Access control method and access control system
An access control and access control technology, applied in the field of communication, to achieve the effect of convenient use, not easy to crack, and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
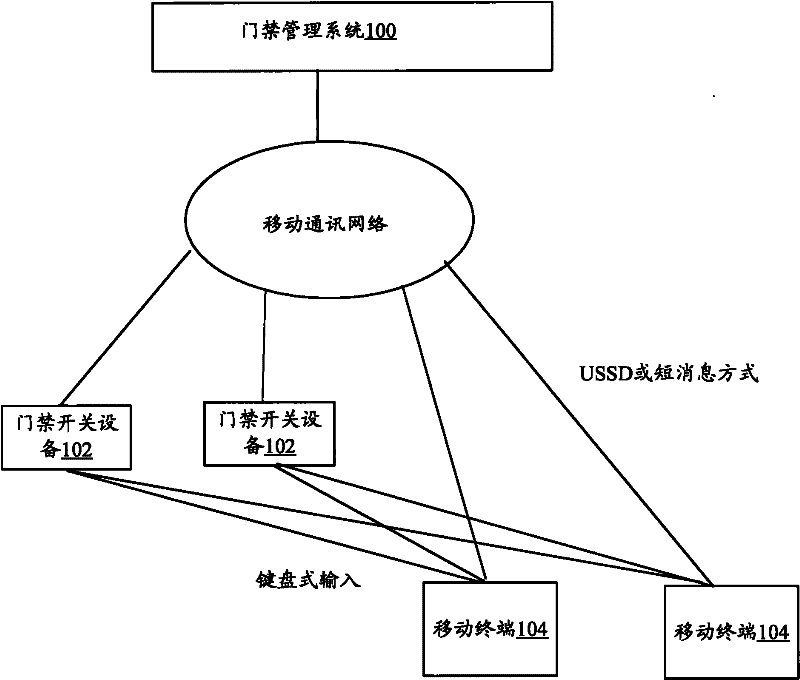
[0024] In this embodiment, an access control system is provided, figure 1 It is a schematic structural diagram of an access control system according to Embodiment 1 of the present invention. The system includes: a remote access control management system 100 and a plurality of access control switch devices 102, wherein,
[0025] Each access control switch device 102 is used to obtain the door opening request and the user account number input by the user using the mobile terminal 104, send the door opening request and the user account number to the remote access control management system 100, and is used to receive the door opening request from the access control management system 100. The verification code, and use the verification code to verify the password entered by the user, and if the verification is passed, the door will be opened;
[0026] The access control management system 100 stores the corresponding relationship between the user account number and the user mobile t...
Embodiment 2
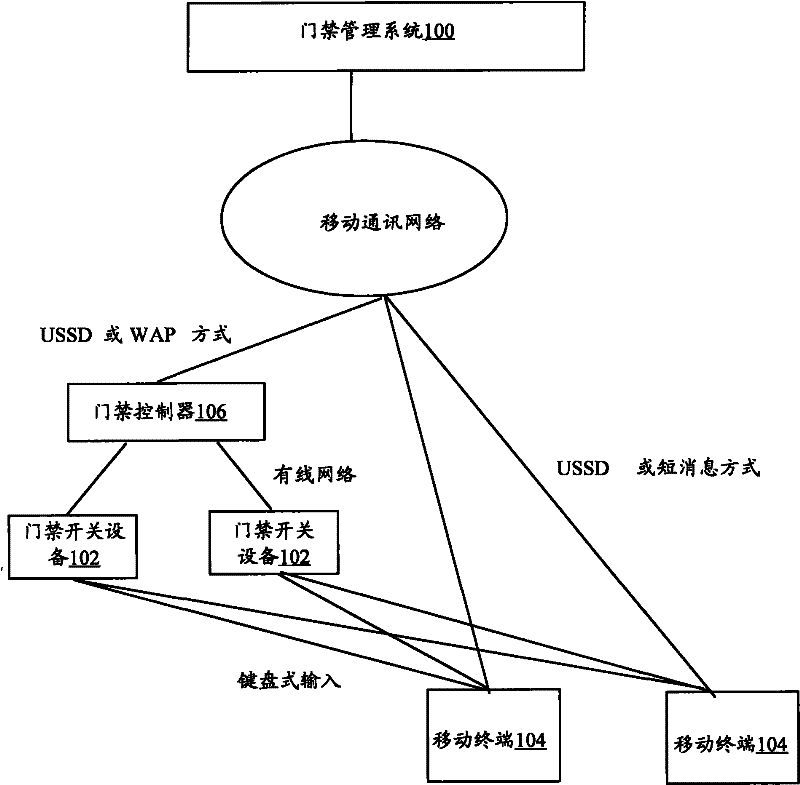
[0036] In the implementation process, system administrators, access control administrators and users (entrants) are required to interact with the access control system provided by Embodiment 1 to realize the door opening or closing operation of each access control switch device. The preferred access control system provided by Example 1 is introduced in detail, as in figure 2 In the shown access control system, the access control management system 100 also provides a WAP portal page to provide registration or setting services for system administrators, access control administrators and entrants, wherein the three roles can have the following usage rights respectively:
[0037] 1. The system administrator has the following authority:
[0038] (1) Have all permissions to operate the access control system, including setting system parameters and portal permissions;
[0039] (2) Has the authority to manage access control administrators and entrants, mainly including: specifying w...
Embodiment 3
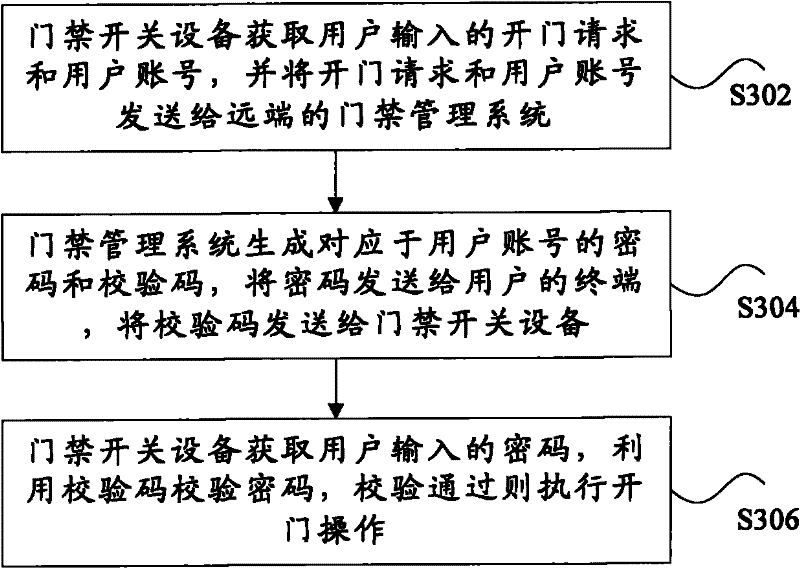
[0053] In this embodiment, an access control method is provided, image 3 It is a flow chart of the access control method according to Embodiment 3 of the present invention, such as image 3 As shown, the method includes:
[0054] Step S302, the access control switch device obtains the door opening request and the user account input by the user, and sends the door opening request and the user account to the remote access control management system, wherein the access control management system stores the corresponding relationship between the user account and the user's mobile terminal identifier;
[0055] Step S304, the access control management system generates a password and a verification code corresponding to the user account in response to the door opening request, and sends the password to the mobile terminal corresponding to the user account according to the corresponding relationship between the user account and the user mobile terminal identifier, and sends the verific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com