Security password input system and implementation method for intelligent terminal
An intelligent terminal and input system technology, applied in transmission systems, user identity/authority verification, digital data authentication, etc., can solve problems such as operability and security, inconvenience for users to enter passwords, and inconvenience for users to carry around. Achieve the effect of easy memory, high security password input and verification, and reduced size
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
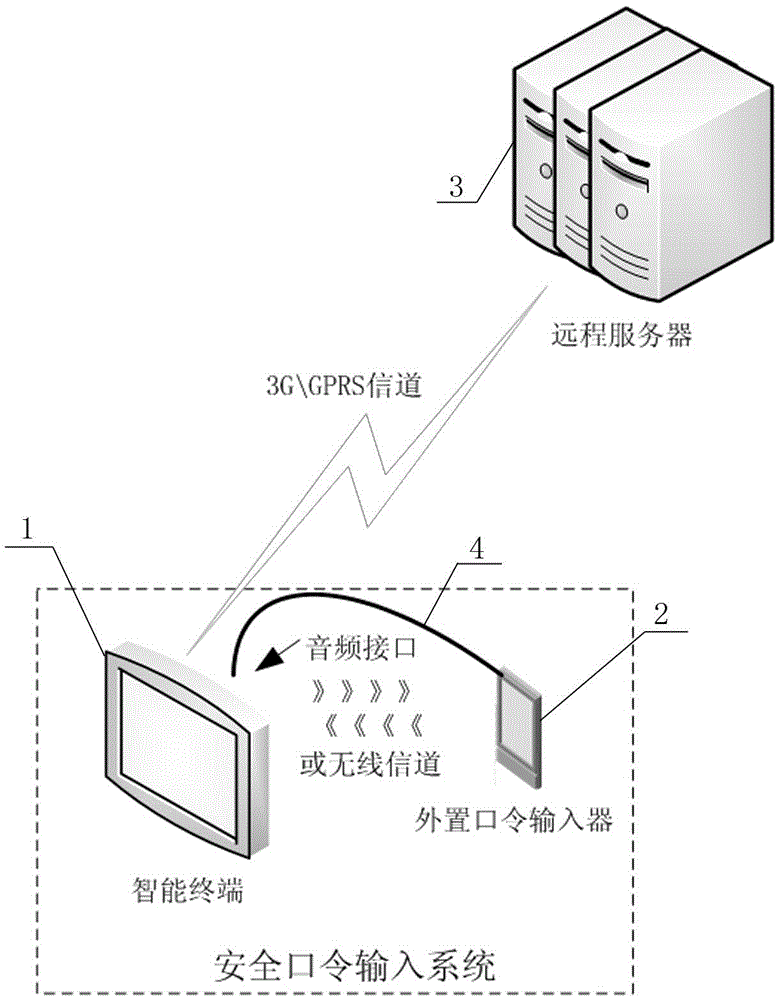
[0033] Such as figure 1 As shown, the schematic diagram of the inventive security password input system for smart terminals is given, which includes smart terminals 1 (such as smart phones, IPADs, tablet computers and other smart mobile terminal devices with Internet access functions), external password input device 2, remote server 3 and communication line 4, and the external password input device 2 communicates with the intelligent terminal 1 in a wired or wireless form. In the case that the external password input device 2 and the smart terminal 1 adopt wired communication, it can be connected with the audio or USB interface of the smart terminal 2 through the communication line 4 . Smart terminal 1 communicates with remote server 3 through 3G or GPRS network. The smart terminal 1 is also used to run the application program of the external password...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com