Encryption method based on DES
An encryption method and a technology for encrypting files, which are applied in the direction of encryption devices with shift registers/memory, etc., can solve the problems of consuming system resources, excessive computing time, and unsuitable system resources, so as to protect copyrights, increase the difficulty of cracking, The effect of fast decryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0016] Embodiment 1: KTV music storehouse left alignment, XOR encryption
[0017] This application example is a KBox play box built on the basis of the AMLogic 7228 chip. In order to protect the intellectual property rights of the KTV music library on the play box, the above encryption method is applied. In the following, only the encryption and decryption of the Rmvb file will be described in detail, and it is assumed that the logical operation set is only XOR and far calculation, and the encryption is left-aligned.
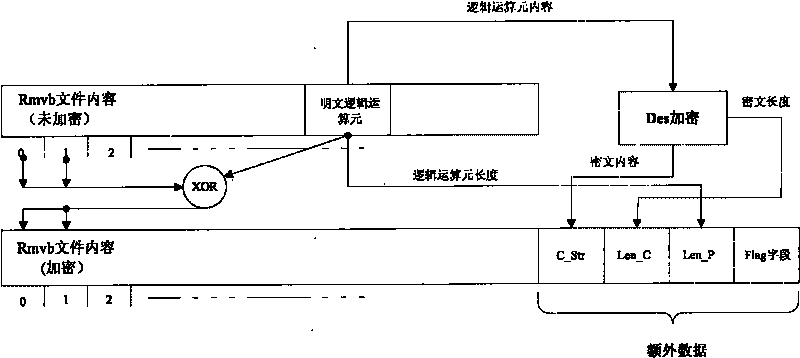
[0018] Such as figure 1 Shown is the encryption schematic diagram of the Rmvb file, where the Flag field is a user-defined flag segment, the type is a string of length 5, and it is assumed to be "UGOOD"; the data type of Len_C and Len_P is int.
[0019] Encryption process of Rmvb file:
[0020] Step 1, randomly obtain a section of plaintext logical operands from the unencrypted rmvb video file, assuming P (setting length as x);
[0021] Step 2. Divide the rmv...
Embodiment 2
[0024] Embodiment two, KTV's music storehouse right alignment, XOR encryption
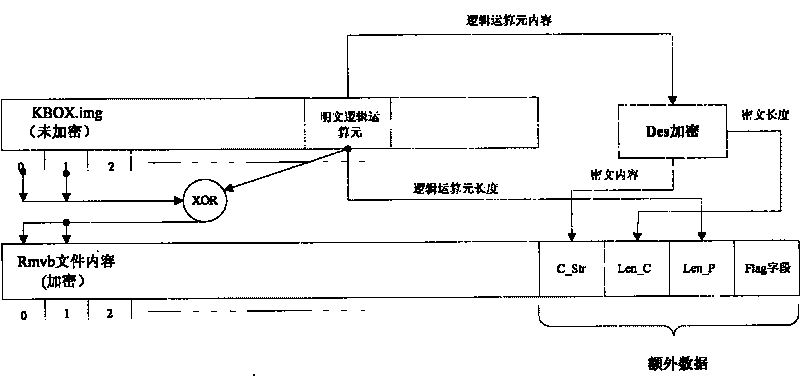
[0025] The method is the same as above, the difference is that the right alignment method is adopted in the process of segment encryption. Such as figure 2 As shown, it is the encryption principle diagram of the Rmvb file, where the Flag field is a user-defined flag segment, the type is a string with a length of 5, and it is assumed to be "MTEST"; the data type of Len_C and Len_P is int.
[0026] Encryption process of Rmvb file:
[0027] Step 1, randomly obtain a section of plaintext logical operands from the unencrypted rmvb video file, assuming P (setting length as x);
[0028] Step 2, divide the rmvb file into small sections with a fixed length (assuming that the length is y), y≥x, and the length of the last section is z, and it can be seen that z must be less than or equal to y;
[0029] Step 3, P performs XOR operation of x bits with the right half of each subsection of the rmvb file (exce...
Embodiment 3
[0031] Embodiment 3, left-aligned, same-or-encrypted application package
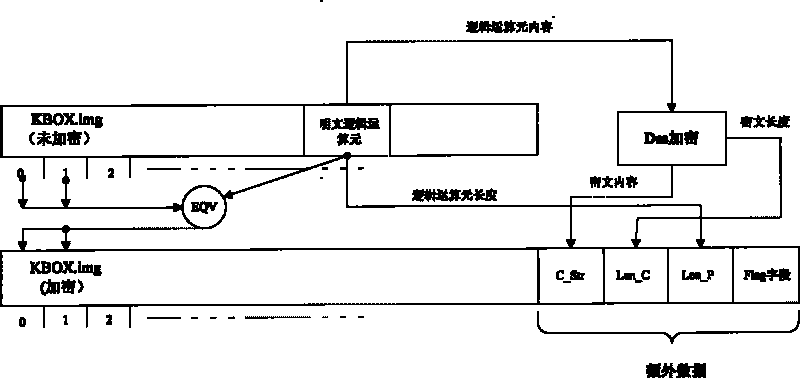
[0032] At the end of the software development, an application package that can be used directly is generated, assuming the name is KBOX.img. We use the encryption method of the present invention to encrypt to protect our application package. Such as image 3 Shown is the schematic diagram of the encryption of the application package.
[0033] Among them, the Flag field is a user-defined flag segment, the type is a character string with a length of 5, and it is assumed to be "TLAST"; the data type of Len_C and Len_P is int.
[0034] The encryption process of KBOX.img:
[0035] Step 1. Obtain a section of plaintext logical operand randomly from the unencrypted KBOX.img, assuming it is P (set the length as x);
[0036] Step 2. Divide KBOX.img into segments with a fixed length (let the length be y), y≥x, and the length of the last segment is z. It can be seen that z must be less than or equal to y;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com