Speech content authentication and tamper recovery method based on modifying least significant digit weight
A minimally effective, voice content technology, applied in voice analysis, instrumentation, etc., to solve problems such as low compression efficiency, poor quality of recovered voice, loss, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
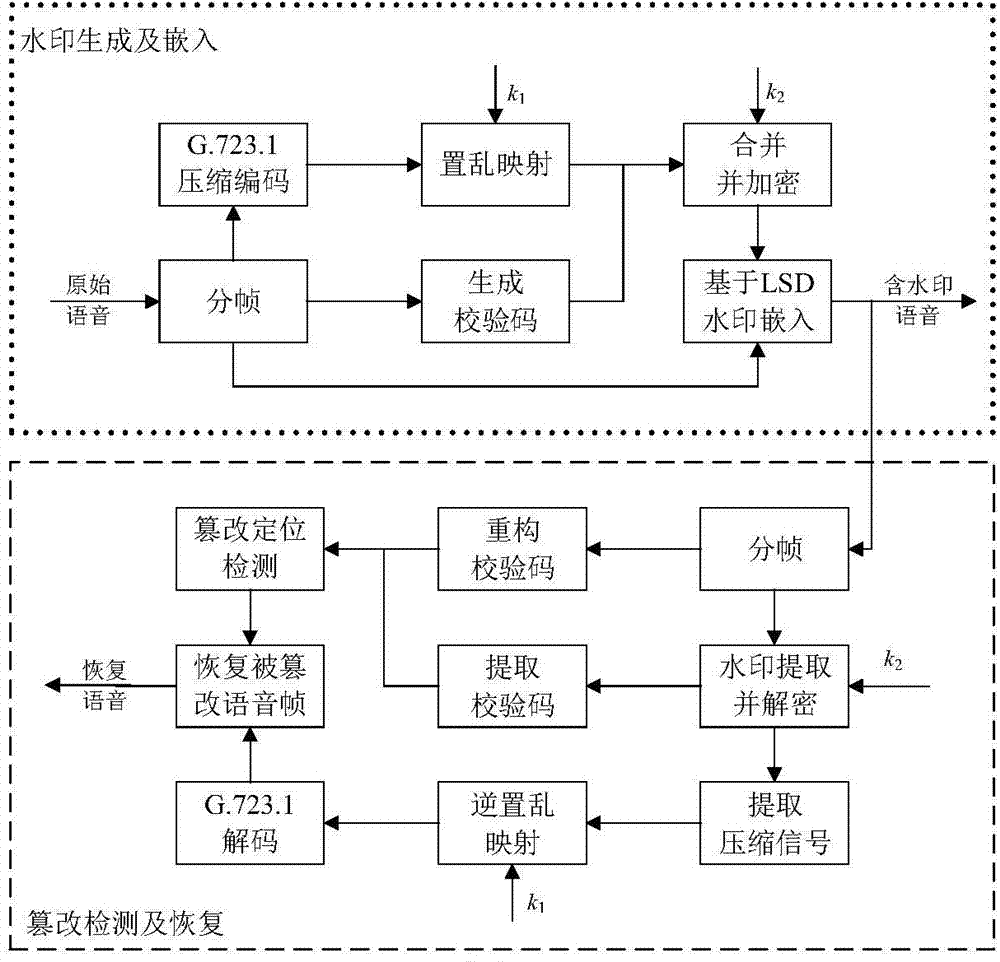
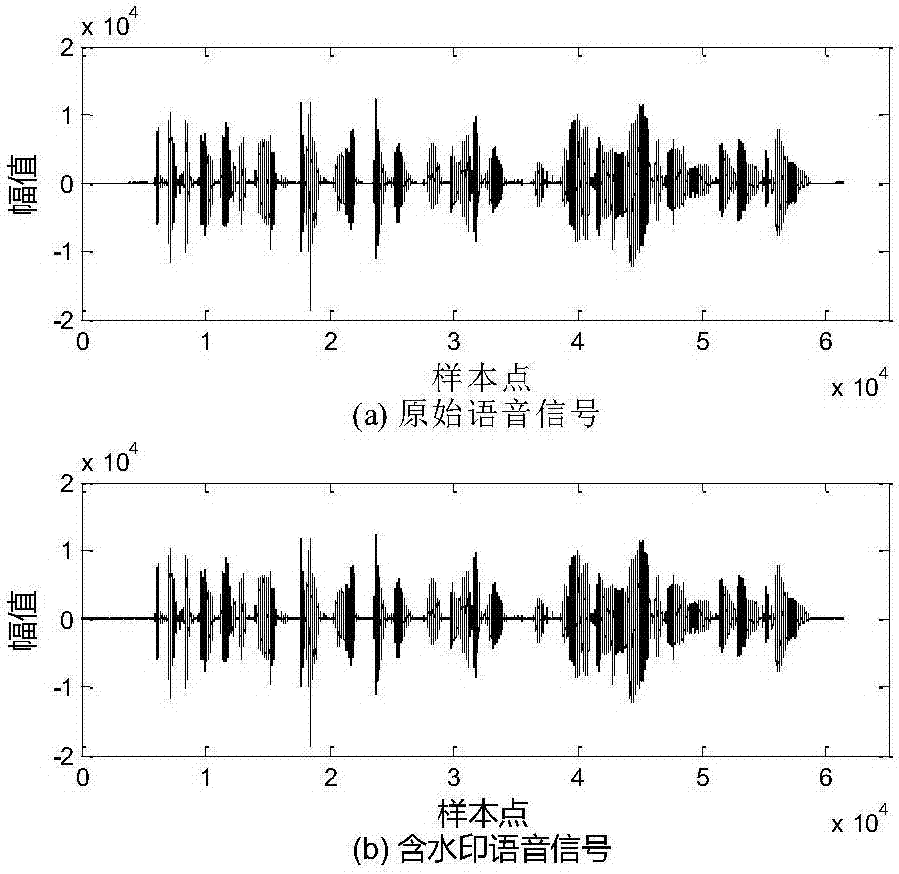
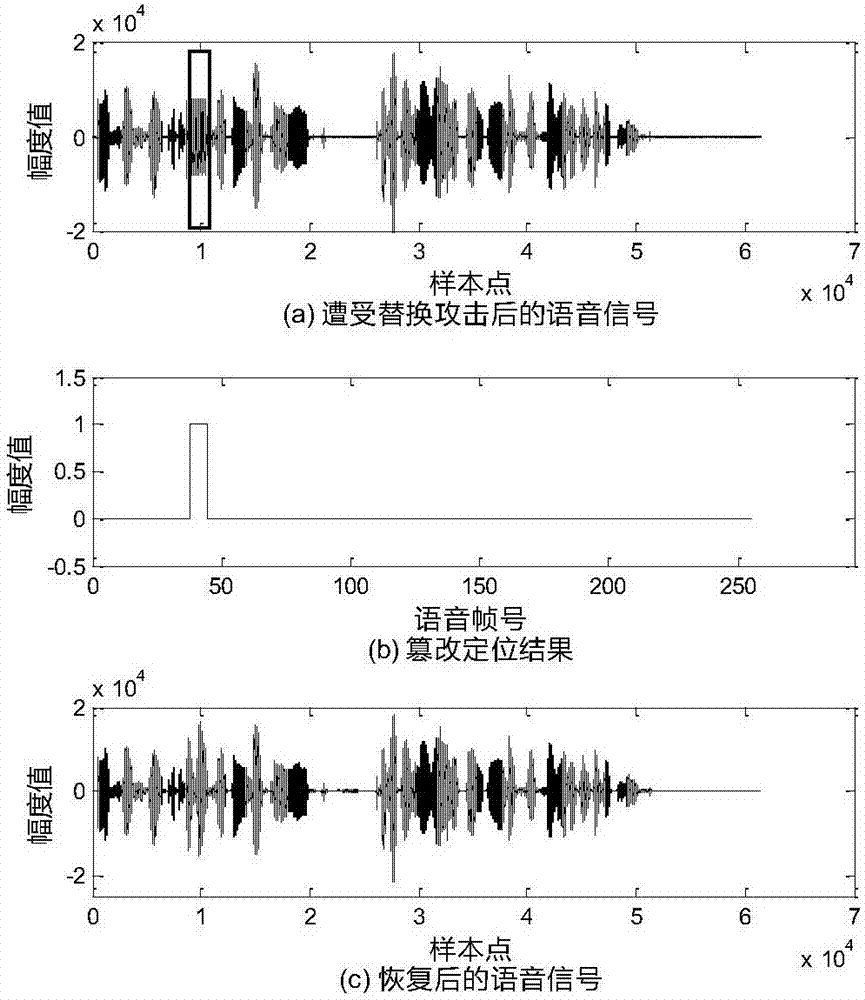
[0056] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
[0057] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0058] 1. Steps of the fragile watermark algorithm modifying the weight of the least significant digit:
[0059] (1) Assume that the original speech segment sampling value is x={x 1 ,x 2 ,...,x n ,...,x N}, the watermark information is w(w∈[0,2 N -1]). First, calculate the least significant number of digits of the speech signal according to the following formula, y={y 1 ,y 2 ,...,y n ,...,y N} is the least significant number of digits of the speech signal x.
[0060] the y n =|x n |mod10
[0061] (2) Calculate the weight value c of the segment by the least significant bit value y of the signal x, and its value range is [0,2 N -1].
[0062]
[0063] (3) Calculate the differenc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com