Asymmetric prediction error histogram modification-based reversible information hiding method
A prediction error and information hiding technology, which is applied in the field of information security and confidential communication, can solve the problems that cannot meet the actual needs, cannot reflect the compensation principle well, and cannot be well reflected.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
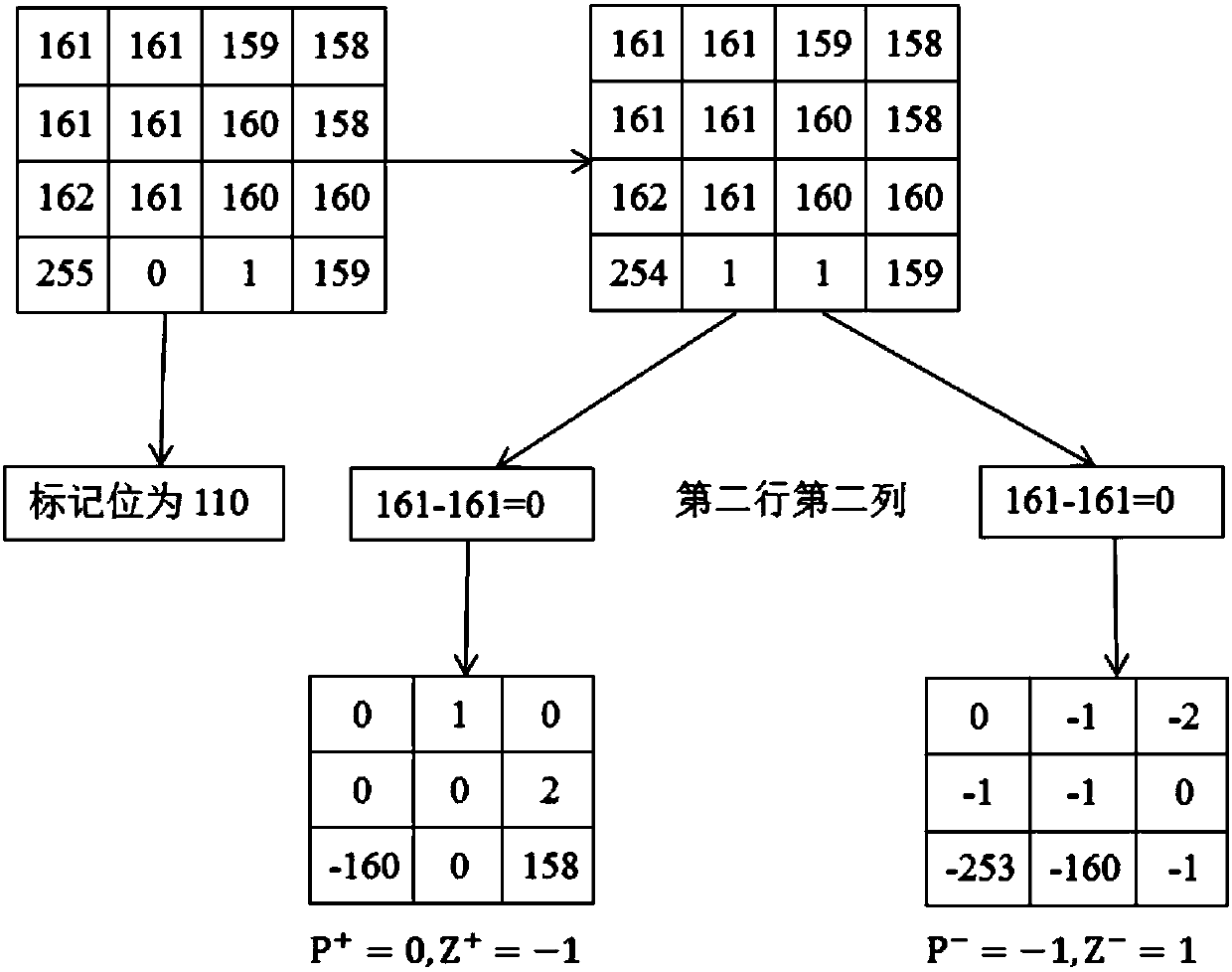
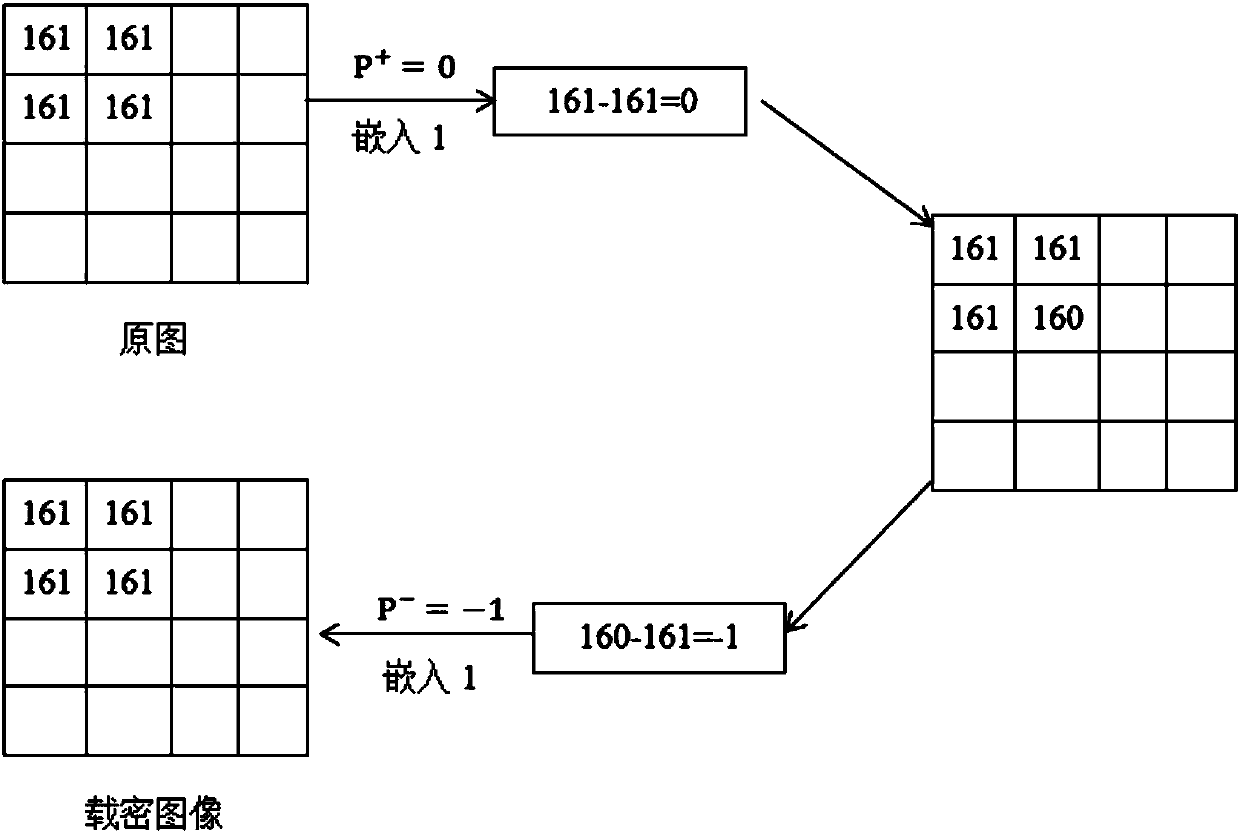
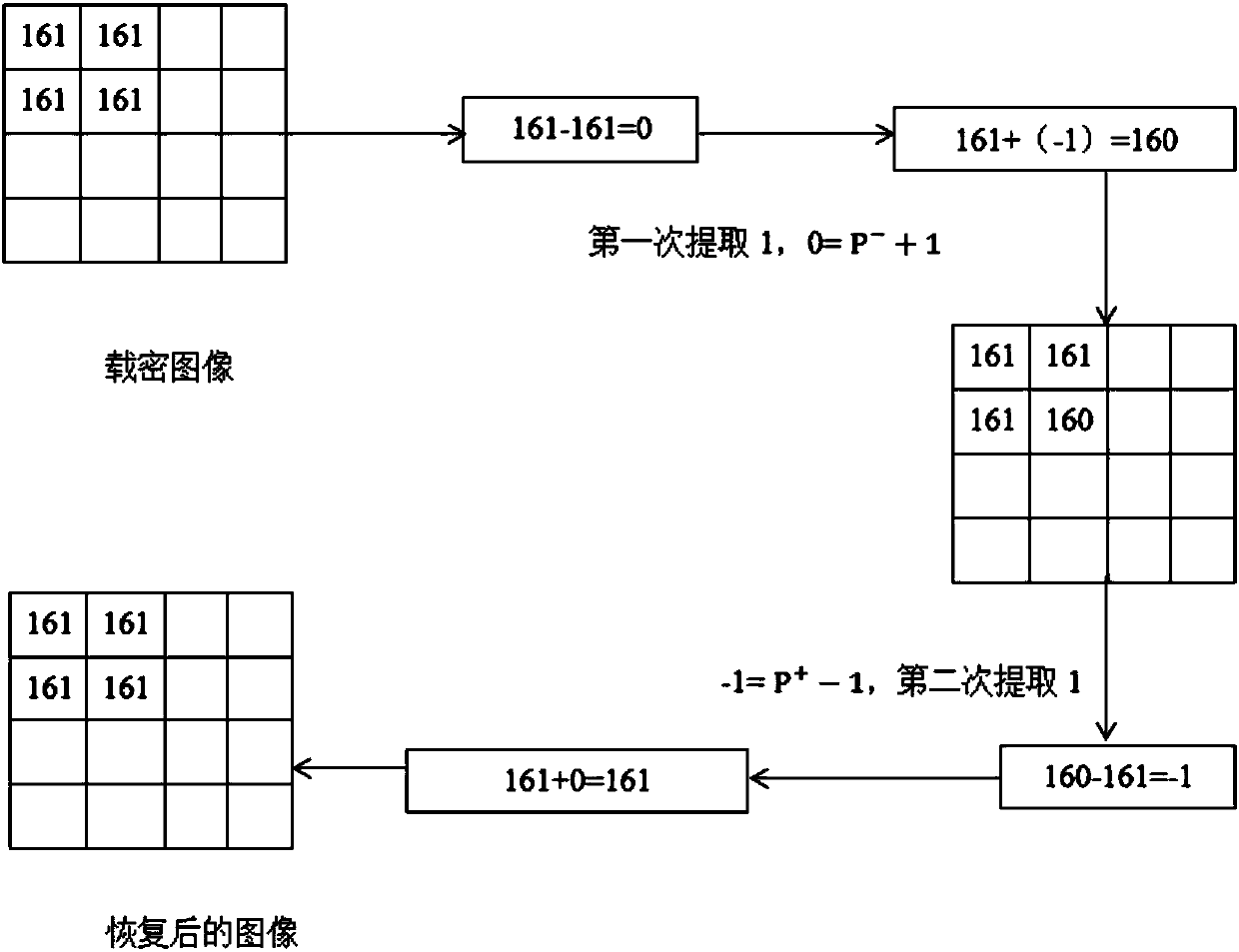
[0068] In this example, information hiding is performed on an original image with a block size of 4×4. It includes the following five steps in turn: perform overflow preprocessing on the original image; search for peak points and zero points on the image after overflow preprocessing; embed 4×4 blocks into secret information; 4×4 blocks after embedding secret information The embedded information is extracted, and the image of the 4×4 block after the secret information is extracted is obtained; overflow recovery processing is performed on the image of the 4×4 block after the secret information is extracted. Specific steps are as follows:
[0069] 1. Perform overflow preprocessing on the original image:
[0070] Such as Figure 4 In the 4×4 block shown in (a), the pixels are traversed in order, and the pixels of 255 or 0 are marked as 1, and the pixels of 254 or 1 are marked as 0, and 254 is assigned to the pixel with a value of 255. 1 is assigned to a pixel with a value of 0, r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com