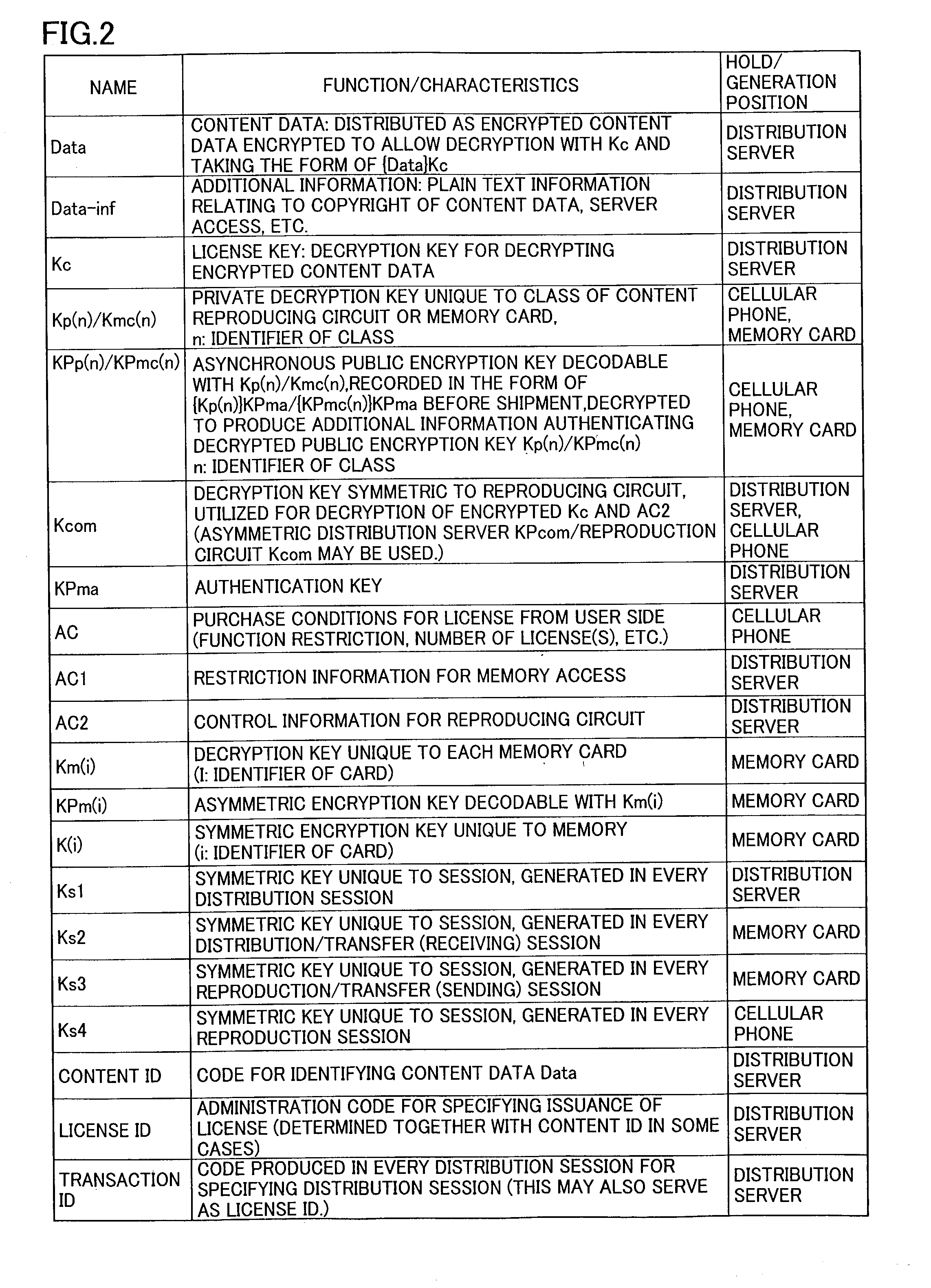
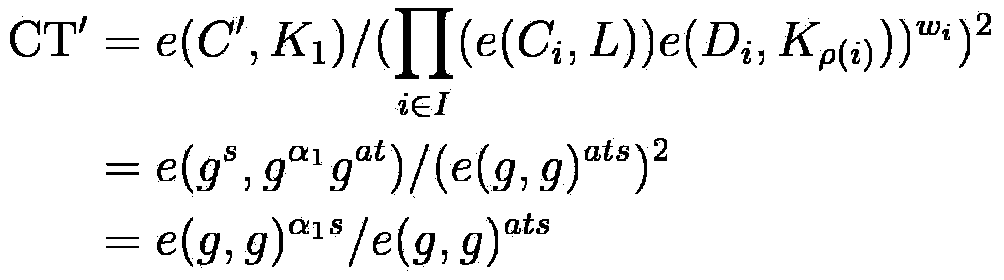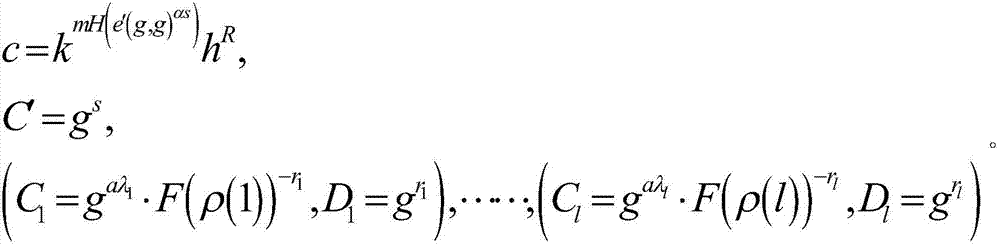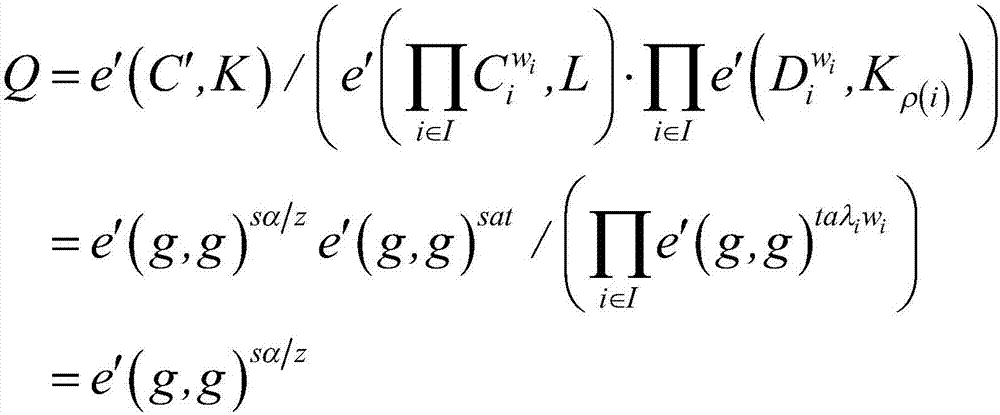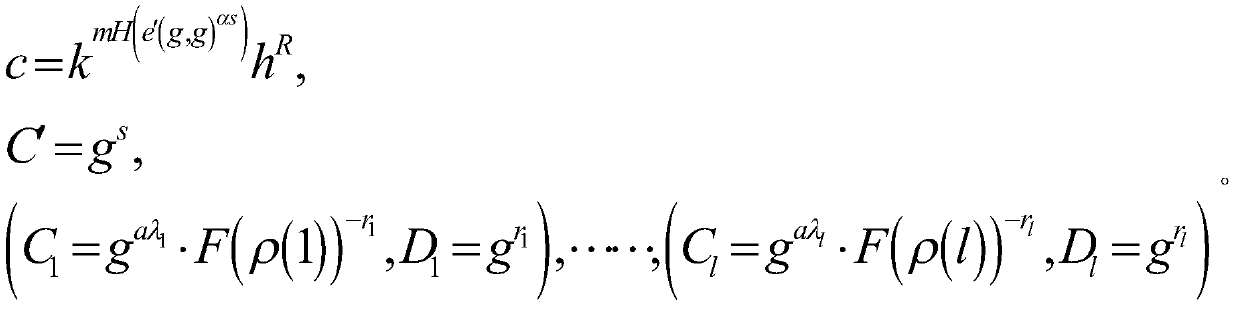Patents
Literature
35results about How to "Fast decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Enhanced system security
ActiveUS20100257351A1Fast decryptionFast locationMultiple keys/algorithms usageComputer security arrangementsThird partyConfidentiality
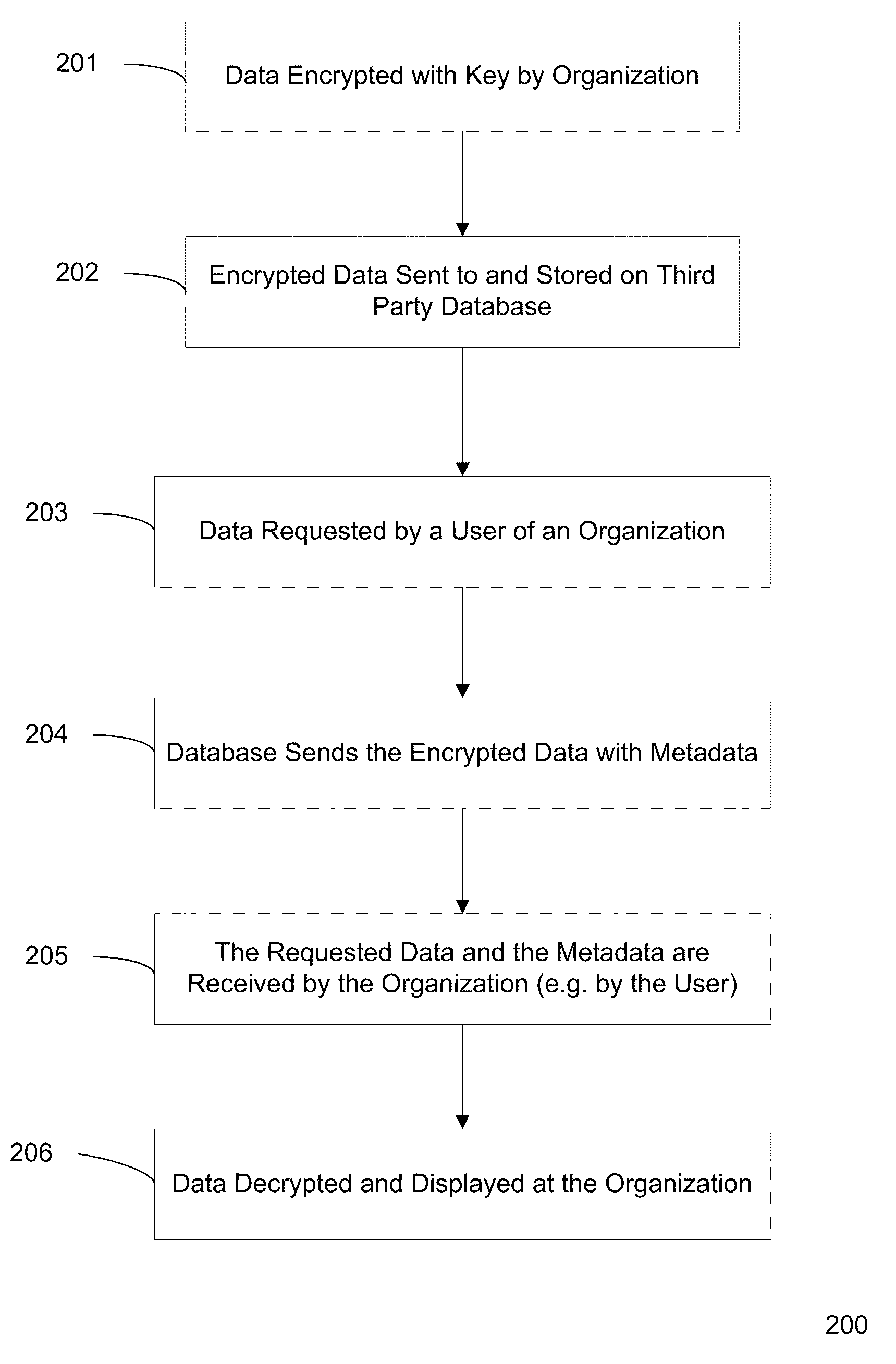
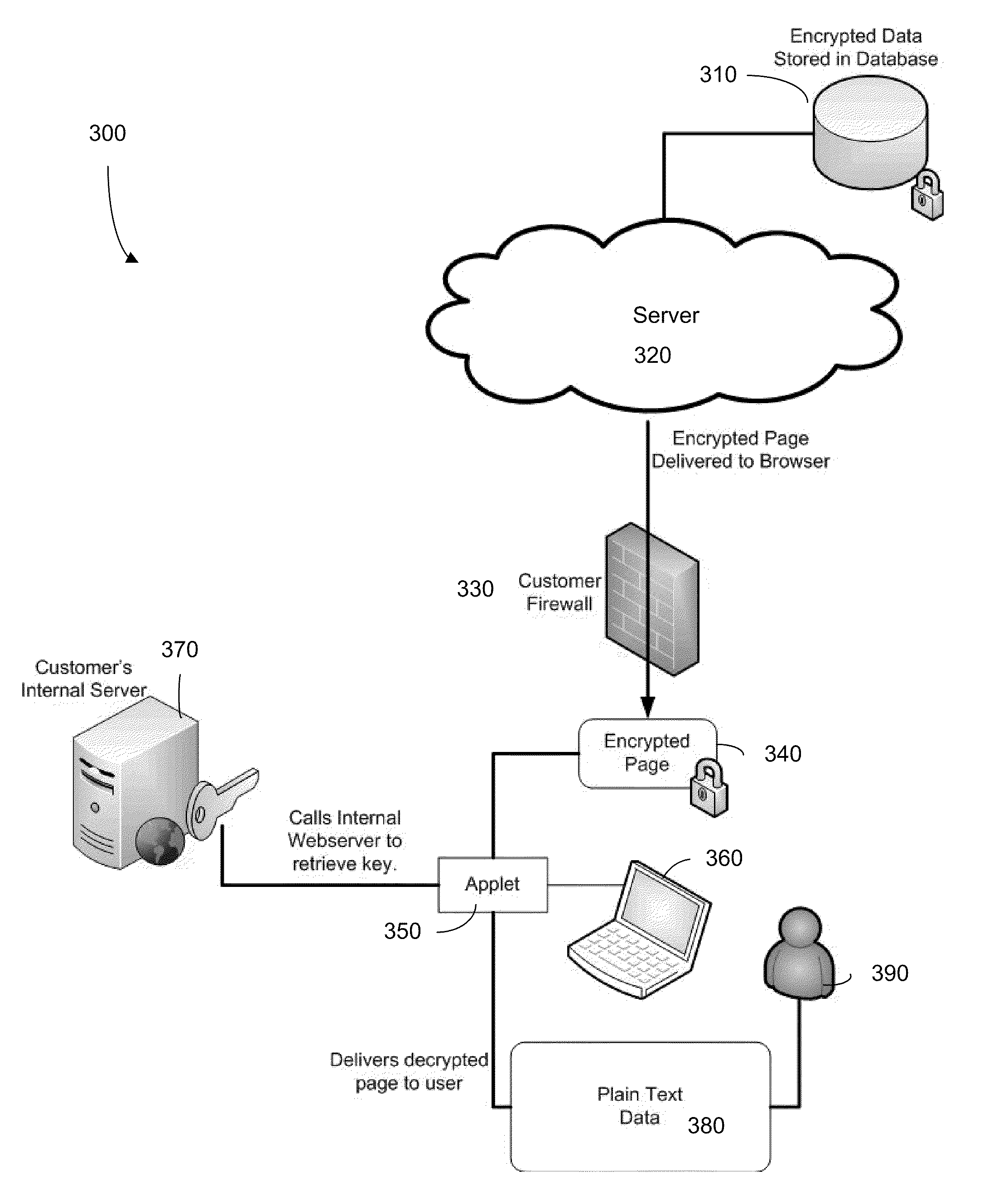
Methods and systems for maintaining the confidentiality of data provided by an organization for storage on a third party database system are provided. The data can encrypted on an internal network of the organization and sent to the third party database system for storage. The third party database system can associate metadata with the encrypted data and can store the encrypted data. Accordingly, when a request for the encrypted data is received from a computing device communicating with an internal network of the organization, the encrypted data and associated metadata can be sent to the computing device. A key that is stored on an internal network of the organization can be called through an applet, which utilizes information within the metadata to locate the key on the internal network of the organization. The computing device to which the encrypted data is sent can use the key location information to retrieve the key and decrypt the data for display to a user.
Owner:SALESFORCE COM INC
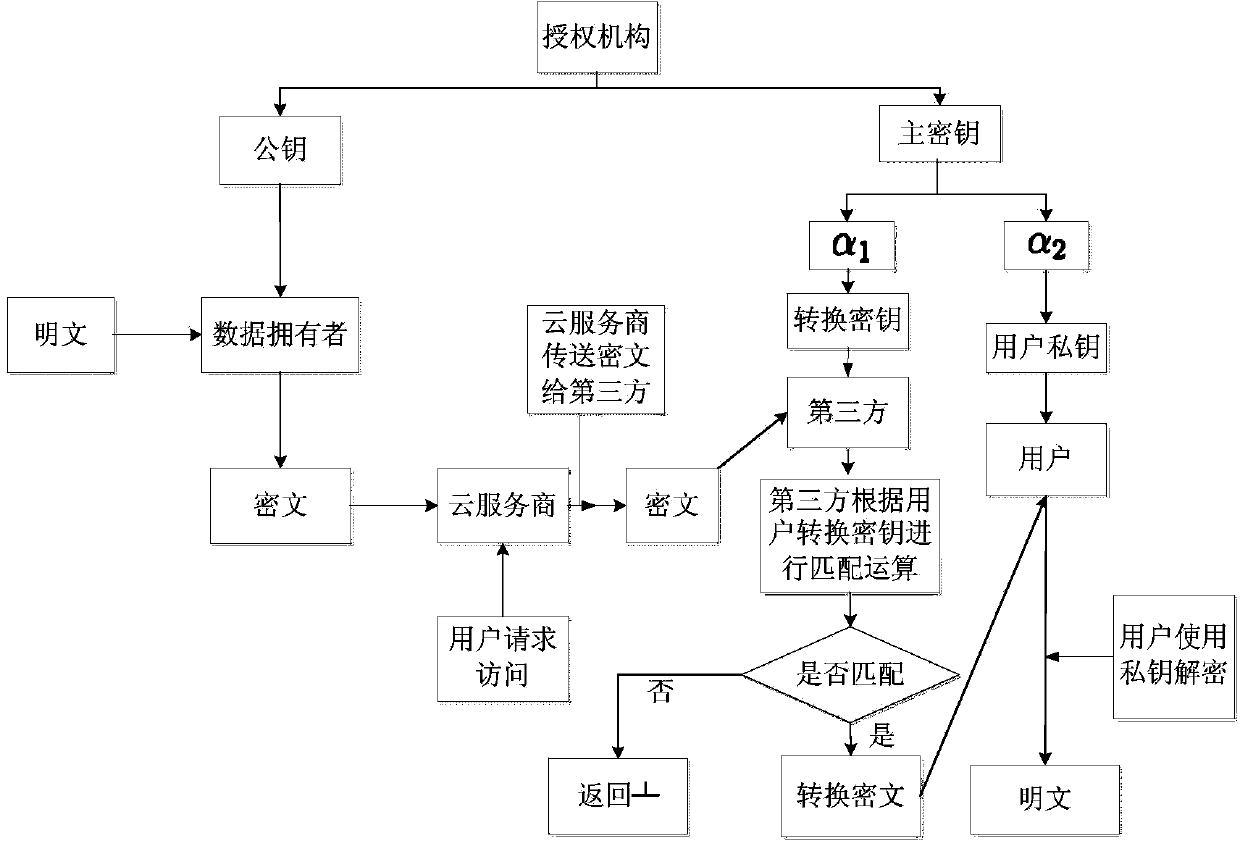
Outsourcing decryption method of attribute-based encryption based on ciphertext policy
InactiveCN104022868AReduce the burden onEfficient and safe decryptionKey distribution for secure communicationUser identity/authority verificationThird partyCiphertext
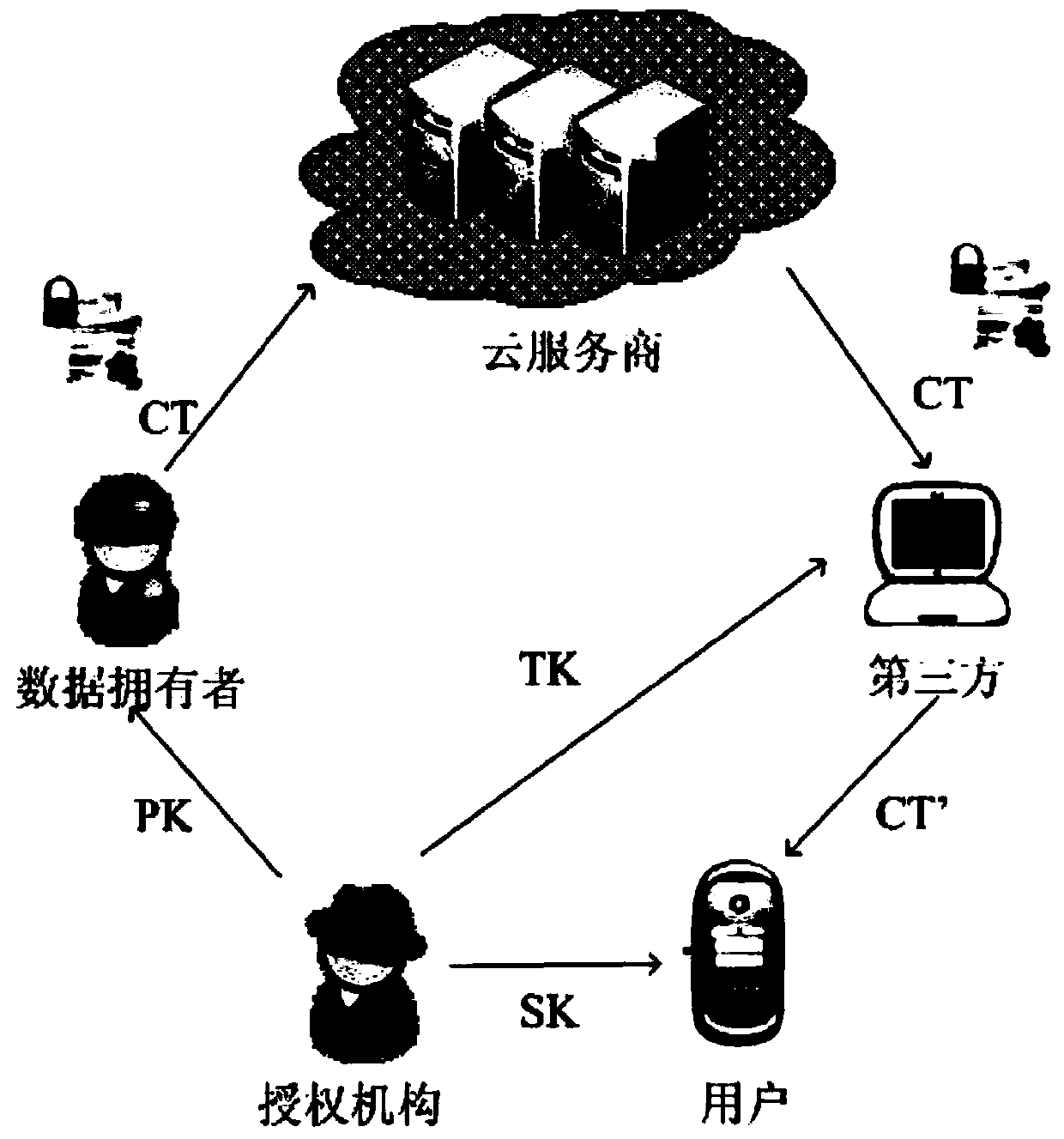
The invention provides a highly-efficient safe outsourcing decryption method based on the attribute encryption in mobile cloud computing environment. The method comprises the following steps: system initialization; a data owner encrypting a file and uploading the file to a cloud service provider; an authorization organization generating secret keys; a third party transforming ciphertexts; and a mobile terminal user decrypting the file. According to the method, targeted for the mobile cloud computing environment, by utilizing a ciphertext policy attribute-based encryption shared data method, according to the requirement of limited operation and storage capacity of a mobile terminal, and under the premise of guaranteeing data security, a portion of complex decryption tasks are outsourced to the third party; and by utilizing outsourcing decryption, secret key decomposition technique and matching algorithm, unnecessary bilinearity pairing operation is reduced, and a reliable method is provided for the mobile terminal to carry out rapid decryption.
Owner:HANGZHOU NORMAL UNIVERSITY
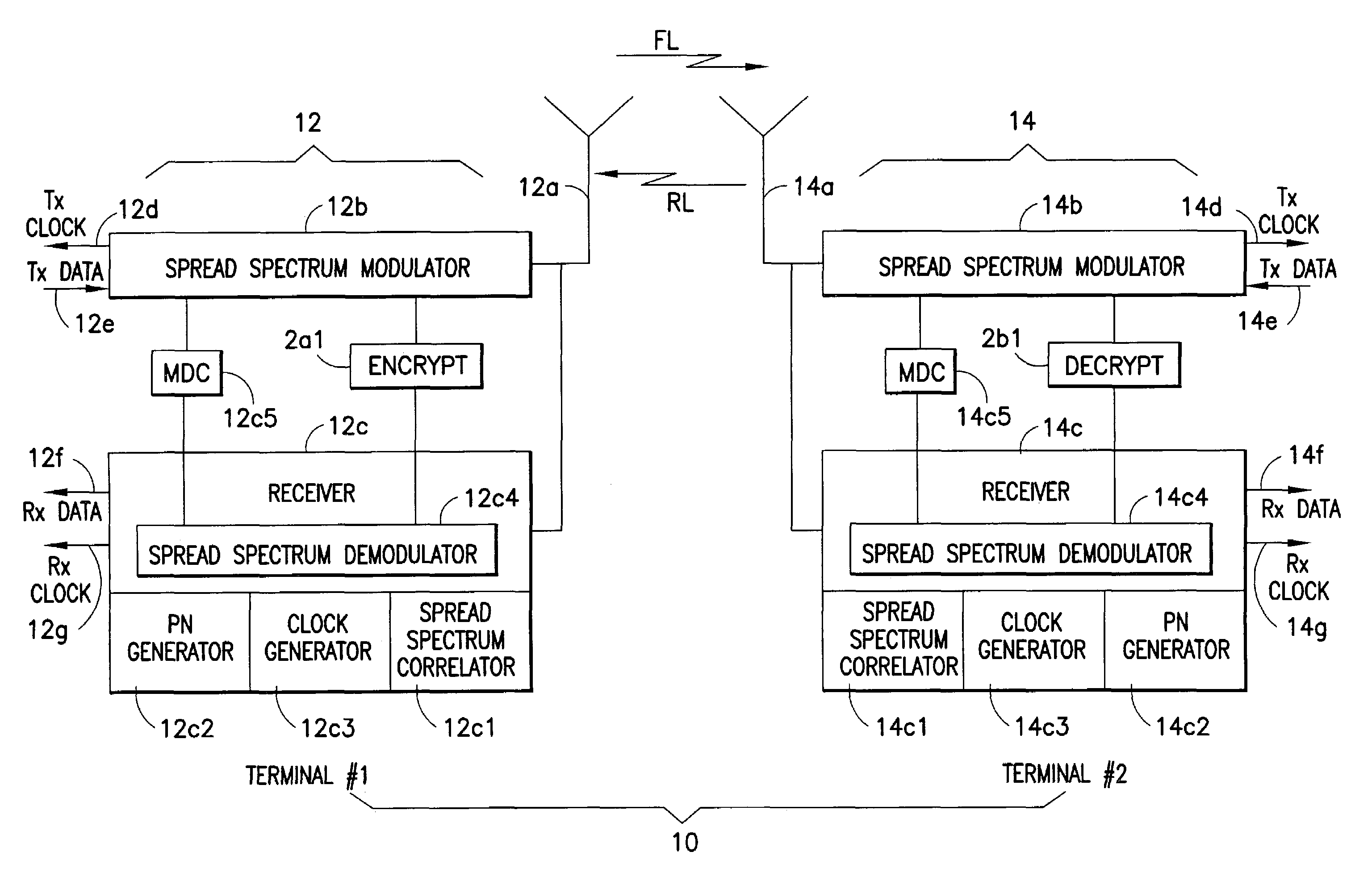
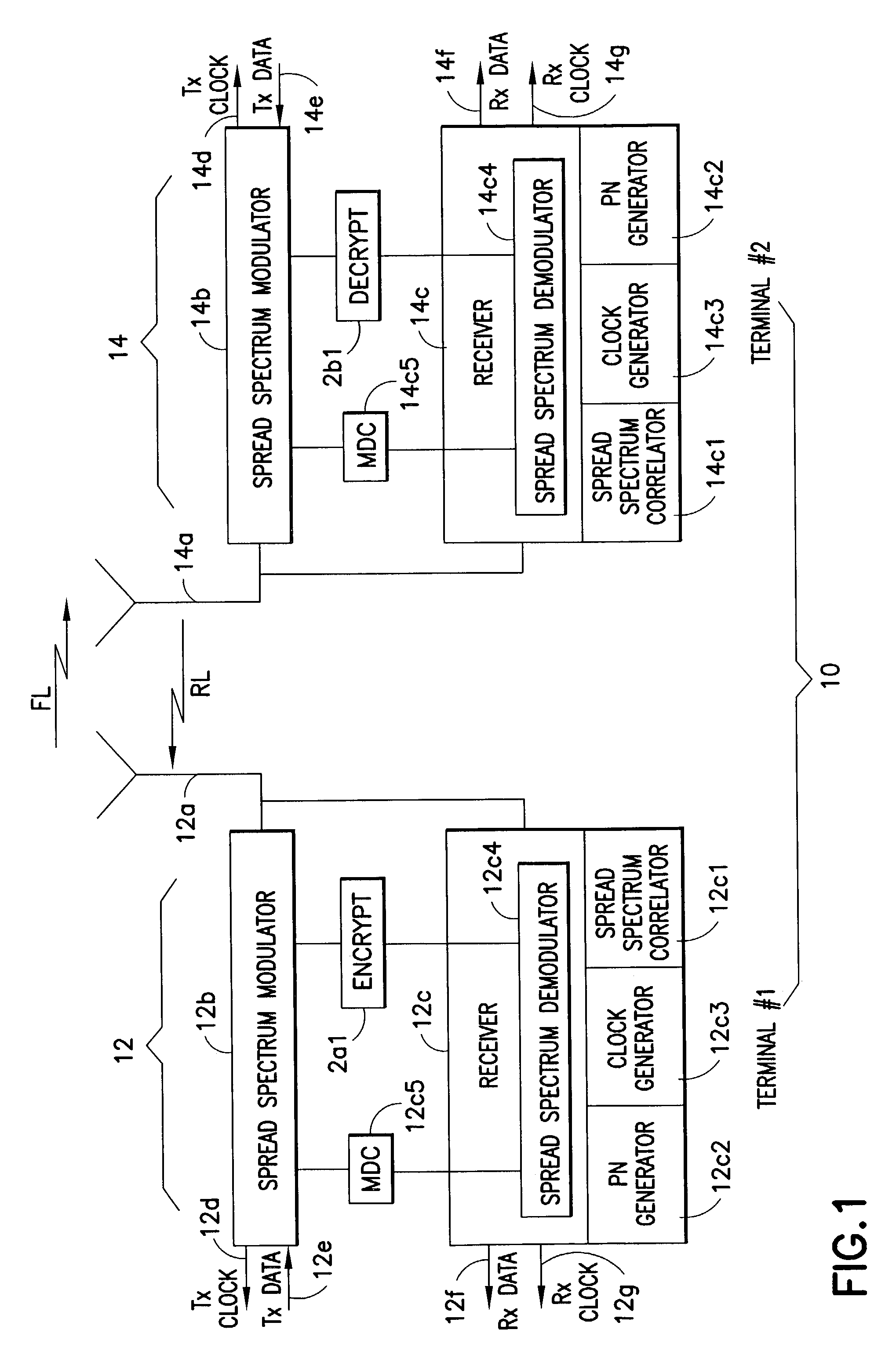
System and method for fast data encryption/decryption using time slot numbering
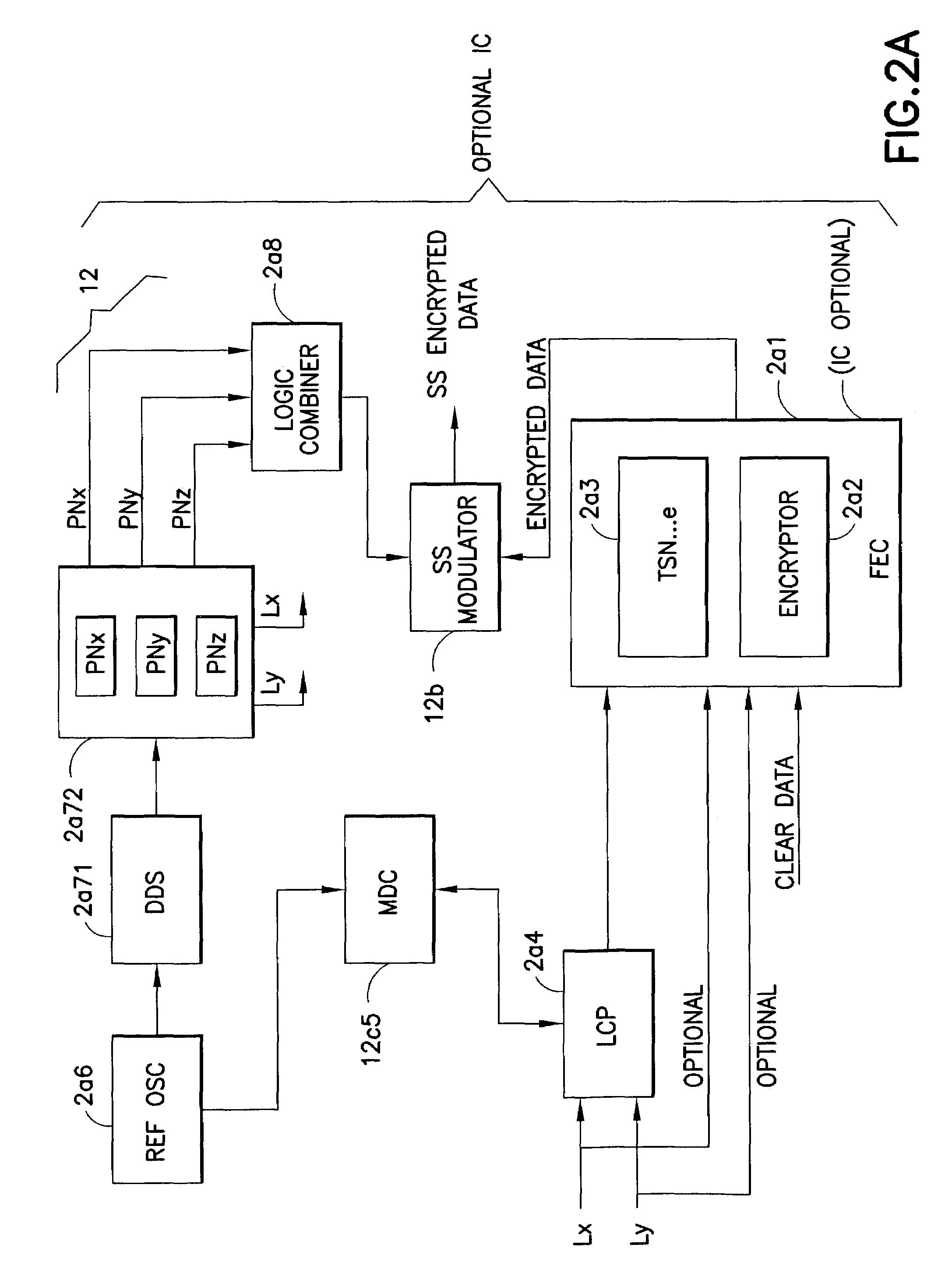
ActiveUS7200233B1Fast decryptionSynchronising transmission/receiving encryption devicesUnauthorized memory use protectionDirect digital synthesizerComputer science
A system for fast data encryption / decryption is provided. The system includes a transmitter system having a transmitter direct digital synthesizer (DDS). The DDS includes at least three transmitter pseudo-noise (PN) component code generators PNx, PNy, PNz, where each transmitter PN component code generator is adapted to generate relatively prime transmitter PN component codes when compared with each of the other transmitter PN component code generators. The transmitter also includes a first processor coupled to the transmitter DDS, where the first processor is adapted to determine a time slot number (TSN) relative to at least two of the relatively prime transmitter PN component codes. Also included in the transmitter is an encryptor for encrypting clear data in accordance with the TSN. The system includes a receiver system having a second processor adapted to determine the TSN; and a decryptor coupled to the second processor. The decryptor is adapted to decrypting the encrypted clear data in accordance with the TSN.
Owner:L3 TECH INC
Information issuing method and system for earthquake tsunami alarm system
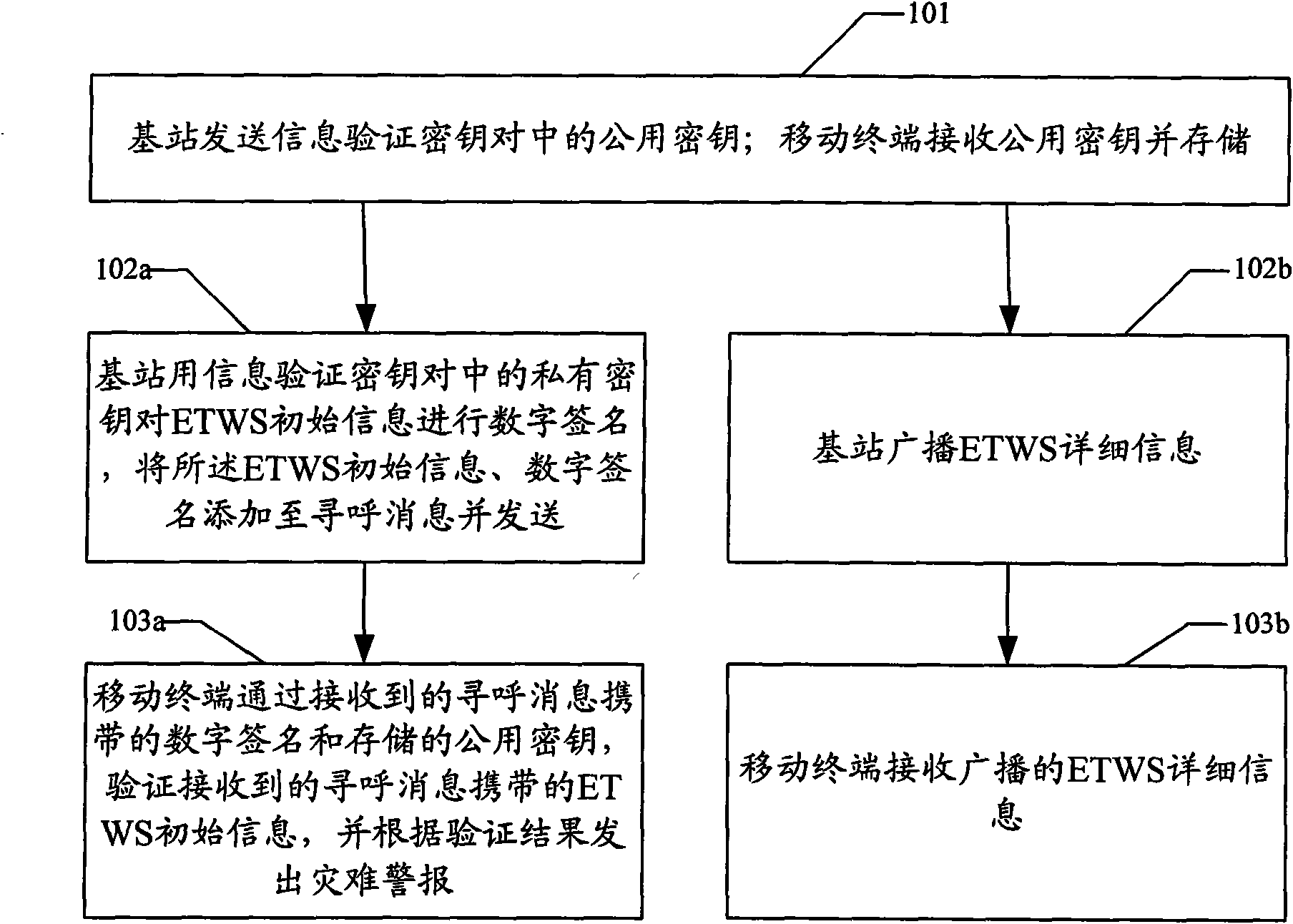
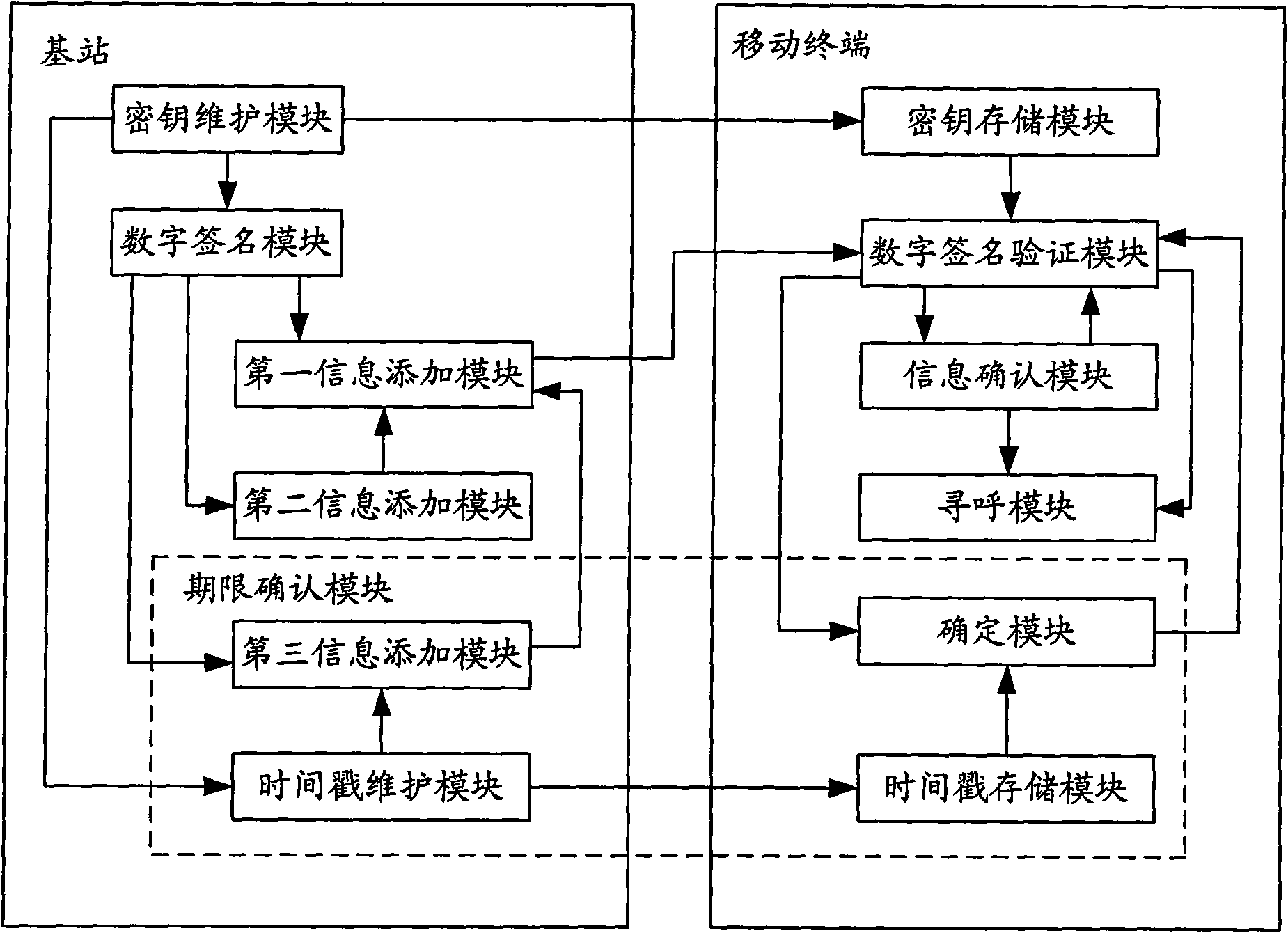
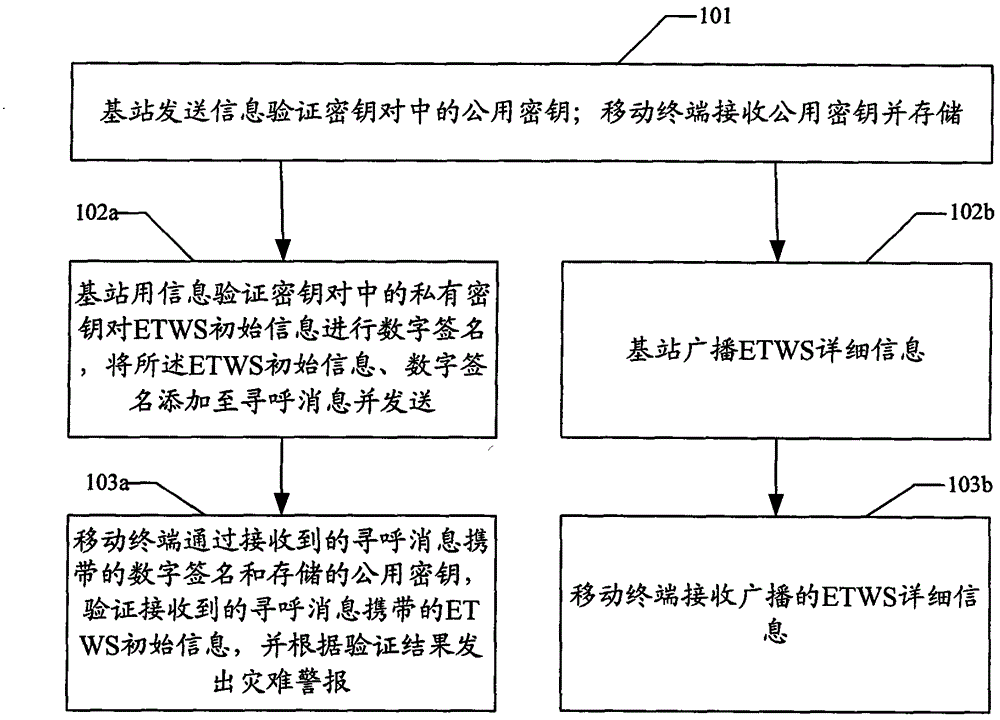
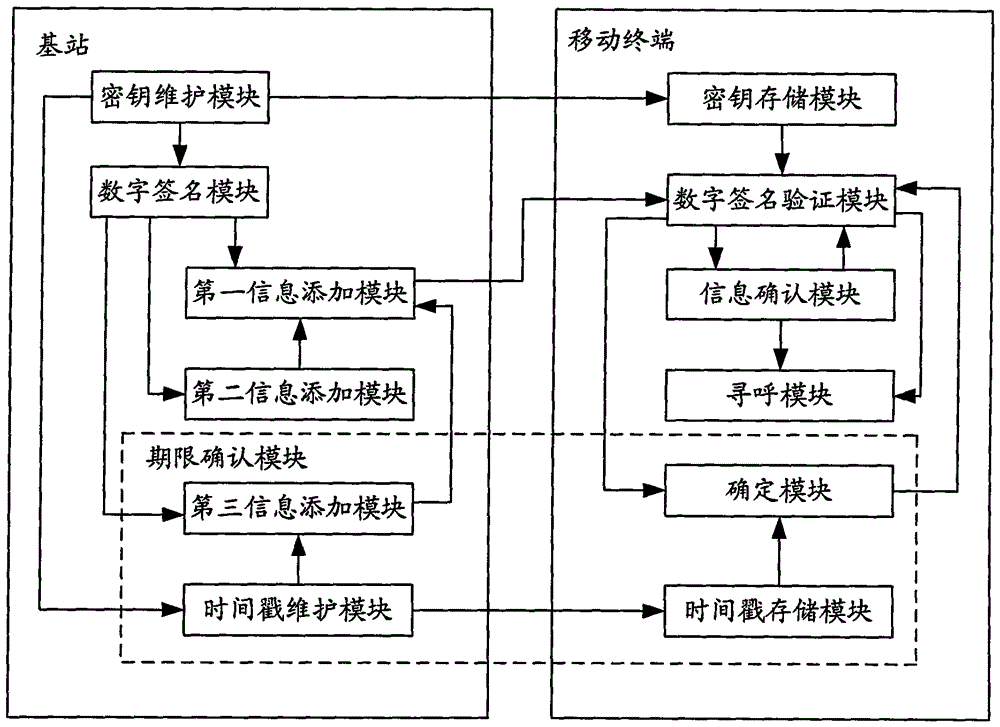
InactiveCN101938740ARelease securityReal-time releaseSecurity arrangementEmergency/hazardous communication serviceDigital signatureComputer terminal
The invention discloses an information issuing method for an earthquake tsunami alarm system, and the method comprises the following steps: leading a base station to send a public key for information verification key centering; leading a mobile terminal to receive the public key and store; leading the base station to use a private key for the information verification key centering to carry out digital signature on ETWS initial information, adding the ETWS initial information and the digital signature to a paging message and sending; and leading the mobile terminal to receive the paging message, verifying the ETWS initial information carried in the received paging message through the digital signature carried in the received paging message and the stored public key, and emitting a disaster alarm according to the verification result. The invention simultaneously discloses an information issuing system for the earthquake tsunami alarm system, which comprises the base station and the mobile terminal. The adoption of the method and the system can issue the ETWS information in a safe and timely manner.
Owner:ZTE CORP
Enhanced system security
ActiveUS8751826B2Fast decryptionFast locationKey distribution for secure communicationUnauthorized memory use protectionThird partyConfidentiality
Methods and systems for maintaining the confidentiality of data provided by an organization for storage on a third party database system are provided. The data can be encrypted on an internal network of the organization and sent to the third party database system for storage. The third party database system can associate metadata with the encrypted data and can store the encrypted data. Accordingly, when a request for the encrypted data is received from a computing device communicating with an internal network of the organization, the encrypted data and associated metadata can be sent to the computing device. A key that is stored on an internal network of the organization can be called through an applet, which utilizes information within the metadata to locate the key on the internal network of the organization.
Owner:SALESFORCE COM INC
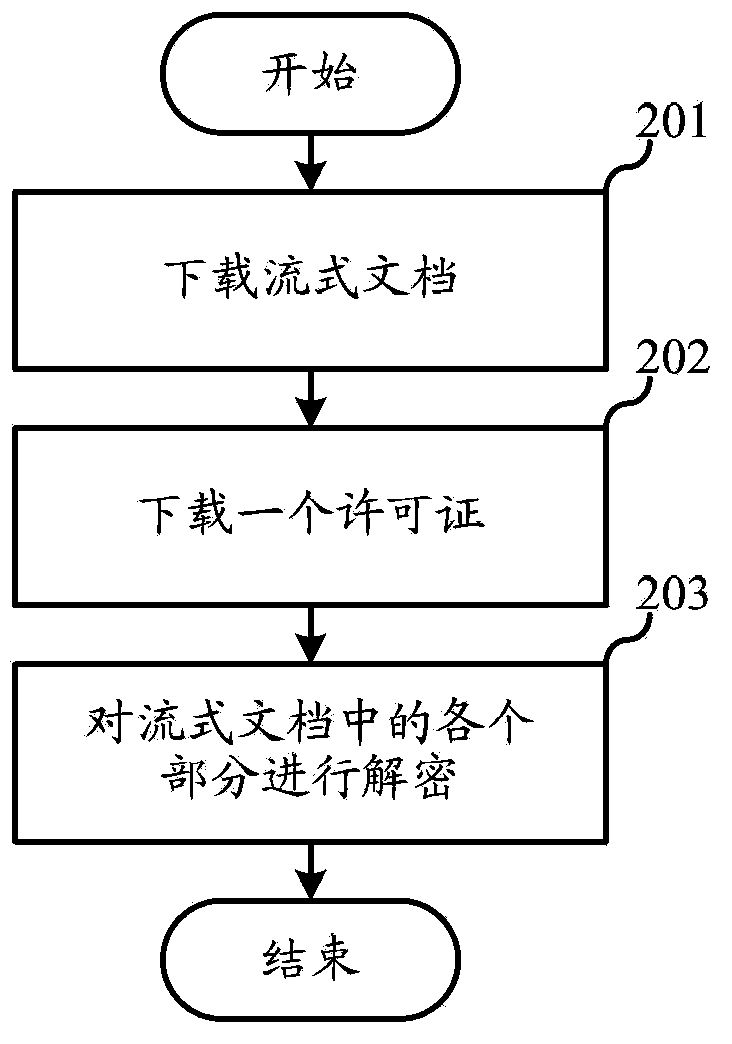
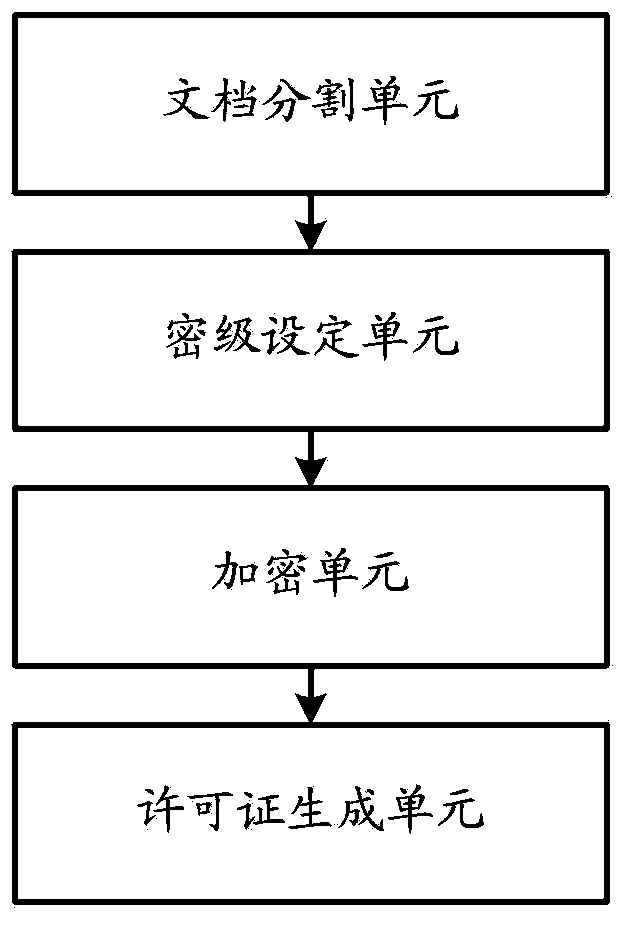
Method for encrypting and decrypting streaming document and device thereof
InactiveCN103577765AFast encryptionReduce the need for computing resourcesDigital data protectionComputer resourcesTerminal equipment
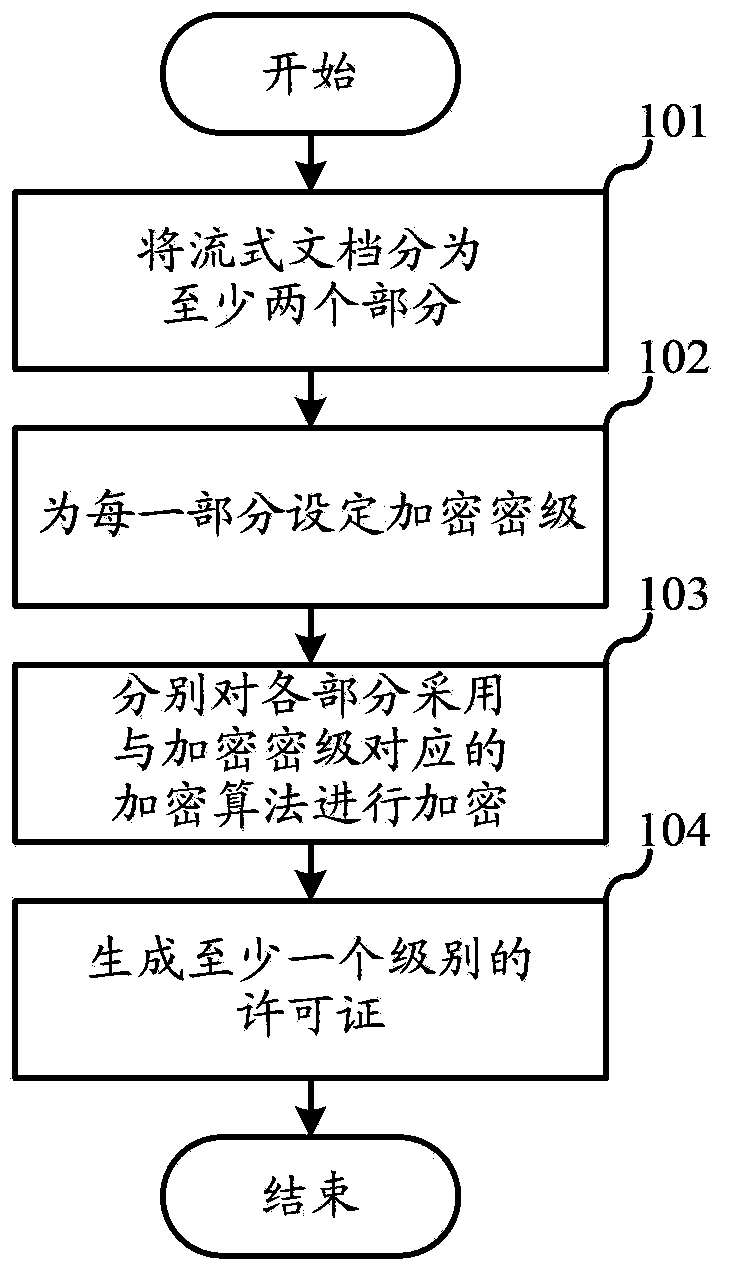
The invention relates to the field of digital publishing, and discloses a method for encrypting and decrypting a streaming document and a device thereof. According to the method, each part of one streaming document is encrypted at different encrypting grades, general contents can be encrypted by adopting a low-security-level rapid encryption algorithm, and important contents are encrypted by adopting a high-security-level safety encryption algorithm, so that the overall encryption speed of the document is increased, the demand on computing resources in a computer system is lowered, and the security of the important contents is ensured. Each part of one streaming document is encrypted by adopting different encrypting grades, and the contents of a low encryption security level can be decrypted rapidly, so that the overall decryption speed of the document is increased. At a lowest encryption security level, encryption is not performed, so that computer resources needed by encryption can be further reduced; parts of contents of the streaming document do not need to be decrypted during use, so that the demand of terminal equipment on computing resources is lowered; the method and the device are particularly suitable for trial reading of parts of chapters.
Owner:JIEFANG DAILY NEWSPAPER GRP
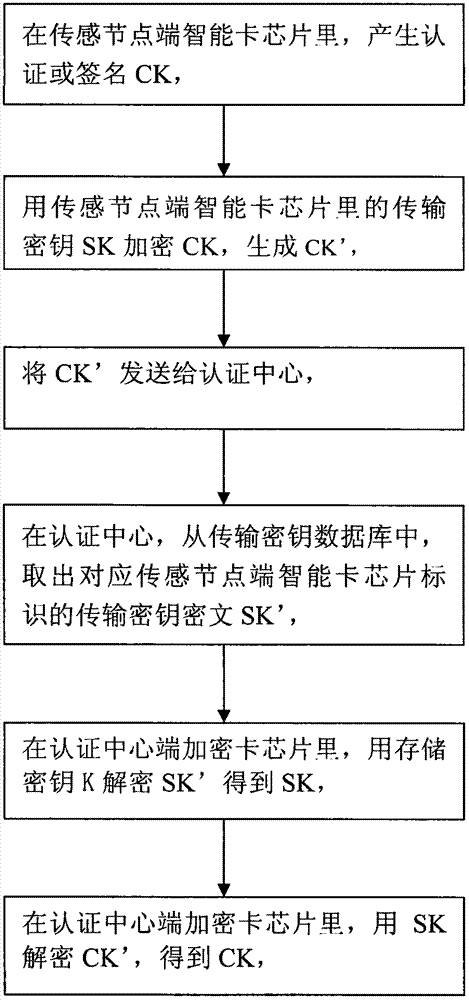
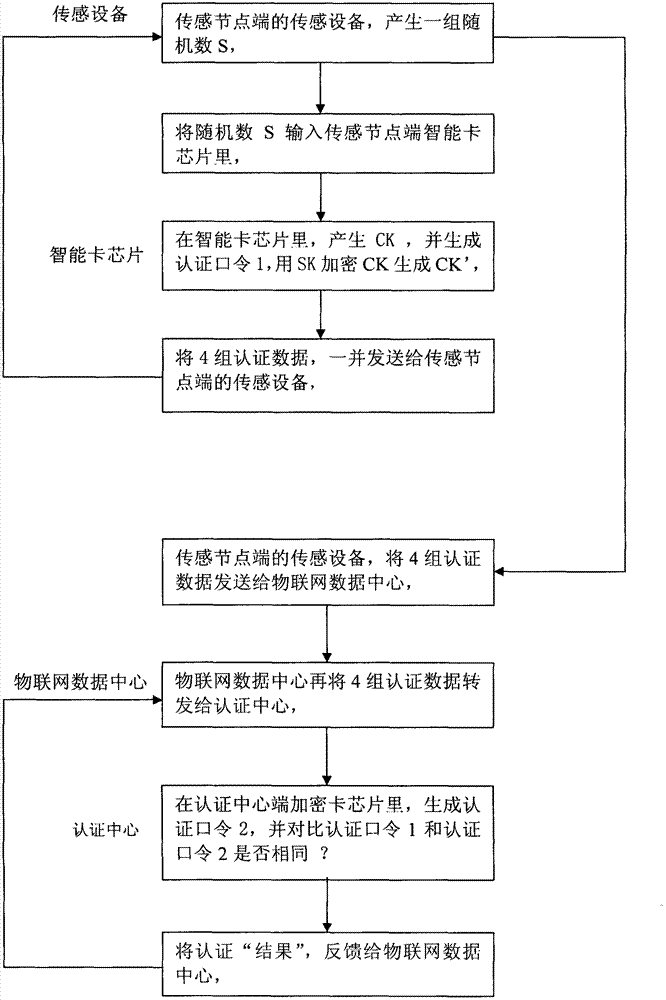
Password authentication method for internet of things by adopting security one-key management technology
InactiveCN102833260ARealize confidential transmissionImprove integrityUser identity/authority verificationStorage securityTransfer procedure
The invention discloses a password authentication method for an internet of things by adopting a security one-key management technology. According to the method, an internet of things security protocol is established by an authentication or a signature key, and the authentication or signature key is encrypted by transmission keys to ensure the security of the process of exchanging and transmitting the authentication or signature key; all transmission keys corresponding to a sensing node end are respectively encrypted by a storage key, to ensure the storage security of the transmission keys on the authentication center end; more encrypting cards are not required to be purchased to store a great amount of transmission keys when the quantity of the sensing node equipment is comparatively great, thereby greatly saving the cost of constructing the authentication center; a security one-key management method is adopted to solve a difficulty on the key updating and management of the one-key password algorithm in the internet of things security protocol, to reduce the cost of one-key updating and maintenance; meanwhile, the advantages of rapid encrypting and decrypting speeds of the one-key password algorithm are developed to effectively improve the operating speed of the internet of things security protocol, thereby establishing an internet of things password authentication system by adopting the security one-key management technology.
Owner:胡祥义
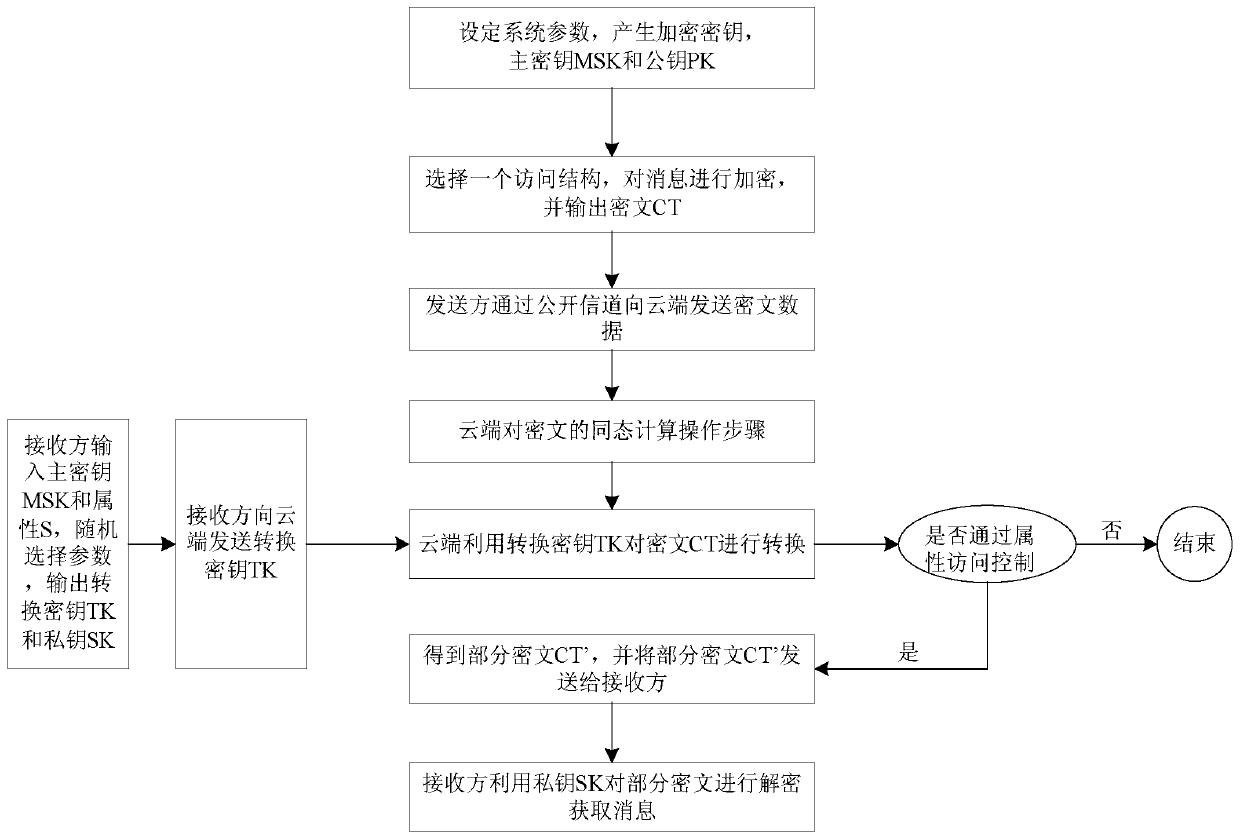
BGN type cryptograph decryption outsourcing scheme based on attributes
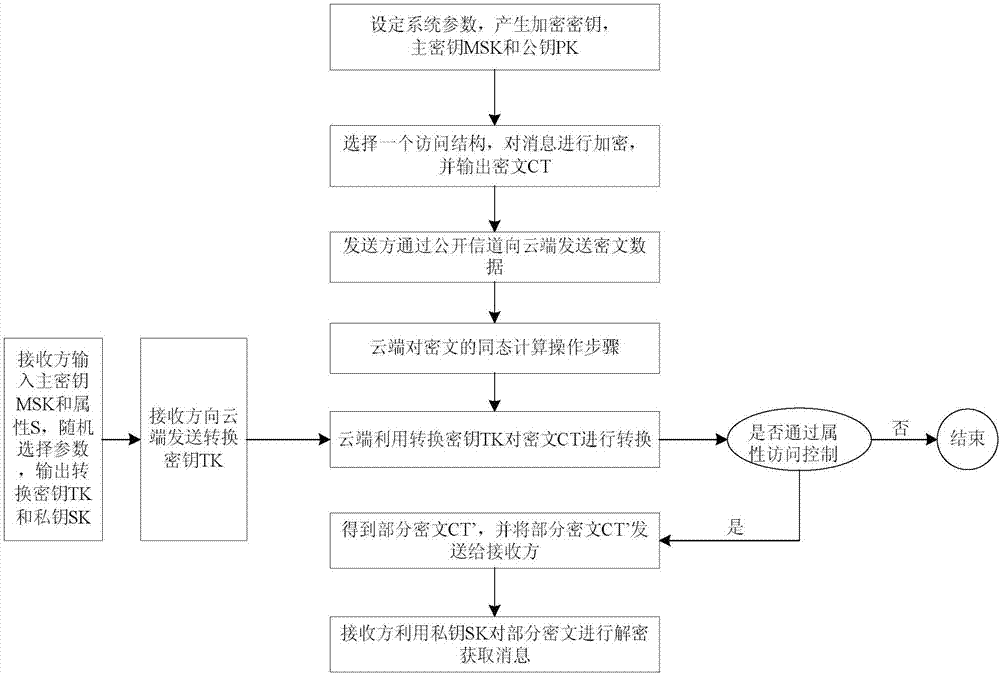
ActiveCN107154845AImprove securityReduce difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess structureSystem parameters
The invention particularly relates to a BGN type cryptograph decryption outsourcing scheme based on attributes. The scheme comprises steps that (1), a system parameter is set, and an encryption secret key is generated; (2), an access structure is selected by a sending side, message encryption is carried out, and cryptograph is generated; (3), a main secret key and the attributes are inputted by a receiving side, and a conversion secret key and a private secret key are outputted; (4), the cryptograph is sent by the sending side to a cloud end; (5), the conversion secret key is sent to the cloud end by the receiving side; (6), the cryptograph is converted by the cloud end through utilizing the conversion secret key to acquire a part of the cryptograph which is sent to the receiving side; and (7), the private secret key is utilized by the receiving side to decrypt the part of the cryptograph to acquire a message, and homomorphic computation operation for the cryptograph carried out by the cloud end is further comprised between the step (4) and the step (5). The scheme is advantaged in that not only can system decryption efficiency be improved, but also storage cost of a receiver is reduced; according to the cryptograph acquired according to the encryption method, a server is permitted to carry out multiple addition homomorphic operation and multiplication homomorphic operation for cryptograph data, on the condition that decryption difficulty does not increase, CPA safety of the user information is substantially improved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
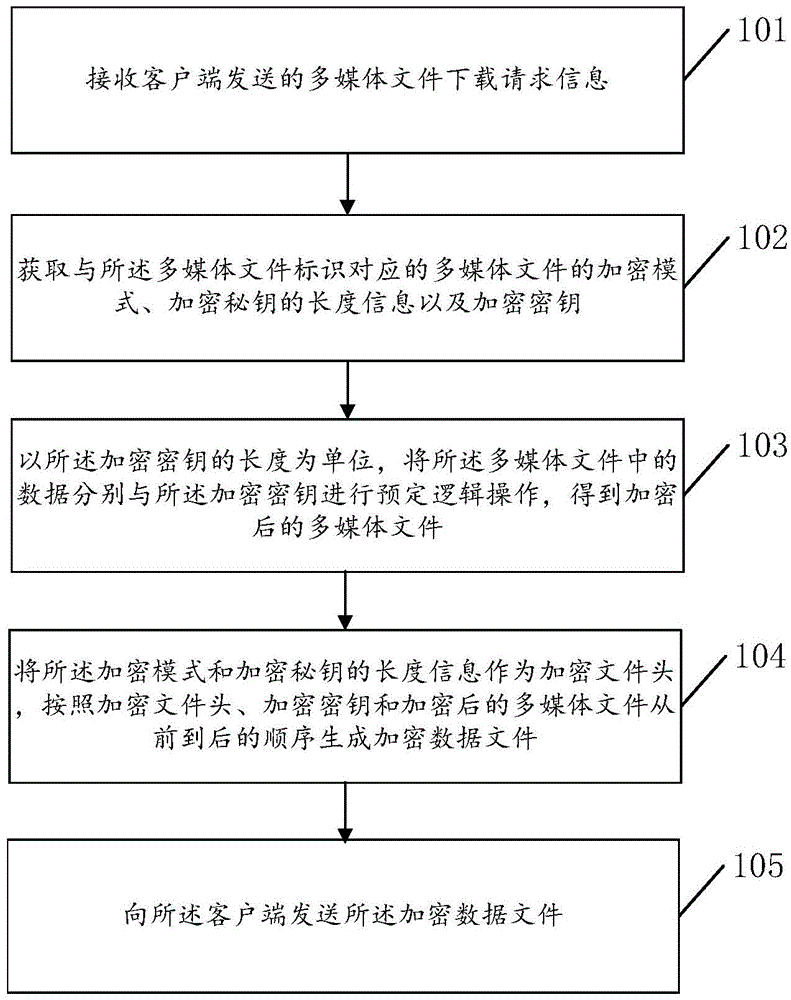
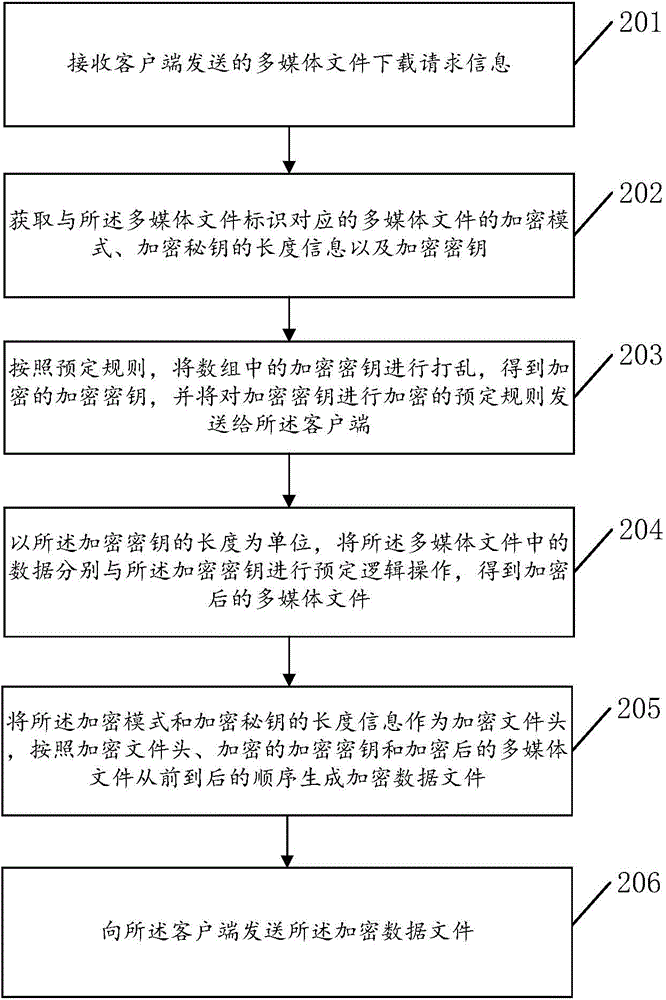
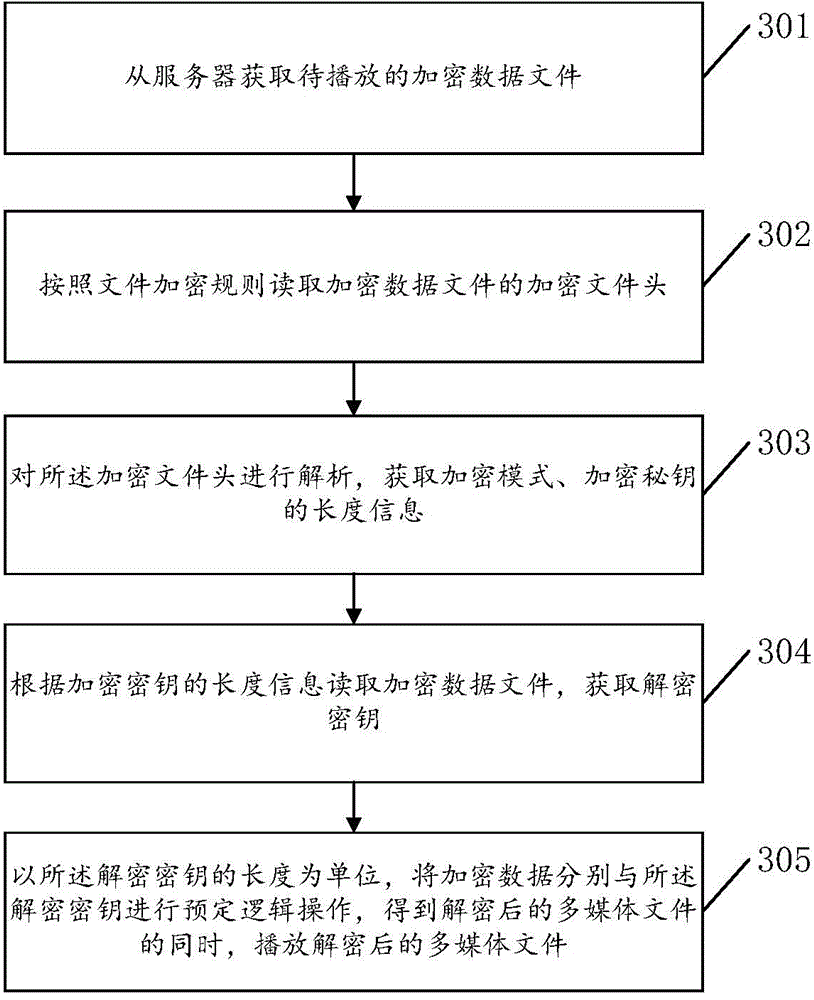
Encryption transmission method and device and decryption playing method and device of multimedia file
The invention discloses an encryption transmission method and device and decryption playing method and device of a multimedia file, and relates to the field of information security. The main purpose is to solve the problems that the encryption is relatively complex and the decryption playing speed of the multimedia file is low. The technical scheme provided by the invention comprises following steps of firstly, obtaining the encryption mode of the multimedia file corresponding to a multimedia file identifier, the length information of an encryption secret key and the encryption secret key; through taking the length of the encryption secret key as a unit, carrying out preset logic operations to the data in the multimedia file and the encryption secret key, thus obtaining an encrypted multimedia file; through taking the encryption mode and the length information of the encryption secret key as an encryption file header, according to a front to back sequence of the encryption file header, the encryption secret key and the encrypted multimedia file, generating an encrypted data file; and finally, sending the encrypted data file to a client. The methods and the devices are mainly used for carrying out encryption transmission and decryption playing to the multimedia file.
Owner:BEIJING QIHOO TECH CO LTD +1
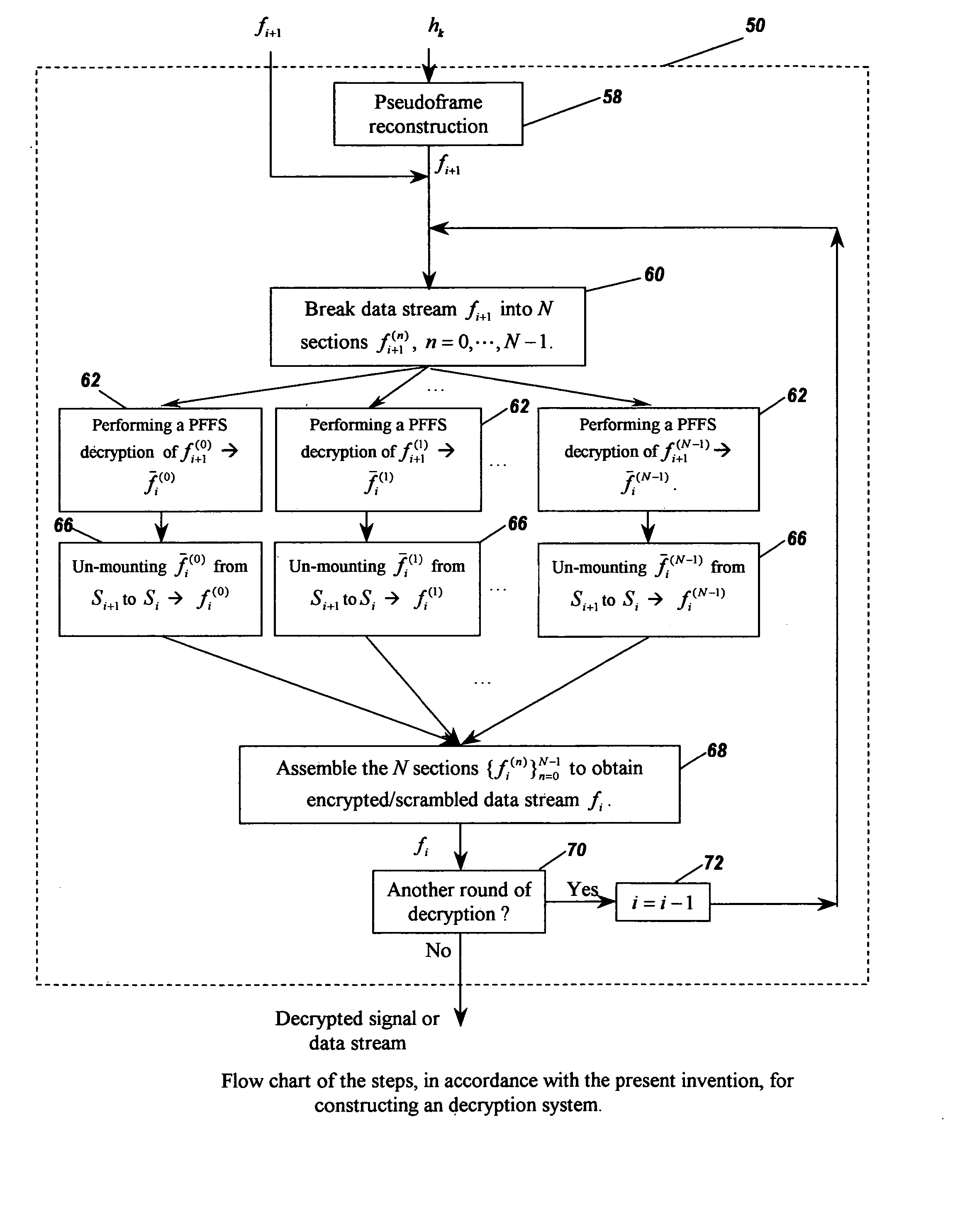
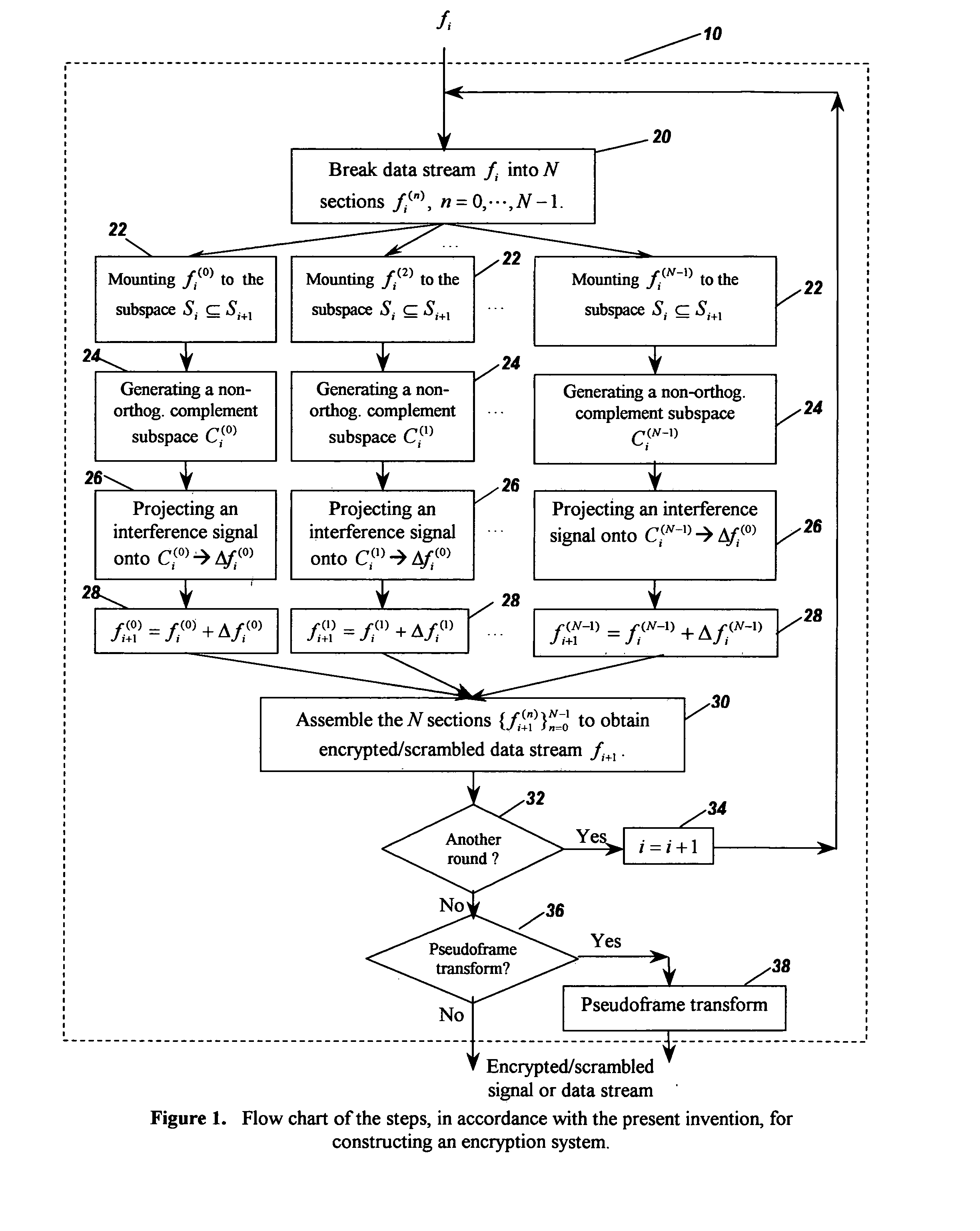
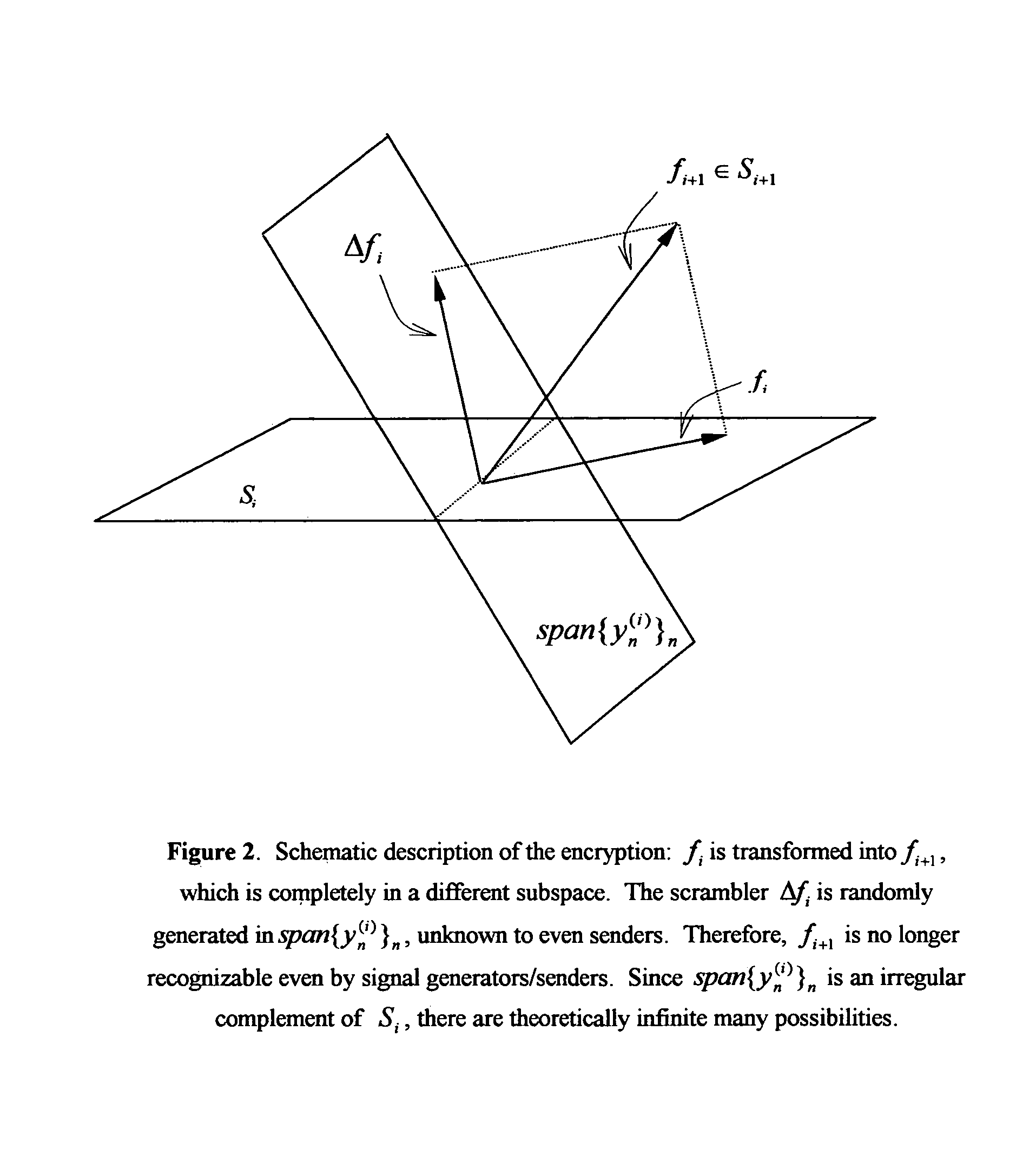
Methods and apparatus for data and signal encryption and decryption by irregular subspace leaping
InactiveUS20070223686A1Fast encryptionFast decryptionData stream serial/continuous modificationSecret communicationPresent methodRandom combination
A data / signal encryption / scrambling and decryption system and methods for constructing said system from irregular subspace leaping. A data / signal is mounted from the first / previous subspace to the second / subsequent subspace. A non-orthogonal complement subspace of the first / previous subspace in the second / subsequent subspace is generated, and spanned by the y-vectors. An encrypting / scrambling data component is generated by either a random combination of the said y-vectors, or by a projection of a partially coherent (with the given data / signal) data onto the span of y-vectors. The encrypting / scrambling is then carried out by combining the given data / signal with the said scrambling data component. The decryption method makes use of pseudoframes for subspace. A set of x-vectors associated with the said y-vectors are evaluated under the principle that the span of x-vectors is orthogonal to the span of y-vectors, and an orthogonal projection of the span of x-vectors covers the first / previous subspace. The said x-vectors forms a pseudoframe for the first / previous subspace. A dual pseudoframe sequence is determined and the decryption is carried out using the pseudoframe expansion with sequences x-vectors and its pseudoframe dual. The said method is fast since it operates on relatively small segments of the data set. The said method has the characteristics that the said scrambling data component is completely unknown to anyone including the message generator / sender, and the said non-orthogonal complementary subspaces have nearly infinite many choices. The combination of the above two uncertainties ensures high security of the present methods.
Owner:LI SHIDONG
Public key cryptographic methods and systems with rebalancing
InactiveUS20080019508A1Improve rendering capabilitiesImprove computing efficiencyPublic key for secure communicationSecret communicationPublic key cryptosystemPublic exponent
A public key cryptosystem and methods for using same including at least one encrypted message wherein the encryption occurs using RSA methods; and at least one key for decrypting the encrypted message(s) wherein the key further comprising a predetermined number of prime factors, including the prime number P, used for the generation of a public modulus N and an exponent e, wherein a proper subset of the prime factors of the modulus N, along with the exponent e, are required to decrypt messages encrypted using the public exponent e and the public modulus N, where e and N are generated using RSA methods, wherein the exponent d for decryption is generated to be as small as possible without compromising security, such that e*d=1 mod (P−1) and gcd(e,d)=1 and the public exponent e contains approximately the same number of bits as the prime number P.
Owner:CRYPTOIP
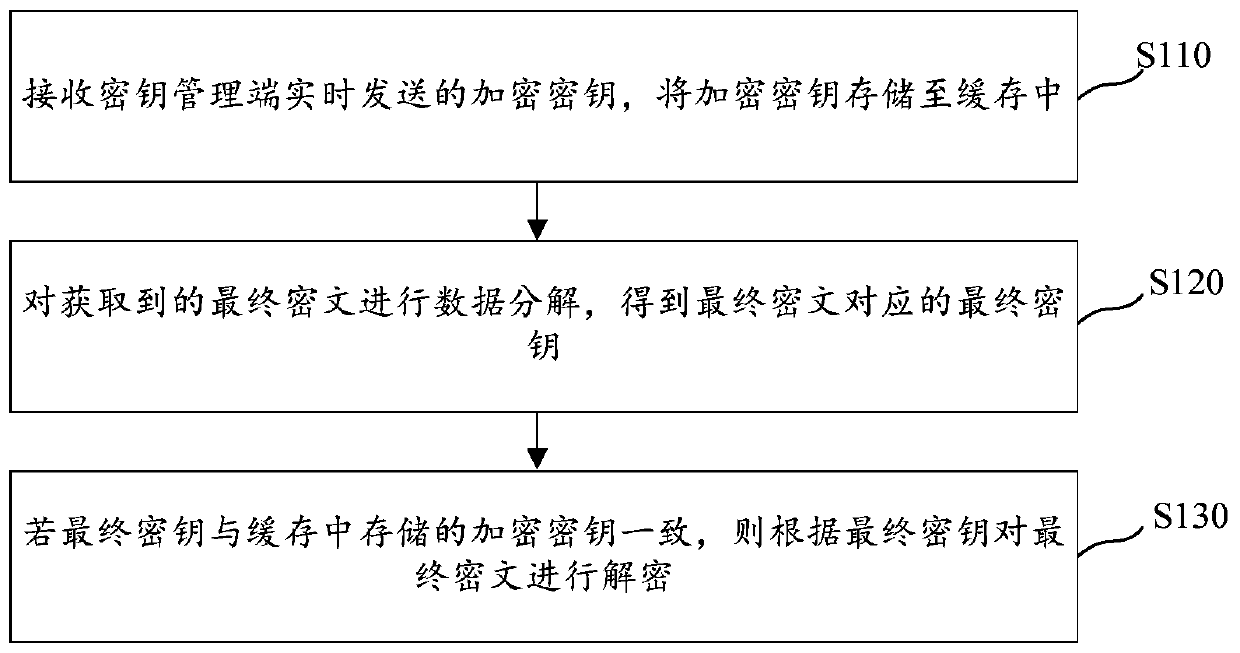
Data processing method and device, computer storage medium and electronic equipment
ActiveCN111131278AReal-time updateImprove decryption efficiencyKey distribution for secure communicationUser identity/authority verificationComputer hardwareTerminal server
The invention relates to the technical field of computers. The invention provides a data processing method, a data processing device, a computer storage medium and electronic equipment. The data processing method is applied to a terminal server for encrypting and decrypting data, the key type used for encryption and decryption processing is a symmetric key, and the data processing method comprisesthe following steps: receiving an encryption key sent by a key management end in real time, and storing the encryption key into a cache; performing data decomposition on the obtained final ciphertextto obtain a final key corresponding to the final ciphertext; and if the final key is consistent with the encryption key stored in the cache, decrypting the final ciphertext according to the final key. According to the data processing method, the security of the secret key can be guaranteed, the decryption speed can be increased, and the project cost is reduced.
Owner:JINGDONG TECH HLDG CO LTD
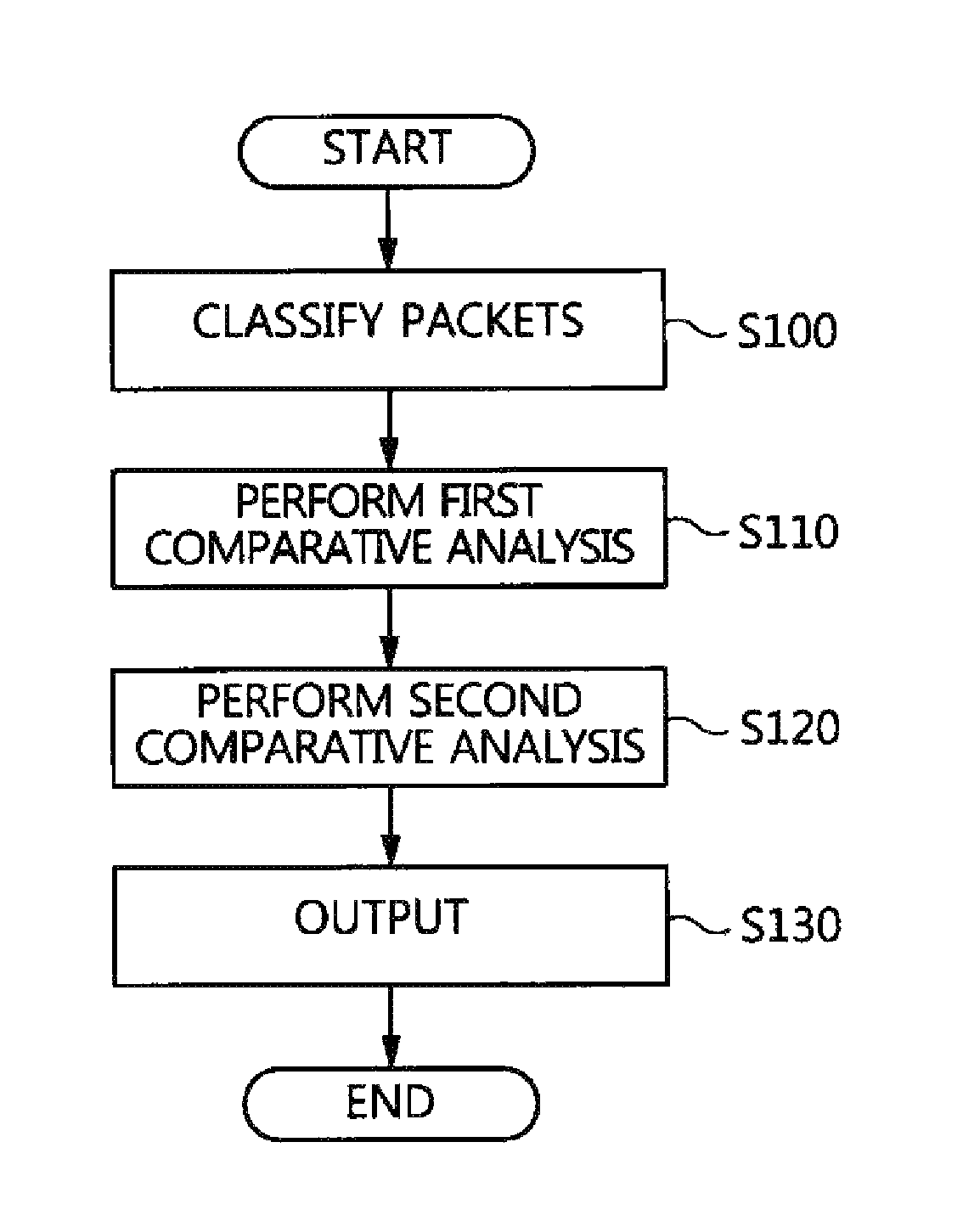
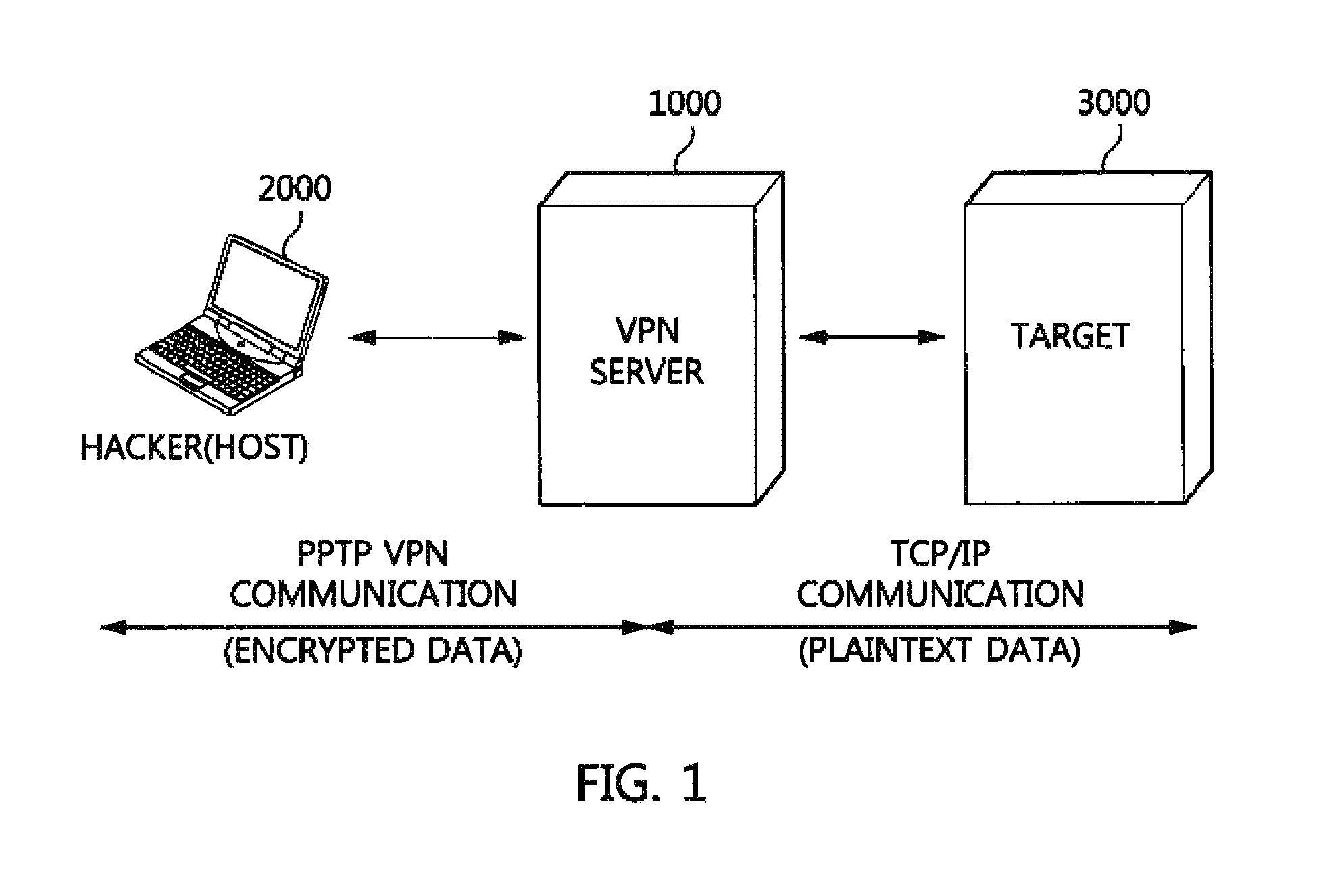
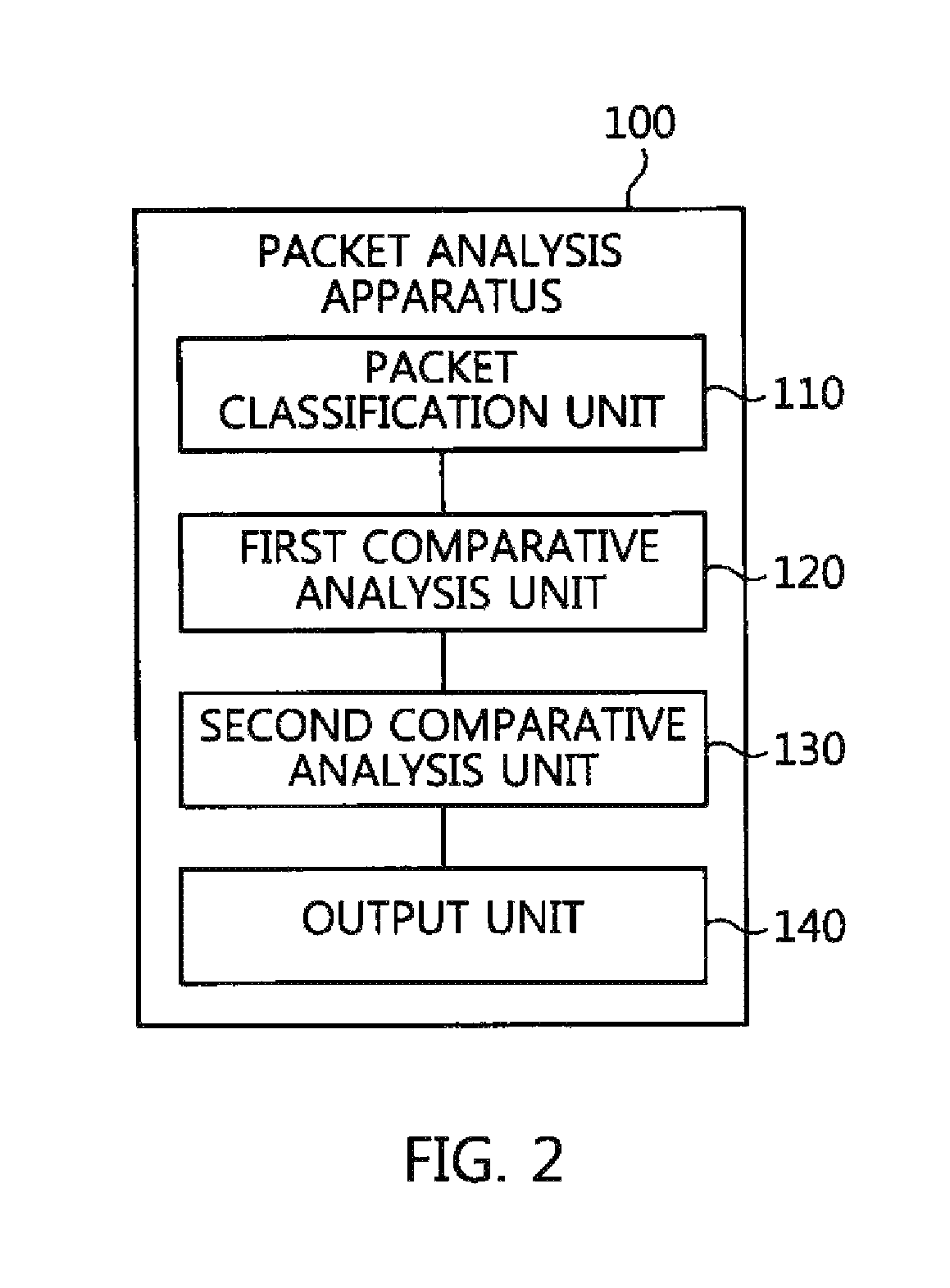
Packet analysis apparatus and method and virtual private network server
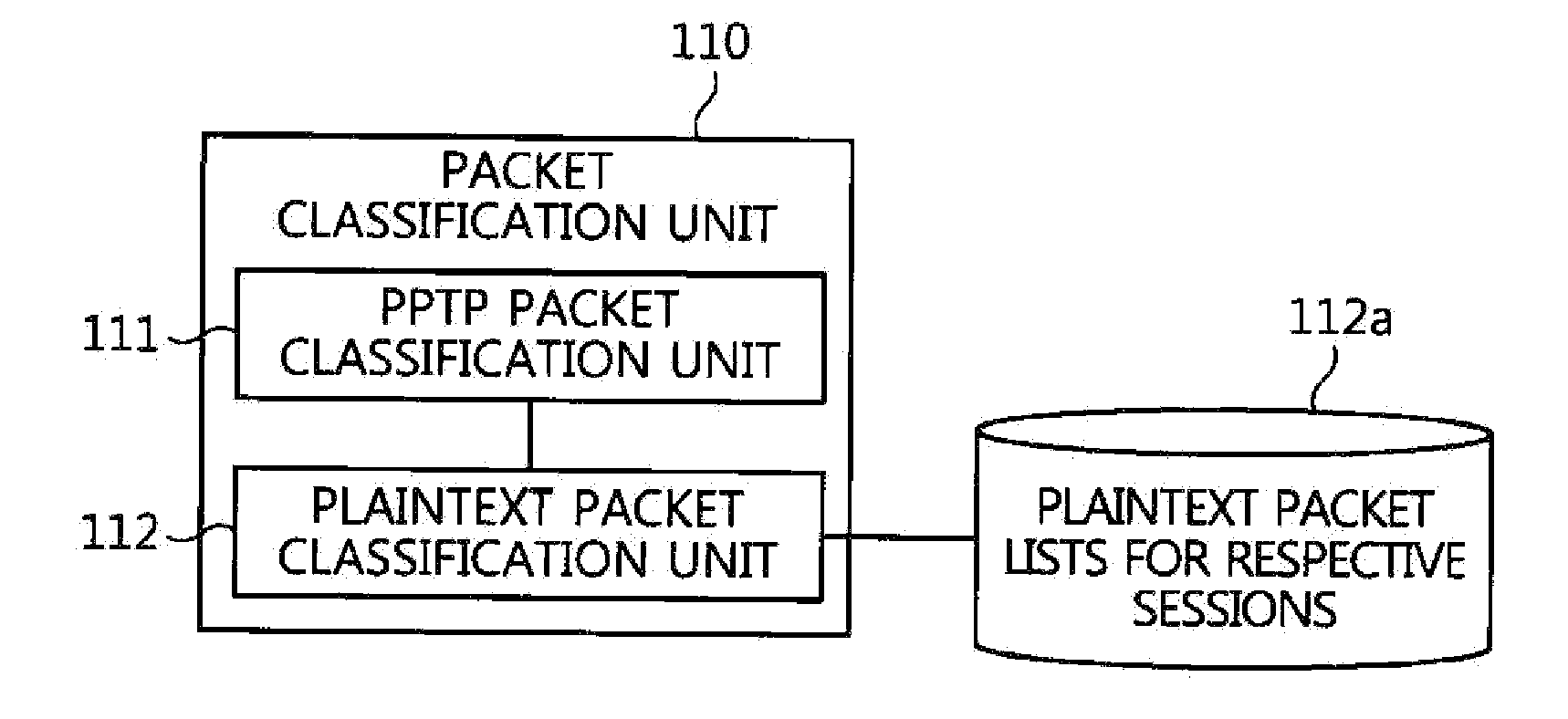
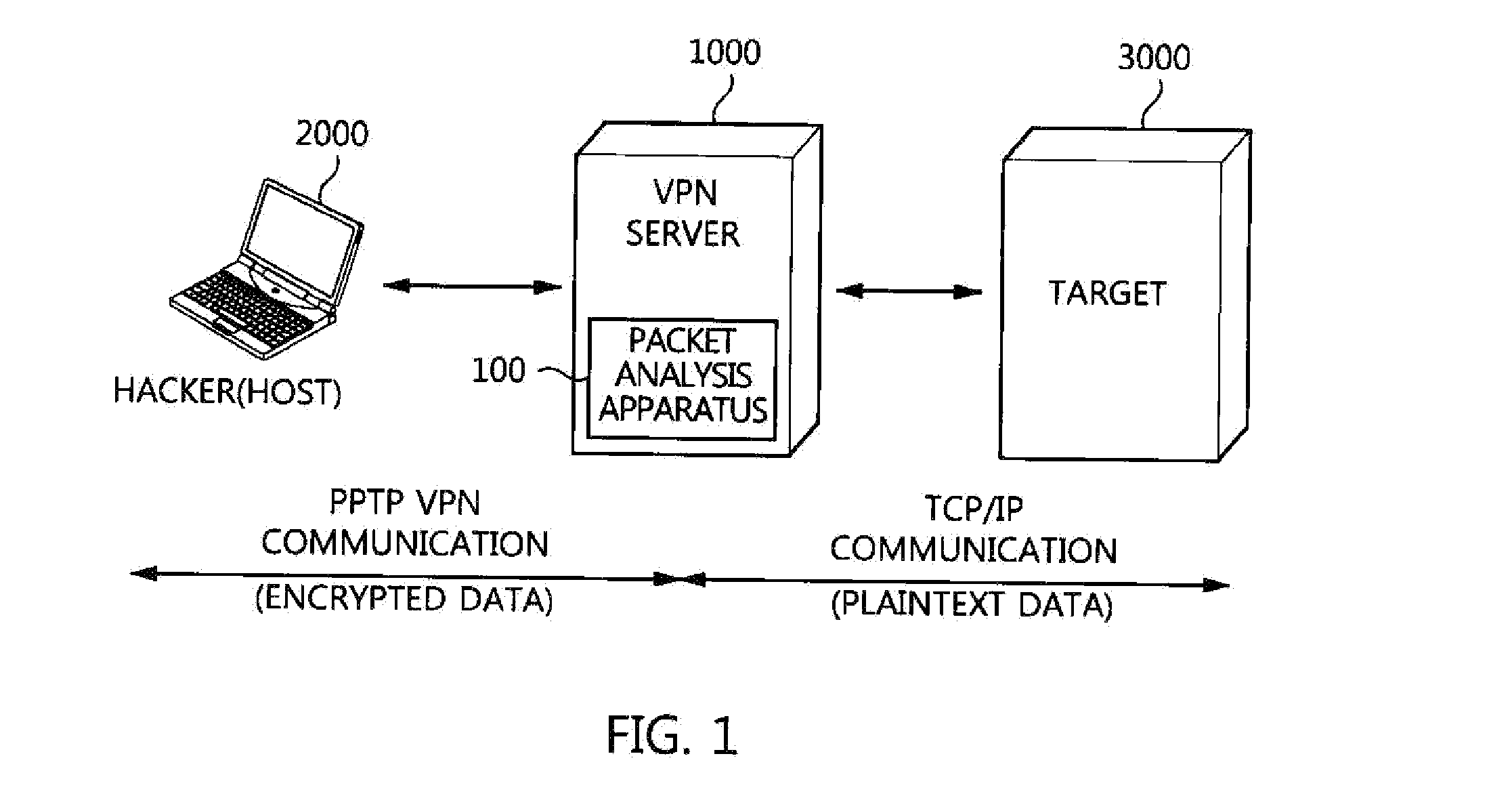
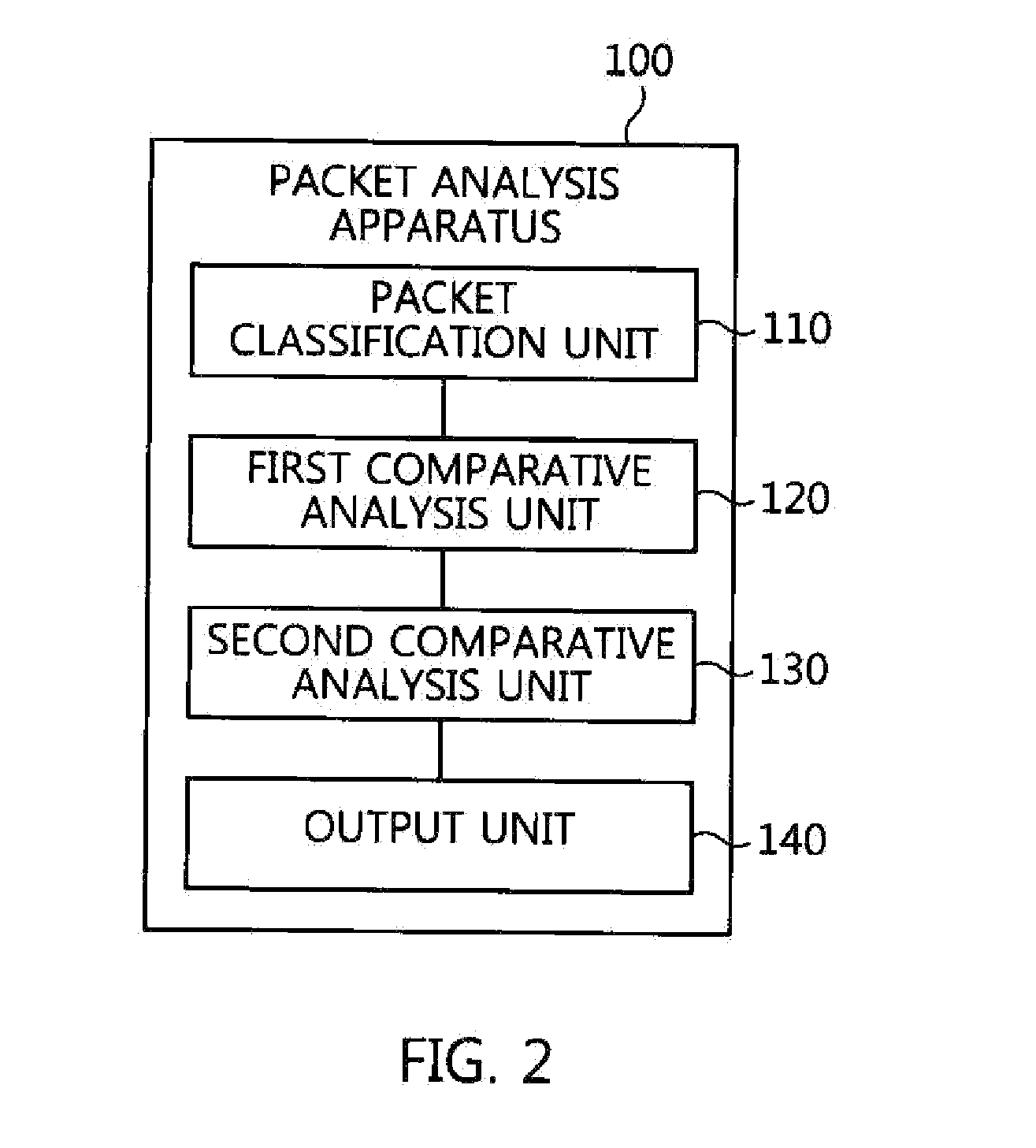
ActiveUS20150195251A1Fast decryptionShort timeUser identity/authority verificationPlaintextPrivate network
A packet analysis apparatus and method and a VPN server, which secure evidence against a situation in which a hacker disguises a packet as a normal packet so as to make an attack using a VPN server as a router. The packet analysis apparatus includes a packet classification unit for classifying packets provided and collected from a host into encrypted VPN packets and plaintext packets. A first comparative analysis unit compares contents of an encapsulated IP datagram of each encrypted VPN packet, obtained by decrypting the encrypted VPN packet, with contents of a plaintext IP datagram that is included in each plaintext packet and that is present for a target to which the host desires to transfer the encrypted VPN packet. A second comparative analysis unit compares lengths of the encapsulated IP datagram and the plaintext IP datagram with each other.
Owner:ELECTRONICS & TELECOMM RES INST
Encryption method based on DES
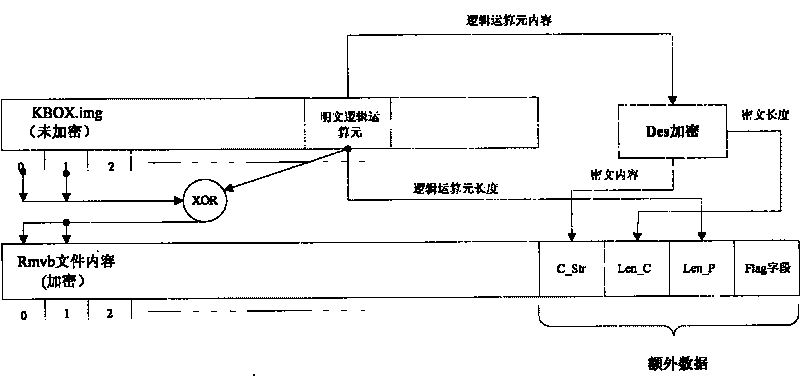
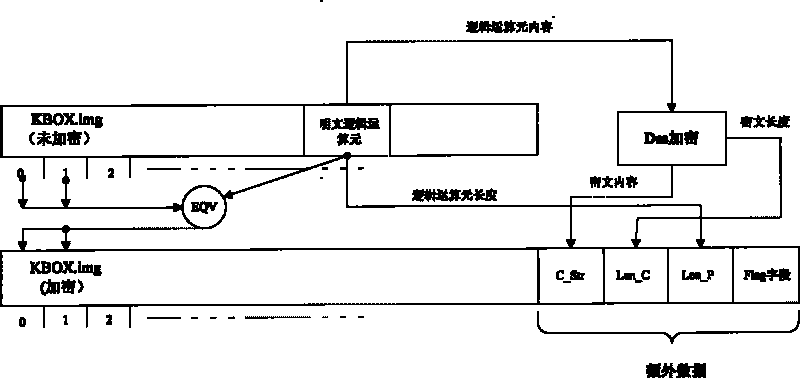
InactiveCN101707521AEasy to operateFast decryptionEncryption apparatus with shift registers/memoriesComputer hardwareLogical operations
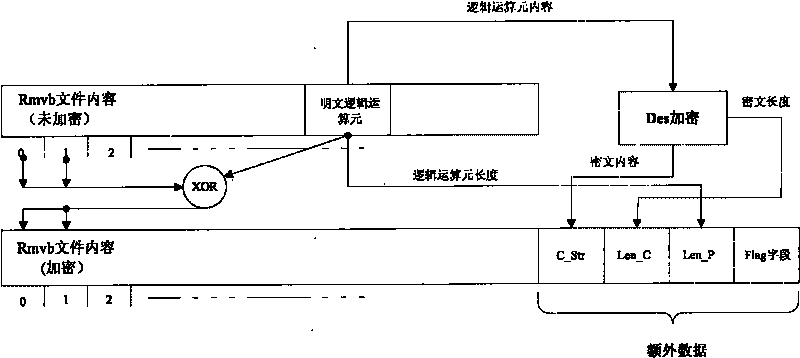
An encryption method based on DES comprises the following steps: randomly obtaining a character string with the length being x and used for logical operation from a file to be encrypted; dividing the file to be encrypted into sections with the length of being y, wherein y is more than and equal to x, the length of the final section is set as z, and z is less than or equal to y; conducting left alignment and right alignment on the subsections and the character string, and conducting logical operation with the character string so as to generate the encryption file, when the subsections and the character string are in the left alignment, conducting the logical operation with x bit on the left haft part, and when the subsections and the character string are in the right alignment, conducting the logical operation with x bit on the right half part, and if z is more than or equal to x, conducting the logical operation with x bit on the final small section, or conducting the logical operation with z bit; and by the DES algorithm, encrypting the character string to obtain encrypted logic element, and then appending the content and the length of the logic element, the length of the character string, and user-defined mark sections behind the encryption file. The method has the advantages that the rapid for decryption is quick, the requirement of playing when conducting decryption is met, and the encryption scheme is flexible.
Owner:FUJIAN STAR NET EVIDEO INFORMATION SYST CO LTD
Recorder
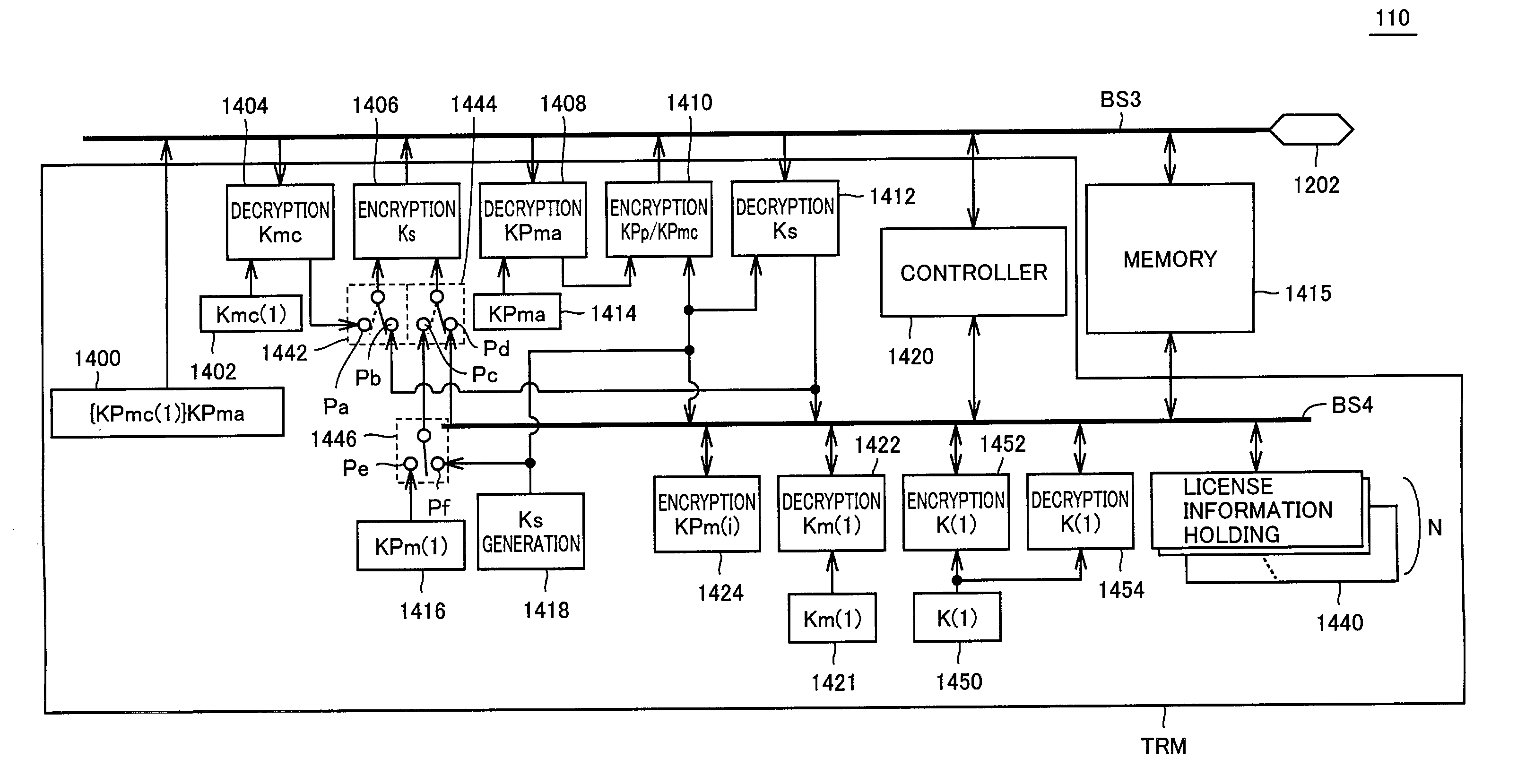
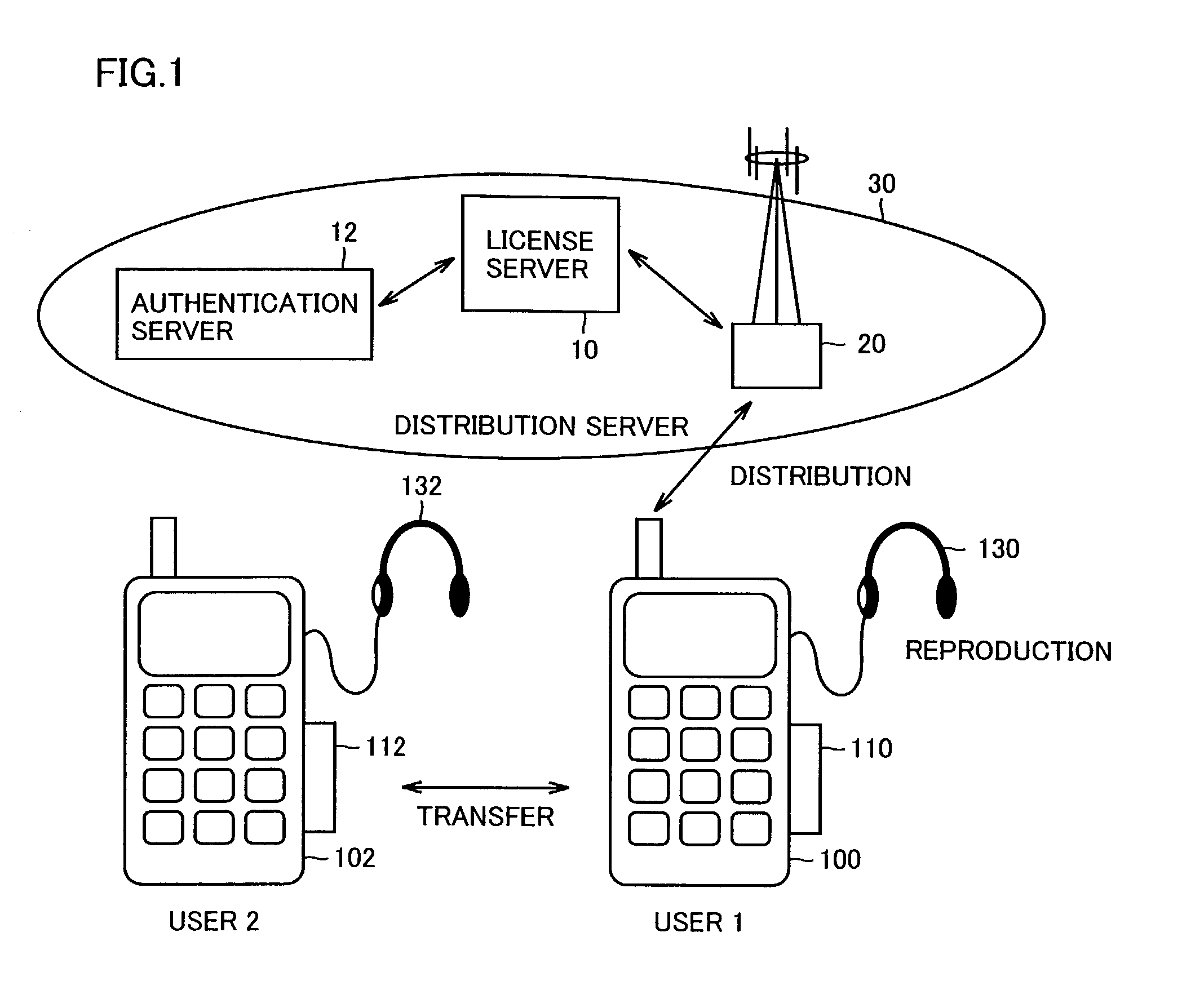
InactiveUS7158641B2Fast decryptionAddressing slow performanceKey distribution for secure communicationDigital data processing detailsEngineeringMemory cards
A memory card (110) decodes data delivered to a data bus (BS3) and extracts a session key (Ks1) sent from a server from the data. Based on the session key (Ks1), an encrypting section (1406) encrypts a public encryption key (KPm (1)) of the memory card (110) and delivers it to a server through the data bus (BS3). The memory card (110) receives data including a license key (Kc) and a license (ID) encrypted with the public encryption key (KPm (1)) different with memory card to memory card, decrypts the data, encrypted it again with uniquely given secret key (K(1)), and stores it in a memory (1415).
Owner:SANYO ELECTRIC CO LTD +1
SM9-based attribute encryption method and system under large attribute set
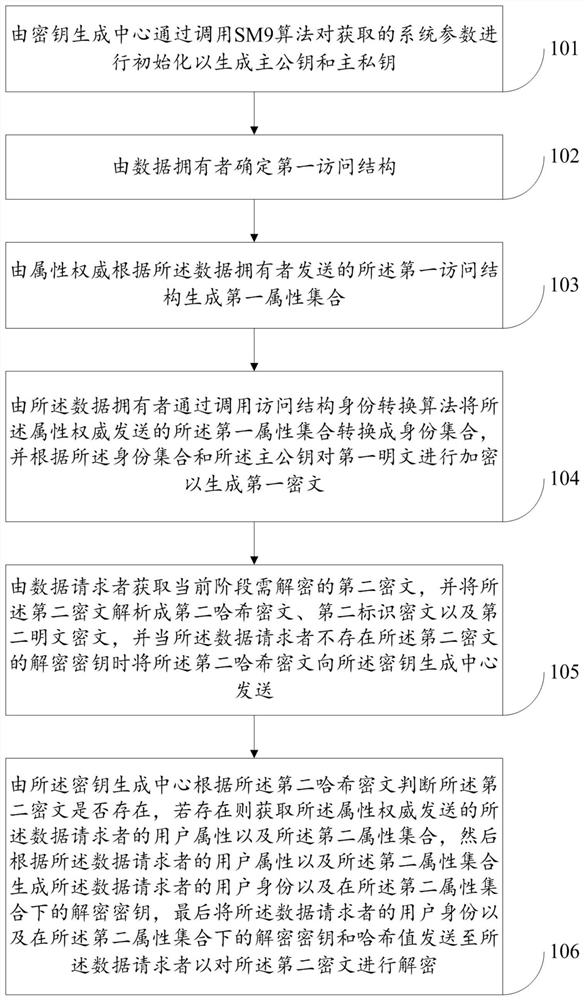
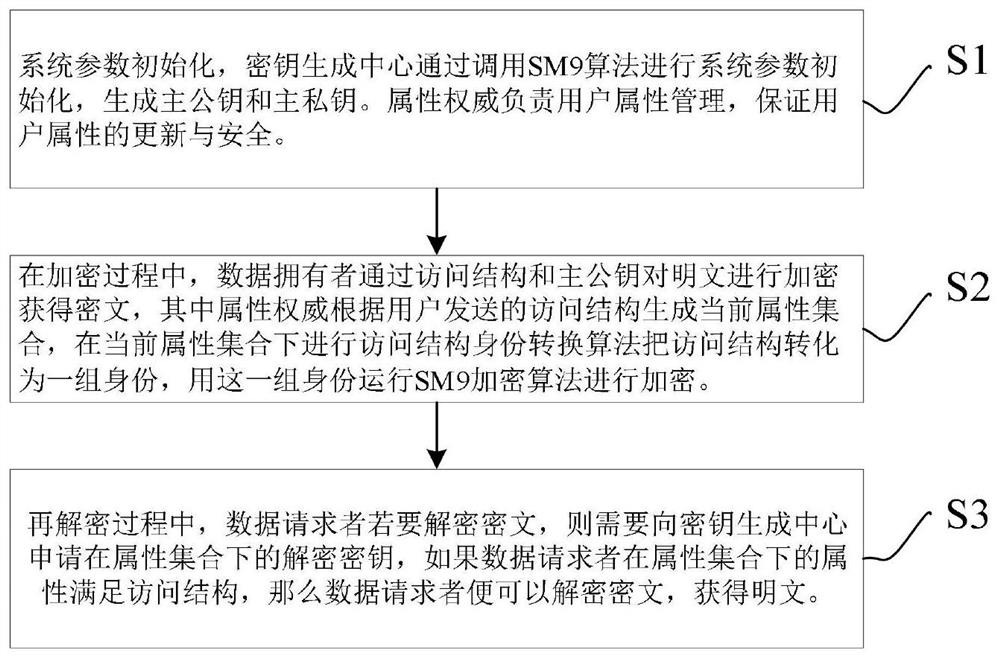
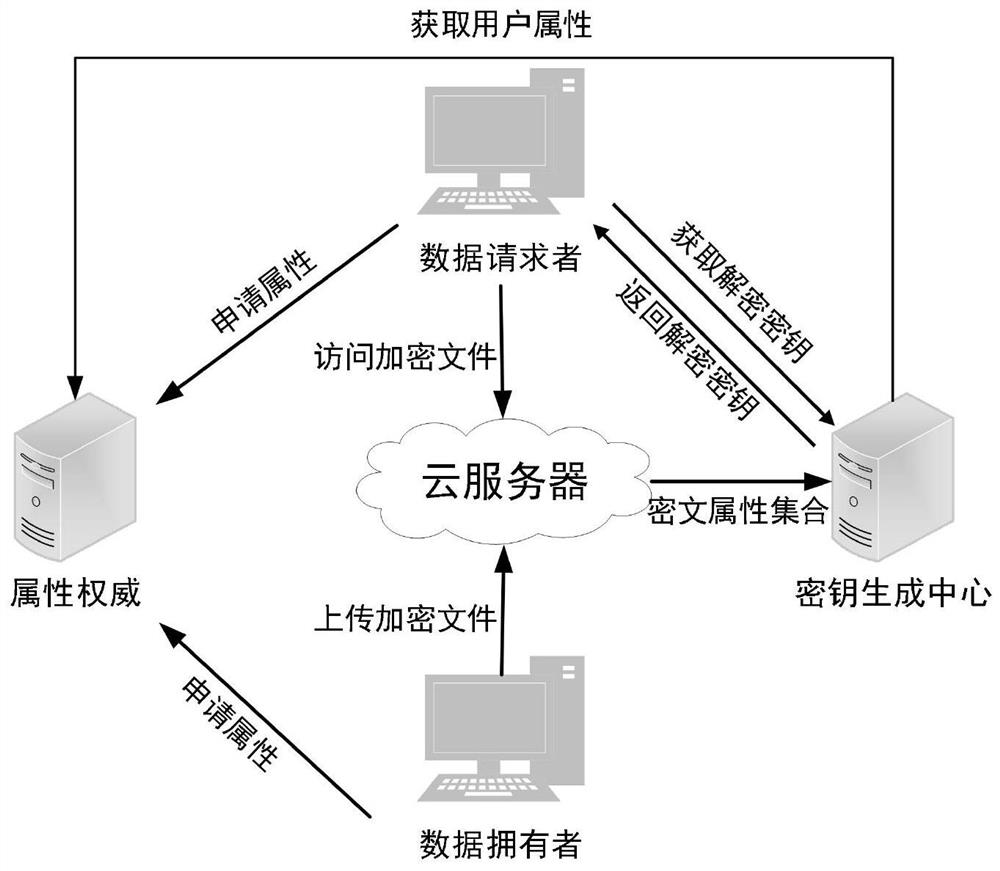
ActiveCN112787822AGuaranteed dynamic performanceImprove efficiencyUser identity/authority verificationPlaintextAccess structure
The invention discloses an SM9-based attribute encryption method and system under a large attribute set, and relates to the technical field of information encryption, and the method comprises the steps that a key generation center generates a main public key and a main private key; the data owner determines a first access structure; the attribute authority generates a first attribute set according to the first access structure; the data owner calls an access structure identity conversion algorithm to convert the first attribute set into an identity set, and encrypts the first plaintext according to the identity set and the main public key to generate a first ciphertext; the data requester obtains a second ciphertext needing to be decrypted at the current stage; and the key generation center judges whether the second ciphertext exists or not, and if yes, the second ciphertext is decrypted according to the user identity of the data requester and the decryption key and the hash value under the second attribute set. According to the invention, the flexibility, the dynamism and the high efficiency of one-to-many data sharing are ensured in a cloud environment.
Owner:GUIZHOU UNIV
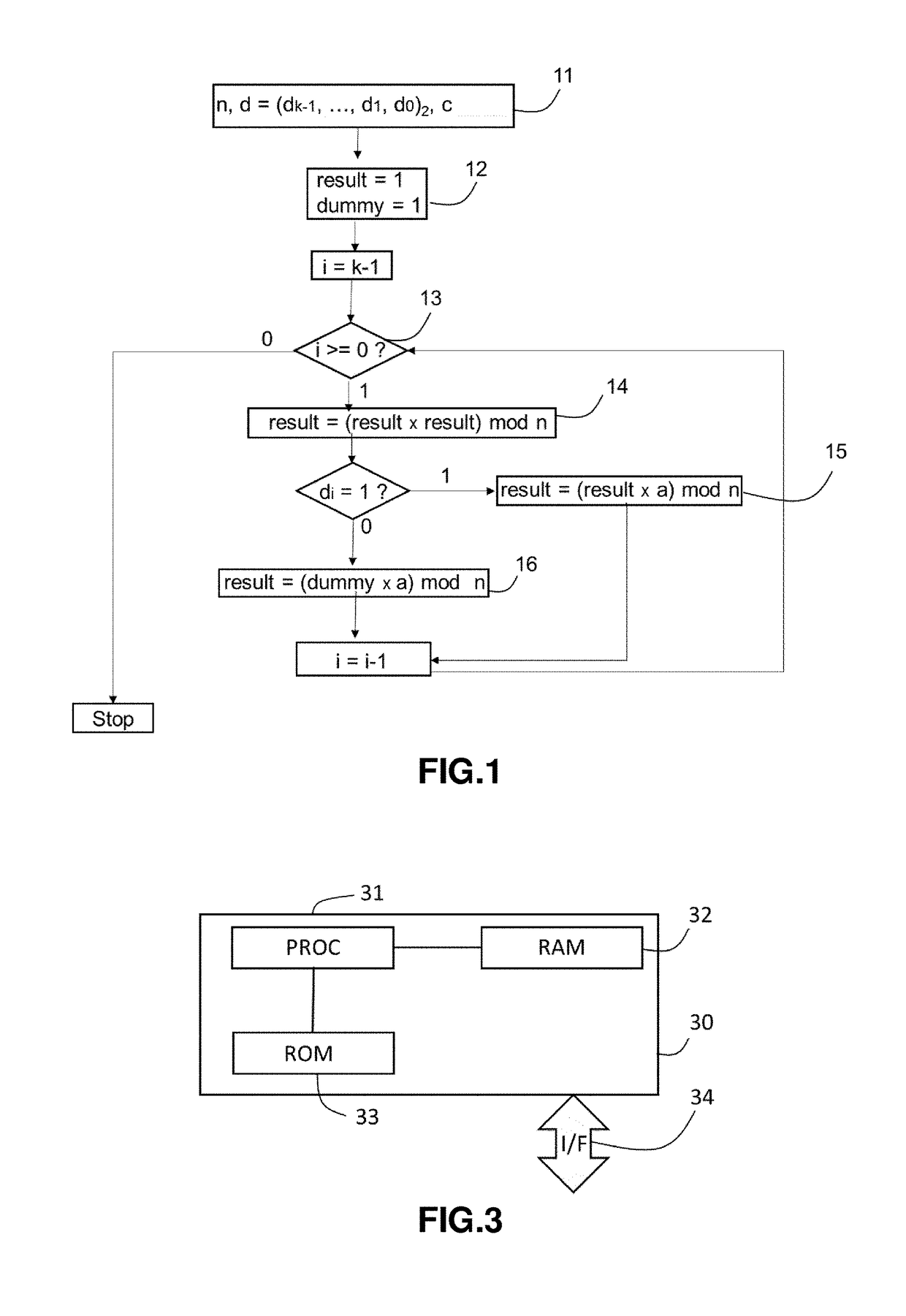
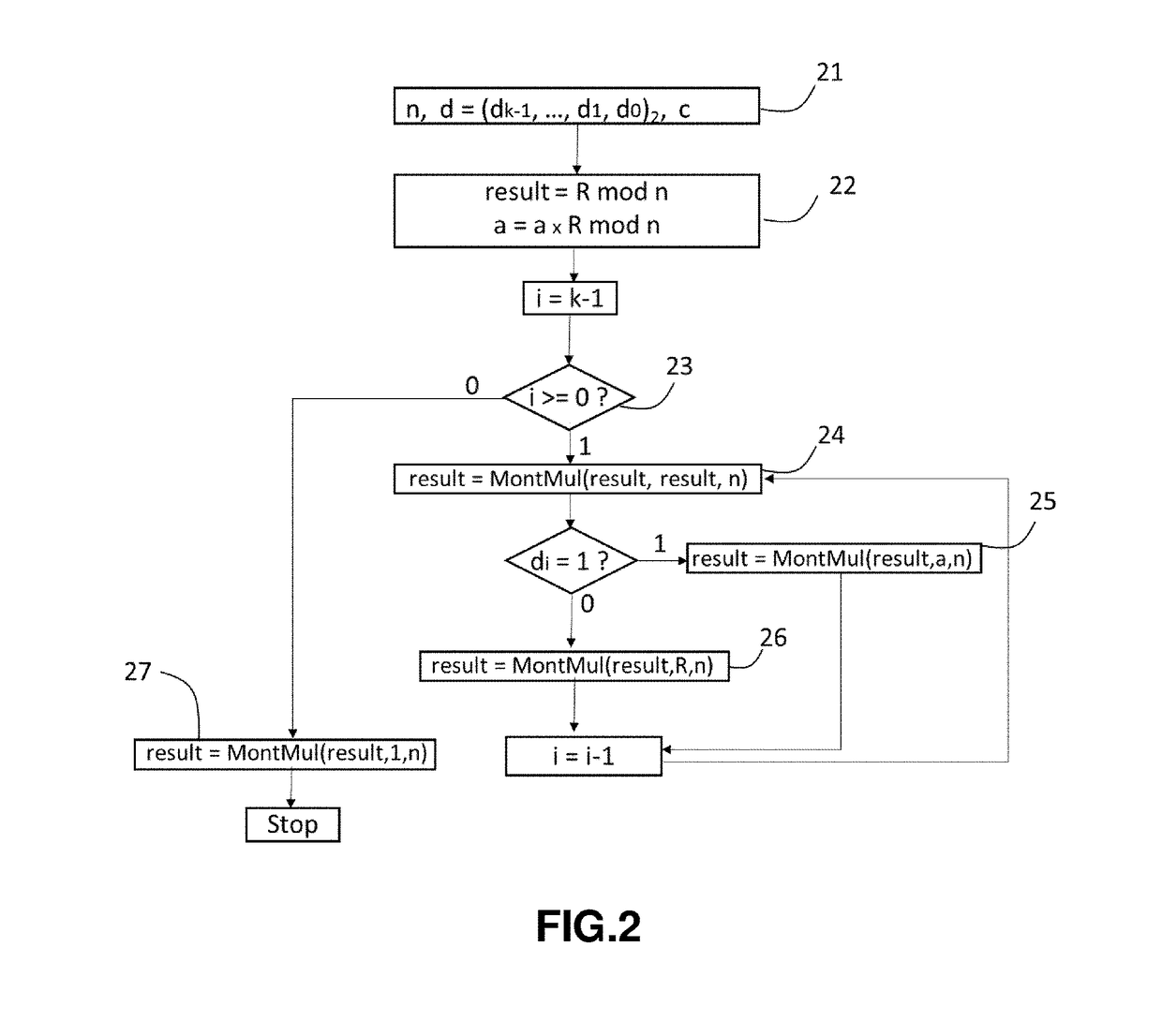
Countermeasure to safe-error fault injection attacks on cryptographic exponentiation algorithms
InactiveUS20190089523A1Simple and efficient solutionFast decryptionEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareCountermeasure
There is disclosed a countermeasure using the properties of the Montgomery multiplication for securing cryptographic systems such as RSA and DSA against, in particular, safe-error injection attacks. In the proposed algorithm, the binary exponentiation b=ad mod n is iteratively calculated using the Montgomery multiplication when the current bit di of the exponent d is equal to zero. In that case, the Montgomery multiplication of the actual result of the exponentiation calculation by R is realized. Thanks to this countermeasure, if there is any perturbation of the fault injection type introduced during the computation, it will have visible effect on the final result which renders such attack inefficient to deduce the current bit di of the private key d.
Owner:GEMPLU
Packet analysis apparatus and method and virtual private network server
Owner:ELECTRONICS & TELECOMM RES INST
Decryption device and method and system on chip
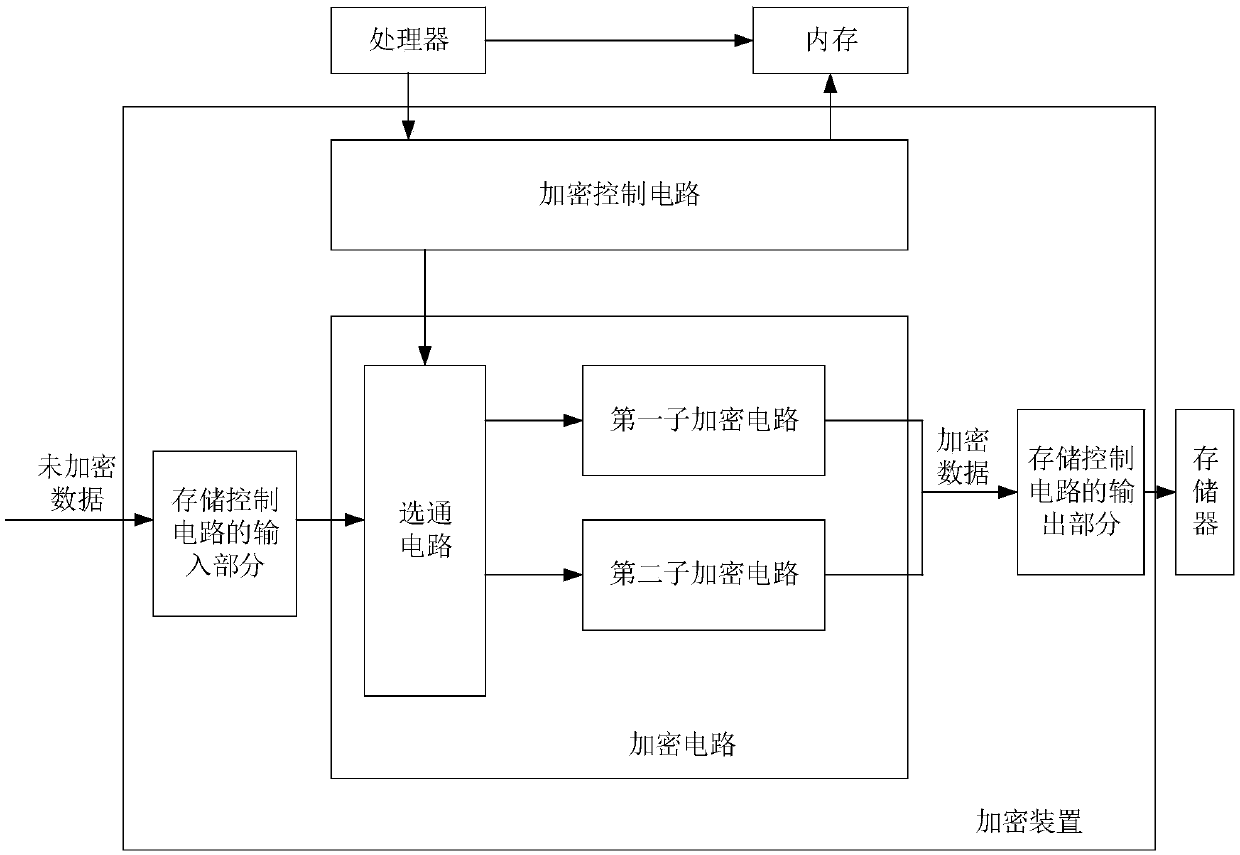
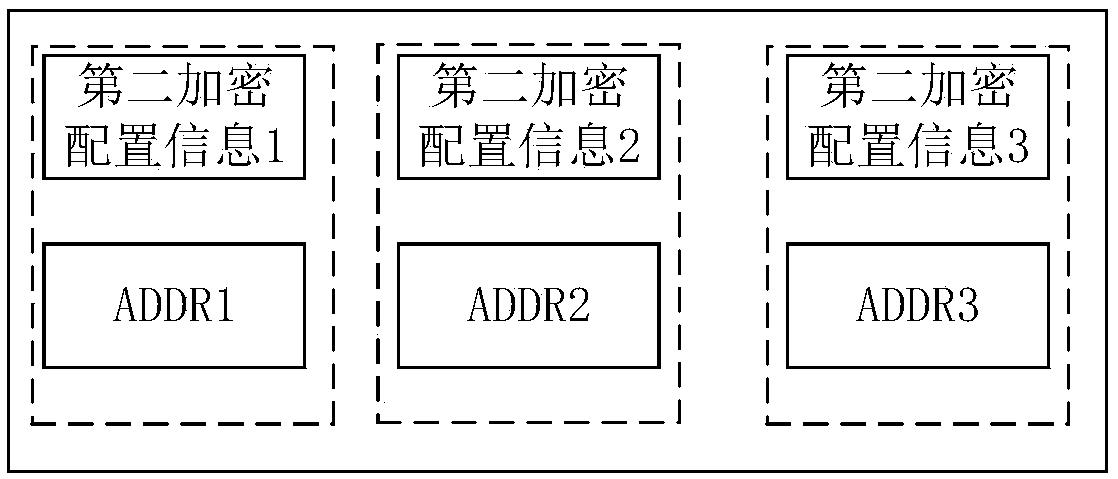
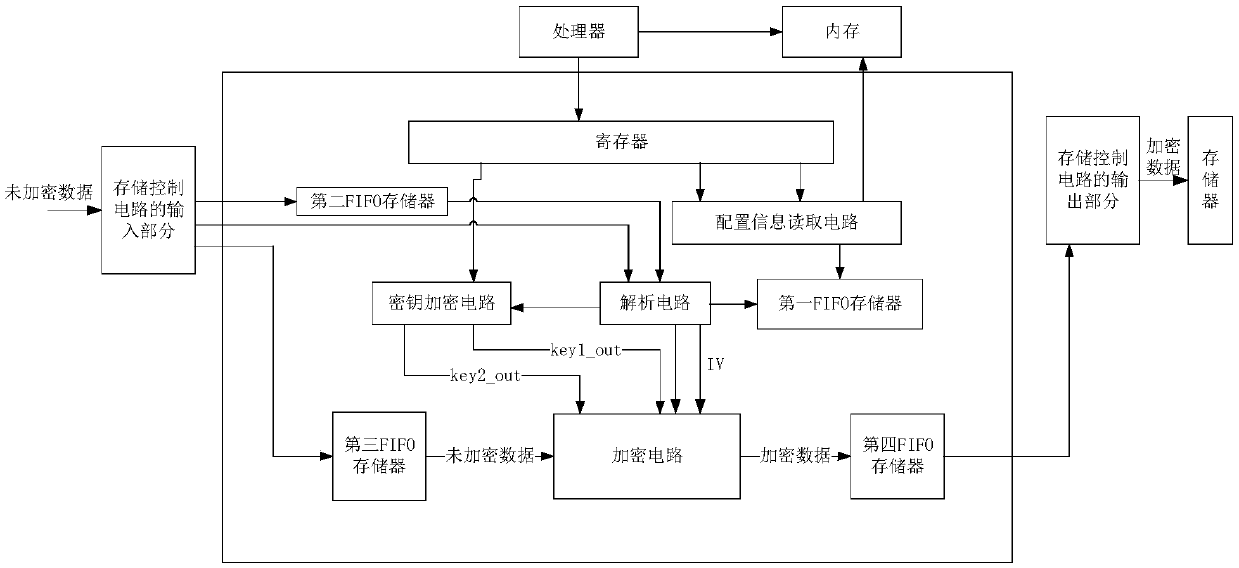
InactiveCN109670347AEfficient decryptionDecrypt fastDigital data protectionInternal/peripheral component protectionMemory addressControl signal
The invention provides a decryption device and method and a system on chip, the decryption device comprises a decryption control circuit and a decryption circuit, and the decryption circuit comprisesa plurality of decryption sub-circuits. The decryption control circuit is used for receiving the first decryption configuration information sent by a processor, and the first decryption configurationinformation comprises the first control information for enabling the decryption control circuit and a memory address. The decryption control circuit is also used for reading the second decryption configuration information used for representing a corresponding decryption algorithm from the memory address according to the first control information, and generating a control signal corresponding to the decryption algorithm according to the second decryption configuration information. The decryption circuit is used for selecting a corresponding sub-decryption circuit according to a decryption algorithm corresponding to the control signal; and the sub-decryption circuit is used for decrypting the encrypted data to obtain decrypted data. According to the method, the decryption speed is greatly improved, and the delay caused by decryption is very small, so that the influence on the storage experience of a user is very small.
Owner:ALLWINNER TECH CO LTD
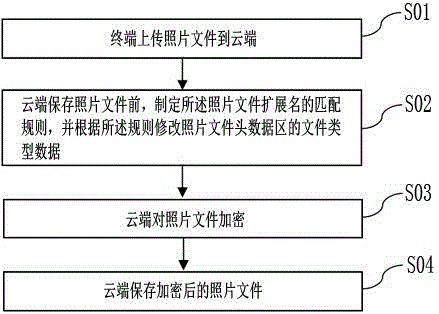
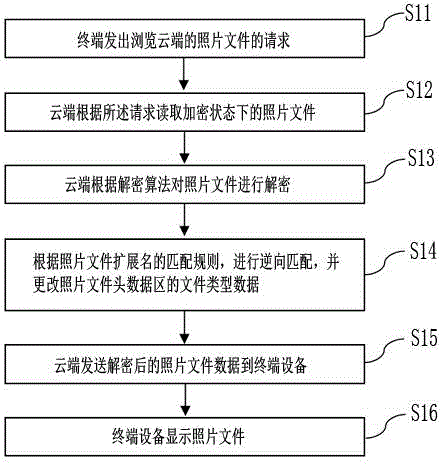
Rapid encryption and decryption method of family cloud photos
InactiveCN105100186AHigh access and decryption efficiencyImprove decryption efficiencyDigital data protectionTransmissionComputer terminalEncryption
Provided is a rapid encryption method of family cloud photos. The rapid encryption method includes the steps that a terminal uploads photo files to a cloud end; the cloud end makes the matching rules of photo file extension names before the photo files are saved, and modifies the file type data in a photo file header data area based on the rules; the cloud end encrypts the photo files; and the end cloud saves the encrypted photo files. The invention further includes a rapid decryption method which achieves the aim of rapid decryption by performing reverse implementation of the matching rules of the photo files. The rapid decryption method is particularly suitable for family cloud, and the decryption speed is fast by comparing with a conventional encryption manner, network accessing efficiency is high, and the speed experience of users to browse photos can be improved.
Owner:MEIBEIKE TECH CO LTD
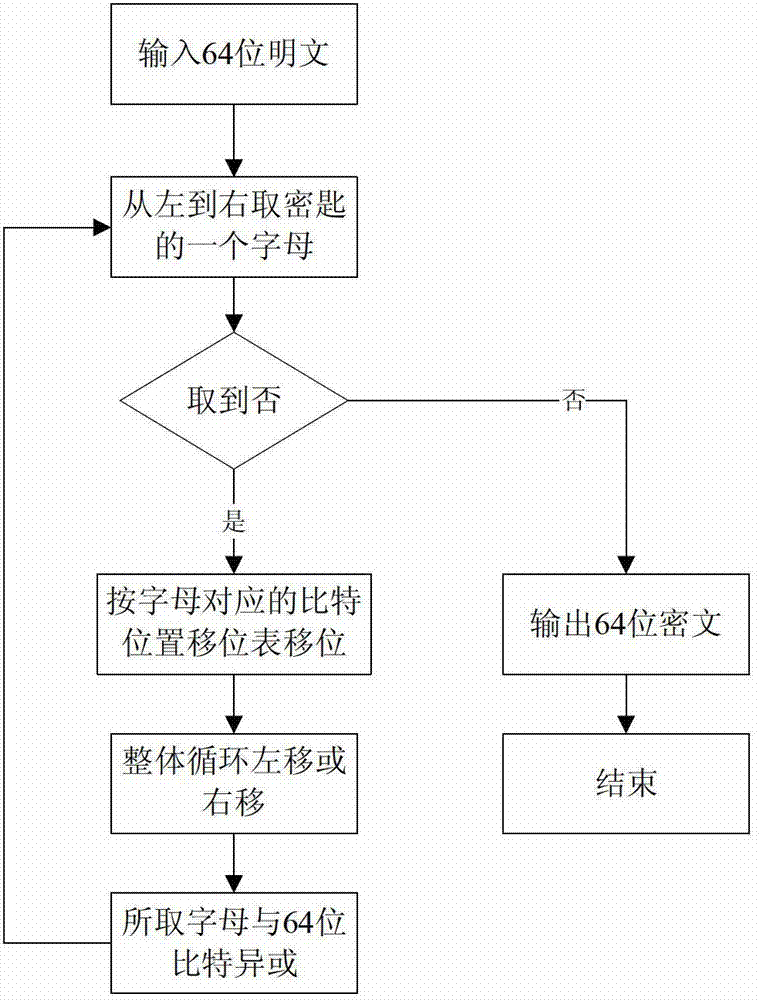
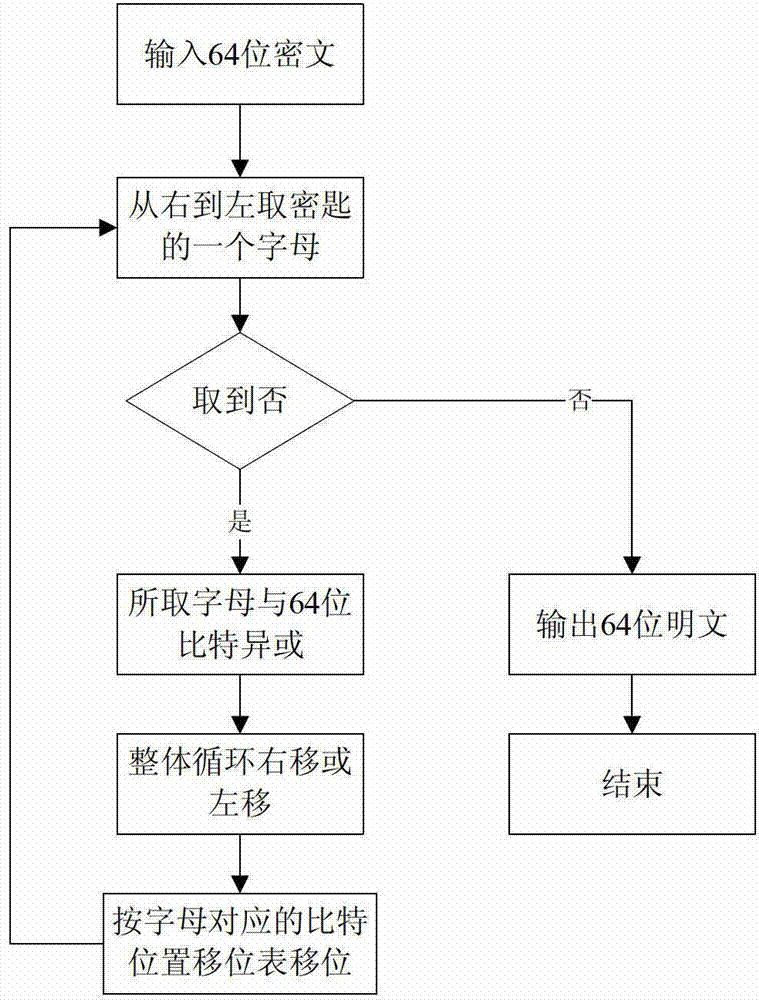
Magic cube encryption and decryption method
The invention discloses a magic cube encryption method, which belongs to the technical field of computer information security. The method is characterized in that a key is specially defined, each character in a key character string is used for expressing one rotary operation of a magic cube, and the rotary operation corresponds to a transposition rule of a series of magic cube diamond sequence numbers; one character in the key is sequentially obtained from left to right in encryption, a series of transposition is carried out on bit number values of a plaintext according to the transposition rule set by the character, exclusive or operation is performed by utilizing a letter after being circularly moved leftwards or rightwards, and finally a ciphertext is obtained. The invention also provides a decryption method based on the encryption method, and the decryption process is the invert operation of the encryption operation process. Due to the adoption of the rotation concept of the magic cube, the decryption speed is fast, the key length is not restricted, the encryption strength is large, the ciphertex highly depends on the key, so that different decipher methods such as password attack and enumeration attack can be prevented.
Owner:武汉迎风聚智科技有限公司
Model encryption method and related equipment
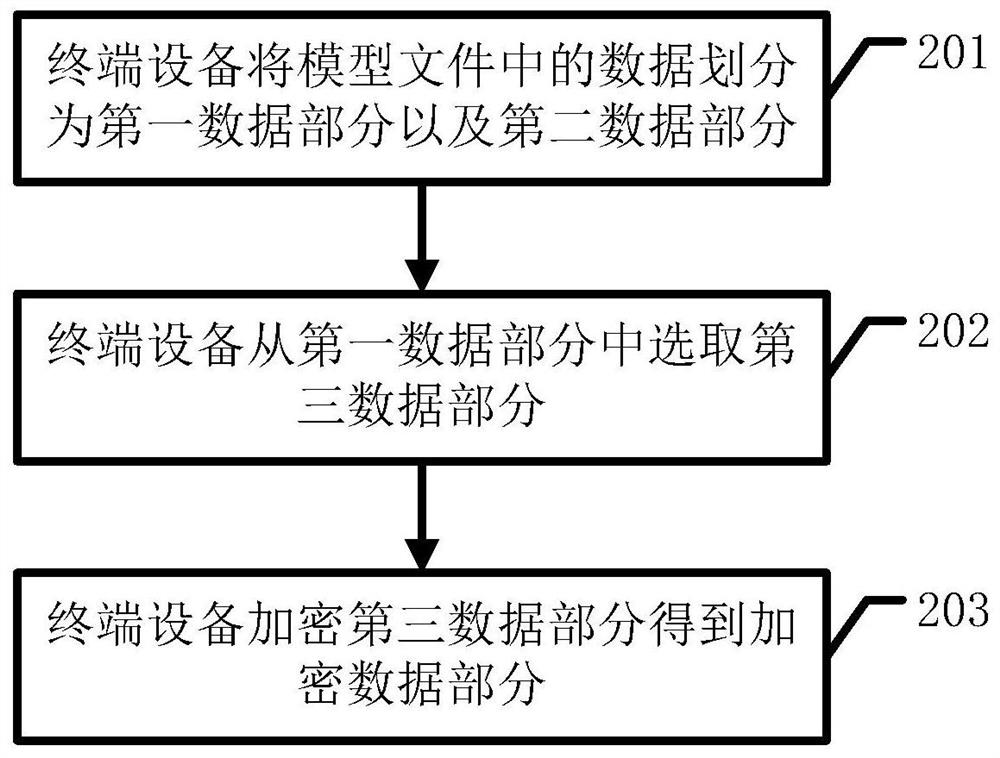
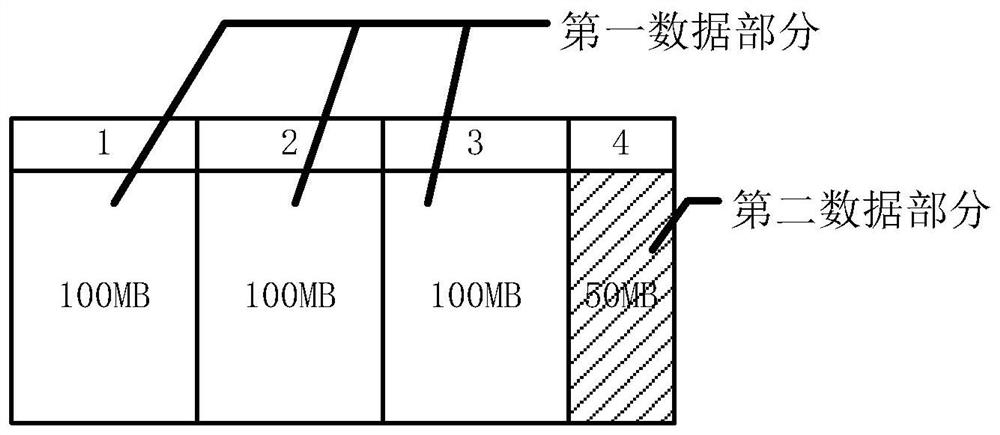
PendingCN114329504AFast encryptionFast decryptionDigital data protectionTerminal equipmentApplication software
The invention discloses a model encryption method in the field of software, and the method comprises the steps: dividing data in a model file into a first data part and a second data part through terminal equipment; and the terminal equipment selects a third data part from the first data part, the third data part is a to-be-encrypted part and is smaller than the first data part, and the terminal equipment encrypts the third data part to obtain an encrypted data part. Thus, the terminal equipment encrypts part of data in the model file, the encryption speed of the terminal equipment on the model file and the decryption speed of the terminal equipment on the model file are improved, the starting speed of application software integrated with a large model is increased, and the user experience is improved.
Owner:HUAWEI TECH CO LTD
Data encryption and decryption device and encryption and decryption method thereof
The invention discloses a data encryption and decryption device and an encryption and decryption method thereof. The data encryption and decryption device comprises a device body, an encryption deviceand a decryption device. The encryption device comprises a data receiving module, a data analysis module, a data judgment module, a microprocessor, a key selection unit, an encryption module, a storage module and a data sending module. The decryption device comprises a database, a determination module, a search module, a call unit, a decryption request module, a decryption algorithm request unit,a decryption module and an output unit. The encryption device and the decryption device are connected through adoption of an RS232 interface or an RS485 interface. In order to ensure the security ofdata, a level of the data is analyzed according to the data analysis module, an encryption method of the data is selected through adoption of the key selection unit, the data is enabled to obtain an encryption method only applicable to related data, the data decryption device searches an encryption mode of the data through adoption of the search module, a corresponding decryption algorithm is called through adoption of the call unit, and the decryption speed is accelerated.
Owner:BEIJING JUNXIU CONSULTATION CO LTD
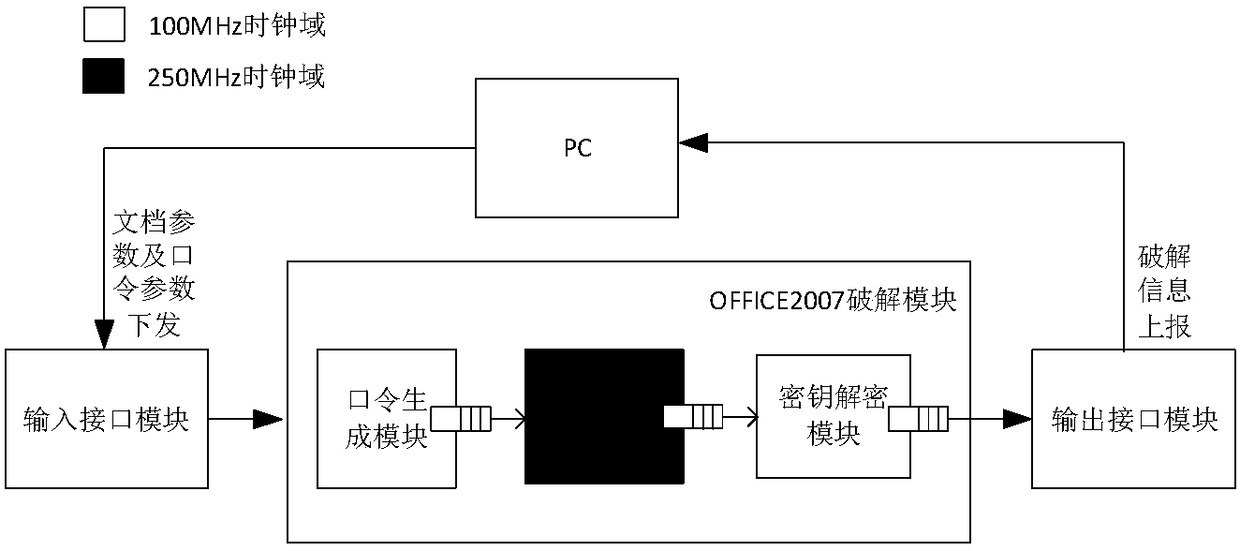
OFFICE2007 document cracking system based on FPGA hardware
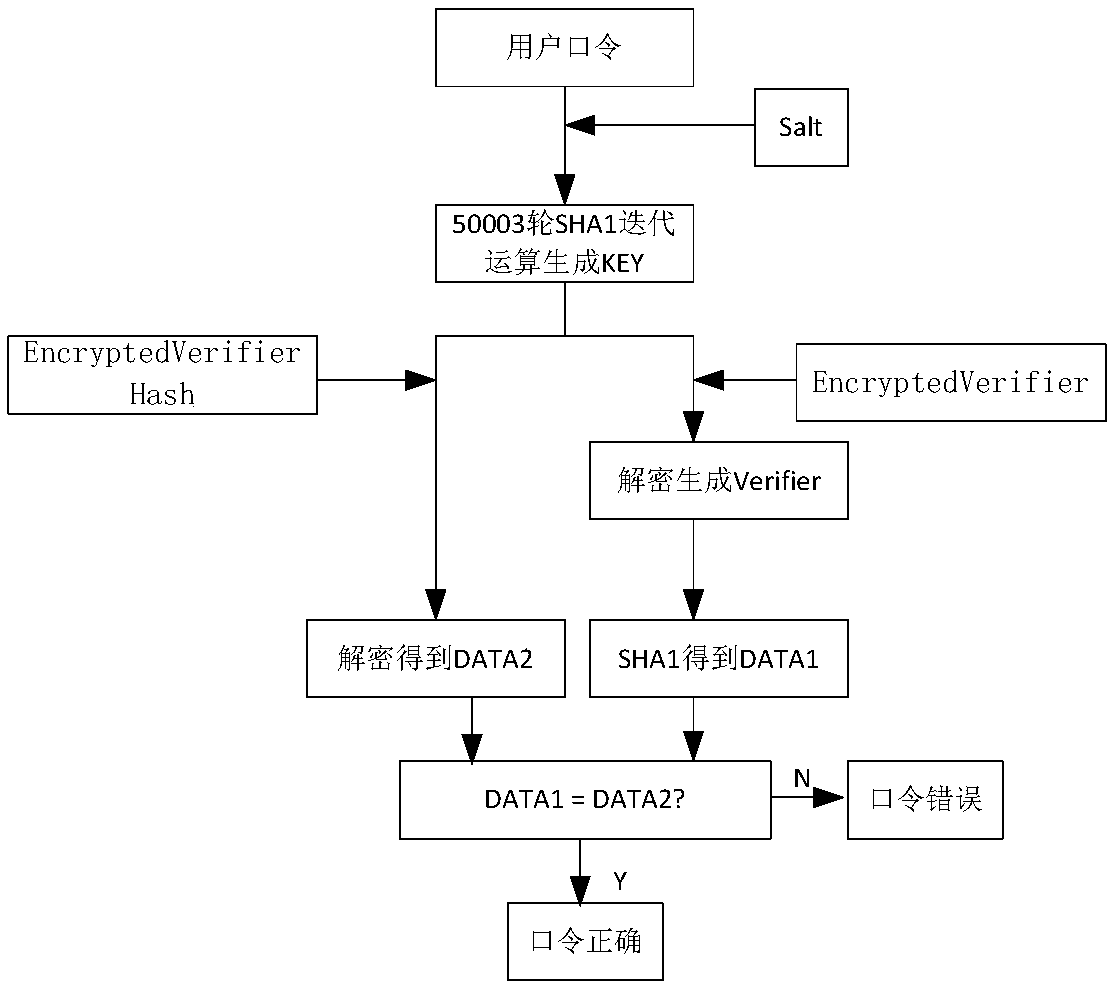
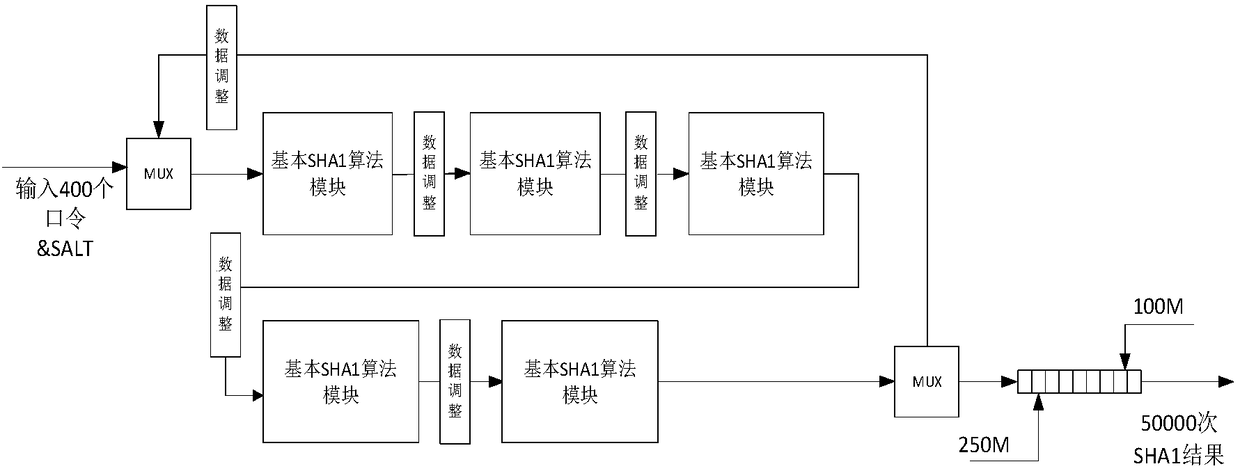
InactiveCN108566269ASpeed up iterative operationsIncrease clock frequencyEncryption apparatus with shift registers/memoriesDigital data protectionPasswordComputer engineering
The invention discloses an OFFICE2007 document cracking system based on FPGA hardware, comprising: an input interface module, an OFFICE2007 cracking module unit and an output interface module, whereinan OFFICE2007 cracking module includes: a password generation module, a SHA1 iterative operation module, and a key decryption module; and the output interface module reports the cracking result. Theinvention fully utilizes the FPGA technology to accelerate the operation, and N basic SHA1 computing modules are cascaded to participate in the tens of thousands of iterative SHA1 operations, therebysimultaneously increasing the module clock frequency and accelerating the SHA1 iterative operation. The iterative SHA1 operation module and the key decryption module may work in parallel to improve the exhaustive speed of the OFFICE2007 document password, so that the decryption speed of the document is significantly improved.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
Rapid decryption method for homomorphic encryption scheme
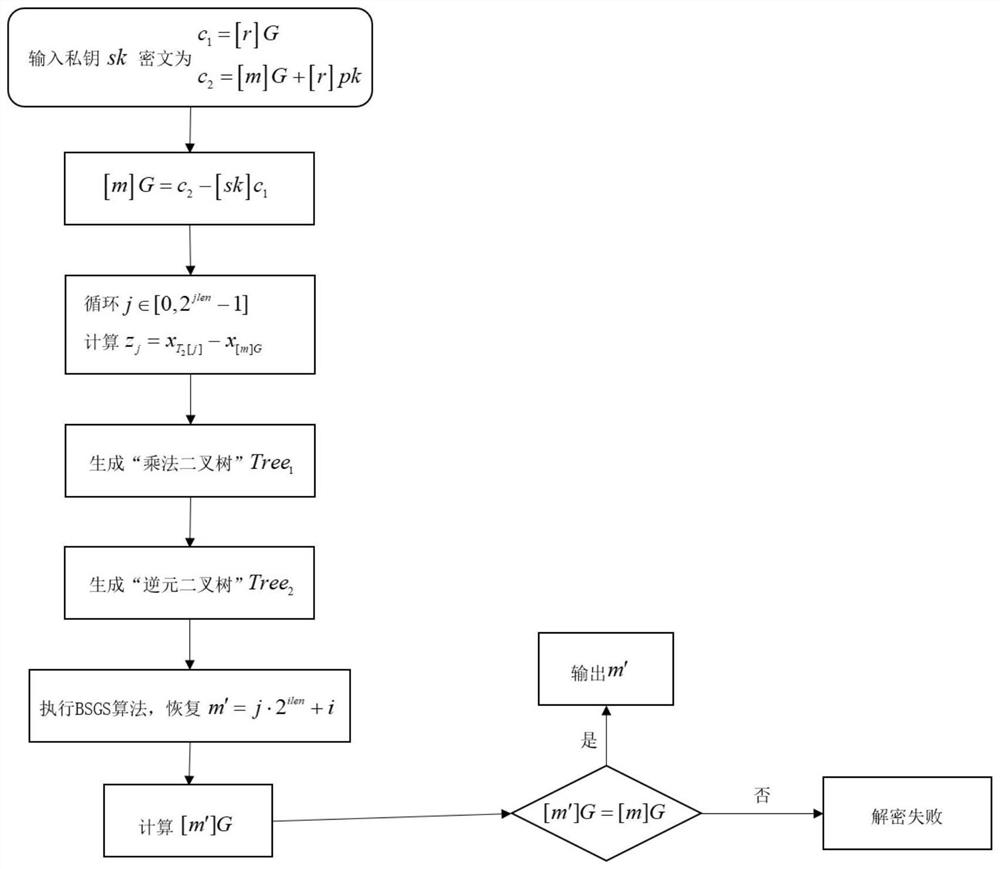
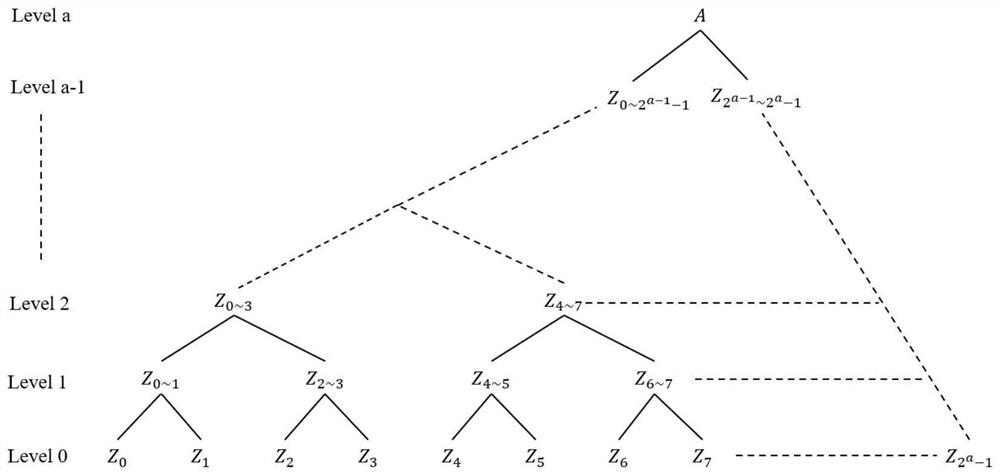
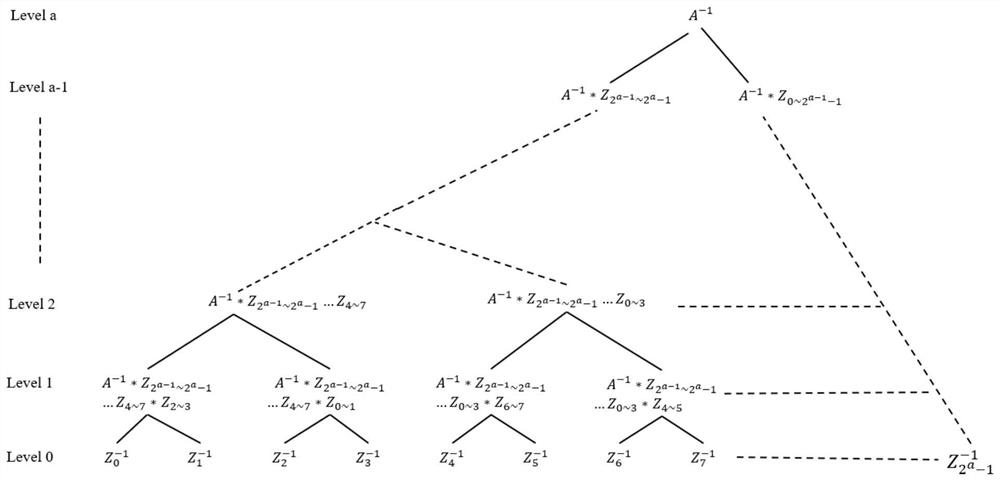
PendingCN114124349ASolve the problem of slow decryptionFast decryptionKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextAlgorithm
The invention relates to the technical field of data security, in particular to a quick decryption method for a homomorphic encryption scheme, which comprises the following steps: an encryption user and a decryption user appoint the used homomorphic encryption scheme in advance, and user sides of the two parties precompute system parameters; the decryption user side receives the encrypted ciphertext; after the decryption user side receives the ciphertext, ciphertext parameters are calculated; performing plaintext recovery on the ciphertext parameter by adopting an improved BSGS algorithm according to the obtained system parameter to obtain a plaintext; if the decryption algorithm of the homomorphic encryption scheme needs to verify the decryption result, ciphertext verification is carried out, namely, if the verification result is correct, the decryption result is output, and if the verification result is wrong, decryption fails; according to the method, the discrete logarithm problem can be rapidly solved when the power exponent is small, and certain universality is achieved; compared with the traditional homomorphic encryption scheme, the fast decryption method provided by the invention can improve the decryption speed of the homomorphic encryption scheme by more than 10 times.
Owner:北京数牍科技有限公司
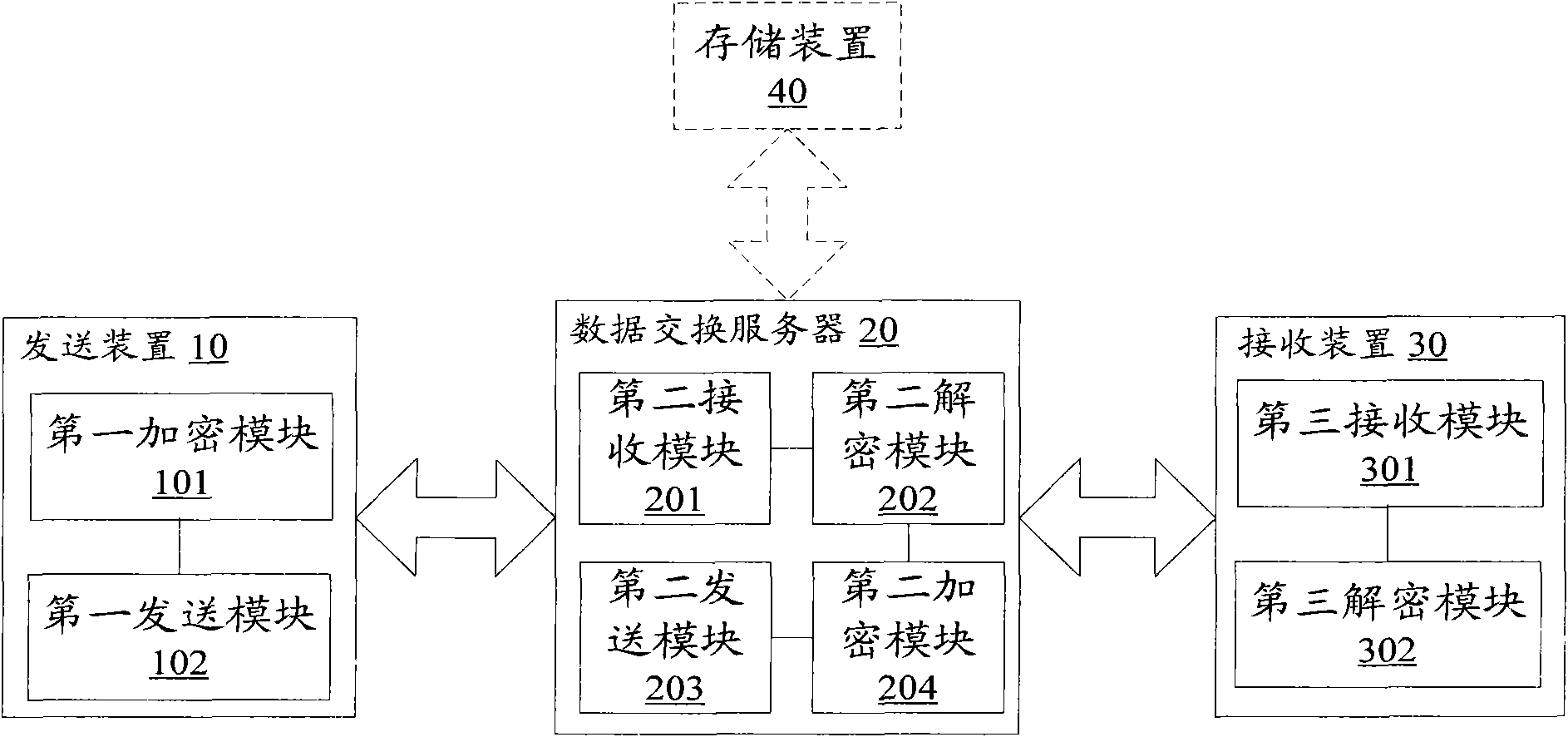
Data encryption transmission method and system for message-oriented middleware
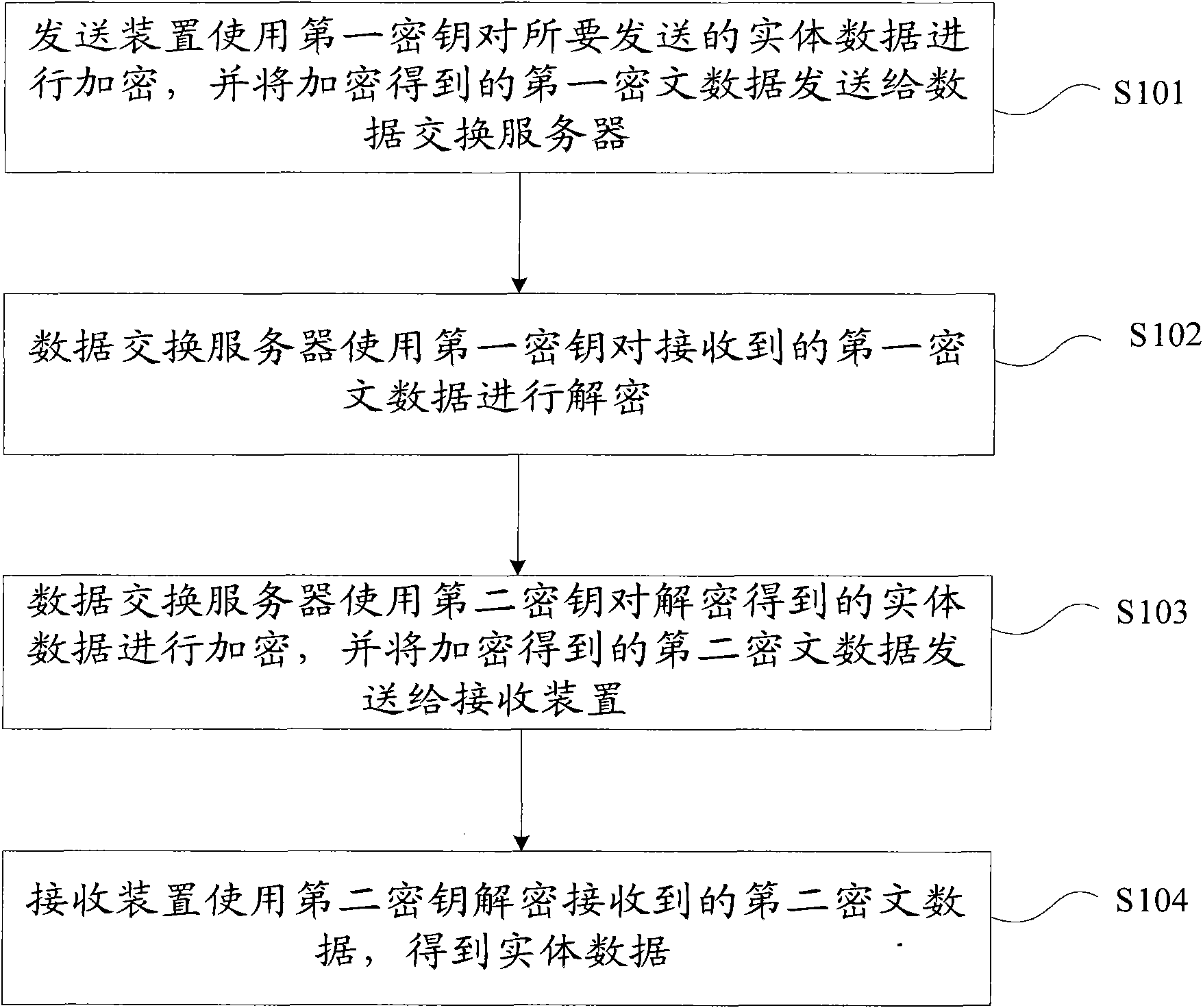
ActiveCN102088441BFast encryptionFast decryptionUser identity/authority verificationConfidentialityCiphertext
The invention provides a data encryption transmission method for a message-oriented middleware. The method comprises the following steps: a transmitting device encrypts entity data to be transmitted by using a first key and transmits first cipher text data obtained by encryption to a data exchange server; the data exchange server decrypts the received first cipher text data by using the first key; the data exchange server encrypts entity data obtained by decryption by using a second key, and transmits second cipher text data obtained by encryption to a receiving device; and the receiving device decrypts the received second cipher text data by using the second key to obtain entity data. The invention also provides a data encryption transmission system for the message-oriented middleware. The method and the system are suitable for encryption transmission of a large volume of data and multi-party communication, various encryption transmission ways such as a point-to-point way, a point-to-multipoint way, a broadcasting way and the like are provided for data exchange among enterprise application systems, and the confidentiality and the security of data transmission on a network are enhanced.
Owner:PEKING UNIV +2
An Attribute-Based Outsourcing Scheme for Bgn-type Ciphertext Decryption
ActiveCN107154845BImprove securityReduce difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess structureCiphertext
The invention particularly relates to a BGN type cryptograph decryption outsourcing scheme based on attributes. The scheme comprises steps that (1), a system parameter is set, and an encryption secret key is generated; (2), an access structure is selected by a sending side, message encryption is carried out, and cryptograph is generated; (3), a main secret key and the attributes are inputted by a receiving side, and a conversion secret key and a private secret key are outputted; (4), the cryptograph is sent by the sending side to a cloud end; (5), the conversion secret key is sent to the cloud end by the receiving side; (6), the cryptograph is converted by the cloud end through utilizing the conversion secret key to acquire a part of the cryptograph which is sent to the receiving side; and (7), the private secret key is utilized by the receiving side to decrypt the part of the cryptograph to acquire a message, and homomorphic computation operation for the cryptograph carried out by the cloud end is further comprised between the step (4) and the step (5). The scheme is advantaged in that not only can system decryption efficiency be improved, but also storage cost of a receiver is reduced; according to the cryptograph acquired according to the encryption method, a server is permitted to carry out multiple addition homomorphic operation and multiplication homomorphic operation for cryptograph data, on the condition that decryption difficulty does not increase, CPA safety of the user information is substantially improved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
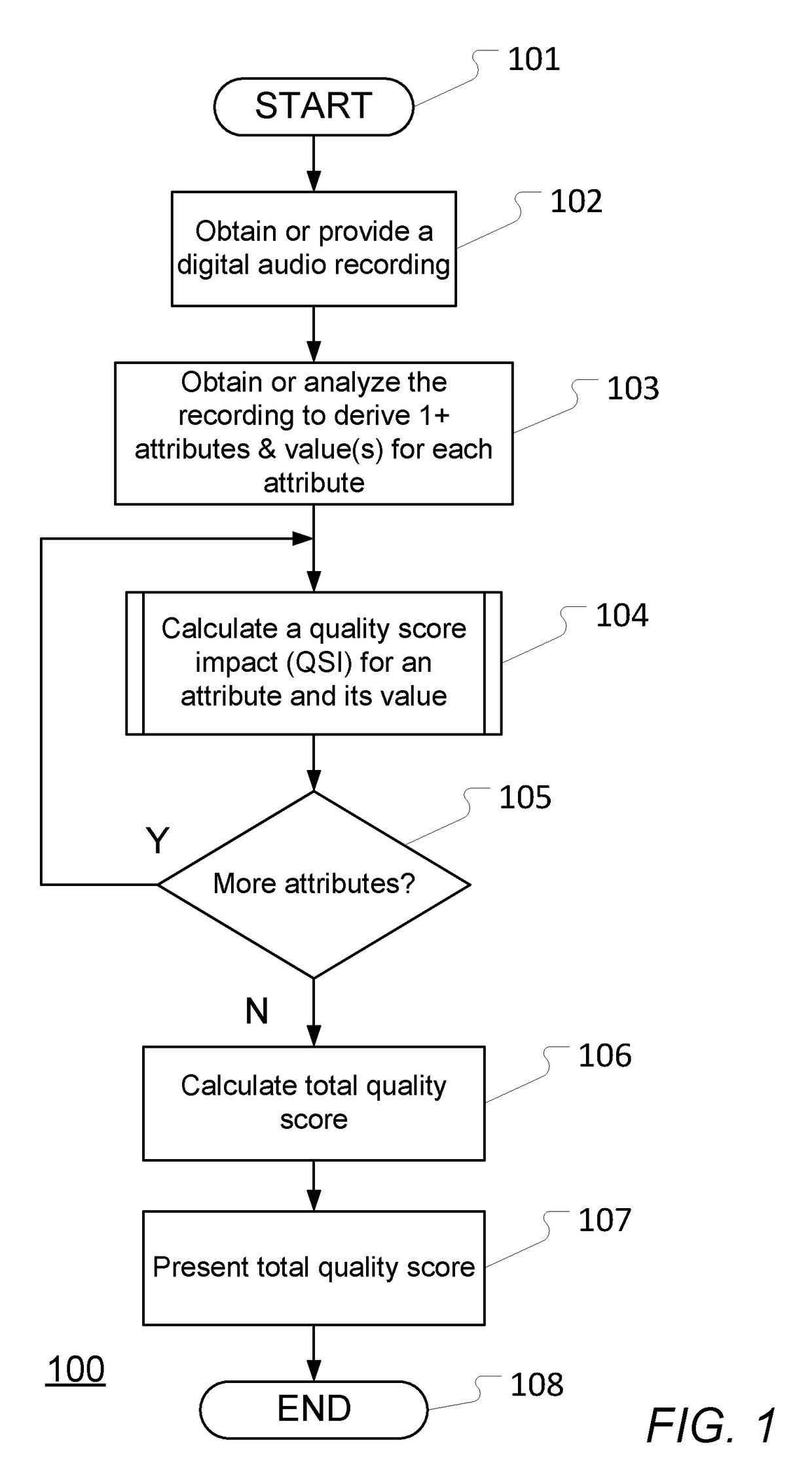
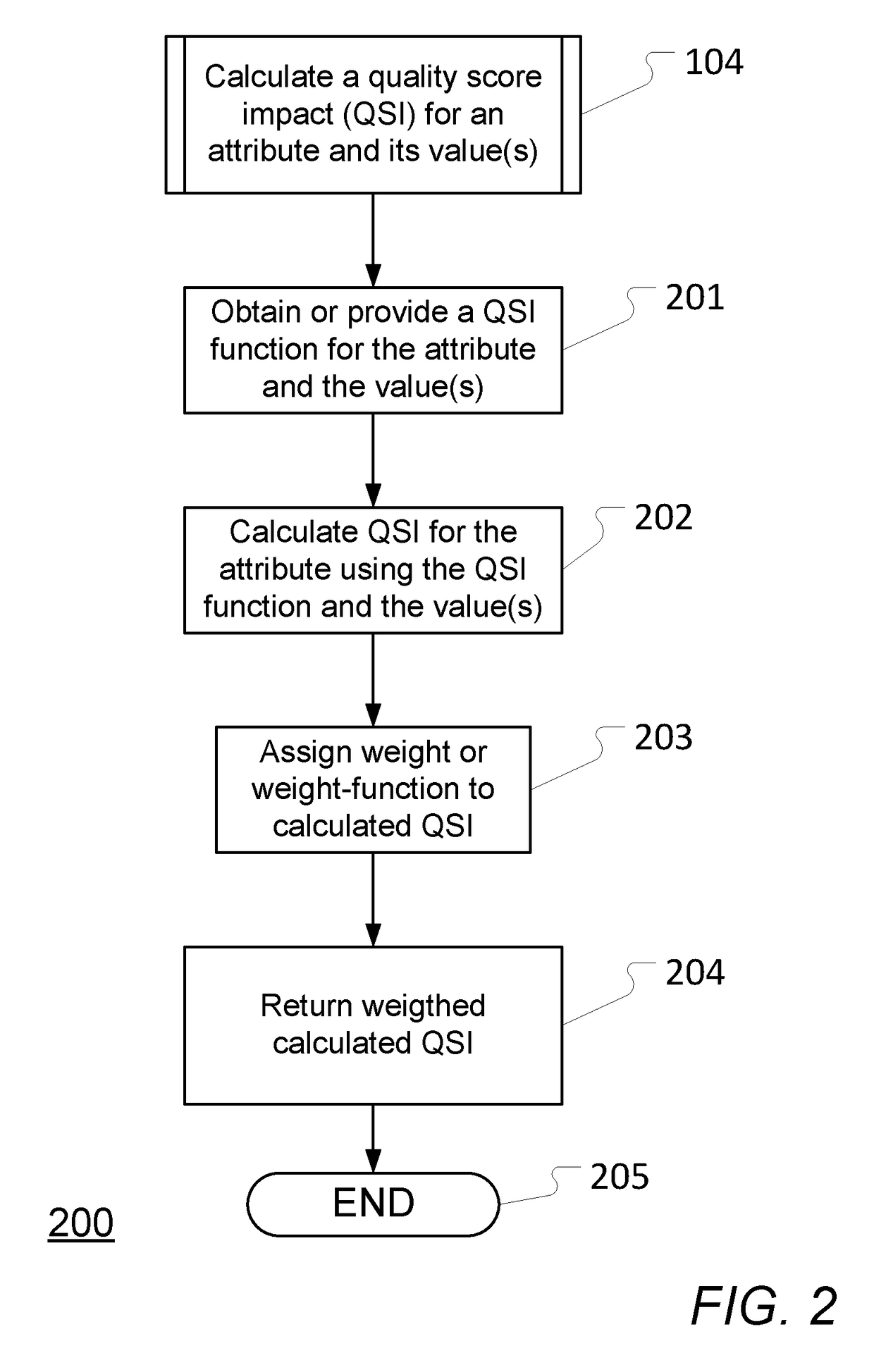
Computer-implemented method performed by an electronic data processing apparatus to implement a quality suggestion engine and data processing apparatus for the same
ActiveUS9653096B1Negative impactLess positive impactSpeech recognitionSound input/outputComputer scienceSpeech sound
A computer-implemented method performed by an electronic data processing apparatus to implement a suggestion engine, comprising: configuring a variable, which is independent from an attribute associated with content of a digital audio recording featuring one or more human voices, by: defining a quality score impact function characterizing a plurality of weight values having a maximum in a central band and tapering away in one or two respective bands adjacent to the central band maximum to produce a range of weight values, and defining a scale setting a minimum and a maximum range of values for the variable corresponding to the range of weight values.
Owner:CAPTURI AS
Method and system for releasing information of an earthquake and tsunami warning system
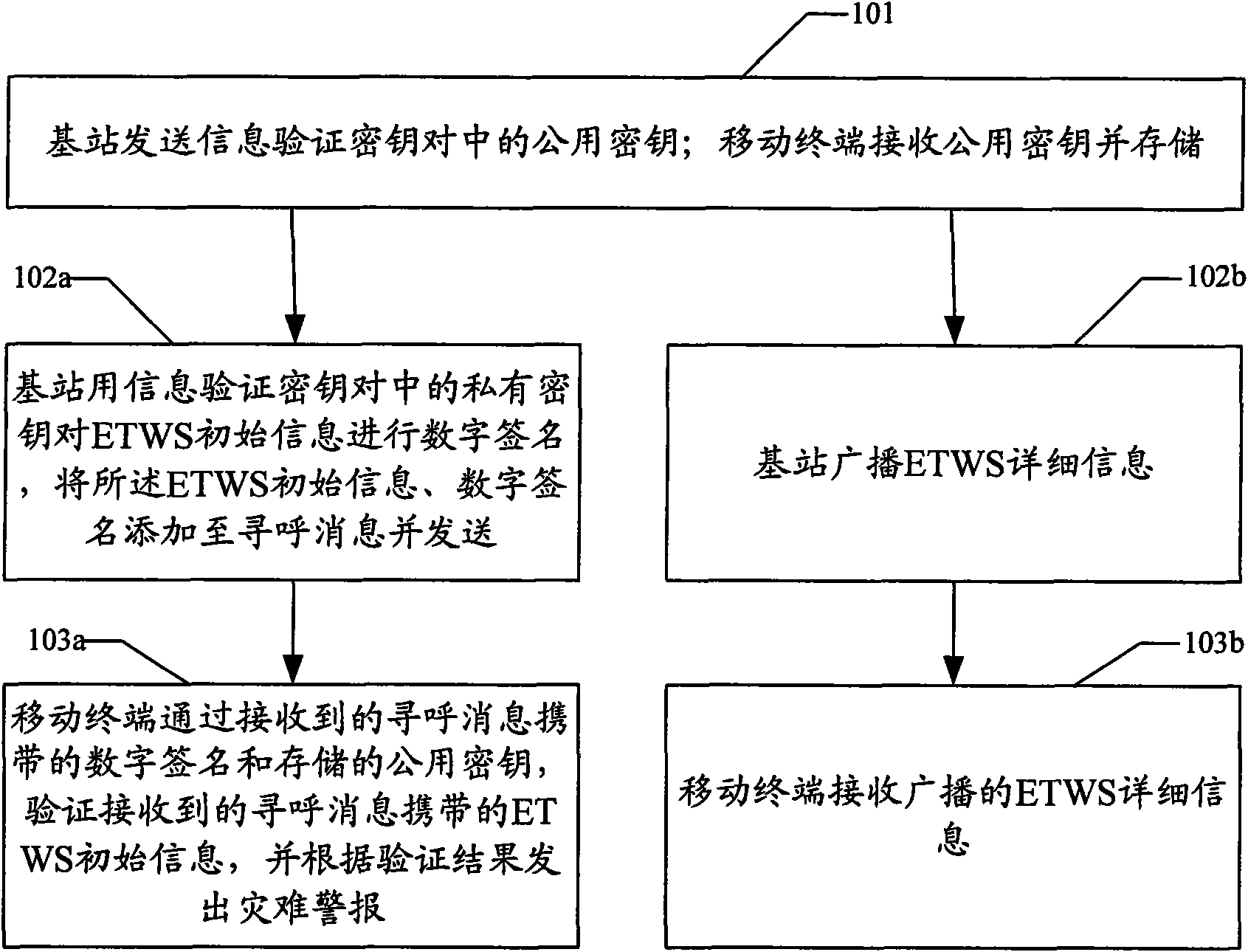
InactiveCN101938740BRelease securityReal-time releaseSecurity arrangementEmergency/hazardous communication serviceDigital signatureEngineering
The invention discloses a method for releasing information of an earthquake and tsunami warning system. The method includes: a base station sends information to verify the public key in the key pair; a mobile terminal receives and stores the public key; and the base station uses information to verify the private key in the key pair. The key digitally signs the ETWS initial information, adds the ETWS initial information and digital signature to the paging message and sends it; the mobile terminal receives the paging message, and uses the digital signature and stored public key carried by the received paging message to Verify the ETWS initial information carried by the received paging message, and issue a disaster alert based on the verification result. The invention also discloses an information release system of an earthquake and tsunami warning system, which includes a base station and a mobile terminal. By adopting the method and system of the present invention, ETWS information can be released safely and in time.
Owner:ZTE CORP
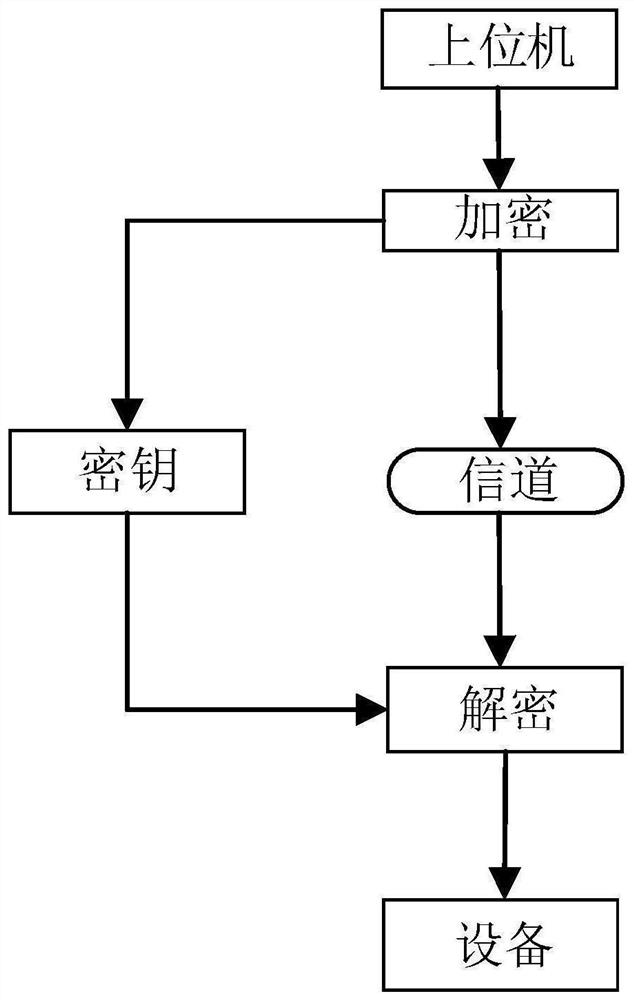
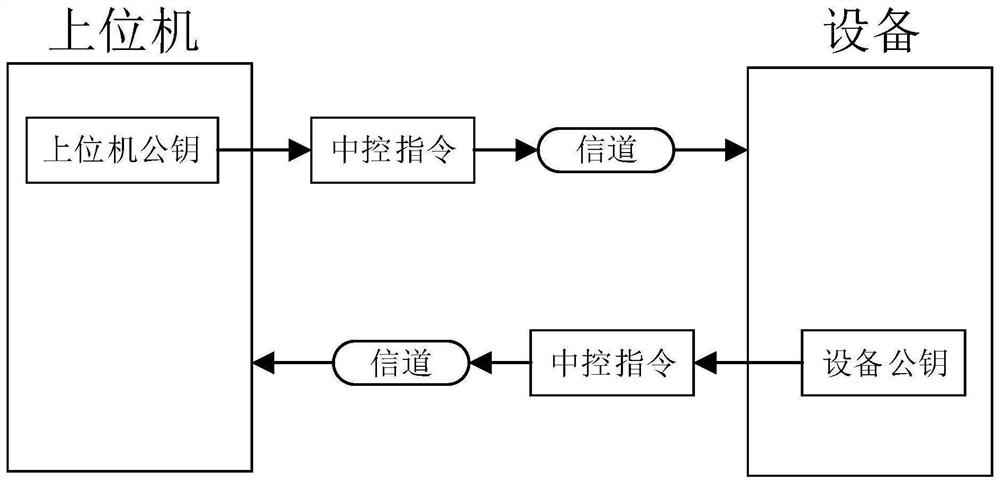
Upper computer communication encryption method and system
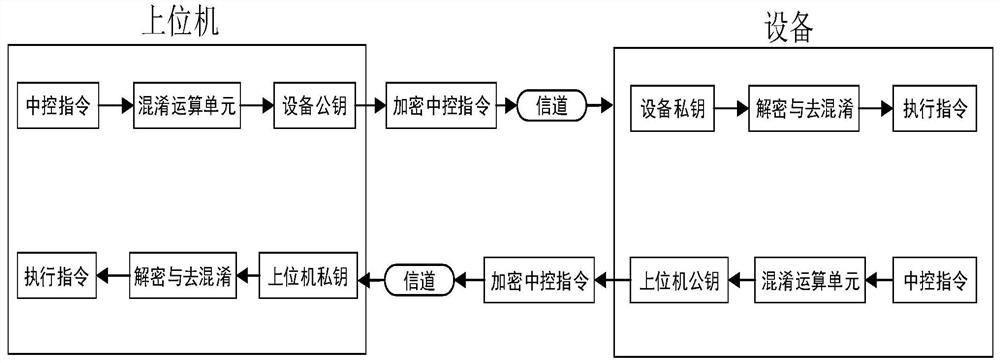
PendingCN112787814AAvoid crackingFast decryptionKey distribution for secure communicationProcessingEncryption
The invention discloses an upper computer communication encryption method and system, and the method comprises the steps: carrying out the confusion processing of a communication instruction between an upper computer and equipment before the communication between the upper computer and the equipment, and obtaining a confusion signal, wherein the communication instruction comprises an obfuscation code and a plurality of function codes, the obfuscation code is randomly interspersed among part of the function codes, the function codes are used for indicating various functions of the equipment, and the equipment acquires execution data according to the indication of the function codes and executes the corresponding functions; encrypting the confusion signal by adopting an asymmetric encryption algorithm to obtain an encrypted signal; when the upper computer communicates with the equipment, performing communication through the encrypted signal; and after the encrypted signal is received, performing decryption firstly, then removing the confusion code, and obtaining and executing a communication instruction. The encryption strategy is flexible and difficult to crack, and the decryption speed is high; and therefore, instructions of the upper computer are not easy to crack, product equipment is not easy to control by a counterfeit upper computer, and important data are not illegally tampered or peeped.
Owner:SICHUAN HUSHAN ELECTRIC APPLIANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com