Method for implementing image digital watermark
A technology of digital watermarking and implementation methods, applied in the field of data security, can solve problems such as insecurity, increased security certification system overhead and management risks, recorded in this book or stored in computer memory or external storage, and solves the problem of publishing Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
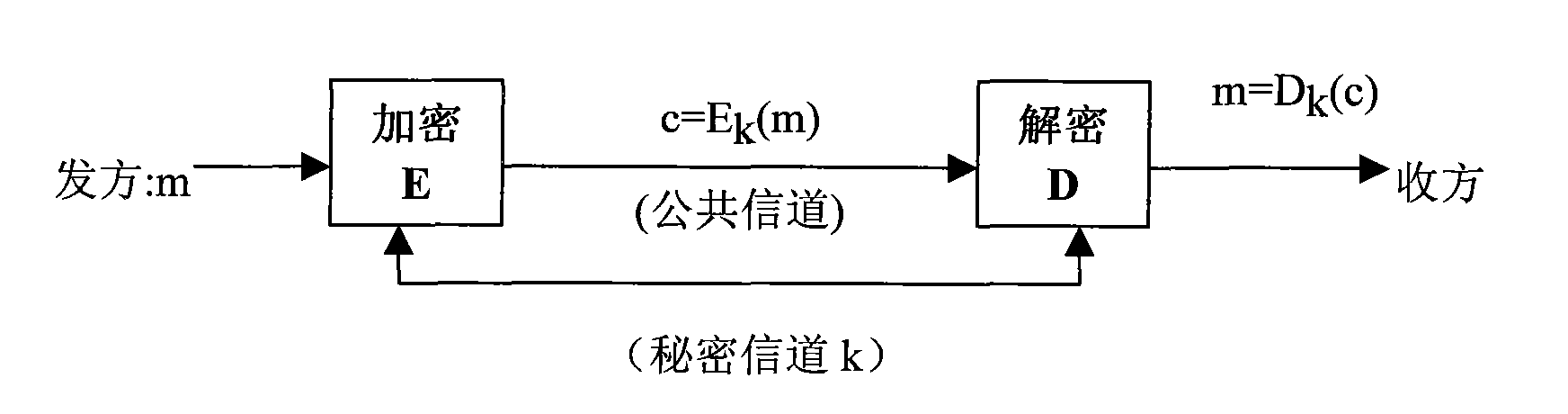
[0026] The cryptography principles and concepts involved in the present invention and the specific implementation of the technical solution of the present invention will be described in detail below with reference to the accompanying drawings.
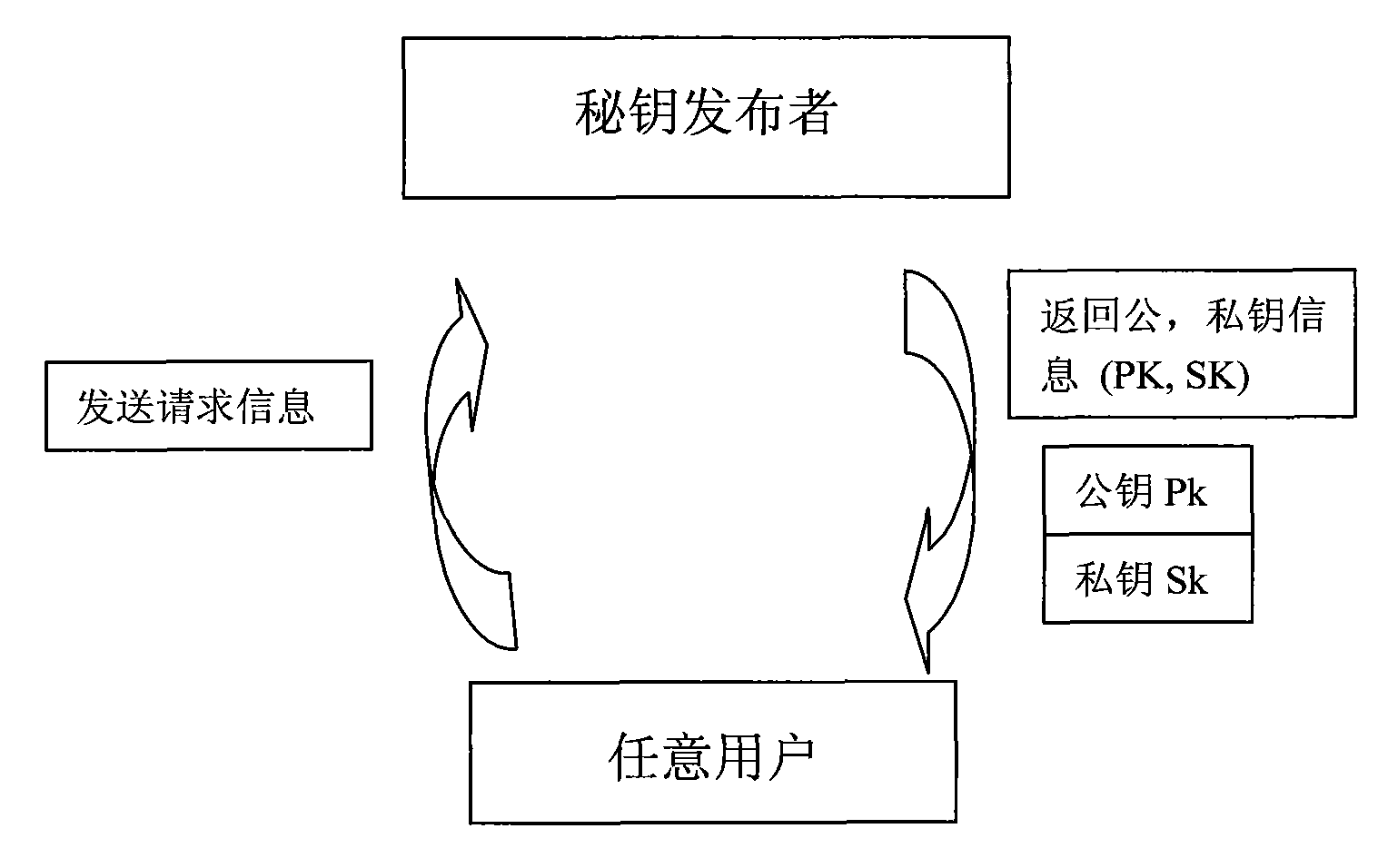
[0027] The idea of public key cryptography proposed by Diffie and Hellman in the article "New Directions in Cryptography": If each user A has an encryption key Ka different from the decryption key Ka', the encryption key Ka can be made public, and Ka' Confidentiality, of course, requires that the disclosure of Ka will not affect the safety of Ka'. If B wants to send plaintext m to A in secret, he can check A’s public key Ka, and if he encrypts the ciphertext with Ka
[0028] C=E Ka (m)
[0029] After receiving C, A decrypts C with the decryption key Ka' that only A himself possesses.
[0030] m=D Ka’ (C)
[0031] Since the encryption key Ka is different from the decryption key Ka', public key cryptography is also called asymmetr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com