Secure communication method based on combined encryption
A secure communication and encrypted technology, which is applied in the field of secure communication based on combined encryption, can solve problems such as transmission content leakage, attacker interception, signature verification leakage, etc., and achieve the effect of ensuring data information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
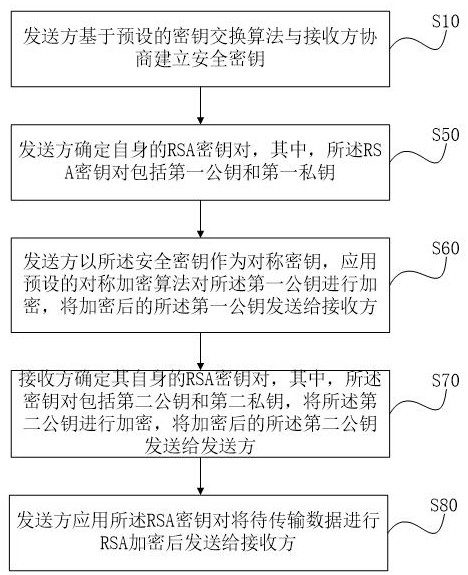
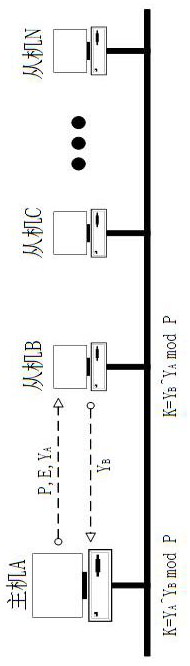
[0062] This embodiment proposes a secure communication method based on combined encryption, in which a sender sends data to a receiver in unicast mode. In the unicast mode, the sender and the receiver first negotiate to establish a security key, and then the sender encrypts the public key in the generated RSA key pair according to the security key and sends it to the receiver for receiving The party uses the sender's public key to decrypt the data sent by the sender, or to perform signature verification on the data sent by the sender.
[0063] like figure 2 As shown, in unicast mode, step S10 includes:
[0064] (1) The sender randomly selects a prime number P and an integer E, and generates a first random number X smaller than the prime number P A , based on the calculation of the first preset algorithm to obtain the first result Y A , the prime number P, the integer E and the first result Y A Send to the server, where the first preset algorithm is Y A =E^X A modP, P is...
Embodiment 2
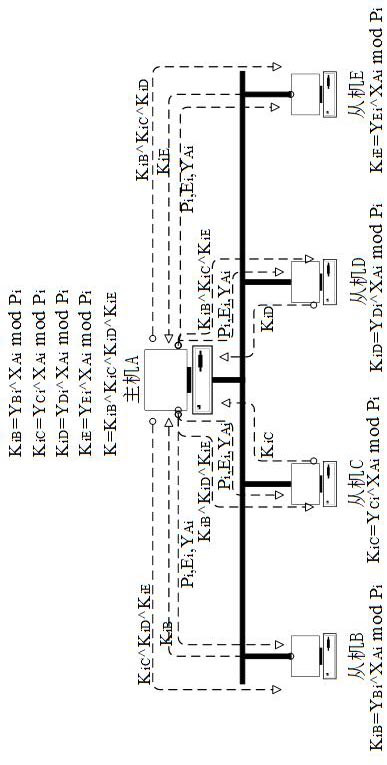
[0072] This embodiment proposes a secure communication method based on combined encryption, in which the sender sends data to multiple receivers in broadcast mode. In broadcast mode, a sender needs to broadcast the data to be transmitted to multiple receivers. First, the sender negotiates with multiple receivers to establish a security key. Then, if the amount of data to be transmitted is large, the security key will be used. The transmission data is symmetrically encrypted and then broadcast to multiple receivers. If the amount of data to be transmitted is small, RSA encryption is performed on the data to be transmitted. Specifically, the RSA public key is first encrypted with a security key, and then broadcast to multiple receivers. For the receiver to use the sender's RSA public key to decrypt the data it sent.
[0073] In broadcast mode, step S10 includes:
[0074] Step 1. The sender randomly selects a prime number P i and an integer Ei to generate a third random number ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com