Patents
Literature
100 results about "Peering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
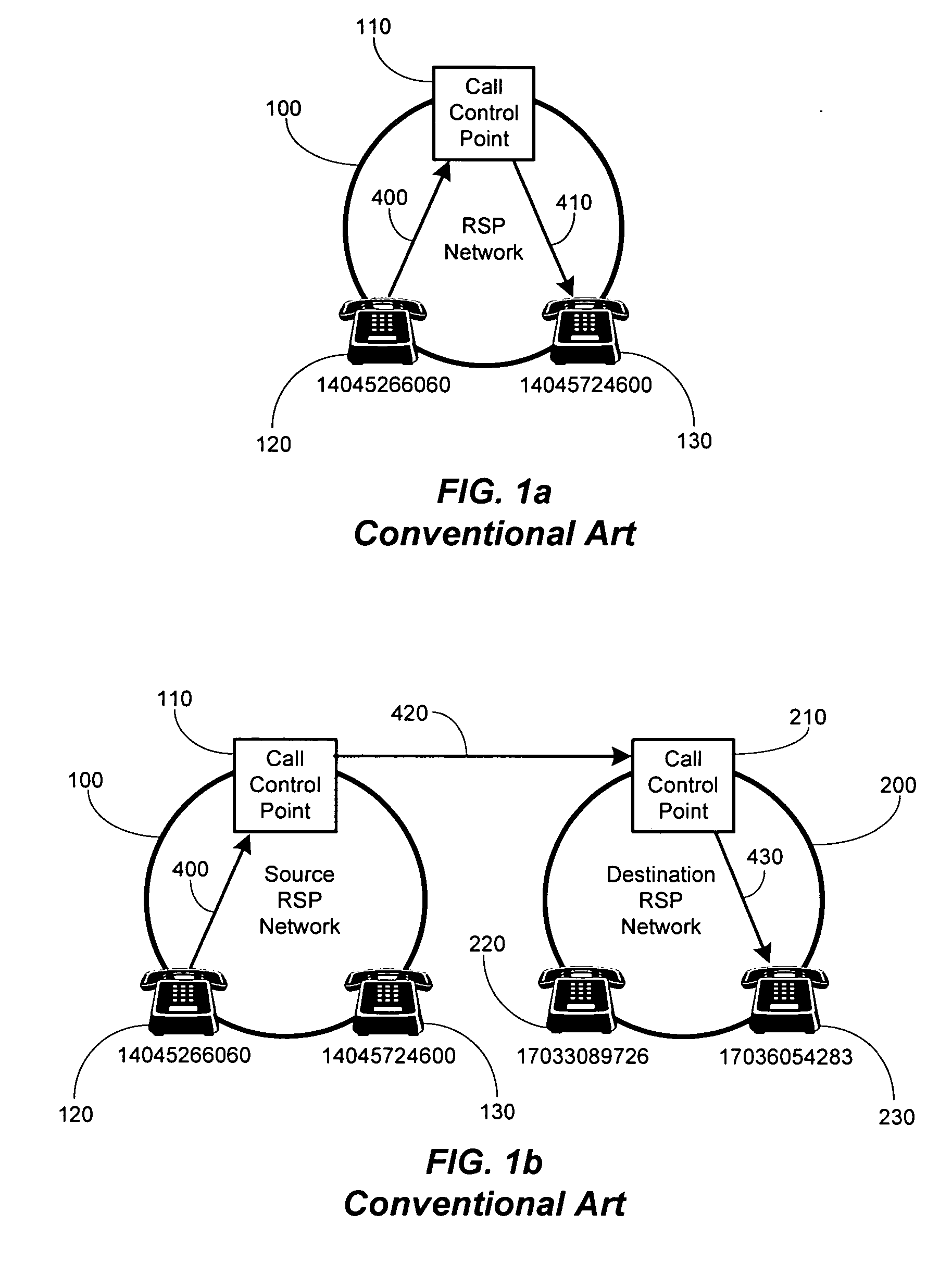
In computer networking, peering is a voluntary interconnection of administratively separate Internet networks for the purpose of exchanging traffic between the users of each network. The pure definition of peering is settlement-free, also known as "bill-and-keep," or "sender keeps all," meaning that neither party pays the other in association with the exchange of traffic; instead, each derives and retains revenue from its own customers.
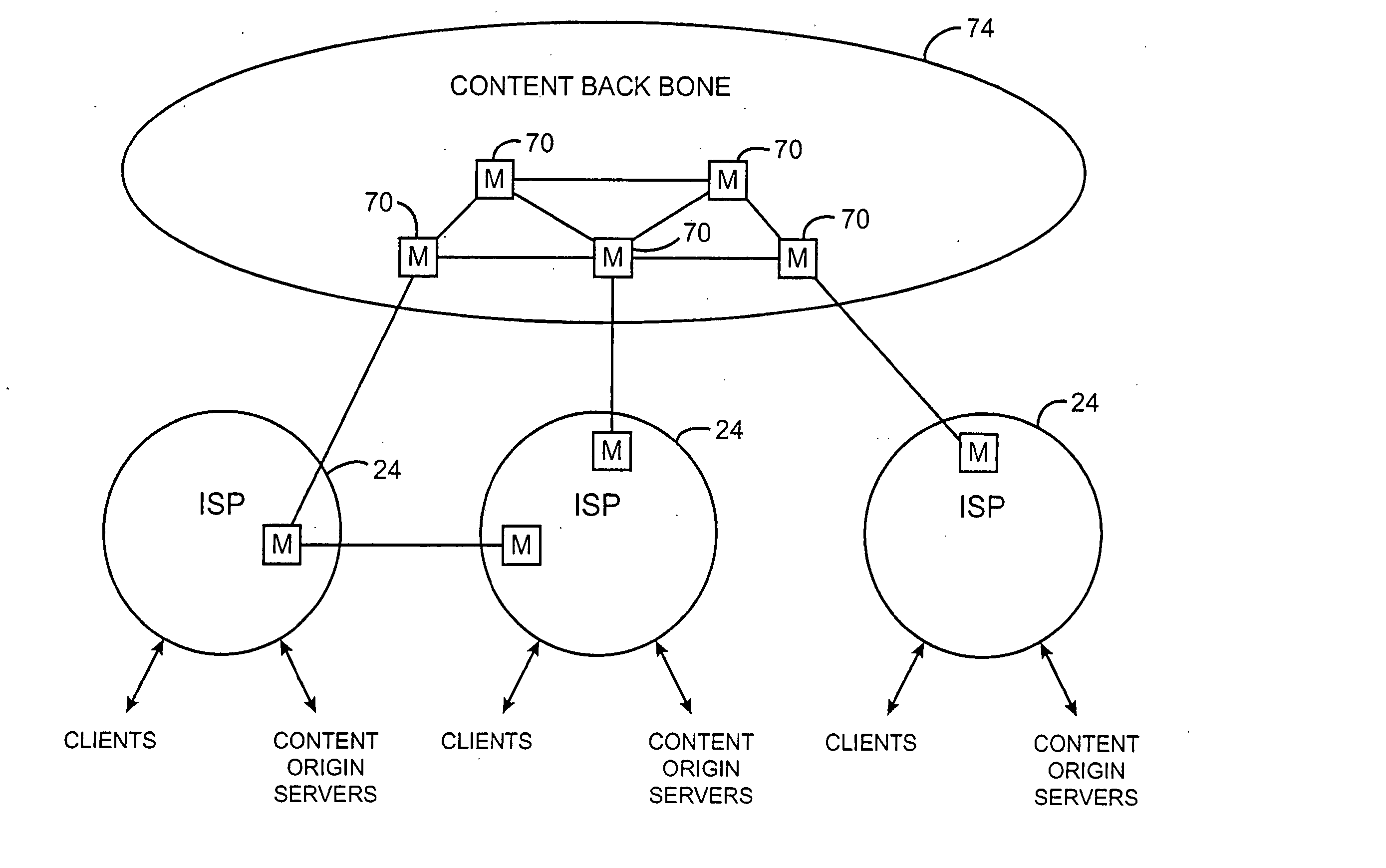
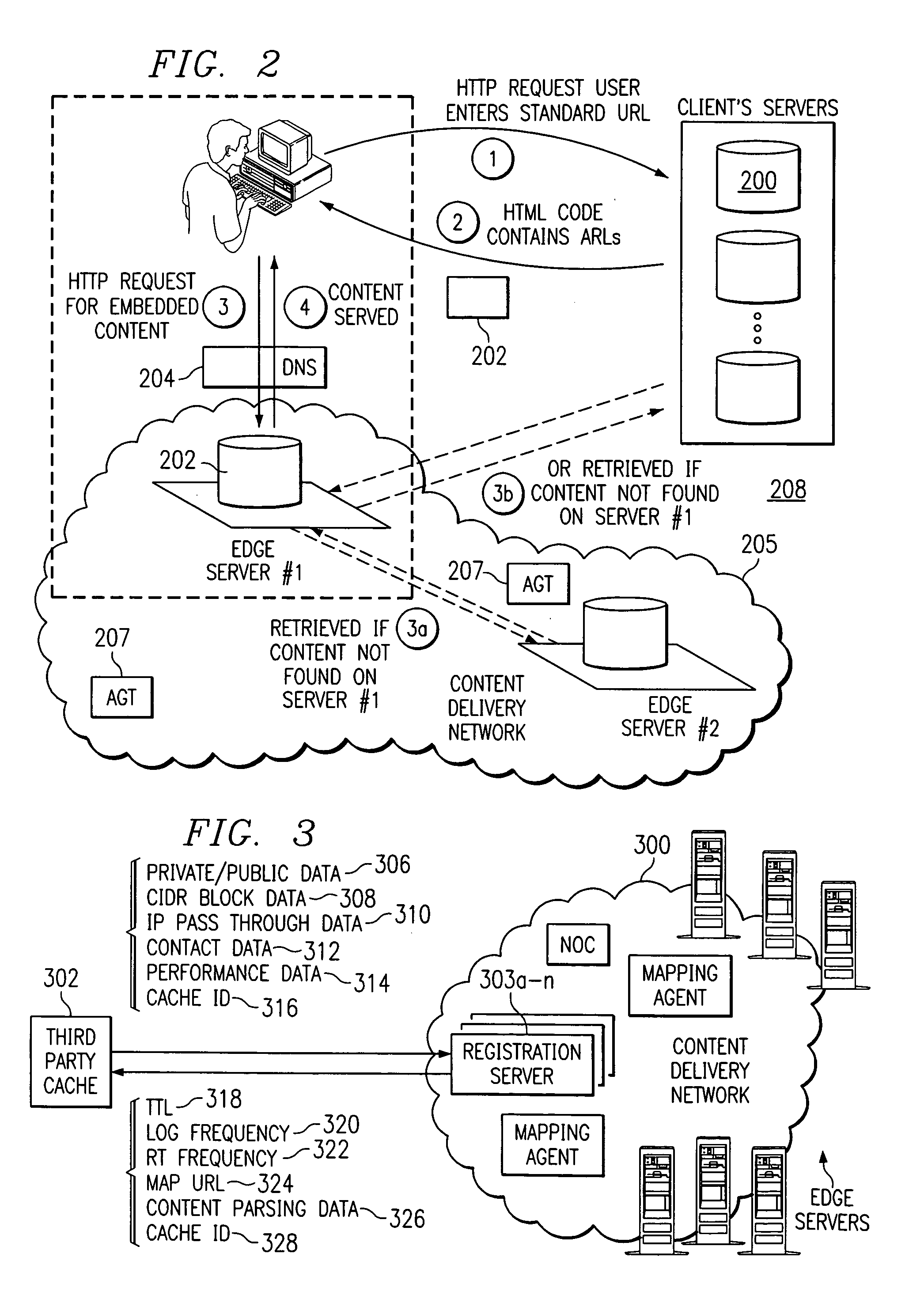
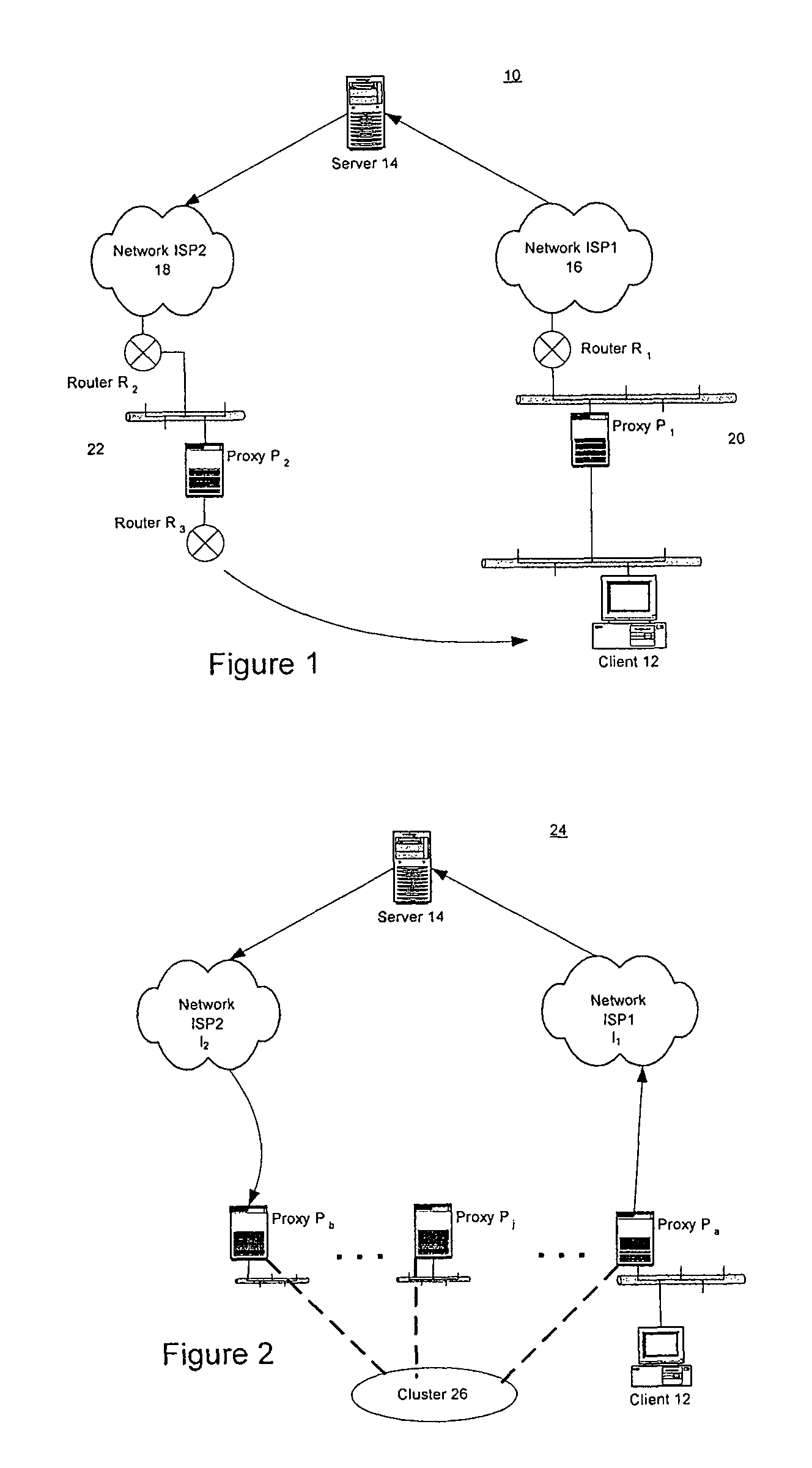
Content distribution system for operation over an internetwork including content peering arrangements
InactiveUS20050010653A1Special service provision for substationMultiple digital computer combinationsContent distributionDomain name
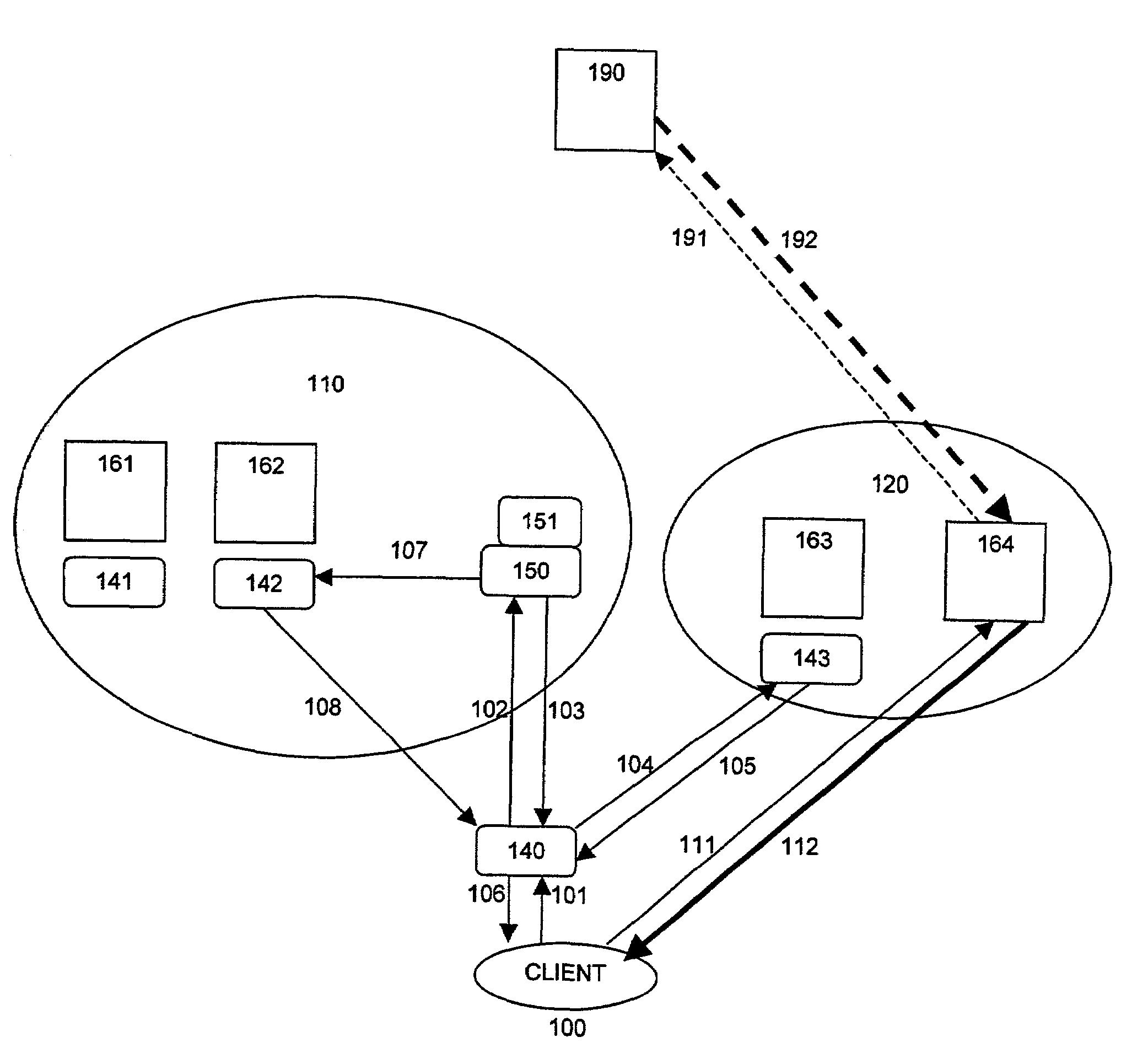
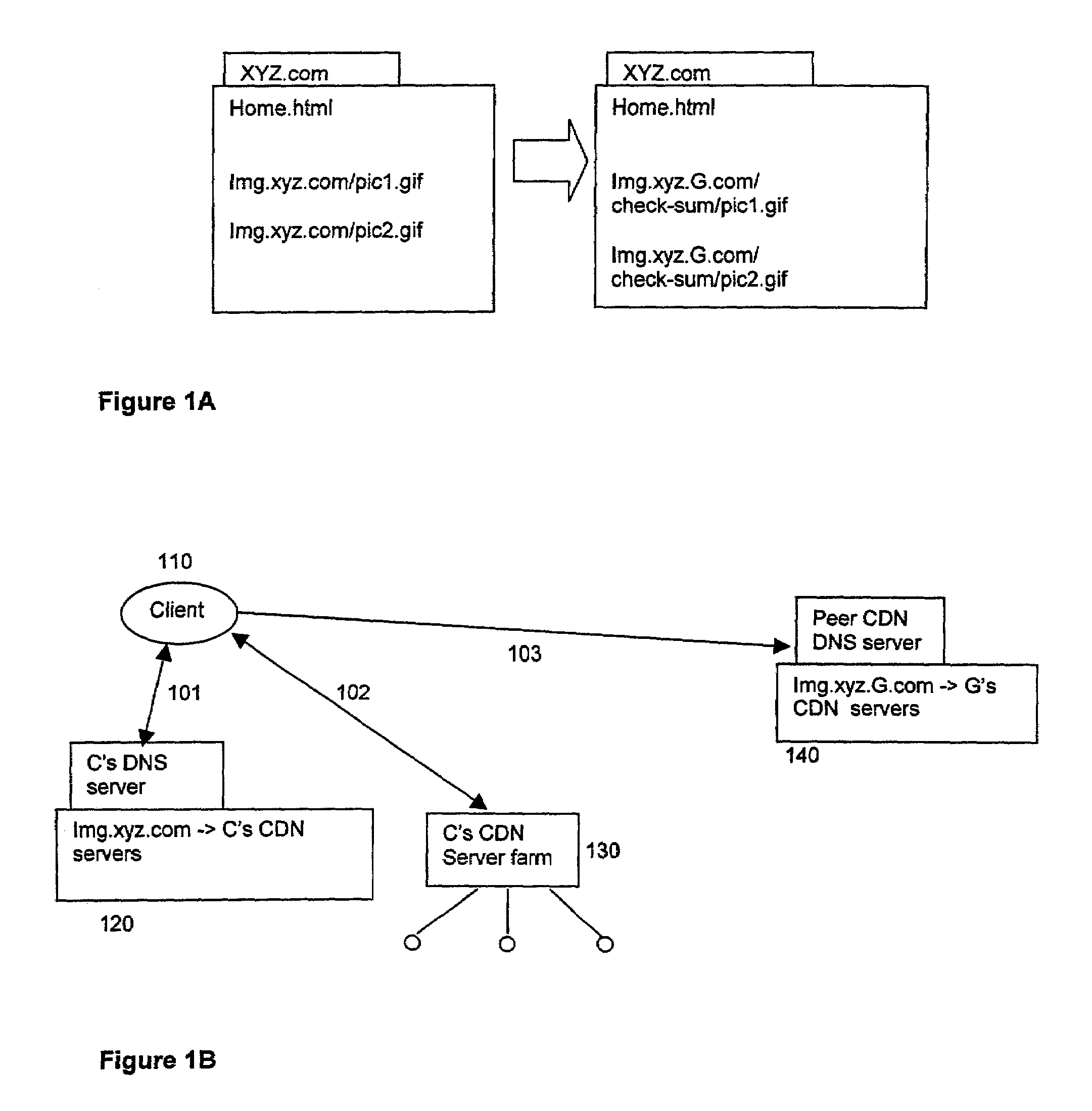
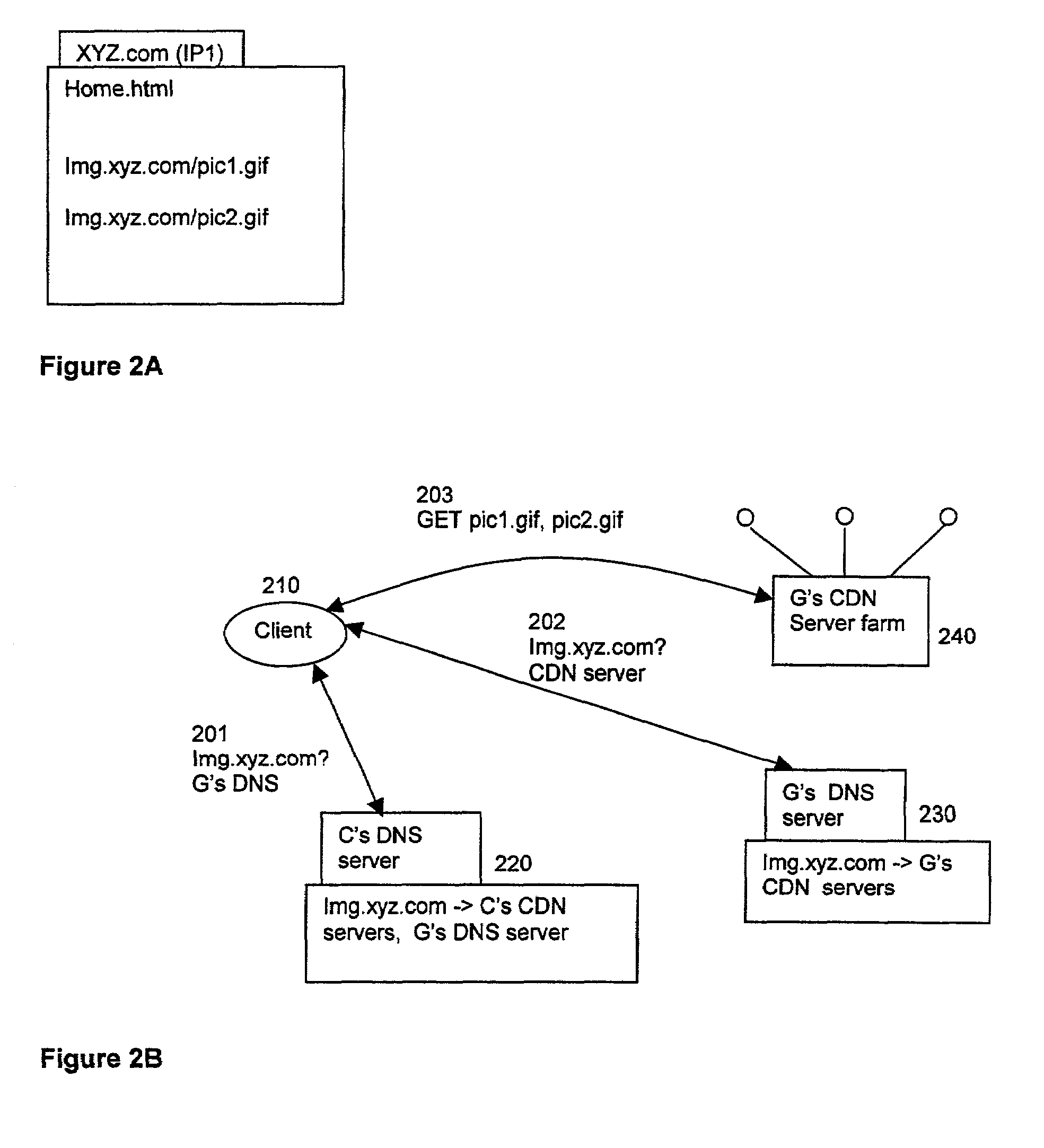
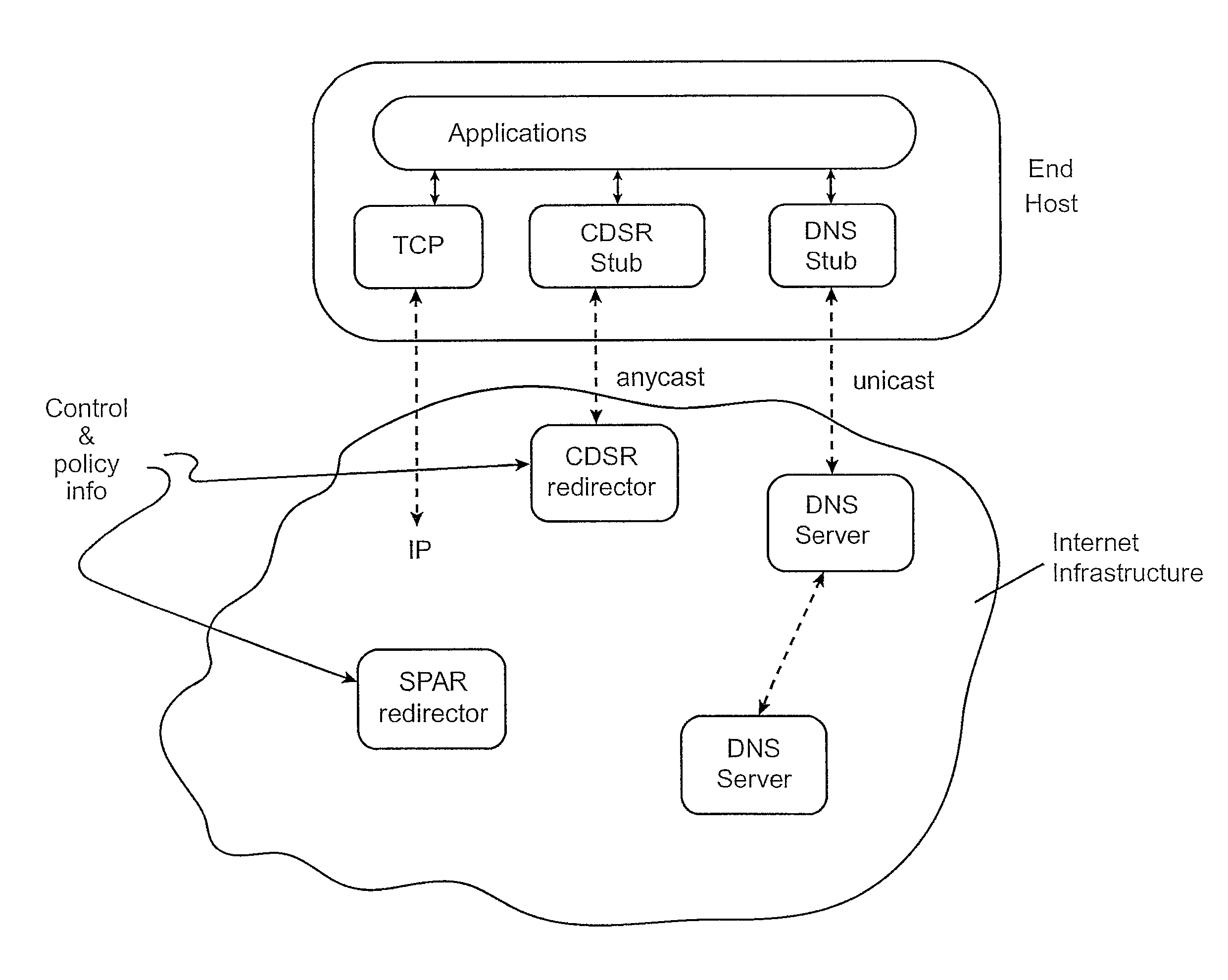
In a network interconnecting a plurality of content providers and a plurality of clients, for providing content to a client, each of the plurality of content providers is coupled to at least one content distribution network of a plurality of content distribution networks, wherein the client is coupled to at least one of the plurality of content distribution networks and a request for the content is sent from the client to a redirector node that receives requests, wherein a redirector at the redirector node provides an address for a server available to serve the requested content. When the client's content distribution network is a primary content distribution network for the content provider providing the requested content, redirecting the client to a server within the client's content distribution network. When the client's content distribution network is not a primary content distribution network for the content provider but the client's content distribution network has a content peering relationship with a primary content distribution network for the content provider, redirecting the client to a server within the client's content distribution network. When the client's content distribution network is not a primary content distribution network for the content provider and the client's content distribution network does not have a content peering relationship with a primary content distribution network for the content provider, redirecting the client to a server outside the client's content distribution network. The redirecting can be done using a domain name service (DNS) server that responds to requests for domain name resolution that include metadata encoding for the content being requested and / or attributes of the resolution request other than a domain name or explicit client / redirector communication to perform the redirection.
Owner:GOOGLE LLC
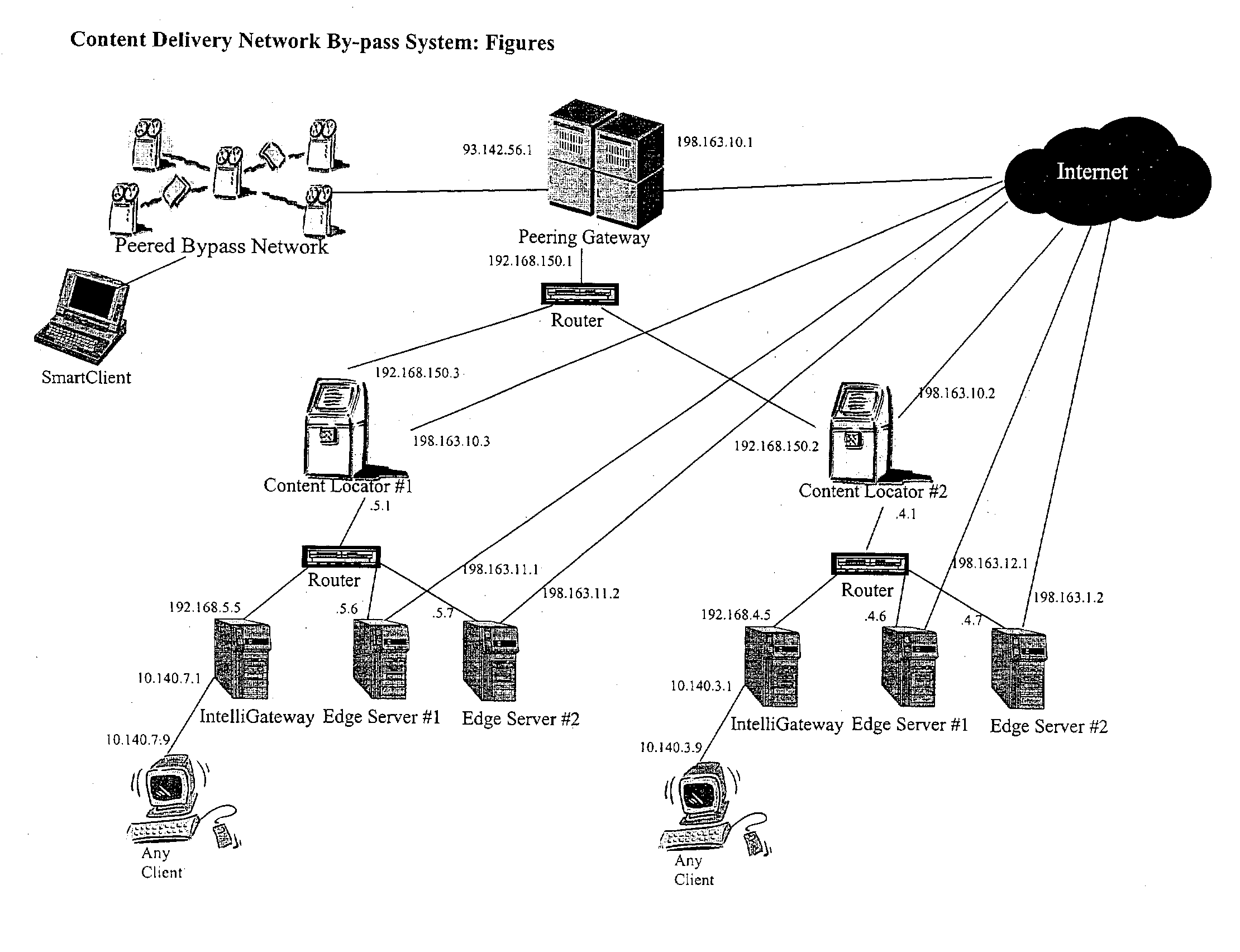
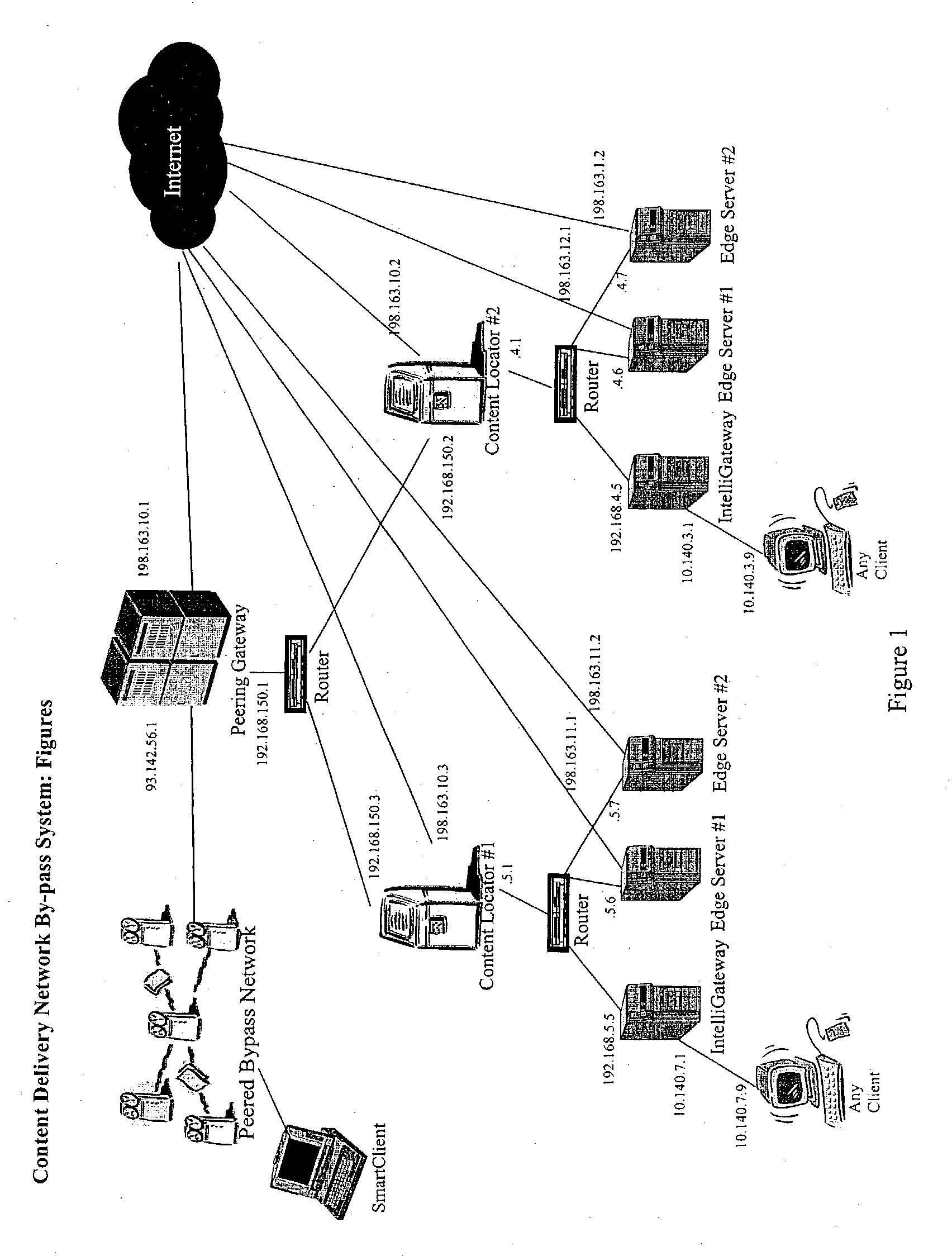
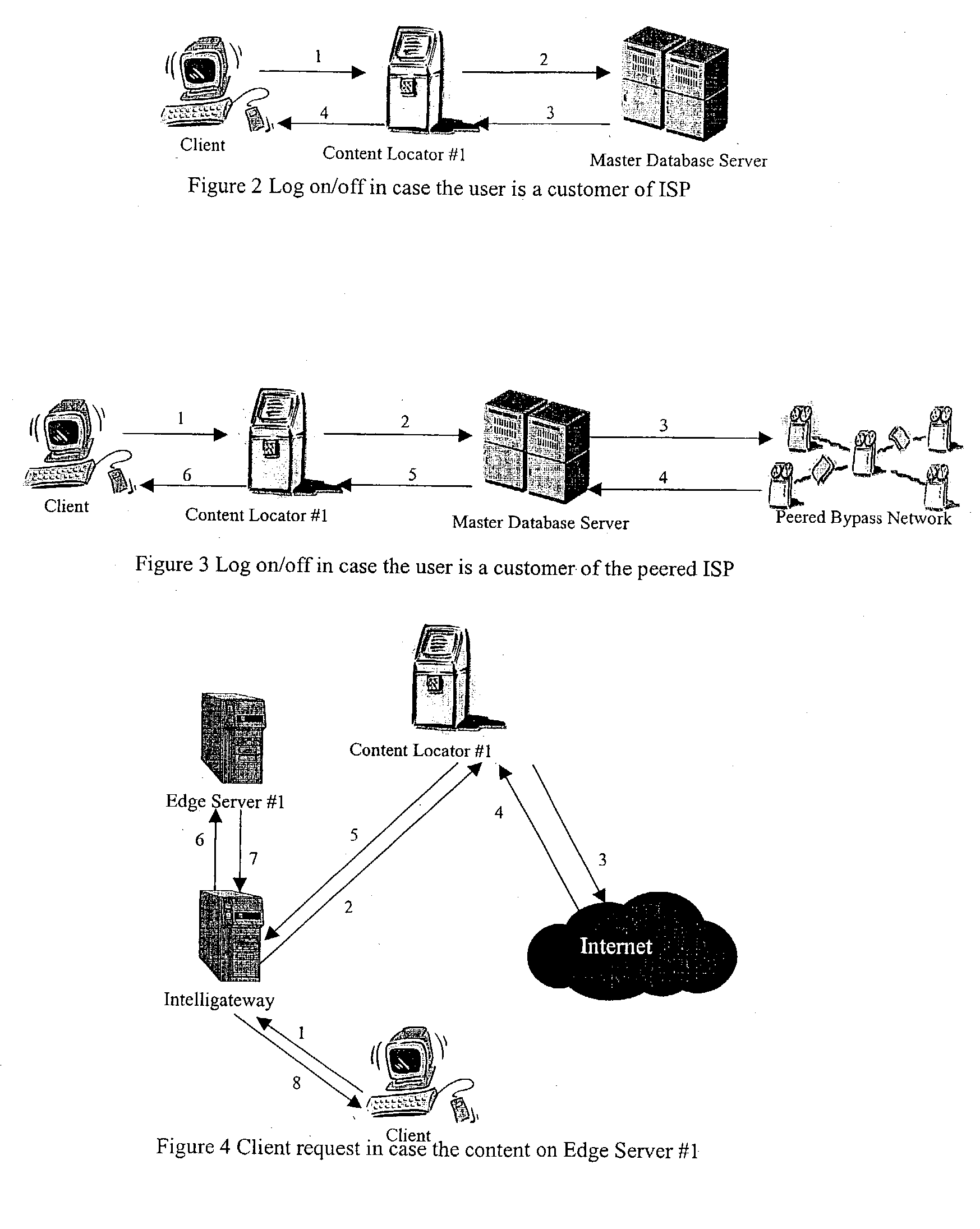
Content delivery network by-pass system
InactiveUS20030174648A1Increase capacityIncrease in sizeError preventionTransmission systemsWeb sitePeering
The bypass network is designed to provide fast access and high quality streaming media services anywhere anytime. There are five major components including Peering Gateway, Content Locator, Edge Server, Gateway and Client. The whole bypass network is divided into number of self-managed sub-networks, which are referred as local networks in this document. Each local network contains Edge Servers, gateways, and a Content Locator. The Edge Servers serve as cache storage and streaming servers for the local network. The gateways provide a connection point for the client computers. Each local network is managed by a Content Locator. The Content Locator handles all client requests by communicating with the Peering Gateway and actual web sites, and makes the content available on local Edge Servers. The Content Locator also balances the load on each Edge Server by monitoring the workload on them. One embodiment is designed for home users whose home machine does not move around frequently. A second embodiment is designed for business users who travel around very often where the laptops would self-configure as a client of the network.
Owner:TELECOMM RES LAB
Internet content delivery service with third party cache interface support
InactiveUS7010578B1Increase reachImprove performanceDigital data information retrievalMultiple digital computer combinationsThird partyOff the shelf
Third party cache appliances are configured into a content delivery service to enable such devices to cache and serve content that has been tagged for delivery by the service. The invention enables the content delivery service to extend the reach of its network while taking advantage of high performance, off-the-shelf cache appliances. If the third party caches comprise part of a third party content delivery network, the interconnection of caches to the CDS according to the present invention enables the CDS and the third party network to share responsibility for delivering the content. To facilitate such “content peering,” the CDS may also include a traffic analysis mechanism to provide the third party network with preferably real-time data identifying the content delivered by the CDS from the third party caches. The CDS may also include a logging mechanism to generate appropriate billing and reporting of the third party content that is delivered from the cache appliances that have been joined into the CDS.
Owner:AKAMAI TECH INC
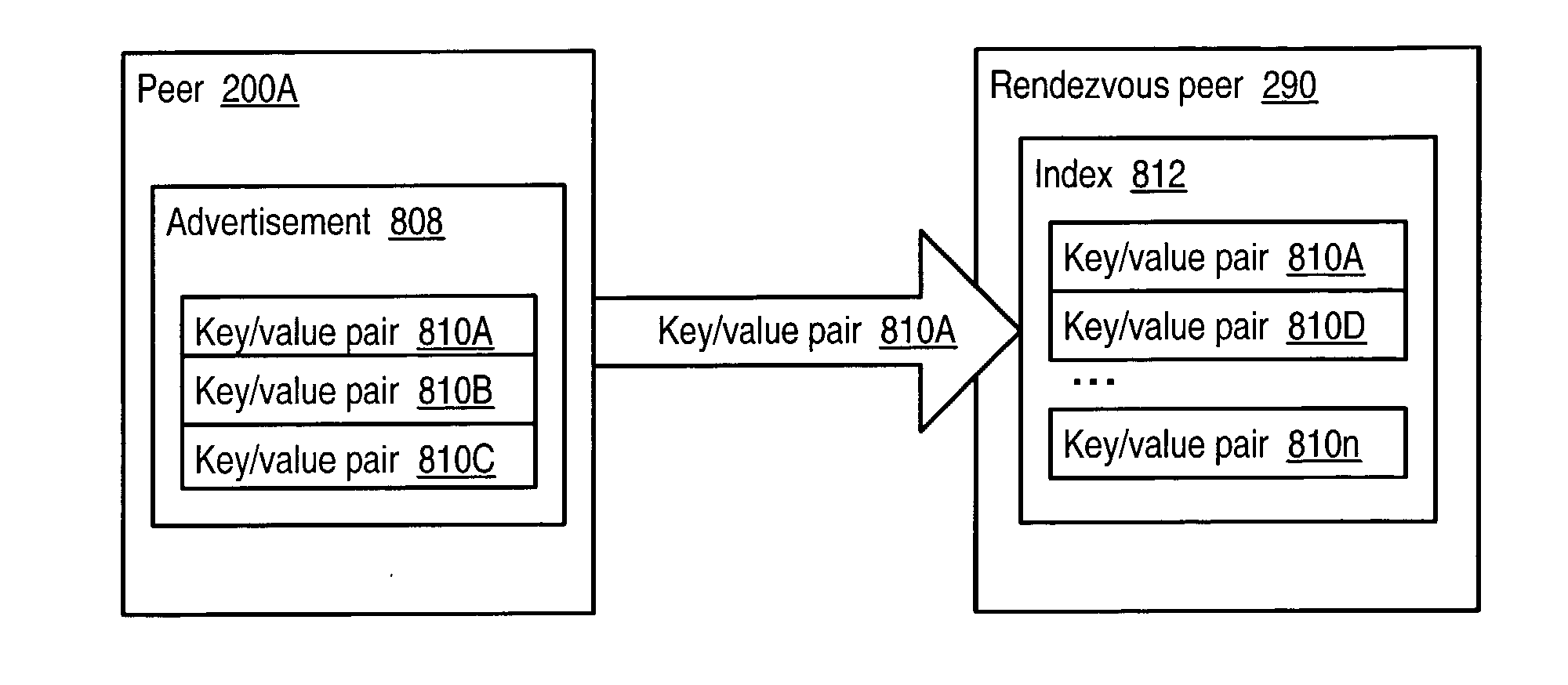
Decentralized peer-to-peer advertisement
Embodiments of a shared resource distributed index mechanism that peers in a peer-to-peer network may utilize to distribute index entries corresponding to resources to indexes of shared resources among one or more other peers. These indexes may be used to direct queries to peers where the queries are most likely to be answered. When a query is received by a rendezvous peer including one or more indexes, contents of the query may be "looked up" in the index to find matches. The results of the lookup may include information on one or peer(s) that may hold advertisement(s) to the resource requested by the query. The query may then be forwarded to one or more peers that may hold the advertisement for the resource. Embodiments may provide "loosely-coupled" distribution of index entries for use in querying for resources in the peer-to-peer network.
Owner:ORACLE INT CORP
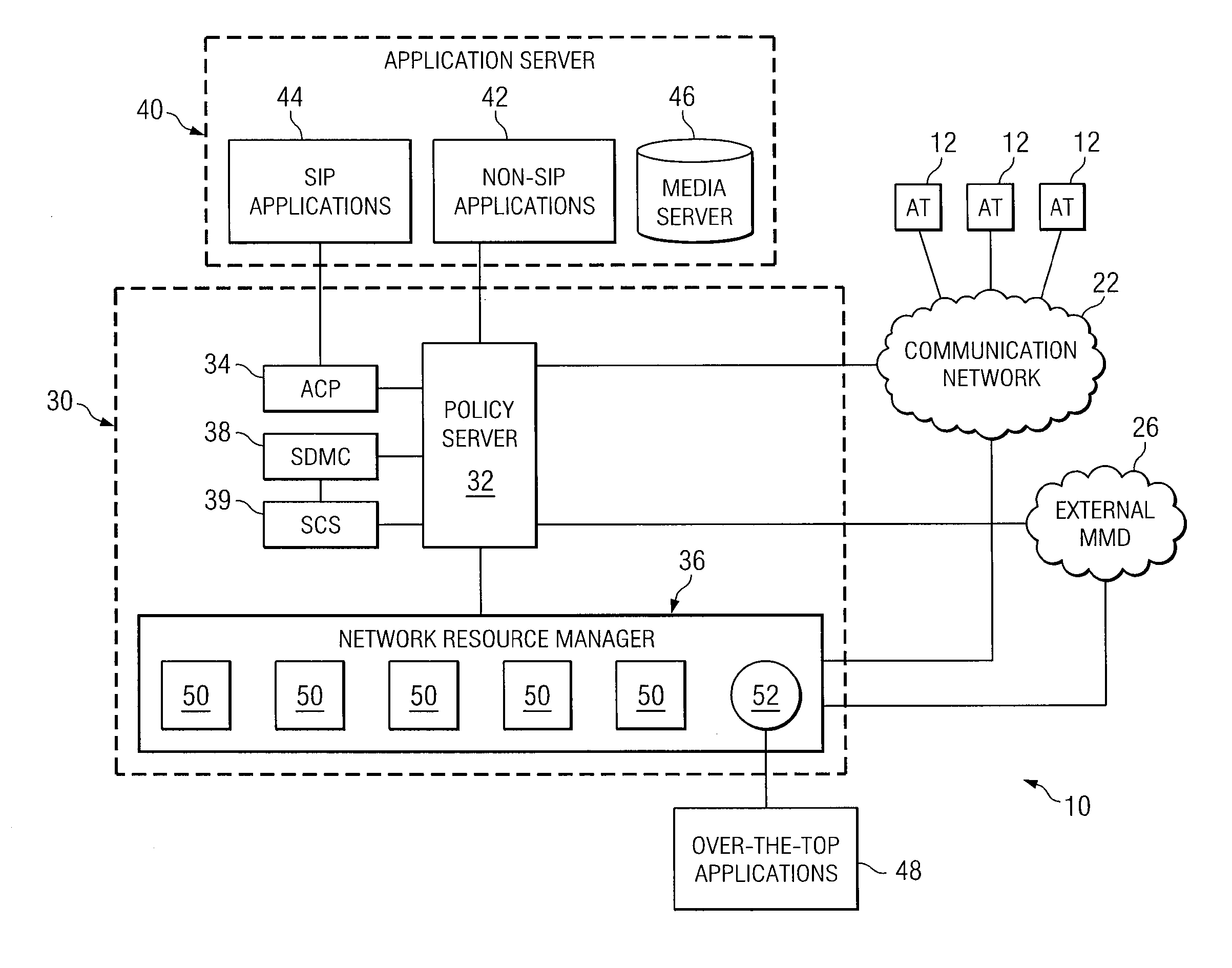
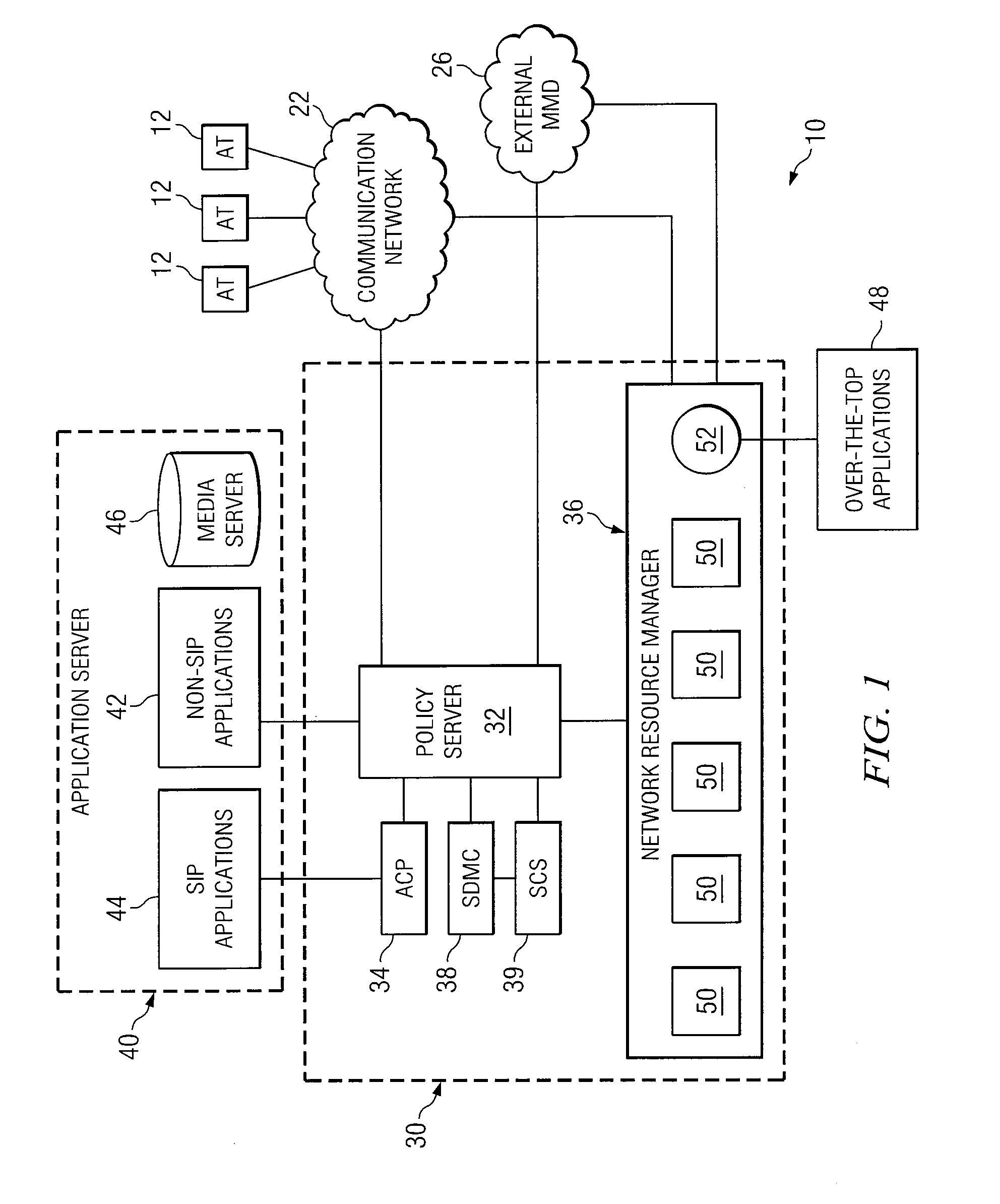
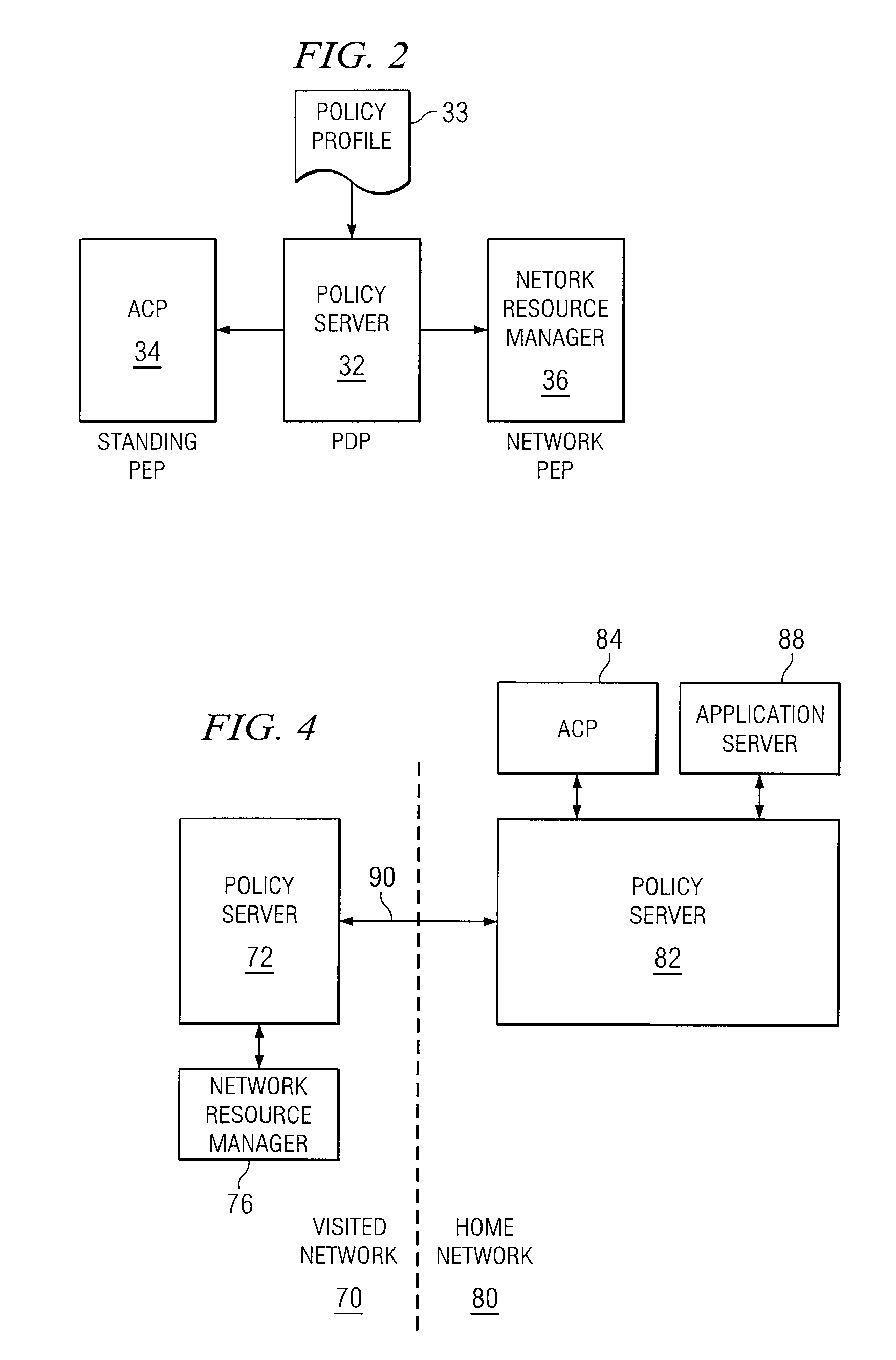
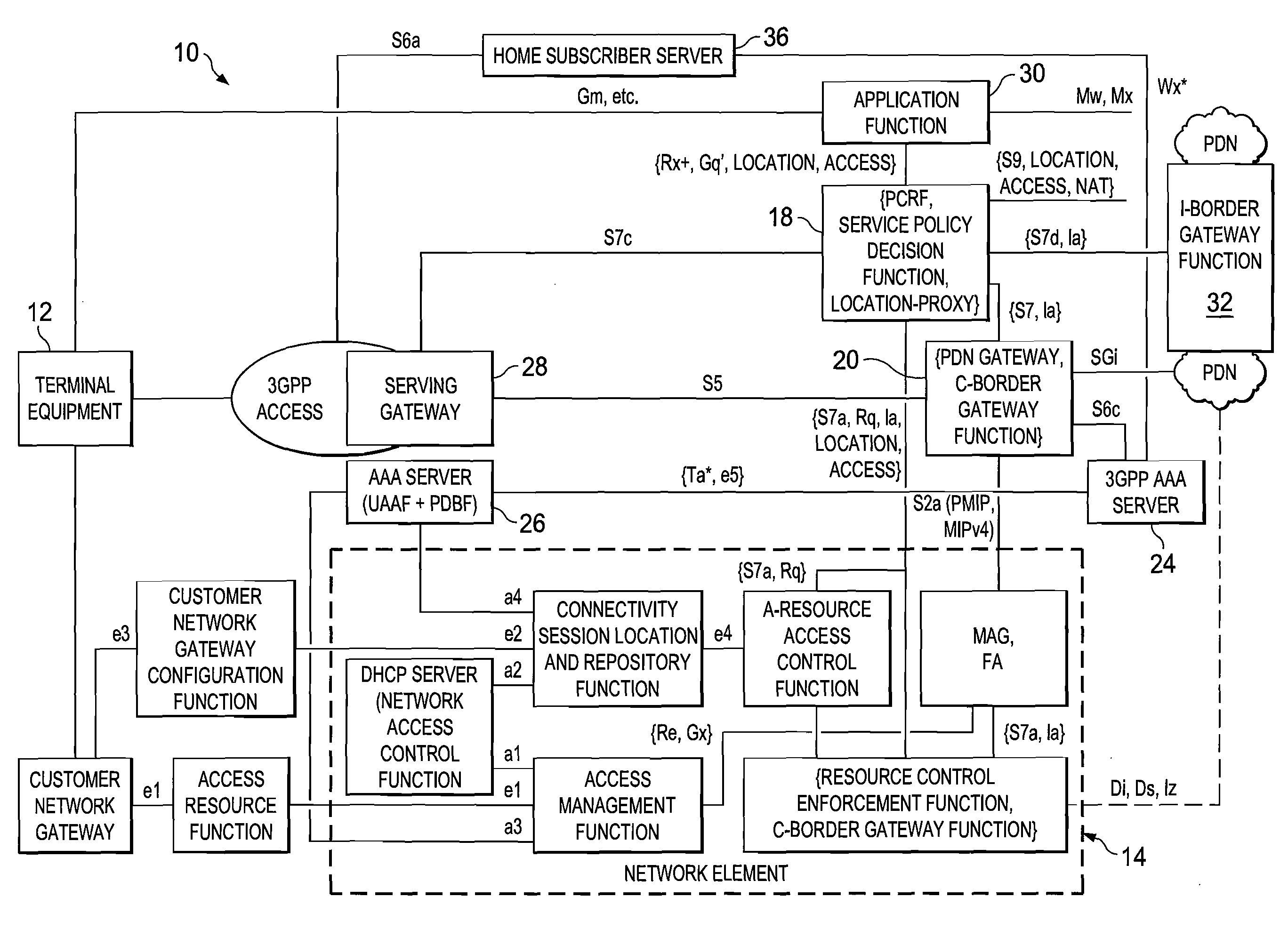
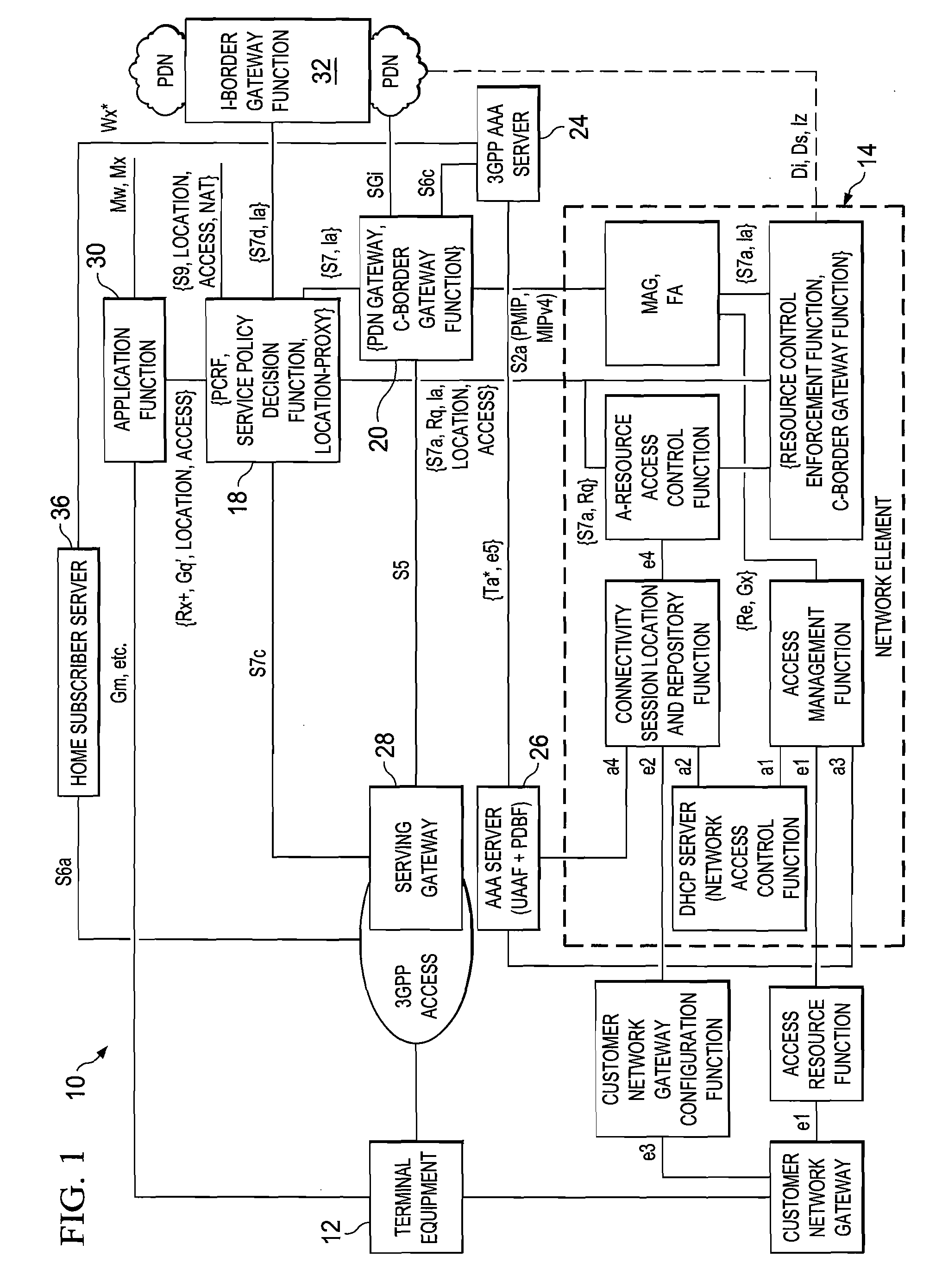
System and Method for Enforcing Policy in a Communication Network
ActiveUS20070226775A1Eliminates and reduces disadvantageEliminates and reduces and problemDigital data processing detailsUser identity/authority verificationNetwork resource managementPeering
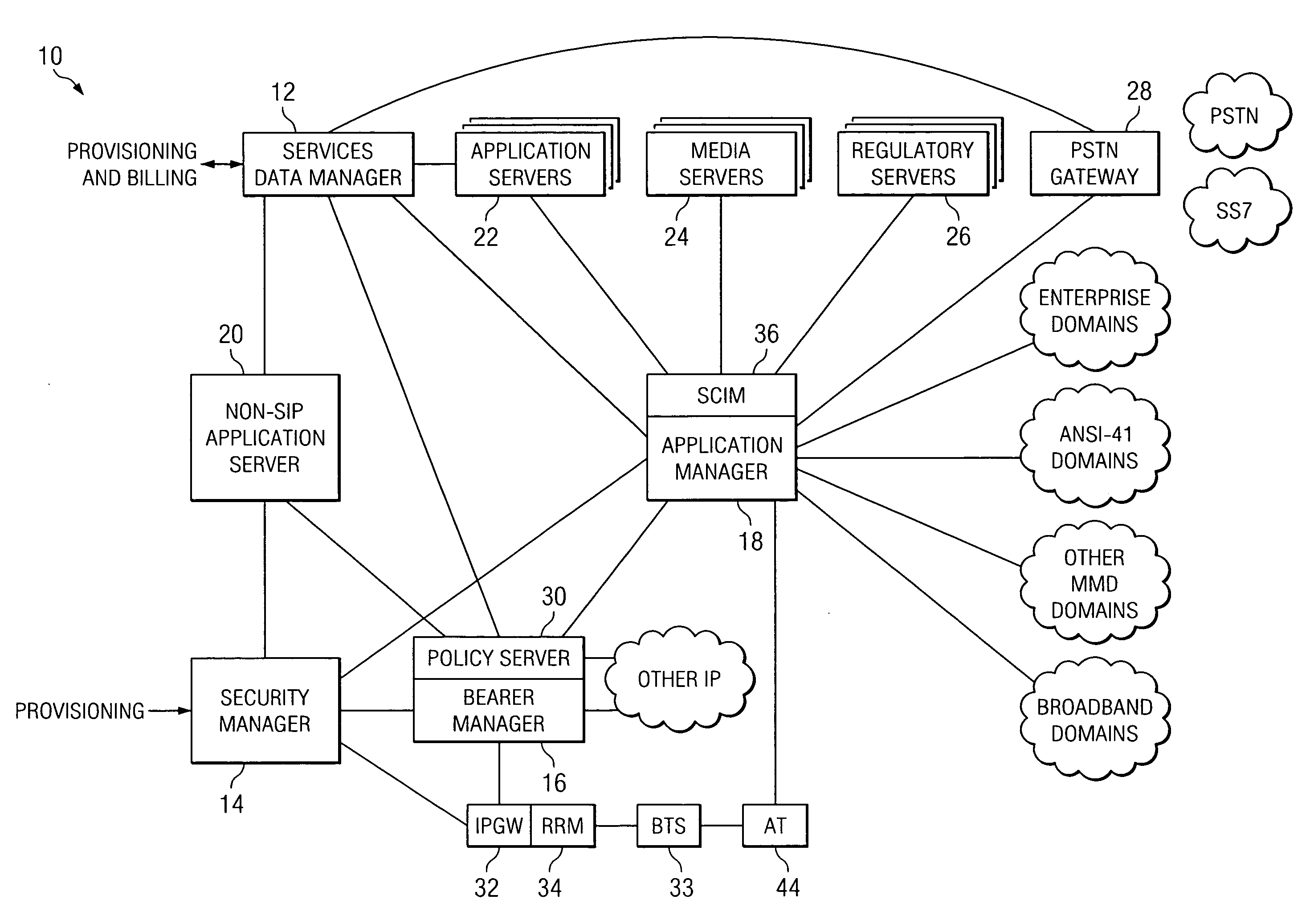
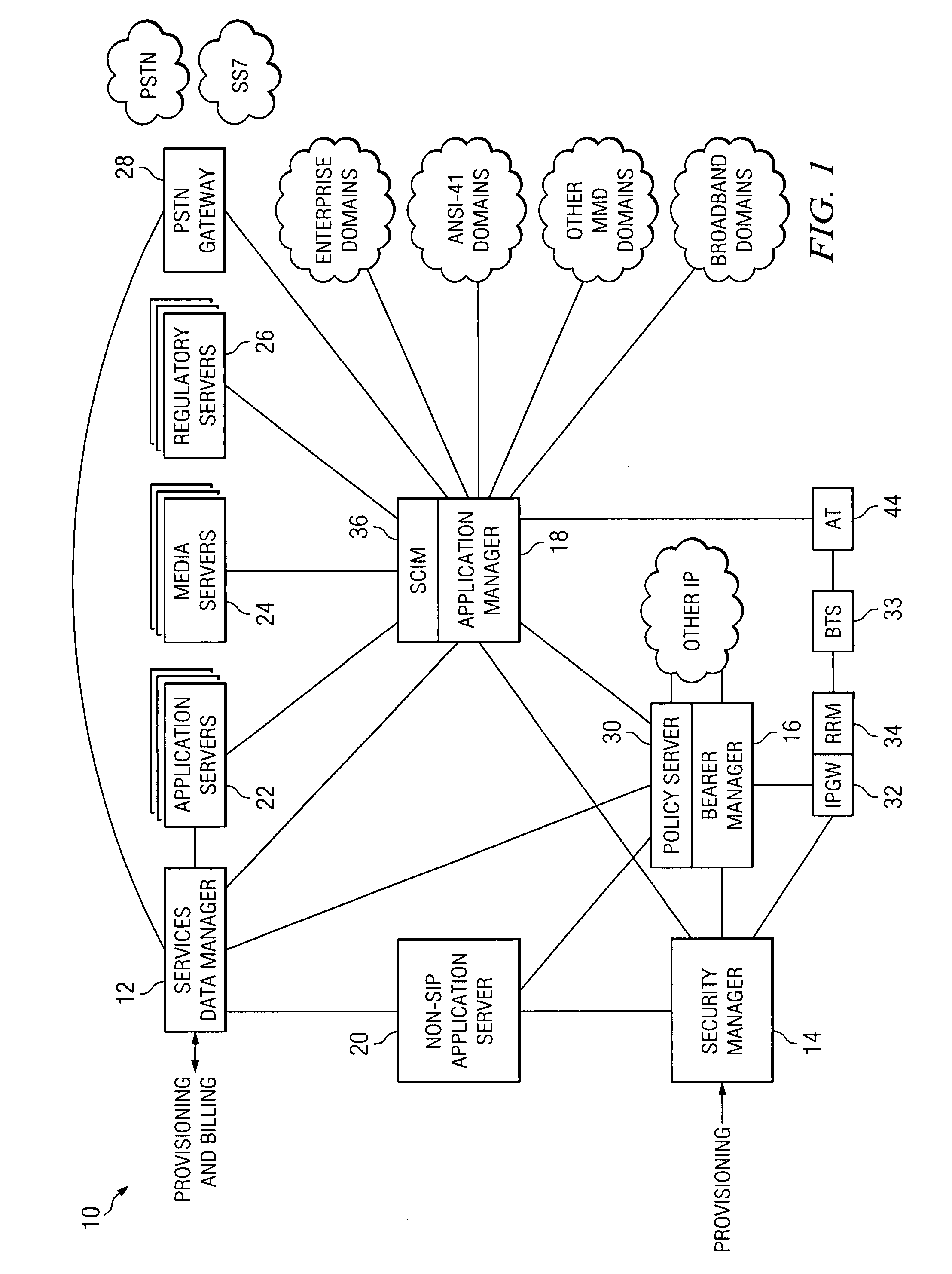
A system for enforcing policy in a communication network includes a policy server which is operable to receive a request to invoke an application, receive a policy profile for a network user, and decide a proper allocation of network users based on the policy profile, the application, and available network resources. The policy server is further operable to communicate with a non-SIP application. The system also includes a network resource manager operably associated with the policy server and operable to monitor available network in the resources in the communication network. In addition, the network resource manager is functional to allocate network resource amongst a plurality of network users. The system also contains an application control point which is operably associated with the policy server and operable to communicate with a SIP application. The system is operable to use policy peering between the home and visited network to enable user-specific policies to be enforced while roaming.
Owner:CISCO TECH INC
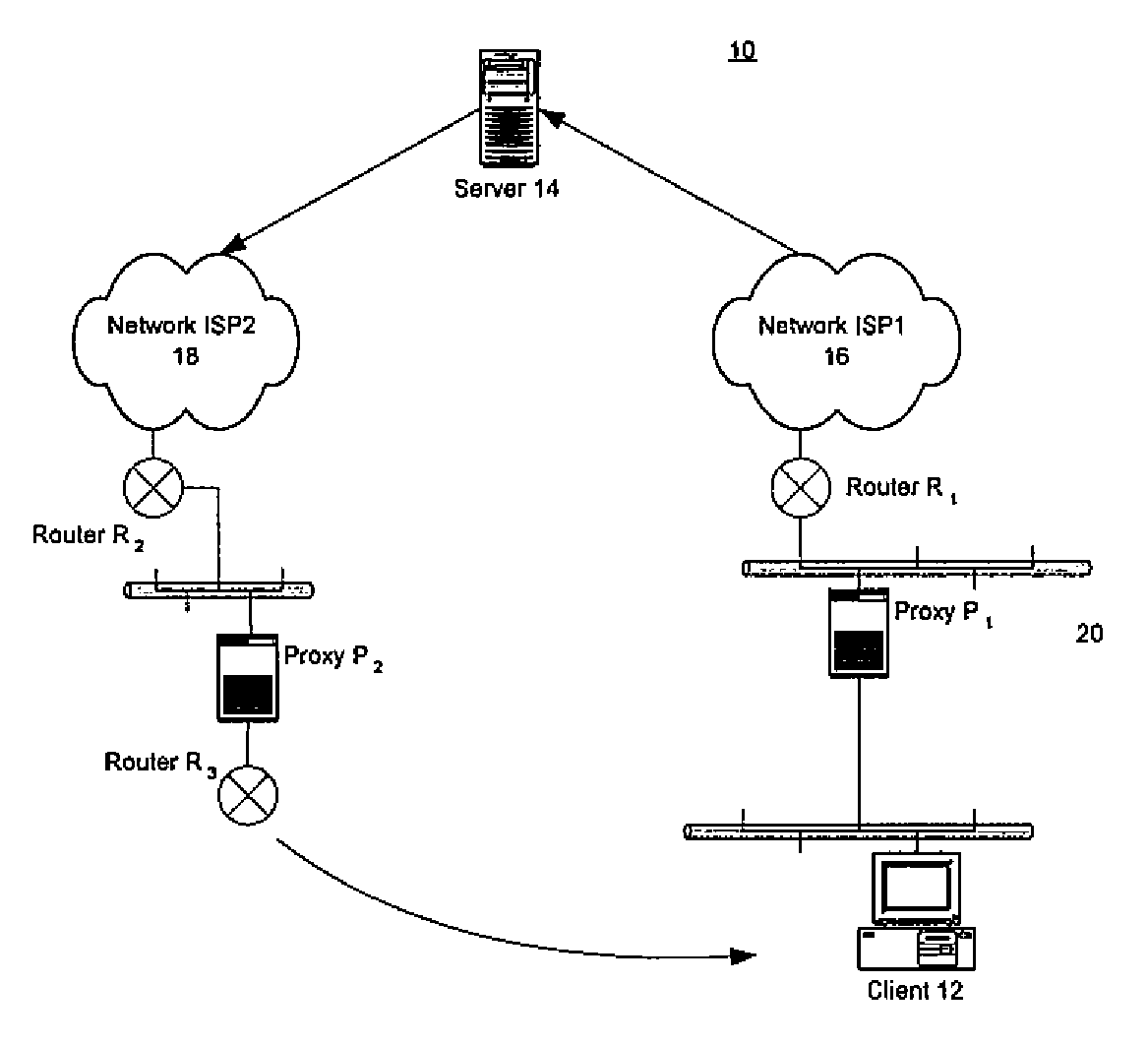
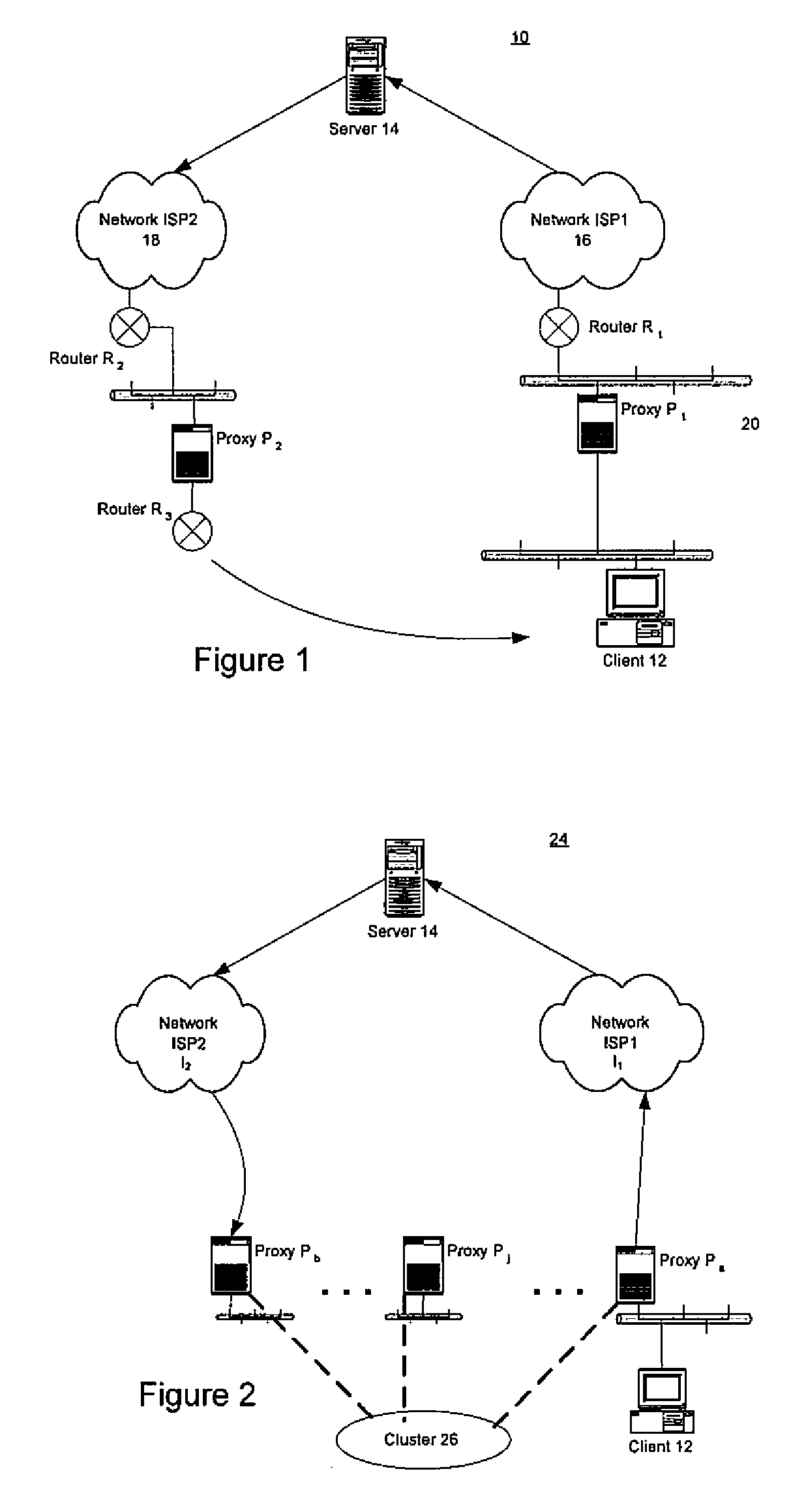
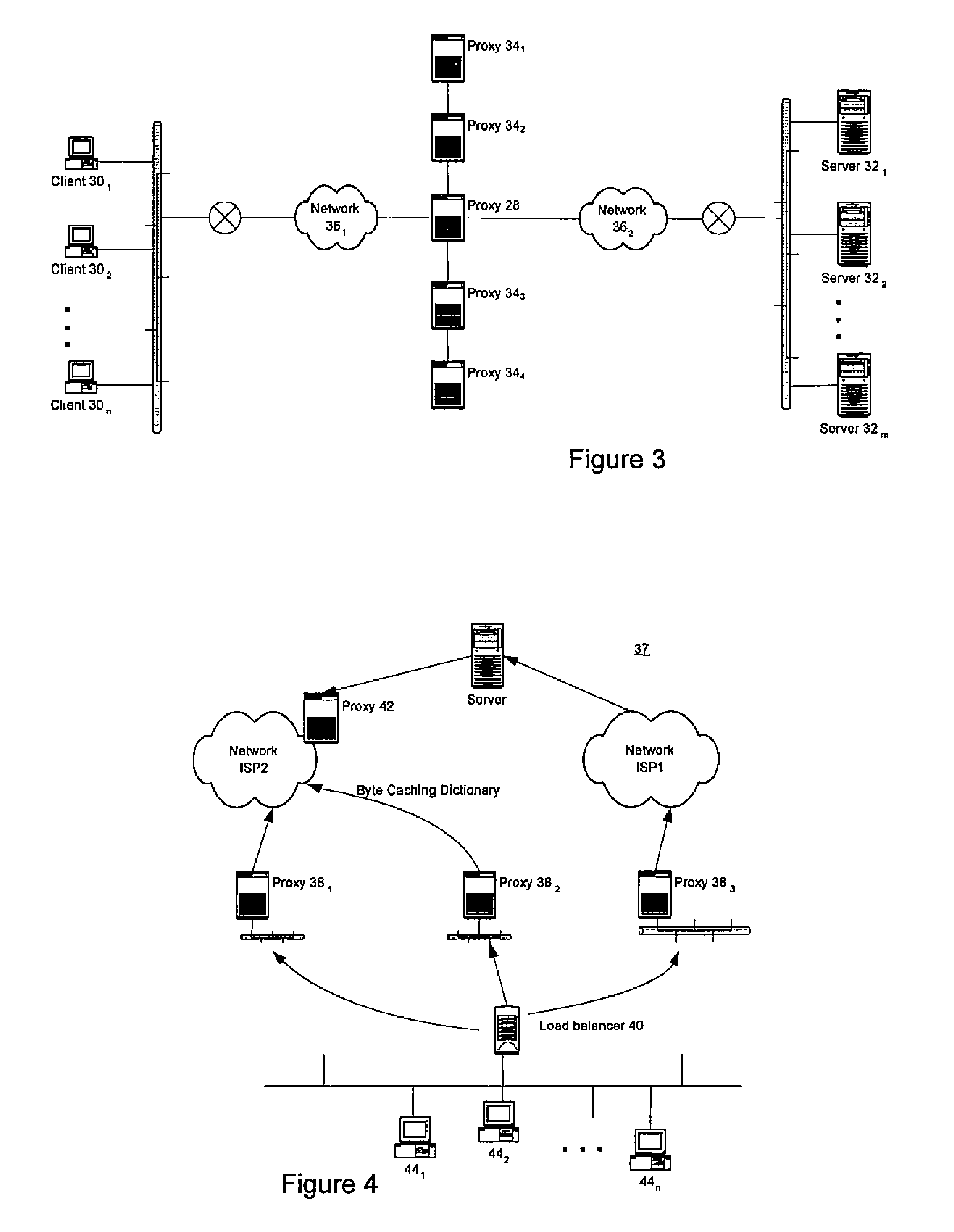
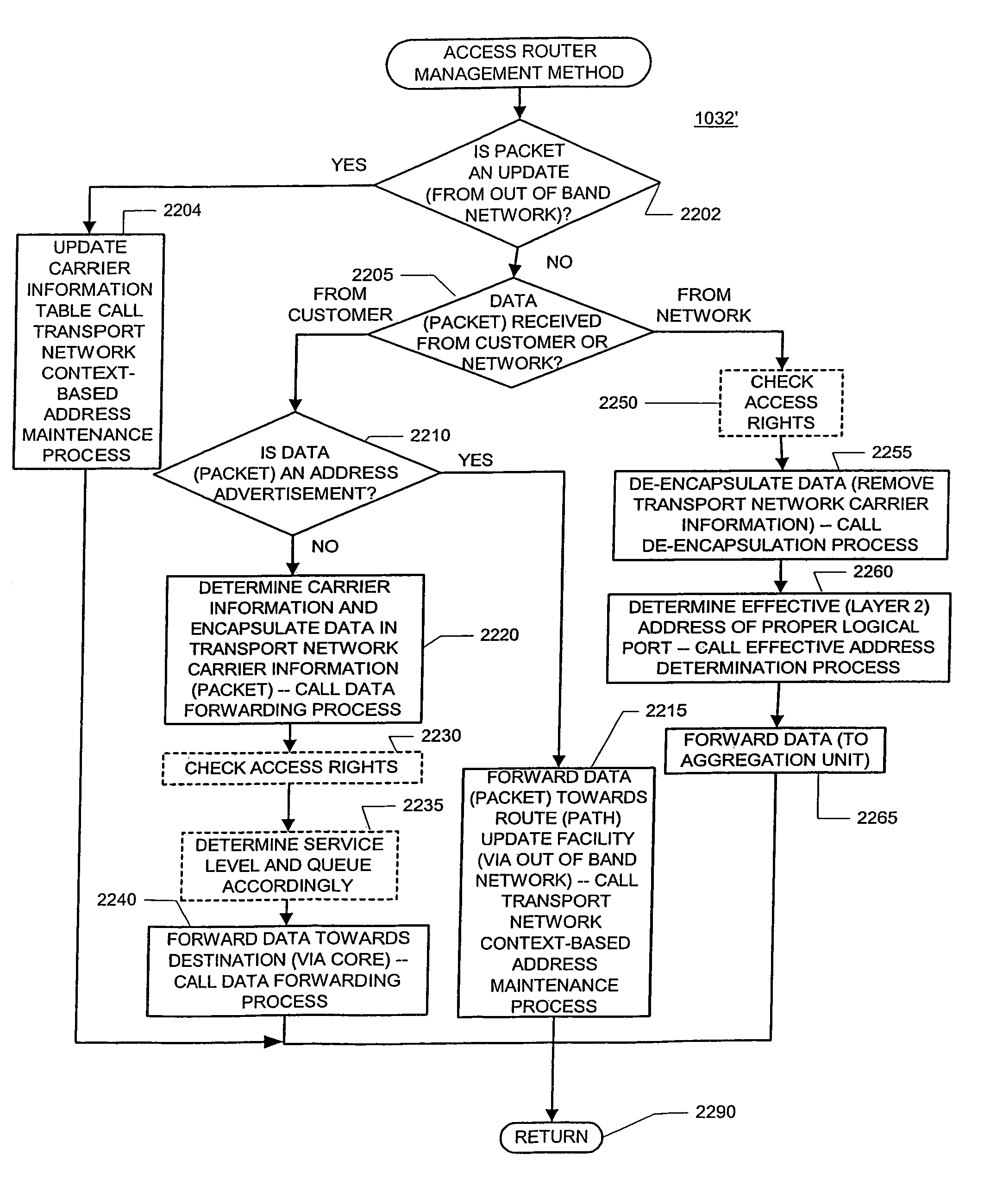
Simple peering in a transport network employing novel edge devices
Simple peering is provided in a novel network in which transport technology is independent of network access technology. An out-of-band network may be used to carry advertisements to an update facility. The update facility may use layer 3 destination address information and at least a part of context information (to identify customers uniquely) to determine a layer 3 address of an edge device of the transport network associated with an addressed customer device. Virtual private networks are supported, as context information is used to distinguish different customers with overlapping layer 3 addresses.
Owner:VERIZON PATENT & LICENSING INC
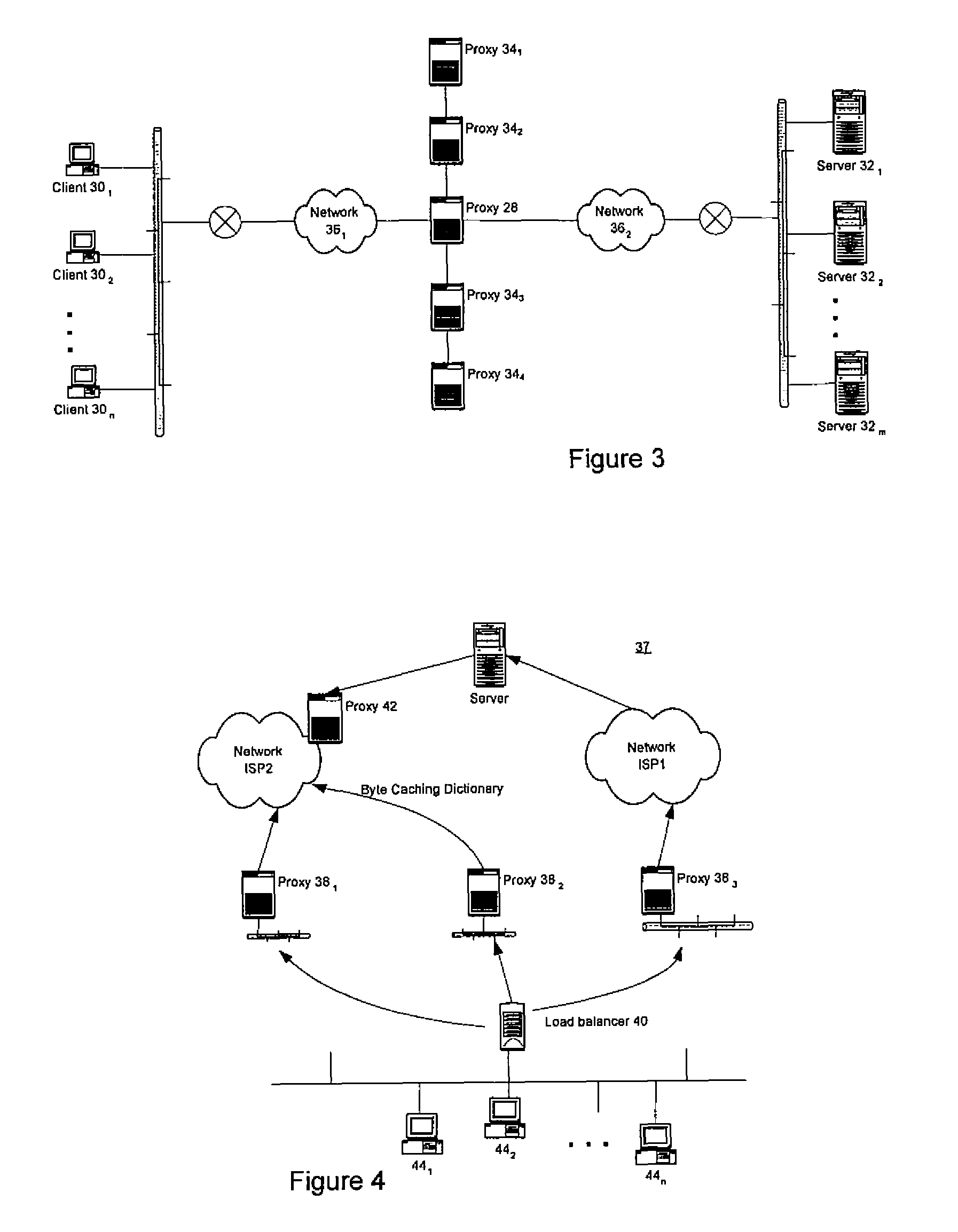
Method and apparatus for content distribution network brokering and peering
InactiveUS7562153B2Multiple digital computer combinationsMemory systemsContent distributionTraffic characteristic
The present invention provides an architecture that advantageously leverages multiple content distribution networks to provide enhanced services. In accordance with an embodiment of the present invention, a share of content requests are served by each of a plurality of content distribution networks. The fraction of content requests served by a particular content distribution network can be determined dynamically, depending on the offered load or other traffic characteristics.
Owner:GOOGLE LLC
Content distribution system for operation over an internetwork including content peering arrangements
InactiveUS7734730B2Special service provision for substationMultiple digital computer combinationsContent distributionDomain name
Owner:GOOGLE LLC
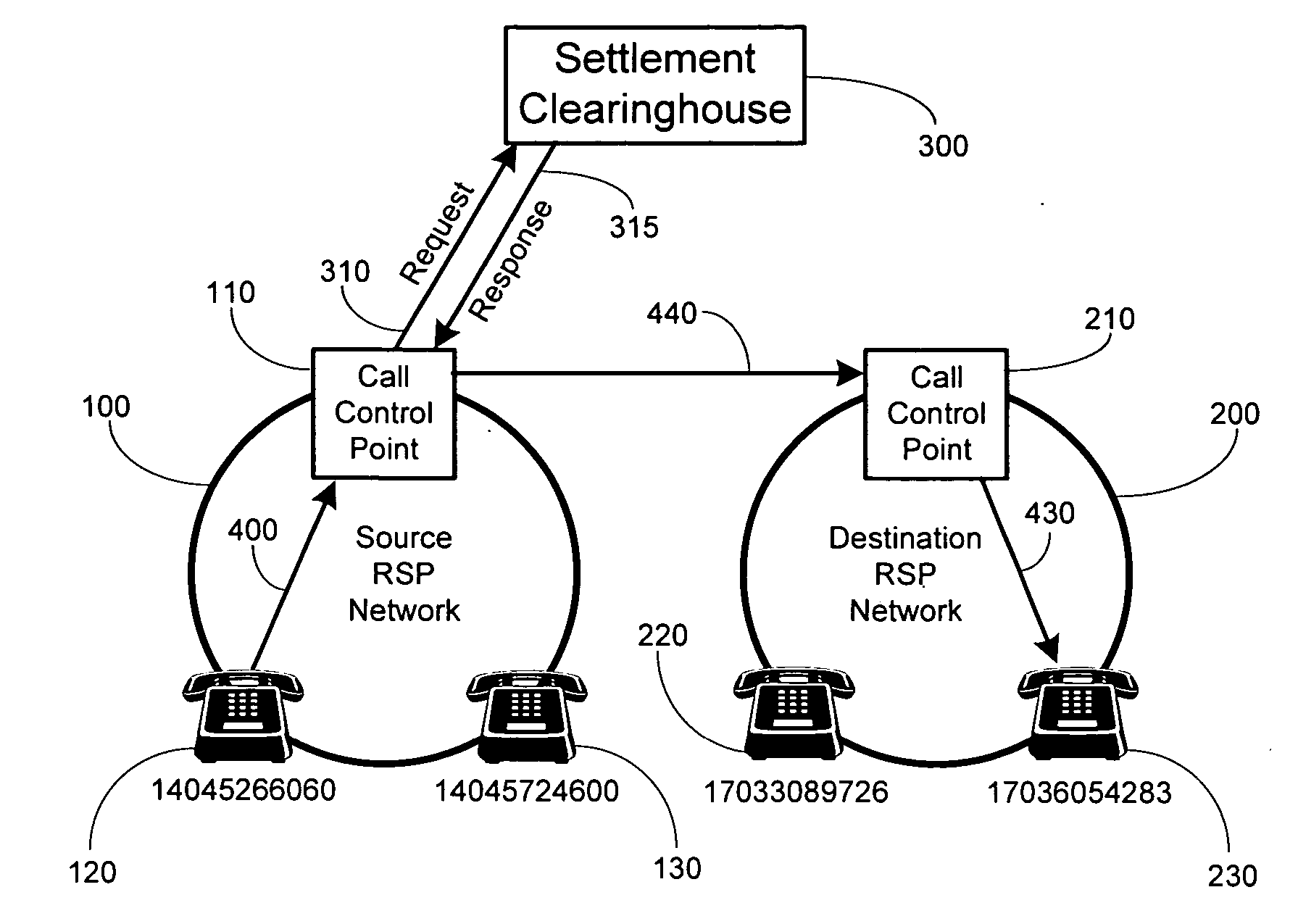
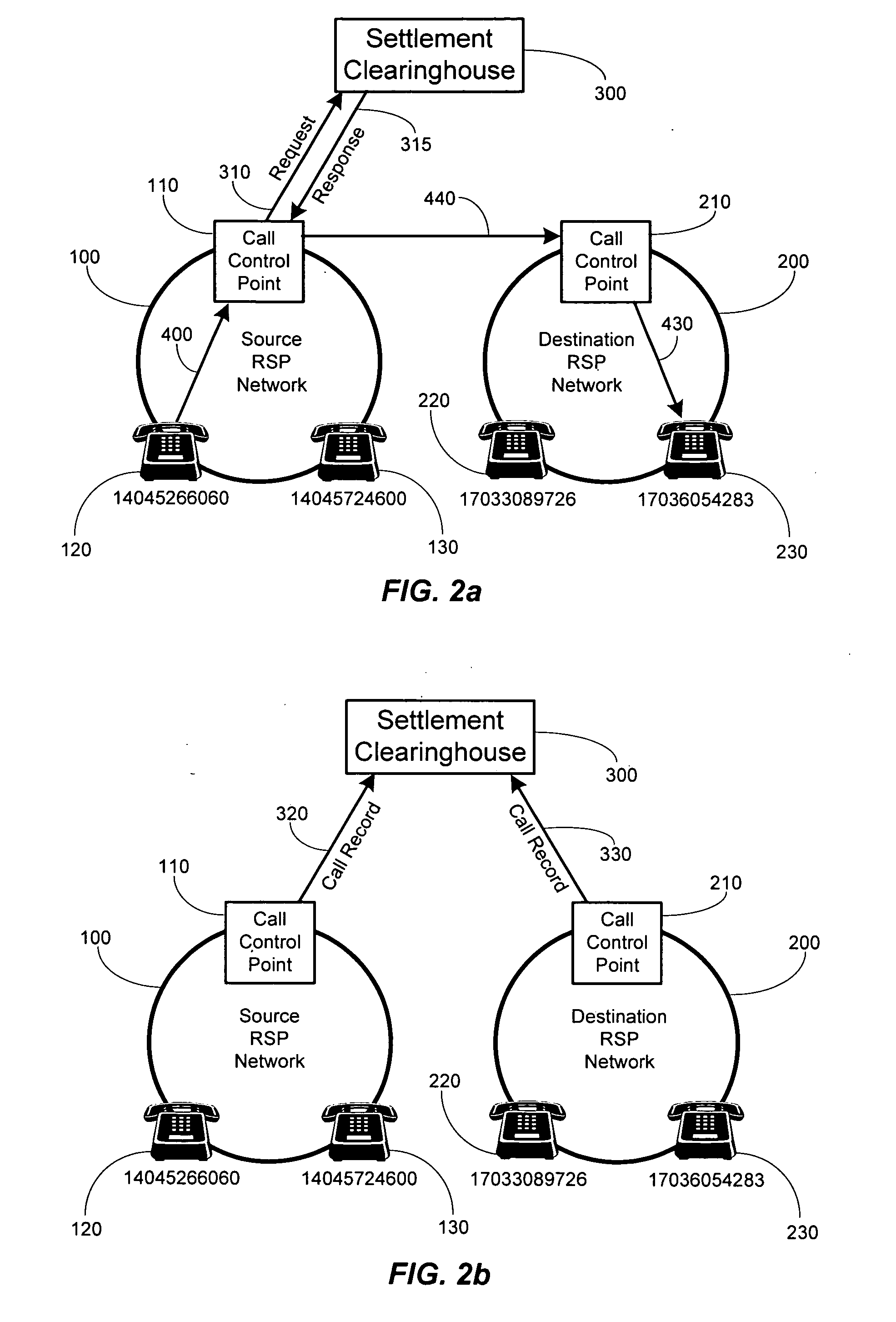
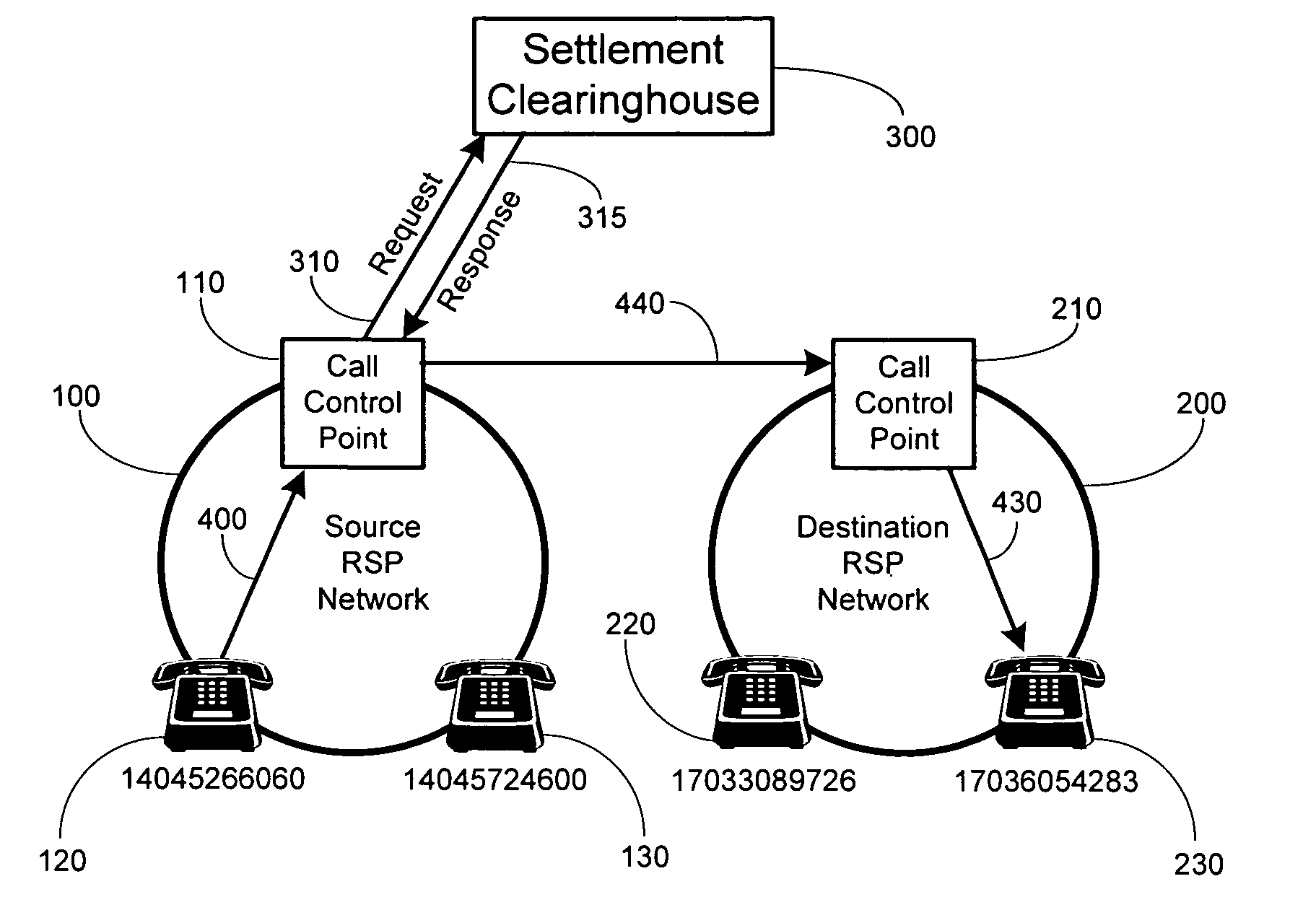
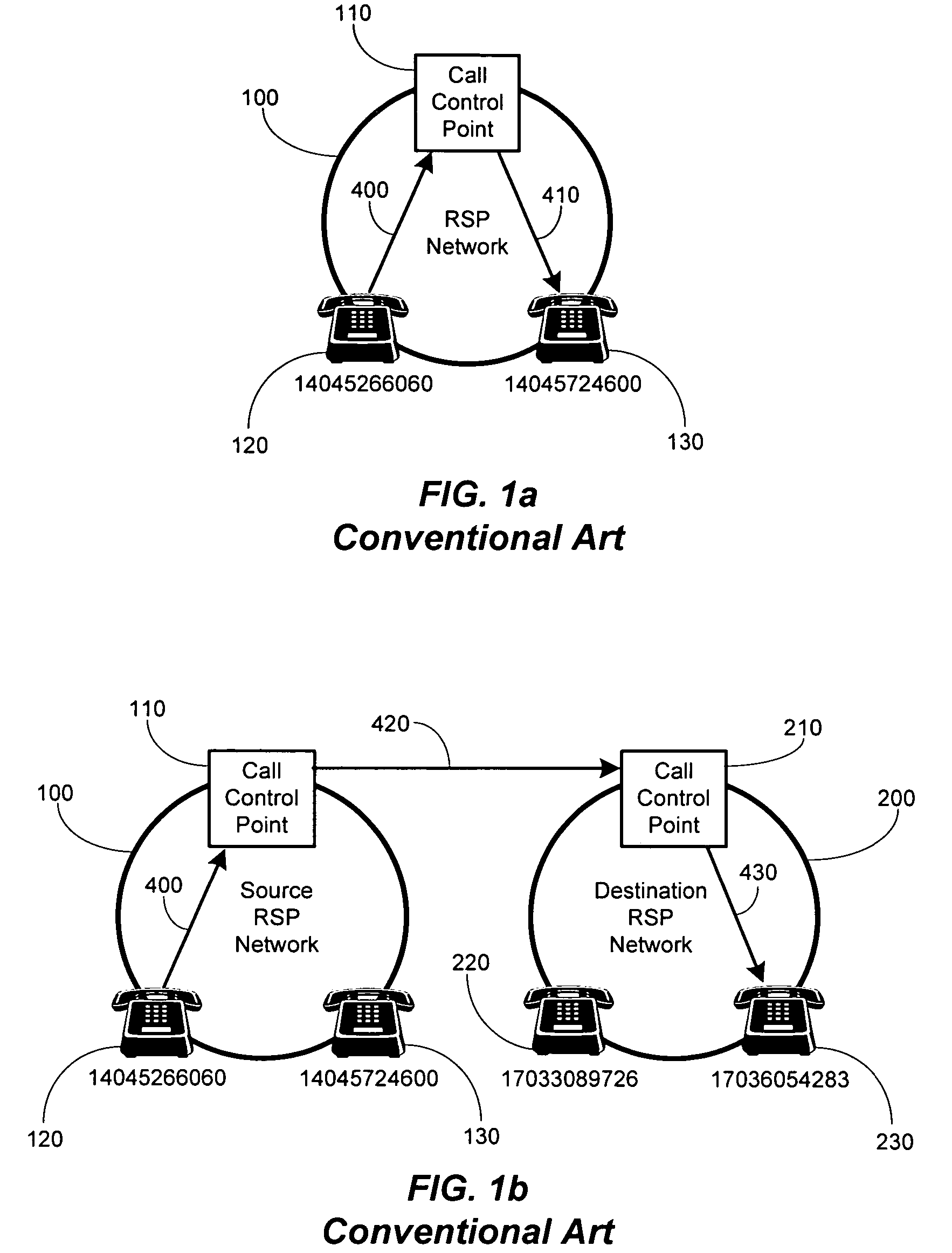
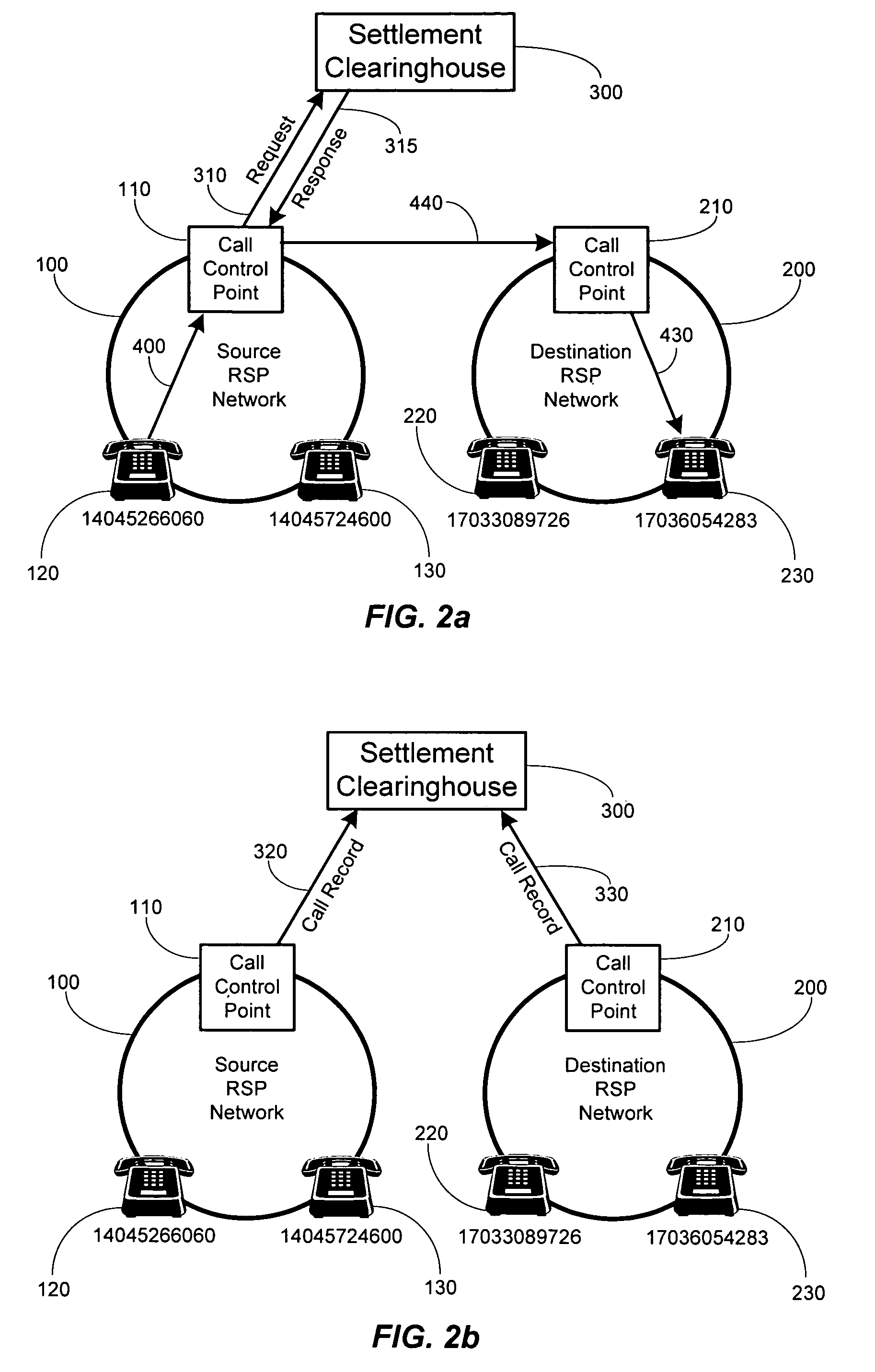
Method and system for securely authorized VoIP Interconnections between anonymous peers of VoIP networks
ActiveUS20060165068A1Safe collectionMetering/charging/biilling arrangementsAutomatic exchangesQuality of servicePeering
A peering authority or settlement clearinghouse can be used to control access, collect session accounting information, and provide financial settlement of interconnect or session fees among anonymous Internet Protocol (IP) peers or networks. The addition of peering policy criteria, such as price and quality of service, to peer to peer route discovery mechanisms enable a trusted intermediary, such as the settlement clearinghouse, to authorize acceptable interconnection or peering sessions between anonymous IP peers. Any financial settlement transactions which result from the peering sessions may be subsequently executed by the settlement clearinghouse.
Owner:TRANSNEXUS
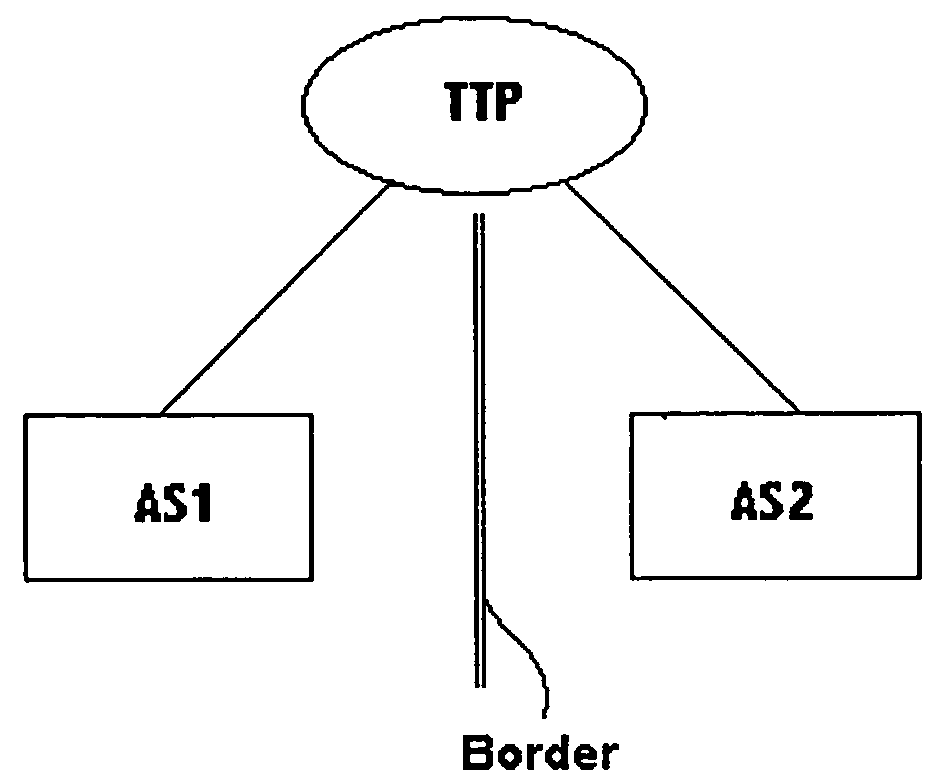
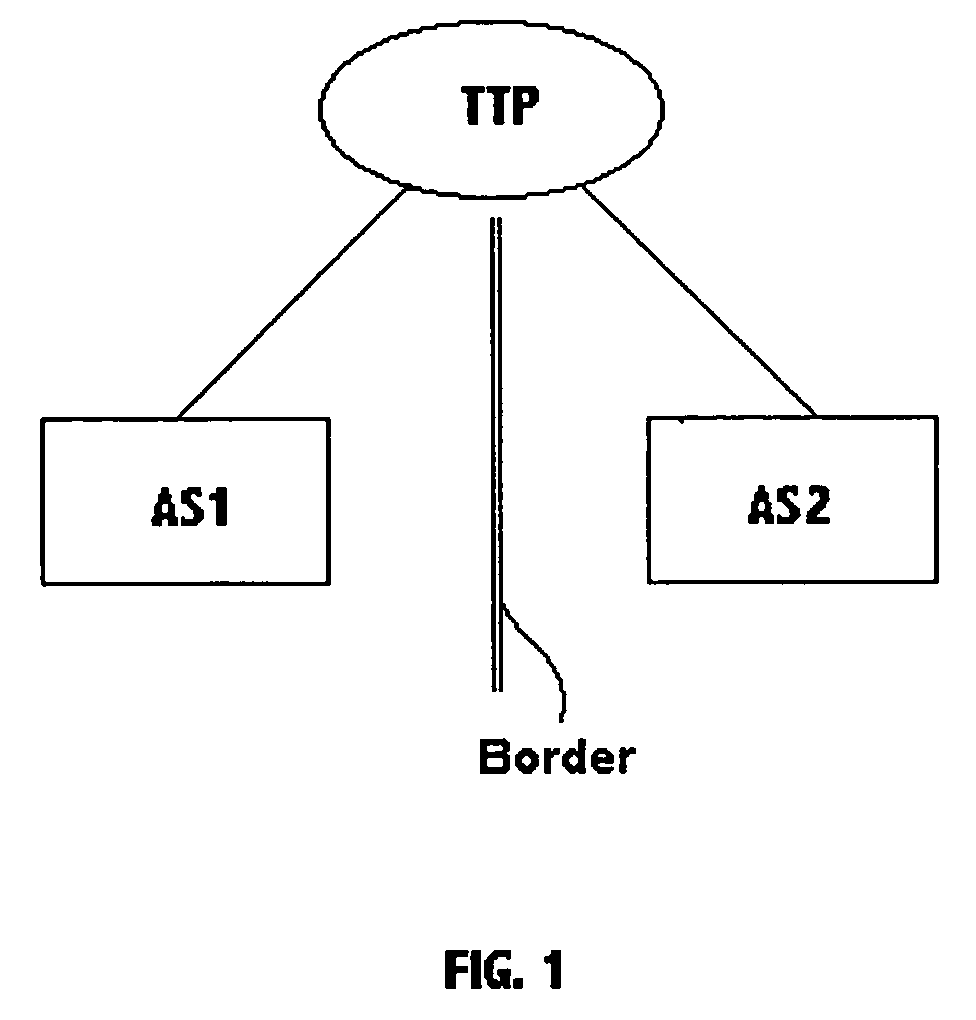
Multicast peering
InactiveUS20050108419A1Reduce the amount of informationSpecial service provision for substationMultiple digital computer combinationsThird partyPeering
Multicast peering in commercial Internets is performed by a trusted third party which has a connection into two or more Autonomous Systems. Multicast streams pass from the trusted third party into the Autonomous Systems independently. There is thus no need for any sharing of information between the Autonomous Systems, with any information sharing taking place only between each Autonomous System and the trusted third party.
Owner:EUBANKS THOMAS MARSHALL
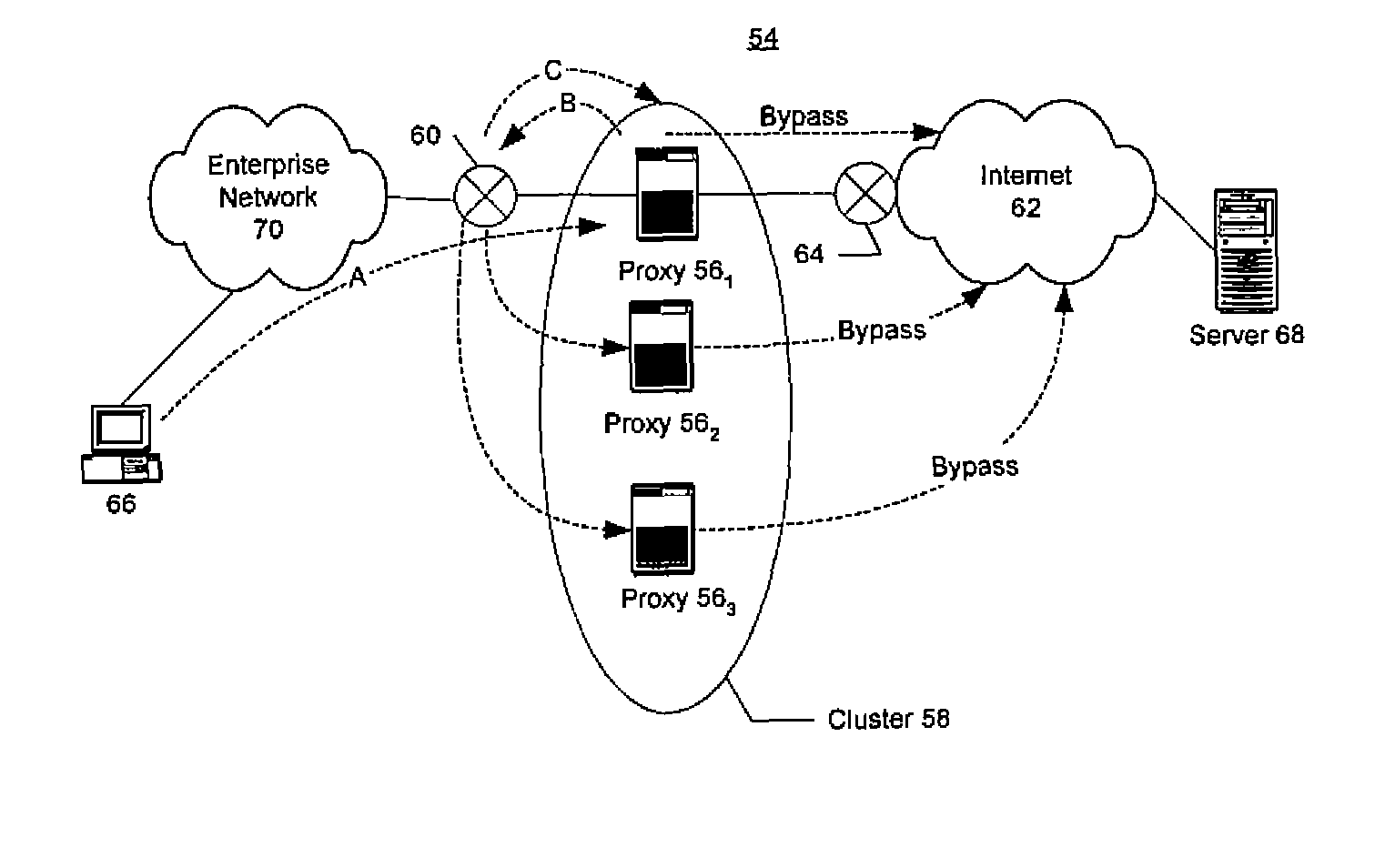
System and Method of Traffic Inspection and Stateful Connection Forwarding Among Geographically Dispersed Network Appliances Organized as Clusters
A peering relationship among two or more network appliances is established through an exchange of control messages among the network appliances. The peering relationship defines a cluster of peered network appliances, and at each network appliance of the cluster traffic flow state information for all the network appliances of the cluster is maintained. Network traffic associated with traffic flows of the network appliances of the cluster is managed according to the state information for the traffic flows. This managing of the network traffic may include forwarding among the network appliances of the cluster (i.e., to those of the appliances handling the respective flows) at least some of the network traffic associated with one or more of the traffic flows according to the state information for the one or more traffic flows. The traffic flows may be TCP connections or UDP flows.
Owner:CA TECH INC
Simple peering in a transport network employing novel edge devices
InactiveUS7315554B2Updating of informationTime-division multiplexNetworks interconnectionPeeringPrivate network
Simple peering is provided in a novel network in which transport technology is independent of network access technology. An out-of-band network may be used to carry advertisements to an update facility. The update facility may use layer 3 destination address information and at least a part of context information (to identify customers uniquely) to determine a layer 3 address of an edge device of the transport network associated with an addressed customer device. Virtual private networks are supported, as context information is used to distinguish different customers with overlapping layer 3 addresses.
Owner:VERIZON PATENT & LICENSING INC
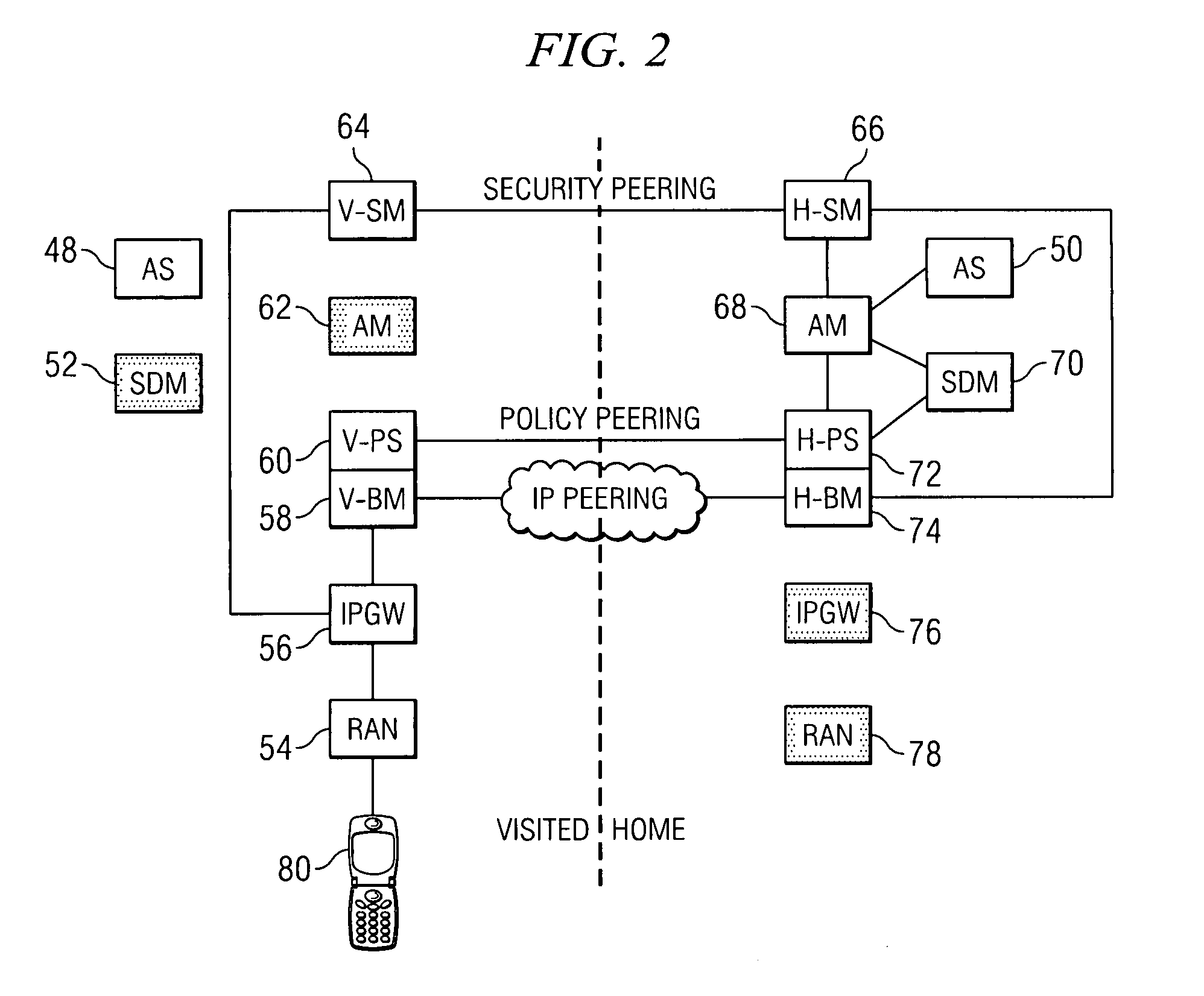
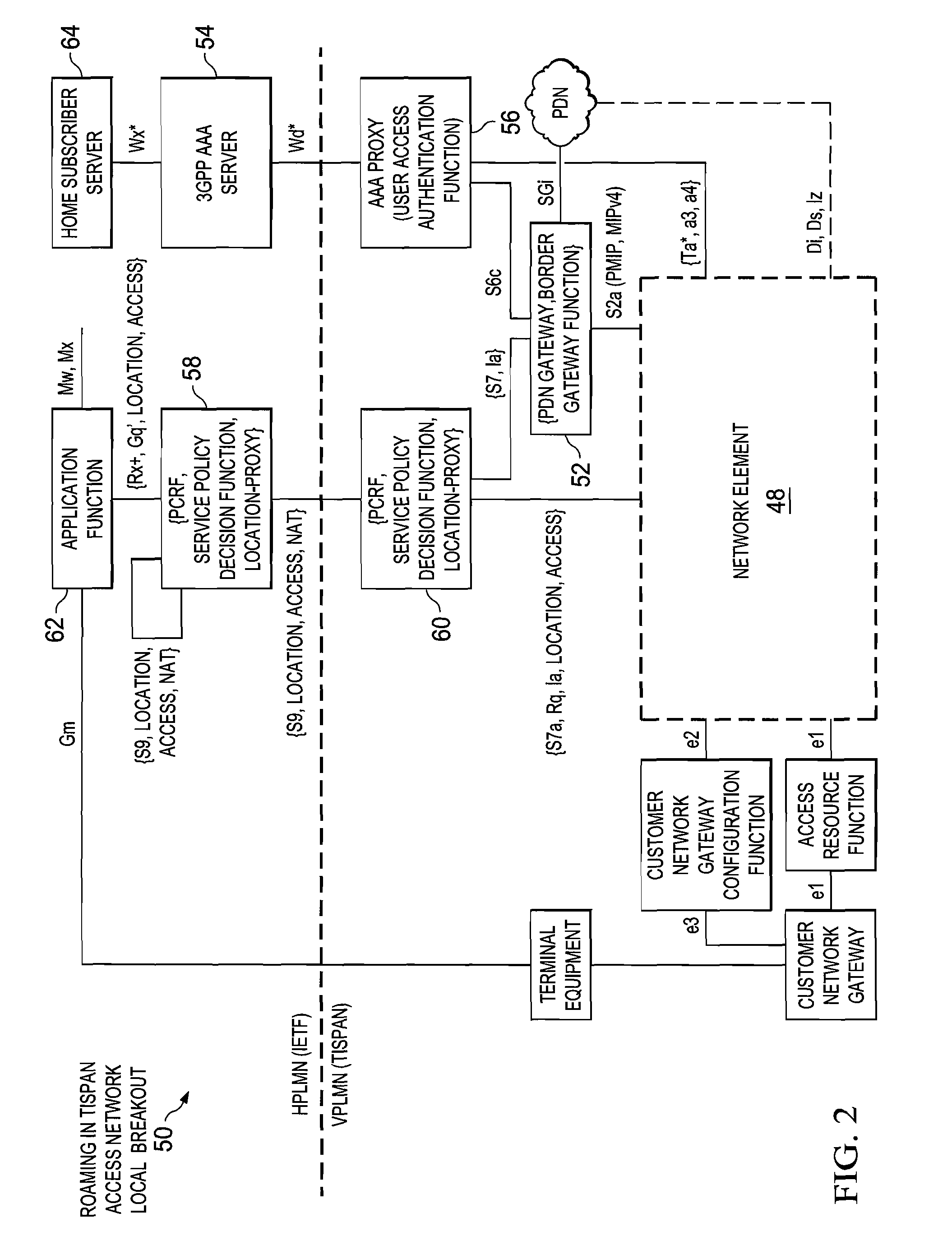
System and method for exchanging policy information in a roaming communications environment
ActiveUS20070207818A1Reduce disadvantagesReduce problemsMetering/charging/biilling arrangementsNetwork traffic/resource managementPolicy decisionAccess network
An apparatus for optimizing roaming in a network environment is provided that includes a bearer manager operable to receive a registration request from a user. An identity of a visited network and access network information is included with the request, a bearer manager consulting the policy server for a policy decision as part of an IP-address assignment or mobile IP registration process. The policy server providing the assigned IP-address, a visited network provider identity and access network information to a home policy server via policy peering. The policy server authorizing the registration and remembering the identity of the visited network provider and the access network information, whereby when the user performs registration, an application manager can request authorization from the policy sever, which checks the identity of the visited network and possible the access network and determines whether to authorize the registration.
Owner:CISCO TECH INC
System and method for providing a converged wireline and wireless network environment
InactiveUS20090207759A1Special service provision for substationMultiplex system selection arrangementsAccess networkPeering
A method is provided in one example embodiment and includes receiving packets for a communications flow from an end user that can conduct the flow through a wireless network and through a wireline network. The method also includes providing policy control for the end user at a network element that receives packets and resolves admission control decisions for the flow for the end user in both the wireless network and the wireline network. The network element providing Internet Protocol (IP) address assignment for the end user in both networks. In more specific embodiments, the method includes providing policy peering in both home and visited networks for the flow, providing access network information that indicates the type of access network being used by the end user, and network address translation (NAT) control for the user.
Owner:CISCO TECH INC
Method and system for securely authorized VoIP interconnections between anonymous peers of VoIP networks
ActiveUS7457283B2Safe collectionMetering/charging/biilling arrangementsAutomatic exchangesQuality of serviceTTEthernet
A peering authority or settlement clearinghouse can be used to control access, collect session accounting information, and provide financial settlement of interconnect or session fees among anonymous Internet Protocol (IP) peers or networks. The addition of peering policy criteria, such as price and quality of service, to peer to peer route discovery mechanisms enable a trusted intermediary, such as the settlement clearinghouse, to authorize acceptable interconnection or peering sessions between anonymous IP peers. Any financial settlement transactions which result from the peering sessions may be subsequently executed by the settlement clearinghouse.
Owner:TRANSNEXUS
System and method of traffic inspection and stateful connection forwarding among geographically dispersed network appliances organized as clusters
A peering relationship among two or more network appliances is established through an exchange of control messages among the network appliances. The peering relationship defines a cluster of peered network appliances, and at each network appliance of the cluster traffic flow state information for all the network appliances of the cluster is maintained. Network traffic associated with traffic flows of the network appliances of the cluster is managed according to the state information for the traffic flows. This managing of the network traffic may include forwarding among the network appliances of the cluster (i.e., to those of the appliances handling the respective flows) at least some of the network traffic associated with one or more of the traffic flows according to the state information for the one or more traffic flows. The traffic flows may be TCP connections or UDP flows.
Owner:CA TECH INC
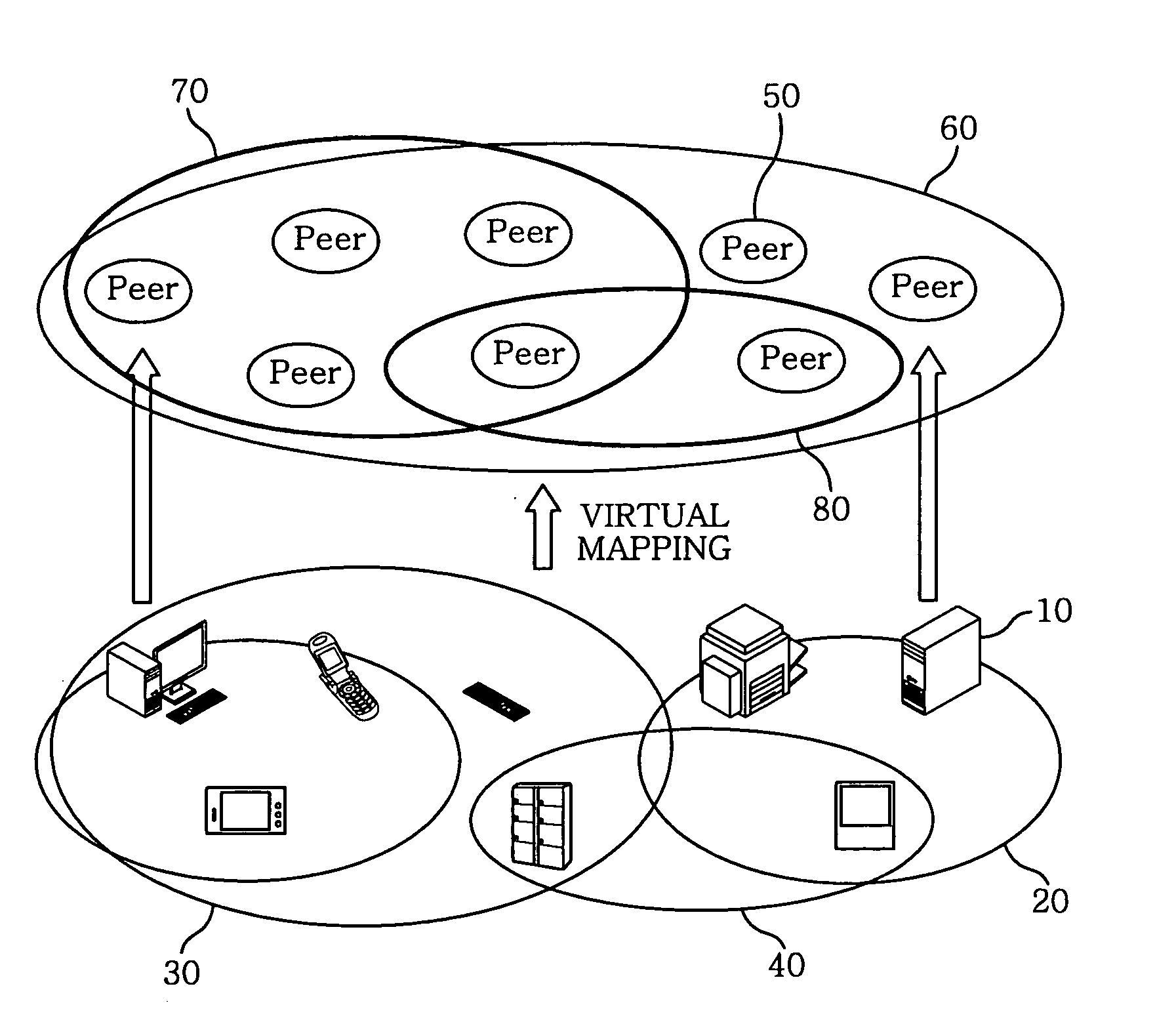
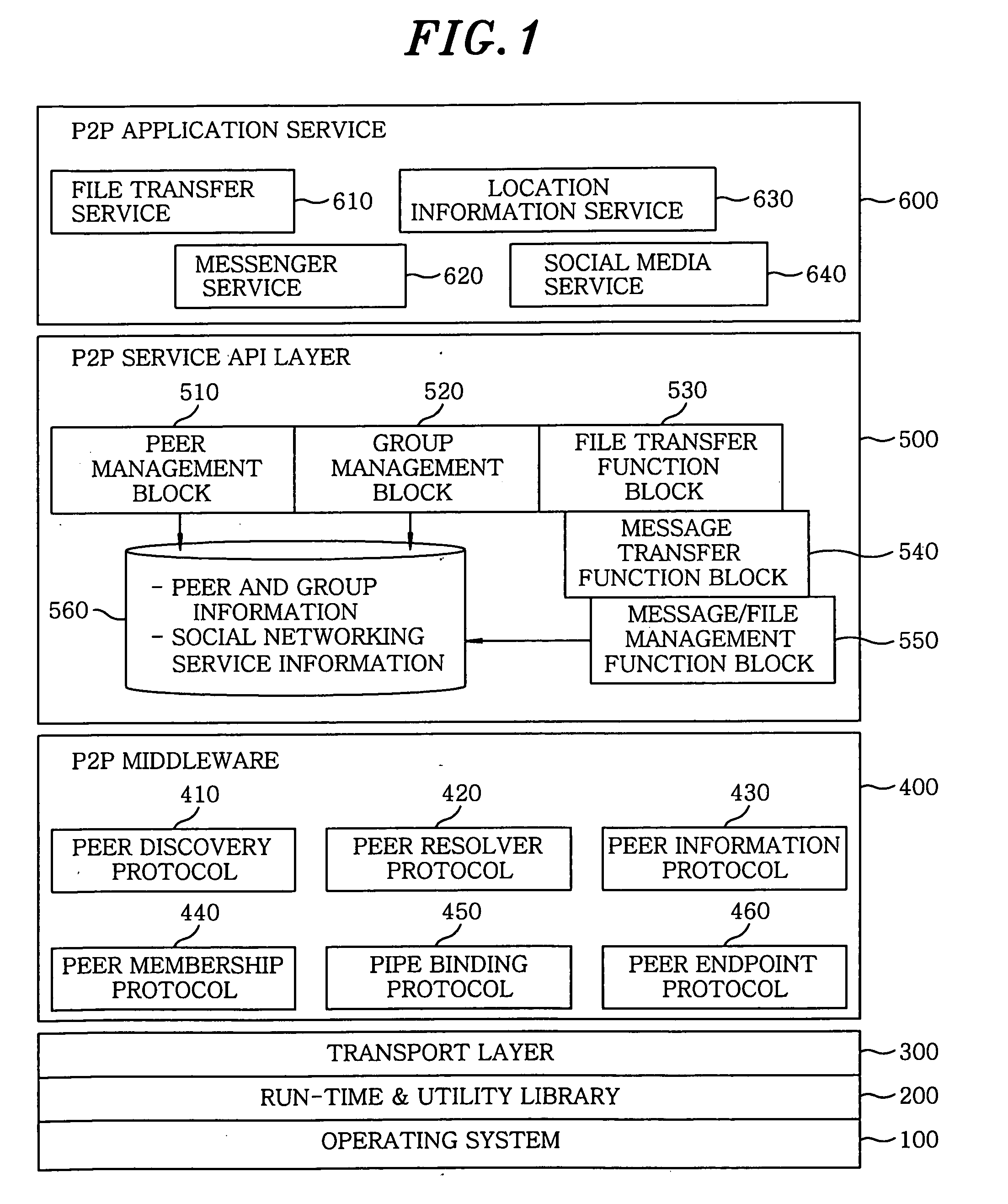
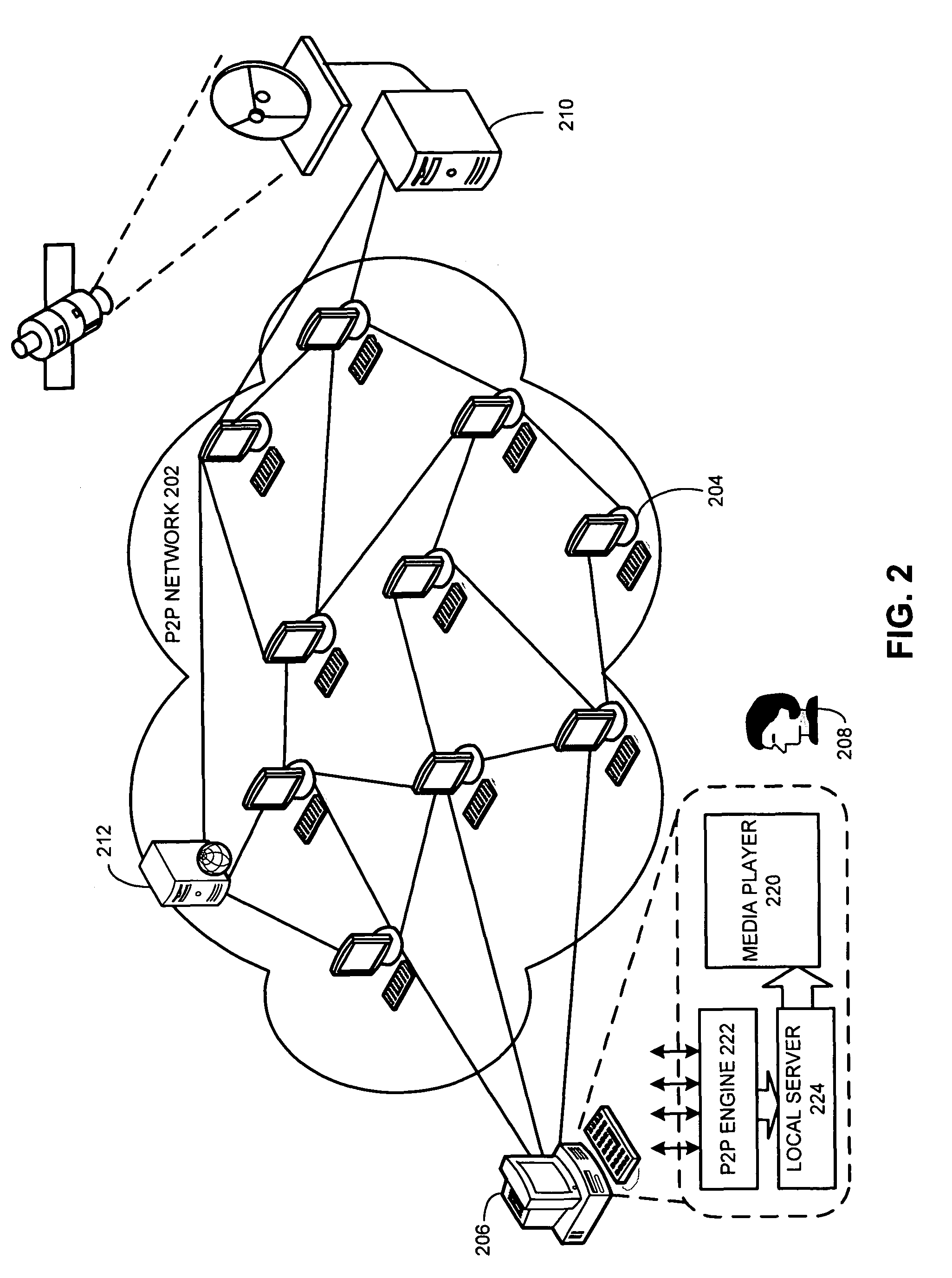
Method and apparatus for providing social networking service based on peer-to-peer network
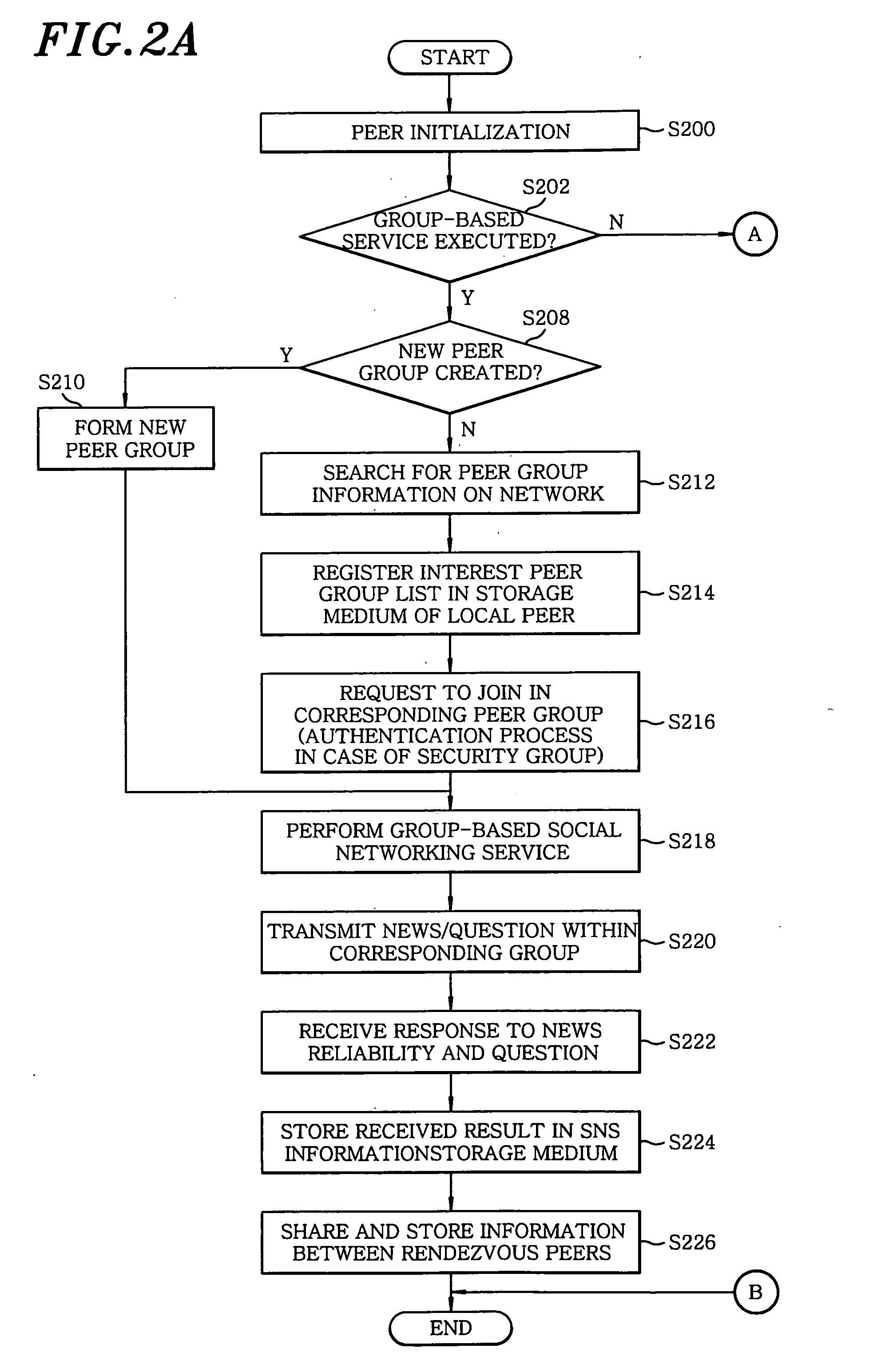
InactiveUS20090157814A1Easy to provideEasy constructionData switching by path configurationMultiple digital computer combinationsPeeringInterface layer
A Peer-to-Peer (P2P) based social networking service method for providing a social networking service, includes transmitting a request to a peer group and performing a group-based social networking service; transmitting news or a question to peers in the peer group, and then receiving a response to the question; and storing the received information in a storage medium, and uploading specific information among the stored to a rendezvous peer. The method further includes delivering the uploaded specific information to another rendezvous peer in a network. A P2P based social networking service system includes a P2P middleware unit for providing services of communicating between and grouping the peers; a P2P service application program interface layer for providing a network element function; and a P2P application service layer for calling the network element function, if required, to thereby provide a user with a P2P based network service.
Owner:ELECTRONICS & TELECOMM RES INST
System for coordinative security across multi-level networks
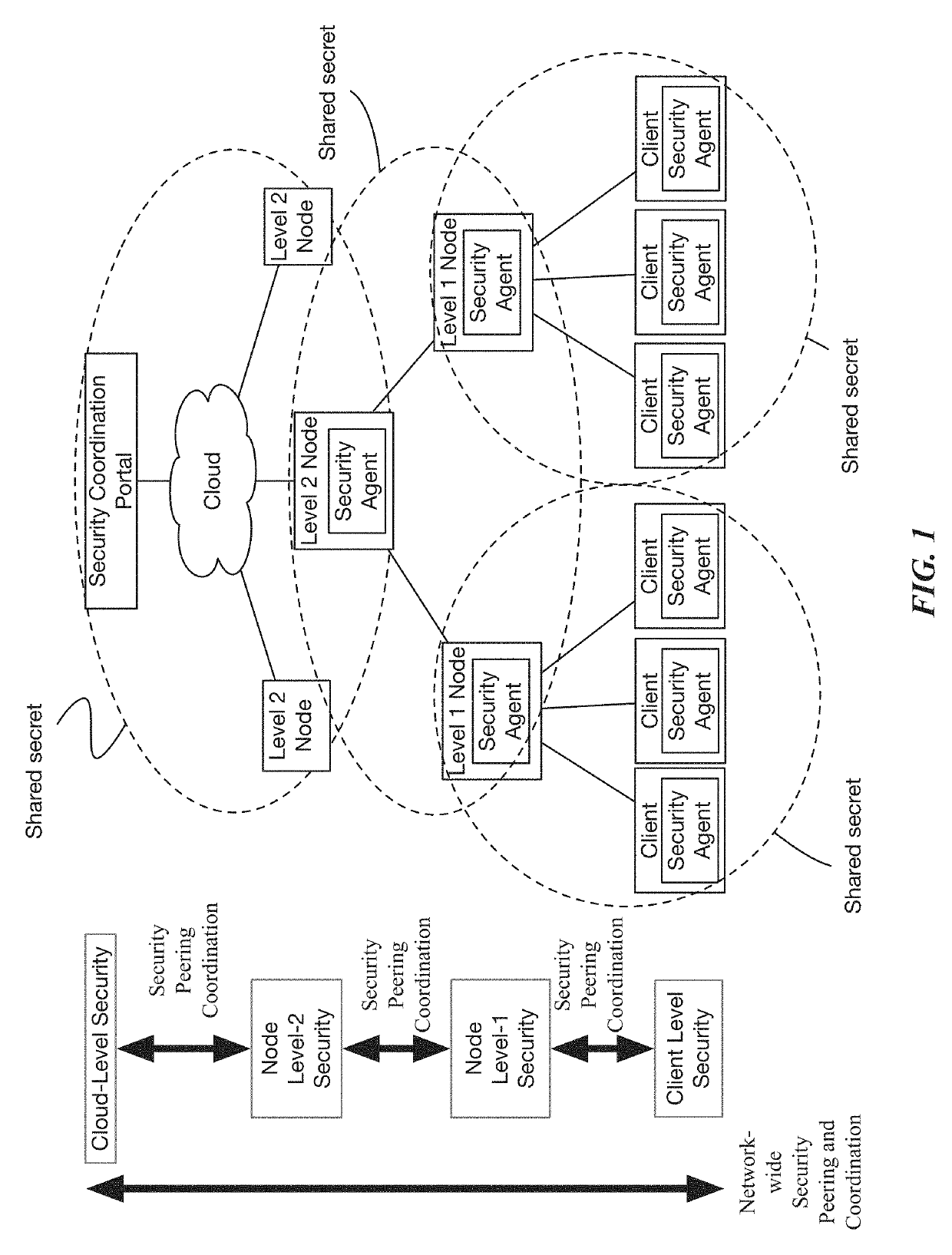
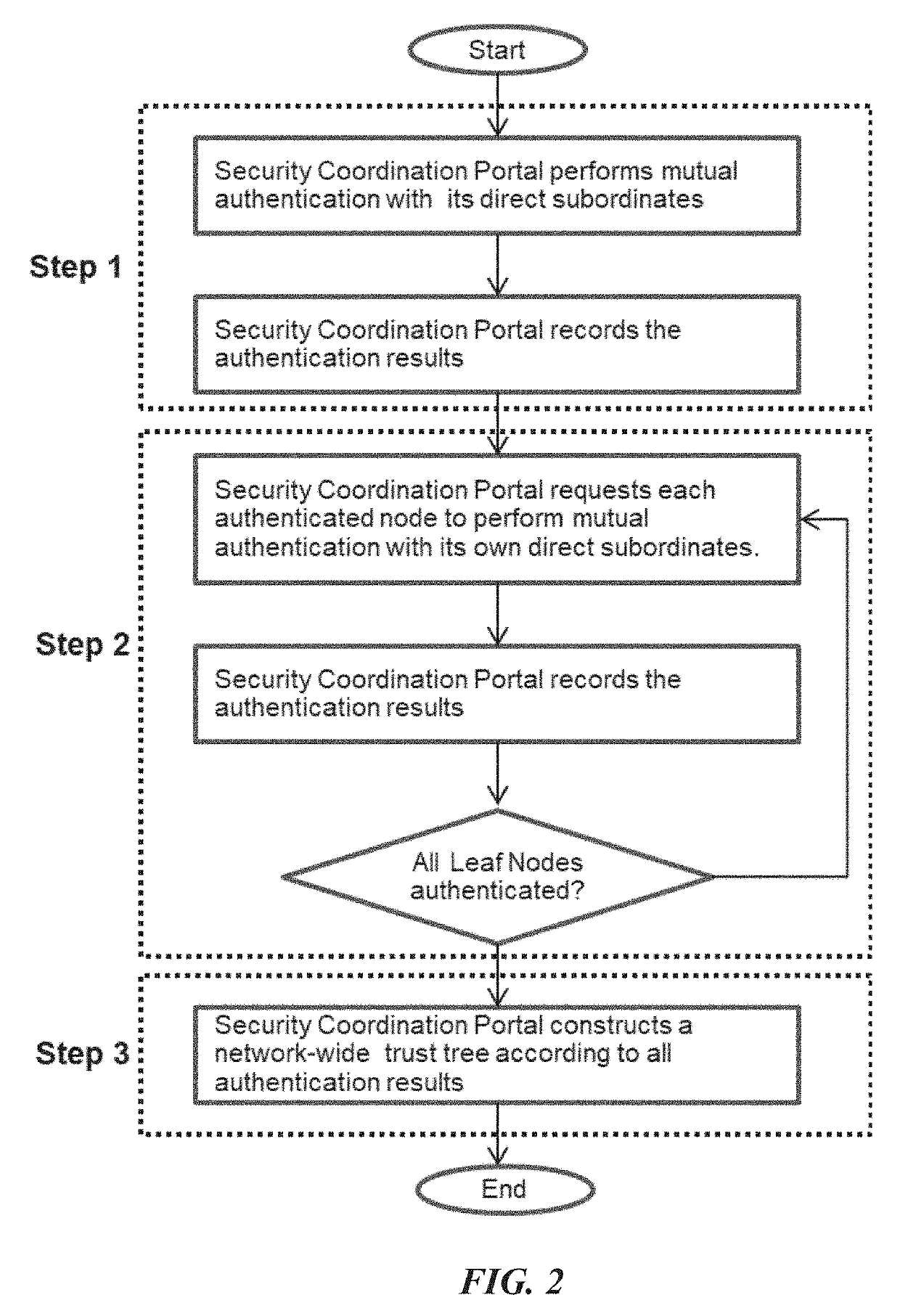
ActiveUS20190289038A1Multiple keys/algorithms usageUser identity/authority verificationPeeringMessage passing
In some aspects, the disclosure is directed to methods and systems for providing coordinative security among network devices across multi-level networks. Shared cryptographic secrets among the network devices are used as the basis for mutual security authentication and peering among these devices. The cryptographic secrets can be embedded in the SoC devices for these devices or dynamically generated based on unique identification information and attributes of these SoC devices. The messages for authentication and peering can be communicated directly among the network devices or indirectly via a cloud security portal entity that acts as a messaging proxy. The mutual authentication and peering process can be carried out coordinately among the network devices and a cloud security portal in a one-to-one mesh relationship, or in a transitive layering relationship, where each network entity authenticates and peers with its direct subordinates in a multi-level network.
Owner:AVAGO TECH INT SALES PTE LTD
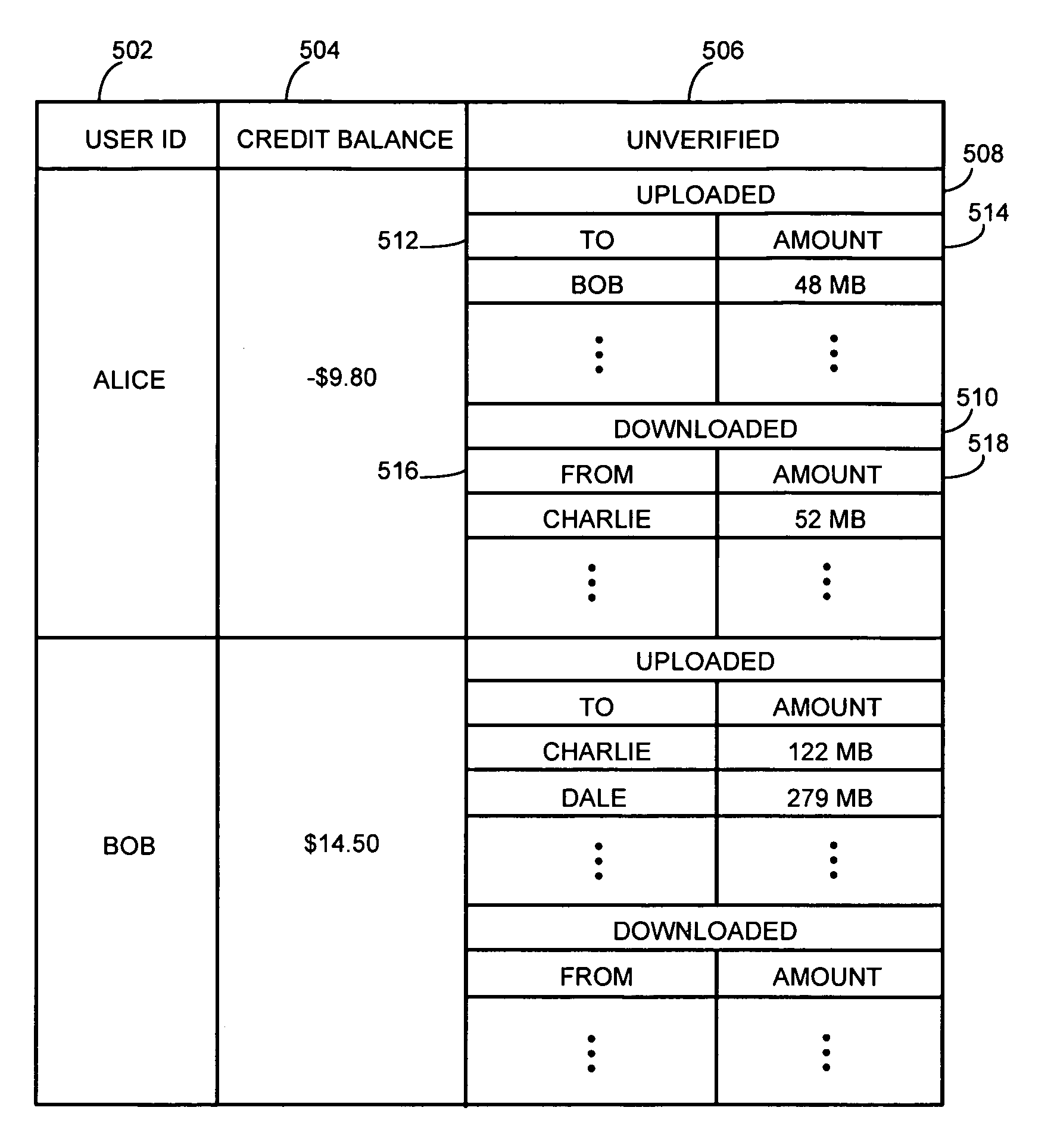
System and method for facilitating a credit system in a peer-to-peer content delivery network
InactiveUS7937362B1Encourage data sharingDigital data processing detailsSpecial data processing applicationsCredit systemPeering
A system and method facilitate a credit system for providing user incentives to encourage data sharing in a P2P network. The credit system maintains a user credit database and respectively increases or decreases a user's credits based on the data uploaded to or downloaded from other peer nodes. The credit system can also associate a user's credits with economic value or rewards to encourage the user to share data with other peer nodes. In one embodiment, the credit system maintains a credit record for each user. The credit system increases the credit for a user based on the amount of data a peer node associated with the user uploads to other peer nodes in the P2P network. The credit system also decreases the credit for the user based on the amount of data downloaded by the peer node associated with the user.
Owner:TV BANK
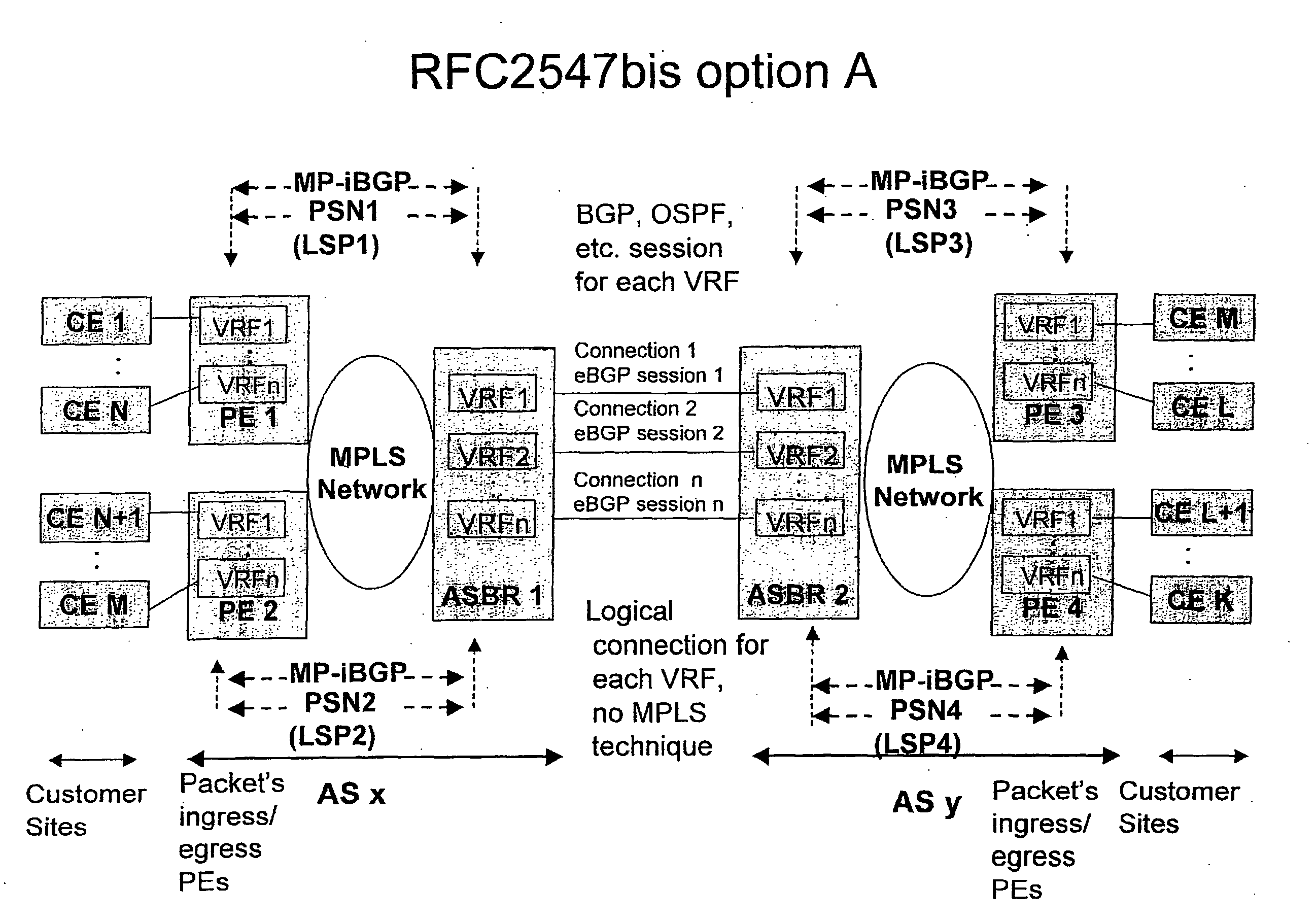
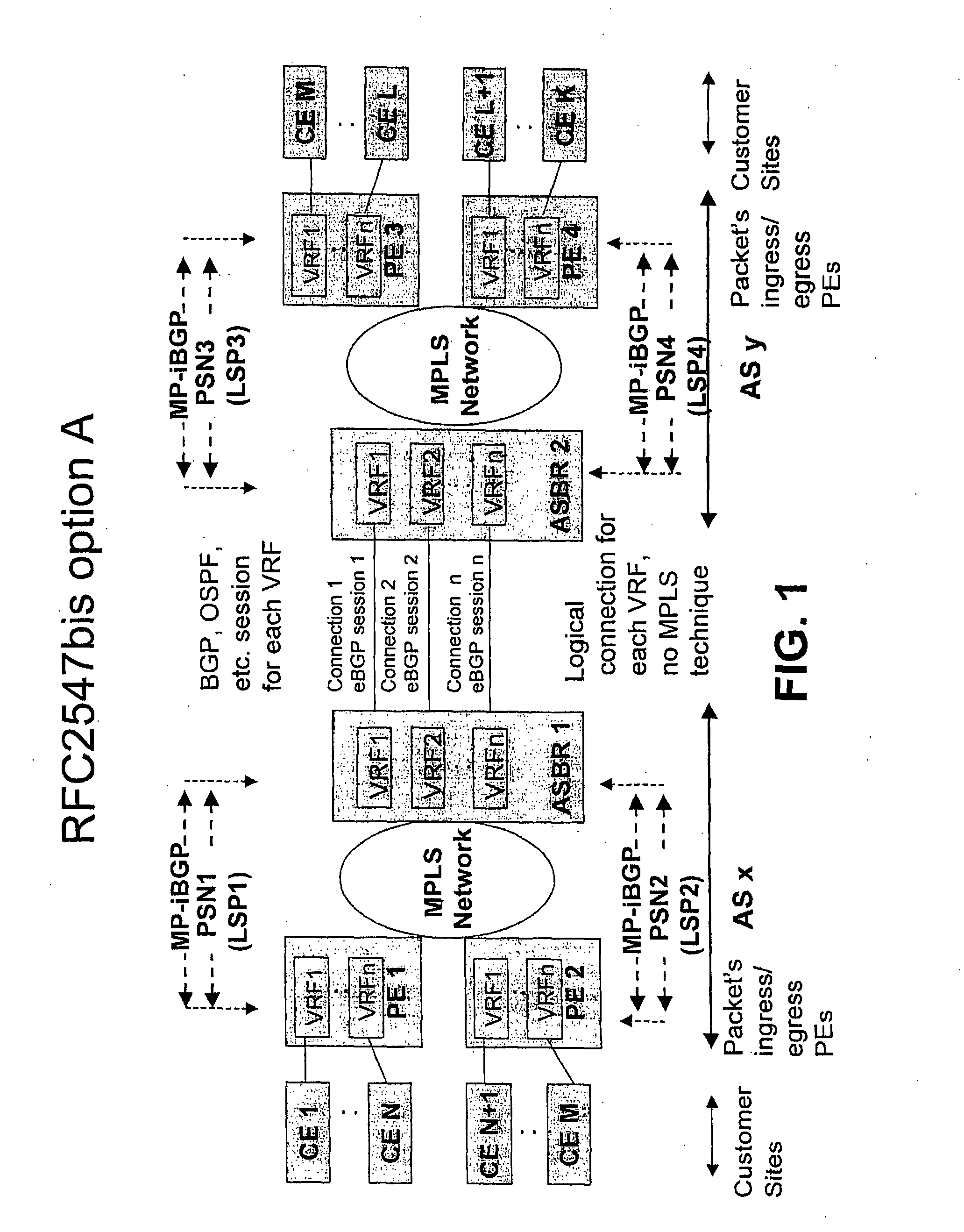
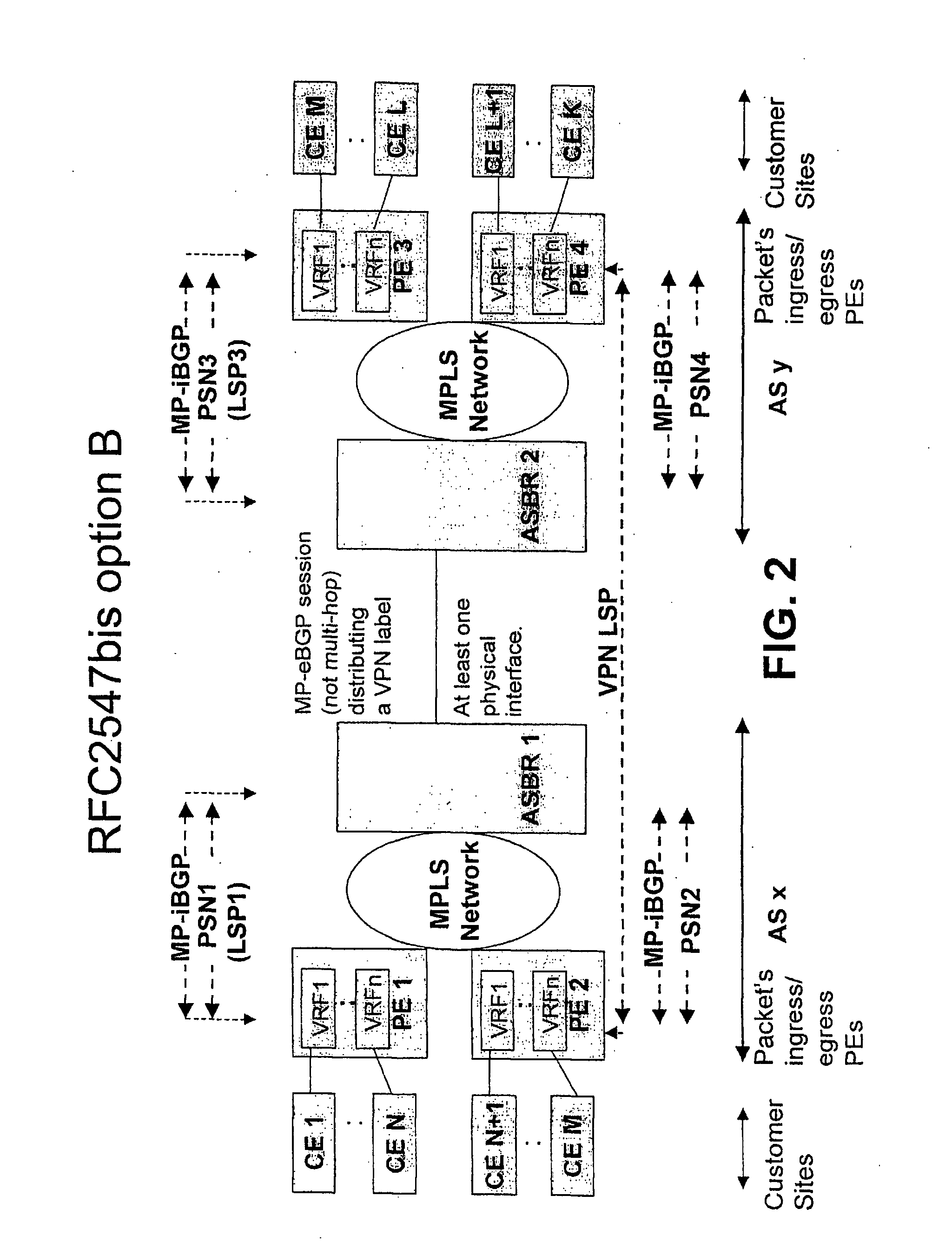
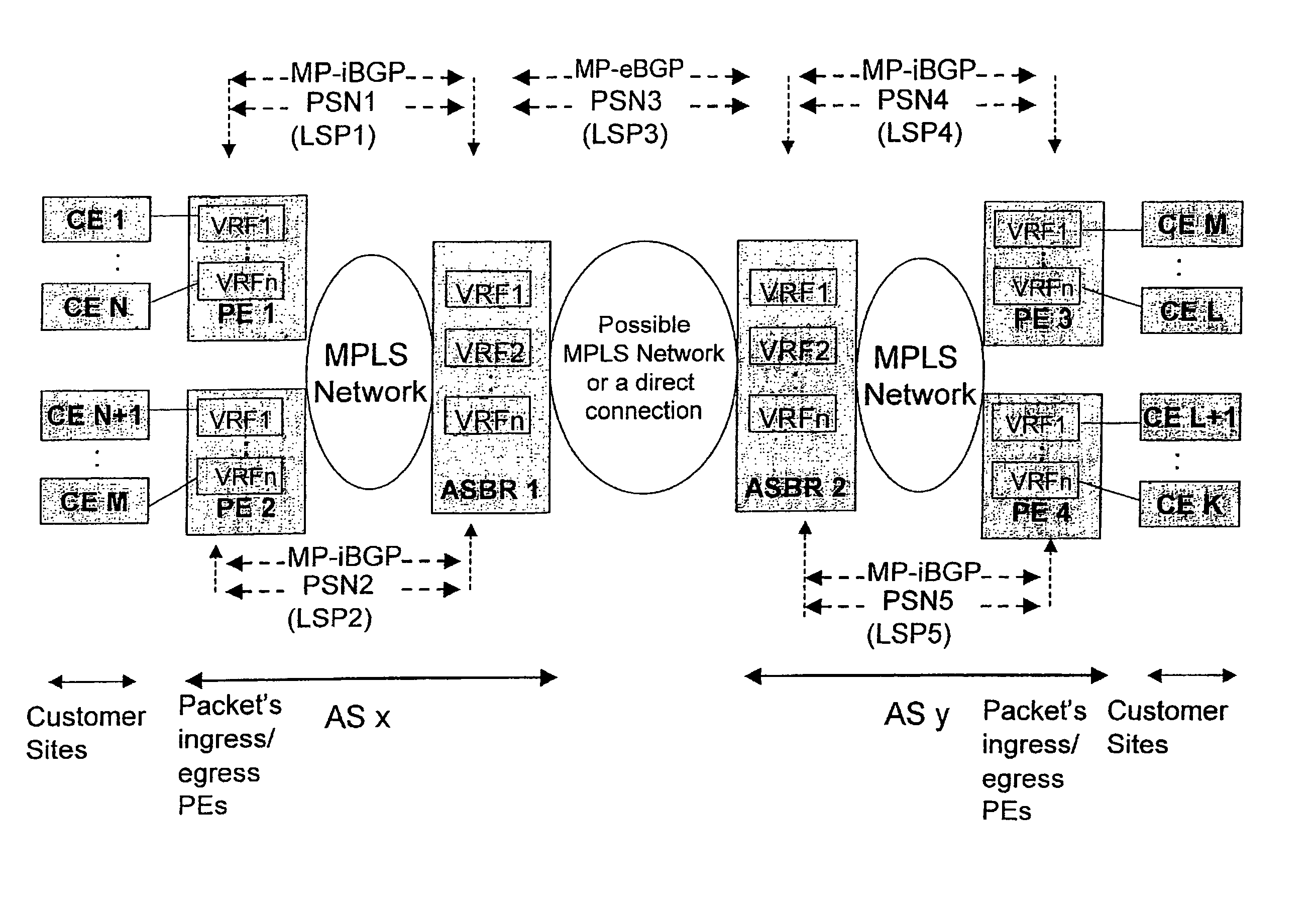
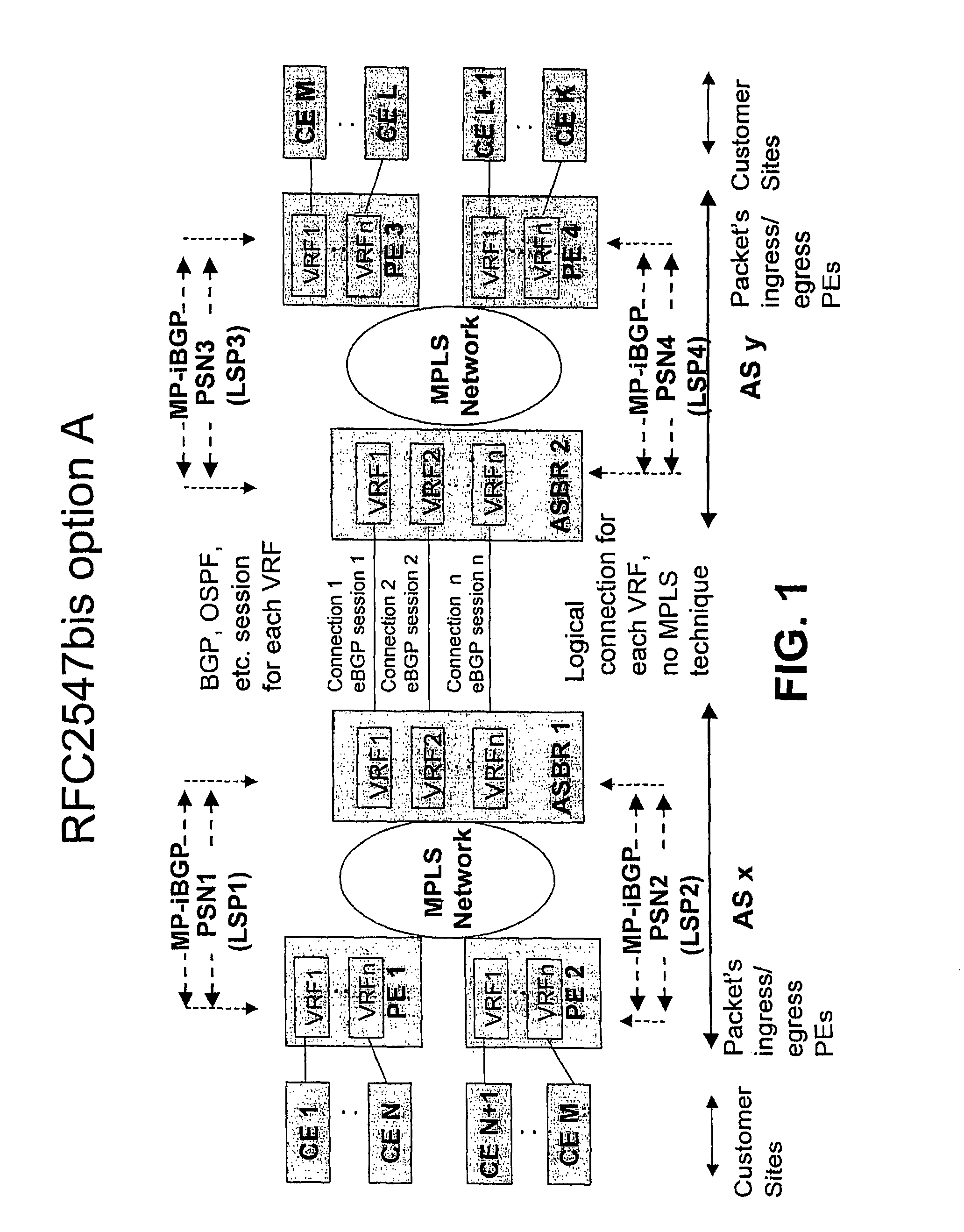
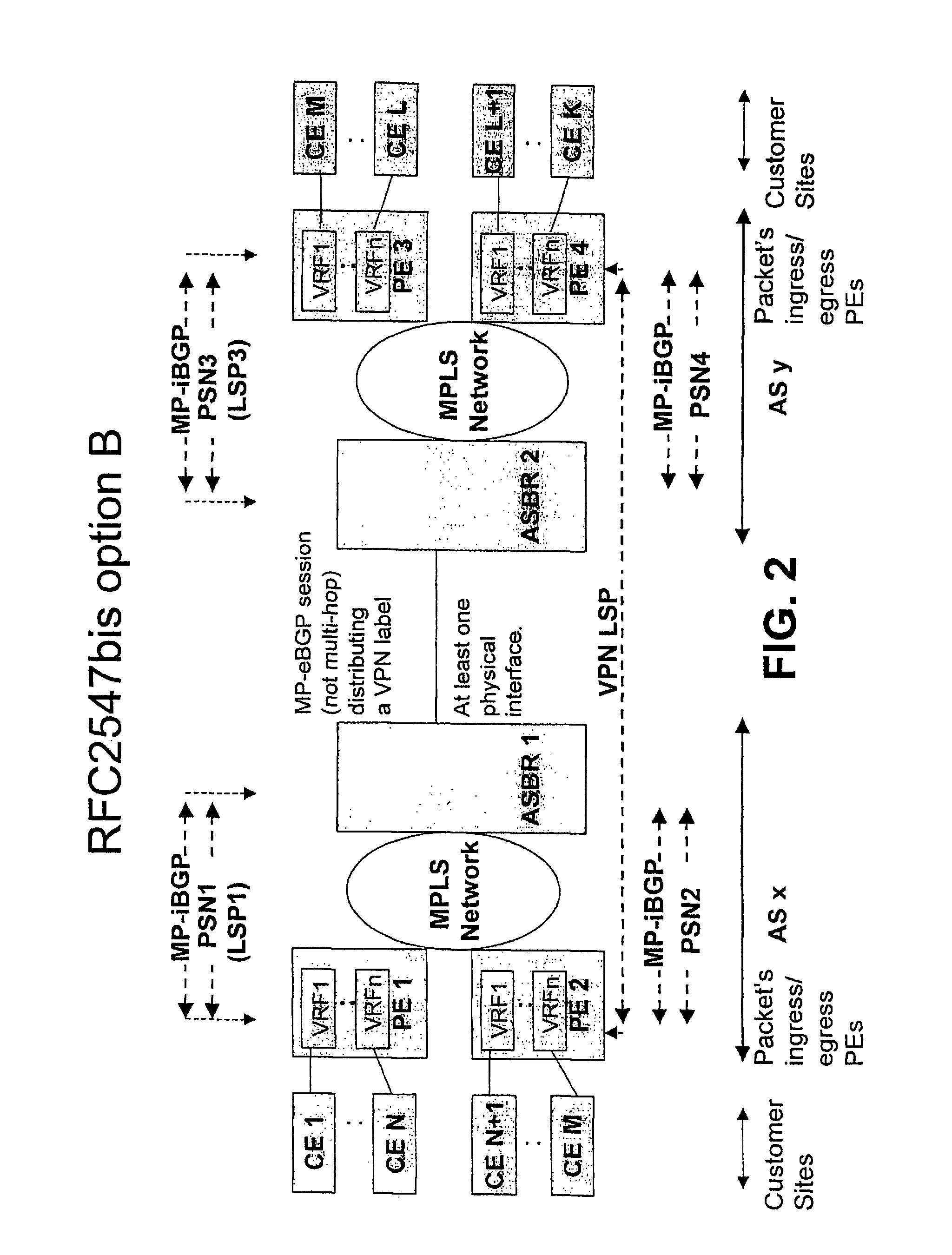
Method for Providing Virtual Private Network Services Between Autonomous Systems
ActiveUS20080267187A1Eliminate needImprove scalabilityNetworks interconnectionPeeringPrivate network
The present invention relates to providing virtual private network (VPN) services between two or more Autonomic Systems (AS). An aggregation edge router (ASBR) is provided in two or more autonomous systems (Asx,Asy). The aggregation edge routers are configured such that routing peering between the two or more autonomous systems is done between the aggregation edge routers in these autonomous systems. Each aggregation edge router is a routing peer of other edge routers (PE) in its own autonomous system. The Multi-Protocol Label Switching (MPLS) network is used between the different autonomous systems.
Owner:TELIASONERA +1
Systems and methods to detect and defend against distributed denial of service attacks
ActiveUS20160099964A1Easy to integrateProvide feedbackMemory loss protectionError detection/correctionPeeringNominal level
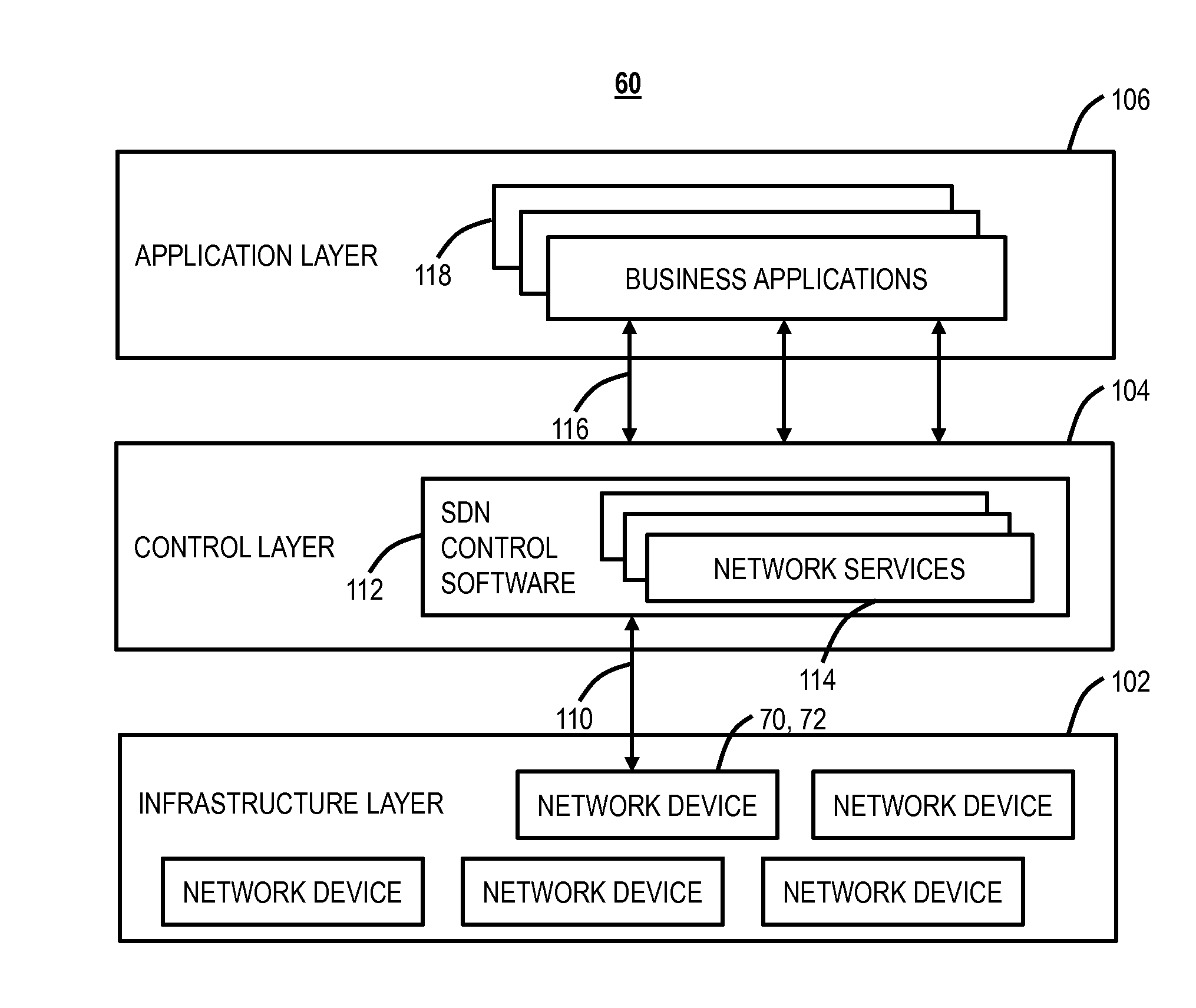
A method, operated by a Software Defined Networking (SDN) controller associated with an Autonomous System (AS) with one or more peering points, each peering point with an associated router communicatively coupled to the SDN controller, the method for detecting and defending against Distributed Denial of Service (DDoS) attacks, and the method includes receiving data from the one or more peering points; detecting malicious traffic at the one or more peering points; determining a peer quality measurement for the one or more peering points; and communicating the peer quality measurement and other data associated with the malicious traffic to one or more other SDN controllers, associated with Autonomous Systems connected through the one or more peering points, to facilitate convergence of the peer quality measurement back to a nominal level.
Owner:CIENA
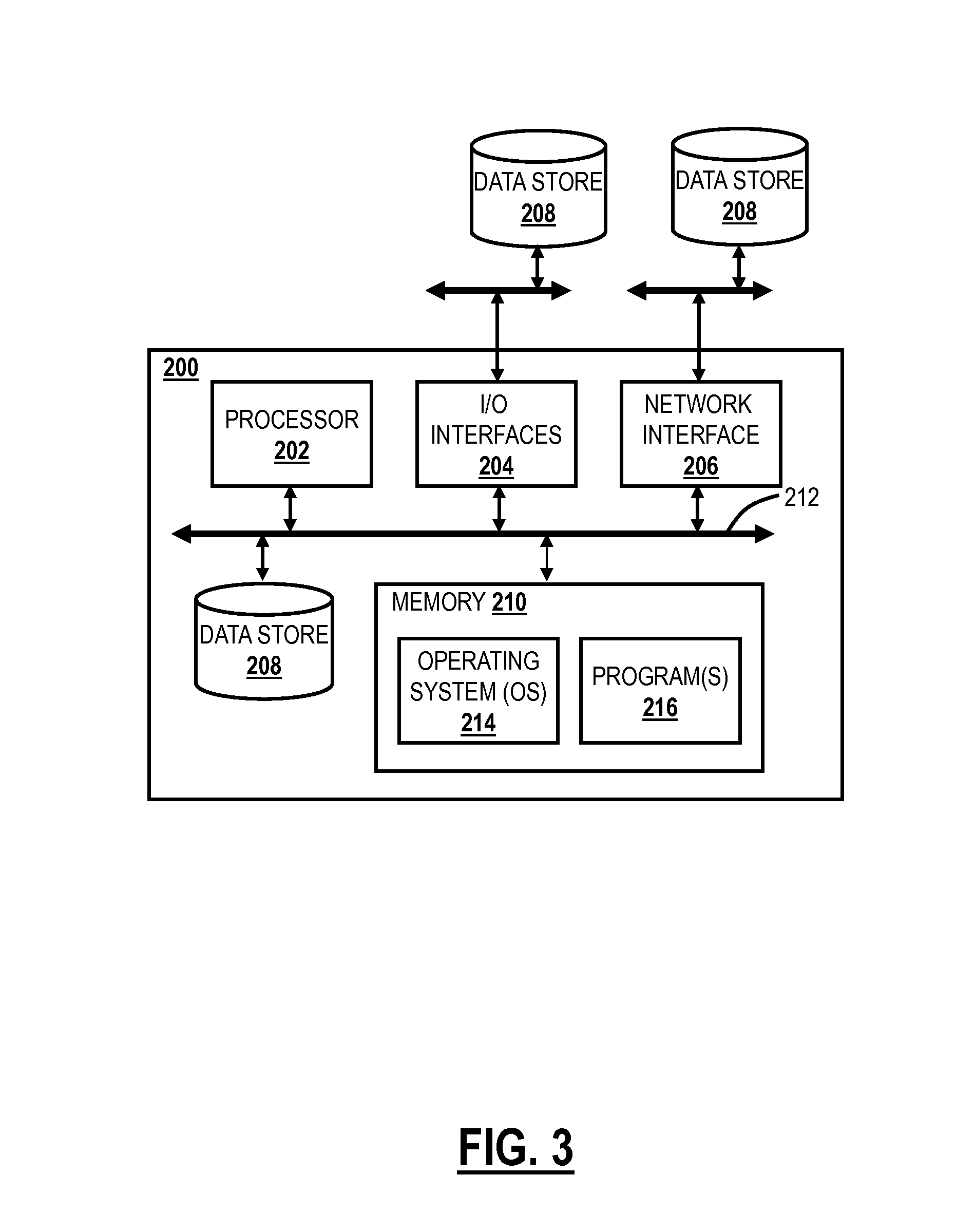
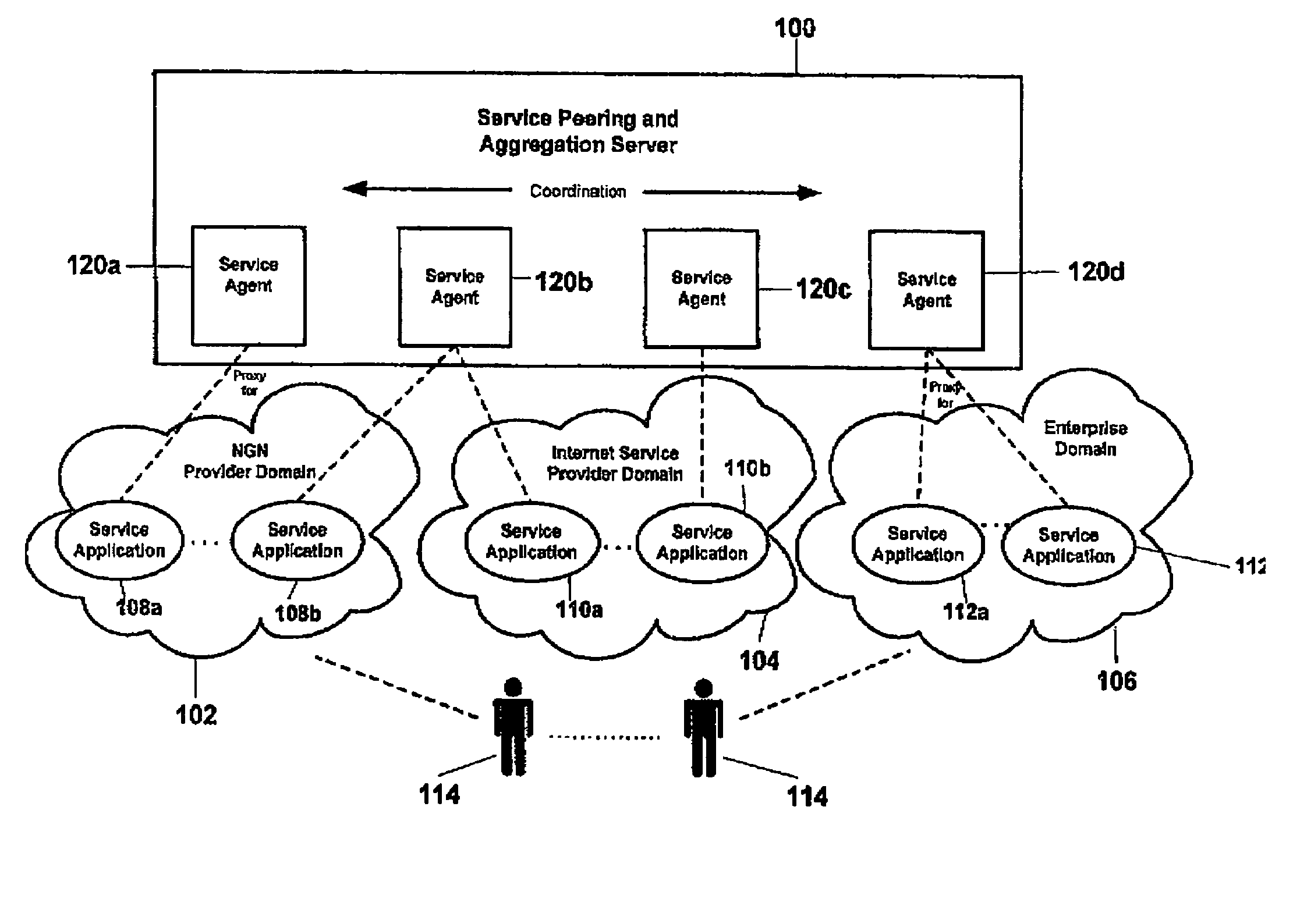
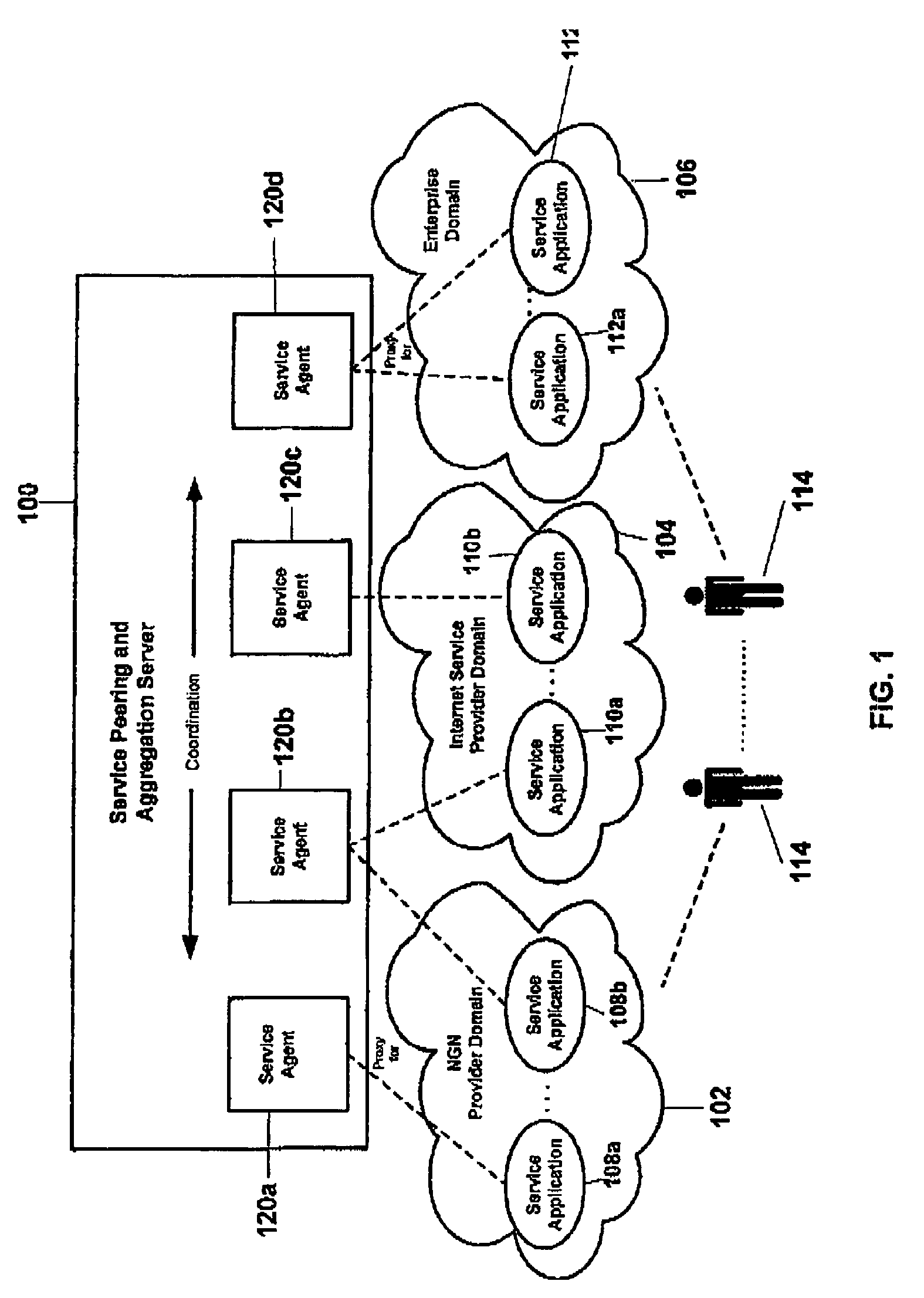
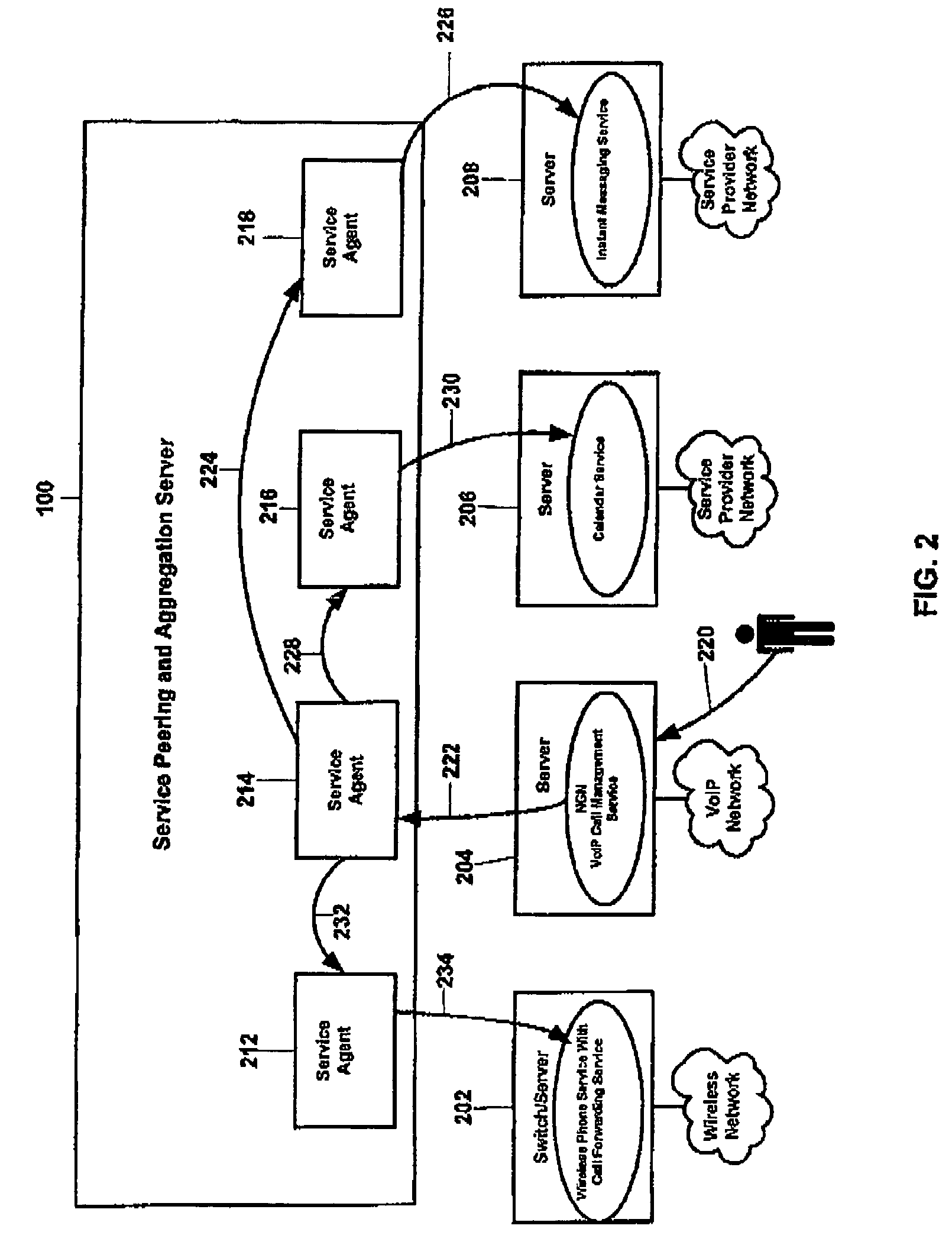
Application service peering and aggregation
Service applications at one or more service providers are bundled through a server thereby creating new services. The server comprises service agents, each of which corresponds to one or more service applications and proxies for its application(s) to perform service bundling. When a subscriber interacts with a service application and affects service specific data, the application sends this data along with the subscriber's intent with respect to this data to the server. The server next identifies a primary service agent, which is the agent proxying for the application. This agent determines a peer group of service agents, wherein each peer agent corresponds to a service application that together define a bundled service. The principal and peer agents subsequently negotiate / coordinate with respect to the service data. As a result, the agents may communicate with their respective service applications to determine a subscriber's current service data configurations and / or to update these configurations.
Owner:NYTELL SOFTWARE LLC
Method for providing virtual private network services between autonomous systems
The present invention relates to providing virtual private network (VPN) services between two or more Autonomic Systems (AS). An aggregation edge router (ASBR) is provided in two or more autonomous systems (Asx,Asy). The aggregation edge routers are configured such that routing peering between the two or more autonomous systems is done between the aggregation edge routers in these autonomous systems. Each aggregation edge router is a routing peer of other edge routers (PE) in its own autonomous system. The Multi-Protocol Label Switching (MPLS) network is used between the different autonomous systems.
Owner:TELIASONERA +1
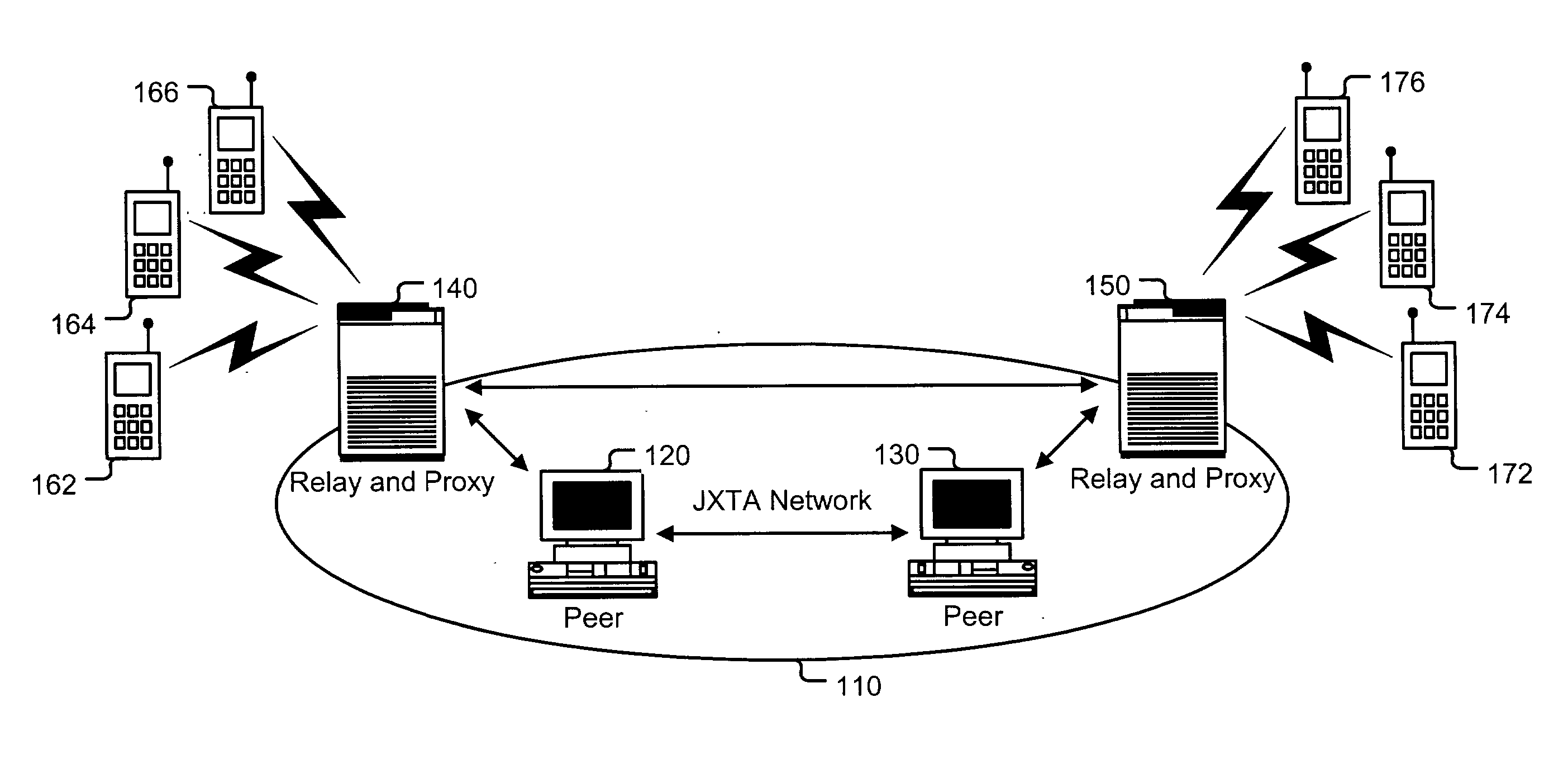
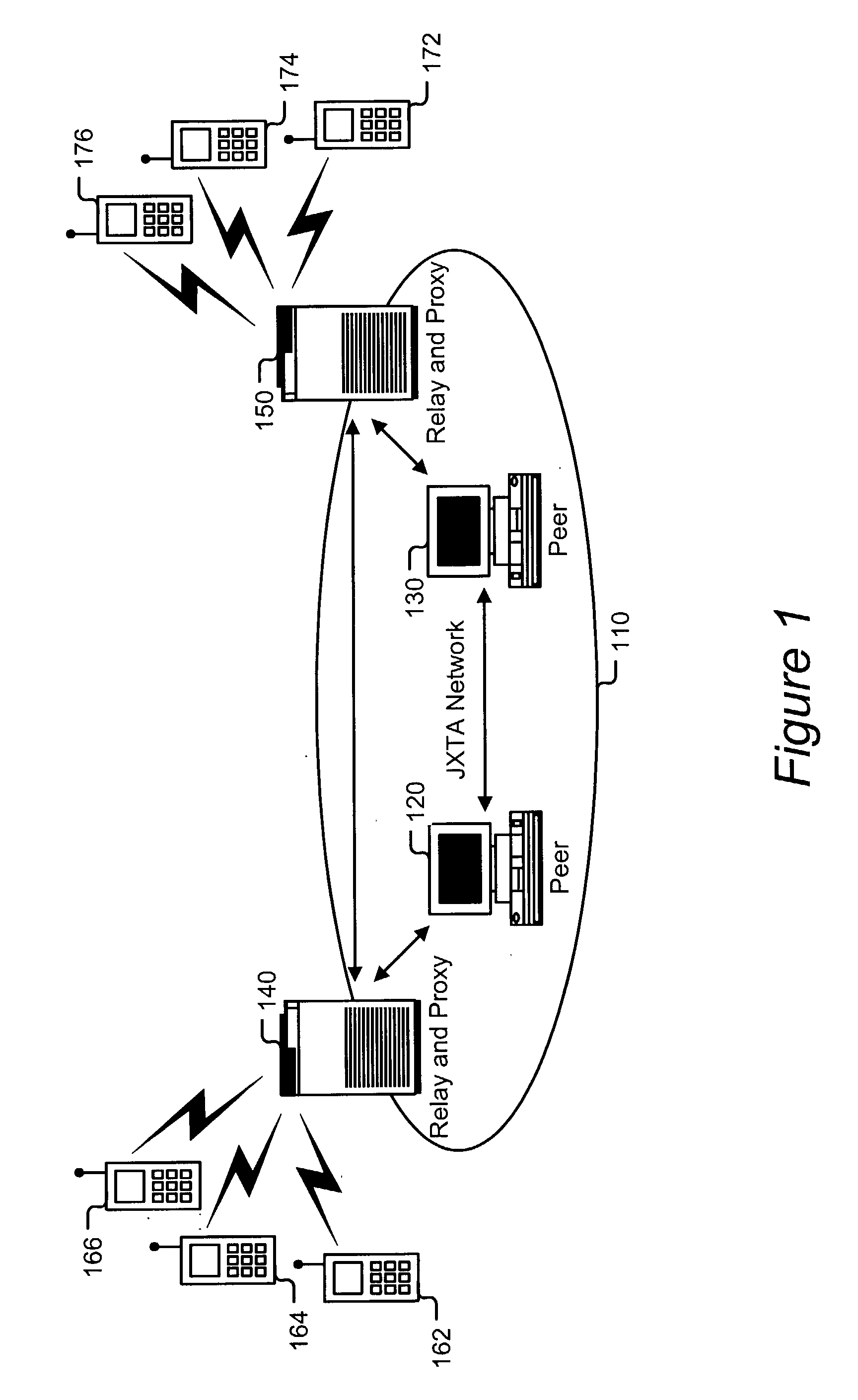
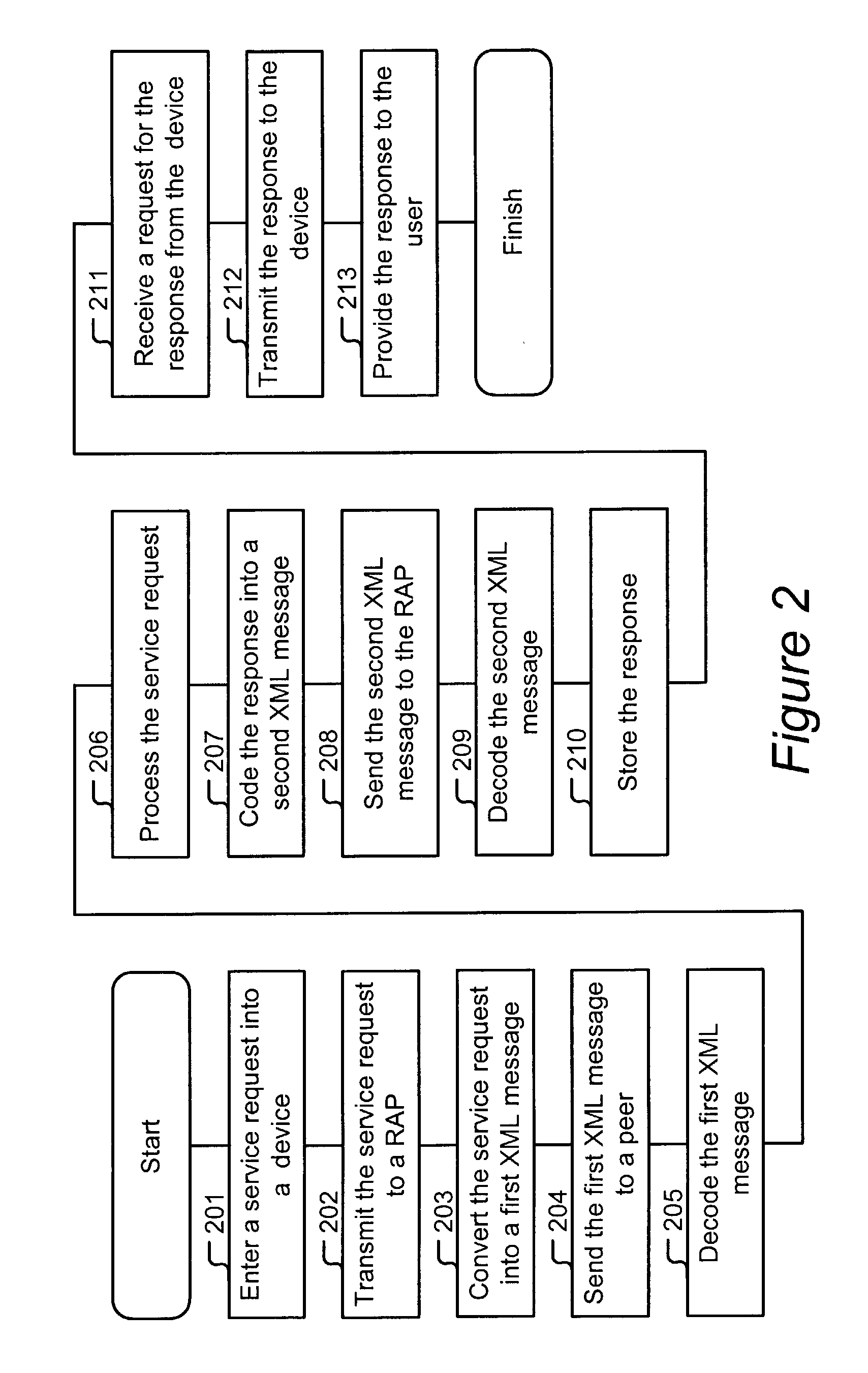
Method for communicating with a resource-constrained device on an edge of a network
A method of requesting a service from a peer on a peer-to-peer network. The method includes entering a service request into a device and transmitting the service request to a relay-and-proxy on the peer-to-peer network. The method also includes converting the service request into a message and sending the message to the peer.
Owner:SUN MICROSYSTEMS INC
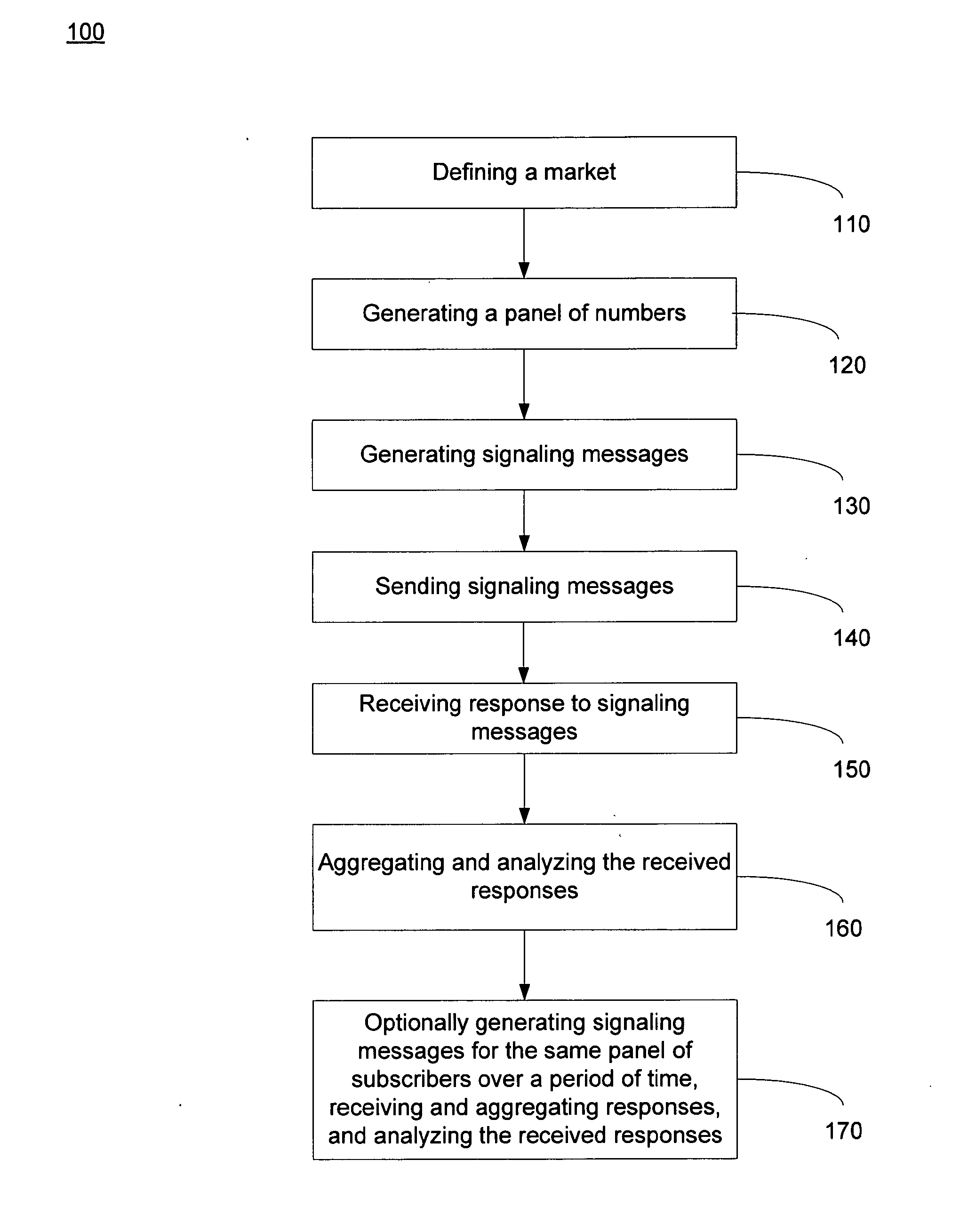
Method and system for measuring market-share for an entire telecommunication market
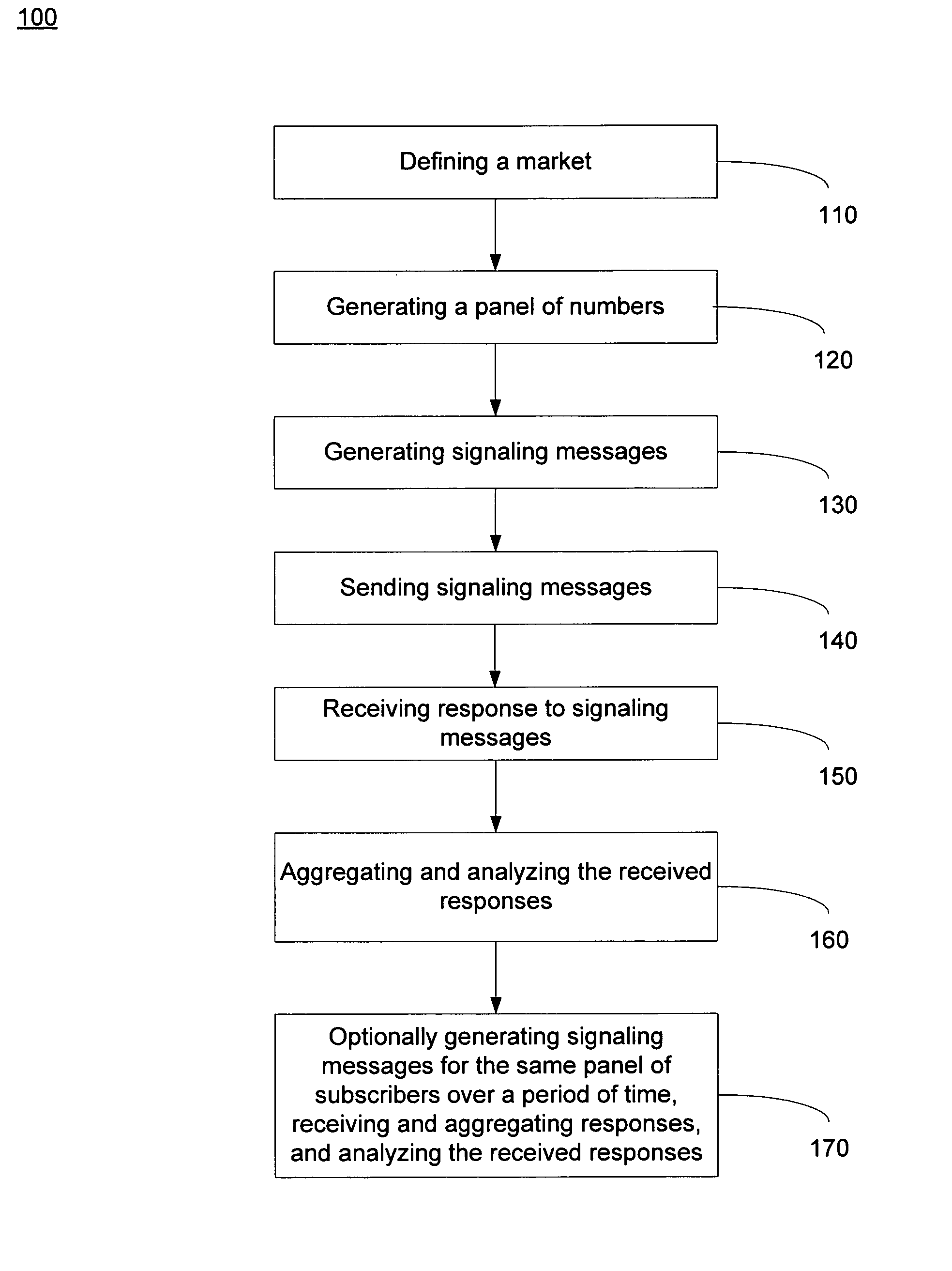
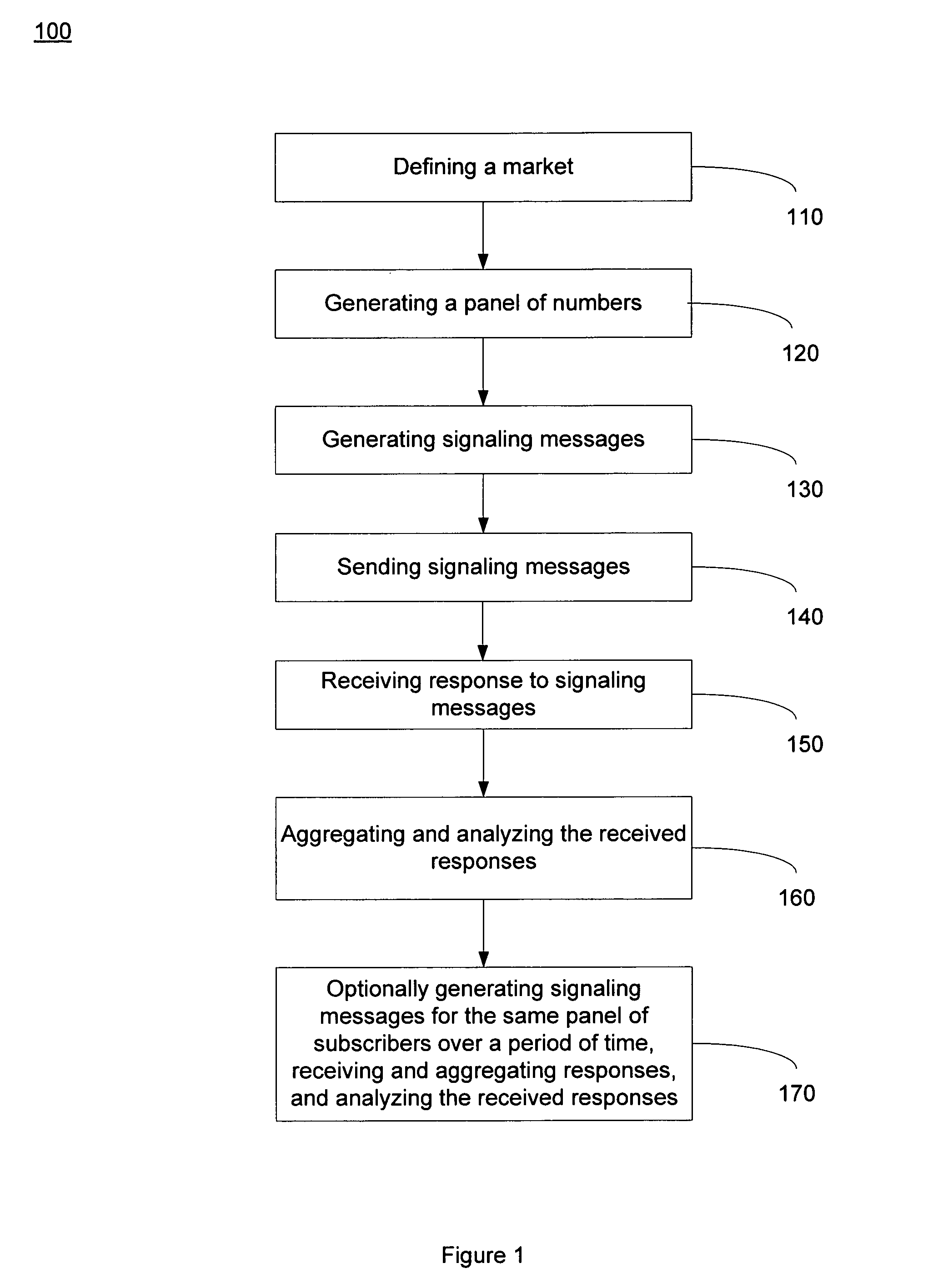
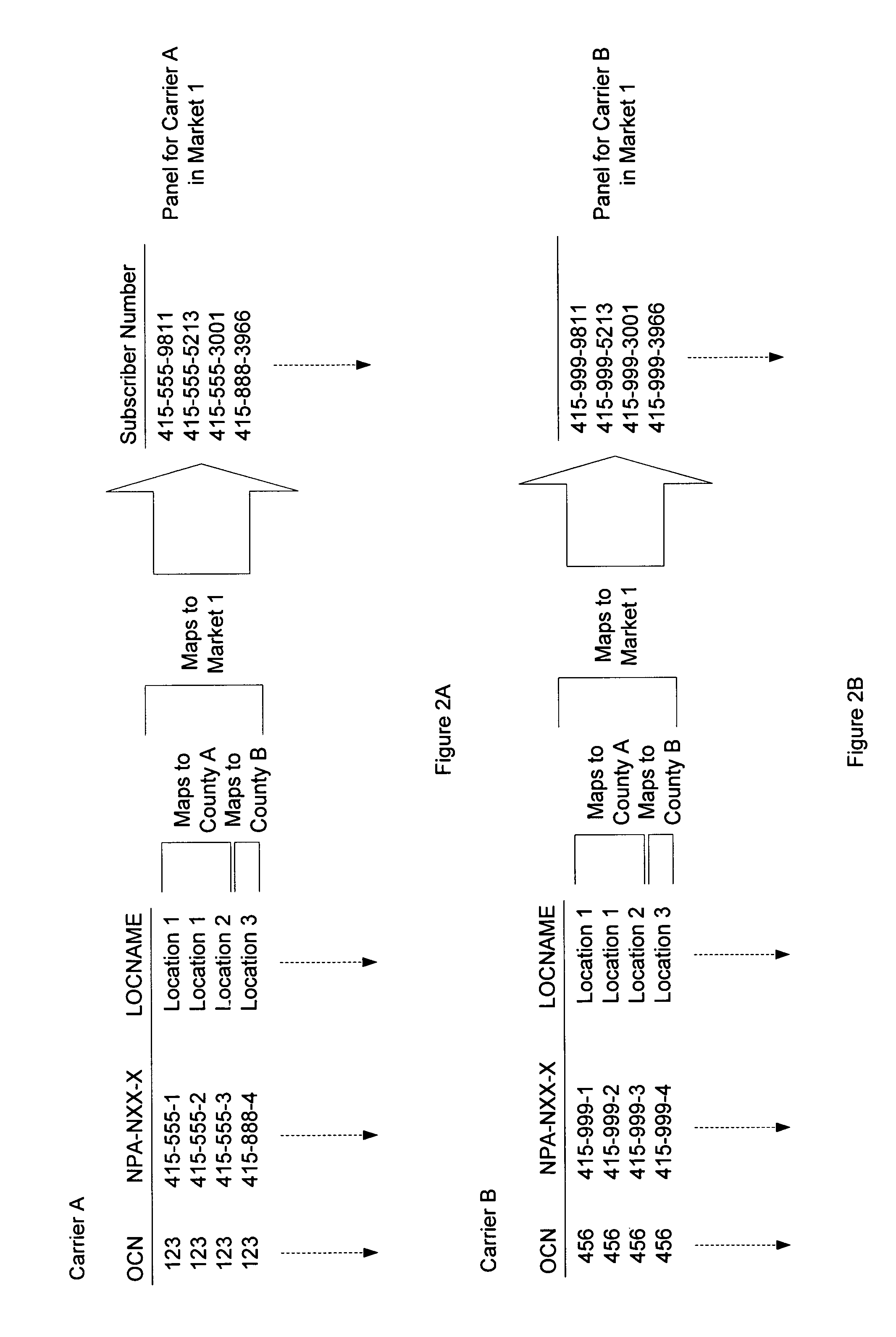
ActiveUS7933392B1Reduce errorsLess time-consumingMultiplex system selection arrangementsMarket predictionsPeeringSignaling system
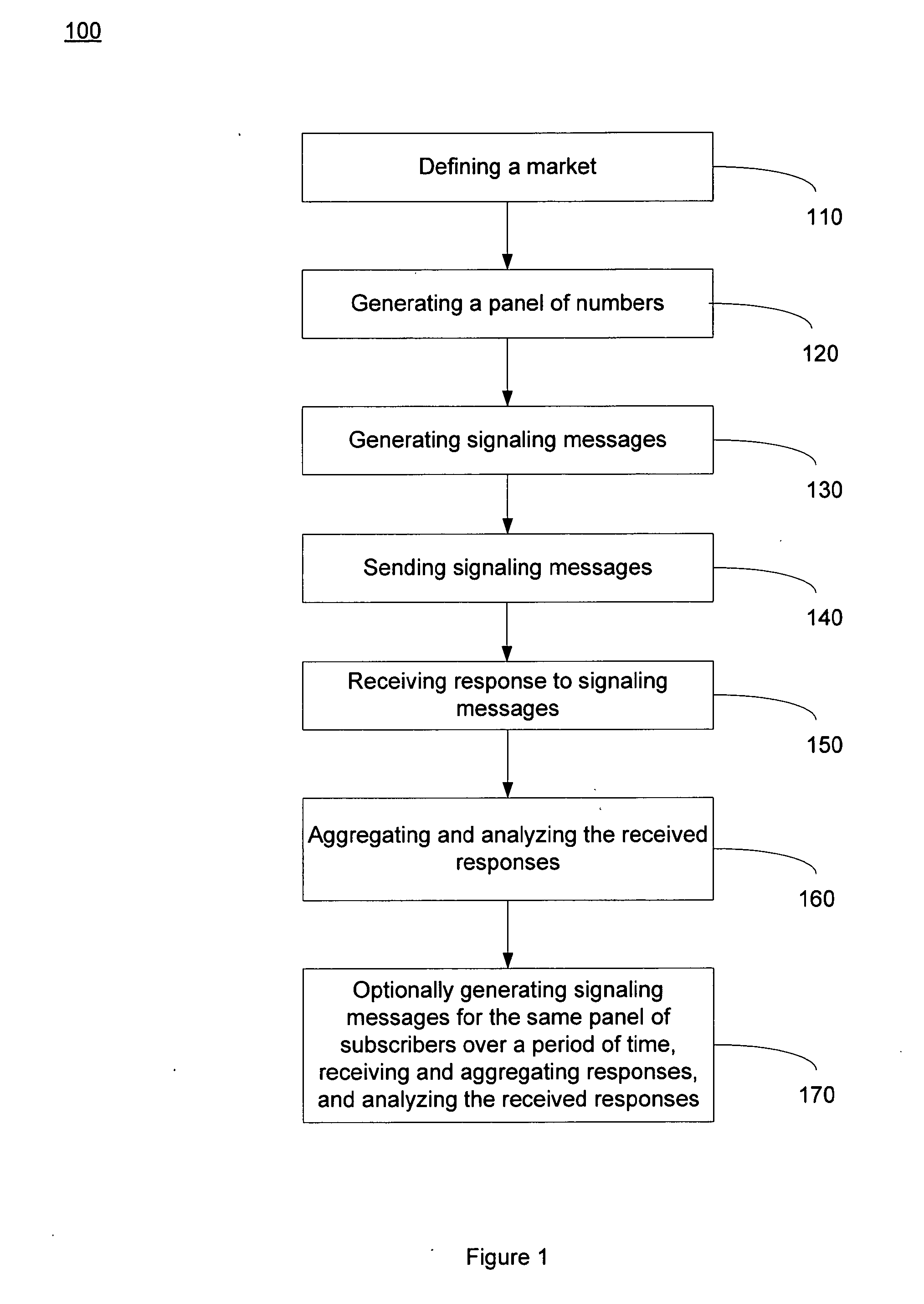
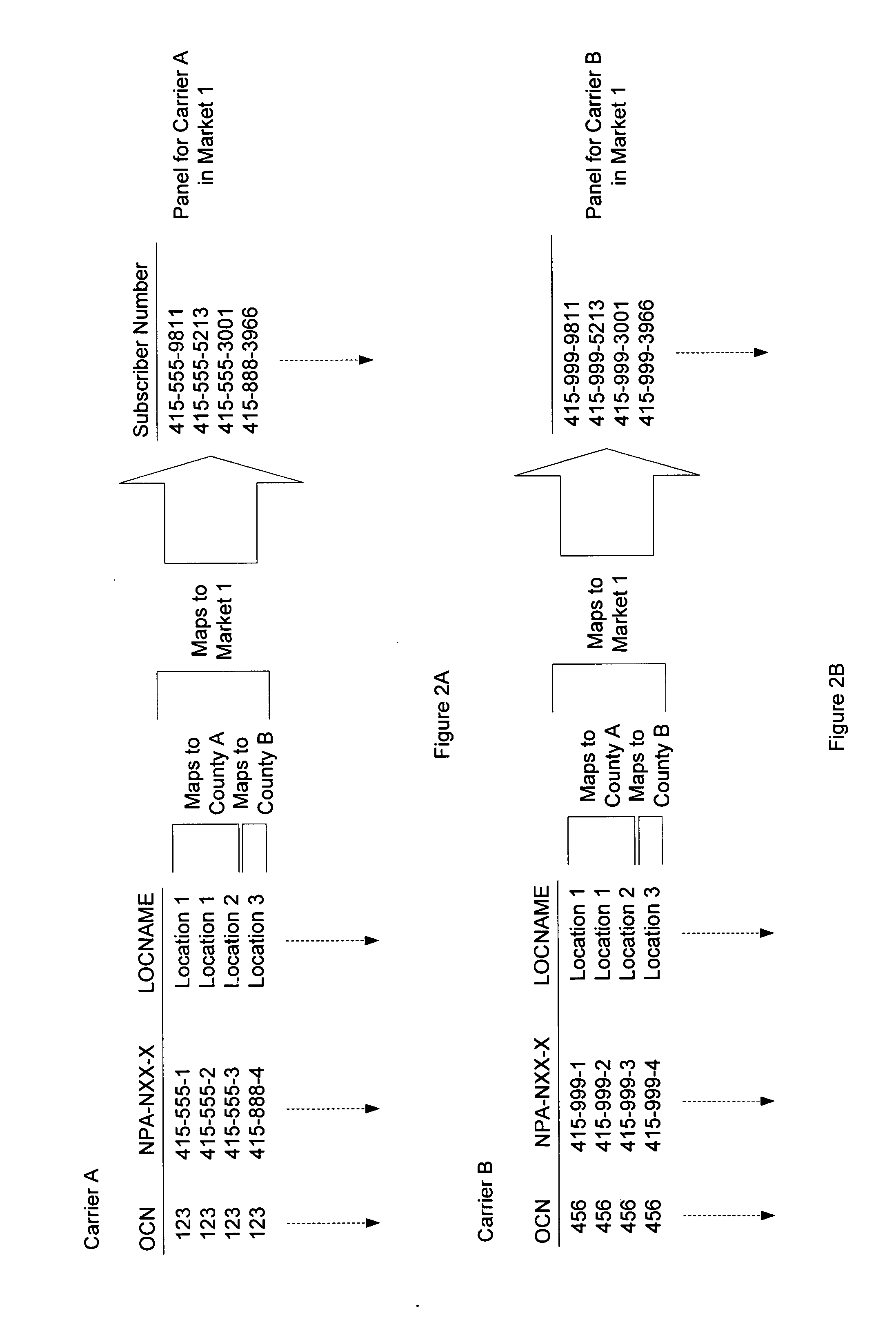
A method for collecting data to measure market-share for a defined telecommunication market. A market of interest is defined and a random panel of numbers is created. A call set-up is initiated to the created random panels by generating signaling messages wherein the signaling messages access a Calling Name Services (CNAM) database, a Local Number Portability (LNP) database, an E-911 Automated Location Information (ALI) database and a Line Information Database (LIDB) using signaling system 7 (SS7) protocol. Generated signaling messages access ENUM (Telephone Number Mapping) database and Internet Protocol (IP) Peering database using IP. The response to the generated signaling messages are used to determine assignment status, business ownership, businesses versus residential status and the technology employed for a given number in the created panel. In one embodiment, the process is repeated over a period in order to determine changes to the market-share and derivative metrics for the telecommunication market.
Owner:THE NIELSEN CO (US) LLC
Methods and systems for providing telephony services and enforcing policies in a communication network
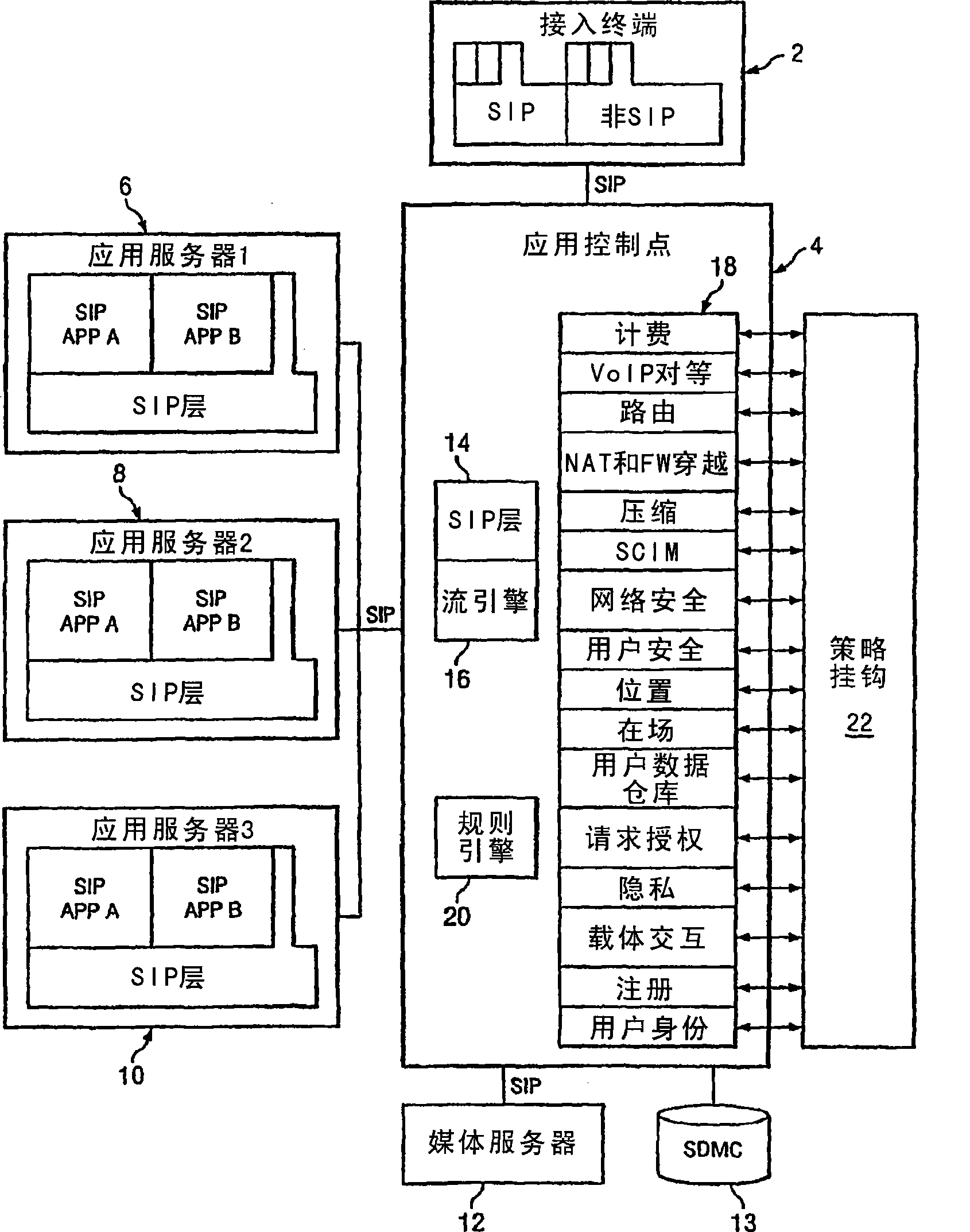
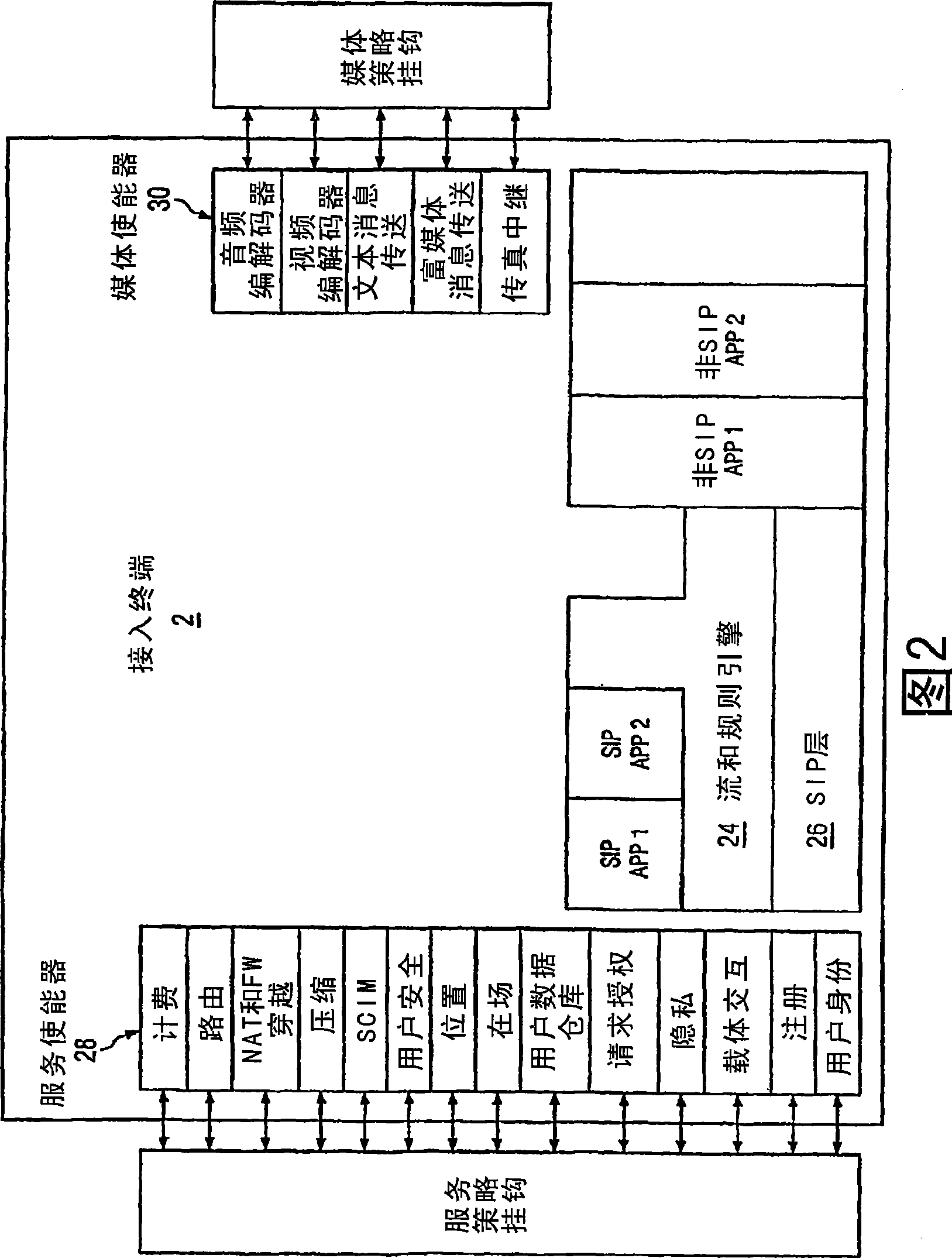
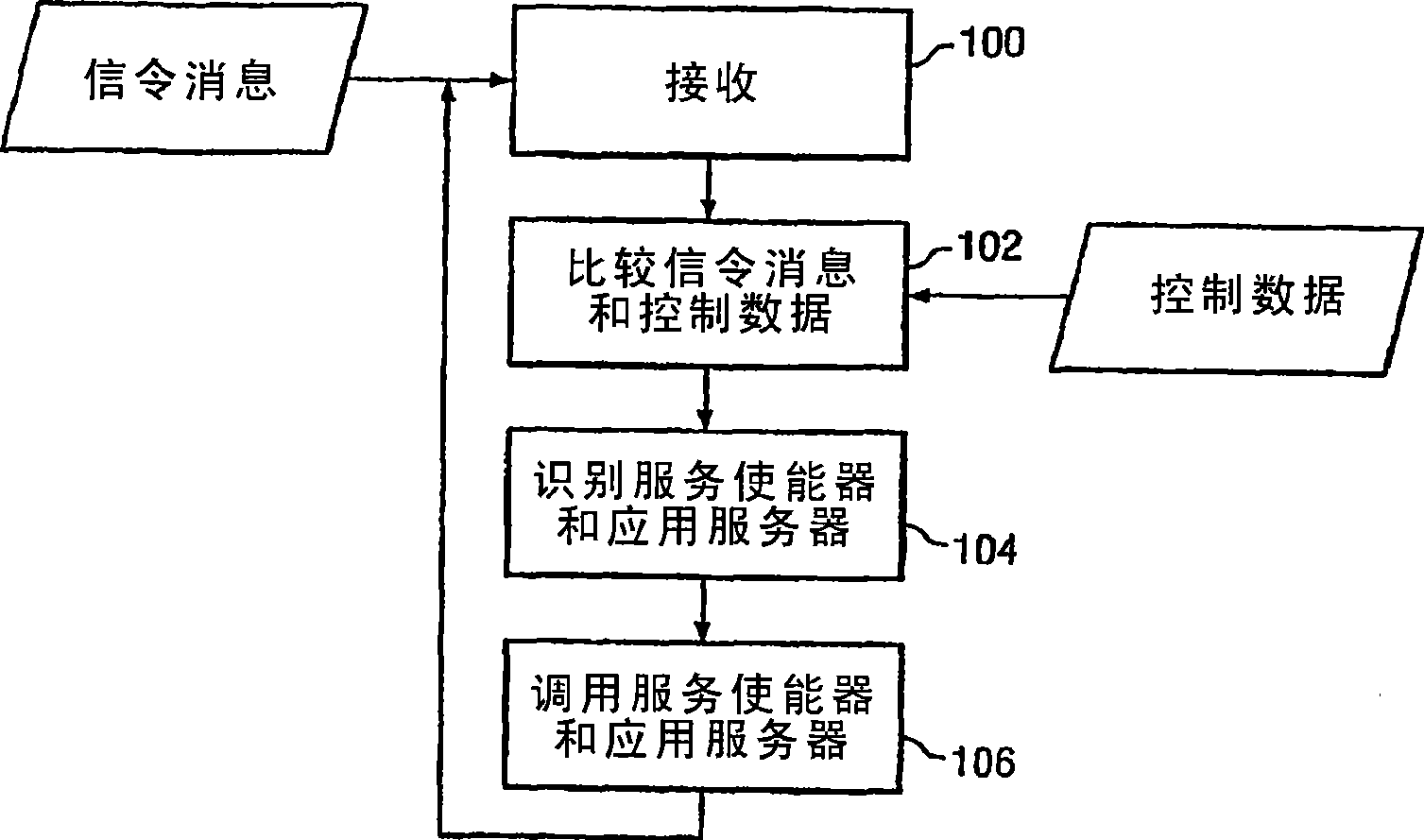
ActiveCN101379757AEliminate or reduce shortcomingsEliminate or reduce problemsSecuring communicationNetwork resource managementApplication server
In certain embodiments, the present disclosure comprises a system and method for providing feature services in a multimedia communication environment. The system and method comprise comparing signaling messages with control data to identify one or more service enablers and application servers that are responsive to the signaling message. Each responsive service enabler is invoked in accordance with an associated policy hook. In certain other embodiments, a system for enforcing policy in a communication network includes a policy server which is operable to receive a request to invoke an application, receive a policy profile for a network user, and decide a proper allocation of network users based on the policy profile, the application, and available network resources. The policy server is further operable to communicate with a non-SIP application. The system also includes a network resource manager operably associated with the policy server and operable to monitor available network in the resources in the communication network. In addition, the network resource manager is functional to allocate network resource amongst a plurality of network users. The system also contains an application control point which is operably associated with the policy server and operable to communicate with a SIP application. The system is operable to use policy peering between the home and visited network to enable user-specific policies to be enforced while roaming.
Owner:CISCO TECH INC
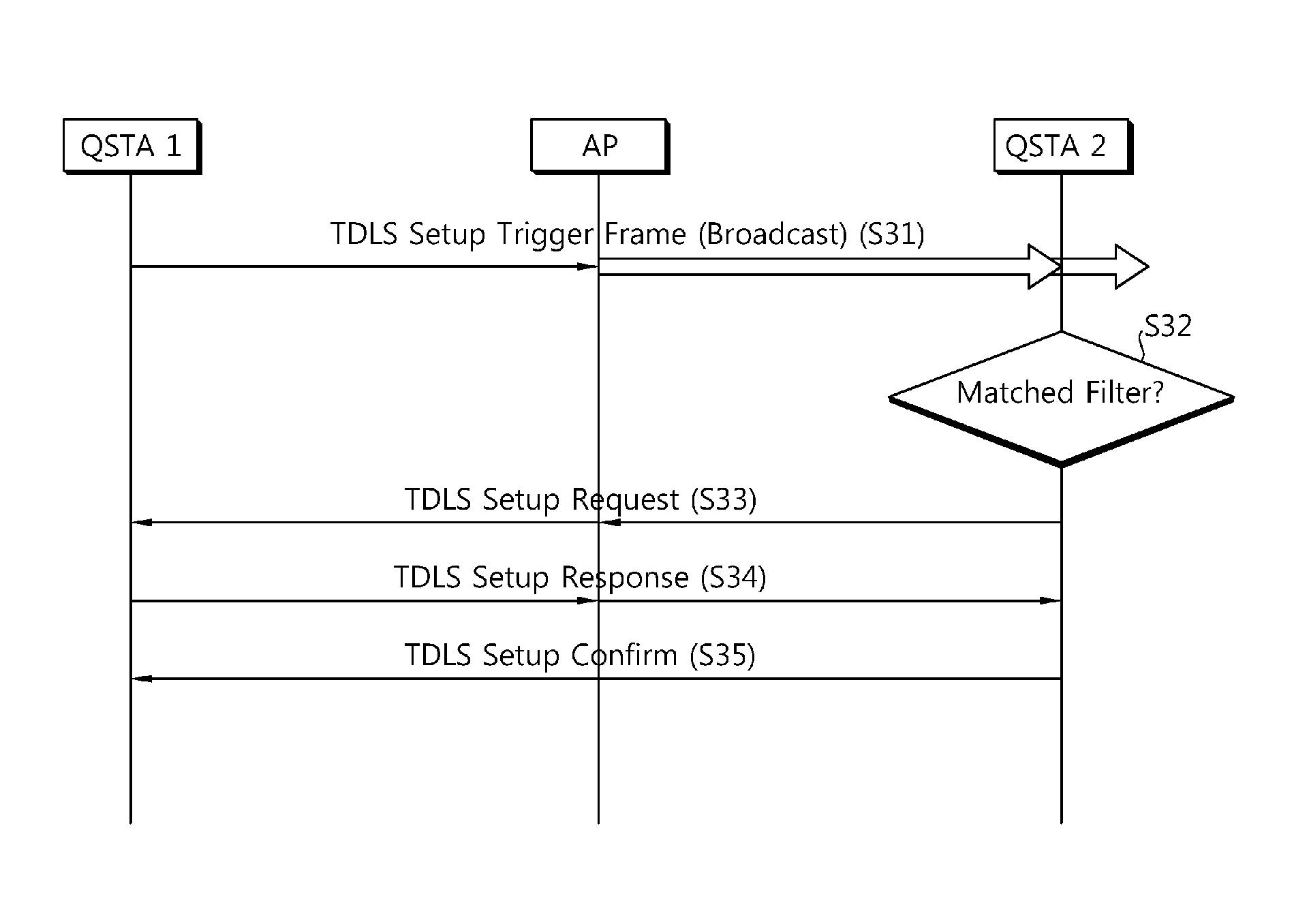
Direct link setup method in tunneled direct link setup (TDLS) wireless network
ActiveUS20110228755A1Process stabilityConnection managementWireless commuication servicesQuality of servicePeering
According to embodiments of the present invention, there is provided a direct link setup method in a tunneled direct link setup (TDLS) wireless communication system. The method including: an initiator QSTA acquiring medium access control (MAC) address information of a peer quality of service station (QSTA); transmitting a TDLS setup request frame comprising the MAC address information to the peer QSTA; receiving a TDLS setup response frame in response to the TDLS setup request frame to the initiator QSTA from the peer QSTA; and transmitting a TDLS setup confirm frame in response to the TDLS setup response frame to the peer QSTA.
Owner:LG ELECTRONICS INC
Method and system for measuring market-share for an entire telecommunication market
ActiveUS20110038468A1Reduce errorsLess time-consumingMultiplex system selection arrangementsMarket predictionsPeeringBusiness enterprise
A method for collecting data to measure market-share for a defined telecommunication market. A market of interest is defined and a random panel of numbers is created. A call set-up is initiated to the created random panels by generating signaling messages wherein the signaling messages access a Calling Name Services (CNAM) database, a Local Number Portability (LNP) database, an E-911 Automated Location Information (ALI) database and a Line Information Database (LIDB) using signaling system 7 (SS7) protocol. Generated signaling messages access ENUM (Telephone Number Mapping) database and Internet Protocol (IP) Peering database using IP. The response to the generated signaling messages are used to determine assignment status, business ownership, businesses versus residential status and the technology employed for a given number in the created panel. In one embodiment, the process is repeated over a period in order to determine changes to the market-share and derivative metrics for the telecommunication market.
Owner:THE NIELSEN CO (US) LLC
BGP dynamic AS renumbering
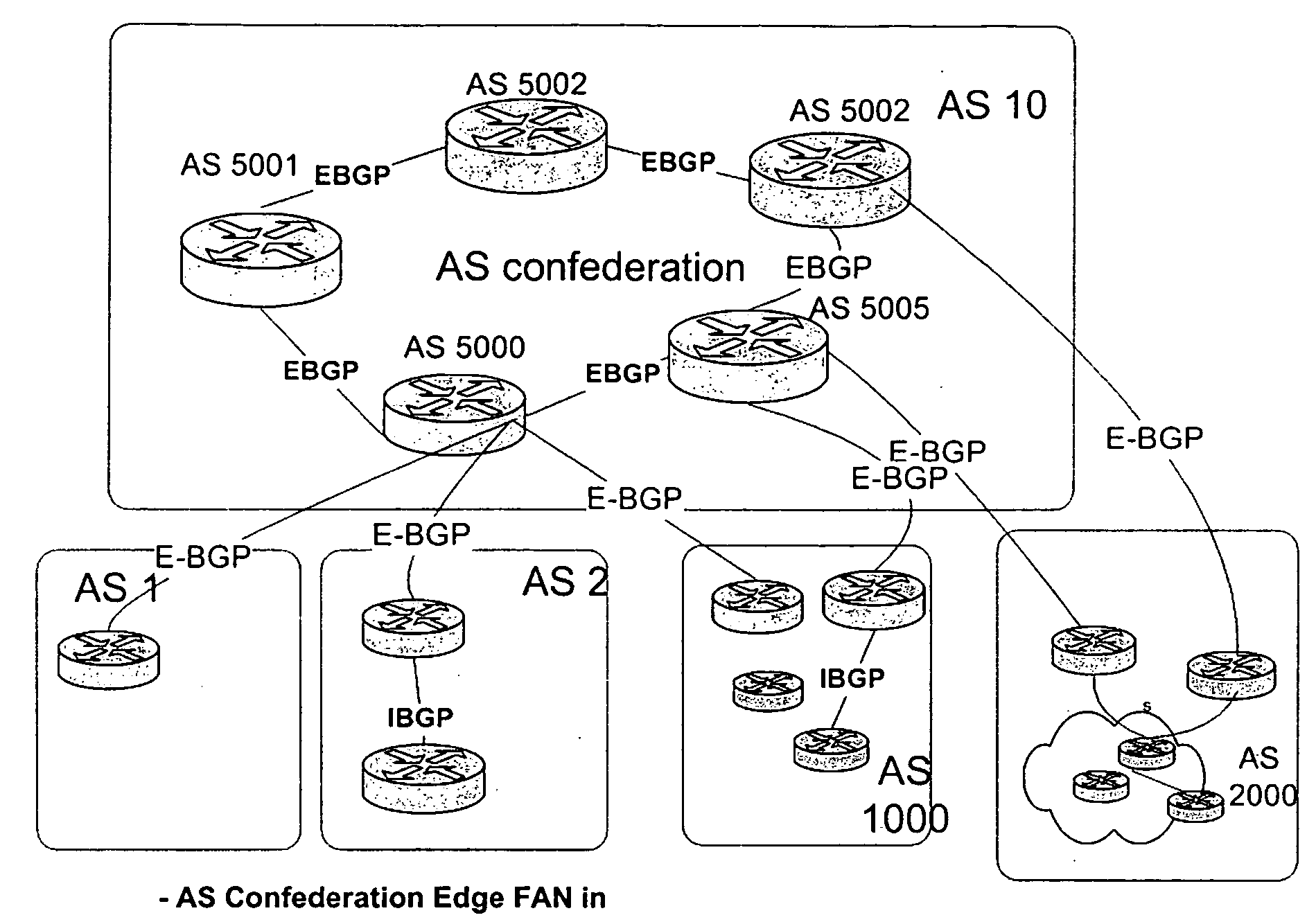
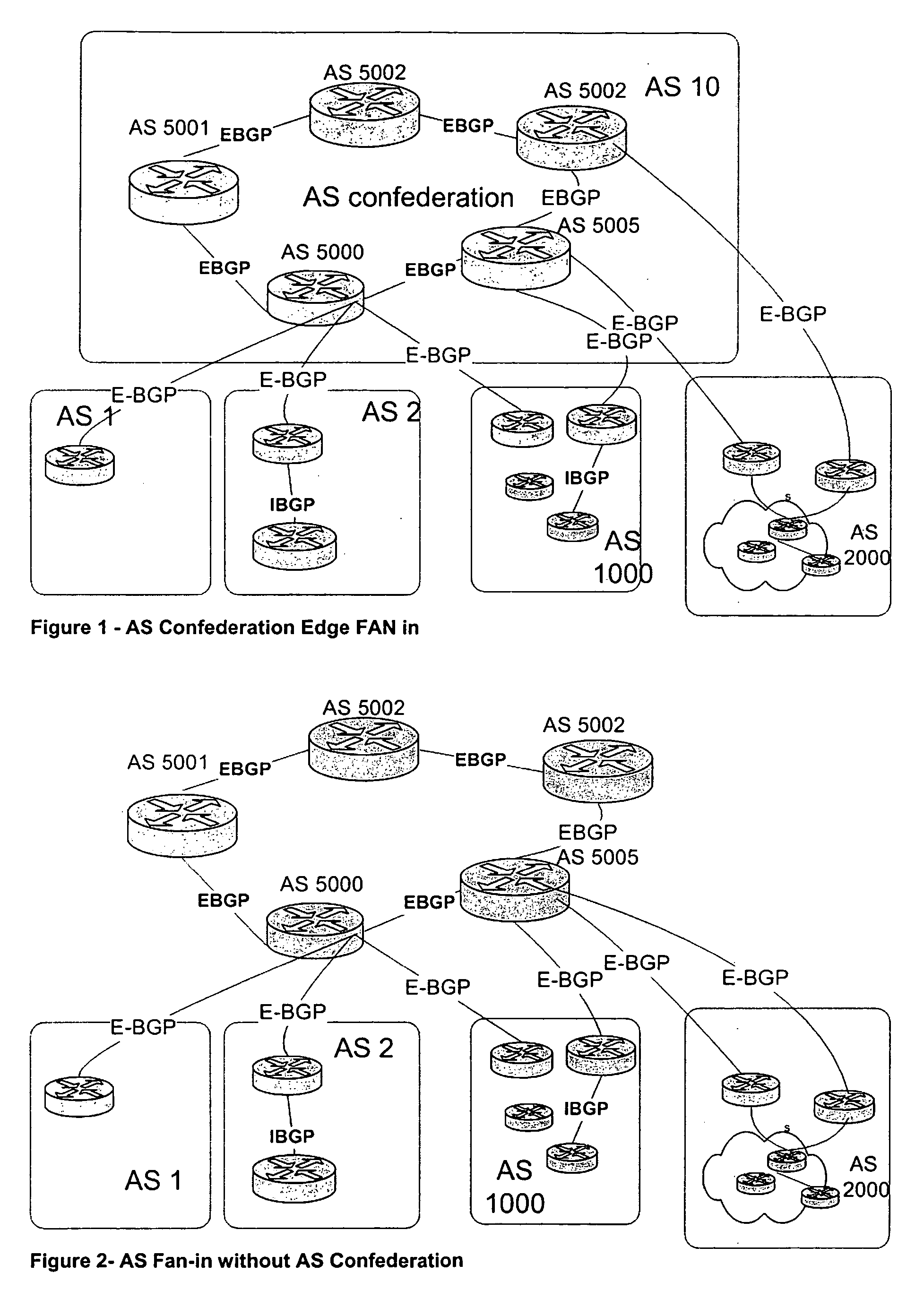
This invention has two mechanisms: Dynamic AS switching for AS confederations and Dynamic AS switching. The Dynamic AS switching for AS confederation mechanism provides a mechanism for an Autonomous System within an AS confederation to survive disconnection from the rest of the Autonomous Systems within the AS Confederation. This invention provides a mechanism for the AS within the AS confederation to use a pre-agreed upon fail-over to the internal AS, so its eBGP connections will not be reset. The Dynamic AS switching mechanisms allows to peers to re-negotiate AS number changes in any Autonomous Systems the peer represent without dropping the BGP peering session.
Owner:NEXTHOP TECH INC
Intelligent use of peering in public cloud
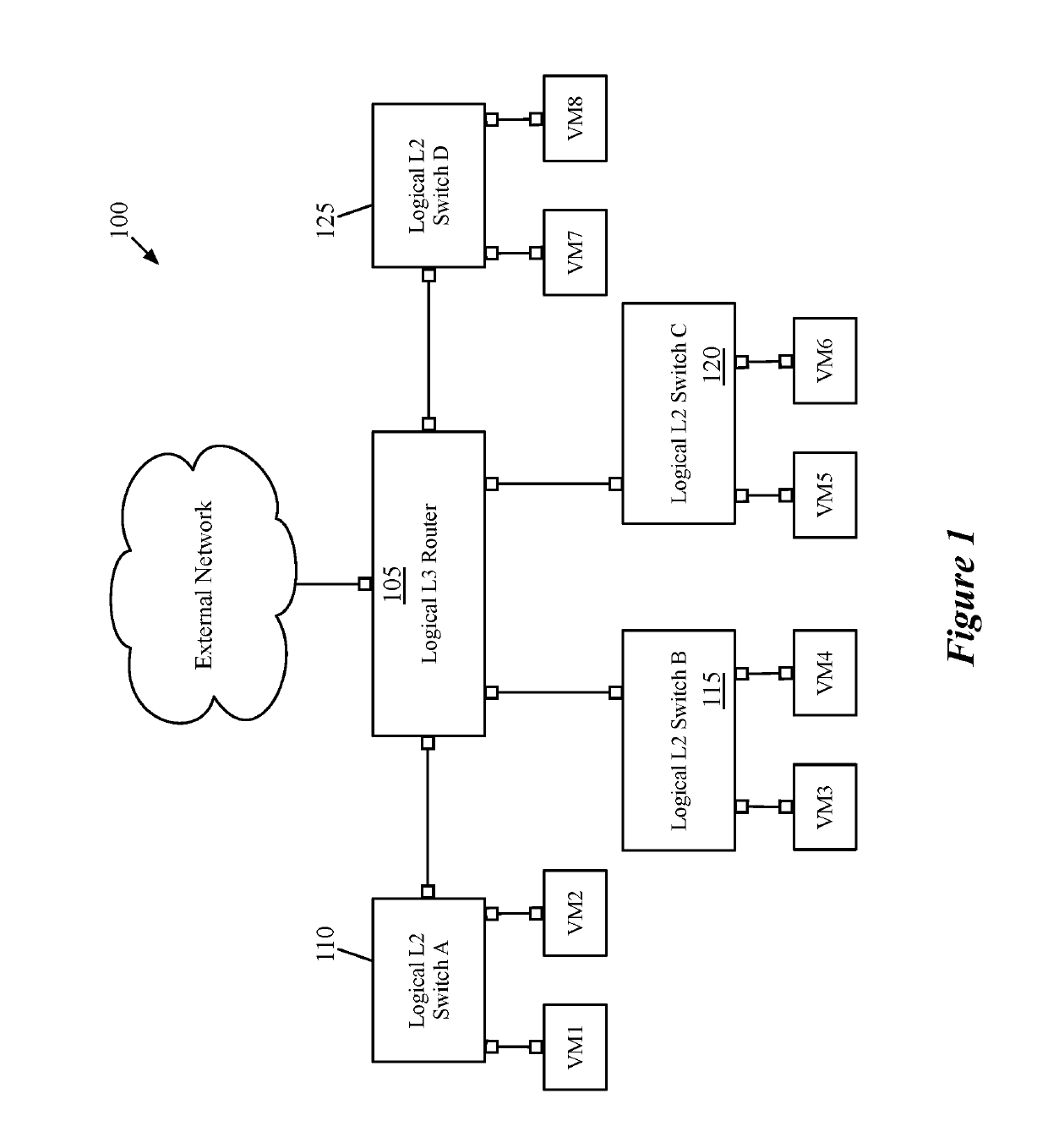
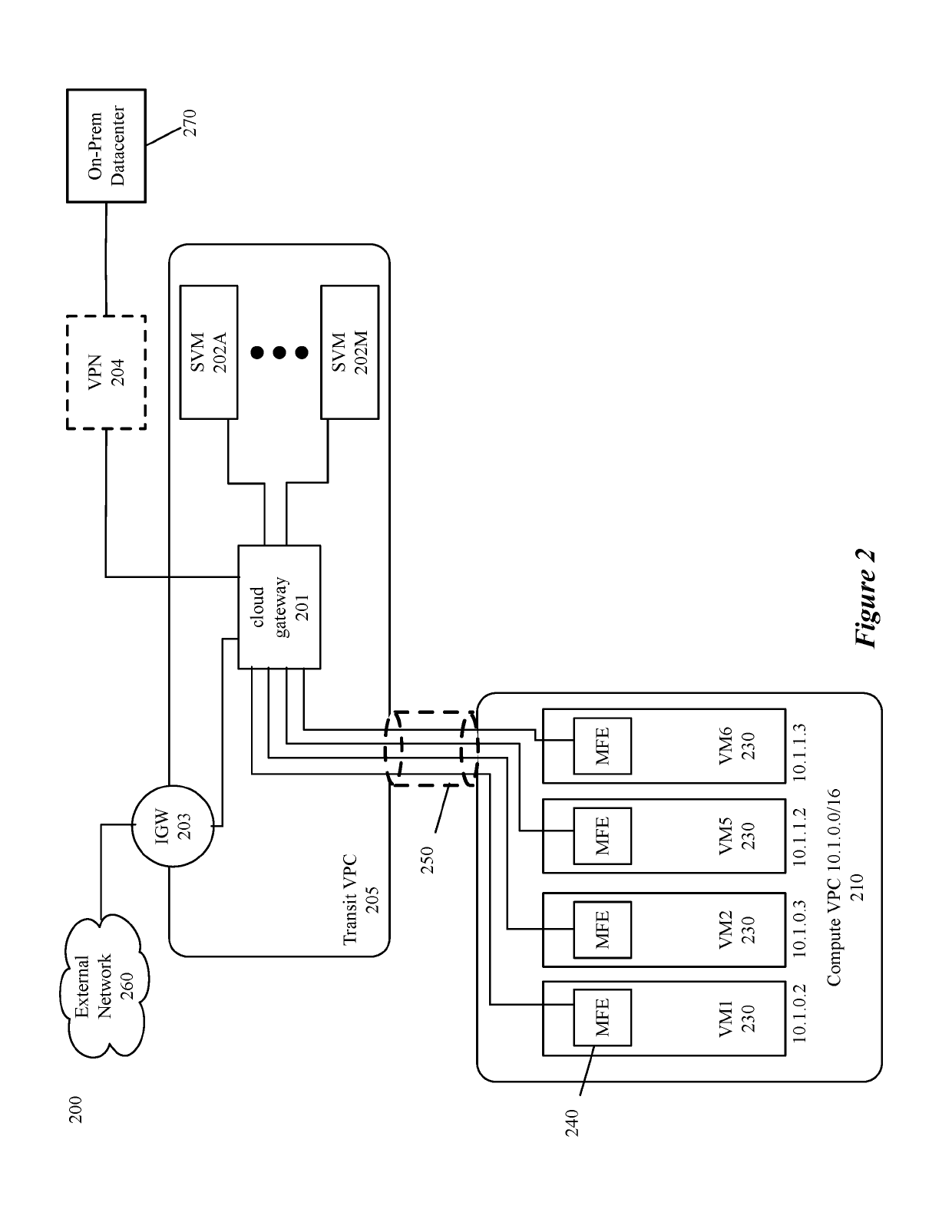
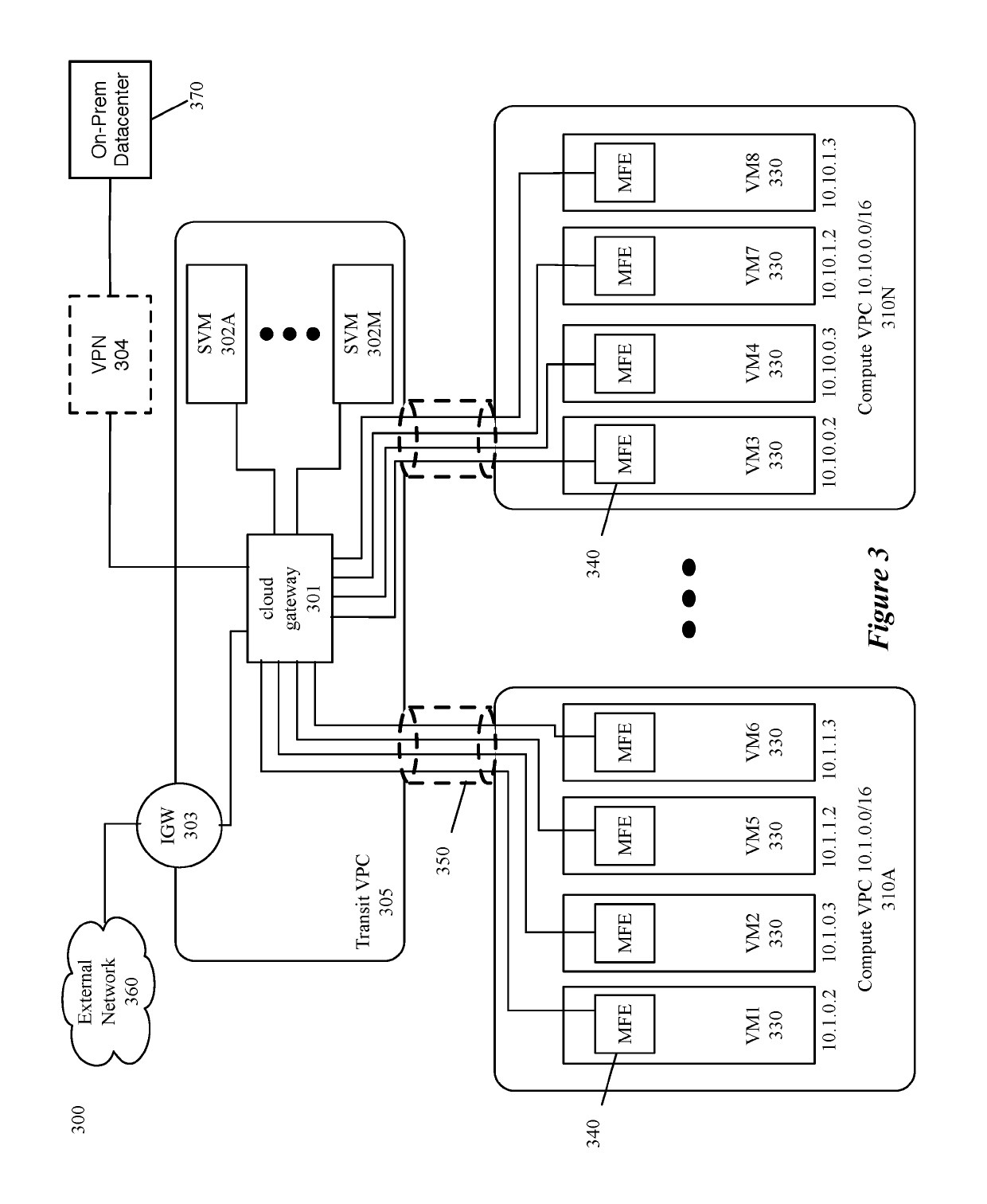
ActiveUS10491466B1Low costReduce management overheadNetworks interconnectionNetwork connectionsRouting decisionPeering
Some embodiments provide a method and system for configuring a plurality of managed forwarding elements (MFEs) in a plurality of cloud-provider virtual networks (CPVNs) to make routing decisions that efficiently use a peered transit CPVN and peering with other CPVNs in the plurality of CPVNs. In some embodiments, a controller set receives an identification of peering relationships between CPVNs in the plurality of CPVNs and generates configuration data for configuring each MFE. The configuration data is used to configure the MFE to forward data messages received at the MFE using a peering between a source CPVN and a destination CPVN when possible and to forward data messages received at the MFE to a transit gateway device in a transit CPVN when it is not possible to use a peering between the source and destination CPVNs.
Owner:VMWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com