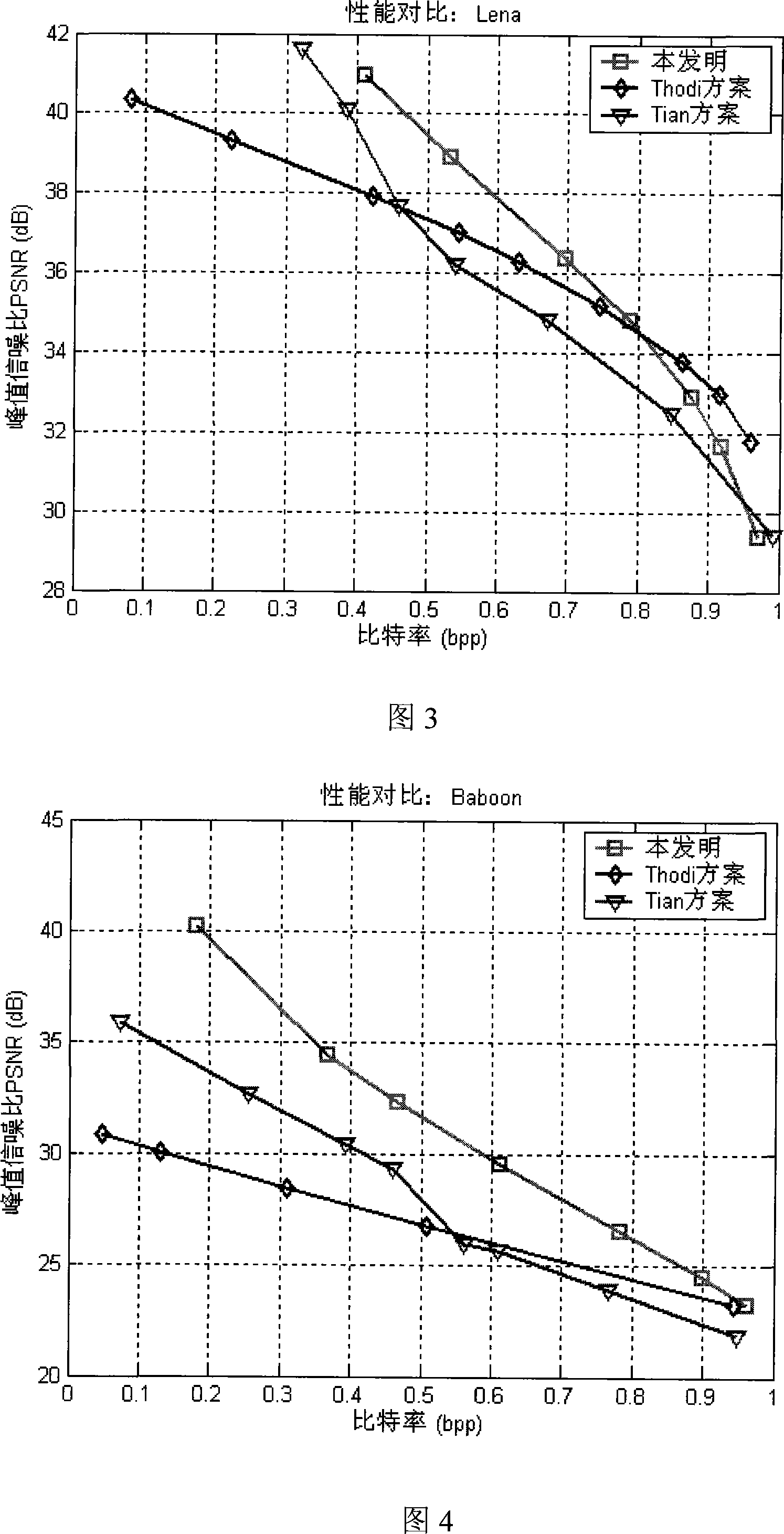
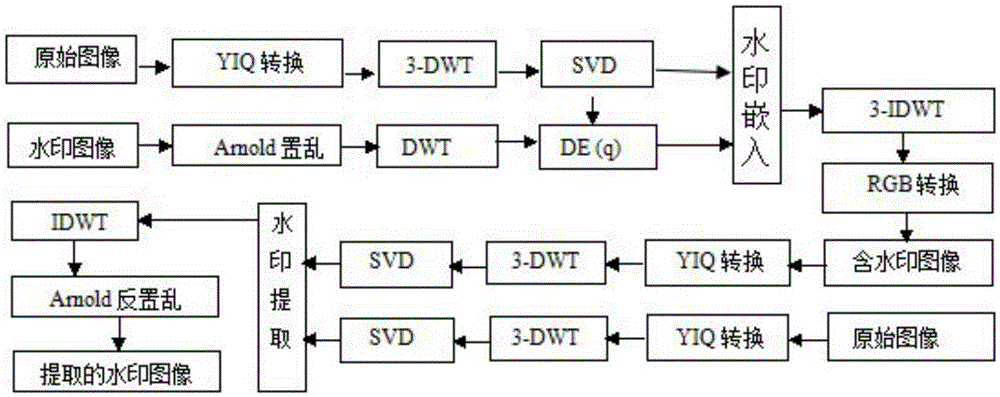
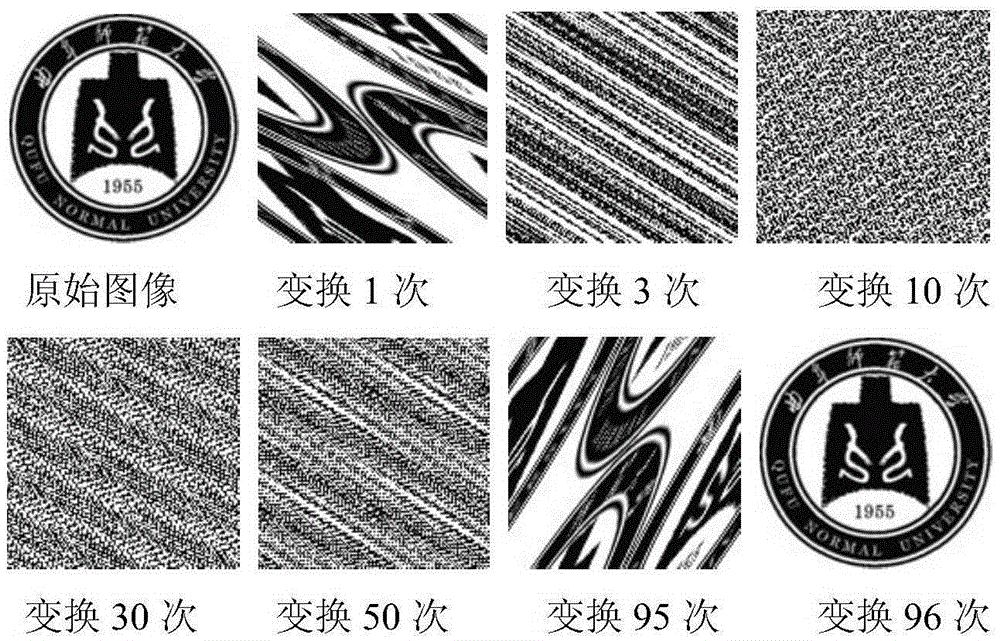
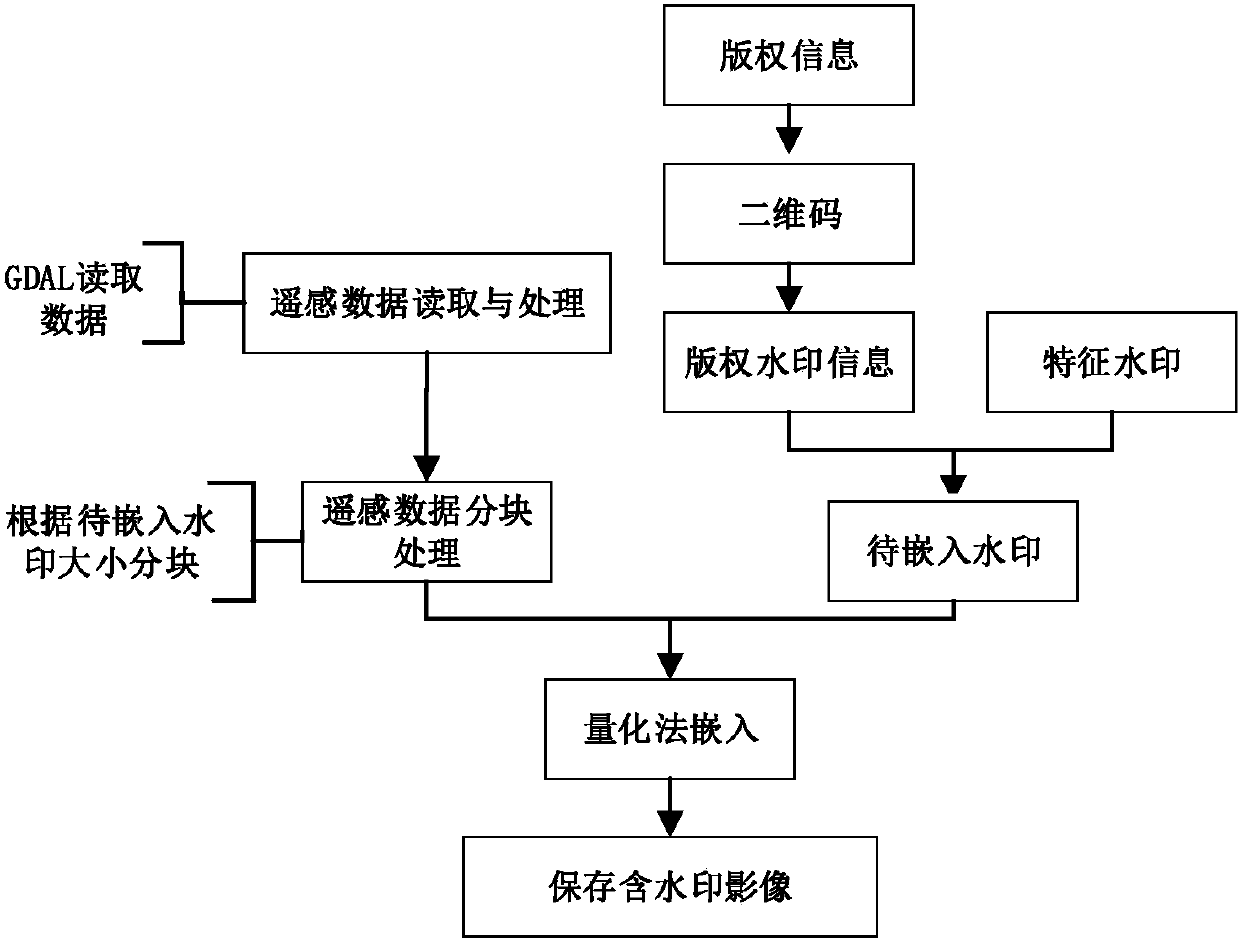
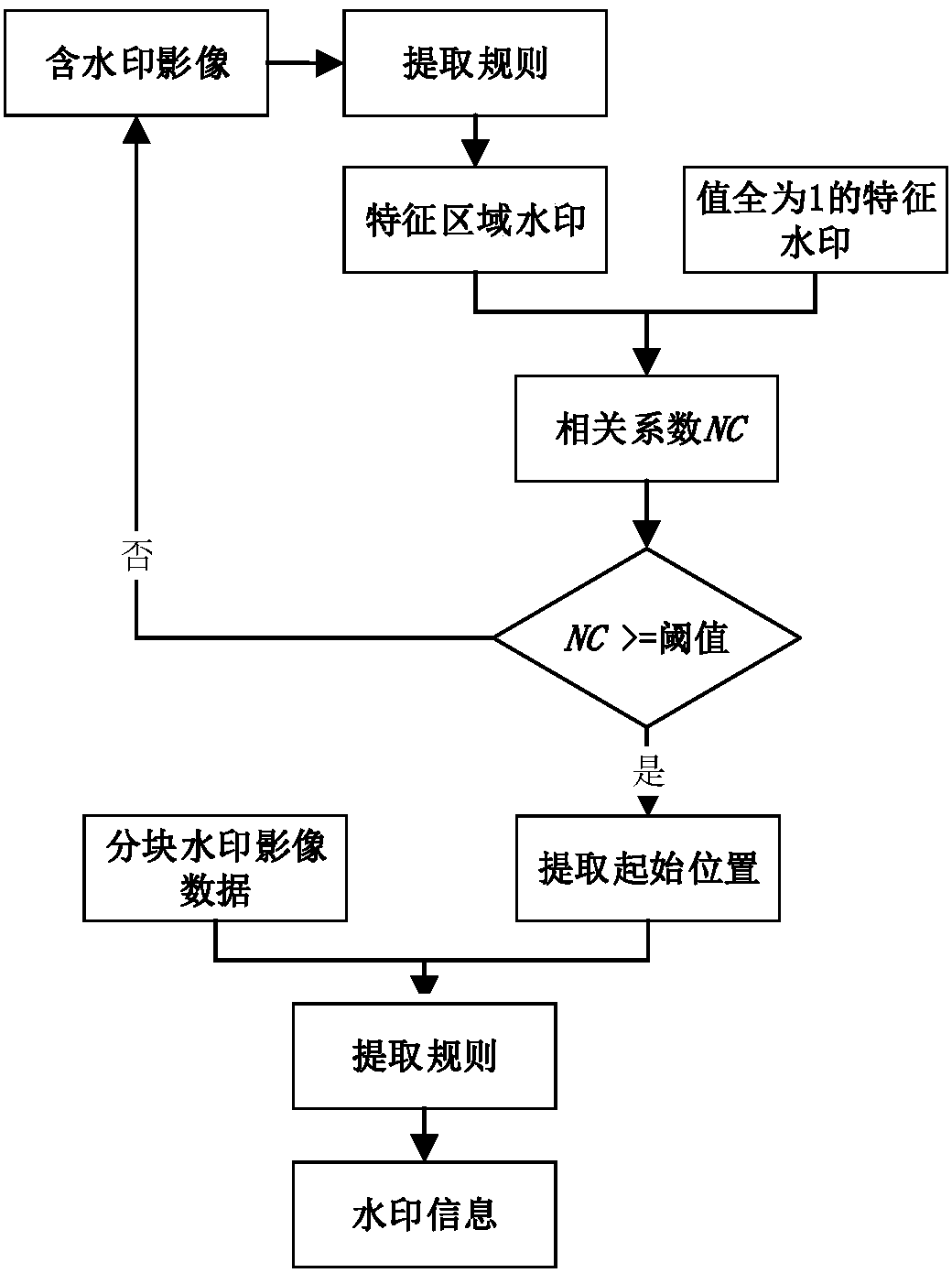
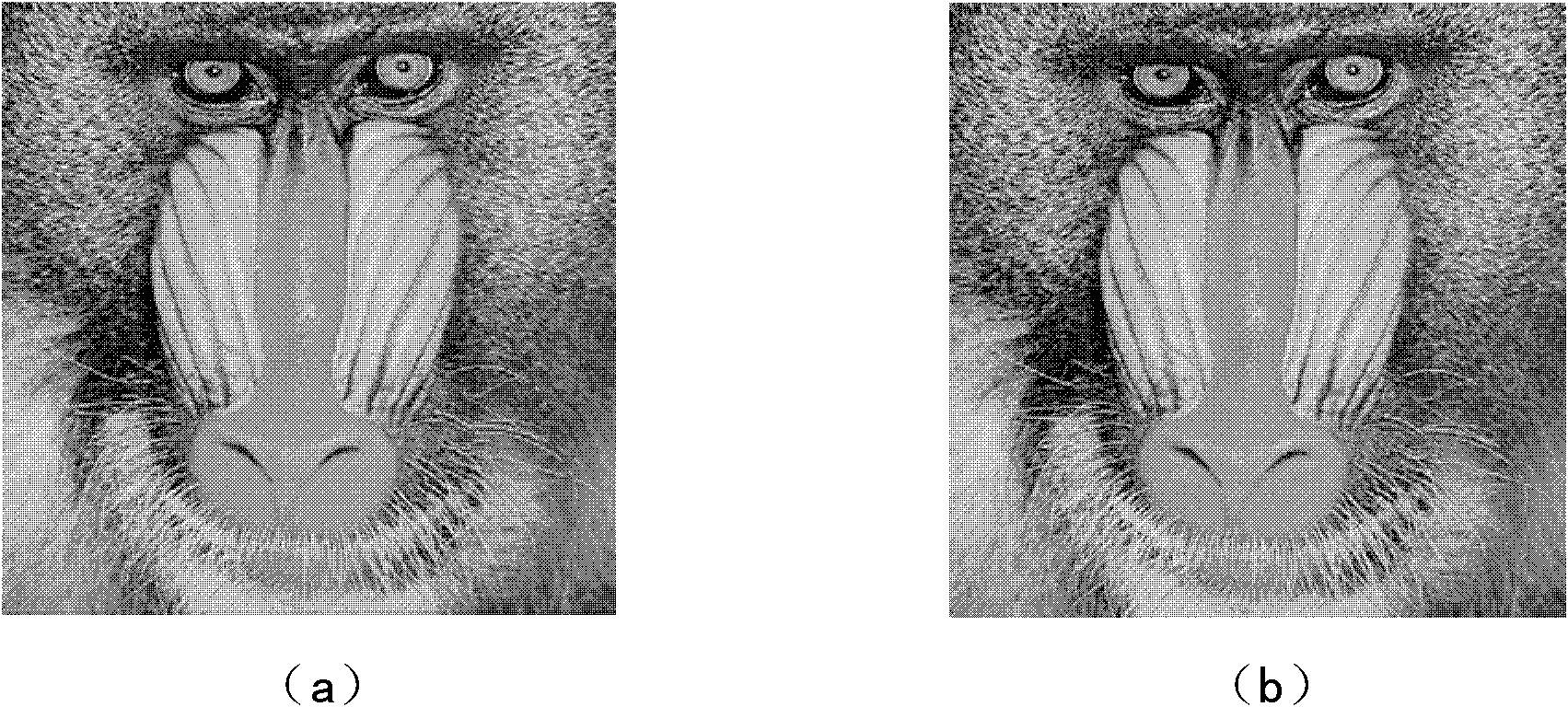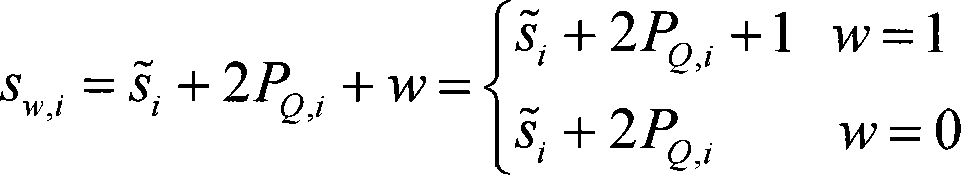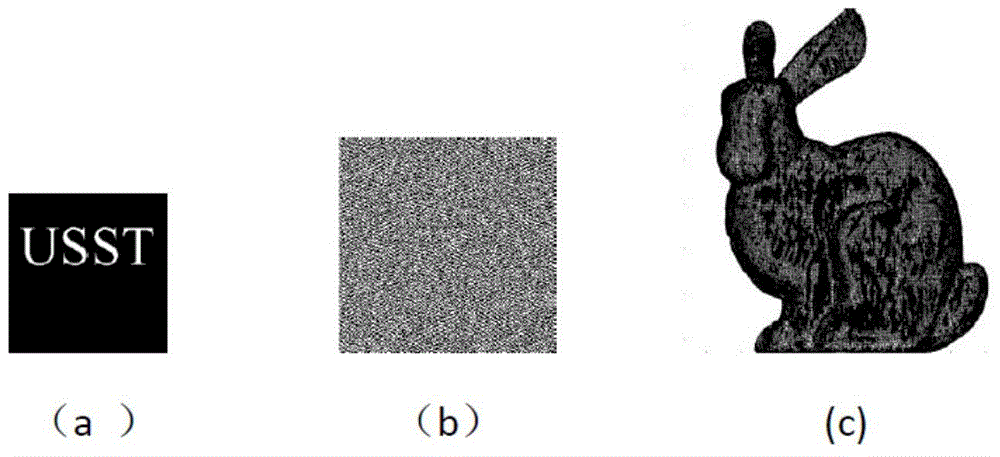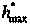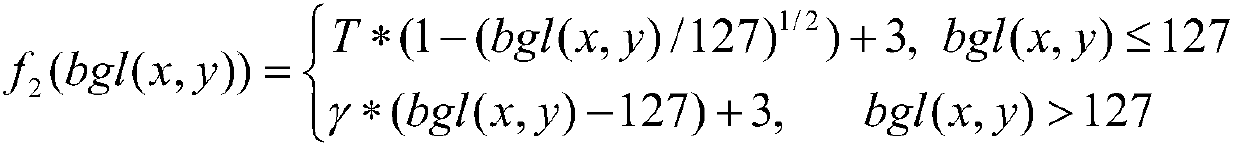Patents
Literature
234 results about "Watermark algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for controlling file access of GIS vector data
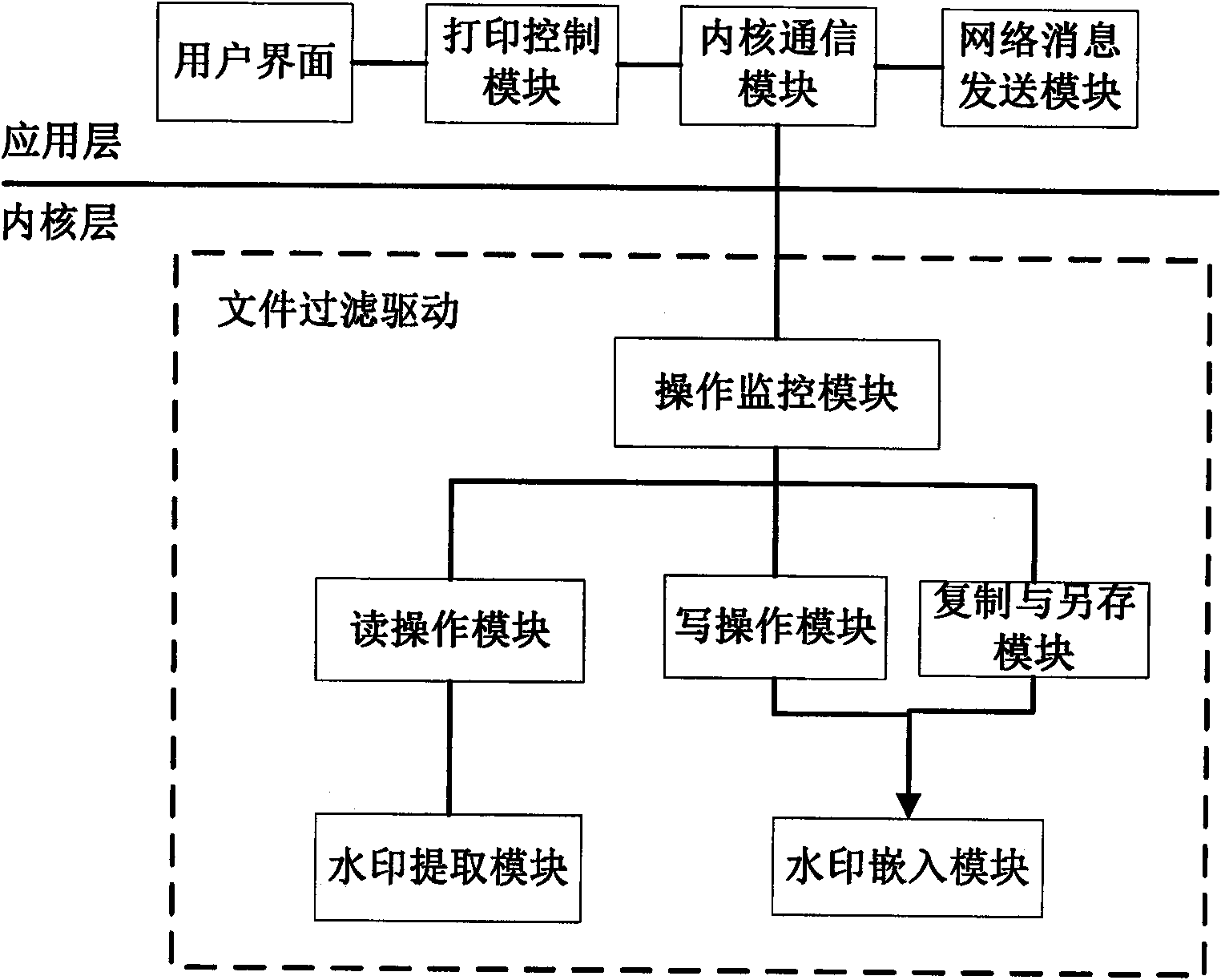
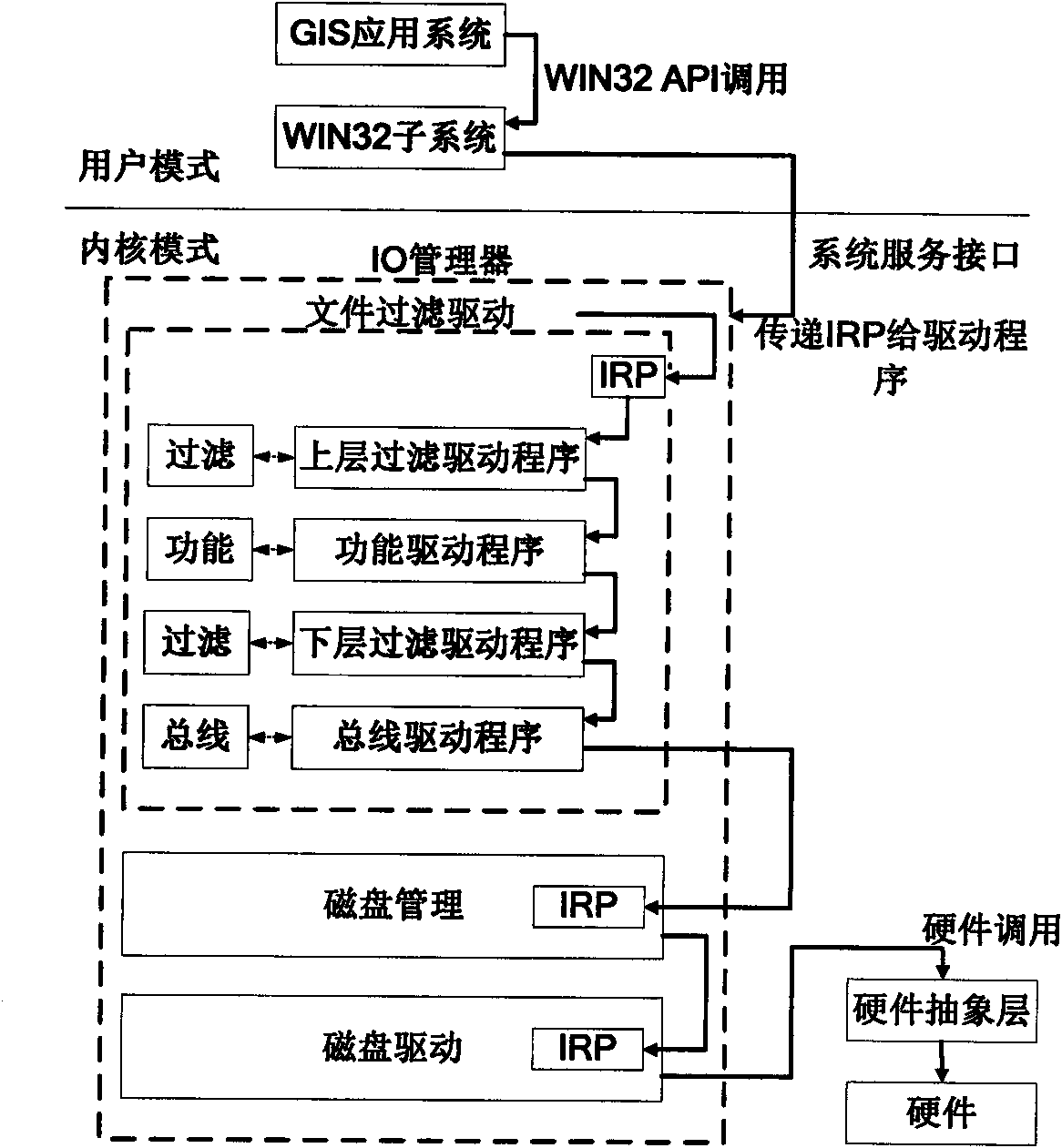
The invention discloses a method for controlling the file access of GIS (geographical information system) vector data. The method comprises three technical links: the insertion of the copyright mark m into the GIS vector data file, the extraction of the copyright mark m and the data recovery, and the data application monitoring and the data access control, wherein, the copyright mark m is divided into copyright marks for indication and certification. When the GIS vector data products are published, an excessive amount of copyright marks are inserted into the published products by the reversible watermark algorithm and the data accuracy is intentionally reduced, therefore, on one hand, the application of data-sharing among subscribers for educational and general purposes can be supported by directly downloading the data, and on the other hand, the commercial use of data can be limited by reducing the data accuracy. When the data is applied among high-end subscribers for research and commercial purposes, the extraction of the copyright mark and the data recovery can be realized in a real-time and open manner by installing the monitoring program based on the filter driver technology, thereby not only realizing the copyright certification on a real-time basis and acquiring the original lossless data products, but also limiting the unauthorized operation of validated subscribers.
Owner:NANJING NORMAL UNIVERSITY
Multiple digital watermarking method for geographic information system (GIS) vector data
InactiveCN101968878AImprove robustnessComputer security arrangementsImage data processing detailsDiscrete cosine transformGeographic information system
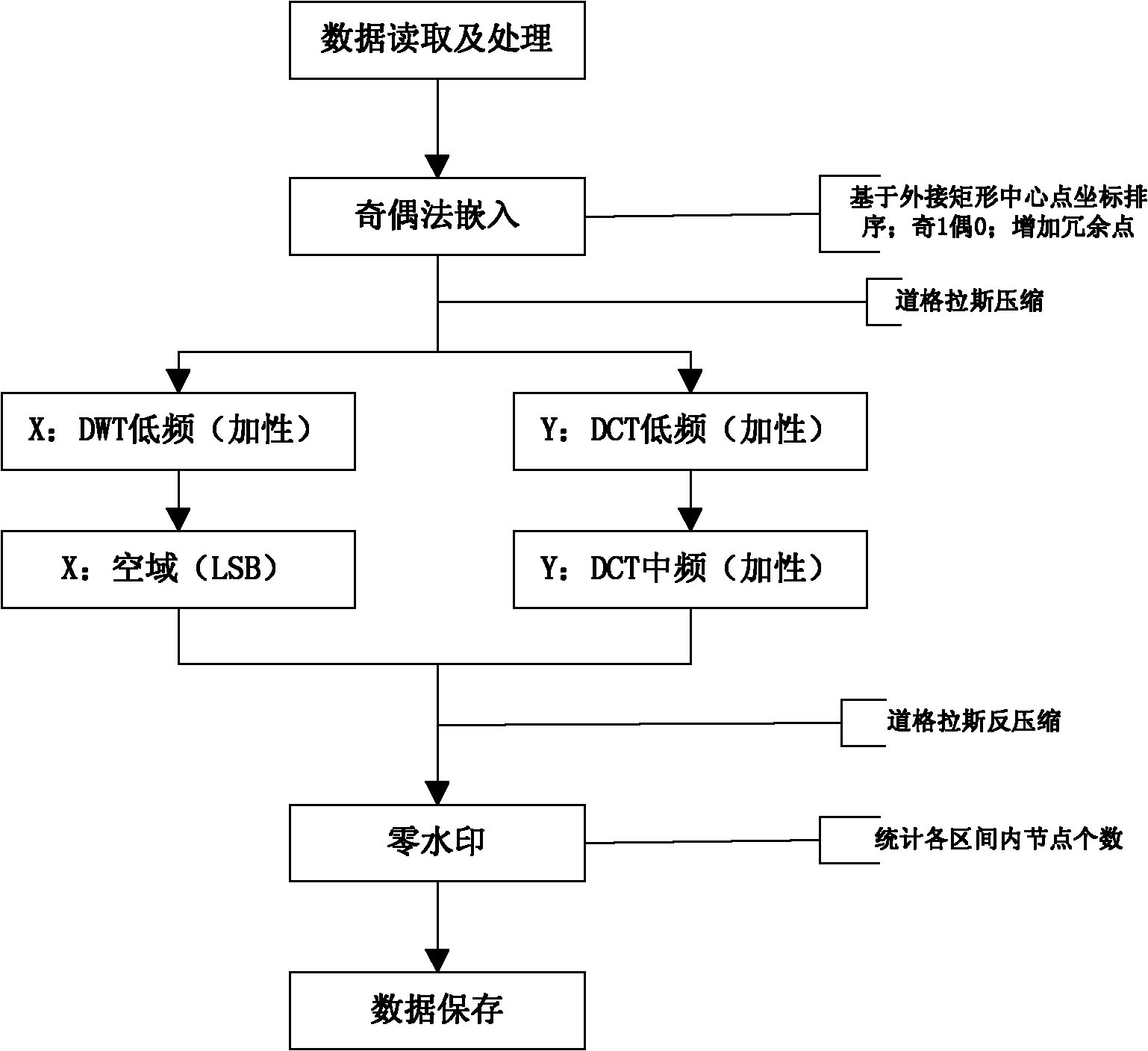
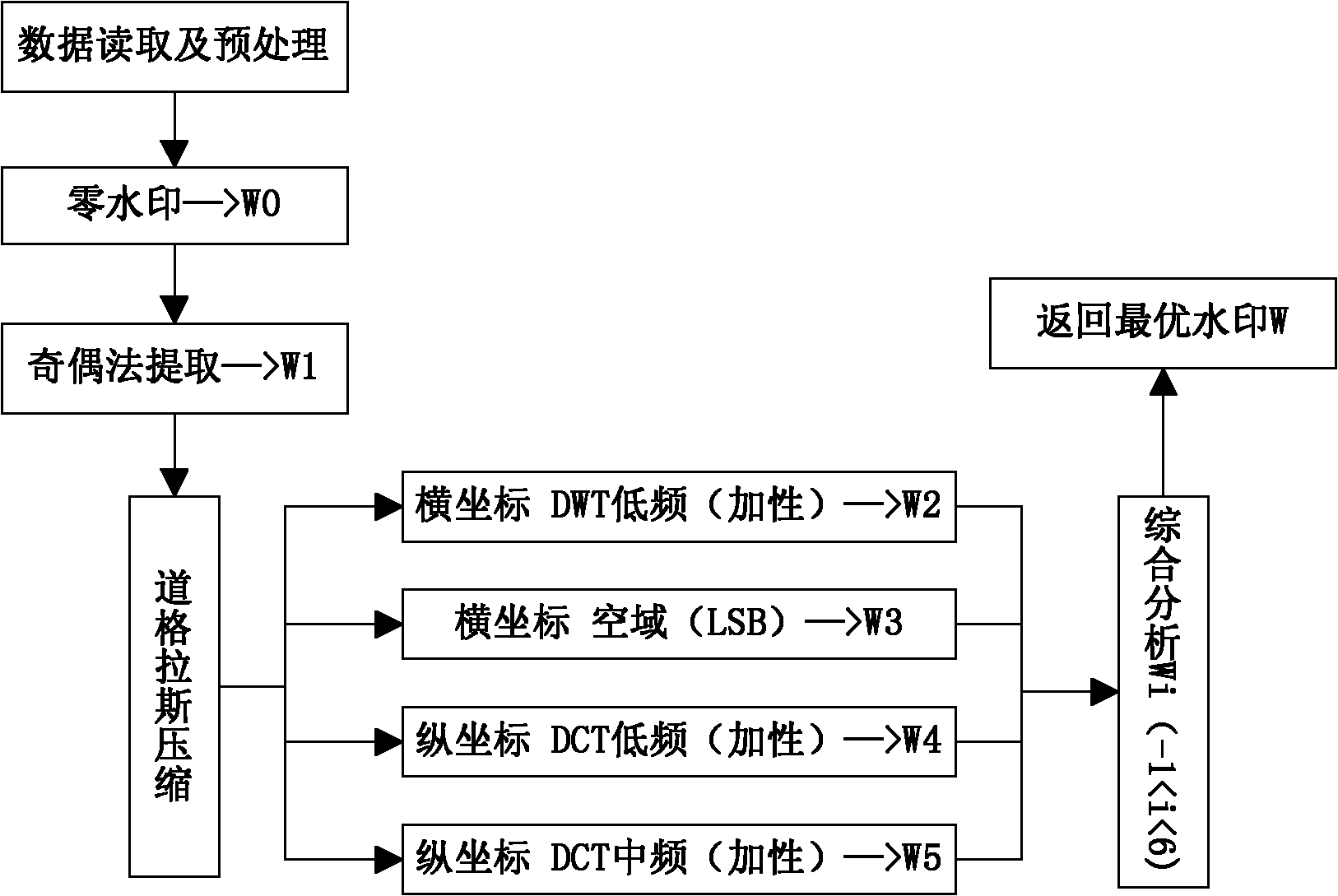
The invention discloses a multiple digital watermarking method for geographic information system (GIS) vector data, and belongs to the field of geographic information copyright protection. The watermark embedding process of the method comprises the following steps of: reading and processing the data; embedding algorithms by an odd-even method; respectively embedding watermarks into a spatial domain, a discrete wavelet transform domain, a discrete cosine transform domain of horizontal coordinates and vertical coordinates by a low-order additive method and a least significant bit substitution method; adopting a zero-watermark algorithm; and storing watermark-containing data. The watermark extraction process of the method is the inverse process of the embedding process. A practical multiple digital watermark protection method is comprehensively integrated aiming at the common attack modes of the GIS vector data and according to the principle and anti-attack performance of each single algorithm. Various embedding modes are adopted and the specific embedding position of each watermark is controlled, so that embedding and extraction are non-interfering, conflicts are avoided, the advantages of each algorithm are exerted and complemented and the anti-attack capability of digital watermarks is greatly improved.
Owner:苏州南师大智慧创意产业有限公司
Reversible watermark method utilizing histogram shifting
InactiveCN102567942AReduce sizeEasy to compressImage data processing detailsProgram/content distribution protectionBit blitGeneration process
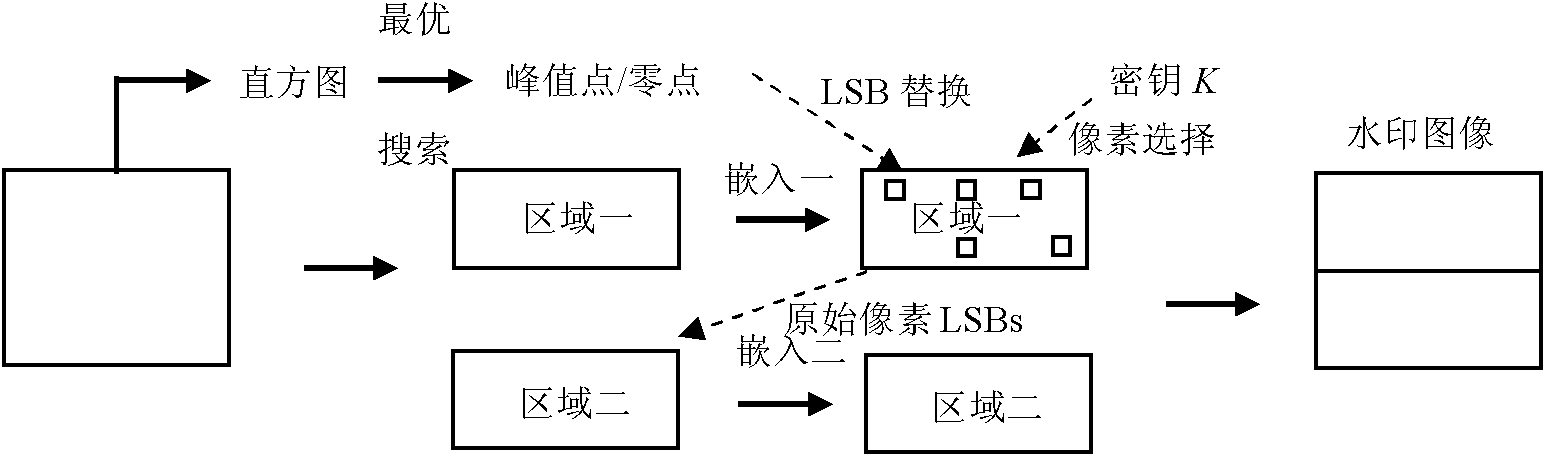
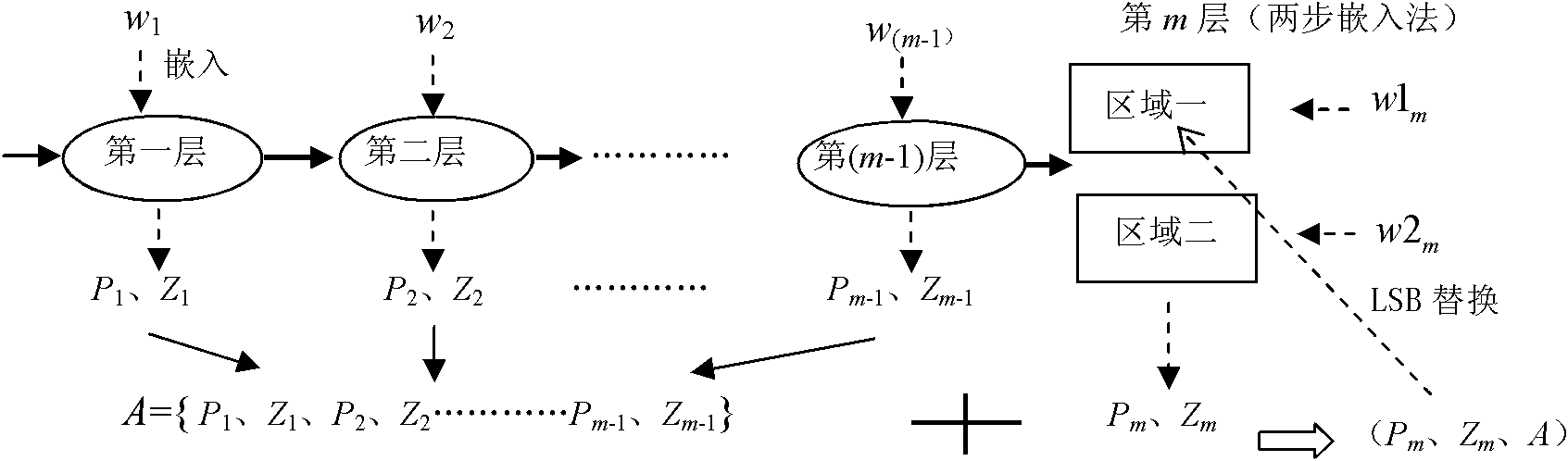
The invention provides a reversible watermark method based on histogram shifting and has significant practical values for protecting multimedia copyrights. By means of the reversible watermark method, traditional histogram shifting algorithms are improved in two aspects, firstly, 1 and 0 in a bite map are more imbalanced by arranging a generation process of the bit map on watermark embedding rather than in a non-pretreatment stage, so that compression is easier, and embedding capacity is improved; and secondly, the reversible watermark method is a two-step embedding method. The watermark blind extraction is achieved and troubles that the histogram shifting method needs extra side information transmitting are solved by dividing an image into an upper large area and a lower large area, subjecting the upper area to the watermark embedding, embedding the generated side information into the lowest significant bit containing watermark pixels in the area, and embedding the left watermark information and the replaced lowest significant information into the lower area.
Owner:SUN YAT SEN UNIV
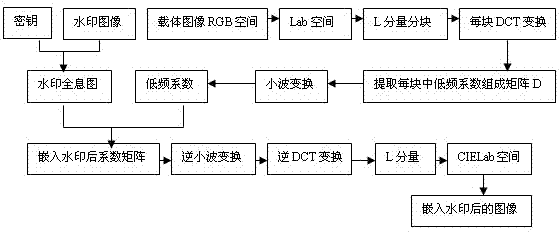
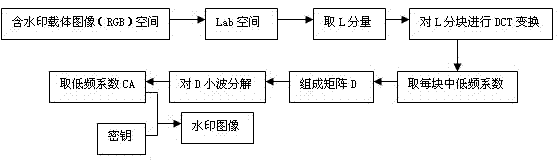
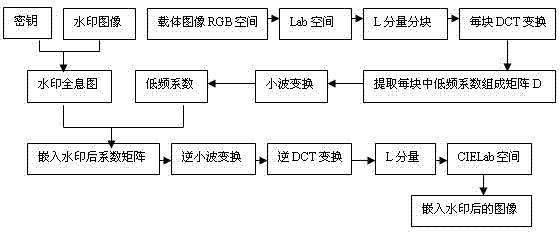
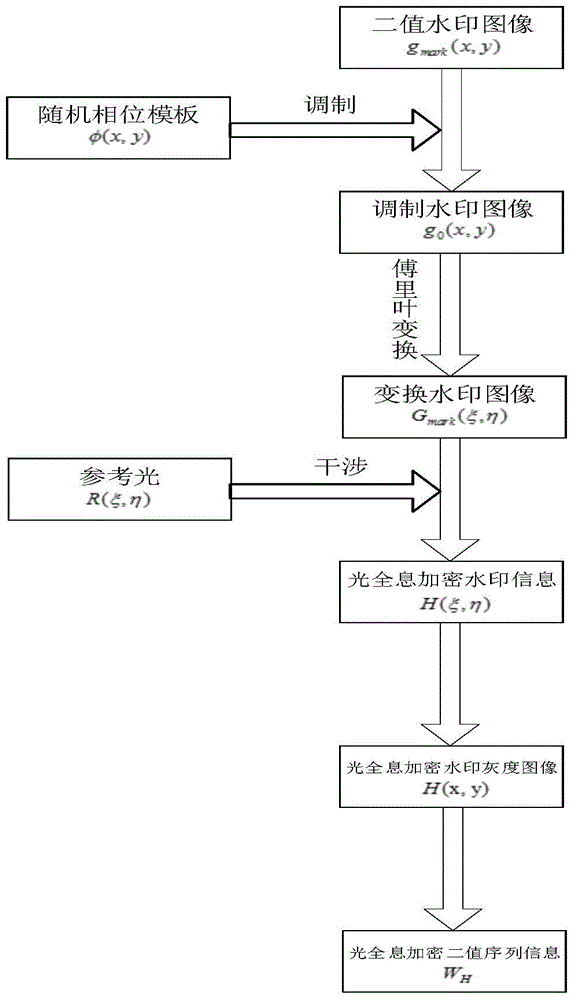
Encrypted holographic watermark algorithm of transform domain based on copyright protection
InactiveCN102236882AImprove visibilityImprove securityImage data processing detailsWavelet decompositionDouble phase
The invention relates to an encrypted holographic watermark algorithm of a transform domain based on copyright protection, comprising the following steps of: carrying out random double-phase modulation on watermark information to generate a watermark holographic image; then carrying out 4*4 partitioning on an L component of a carrier image in a Lab space; carrying out DCT (Discrete Cosine Transformation) conversion on each partition; extracting a middle-low frequency coefficient of each matrix to form a new matrix and carrying out wavelet decomposition on the new matrix; embedding the watermark holographic image into the middle-low frequency wavelet coefficient to obtain an embedded colorful image; and then extracting the watermark image again by directionally operating the steps. The watermark has good invisibility and higher safety by carrying out random double-phase encryption on the watermark image; and the original image is not needed in the step of extracting the watermark image, and the watermark belongs to a blind testing watermark.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
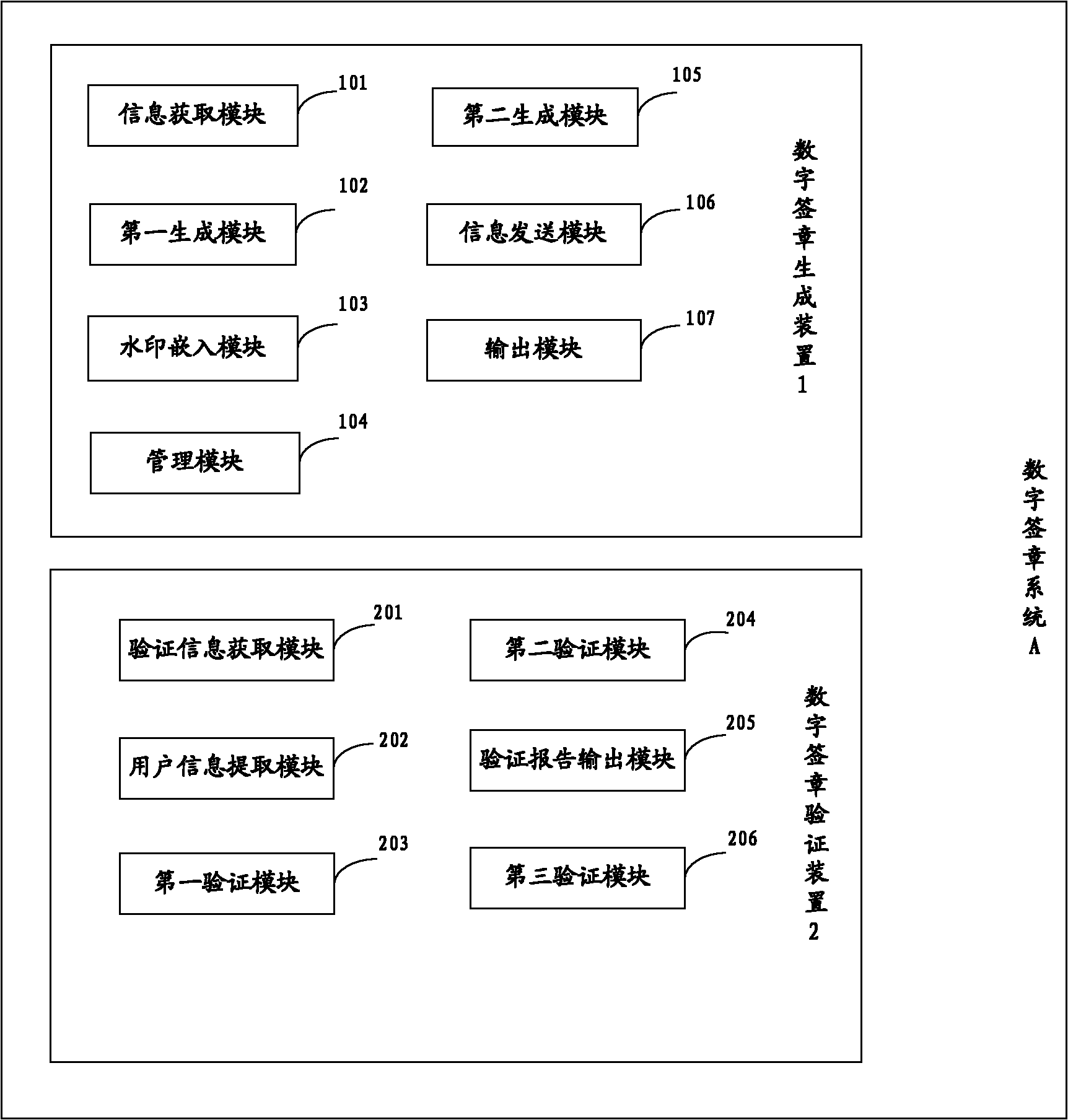
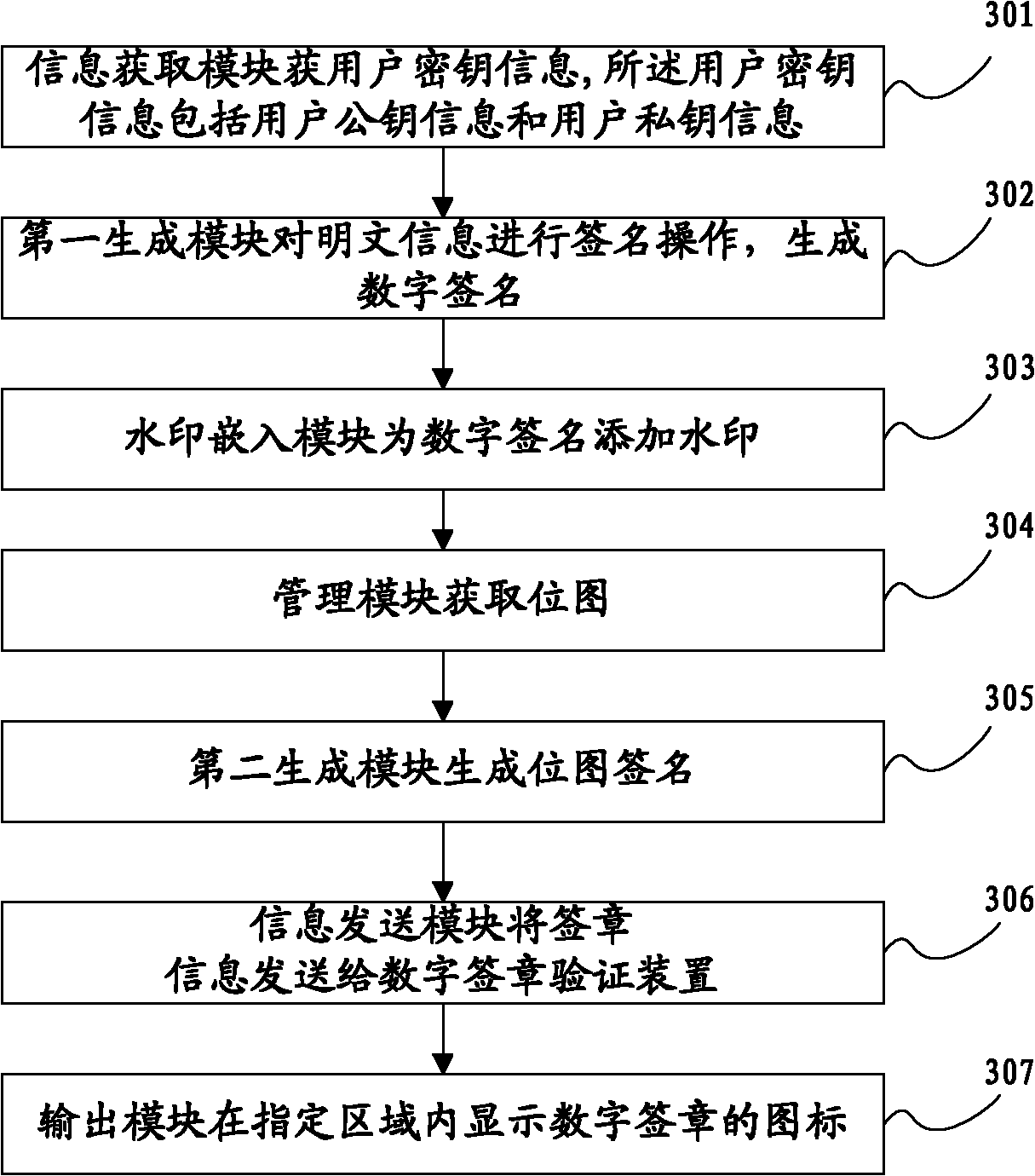
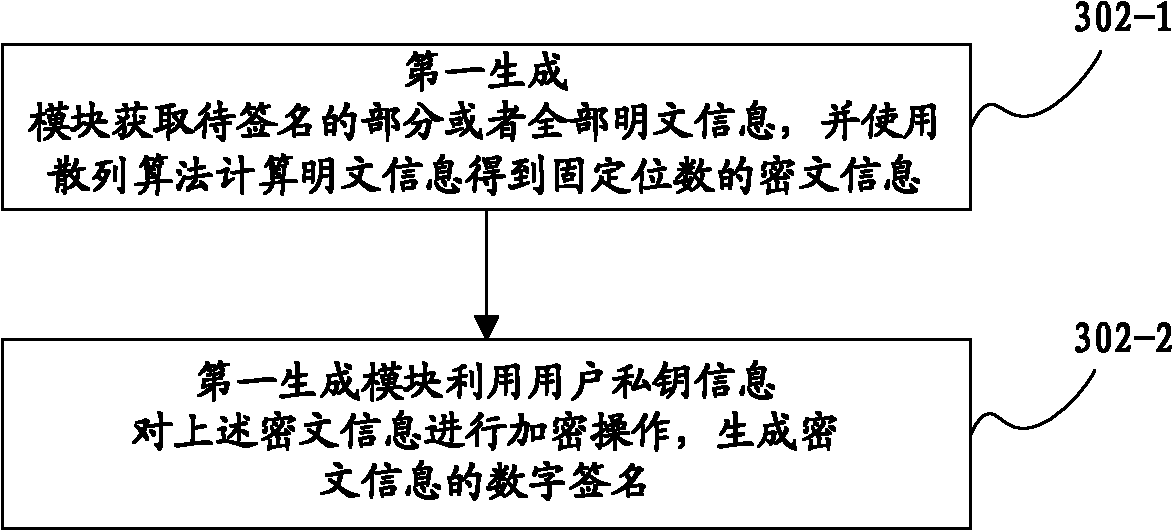
Digital signing system and method
ActiveCN102164037AEnsure safetyGuarantee authenticityUser identity/authority verificationTamper resistancePlaintext
The invention provides a digital signing method which comprises the following steps: acquiring the secret key information of a user; carrying out signing operation on plaintext information so as to generate a digital signature; changing the digital signature by using a watermark algorithm so as to form watermark information with the digital signature; acquiring a bitmap; processing the watermark information and the bitmap and carrying out signing on the bitmap so as to generate a bitmap signature; sending the digital signing information and the public key information of the user; showing the icon of the digital signature; acquiring the digital signing information and the public key information of the user; and verifying the bitmap signature and the digital signature; reporting the verification results of the bitmap signature and the digital signature; and verifying the effectiveness of the digital signature. The invention also provides a digital signing system. In the invention, through respectively carrying out signing on the plaintext information and the bitmap, the safety of a document is ensured; and through respectively verifying the bitmap signature and the digital signature, the authenticity of the document is ensured, and a tamper-proof effect is achieved.
Owner:FEITIAN TECHNOLOGIES
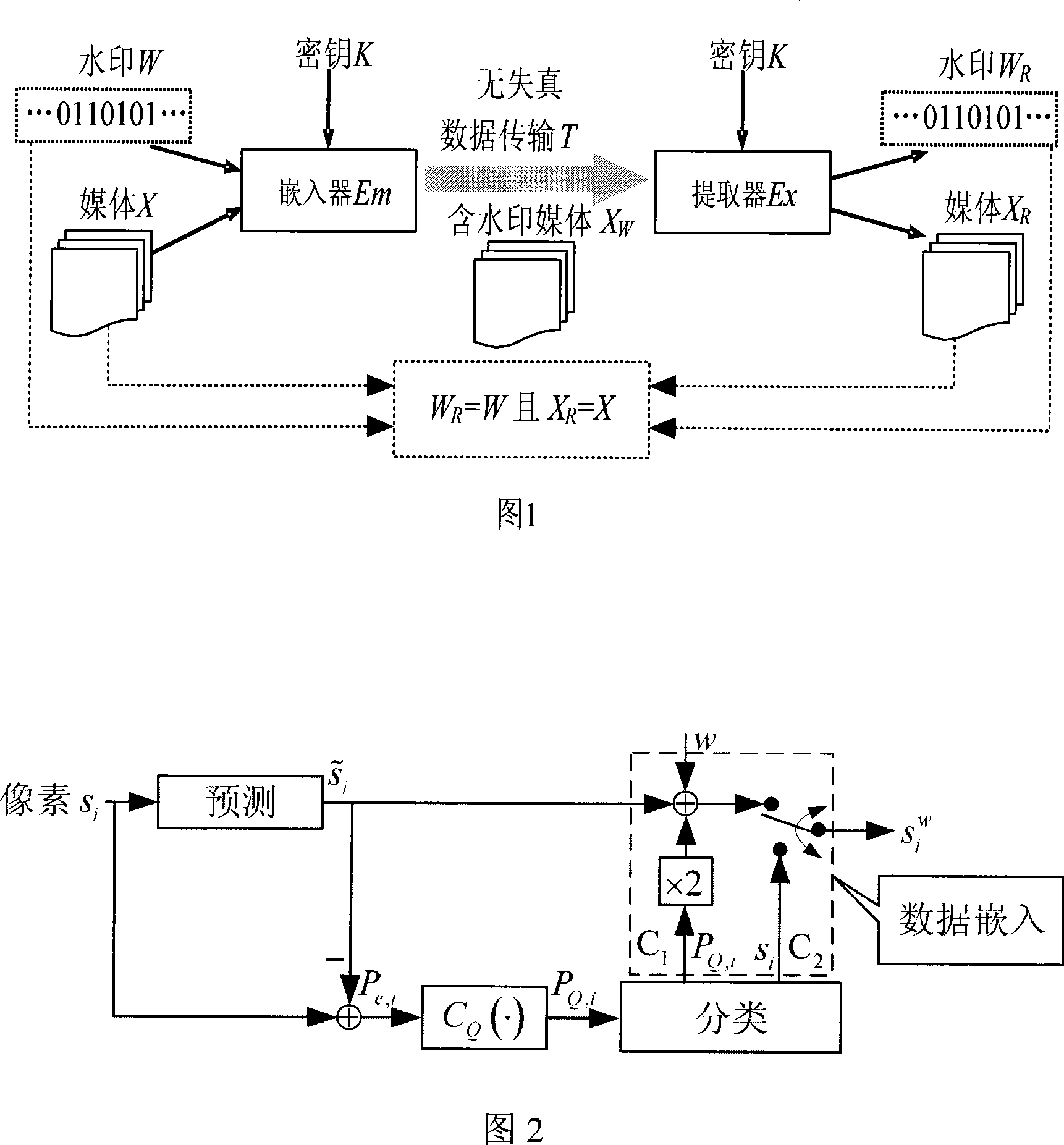
High capacity reversible water mark method based on predication and companding technology
InactiveCN101105857AExcellent Peak Signal to Noise RatioReduce computational complexityImage data processing detailsSignal-to-noise ratio (imaging)High peak
The invention discloses a high-capacity reversible watermark method based on predication and companding technique. Through the introduction of the companding technique, the invention includes two processes: watermark embedding and watermark extracting. The invention effectively solves the problem of capacity consumption of position drawing in reversible watermark algorithm, and achieves high embedding capacity even in the situation of low threshold value. Meanwhile, due to the operation of data re-embedding after the compression of high predication errors, the invention still can maintain high peak signal to noise ratio (PSNR value).
Owner:BEIJING JIAOTONG UNIV
Wavelet domain color image watermark encryption algorithm based on differential evolution
InactiveCN105335924ASafeImprove visibilityImage data processing detailsSingular value decompositionVisual perception
The invention discloses a wavelet domain color image watermark encryption algorithm based on differential evolution. The operating method comprises the following steps: performing color space transformation on an original image to obtain a YIQ color format suitable for a human vision system and extracting a brightness component Y; adopting Arnold scrambling on a watermark image; performing three-stage discrete wavelet decomposition on the component Y of the original image to generate four sub-bands of different frequencies by utilizing discrete wavelet transform, thereby obtaining a sub-band image; representing a sub-band image matrix by using A, and performing singular value decomposition on the image subjected to three-stage wavelet decomposition; performing primary discrete wavelet decomposition on the watermark image subjected to scrambling encryption processing; performing watermark embedding; adaptively optimizing and selecting embedding strength by adopting differential evolution, and adding watermark information into the original image subjected to singular value decomposition in a multiplicative addition form. The invention has the beneficial effects that the watermark algorithm has high invisibility and is high in robustness.
Owner:QUFU NORMAL UNIV
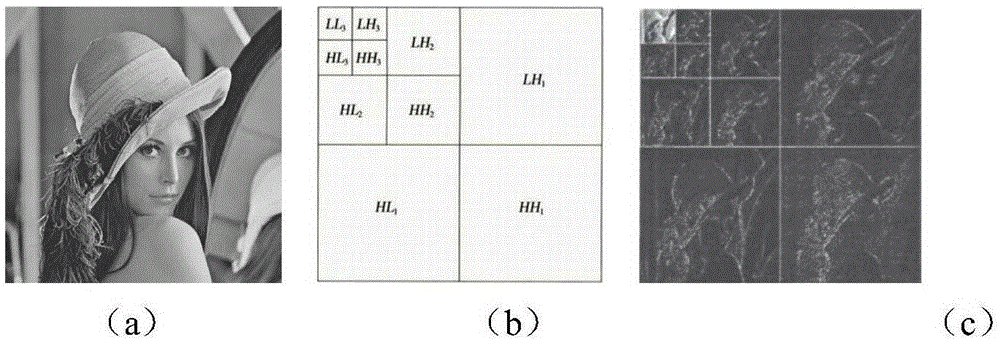
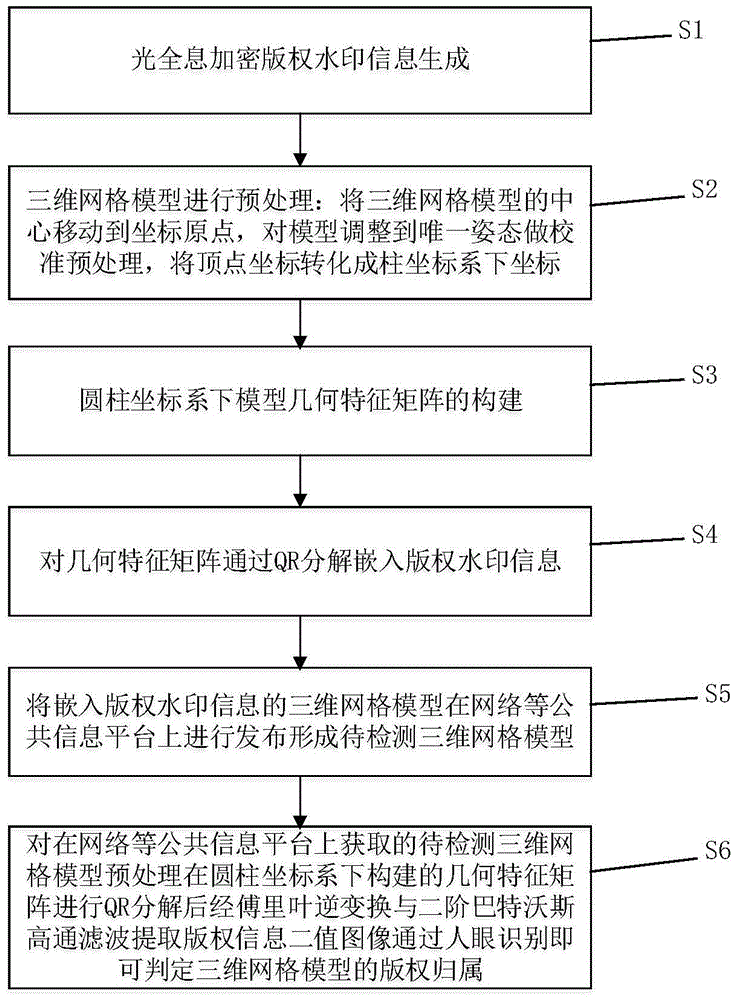
Three-dimension mesh model copyright verification method
InactiveCN104408338AAchieve copyright certificationImprove robustnessImage data processing detailsProgram/content distribution protectionQR decompositionThe Internet
The invention provides a three-dimension mesh model copyright verification method, which comprises the following steps that S1, light holographical encryption copyright watermark information is generated; S2, a three-dimension mesh model is preprocessed; S3, a model geometrical characteristic matrix is built in a cylindrical coordinate system; S4, the geometrical characteristic matrix is subjected to QR decomposition to embed copyright watermark information; S5, the three-dimension mesh model embedded with the copyright watermark information is issued on public information platforms such as Internet; S6, the obtained three-dimension mesh model to be detected is subjected to pre-processing for carrying out QR decomposition on the geometrical characteristic matrix to extract a copyright encryption information grey-scale map, a copyright two-value watermark image is obtained through Fourier inversion and filtering by a two-order Butterworth high pass filter, and the copyright ownership of the three-dimension mesh model can be judged through human eye identification. The method belongs to an air space blind watermark algorithm, higher robustness is realized, and the obvious problems that the existing three-dimension mesh model copyright verification method can be easily cracked and copied, and the copyright anti-fake certification cannot be conveniently or effectively carried out are solved.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Robust image watermark method based on local Tchebichef moment
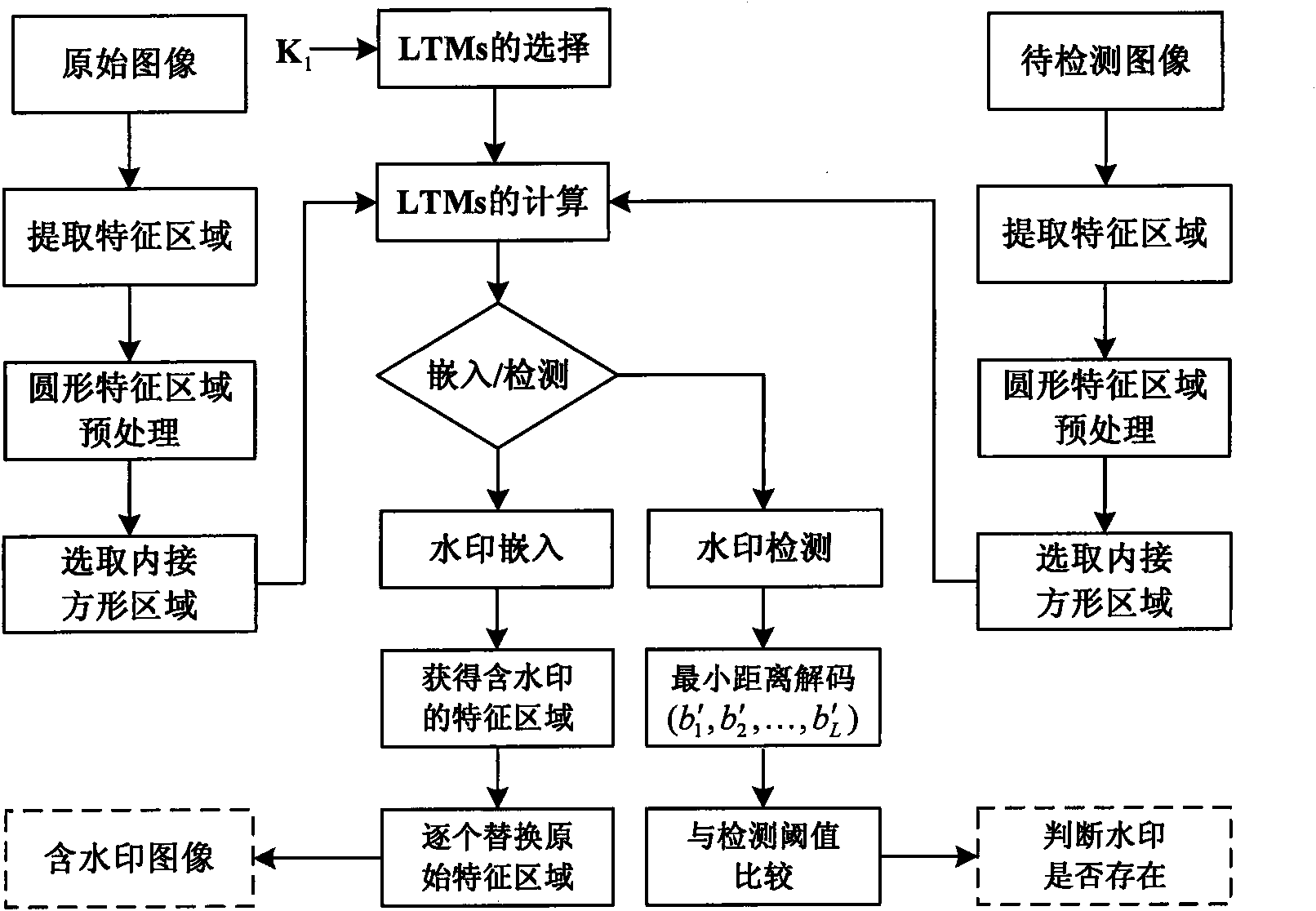
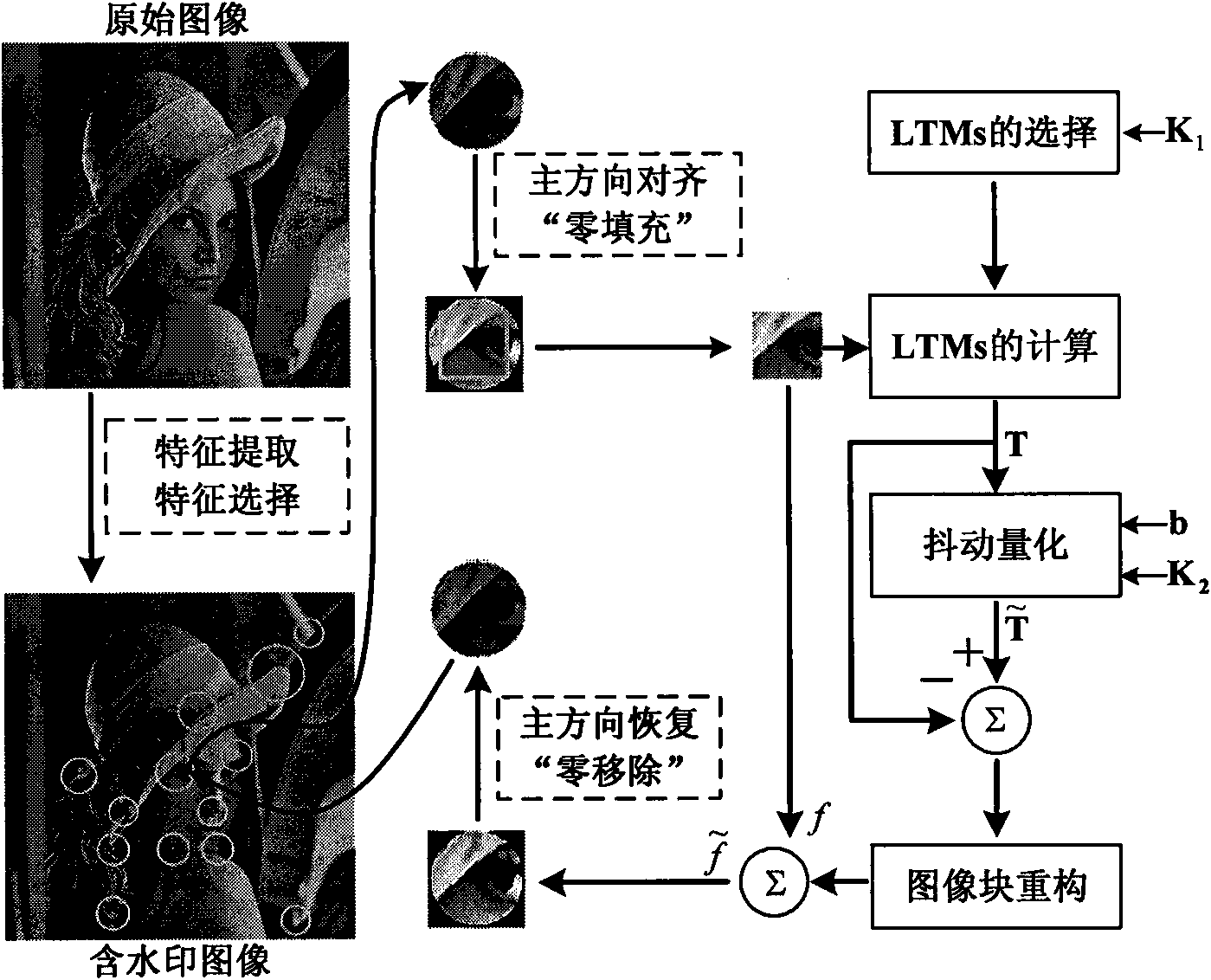
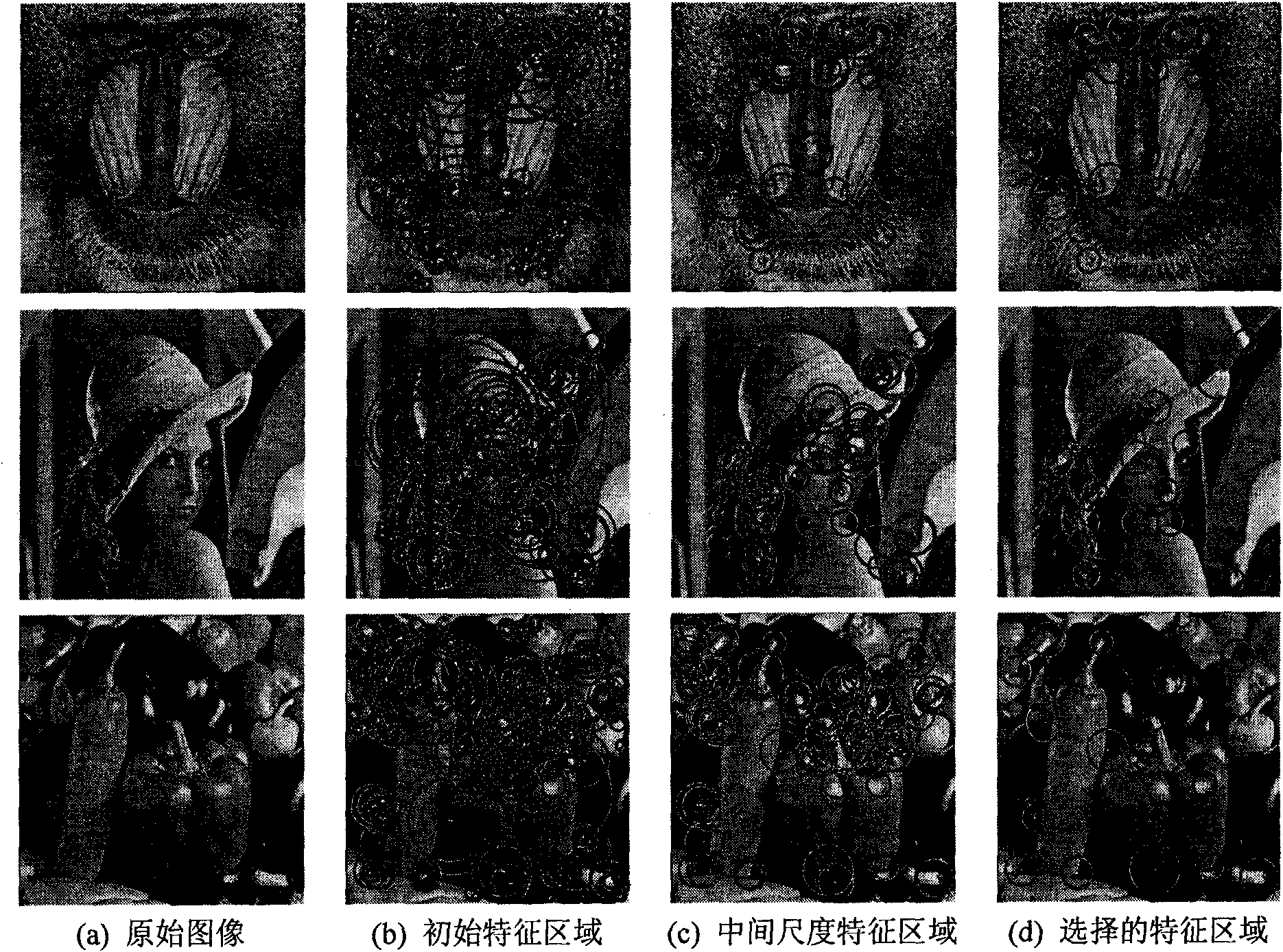
InactiveCN101556686AImprove detection accuracyOvercoming the problem of low detection rateImage data processing detailsImaging processingWatermark method
The invention discloses a robust image watermark new method based on a local Tchebichef moment, mainly solving the problem that a watermark arithmetic based on image characteristic at present can not effectively resist general image processing and geometry attack simultaneously. The method comprises the steps as follows: firstly, extracting characteristic points of an original image by utilizing a Harris-Laplace detection operator, and obtaining a group of stable and mutually independent round characteristic areas through characteristic selection; then obtaining a geometrically unchanged round characteristic area through principle direction alignment; and finally, calculating the Tchebichef moment in an inscribed square image block of the round characteristic area, and embedding a watermark through dithering quantized modulation to modify an amplitude value with low-level Tchebichef moment. In detection, the modified low-level Tchebichef moment is obtained through the dithering quantized modulation, and a minimum distance is utilized to realize the blind extraction of the watermark. The invention has favorable nonvisibility, excellent robust performance for general image processing, geometry attach and combined attach and superior performance to similar methods and can be used for copyright protection for different images.
Owner:XIDIAN UNIV
Method for implementing image digital watermark
InactiveCN101847249APost problem solvedPublic key for secure communicationUser identity/authority verificationEncryptionHuman language
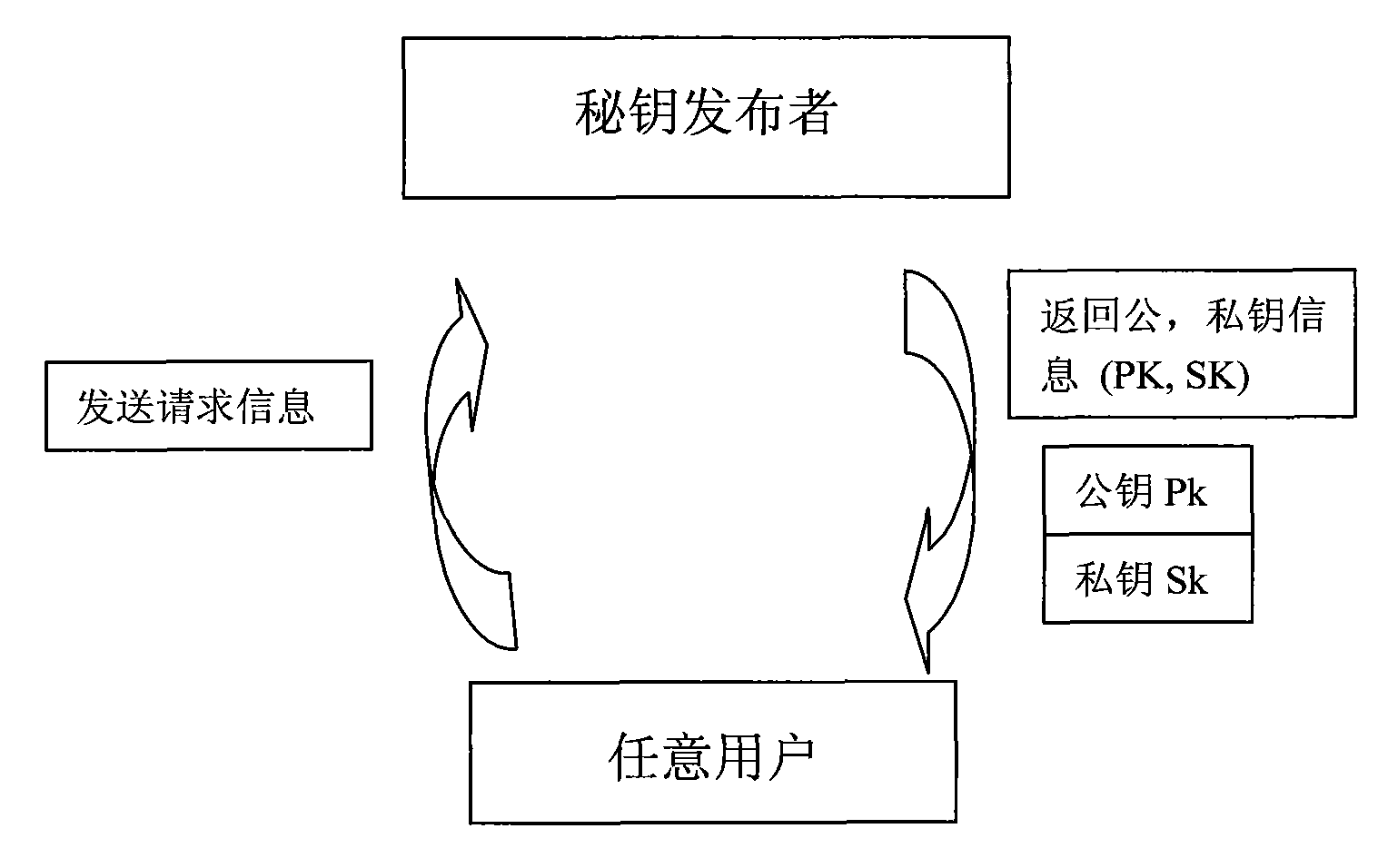
The invention discloses a technical scheme of image digital watermark encryption, which comprises the following steps of: acquiring a public key and a private key by a user, wherein the public key is used for performing signature verification on any other person obtaining an image, and the private key is used for signing and sealing the image; signing the information contained in the image by using the private key to obtain signature information D, signing a combination of a hash value of a data area B of the image and public key information C by using the private key to obtain a signature result D, and finally immigrating the public key information C and the signature result D into the image; and extracting the public key information C and the signature result D embedded into the data area B of the image by a basic watermark algorithm, and verifying the public key information C and the signature result D. According to the method, an ID-based signature system of an ID-based public key encryption algorithm is adopted, so the public key information can have linguistic meaning, and the release problem of the public key is correspondingly well solved.
Owner:SHANGHAI DETONG ENERGY & ENVIRONMENTAL PROTECTION TECH
Image digital watermark embedding method and image digital watermark detecting method
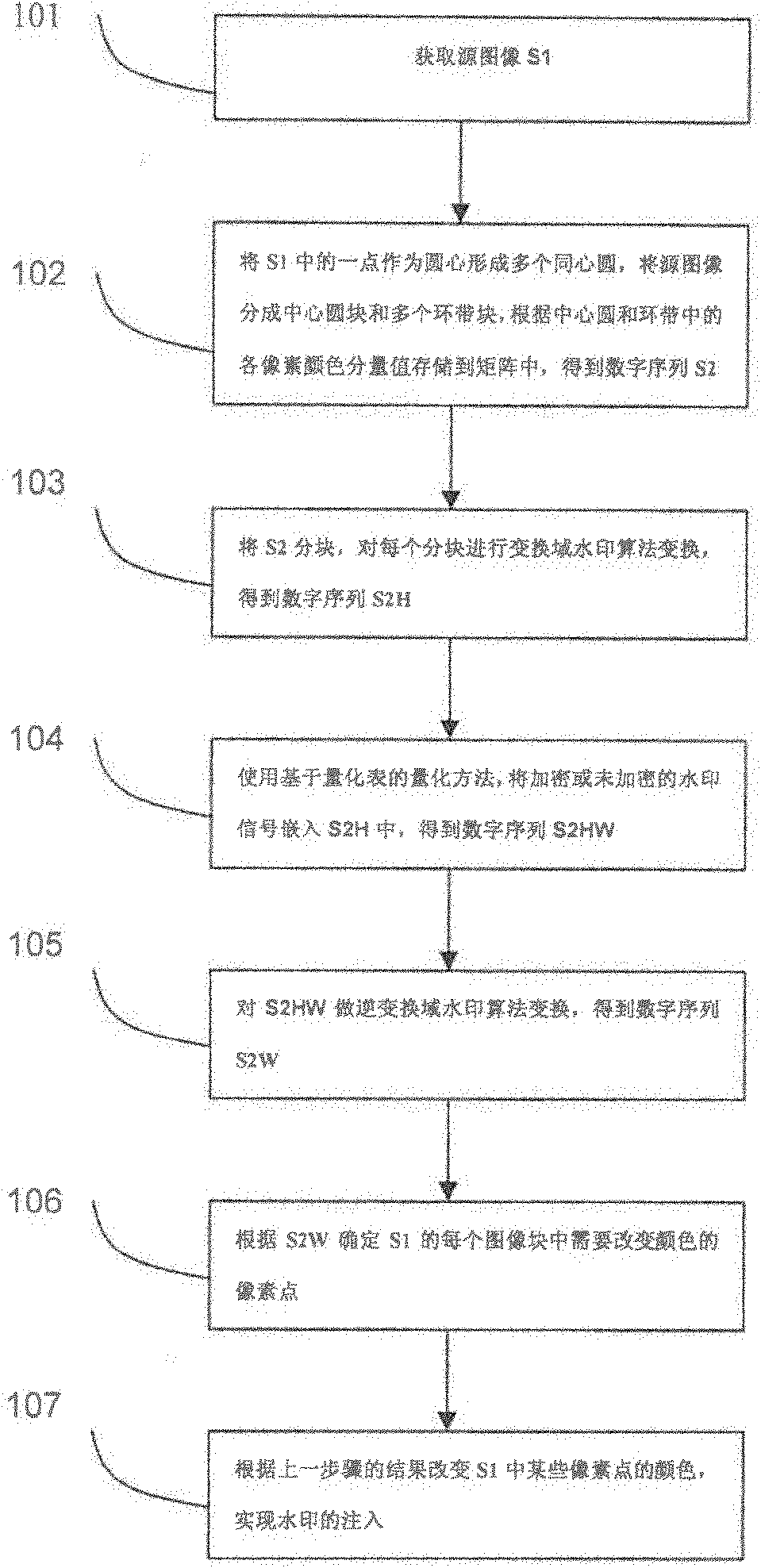
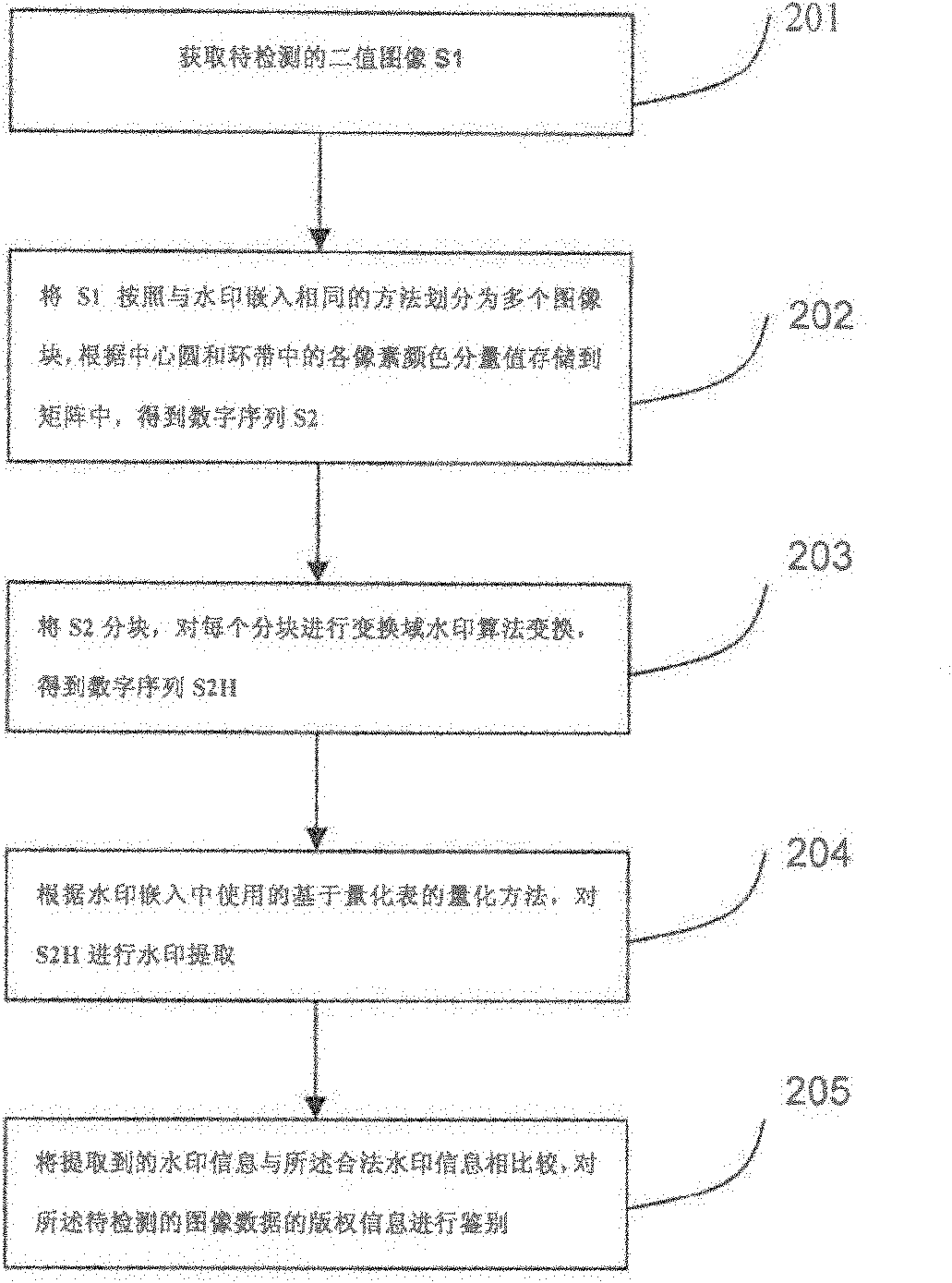
InactiveCN102609889AEasy to controlShort processImage data processing detailsSource imageLossy compression
The invention provides an image digital watermark embedding method and an image digital watermark detecting method. The watermark embedding method comprises the following steps of: dividing a source image into a center circular block and a plurality of ring belt blocks, and transforming each set of data by a transform domain watermark algorithm and embedding the image digital watermark into the source image; and the watermark detecting method comprises the following steps of: carrying out a blocking step which is as the same as the embedding process on an image to be detected, transforming by the same transform domain watermark algorithm, and extracting and comparing the watermark. After the watermark embedding method and detecting method of the invention are adopted, the technical problem that the common image digital watermark is bad in attack robust performance resistance and small in watermark information capability in the prior art can be solved, the rotation with any angles can be resisted, the zooming with larger times can be resisted, the geometrical transformation attack with larger edge cutting can be resisted, and the methods are easily combined with the other digital watermark technologies, so that the non-geometric transformation attack such as the channel noise, the filtering and the lossy compression can be resisted.
Owner:北京中盈信安科技发展有限责任公司
Time-domain digital audio watermarking method based on audio breakpoint
InactiveCN104810022AGood auditory characteristicsExcellent auditory characteristicsSpeech analysisTime domainAudio watermark
The invention provides a method for embedding and extracting digital audio watermarks in a time domain on the basis of audio breakpoints, and an energy value of an original audio is directly changed on the basis of the original audio according to a numerical value of watermark information and the energy value of the original audio. Only little change is made on the basis of an original signal, and good robustness, cutting resistance and less information increase of watermarks are guaranteed on the premise that the hearing quality of the original audio is not influenced. In a watermark extraction link, the positions of the embedded watermarks can be automatically screened by an extraction algorithm, information which looks like watermarks in numerical logic is excluded, and the capability of storing original watermark information is provided. According to the method, the watermark information is encrypted. The used watermark extraction scheme is a blind watermark algorithm and can be used for processing audio signals, protecting audio products and the like, only fragmentation information of the original audio and reconstruction parameters of watermark signals are needed, and the participation of the original audio and original watermarks is not needed.
Owner:NORTHEAST NORMAL UNIVERSITY
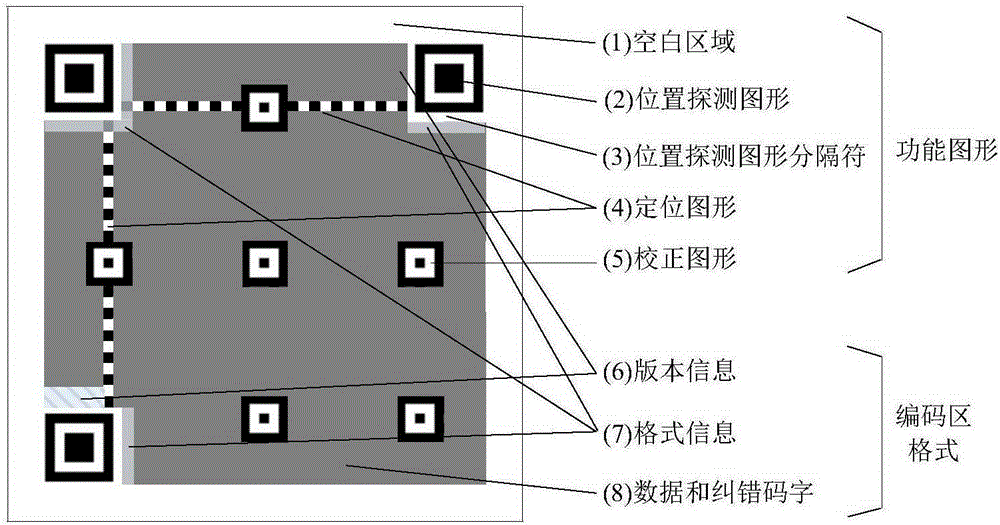
Video dual watermark method based on SVD and QR codes
ActiveCN105303512AImprove concealmentImprove securityImage data processing detailsAlgorithmWatermark method
The invention provides a video dual watermark method based on SVD and QR codes. The method comprises the steps of watermark embedding and watermark extracting. Watermark embedding comprises the steps of Arnold scrambling, original video preprocessing, grayscale watermark embedding, reconstructing, grayscale watermark text information QR coding and QR code embedding. Watermark extracting comprises the steps that a key1 is used to acquire a watermark carrier image; mark extracting and Arnold inverse scrambling are carried out; a key2 is selected, and the image block of the QR code is hidden; and the QR code is decoded to acquire verification text information. According to the invention, embedded dual watermarks have the advantage of small mutual interference and good robustness for common attacks; the QR code information is embedded into the image block which is highly invisible; the safety of a video watermark algorithm is enhanced; and the problem of single function of a single robust watermark algorithm is effectively solved.
Owner:深圳品阔信息技术有限公司
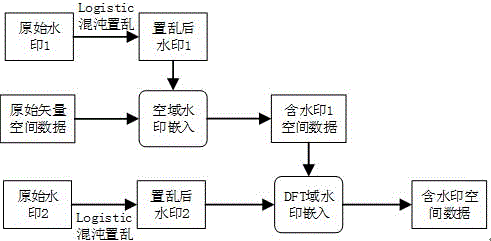
Space domain and frequency domain combined vector spatial data multi-blind watermarking method
ActiveCN104680472AOvercome the shortcomings of weak anti-attack abilitySmall embedding errorImage data processing detailsAlgorithmWatermarking attack
Digital watermarking is considered as an effective digital map copyright protection method. If a watermark has low robustness on a certain aspect, the watermark can be caused to be damaged or deleted, so that data protection can be lost. Currently, for a vector spatial data watermark, a vector spatial data watermark algorithm can be divided into a space domain watermark algorithm and a frequency domain watermark algorithm according to an embedded position of the watermark. However, most of the watermark algorithms adopt a single watermarking technology and each watermarking technology is realized on the basis of one algorithm routine. Vector spatial data adopt a single digital watermarking technology usually cannot resist to various different types of attacks. Aiming at the problem that the single watermark algorithm is difficult to resist to various watermarking attacks, the invention constructs a novel space domain and frequency domain combined vector spatial data multi-blind watermarking method. According to the method, by carrying out chaotic scrambling on a watermark image, a Hash one-way mapping function between the watermark and carrier data is established, and two different embedding methods are used and the watermark is sequentially embedded into a space domain and a frequency domain. The watermark is repeatedly embedded so as to implement blind extraction of the watermark.
Owner:LANZHOU JIAOTONG UNIV
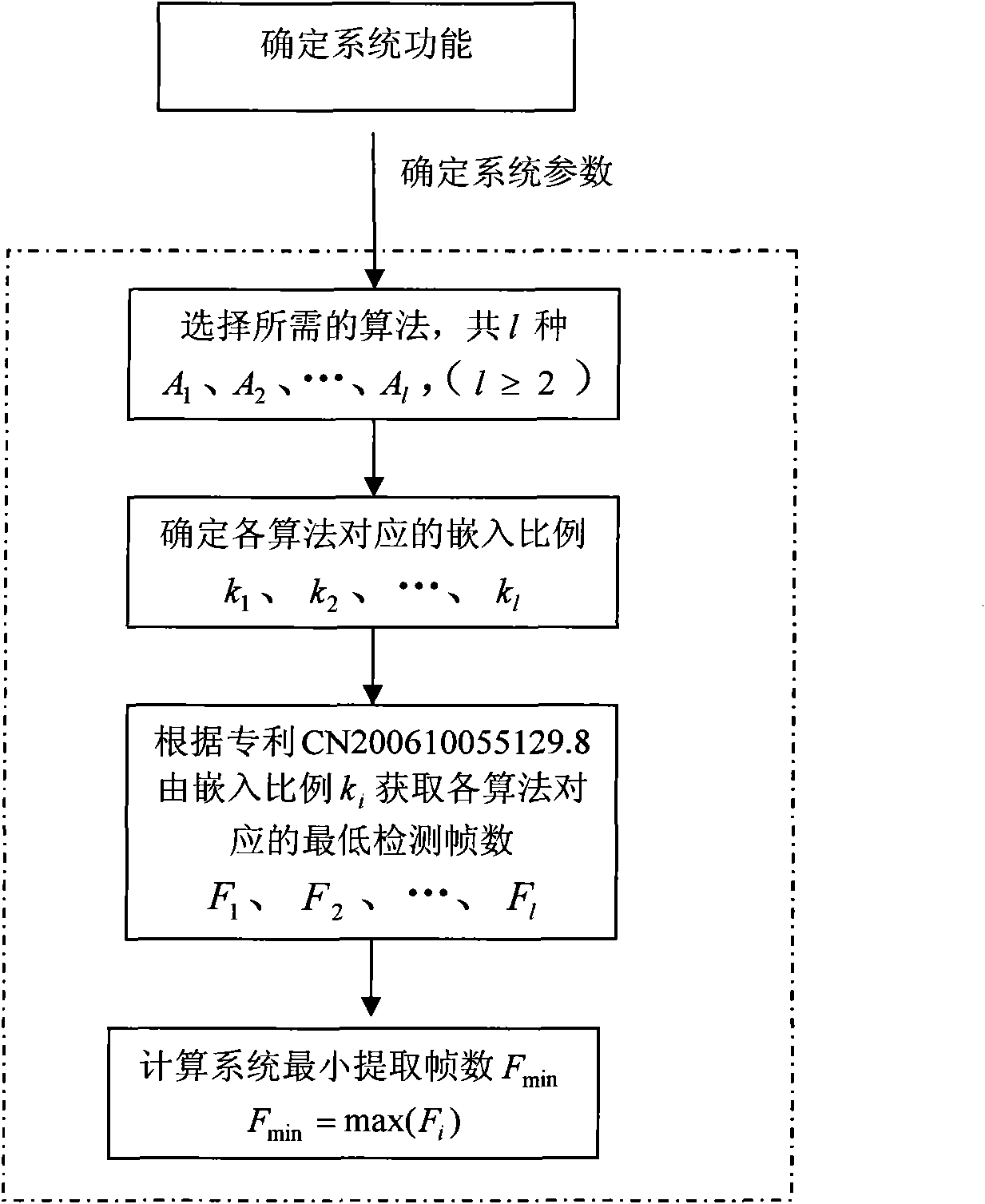
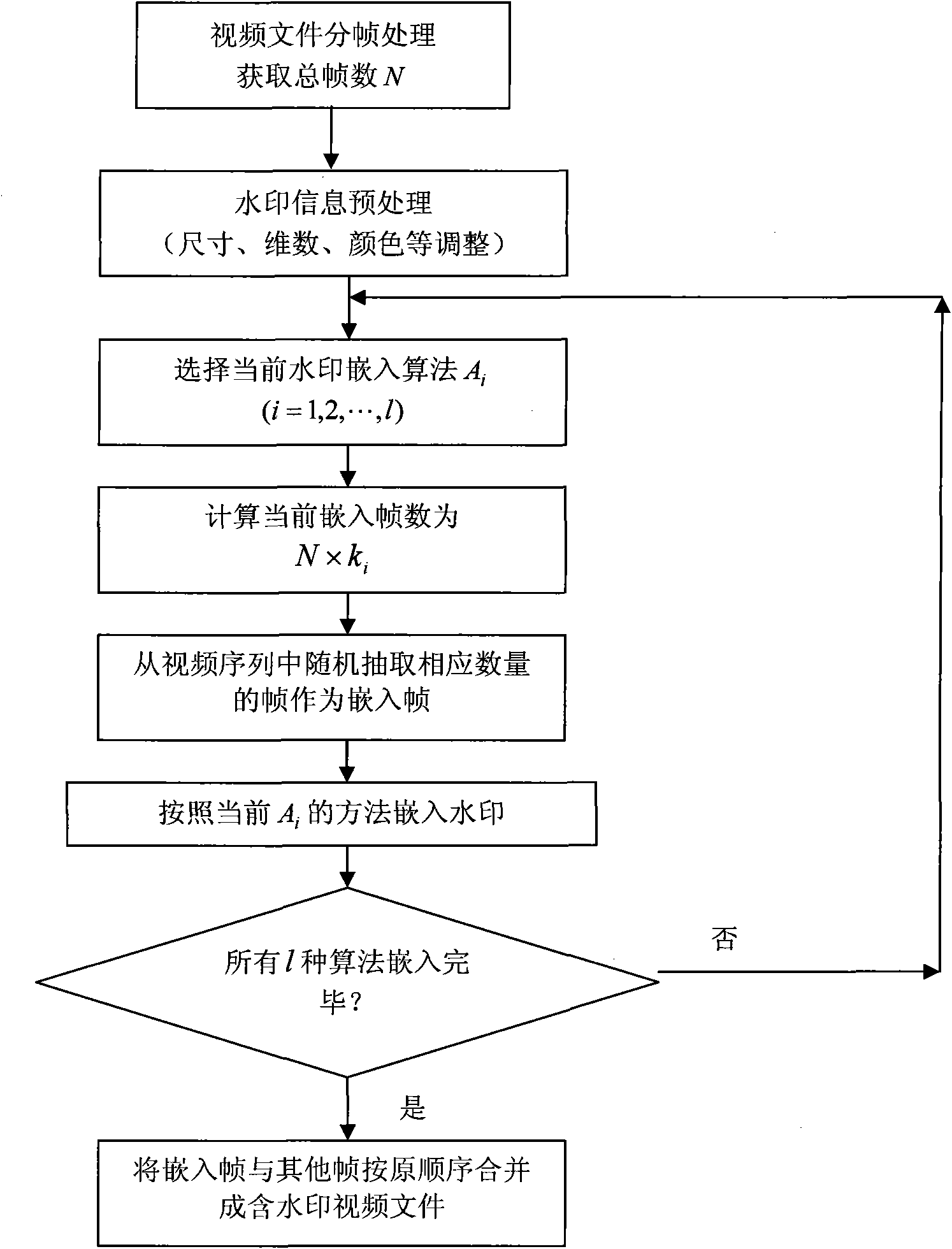
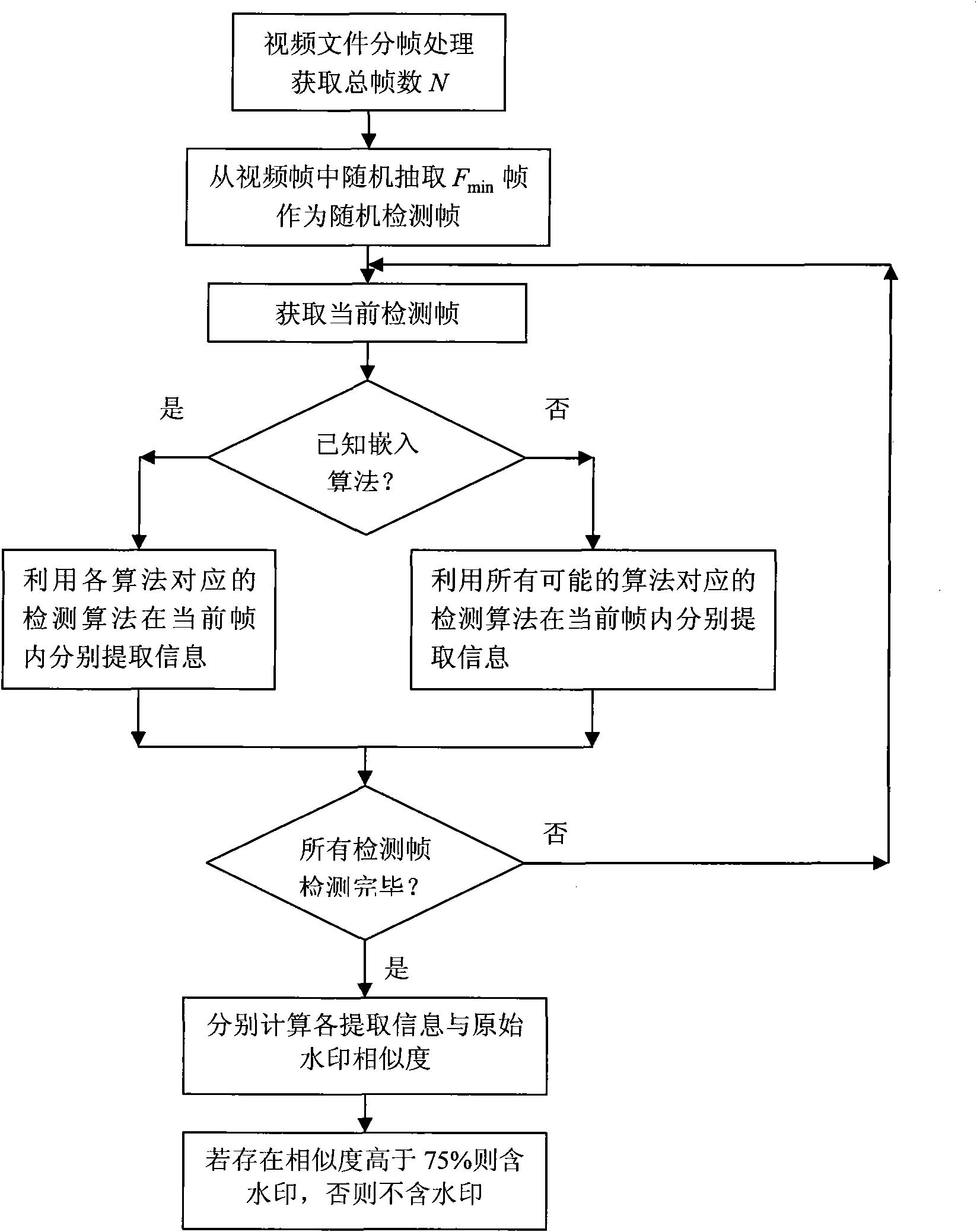
General video digital watermark method
InactiveCN101938618AImprove performanceFlexible adjustment of embedding ratioTelevision system detailsColor television detailsSystems designWatermark method
The invention discloses a general video digital watermark method mainly comprising analysis, embedding and extraction processes of a system design scheme. The analysis of the system design scheme comprises determination of a system function, watermark algorithms Ai to be embedded, embedding proportions of all algorithms and minimum extraction frame number Fmin; the watermark embedding process comprises frame distribution of a video file, watermark information pre-processing, embedding of watermark algorithms and formation of video files containing watermarks, wherein the embedding of watermark algorithms comprises the steps of: calculating embedding frame numbers, selecting embedding frames and embedding the watermark; and the watermark extracting process comprises frame distribution of the video file, selection of video frames to be detected, extraction of watermark information and calculation similarity. In the invention, the plurality of watermark algorithms are embedded at the same time and the embedding proportions can be selected, thereby the watermark method obviously enhances attack-resistant property; the watermark embedding ensures the appreciation and the embedding speed of the video file by using a non-frame-by-frame embedding way; in the watermark extracting process, the number of the detecting frames is less and the detection efficiency is improved; in addition, the general video digital watermark method also intensifies the capability of resisting frame edition.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Self-adapting watermarking algorithm of colorful image hypercomplex number spacing
InactiveCN101246588AImprove robustnessAvoid destructionImage data processing detailsPattern recognitionColor image
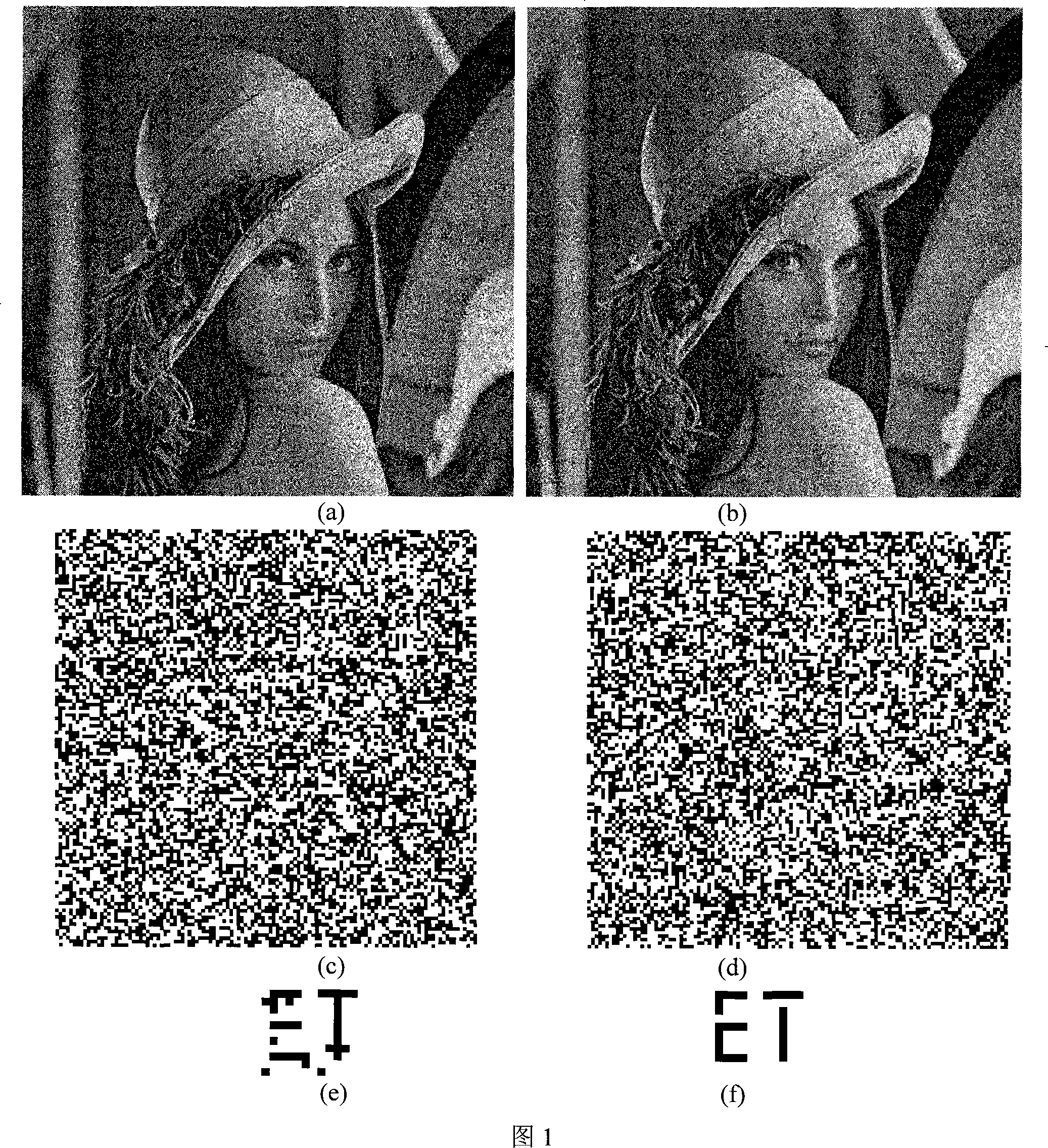
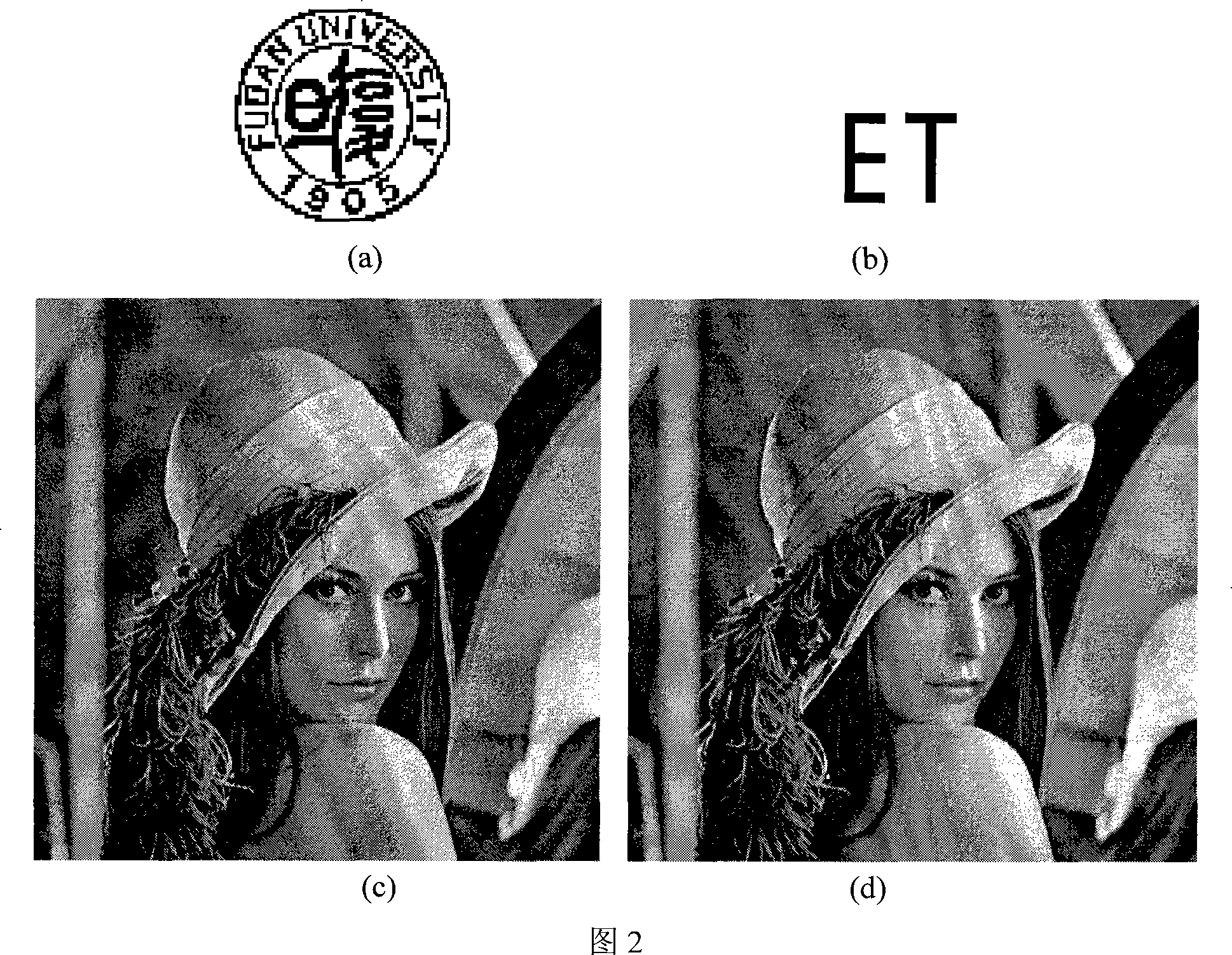
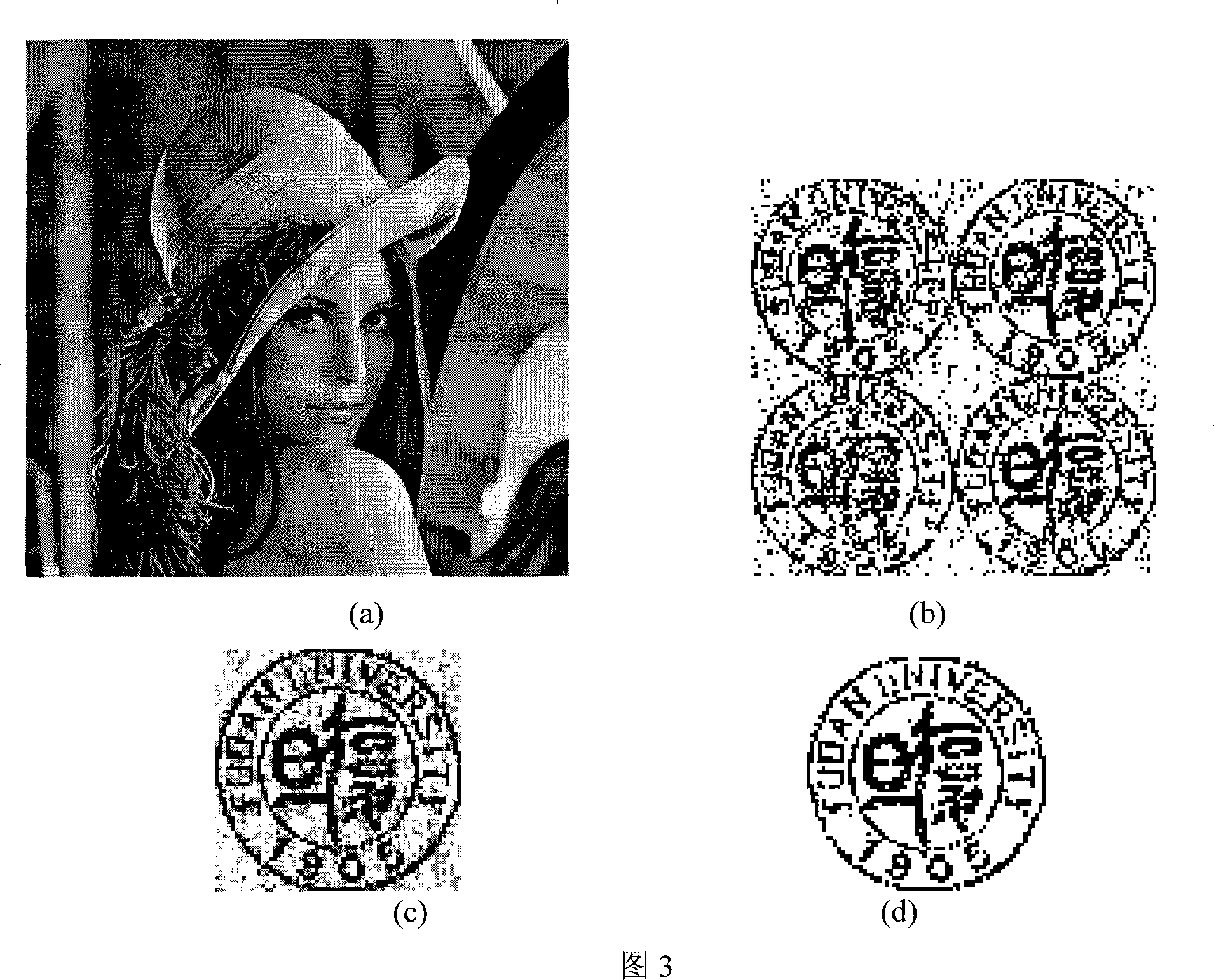
The present invention belongs to the image signal processing field, in particular a self-adapting watermark algorithm of a color image supercomplex frequency domain. Fistly, the algorithm processes a quick supercomplex Fourier transform to color carrier image, selecting proper frequency band in the supercomplex frequency spectrum real component, masking the vein, edge and brightness of the color carrier image by the human visual system, bestowing different masking intensities to the selecting frequency bands to embed watermark, achieving a self-adapting watermark algorithm of a color image supercomplex space. The result shows that the self-adapting masking of the color image greatly improve non intangibity and safety of the supercomplex frequency domain watermark algorithm, and having better aggressivity than the supercomplex frequency domain watermark algorithm having non-self-adapting mask; contrast to the present documents, the advantages of the invention are verified.
Owner:FUDAN UNIV
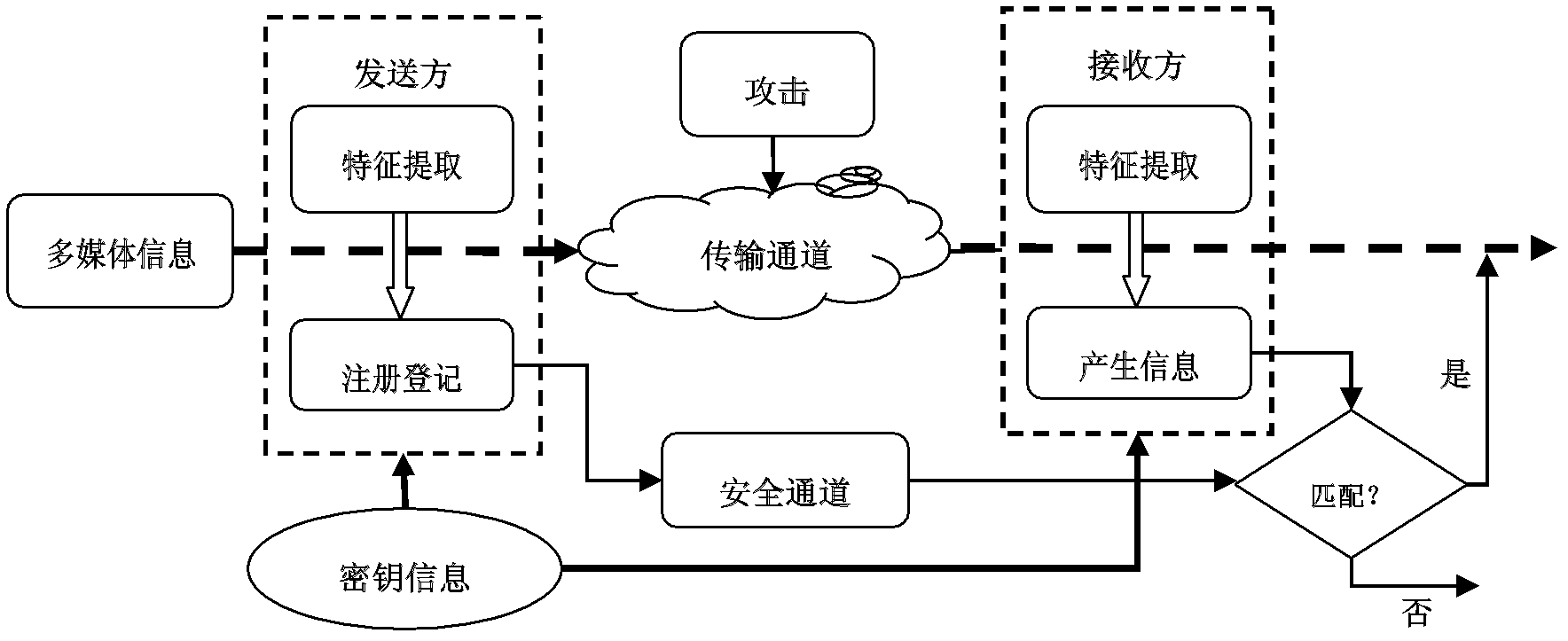
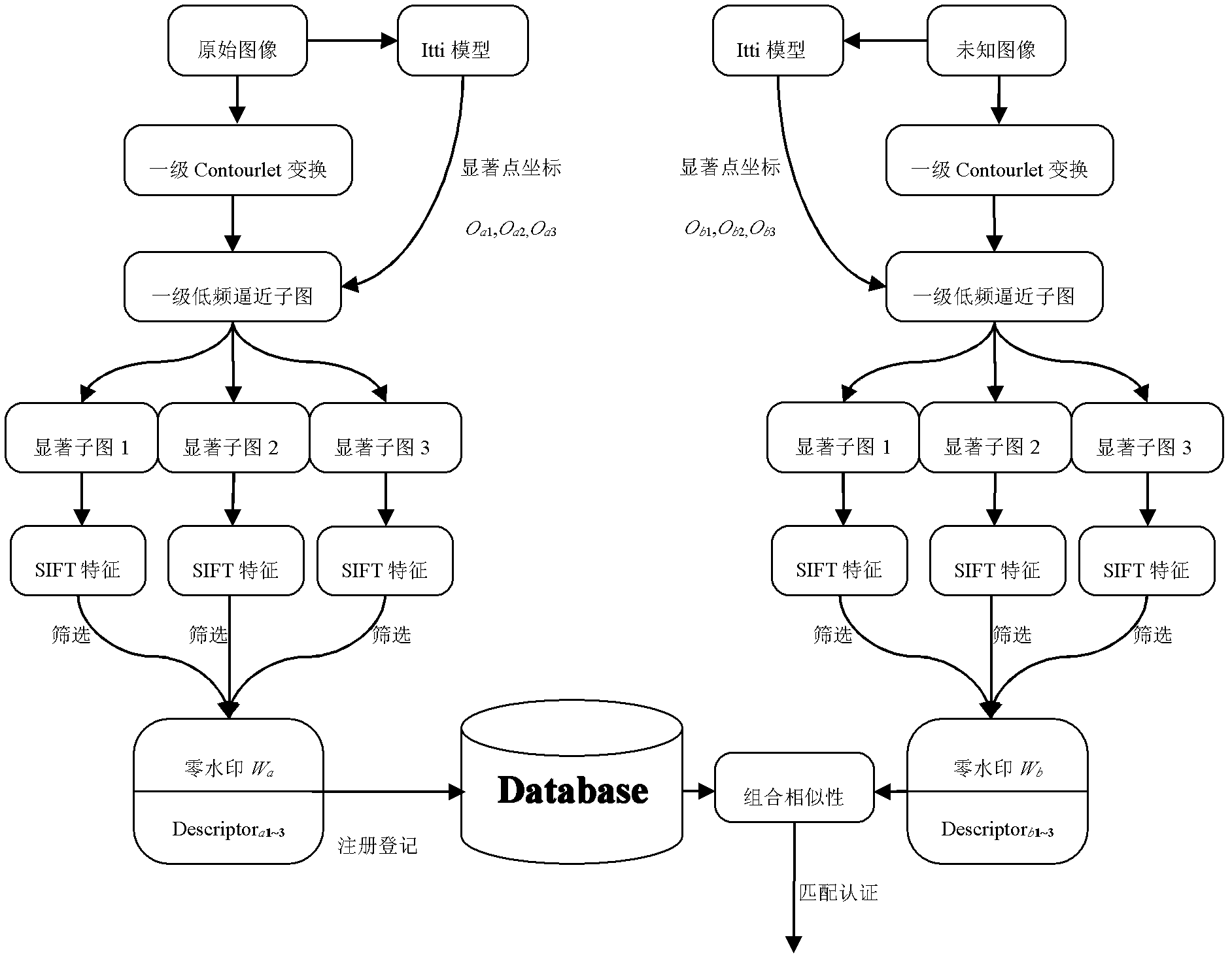
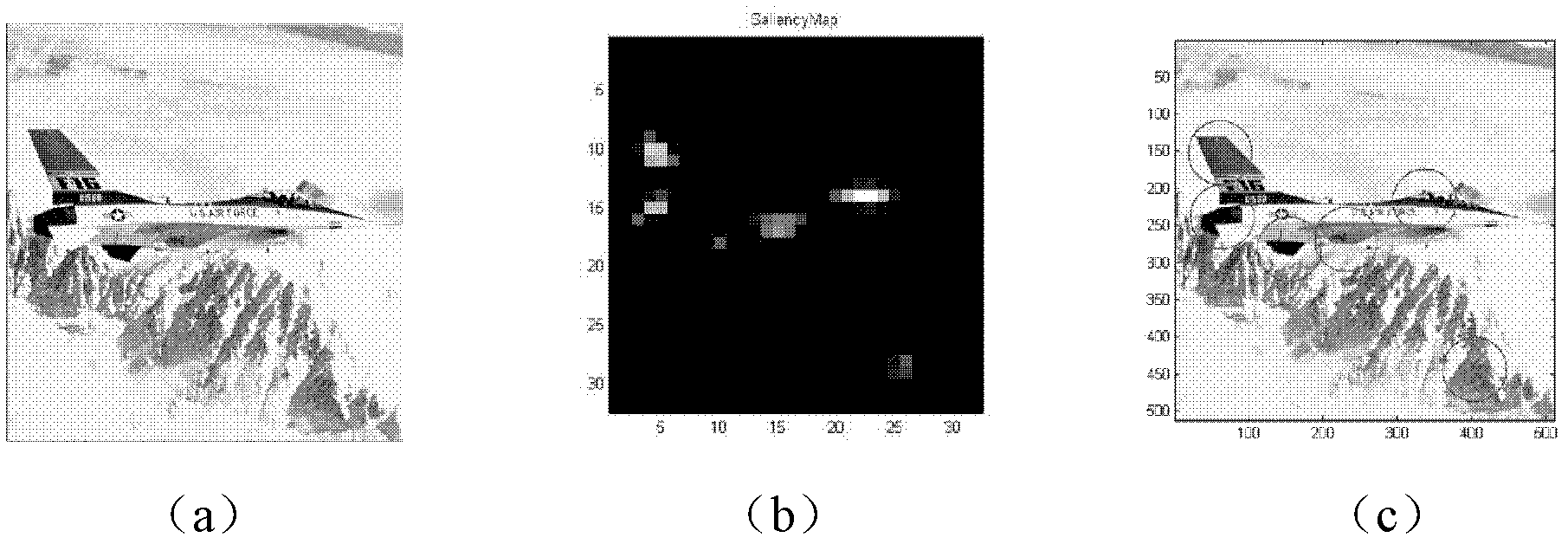
Visual-saliency-based image non-watermark algorithm and image copyright authentication method
The invention discloses a visual-saliency-based image non-watermark method and belongs to the technical field of information hiding. The visual saliency based image non-watermark algorithm is characterized by introducing a KochandItti visual attention mechanism model to automatically analyze and divide an image saliency region, executing SIFT (scale invariant feature transform) feature extraction on the image saliency region, further screening the extracted feature information, and registering the screened feature information as non-watermark information which identifies the image uniquely. The invention further discloses an image copyright authentication method based on the non-watermark algorithm. The algorithm has better robustness to synchronization attacks and regular image processing for moderate image geometric distortion, filtering, noise pollution and the like, thus providing a new way for protecting and authenticating copyright of digital images.
Owner:HOHAI UNIV
Three-dimensional geographic model digital watermarking method with copyright protection service orientation
ActiveCN103377455AImprove resistance to attackImprove robustnessImage data processing detailsAlgorithmData file
The invention discloses a three-dimensional geographic model digital watermark embedding and detection method, and belongs to the technical field of geographic information copyright protection. The method is based on that a texture coordinate value of three-dimensional geographic model data after an attack is changed without a variation in a data value of corresponding texture mapping. Thus, the method, on the basis of analysis of a previous watermark algorithm and by making full use of characteristics of texture mapping, re-establishes an embedding position of a watermark and builds a new digital watermarking model of the three-dimensional geographic model data. Not only is a three-dimensional grid data file of a three-dimensional geographic model embedded, but also a data file of the texture mapping is embedded with the watermark information. The problems are solved that a single geographic model algorithm is low in robustness for some attacks and that a current three-dimensional geographic model data file with texture mapping data cannot detect a watermark after a file attack and a model attack.
Owner:NANJING JIYIN INFORMATION TECH
Image digital watermarking algorithm system on basis of texture complexity and JND (just noticeable difference) models
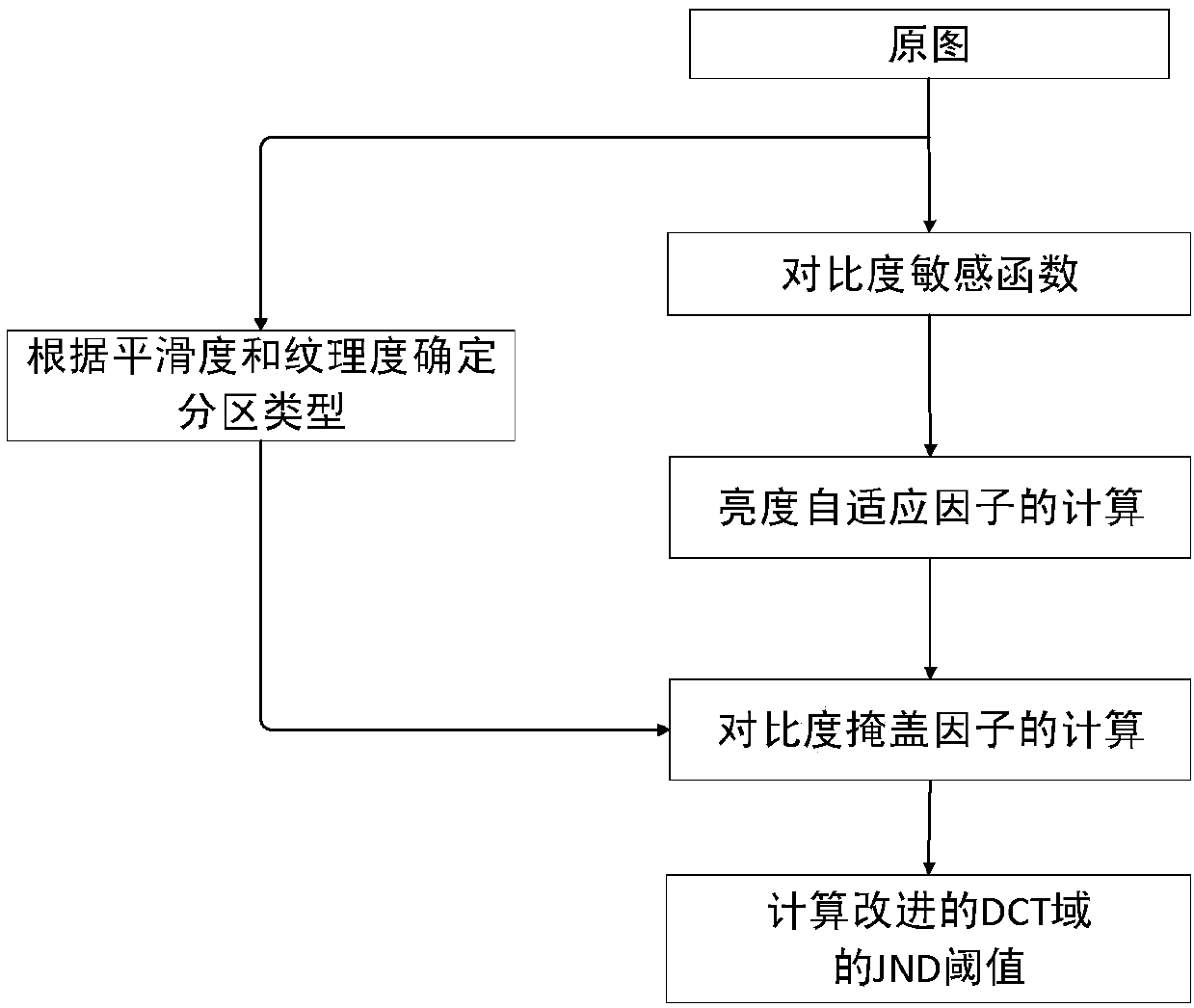
ActiveCN108280797AExpand watermark embedding capacityImprove accuracyImage analysisImage data processing detailsHuman eyeDiscrete cosine transform
The invention discloses an image watermarking algorithm. Texture complexity and just noticeable difference (JND) models in discrete cosine transform (DCT) domains are combined with one another by theimage watermarking algorithm. The image watermarking algorithm includes segmenting original images into sub-blocks; computing the texture complexity of the sub-blocks by the aid of four texture features of a gray-level co-occurrence matrix of the various sub-blocks; sorting the sub-blocks on the basis of the texture complexity to determine locations of the sub-blocks with embedded watermarks and then carrying out DCT on pixel matrixes of the original images; computing JND values of various blocks by the aid of new partition modes; determining embedding modes for the watermarks in the sub-blocks according to the JND values and new embedding rules. The image watermarking algorithm has the advantages that texture features of image blocks and the vision sensitivity of human eyes are effectively considered, accordingly, the quality of images with the embedded watermarks can be improved, and the watermark embedding capacity can be expanded.
Owner:JIANGXI UNIV OF SCI & TECH
Feature invariants based remote sensing image watermark method
InactiveCN105761197AImprove robustnessLarge amount of stored informationImage data processing detailsProgram/content distribution protectionPattern recognitionImaging processing
The invention discloses a feature invariant based remote sensing image watermark method which is directed at overcoming the incompatibility between anti-geometric attack and anti common image processing attack of the DCT algorithm and at the same time fully exhibits the advantages of 2D code, such as large storage information amount and strong error correction. The method includes the following steps: looking for invariants in 8 x 8 subblocks converted by the DCT algorithm, calculating embedded watermark information bits by using a mapping function in combination with the invariants, marking an initial position of each 8 x 8 subblock with intermediate frequency coefficients. In the process of watermark detection, image blocks containing watermark information can be located in a rapid and accurate manner through the determination of a feature location region. According to the invention, features of pixel digital numbers of remote sensing images before and after the geometric attack are fully utilized to address the problem of desynchrony of watermark information, which substantially increases robustness of the DCT algorithm, addresses the problem of inability of current remote sensing image digital watermark algorithm to resist cropping attacks, and effectively protects copyright of remote sensing image data.
Owner:NANJING NORMAL UNIVERSITY
Two-color image blind watermarking method based on Hessenberg disintegration
The invention discloses a color image blind watermarking method. A color digital image is used as a digital watermark to be inserted in a color host image by utilizing Hessenberg matrix disintegration, and the inserted color image watermark is good in invisibility, so that the requirement for protecting a copyright based on a color image marker can be met. A 4*4 pixel block is disintegrated in a Hessenberg way, the encrypted color image digital watermark information is inserted into a maximum coefficient of the Hessenberg matrix by utilizing a coefficient quantization technology, the original host image or the original watermark image is not needed when the watermark is extracted, and a blind detection object can be realized. The method is good in watermark algorithm performance and suitable for the copyright protection adopting the color digital image as the digital watermark.
Owner:LUDONG UNIVERSITY
Vector map data blind watermarking method based on DCT transformation
ActiveCN101847250AImprove robustnessGood practical valueImage data processing detailsComplex mathematical operationsInformation embeddingVector map
The invention discloses a vector map data blind watermarking method based on DCT transformation. The conventional watermarking algorithm is difficultly applied directly on vector map data. The method comprises watermark information embedding and watermark information extraction. In the watermark information embedding step, the watermark information selected by a user is embedded into an original vector map to obtain a new vector map, and the step specifically comprises modulating the watermark information, processing the vector map data in different blocks and embedding the watermark information. In the watermark information extraction step, watermark information contents are extracted from a vector map to be detected, and the step specifically comprises processing the vector map data to be detected in different blocks, extracting the watermark information and generating a watermark information graph. The method has better robustness, and is a blind detection algorithm with better practical value.
Owner:新沂高科信息科技有限公司
Security watermark algorithm combining cryptography
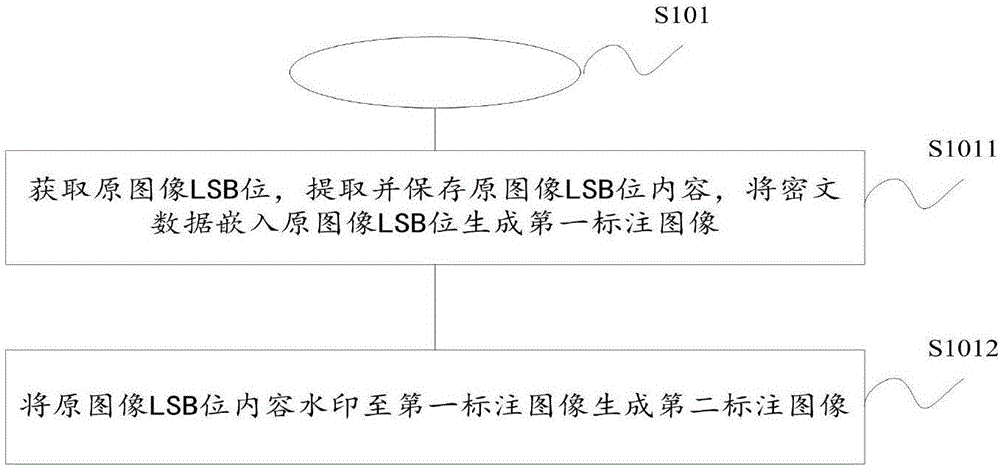
The invention mainly aims to solve the security attack problem of watermarks, and provides a high-security watermark algorithm by further referring to an encryption mechanism and a dual-watermark mechanism on the basis of making full use of a password thought and a theory of error-correcting codes specific to different security attack characteristics. In the algorithm, a watermark embedding link is partitioned into a private watermark embedding part and a public watermark embedding part. Private watermarks are embedded through an adaptive spatial domain watermark algorithm; original watermarks are encrypted by further referring to a carrier feature sequence on an information layer; error correction coding is performed on an encrypted sequence through Hamming error correcting coding in order to cope with copy attacks; and watermark embedding positions and embedding strengths are encrypted on a transmission layer in order to cope with homologous detection attacks. Public watermark embedding is finished through an adaptive watermark algorithm which has high robustness and is based on DCT (Discrete Cosine Transform), so that detection of collusion attacks can be realized. As proved by a test result, the problem of security attacks to the watermarks can be well solved.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
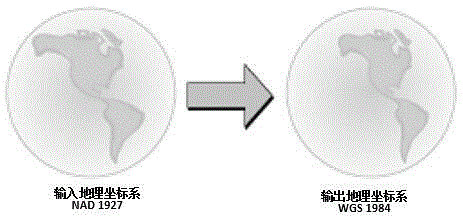
Vector space data blind watermark method resistant to projection attack
The invention, specific to the defects of an existing vector geographic space data digital watermarking method, provides vector space data watermark algorithm resistant to projection transformation and a coordinate transformation attack effectively. The method fully takes account of the features of the projection transformation and coordinate transformation of a vector space data, in the watermark embedding scheme, an original vector space data is converted below a WGS84 geographic coordinate system firstly, then a DFT domain watermark algorithm is applied, the watermark is embedded into a WGS84 coordinate system space data, finally, the WGS84 coordinate system space data containing the watermark is converted into the original data coordinate system. When the watermark is extracted, after the vector space data is converted to the WGS84 coordinate system, then the watermark information is extracted. The experimental results indicate that the watermark scheme has good robustness for the projection transformation and the coordinate system transformation attack, and has relatively strong robustness for the attacks of data such as clipping, rotation, translation and the like.
Owner:LANZHOU JIAOTONG UNIV
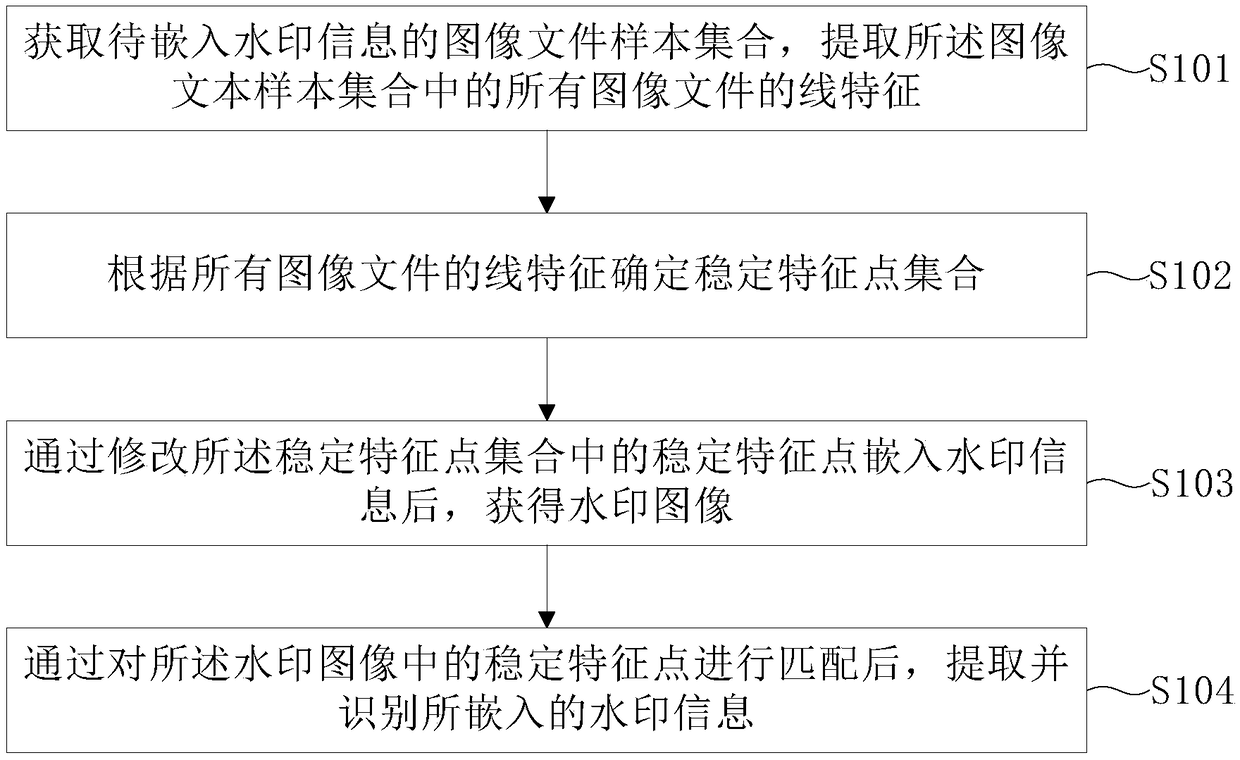
Image feature matching-based watermarking method and apparatus
ActiveCN108711131AImprove practicalityImprove robustnessImage data processing detailsComputation complexityImage resolution
Embodiments of the invention provide an image feature matching-based watermarking method and apparatus. The method comprises the steps of acquiring an image file sample set of to-be-embedded watermarkinformation, and extracting line features of all image files in the image file sample set; determining a stable feature point set according to the line features of all the image files; after the watermark information is embedded by modifying stable feature points in the stable feature point set, obtaining a watermark image; and after the stable feature points in the watermark image are matched, extracting and identifying the embedded watermark information. According to the method, the watermark information is embedded by modifying the stable feature points, so that the embedding of the watermark information no longer depends on a watermark font library, and the implementation process is simpler; the watermark algorithm is better in robustness, can resist the attack of zooming and unequalresolution, and is widely suitable for identification of the watermark information in images shot by equipment such as a digital camera, a mobile phone or the like; and feature information-based imagematching is adopted, so that the calculation complexity of watermark information extraction and identification is lower.
Owner:北京数科网维技术有限责任公司
Image retrieval method and system
The invention discloses an image retrieval method and system. The method comprises the steps that an original image is embedded after annotation information is encrypted into ciphertext data, and substituted original pixels are used as a watermark generation annotation image through a reversible watermarking algorithm; and the ciphertext data in the annotation image is extracted and decrypted, the decryption result is matched with retrieval conditions to acquire a target annotation image, a pixel value of the original image corresponding to the target annotation image is calculated, and a watermark is output after being extracted. The algorithm has a small influence on the original image, and the original image can be restored in one hundred percent at a receiving end; meanwhile, the algorithm is high in speed and adaptive to a large quantity of sample annotation scenes, so that space complexity is lowered; the encrypted annotation information is prevented from being tampered, and therefore the validity, relevancy and manageability of the annotation information are improved.
Owner:开易(北京)科技有限公司
Digital watermark algorithm based on text document protection
ActiveCN107688731AStrengthen copyright protectionImprove robustnessImage analysisImage data processing detailsComputer graphics (images)Documentation
The invention discloses a digital watermark algorithm based on text document protection. Implementation of watermark information in a text document consists of watermark embedding and watermark extracting; a watermark embedding treatment process comprises carrier text image pretreatment, ciphertext ID coding, pseudo-random periodic sequence watermark generation and carrier image fusion; and the watermark extracting treatment process comprises image reinforced treatment, extraction of a pseudo-random sequence watermark texture map and decoding of watermark information. For solving the technicalproblem that an existing digital watermark algorithm is poor in robustness, required ID information can be embedded in a text document by the algorithm, and even if a watermarked text is copied, photographed and sheared and the geometric structure of the watermarked text is damaged, watermark information concealed in the watermarked text can still be detected. The digital watermark algorithm based on text document protection can be widely applied to protection and tracing of documents with secret, document copyright protection, web page copyright protection, image mark protection of some commercial products and the like.
Owner:ANHUI ZHONGXIN SOFTWARE
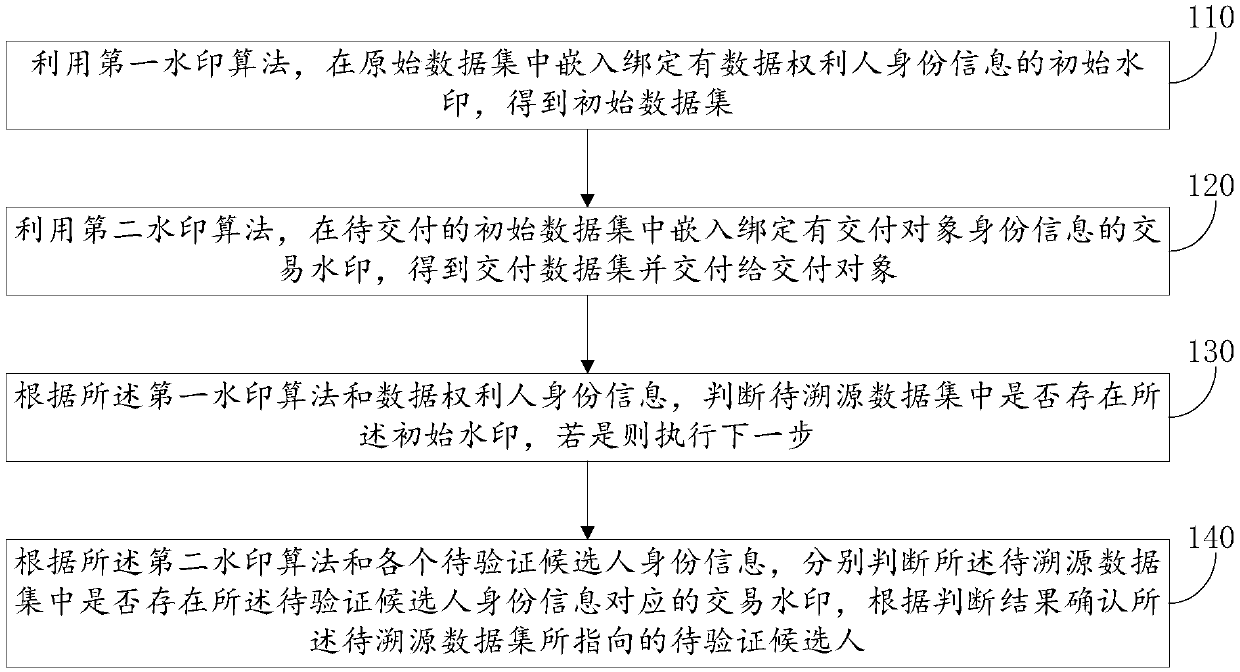
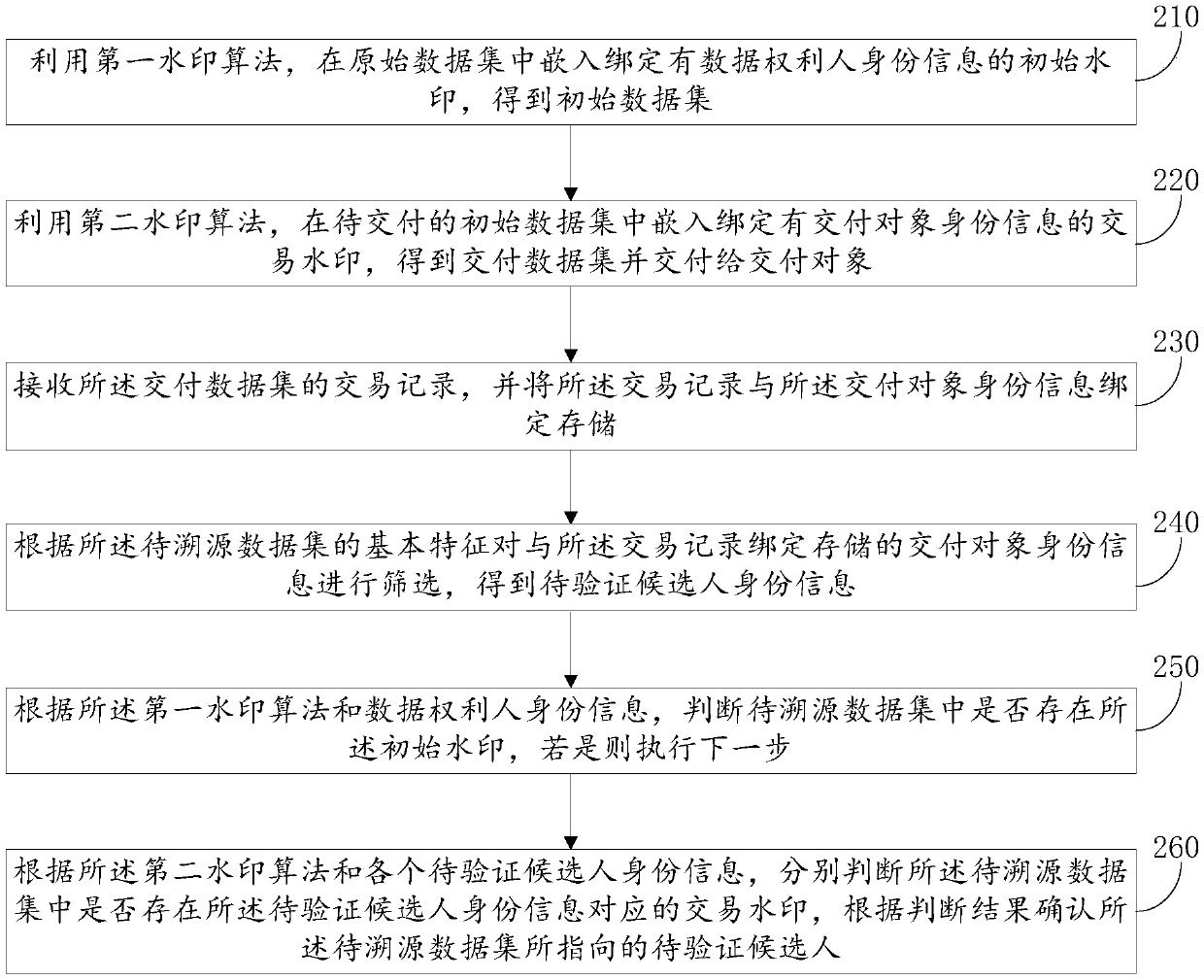
The invention discloses a dData tracing method and system based on a digital watermarking technology
The invention relates to a data tracing method and system based on a digital watermarking technology, and the method comprises the steps: employing a first watermark algorithm, embedding an initial watermark in an original data set, and obtaining an initial data set; E; embedding a transaction watermark into the initial data set to be delivered by utilizing a second watermark algorithm to obtain adelivery data set and delivering the delivery data set to a delivery object; J; judging whether initial watermarks exist in the to-be-traced data set or not, if yes, judging whether transaction watermarks corresponding to the identity information of the to-be-verified candidates exist in the to-be-traced data set or not, and confirming the to-be-verified candidates pointed by the to-be-traced data set according to a judgment result. According to the invention, t, the initial watermark and the transaction watermark are embedded into the data circulated by the data obligee; I; in the data rights protection stage, rights protection audit is conducted on a data obligee through an initial watermark, declaration of a membership right is achieved, t, then in the further data tracing stage, a delivery object pointed by a to-be-traced data set is confirmed through a transaction watermark, and therefore tracing of a leakage source is achieved.
Owner:BEIJING SANSEC TECH DEV
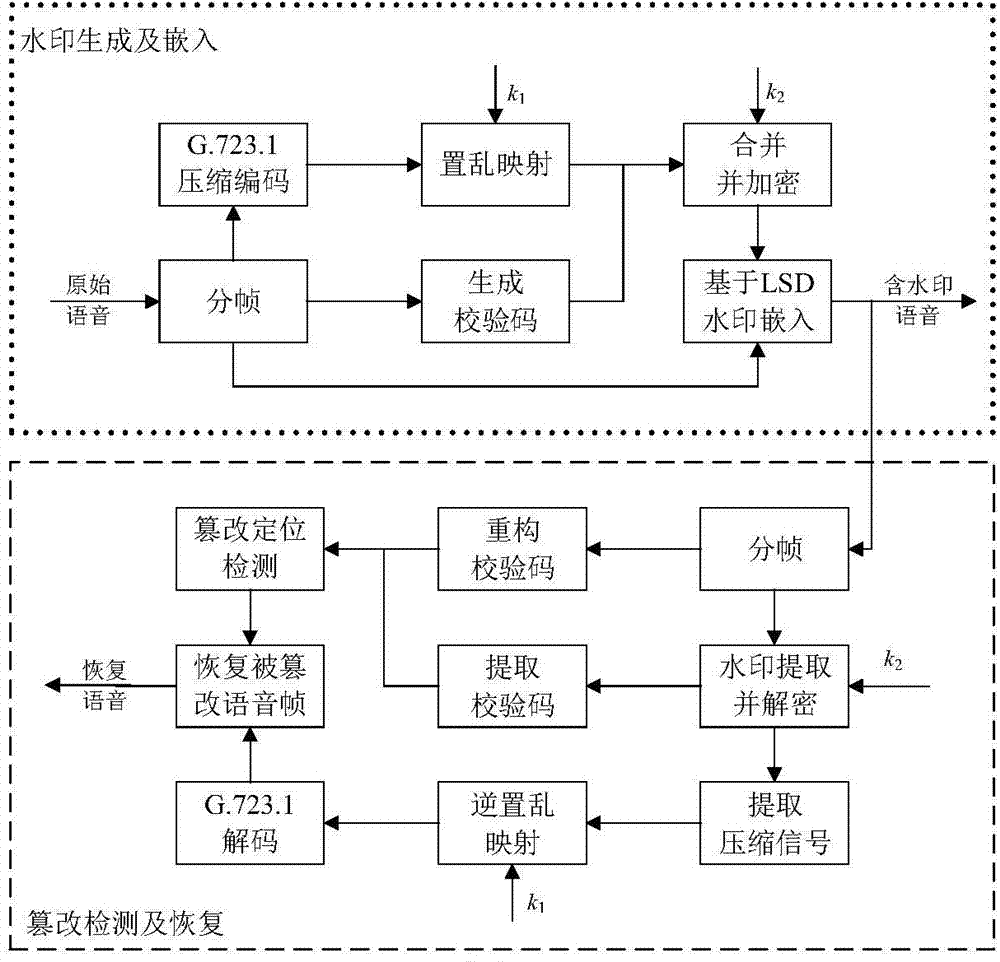
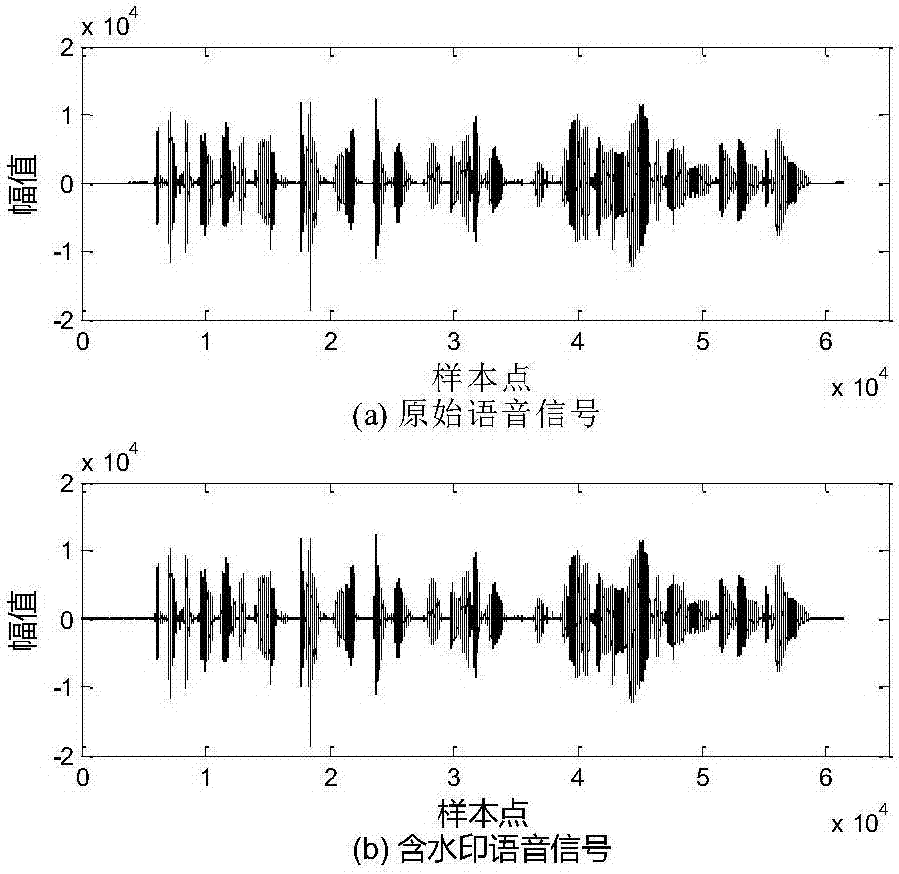
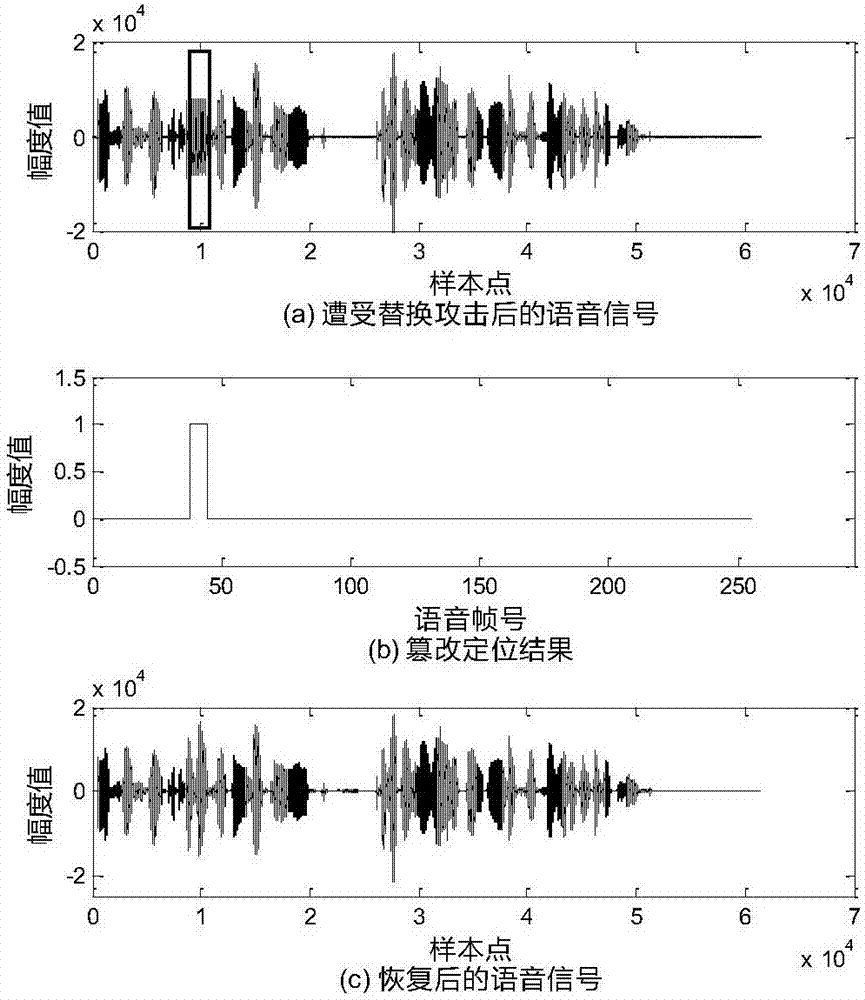
Speech content authentication and tamper recovery method based on modifying least significant digit weight
The invention discloses a speech content authentication and tamper recovery method based on modifying a least significant digit weight. On the basis of characteristics of a speech signal as well as asensitive position, namely least significant digit, of speech, a novel speech fragile watermarking algorithm is designed; and the method comprises the fragile watermarking algorithm based on modifyingthe least significant digit weight of a speech sampling point, a watermark generating and embedding part based on speech contents, and a speech content authentication and recovery part. In comparisonwith an existing speech content authentication watermarking algorithm, the method provided by the invention achieves full use of such characteristics of a speech coding technology, speech sampling point least significant digit weight sensitivity and the like, so that the sensitivity and fragility of the method to tamper attack are guaranteed, and meanwhile, effective recovery of a tampered regionin the case of tamper is also guaranteed; therefore, the invention is conducive to promotion and application of the method.
Owner:SOUTHWEST JIAOTONG UNIV
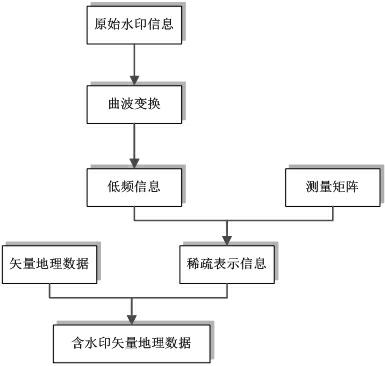
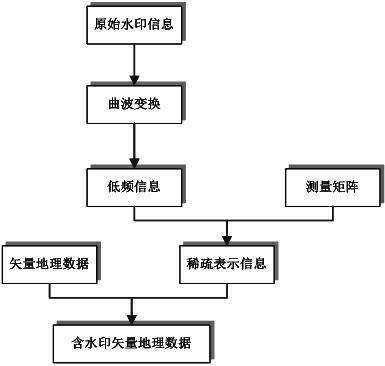
Compressed-sensing-based vector geographic data watermark information generation method
InactiveCN102682417AImprove adaptabilityImprove securityDigital data protectionImage data processing detailsSmall dataCompressed sensing
The invention discloses a compressed-sensing-based vector geographic data watermark information generation method. The method comprises the following steps of: establishing a sparse representation method of vector geographic data watermark information on the basis of a compressed sensing theory, designing a measurement matrix and a constraint condition thereof for the sparse representation of the watermark information, constructing a spare representation model of the watermark information, and reconstructing extracted watermark information. By the method, the sparsity of the vector geographic data watermark information is fully utilized, and the problems of limitation to watermark information capacity and incapability of embedding watermark information in a small data volume are solved, so that the security and adaptability of a vector geographic data digital watermark algorithm are improved.
Owner:CHANGSHU NANJING NORMAL UNIV DEV RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com