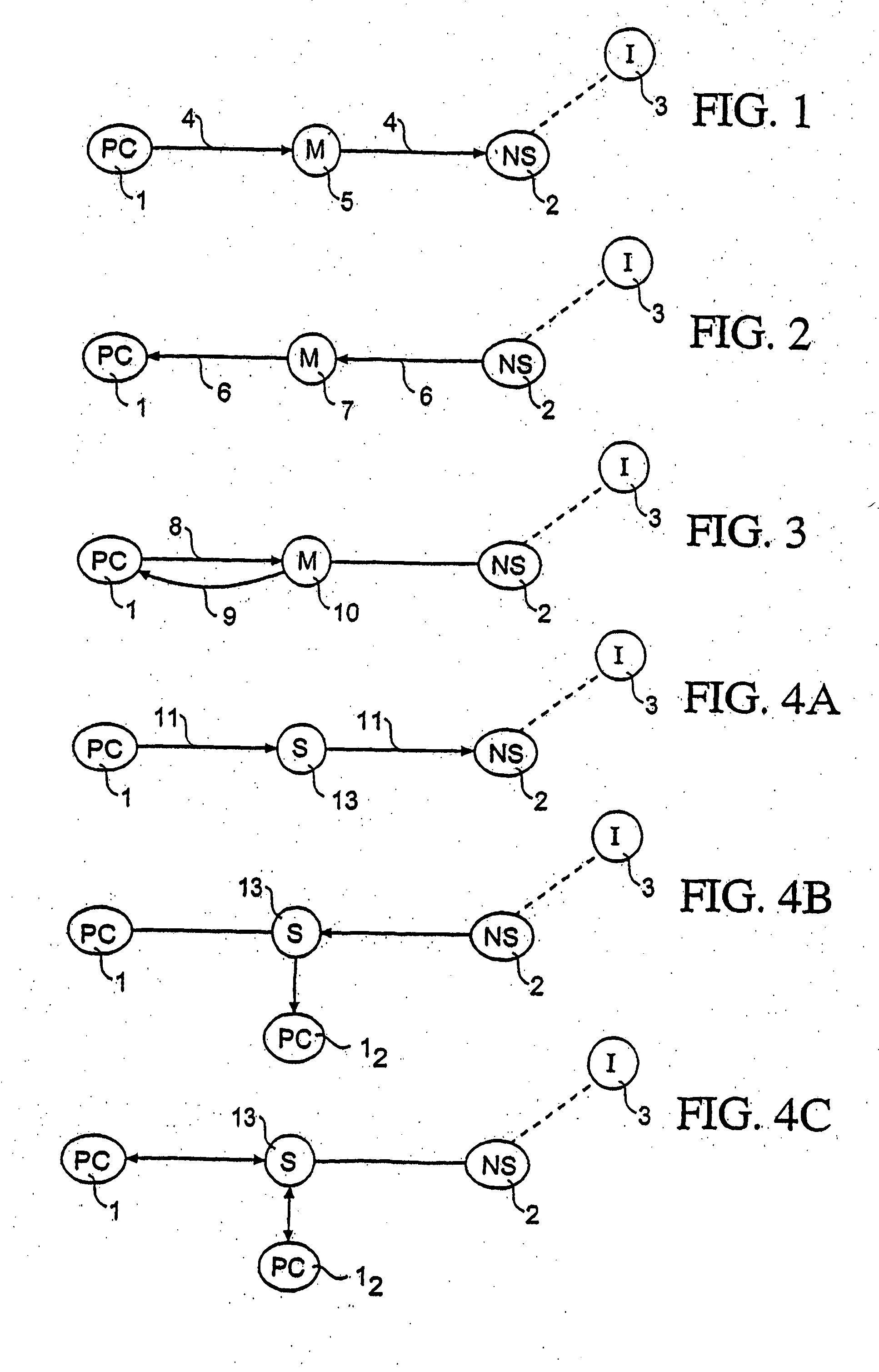
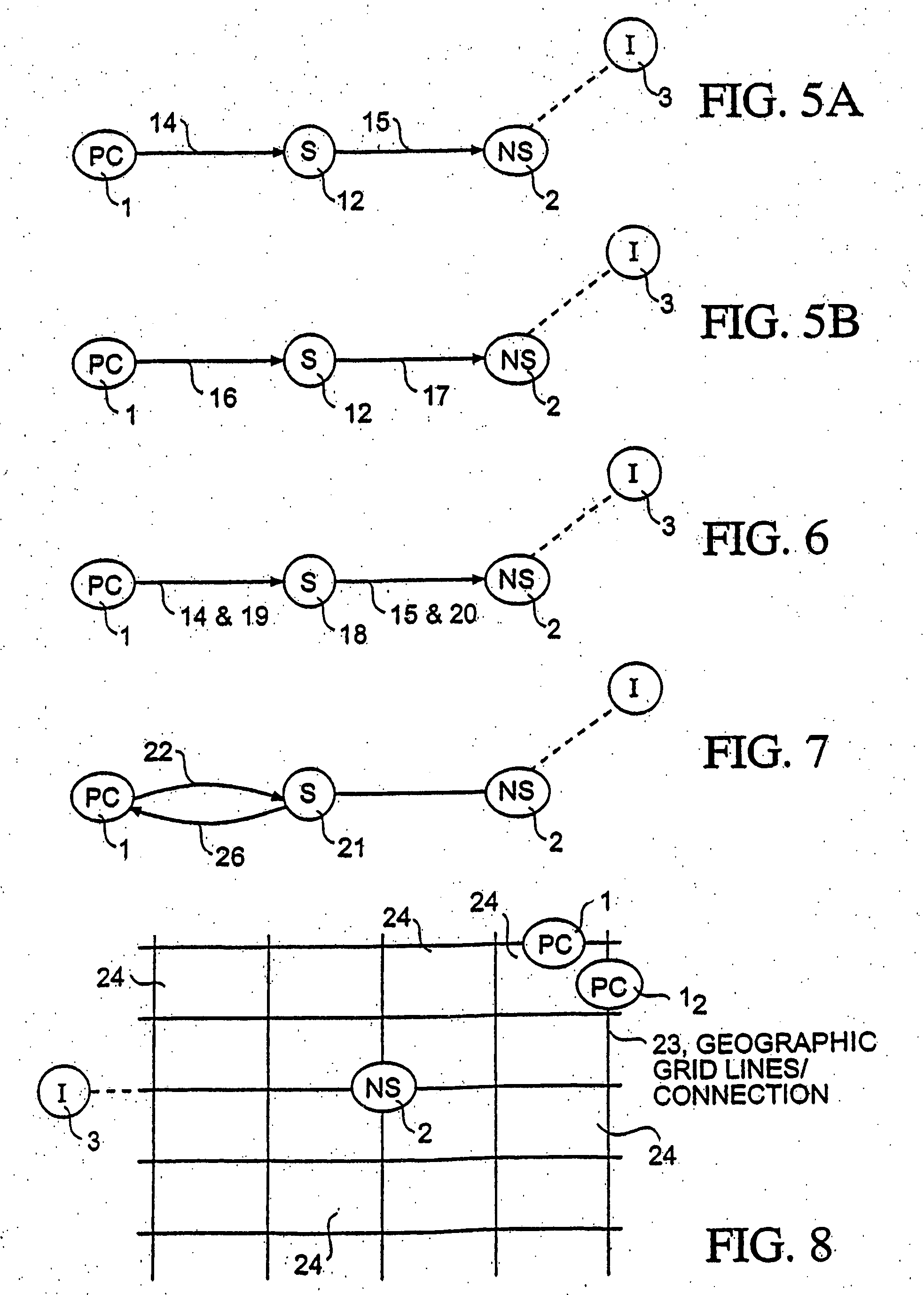
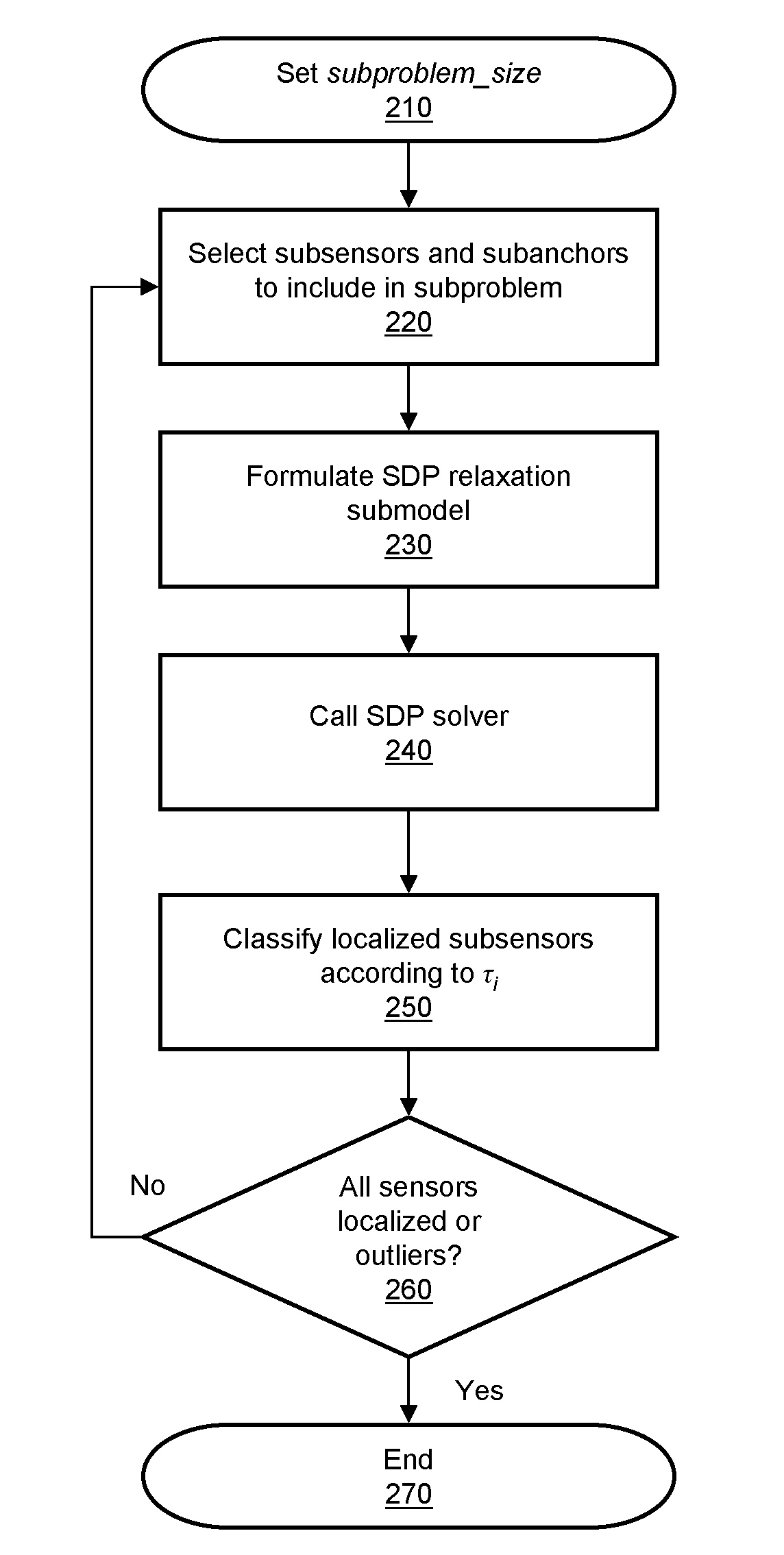
Scalable sensor localization for wireless sensor networks
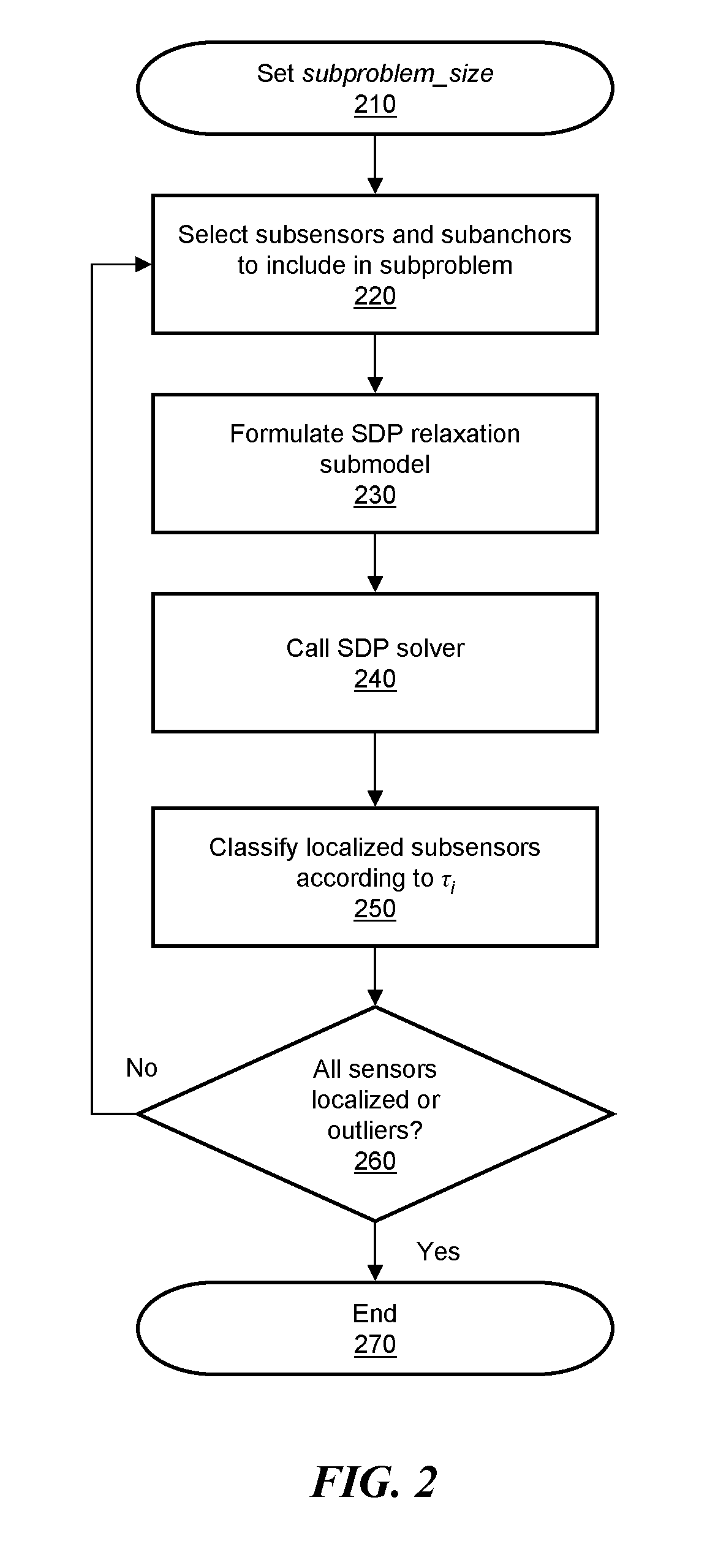
ActiveUS20070005292A1Error minimizationSolve small or large problems more accuratelyNetwork traffic/resource managementNetwork topologiesWireless sensor networkingComputer science
Adaptive rule-based methods to solve localization problems for ad hoc wireless sensor networks are disclosed. A large problem may be solved as a sequence of very small subproblems, each of which is solved by semidefinite programming relaxation of a geometric optimization model. The subproblems may be generated according to a set of sensor / anchor selection rules and a priority list. The methods scale well and provide improved positioning accuracy. A dynamic version may be used for estimating moving sensors locations in a real-time environment. The method may use dynamic distance measurement updates among sensors, and utilizes subproblem solving for static sensor localization. Methods to deploy sensor localization algorithms in clustered distributed environments are also provided, permitting application to arbitrarily large networks. In addition, the methods may be used to solve sensor localizations in 2D or 3D space. A preprocessor may be used for localization of networks without absolute position information.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Trainable hierarchical memory system and method
Memory networks and methods are provided. Machine intelligence is achieved by a plurality of linked processor units in which child modules receive input data. The input data are processed to identify patterns and / or sequences. Data regarding the observed patterns and / or sequences are passed to a parent module which may receive as inputs data from one or more child modules. the parent module examines its input data for patterns and / or sequences and then provides feedback to the child module or modules regarding the parent-level patterns that correlate with the child-level patterns. These systems and methods are extensible to large networks of interconnected processor modules.
Owner:NUMENTA INC
Extended file system
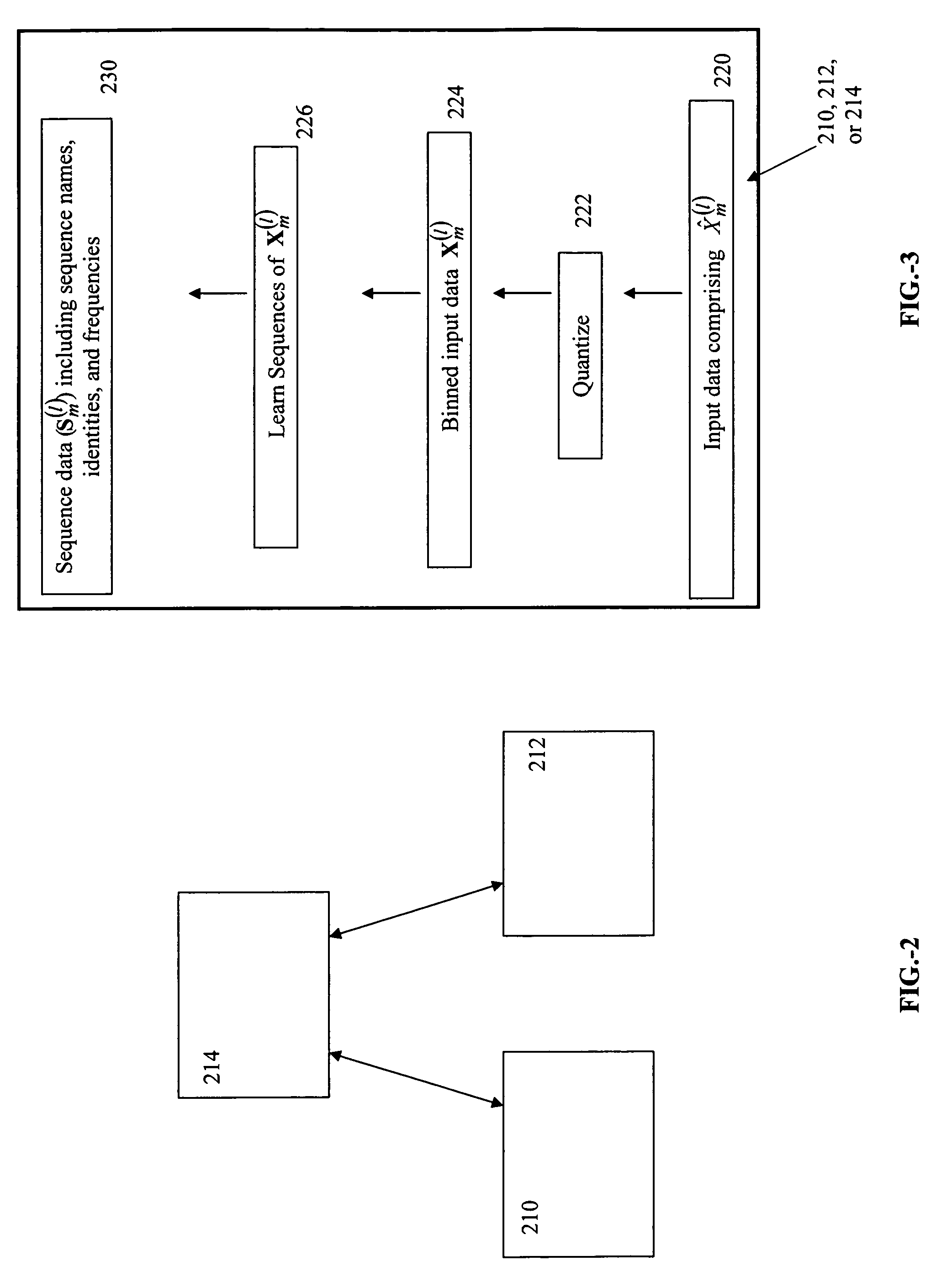
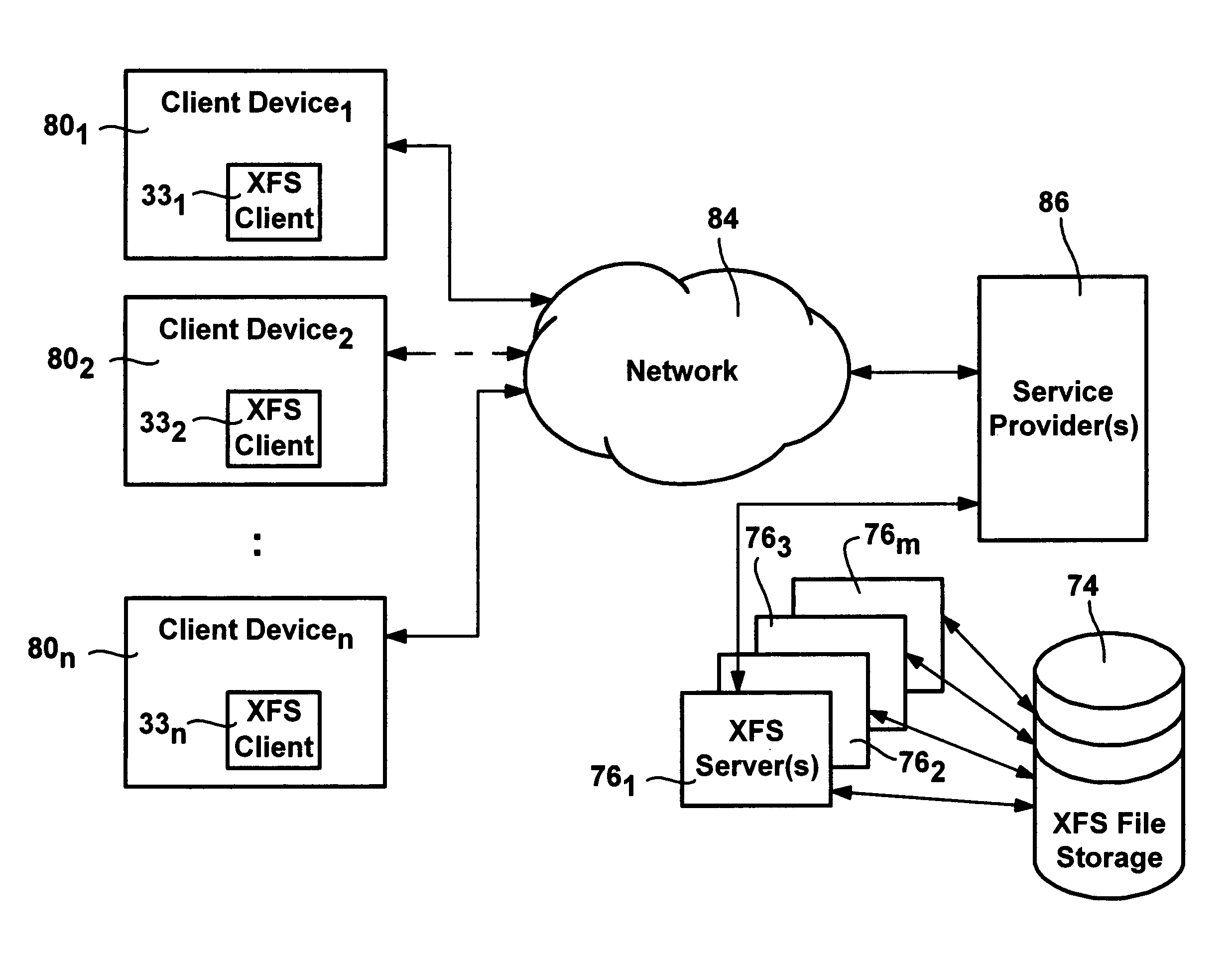
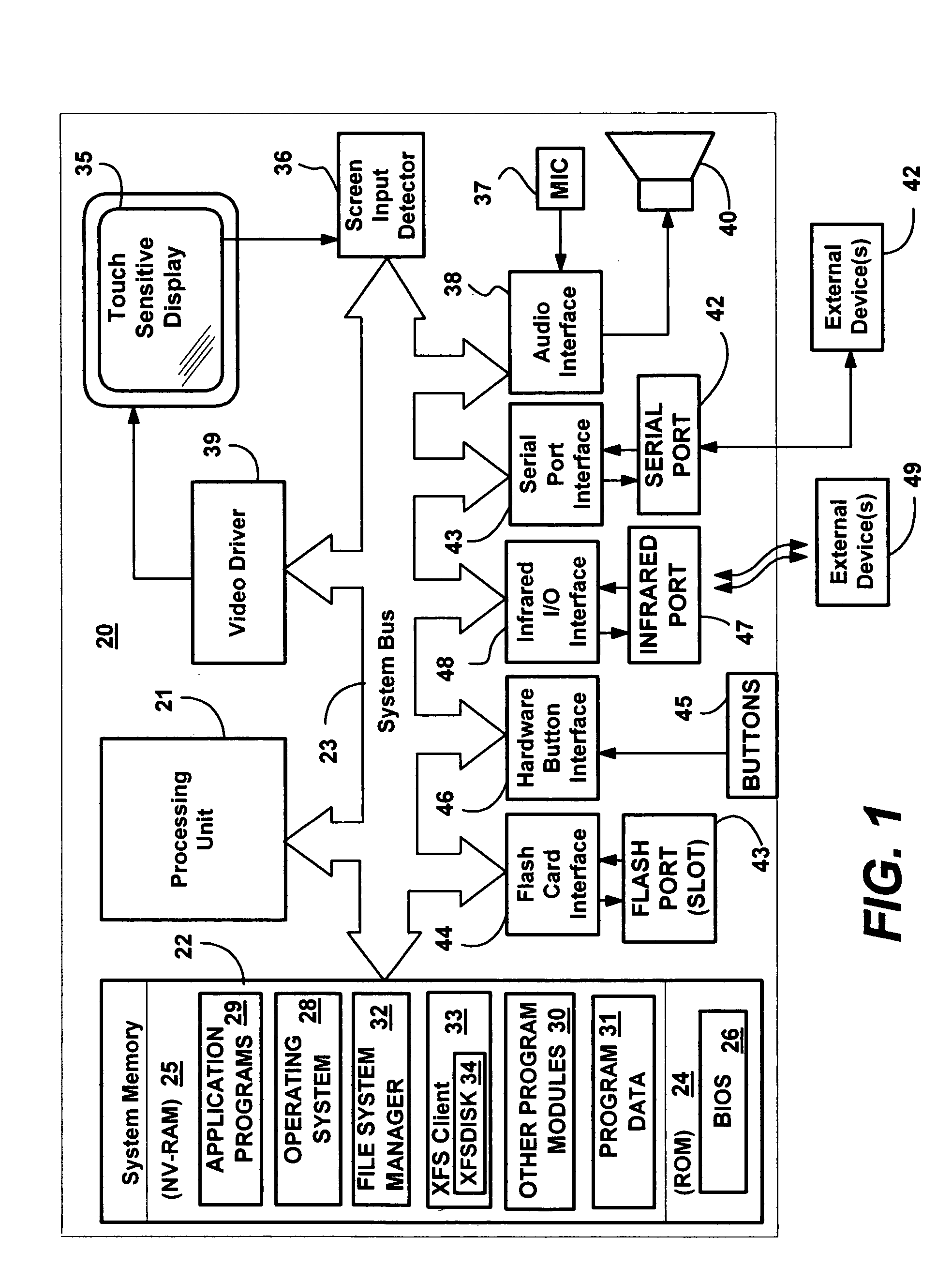
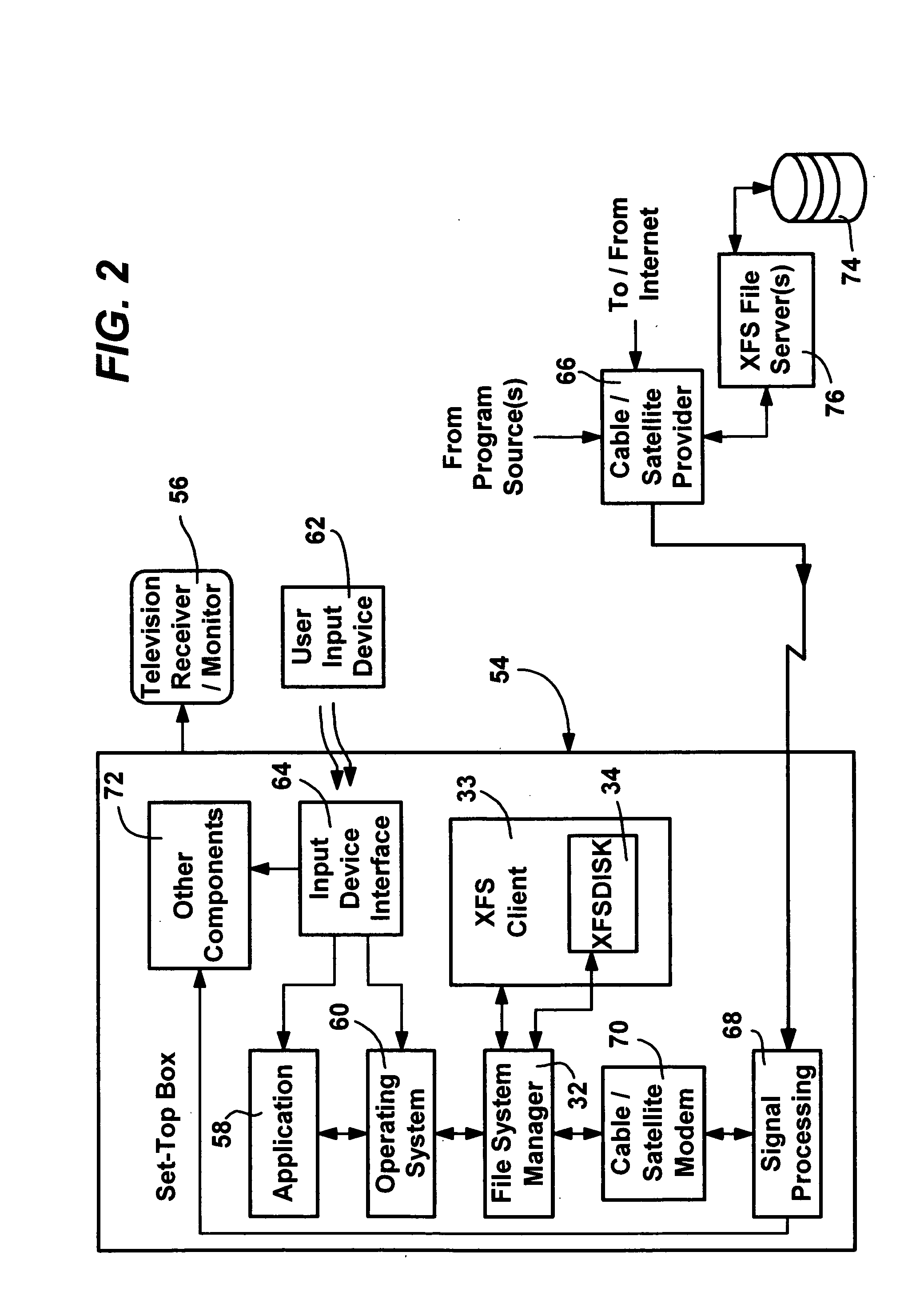
InactiveUS20050060316A1Fast communicationData processing applicationsNatural language data processingFile systemPersonal computer
A method and system for transparently combining remote and local storage to provide an extended file system such as a virtual local drive for a computer system client / user, e.g., a user of a pocket sized personal computer or a cable set-top box. A client device may load file system object data, storing the directories and files remotely, and retrieving the files only when required. Via its local storage, the extended file system handles unreliable connections and delays. When a connection to an extended file system server is present, the extended file system provides automatic downloading of information that is not locally cached, and automatically uploading of information that has been modified on the client. Extended file system attributes are employed to determine the actual location of file system data, and a lightweight protocol is defined to download or upload remote data by low-level components that make the remote source transparent from the perspective of the application. The system scales to large networks as it employs the lightweight protocol and establishes a connection only to retrieve and submit data.
Owner:MICROSOFT TECH LICENSING LLC
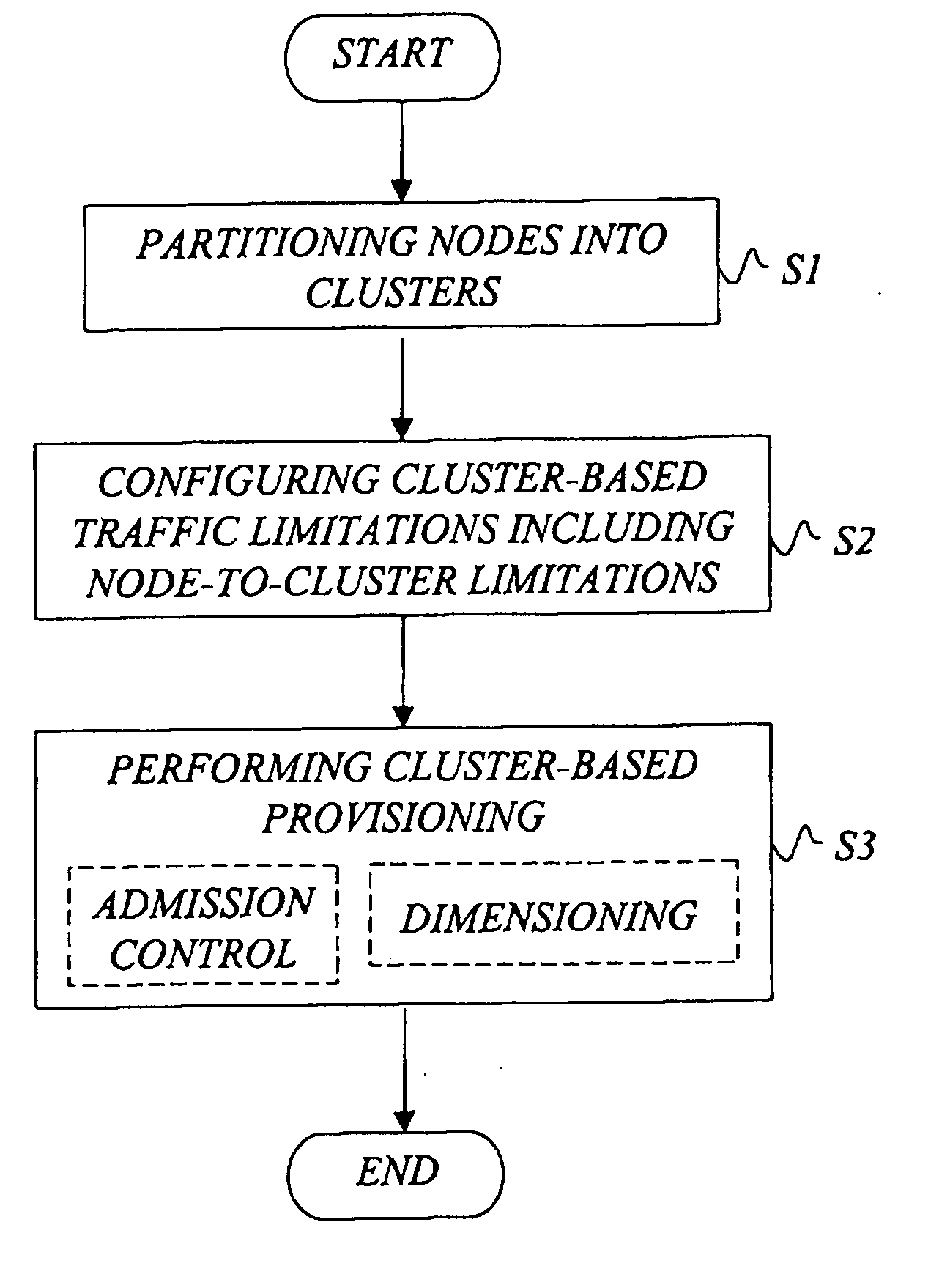
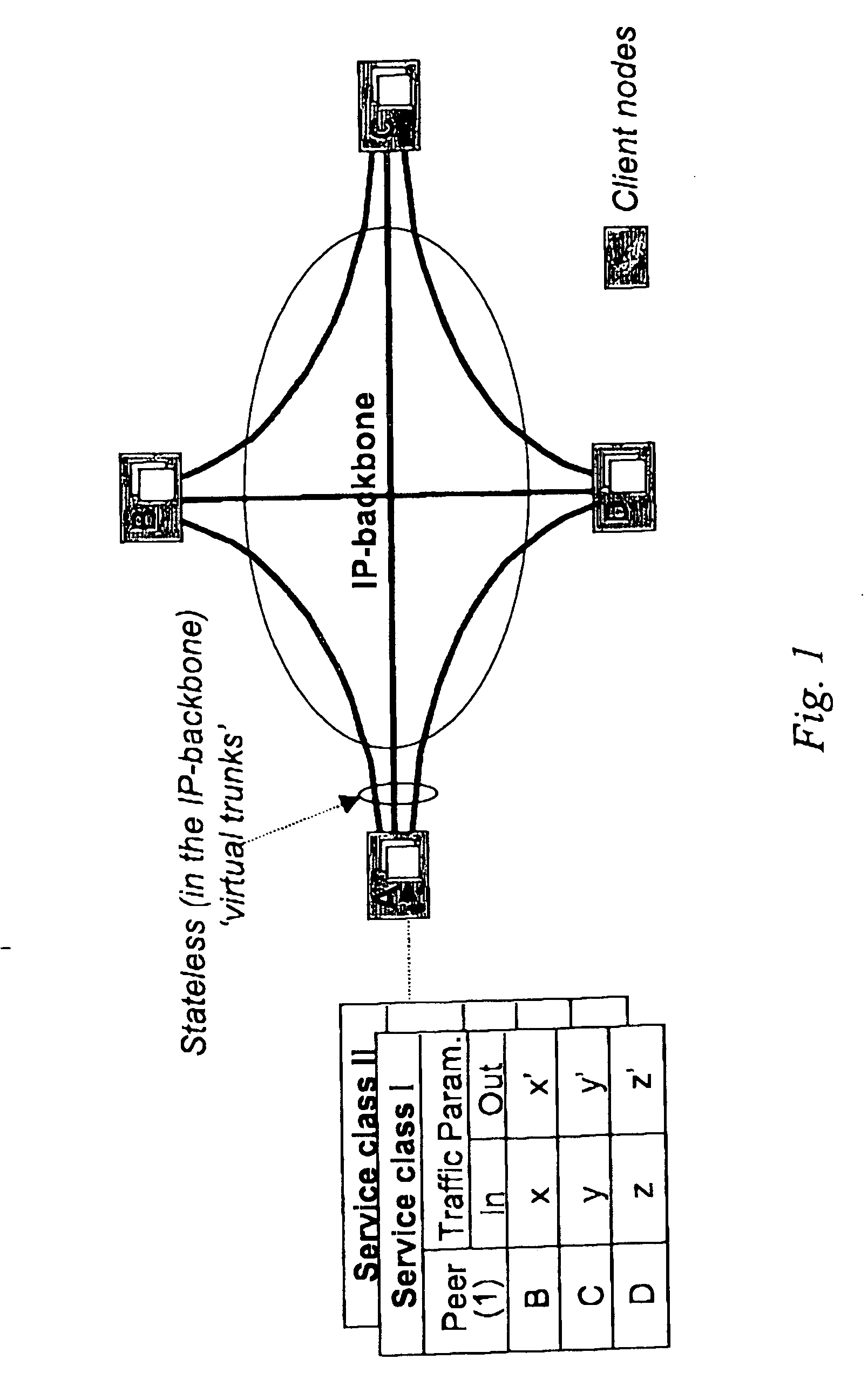
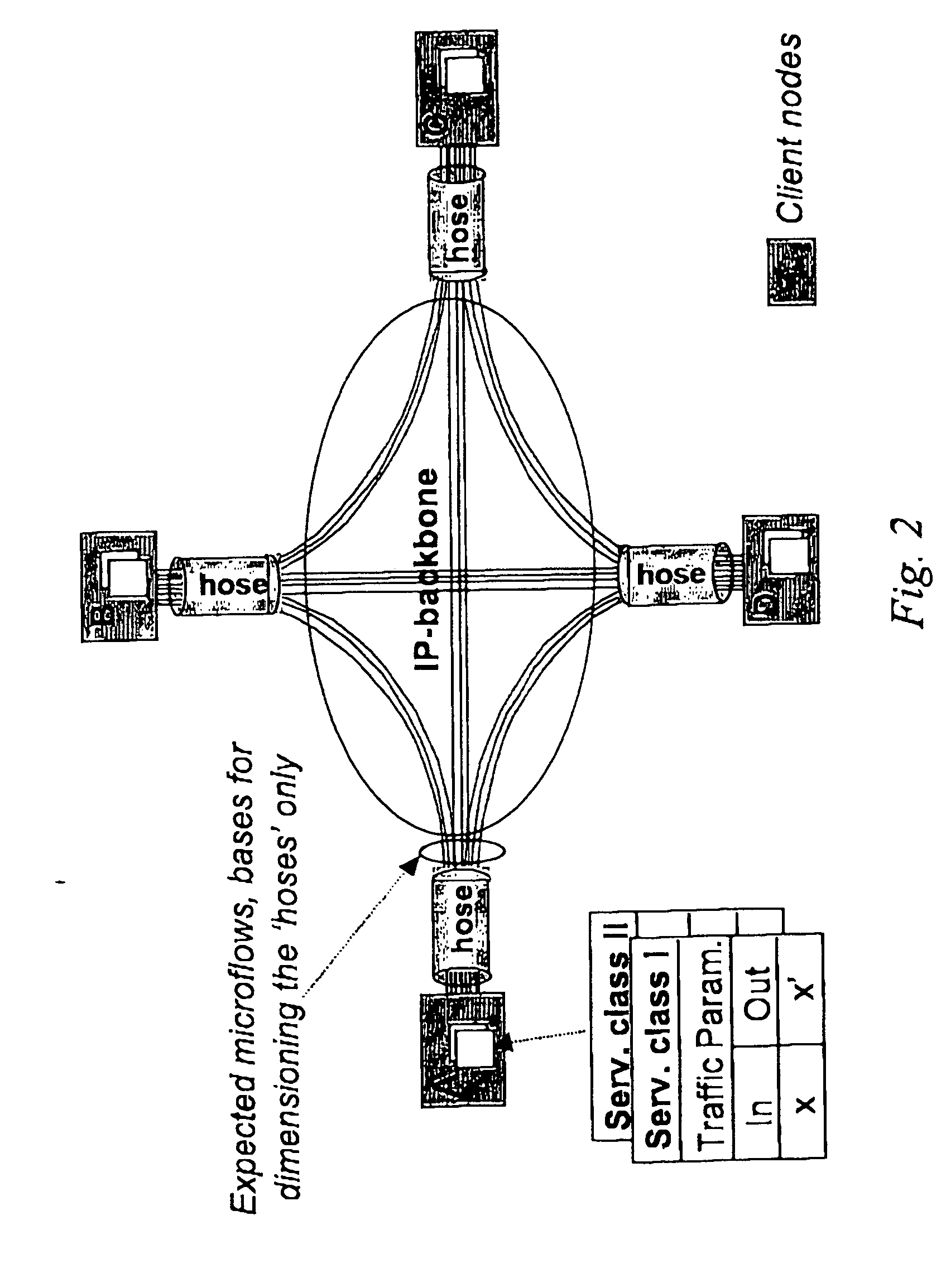
Cluster-based network provisioning
ActiveUS20050169179A1Efficient network operationImprove bandwidth efficiencyError preventionTransmission systemsNode clusteringTrade offs
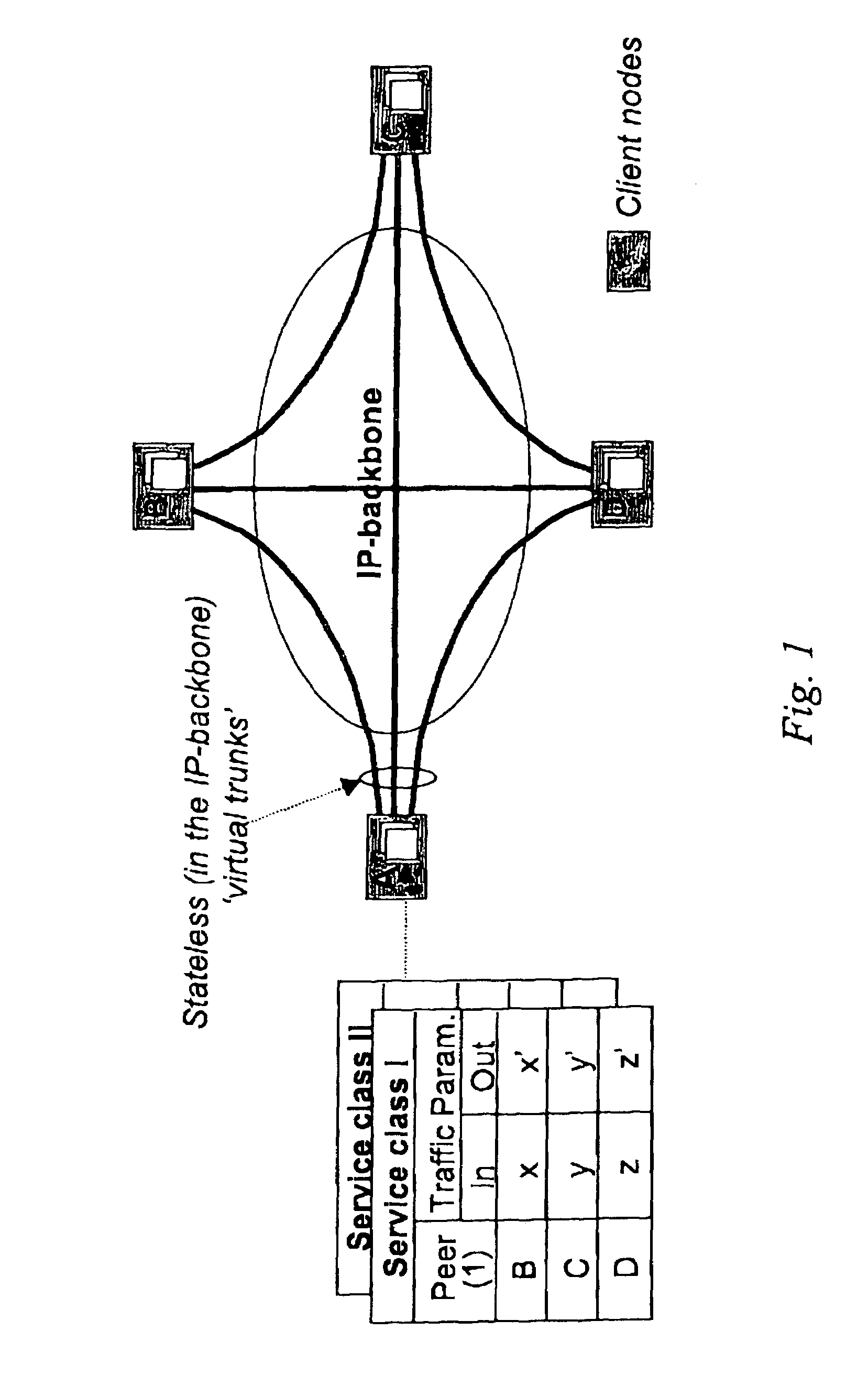
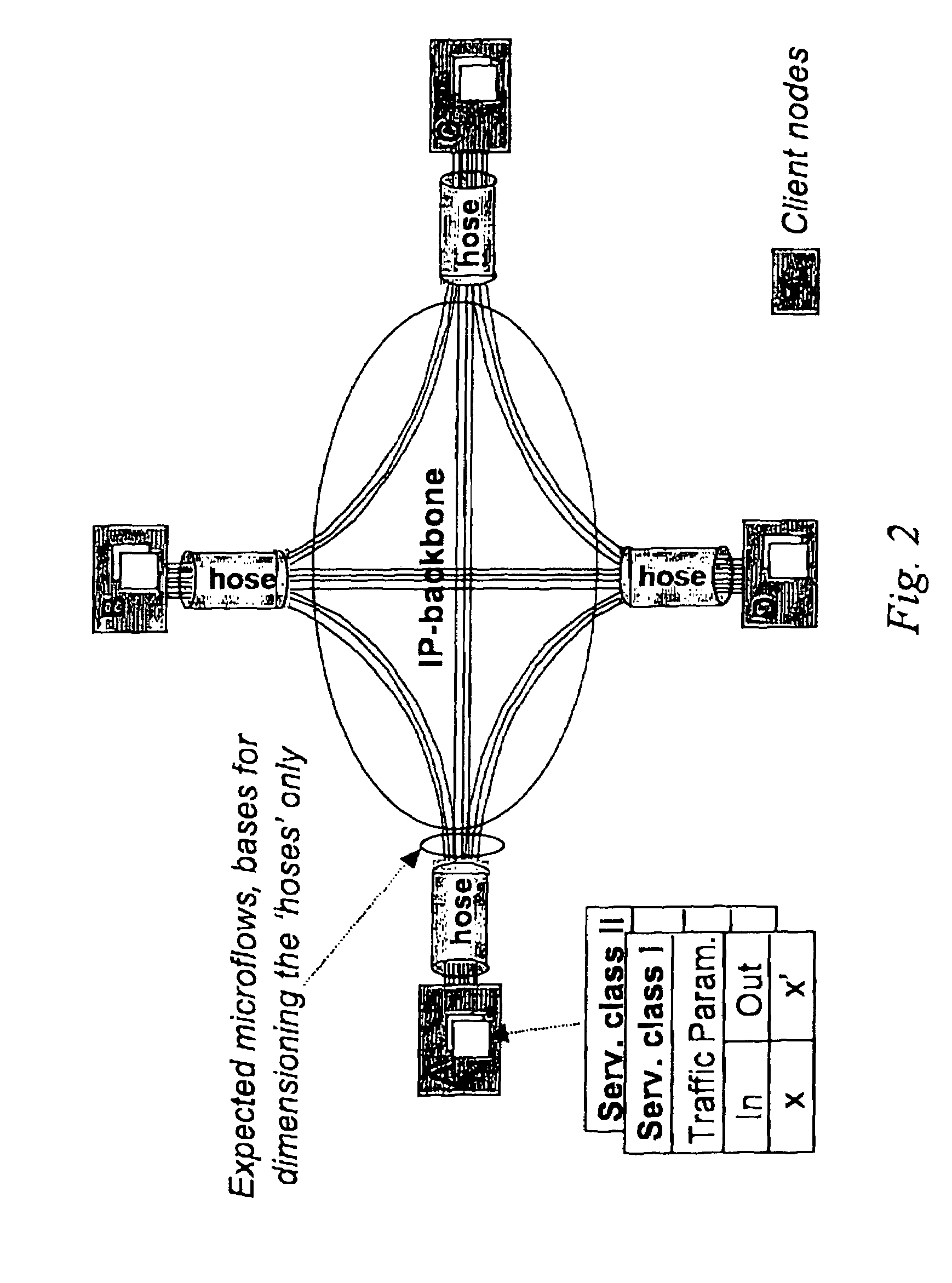
In the area of network provisioning, there is a problem of selecting a suitable traffic-provisioning model for large networks due to the high management complexity of the resource-efficient trunk model and the poor bandwidth efficiency of the easy-to-configure hose model. The invention is based on the idea of partitioning at least part of the network into multi-node clusters, and defining traffic limitations on at least two levels, including the intra-cluster level and the inter-cluster level, where the traffic limitations include one or more node-to-cluster traffic limitations for inter-cluster traffic. Subsequently, cluster-based provisioning of the network is performed based on the traffic limitations. The novel node-to-cluster limitations proposed by the invention are preferably applied in a cluster-based trunk or hose model on the inter-cluster level. In other words, for the description of the inter-cluster traffic (traffic between the clusters) cluster-based trunk or hose models can be used, preferably depending on the available information about the traffic. The cluster-based provisioning makes it possible to find a trade-off between management complexity and overprovisioning.
Owner:TELEFON AB LM ERICSSON (PUBL)
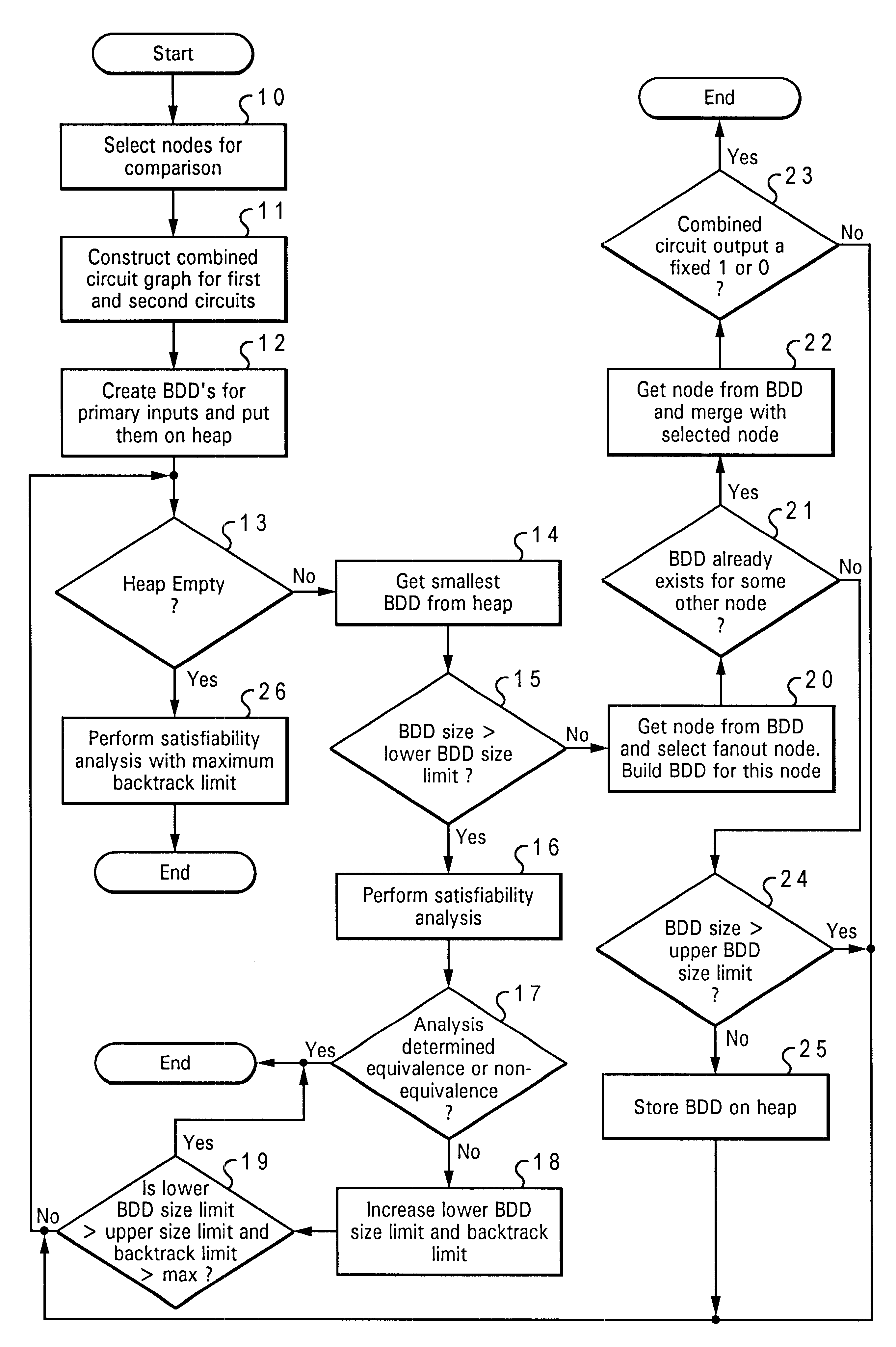
Method and system for equivalence-checking combinatorial circuits using interative binary-decision-diagram sweeping and structural satisfiability analysis
InactiveUS6473884B1Computer aided designSoftware simulation/interpretation/emulationBinary decision diagramLogical network
A method and system for equivalence checking of logical circuits using iterative circuit reduction and satisfiability techniques provide improved performance in computer-based verification and design tools. By intertwining a structural satisfiability solver and binary decision diagram functional circuit reduction method, computer-based tools can make more efficient use of memory and decrease computation time required to equivalence check large logical networks. Using the circuit reduction technique back-to-back with the simulation technique, optimum local and global circuit reduction are simultaneously achieved. By iterating between the structural and functional techniques, and adjusting the size of sub-networks being analyzed within a larger network, sub-networks can be reduced or eliminated, decreasing the amount of memory required to represent the next larger inclusive network.
Owner:IBM CORP
Flexible Radix Switch
ActiveUS20130083701A1High trafficImprove the level ofData switching by path configurationNetwork structureInterconnection
A system and method for interconnecting nodes and routing data packets in high radix networks includes constructing or redefining a network structure to provide improved performance. Computation and data storage nodes are connected to a network of switching nodes that provide near optimum bandwidth and latency for networks of any size. Specialized interconnection patterns and addressing methods ensure reliable data delivery in very large networks with high data traffic volume.
Owner:THE J SCOTT BENSON LIVING TRUST
Logistics distribution control method with soft time windows
A logistics distribution control method with soft time windows includes the following steps: (A1) a network model is built, cost resistances are assigned to roads to which network data are concentrated, and taking road nodes into consideration, toll weights are assigned to road traffic light intersections and toll stations; (A2) an optimized vehicle routing model with soft time windows (VRPTW) is built, a target function is established with lowest transportation costs, and the transportation costs are respectively composed of fixed distribution vehicle cost, transportation cost, vehicle waiting cost and delay cost; (A3) a fuzzy clustering analysis algorithm is designed, and a method based on the integration of quantitative analysis and qualitative analysis is adopted for clustering; (A4) a heuristic optimized vehicle routing algorithm is designed, the optimized vehicle routing algorithm is adopted for distribution target nodes in each class, and thereby a distribution result can be obtained. The logistics distribution control method with soft time windows adopts the distances of actual delivery road network routes between distribution nodes as a calculation basis and also takes the actual traffic capacities of roads, large network node number and transportation time needed by distribution nodes into consideration.
Owner:ZHEJIANG UNIV OF TECH
Machine for distributing articles and management system thereof
InactiveUS20060247823A1Controlling coin-freed apparatusCoin-freed apparatus detailsModem deviceNetwork link
A computerized vending machine comprising a micro-controller, a network interface and a large touch screen is provided. The machine is further part of a larger networked system. The system is administrated with the use of a computer network linked by modem or other communication means, comprising a server and its database, administration and communication software. The vending machines are equipped with computer systems allowing for remote inventory management and methods to put products on the market which are offered via a vending machine including medical or other supplies. The display screen acts as interface between a user and the machine and can also be used for multimedia presentation such as advertisement.
Owner:LAB ORTHOPEDIQUES NOUV GENERATION DIV DISTRIBUTION
Global network computers
InactiveUS7035906B1High potential economic savingOptimize networkGeneral purpose stored program computerMultiple digital computer combinationsBroadband transmissionThe Internet
This invention generally relates to one or more computer networks having computers like personal computers or network servers with microprocessors linked by broadband transmission means and having hardware, software, firmware, and other means such that at least one parallel processing operation occurs that involve at least two computers in the network. More particularly, this invention relates to one or more large networks composed of smaller networks and large numbers of computers connected, like the Internet, wherein more than one separate parallel processing operation involving more than one different set of computers occurs simultaneously and wherein ongoing processing linkages can be established between virtually any microprocessors of separate computers connected to the network. Still more particularly, this invention relates to business arrangements enabling the shared used of network microprocessors for parallel and other processing, wherein personal computer owners provide microprocessor processing power to a network, preferably for parallel processing, in exchange for network linkage to other personal and other computers supplied by network providers, including linkage to other microprocessors for parallel or other processing; the basis of the exchange between owners and providers being whatever terms to which the parties agree, subject to governing laws, regulations, or rules, including payment from either party to the other based on periodic measurement of net use or provision of processing power.
Owner:ELLIS III FRAMPTON E
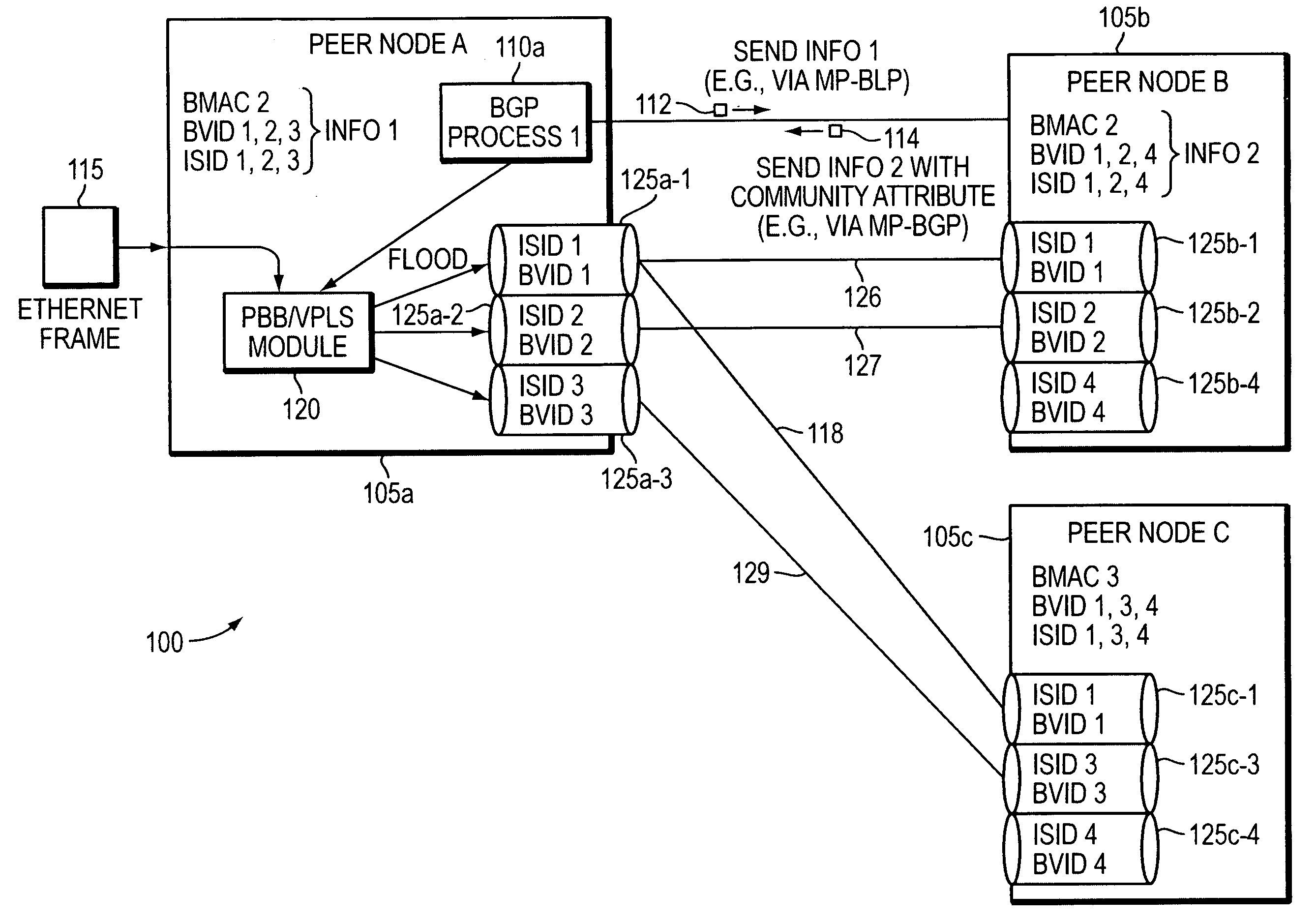
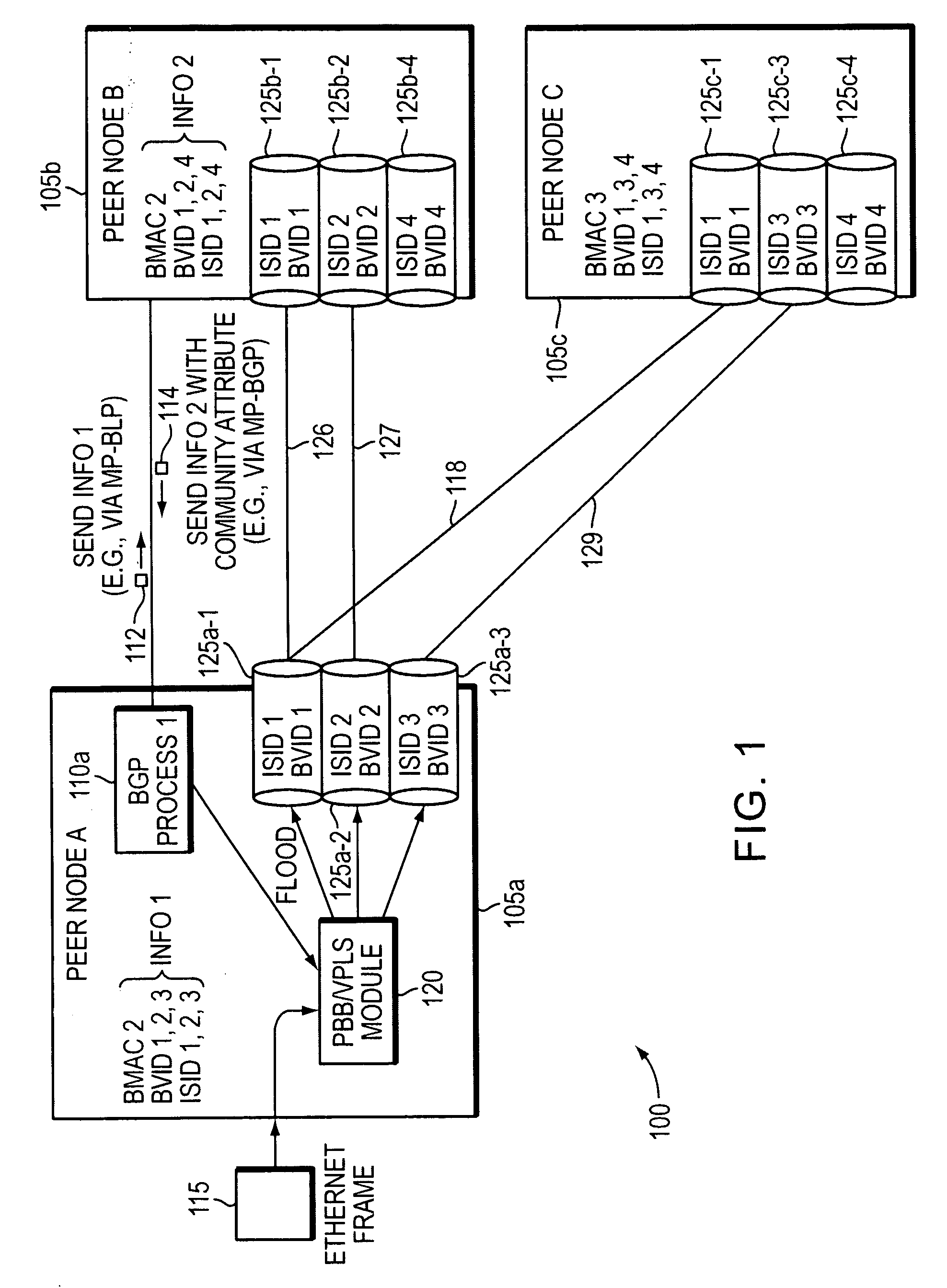
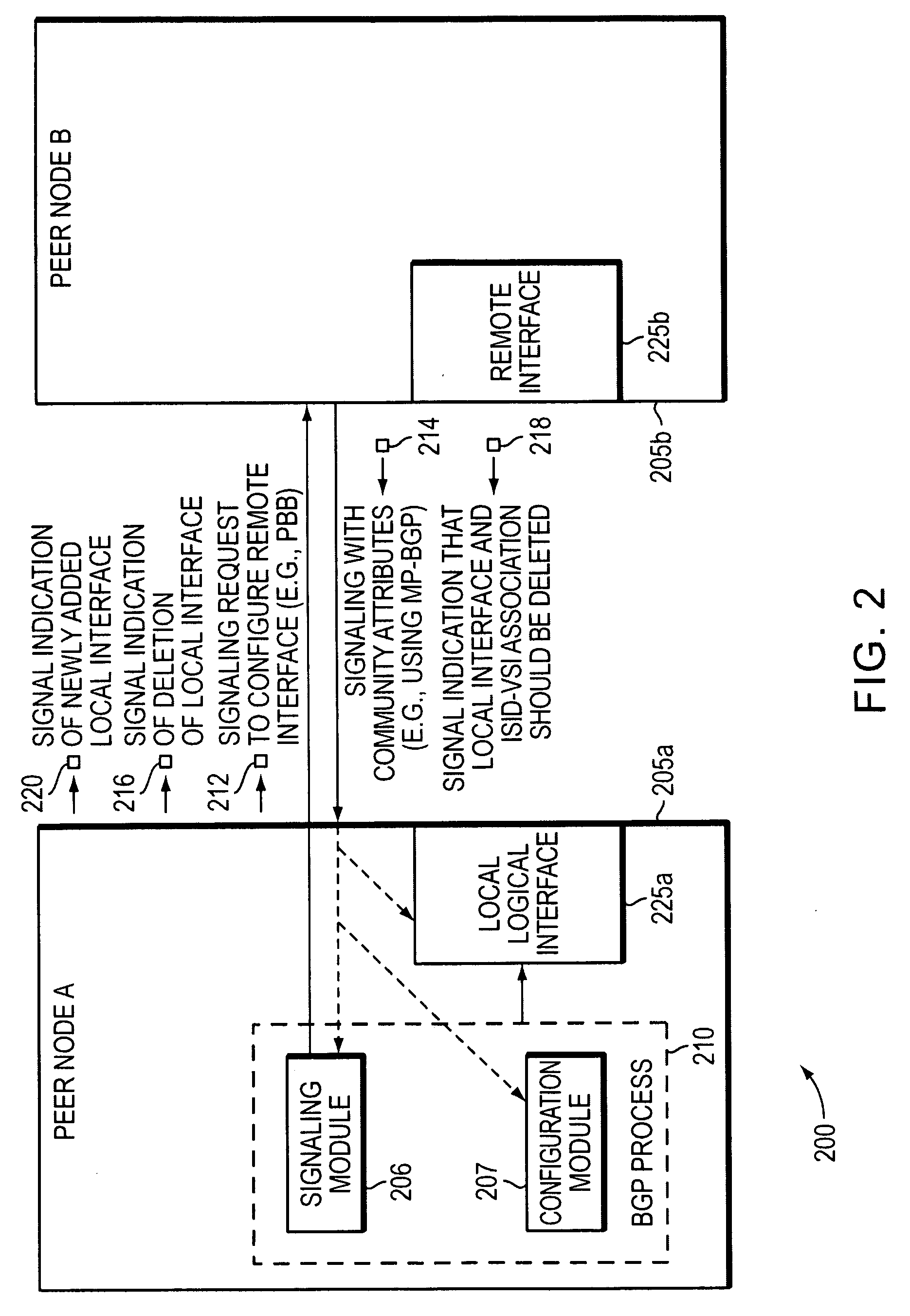
Method and apparatus for provisioning a network element
Methods and apparatuses are disclosed for configuring a Provider Backbone Bridge (PBB) interface within Virtual Private LAN Service using Multi-Protocol Border Gateway Protocol (MP-BGP). Previously, the only ways to enable PBB interfaces for transmission were by learning, which poses security and scalability concerns due to flooding, or by manual configuration, which is impractical for large networks. Embodiments of the present invention enable custom topologies to be built in a controlled manner, which has not previously been possible for PBB over VPLS. By using MP-BGP messages to exchange PBB interface information between nodes, peering relationships are established, and communities may be built with any desired topology. Previously, PBB has only been used as a connectionless bridge; embodiments of the present invention use PBB as a connection between edge nodes. Network designers are provided increased flexibility, and security and congestion are improved, benefiting end users.
Owner:TELLABS OPERATIONS
Cluster-based network provisioning
ActiveUS7577091B2Improved network provisioning strategyImprove performanceError preventionFrequency-division multiplex detailsNode clusteringTrade offs
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for performance testing of scalable distributed network transactional databases
ActiveUS20190140935A1Shorten the timeEasy loadingEncryption apparatus with shift registers/memoriesDesign optimisation/simulationComputer hardwareScalable distributed
A system for performance testing of scalability implementations and testing of stability in blockchain database implementations. The testing system comprises a cluster of private blockchain nodes instantiated on a network and a control console that allows the user to set the number of nodes in the network and the number of clients for testing of a particular blockchain implementation. Performance metrics are established and tested. The test system allows for staged testing using generated databases, wallets, and accounts starting with simple 5-node networks, expanding to larger networks, then testing with decreased block validation times, continuing to testing using alternative, faster trust schemes, then testing implementation on divided blockchains, and finally testing on shared blockchains.
Owner:LIQUINEQ AG
Method for processing resource of network game client
InactiveCN101626391AFast game experienceRealize batch downloadData switching networksGame playerClient-side
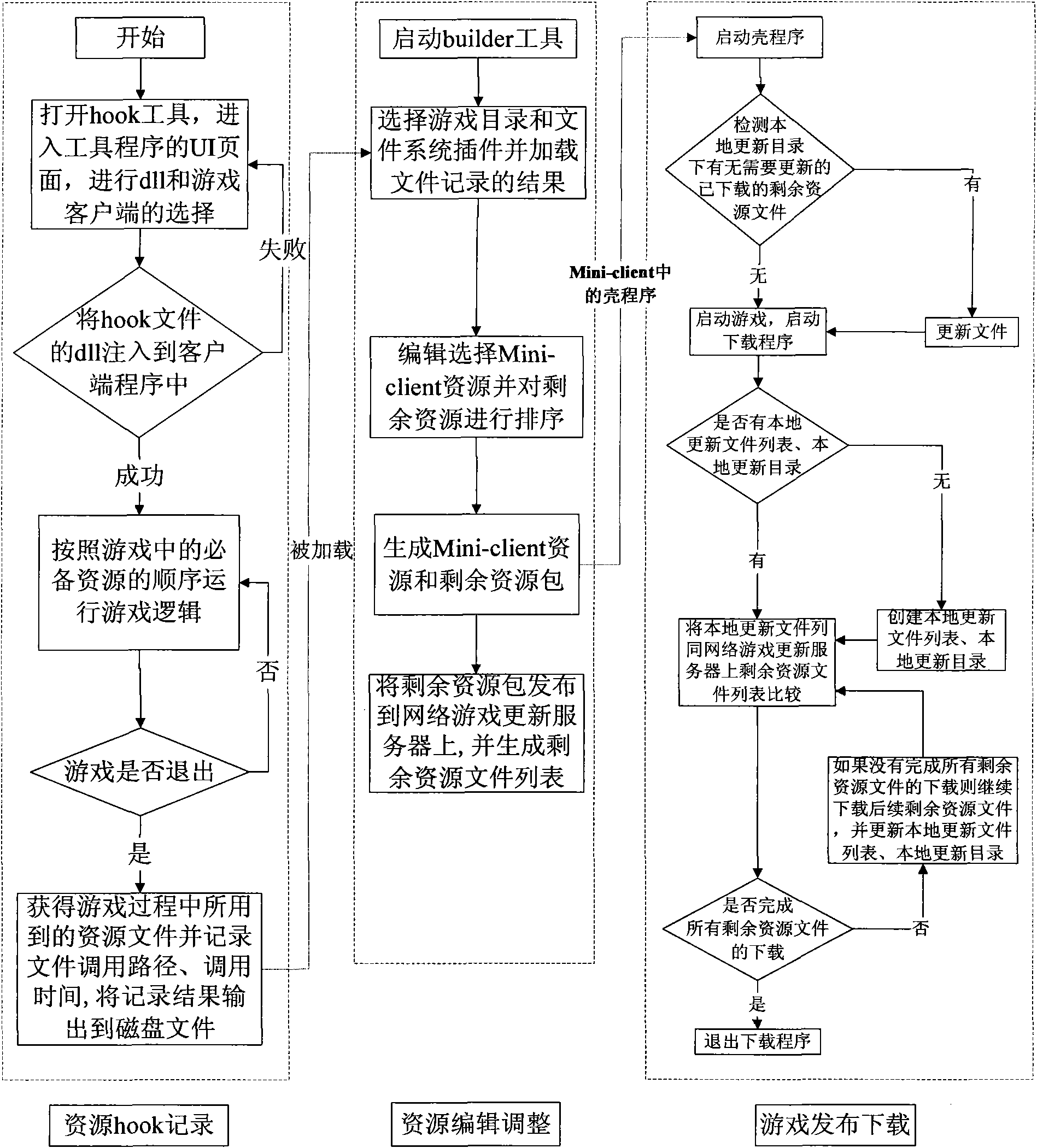
The invention discloses a method for processing resources of a network game client, which comprises the following steps: carrying out capturing processing on a resource file used by a game client through a hook tool, acquiring the resource file used in the game process, recording a transferring path and the transferring time of the file, carrying out editing regulation on the acquired resource file used in the game process by utilizing a resource editing regulation tool to generate a minimal client resource and a residual resource, releasing the residual resource to a network game update server, configuring the minimal client resource for the game client, starting a game by the game client, filling the downloaded residual resource needing to be updated to an original position of the client, entering the game and simultaneously starting a downloading program, downloading the undownloaded residual resource in backstage, and updating a local update file list and a local update catalog. The method is adopted and can simply download a program of a large network game client; and a game player can rapidly carry out game experience.
Owner:SHENGQU INFORMATION TECH SHANGHAI
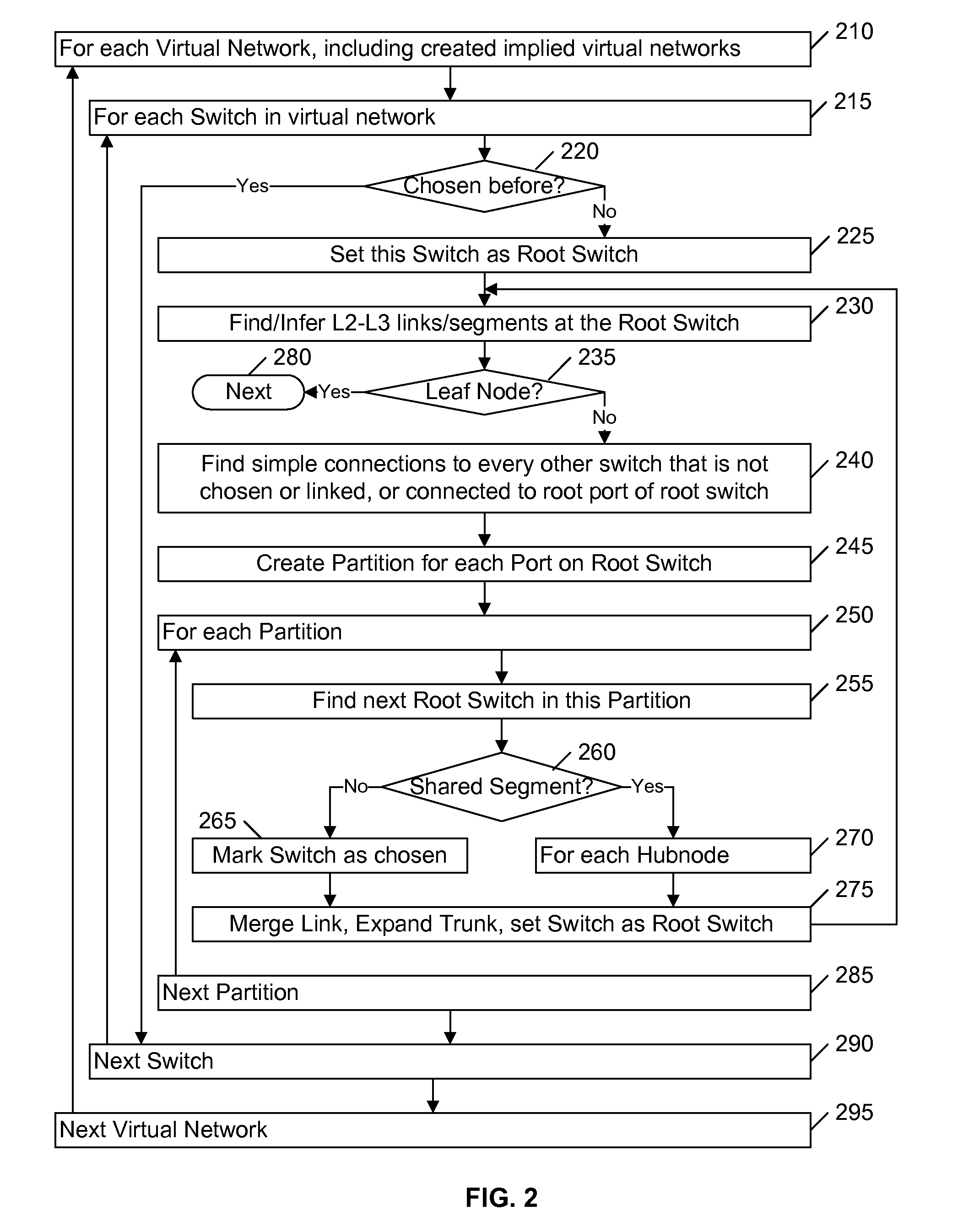
Link inference in large networks based on incomplete data
ActiveUS8089904B2Efficient implementationFirmly connectedData switching by path configurationNetwork connectionsTheoretical computer scienceLarge networks
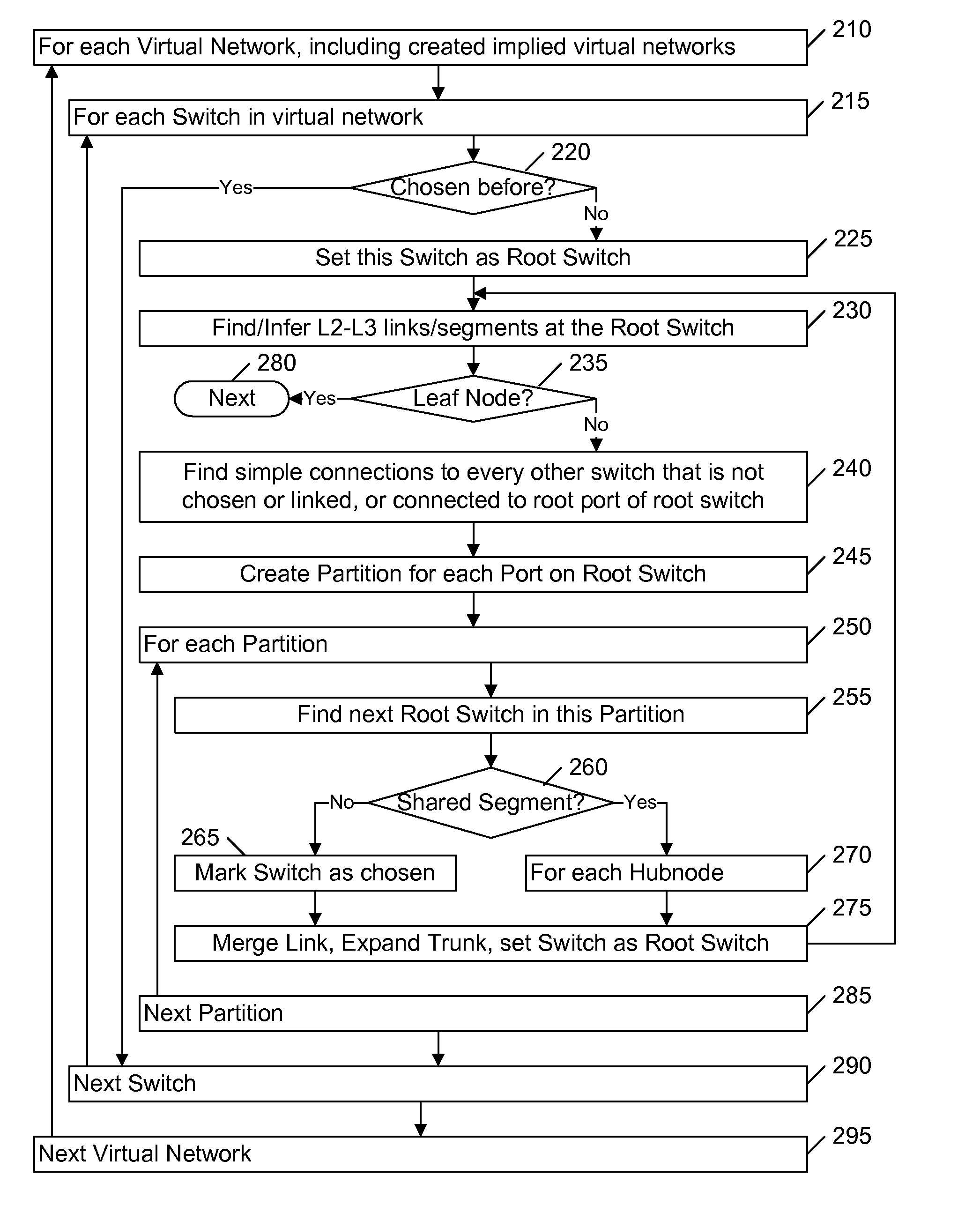
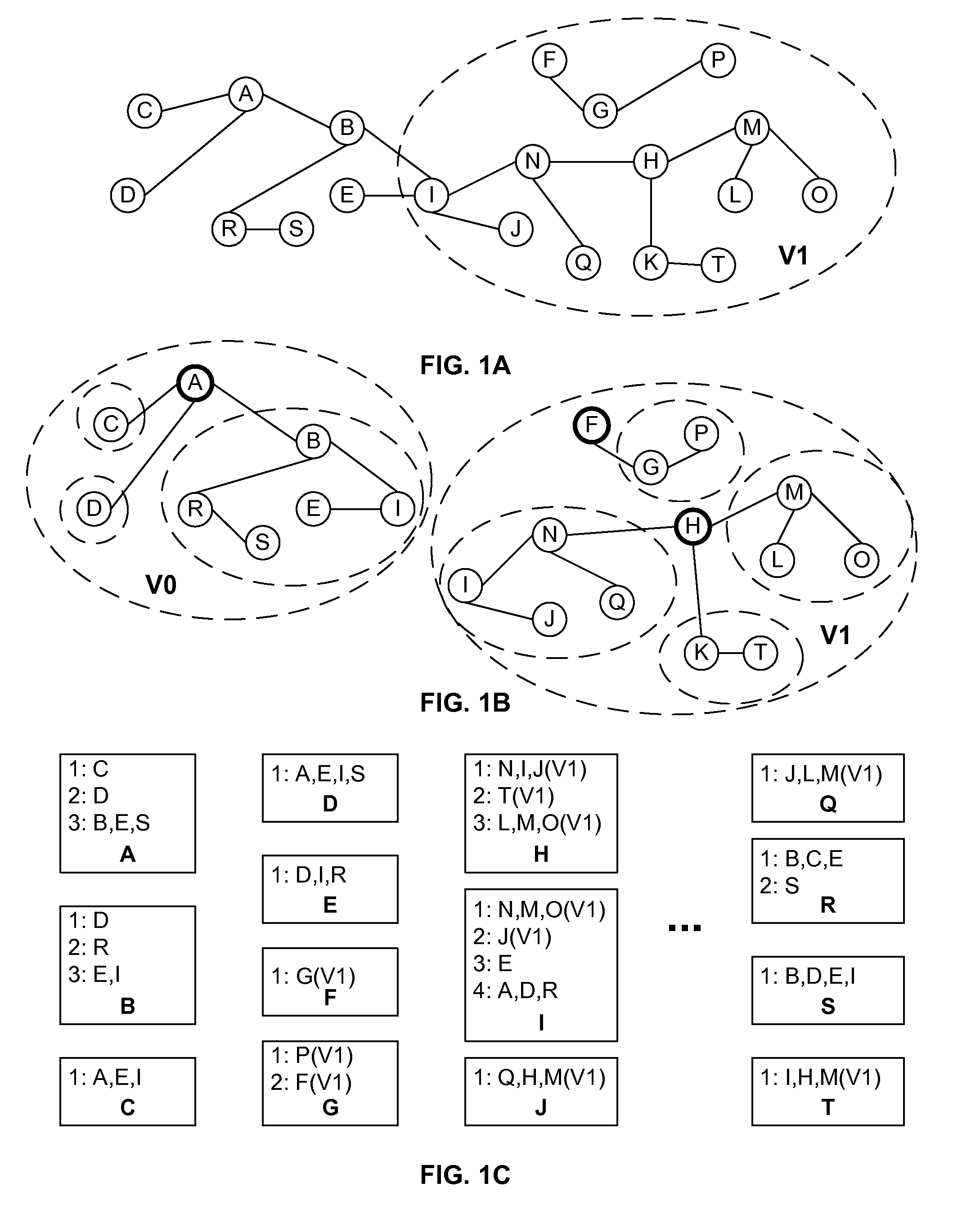
A network is partitioned into a set of independent partitions, and the topology of each partition is determined, then merged to form a topology of the entire network. Preferably, the partitioning is hierarchical, wherein the network is partitioned to form individual VLAN partitions, and each of the VLAN partitions is further partitioned based on the nodes that are simply connected to each port of one or more selected root switches within the VLAN partition. Simple connections to each port are efficiently determined based on an aggregate address forwarding table associated with each node. Ancillary information, such as spanning tree or CDP data, may be used to facilitate efficient partitioning and / or to validate inferences that are made with incomplete information.
Owner:RIVERBED TECH LLC
Intelligent measurement and control Internet of things platform and its measurement and control method based on cloud computing
InactiveCN102291280AReliable Monitoring Information ServiceEasy to monitorData switching networksNetwork securityComputer terminal
An intelligent measurement and control Internet of Things platform based on cloud computing includes a resource layer, a service system for managing the resource layer, and an SOA service-oriented service interface provided to user terminals through WebServices; The customer provides a general, cross-industry, and cross-regional information platform, and does not need to carry out tedious work such as the construction of the monitoring center, the selection and maintenance of software and hardware systems, the planning of network transmission, and the continuous improvement and upgrading of network security. Smart home, including home anti-theft, video intercom, video surveillance, lighting control adjustment, electrical control, and future home health care, home robots, etc., applied to industry users, including machine room monitoring, environmental monitoring, landscape lighting monitoring, elevators Operation monitoring, hydrology and water conservancy monitoring, agricultural irrigation monitoring, storage and transportation monitoring, urban pipe network monitoring, shop anti-theft and other monitoring system large network platform.
Owner:SHENZHEN HEGUANG MEASUREMENT CONTROL TECH
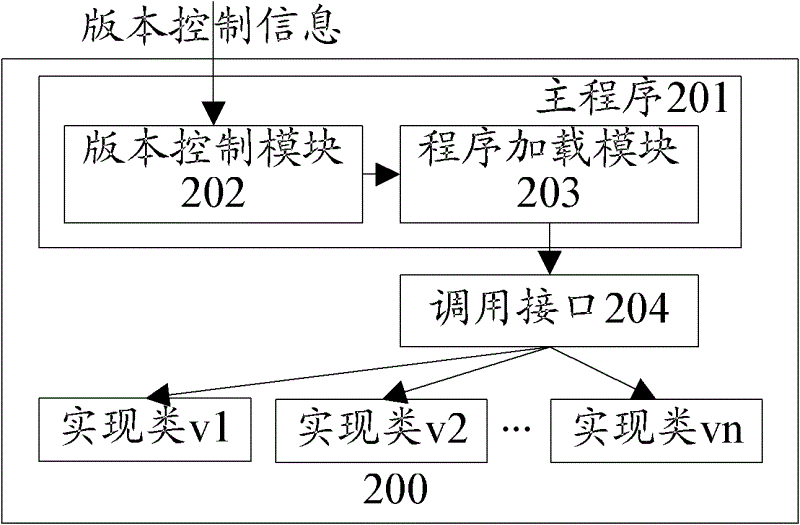
Software upgrading method and software upgrading device
ActiveCN102622241AReduce occupancyAchieve the purpose of silent updateProgram loading/initiatingTraffic capacitySoftware update
The invention discloses a software upgrading method and a software upgrading device which are used for solving the problems that update of application software of a mobile terminal occupies large network flow and is complex and inconvenient. Function codes finishing concrete program functions in a main program are extracted and packaged to form an implementation class, a call interface is abstracted, and the main program calls the implementation class through the call interface so as to finish the concrete program functions. When the function codes need updating, the main program acquires an implementation class of a new version, and the implementation class of an old version is replaced with the implementation class of the new version. When the software is updated, users only need to download code files of part of logic from a server so as to replace original code logic, and because updated content is only a subset of overall program codes, the occupied network flow is small. Under a silent update mode, the software automatically finishes an upgrading process during the software using process of the users, and accordingly the aim of silent update is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
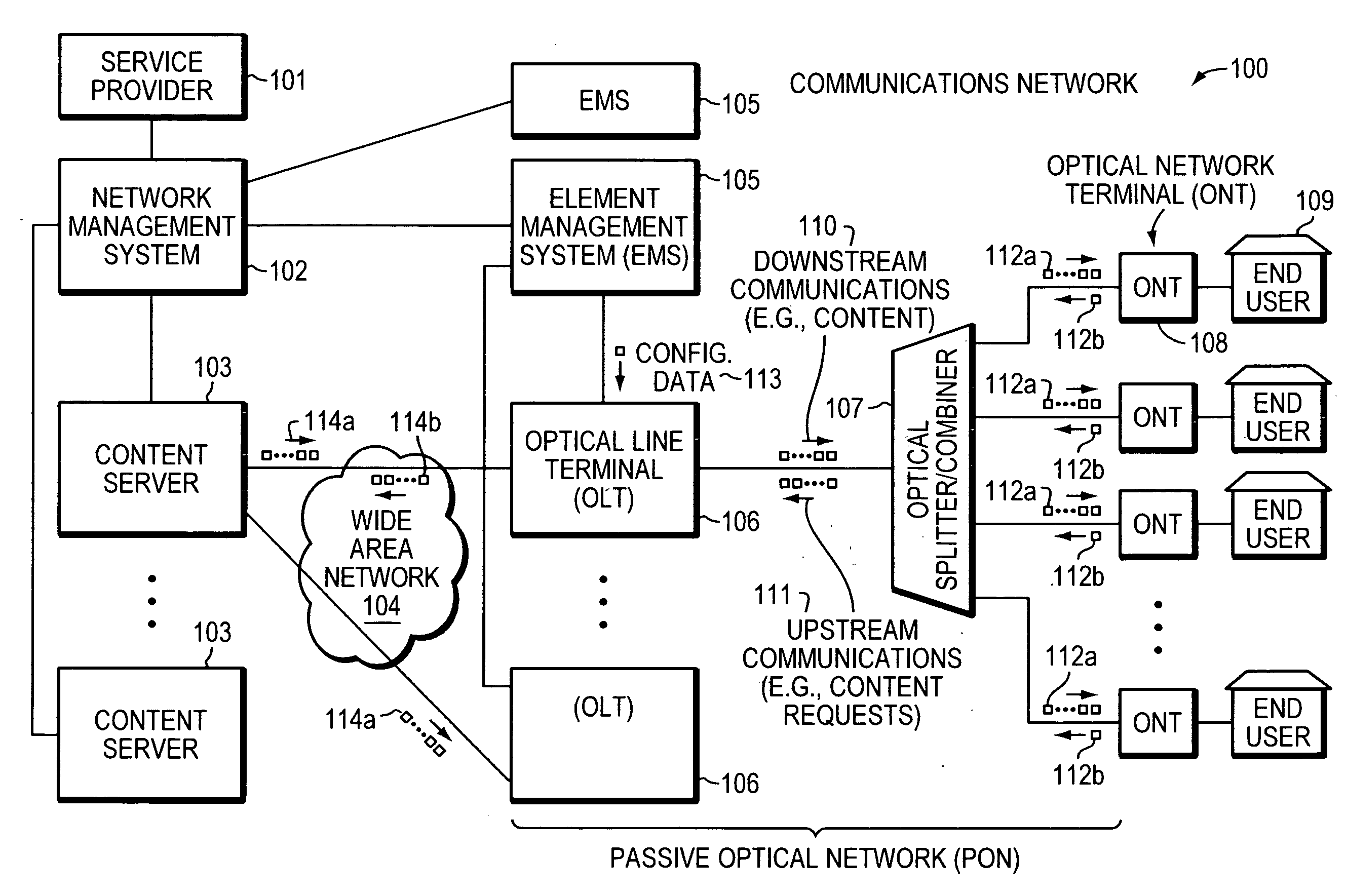
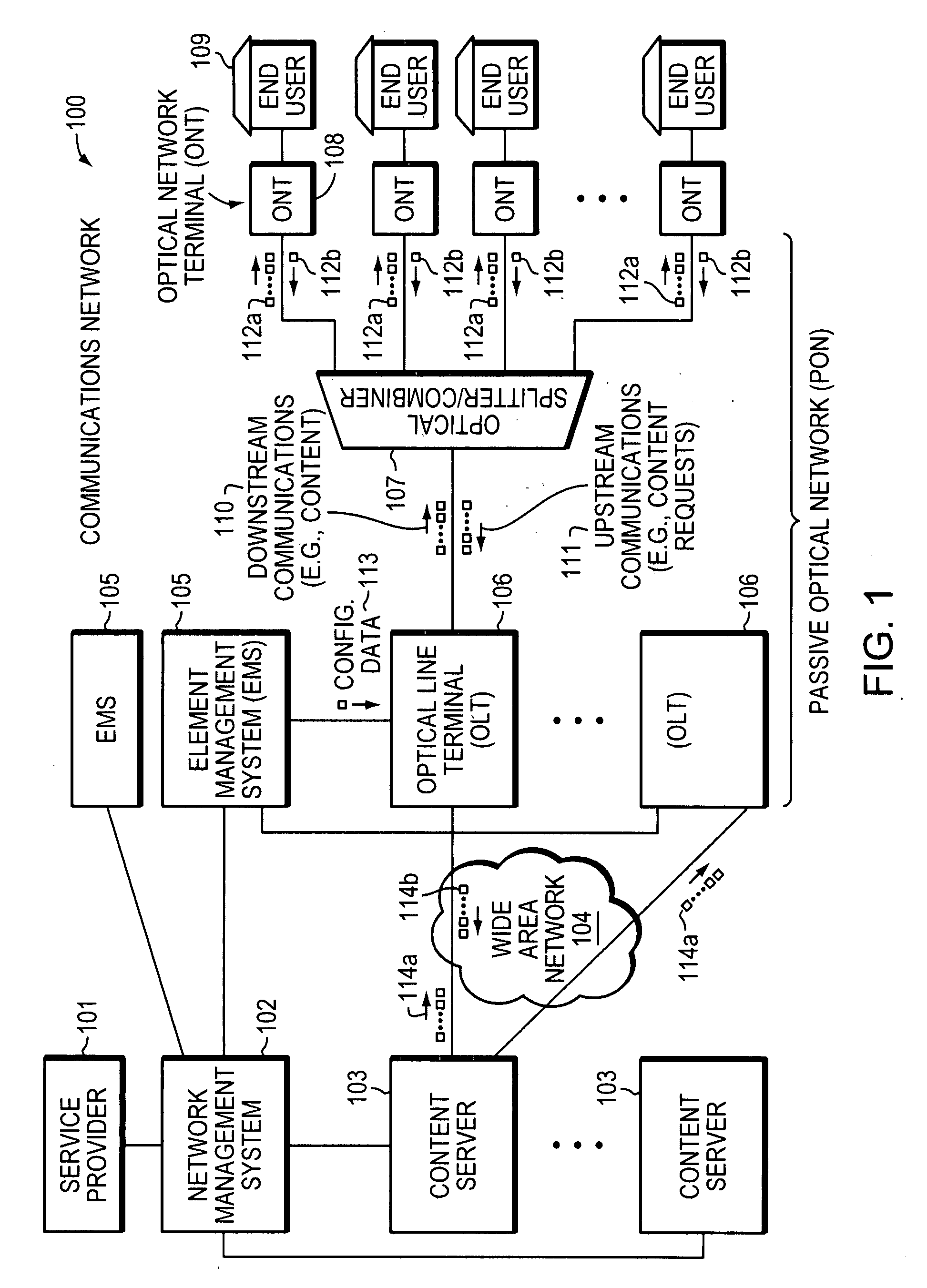
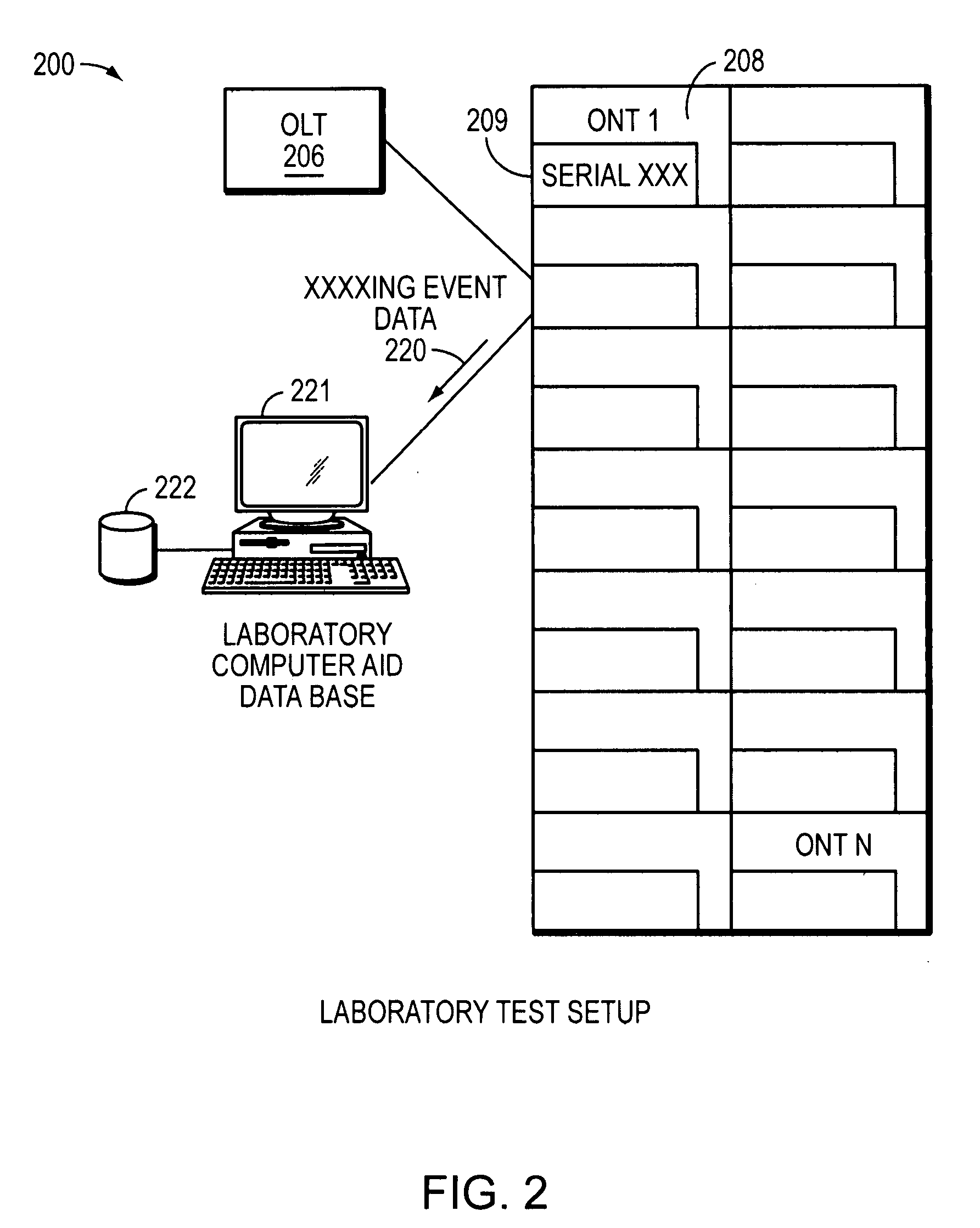
Method and system for enabling diagnosing of faults in a passive optical network
InactiveUS20090060496A1Multiplex system selection arrangementsTime-division multiplexFiberInstability
In a passive optical network (PON), multiple optical network terminals (ONTS) transmit data to an optical line terminal (OLT) using a common optical wavelength and fiber optical media. Various components of the PON, including the OLT and ONT(s), can malfunction. Centralized techniques for maintaining or diagnosing fault conditions may be ineffective in large networks or in relatively small networks because of vast amounts of information and limited storage capacity for the information. Thus, fault conditions may occur and not be diagnosed due to lost or overwritten information. Therefore, a distributed approach based on information related to ranging of ONTs within the PON is employed in an example embodiment of the invention. This distributed approach can improve monitoring and diagnosis of fault conditions that may lead to instability of the PON.
Owner:TELLABS VIENNA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com