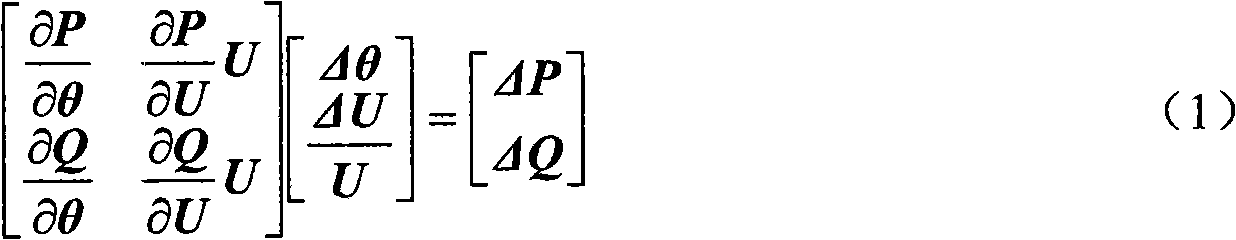Patents
Literature
193 results about "Network partition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
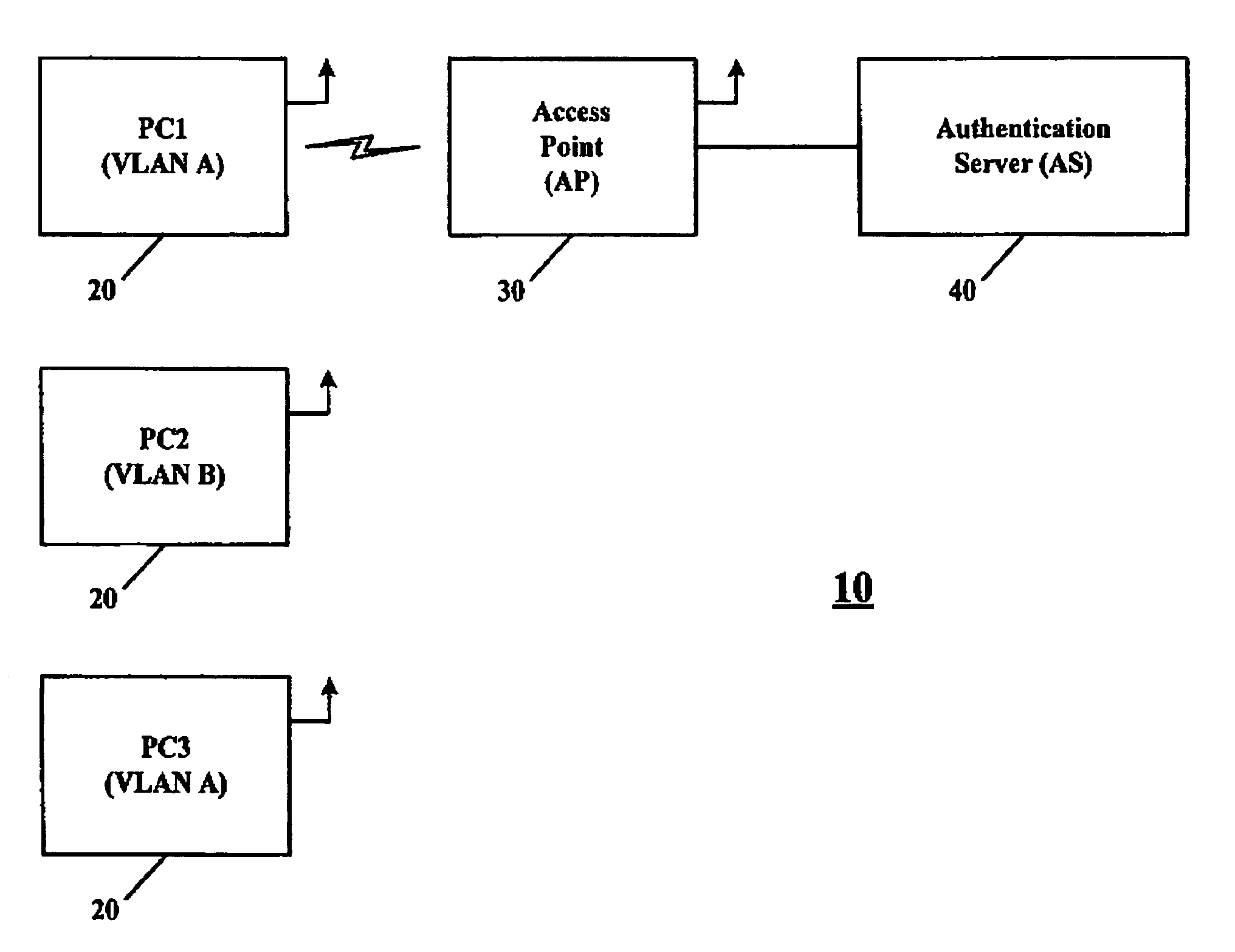
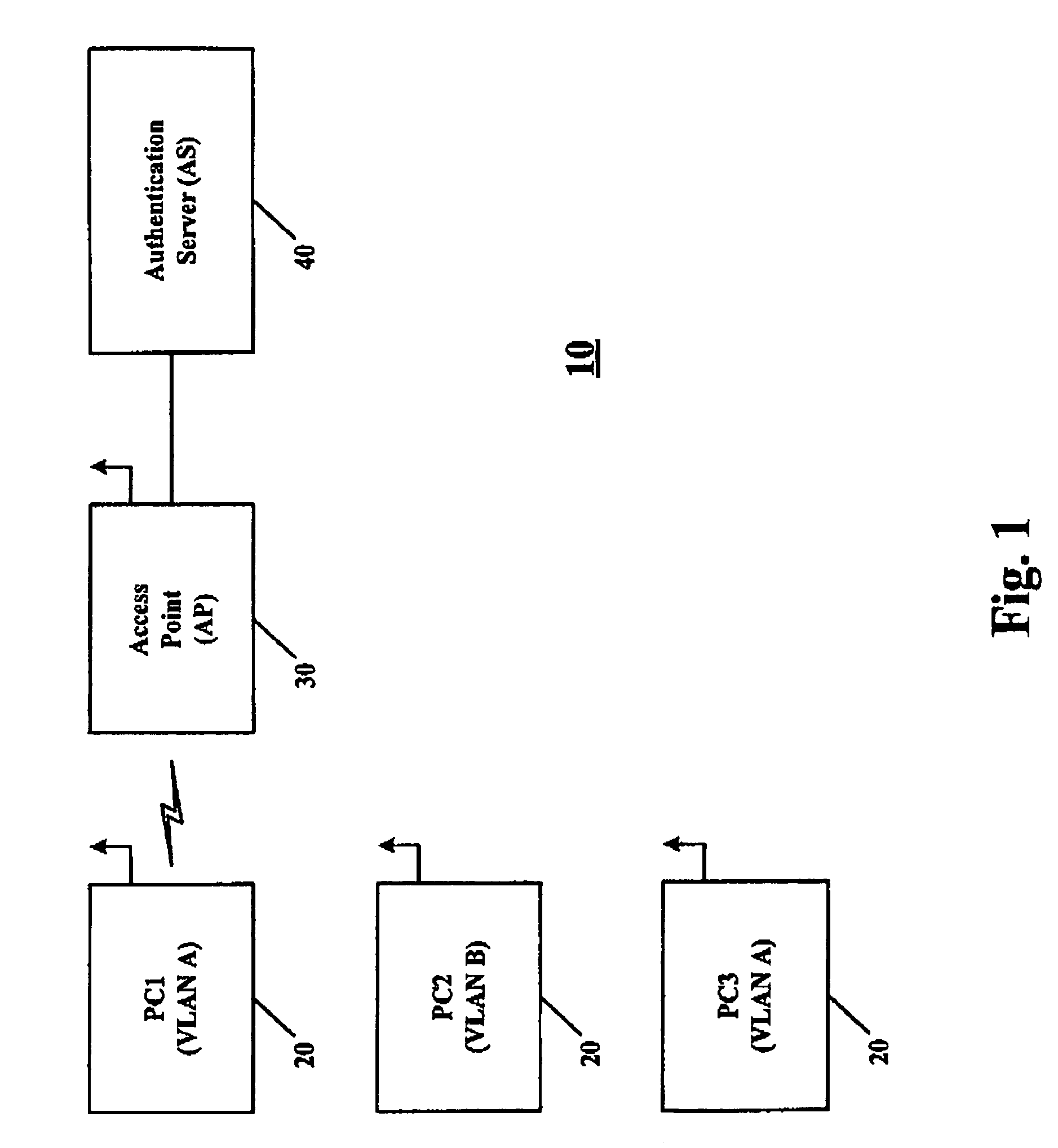
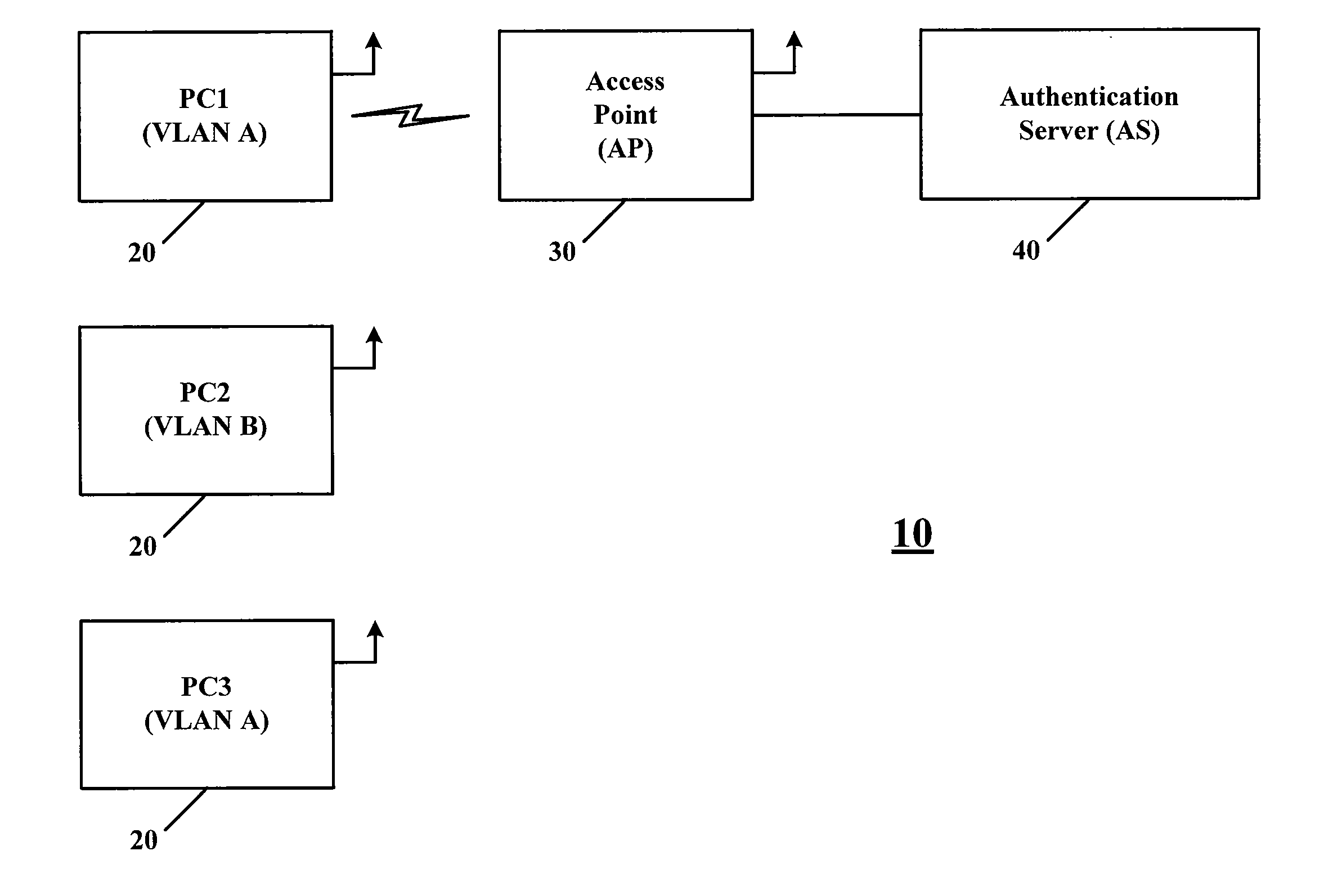
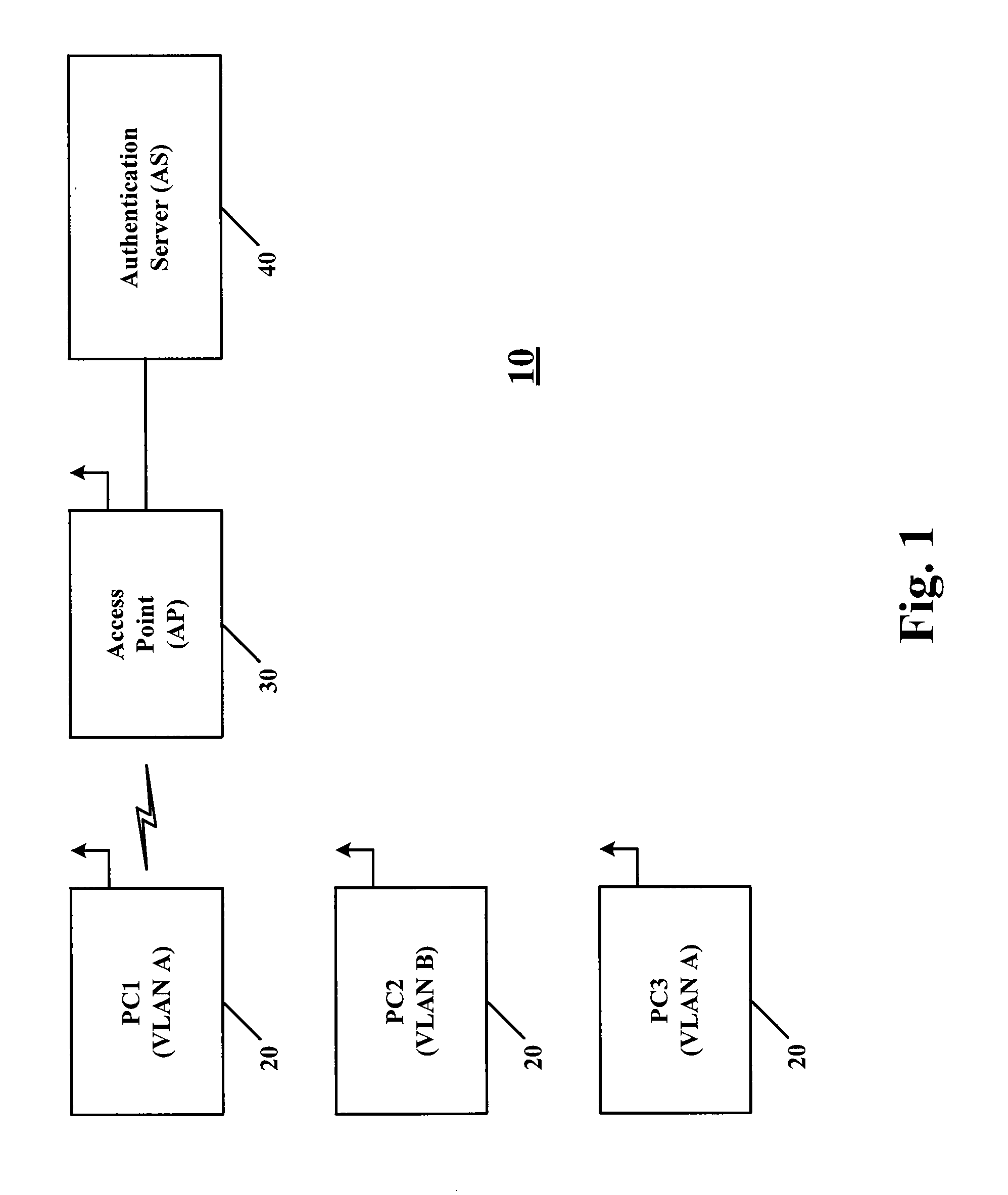
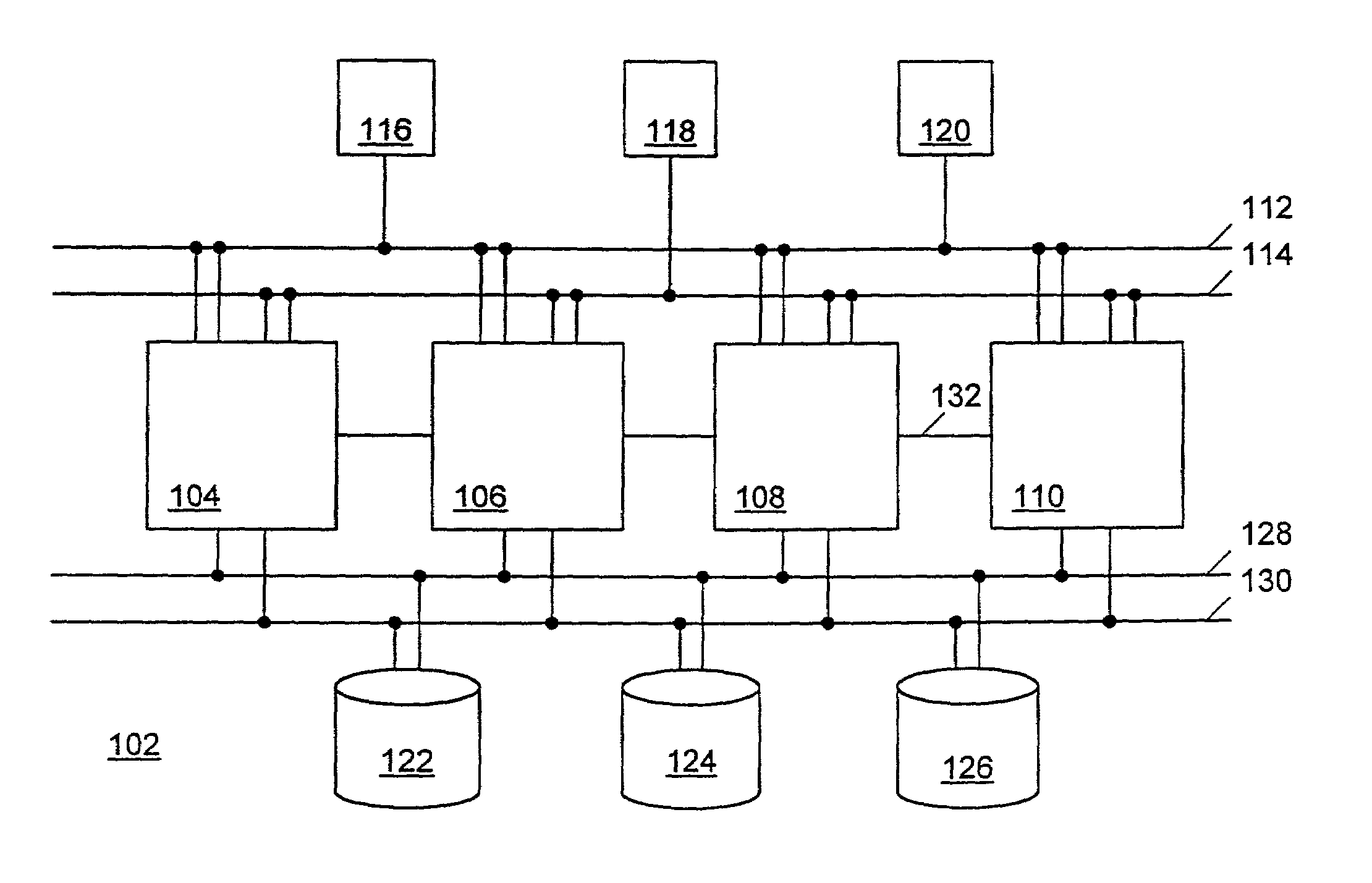
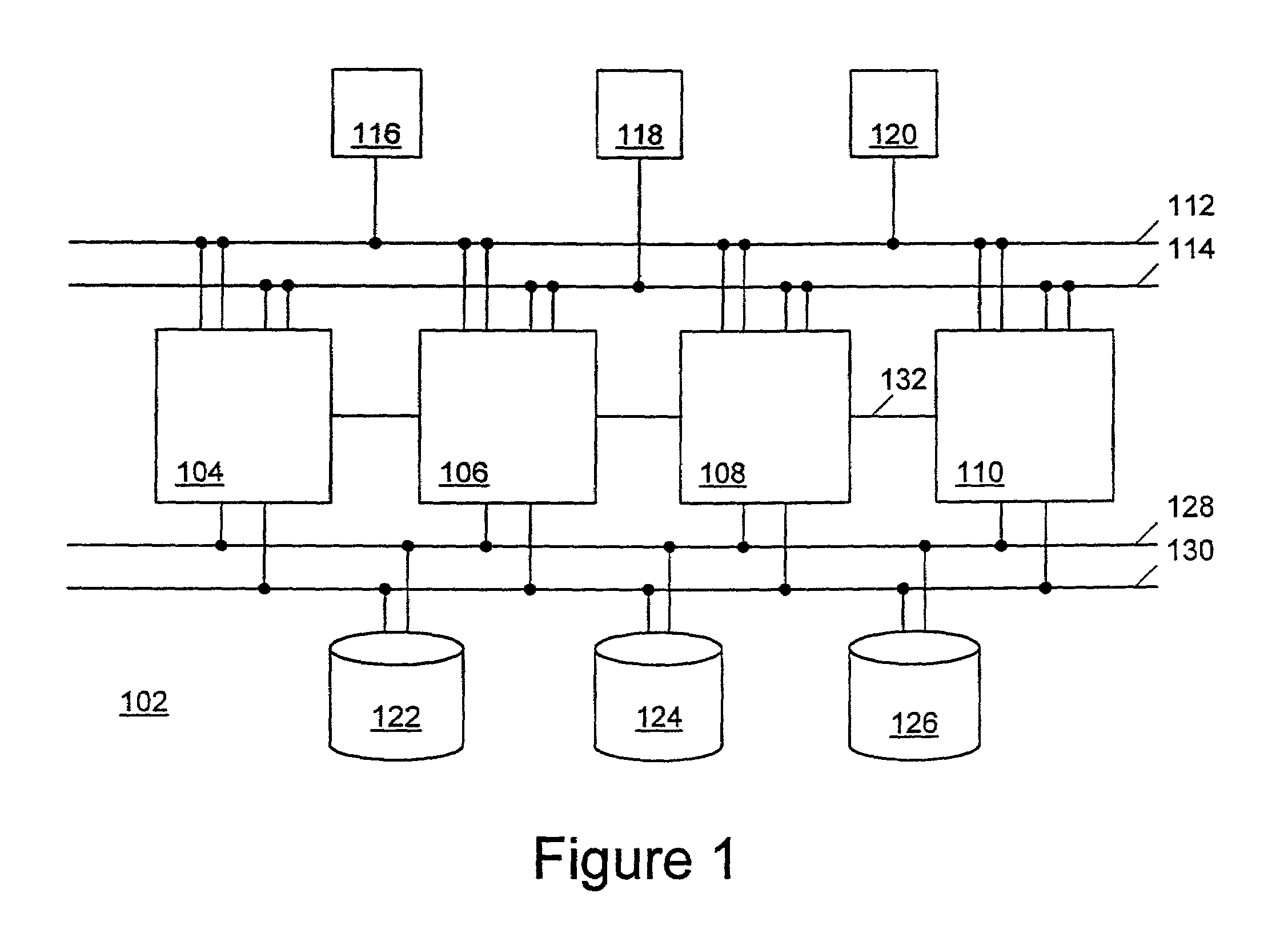
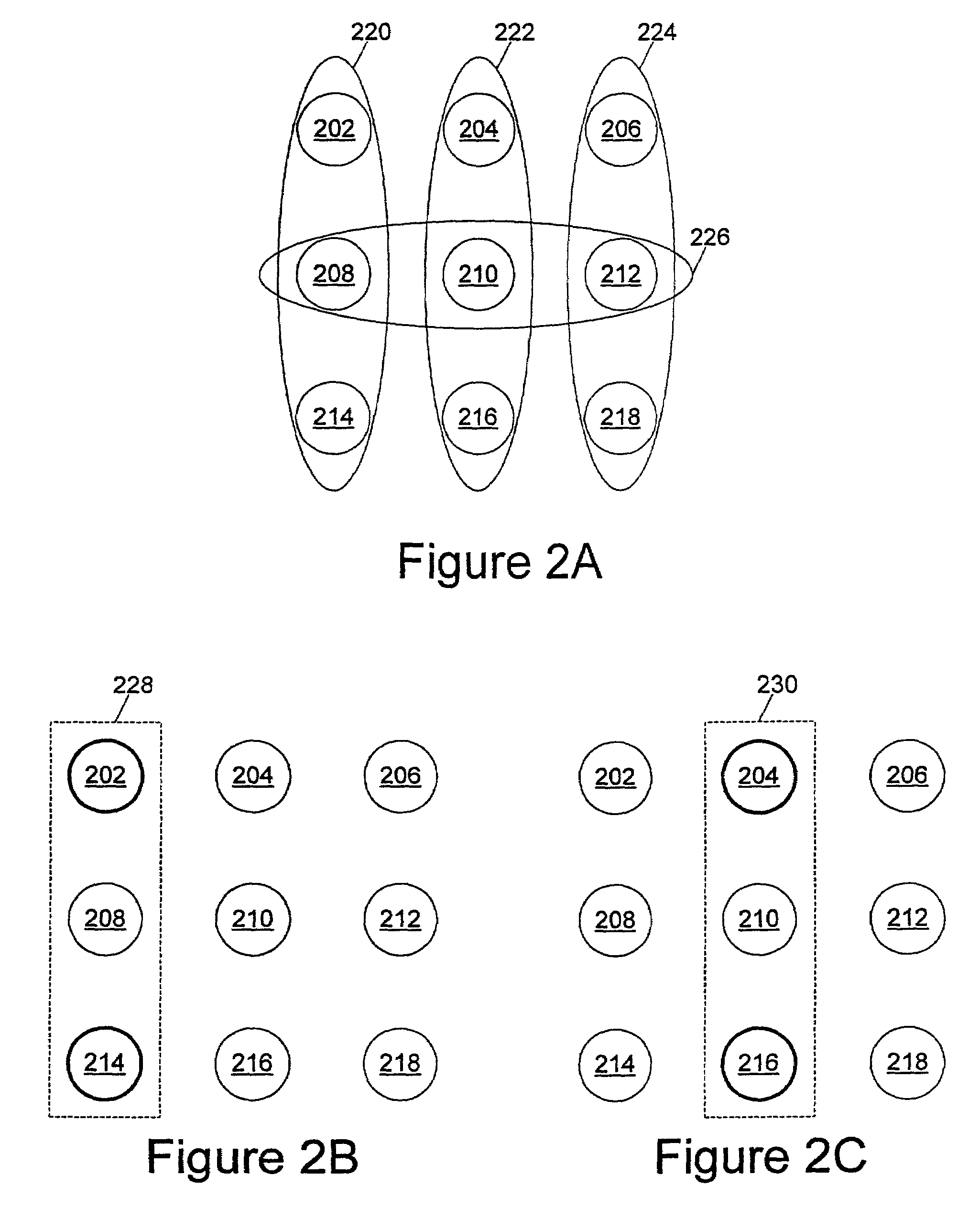
A network partition refers to network decomposition into relatively independent subnets for their separate optimization as well as network split due to the failure of network devices. In both cases the partition-tolerant behavior of subnets is expected. This means that even after the network is partitioned into multiple sub-systems, it still works correctly.
Source assignment based on network partitioning
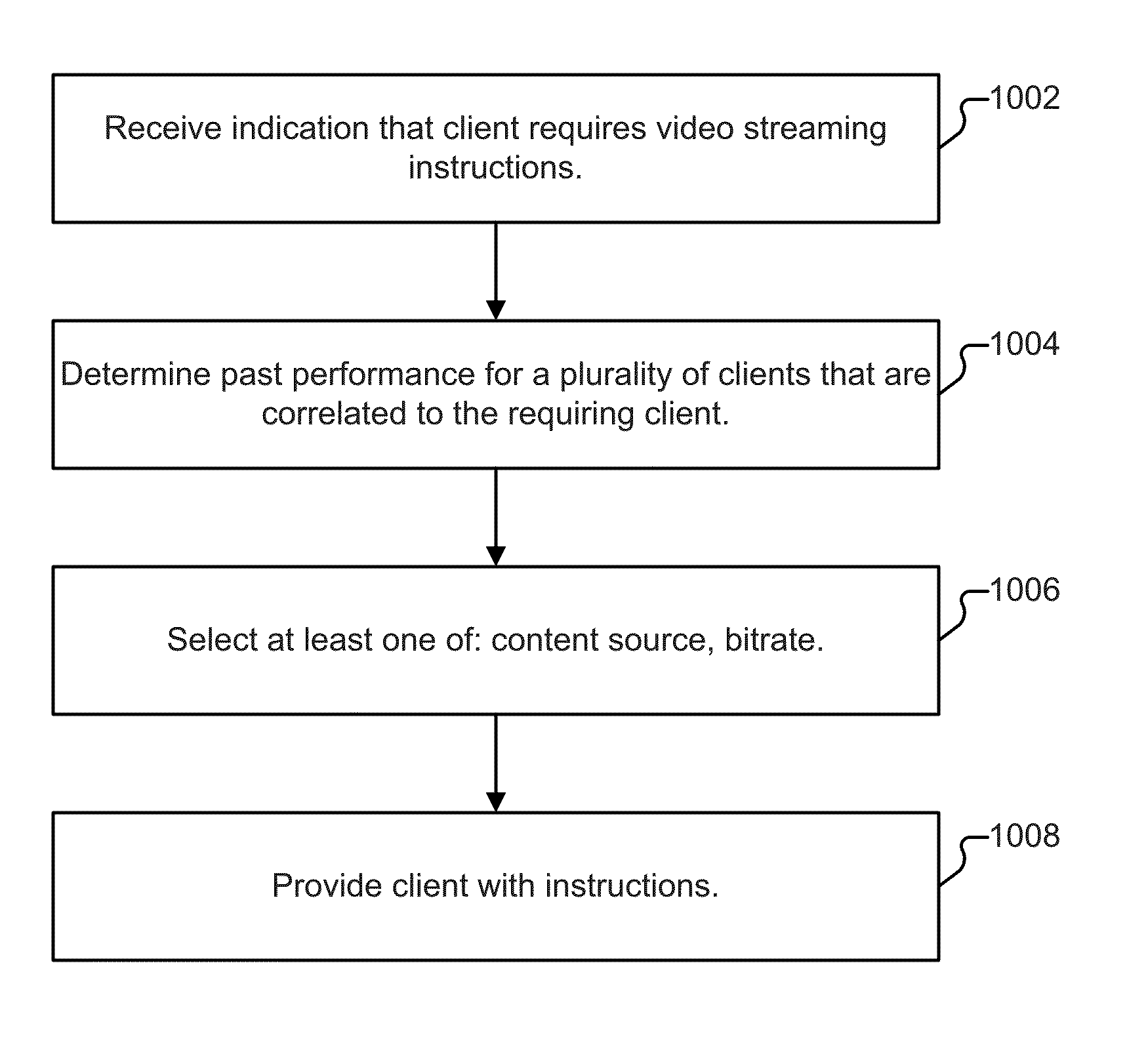
Directing a video player to a video source is disclosed. An indication that a client requires video streaming instructions is received. A past download performance for a plurality of clients that or correlated to the client requiring video streaming instructions is determined. At least one of: a content source, and a bitrate, is selected, based at least in part on the determined past download performance of the plurality of correlated clients. The client is provided with instructions based at least in part on the selection.
Owner:CONVIVA
High availability for intelligent applications in storage networks
ActiveUS20060168192A1Effective failoverMultiple digital computer combinationsTransmissionFailoverStorage area network
Methods and apparatus provide formation and management of intelligent application clusters in a storage area network. Disk arbitration mechanisms ensure that a cluster is owned by a single member. In the event of a network partition, each cluster member involved arbitrates to gain ownership of a cluster. High availability mechanisms allow monitoring of system resources and effective failover capabilities.
Owner:CISCO TECH INC
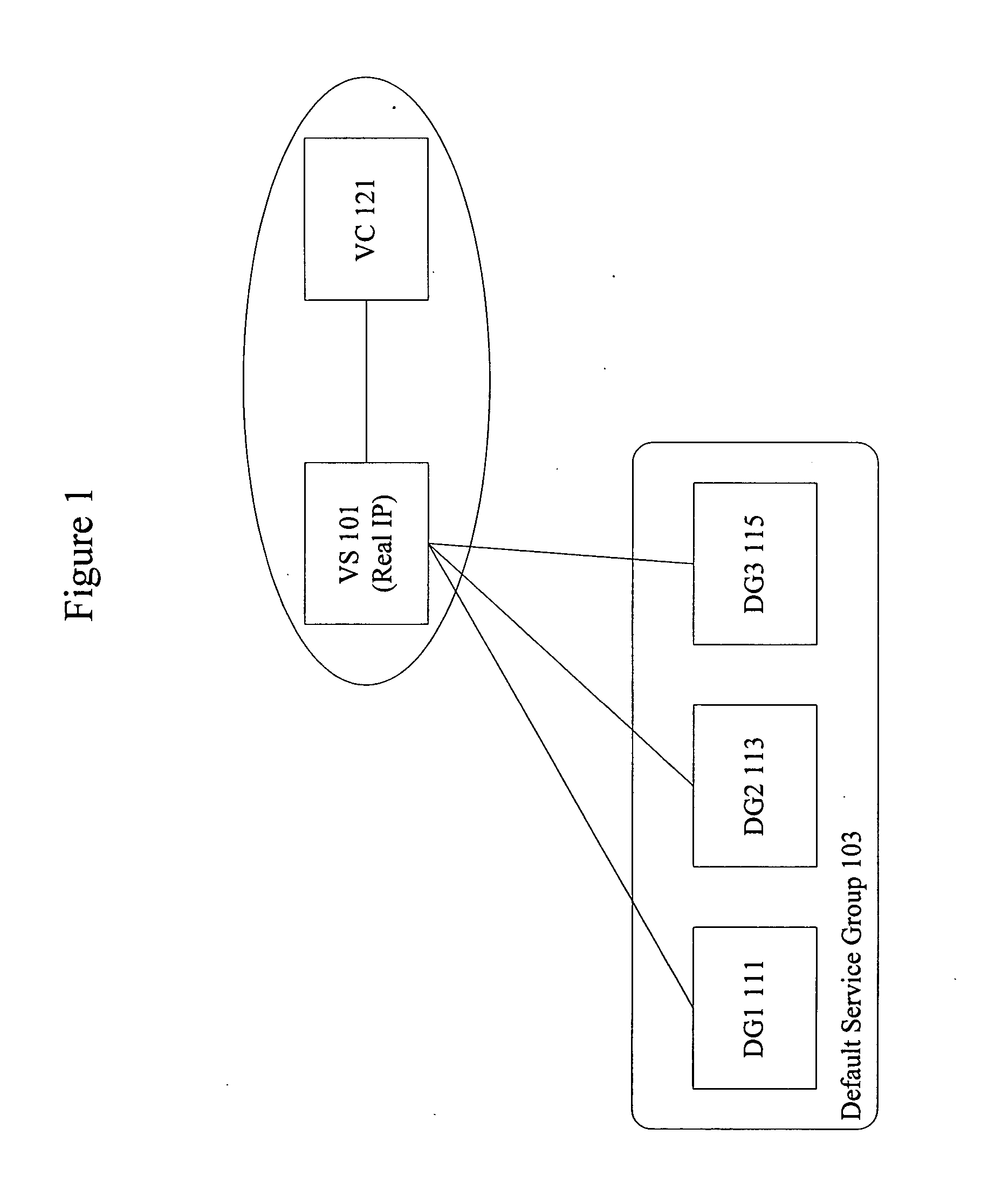
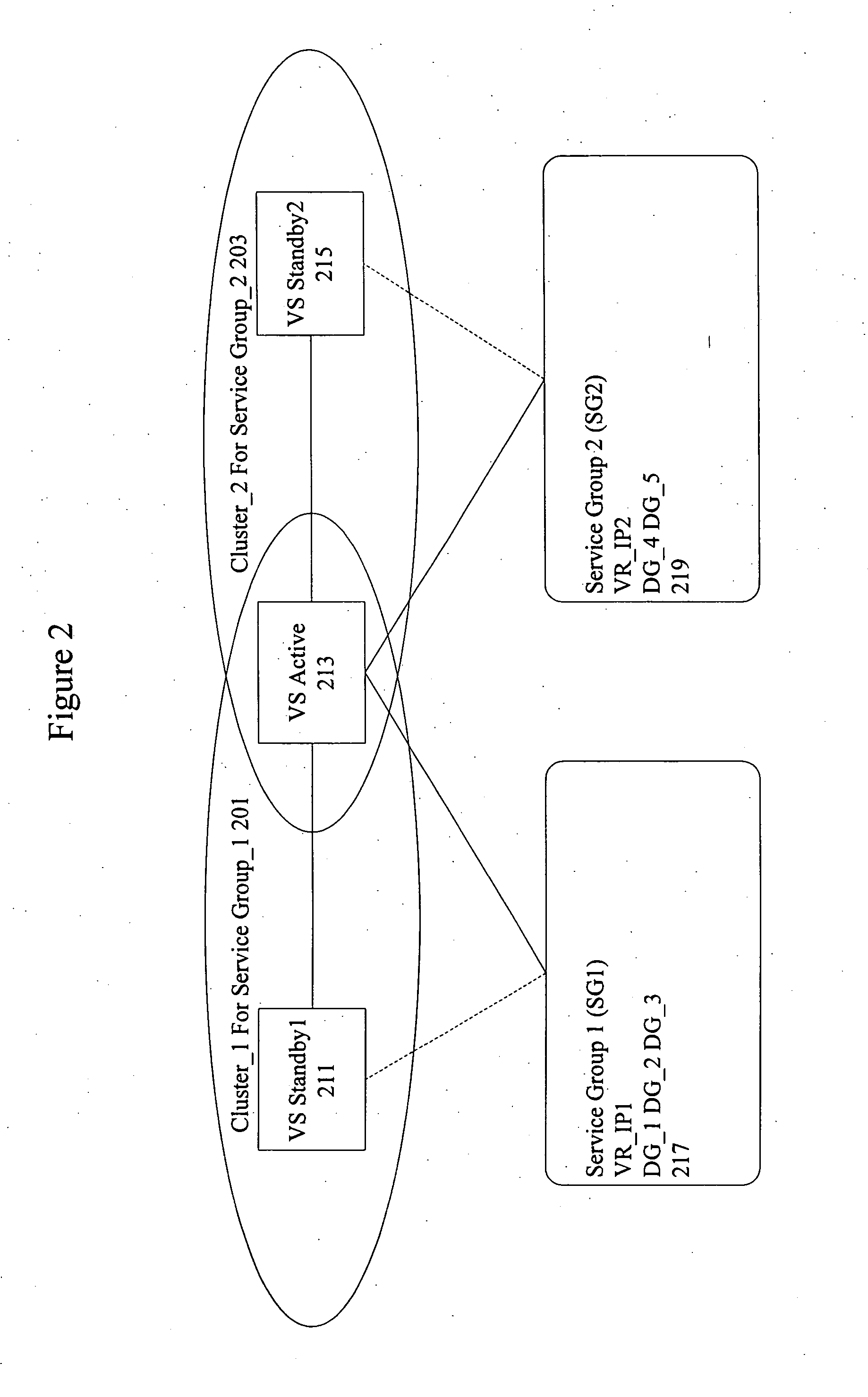
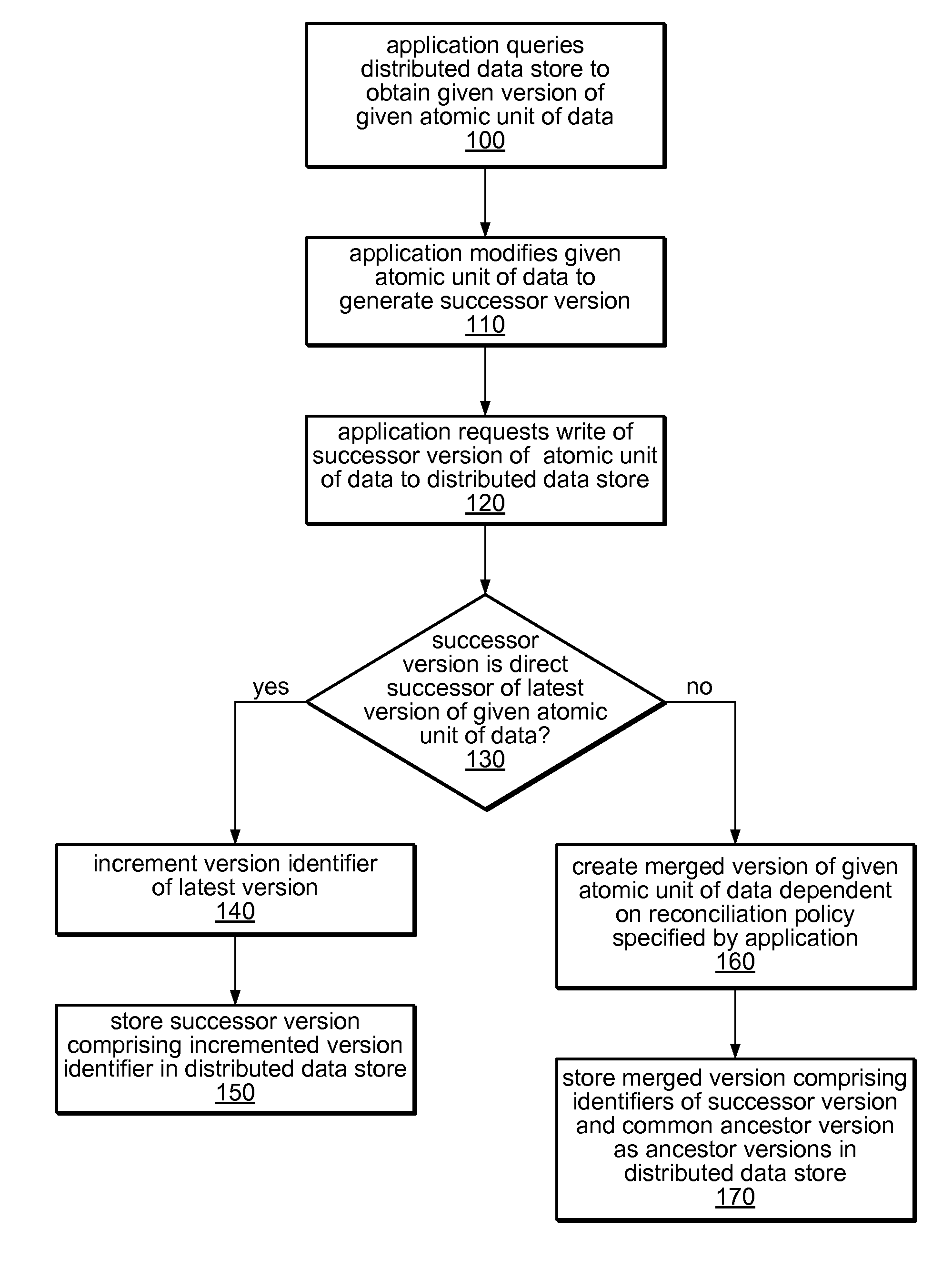
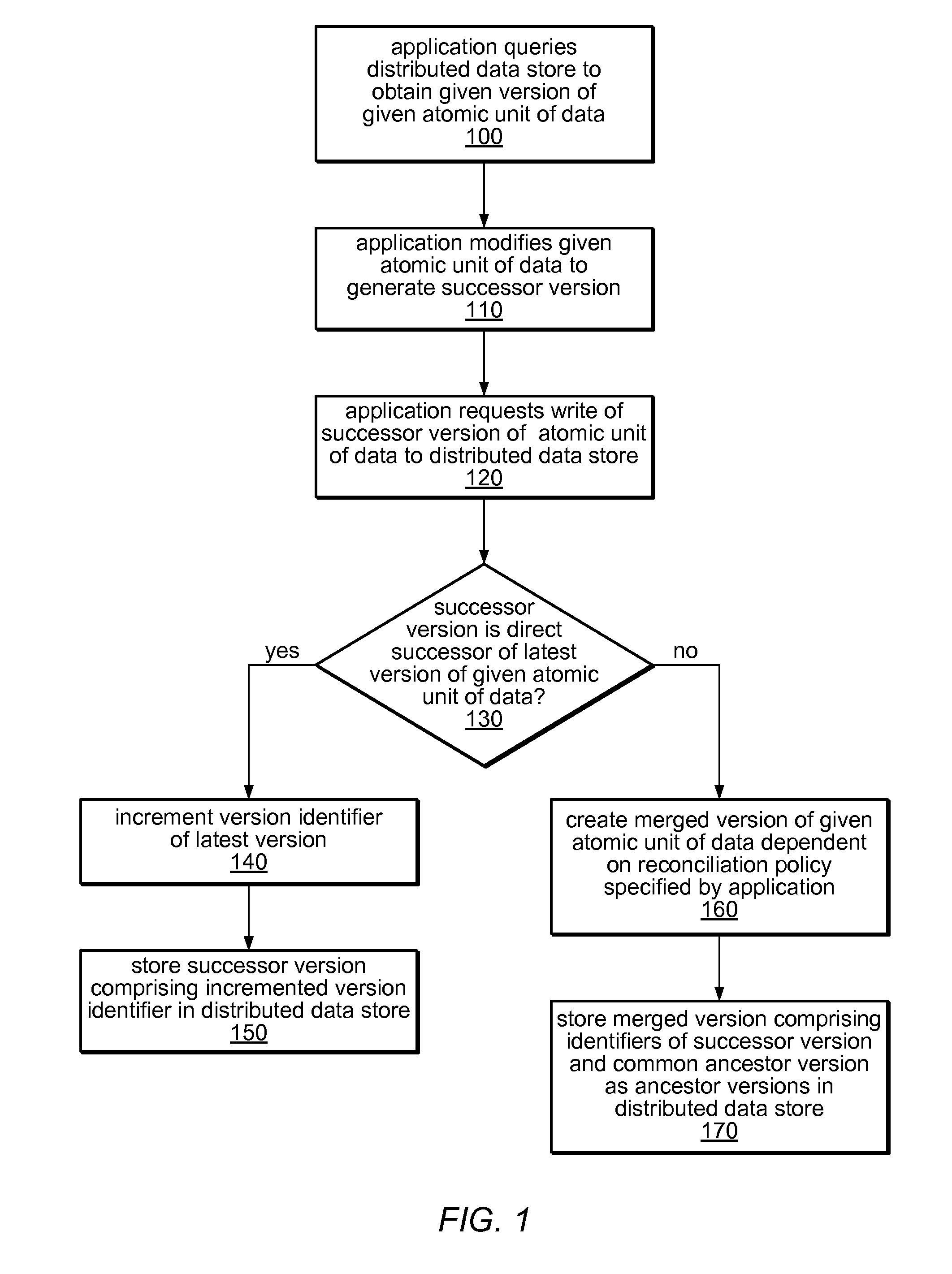
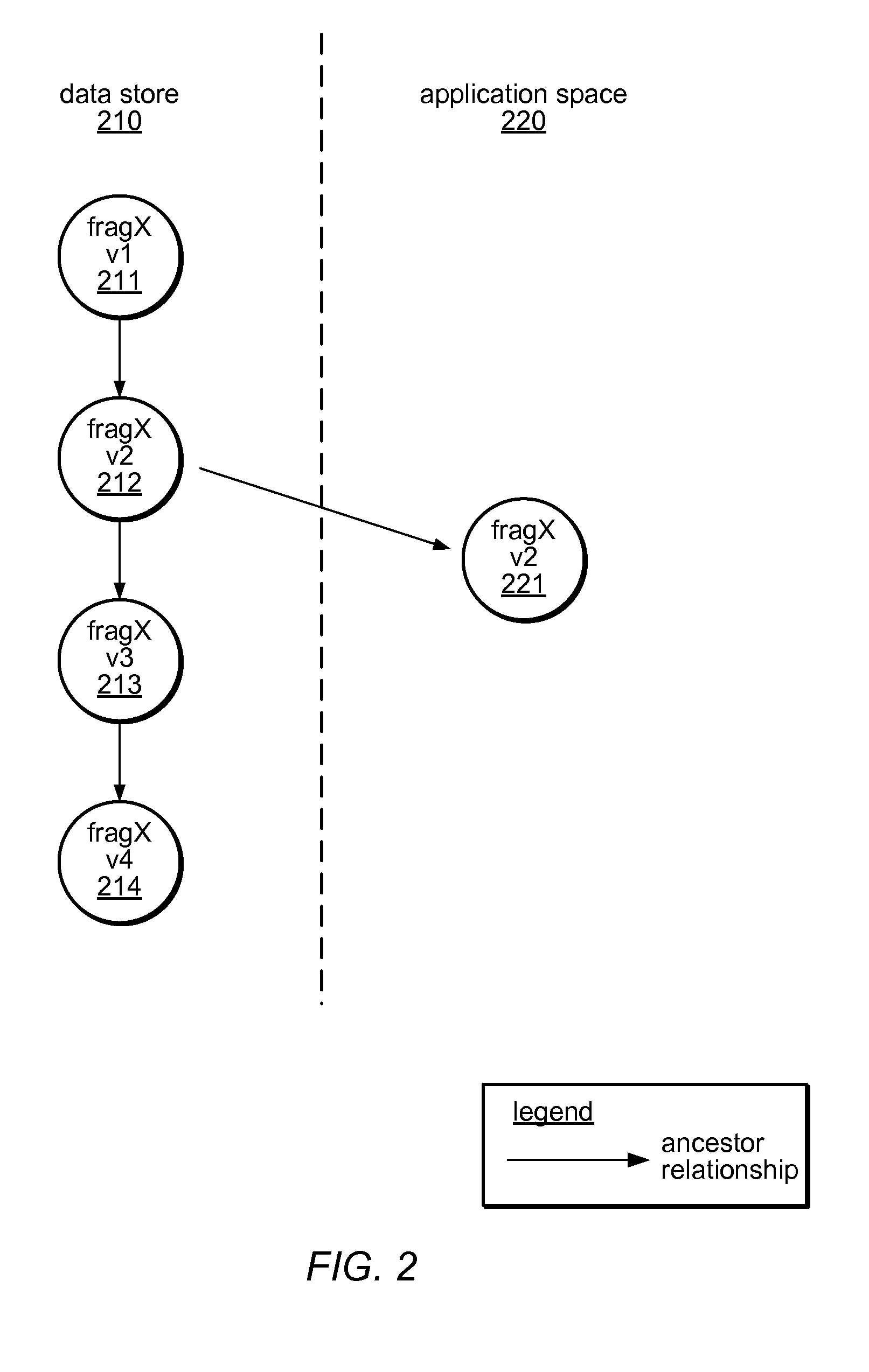
System and method for versioning data in a distributed data store
InactiveUS8266122B1Digital data processing detailsDatabase distribution/replicationApplication programming interfaceDistributed data store
A system and method for versioning of atomic units of data (such as XML fragments) in a distributed data store are disclosed. The distributed data store may maintain a linear version history for each fragment, such that each has no more than one successor and one predecessor, with no implicit branching. An application programming interface may provide an explicit branching request (indicating an intent to merge modified data in a child branch into its parent branch), along with read, create, create-merge, and / or integrate requests. A reconciliation policy may be specified on a per-application basis, and may include automatic reconciliation using a callback function or interactive reconciliation, with inputs returned to the application. Writes to a minority side of a network partition may be refused unless an explicit branch is requested. Transactions may not be supported in client applications or may be supported through explicit branching. Transactions may be used internally.
Owner:AMAZON TECH INC
Method for ensuring operation during node failures and network partitions in a clustered message passing server
ActiveUS6877107B2High degreeGuaranteed JMS conformanceError detection/correctionInterprogram communicationComputer failureMessage delivery
A means for guaranteeing the proper behavior as specified by the JMS semantics of clustered message server when the individual computer that comprise the cluster are separated by a network partition. A clustered message server is responsible for the reliable transportation of messages between different distributed computer applications. It employs multiple computers to perform a function that otherwise appears to be performed by a monolithic server running on one computer, but with more capacity and reliability than can be provided by one computer. If a computer in the cluster fails, another computer should automatically assume the role of the failed computer. However, it is not possible for the other machines in the cluster to detect the difference between the failure of one or more computers in the cluster, and the failure of data network connecting those computers. In ordinary clusters, different actions would be required in these two cases, but since they are impossible to distinguish, computer failure is always assumed and network failure is ignored and the consequence non-deterministic. The invention described here provides a means of responding to failures that yields correct behavior as specified by the JMS semantics whether the failure is due to computer failure or network failure.
Owner:TAIWAN SEMICON MFG CO LTD
Network partitioning using encryption
InactiveUS7194622B1Change the environmentSuitable environmentSecret communicationSecuring communicationVirtual LANEncryption
A system for providing a Virtual Local Area Network (VLAN) by use of an encryption states or encryption keys for identifying a VLAN. A table of data including a VLAN and an associated encryption state or key is provided for assignment of encryption states or keys, for devices in a wireless local area network.
Owner:CISCO TECH INC
Network partitioning using encryption
InactiveUS20070121565A1Key distribution for secure communicationRadio/inductive link selection arrangementsVirtual LANEncryption
In an example embodiment, a system for providing a Virtual Local Area Network (VLAN) by use of encryption states or encryption keys for identifying a VLAN. A table of data including a VLAN and an associated encryption state or key is provided for assignment of encryption states or keys, for devices in a wireless local area network.
Owner:CISCO TECH INC
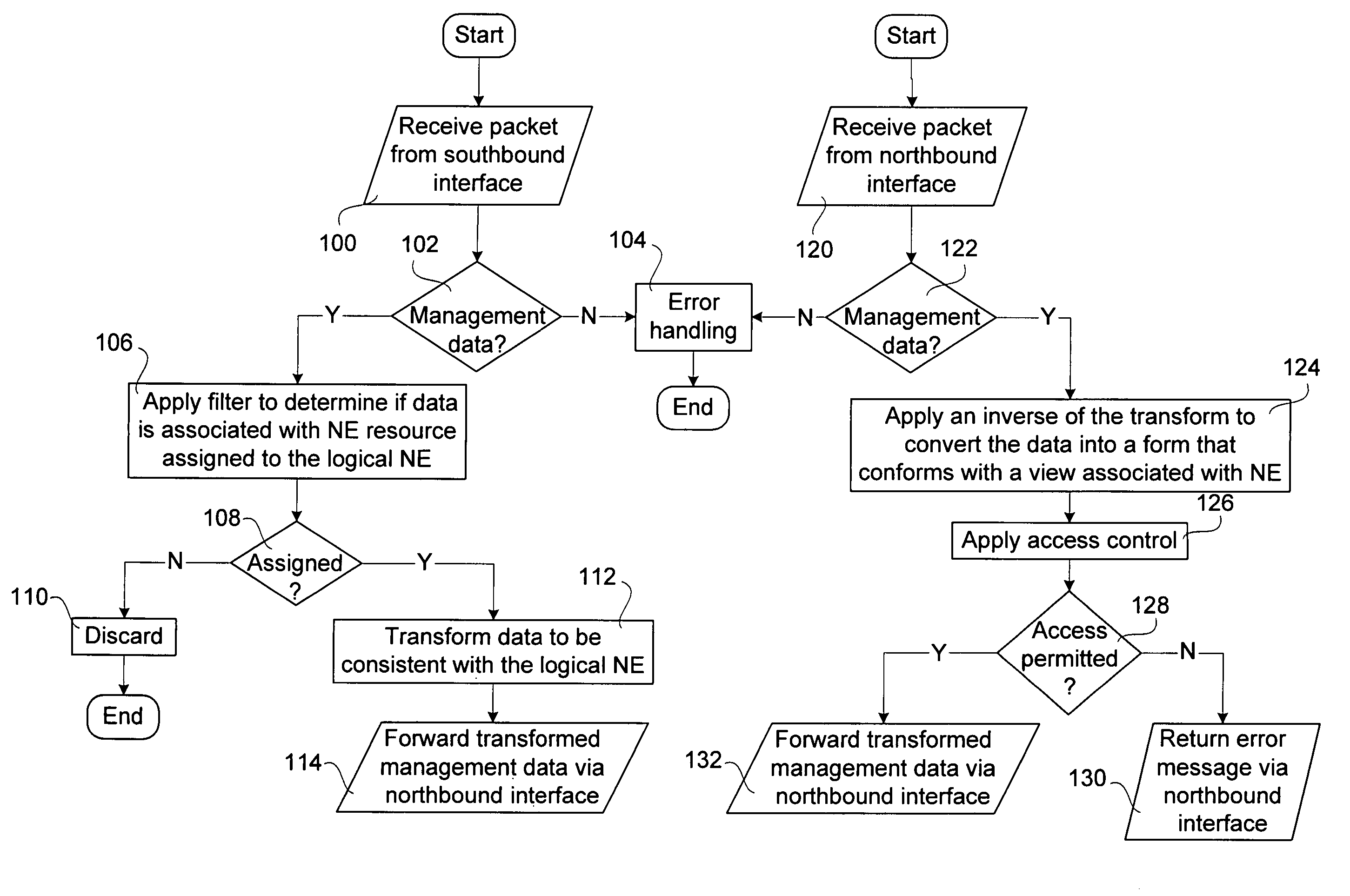
Method and apparatus for efficient communication of management data in a telecommunications network
InactiveUS7925727B2Valid reportDigital data processing detailsMultiple digital computer combinationsTelecommunications networkElement management system
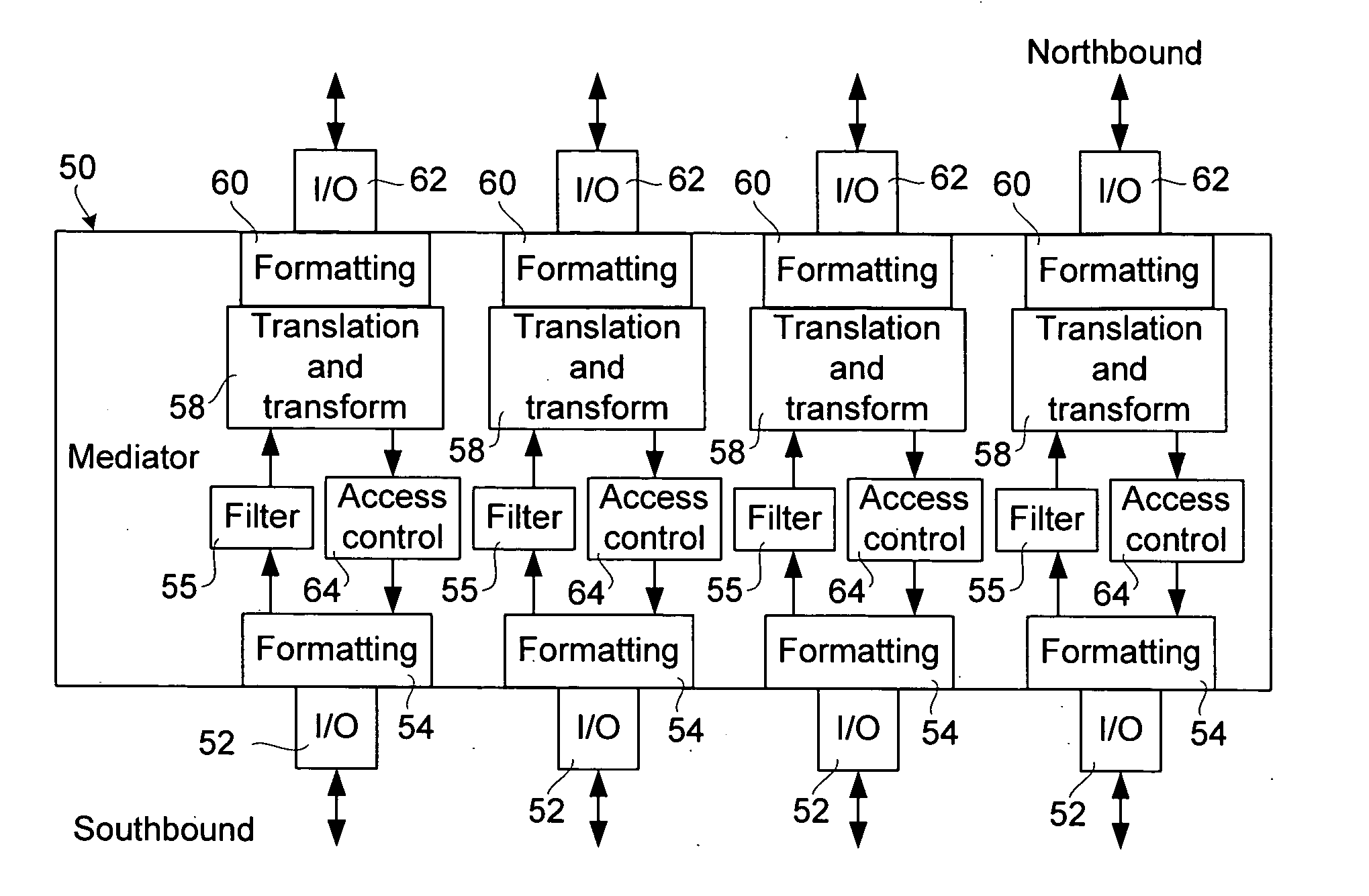
A mediator for efficiently exchanging management data in a hierarchical management network for managing network elements of a data transport network partitions resources of the network elements among a plurality of management representations of the network elements and selectively forwards management data associated with respective management representations to a higher level of the hierarchy. The mediator modifies the management data so that the higher level (i.e. a northbound element management system or a network management system) receives the management data in a view consistent with the management representation of the network element. Client-based management representations may be created to permit clients to manage selected resources of a network element, and testing-based management representations may be created to facilitate concurrent testing of a network element.
Owner:RPX CLEARINGHOUSE
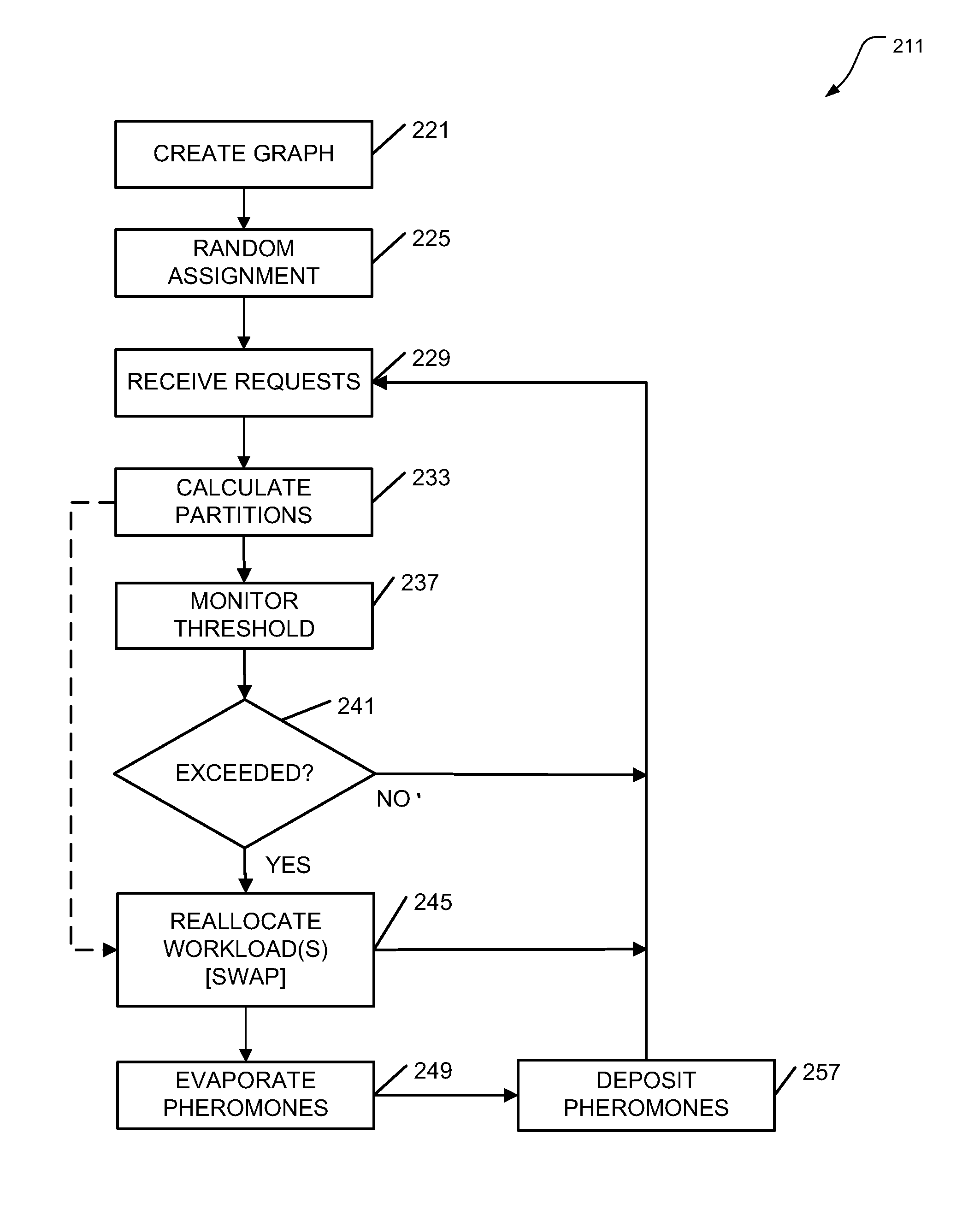
Autonomous intelligent workload management
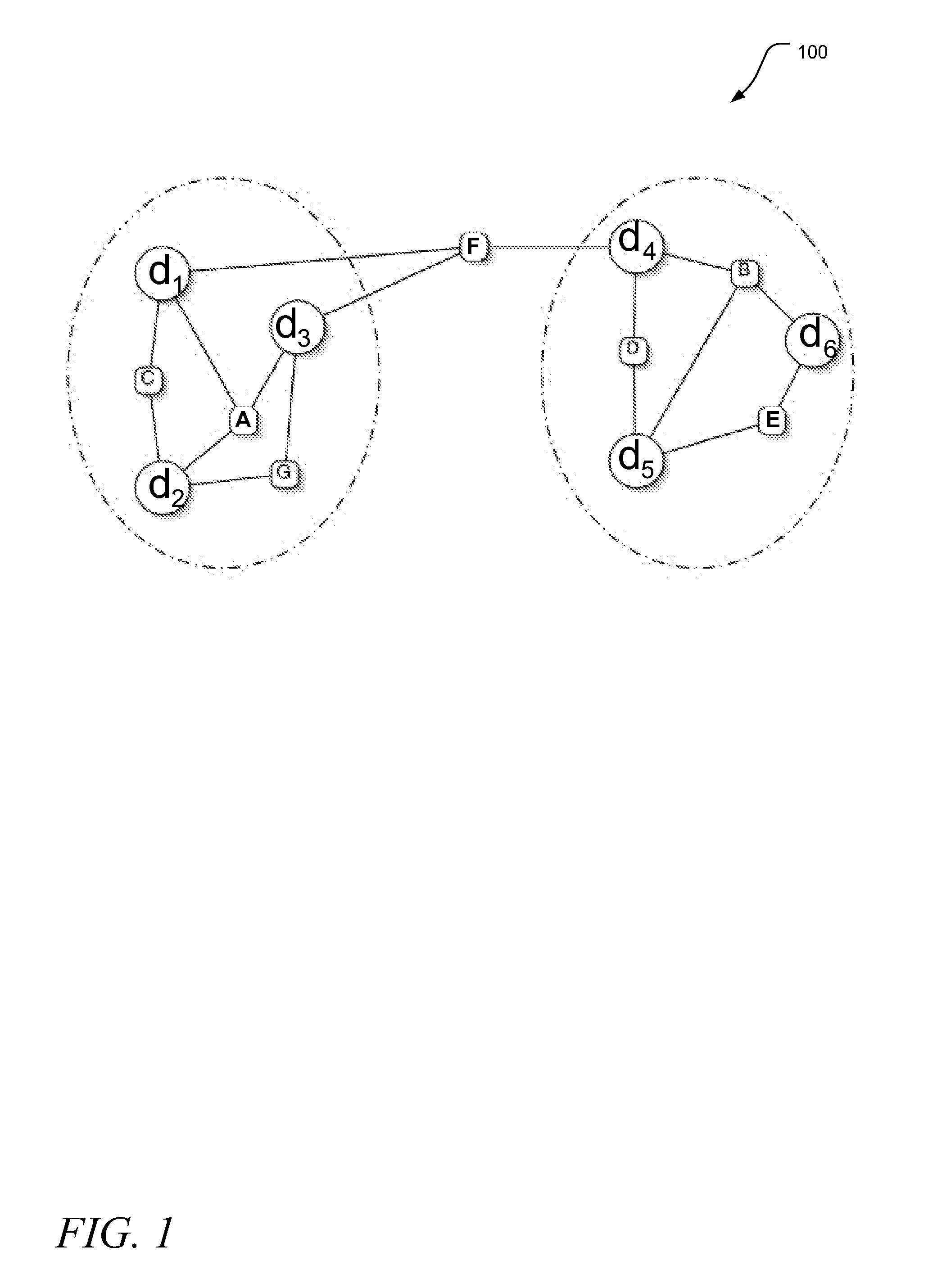
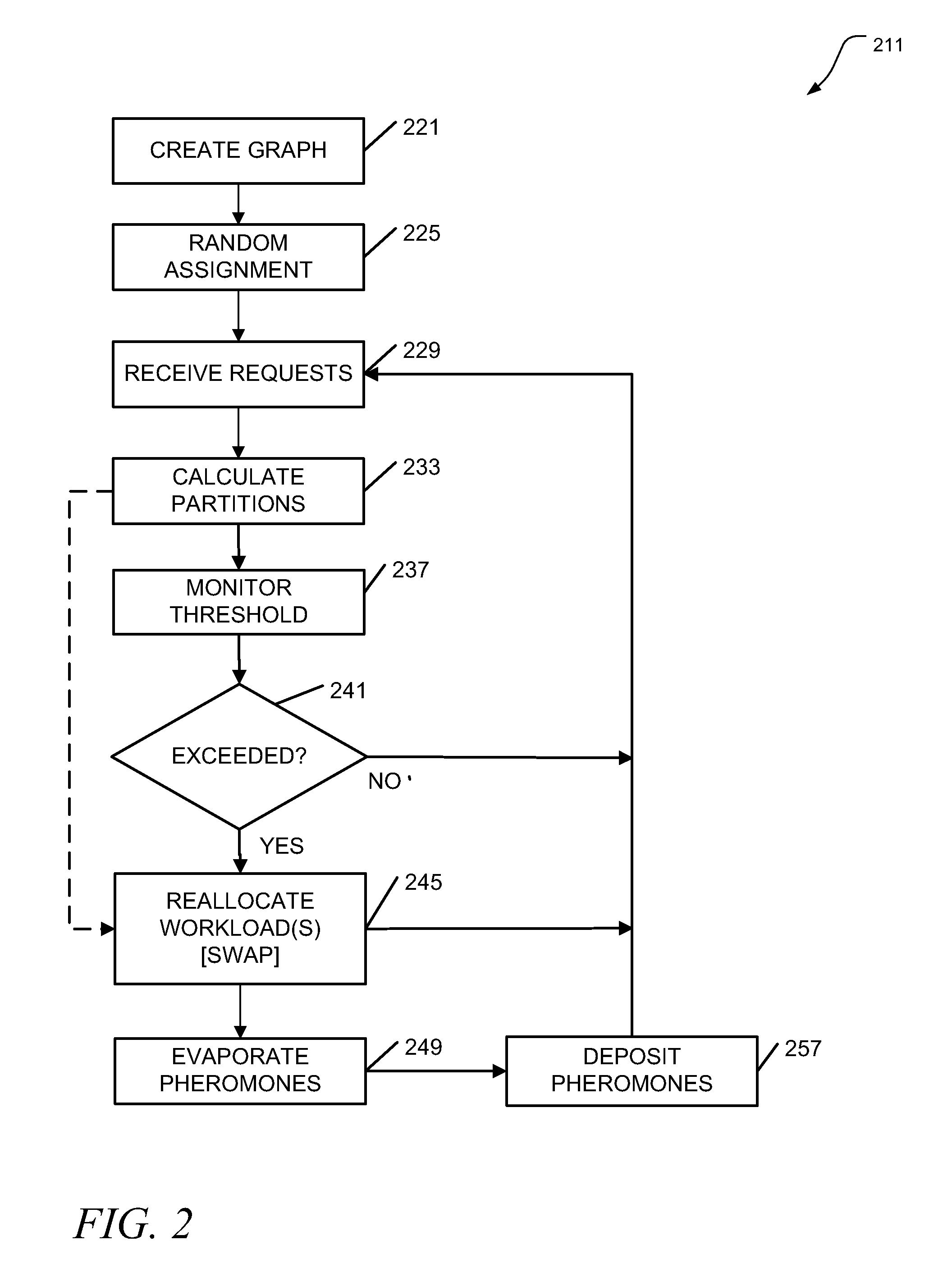
Apparatus, systems, and methods may operate to create a hypergraph of weighted vertices comprising computing resources and storage resources, and nets comprising workloads; to receive a plurality of requests to be addressed by a network associated with the hypergraph, at least some of the requests associated with data objects; to calculate partition schemes for the network based on the requests and the data objects according to an ant colony optimization heuristic; and to autonomously reallocate the workloads to the computing resources and / or the storage resources according to the partition schemes. The workloads may act as ants following a path defined by the vertices of the hypergraph. Further activities may thus include depositing pheromones along hyperedges of the hypergraph, wherein the hyperedges are used for swapping the vertices between the workloads. Additional apparatus, systems, and methods are disclosed.
Owner:MICRO FOCUS SOFTWARE INC
Highly scalable and highly available cluster system management scheme
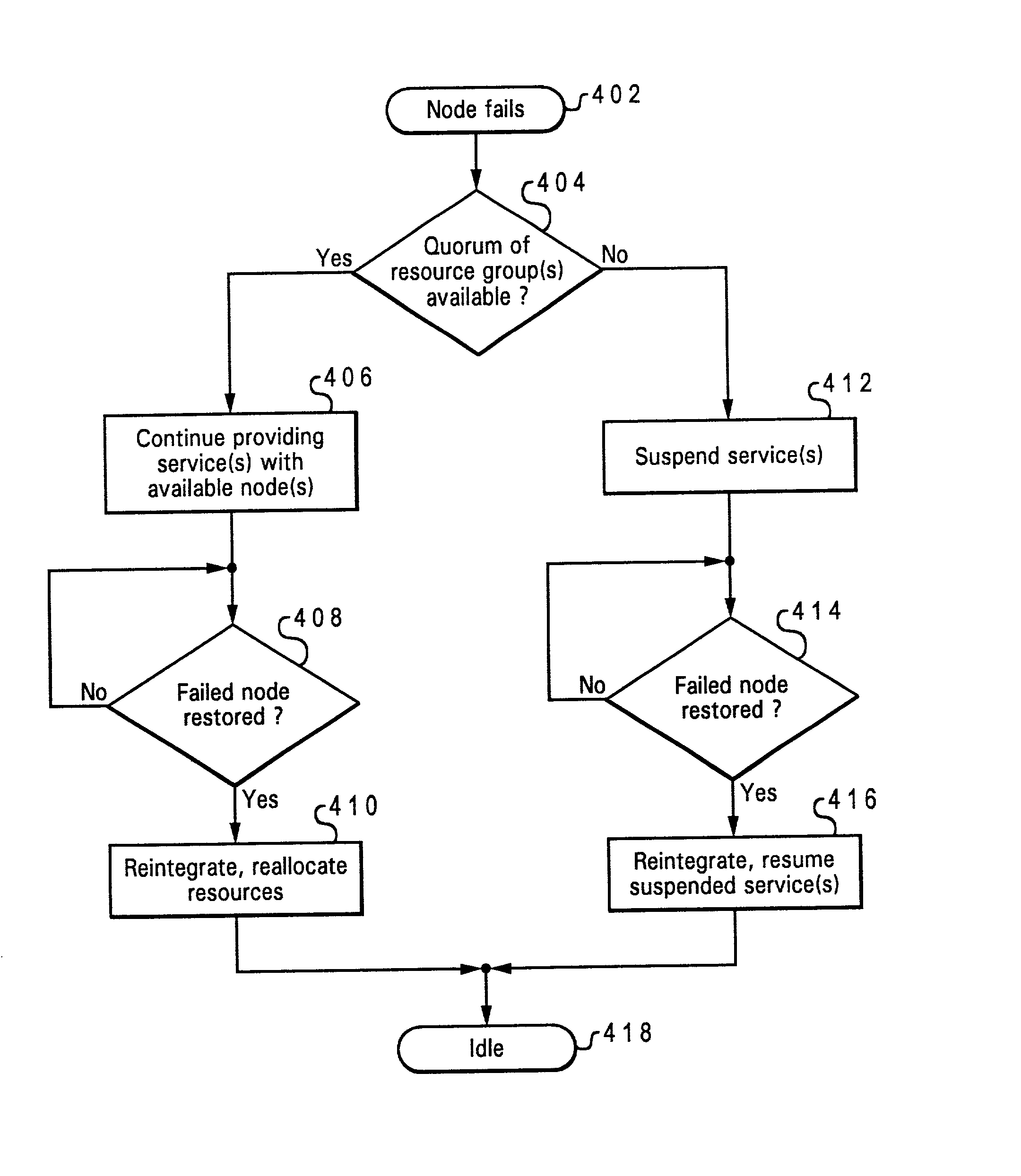
InactiveUS20020091814A1Low costImprove scalabilityError detection/correctionMultiple digital computer combinationsData processing systemCluster systems
A cluster system is treated as a set of resource groups, each resource group including an highly available application and the resources upon which it depends. A resource group may have between 2 and M data processing systems, where M is small relative to the cluster size N of the total cluster. Configuration and status information for the resource group is fully replicated only on those data processing systems which are members of the resource group. A configuration object / database record for the resource group has an associated owner list identifying the data processing systems which are members of the resource group and which may therefore manage the application. A data processing system may belong to more than one resource group, however, and configuration and status information for the data processing system is replicated to each data processing system which could be affected by failure of the subject data processing system-that is, any data processing system which belongs to at least one resource group also containing the subject data processing system. The partial replication scheme of the present invention allows resource groups to run in parallel, reduces the cost of data replication and access, is highly scalable and applicable to very large clusters, and provides better performance after a catastrophe such as a network partition.
Owner:BLUECAT NETWORKS USA
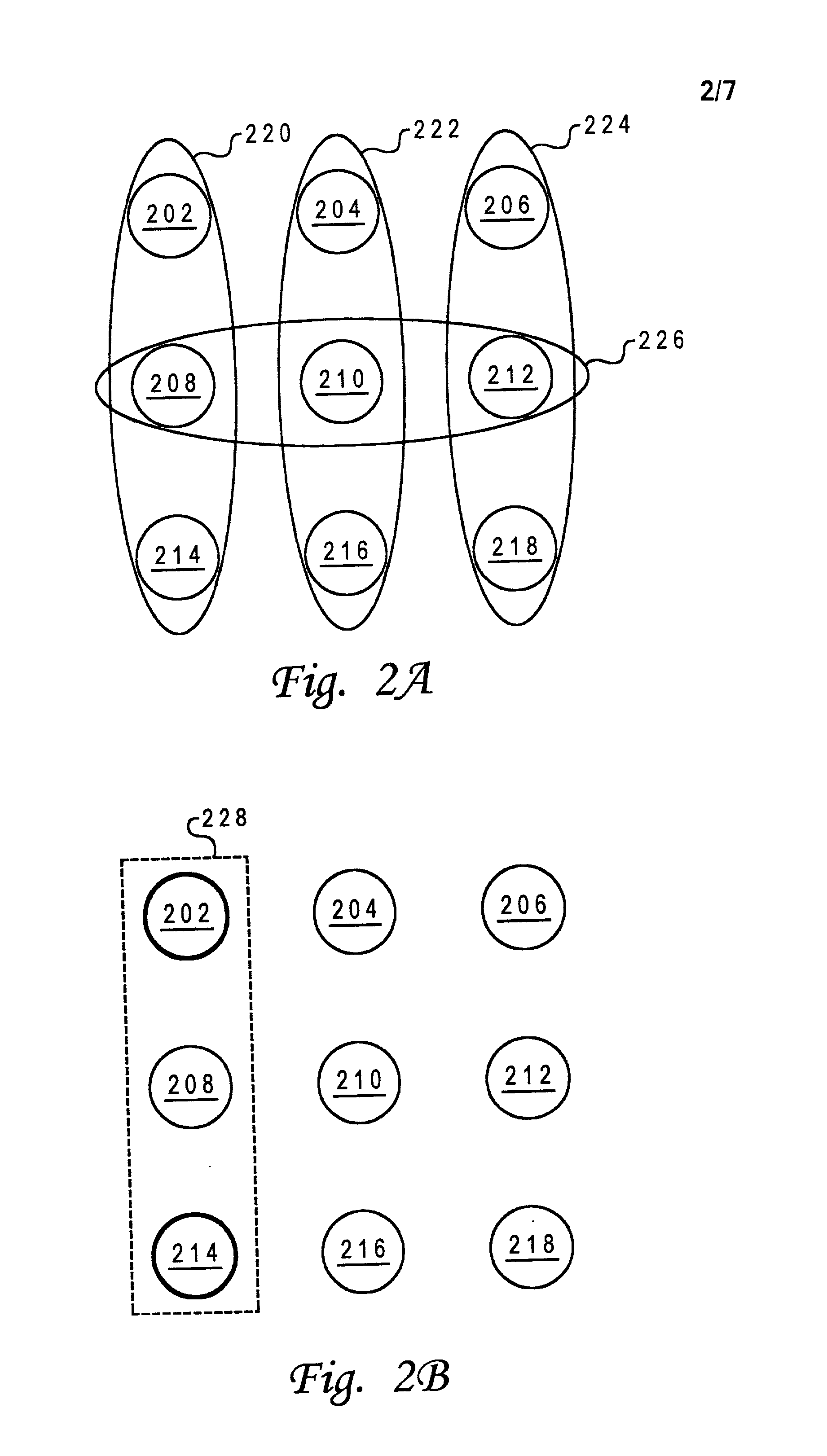
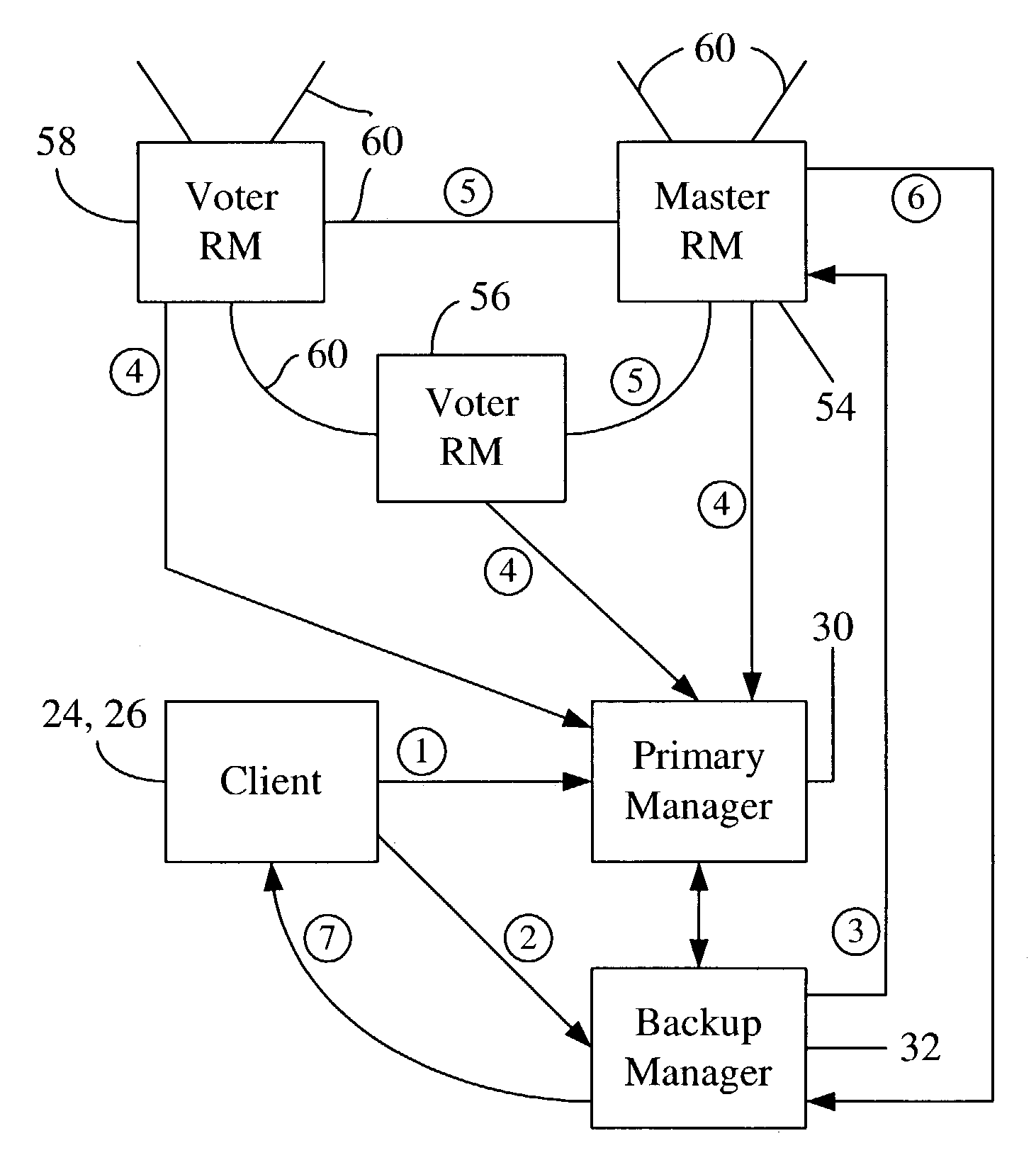
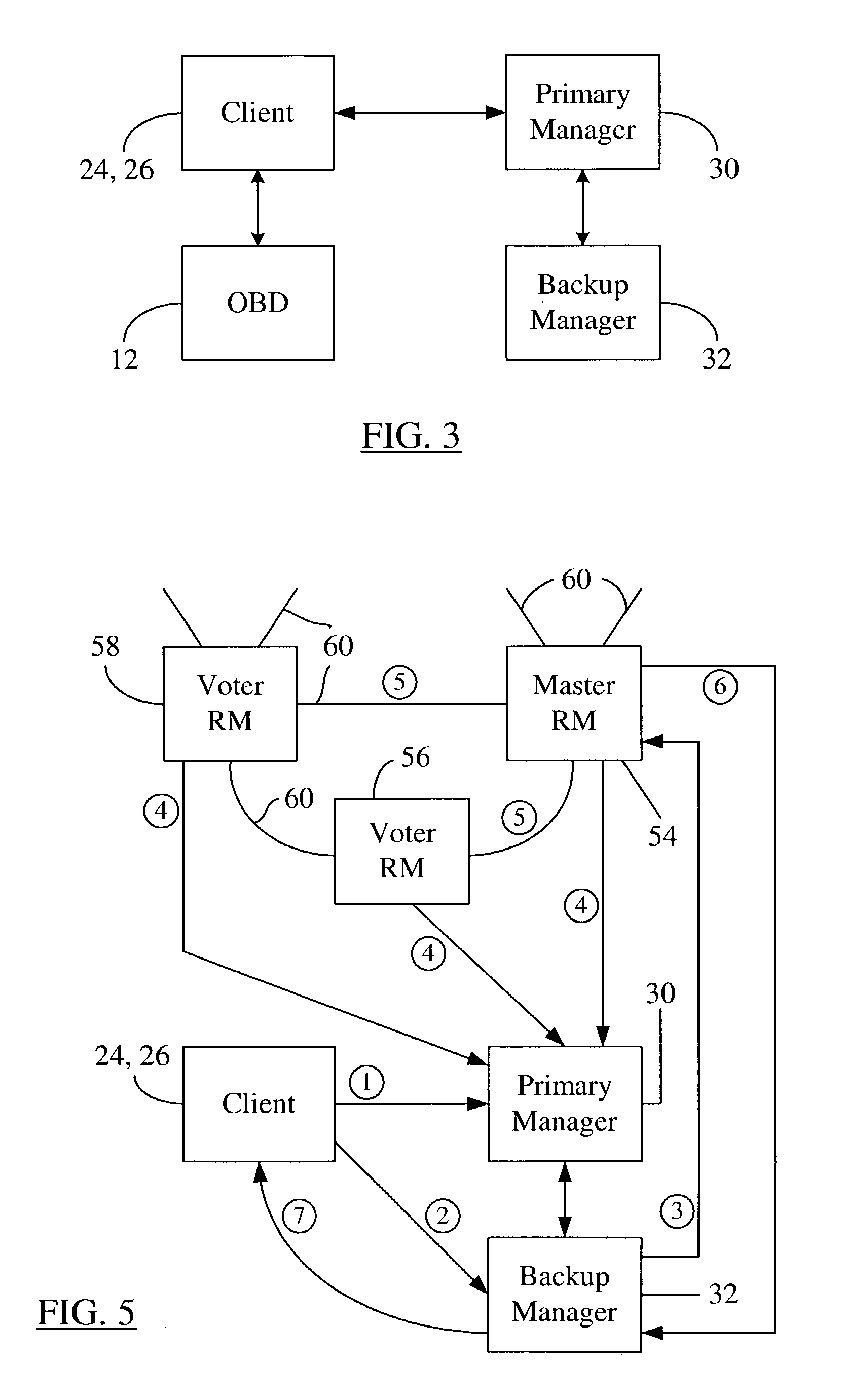
Hybrid quorum/primary-backup fault-tolerance model
ActiveUS7191357B2Functional performanceObject oriented databasesMultiprogramming arrangementsFault toleranceObject based
A hybrid quorum / consensus and primary-backup fault-tolerance model in an object-based distributed data storage system. When a primary manager fails, a hierarchy of network entities is established in which a group of realm managers first authorizes a failure-handling event through quorum / consensus and a backup manager (for the failing primary manager) then executes the decision of the quorum of realm managers. The realm managers, operating by consensus, determine whether (a) the primary manager can indeed be asserted to be down, and (b) whether there is a quorum of realm managers in agreement on this decision. If both are true, a master realm manager instructs the backup manager to proceed to execute the necessary steps to become the primary manager and function as the primary until the original primary manager is brought back into service. The hybrid fault-tolerance approach handles both single unit failures and network partitions in a unified way, without creating a single cluster out of the fault domain.
Owner:PANASAS INC
Quorum disk-based non-interrupted operation method for high availability system
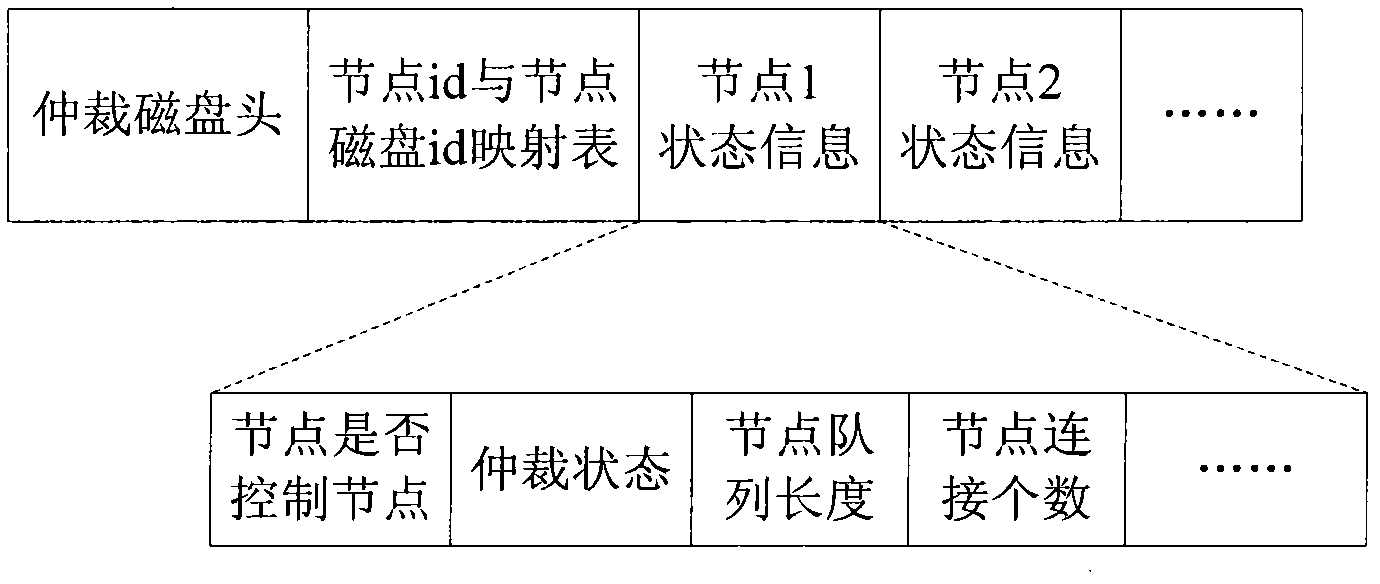
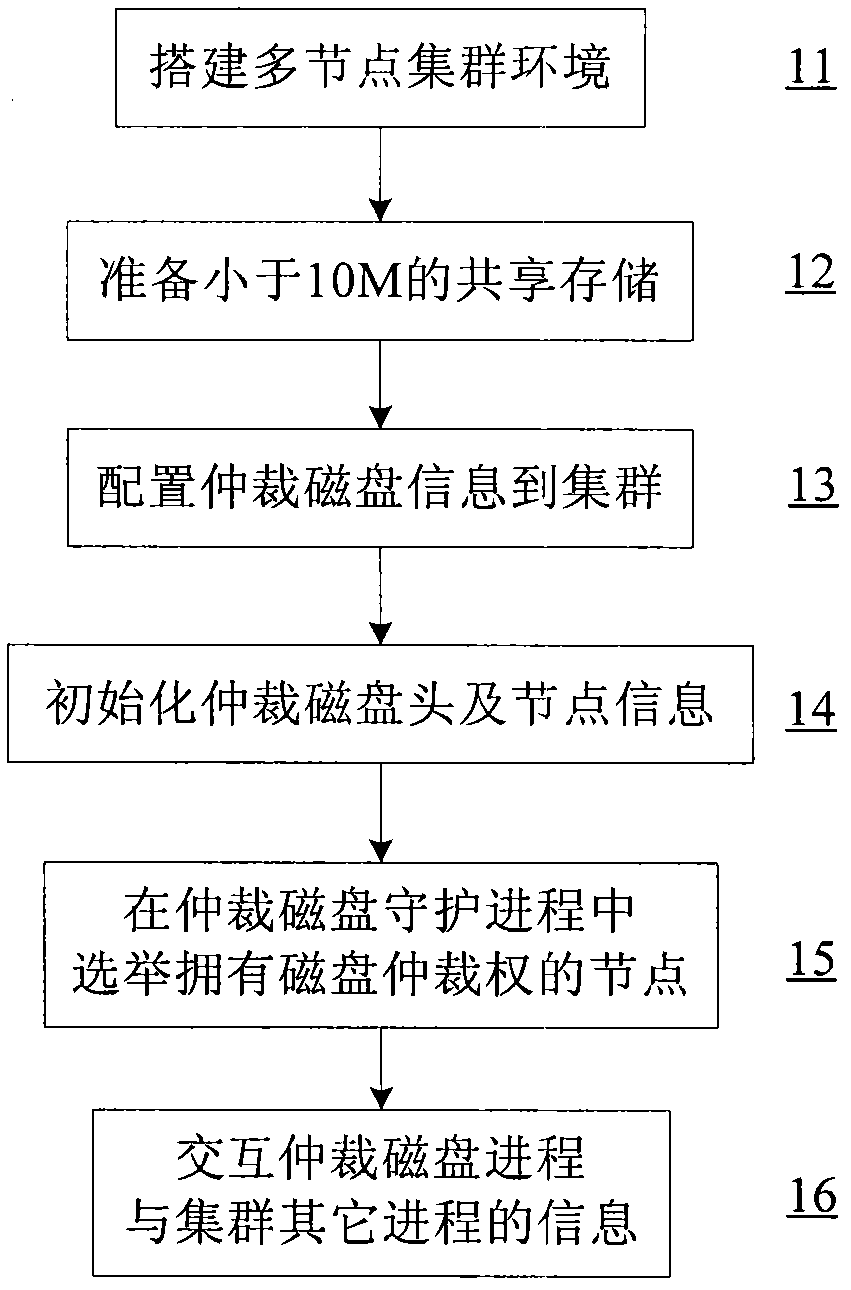
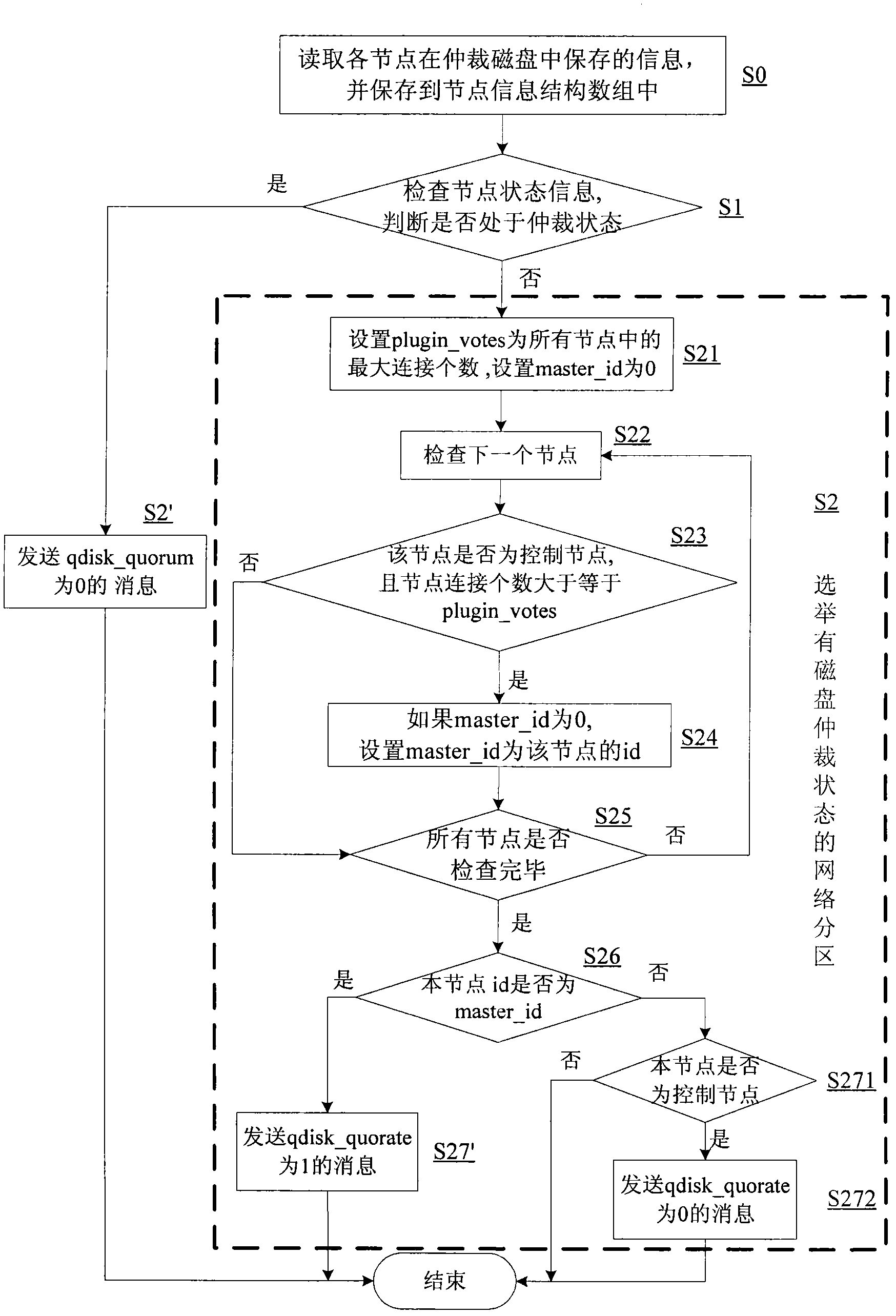
ActiveCN102402395AImprove service efficiencyInput/output to record carriersDigital computer detailsCluster systemsHigh availability
The invention discloses a method for non-interrupted operation of a high availability system through a technology of interacting information by a magnetic disk. For a multi-node high availability cluster system with shared storage equipment, a small space of a shared storage is used as a quorum disk. Various high availability nodes can simultaneously read and write the quorum disk; a quorum disk daemon process of each node writes state information of the node into the quorum disk, and detects stored information of all nodes in the quorum disk, and when nodes fail and network partition occurs, a main control node of the whole cluster is intelligently selected from normally working nodes, so that the cluster system restores a normal working state; therefore, split-brain of the high availability system is avoided and the non-interrupted normal operation of the high availability system is ensured.
Owner:CHINA STANDARD SOFTWARE
Method and apparatus for efficient communication of management data
InactiveUS20060026272A1Valid reportDigital data processing detailsMultiple digital computer combinationsElement management systemData transport
A mediator for efficiently exchanging management data in a hierarchical management network for managing network elements of a data transport network partitions resources of the network elements among a plurality of management representations of the network elements and selectively forwards management data associated with respective management representations to a higher level of the hierarchy. The mediator modifies the management data so that the higher level (i.e. a northbound element management system or a network management system) receives the management data in a view consistent with the management representation of the network element. Client-based management representations may be created to permit clients to manage selected resources of a network element, and testing-based management representations may be created to facilitate concurrent testing of a network element.
Owner:RPX CLEARINGHOUSE
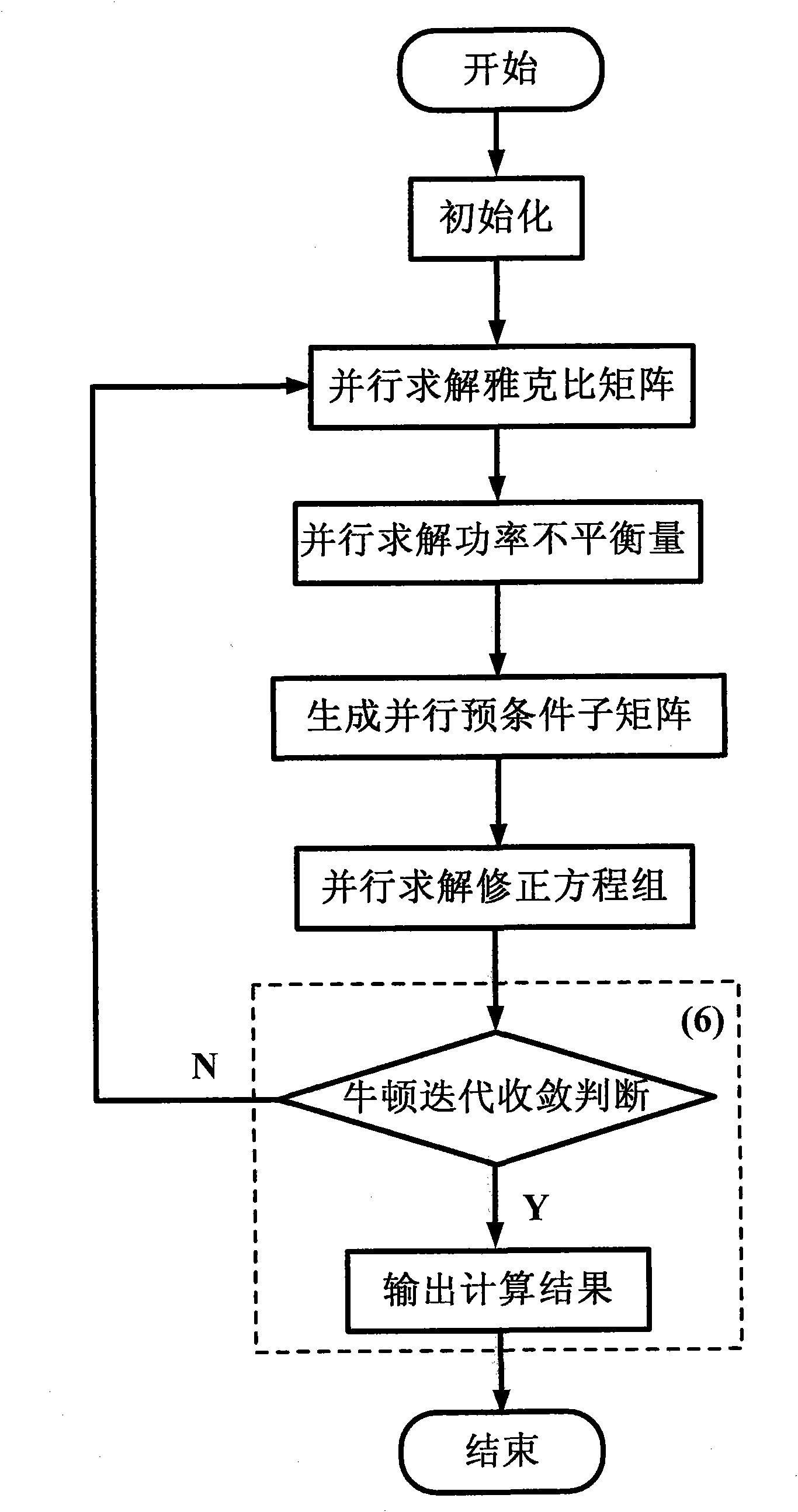
Parallel computation method for Newton power flow of large-scale electric power system
ActiveCN101976835ASimple calculationImprove versatilityAc network circuit arrangementsPower flowParallel computing
The invention discloses a parallel computation method for Newton power flow of a large-scale electric power system, which belongs to the technical field of safe analysis and computation of electric power systems. A modified equation set of the Newton power flow is resolved by using a computer according to a parallel cluster through a program in combination with parallelization technology for updating a Jacobian matrix by a generalized minimal residual method combined with a quasi-diagonal parallel preconditioner so as to realize parallelization of a power flow resolving process of the large-scale electric power system. The method does not need network partitioning in any form and has simple computation and high generality; a forward / backward sweeping dependency relationship does not exist inside an algorithm, and parallel efficiency and computation speed are high; and computation can be performed by the common parallel computer and the parallel cluster and the method is convenient to popularize and apply, and the like. The method can be applied to the parallel power flow computation of the electric power system and is particularly suitable for the parallel computation of the Newton power flow of a large-scale complex electric power system.
Owner:CHONGQING UNIV
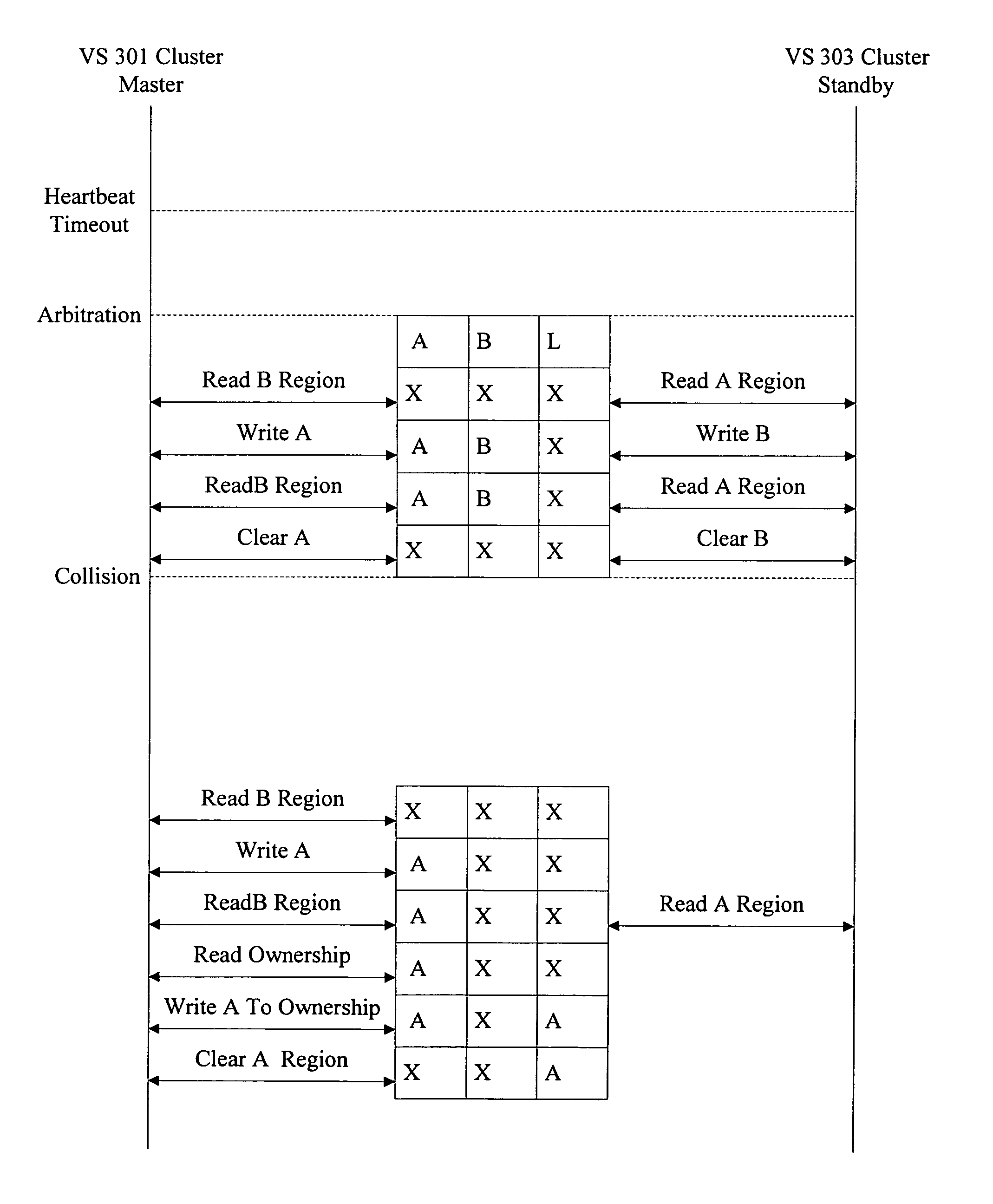
Arbitration of disk ownership in a storage pool
InactiveUS20130227009A1Multiple digital computer combinationsFile access structuresS/KEYStorage pool
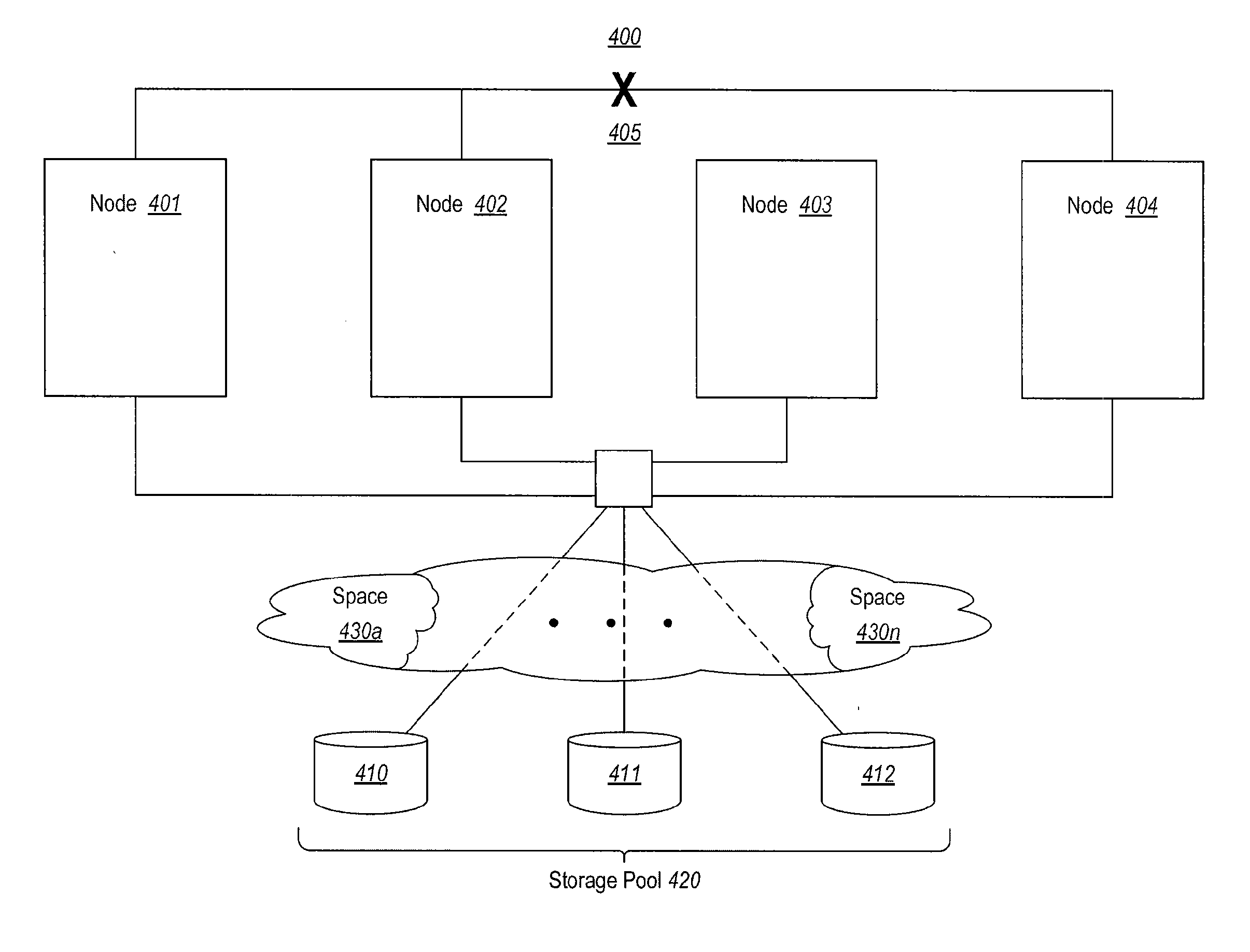
The present invention extends to methods, systems, and computer program products for implementing persistent reservation techniques for establishing ownership of one or more physical disks. These persistent reservation techniques can be employed to determine ownership of physical disks in a storage pool as well as in any other storage configuration. Using the persistent reservation techniques of the present invention, when a network partition occurs, a defender of a physical disk does not remove a challenger's registration key until the defender receives notification that the challenger is no longer in the defender's partition. In this way, pending I / O from applications executing on the challenger will not fail due to the challenger's key being removed until the proper ownership of the physical disk can be resolved.
Owner:MICROSOFT TECH LICENSING LLC
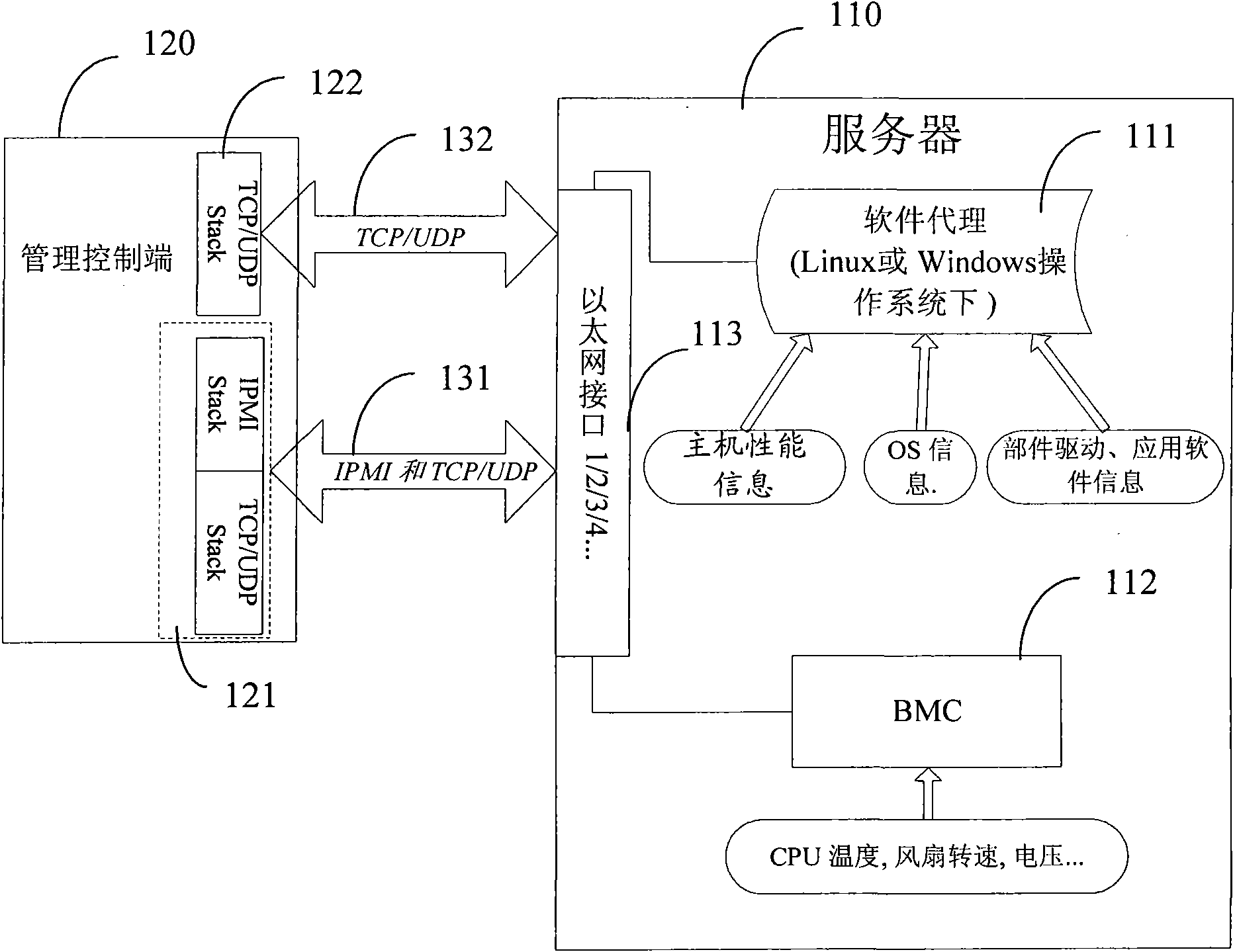
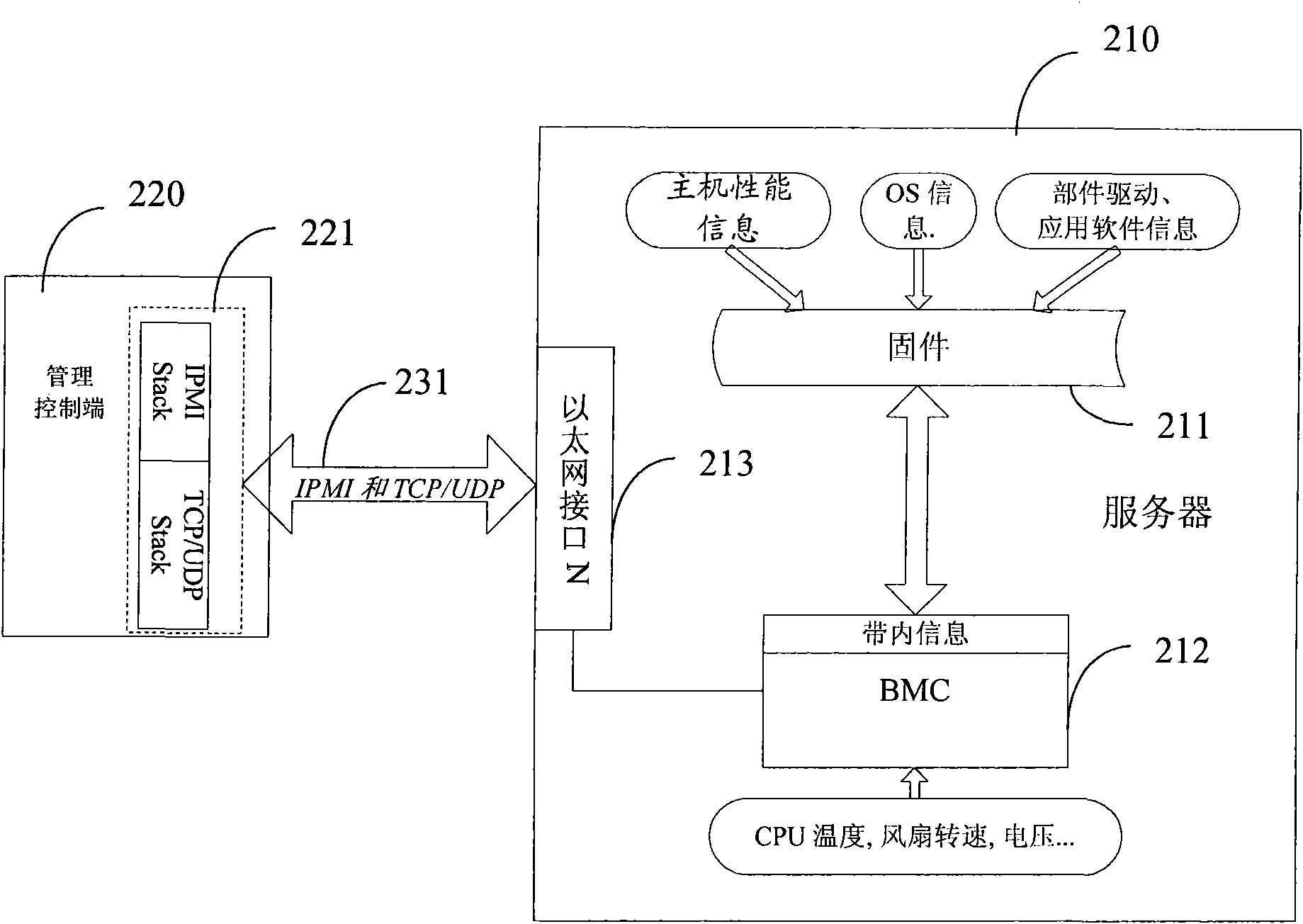
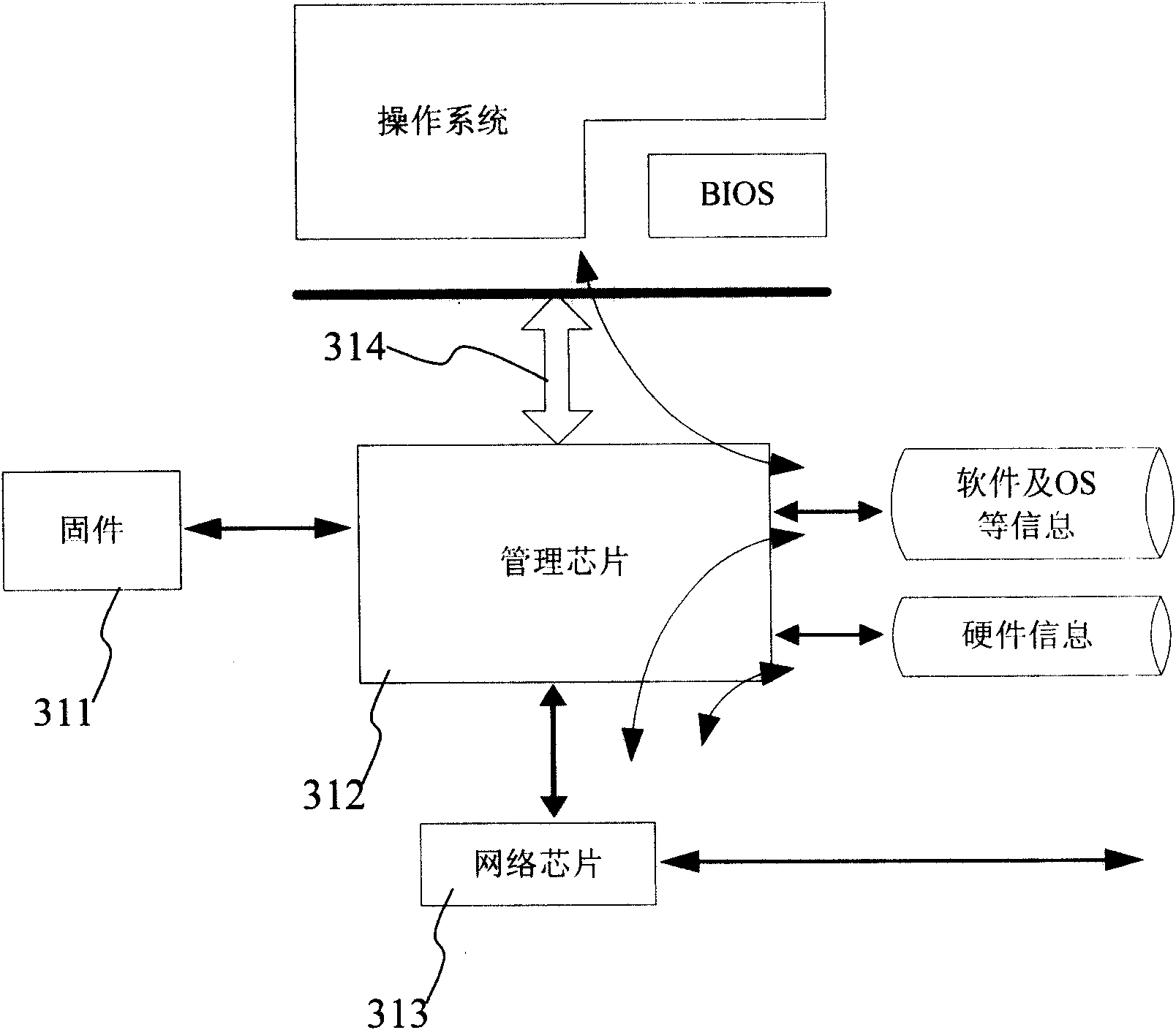
Method for monitoring server and server adopting same
InactiveCN101540694AReduce installation hassleSimplify writingHardware monitoringData switching networksInterface protocolSoftware
The invention provides a method for monitoring a server and the server adopting the same. The server comprises a main board management controller and firmware arranged in the main board management controller; the firmware performs loaded operation after the server operates so as to acquire the in-band information of the server; and the main board management controller is used for acquiring the out-band information of the server. The server is unnecessarily installed with agent software, thereby reducing installation trouble; the management controller acquires the monitoring information only by an out-band interface and unnecessarily supports the in-band interface protocol, so that the software on the management control end can be easily written, and when the software is installed, the network partition is unnecessary; and the in-band and out-band information can be sent to the management control end by a uniform network interface, so work load for installing the software is reduced.
Owner:LENOVO (BEIJING) LTD
High availability for intelligent applications in storage networks
Methods and apparatus provide formation and management of intelligent application clusters in a storage area network. Disk arbitration mechanisms ensure that a cluster is owned by a single member. In the event of a network partition, each cluster member involved arbitrates to gain ownership of a cluster. High availability mechanisms allow monitoring of system resources and effective failover capabilities.
Owner:CISCO TECH INC
Automatic lattice dividing method for analyzing multiple antenna and scatterer structure by method of moment
InactiveCN1858937AFast operationGood binning qualityElectromagentic field characteristicsIndependent non-interacting antenna combinationsStructure analysisGeometric modeling
This invention discloses an automatic dividing method for networks to a multi-antenna-scattered structure with a moment method, which carries out three times of network partition to the dispersion surface on the basis of setting up geometrical models, firstly, it neglects antennas connected by the scatterer surfaces to apply a recursive dichotomy to divide the surface of the scatterer into triangles and quadrangles surface elements, secondly, it considers the antenna of the scatterer surface and divides the divided triangle and the quadrangle surface elements again into a square element with the line-surface link points at the center of the quadrangle, several triangles without line-surface link points and quadrangles in terms of different positions of the line-surface link points, thirdly, carries out network dividing to the narrow and long elements to get triangles and quadrangles even smaller than those of last two times.
Owner:XIDIAN UNIV
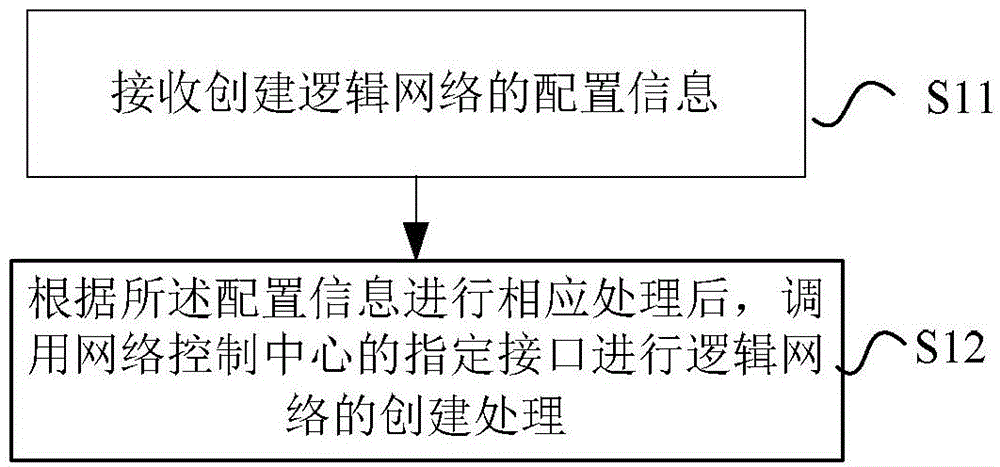
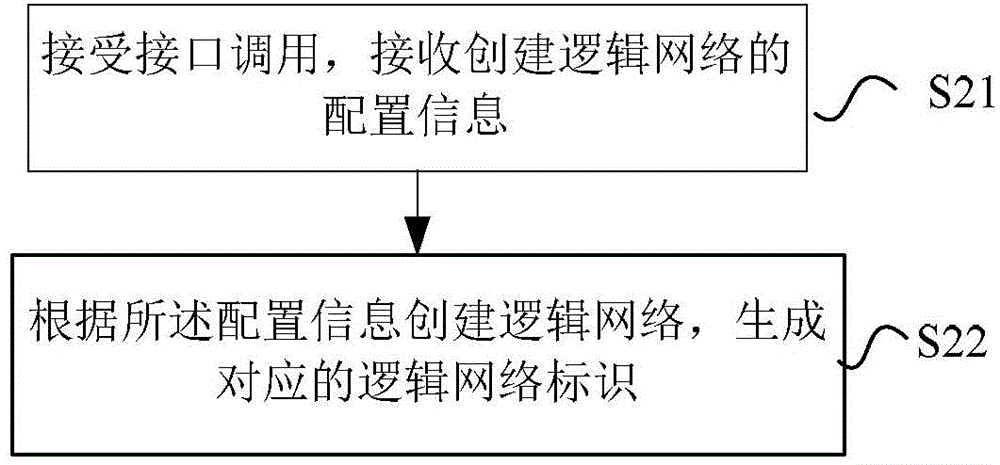
Network establishment method and system, and network control center
ActiveCN103607432AImprove automation performanceGranularityTransmissionStrategy executionNetwork control
The invention provides a network establishment method and a system, and a network control center. The method comprises the following steps of receiving configuration information used for establishing a logic network; according to the configuration information, after corresponding processing is performed, calling an assigned interface of the network control center to carry out establishment processing of the logic network. Through the method, the system and the network control center of the invention, the private and isolated logic network is established for different users; according to distribution of calculating resources owned by the user, network partition and connection are completed; network configuration is uniformly performed and strategy execution is controlled; a QOS demand needed by the user is satisfied and flexible expansion can be performed according to a need.
Owner:NANJING ZHONGXING SOFTWARE
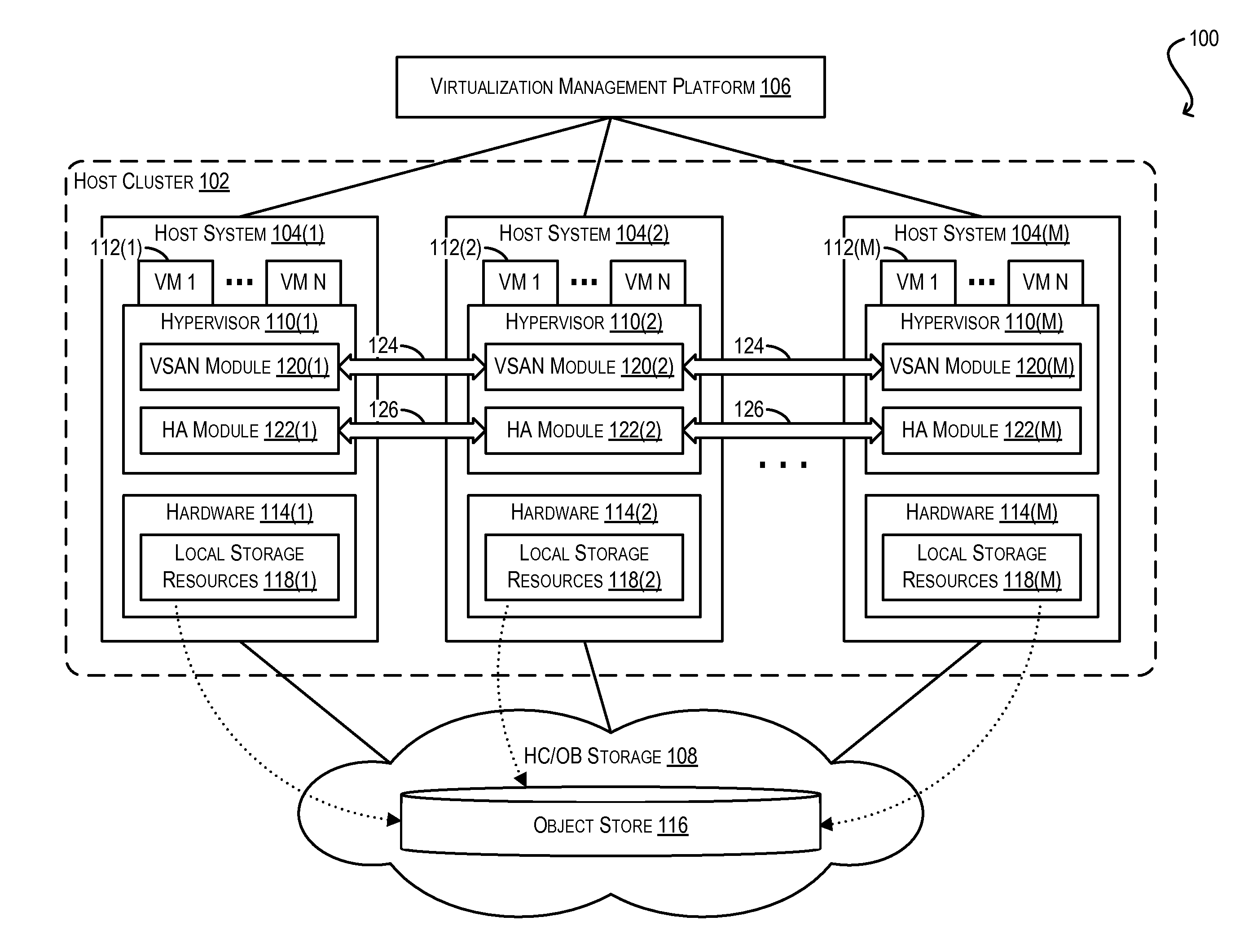
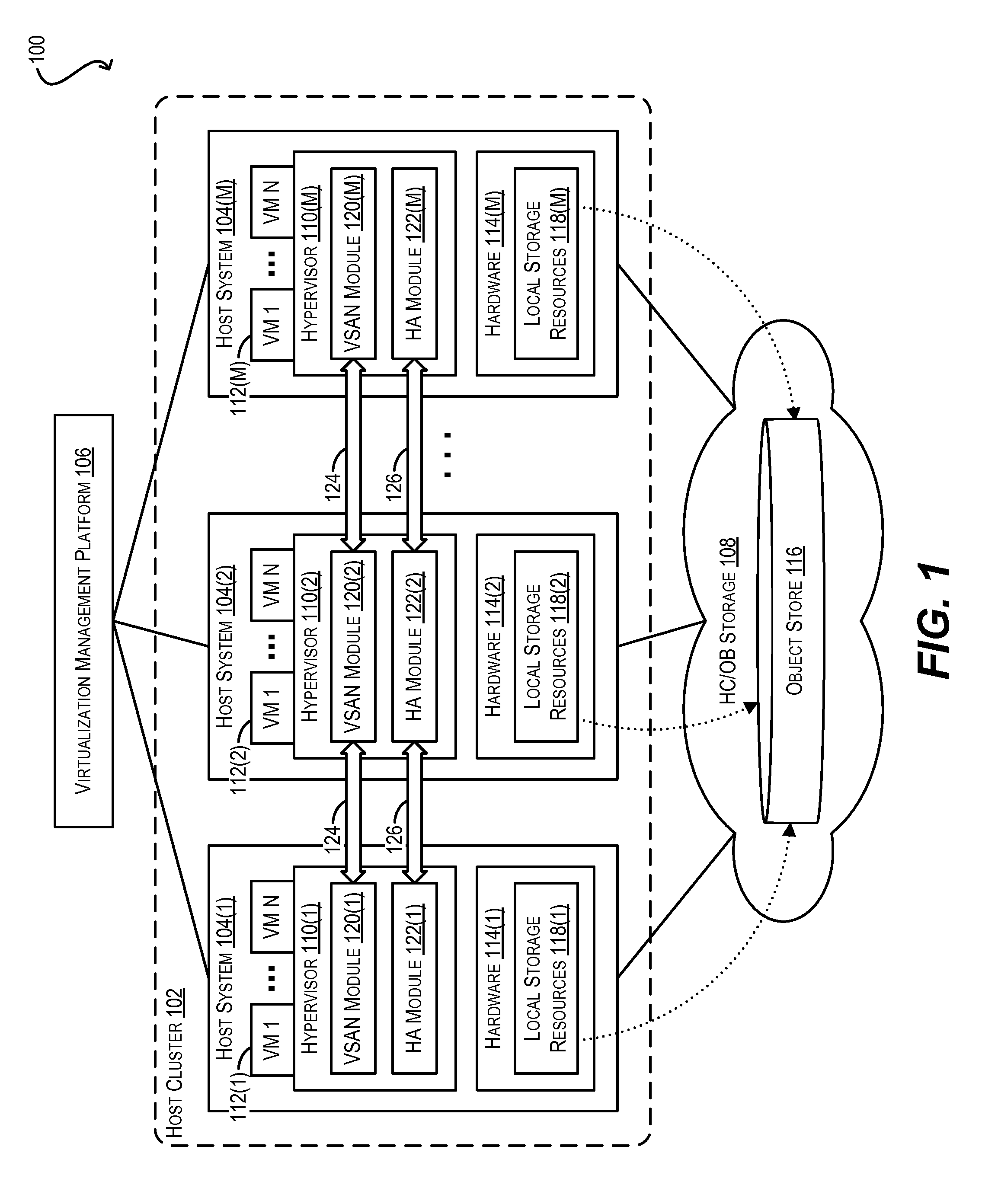
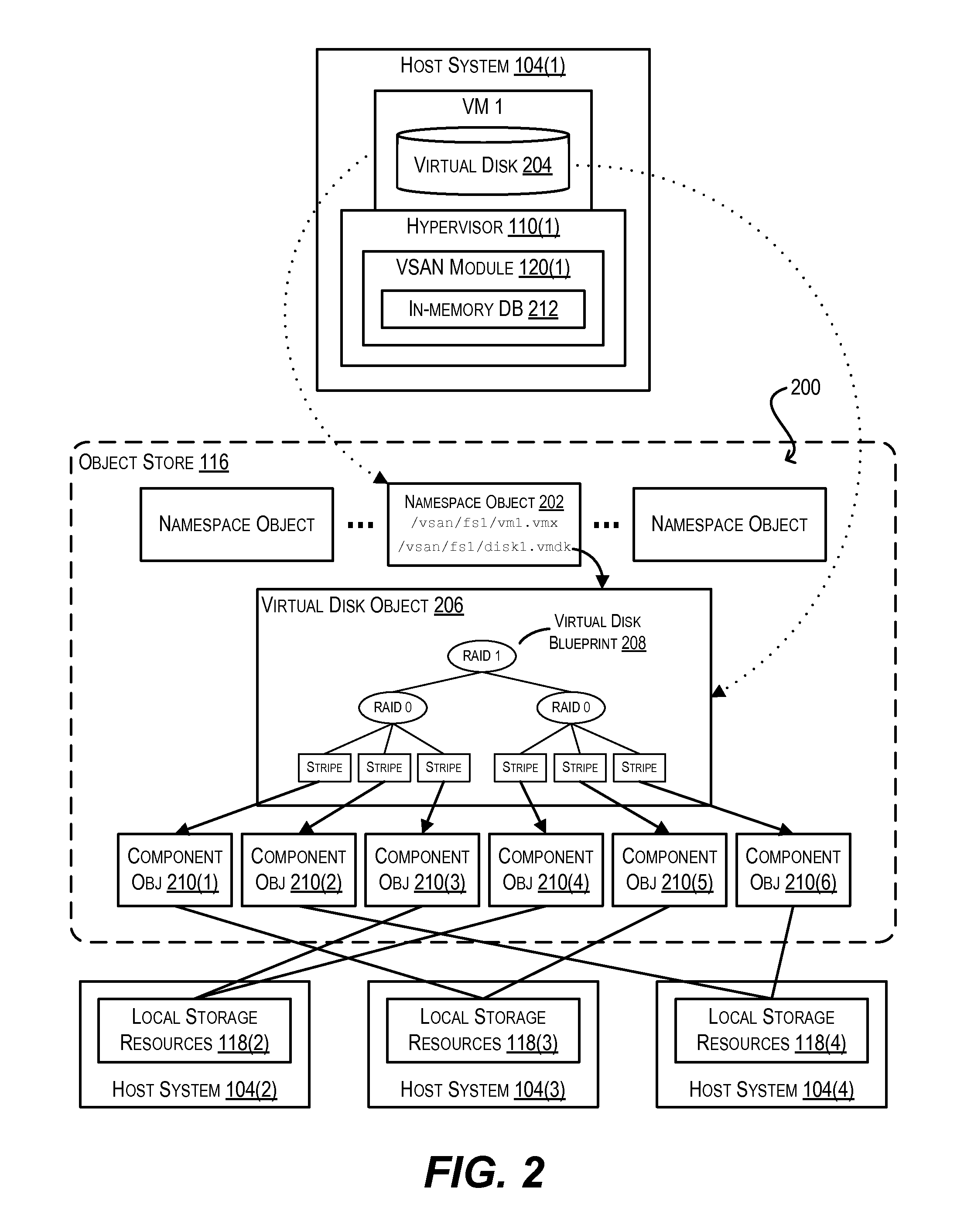
Maintaining high availability during network partitions for virtual machines stored on distributed object-based storage
ActiveUS9513946B2Interprogram communicationDigital computer detailsDistributed objectComputer module
Techniques are disclosed for maintaining high availability (HA) for virtual machines (VMs) running on host systems of a host cluster, where each host system executes a HA module in a plurality of HA modules and a storage module in a plurality of storage modules, where the host cluster aggregates, via the plurality of storage modules, locally-attached storage resources of the host systems to provide an object store, where persistent data for the VMs is stored as per-VM storage objects across the locally-attached storage resources comprising the object store, and where a failure causes the plurality of storage modules to observe a network partition in the host cluster that the plurality of HA modules do not. In one embodiment, a host system in the host cluster executing a first HA module invokes an API exposed by the plurality of storage modules for persisting metadata for a VM to the object store. If the API is not processed successfully, the host system: (1) identifies a subset of second HA modules in the plurality of HA modules; (2) issues an accessibility query for the VM to the subset of second HA modules in parallel, the accessibility query being configured to determine whether the VM is accessible to the respective host systems of the subset of second HA modules; and (3) if at least one second HA module in the subset indicates that the VM is accessible to its respective host system, transmits a command to the at least one second HA module to invoke the API on its respective host system.
Owner:VMWARE INC
Failure diagnosis chart clustering method based on network dividing
InactiveCN101178703AEasy to knowImprove the accuracy of fault diagnosisComputing modelsSpecial data processing applicationsData setDegree of similarity
The invention discloses a fault diagnosis spectral clustering operation method based on network partition. The method comprises the steps that: the fault diagnosis is molded into a network partition by the characteristic of network description fault sample which consists of nodes and relations; the objective function of the partition is made by utilizing the smallest and the largest criterion of the comprehensive evaluation of larger similarity between classes and smaller similarity inside a class; the objective function is optimally solved by a method of spectral clustering based on the theory of spectrogram; the operation method can acquire the state characteristics more quickly and acquire a comparatively high diagnosis accurate rate. The fault diagnosis embodiment of a UCI standard data set and a four-grade compressor proves the quick and effective performance of the operation method.
Owner:XI AN JIAOTONG UNIV
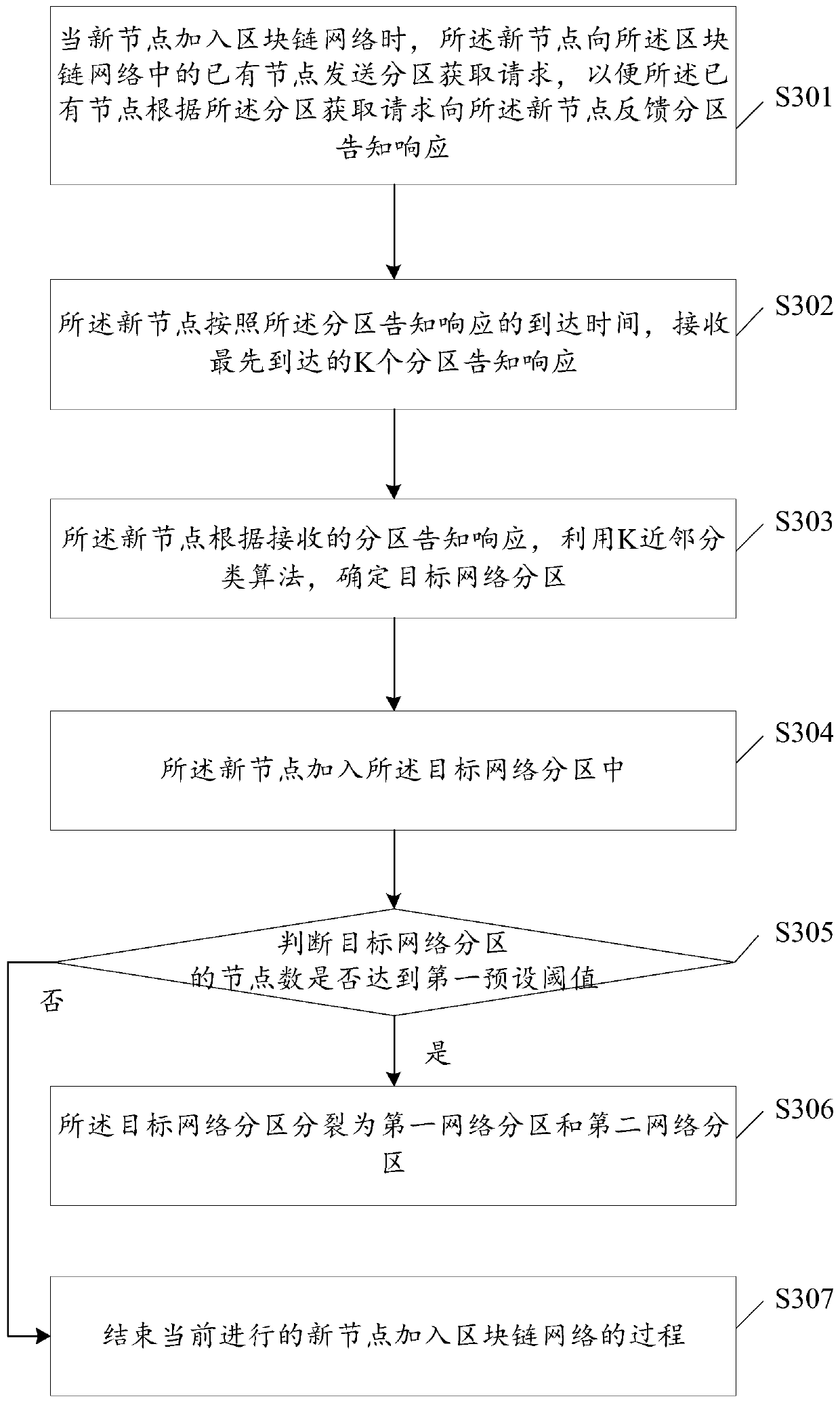
A block chain fragmentation method and device
InactiveCN109949160AImprove throughputImprove communication efficiencyFinanceCharacter and pattern recognitionShortest distanceProcess efficiency
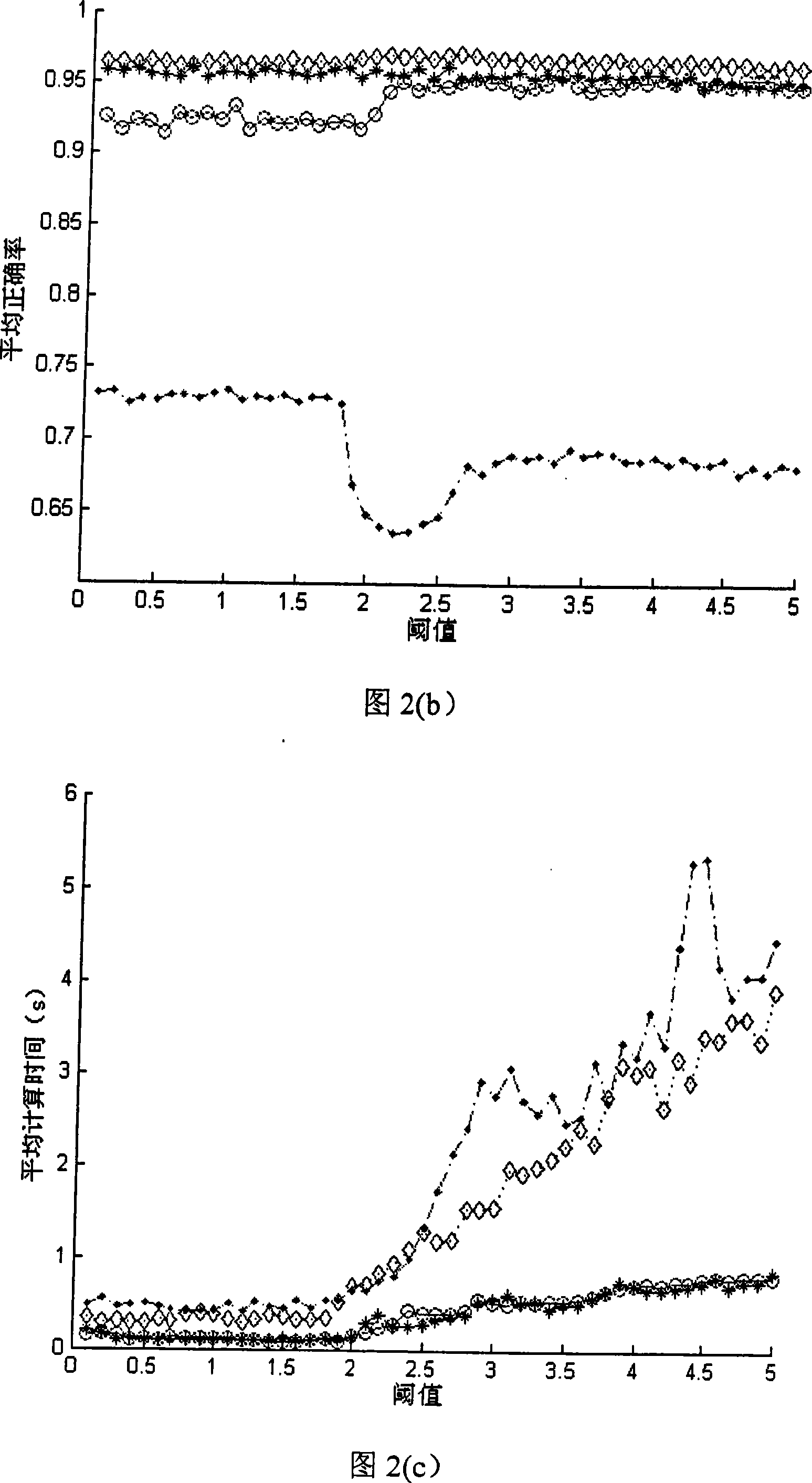
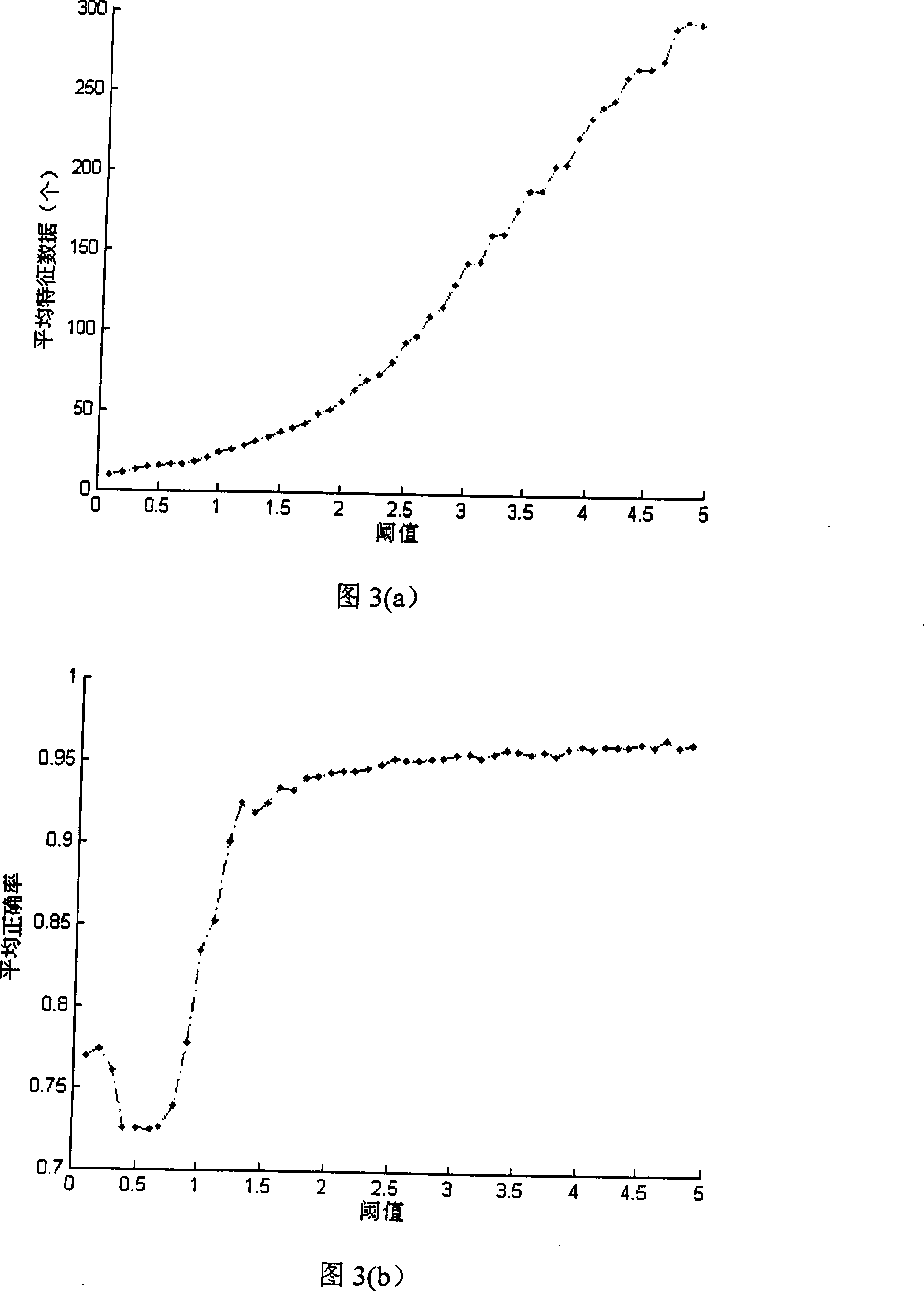
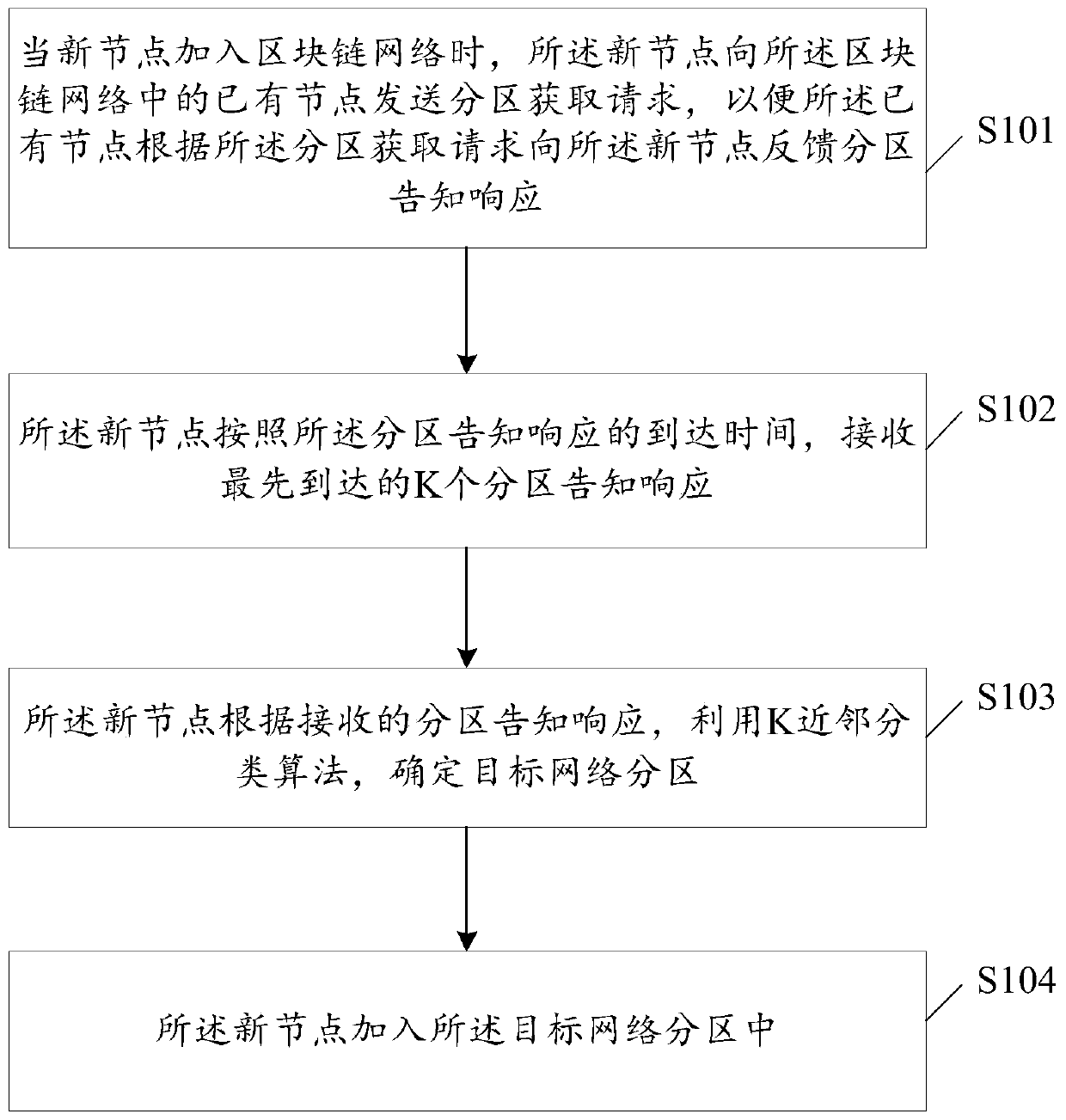
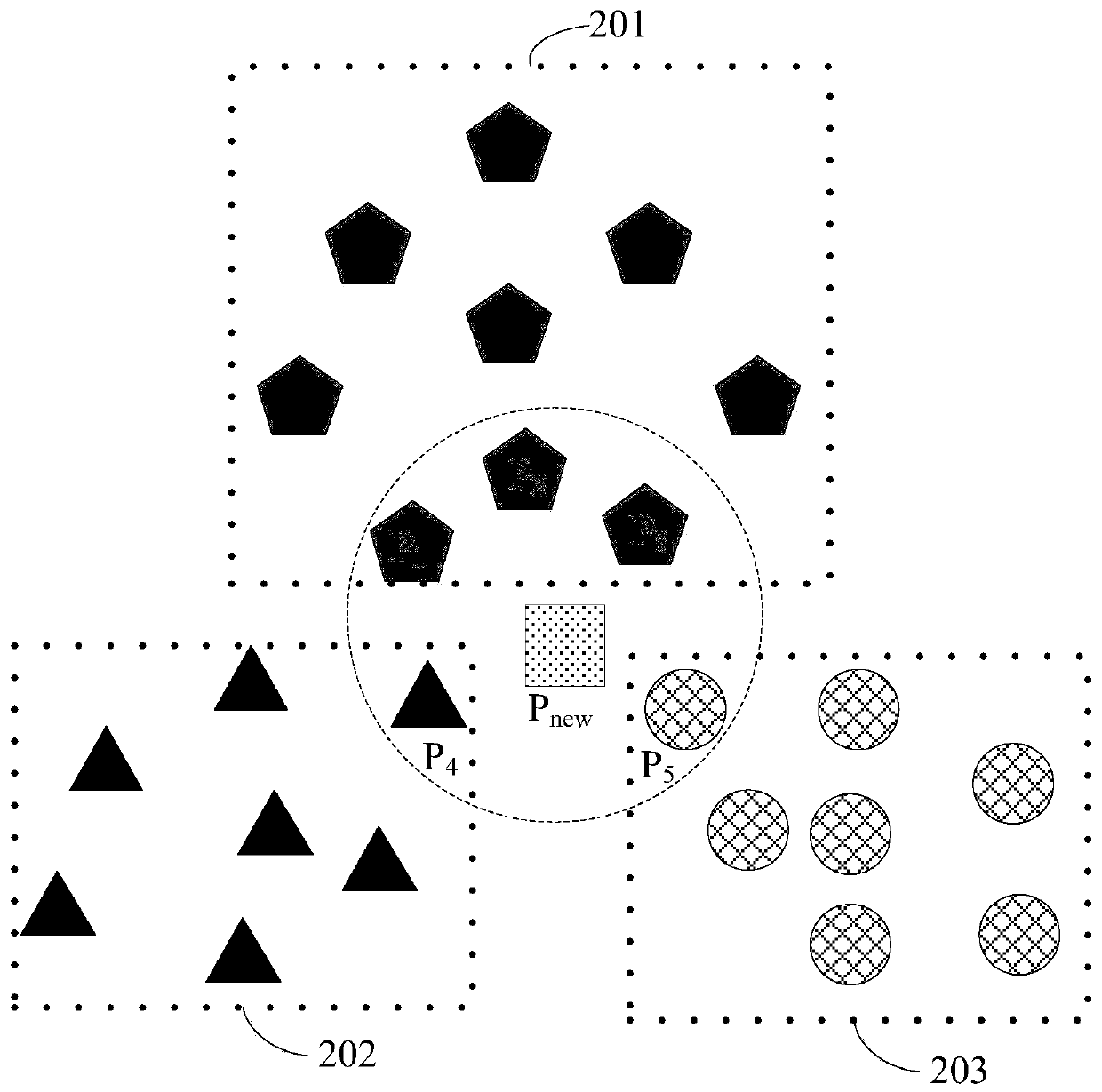
The invention discloses a block chain fragmentation method and device, and the method comprises the steps: determining a target network partition to which a new node belongs through employing a K neighbor classification algorithm according to K partition notification responses received by the new node, so that the new node can be added into the target network partition. The K neighbor classification algorithm can screen out the network partition including the most neighbor nodes of the new node according to the partition notification response; therefore, the new nodes can be divided into the network partitions including the most neighbor nodes by using the K neighbor classification algorithm, so that the nodes with relatively short distances can be divided into the same network partition,the communication efficiency between different nodes in the network partition is improved, and the transaction processing efficiency in the network partition is further improved. Besides, each networkpartition can independently process the transaction, so that each fragment can process different transactions in parallel, the transaction processing and confirmation concurrency is improved, and thethroughput of the whole block chain network is improved.
Owner:度小满科技(北京)有限公司
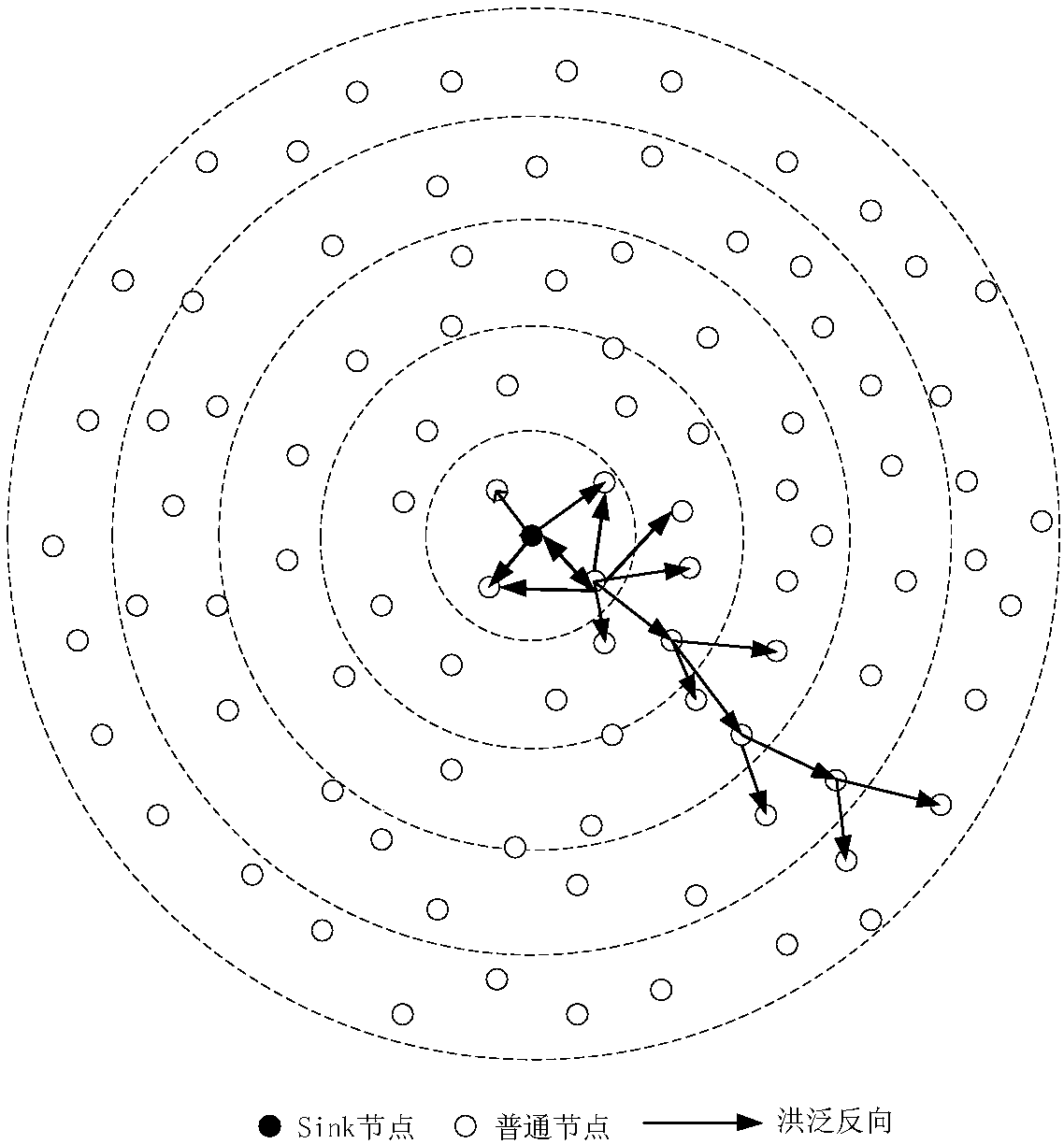
Multi-sink deployment and fault tolerance method for wireless sensor network
InactiveCN105915451AGuaranteed uptimeNetwork topologiesData switching networksLine sensorFault tolerance
Owner:DONGHUA UNIV
Highly scalable and highly available cluster system management scheme
InactiveUS7412479B2Low costImprove scalabilityError detection/correctionMultiple digital computer combinationsData processing systemCluster systems
A cluster system is treated as a set of resource groups, each resource group including an highly available application and the resources upon which it depends. A resource group may have between 2 and M data processing systems, where M is small relative to the cluster size N of the total cluster. Configuration and status information for the resource group is fully replicated only on those data processing systems which are members of the resource group. A configuration object / database record for the resource group has an associated owner list identifying the data processing systems which are members of the resource group and which may therefore manage the application. A data processing system may belong to more than one resource group, however, and configuration and status information for the data processing system is replicated to each data processing system which could be affected by failure of the subject data processing system—that is, any data processing system which belongs to at least one resource group also containing the subject data processing system. The partial replication scheme of the present invention allows resource groups to run in parallel, reduces the cost of data replication and access, is highly scalable and applicable to very large clusters, and provides better performance after a catastrophe such as a network partition.
Owner:BLUECAT NETWORKS USA
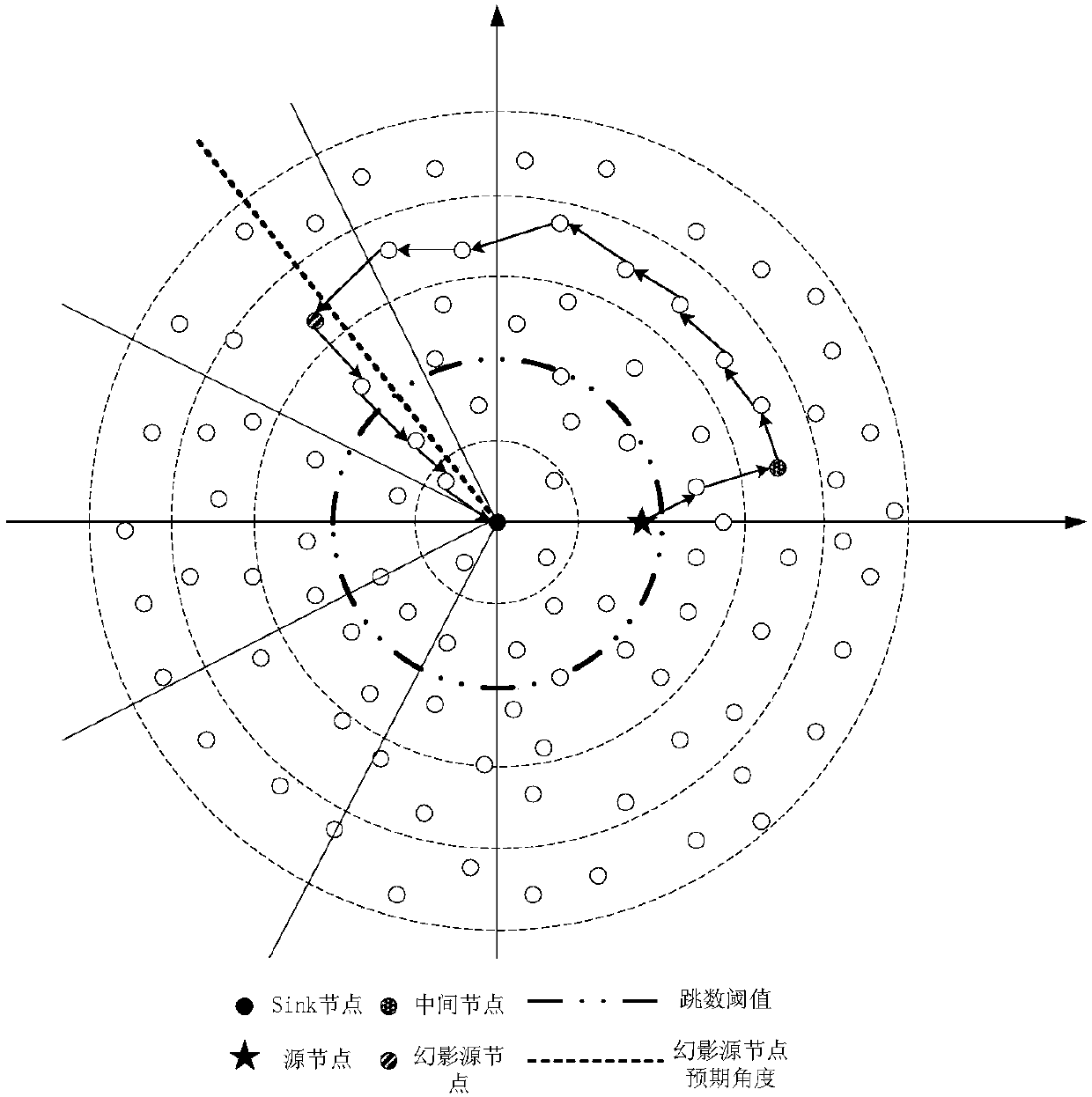
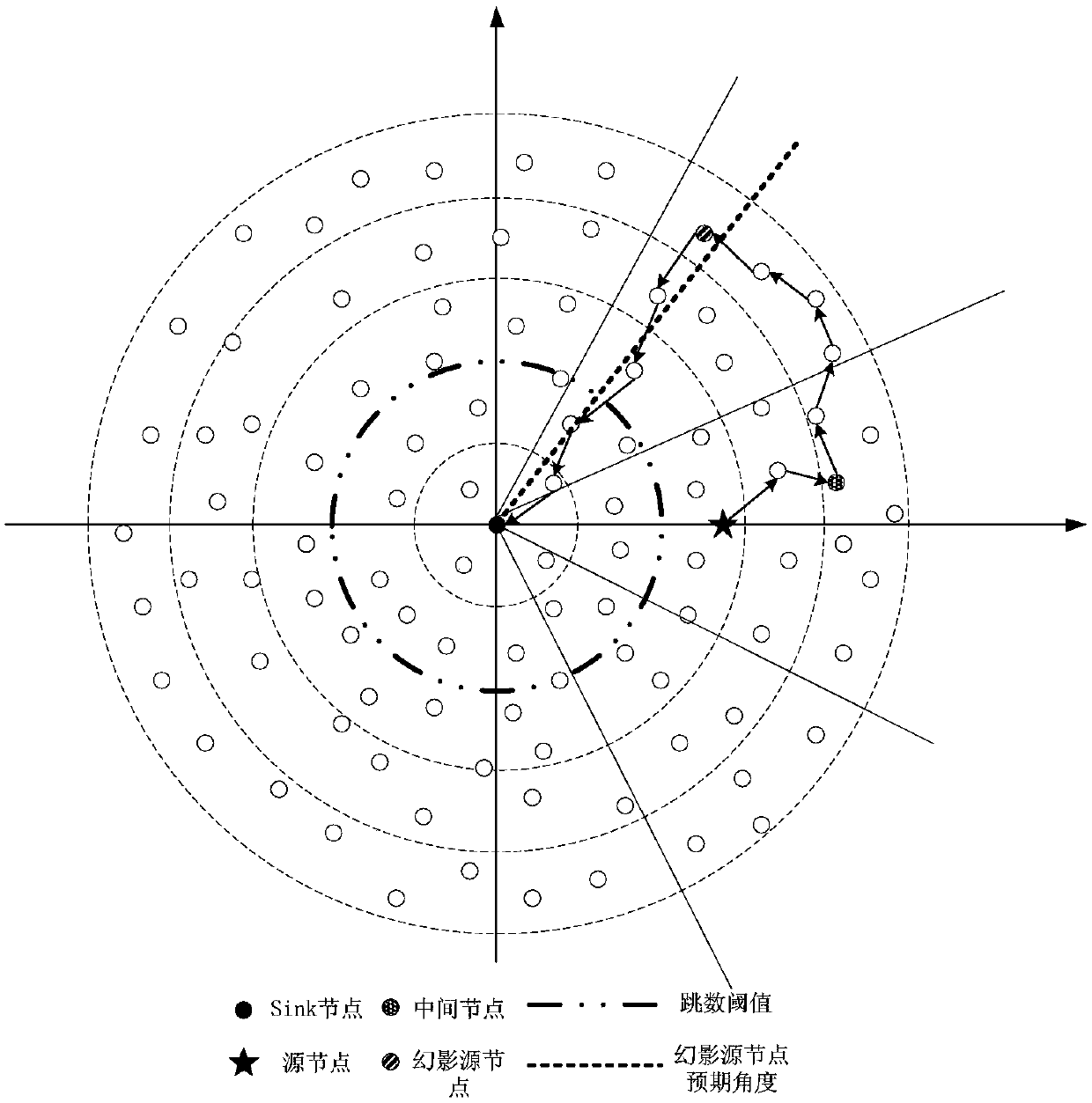
Method for protecting source node location privacy in wireless sensor network based on phantom routing
ActiveCN107835510ALong secure transmission timeSend accuratelyPower managementSecurity arrangementWireless mesh networkNetwork packet
The invention discloses a method for protecting source node location privacy in a wireless sensor network based on phantom routing. Firstly, base station nodes perform network initialization in a beacon flooding manner, so that the nodes can generate respective neighbour lists; secondly, a source node calculates a proper expected phantom source node location through network partition; furthermore,a data packet is sent to the location according to a routing algorithm, and finally arrives at a phantom source node; and finally, the phantom source node transmits the data packet to the base station nodes in a manner of randomly selecting a neighbour node. By means of the method disclosed by the invention, the fact that the phantom source node is enough far away from a real source node can be ensured; furthermore, the path of the data packet from the source node to a base station every time has the randomness; furthermore, the paths of adjacent data packets are not repetitive; therefore, the source node can be ensured to have the enough security data transmission time; and the location privacy of the source node is protected.
Owner:HOHAI UNIV CHANGZHOU
Network partitioning method for large-scale complicated network
InactiveCN1571363AEffective segmentationSolve the problem of survivabilityData switching by path configurationPretreatment methodDistributed intelligence
The invention is a large-scale complex network dividing method, including three parts of network preprocessing method, sub-network judging method and network dividing method, firstly adopting the network preprocessing method to improve large-scale network topology into a diagram with side conductivity not less than 2, then further combining the sub-network judging method and the network dividing method to divide the large-scale network into several ring sub-networks and fan-shaped sub-network, where it uses the network dividing method to divide the whole network into sub- networks, and divides the sub-networks into a ring sub-network with closed outer ring link and a fan-shaped sub-network with unclosed outer ring link. The large-scale network uses each sub-network as unit and adopts a distributed intelligent recovery policy, able to flexibly and conveniently solve the existence problem that the large- scale complex network confronts and each sub-network can simultaneously and parallel process many failures, thus wining time for failure recovery.
Owner:SHANGHAI JIAO TONG UNIV
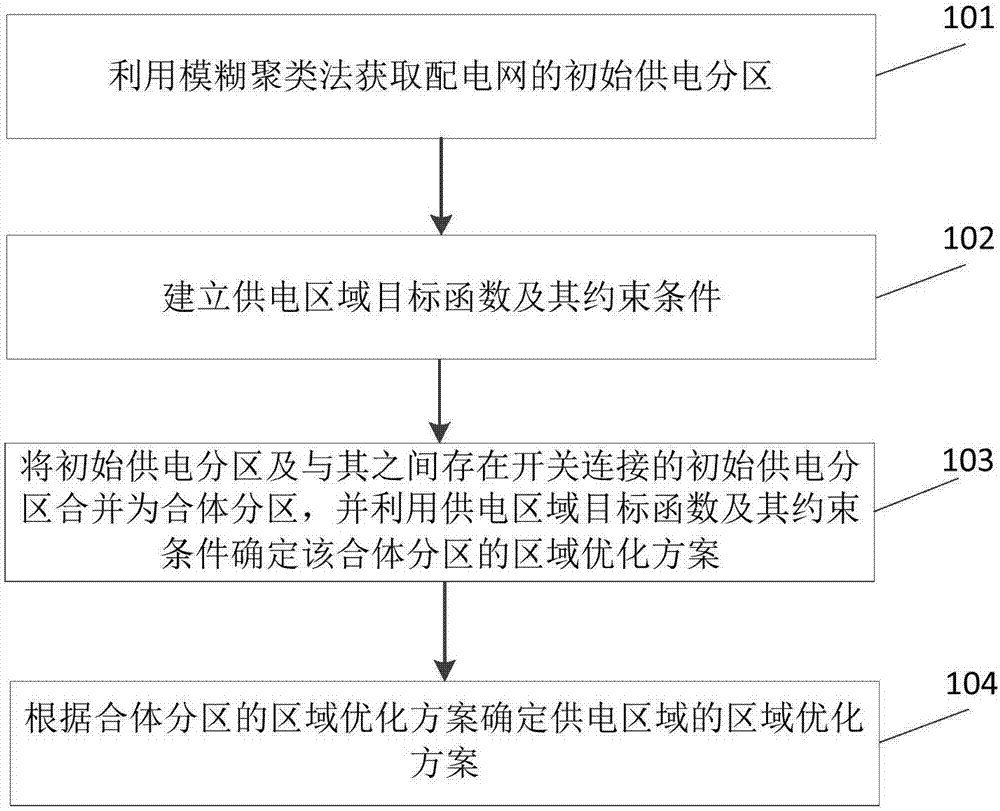
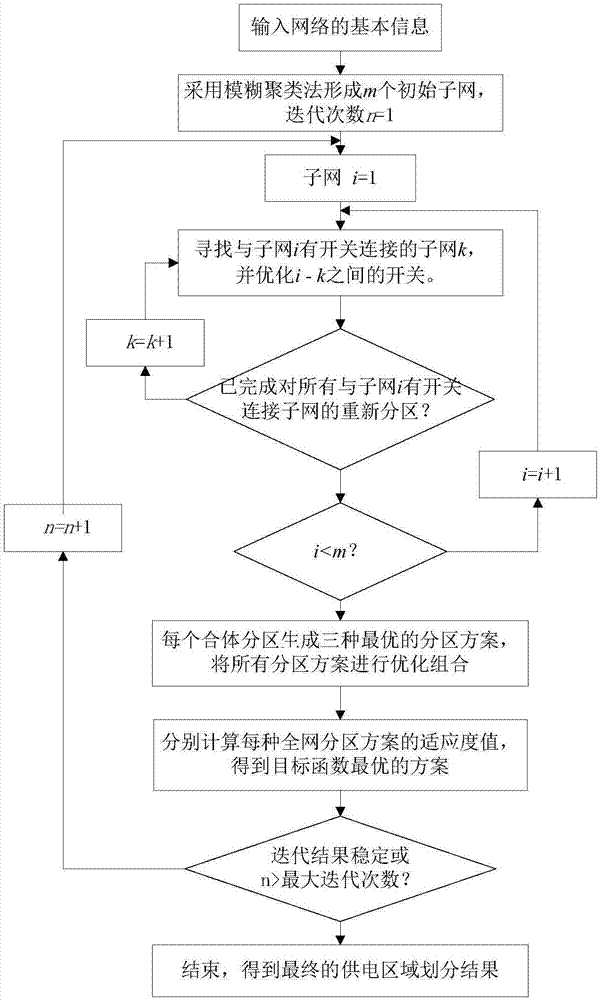
Active power distribution network power supply area division method and apparatus thereof
ActiveCN107017618AImprove structural performanceImprove economyResourcesSystems intergating technologiesBasic modeObject function
The invention relates to an active power distribution network power supply area division method and an apparatus thereof. The method comprises the following steps of using a fuzzy clustering method to acquire an initial power supply subarea of a power distribution network; establishing a power supply area target function and a constraint condition; merging the initial power supply subarea and an initial power supply subarea which has a switch connection relationship with the initial power supply subarea into a combination subarea, and using the power supply area target function and the constraint condition to determine an area optimization scheme of the combination subarea; and according to the area optimization scheme of the combination subarea, determining an area optimization scheme of a power supply area. By using the technical scheme of the invention, a basic mode of subarea optimization and total assessment is adopted so that a reasonable network subarea structure is acquired; and switch operation of a network is simplified and operation efficiency of the power distribution network is increased.
Owner:CHINA ELECTRIC POWER RES INST +2
Neural network wind power short-term forecasting method based on fuzzy partition theory
ActiveCN104732300AImproving Wind Power Prediction AccuracyAchieve high-precision forecastingBiological neural network modelsForecastingPredictive methodsEngineering
The invention provides a neural network wind power short-term forecasting method based on a fuzzy partition theory. The neural network wind power short-term forecasting method based on the fuzzy partition theory adopts the mode of combining a fuzzy theory, artificial intelligence and a statistical theory through analyzing the important features of wind velocity variation and the relationship between wind velocity and power. When wind power forecasting is conducted, wind scale fuzzy partition processing is conducted on wind velocity data obtained from weather forecasting according to periods of time, BP neural network partition forecasting is conducted, a forecast power value is obtained through multiplying a partition forecast value by a membership degree value of the partition forecast value and adding all partition values, a probability statistics modified algorithm is conducted, and the forecast power is obtained. The neural network wind power short-term forecasting method based on the fuzzy partition theory improves the accuracy of a forecasting model effectively.
Owner:国能日新科技股份有限公司
Method for determining power system parallel load flow based on heuristic automatic network partitioning
ActiveCN103353921AFast convergenceEasy to deploySpecial data processing applicationsPower flowMemory footprint
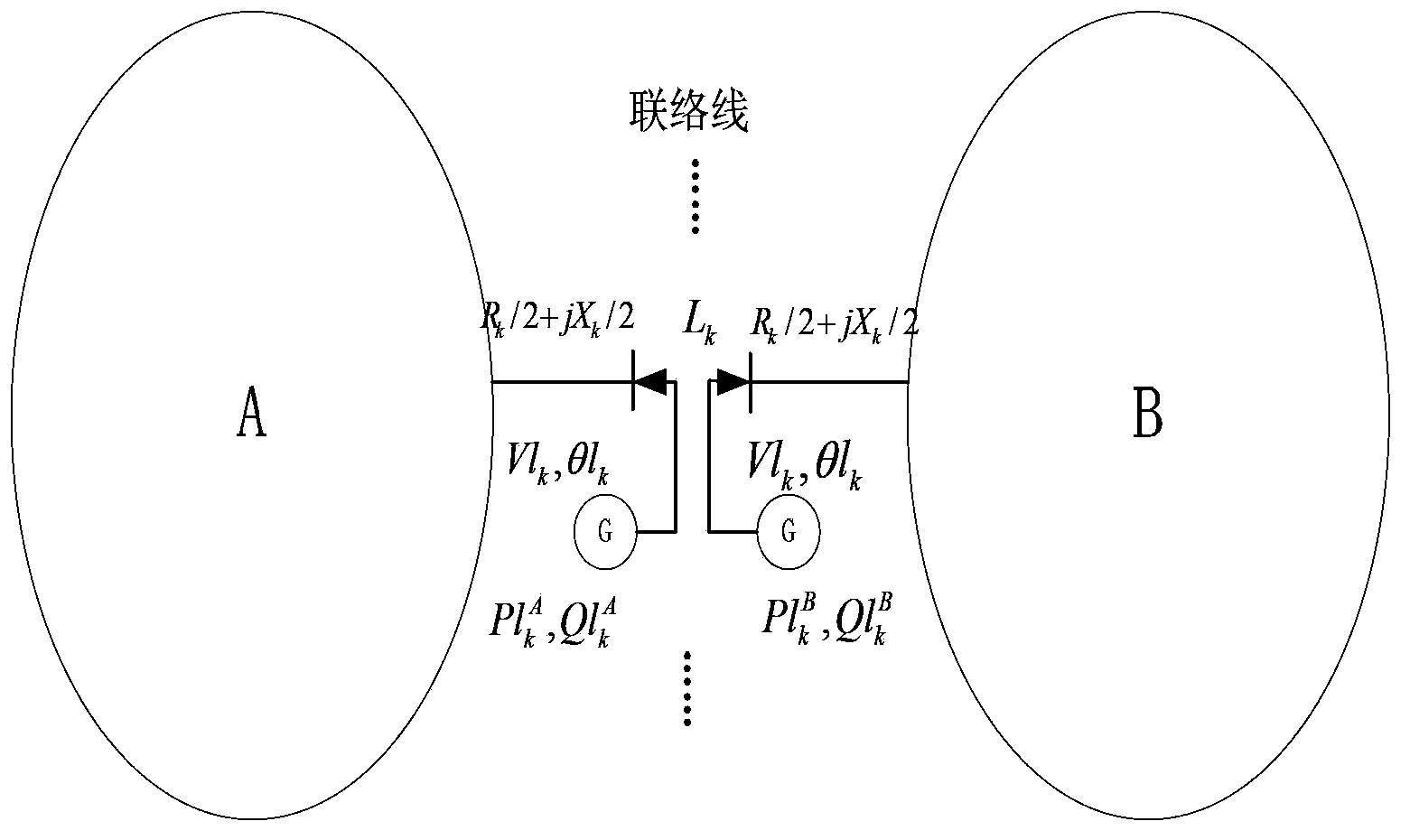
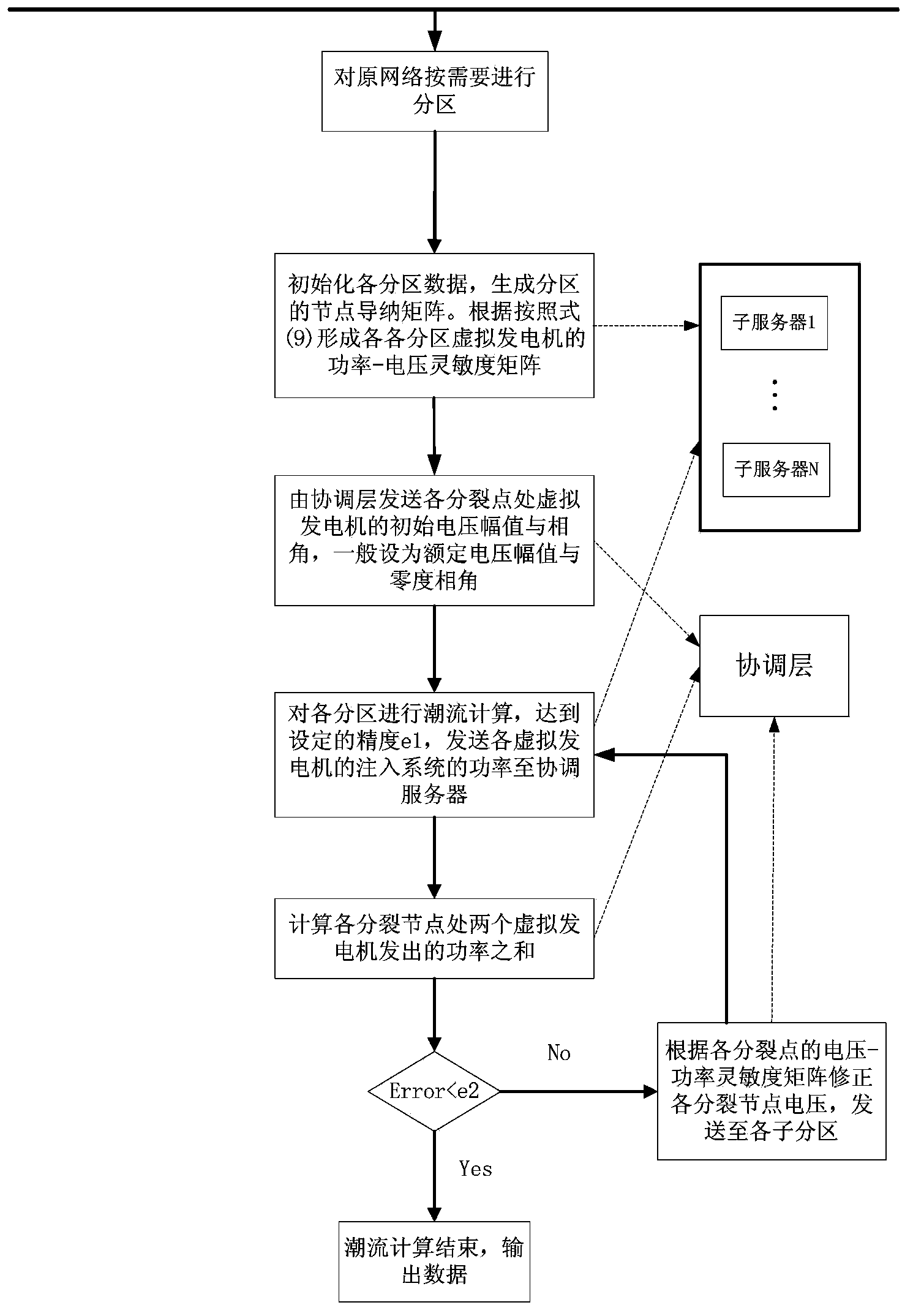
The invention relates to a method for determining a power system parallel load flow based on heuristic automatic network partitioning, which comprises the following steps: partitioning distribution network; generating the admittance matrixes of the partitioning nodes, the power flow calculation constant-jacobian matrix and the voltage-power sensitivity matrixes of virtual generators in partitions, sending the voltage-power sensitivity matrixes to a coordination layer; sending initial voltage magnitude and phase angle of virtual engines at the split points by the coordination layer; carrying out power flow calculation on the partitions, sending output power of the virtual engines to a coordination server; judging whether the boundary coordination quantity precision is met or not according to the mismatch quantity of the sum of output power of two virtual engines at the split points by the coordination layer, if no, correcting the voltage of the partitioning points, sending the corrected result to sub-areas, skipping to the last step, and otherwise, skipping to the next step; outputting the data result. The determining method has good convergence, high calculation speed, less memory occupied rate and calculation convenience and flexibility.
Owner:STATE GRID CORP OF CHINA +1
Byzantine fault-tolerant consensus method and system
ActiveCN112187490AResolve issues where agreement cannot be reachedImprove fault toleranceData switching networksSecuring communicationByzantine fault toleranceEngineering
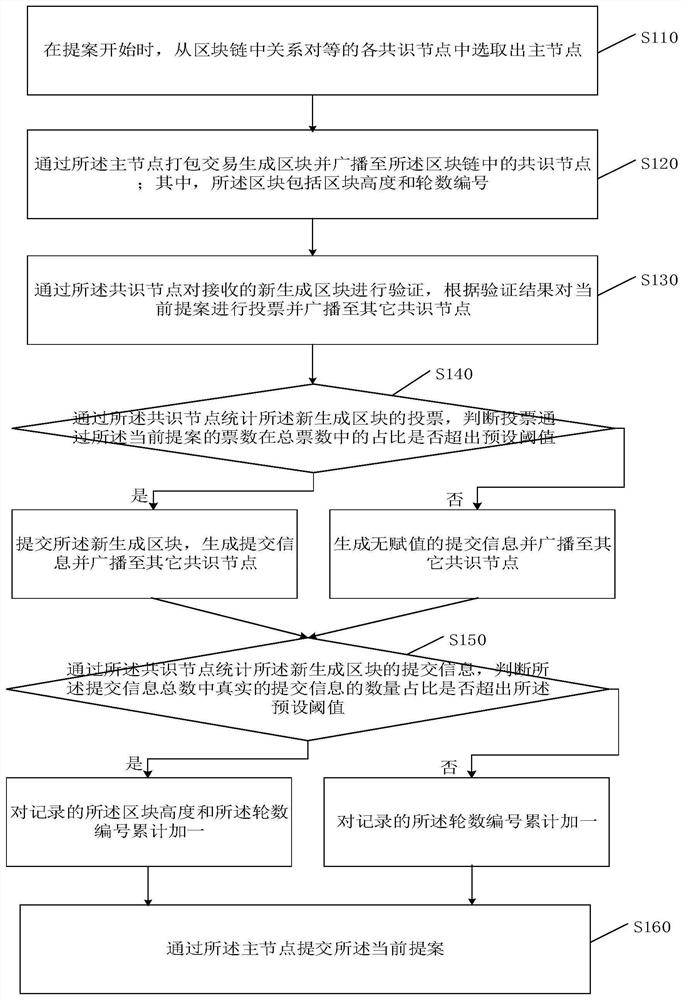
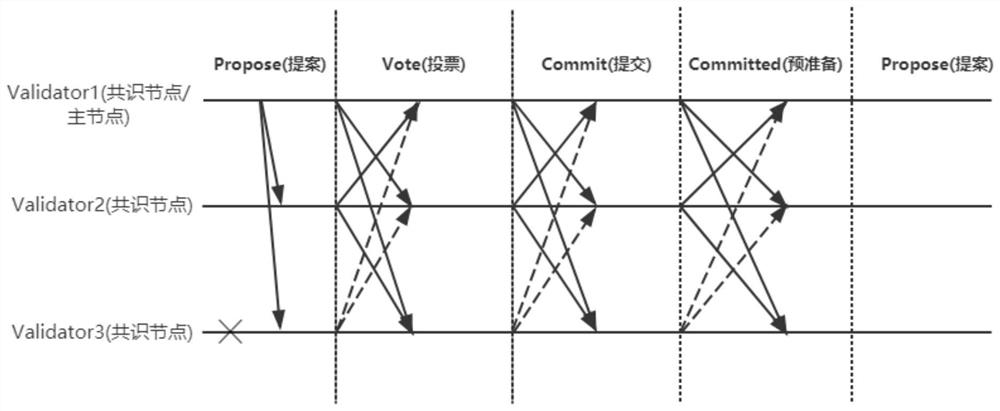
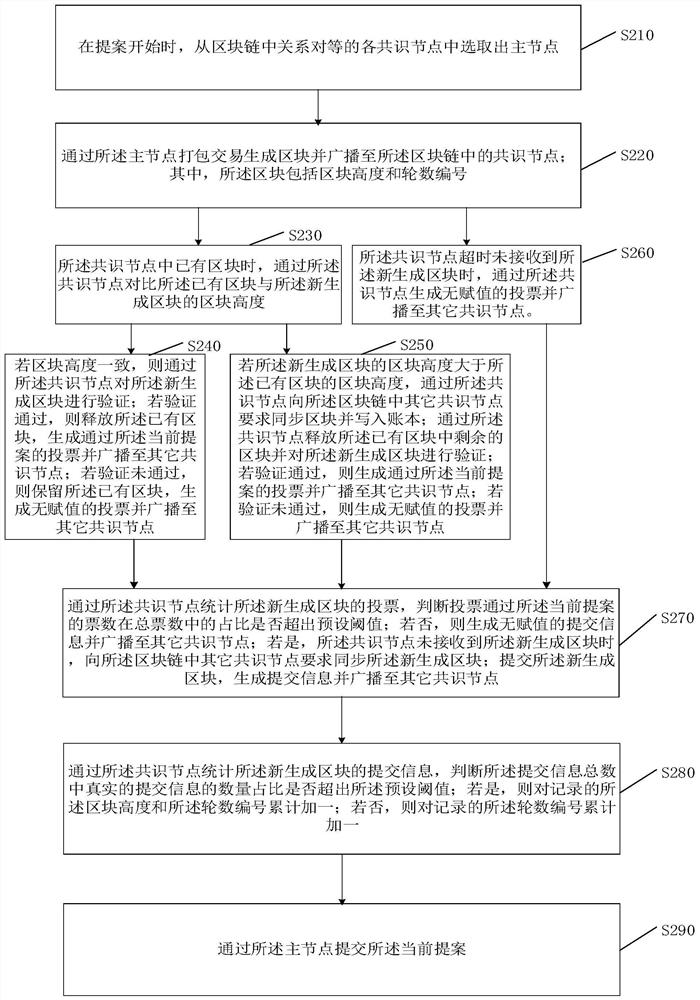
The invention belongs to the technical field of block chains, and provides a Byzantine fault-tolerant consensus method and system. The Byzantine fault-tolerant consensus method comprises the steps of:generating a block through a packaging transaction of a main node, and broadcasting the block to a consensus node in a blockchain; verifying the received newly generated block through using the consensus node, voting a current proposal according to a verification result, and broadcasting the voted current proposal to other consensus nodes; counting votes of the newly generated block through usingconsensus node, and judging whether the proportion of votes voting through in total votes exceeds a preset threshold value or not; if so, submitting the newly generated block, generating submission information and broadcasting the submission information to other consensus nodes; if not, generating non-assigned submission information and broadcasting the non-assigned submission information to other consensus nodes; and counting the submission information of the newly generated block through using the consensus node. According to the Byzantine fault-tolerant consensus method and the system of the invention, the fault-tolerant rate of the Byzantine fault-tolerant consensus method is improved, the tolerableness of network partition is realized, and the problem that states of the consensus nodes in the blockchain cannot be consistent due to the network partition is solved.
Owner:深圳法大大网络科技有限公司
Method and device for confirming network topology and storage medium
ActiveCN108712286AOrderly displayRealize displayData switching networksStructure of Management InformationInterconnection
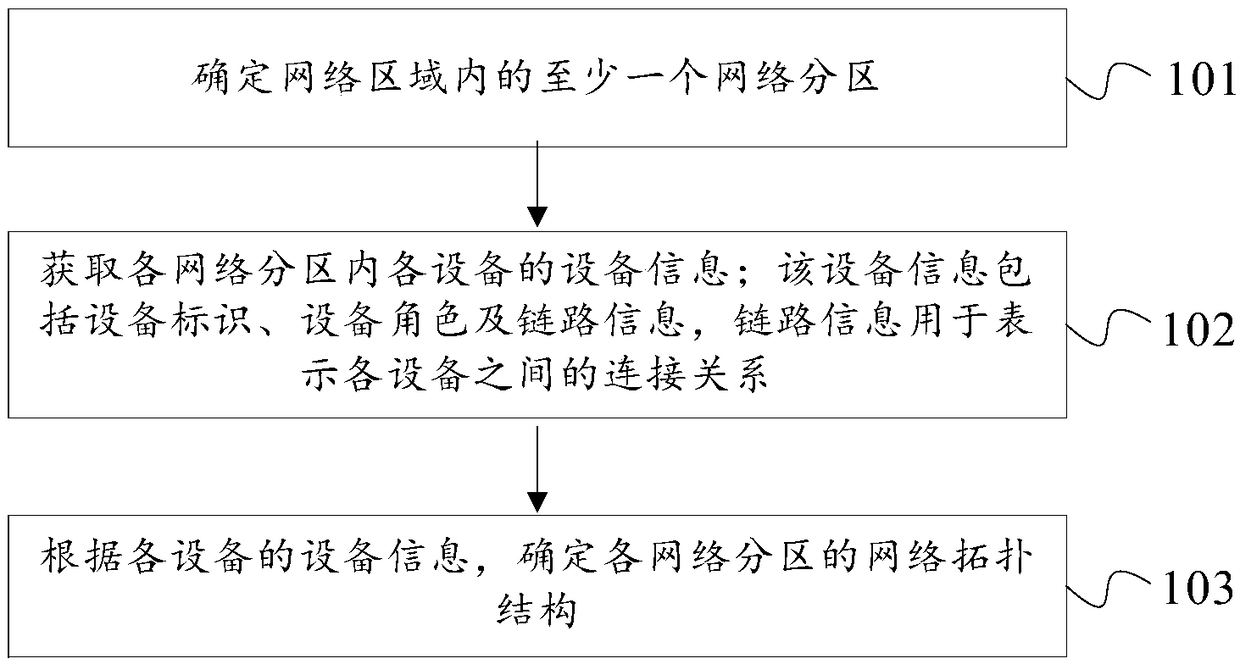
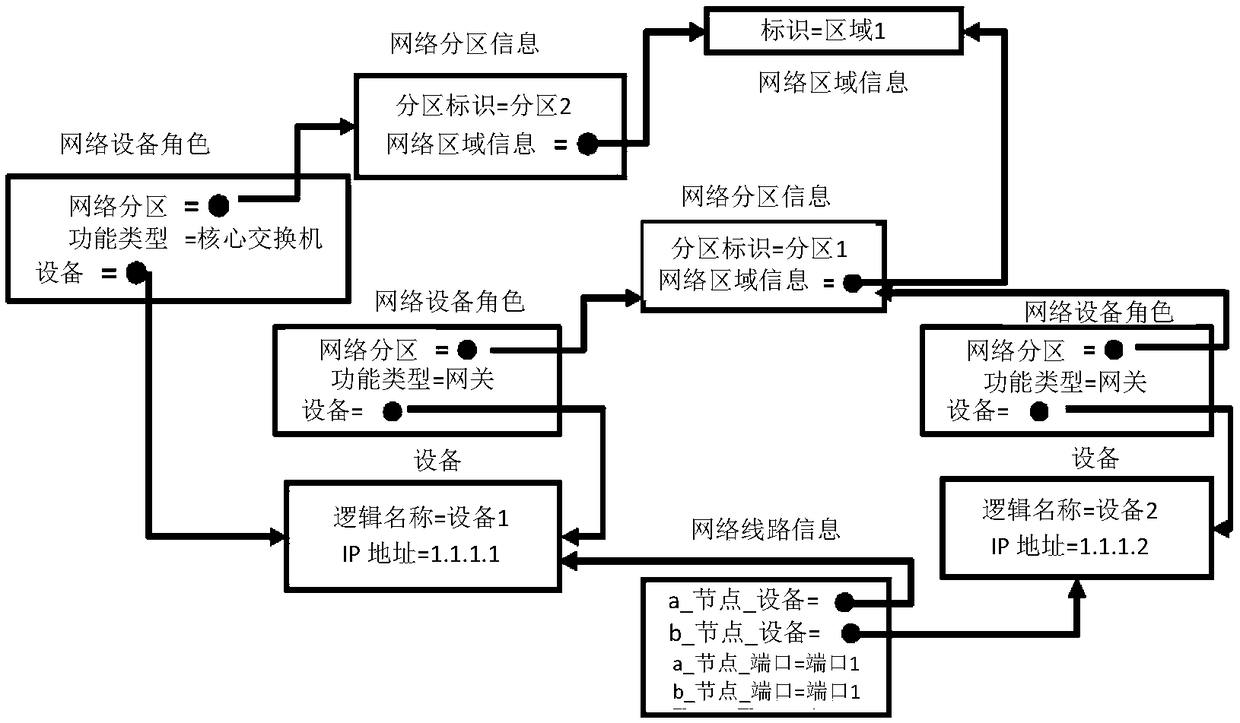
The application provides a method and device for confirming a network topology and a storage medium. The method for confirming the network topology comprises the following steps: confirming at least one network partition in a network area; obtaining the device information of each device in the network partition, wherein the device information comprises device identifiers, device roles and link information, and the link information is used to represent the connection among devices; and confirming the network topology of each network partition according to the device information of each device.The application can recognize interconnection devices among network partitions.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com