Password authentication method for internet of things by adopting security one-key management technology
A password authentication, Internet of Things technology, applied in the direction of user identity/authority verification, electrical components, transmission systems, etc., can solve the problem that cannot meet the market demand for concurrent authentication of sensor node devices, sensor data decryption and signature verification, and affects the application of PKI technology , the problem of high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
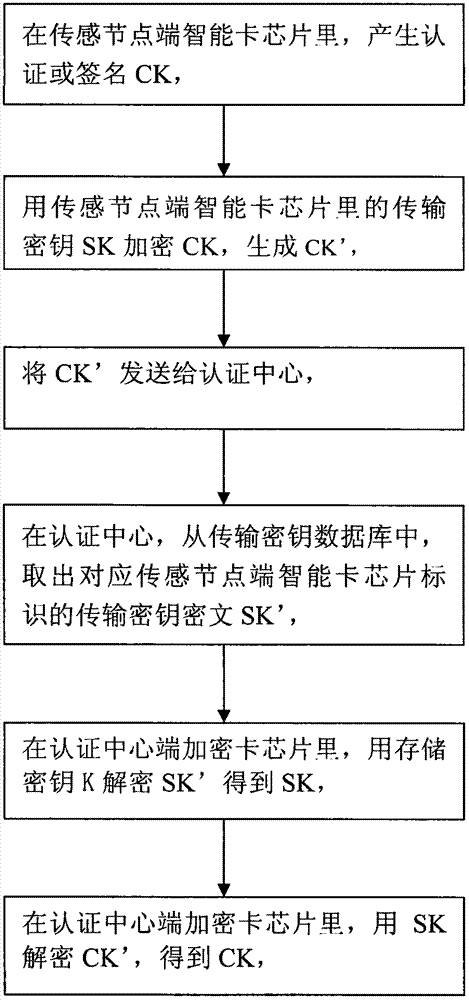
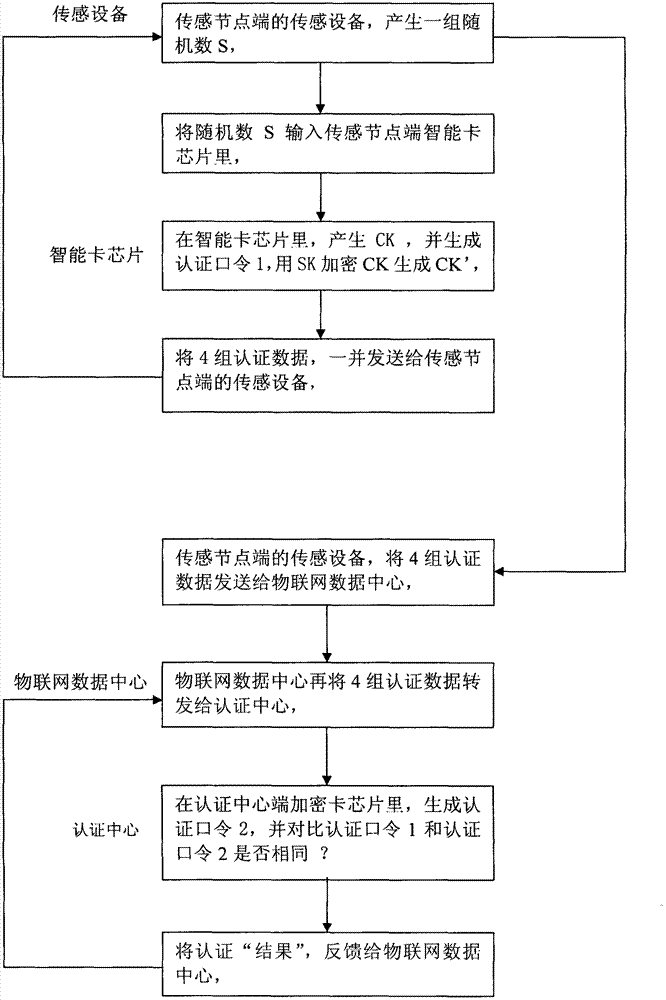
[0034] The following is a description with reference to the accompanying drawings: the process of using the three single keys in the Internet of Things security protocol, and the implementation steps of data transmission between the four types of devices in the Internet of Things password authentication system:
[0035] figure 1: Explain the use process of three single keys in the Internet of Things security protocol. First, in the smart card chip at the sensor node end, the Internet of Things security protocol at the sensor node end controls the random number generator to generate a set of random numbers. The number is used as the authentication or signature key CK, and the transmission key SK in the smart card chip of the sensor node is used to encrypt the authentication or signature key CK to generate the ciphertext of the authentication or signature key CK: CK', and send CK' To the authentication center, in the authentication center, the Internet of Things security protoco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com