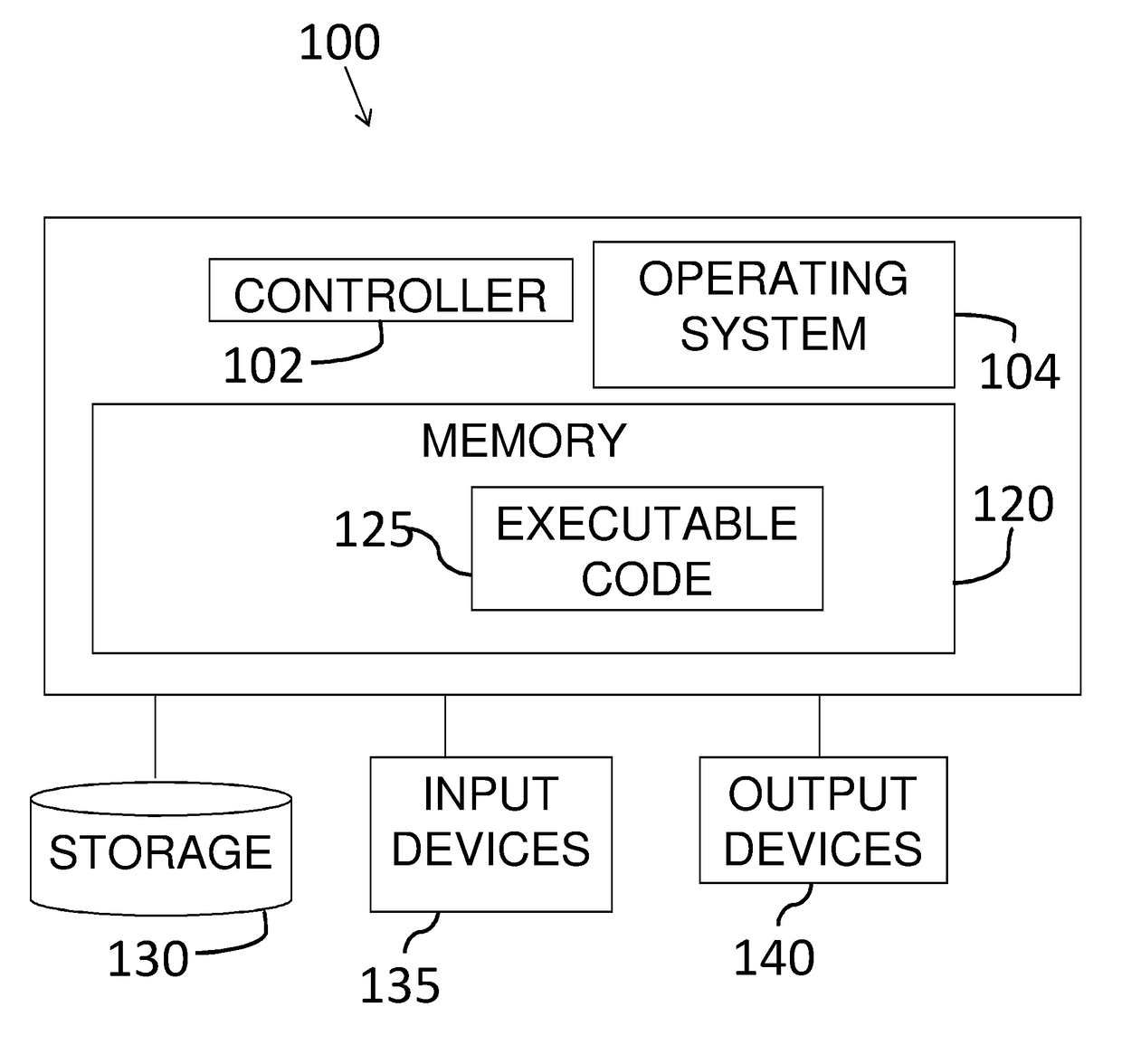
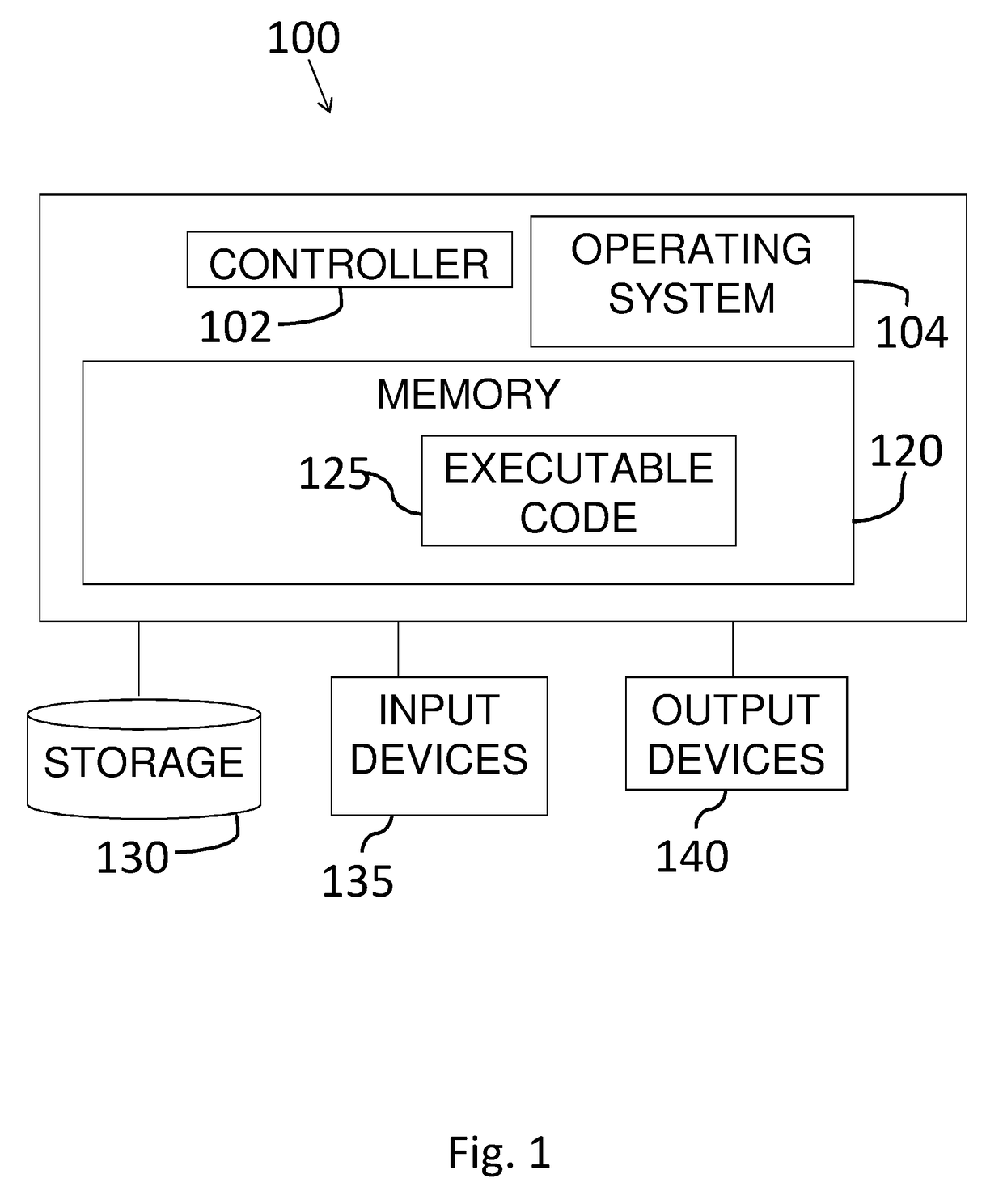
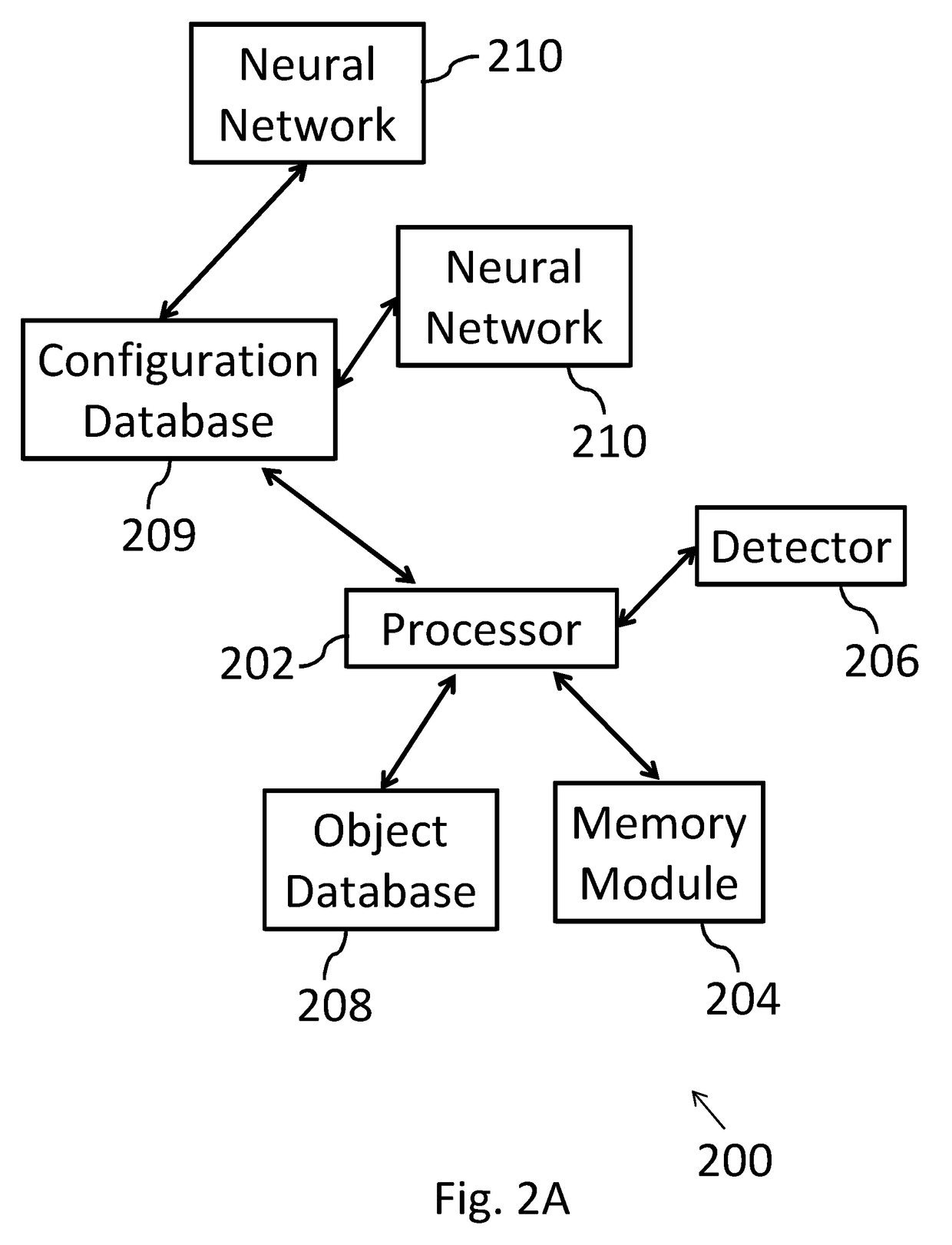
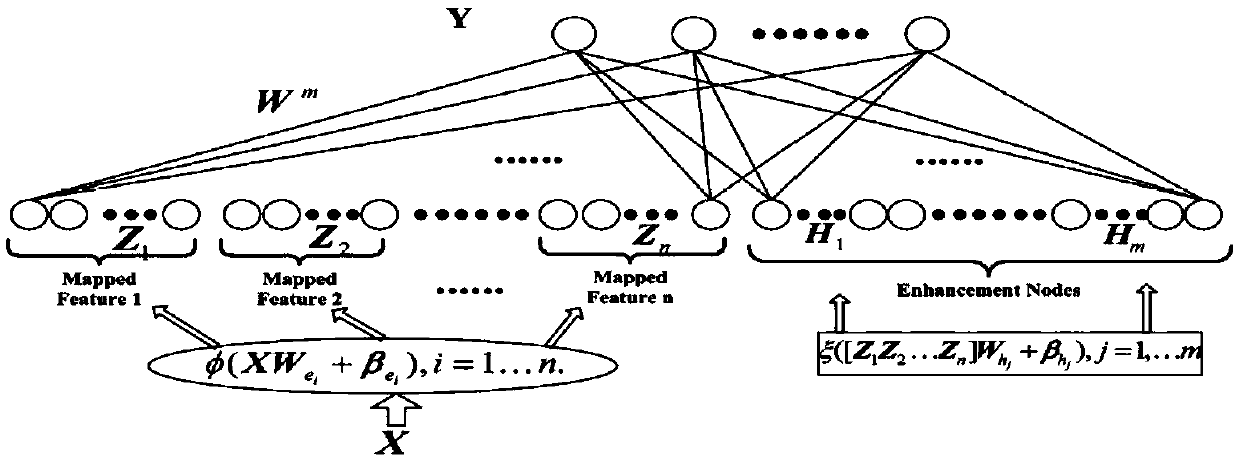
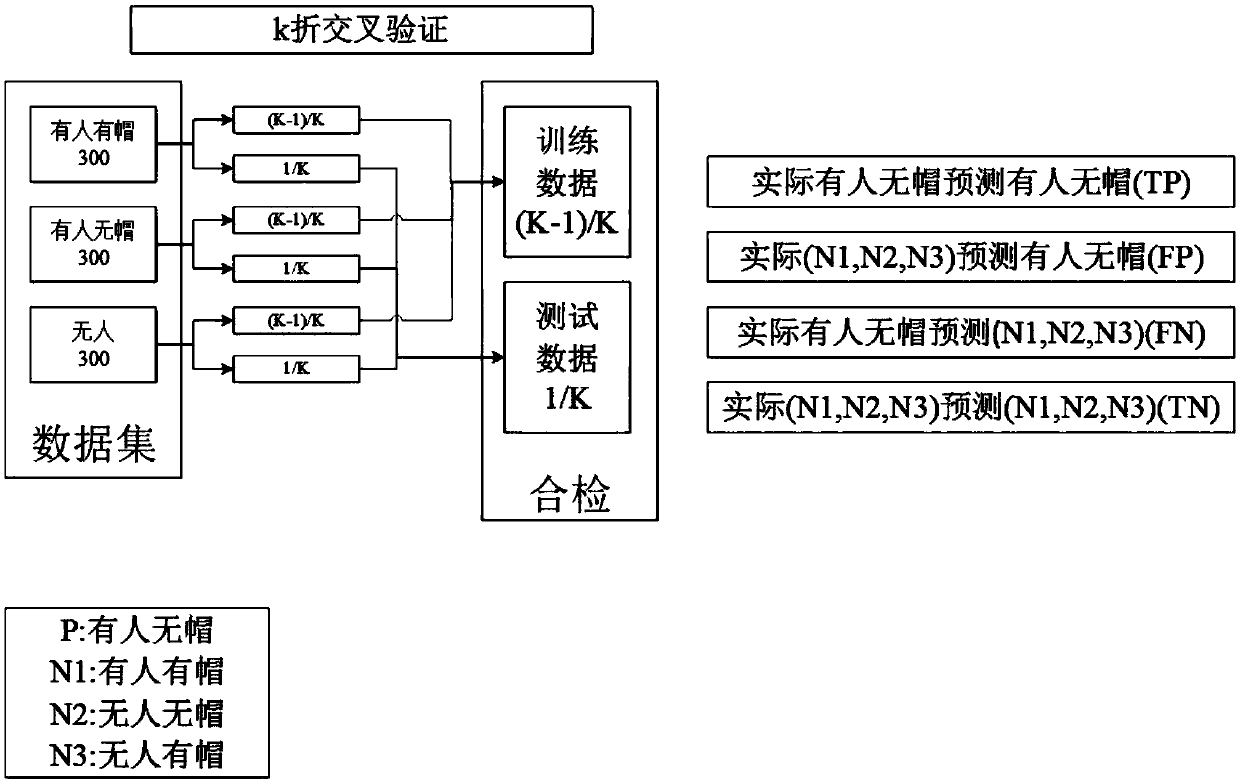
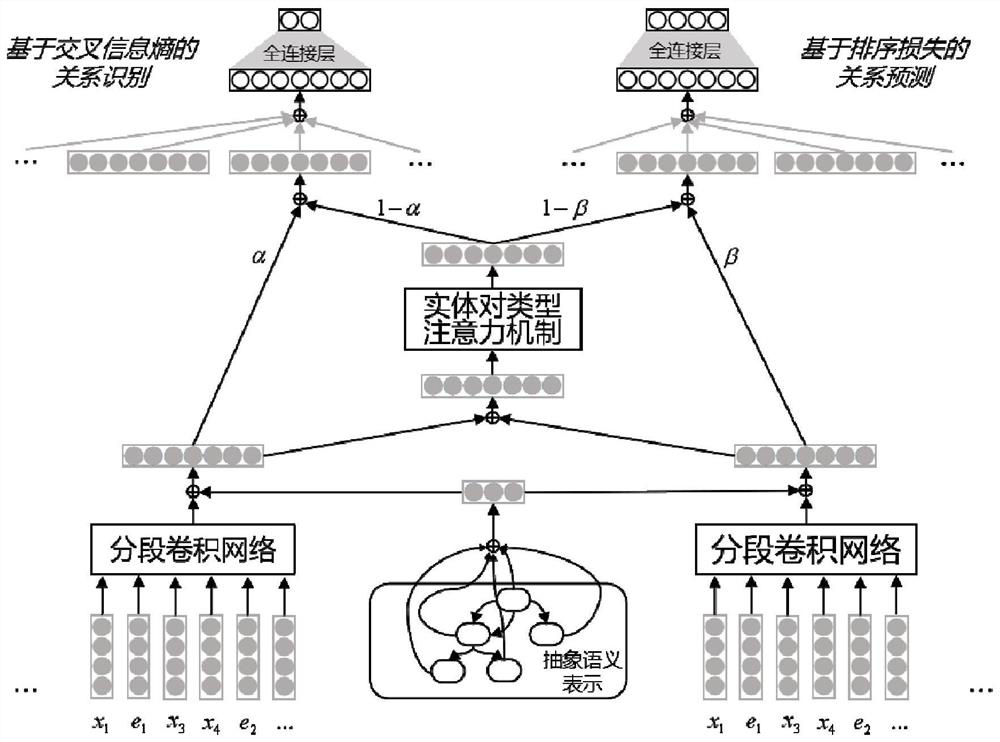
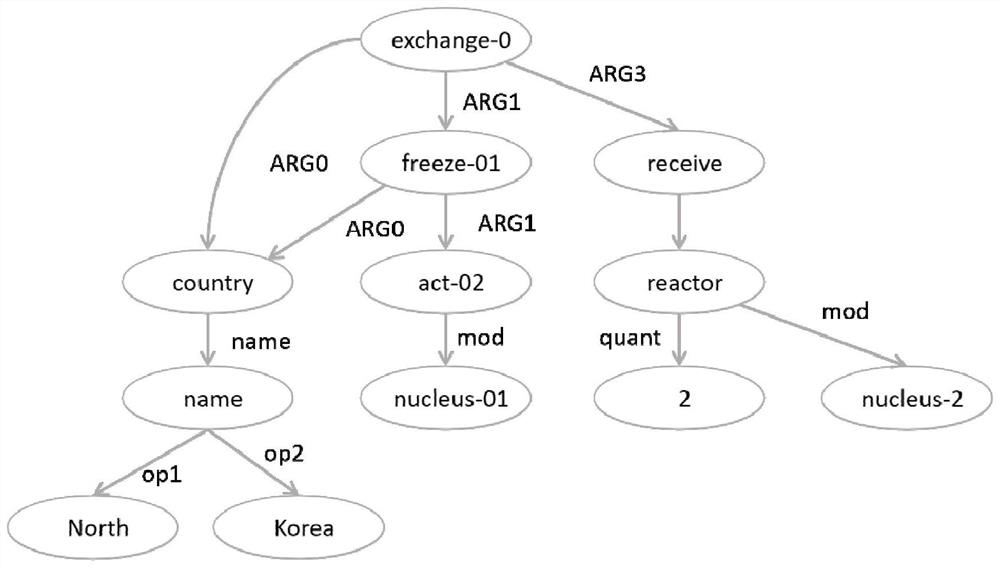
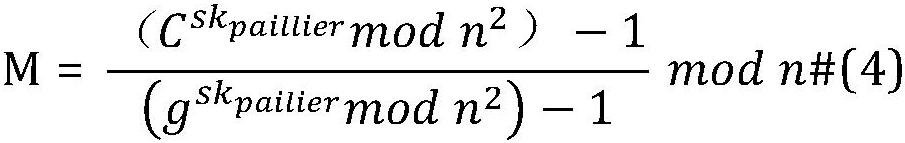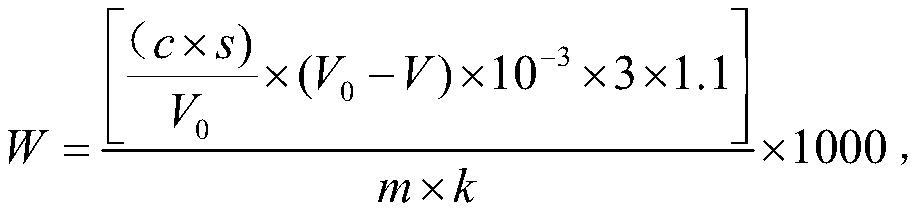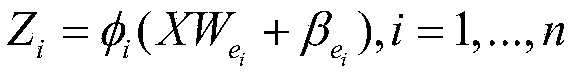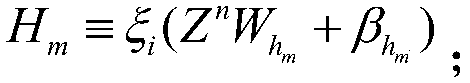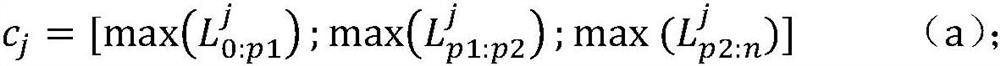Patents
Literature
165 results about "Learning architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
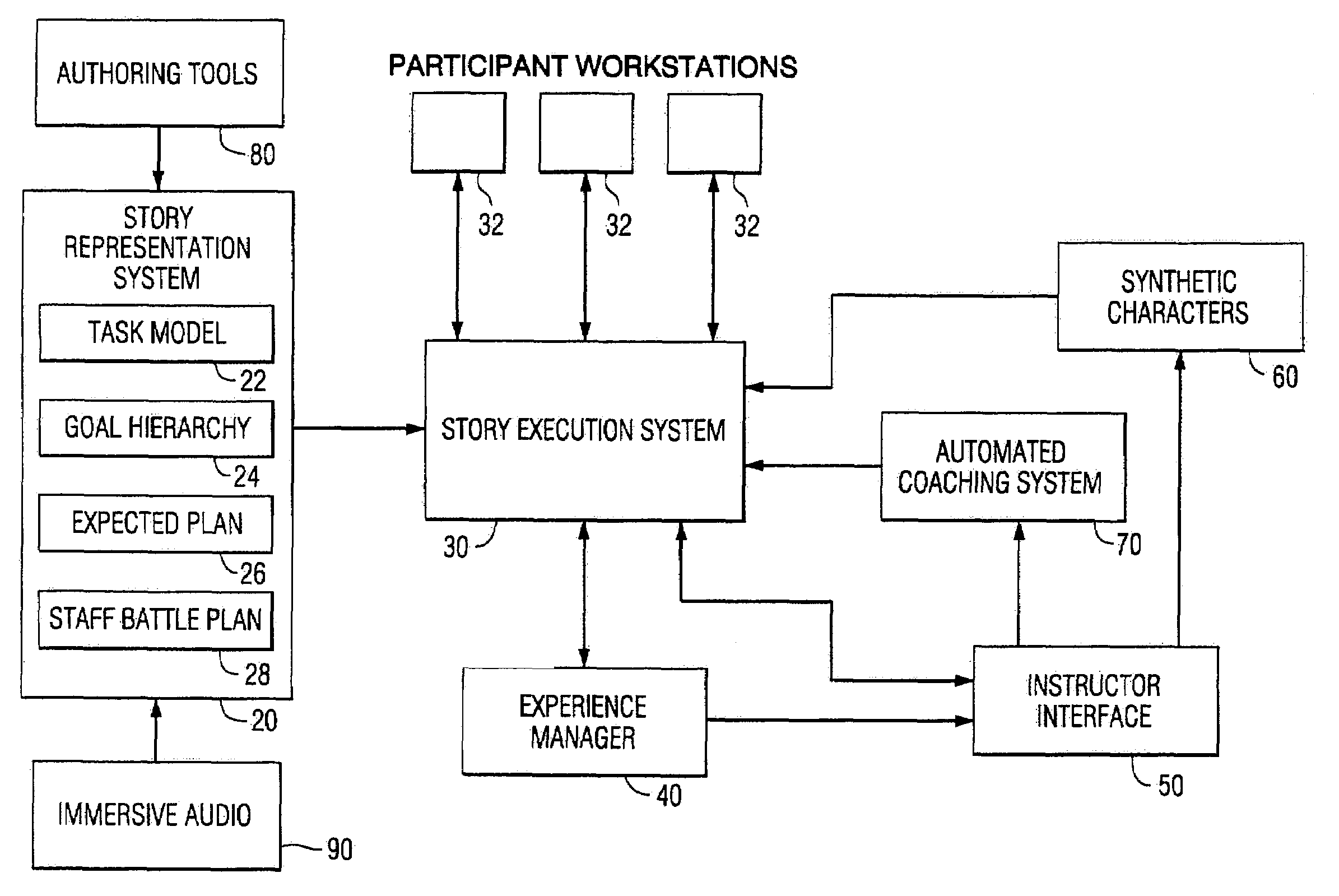
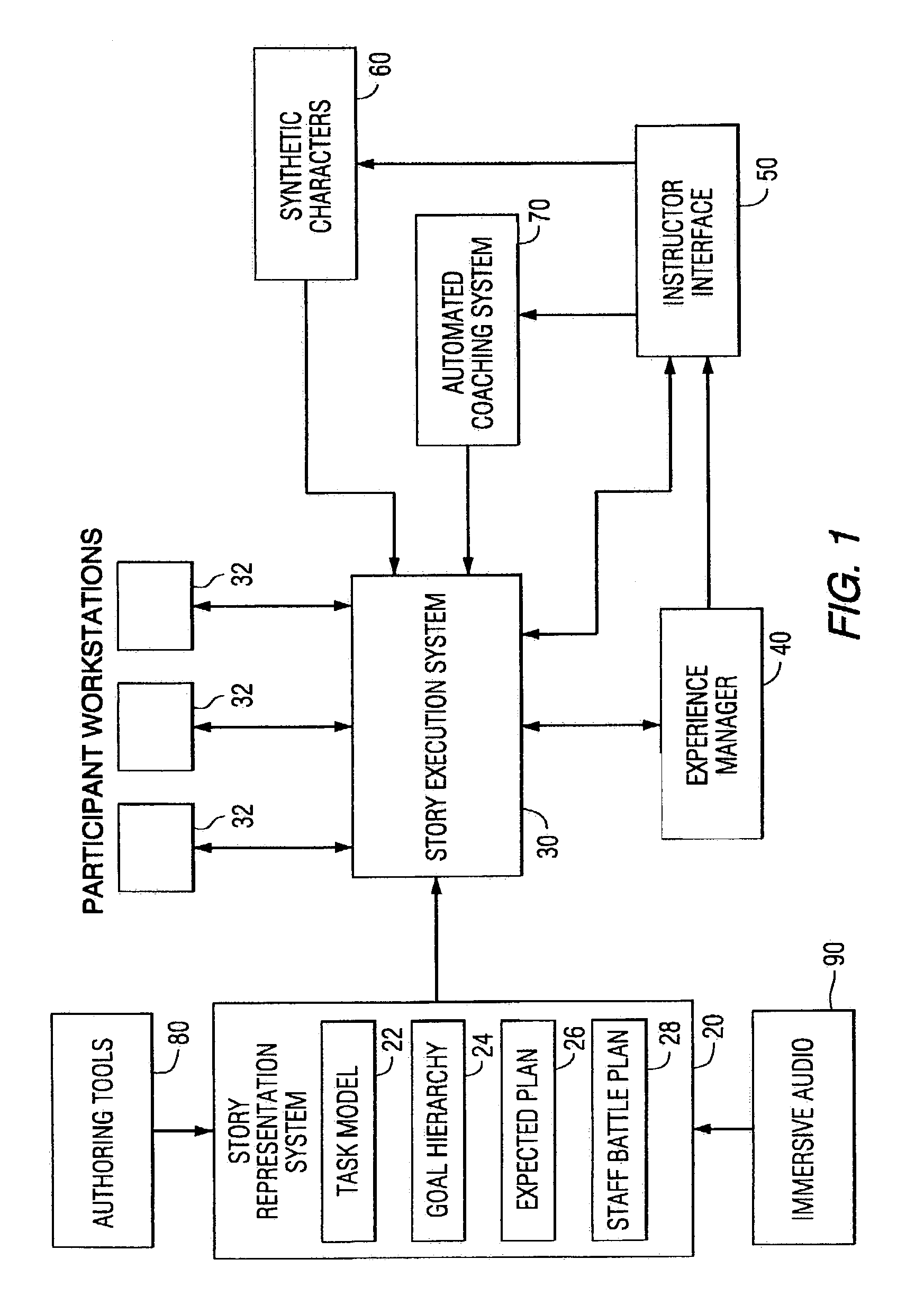
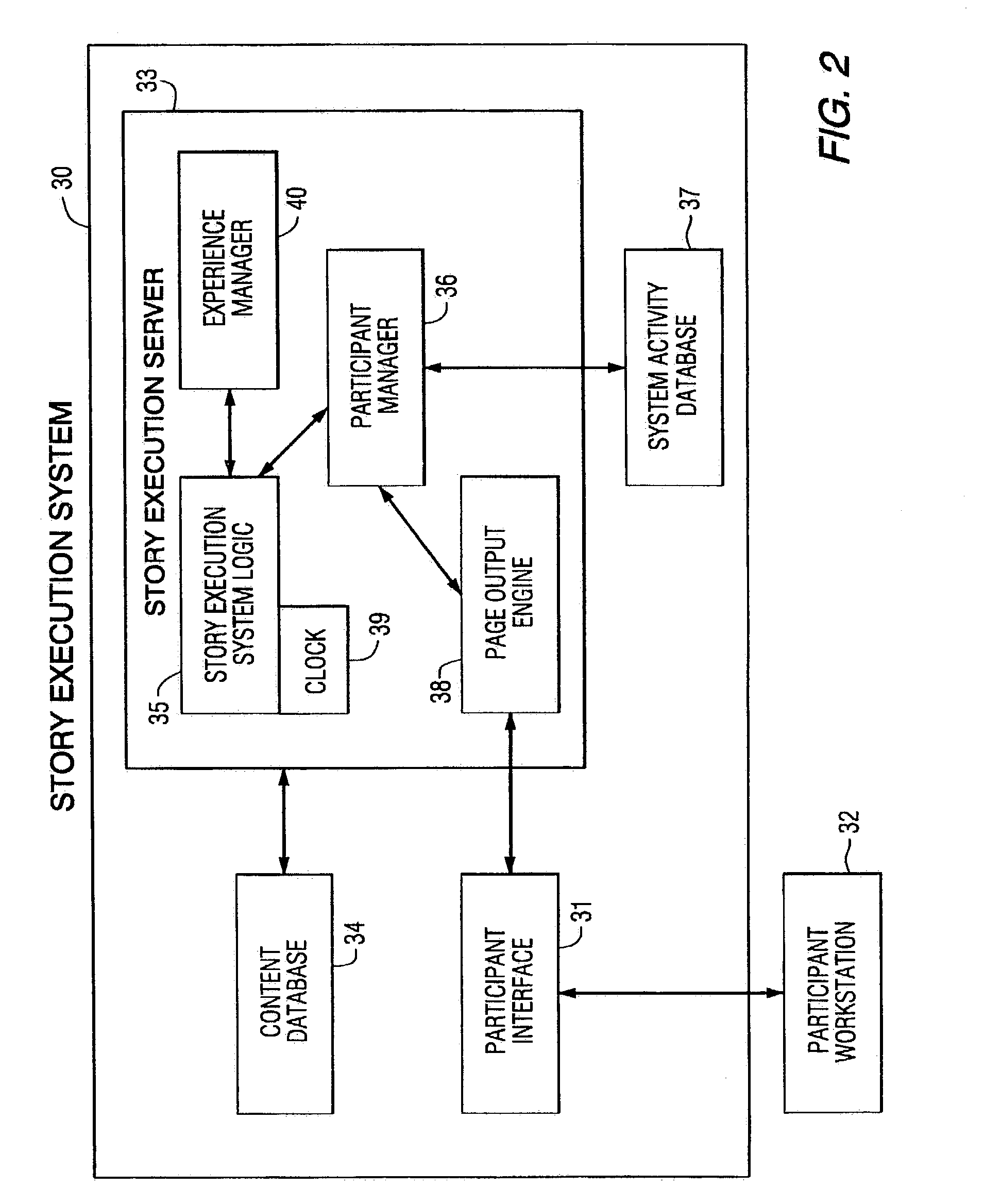
Method and apparatus for advanced leadership training simulation and gaming applications
InactiveUS7155158B1Maximize dramatic and educational effectivenessPromote achievementCosmonautic condition simulationsVideo gamesSkill setsLearning architecture
A method and apparatus advanced leadership training simulation wherein the simulation teaches skills in leadership and related topics through an Internet-based distance-learning architecture. The distance-learning features link trainees at remote locations into a single collaborative experience via computer networks. Instructional storylines are created and programmed into a computer and then delivered as a simulated but realistic story to one or more participants. The participants' reactions are monitored and compared with expected results. The storyline may be altered in response to the participants' responses and synthetic characters may be generated to act as automated participants or coaches. Constructive feedback is provided to the participants during or after the simulation.
Owner:UNIV OF SOUTHERN CALIFORNIA +1
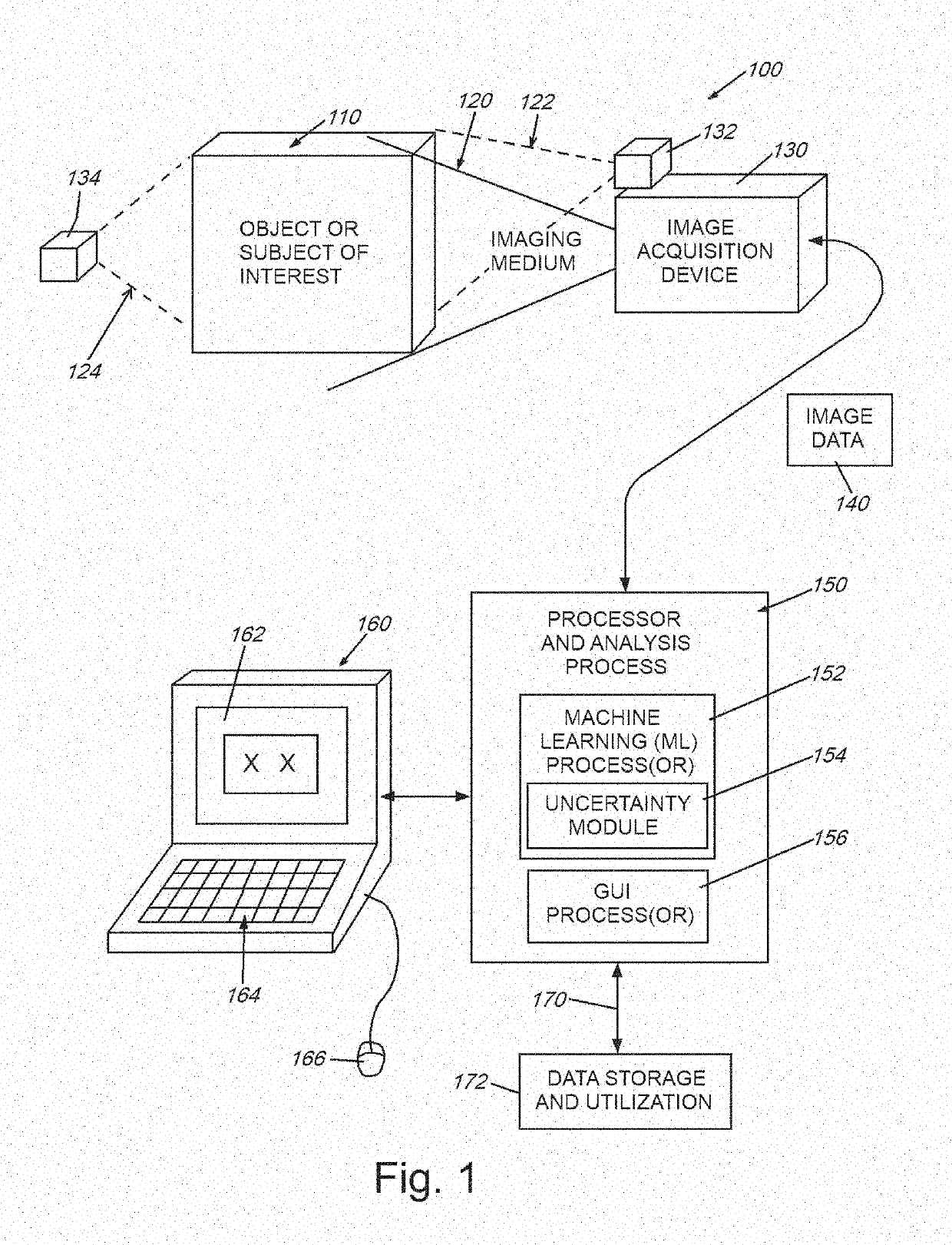
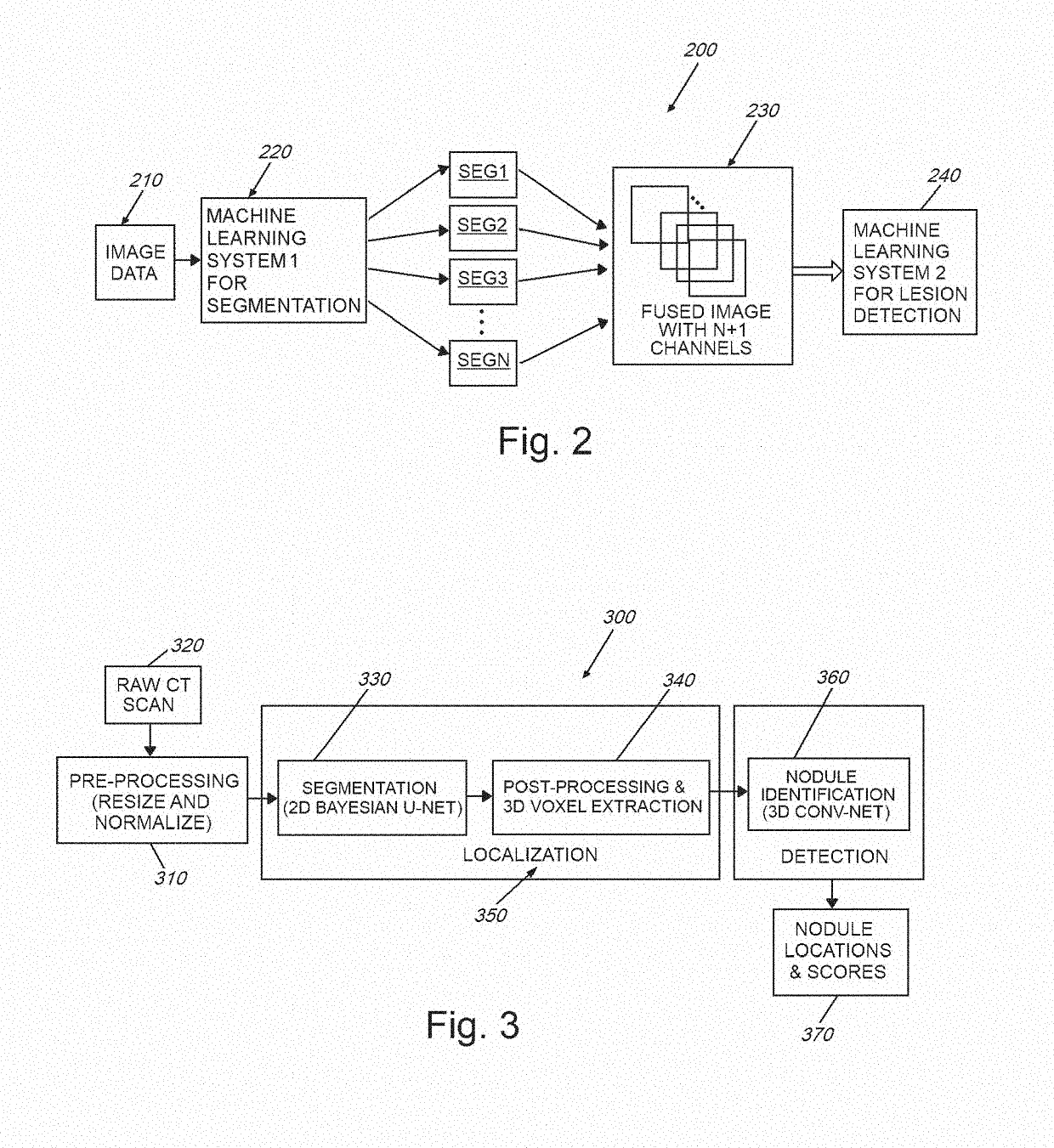
System and method for quantifying uncertainty in reasoning about 2d and 3D spatial features with a computer machine learning architecture
InactiveUS20190122073A1Efficient use ofOvercome disadvantagesImage enhancementImage analysisData setPropagation of uncertainty
This invention provides a system and method to propagate uncertainty information in a deep learning pipeline. It allows for the propagation of uncertainty information from one deep learning model to the next by fusing model uncertainty with the original imagery dataset. This approach results in a deep learning architecture where the output of the system contains not only the prediction, but also the model uncertainty information associated with that prediction. The embodiments herein improve upon existing deep learning-based models (CADe models) by providing the model with uncertainty / confidence information associated with (e.g. CADe) decisions. This uncertainty information can be employed in various ways, including (a) transmitting uncertainty from a first stage (or subsystem) of the machine learning system into a next (second) stage (or the next subsystem), and (b) providing uncertainty information to the end user in a manner that characterizes the uncertainty of the overall machine learning model.
Owner:CHARLES STARK DRAPER LABORATORY
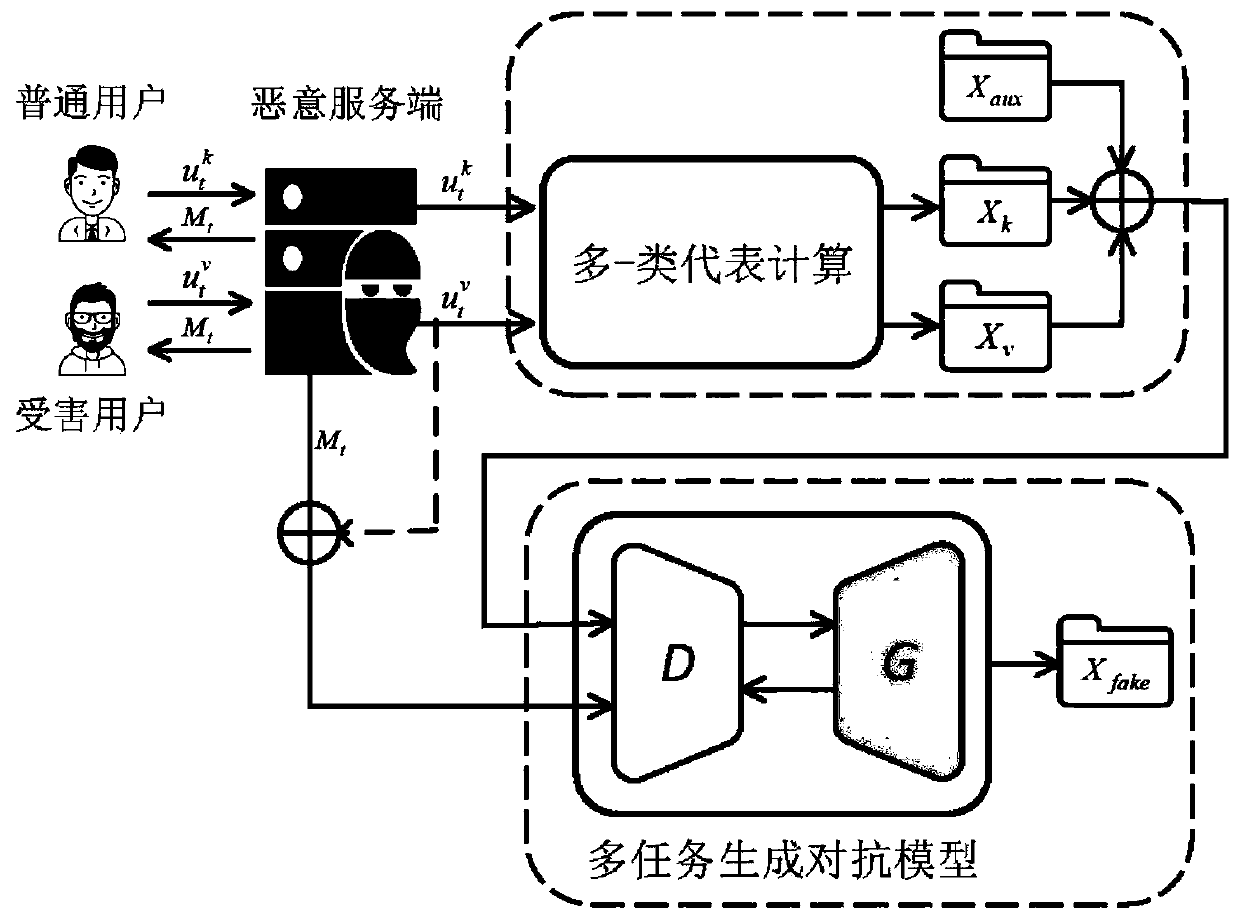
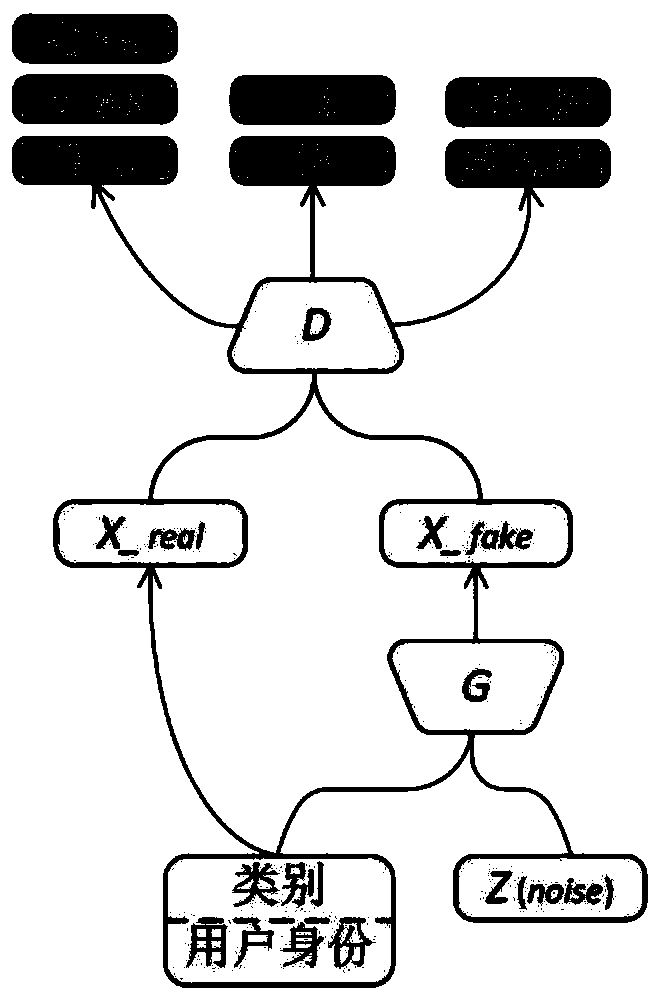
User data reconstruction attack method oriented to deep federal learning
PendingCN110008696AIncrease authenticityImprove concealmentDigital data protectionPlatform integrity maintainancePrivacy protectionData mining
The invention discloses a user data reconstruction attack method oriented to deep federal learning, which can reconstruct private data of a specific user and consider that attacks are implemented by amalicious server, so that negative effects are prevented from being introduced into an original shared model compared with a conventional attack method which can only reconstruct category representation data. Furthermore, the method introduces a multi-task generative adversarial model to simulate the distribution of user data, and the model is used for training the authenticity and category of aninput sample and the identification of the user identity to which the model belongs, so that the quality of the generated sample is improved. In order to better distinguish different users, the method introduces an optimized user data representative calculation method to describe user characteristics participating in federal learning, and the method is used for supervising training of a generative adversarial model. For an existing federal learning architecture concerning privacy protection, privacy leakage can be caused by a data reconstruction attack based on a multi-task generative adversarial model provided by the invention.
Owner:WUHAN UNIV
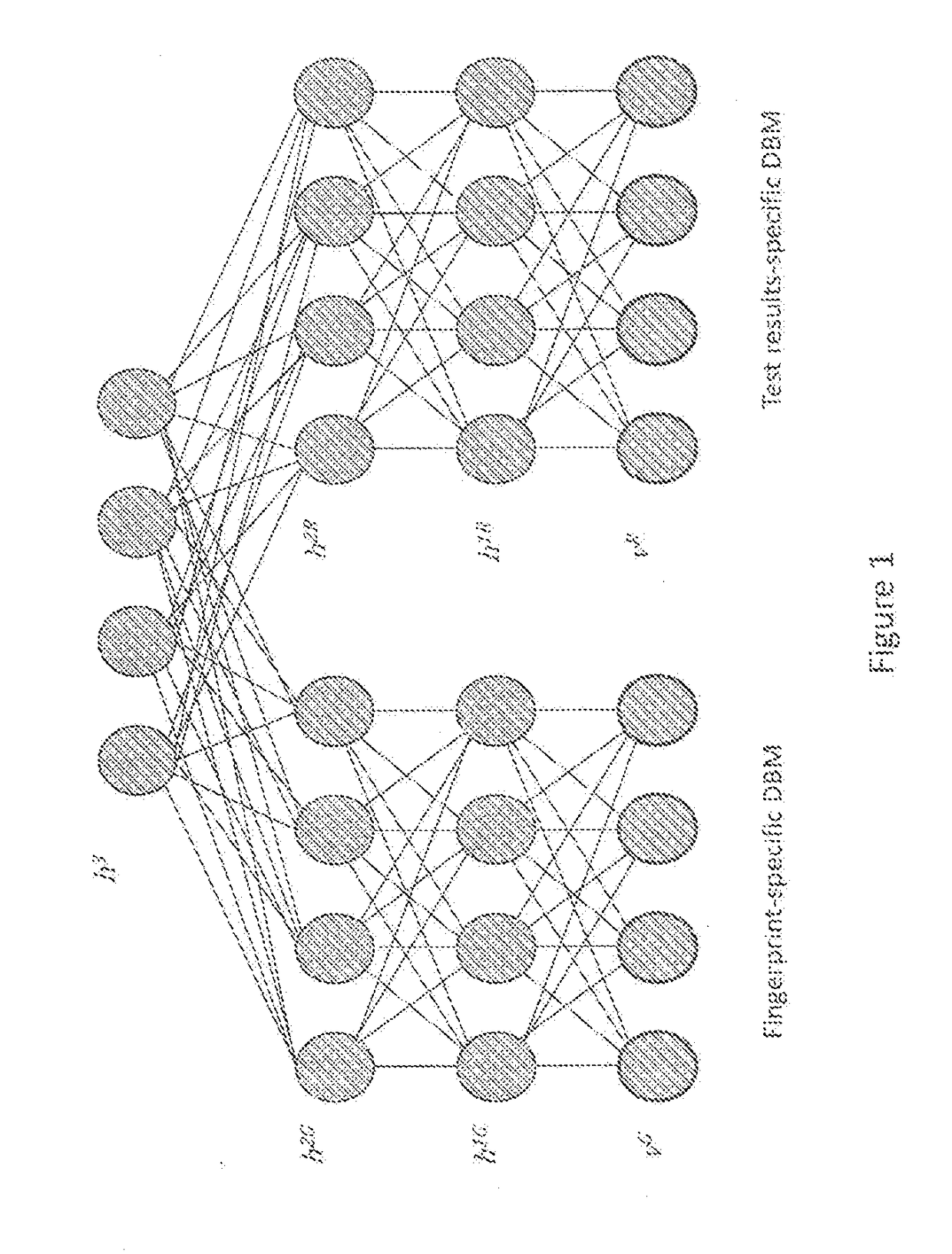
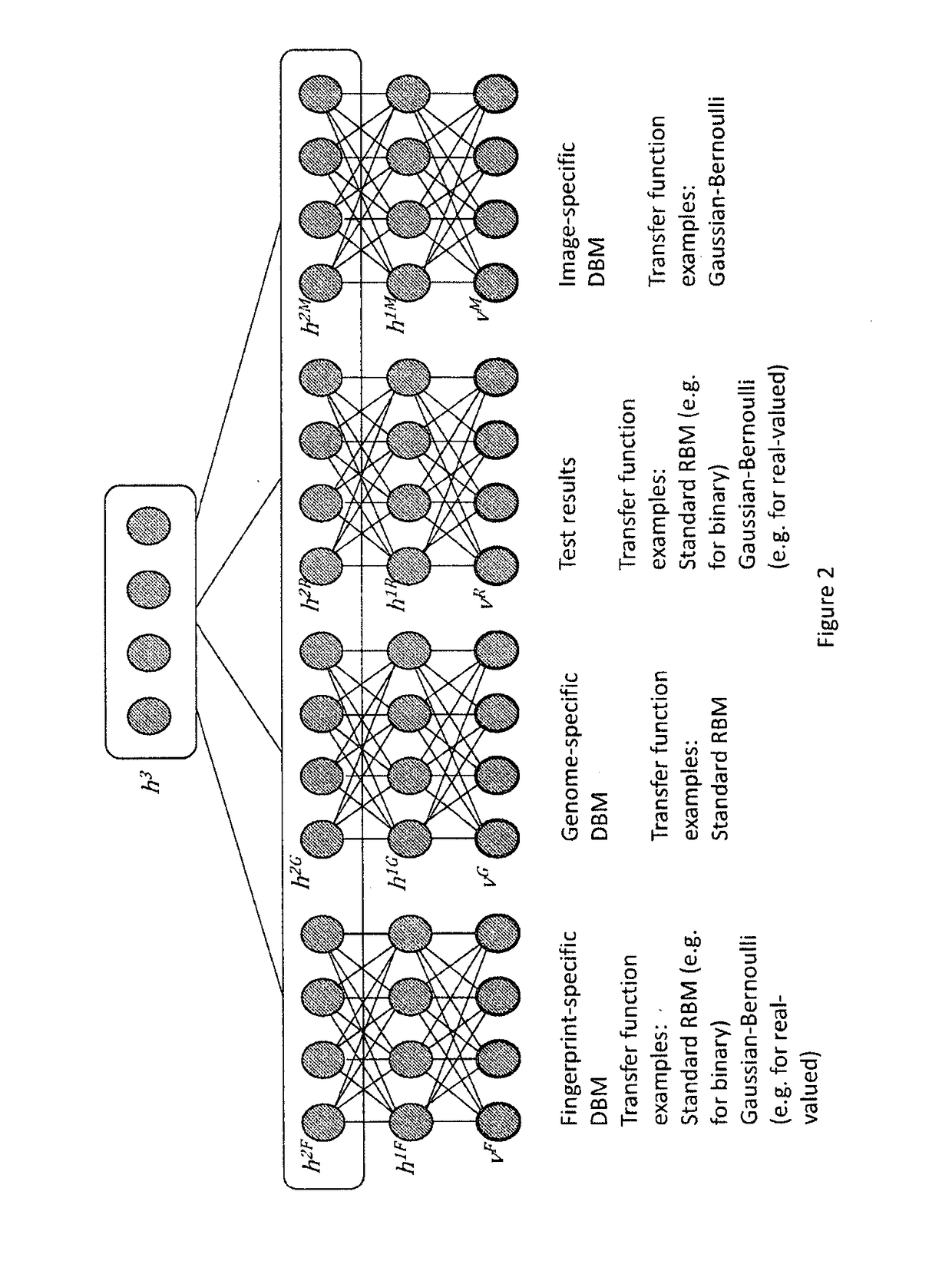
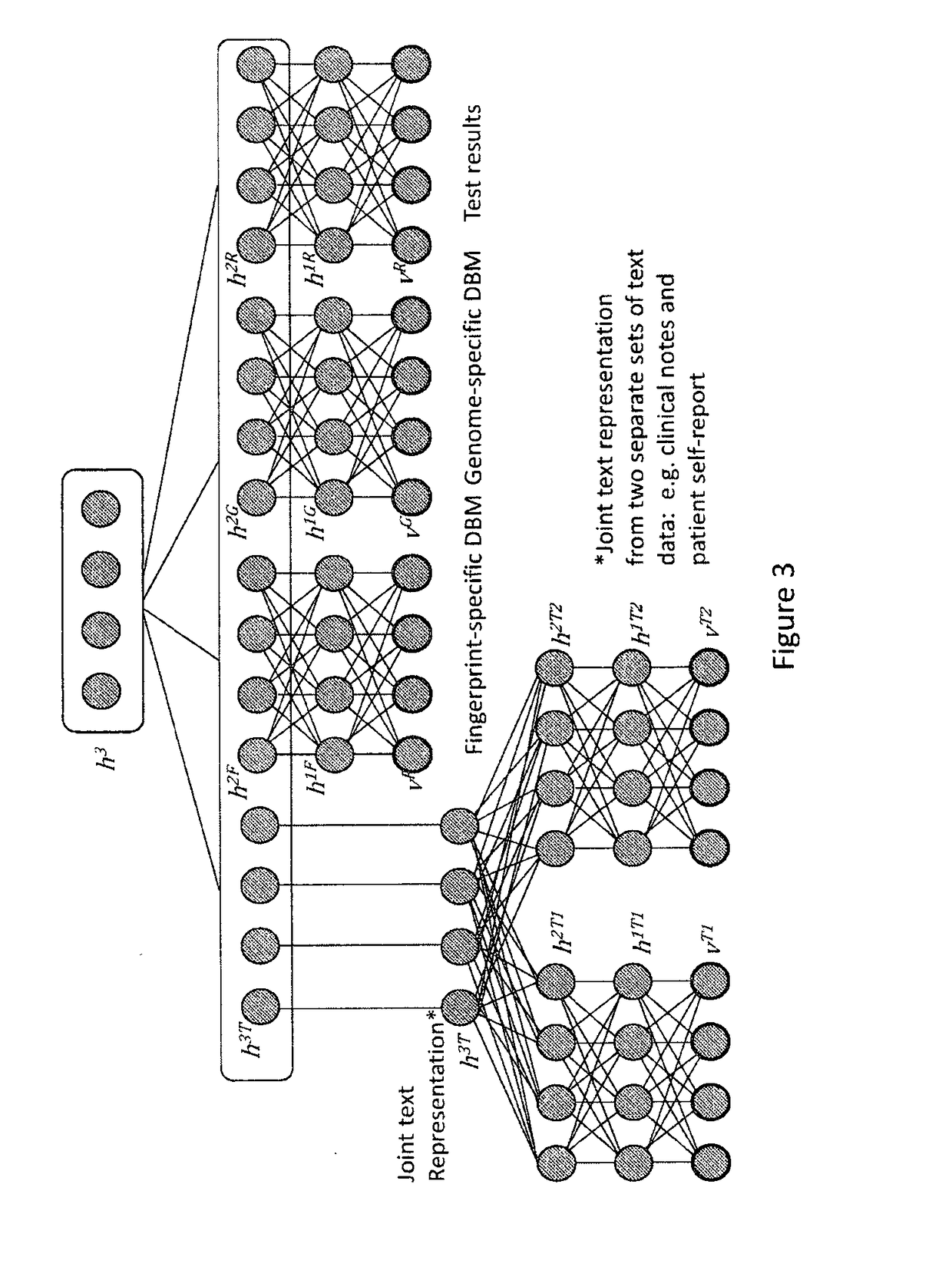
Systems and methods for multimodal generative machine learning
PendingUS20190018933A1Low costImprove throughputBiostatisticsChaos modelsChemical compoundClinical information
In various embodiments, the systems and methods described herein relate to multimodal generative models. The generative models may be trained using machine learning approaches, using training sets comprising chemical compounds and one or more of biological, chemical, genetic, visual, or clinical information of various data modalities that relate to the chemical compounds. Deep learning architectures may be used. In various embodiments, the generative models are used to generate chemical compounds that satisfy multiple desired characteristics of different categories.
Owner:PREFERRED NETWORKS INC
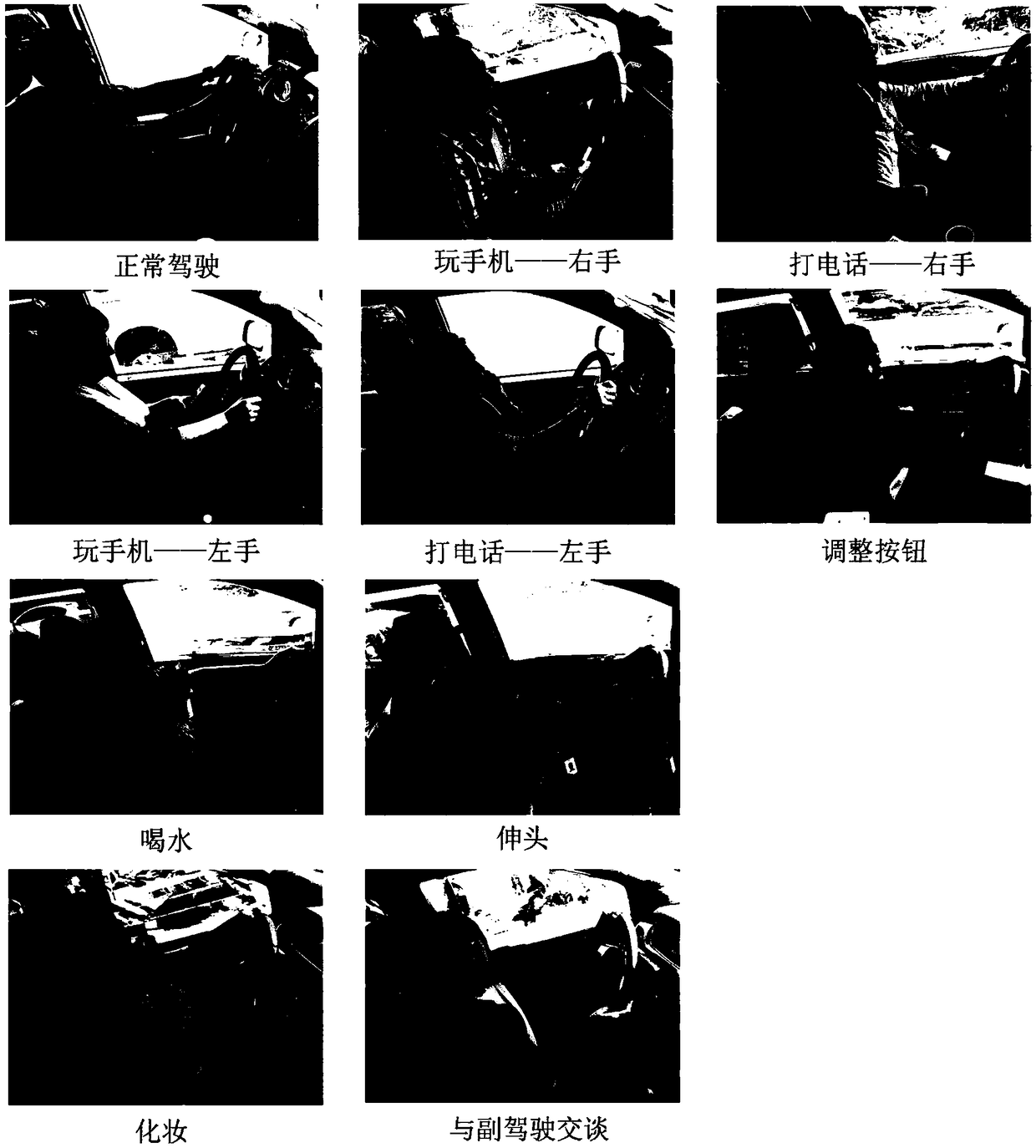
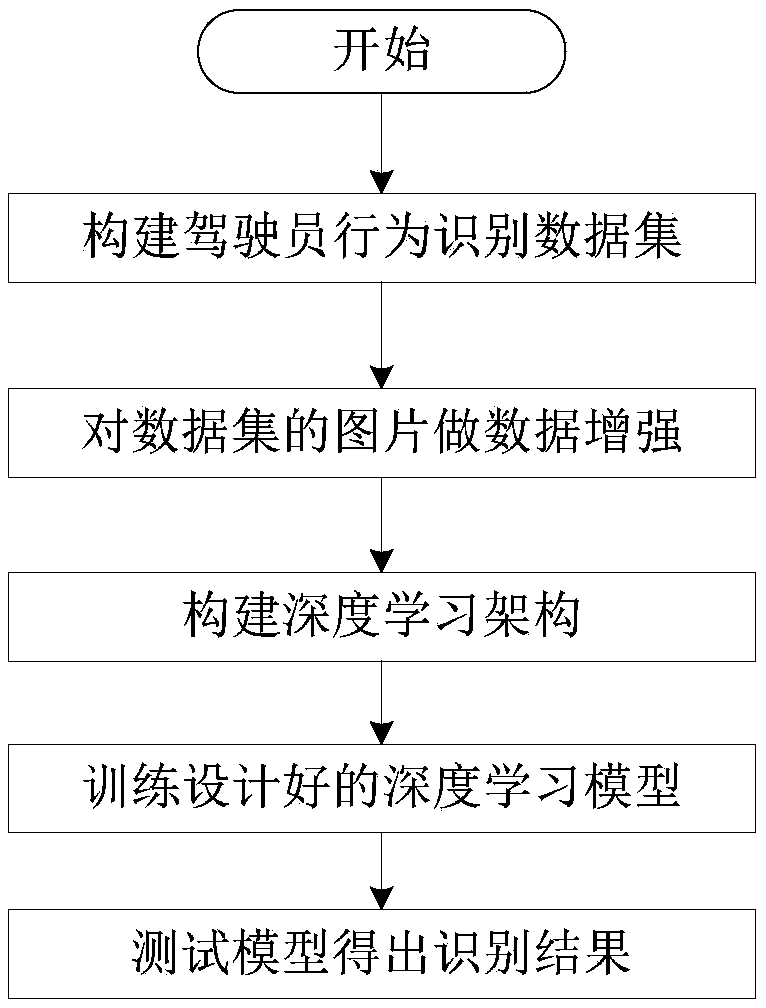
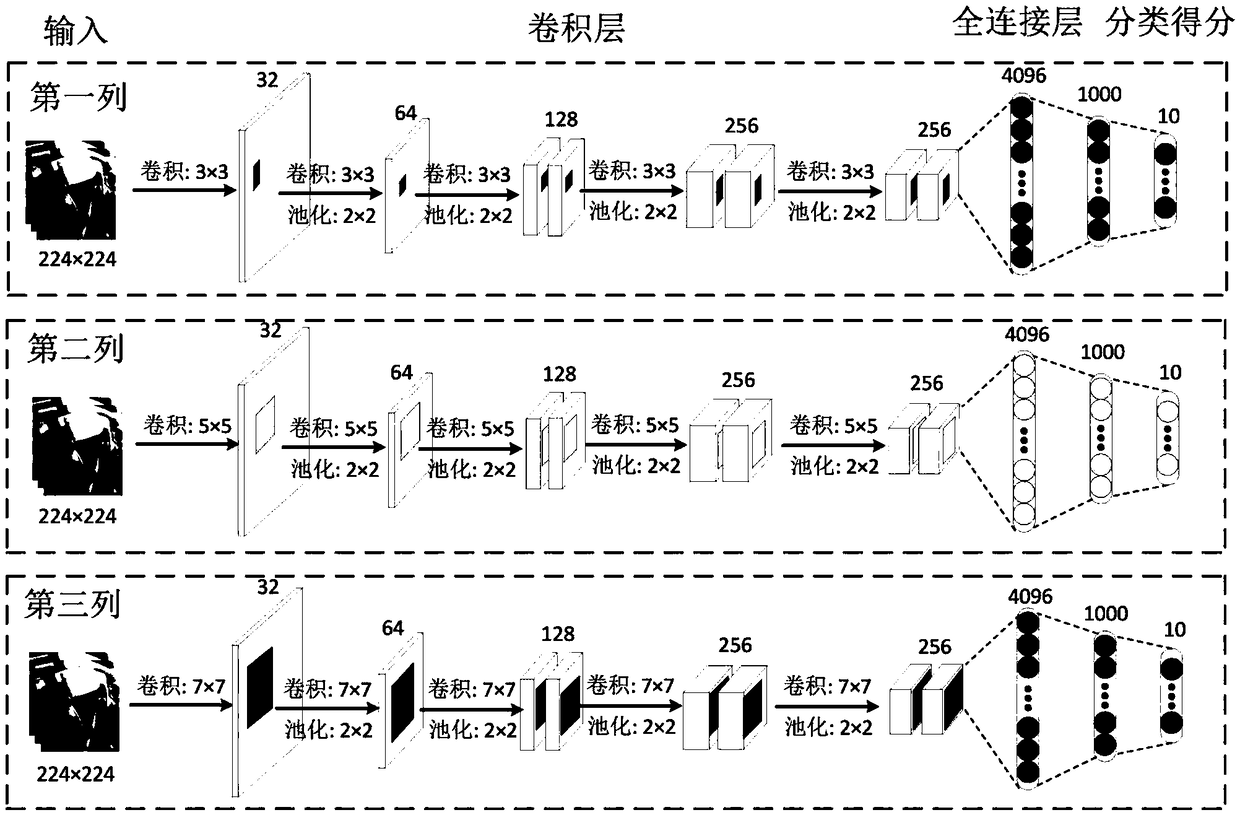
Driver behavior recognition method based on multi-column fusion convolutional neural network
ActiveCN108875674AImprove accuracyEasy extractionCharacter and pattern recognitionNeural architecturesData setLearning architecture
The invention provides a driver behavior recognition method based on a multi-column fusion convolutional neural network. The method comprises the following steps of: constructing a driver behavior recognition data set; performing data enhancement on a picture of the driver behavior recognition data set; constructing a deep learning architecture; training a designed deep learning model; and obtaining a recognition result by testing the model. The driver behavior recognition method based on the multi-column fusion convolutional neural network adopts the deep learning architecture, which is beneficial to extract more abstract hierarchical features for a driver behavior classification; and adopts the deep learning architecture of the convolutional neural network branch fusion with multiple different filter kernels, which is beneficial to extract image multi-scale features for the driver behavior classification. The multi-column fusion convolutional neural network designed in the driver behavior recognition method has more abstract local feature representation capability, can further improve the accuracy of the driver behavior recognition, and has important application value in public safety and intelligent transportation.
Owner:SOUTHEAST UNIV
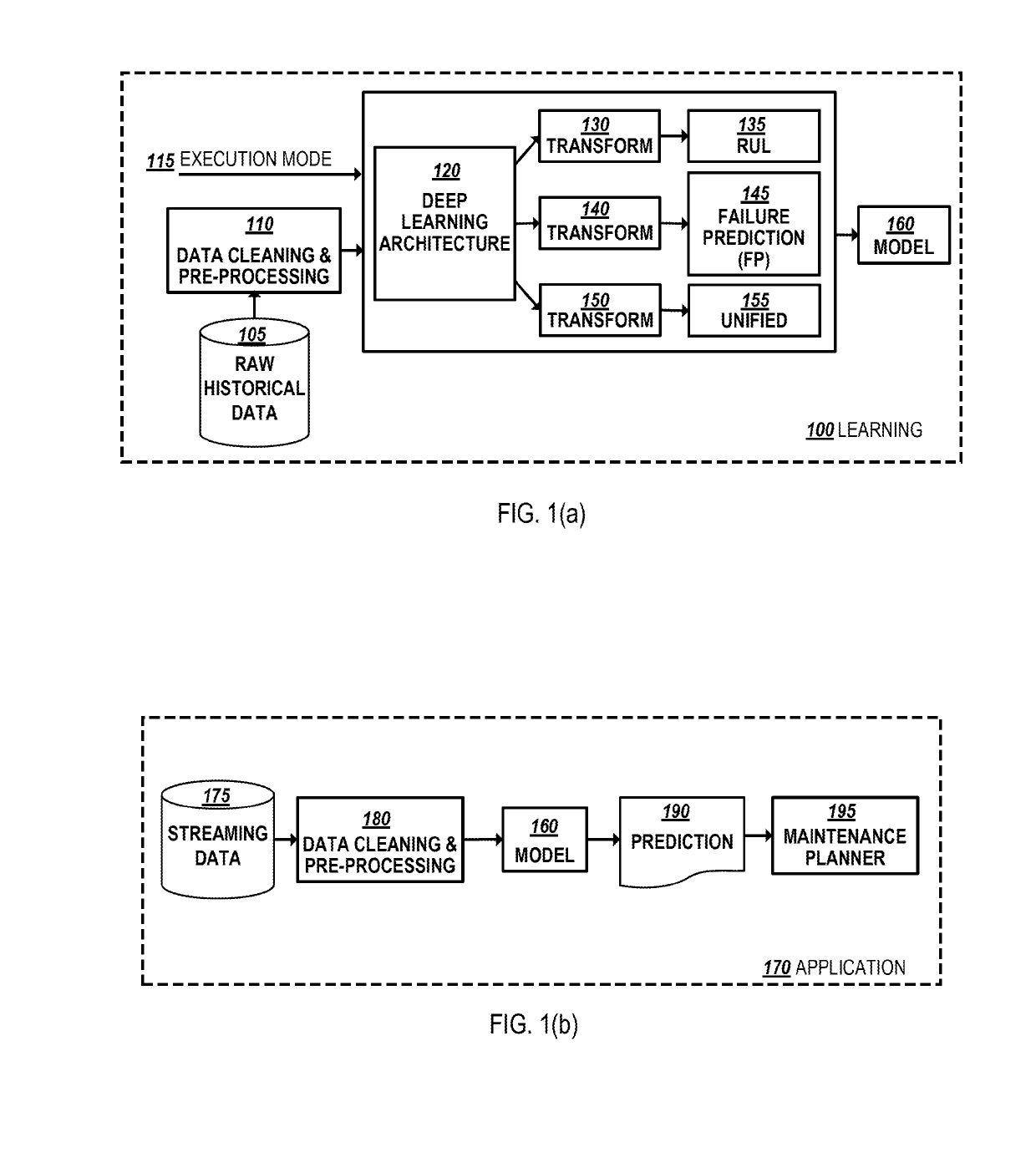
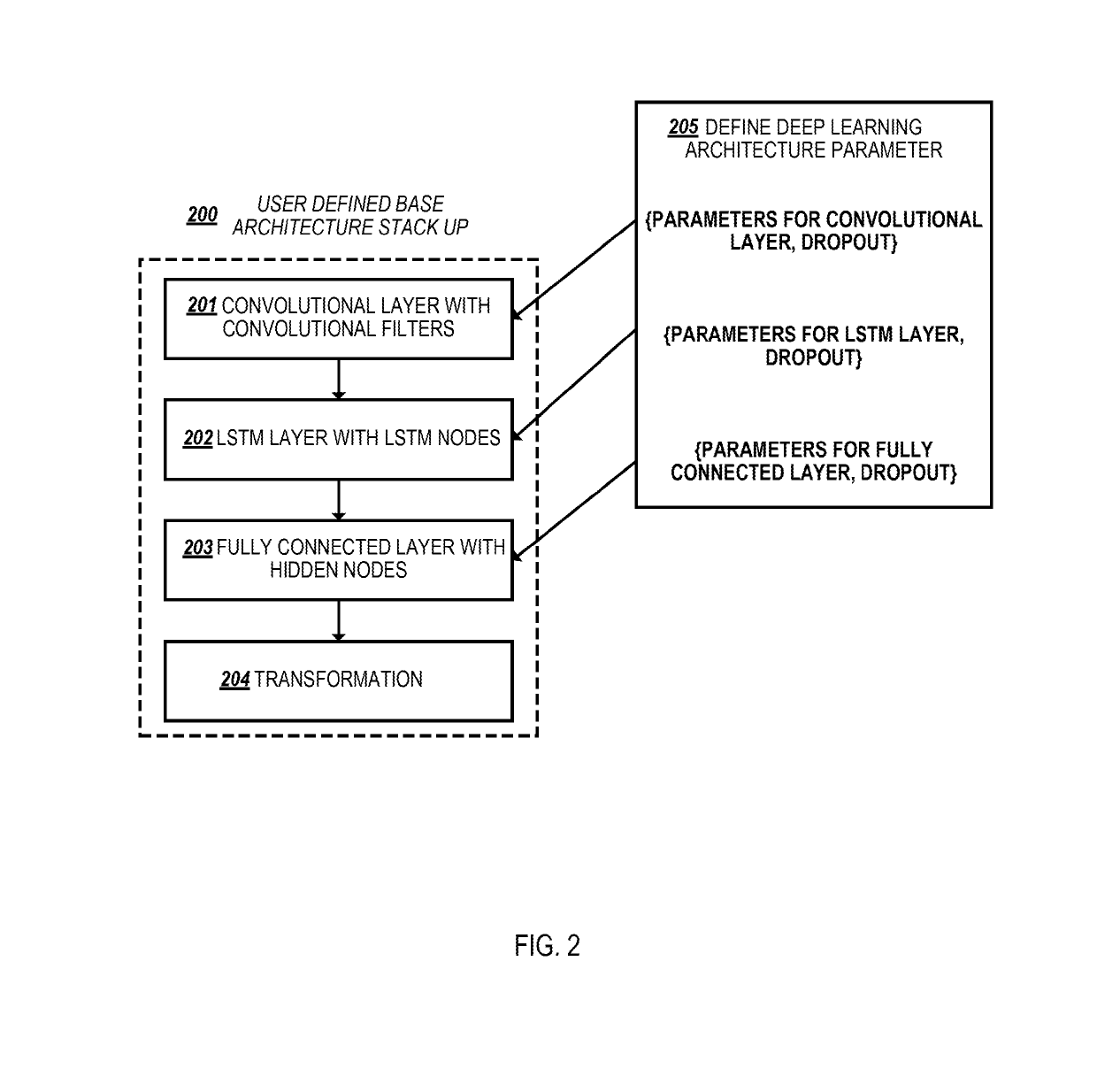
Deep learning architecture for maintenance predictions with multiple modes
ActiveUS20190235484A1Improve insightsImproved deep learning performanceDigital computer detailsElectric testing/monitoringStreaming dataMultiple modes
Example implementations described herein involve a system for maintenance predictions generated using a single deep learning architecture. The example implementations can involve managing a single deep learning architecture for three modes including a failure prediction mode, a remaining useful life (RUL) mode, and a unified mode. Each mode is associated with an objective function and a transformation function. The single deep learning architecture is applied to learn parameters for an objective function through execution of a transformation function associated with a selected mode using historical data. The learned parameters of the single deep learning architecture can be applied with streaming data from with the equipment to generate a maintenance prediction for the equipment.
Owner:HITACHI LTD
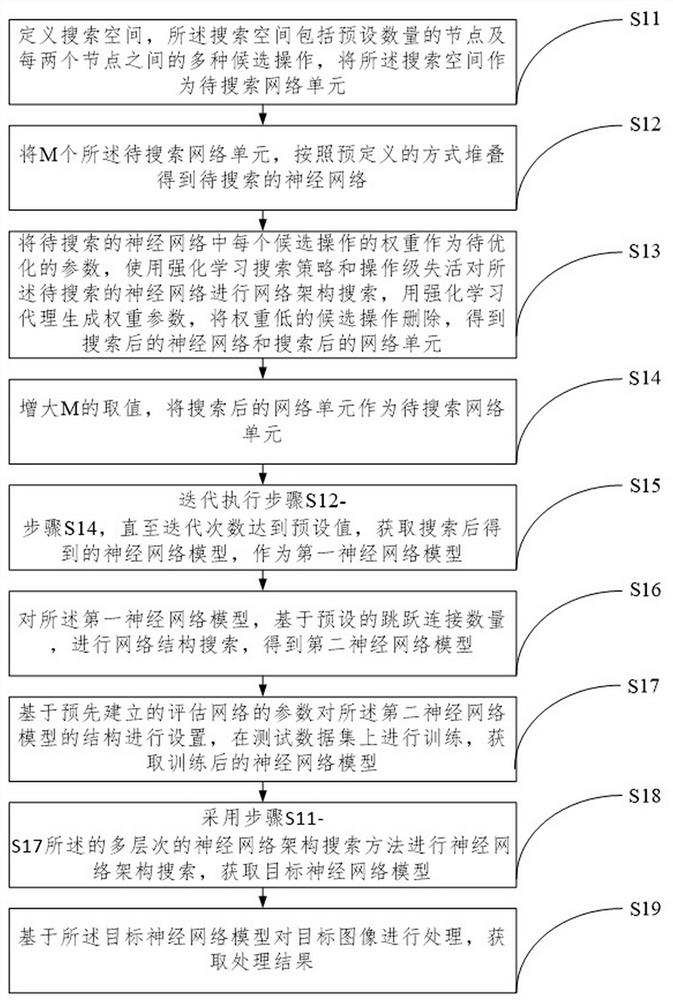
Neural network architecture search method, neural network application method, equipment and storage medium
InactiveCN111814966AFast searchSolve the problem of consuming too muchNeural architecturesNeural learning methodsData setImage manipulation
The invention belongs to the technical field of deep learning, and particularly relates to a neural network architecture search method, a neural network application method, equipment and a storage medium. The method comprises the steps of searching a first neural network model through a reinforcement learning architecture search method, and performing network structure search on the first neural network model based on a preset jump connection number to obtain a second neural network model; and setting the structure of the second neural network model based on parameters of a pre-established evaluation network, and performing training on a test data set to obtain a trained neural network model. The neural network architecture in the method is higher in search speed, and the problem that network architecture search resources are consumed too much is effectively solved. The target image is processed through the neural network model obtained through training, various image processing taskscan be executed, and the recognition precision is higher during image processing.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
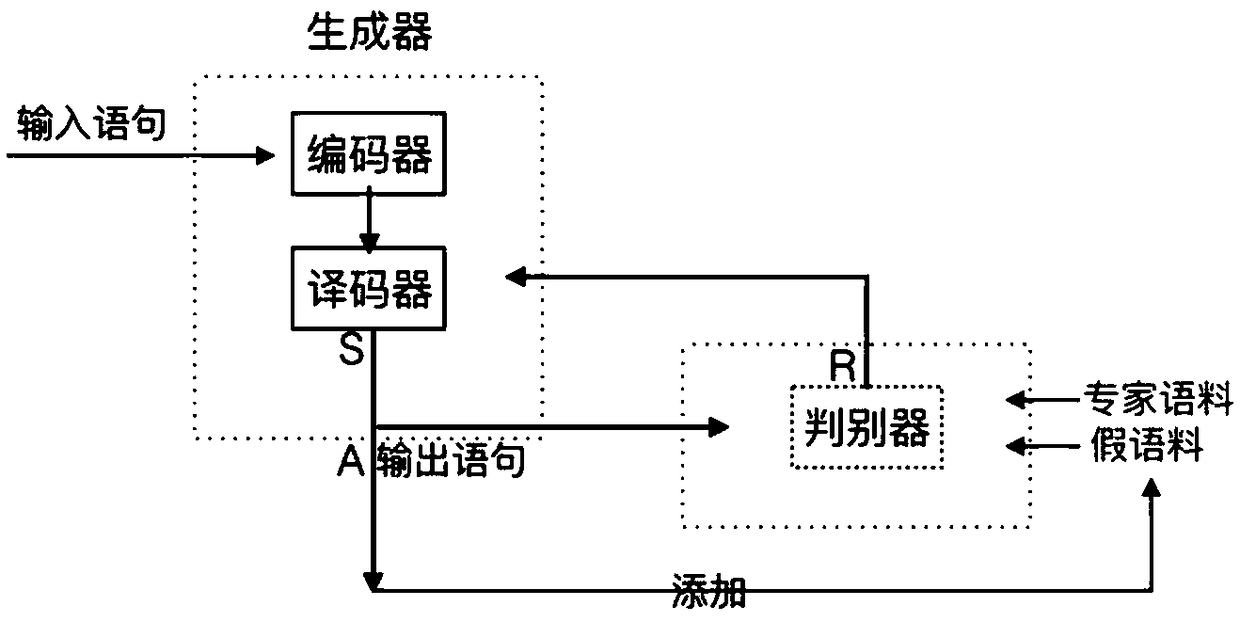
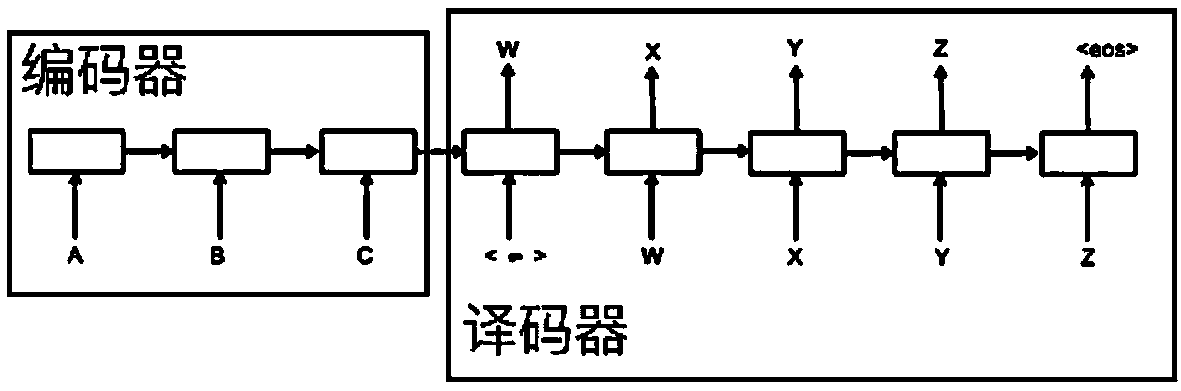
Learning by imitation dialogue generation method based on generative adversarial networks
ActiveCN108734276AIncrease diversityAvoid prone to overfitting problemsNeural architecturesNeural learning methodsDiscriminatorGenerative adversarial network
The invention relates to a learning by imitation dialogue generation method based on generative adversarial networks. The method comprises the following steps: 1) building a dialogue statement expertcorpus; 2) building the generative adversarial network, wherein a generator in the generative adversarial network comprises a pair of encoder and decoder; 3) building a false corpus; 4) performing first classification training for a discriminator; 5) inputting an input statement into the generator, and training the encoder and the decoder in the generator through a reinforcement learning architecture; 6) adding an output statement generated in the step 5) into the false corpus, and continuing training the discriminator; 7) alternatively performing training of the generator and training of thediscriminator through a training mode of the generative adversarial network, until that the generator and the discriminator both are converged. Compared with the prior art, the method provided by theinvention can generate the statements more similar as that of human and avoid emergence of too much general answers, and can promote training effects of a dialogue generation model and solve a problemof extremely high frequency of the general answers.
Owner:TONGJI UNIV
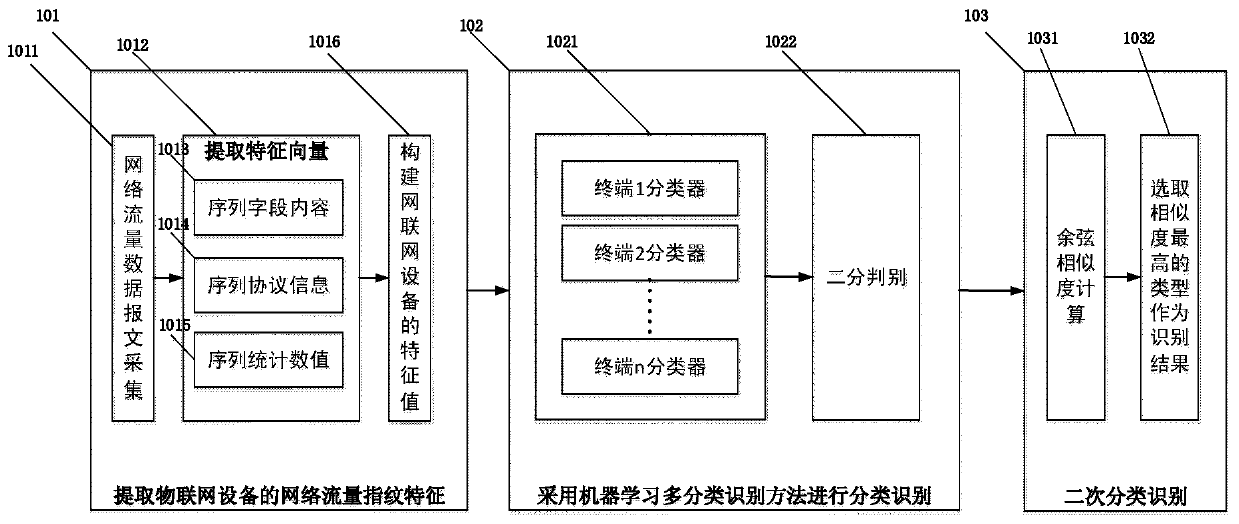
Network flow fingerprint feature two-stage multi-classification Internet of Things device identification method
ActiveCN110380989AProne to identification confusionEfficient identificationData switching networksThe InternetRecognition algorithm
The invention discloses a network flow fingerprint feature two-stage multi-classification Internet of Things device identification method, belongs to the technical field of Internet of Things device access control, and the algorithm extracts network flow features from network flow and matches and identifies accessed Internet of Things devices. The algorithm mainly comprises the following steps: firstly, acquiring N pieces of network message data when an Internet of Things device starts an access stage, and extracting features from three dimensions of sequence field contents, sequence protocolinformation and sequence statistical values to serve as device fingerprint features; using a one-to-many multi-classification machine learning architecture to perform preliminary identification on theto-be-detected Internet of Things device; and if a plurality of identification results appear in the preliminary identification, inputting the results into a maximum similarity comparison module forsecondary classification identification, and selecting the type with the highest similarity as a final identification result. According to the method, the problem that identification overlapping is easy to occur when the existing identification algorithm is used for identifying the Internet of Things device is solved, and the identification accuracy and uniqueness are improved.
Owner:SOUTHEAST UNIV
System and method for machine learning architecture for enterprise capitalization
ActiveUS20210049700A1Reduce ambiguityTechnical challenge to overcomeMathematical modelsFinanceData setDecision boundary
Systems and methods are described in relation to specific technical improvements adapted for machine learning architectures that conduct classification on numerical and / or unstructured data. In an embodiment, two neural networks are utilized in concert to generate output data sets representative of predicted future states of an entity. A second learning architecture is trained to cluster prior entities based on characteristics converted into the form of features and event occurrence such that a boundary function can be established between the clusters to form a decision boundary between decision regions. These outputs are mapped to a space defined by the boundary function, such that the mapping can be used to determine whether a future state event is likely to occur at a particular time in the future.
Owner:ROYAL BANK OF CANADA
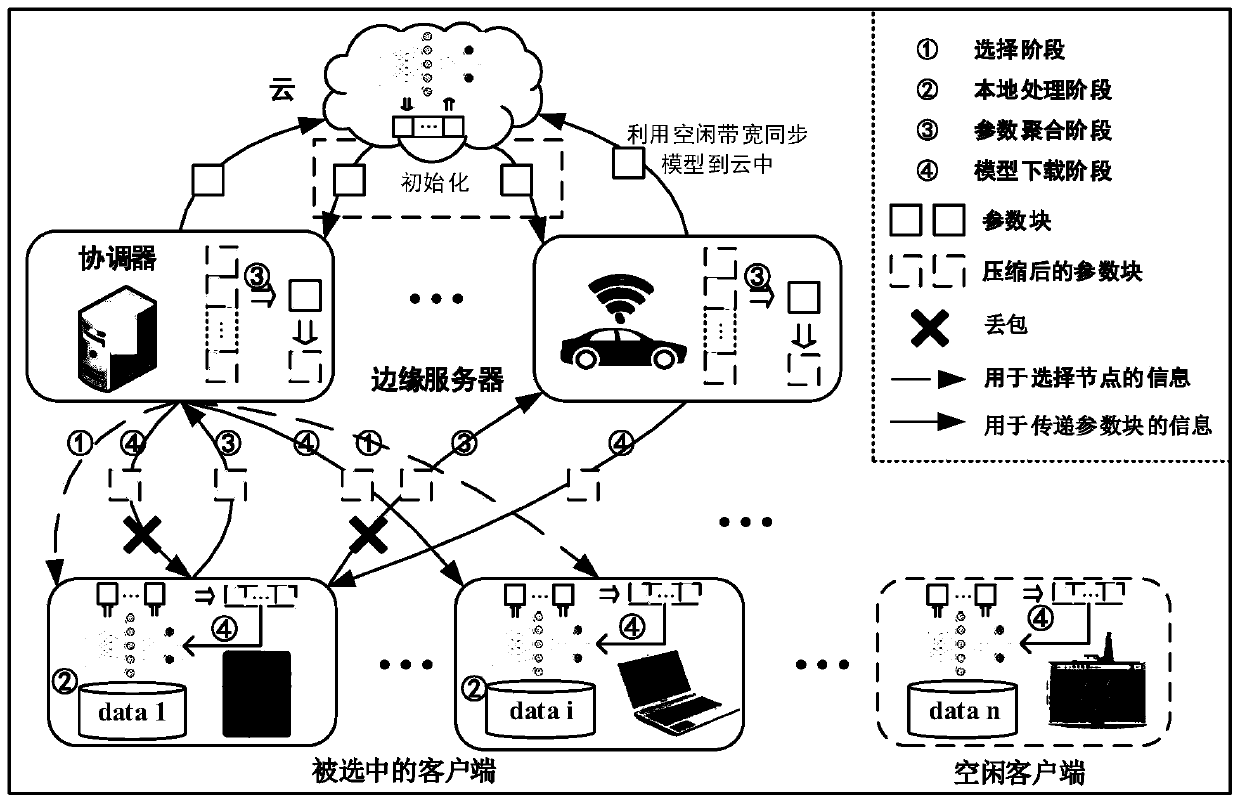
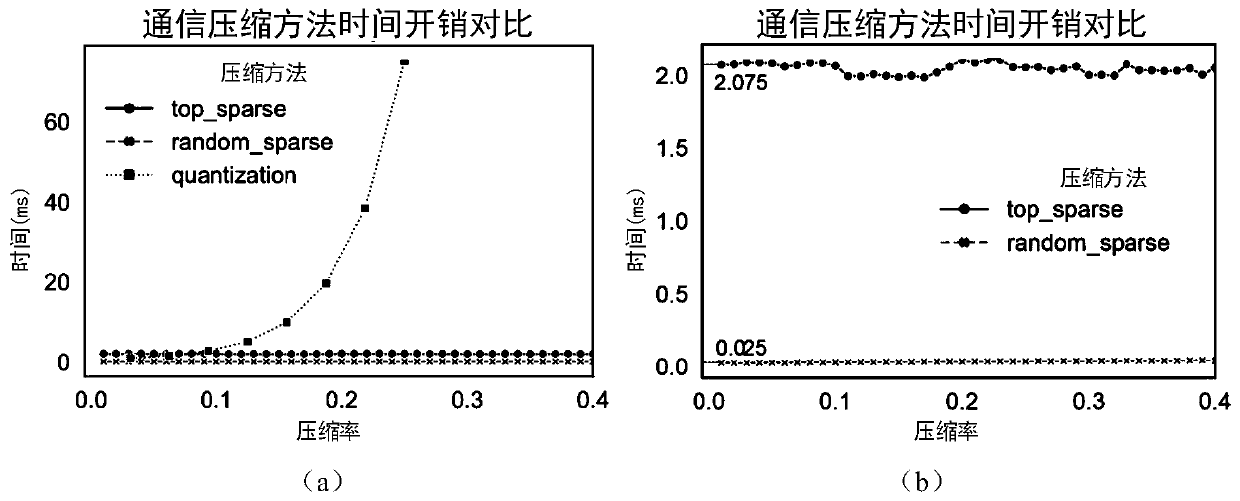
Federated learning architecture under dynamic bandwidth and unreliable network and compression algorithm of architecture
ActiveCN111447083AShorten the transmission distanceReduce communication delayMachine learningData switching networksData packPacket loss
The invention provides a federated learning architecture under a dynamic bandwidth and unreliable network and a compression algorithm of the architecture. The architecture comprises a cloud, a clientand a plurality of edge servers, the edge servers can exchange data with each other, and one of the edge servers is used as a coordinator. Data transmission between the client and the edge servers istransmission of data blocks, and an adopted edge server mechanism shortens a traditional transmission distance between the client and the cloud, and the communication delay between the client and theserver is reduced. Besides, a plurality of edge servers are introduced, and a trained model is divided into corresponding number of blocks, so that influence of data packet loss on training is reducedby avoiding losing the whole model. The compression algorithm adaptively adjusts the compression rate to adapt to the dynamic bandwidth, and the bandwidth is adaptively adjusted to replace the fixedcompression rate, so that bandwidth resources are effectively utilized, and redundant data exchange is reduced.
Owner:NAT UNIV OF DEFENSE TECH
Systems and methods for layered training in machine-learning architectures
A computer-implemented method for layered training of machine-learning architectures includes receiving a plurality of data elements wherein each data element is associated with a timestamp, determining a training window for each model layer of a layered stack of model layers, determining a plurality of training data elements for each training window by identifying the data elements with timestamps corresponding to each of the training windows, identifying a previous checkpoint for each model layer wherein the previous checkpoint for each model layer is generated by a parent model layer, training each model layer with the determined training data elements for each model layer and the identified previous checkpoint for each model layer, generating a plurality of current checkpoints wherein each current checkpoint of the plurality of current checkpoints is associated with a model layer, and storing the plurality of current checkpoints at the memory.
Owner:GOOGLE LLC
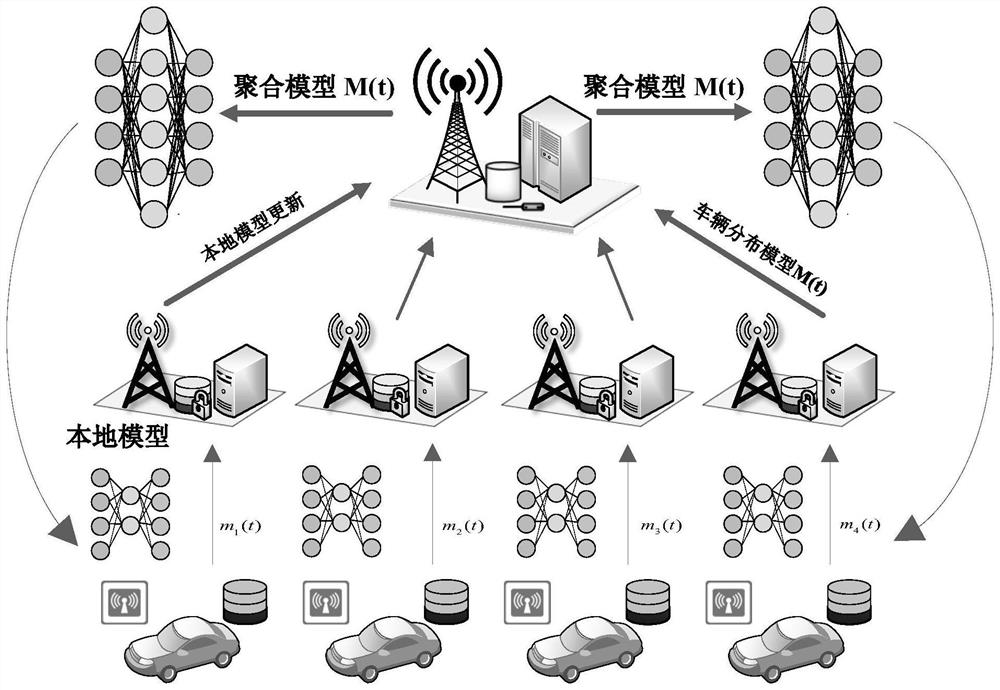
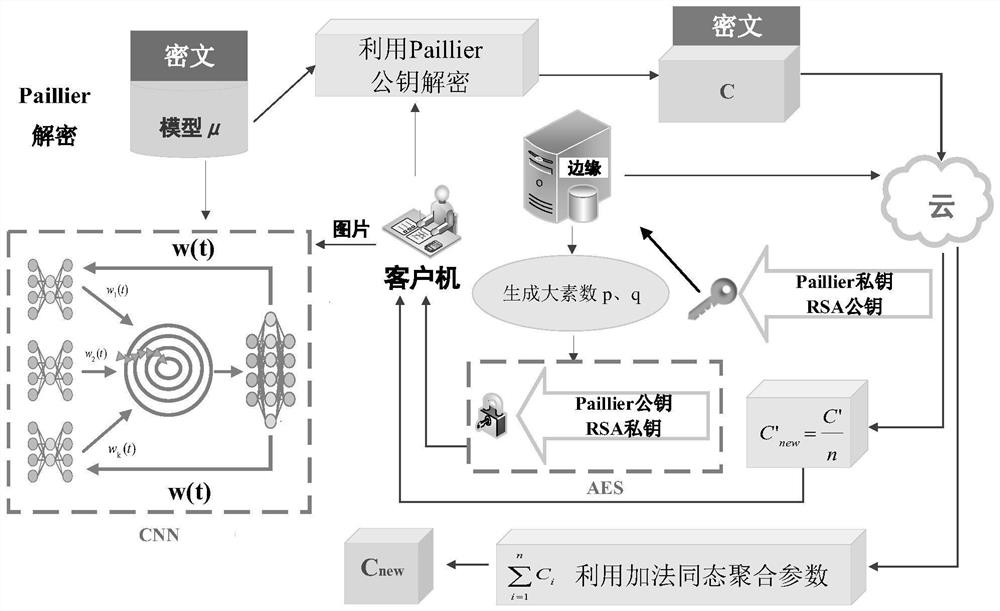
Federated learning privacy protection method based on homomorphic encryption in Internet of Vehicles
ActiveCN112583575AFully homomorphic encryptionNo need to exposeKey distribution for secure communicationEnsemble learningAlgorithmAttack
The invention provides a federated learning privacy protection method based on homomorphic encryption in the Internet of Vehicles, which introduces federated learning based on homomorphic encryption into the Internet of Vehicles, improves a Paillier algorithm with addition homomorphic lines and an RSA algorithm with multiplication homomorphism, combines an AES algorithm and a step size confusion mode, and adopts a hierarchical encryption technology at the same time. According to the method, the addition homomorphism is completed at the edge end, and the multiplication homomorphism is completedat the cloud end to improve the encryption efficiency, so that federated learning malicious attacks are effectively prevented, and the delay caused by encryption is effectively reduced. The method can be applied to privacy protection in the Internet of Vehicles to introduce federated learning into the IoV so as to solve the problem of user privacy leakage. In order to further enhance the data safety, efficient homomorphic encryption is introduced into federated learning; moreover, a Paillier algorithm with addition homogeneity and an RSA algorithm with multiplication homogeneity are improved,and a federated learning architecture with full homomorphic encryption is constructed in combination with an AES algorithm and a step length confusion mode.
Owner:HUAQIAO UNIVERSITY +1
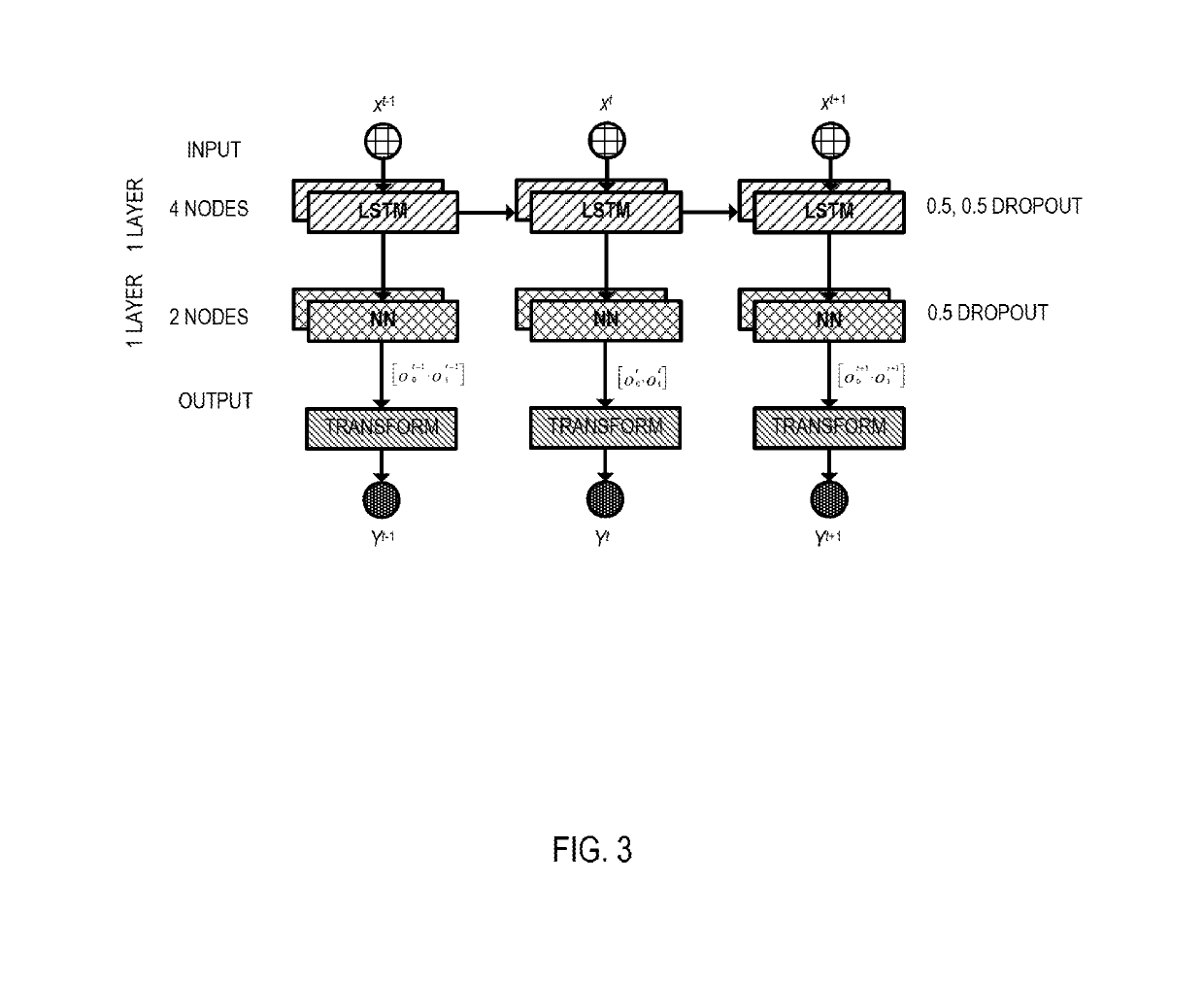
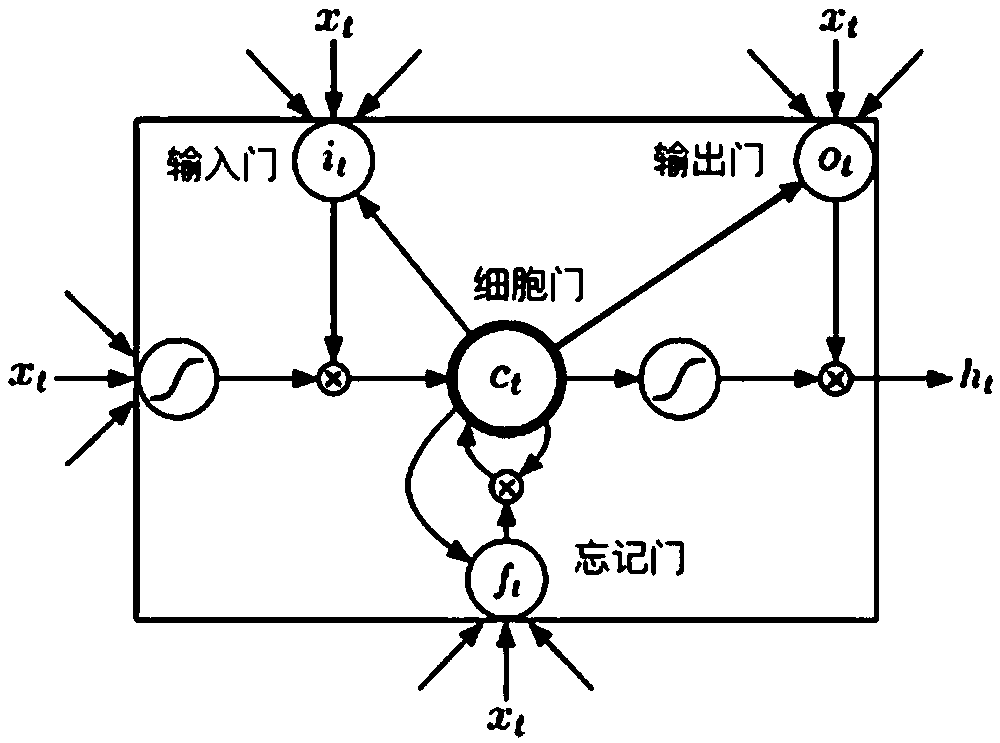
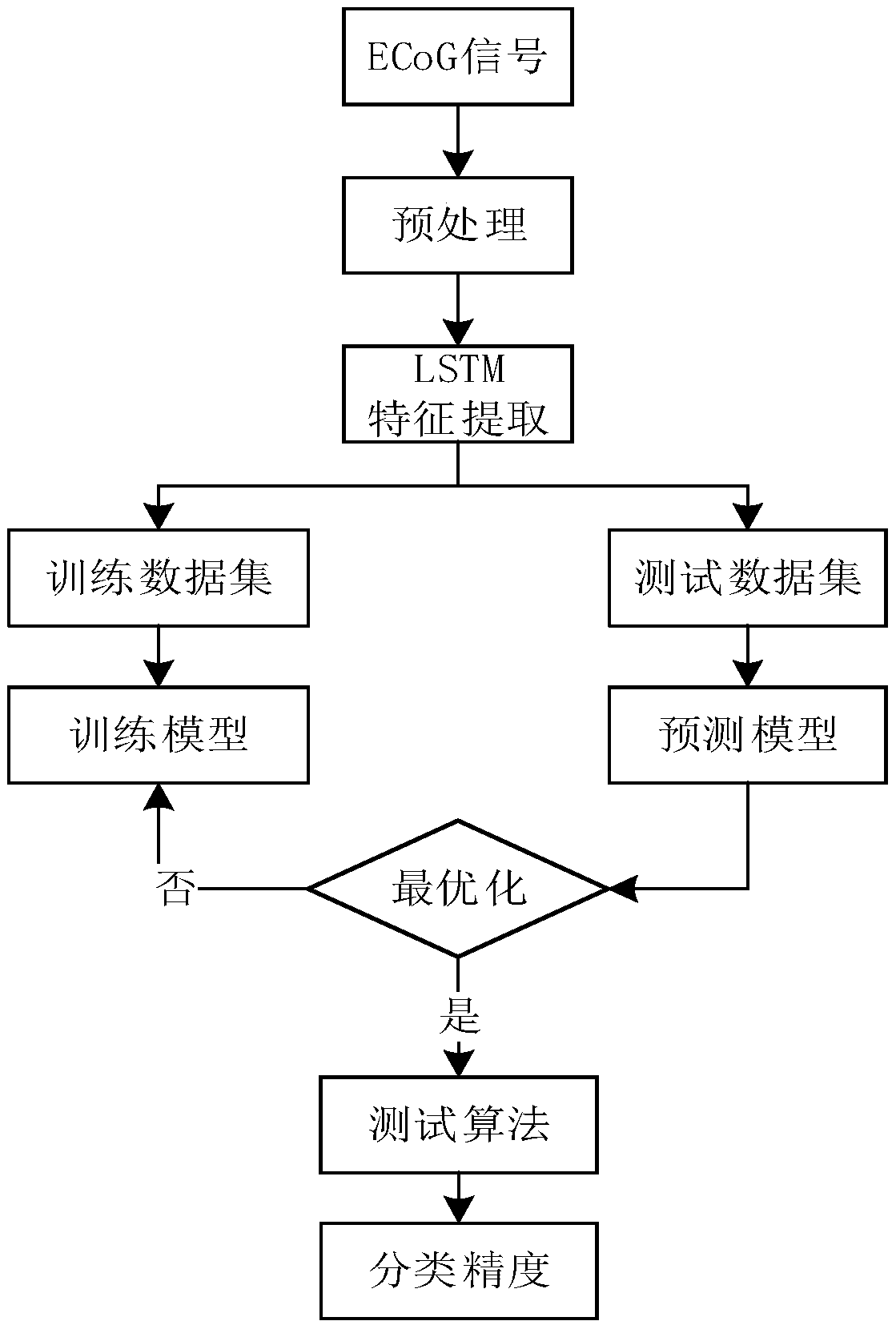
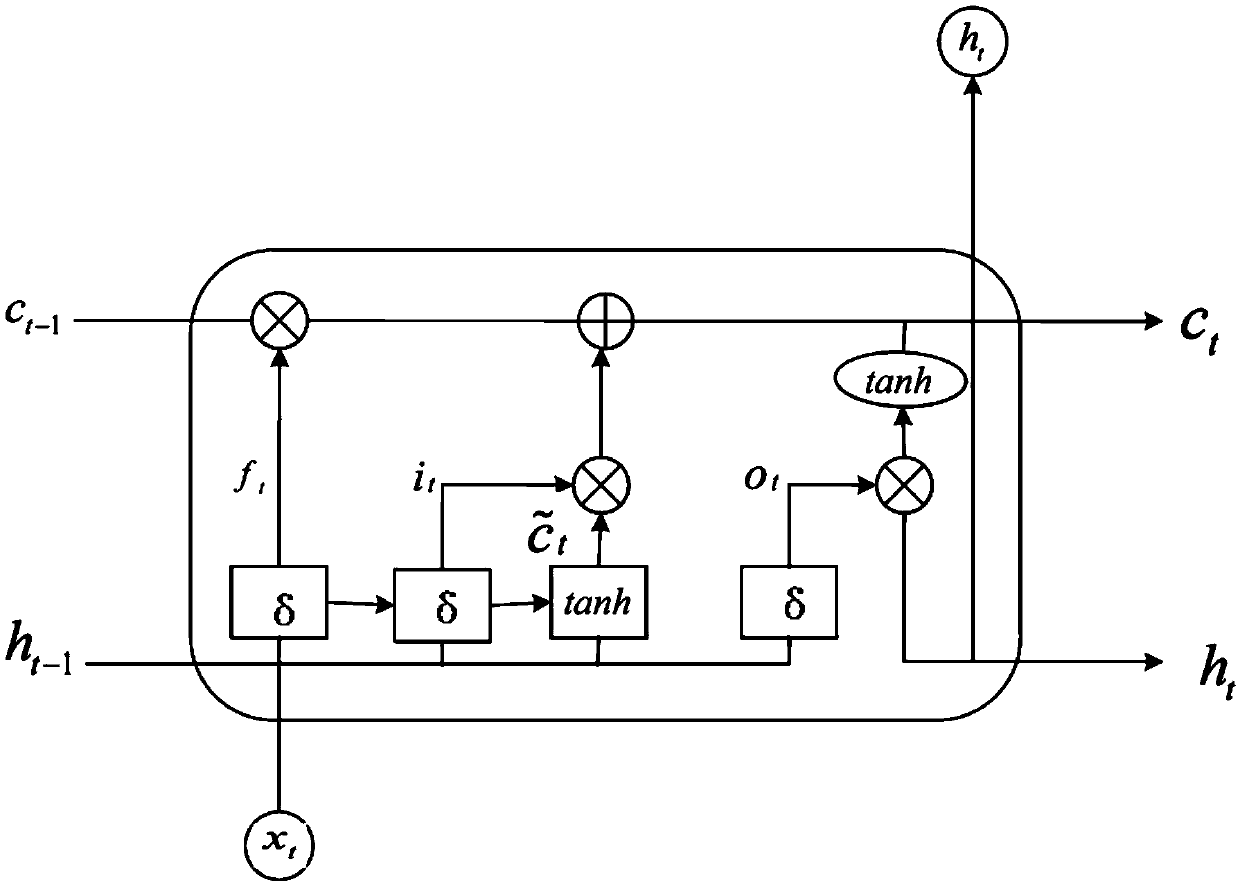
The invention discloses an LSTM-based electroencephalogram signal rapid classification and identification method
PendingCN109614885AImprove accuracyReduce complexityCharacter and pattern recognitionNeural architecturesNetwork structureOpen source
The invention relates to an LSTM (Long Short Term Memory)-based electroencephalogram signal rapid classification and identificationrecognition method, which is characterized by comprising the following steps of: S1, acquiring and preprocessing electroencephalogram signals; S; s2, defining an LSTM network structure, and constructing a network model by using open-source deep learning architecture TensorFlow; S; s3, comparing the real label with the predicted label, calculating loss by utilizing a cross entropy loss function, and selecting an optimal optimization function to optimize the network,so as to improve the training accuracy; and S4, predicting labels of the test set by using the trained model, comparing the labels with real labels, and evaluating the model.
Owner:QILU UNIV OF TECH
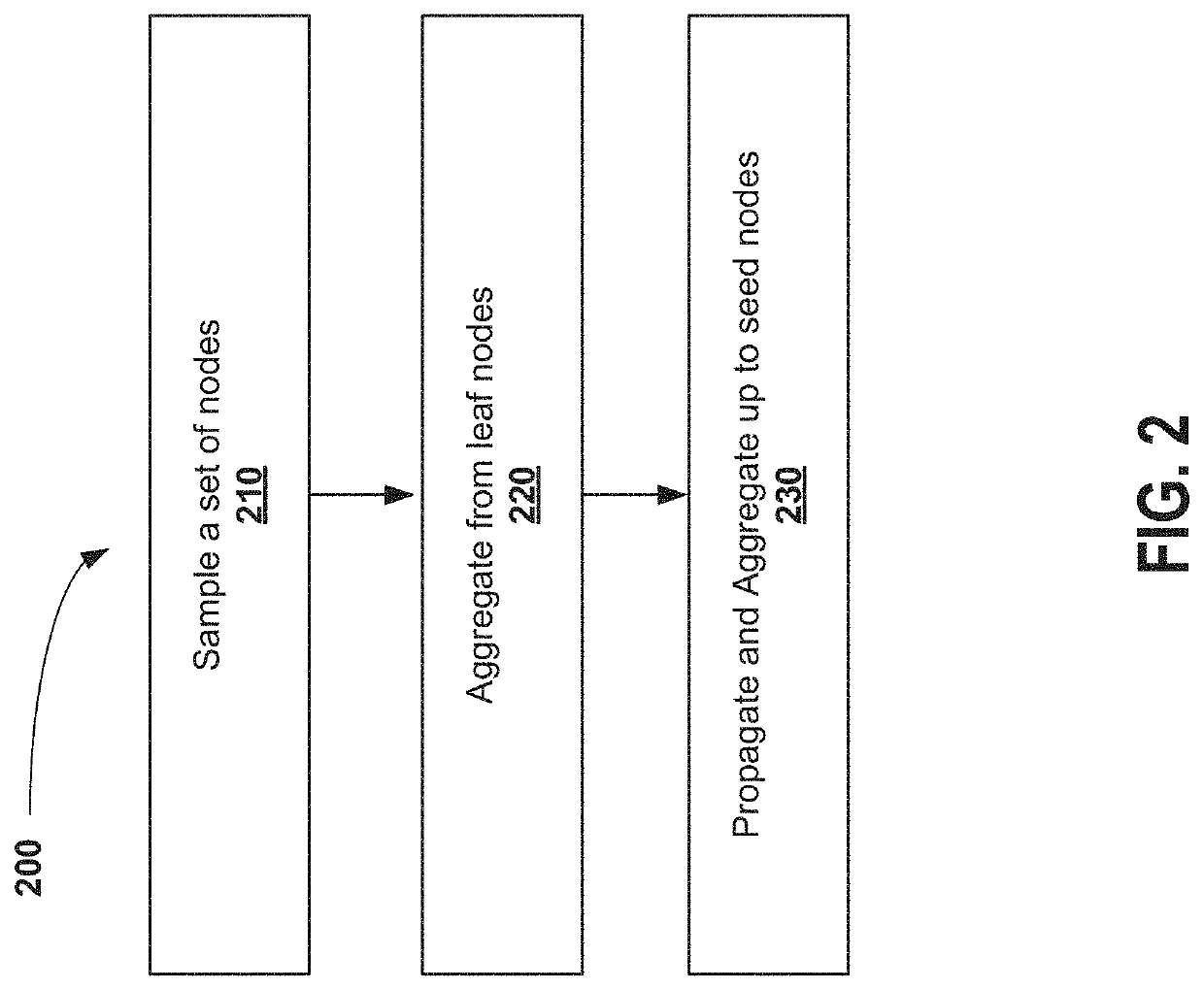
System and method for machine learning architecture with privacy-preserving node embeddings
ActiveUS20200356858A1Improve securityEnhance differential privacyOther databases indexingNeural architecturesEngineeringPrivacy preserving
A computer system and method for machine inductive learning on a graph is provided. In the inductive learning computational approach, an iterative approach is used for sampling a set of seed nodes and then considering their k-degree (hop) neighbors for aggregation and propagation. The approach is adapted to enhance privacy of edge weights by adding noise during a forward pass and a backward pass step of an inductive learning computational approach. Accordingly, it becomes more technically difficult for a malicious user to attempt to reverse engineer the edge weight information. Applicants were able to experimentally validate that acceptable privacy costs could be achieved in various embodiments described herein.
Owner:ROYAL BANK OF CANADA
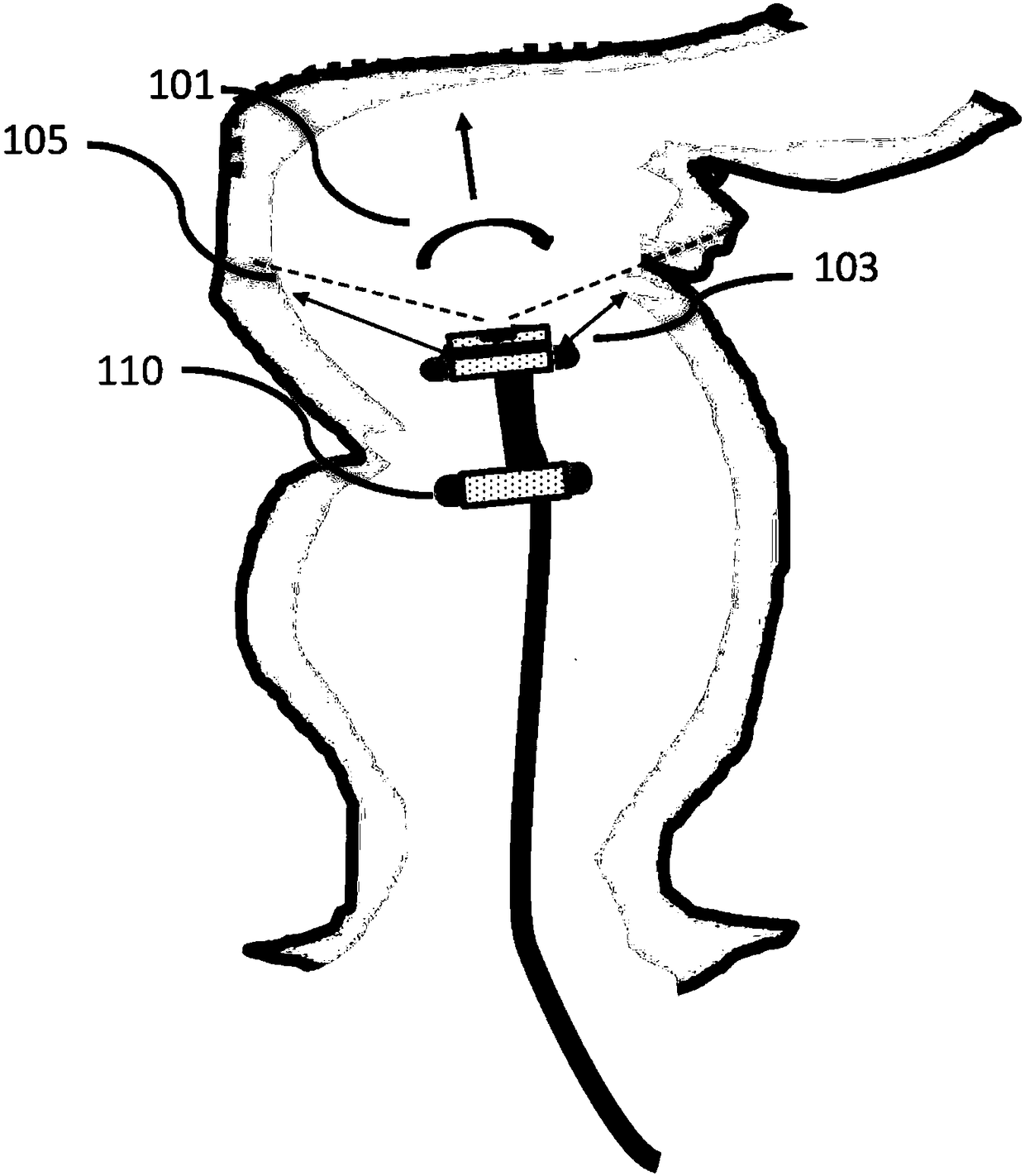
Automated steering systems and methods for a robotic endoscope
Systems and methods for automated steering control of a robotic endoscope, e.g., a colonoscope, are provided. The control system may comprise: a) a first image sensor configured to capture a first input data stream comprising a series of two or more images of a lumen; and b) one or more processors that are individually or collectively configured to generate a steering control output signal based on an analysis of data derived from the first input data stream using a machine learning architecture, wherein the steering control output signal adapts to changes in the data of the first input data stream in real time.
Owner:BIO MEDICAL ENG (HK) LTD
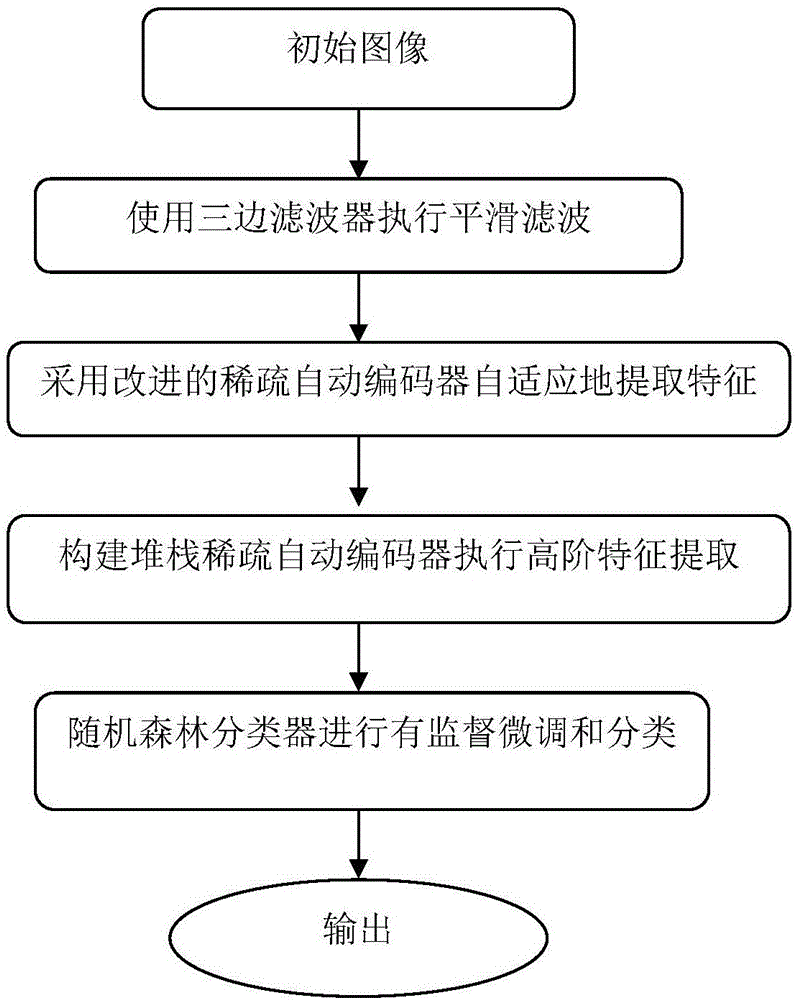
Image classification method based on three-side filter and stacked sparse autocoder
ActiveCN106503734AImprove stabilityThe result is accurateScene recognitionArtificial lifeHyperspectral data classificationClassification methods
The invention provides an image classification method based on a three-side filter and a stacked sparse autocoder. The method comprises: a smooth image is obtained by using a three-side filter, and Gaussian, speckle, pulse noises of a degraded image are filtered while a spectral-spatial feature of a pixel of the image is extracted; high-order feature extraction is carried out by using an improved stacked sparse autocoder; and supervised network fine tuning and classification are carried out by using a random forest classifier. According to the method provided by the invention, the improved stacked sparse autocoder and the random forest classifier are introduced into the hyperspectral data classification to form depth learning architecture; the improved stacked sparse autocoder can extract abstract and useful underlying features of spectroscopic data layer by layer, thereby improving the classification performance of the spectroscopic data. The method is not only suitable for hyperspectral image classification but also suitable for other image classification and has high transportability; and the image classification demand can be satisfied easily.
Owner:HARBIN ENG UNIV
Cleaning robot optimal target path planning method based on model learning
ActiveCN105740644AImprove learning efficiencyExplore completelySpecial data processing applicationsInformaticsSimulationPlanning approach
The invention discloses a cleaning robot optimal target path planning method based on model learning to solve the problem that cleaning robots in the current market are not high in efficiency.A Dyna algorithm based on self-simulation measurement and R-MAX is put forward based on a Dyna-H algorithm, and by means of the route planning method, a robot can be driven to preferentially treat places where rubbish is possibly maximal; an exploration mechanism in an R-MAX algorithm is used based on an intensive learning architecture and the Dyna-H algorithm; on the basis of a state distance measurement method, a Euclidean distance measurement method in Dyna-H is improved through self-simulation measurement, and therefore the learning efficiency of a model is improved.The cleaning robot optimal target path planning method has the advantages that the model learning efficiency is high, the method is suitable for a definite environment and a random environment, the robot can quickly and efficiently obtain an accurate environment model in the complex environment, and an optimal path of the places with maximal rubbish can be planned.
Owner:海博(苏州)机器人科技有限公司
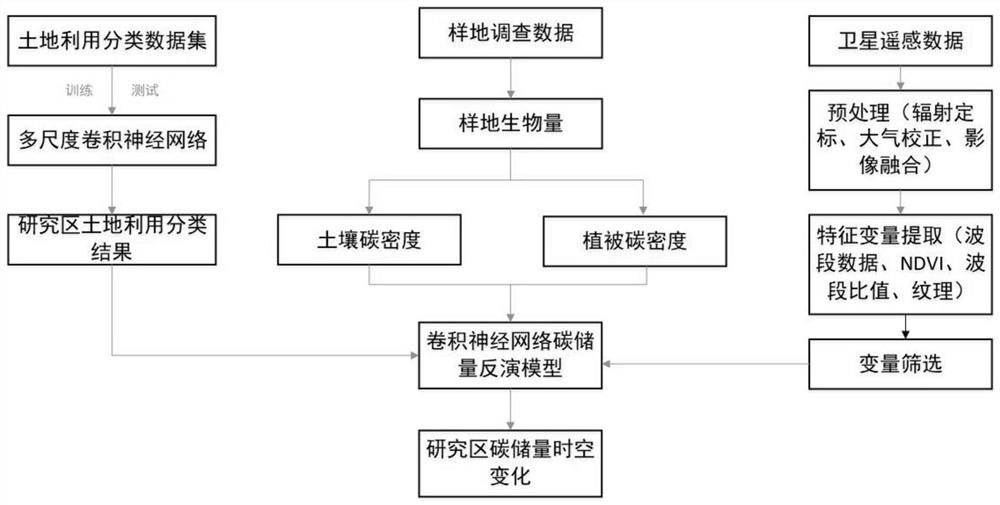
Land utilization change and carbon reserve quantitative estimation method based on remote sensing data
ActiveCN112836610AFitting Nonlinear RelationshipsFit closelyScene recognitionNeural architecturesAlgorithmNetwork output
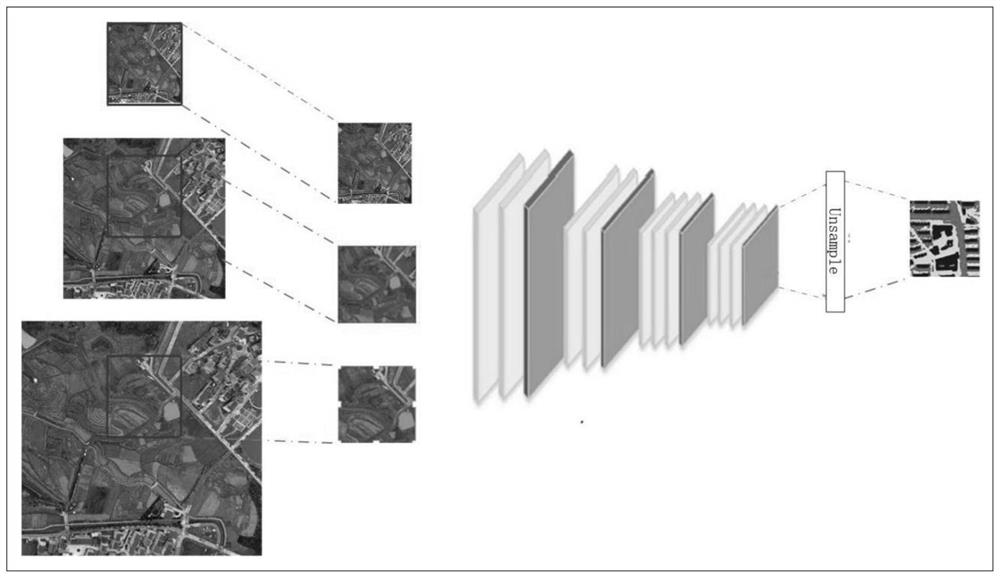
The invention discloses a land utilization change and carbon reserve quantitative estimation method based on remote sensing data. The method comprises the following steps: downloading an image; preprocessing the image; using and classifying land; calculating ground object carbon density according to ground survey data; making correlation analysis on the carbon reserves in the sample plots and the characteristic values, and selecting the characteristic values with significant correlation for modeling; and normalizing the screened characteristic values as an input layer of the convolutional neural network, putting the calculated carbon density of each sample plot into a network output layer, carrying out network training, and carrying out carbon reserve quantitative estimation on a to-be-studied region by utilizing a trained model. The invention is based on a hierarchical learning architecture of the multi-scale convolutional neural network, so that a land utilization classification result is better. On the basis of different feature values in the image and the carbon density obtained from ground survey data, the nonlinear relation between the feature variables and the carbon reserves is better fitted, and the final quantitative estimation result of the regional carbon reserves is improved.
Owner:平衡机器科技(深圳)有限公司
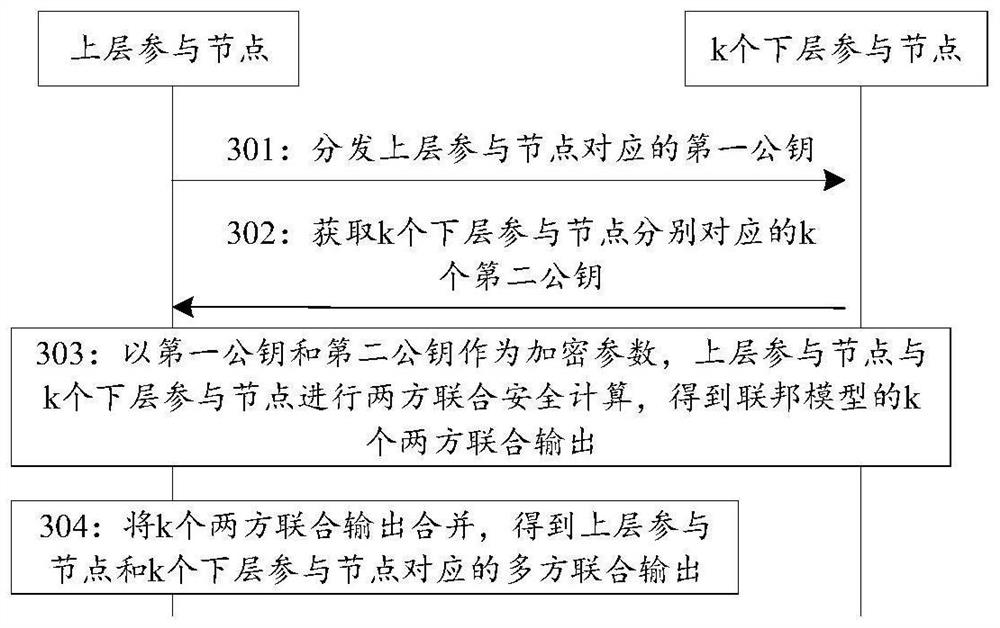
Longitudinal federation learning calculation method and device, equipment and medium
PendingCN112132293AImprove equalityMultiple keys/algorithms usageEnsemble learningAlgorithmLearning architecture
The invention discloses a longitudinal federation learning calculation method and device, equipment and a medium, and relates to the field of federation learning in artificial intelligence. Accordingto the application, a plurality of participation nodes are deployed by adopting a multi-way tree topology, one upper-layer participation node is provided with k lower-layer participation nodes, and the upper-layer participation node and the k lower-layer participation nodes exchange public keys of two parties, the upper-layer participation node and the lower-layer participation node perform two-party joint security calculation by taking the first public key and the second public key as encryption parameters to obtain k two-party joint outputs of the federation model; and the k two-party jointoutputs are combined by the upper-layer participation node to obtain a first joint model output corresponding to the federation model. Therefore, a longitudinal federated learning architecture of multi-way tree topology deployment is provided, and the equivalence of each participating node in the longitudinal federated learning process is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
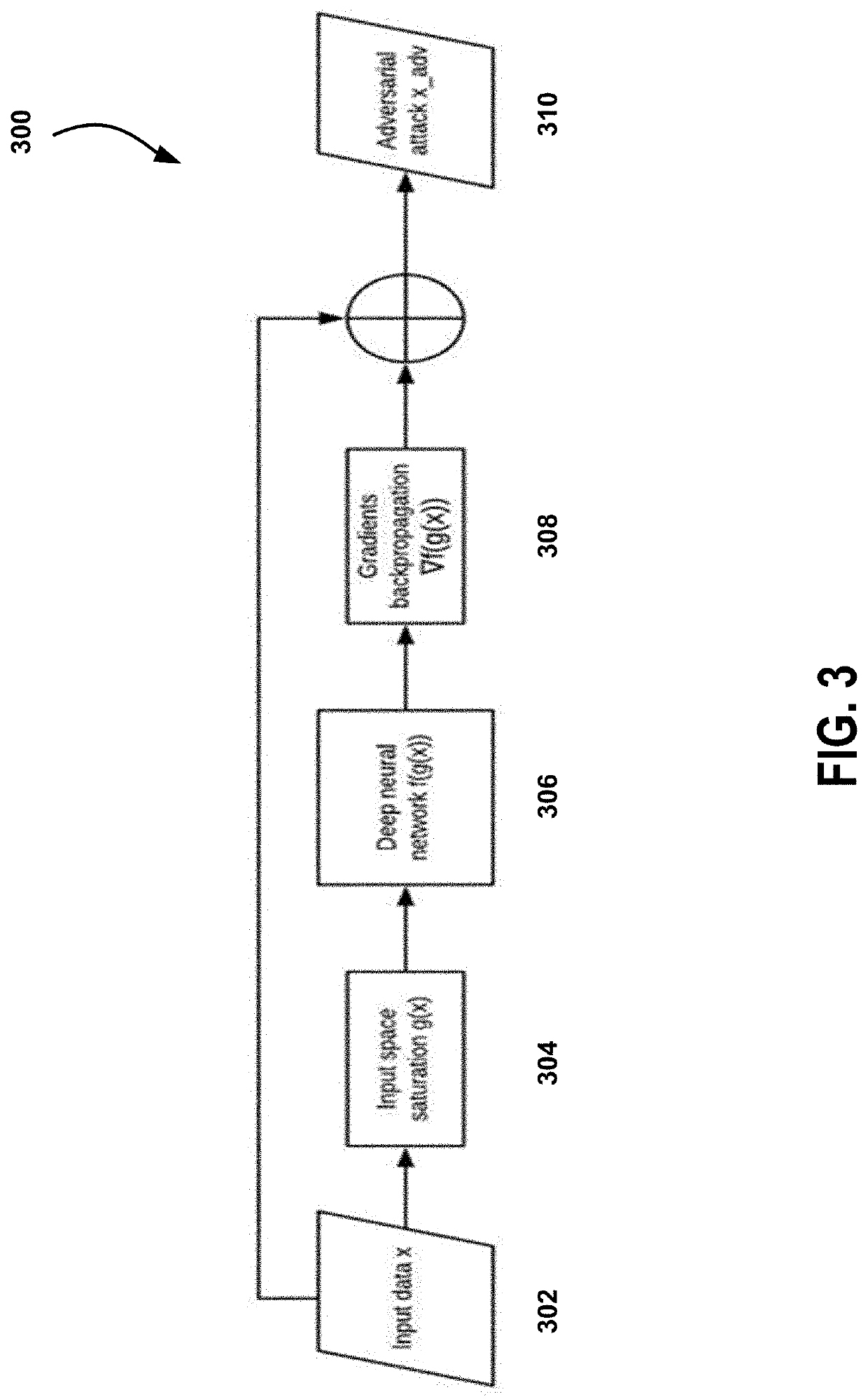
System and method for machine learning architecture with adversarial attack defence
ActiveUS20190354688A1Fuzzy logic based systemsPlatform integrity maintainanceLearning architectureMachine learning
A platform for training deep neural networks using push-to-corner preprocessing and adversarial training. A training engine adds a preprocessing layer before the input data is fed into a deep neural network at the input layer, for pushing the input data further to the corner of its domain.
Owner:ROYAL BANK OF CANADA
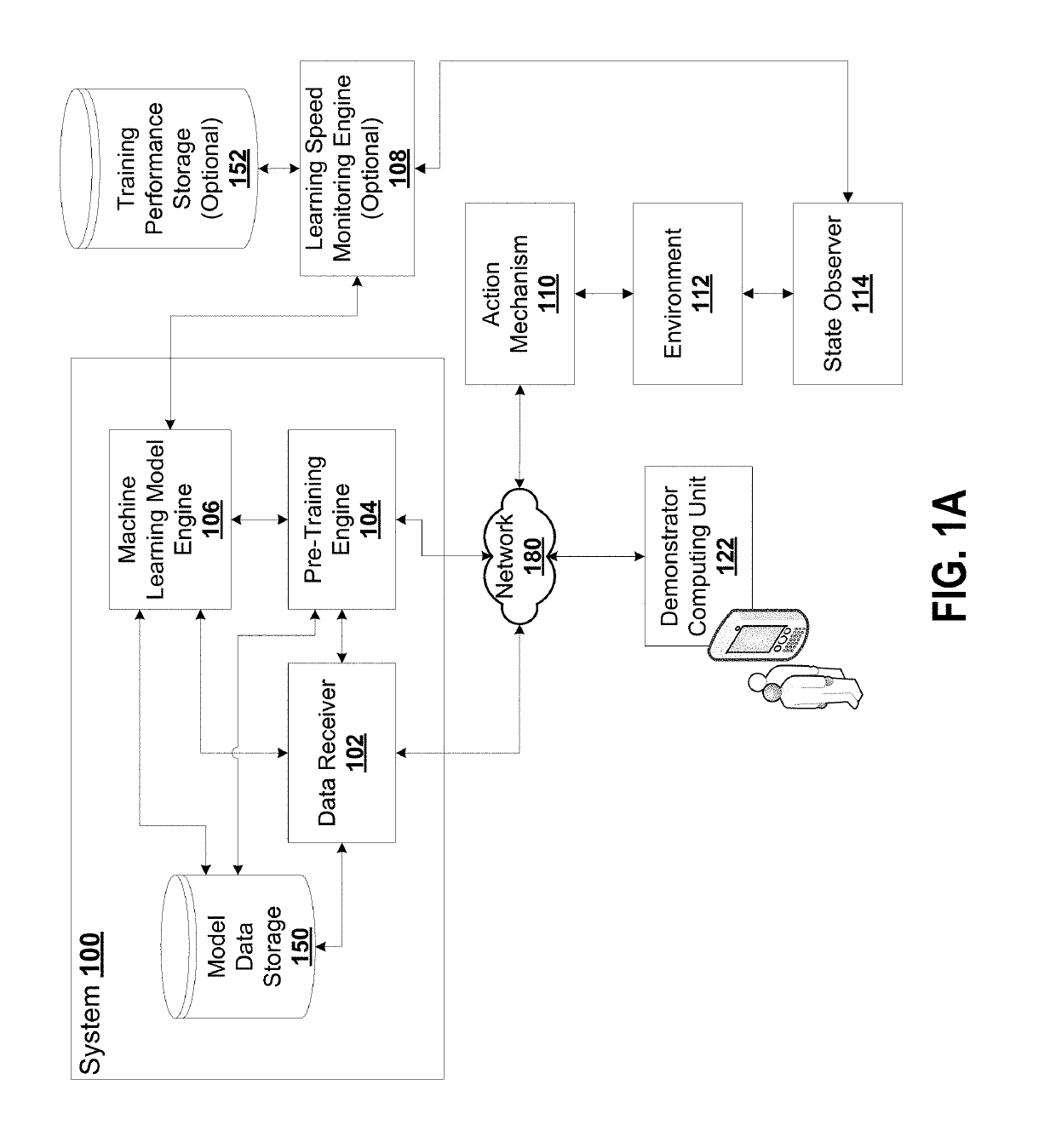
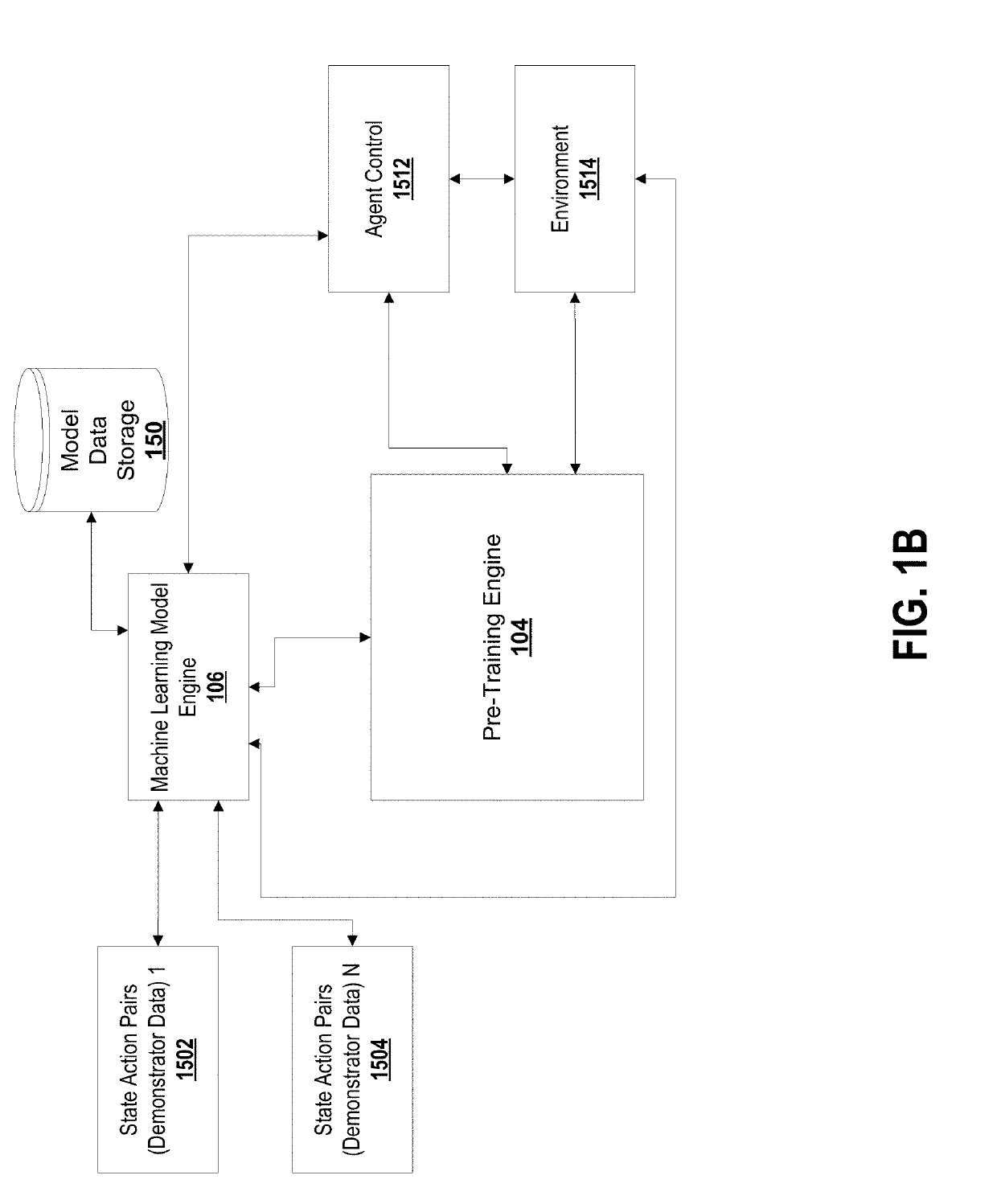
Pre-training neural networks with human demonstrations for deep reinforcement learning
PendingUS20190236455A1Minimize loss functionMathematical modelsCharacter and pattern recognitionData setEngineering
Disclosed herein are a system and method for providing a machine learning architecture based on monitored demonstrations. The system may include: a non-transitory computer-readable memory storage; at least one processor configured for dynamically training a machine learning architecture for performing one or more sequential tasks, the at least one processor configured to provide: a data receiver for receiving one or more demonstrator data sets, each demonstrator data set including a data structure representing the one or more state-action pairs; a neural network of the machine learning architecture, the neural network including a group of nodes in one or more layers; and a pre-training engine configured for processing the one or more demonstrator data sets to extract one or more features, the extracted one or more features used to pre-train the neural network based on the one or more state-action pairs observed in one or more interactions with the environment.
Owner:ROYAL BANK OF CANADA
System and method for automatic selection of deep learning architecture
A system and method of determining a neural network configuration may include receiving at least one neural network configuration, altering the received configuration for at least two iterations, calculating a first parameter of an altered configuration, calculating a second parameter of a consecutive altered configuration of the at least two iterations, comparing values of the calculated first parameter and second parameter, and determining a configuration having largest value of the calculated parameters.
Owner:VIDEO INFORM
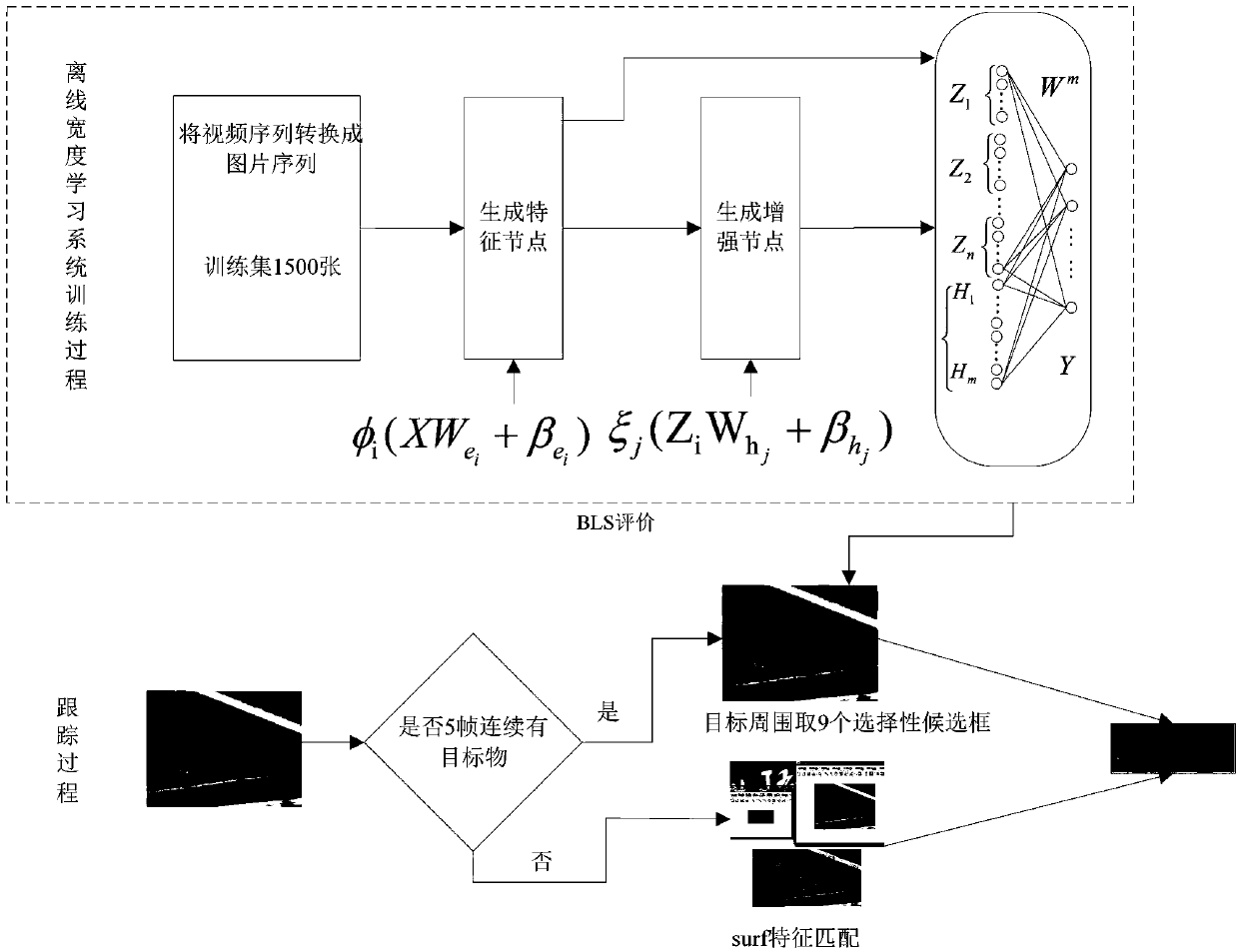
Width learning-based long-term target tracking algorithm
ActiveCN108921877AShallowLow computing resource requirementsImage enhancementImage analysisPattern recognitionLearning based
The invention discloses a width learning-based long-term target tracking algorithm. The algorithm comprises the following steps of: establishing a width learning system; and carrying out tracking on the basis of the width learning system and establishing an acceleration steady feature algorithm-based whole-image detection mechanism. According to the algorithm, width learning system-based long-termtarget tracking is carried out, width learning architecture is relatively shallow in layer and relatively low requirement is put forward for calculation resources, so that deployment can be carried out on low-end equipment without losing great precision. According to the algorithm, an obtained target tracking model is high in training speed, small in reconstruction cost and low in time cost, andhas great superiority for detection of deformation, rotation and shielding in target tracking process. According to the algorithm, the SURF algorithm-based whole-image detection mechanism is applied,so that target information can be rapidly obtained when targets re-appear under the condition that the width learning system judges that the targets are lost, and the target positions can be updated so as to ensure that the tracking effect is more stable, robust and reliable.
Owner:DALIAN MARITIME UNIVERSITY +1
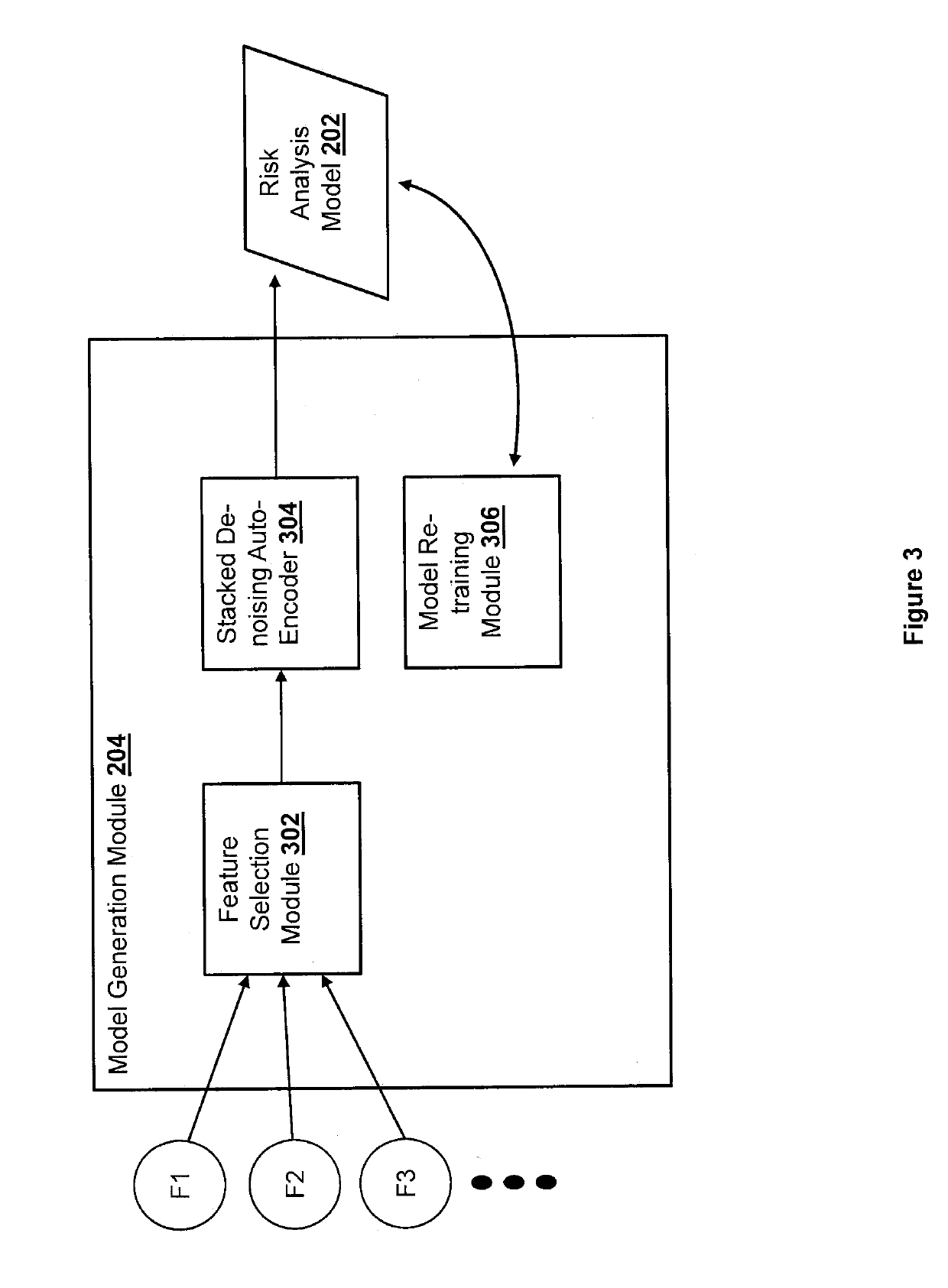
Generic learning architecture for robust temporal and domain-based transfer learning
Methods and systems for generating a targeted risk analysis model by using a knowledge transfer technique to enhance a generic risk analysis model are presented herein. The knowledge transfer may be temporal-based or domain-based. A first generic risk analysis model is generated to produce an outcome based on a set of input data related to a first set of features. The first generic risk analysis model is trained using a first set of training data having first characteristics. Based on a type of knowledge transfer requested, a second set of training data having second characteristics is obtained. The first generic risk analysis model is enhanced to produce a second targeted risk analysis model by retraining the first generic risk analysis model using the second set of training data.
Owner:PAYPAL INC
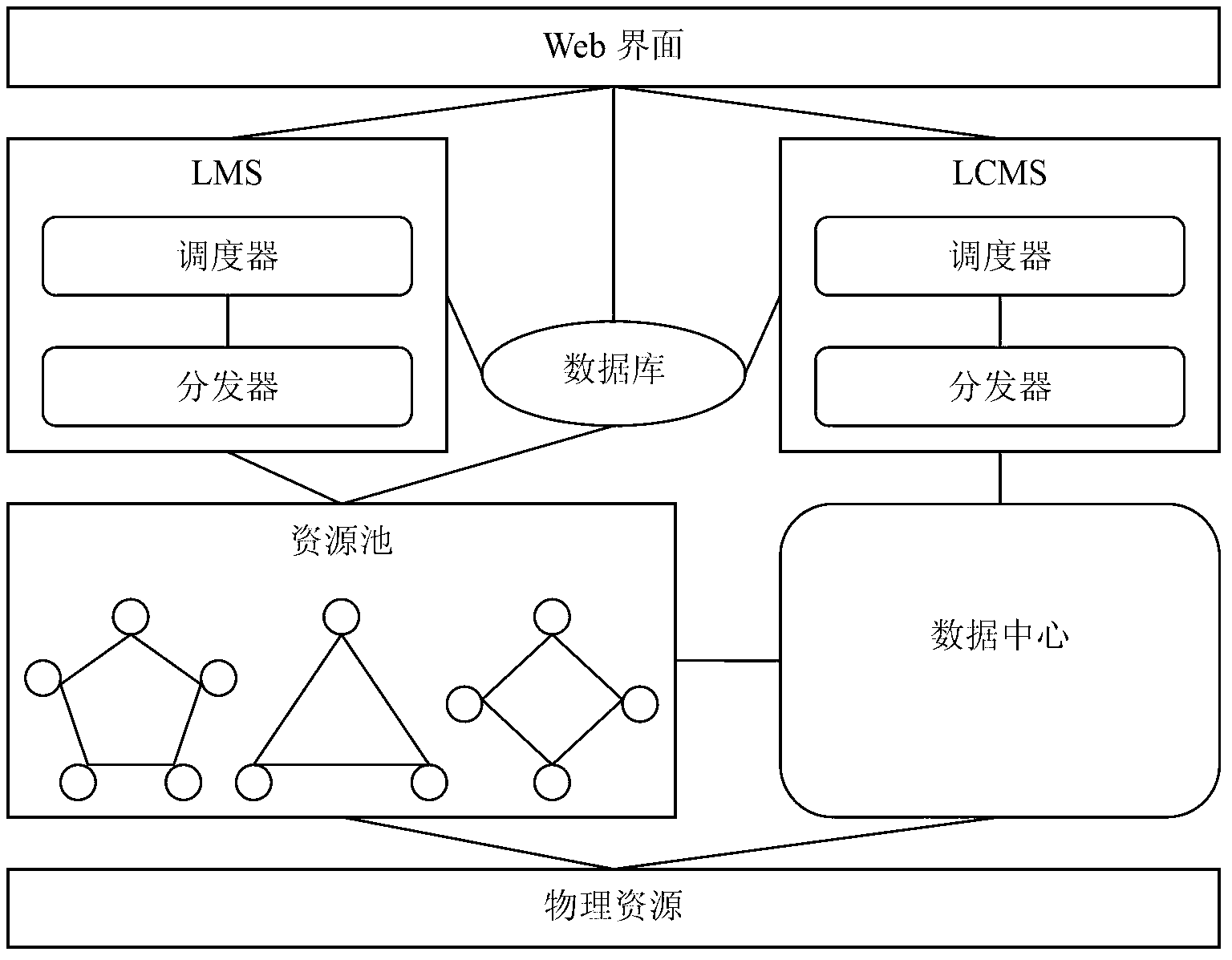
Online collaborative learning architecture and method based on virtualization and cloud computing
InactiveCN103167040AAchieve full coverageImprove the efficiency of online collaborative learningTransmissionElectrical appliancesVirtualizationResource pool
The invention discloses an online collaborative learning architecture and an online collaborative learning method based on virtualization and cloud computing. The architecture comprises a physical layer, a supporting layer, a management layer and a user layer, wherein the physical layer is positioned on the lowermost layer of the architecture and provides hardware support upwardly; the supporting layer is a concentration area of a resource pool and comprises various resources; the management layer is a decision layer of the architecture and comprises a scheduling policy of a virtual machine and an energy management policy; and the user layer enables a user to configure and reconfigure a request. By the invention, the aim of improving online collaborative learning efficiency is fulfilled.
Owner:SHANGHAI DIANJI UNIV
Millimeter wave MIMO-NOMA method of downlink broadcast link based on beam aggregation
ActiveCN111371482ARaise the possibilityReduce distractionsSpatial transmit diversityInterference (communication)Learning architecture
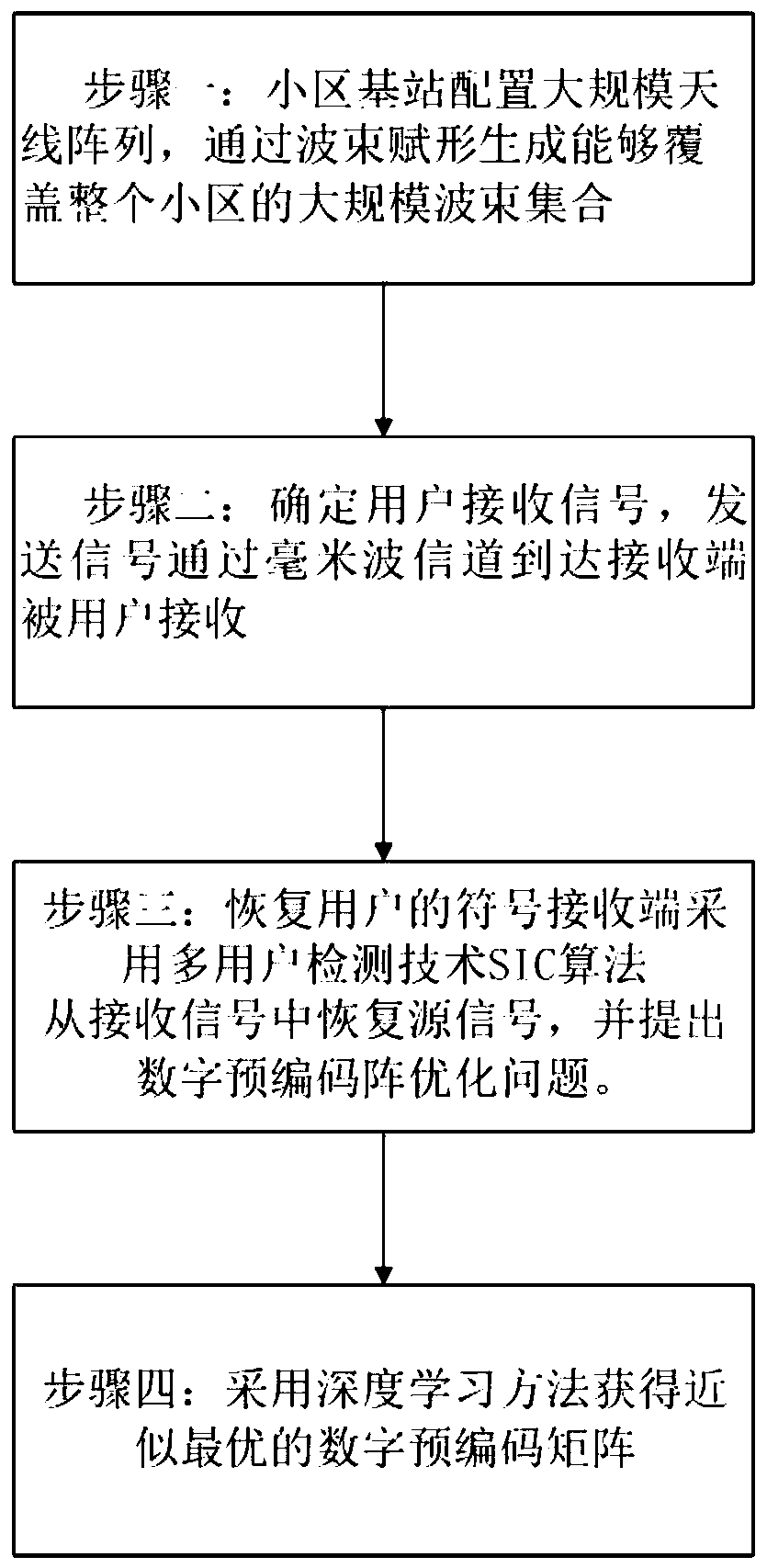
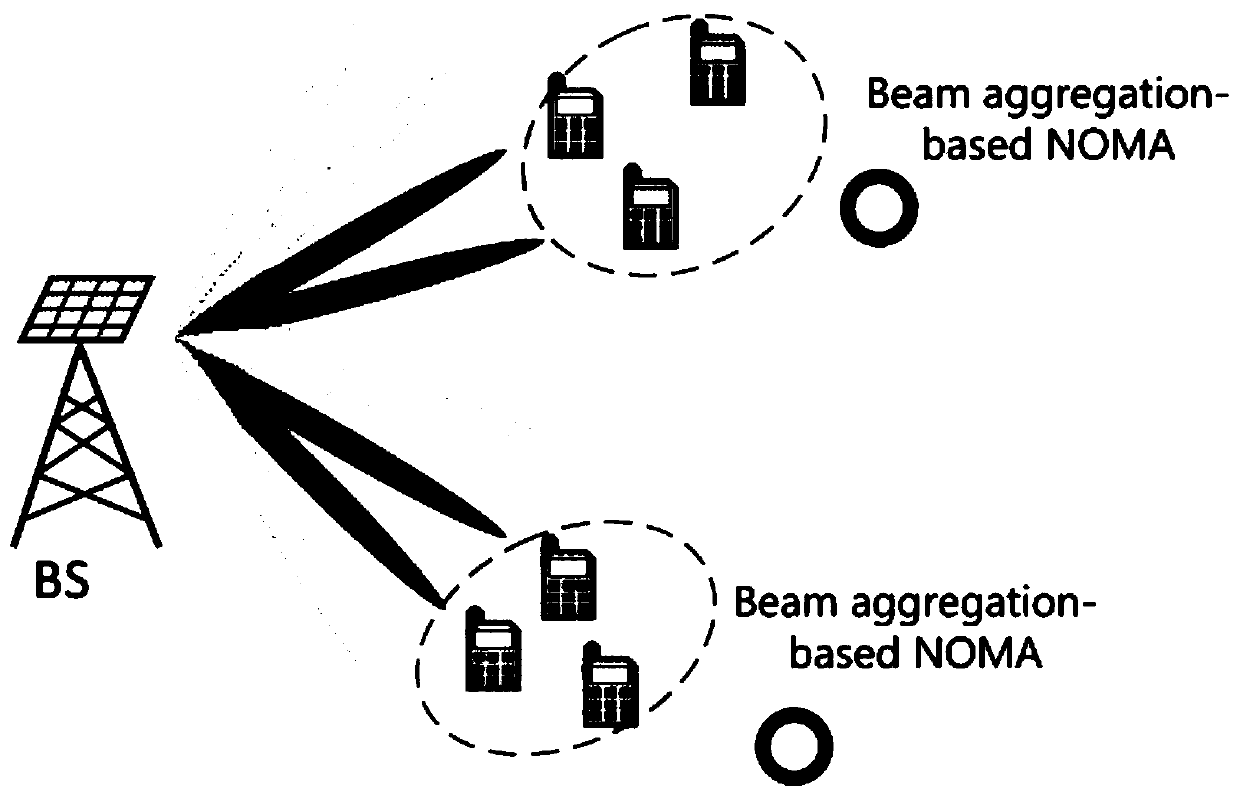
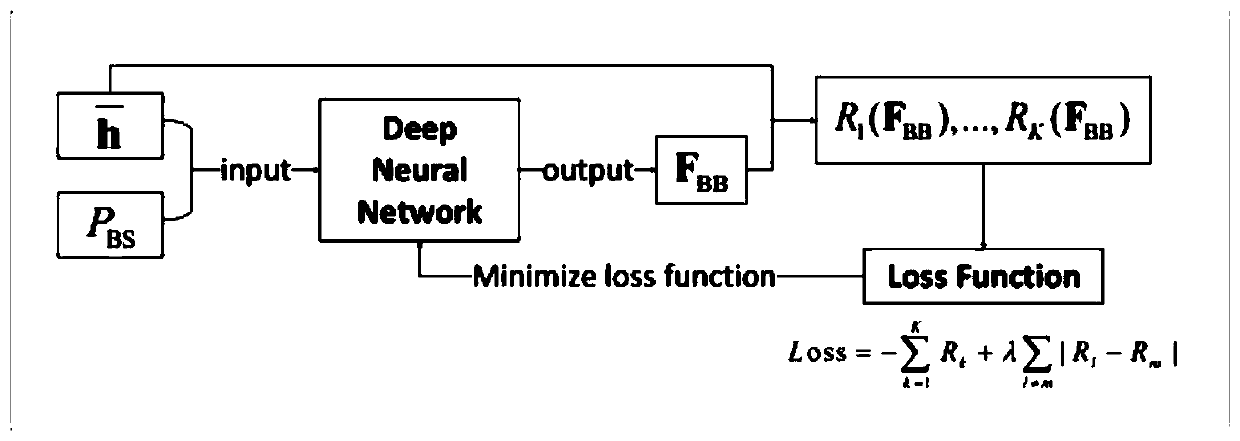
The invention relates to a millimeter wave MIMO-NOMA method of a downlink broadcast link based on beam aggregation, and belongs to the field of communication. In order to solve the problems of user pairing and beam accurate alignment in a downlink broadcast link in the prior art, the invention provides a millimeter wave large-scale MIMO-NOMA method based on beam aggregation. According to the invention, the device is provided, the base station generates a large-scale beam set covering the whole cell through beam forming; wherein a plurality of adjacent beams are gathered together to provide services for a group of adjacent users in a non-orthogonal mode, and an approximately optimal digital precoding matrix is designed according to channel state information by constructing a deep learning architecture and adopting an offline training online application mode, so that interference among the users is reduced, and fairness of users' households is realized. According to the invention, strictbeam alignment between users is not required, and the possibility of NOMA scheme application in downlink millimeter wave MIMO can be increased.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Safety helmet image recognition algorithm based on width learning
PendingCN109522838AShallowLow computing resource requirementsBiometric pattern recognitionAlgorithmImage detection
The invention discloses a safety helmet image recognition algorithm based on width learning. The safety helmet image recognition algorithm is characterized by comprising the following steps: S1, preparing data of a width learning system; S2, training a safety helmet image recognition model based on width learning; S3, a safety helmet image detection mechanism based on a width learning system: S31,reading the image test set obtained in the step S1 and the safety helmet image recognition model obtained in the step S2; S32, inputting images in the image test set into the safety helmet image recognition model to obtain an output value; And S33, marking a picture of a person without a safety helmet, and giving an alarm. The method is a safety helmet image recognition technology based on a width learning system, the width learning architecture is shallow in hierarchy, and the requirement for computing resources is low, so that the wide learning architecture can be deployed on low-end equipment without losing too much precision.
Owner:DALIAN MARITIME UNIVERSITY
Remote supervision relation extraction method based on multiple tasks and multiple examples
ActiveCN112395393ASolve the costSemantic Structure ExpansionSemantic analysisNeural architecturesData classEntity type
Owner:EAST CHINA NORMAL UNIV +1
Bionic robot peacock image identification method based on deep learning
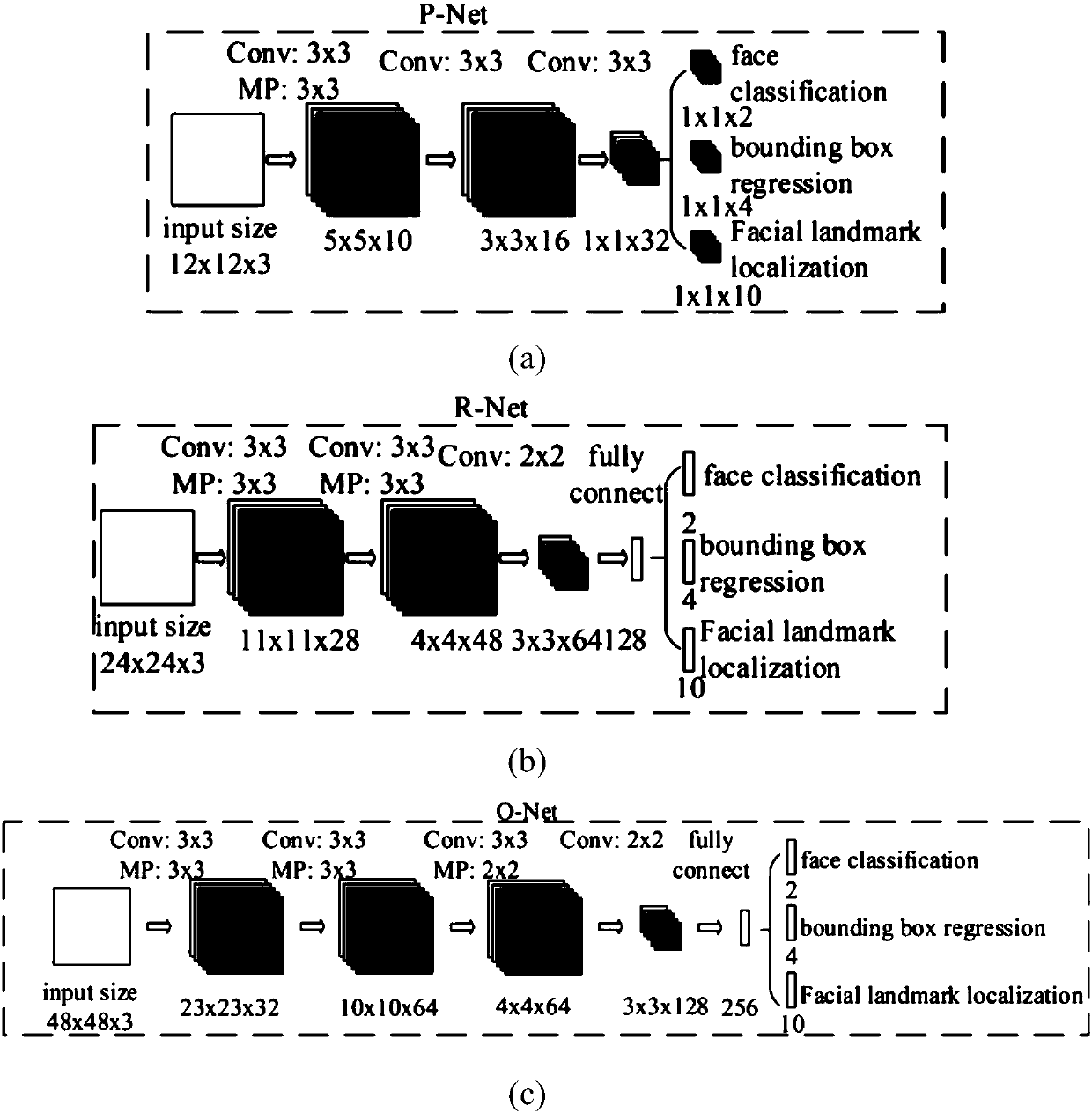
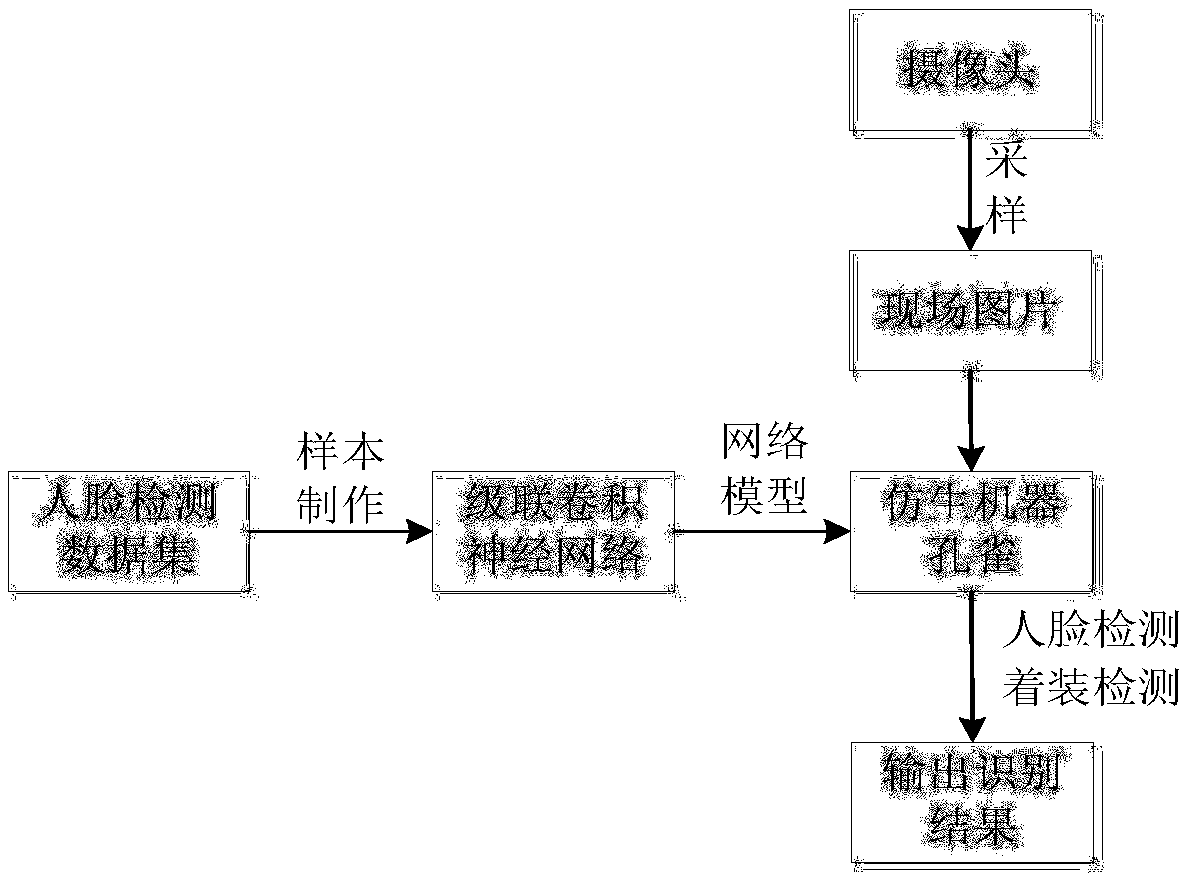
InactiveCN108038455AImprove robustnessCharacter and pattern recognitionArtificial lifeFace detectionBionics
The invention discloses a bionic robot peacock image identification method based on deep learning. The method comprises the following steps that: collecting a public face detection database as an image dataset for training and verification; designing deep learning architecture based on a convolutional neural network, and realizing a face detection function in the deep learning architecture; collecting a site image shot by a bionic robot peacock camera to fine tuning on the trained convolutional neural network to realize the face detection function under an indoor complex environment; and obtaining an empirical parameter to determine the dressing positioning of an audience, and carrying out statistics on the corresponding proportion of various colors. By use of the method, the accurate andefficient face detection and color identification of the recreational bionic robot under the complex environment can be realized, and robustness is high; in addition, for the site image, carrying outparameter fine tuning on the trained deep learning architecture; and finally, carrying out real-time face detection and dressing identification on the site image captured by the camera. The method canbe applied to science and technology museums, hotels and shops for tourists to visit and amuse.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com