Patents
Literature
79 results about "Flag field" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, a flag field is an integer interpreted as a sequence of boolean bits, each called a "flag". Flags are typically found as members of a defined data structure, such as a database record, and the meaning of the value contained in a flag will generally be defined in relation to the data structure it is part of. In many cases, the binary value of a flag will be understood to represent one of several possible states or statuses. In other cases, the binary values may represent one or more attributes in a bit field, often related to abilities or permissions, such as "can be written to" or "can be deleted". However, there are many other possible meanings that can be assigned to flag values. One common use of flags is to mark or designate data structures for future processing. Within microprocessors and other logic devices, flags are commonly used to control or indicate the intermediate or final state or outcome of different operations. Microprocessors typically have, for example, a status register that is composed of such flags, and the flags are used to indicate various post-operation conditions, such as when there has been an arithmetic overflow.
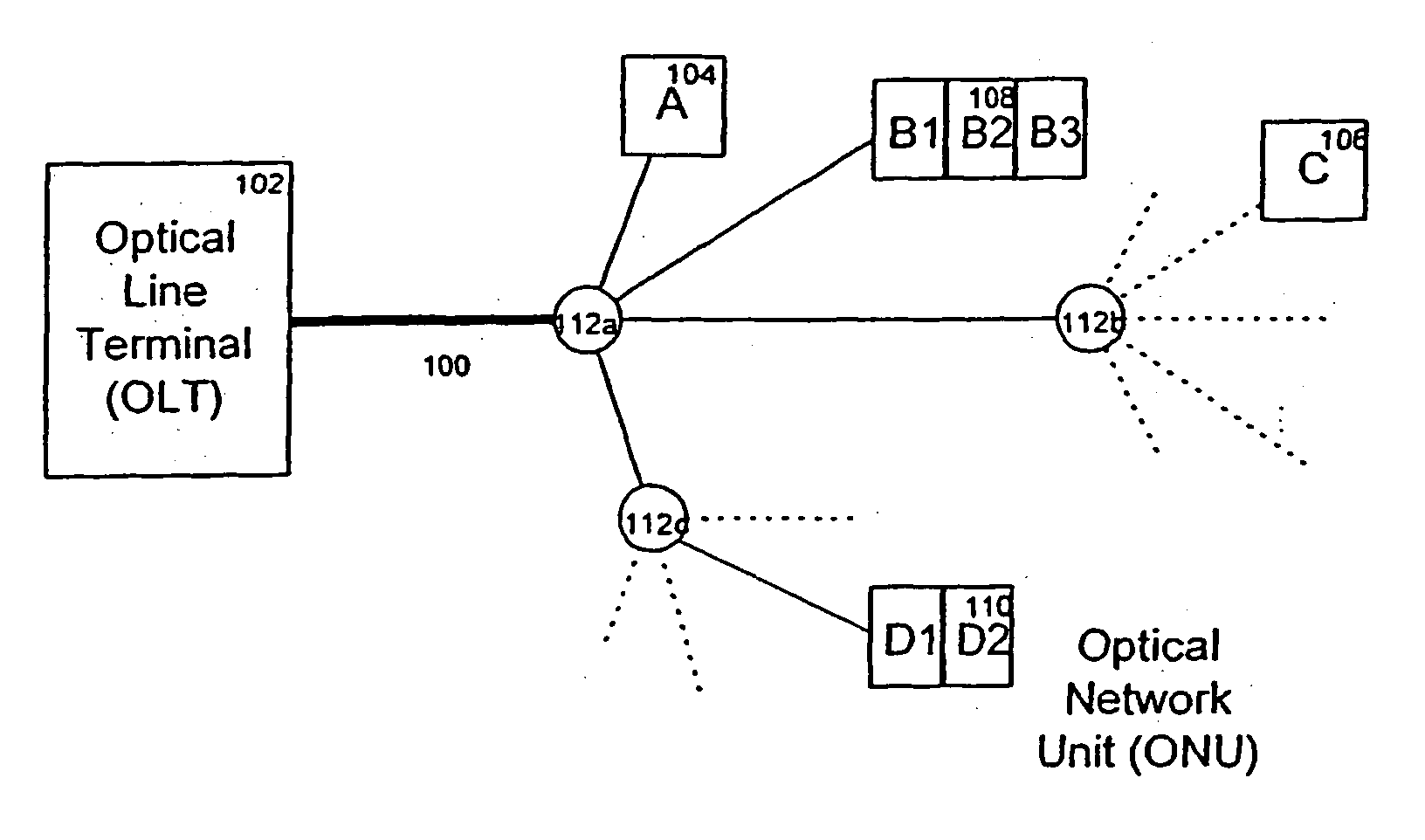
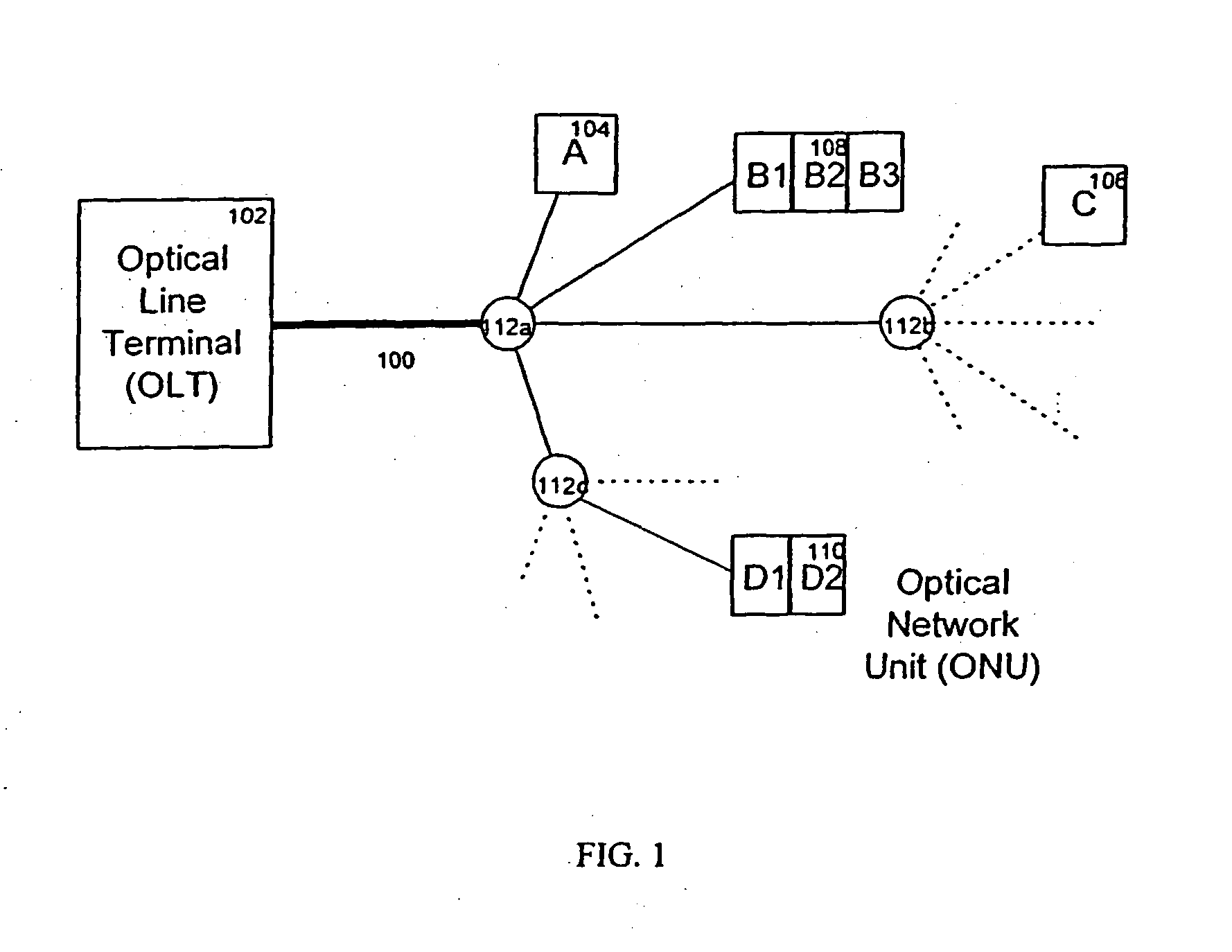
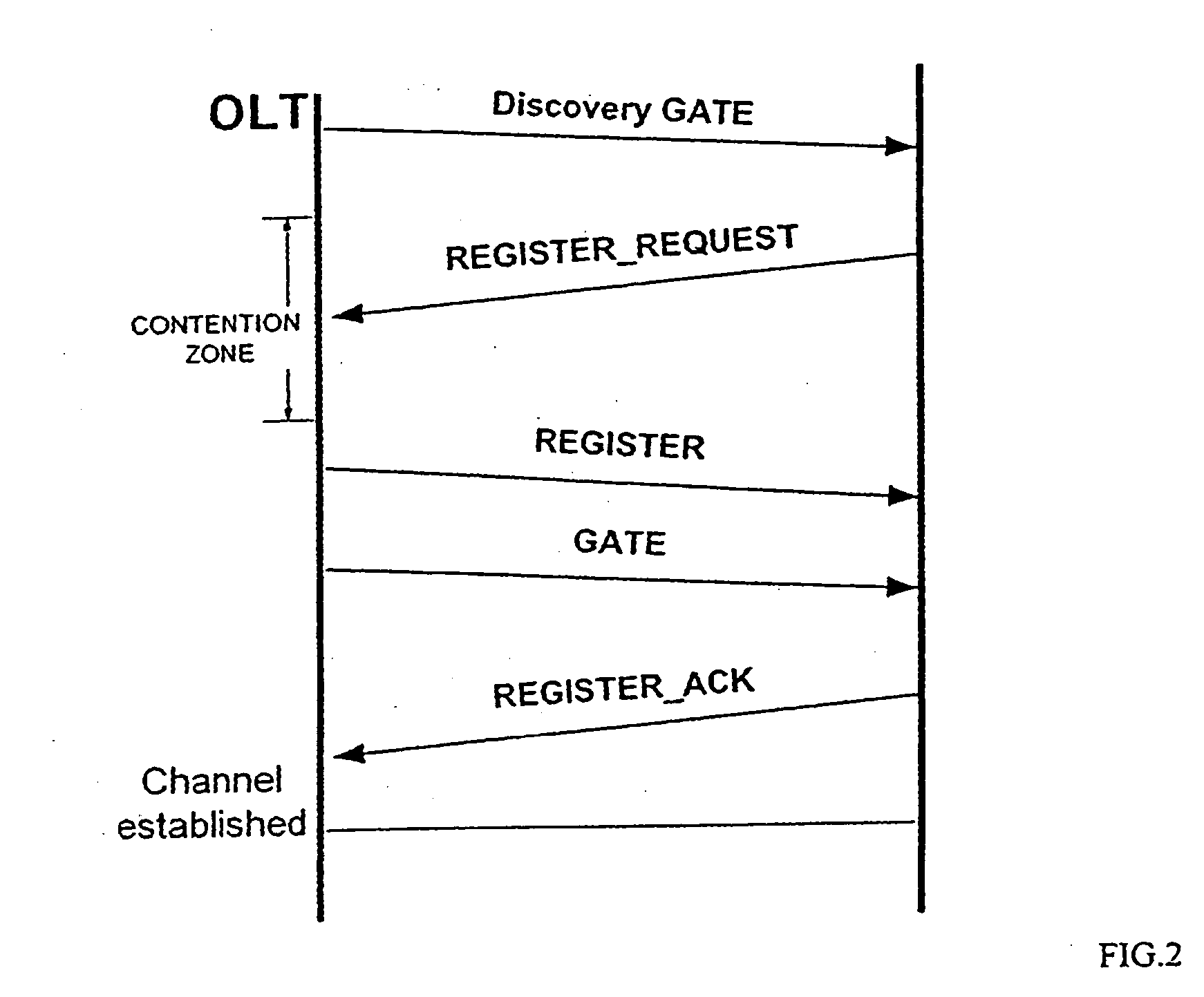
Operations method in an ethernet passive optical network that includes a network unit with multiple entities
ActiveUS20050249498A1Improved data flow controlIncrease overheadMultiplex system selection arrangementsStar/tree networksData streamOptical line termination
Owner:MICROSEMI ISRAEL STORAGE SOLUTIONS LTD
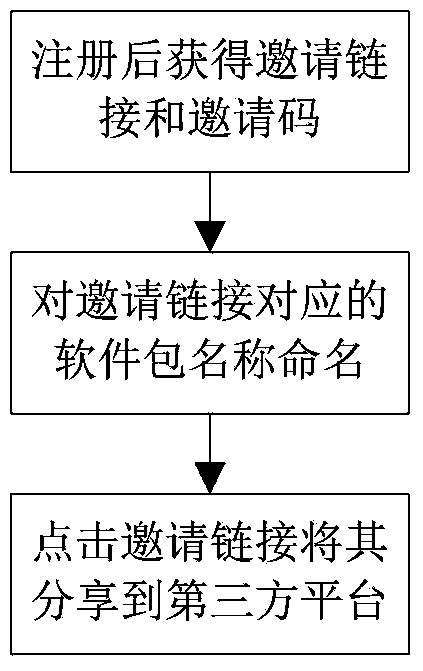
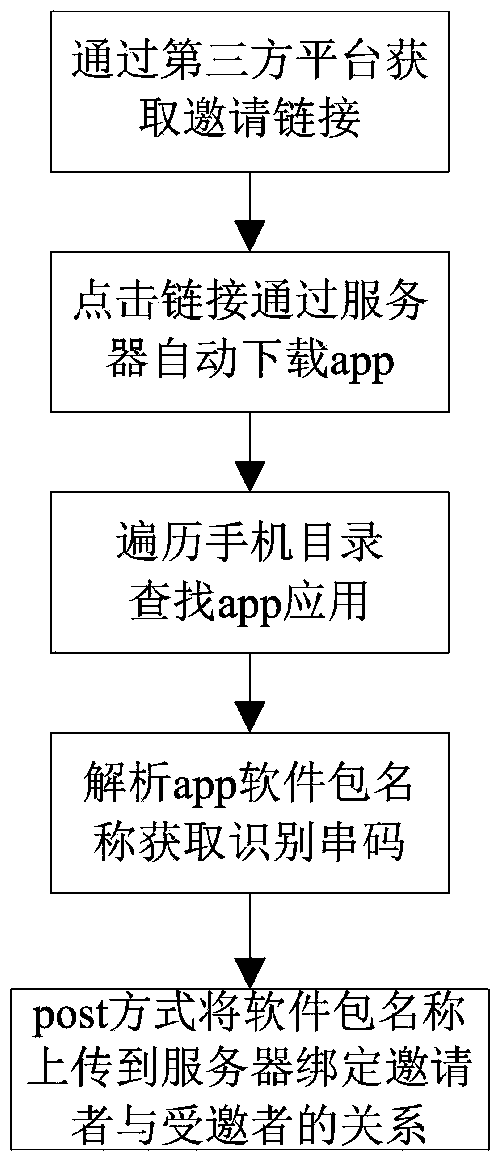
Invitation method based on cellphone applications
InactiveCN103561067AUniqueness guaranteedImprove securityUser identity/authority verificationSpecial data processing applicationsThird partySoftware engineering
The invention relates to an invitation method based on cellphone applications. The invitation method includes the steps that an inviter shares invitation links through a third party network platform, the invitation links comprise invitation codes, recognition serial codes and the download path of app software installation packages, the name of the software installation package corresponding to each invitation link comprises an invitation flag field, and the invitation flag fields comprise the recognition serial codes; after acquiring invitation links and downloading the app applications, invitees search catalogues of cellphones for the downloaded applications by traversing the catalogues of the cellphones, and then relationships between the inviter and the invitees are bound by analyzing the recognition serial codes of the software installation packages. By the adoption of the invitation method based on the cellphone applications, invitation and interconnection of cellphone communication can be achieved, and convenience is brought for utilization and popularization of the cellphone applications.
Owner:山东英网资讯股份有限公司
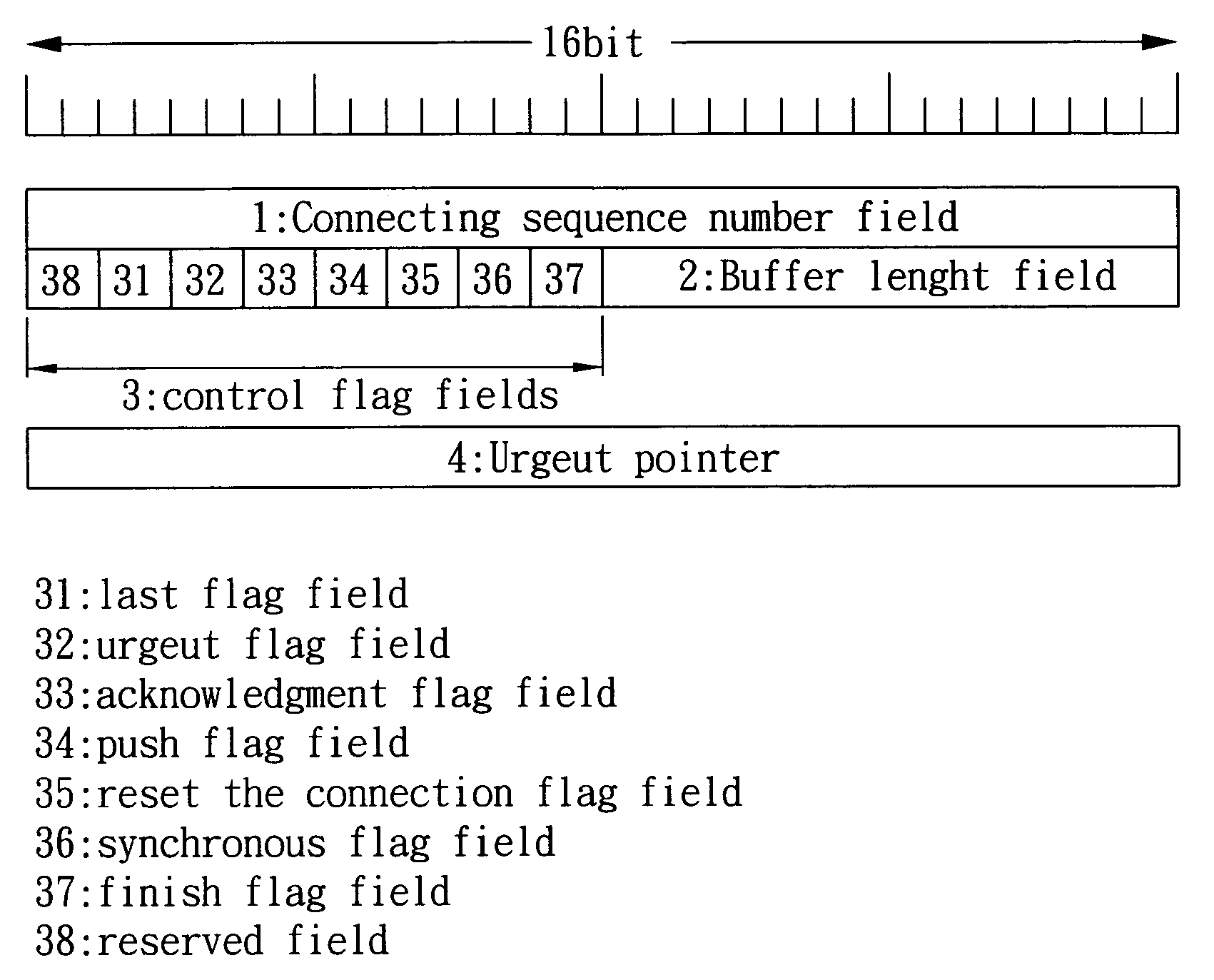
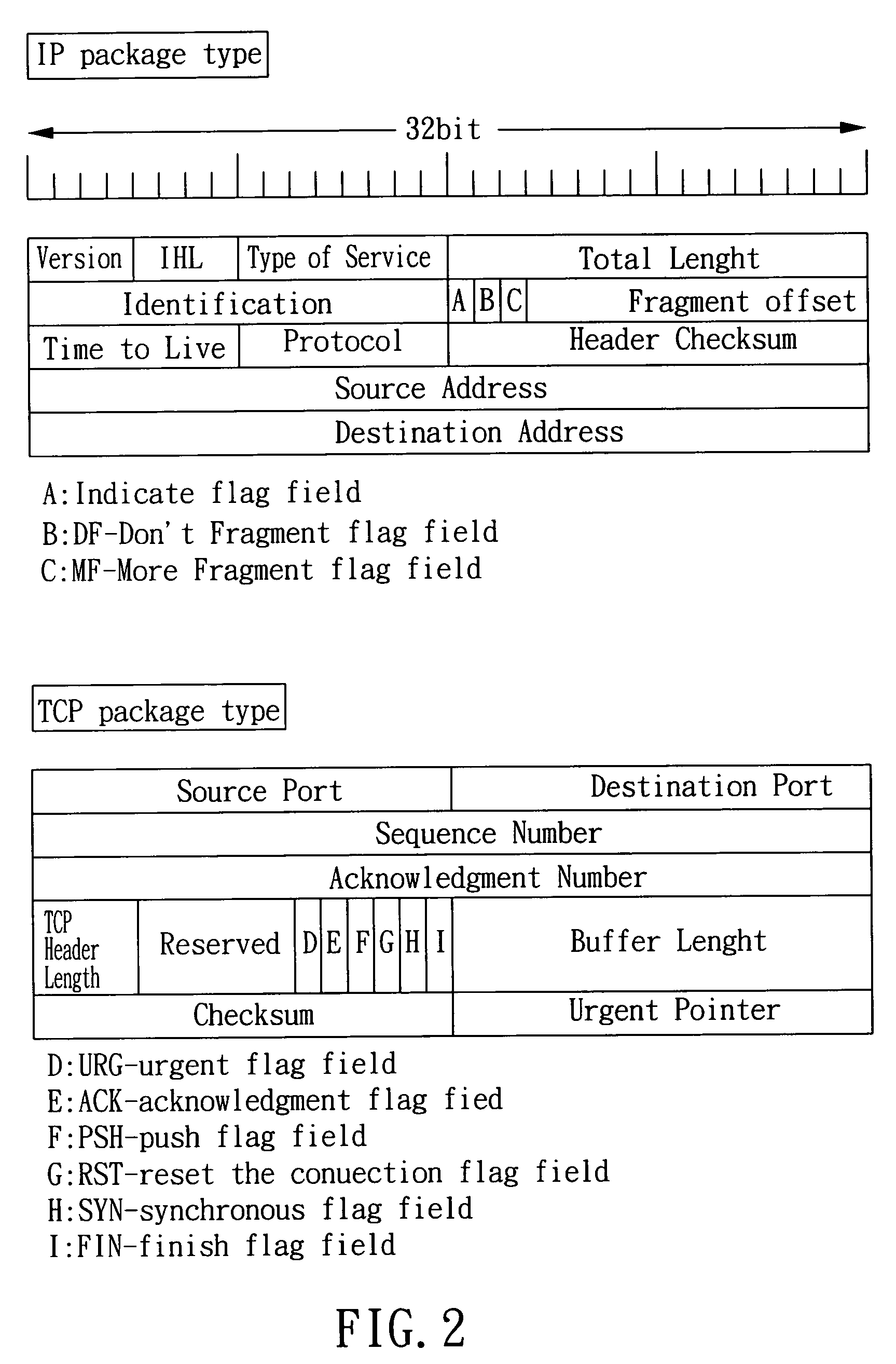
TCP/IP header compression format and method over wireless network
InactiveUS7403543B2Efficient compressionIncreasing amount of transmissionError prevention/detection by using return channelTransmission systemsMobile stationComputer science
The present invention provides a TCP / IP header compression format as a label in package transmitting. The header format is used under the acknowledgement mode in wireless network to reduce the header transmission amount between the base station and the mobile station, comprising: a connecting sequence number field for storing a connecting sequence number to indicate the required TCP / IP header information related base stations; a buffer length field for storing a length value of the buffer region to indicate the acceptable package number of the buffer region in receiver; and a plurality of control flag fields for providing certain necessary information for transmission control.
Owner:QUISDA CORP
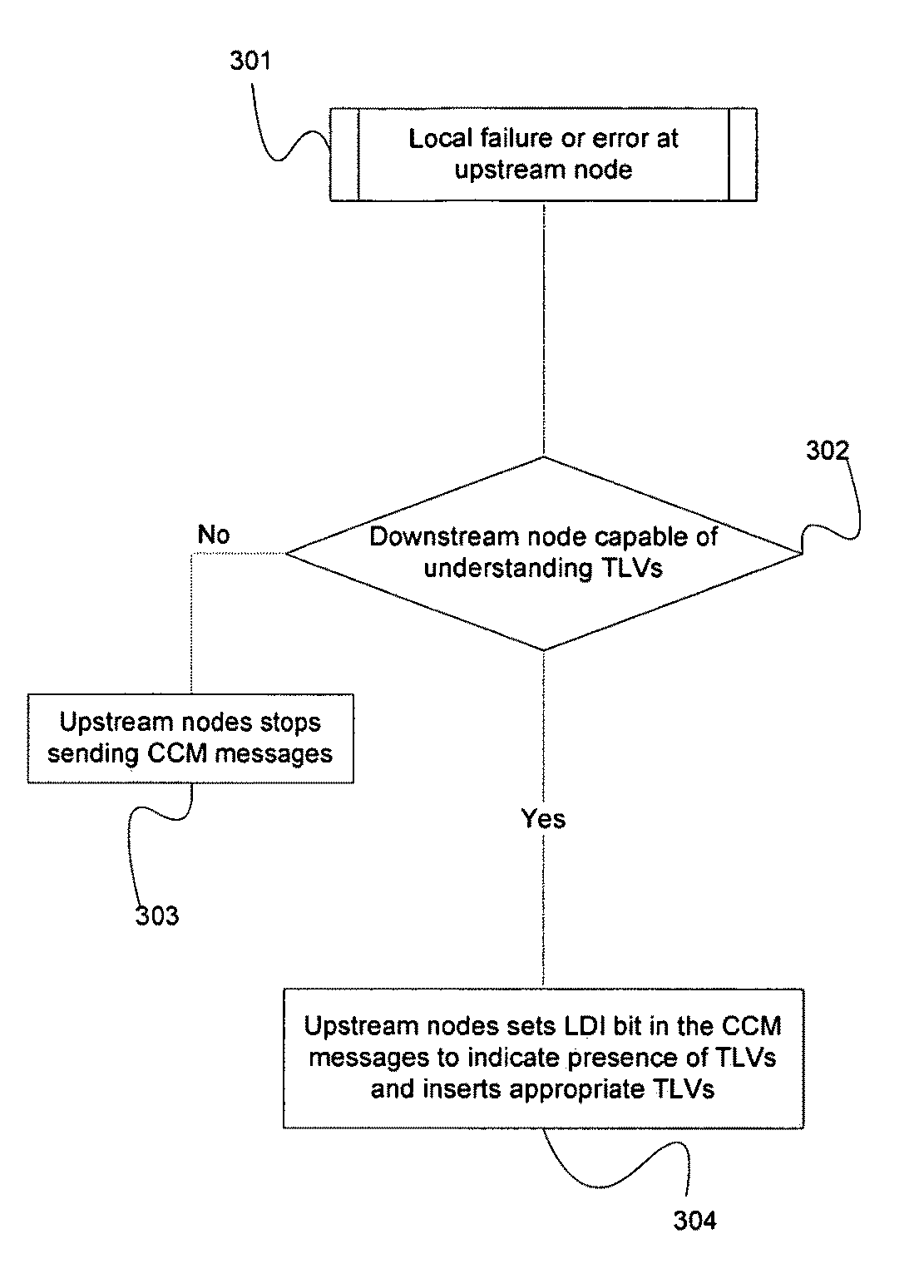
Carrier ethernet with fault notification
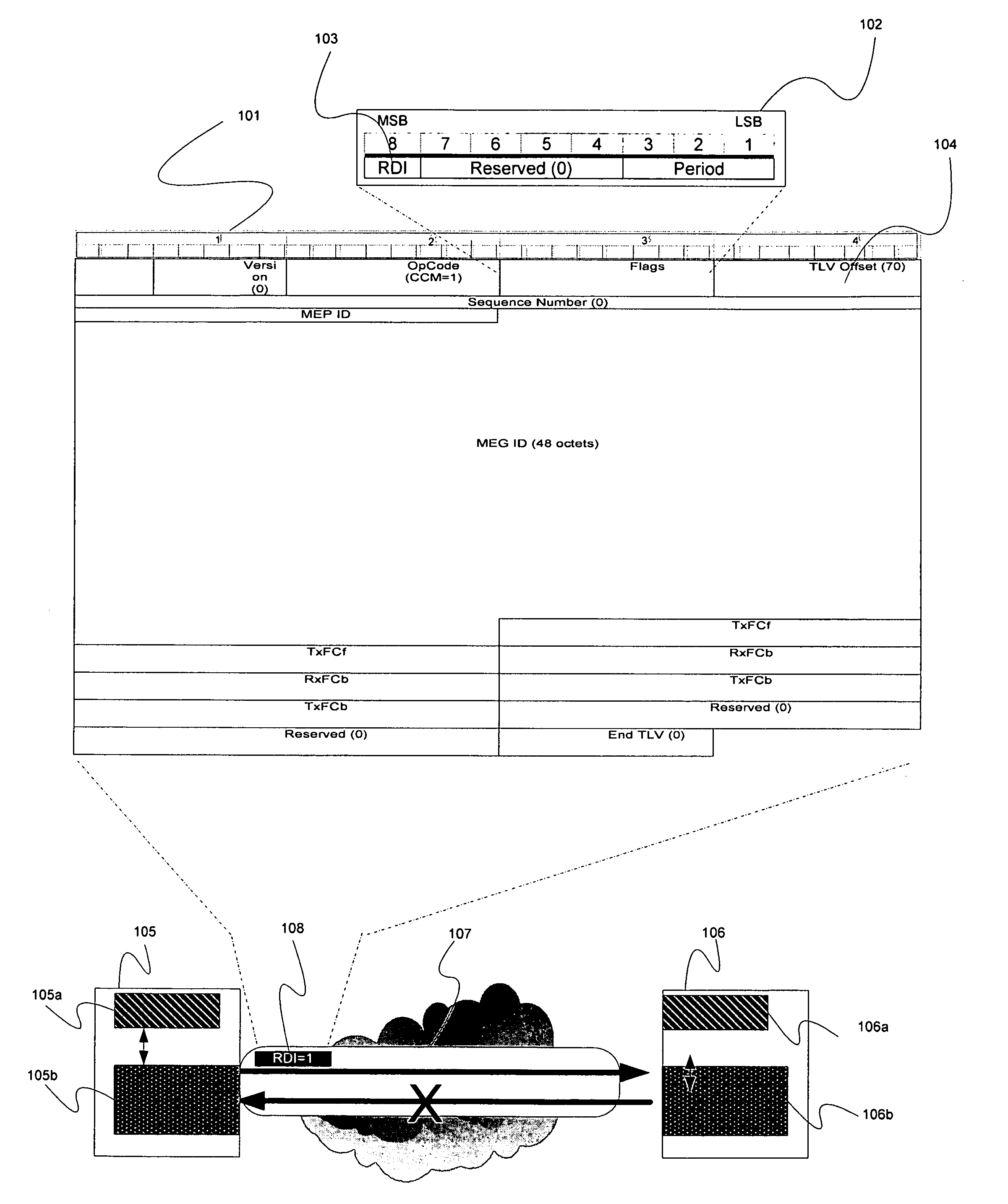
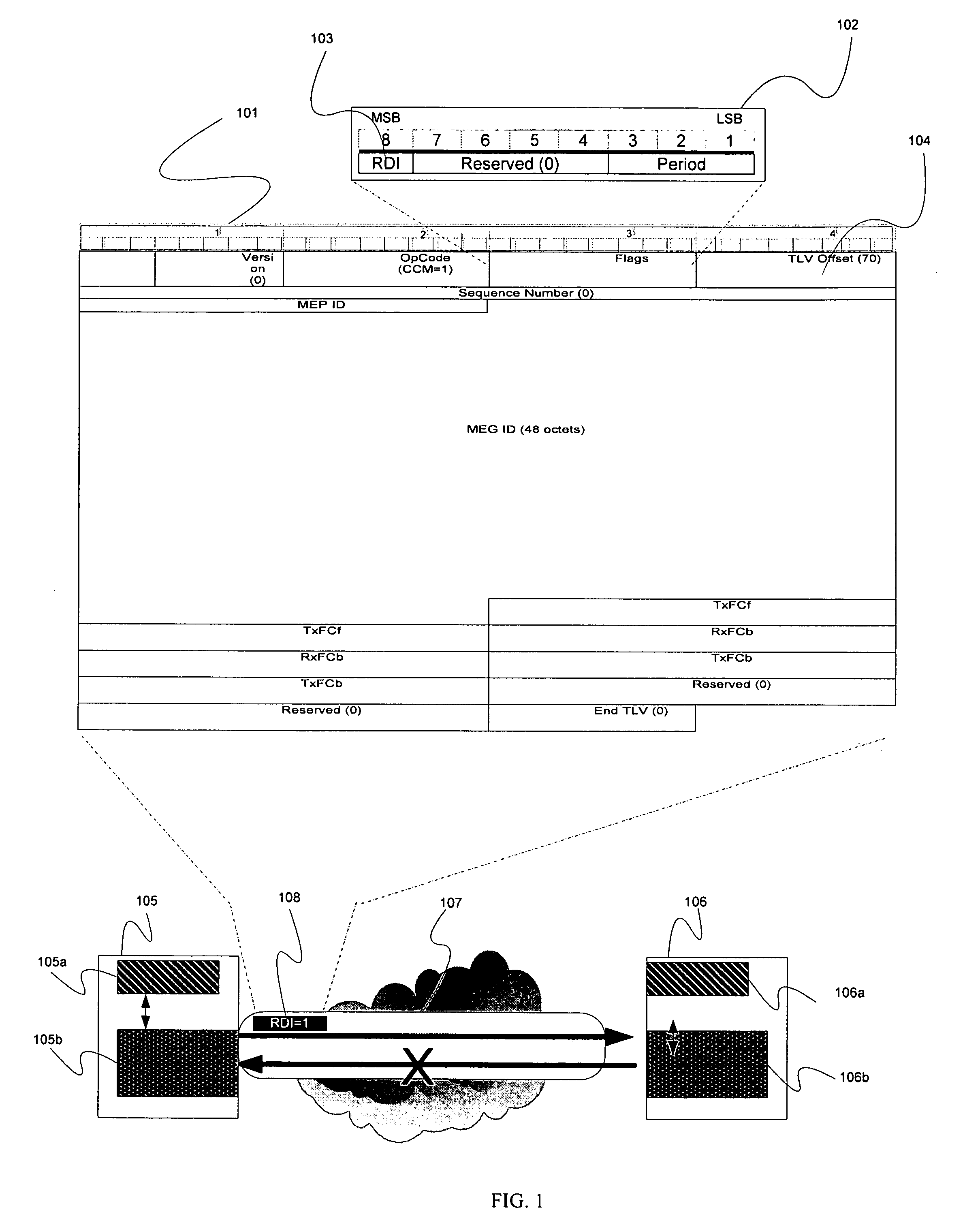
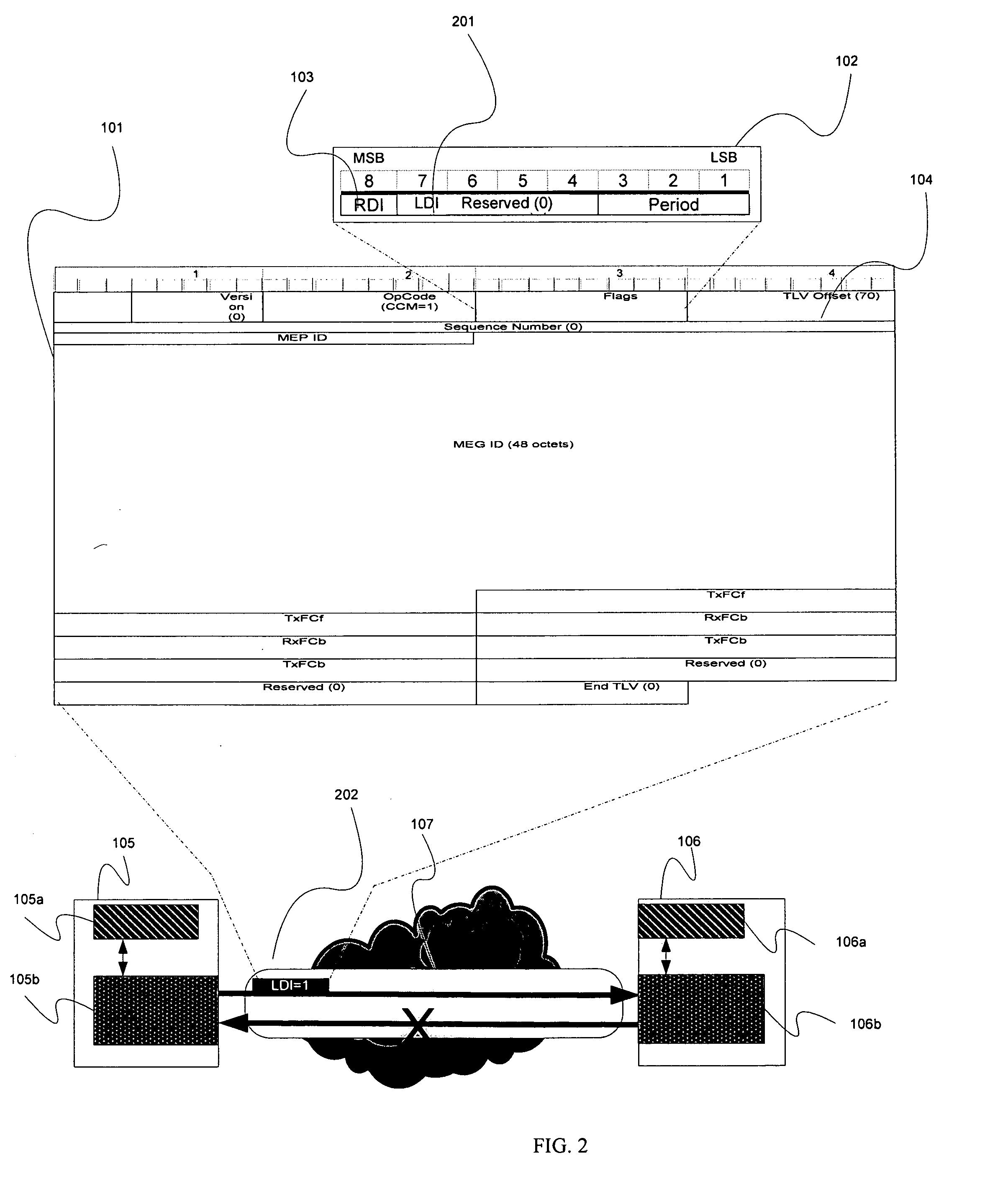
A method of fault notification in a carrier Ethernet having the capability of generating and transmitting OAM packets having flag fields, comprises inserting a bit in one of the flag fields to indicate the presence of service-affecting information in the OAM packets, detecting the presence of the inserted bit at the end of a data path, and performing a service protection action in response to the detection of the inserted bit prior to parsing the information in the message. One type of service protection action is protection switching.
Owner:CIENA
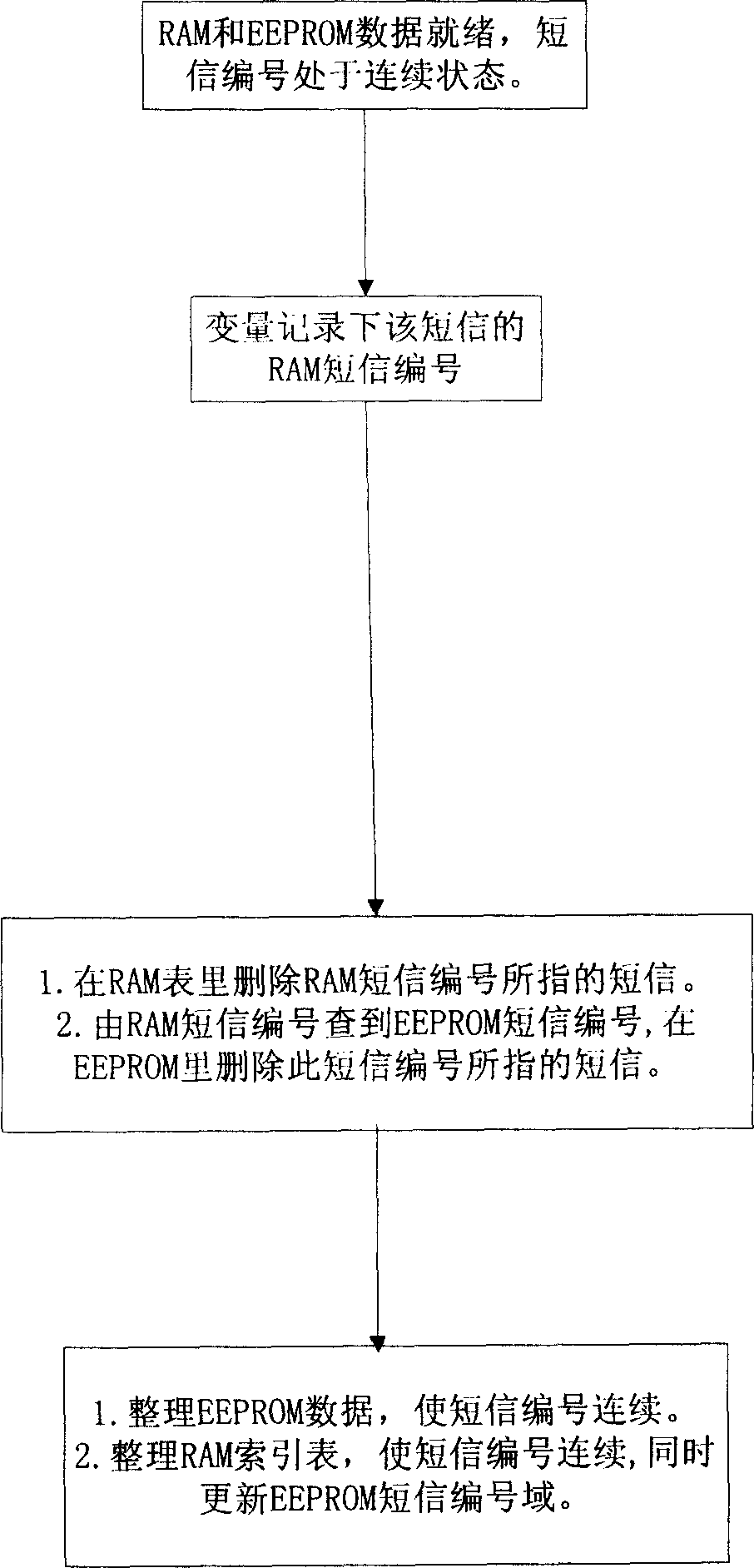
Method of deleting short messages in mobile communication terminal
InactiveCN1809186AQuick deleteFulfil requirementsRadio/inductive link selection arrangementsSubstation equipmentUser inputTheoretical computer science
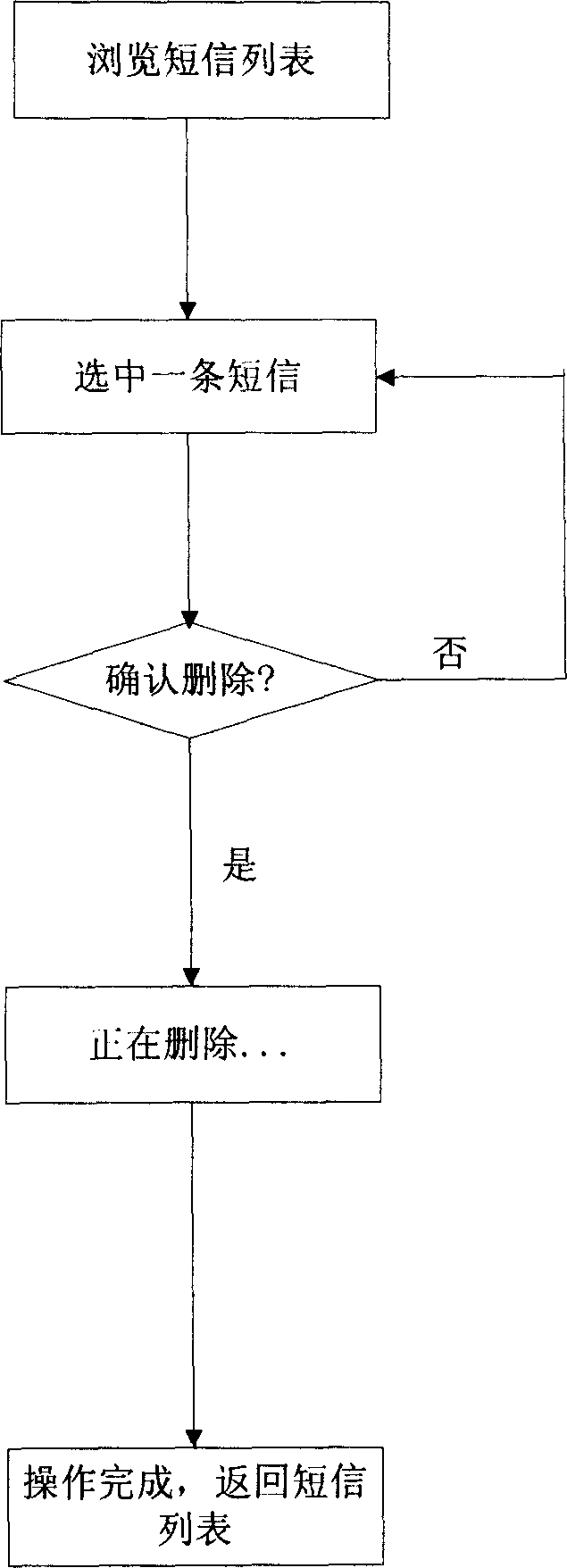
This invention relates to a note deleting method of the mobile communication terminal, which includes: building an index table in the random memorizer, and editing the sender's name and deleting marking field in the note data structure of the index table, and arranging the deleting marking field as the first value; according to the sender's name, matching the sender's name field in the index table, and arranging the deleting marking field of the matched note as the second value; deleting all the note of the read-only memorizer that match to the note whose deleting marking field is the second value, and deleting all the note whose deleting marking filed is the second value in the random memorizer. This invention also supports the reverse protect function, which can arranging the protect marking field in the index table data structure, and arranging the protective field as a certain value, and if the protective field is the certain value, then the note won't be deleted.
Owner:UTSTARCOM TELECOM CO LTD
Method for implementation of FLASH chip data security
InactiveCN101079010AEnsure data securityEnsure safetyMemory loss protectionRedundant operation error correctionElectricityFlag field
The invention discloses a method to realize FLASH chip data safety, which comprises the following steps: 1, dividing the FLASH chip to index zone, standby zone and host using zone; storing effective index structure with the index zone; setting the effective index structure as host using zone effective index field, host using zone address field, data length field and standby zone effective index field; 2, writing the present data of the host using zone, writing data and integral data into the standby zone; rewriting the field arrangement of the effective index structure; 3, writing the present data, writing data and integral data of the standby zone to the host using zone; rewriting the filed arrangement of the effective index structure. This invention is a method, which can keep the safety of the FLASH chip.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Input parameter generalization method and device based on rule engine packet, and storage medium
ActiveCN108492195ATo achieve the goal of "once and for all"FinanceSpecial data processing applicationsData transmissionDatabase
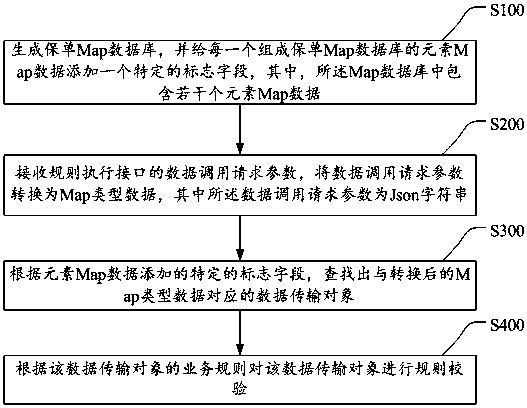
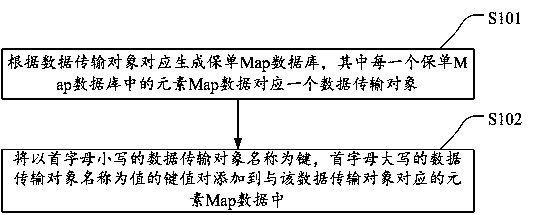
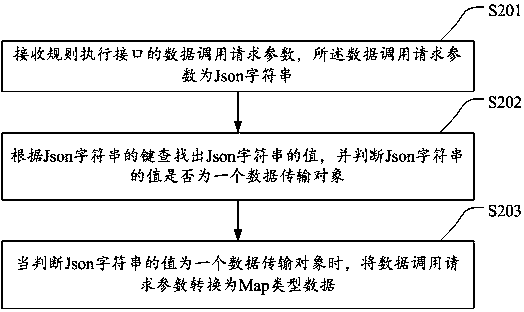
The invention discloses an input parameter generalization method and device based on a rule engine packet, and a storage medium. The method comprises the steps: generating a warranty Map database, andadding one specific mark field to each piece of element Map data in the warranty Map database, wherein the Map database comprises a plurality of pieces of element Map data; receiving a data call request parameter of a rule execution interface, and converting the data call request parameter into the data at the Map format, wherein the data call request parameter is a Json character string; searching a data transmission object corresponding to the converted data at the Map format according to the added specific mark fields of the element Map data; and carrying out the rule verification of the data transmission object according to a business rule of the data transmission object. The method can generalize the parameters of the rule engine packet, so only the corresponding rule needs to be developed when a business system needs to join in a rule cloud platform system afterwards, thereby achieving a once-for-all purpose.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Safety production comprehensive supervisory platform data transmission method
InactiveCN103793749AReduce the number of deploymentsReduce occupancyTransmissionInstrumentsSynthetic dataData content
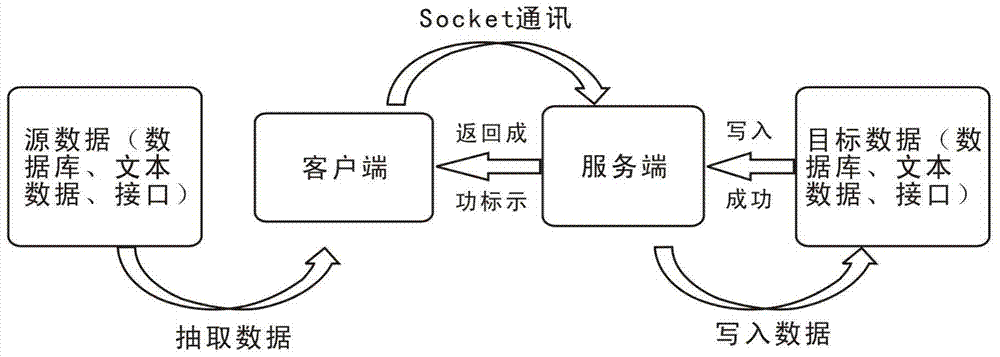
The invention discloses a safety production comprehensive supervisory platform data transmission method which is used for achieving data transmission between a client side and a central server, namely a server side. The method comprises the following steps that the client side reads a configuration file, safety production comprehensive data are analyzed, after a client side position flag field value is obtained or updated according to a position flag field value fed back by the server side, the analyzed data generate text message data and the text message data are encrypted, and then the text message data are sent to the server side through Socket communication; after the server side receives the data, the data content is analyzed to be in a target data format to be judged whether it meets writing in conditions, the position flag field value which is not written in is returned to the client side, or after the data are written in, the position flag field value which is successfully processed is returned to the client side, and meanwhile the position flag field value is stored and the server side position flag field value is updated. The method supports calling of various mainstream databases, various text protocols and data interfaces which are popular currently, and can cross platforms and carry out distributed deployment.
Owner:SICHUAN SENSINGNET HEALE SECURITY TECH LTD
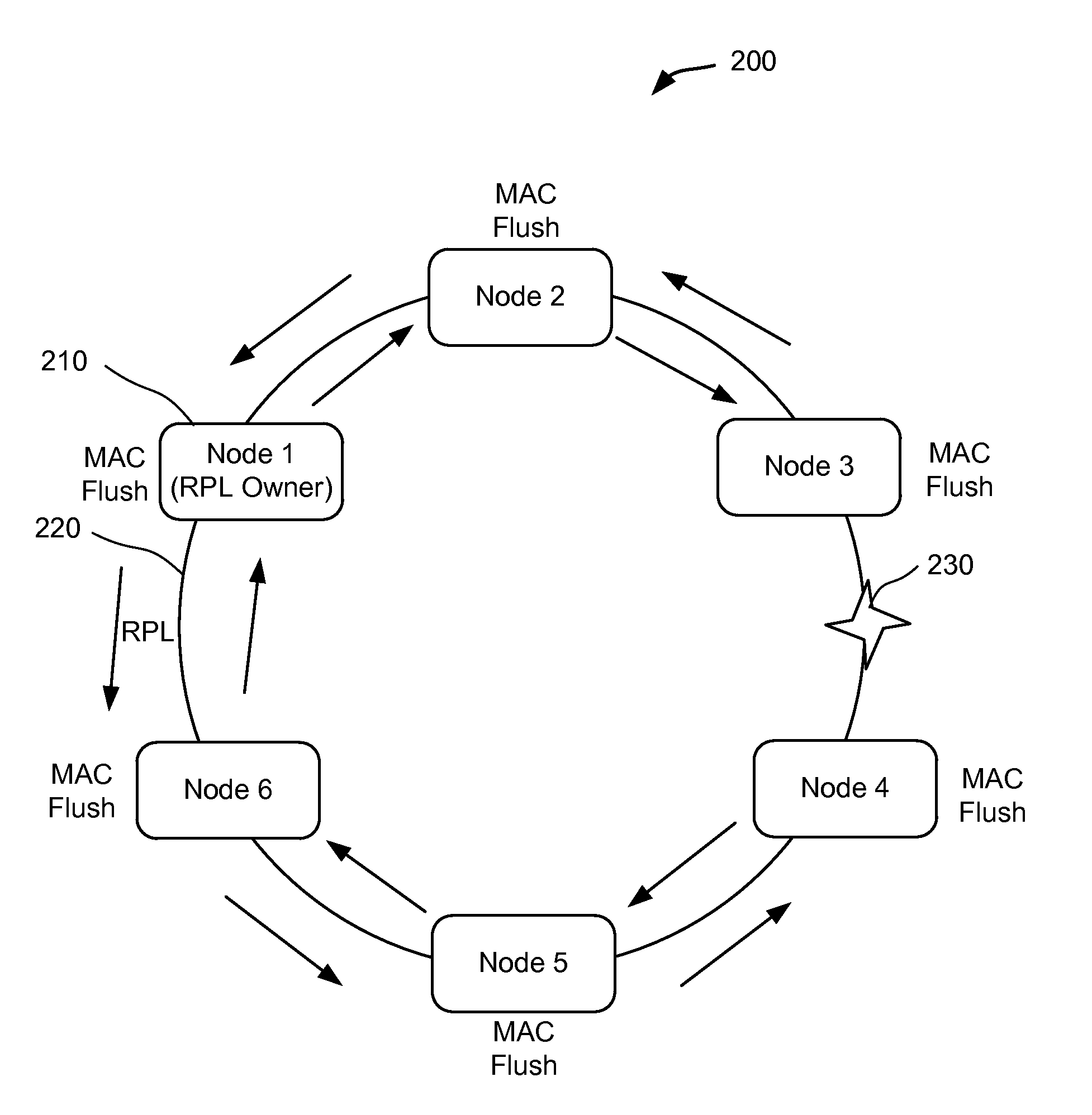
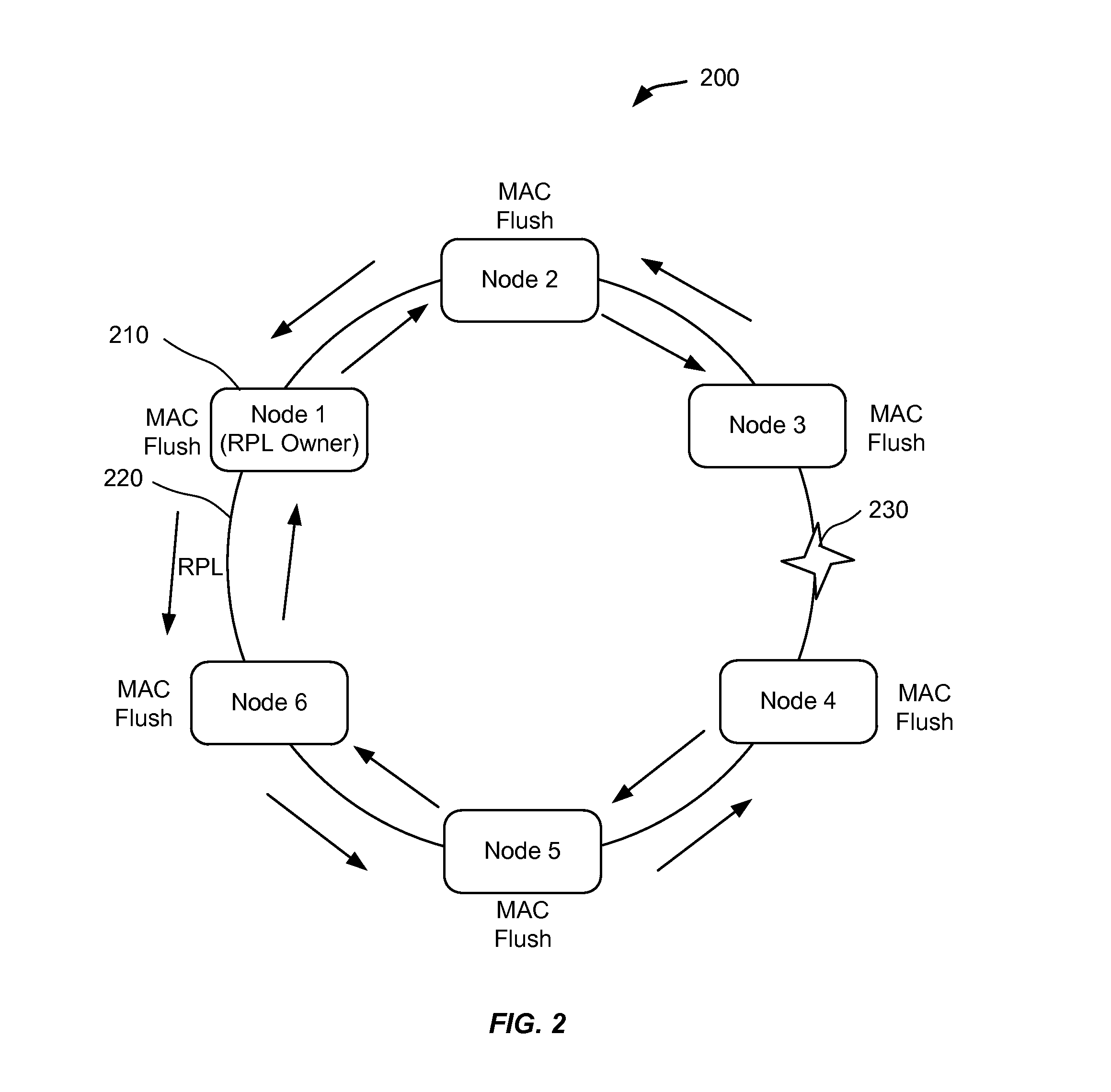
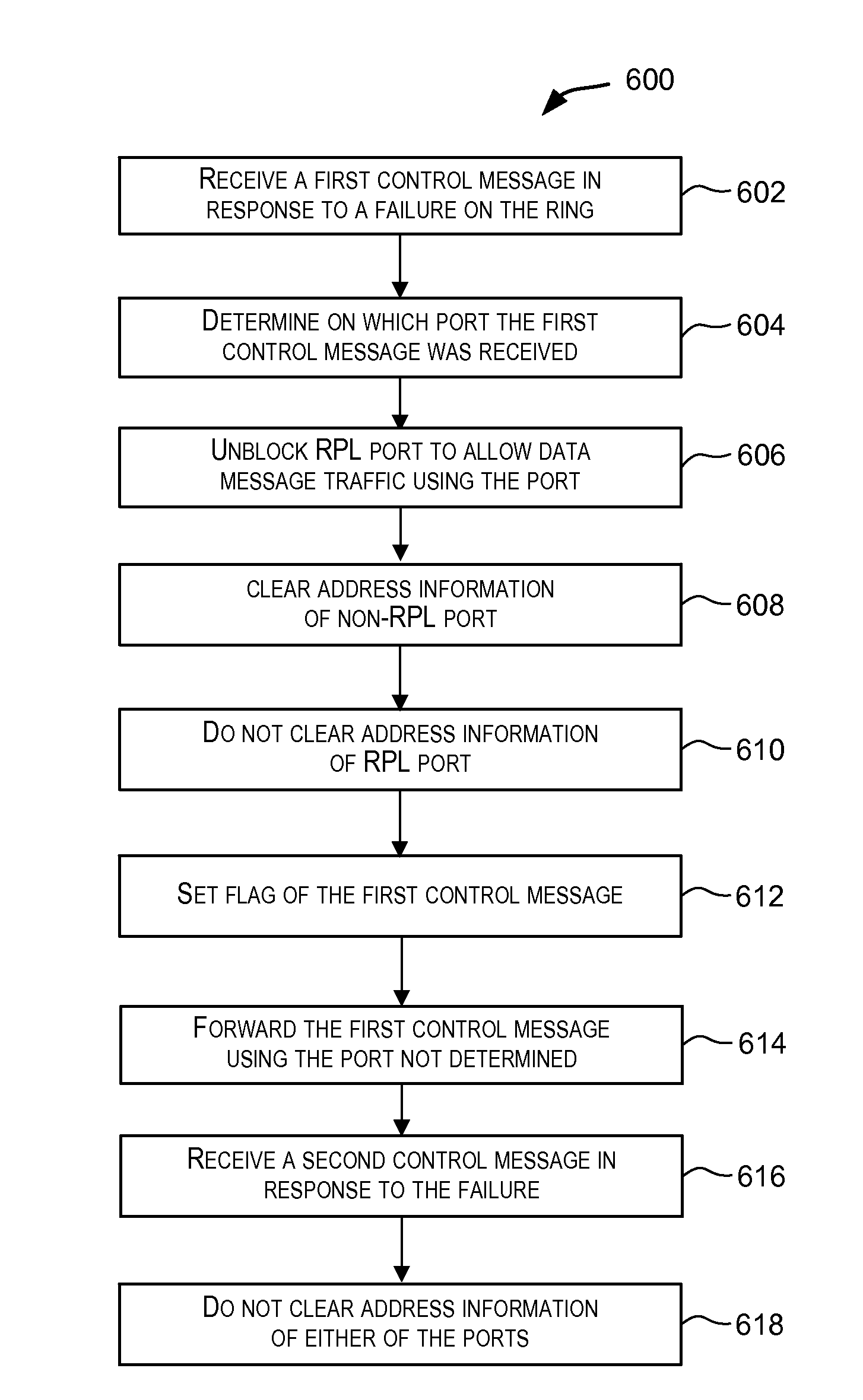
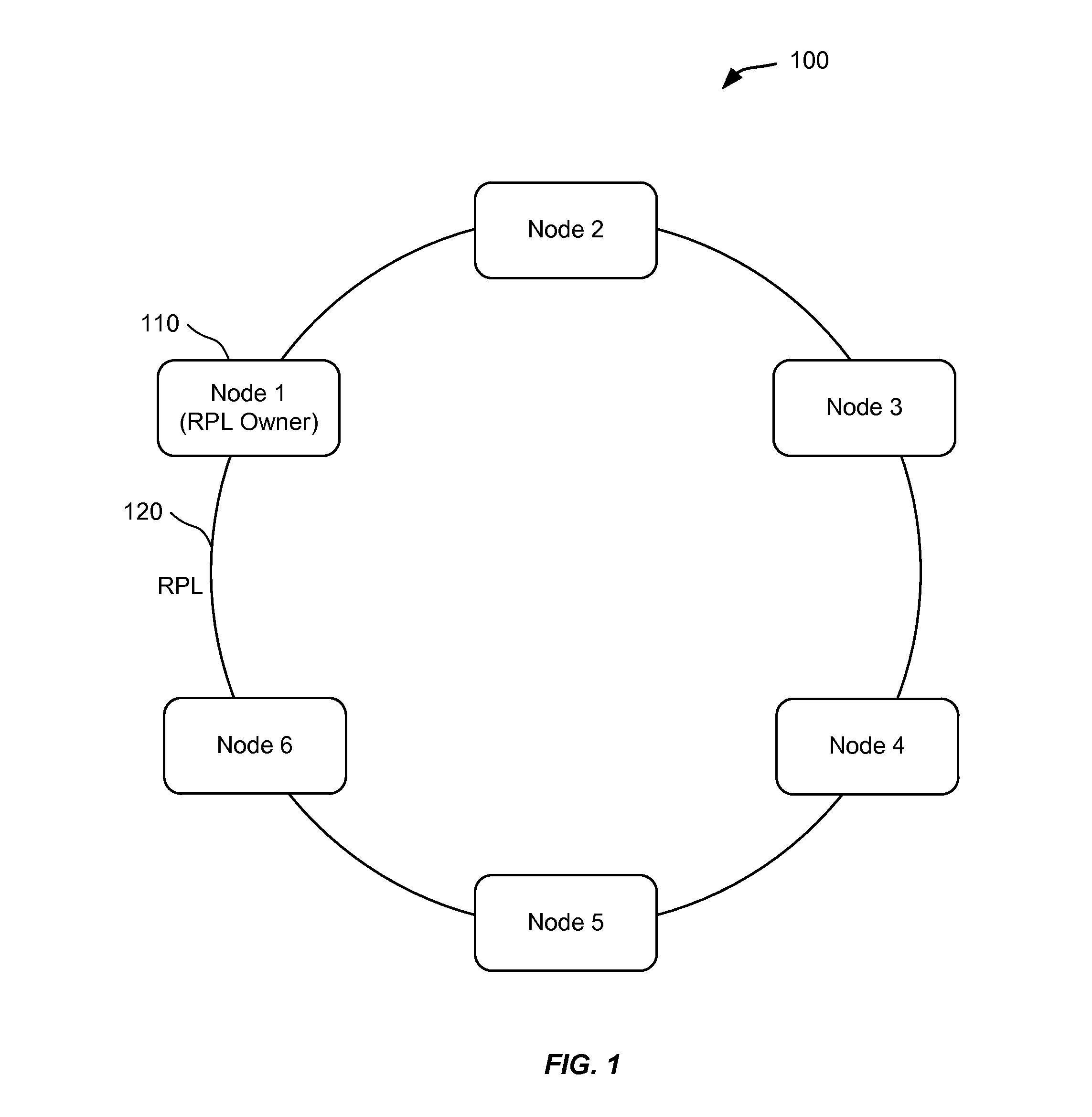
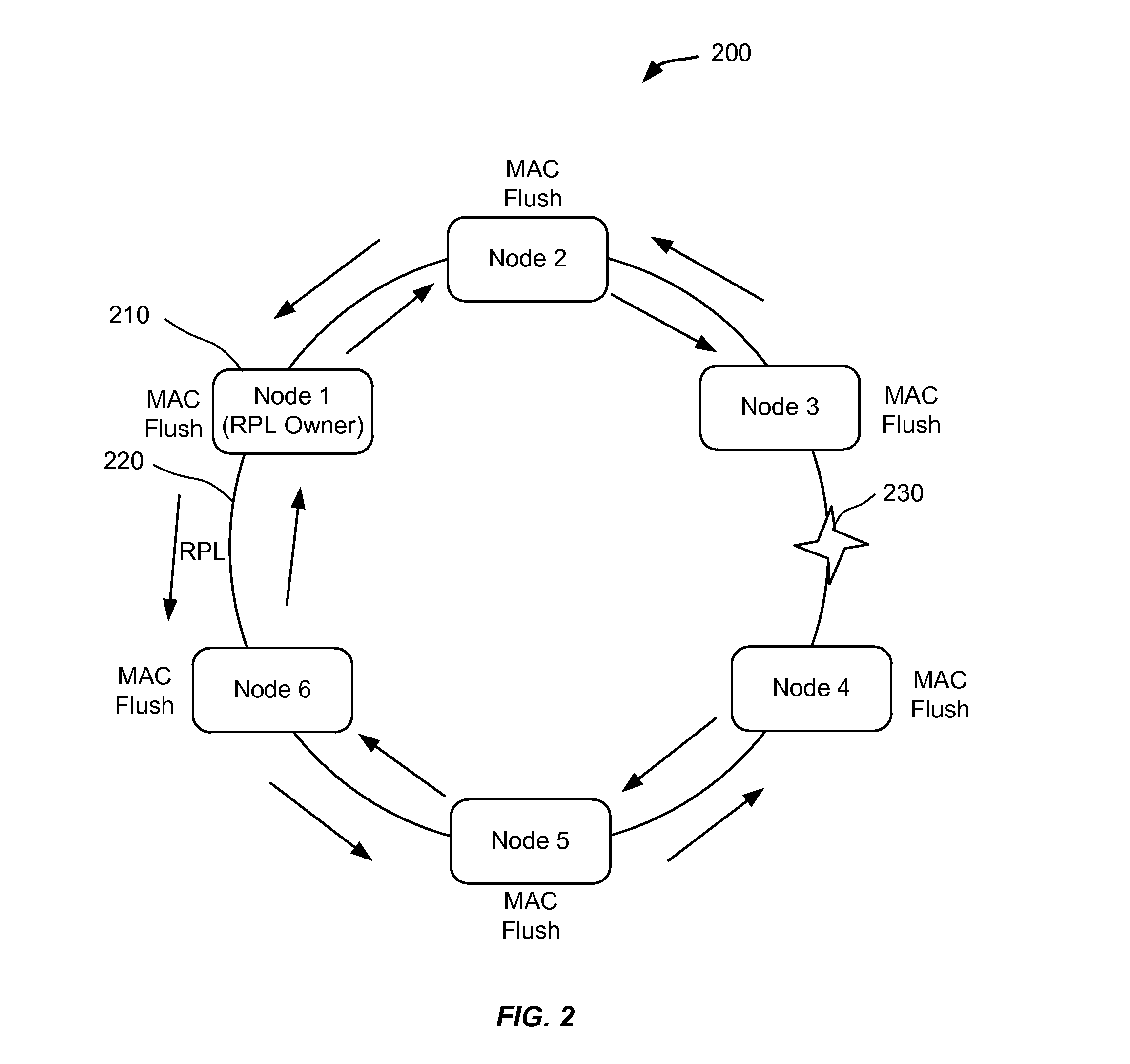
Mac flush optimizations for ethernet rings
Techniques are identified for optimizing the MAC flush in Ethernet rings for faster traffic restoration. In one embodiment, flushing of MAC addresses is performed only once on receiving a first control message. For example, when a first control message is received, a network device may switch from a first state to a second state, which may indicate that the MAC addresses are not to be flushed if additional control messages are received. In another embodiment, flushing of MAC addresses is performed on one ring port rather than on both ring ports. For example, a flag field of a control message header may be used to determine on which port to flush. In another embodiment, flushing of MAC addresses is performed on only one ring port of an interconnection node. For example, the ring port can be determined using a flag field and possibly labels associated with the ring ports.
Owner:AVAGO TECH INT SALES PTE LTD
Mac flush optimizations for ethernet rings
ActiveUS20140064061A1Error preventionFrequency-division multiplex detailsTraffic capacityInterconnection
Techniques are identified for optimizing the MAC flush in Ethernet rings for faster traffic restoration. In one embodiment, flushing of MAC addresses is performed only once on receiving a first control message. For example, when a first control message is received, a network device may switch from a first state to a second state, which may indicate that the MAC addresses are not to be flushed if additional control messages are received. In another embodiment, flushing of MAC addresses is performed on one ring port rather than on both ring ports. For example, a flag field of a control message header may be used to determine on which port to flush. In another embodiment, flushing of MAC addresses is performed on only one ring port of an interconnection node. For example, the ring port can be determined using a flag field and possibly labels associated with the ring ports.
Owner:AVAGO TECH INT SALES PTE LTD
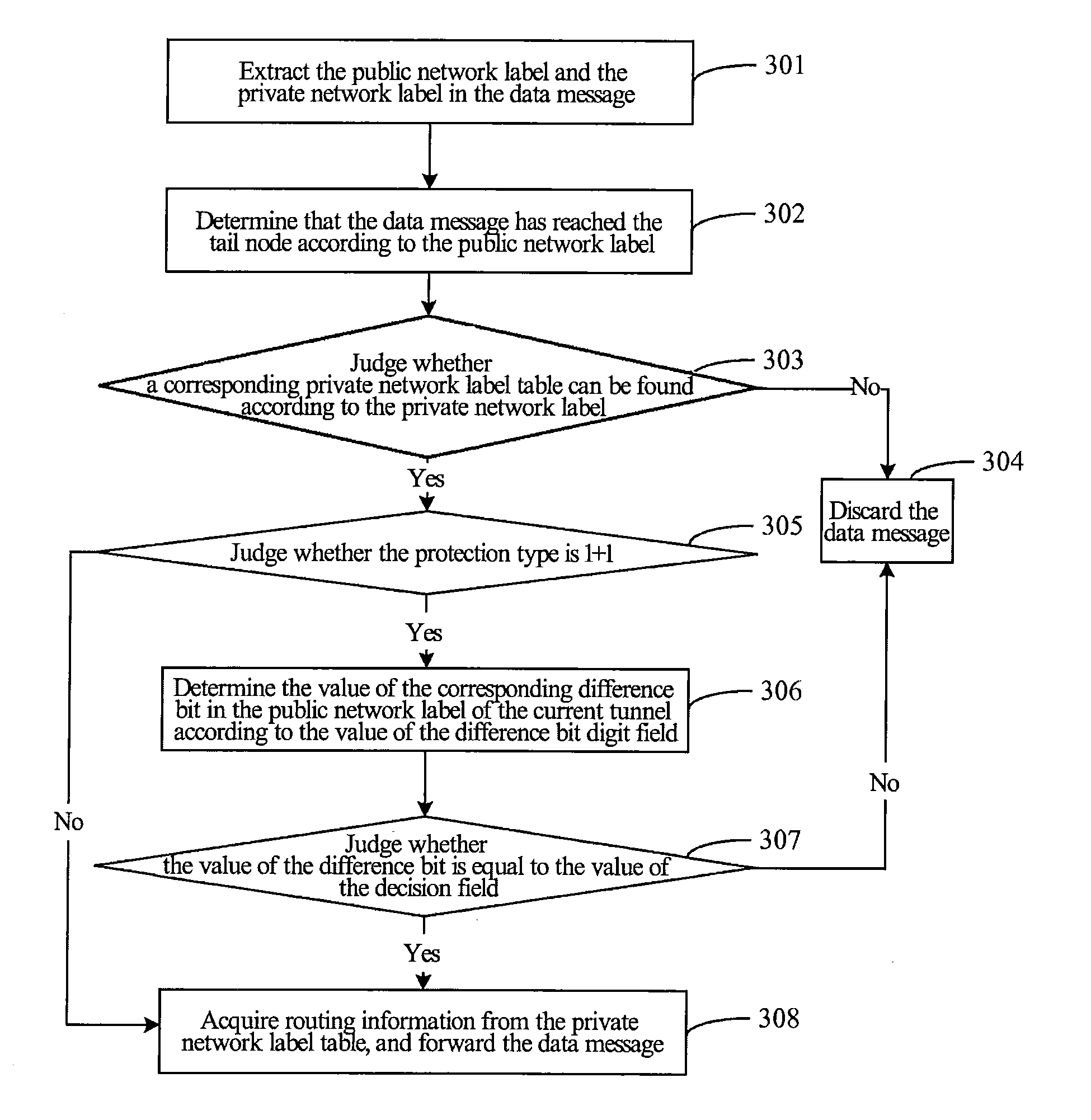
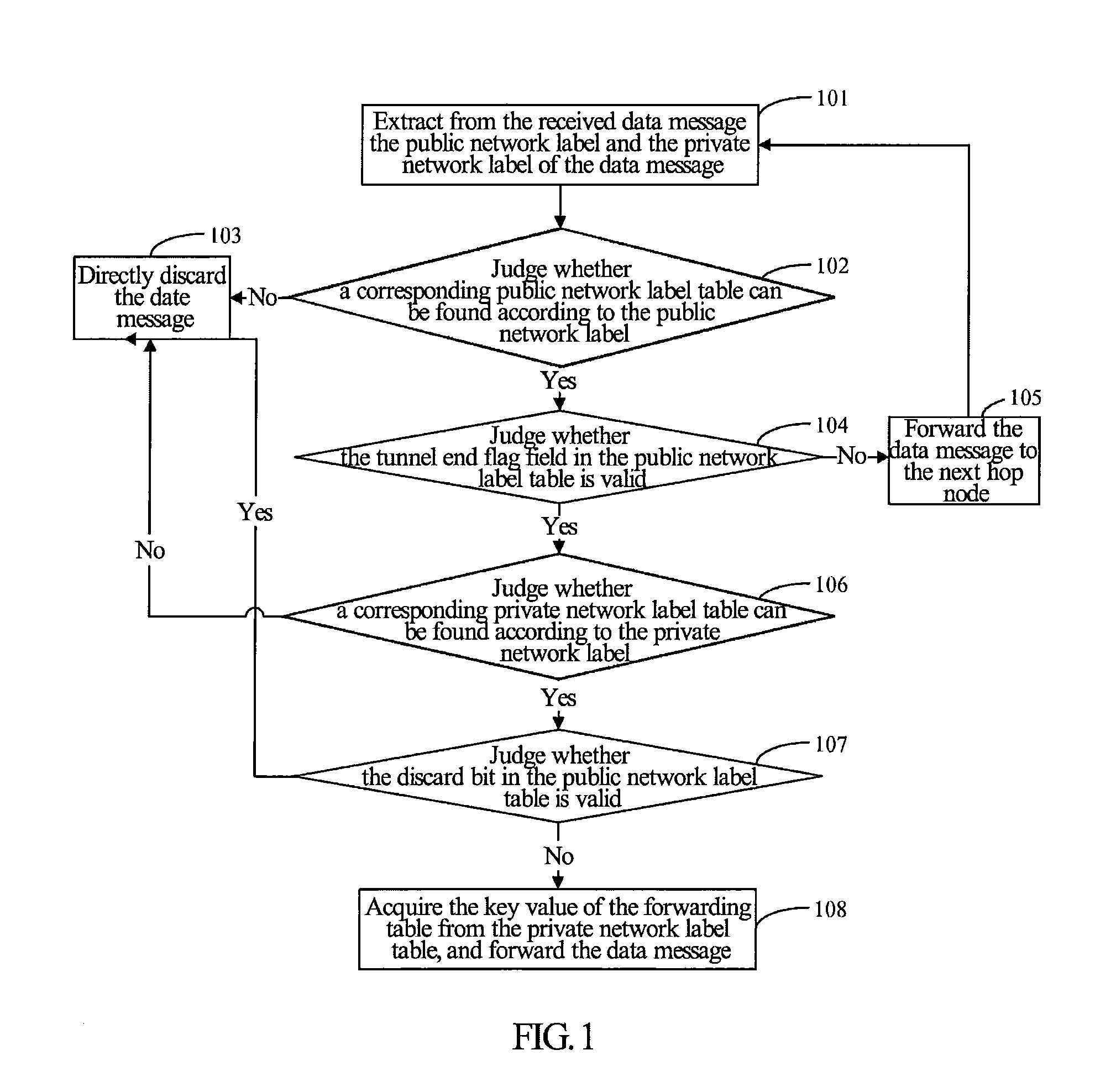
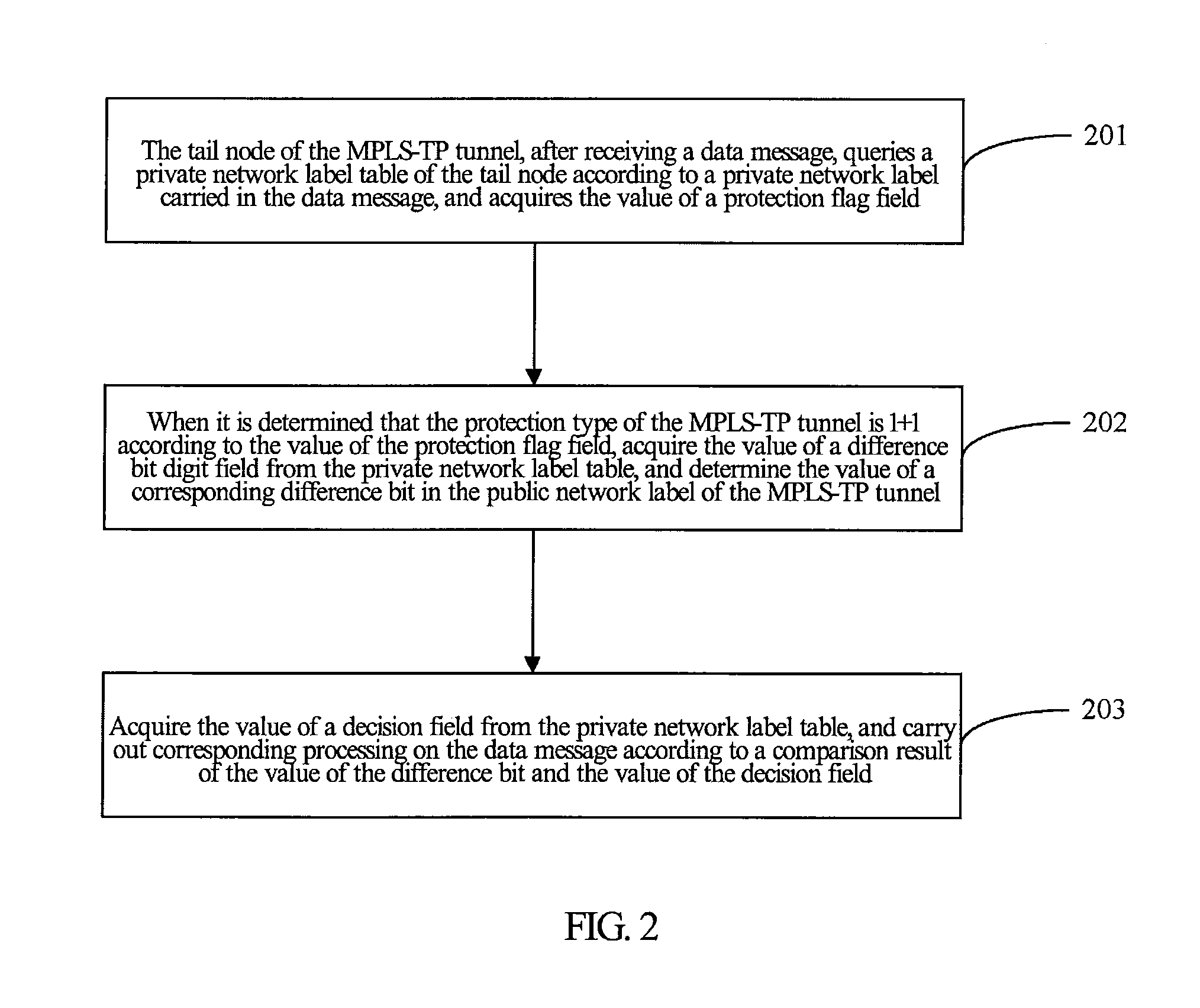
Method and system for mpls-tp tunnel protection processing
InactiveUS20120182990A1Shorten the timeImprove data processing capabilitiesData switching by path configurationPrivate networkPublic network
The present invention discloses a method and system for processing an MPLS-TP tunnel protection, including: a tail node of a multiprotocol label switching transport profile (MPLS-TP) tunnel, after receiving a data message, querying a private network label table of the tail node according to a private network label carried in the data message, and acquiring a value of a protection flag field; when judging that a protection type of the MPLS-TP tunnel is 1+1 according to the value of the protection flag field, acquiring a value of a difference bit number field, and determining a value of a corresponding difference bit in a public network label of the MPLS-TP tunnel; and acquiring a value of a decision field, and carrying out corresponding processing on the data message according to a comparison result of the value of the difference bit and the value of the decision field. With the present invention, the processing performance of the data message on the MPLS-TP tunnel can be improved.
Owner:ZTE CORP
Carrier Ethernet with fault notification
A method of fault notification in a carrier Ethernet having the capability of generating and transmitting OAM packets having flag fields, comprises inserting a bit in one of the flag fields to indicate the presence of service-affecting information in the OAM packets, detecting the presence of the inserted bit at the end of a data path, and performing a service protection action in response to the detection of the inserted bit prior to parsing the information in the message. One type of service protection action is protection switching.
Owner:CIENA
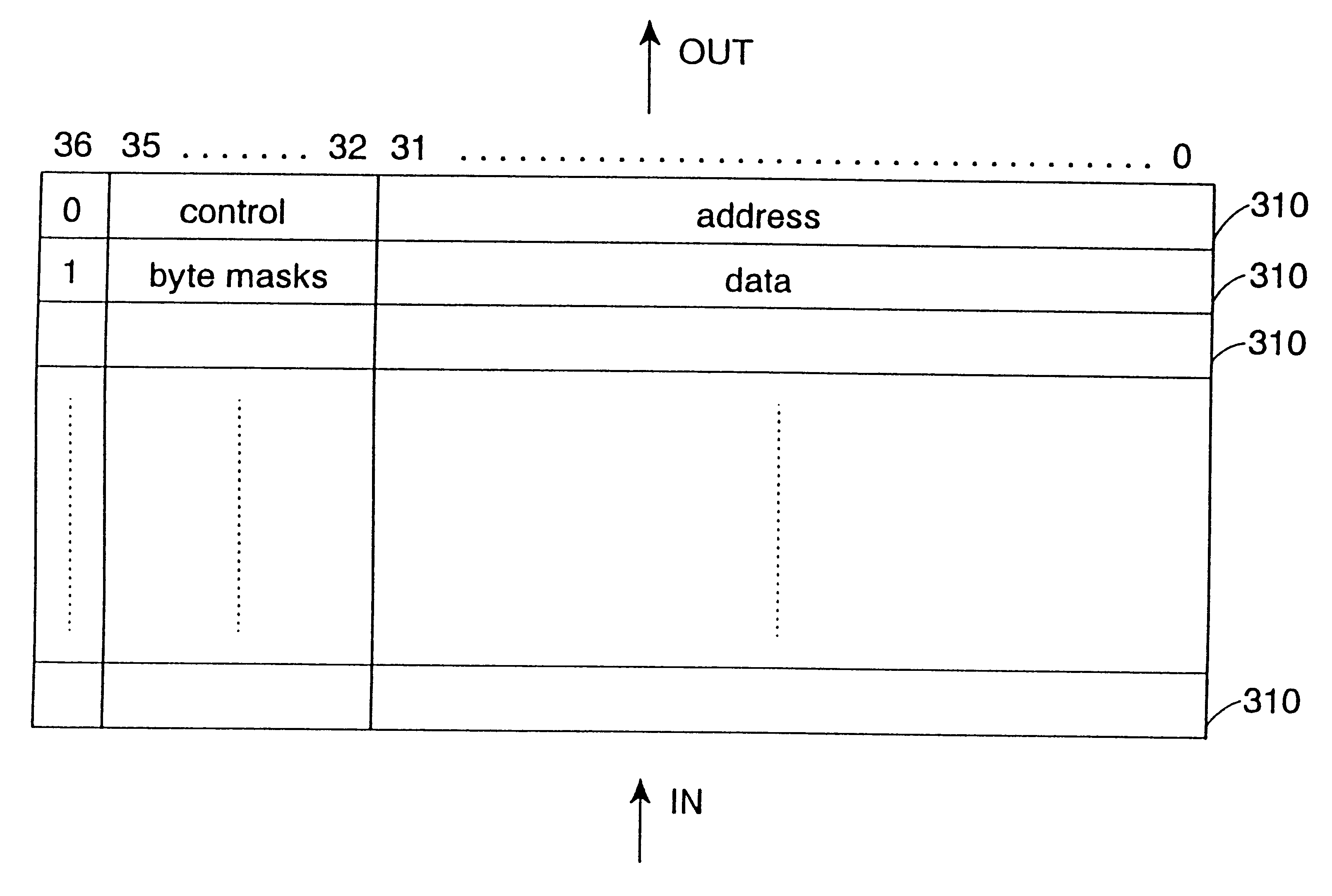
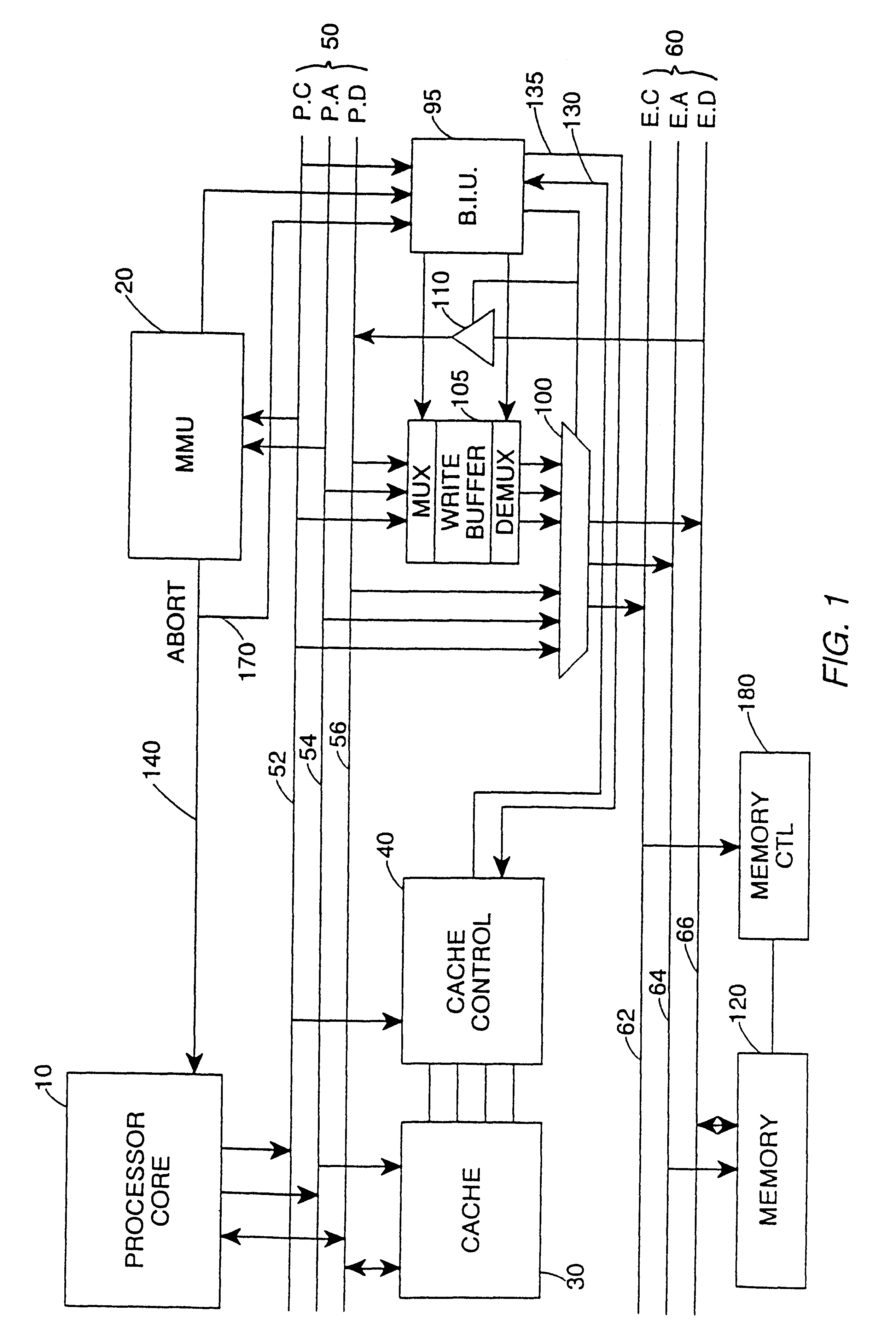
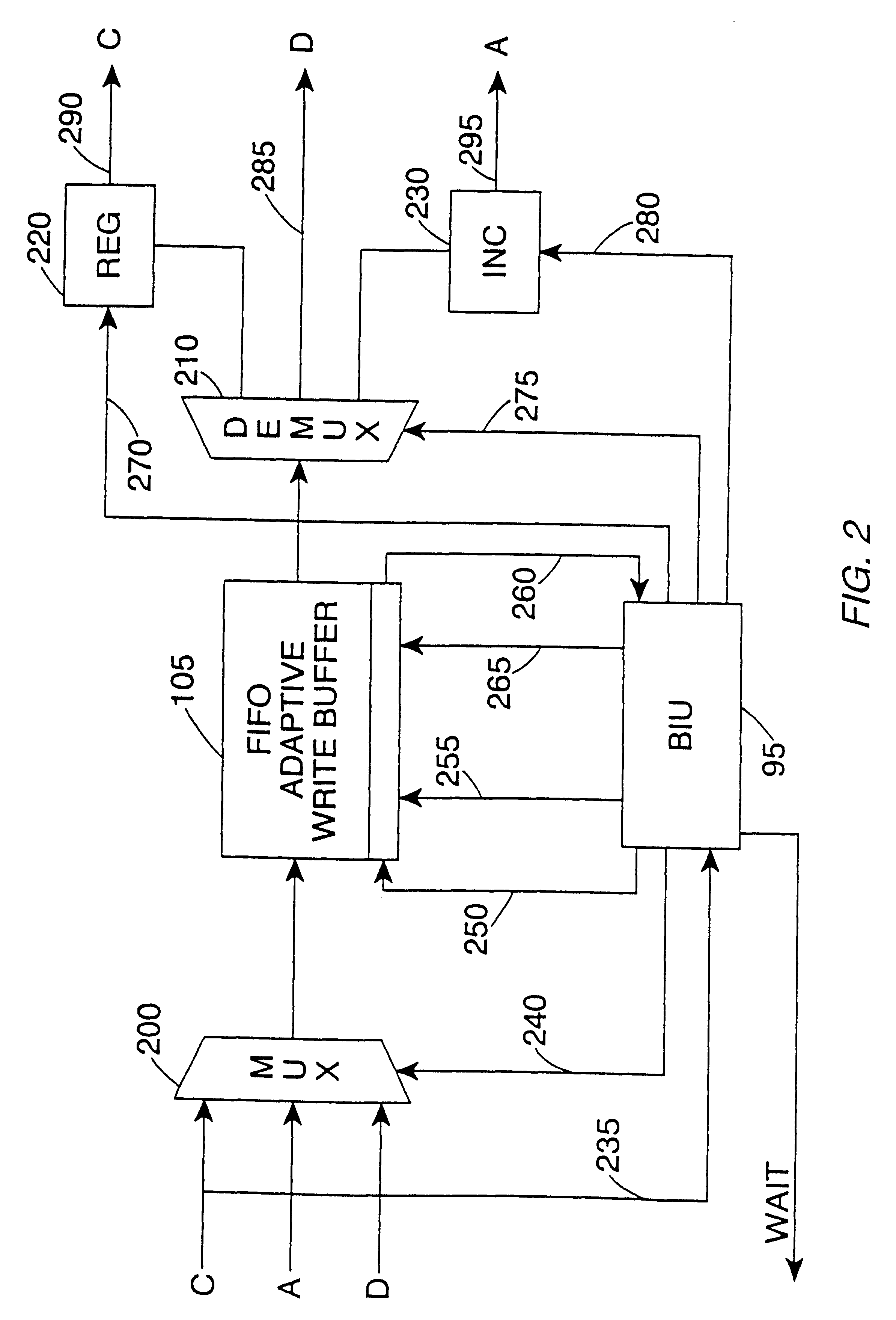
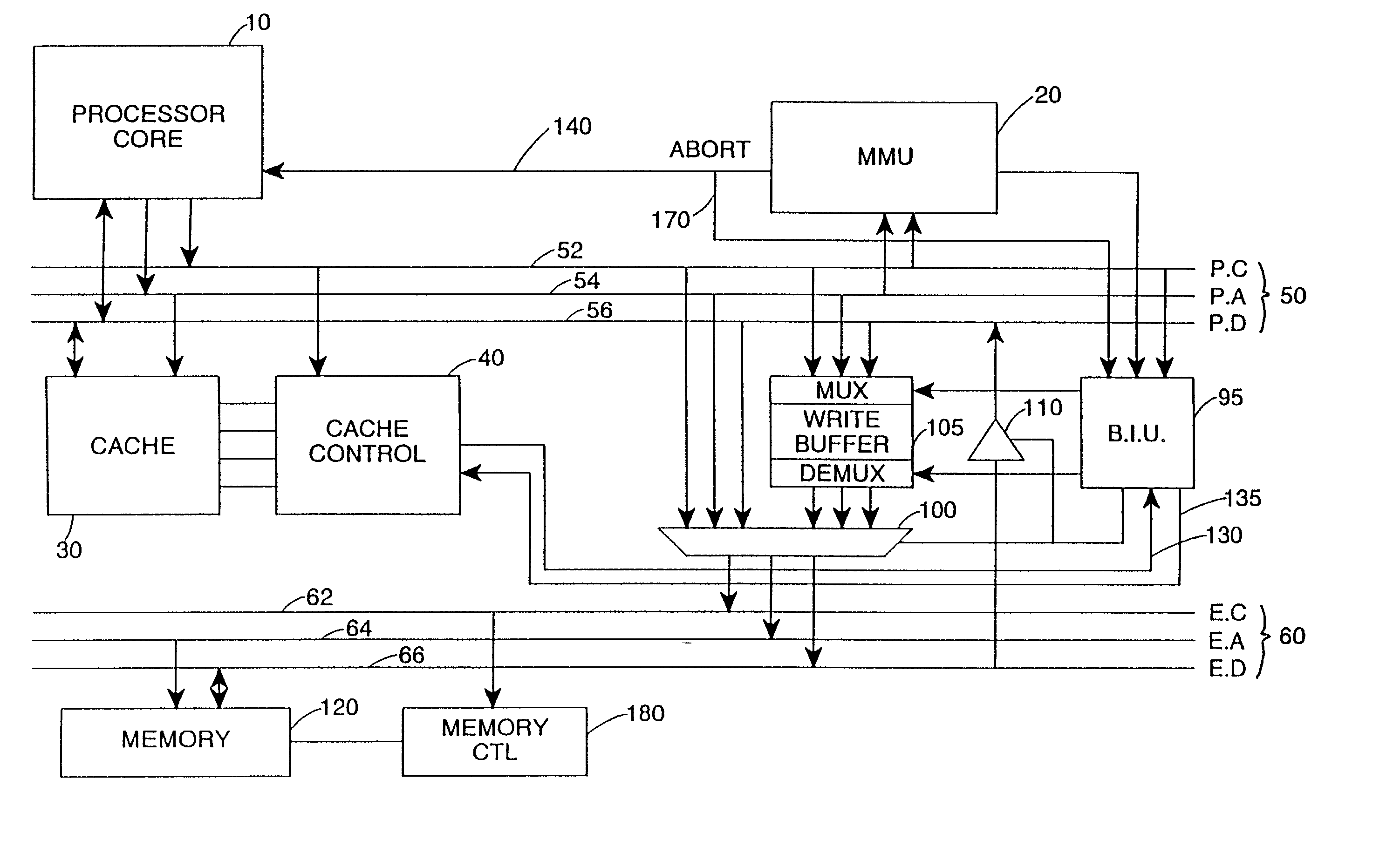
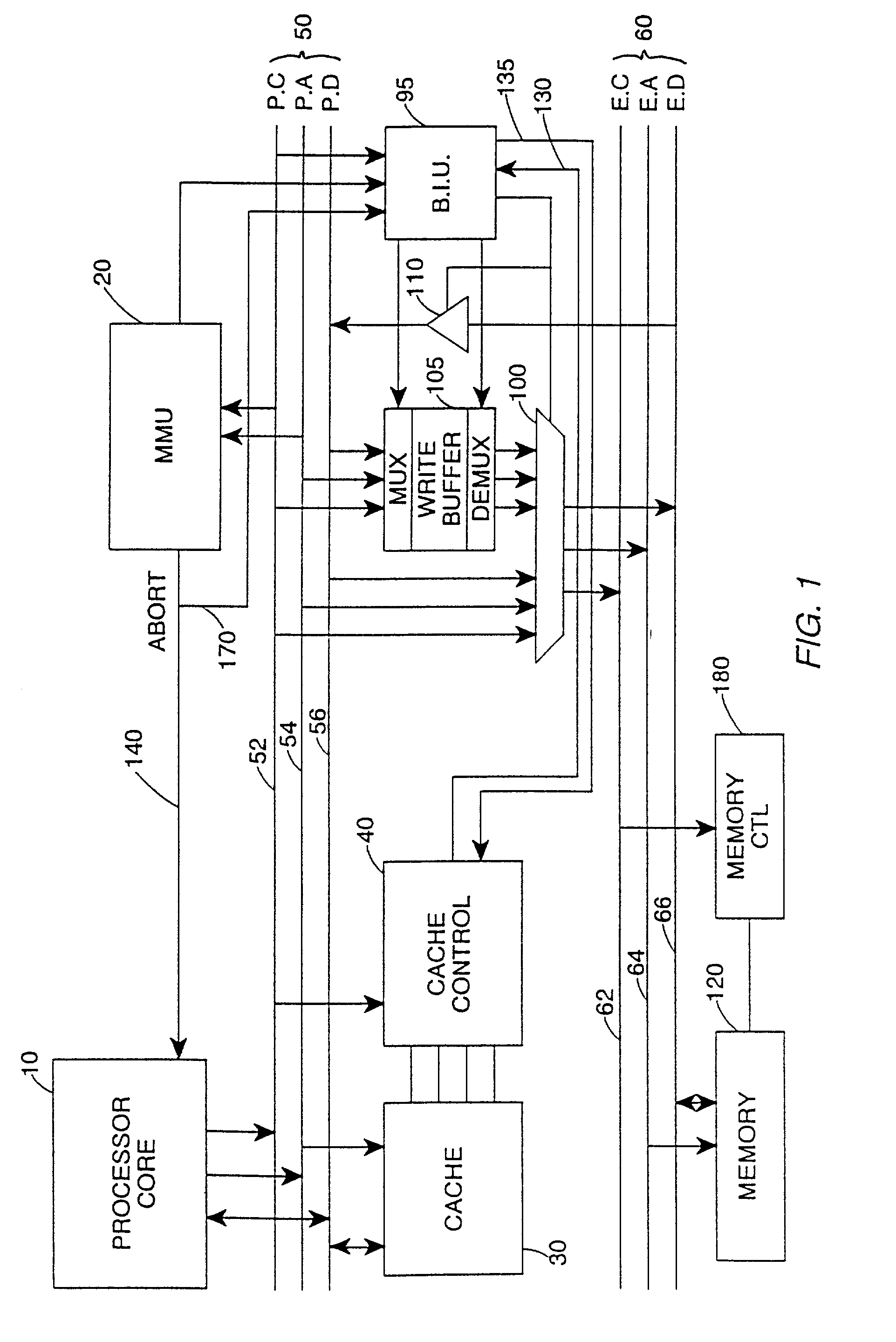
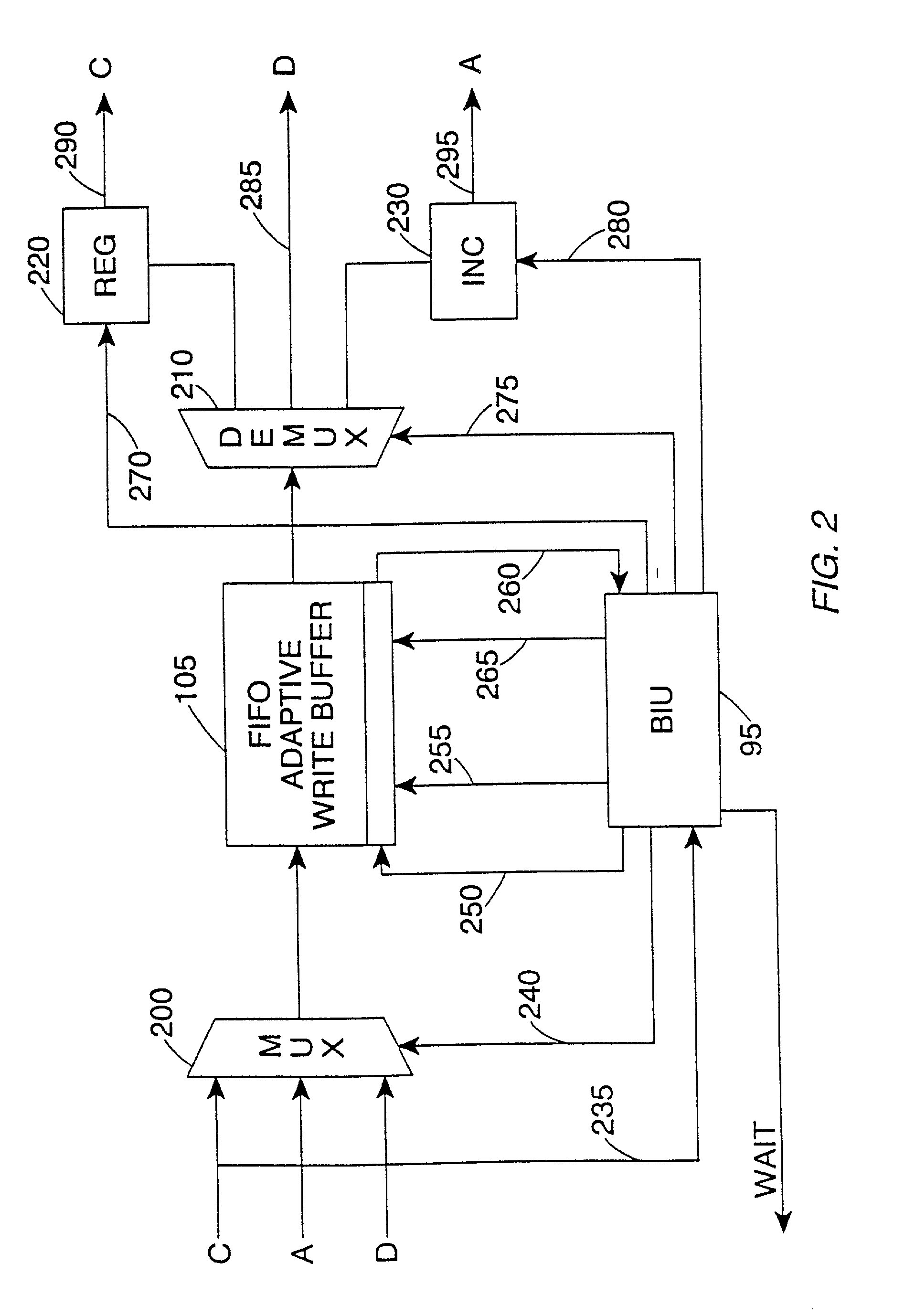
Write buffer for use in a data processing apparatus
InactiveUS6415365B1Easy to useReduce areaMemory adressing/allocation/relocationData conversionWrite bufferData value
The present invention provides a data processing apparatus comprising a processor core for generating addresses identifying locations in a memory and data values for storing in the memory, and a write buffer for storing the addresses and data values output by the processor core, and for subsequently outputting said addresses and data values to cause the data values to be stored in said memory. The write buffer comprises a plurality of rows, each row being arranged to store an address or data value, and each row having associated therewith a flag field settable to indicate whether that row contains an address or a data value.In accordance with the present invention, the write buffer provided by the data processing apparatus adaptively adjusts the number of rows it requires for addresses, and hence can be arranged to occupy a relatively small area, whilst still efficiently supporting both burst mode and non-burst mode write traffic.
Owner:ARM LTD
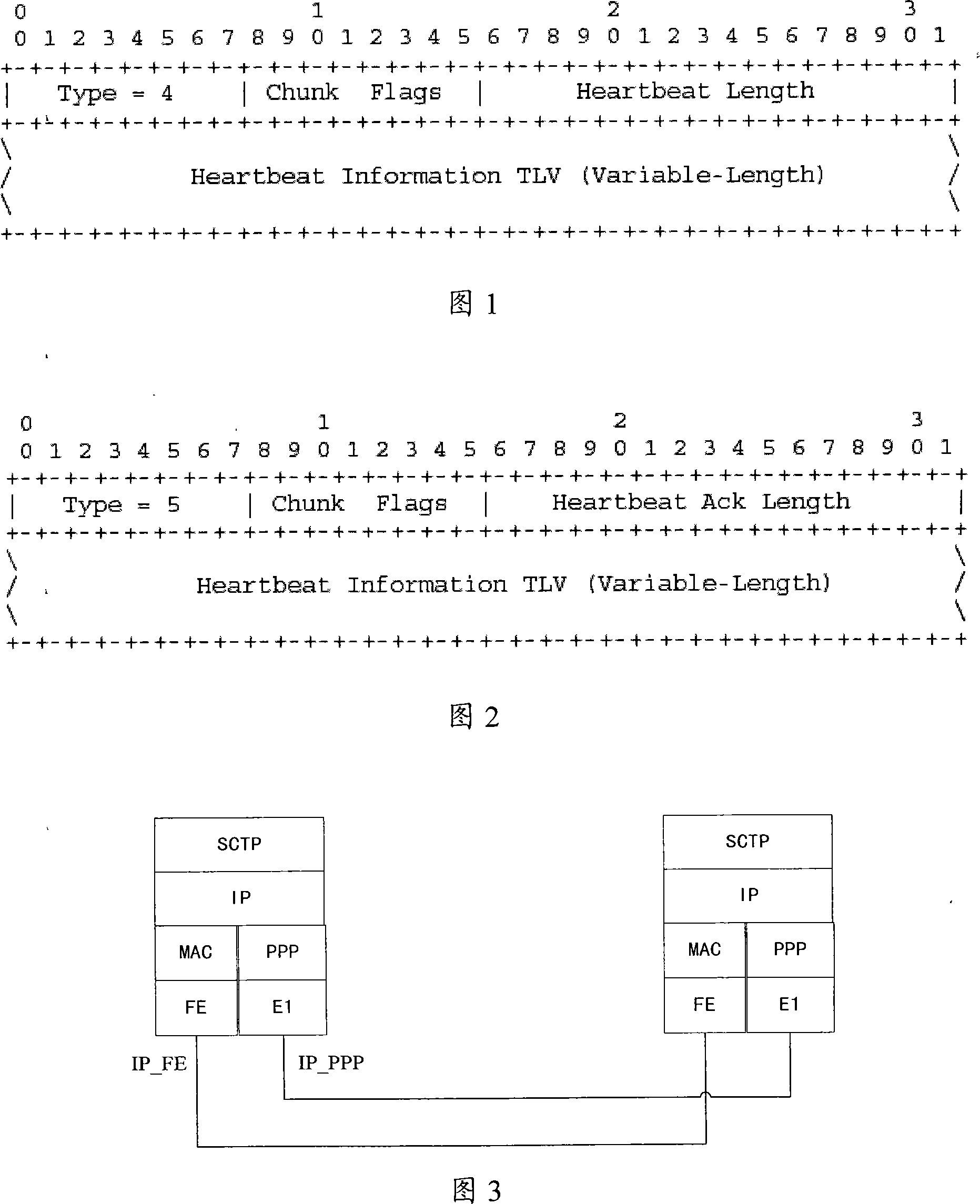
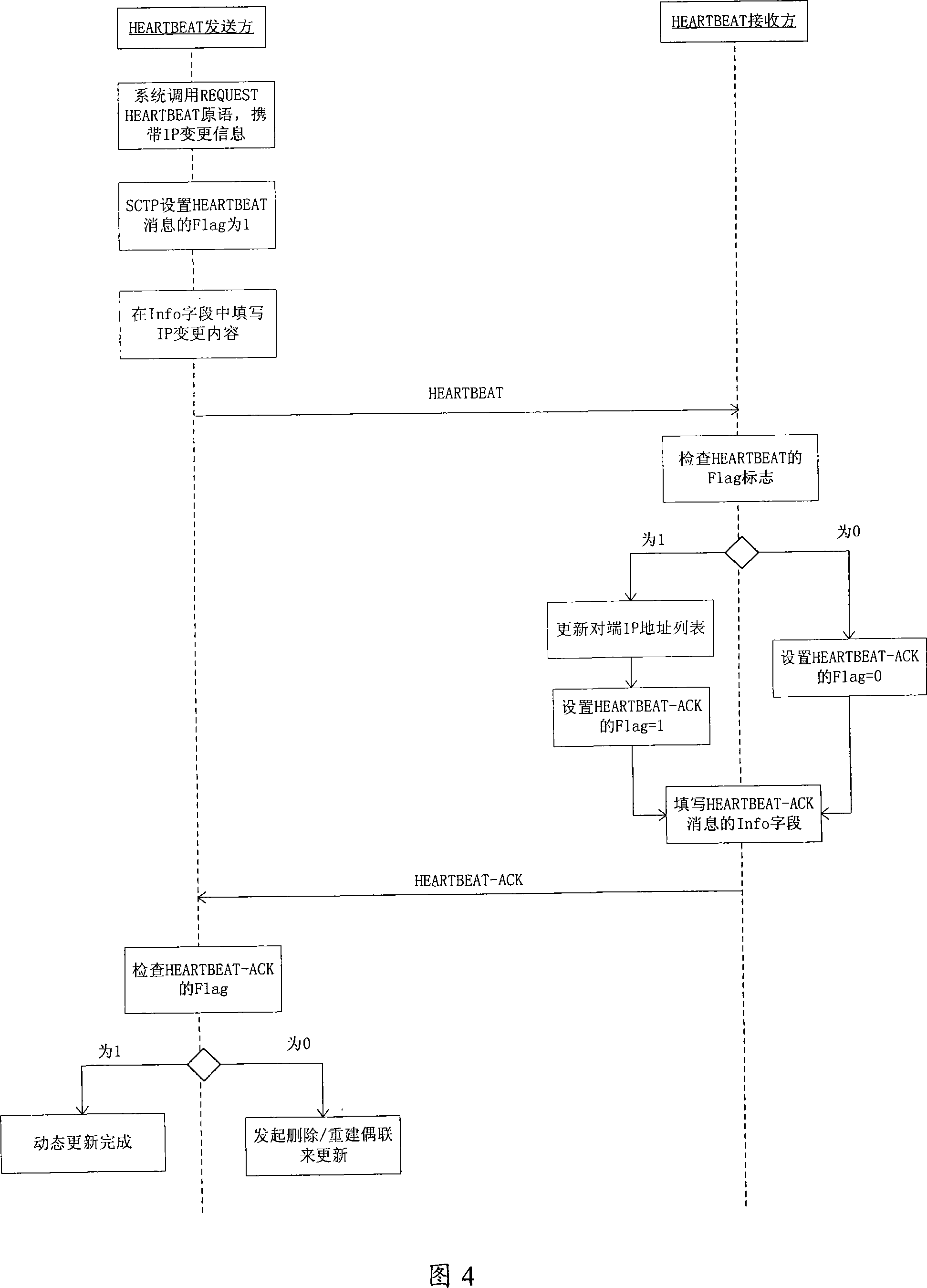
A method for dynamic update of flow control transmission protocol address list
InactiveCN101127778ADoes not affect connectivityData switching networksTransmission protocolCoupling
The utility model discloses a method for the dynamic update of the address list of the stream control transport protocol, comprising the following steps: after a stream control transmission coupling is built, the end in which an IP address list changes is as a sender; the sender calls heart-beat detection primitive; the IP address list information needed to update is arranged in the parameter of the heart-beat detection primitive; the IP address list information comprises an updating address number, an updating mode and an IP address needed to update; the heart-beat detection information is built by the sender, and a flag field is arranged by the sender to indicate whether the receiver need to update the IP address list received from the sender; the change of the IP address is written in the information field of the heart-beat detection information by the sender, and the information field is sent to the receiver; the maintained IP address list needed to update is judged by the receiver according to the flag field of the heart-beat detection information, and the maintained IP address list is updated by the receiver according to the information field. In this way, the dynamic modification of the IP address list in both ends of the coupling is feasible without disconnecting the coupling.
Owner:ZTE CORP
Method and system for devices efficiently sharing information regarding the content of a digital television bit-stream
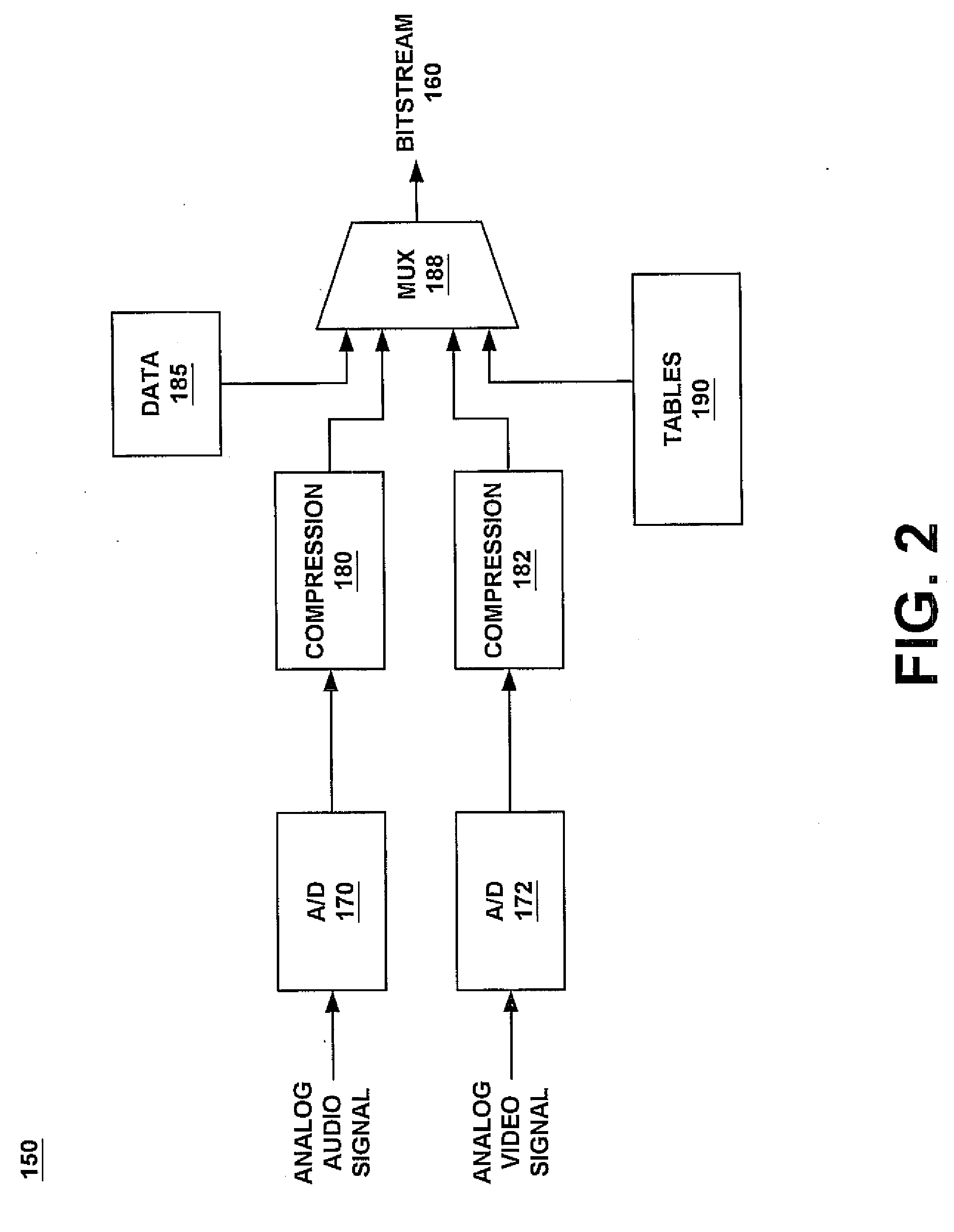
InactiveUS20080243760A1Minimum of bandwidthEfficiently receiving informationTelevision systemsSelective content distributionData informationComputer science
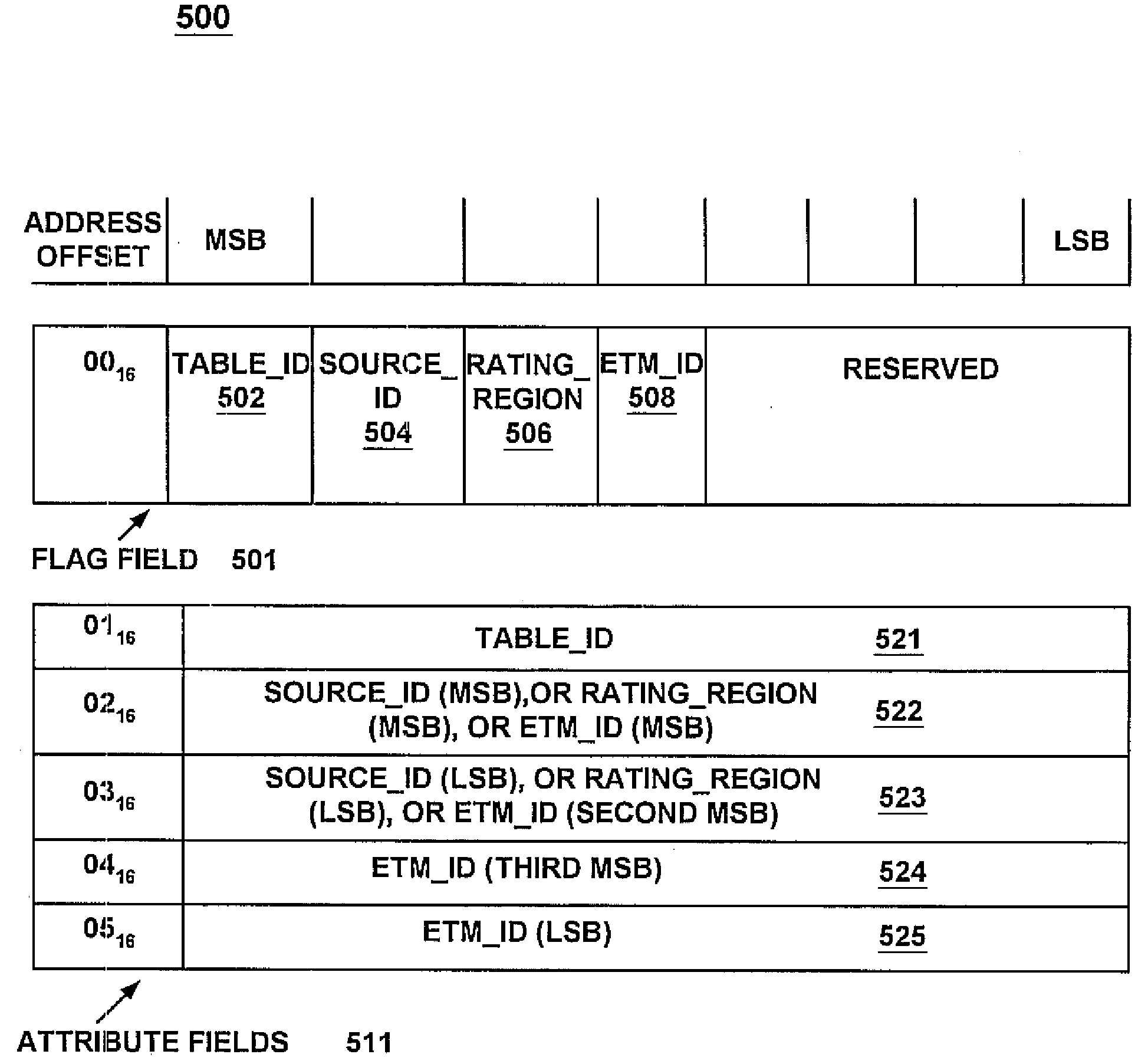
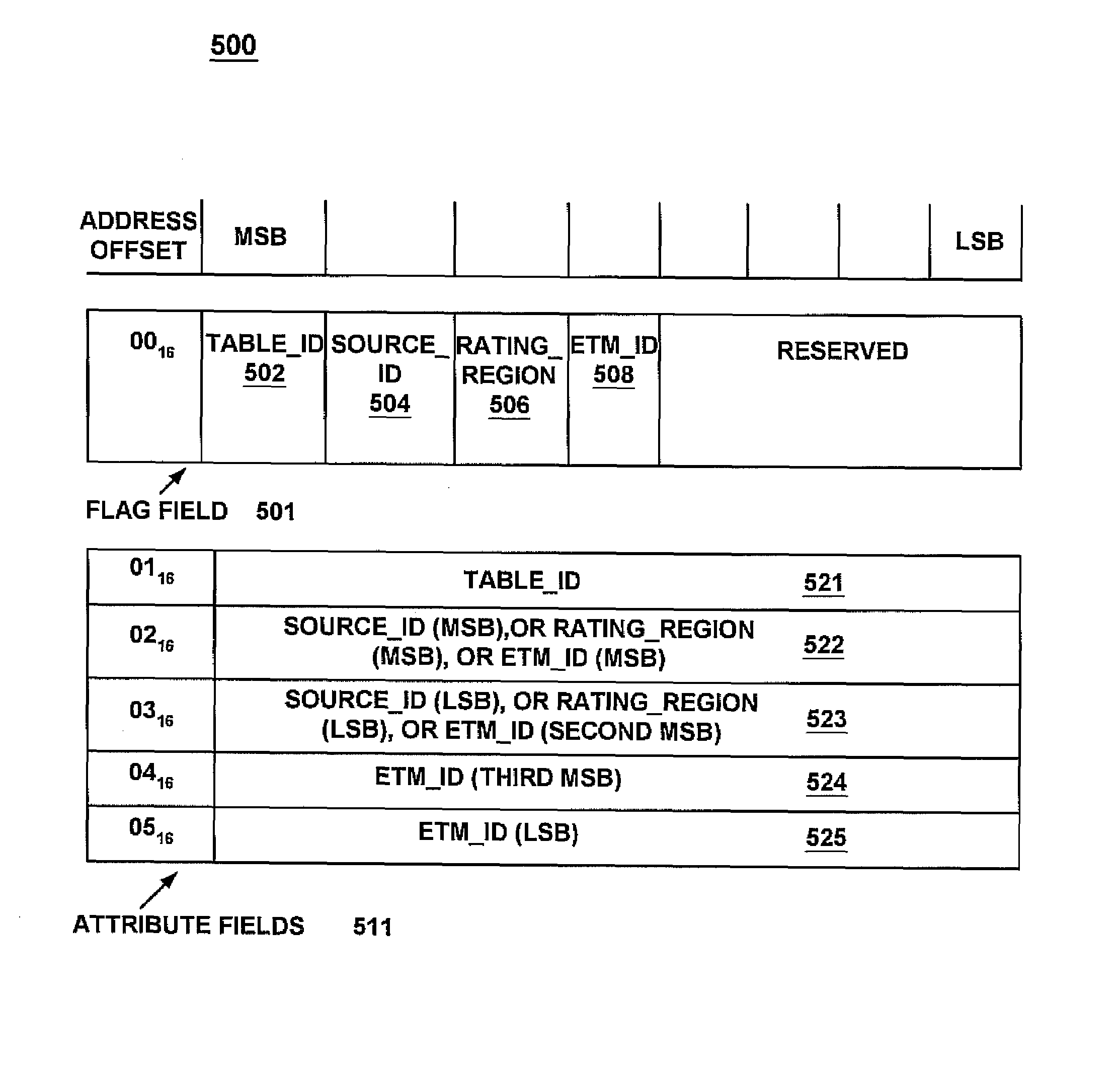
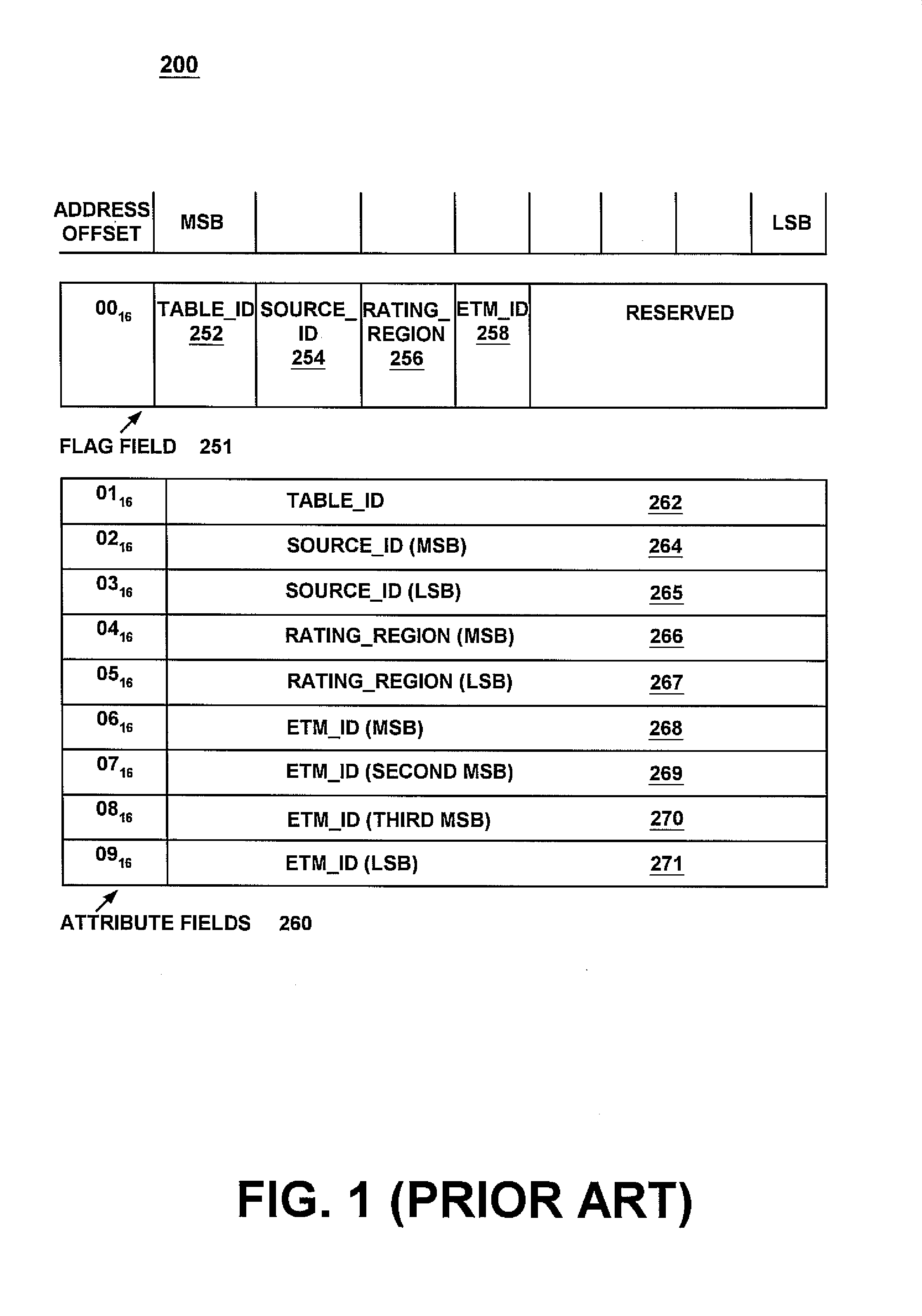
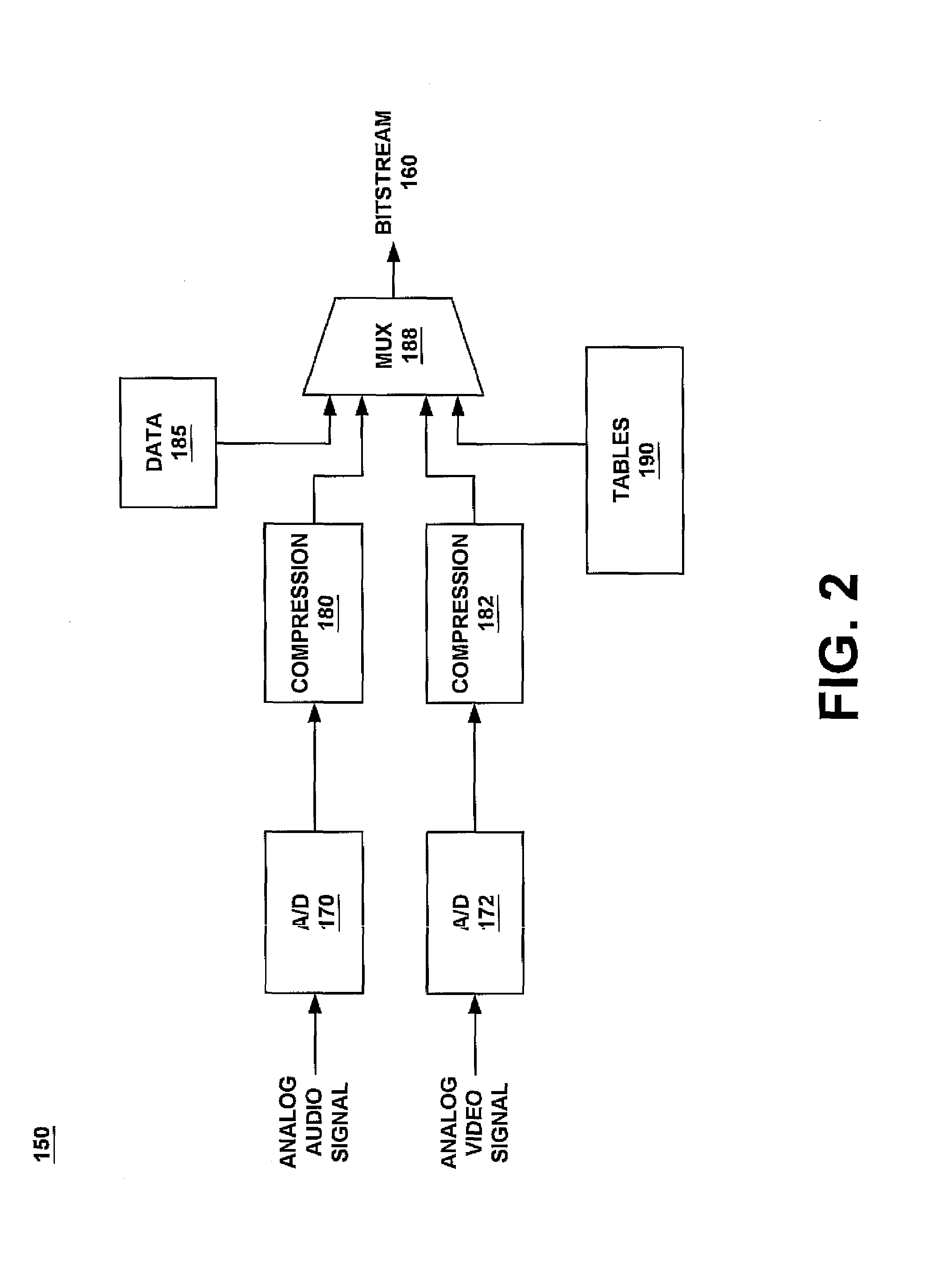
A method and system for efficiently allowing a controller device to receive information from a tuner device regarding the content of a digital television bit-stream. The present invention first receives a digital television bit-stream at a tuner device. The digital television bit-stream comprises video, audio, and data information, as well as tables that describe the content of the bit-stream. Next, to obtain a table, a controller device sets a value specifying a desired table in an attribute field of a command. Next, the controller sets at least one flag in a flag field of the command. The setting of the flag indicates the table which is being requested. Additionally, because a single attribute field may hold different types of information, the flags indicate which type of information is in the attribute field for this issuance of the command. The controller, then issues the command to the tuner, which determines what table is being requested, based upon the flags set. The tuner then returns that table to the controller.
Owner:SONY CORP +1
SRv6 Endpoint fault protection method
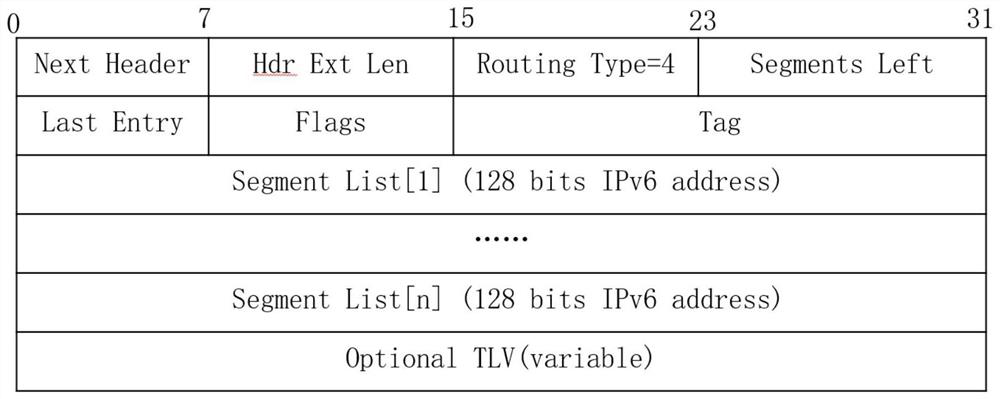
ActiveCN113364677AAvoid looking up table entries multiple timesReduce processing timeData switching networksData packPathPing
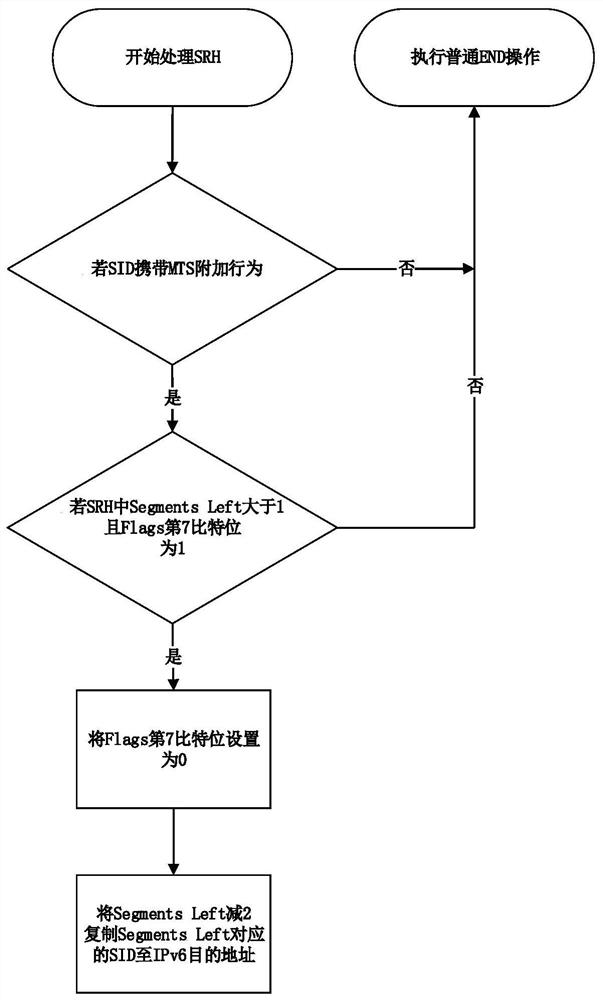
The invention belongs to the technical field of networks, and particularly relates to an SRv6 Endpoint fault protection method, which is used for solving the problems that the processing time of an upstream node, namely a proxy forwarding node, is increased and the processing efficiency of the node is reduced in the existing SRv6 Endpoint fault protection method. According to the method, the reduction of the processing time of the proxy forwarding node is considered, after the proxy forwarding node only executes a routing table searching operation once, if a table item exists, a repair path SID is packaged, a data packet is guided to a next-hop backup node, and the node executes an additional behavior of the SID, bypasses a fault Endpoint node and forwards the data packet. According to the method, a new Flags field in the SRH is designed and used for judging the SID additional behavior, a new SID additional behavior MTS is designed, and a selection mechanism of a next-hop backup node is designed, so that a fault Endpoint node can be bypassed.
Owner:BEIJING UNIV OF TECH
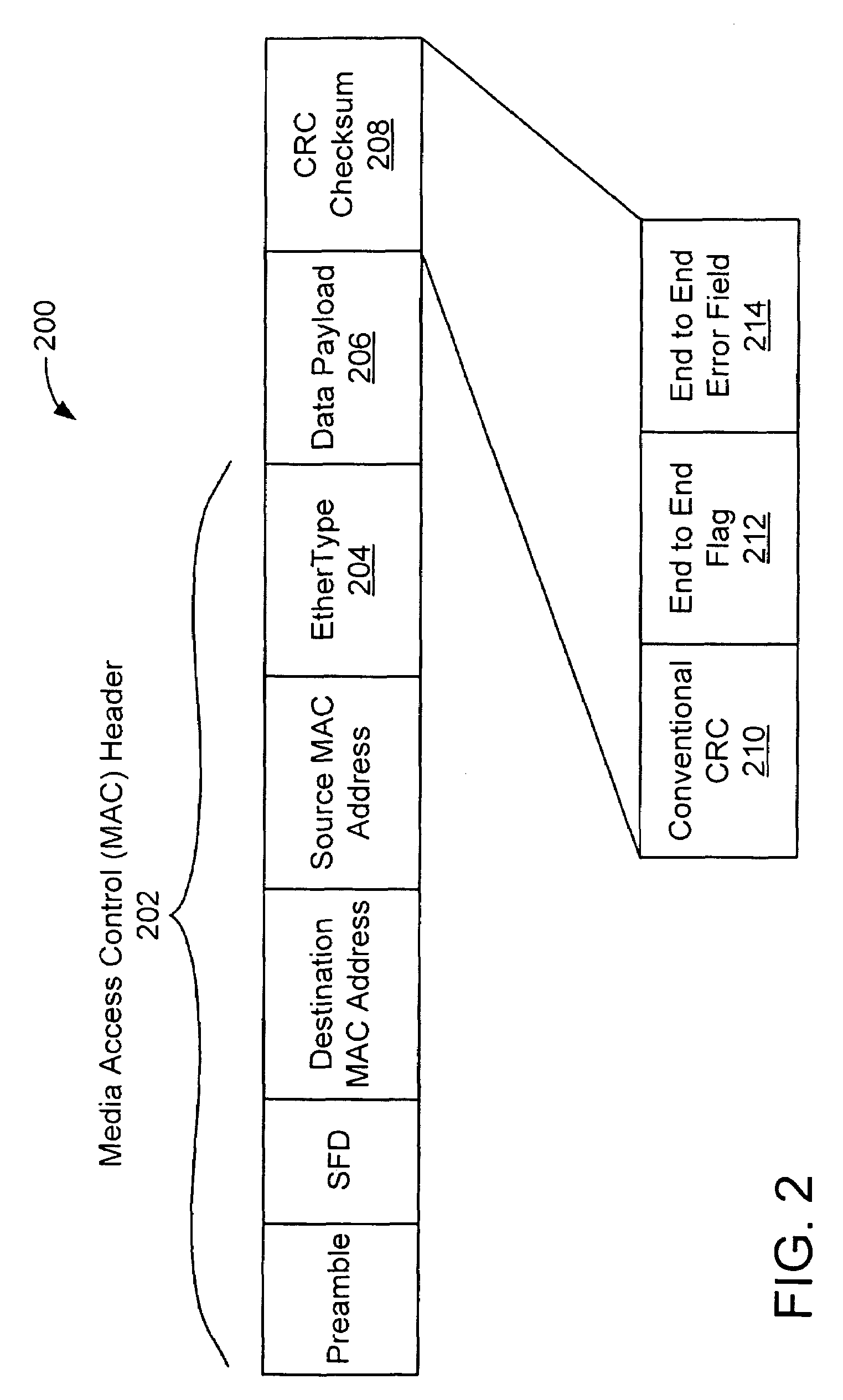
Method, system and computer program product for end to end error checking in ethernet
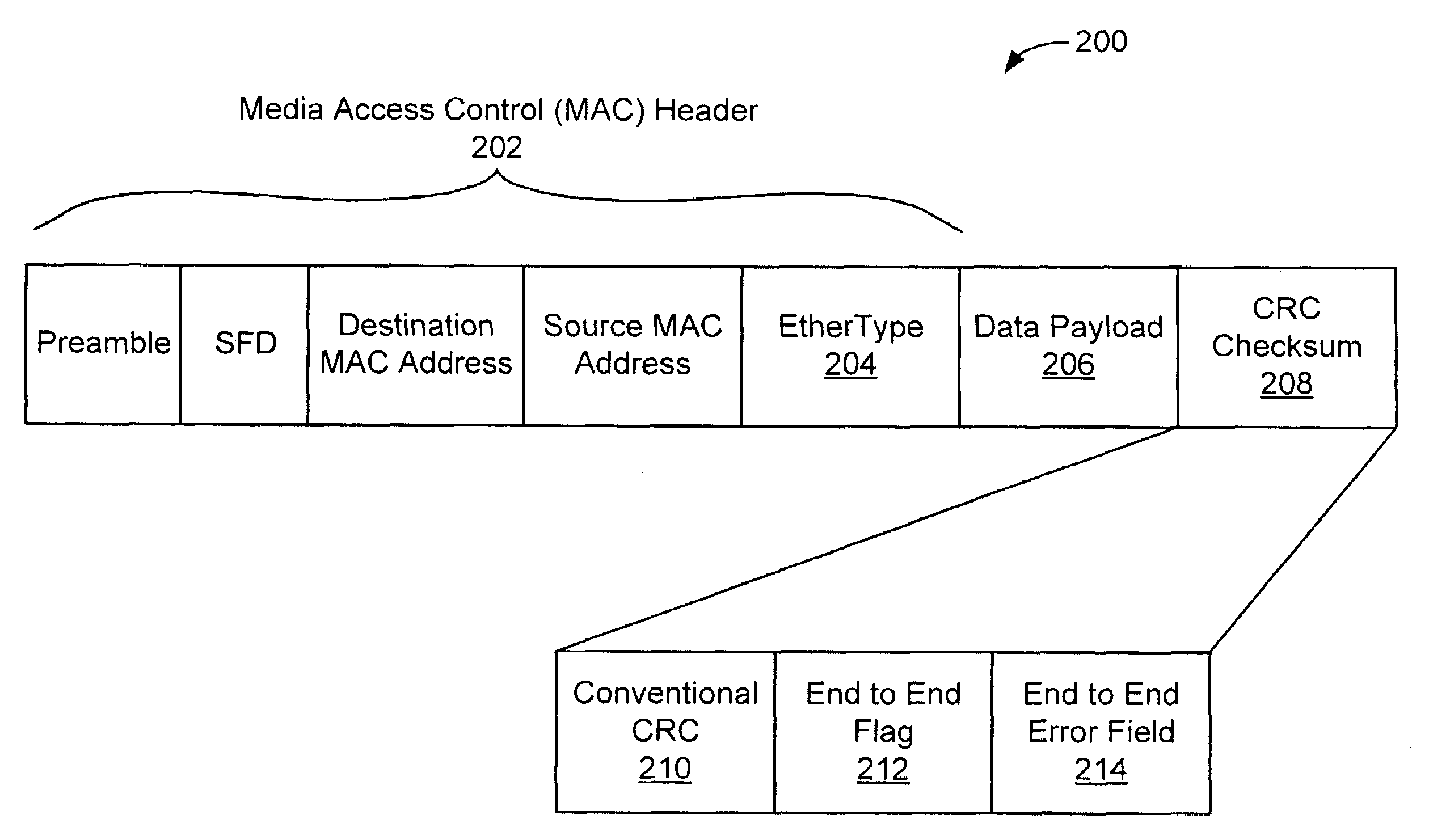
A method for network protocol error correction comprising, generating a data packet including a cycle redundancy check (CRC) field, an end to end error field that remains unchanged as the data packet is sent over a network, for use in performing error detection in one or more field of the data packet, and a flag field associated with the end to end field to indicate that the end to end error field contains error correction data, and sending the data packet over a network via an Ethernet protocol.
Owner:IBM CORP
System and method for realizing parallel upgrade of multiple terminals in same IP (Internet Protocol) local area network
ActiveCN103281295AAvoid modificationImprove processing efficiencyData switching by path configurationNetwork terminationBody area network
The invention provides a system and a method for realizing parallel upgrade of multiple terminals in the same IP (Internet Protocol) local area network. The method comprises the following steps of configuring a mapping relation table containing IP characteristics positioned at non-address flag fields in an IP message and a physical port index on a mapping equipment side at the end of a PC (Personal Computer) and transmitting the mapping relation table to the mapping equipment; meanwhile, transmitting a plurality of IP upgrade packets corresponding to different terminals to be upgraded to the mapping equipment by the PC, wherein each IP upgrade packet contains the IP characteristic mapped to the corresponding physical port on the mapping equipment side; thoroughly transmitting through each IP upgrade packet to the corresponding terminal to be upgraded through the corresponding physical port according to the mapping relation table by the mapping equipment; and upgrading the terminal to be upgraded according to the IP upgrade packet. According to the embodiment of the invention, network terminals with the same IP / MAC (Internet Protocol / Media Access Control) are distinguished and accessed by using the non-address flag fields in the IP message and no modification is carried out on the IP message, so that the processing efficiency is increased; and the part using the IP address in an application layer message does not need to be processed, so that the problem of compatibility is solved.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
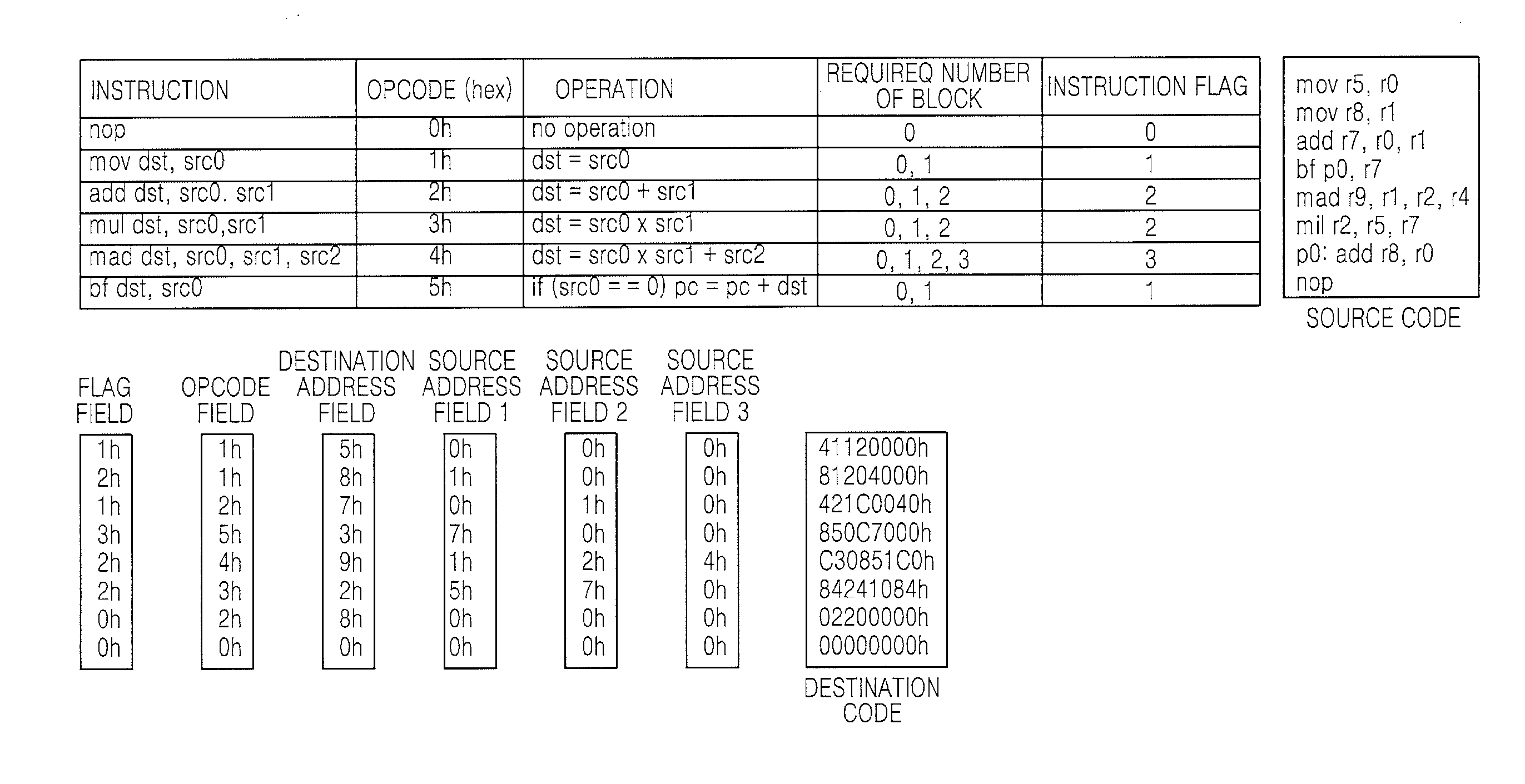
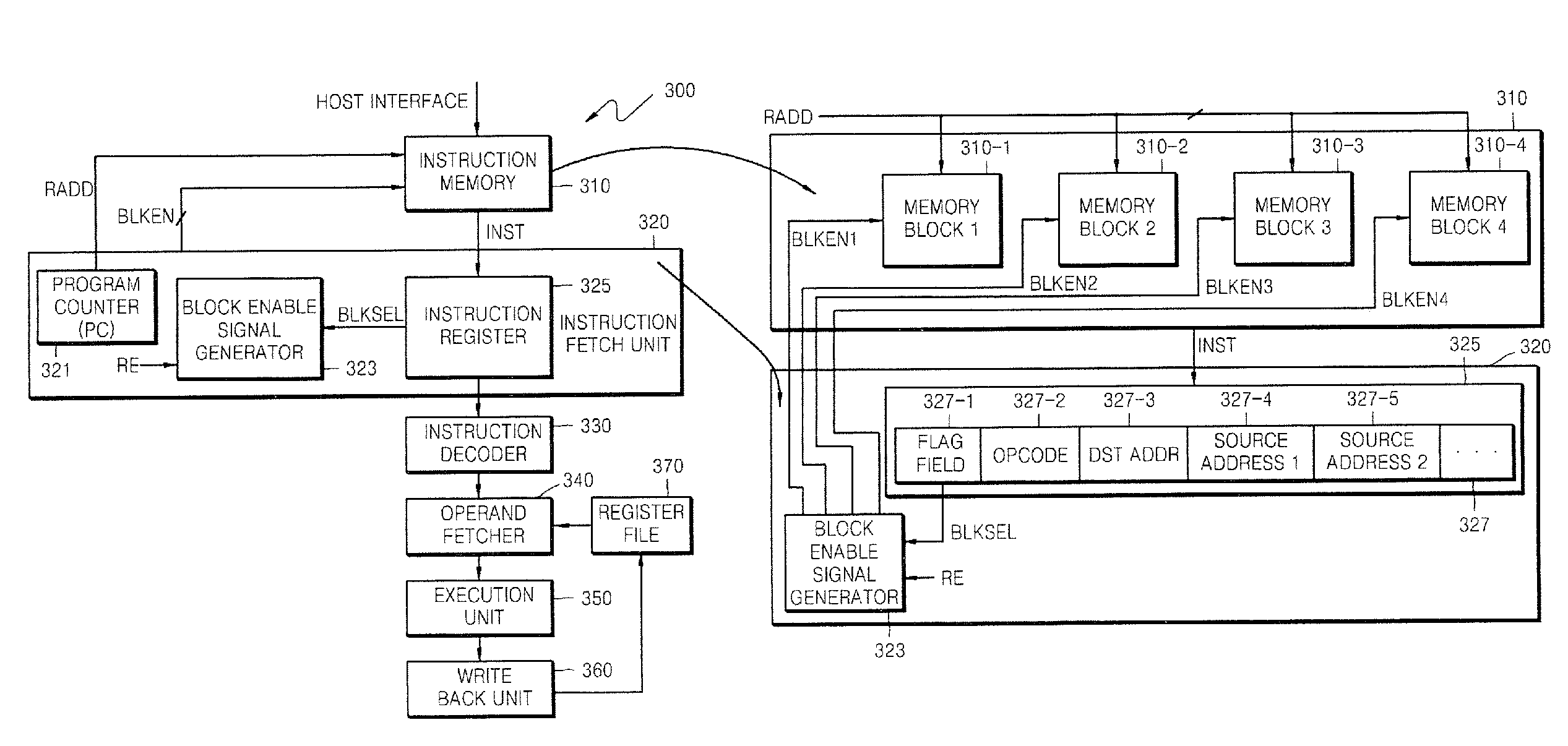
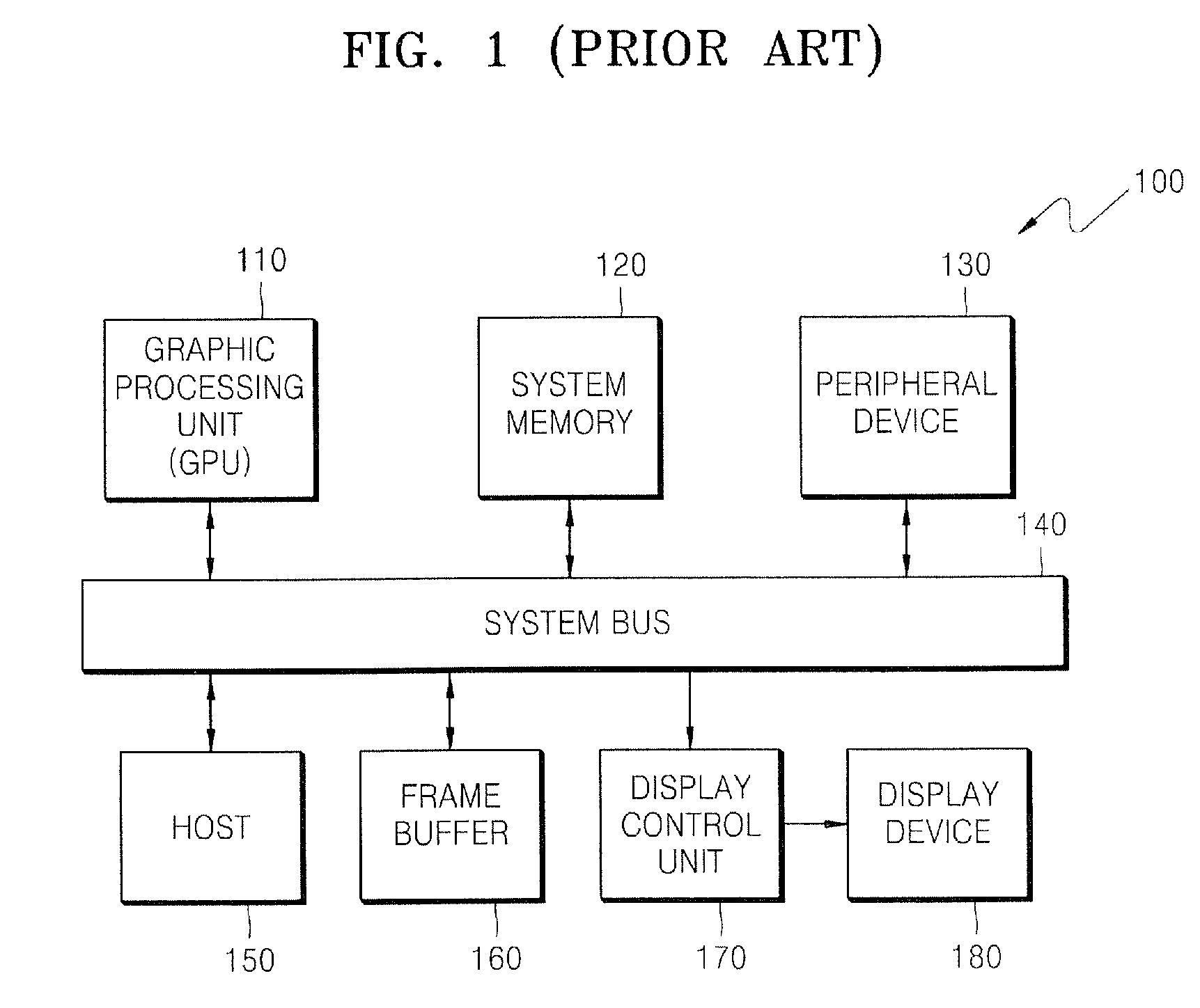
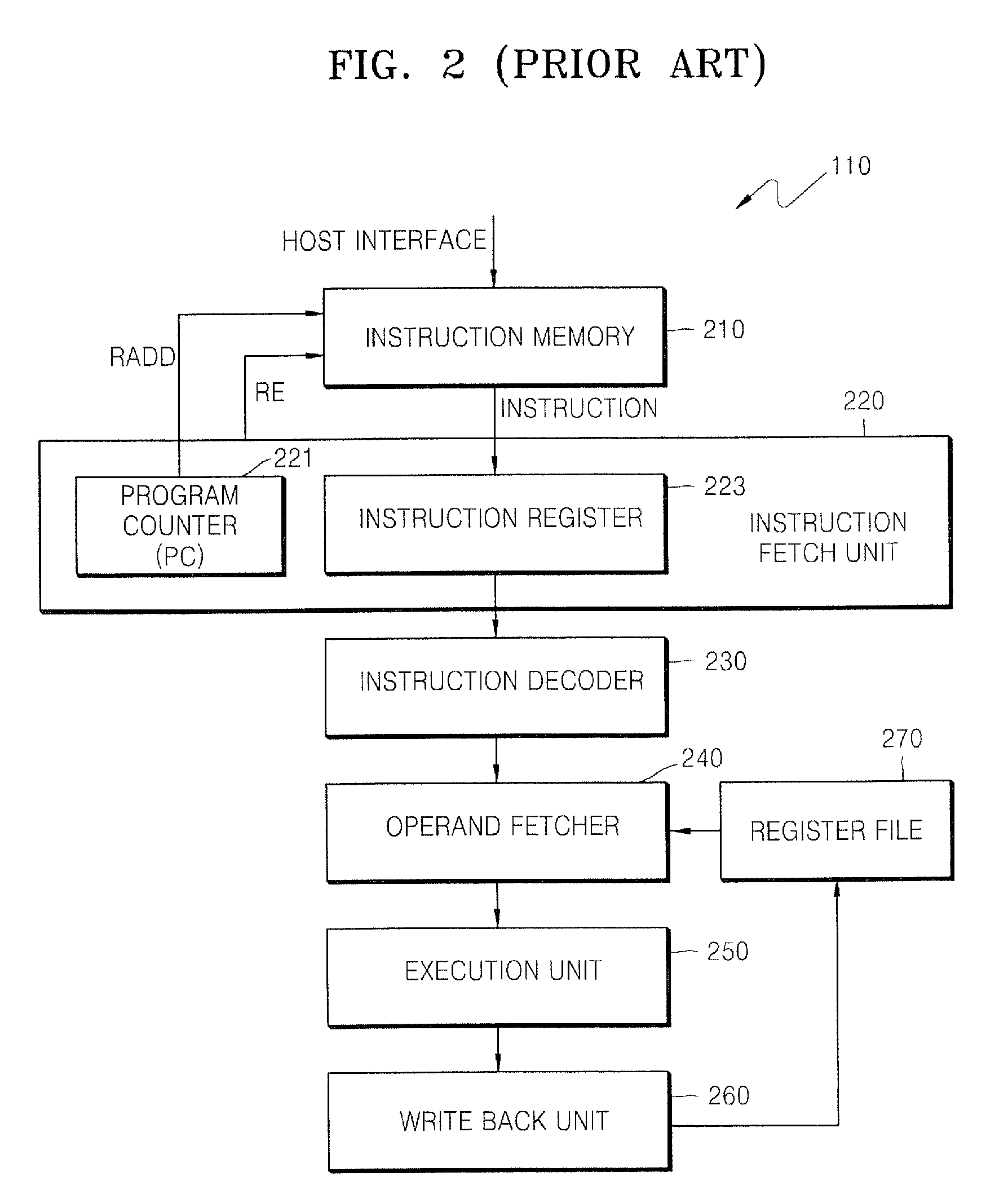
Data processing systems and methods of operating the same in which memory blocks are selectively activated in fetching program instructions
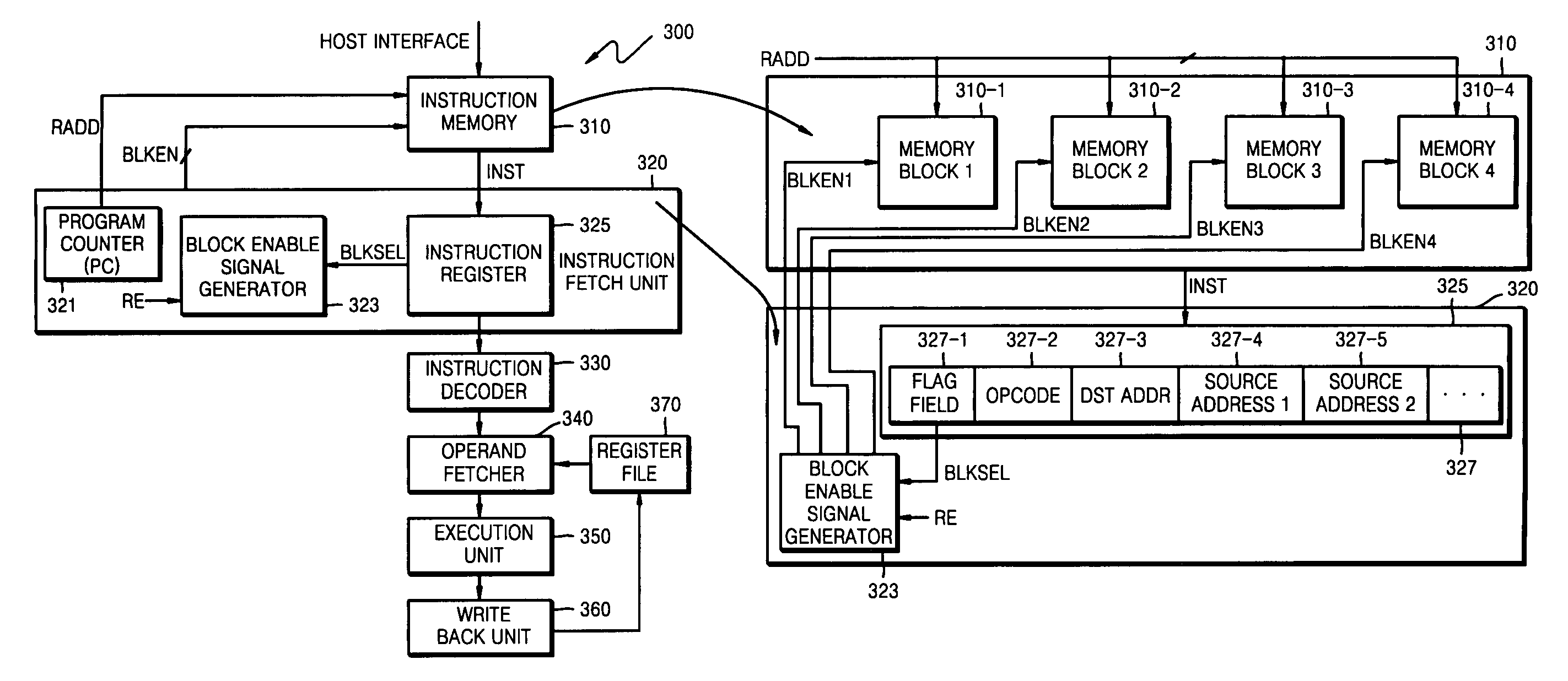
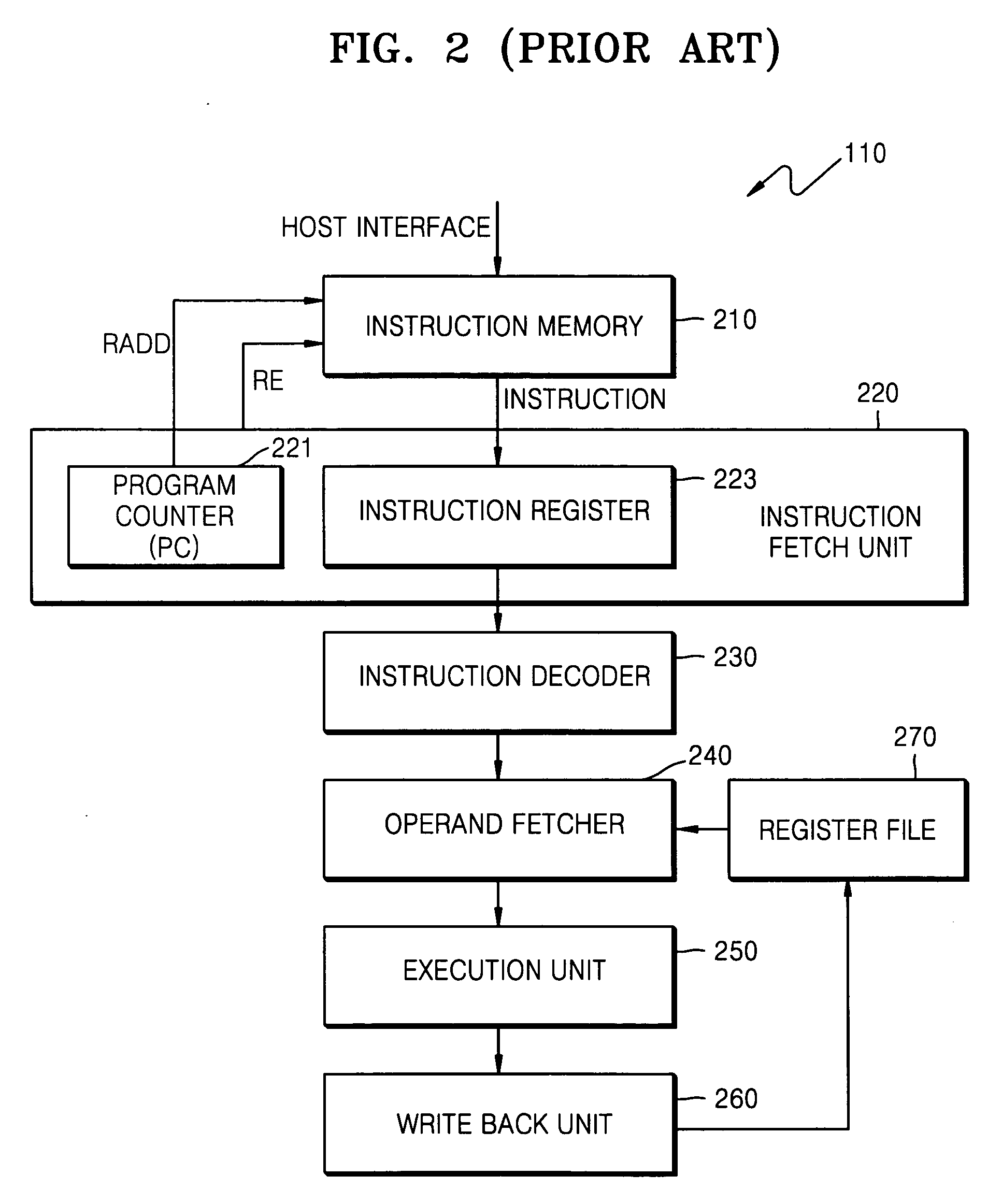
ActiveUS20100225656A1Digital data processing detailsInstruction analysisData processing systemProgram instruction
A processing unit includes an instruction fetch unit that is configured to process a compiled instruction that includes a plurality of fields. The plurality of fields includes a flag field that identifies memory blocks to be activated for fetching a next instruction. Each of the memory blocks has stored therein one or more fields used to form the next instruction and assigned to the memory blocks in a predetermined way. A block enable signal generator is configured to generate at least one block enable signal to selectively activate the memory blocks in the predetermined way. The flag field is included in fields of an instruction having the shortest length among instructions of the processing unit.
Owner:SAMSUNG ELECTRONICS CO LTD
Data processing systems and methods of operating the same in which memory blocks are selectively activated in fetching program instructions
ActiveUS8327175B2Instruction analysisPower supply for data processingData processing systemProgram instruction
A processing unit includes an instruction fetch unit that is configured to process a compiled instruction that includes a plurality of fields. The plurality of fields includes a flag field that identifies memory blocks to be activated for fetching a next instruction. Each of the memory blocks has stored therein one or more fields used to form the next instruction and assigned to the memory blocks in a predetermined way. A block enable signal generator is configured to generate at least one block enable signal to selectively activate the memory blocks in the predetermined way. The flag field is included in fields of an instruction having the shortest length among instructions of the processing unit.
Owner:SAMSUNG ELECTRONICS CO LTD
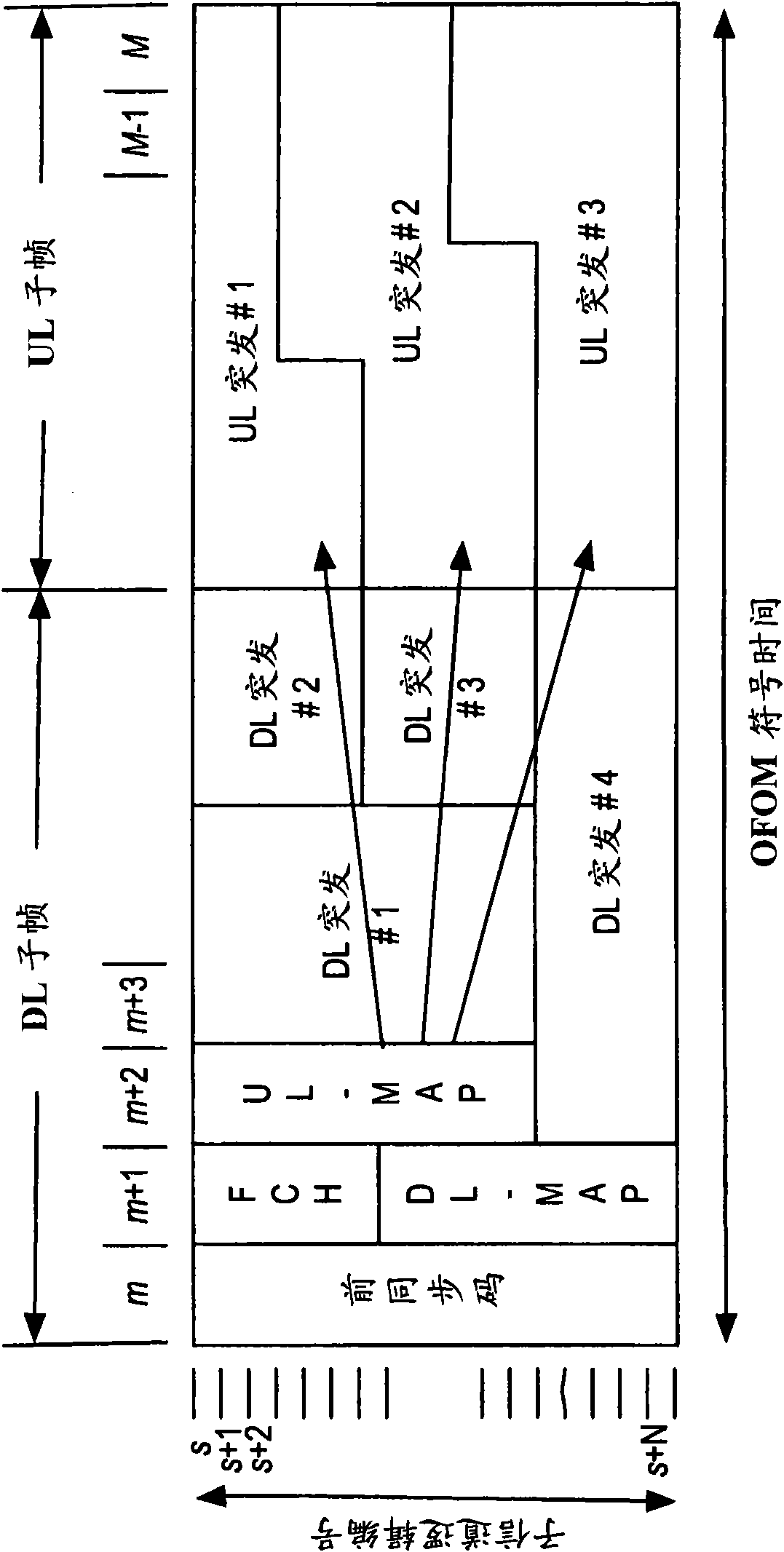
Aggregation of resources over multiple frames in a TDD communication system
InactiveCN102017758AIncreased cell sizeMaintain DL RatioTransmission path divisionWireless communicationCommunications systemMultiple frame
According to embodiments of the present invention, multiple frames or sub- frames on an uplink channel may be aggregated into one logical unit for demodulation and decoding to allow one data packet to span over multiple frames. Multi-frame aggregation is enabled by modifying the uplink resource allocation messages transmitted to the user terminals. The multi-frame resource allocation message includes a BEGIN FLAG field indicating whether a corresponding frame is the first frame in a multi-frame allocation and a REMAINING RESOURCES field to indicate the number of units (e.g., slots or frames) remaining in the multi-frame allocation.
Owner:TELEFON AB LM ERICSSON (PUBL)
Pre-charging data access control device and method thereof
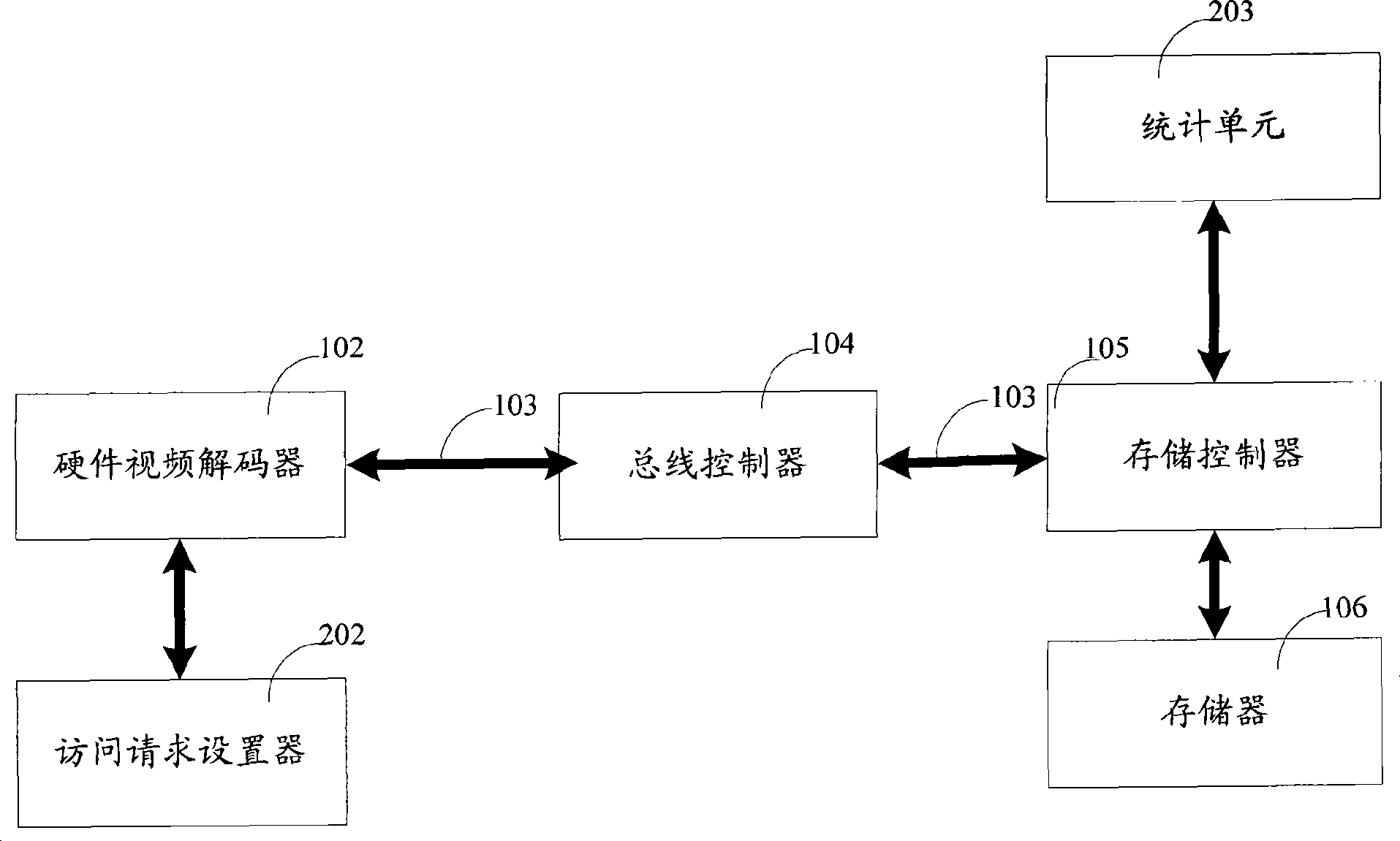
ActiveCN101488117ADoes not affect the efficiency of read requestsReduce access latencyElectric digital data processingData access controlControl store
The invention provides a pre-charging data access control device and a method thereof. The control device comprises: an access initiating unit which is used for generating an access request that reads data from or write data into a memory and at least comprises a self-Master ID field and a read-write access marker field; a bus which is used for transmitting the access request and corresponding data; a storing controller which is used for judging the read-write access marker field when the value of the Master ID field in the access request accords with a prearranged value, and if the access request is a reading request, the pre-charging is not carried out, and if the access request is a writing request, the pre-charging is carried out when the writing request is finished; and a memory which is used for storing data corresponding to the access request. The embodiment of the invention has the beneficial effects that with the improvement scheme adopted, the access delay of write access is effectively lowered without influencing the efficiency of the read request and the working efficiency of the whole system is improved.
Owner:南通市崇川科技园投资发展有限公司
Write buffer for use in a data processing apparatus
InactiveUS20020038410A1Easy to useReduce areaMemory adressing/allocation/relocationData conversionTraffic capacityWrite buffer
The present invention provides a data processing apparatus comprising a processor core for generating addresses identifying locations in a memory and data values for storing in the memory, and a write buffer for storing the addresses and data values output by the processor core, and for subsequently outputting said addresses and data values to cause the data values to be stored in said memory. The write buffer comprises a plurality of rows, each row being arranged to store an address or data value, and each row having associated therewith a flag field settable to indicate whether that row contains an address or a data value. In accordance with the present invention, the write buffer provided by the data processing apparatus adaptively adjusts the number of rows it requires for addresses, and hence can be arranged to occupy a relatively small area, whilst still efficiently supporting both burst mode and non-burst mode write traffic.
Owner:ARM LTD
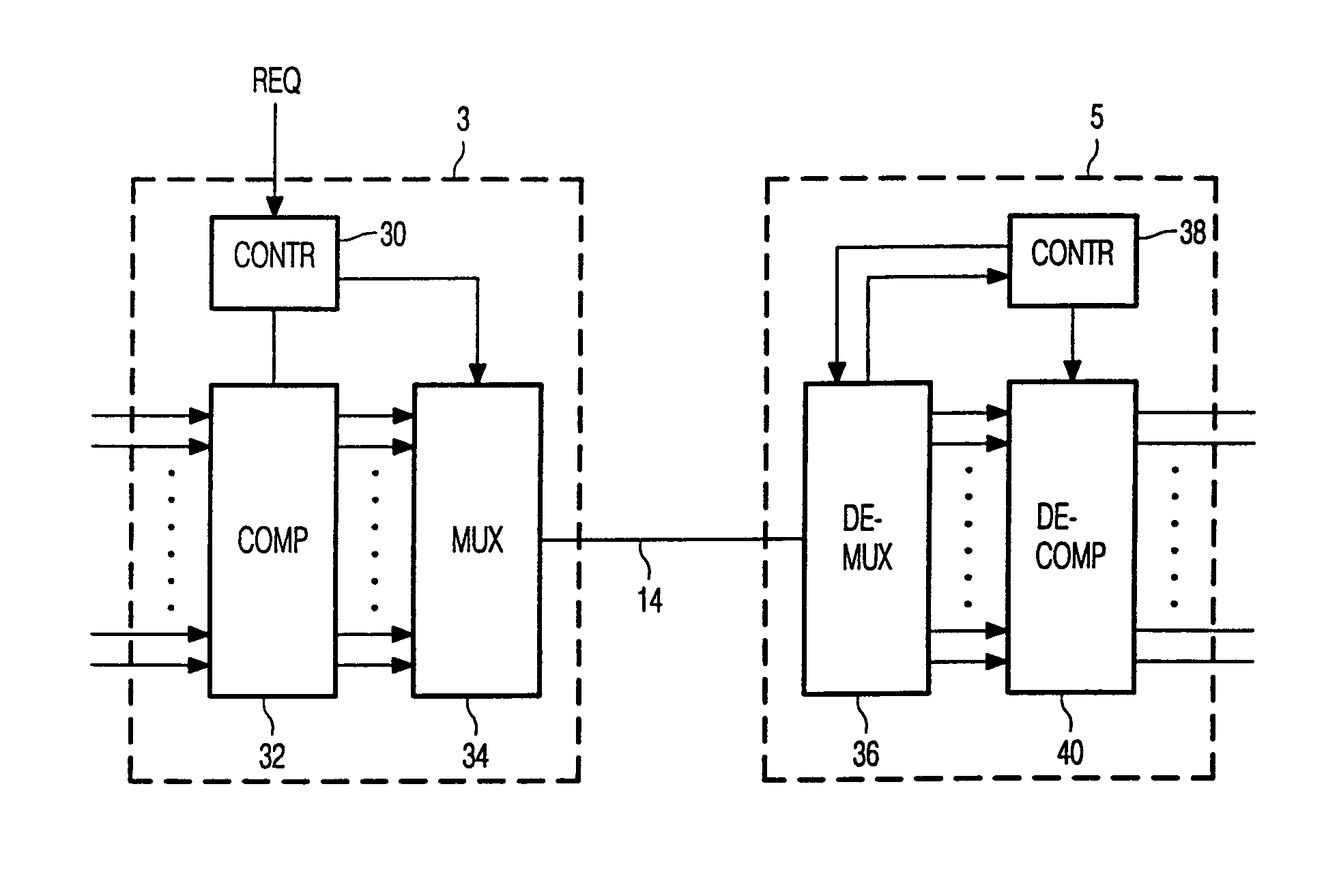
Communication system using a multiplex signal carrying an auxiliary signal
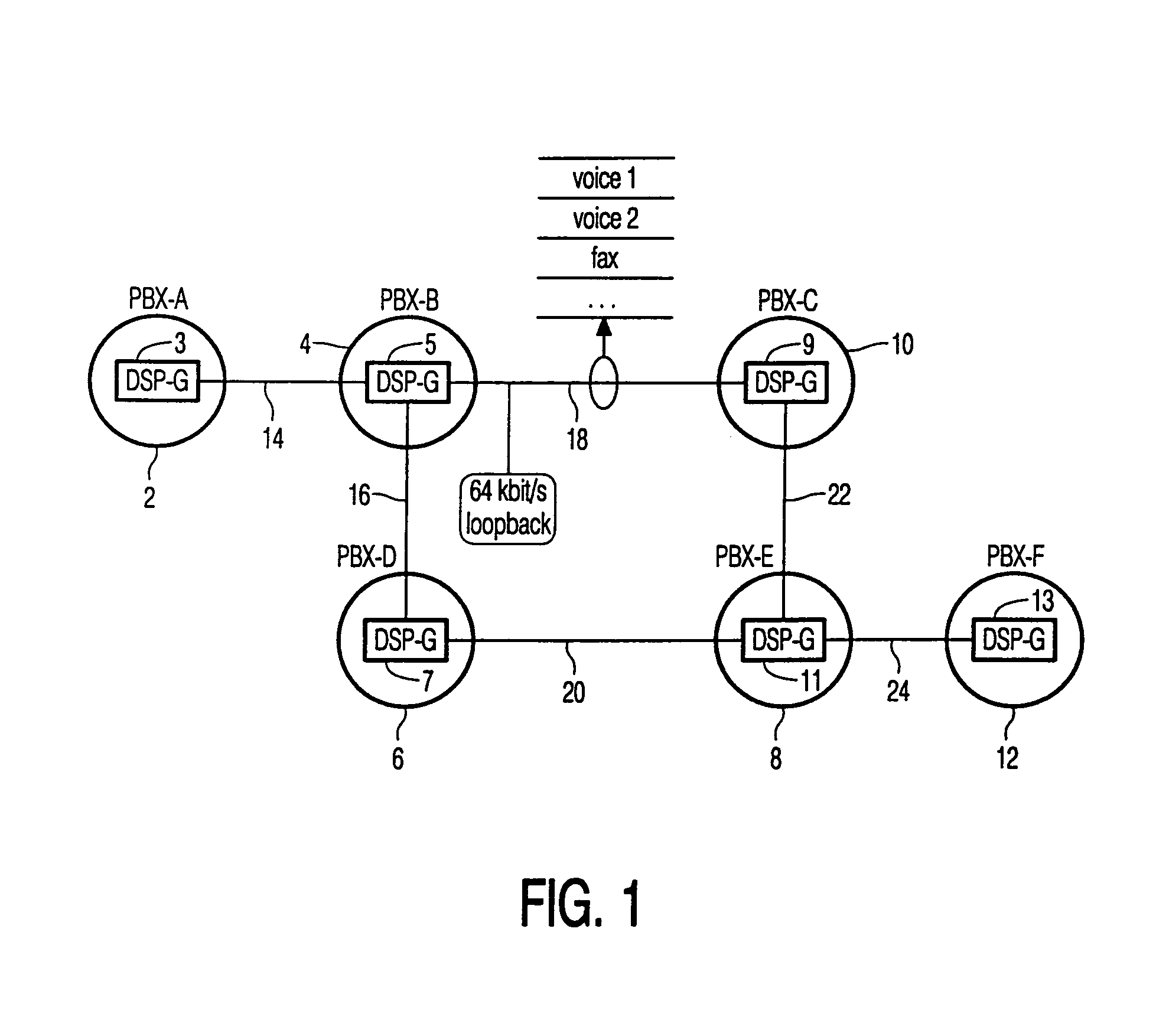
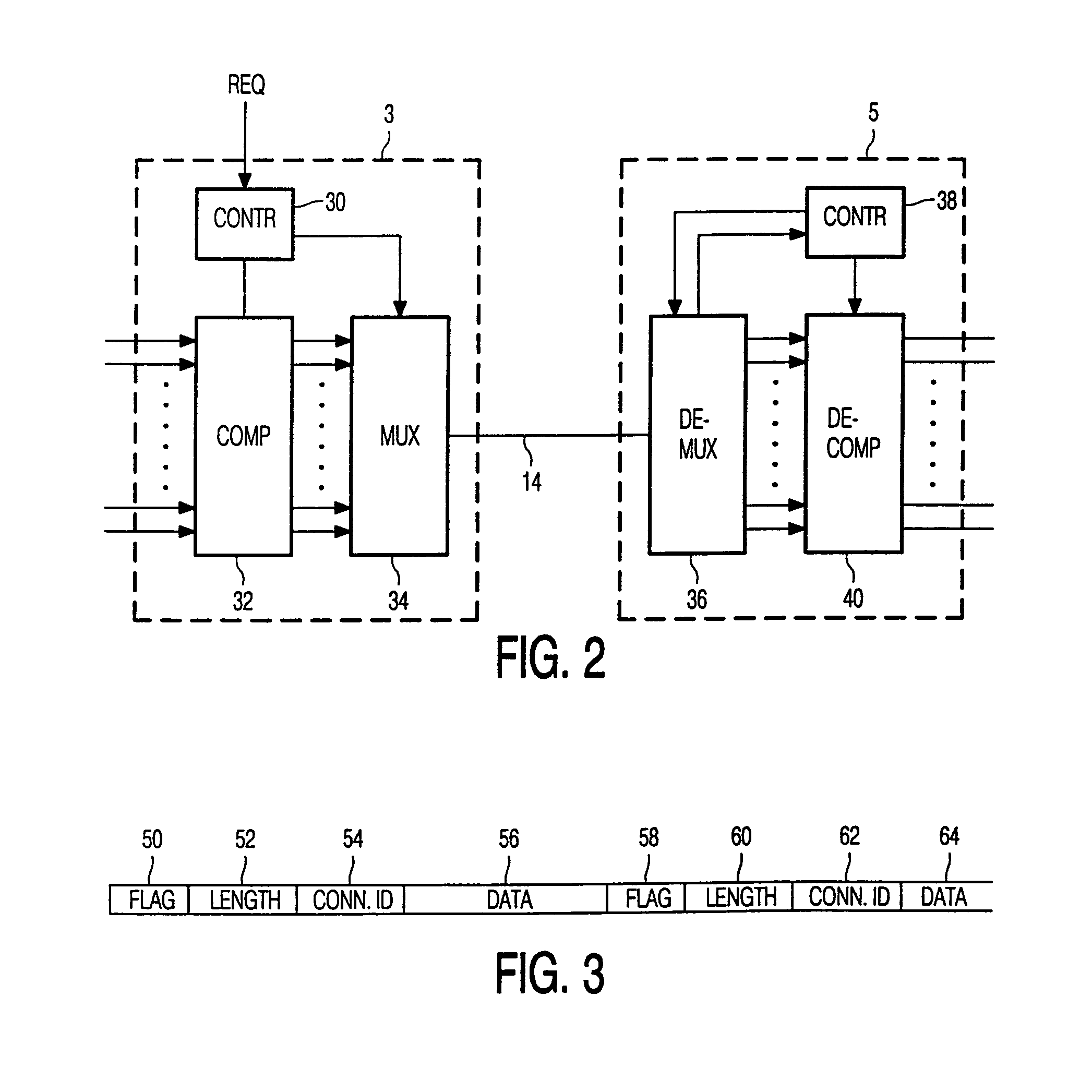
InactiveUS7082144B1Increase the number ofIncrease spaceTime-division multiplexTime-division multiplexing selectionCommunications systemControl signal
In a transmitting node (3) in a transmission system, a plurality of source signals are multiplexed by a multiplexer (34) into a multiplex signal. The multiplex signal is transmitted to a receiving node (5) where it is demultiplexed in the source signals. The multiplex signal comprises a plurality of packets having a flag field, a length field, a connection ID field and a data field. The flag field can be present to enable the receiver to find the beginning of the packet or to carry non-urgent control signals. According to the present invention, the length of the flag field is dependent on the aggregate bitrate of the source signals, making it possible that more source signals can be transmitted over the transmission link under heavy traffic conditions.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Data processing systems and methods of operating the same in which memory blocks are selectively activated in fetching program instructions
InactiveUS20070011439A1Instruction analysisDigital computer detailsData processing systemProgram instruction
A processing unit includes an instruction fetch unit that is configured to process an instruction that includes a plurality of fields. The plurality of fields includes a flag field that identifies at least one of a plurality of memory blocks to be activated for fetching a next instruction.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for devices efficiently sharing information regarding the content of a digital television bit-stream
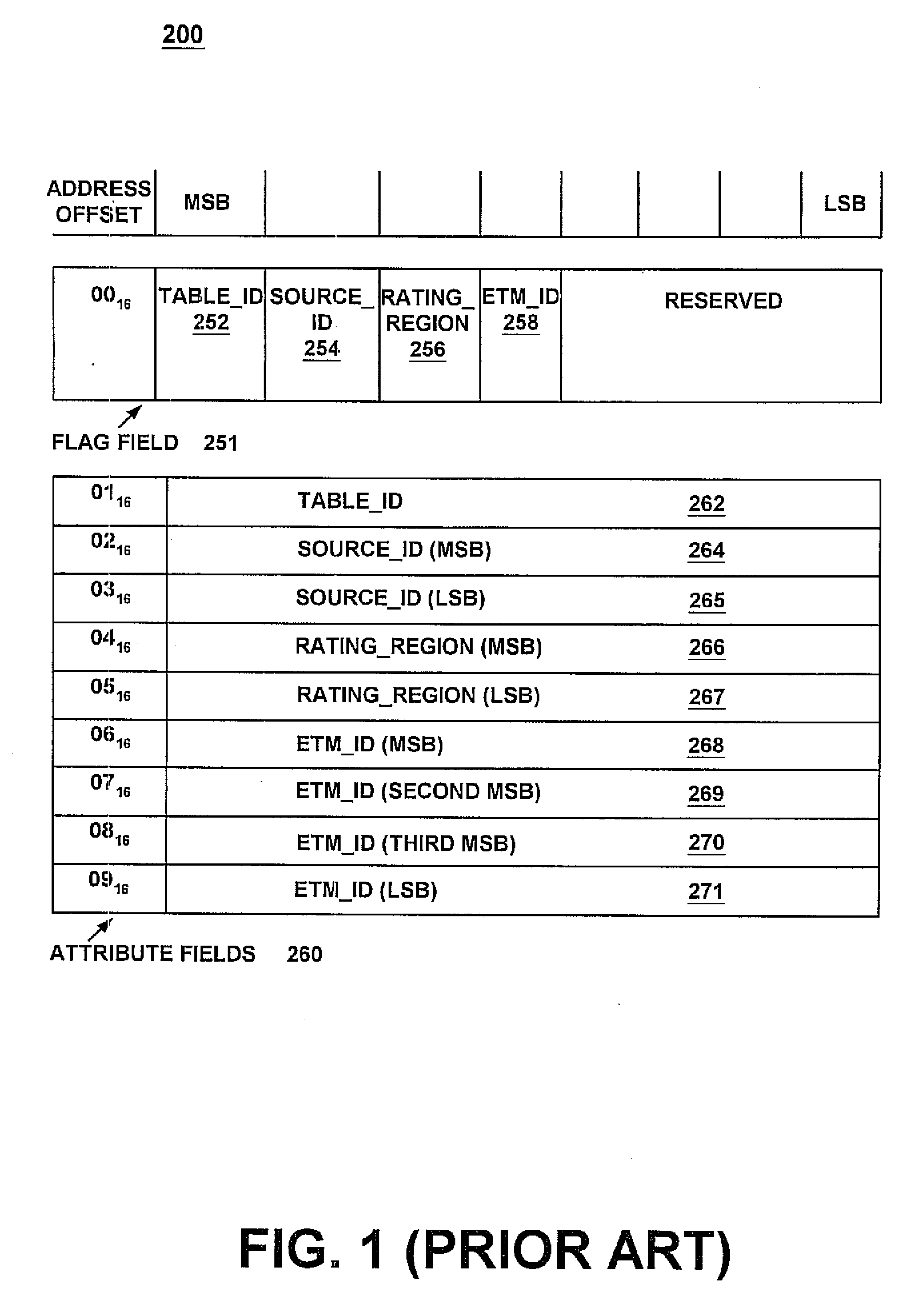
InactiveUS7406706B1Minimum of bandwidthEfficiently receiving informationAnalogue secracy/subscription systemsTwo-way working systemsData informationComputer science
A method and system for efficiently allowing a controller device to receive information from a tuner device regarding the content of a digital television bit-stream. The present invention first receives a digital television bit-stream at a tuner device. The digital television bit-stream comprises video, audio, and data information, as well as tables that describe the content of the bit-stream. Next, to obtain a table, a controller device sets a value specifying a desired table in an attribute field of a command. Next, the controller sets at least one flag in a flag field of the command. The setting of the flag indicates the table which is being requested. Additionally, because a single attribute field may hold different types of information, the flags indicate which type of information is in the attribute field for this issuance of the command. The controller, then issues the command to the tuner, which determines what table is being requested, based upon the flags set. The tuner then returns that table to the controller.
Owner:SONY CORP +1
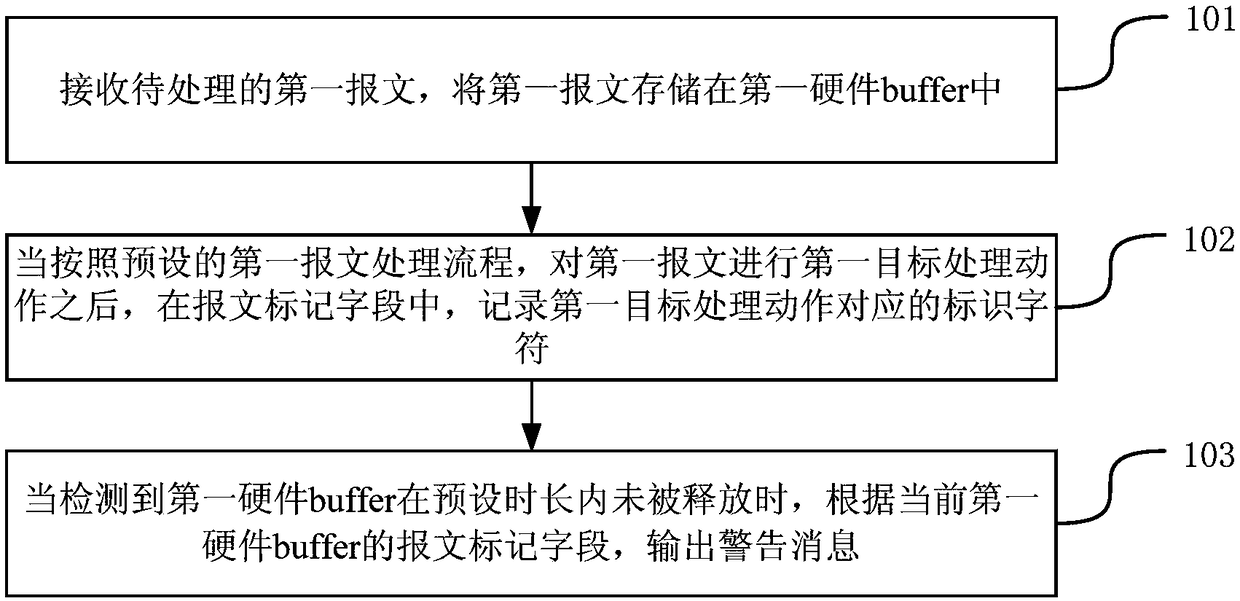
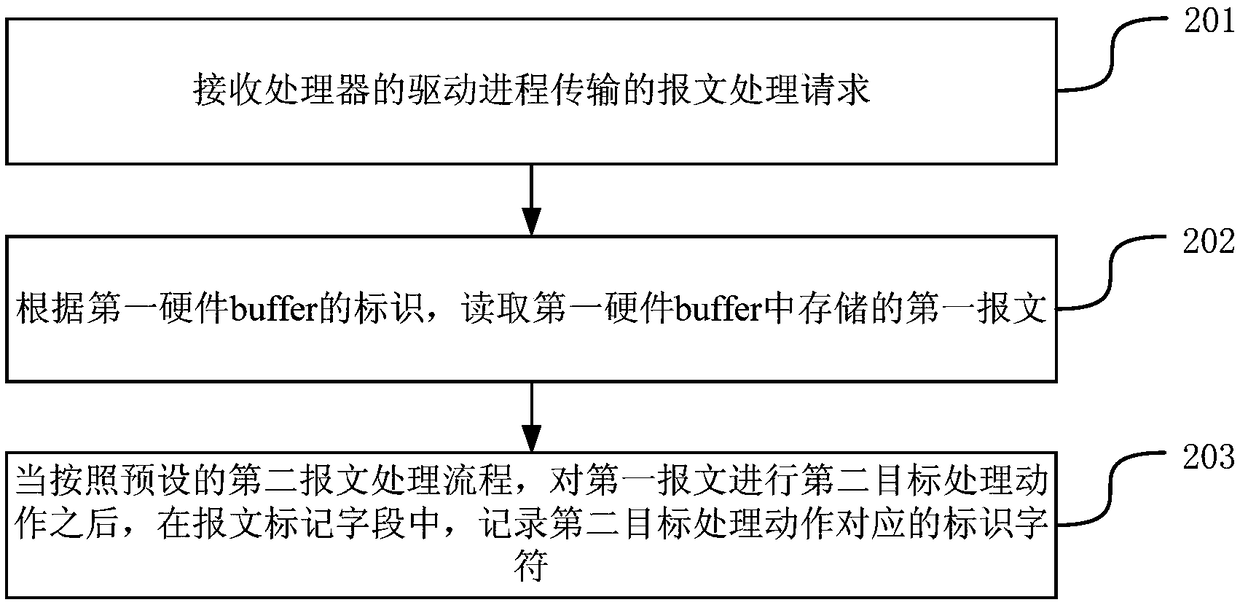
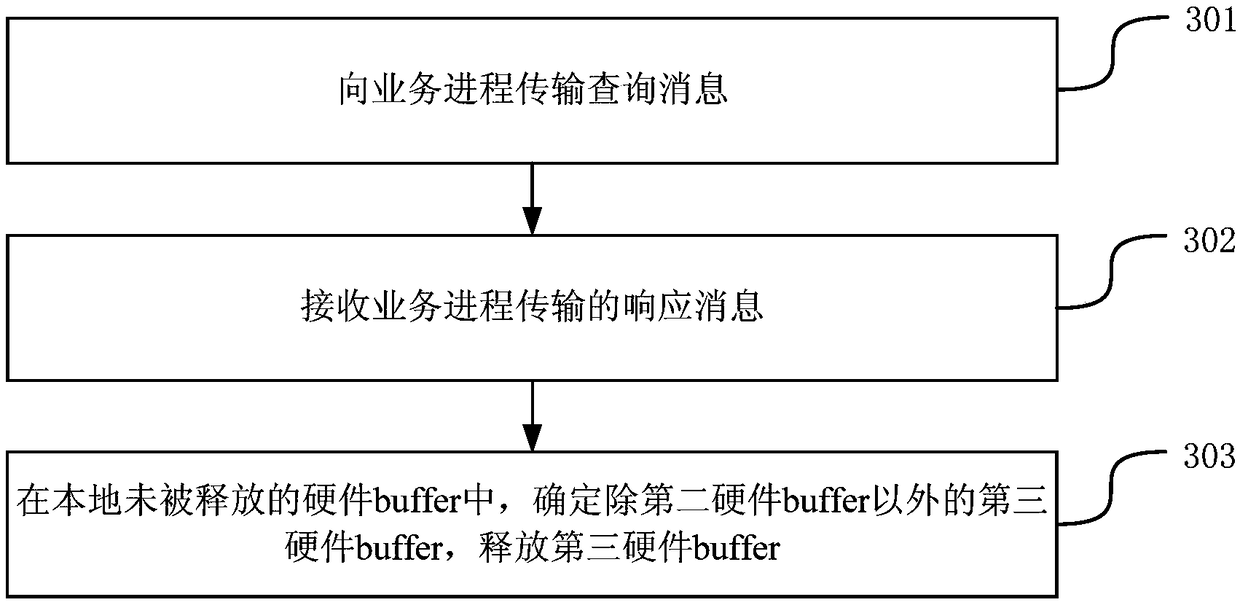
A method and apparatus for outputting a warning message
Embodiments of the present application provide a method and apparatus for outputting warning messages, belonging to the field of computer technology. The method is applied to a processor. The processor comprises a plurality of hardware buffer buffers. A message mark field is arranged in the hardware buffer. The method comprises the following steps: receiving a first message to be processed and storing the first message in the first hardware buffer; after the first target processing action is performed on the first message according to a preset first message processing flow, an identification character corresponding to the first target processing action being recorded in the message mark field; when detecting that the first hardware buffer is not released within a preset time period, a warning message being outputted according to the current message flag field of the first hardware buffer. With the present application, it is possible to locate the cause of the delay in releasing the hardware buffer.
Owner:NEW H3C SECURITY TECH CO LTD
Efficient access to variable-length data on a sequential access storage medium
InactiveCN1571061ADigital data information retrievalCarrier indexing/addressing/timing/synchronisingData segmentIterative search
A system, a method and a program product provide access to variable-length data segments on a sequential access storage medium using an iterative search for a specified data offset based on estimates of media offsets. The data is recorded in variable-length data segments aligned to predetermined alignment intervals. Each data segment has a predetermined signature field to identify the header of each data segment. Session data recorded on the medium so as to prevent session data that matches the signature field from being aligned with the predetermined alignment interval. Approximate or default parameters for data segment size are used for each estimate and are updated with each iteration based on actual data derived from data segment headers on the medium.
Owner:MICROSOFT TECH LICENSING LLC
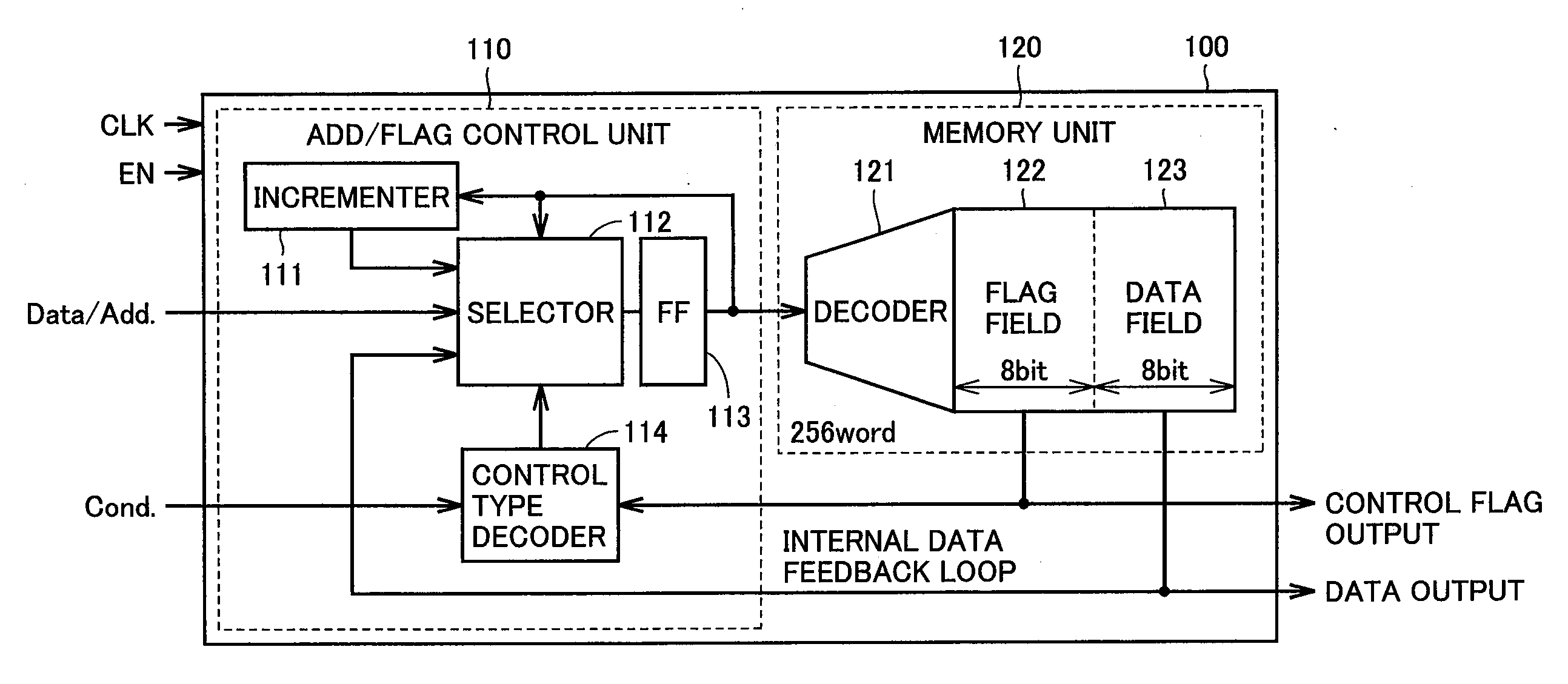
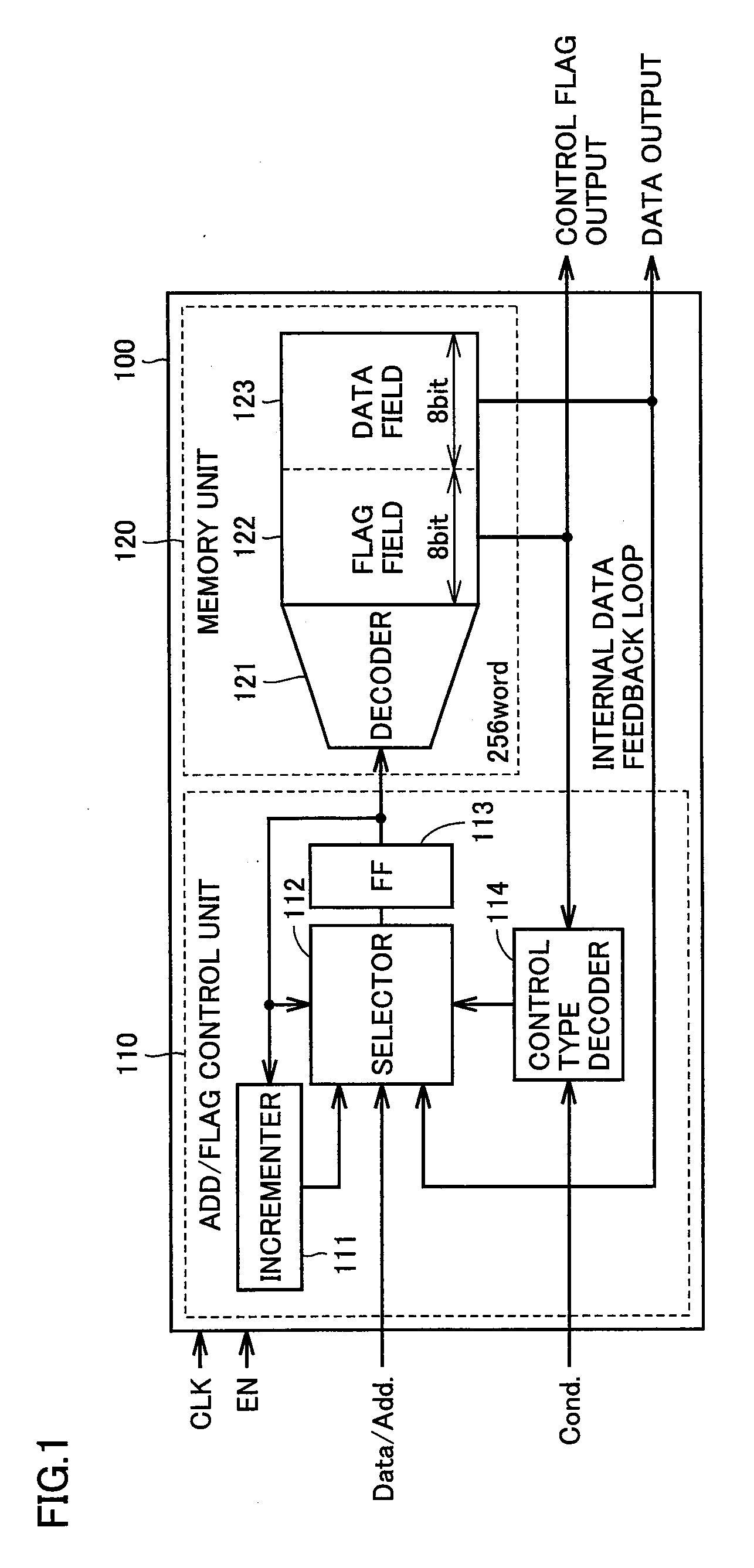
Semiconductor device
InactiveUS20110006806A1Increase flexibilitySolid-state devicesLogic circuits using elementary logic circuit componentsAutomatic controlGranularity
An ePLX unit includes a logic unit having an SRAM and a MUX, and a switch unit having an SRAM and a TG for establishing wiring connection in the logic unit. When a composite module is set in the first mode, an Add / Flag control unit uses the SRAMs as a data field and a flag field, respectively, to autonomously control the read address of each of the data field and the flag field in accordance with a control flag stored in the flag field. Furthermore, when the composite module is set in the second mode, the Add / Flag control unit writes configuration information into each of the SRAMs to reconfigure a logic circuit. Consequently, the granularity of the circuit configuration can be rendered variable, which allows improvement in flexibility when configuring a function.
Owner:RENESAS ELECTRONICS CORP
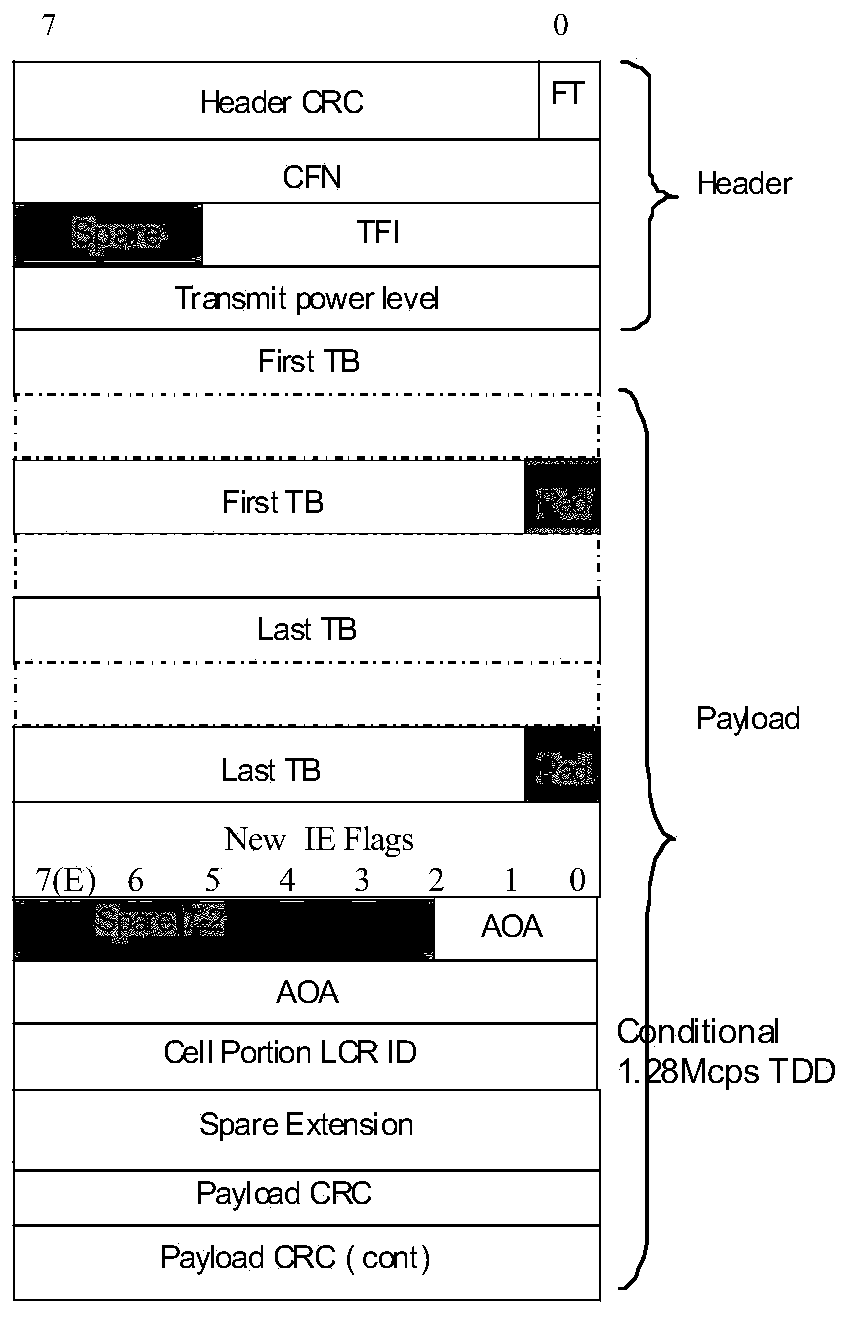
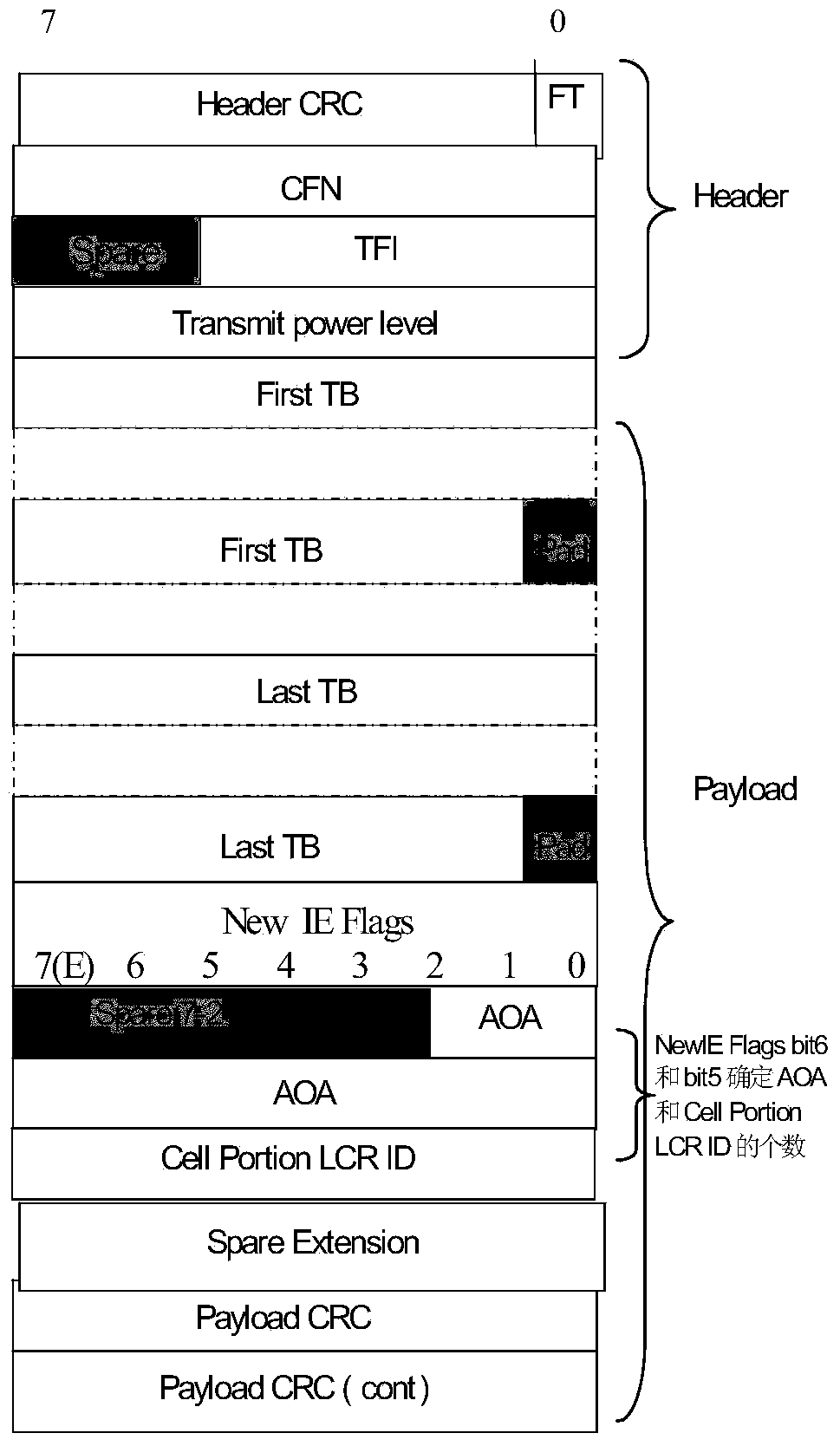
Method and device achieving multi-user shaping based on FP frame extension field
The invention relates to a method achieving multi-user shaping based on an FP frame extension field. The method achieving the multi-user shaping based on the FP frame extension field comprises the steps that a New IE Flags field is extended, and the number of users is identified by part of bits of the field; according to the number, identified by the field, of the users, user azimuth angles or Cell Portion LCR ID with the number corresponding to the number of the users behind a New IE Flags field is loaded; based on the azimuth angles or the Cell Portion LCR ID, the data of multiple users are loaded through a transmission block. According to the method achieving the multi-user shaping based on the FP frame extension field, multi-user shaping in one TTI is achieved, FACH channel utilization rate is improved, and network capacity is enlarged.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com