Security watermark algorithm combining cryptography
A security and cryptography technology, applied in the direction of image communication, electrical components, etc., can solve the problem of collusion attack of double watermarking mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Various details involved in the method provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
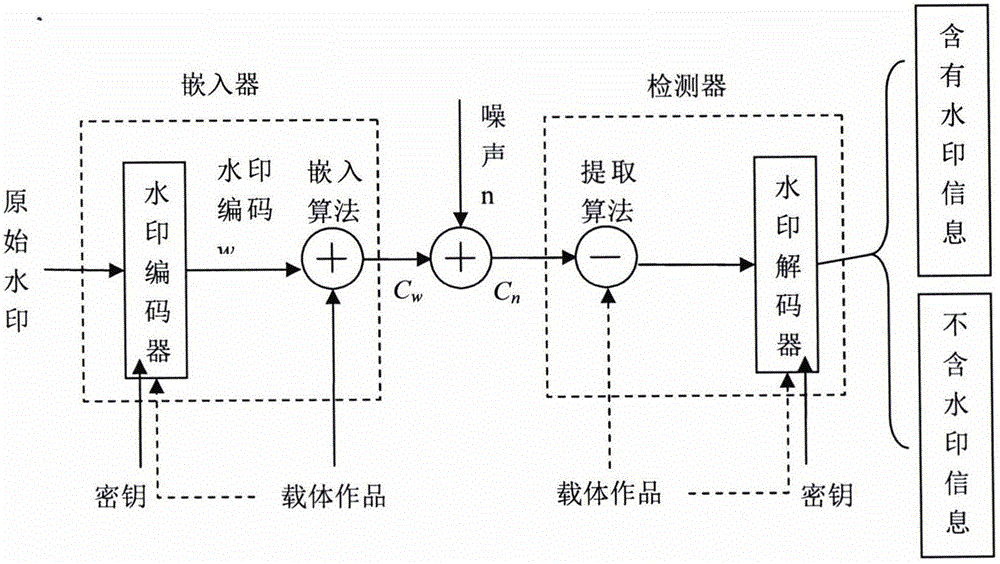
[0035] 1. Embedding of watermark information
[0036] The specific implementation scheme of watermark information embedding provided by the present invention is as follows:
[0037] 1) Extraction of side information
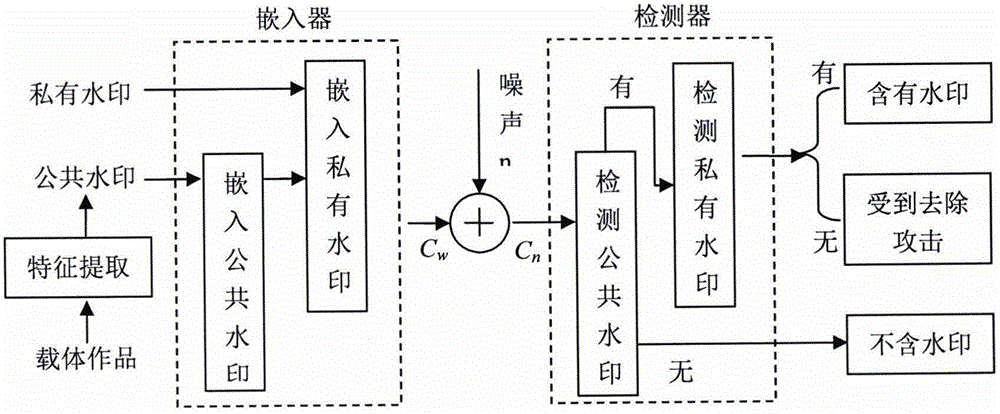
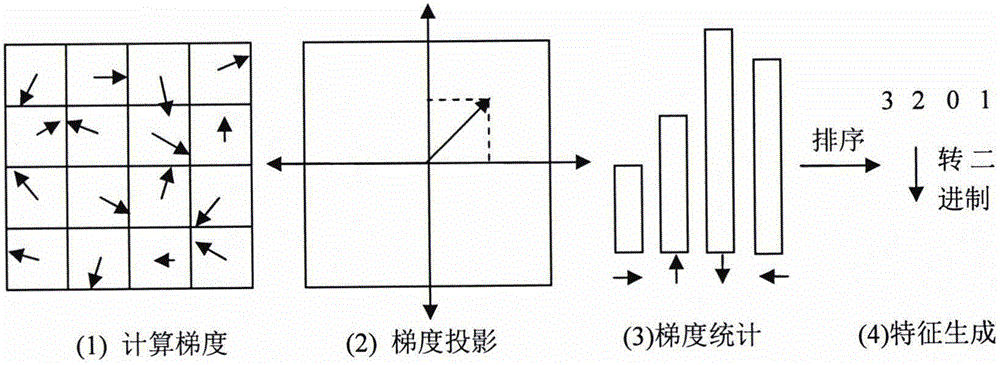
[0038]The introduction of side information associates the watermark with the carrier, which can resist copy attacks and same-origin detection attacks. Because the side information is extracted from the carrier and participates in the encryption process of the watermark, the watermark extraction process also needs to use the side information. This means that the edge information extraction algorithm must extract the same information from the carrier before and after embedding the watermark, otherwise it cannot be decrypted correctly. Therefore, the side information must be a relatively stable feature ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com