SM9-based attribute encryption method and system under large attribute set
An attribute encryption and attribute collection technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as low efficiency, many SM9 encryption and decryption times, and large attribute set implementations are not considered, to improve usability. , the effect of speeding up the decryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
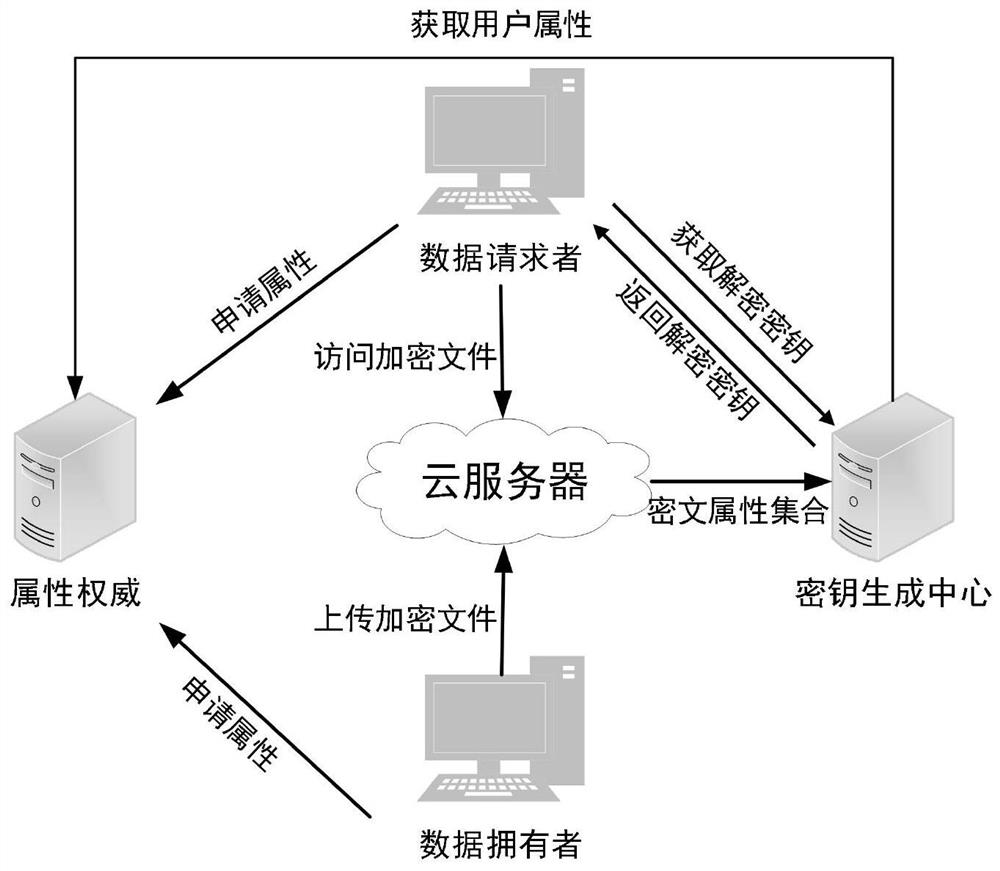
[0052] Such as figure 1 As shown, this embodiment provides an SM9-based attribute encryption method under a large attribute set. In this embodiment, the encryption and decryption operations are performed when the attribute is dynamic, that is, a large attribute set. The attribute of the user is managed by the attribute authority. When the user sends a request to generate a private key to the key generation center, the attribute authority sends the corresponding attribute to the Key Generation Center. This embodiment includes: 1. System initialization. The key generation center initializes the system parameters to generate the master public key and the master private key. The attribute authority manages user attributes; The public key encrypts the plaintext message to generate the ciphertext; 3. During the decryption process, if the attributes of the data requester satisfy the access structure, the ciphertext can be decrypted to obtain the plaintext; otherwise, it cannot be de...
Embodiment 2
[0080] This embodiment provides a SM9-based attribute encryption system under a large attribute set, including:
[0081] The key generation center is used to initialize the obtained system parameters by calling the SM9 algorithm to generate a master public key and a master private key; the master public key is open to all legitimate users, and the master private key is generated by the key Center is kept privately.
[0082] The data owner is used to determine the first access structure.
[0083] The attribute authority is used to generate a first attribute set according to the first access structure sent by the data owner; the attribute authority is used to manage and update stored user attributes; the attribute authority includes multiple attribute sets.
[0084] The data owner is also used to convert the first attribute set sent by the attribute authority into an identity set by calling the access structure identity conversion algorithm, and encrypt the first plaintext acco...
Embodiment 3
[0088] Such as figure 2 and 3 As shown, this embodiment provides an SM9-based attribute encryption method under a large attribute set, including the following steps.
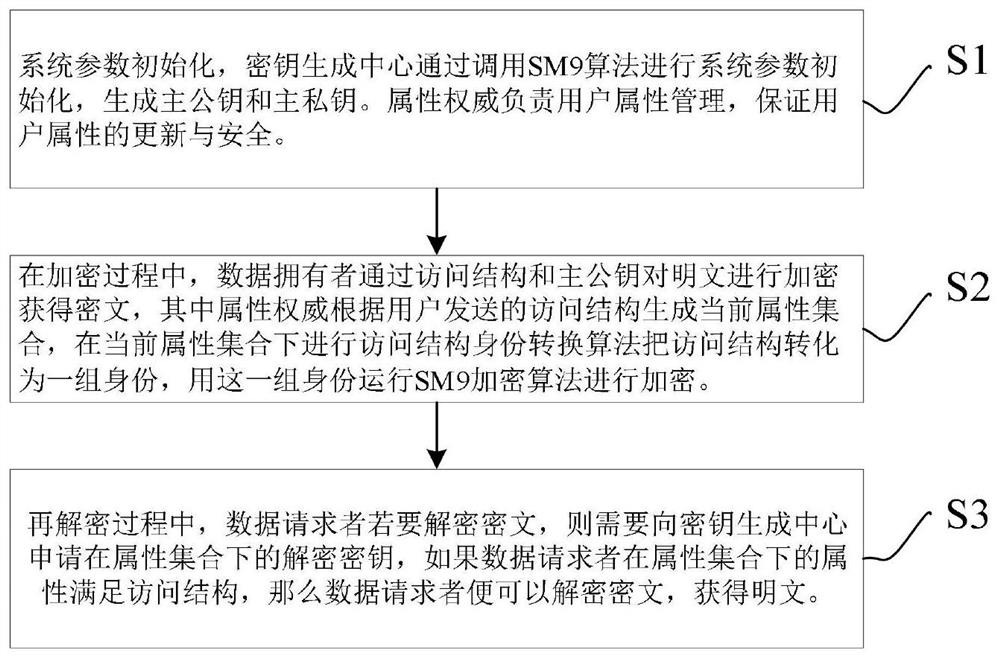
[0089] Step S1, system parameter initialization, the key generation center initializes the system parameters by calling the SM9 algorithm, and generates the master public key M pk and master private key M sk . The attribute authority is responsible for the management of user attributes to ensure the update and security of user attributes.
[0090] Further, in the step S1, the following steps are included:
[0091] Step S11, the key generation center calls the initialization algorithm of SM9, and passes in the initial system parameter k, through (M pk , M sk )←SM9.Setup(1 k ), get the master public key M pk and master private key M sk , master public key M pk Public within the system, namely the master public key M pk Shared with all legal users, the master private key M sk Then it is kept secretly b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com