Upper computer communication encryption method and system
An encryption method and computer technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as easy forgery of industrial control upper computers, complicated encryption/decryption of encryption technology, and increased decryption time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
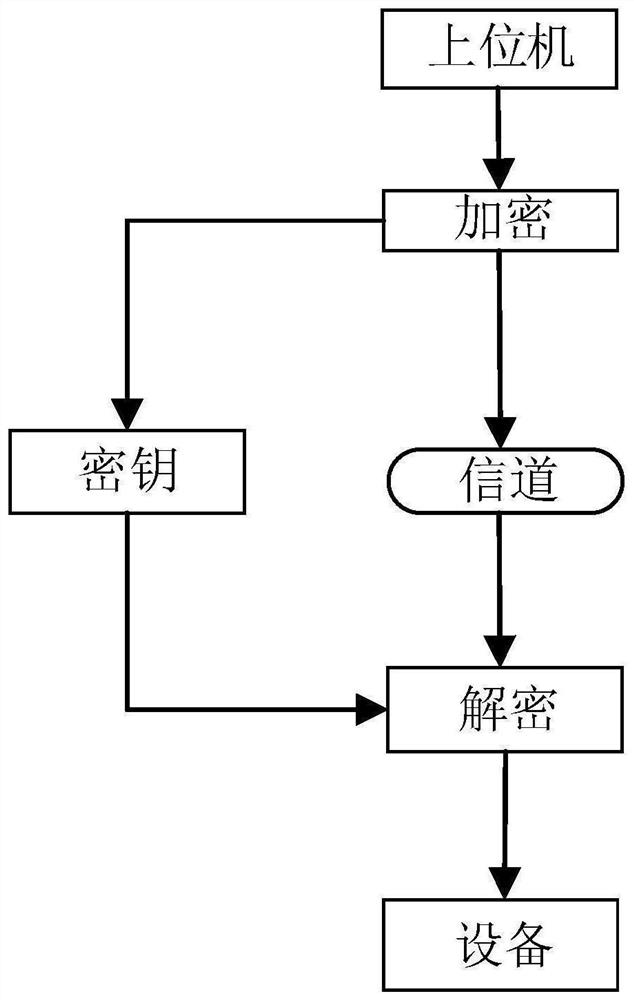
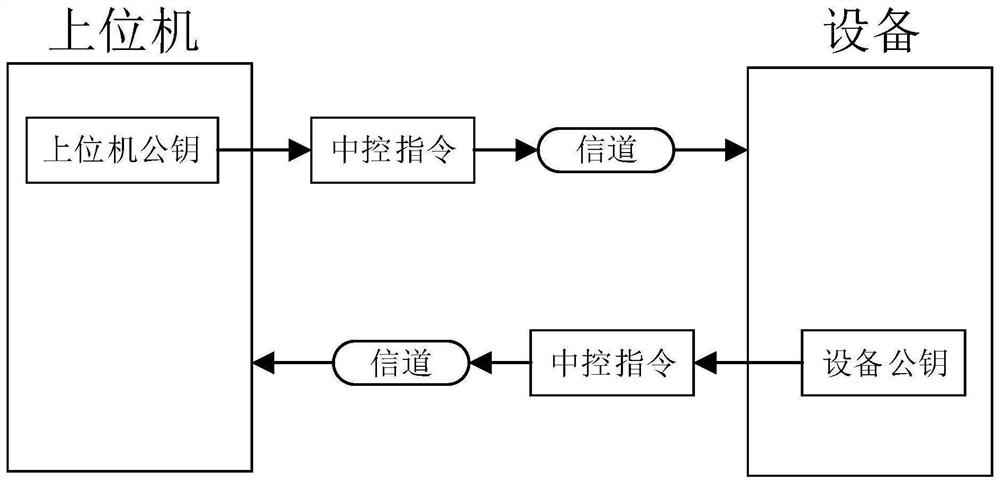
[0028] In engineering, in order to protect the control instructions of the upper computer software from being deciphered, an encryption mechanism is used for protection, such as figure 1 As shown, the central control command sent on the basis of non-encryption is easy to be intercepted and analyzed. After the central control command is cracked, the upper computer can be counterfeited, such as Figure 7 shown. The device can be controlled according to the instructions sent by the host computer software. However, since the central control instructions are not encrypted, the central control instructions are easily leaked and the device is deciphered, thereby imitating a similar upper computer software control device. If the central control instructions are over-encrypted, the decryption process will take time, and it will be difficult for the device to achieve high real-time performance during the execution of the instructions. Especially in the audio industry, audio processing ...
Embodiment 2
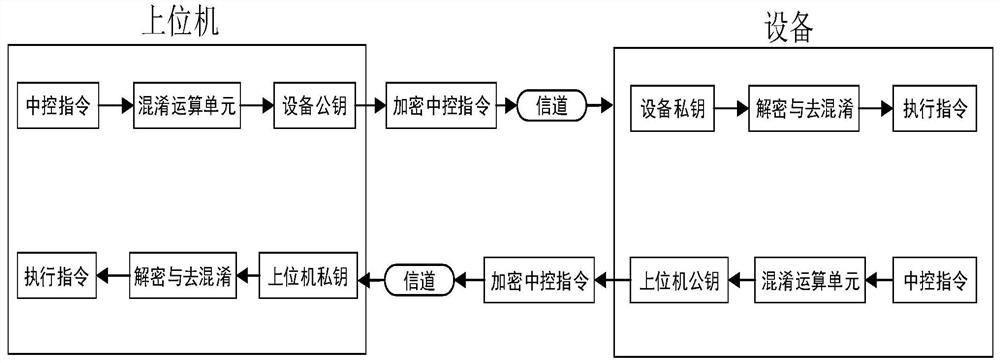
[0041] Present embodiment 2 is on the basis of embodiment 1, a kind of host computer communication encryption method, comprises the following steps:
[0042] Step 1: Divide the central control instructions of the upper computer, specifically: frame header sa, function frame s1, function code s2, ..., function code sn, obfuscation code sv, data data, check code sx, frame tail se ,Such as Figure 6 shown. And calculate the obfuscation code sv=f{s1, s2,..., sn, data, sx} according to the data bits;
[0043] Step 2: encryption / decryption processing, the specific steps are as follows:
[0044] Asymmetric encryption is used to generate a pair of secret keys, public key PUB_R and private key PRI_R. The key information R{s1,s2,…,sn,sv,sx} is encrypted with the private key PRI_R to generate R_h; after encryption, the central control Command: M={sa,R,data,se}
[0045] Step 3: Distribute the public key PUB_R and the encrypted central control instruction M.
[0046] Step 4: After rec...
Embodiment 3
[0052] Embodiment 3 is based on Embodiment 2, a host computer communication encryption system, including an encryption and decryption unit and a hash operation unit, the encryption and decryption unit is used to encrypt and decrypt the central control instructions, and the hash operation unit is used to Generate obfuscated code.
[0053] The hash operation unit is responsible for collecting information and performing hash operations. The obfuscation code is generated by using a hash operation unit. The function code determines the command to be executed after the central control command is received by the device or the host computer. Mix the currently executed function codes with data and check codes into the hash operation unit. The hash operation unit receives and performs hash operations step by step to generate an initial obfuscation code with a length of n bytes, and the obfuscation code is obtained by adding an obfuscation flag to the obfuscation code. Such as Figur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com