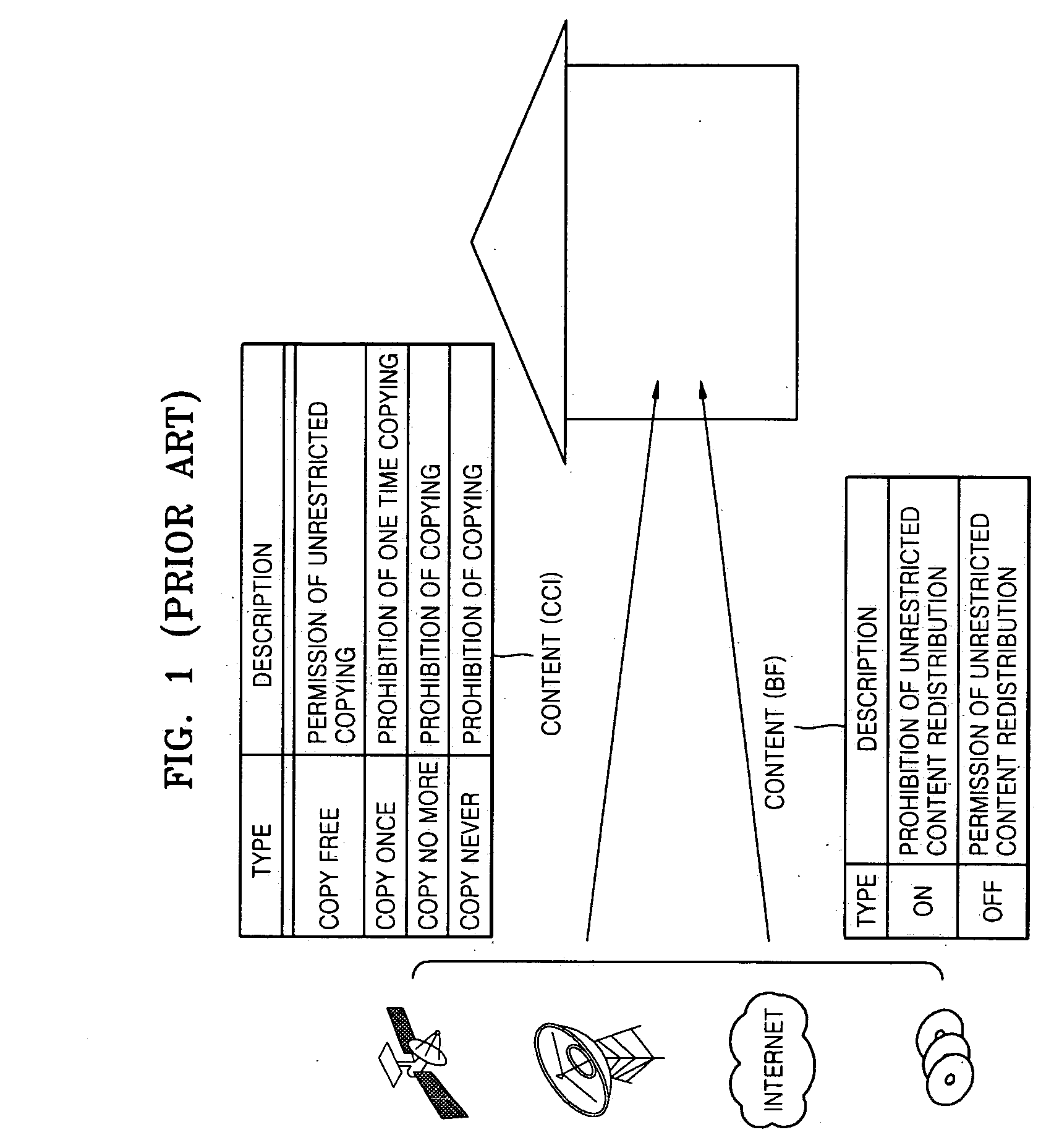
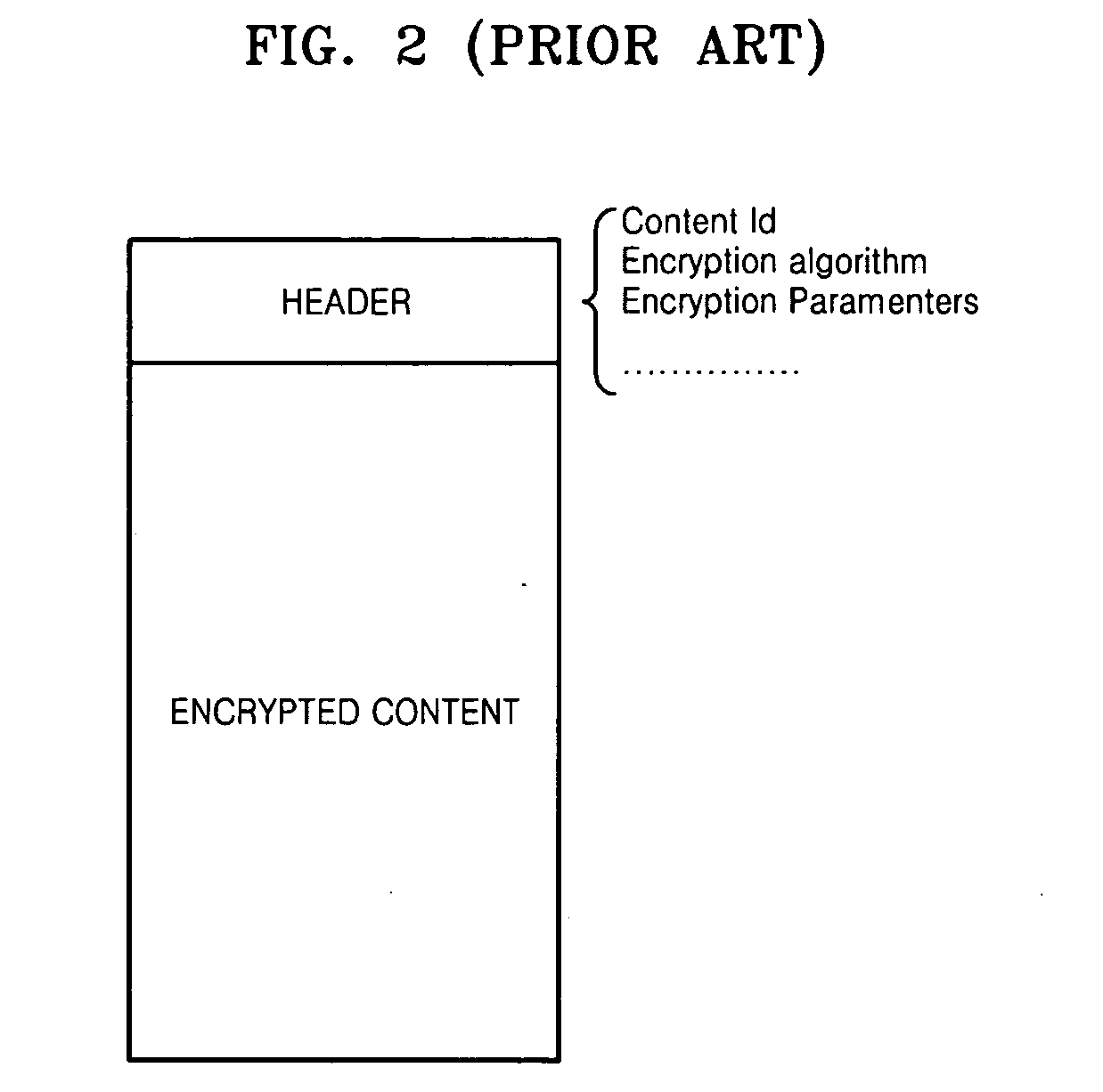
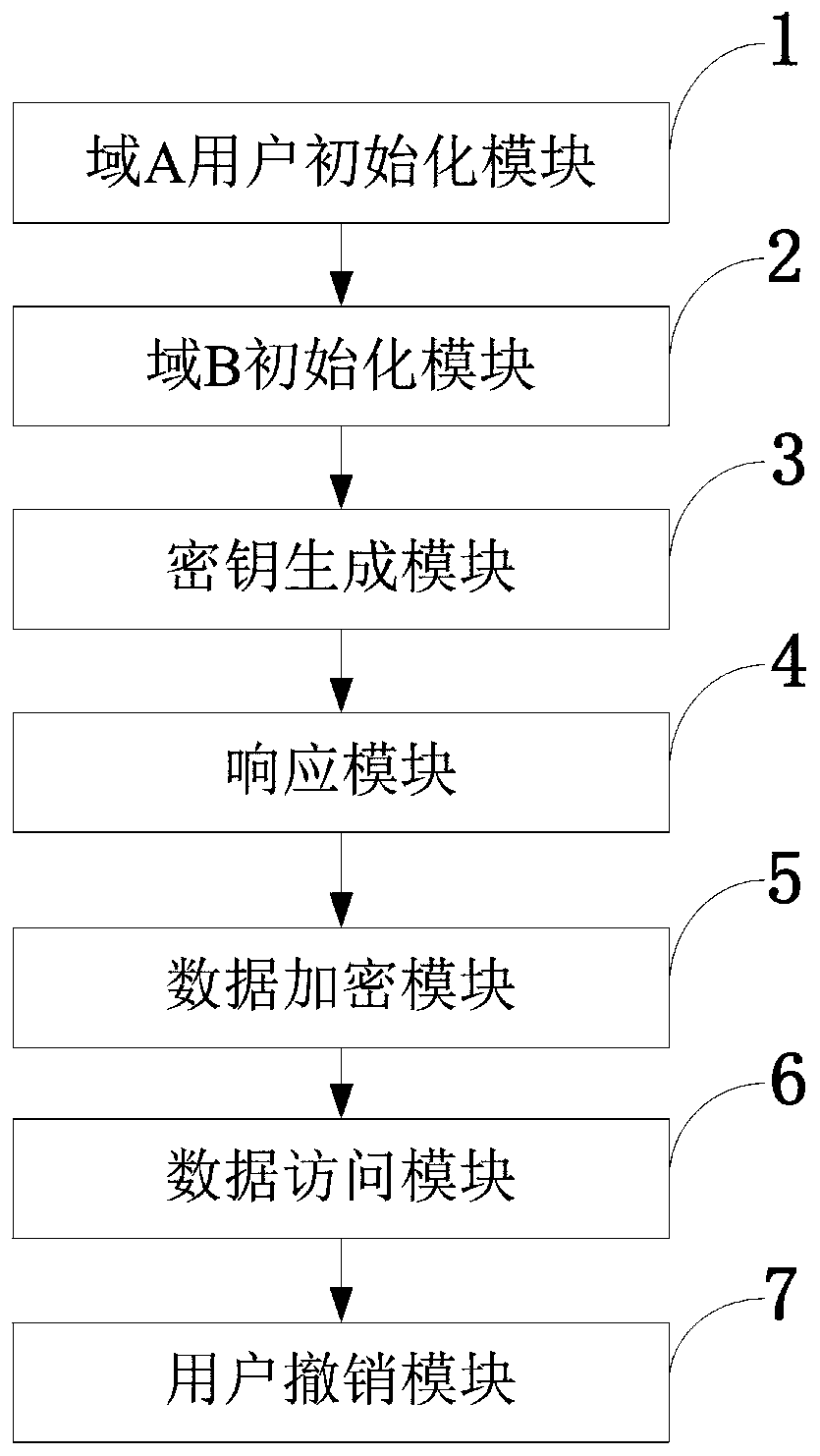
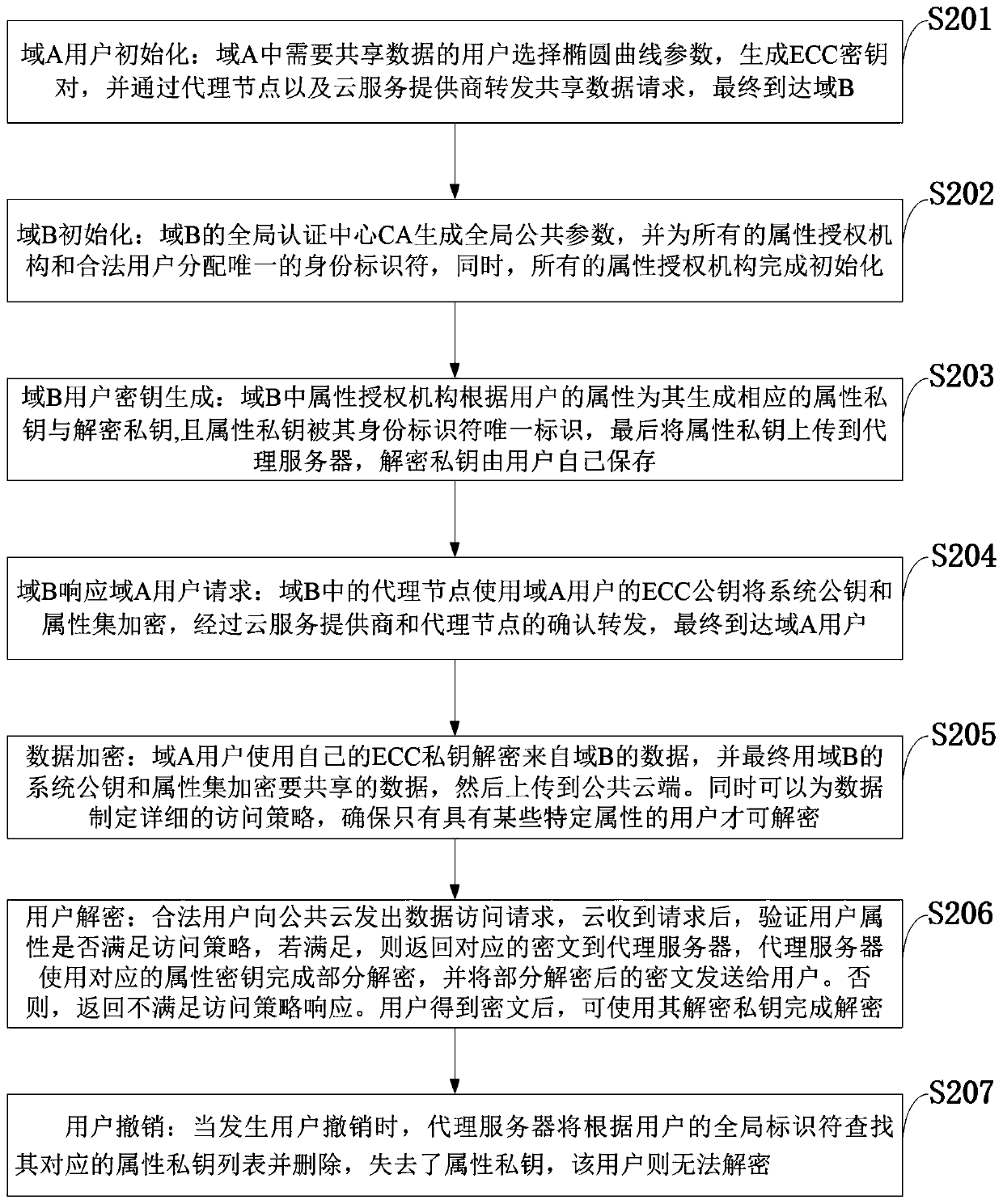
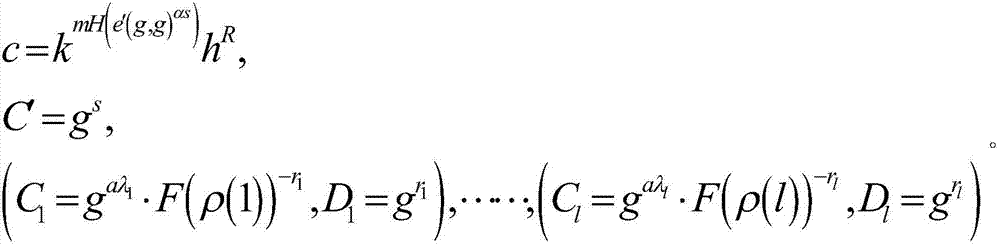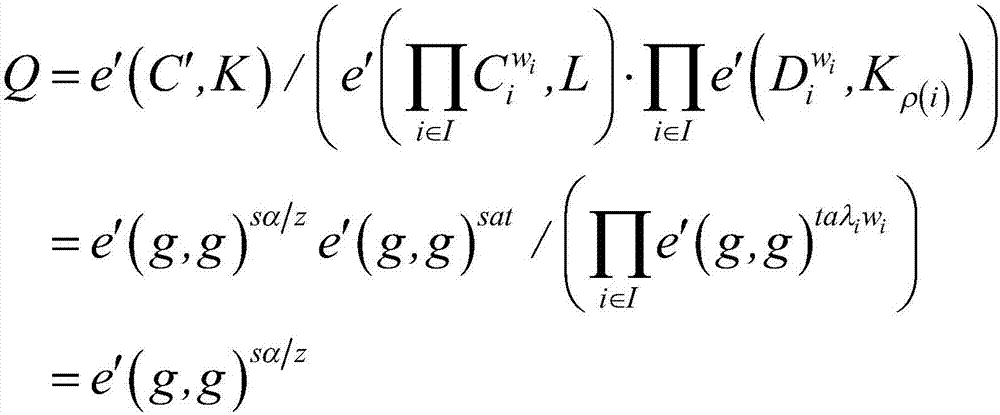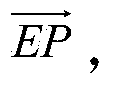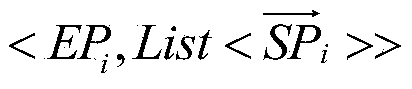Patents
Literature
97results about How to "Improve decryption efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
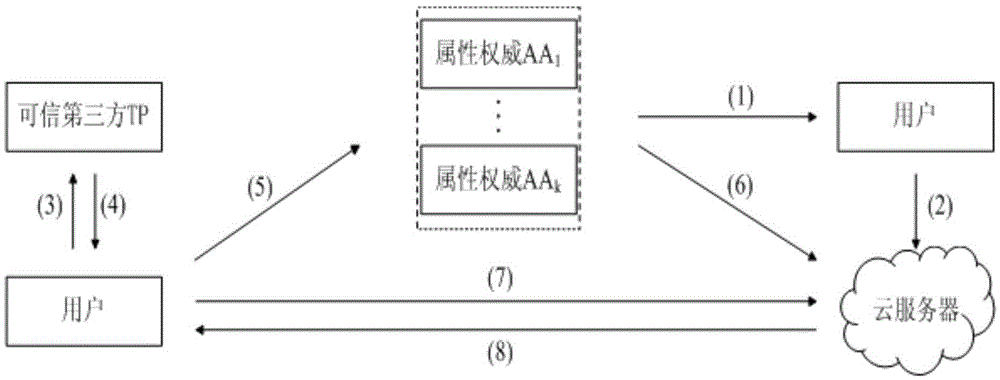
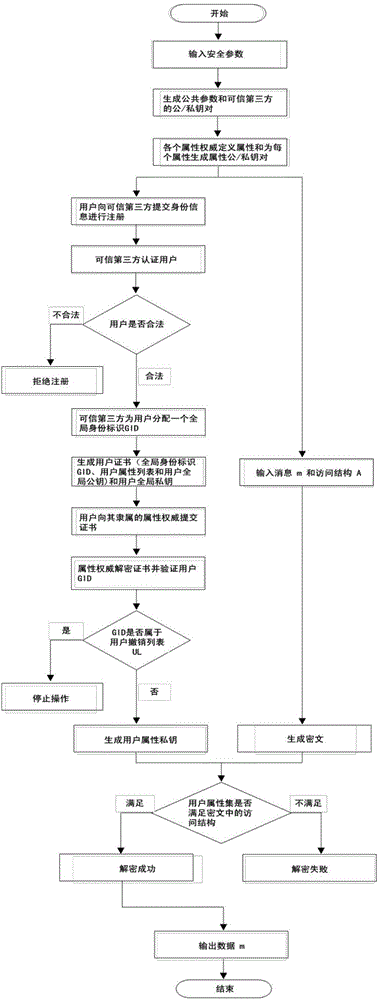
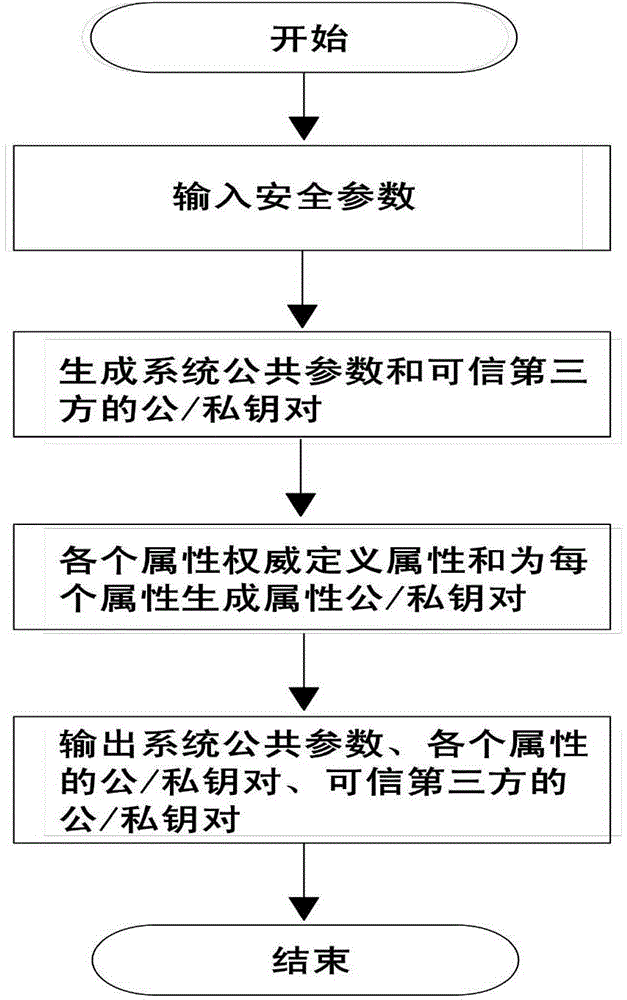
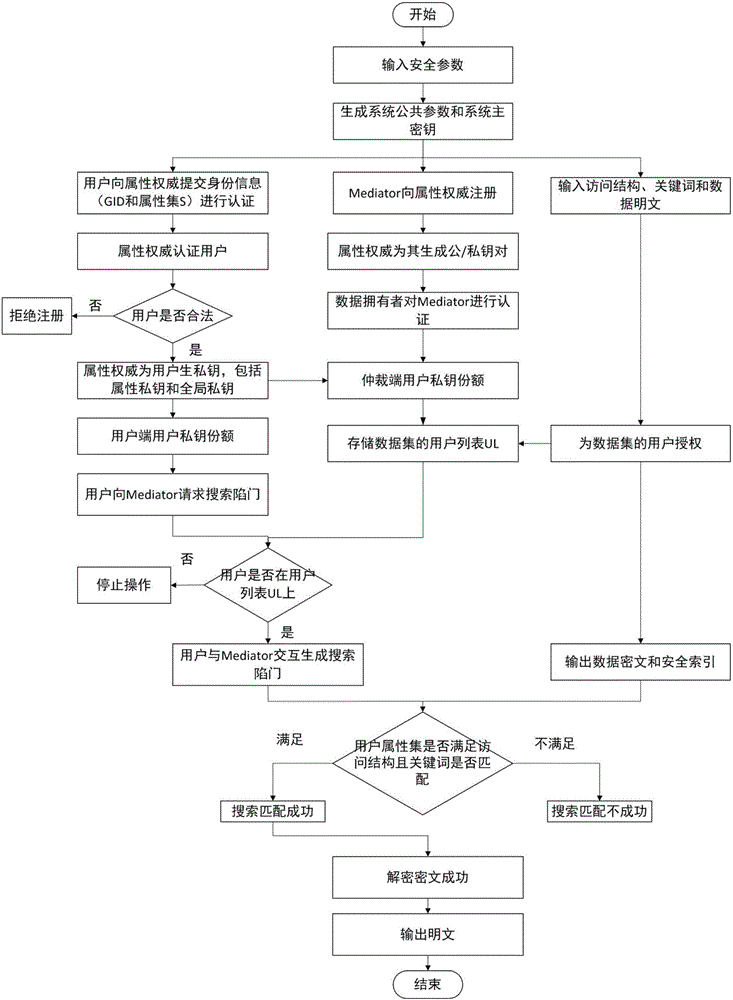
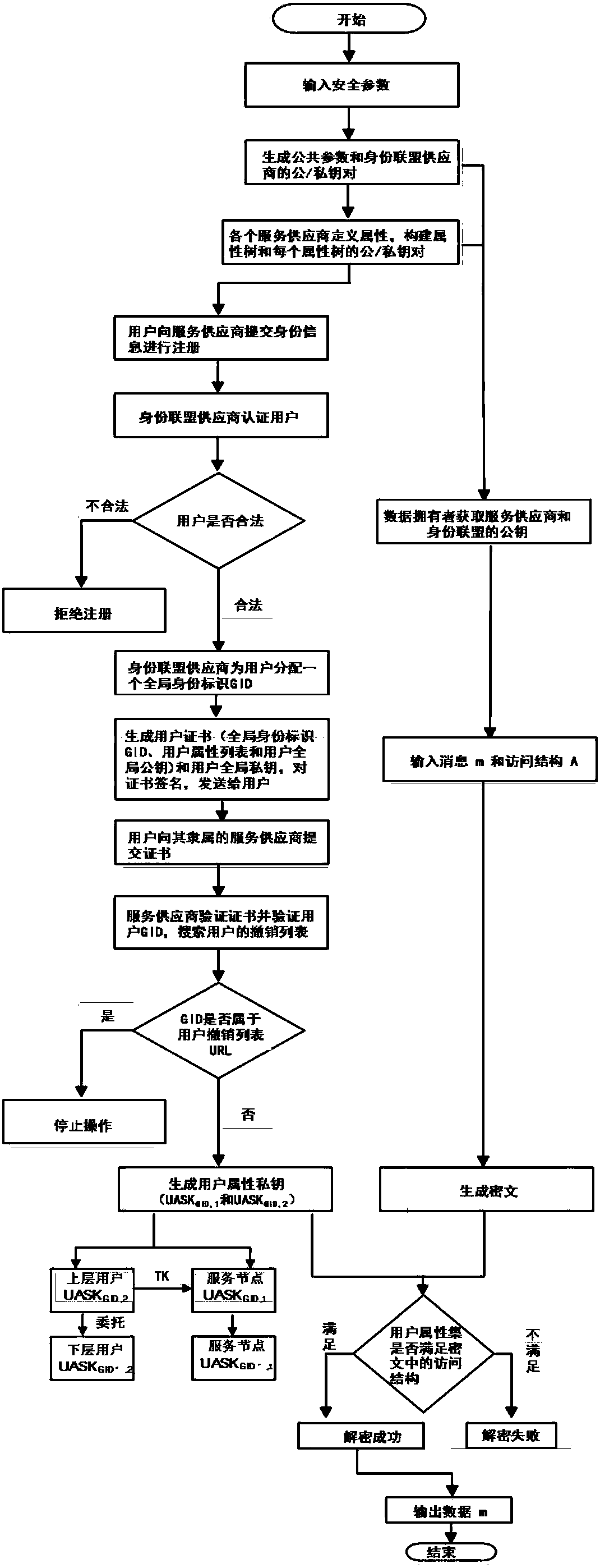
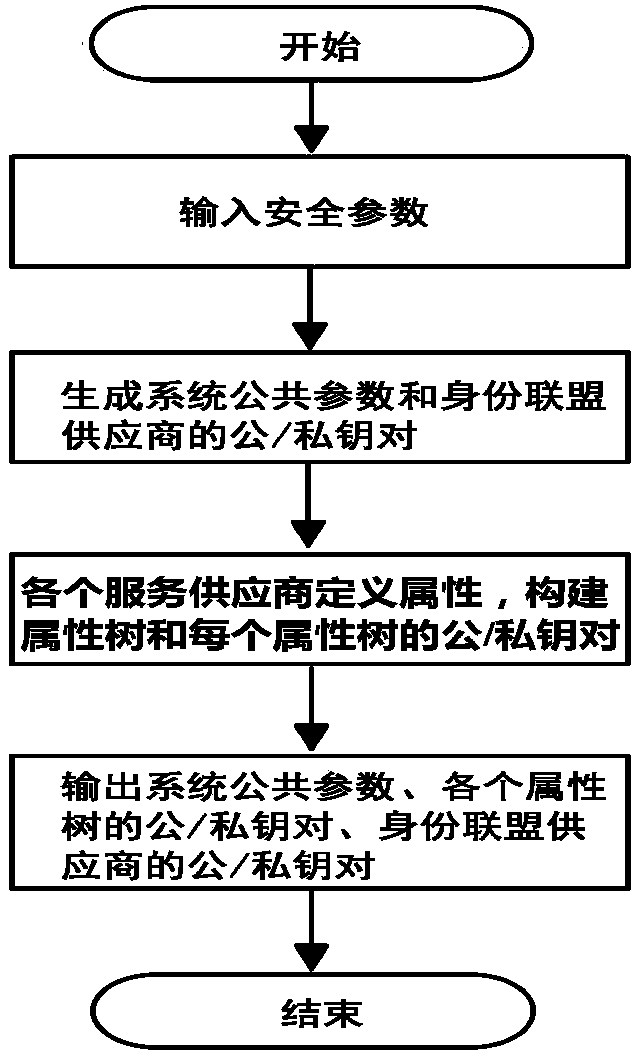
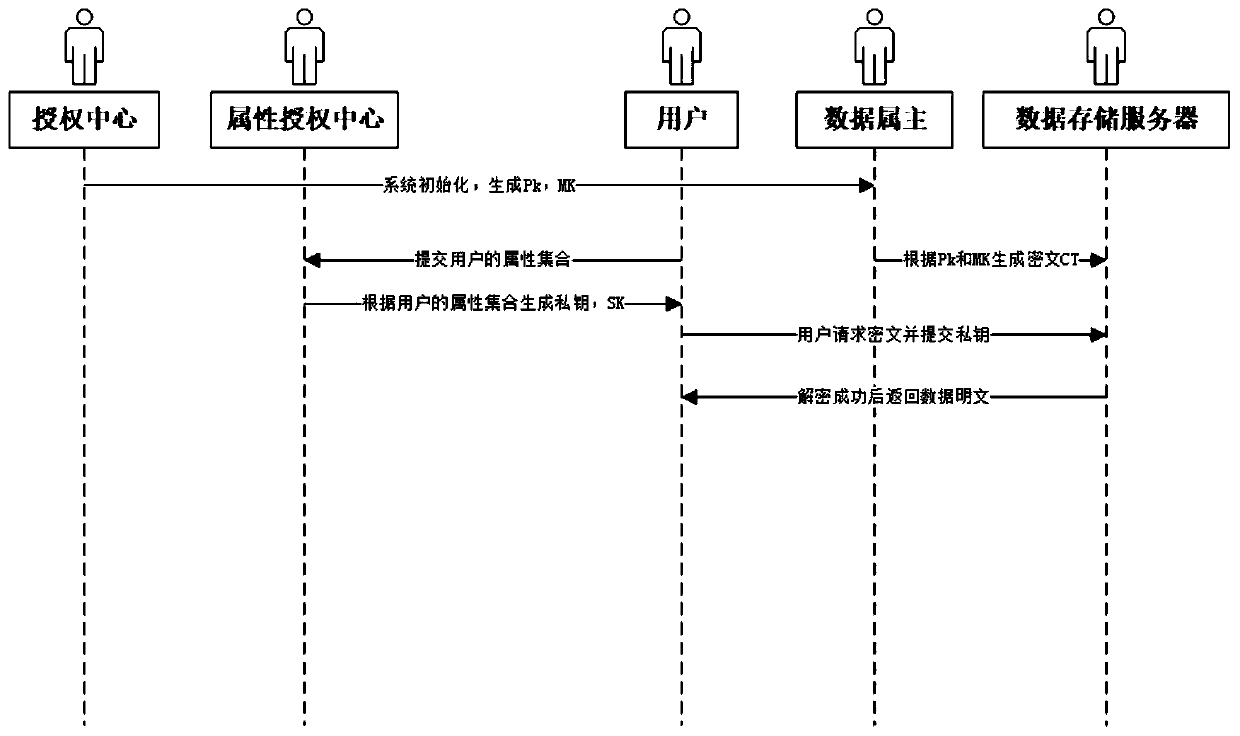
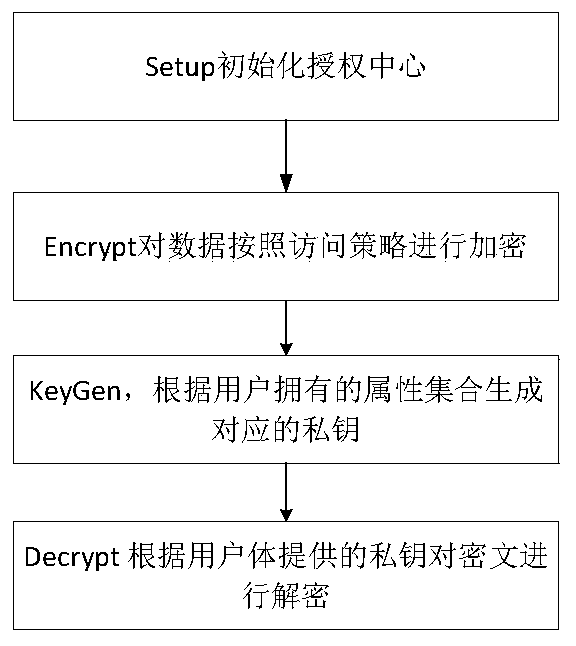
Distributed access control method for attribute-based encryption
ActiveCN104901942AAvoid collusionAbility to decrypt all system ciphertextsKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEngineering
The invention provides a distributed access control method for attribute-based encryption, and mainly aims to solve the problems of security and privacy protection of massive data in a cloud environment. A multi-authority ciphertext-policy attribute-based encryption (CP-ABE) mechanism is provided on the basis of CP-ABE. According to the mechanism, the workload of a single authority is shared with a plurality of authorities, and efficient outsourcing decryption, user revocation and dynamic join and exit supporting attribute authority (AA) can be realized. Through adoption of an access control mechanism provided by the invention, efficient, distributed, extensible and fine-granularity access control can be realized while the security and privacy of the massive data are protected.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
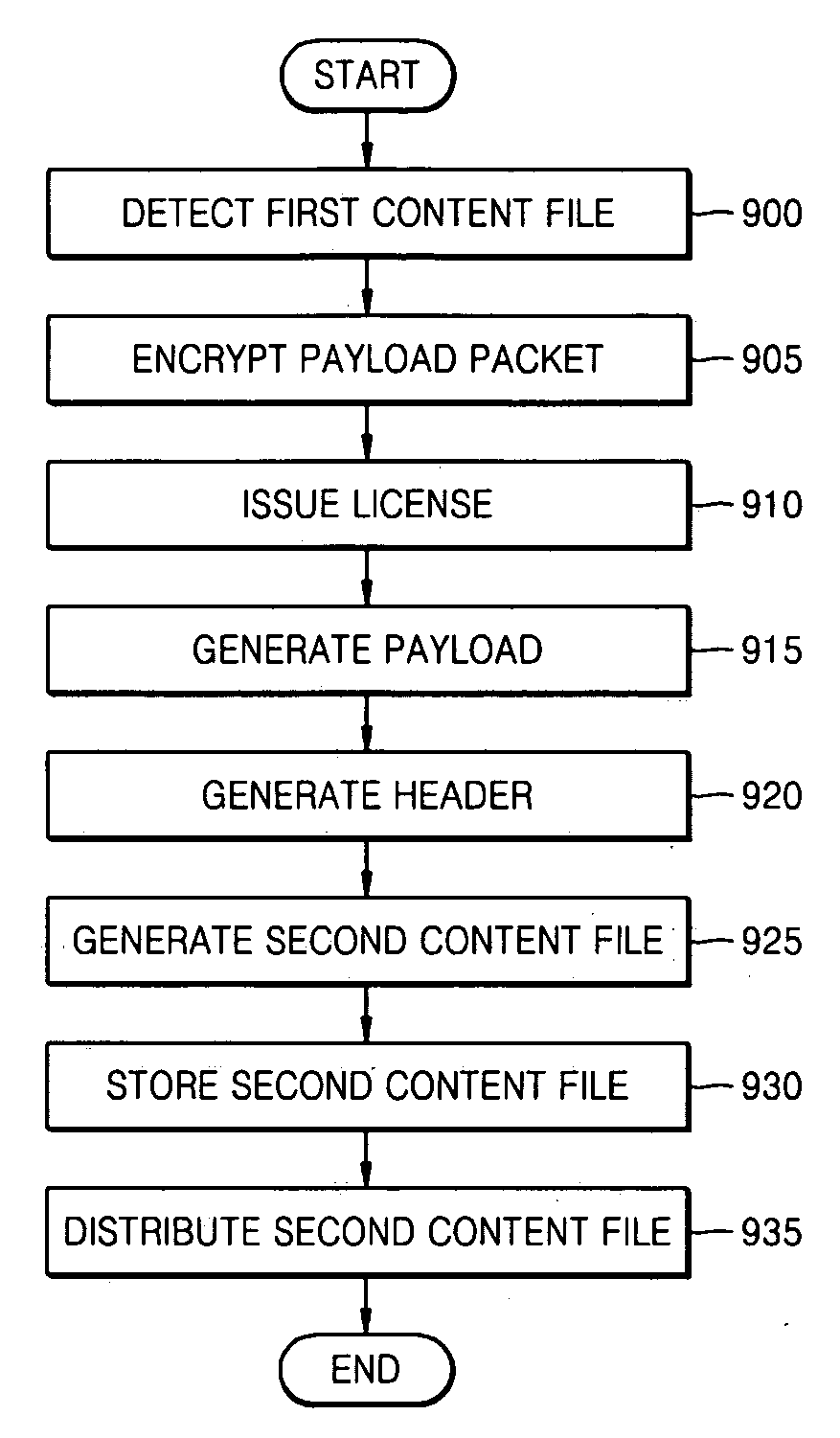
Method and apparatus for importing a transport stream
ActiveUS20070198858A1Improve decryption efficiencyImprove import efficiencyPulse modulation television signal transmissionDigital data processing detailsComputer networkTime delays
A content import method in a digital rights management (DRM) system imports transport streams received from outside a domain, generates a content file, and regularly inserts information in the form of transport packets necessary for decrypting encrypted content into a payload of the content file. Accordingly, even if usage constraint information (UCI) included in the received content changes, packaging is possible. When a device pertaining to the domain receives half of an imported content file via streaming, transport packets of the received half of the imported content file can be promptly decrypted without a time delay.
Owner:SAMSUNG ELECTRONICS CO LTD
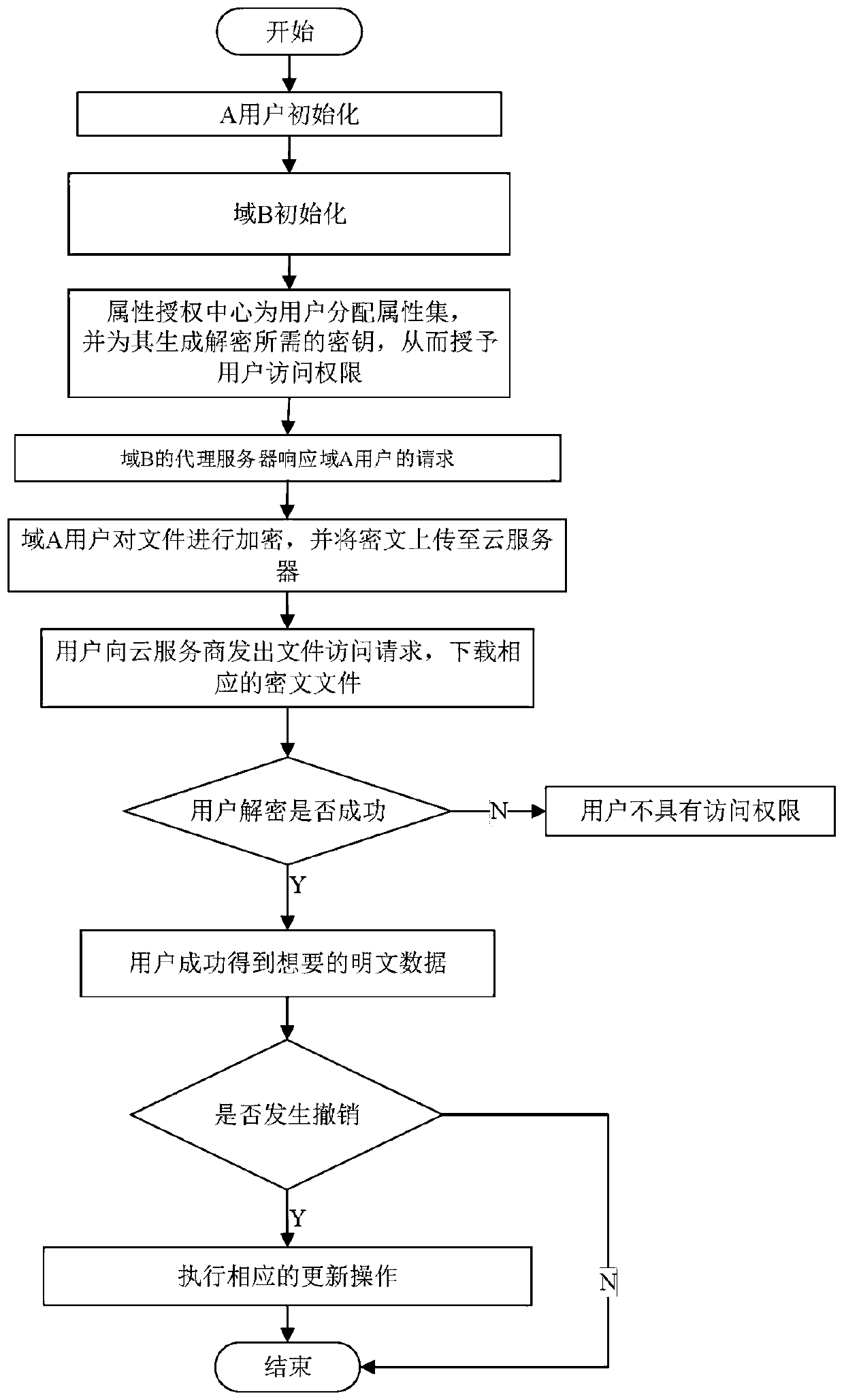
Access control system and method supporting cross-domain data sharing and wireless communication system
ActiveCN110636500AGuaranteed safe transmissionImprove securityPublic key for secure communicationSecurity arrangementKey sizeCommunications system
The invention belongs to the technical field of wireless communication networks, and discloses an access control system and method supporting cross-domain data sharing, and a wireless communication system. Users needing to share data in a domain A select elliptic curve parameters to generate ECC key pairs; a global authentication center CA of the domain B generates a global public parameter; the proxy node in the domain B encrypts the system public key and the attribute set by using the ECC public key of the domain A user; the domain A user decrypts the data from the domain B by using the ECCprivate key of the domain A user and uploads the data to the public cloud; the legal user sends a file access request to the public cloud; and when user revocation occurs, the proxy server searches acorresponding attribute private key list according to the global identifier of the user and deletes the attribute private key list. The method is high in safety under the condition of the same secretkey length. The method gives full play to the characteristic of strong computing power of agent nodes, completes the preprocessing of some data, helps a user to carry out partial decryption, and improves the decryption efficiency of the user.
Owner:XIDIAN UNIV
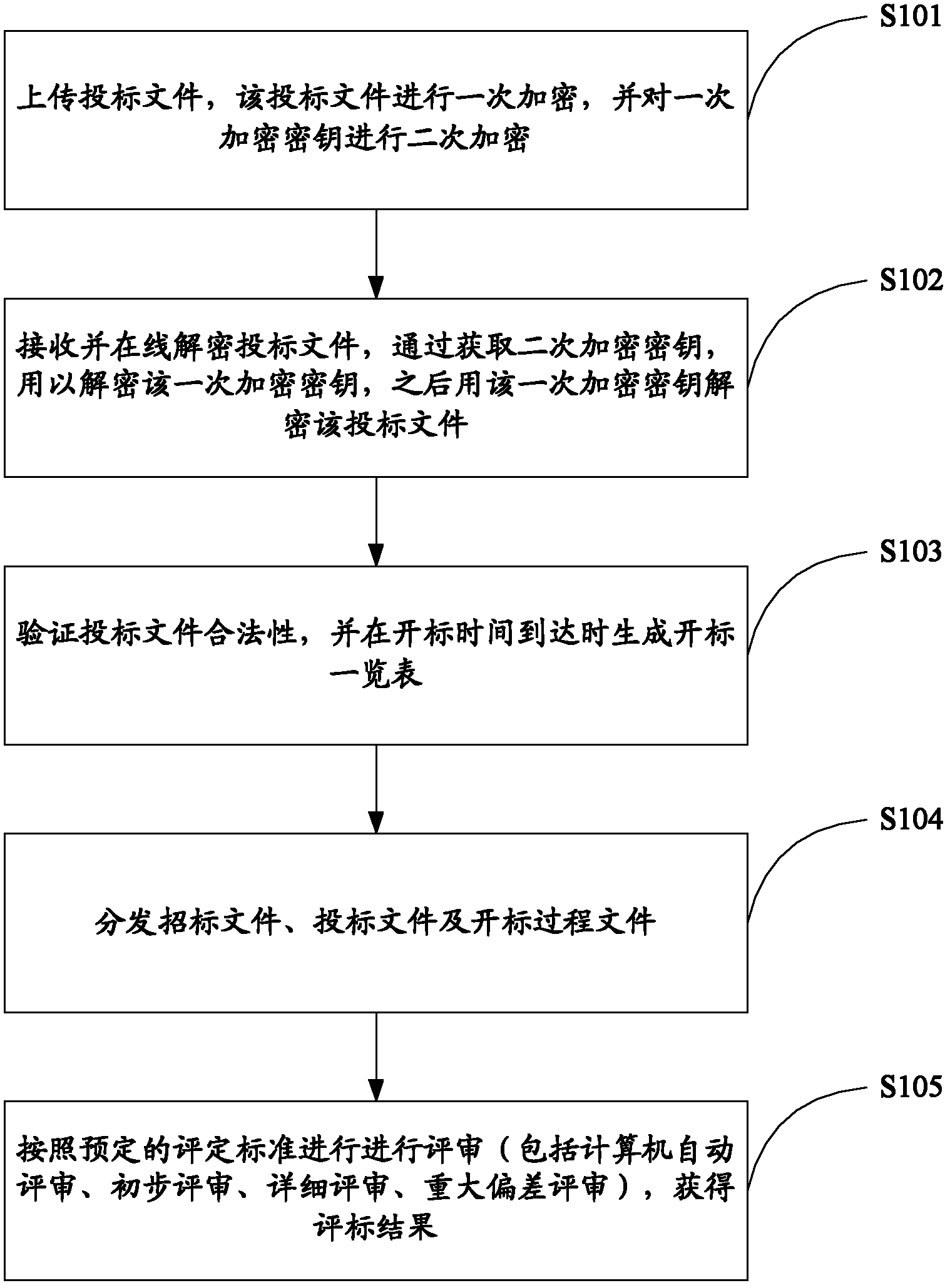
Method and system for remote bid opening and bid evaluation
InactiveCN102684879AEnsure data securityImprove data securityUser identity/authority verificationPlatform integrity maintainancePaper documentDocument preparation
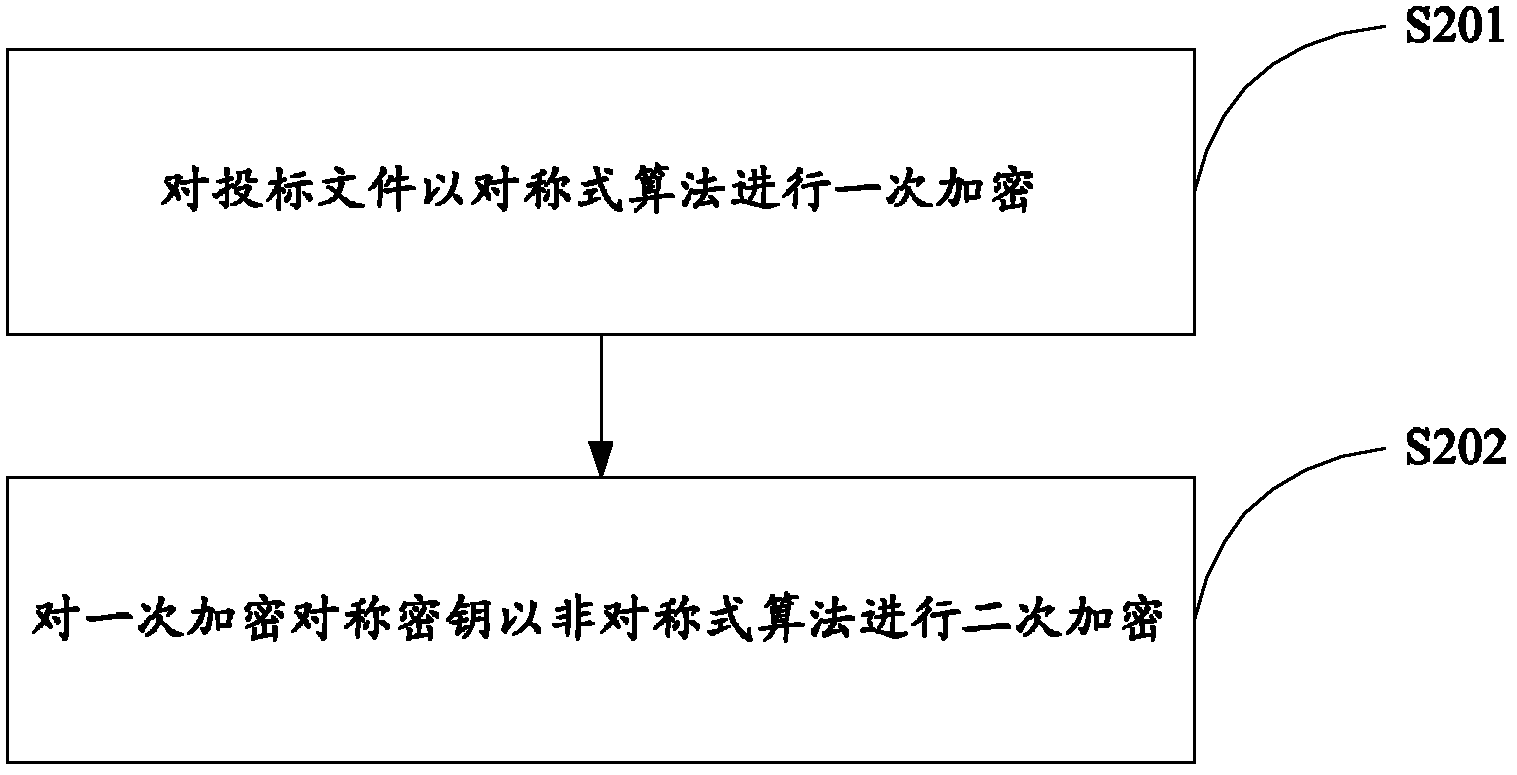
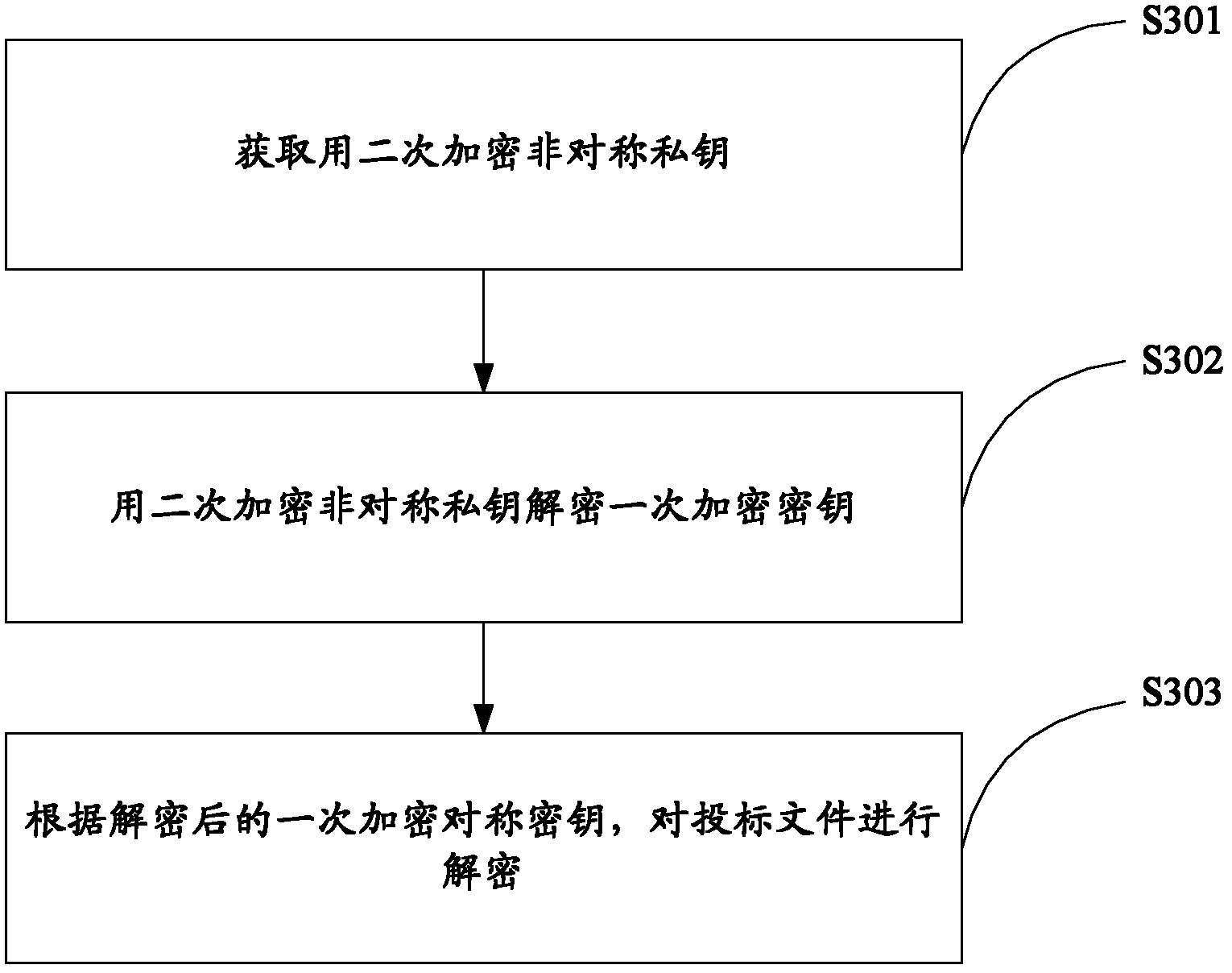
The invention relates to data safety technology, and particularly discloses a method and a system for remote bid opening and bid evaluation. The method includes the steps: uploading bidding documents, primarily encrypting the bidding documents and secondarily encrypting a primary encryption key; receiving and decrypting the bidding documents in an online manner, decrypting the primary encryption key by acquiring a secondary primary encryption key, and then decrypting the bidding documents by the aid of the primary encryption key; verifying validity of the bidding documents and generating a bid opening list when bid opening time comes; distributing bid inviting documents, the bidding documents and bid opening process documents; and performing evaluation according to preset evaluation standards to obtain bid evaluation results. The system comprises a bidding service subsystem, a bid opening service subsystem and a bid evaluation service subsystem, wherein the bid opening service subsystem is capable of decrypting the secondarily encrypted bidding documents in the online manner and providing the corresponding bid inviting documents, the bidding documents and the bid opening process documents to the bid evaluation service subsystem for evaluation. By the aid of the method and the system, safety of the bidding documents is facilitated, and decrypting efficiency is improved.
Owner:SICHUAN CONSTR NETWORK
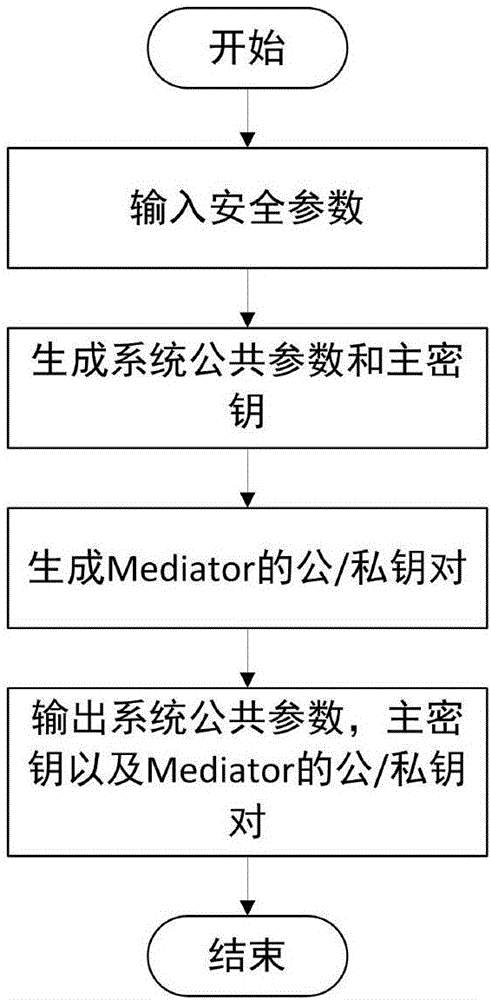
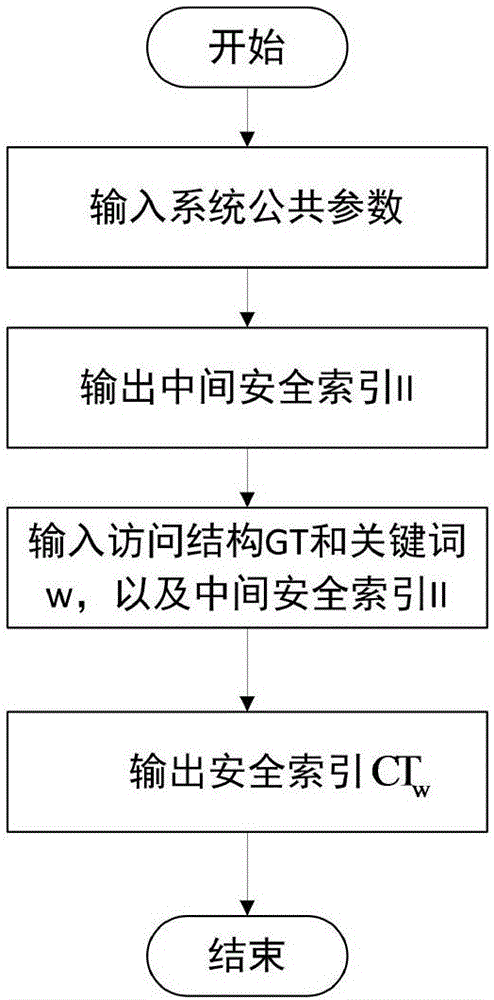
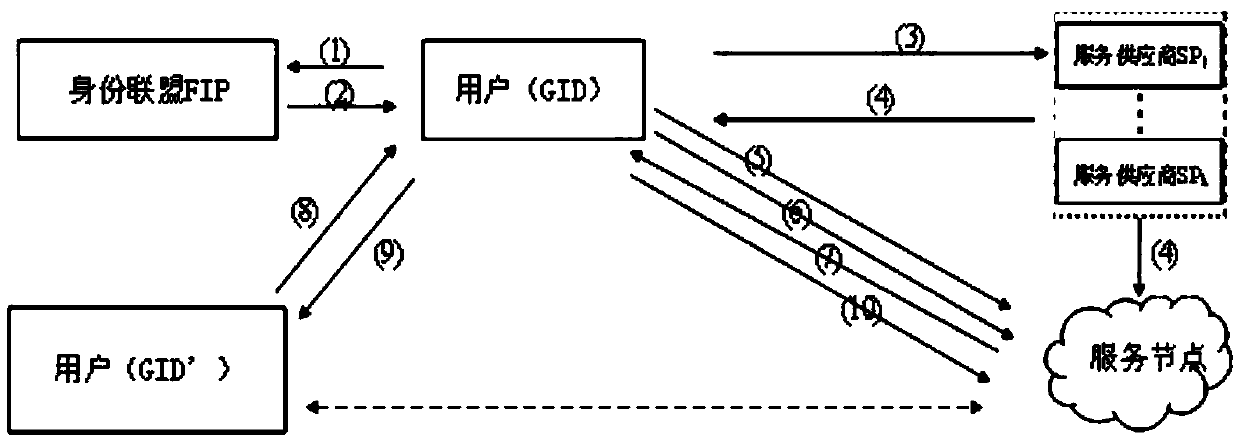
Mediated and searchable encryption method
ActiveCN106850652AEfficient undoImprove decryption efficiencyKey distribution for secure communicationOnline and offlineXML Encryption
The invention relates to a mediated and searchable encryption method. The method comprises the following steps: S1, system initialization; S2, keyword encryption; S3, data encryption; S4, user key generation; S5, search Trapdoor generation; S6, data searching; S7, data decryption; and S8, user revocation. The mediated and searchable encryption method provided by the invention has the advantages that online and offline encryption and mediated encryption can be achieved, the method is applicable to a mobile cloud computing environment, and user permissions can be revoked instantly.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Distributed cross-domain authorization and access control method based on attribute password
ActiveCN108418784AAvoid bottlenecksAvoid security issuesKey distribution for secure communicationPasswordSecret code
The invention provides a distributed cross-domain authorization and access control method based on an attribute password. The method is mainly used for solving the problems of cross-domain authorization and access control under a large-scale distributed environment. The invention designs a hierarchical attribute-based encryption with controlled key delegation and attribute authorities, supportingdecentralized and controlled security authorization for users of a plurality of domains, preventing abuse of the key delegation, and accordingly achieving non-interactive access control. The method also supports decoding of an external packet, and supports the authorization to the light-weight users for accessing the system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
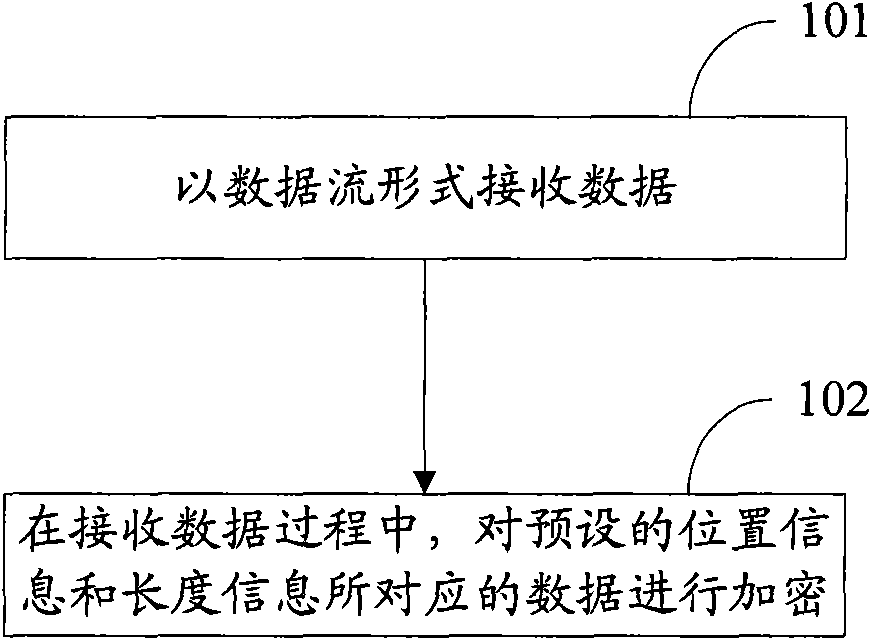
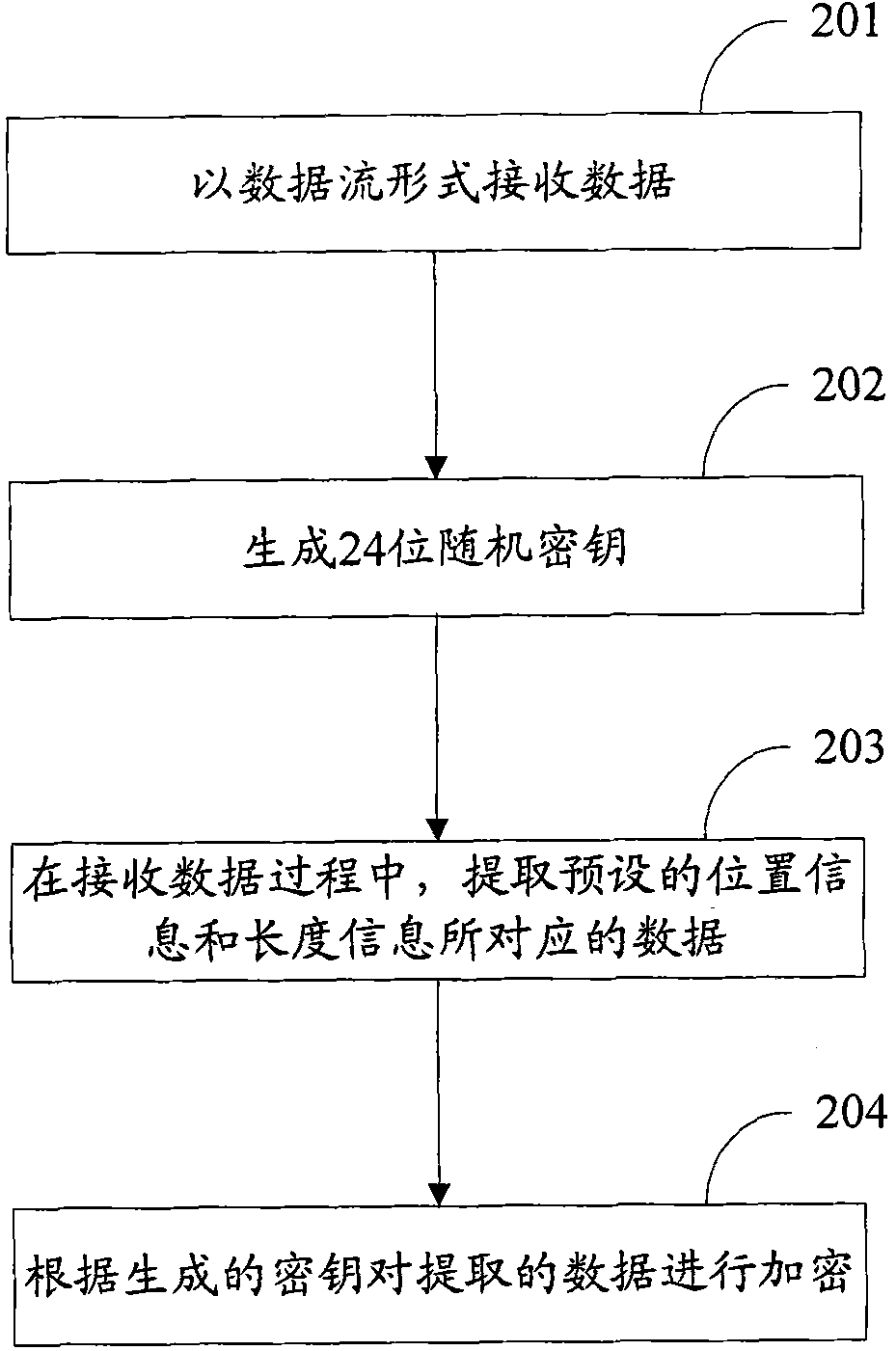
Data encryption and decryption methods and devices
InactiveCN102063598AAvoid problems with encryptionFor encryption purposeDigital data protectionData streamData decryption
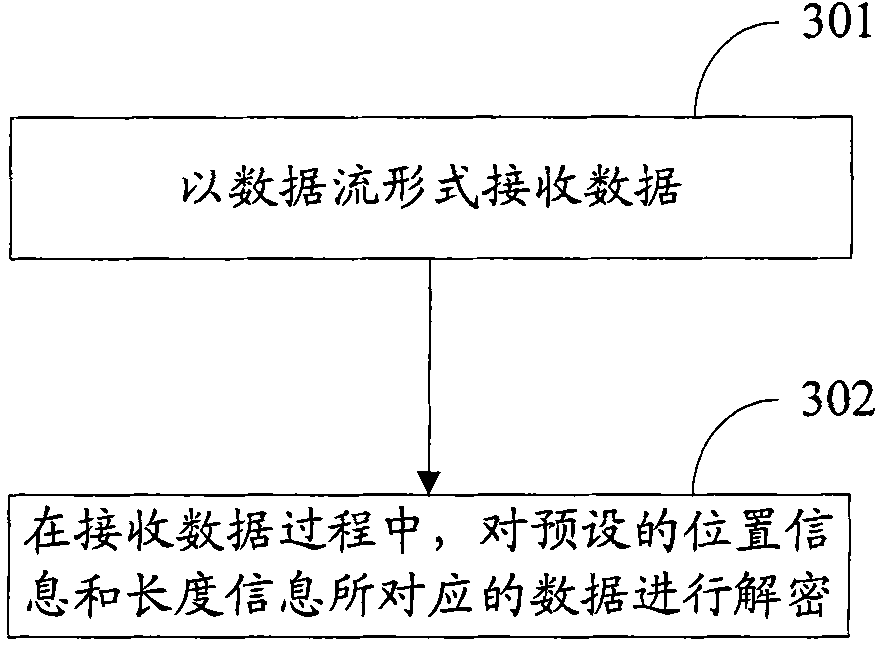
The invention discloses data encryption and decryption methods, which are used for locally encrypting data to improve encryption efficiency and realizing a corresponding decryption scheme. The data encryption method comprises the following steps of: receiving data in a data stream form; and in the process of receiving data, encrypting data corresponding to preset position information and length information, wherein the data to be encrypted is partial data in file data. The data decryption method comprises the following steps of: receiving data in a data stream form; and in the process of receiving the data, decrypting data corresponding to preset position information and length information, wherein the data to be decrypted is partial data in file data. The invention also discloses devices for implementing the methods.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Remote-authorization-based bidding document encryption and decryption method
ActiveCN102664740AConvenient remote authorization decryption methodEnsure safetyUser identity/authority verificationInformation securityAuthorization
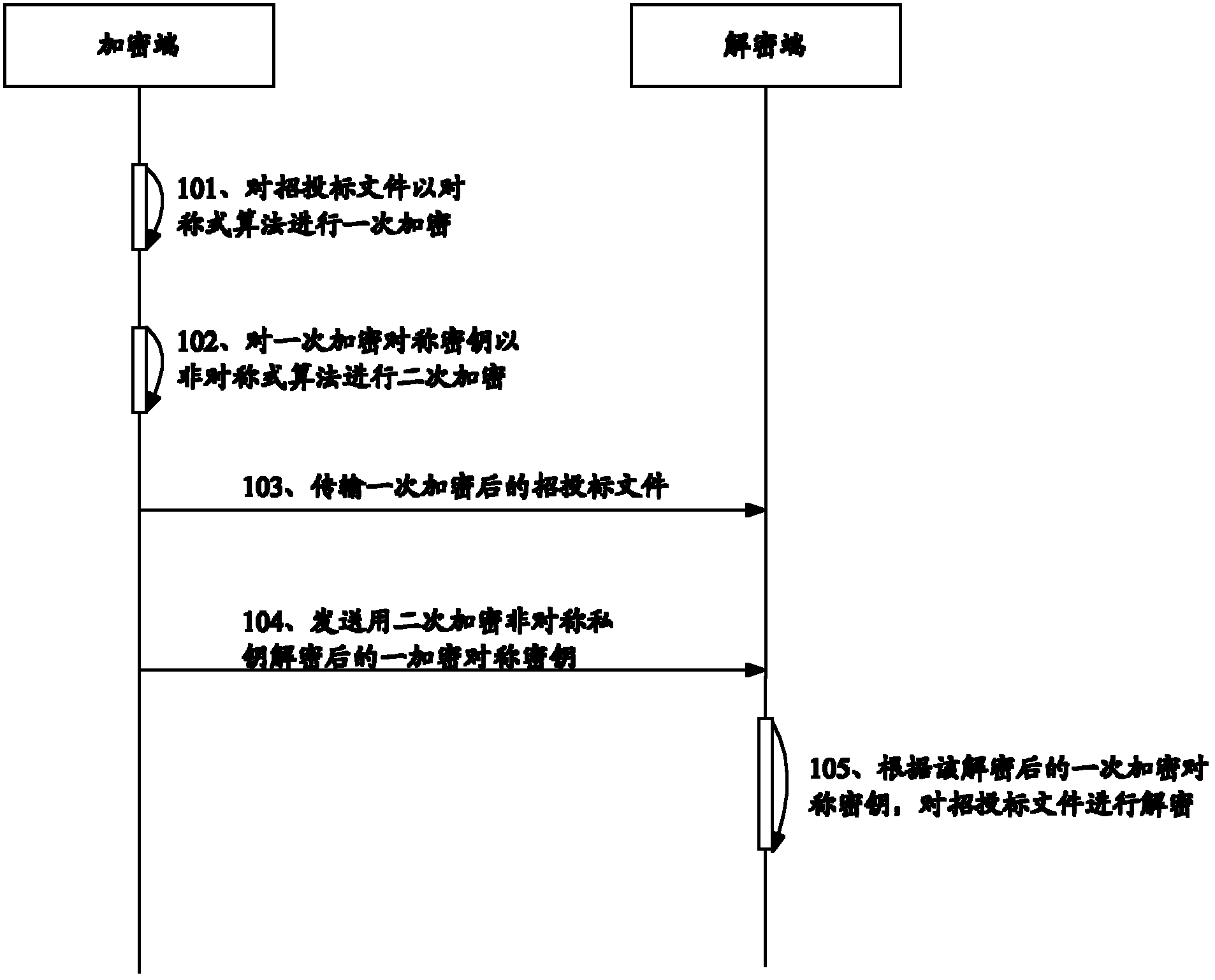
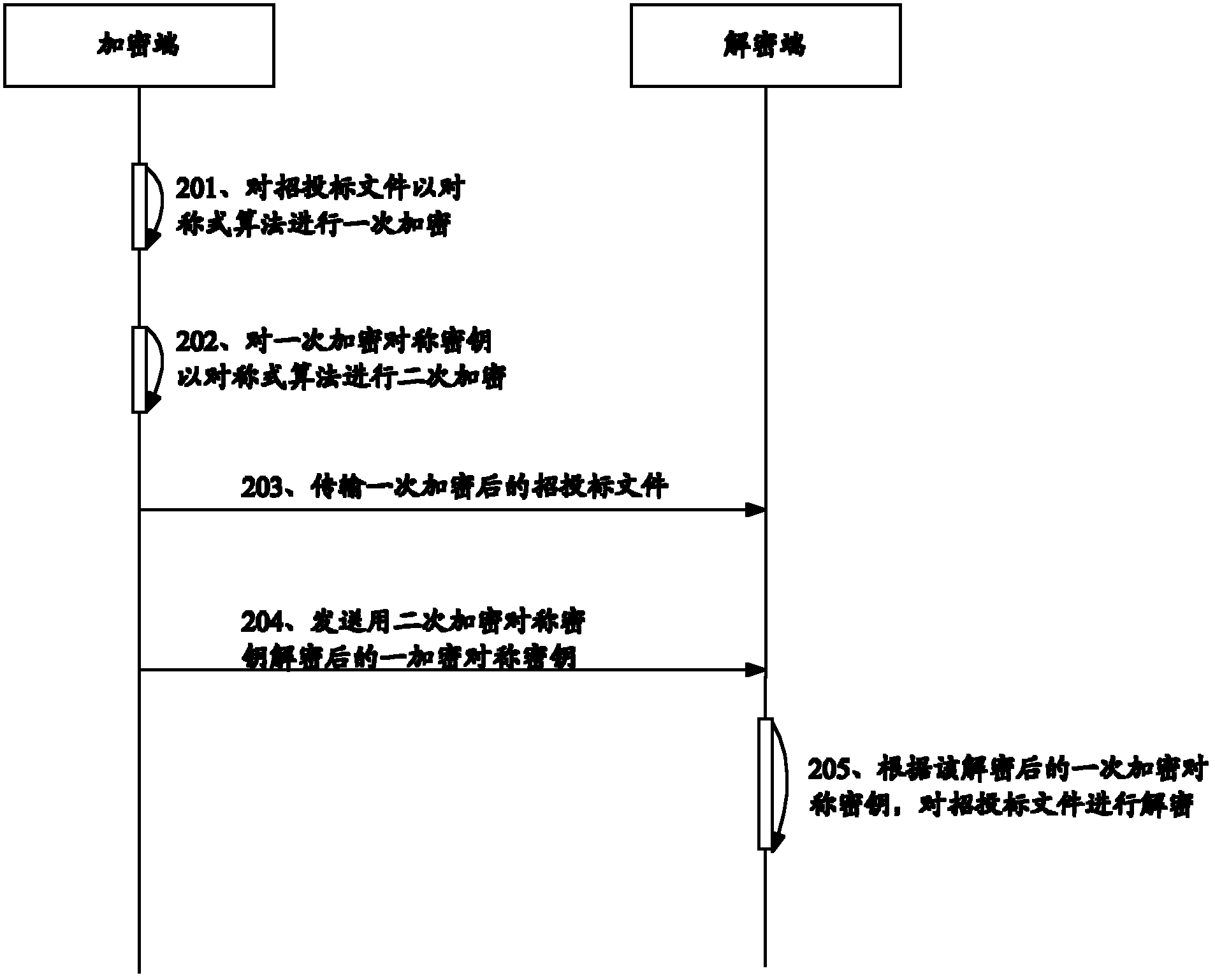
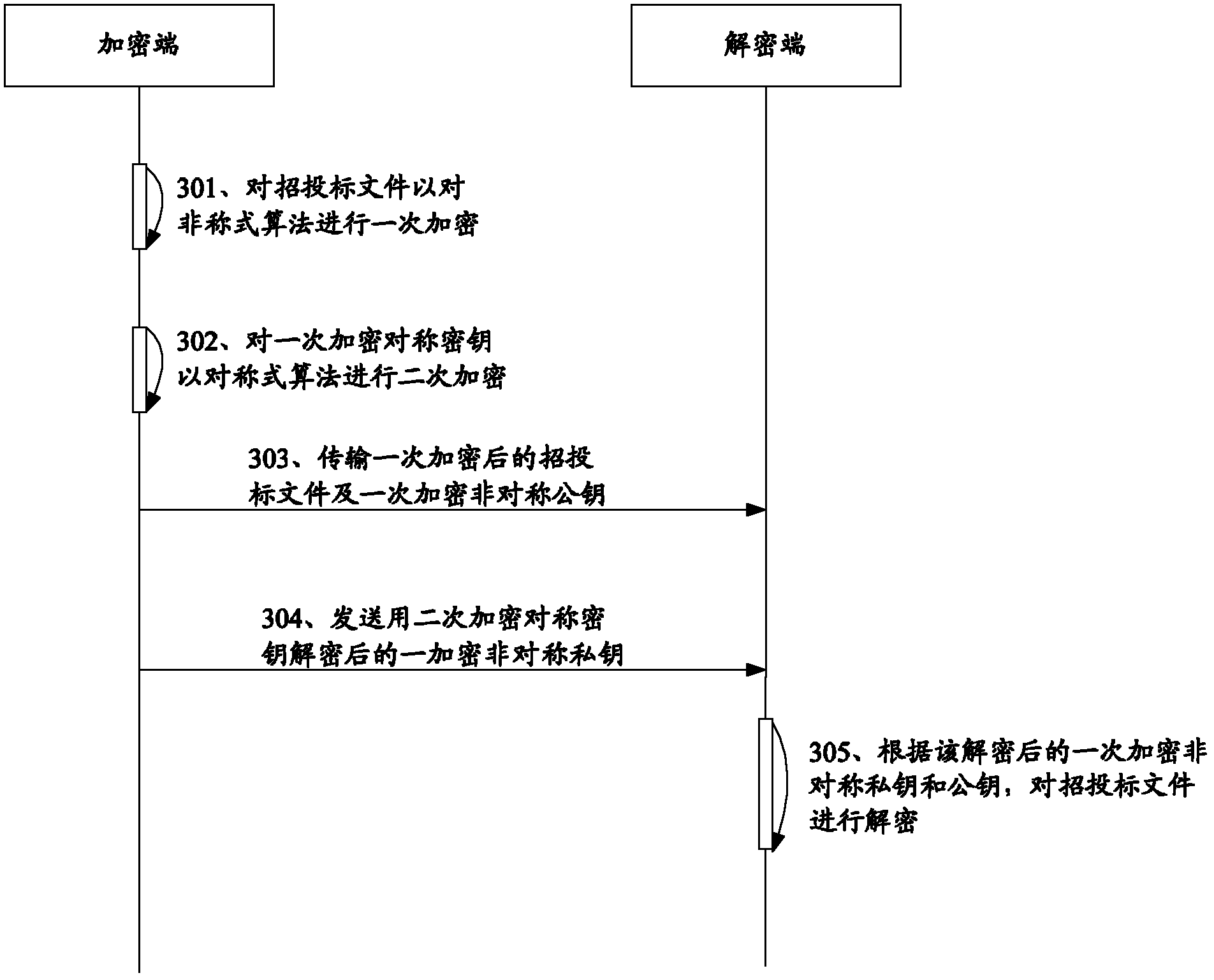
The invention relates to a computer information security technology, and particularly discloses a remote-authorization-based bidding document encryption and decryption method, which comprises the following steps that: an encryptor primarily encrypts a bidding document; the encryptor secondarily encrypts a primary encryption key; the encryptor transmits the primarily encrypted bidding document to a decryptor; the encryptor transmits the primary encryption key decrypted by a secondary encryption key to the decryptor when specified time is reached; and the decryptor decrypts the bidding document according to the decrypted primary encryption symmetric key. The encryption key is secondarily encrypted when the bidding document is primarily encrypted, so that the remote authorization decryption of the bidding document can be facilitated, the security of the bidding document can be ensured, and the decryption efficiency of the bidding document can be improved.
Owner:SICHUAN CONSTR NETWORK
White-box cryptography encryption-decryption method based on expansion ciphertext
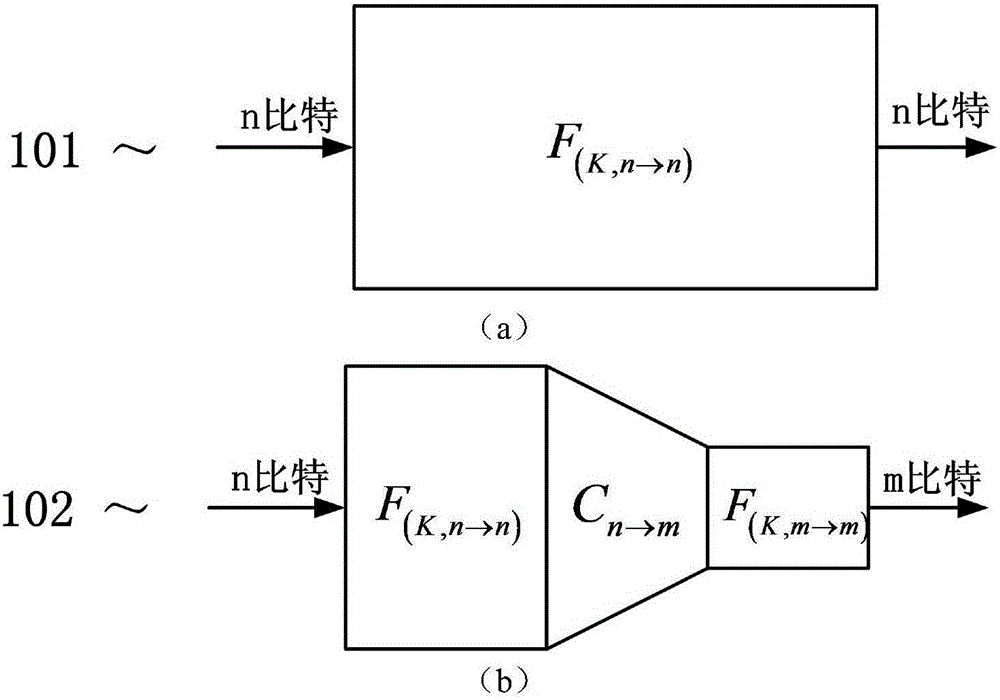
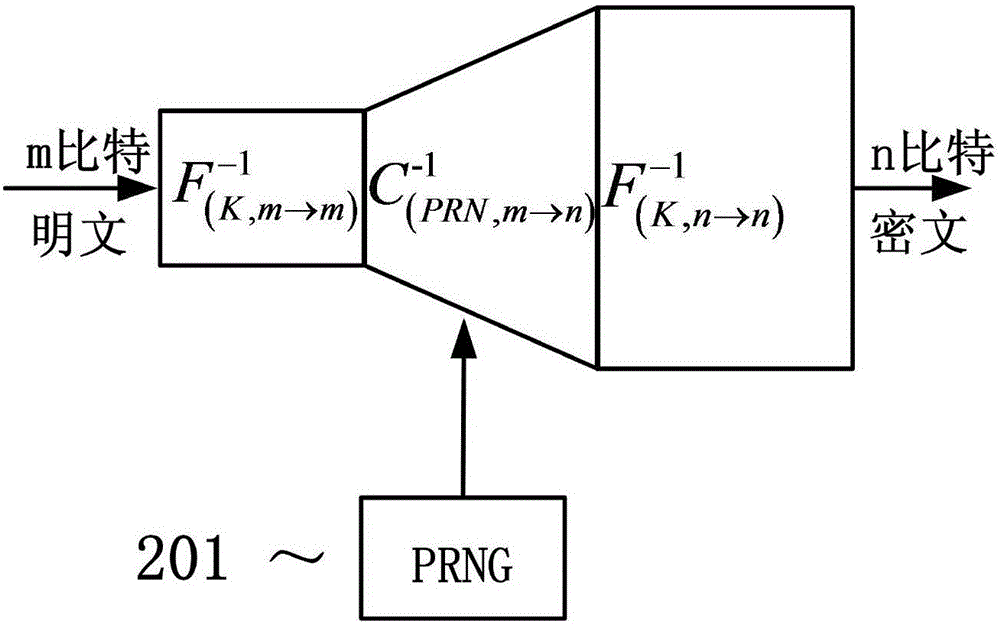
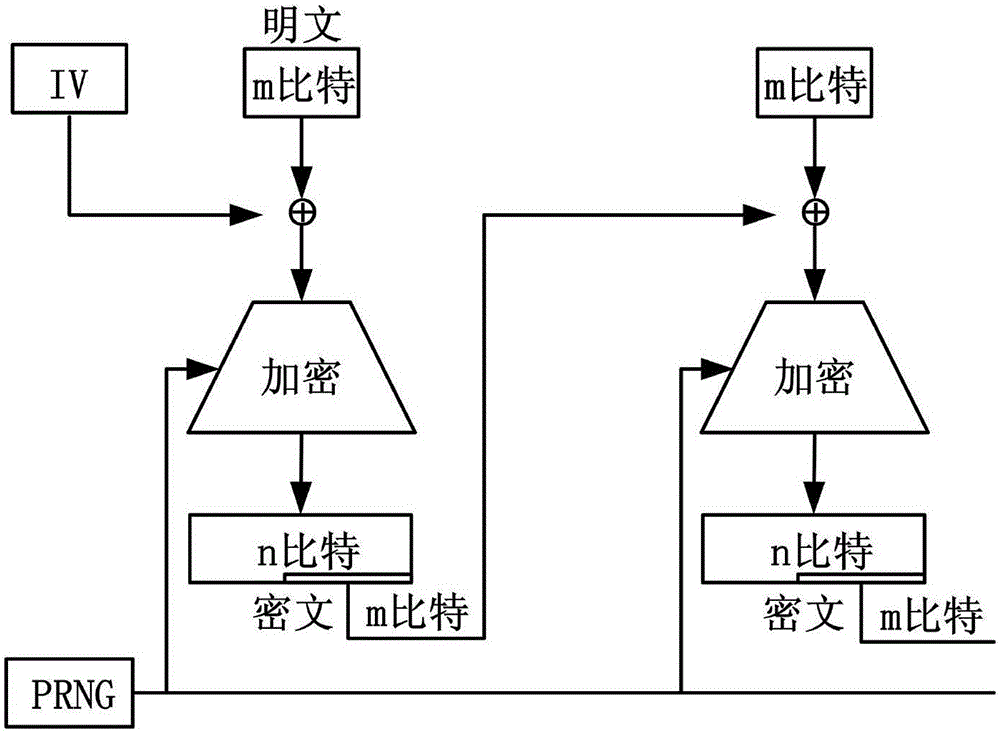
InactiveCN106059752AImprove efficiencySimple structureData stream serial/continuous modificationComputer hardwarePlaintext
The invention discloses a white-box cryptography encryption-decryption method based on an expansion ciphertext. The method comprises the expansion ciphertext and a lookup table, wherein a pseudorandom bit stream is implied in the expansion ciphertext; the lookup table is used for decrypting n bits to m bits (the n is greater than the m); and a table lookup operation is a combination of three functions, namely the one-to-one mapping function F <(K, n-n)> of n-bit inputs to n-bit outputs relevant to a secret key K, the function C<n-m> of the n-bit inputs to the n-bit outputs, and the one-to-one mapping function F <(K, m-m)> of m-bit inputs to m-bit outputs relevant to the secret key K. According to the method disclosed by the invention, in encryption, a server side takes the pseudorandom bit stream as a mask, is combined with the ciphertext and is scrambled to obtain the expansion ciphertext; and in decryption, the n-bit ciphertext is decrypted into a m-bit plaintext via the table lookup operation. The decryption efficiency can be obviously improved.
Owner:INST OF INFORMATION ENG CAS
Fingerprint identification method and device, mobile terminal and storage medium
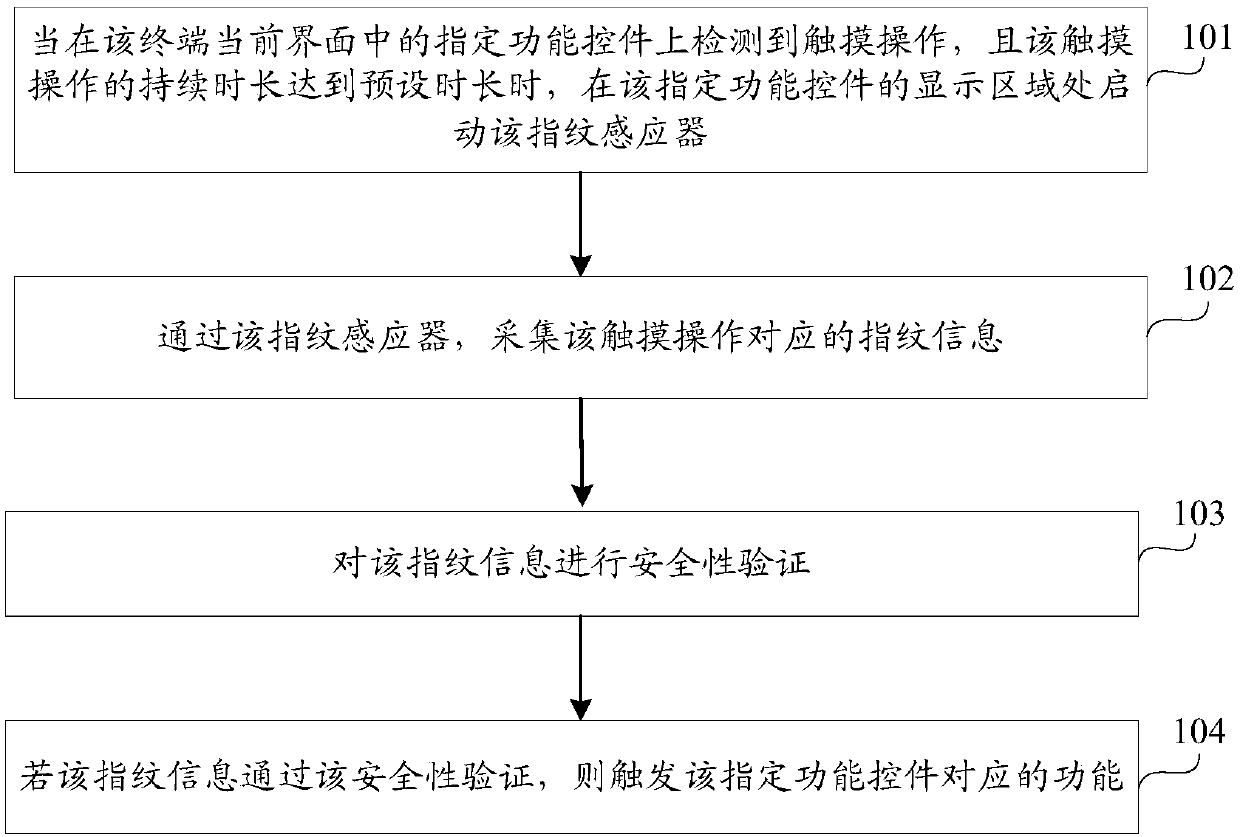
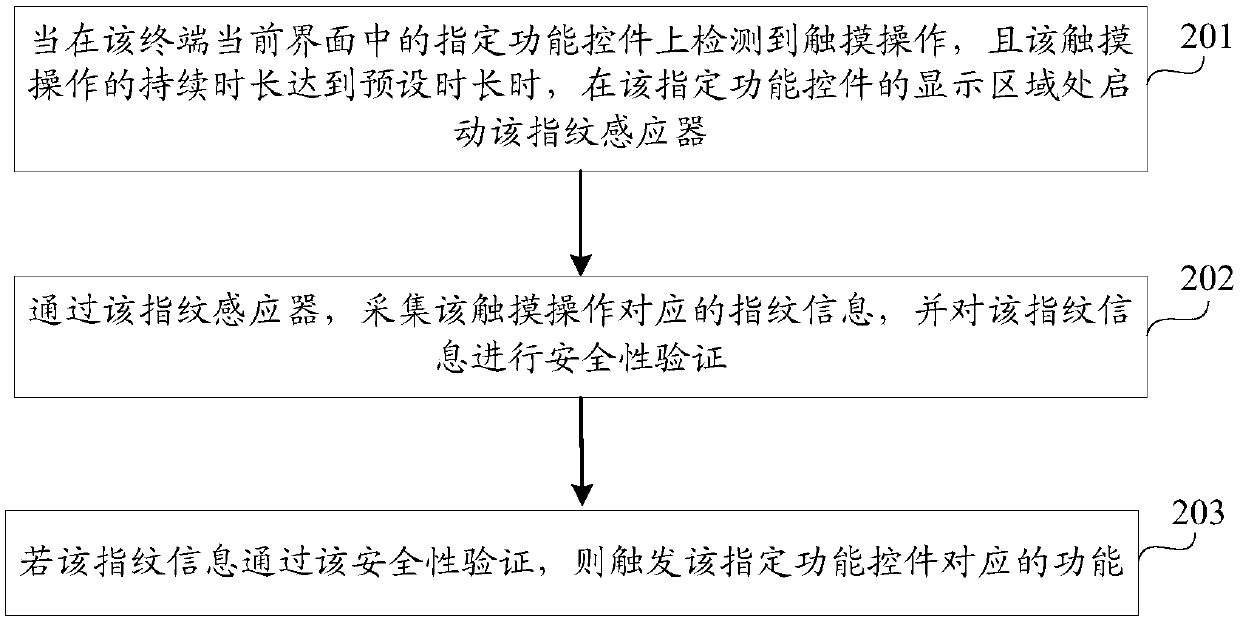
InactiveCN107609372AImprove decryption efficiencyUnauthorised/fraudulent call preventionDigital data processing detailsInformation processingComputer terminal
The application discloses a fingerprint identification method and device, a mobile terminal and a storage medium, and belongs to the technical field of information processing. The method is applied tothe terminal, and includes: when a touch operation is detected on a designated function control in a current interface of the terminal and sustained duration of the touch operation reaches preset duration, starting a fingerprint sensor at a display area of the designated function control, and collecting fingerprint information, which corresponds to the touch operation, through the fingerprint sensor; carrying out security verification on the fingerprint information; and triggering a function, which corresponds to the designated function control, if the fingerprint information passes the security verification. The embodiment of the application improves efficiency of decryption for the function.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
BGN type cryptograph decryption outsourcing scheme based on attributes
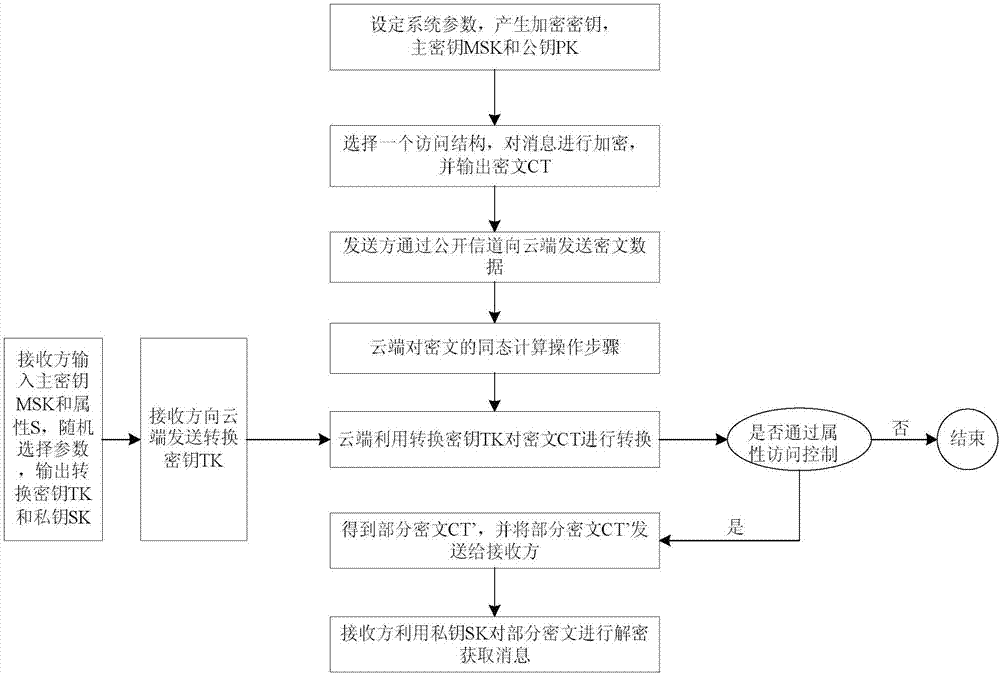
ActiveCN107154845AImprove securityReduce difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess structureSystem parameters
The invention particularly relates to a BGN type cryptograph decryption outsourcing scheme based on attributes. The scheme comprises steps that (1), a system parameter is set, and an encryption secret key is generated; (2), an access structure is selected by a sending side, message encryption is carried out, and cryptograph is generated; (3), a main secret key and the attributes are inputted by a receiving side, and a conversion secret key and a private secret key are outputted; (4), the cryptograph is sent by the sending side to a cloud end; (5), the conversion secret key is sent to the cloud end by the receiving side; (6), the cryptograph is converted by the cloud end through utilizing the conversion secret key to acquire a part of the cryptograph which is sent to the receiving side; and (7), the private secret key is utilized by the receiving side to decrypt the part of the cryptograph to acquire a message, and homomorphic computation operation for the cryptograph carried out by the cloud end is further comprised between the step (4) and the step (5). The scheme is advantaged in that not only can system decryption efficiency be improved, but also storage cost of a receiver is reduced; according to the cryptograph acquired according to the encryption method, a server is permitted to carry out multiple addition homomorphic operation and multiplication homomorphic operation for cryptograph data, on the condition that decryption difficulty does not increase, CPA safety of the user information is substantially improved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
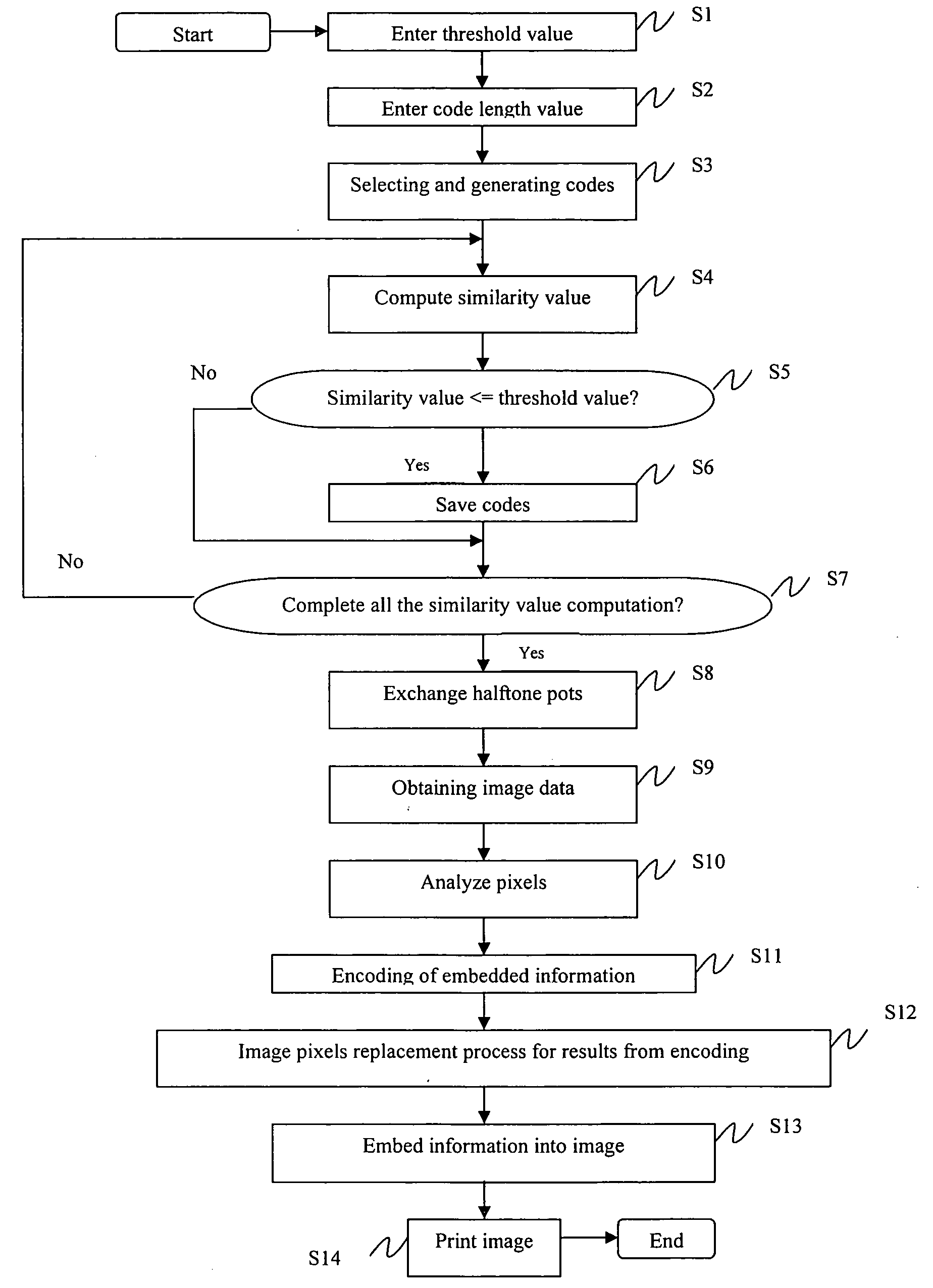
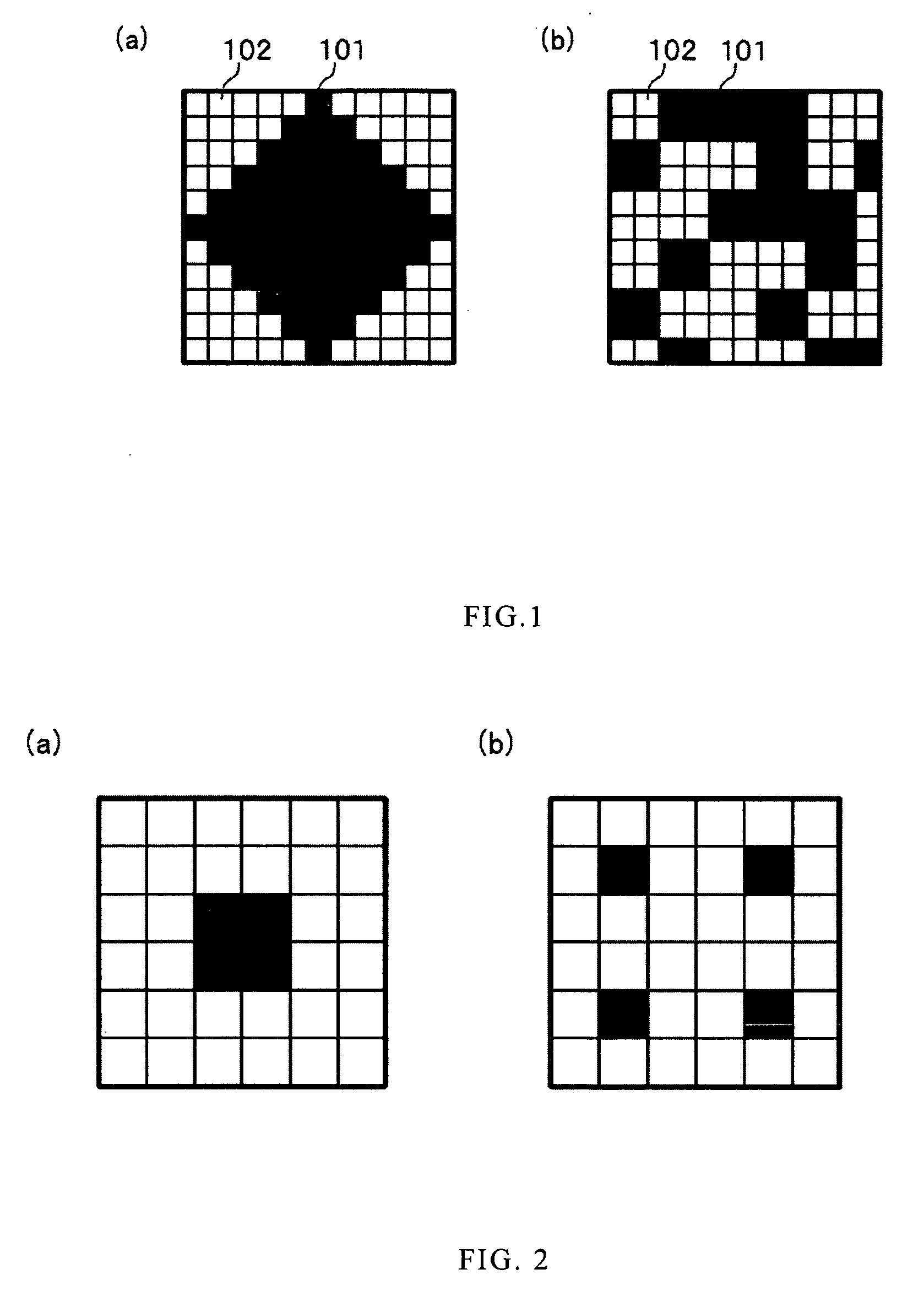
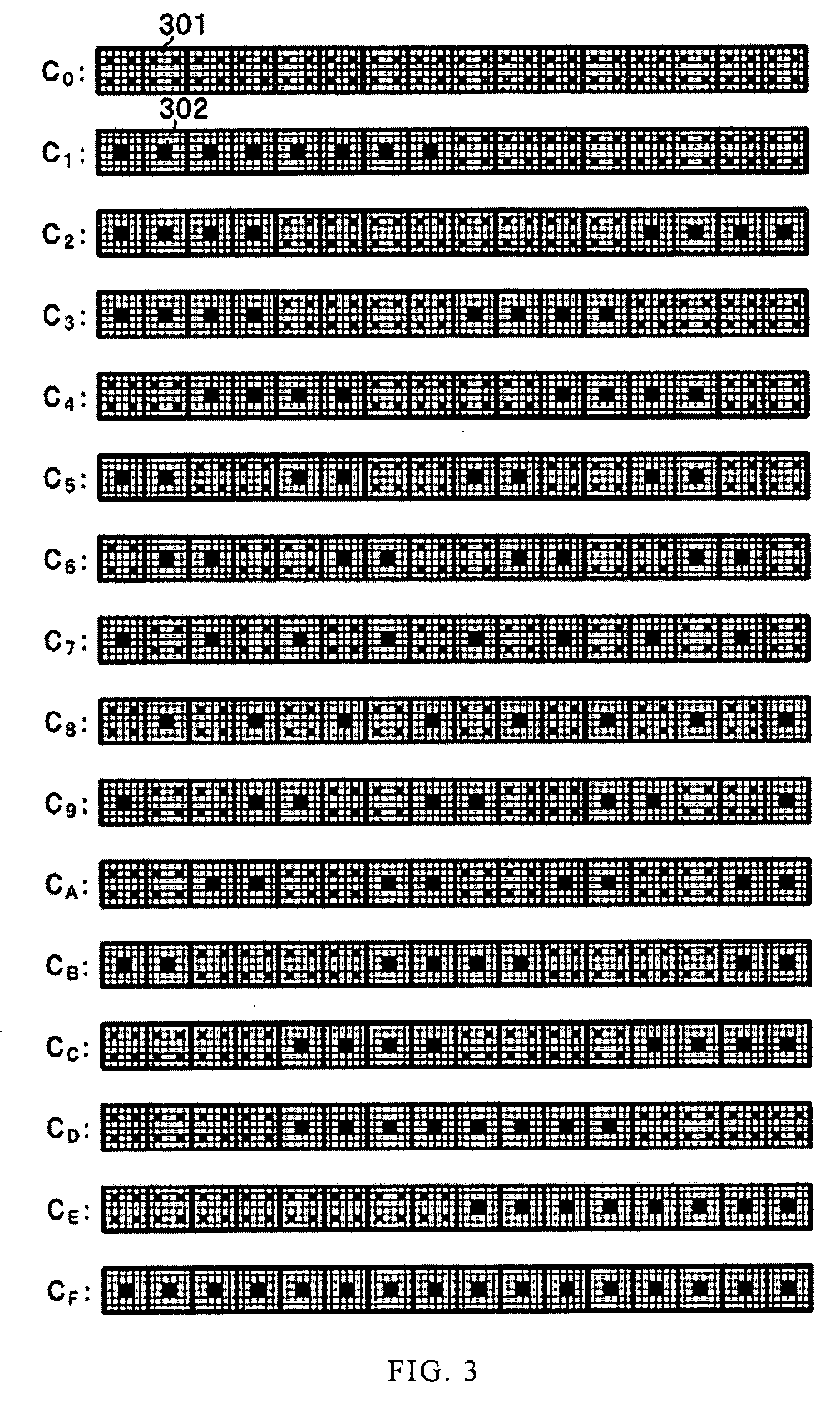
Embedding computer information into printed media and process method thereof
InactiveUS20060256386A1Increase valueDecryption be improvedDigitally marking record carriersDigital computer detailsPrint mediaHue
The present invention provides a method of generating information embedded halftone screen code. According to this method, massive digital information can be stored through printing on at least one type of print media, such as images, texts, symbols, background, and so on. And the information embedded can be read and recognized simply and reliably. Particularly, the quality of the images will not be reduced after information embedded. The information printed on the media comprises a predetermined array of halftone dots with different morphology including physical and geometrical characteristics, which forms the computer codes to embed information into printed content. The advantages of this invention are: the maximum similarity value can be reduced to under the threshold value according to this method; the recognition performance of the halftone screen code can be improved; and robustness can still be maintained at a high level even though the paper is defected or polluted. Besides, the quality of the image will not be lowered and the image can keep its original condition after information embedded.
Owner:GU ZECANG
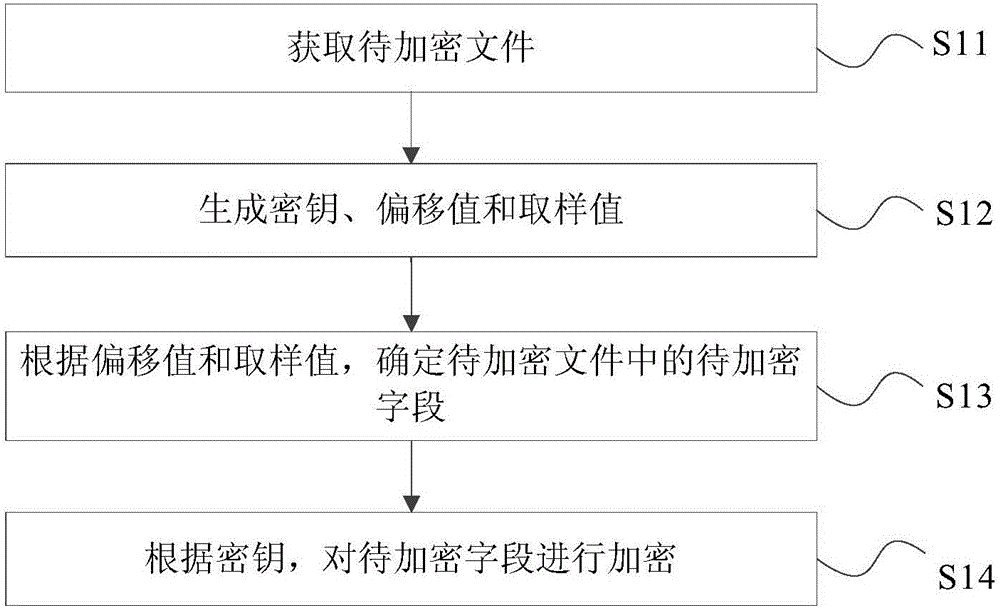
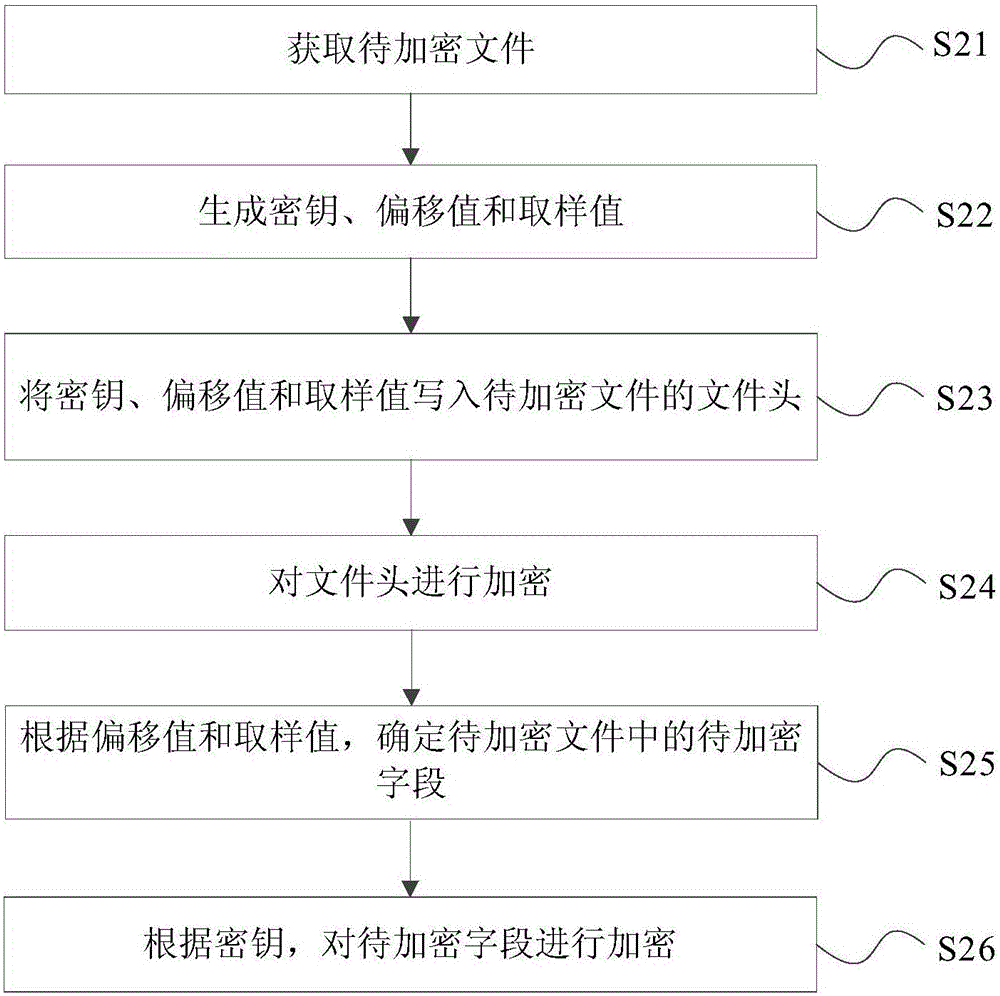
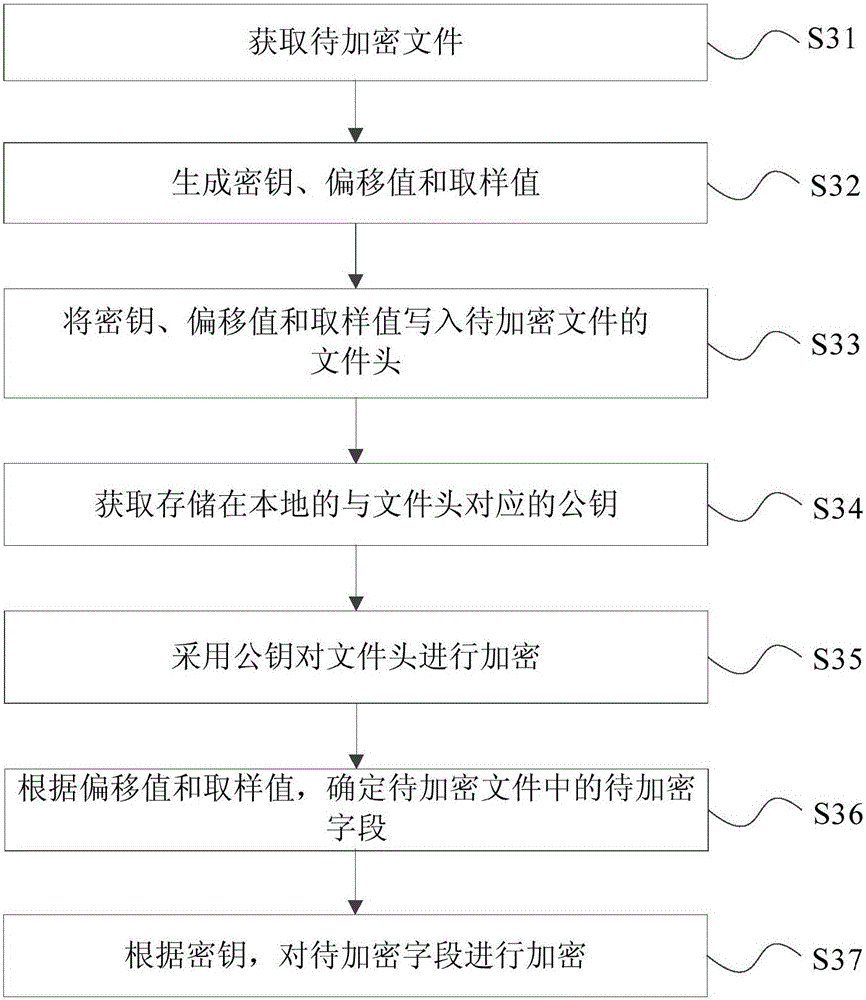
File encryption method, file decryption method, file encryption device and equipment
InactiveCN106372517AAvoid EncryptionImprove encryption efficiencyDigital data protectionComputer hardwareEncryption
The invention discloses a file encryption method, a file decryption method, a file encryption device and equipment. The method comprises the following steps: obtaining a to-be-encrypted file; generating a secrete key, an offset value and a sampling value; determining the to-be-encrypted field in the to-be-encrypted file according to the offset value and the sampling value; and encrypting the to-be-encrypted field according to the secrete key. According to the invention, the file encryption efficiency can be improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
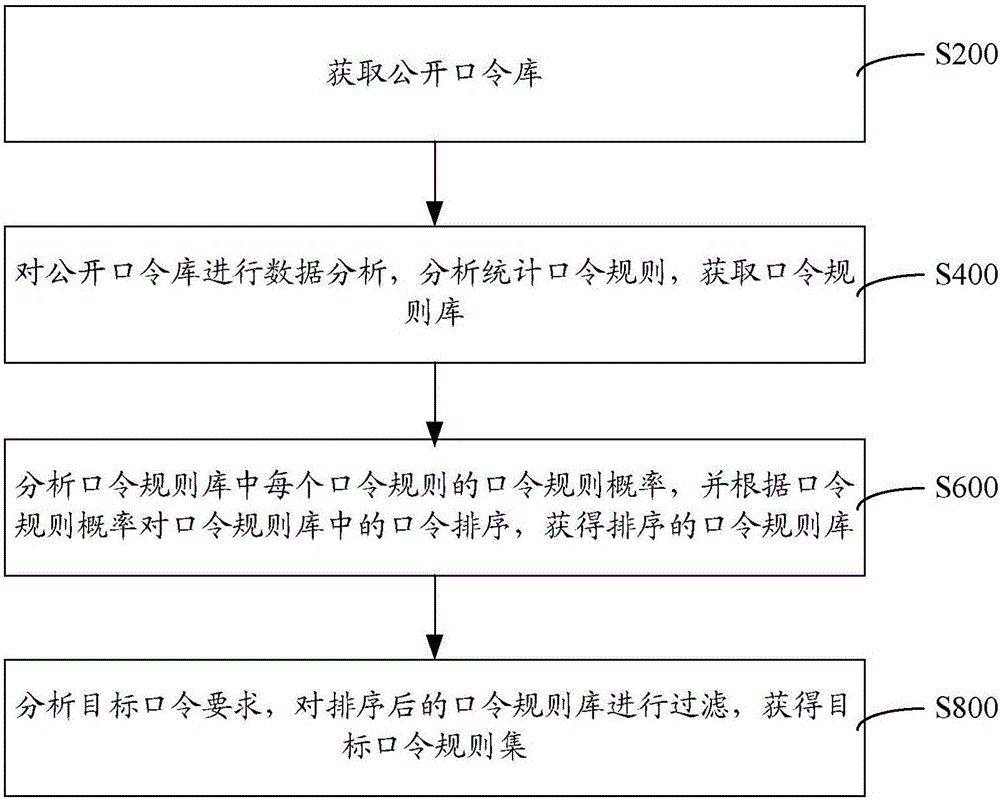
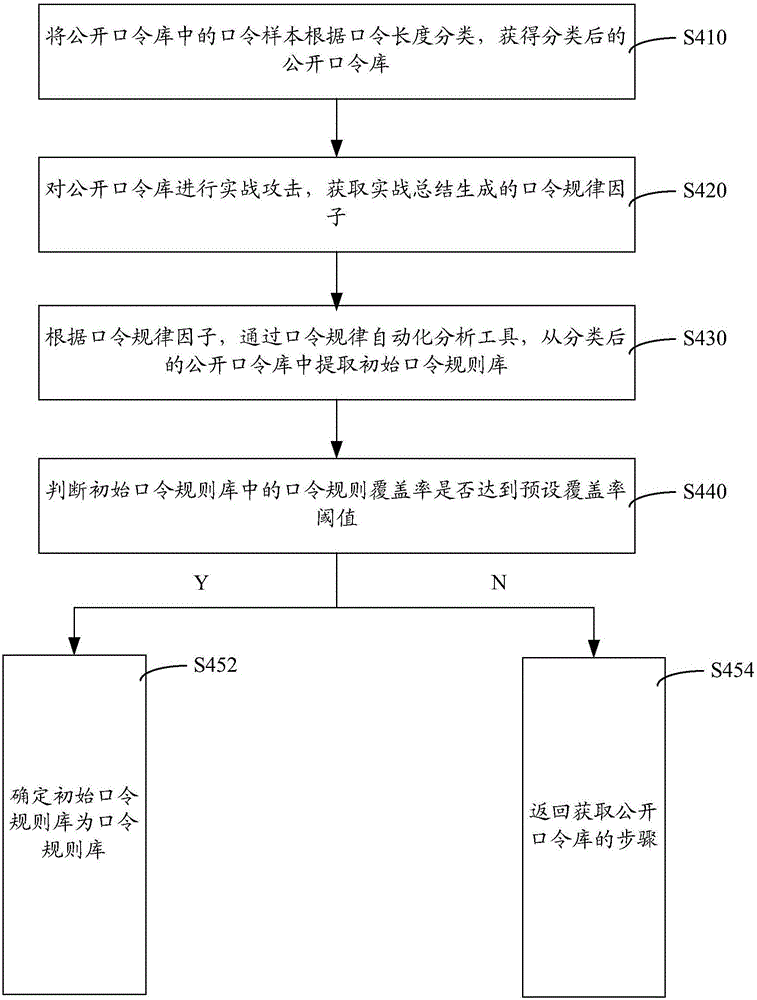
Method and system for obtaining target password rule set in exhaustion-method decryption
InactiveCN106559222AReduce the number of password attemptsImprove decryption efficiencyUser identity/authority verificationCryptographic attack countermeasuresPasswordSocial engineering (security)
The invention provides a method and system for obtaining a target password rule set in exhaustion-method decryption. A public password library is obtained; a data analysis is carried out on the public password library and analysis and statistic processing is carried out on password rules to obtain a password rule library; the password rule probability of each password rule in the password rule library is analyzed, password sorting in the password rule library is carried out based on the password rule probability, thereby obtaining a sorted password rule library; and a target password requirement is analyzed and the sorted password rule library is filtered to obtain a target password rule set. During the whole process, the password rule is analyzed based on the psychology and social engineering; and the target password rule set is determined by means of probability-based statistic sorting and filtering. Therefore, the number of passwords needed to be tried in exhaustion-method decryption can be reduced substantially, so that the efficiency of the exhaustion-method decryption can be improved substantially.
Owner:广东省信息安全测评中心 +1
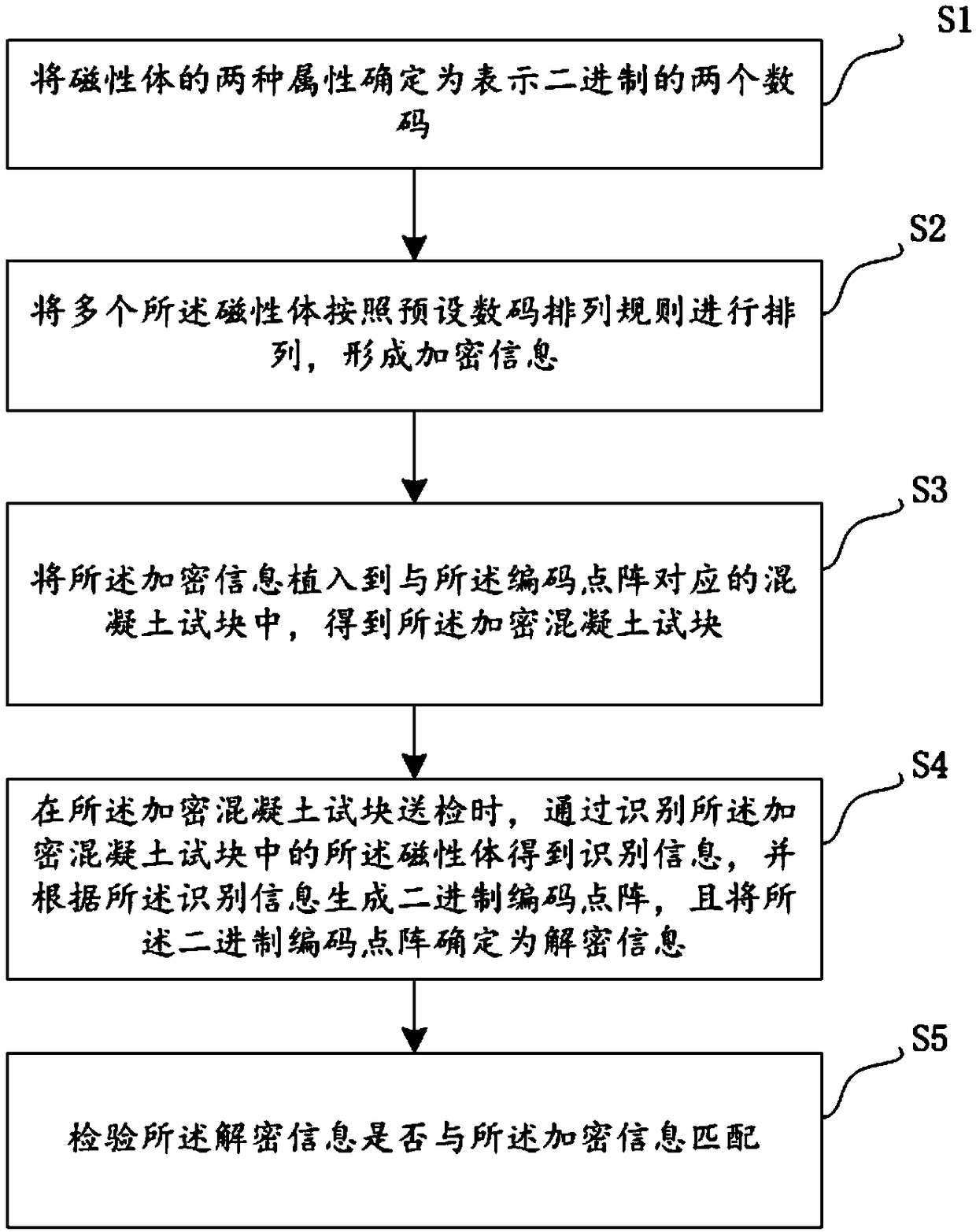
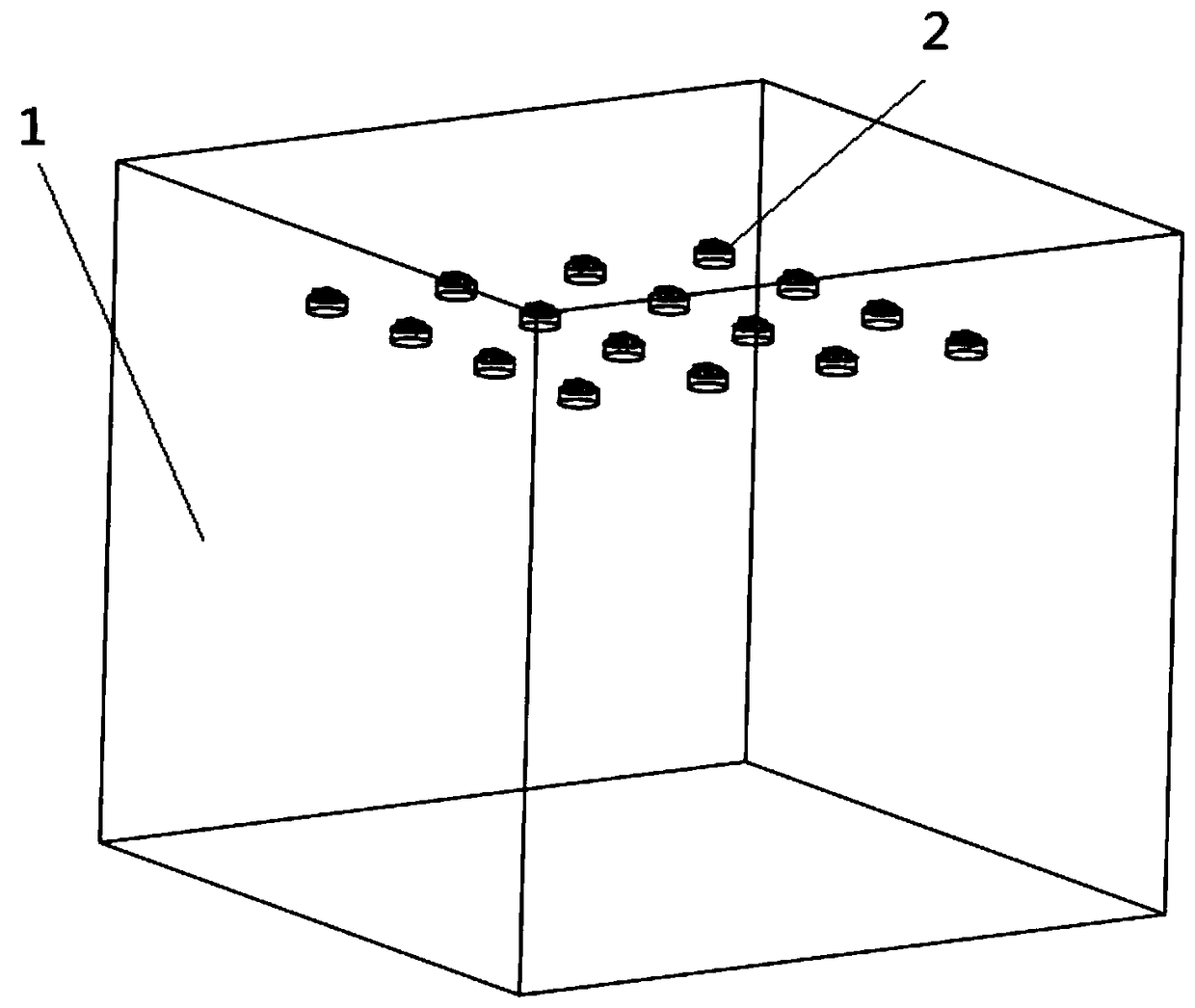
An intelligent management method and a system for a construction project concrete standard culture homoculture test block
InactiveCN109146712AImprove management efficiencyEnsure real qualityStampsData processing applicationsIntelligent managementComputer science
The invention relates to an intelligent management method and a system for a construction project concrete standard curing homoculture test block. The method comprises the following steps: S1, two attributes of a magnetic body being determined as two numbers representing binary; 2, arranging a plurality of magnetic bodies accord to a preset digital arrangement rule to form encrypted information; S3, embedding the encrypted information into the concrete test block corresponding to the encoded lattice to obtain the encrypted concrete test block; S4, when the encrypted concrete test block is sentfor inspection, identifying information obtained by identifying the magnetic body in the encrypted concrete test block, generating a binary encoded lattice according to the identifying information, and determining the binary encoded lattice as decryption information; 5, checking whether that decrypt information matches the encrypted information. Through the management method, the replacement of standard curing by the construction side and the submission of concrete test blocks under the same conditions are effectively prevented, and the concrete can not be tampered with after densification, thus ensuring the true quality of the construction project concrete.
Owner:四川广聚其力电子科技有限公司
Data processing method and device, computer storage medium and electronic equipment
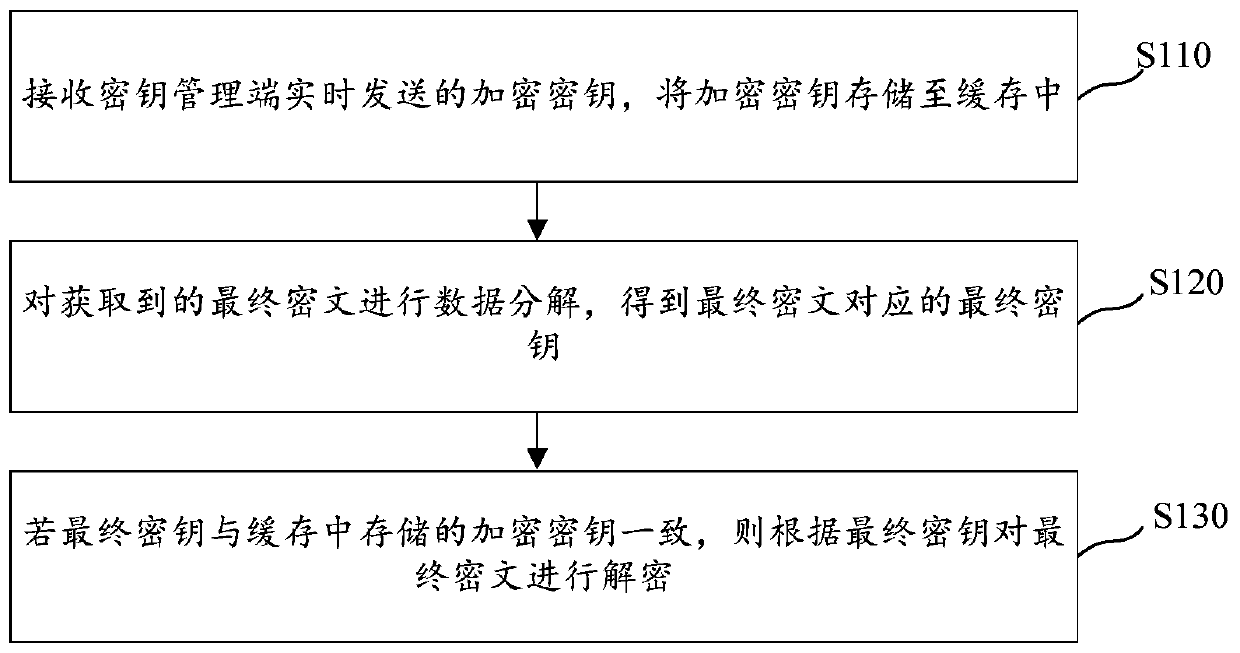
ActiveCN111131278AReal-time updateImprove decryption efficiencyKey distribution for secure communicationUser identity/authority verificationComputer hardwareTerminal server
The invention relates to the technical field of computers. The invention provides a data processing method, a data processing device, a computer storage medium and electronic equipment. The data processing method is applied to a terminal server for encrypting and decrypting data, the key type used for encryption and decryption processing is a symmetric key, and the data processing method comprisesthe following steps: receiving an encryption key sent by a key management end in real time, and storing the encryption key into a cache; performing data decomposition on the obtained final ciphertextto obtain a final key corresponding to the final ciphertext; and if the final key is consistent with the encryption key stored in the cache, decrypting the final ciphertext according to the final key. According to the data processing method, the security of the secret key can be guaranteed, the decryption speed can be increased, and the project cost is reduced.
Owner:JINGDONG TECH HLDG CO LTD
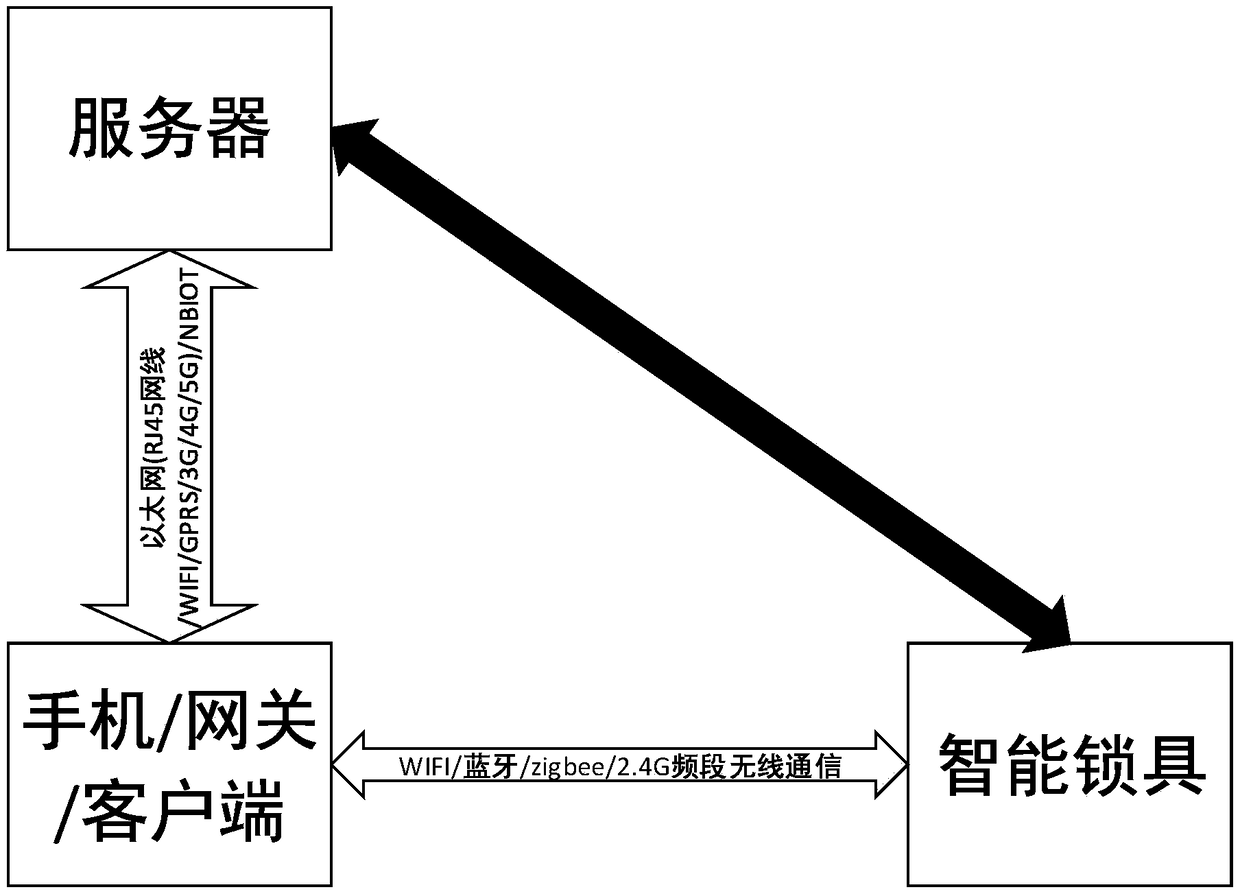
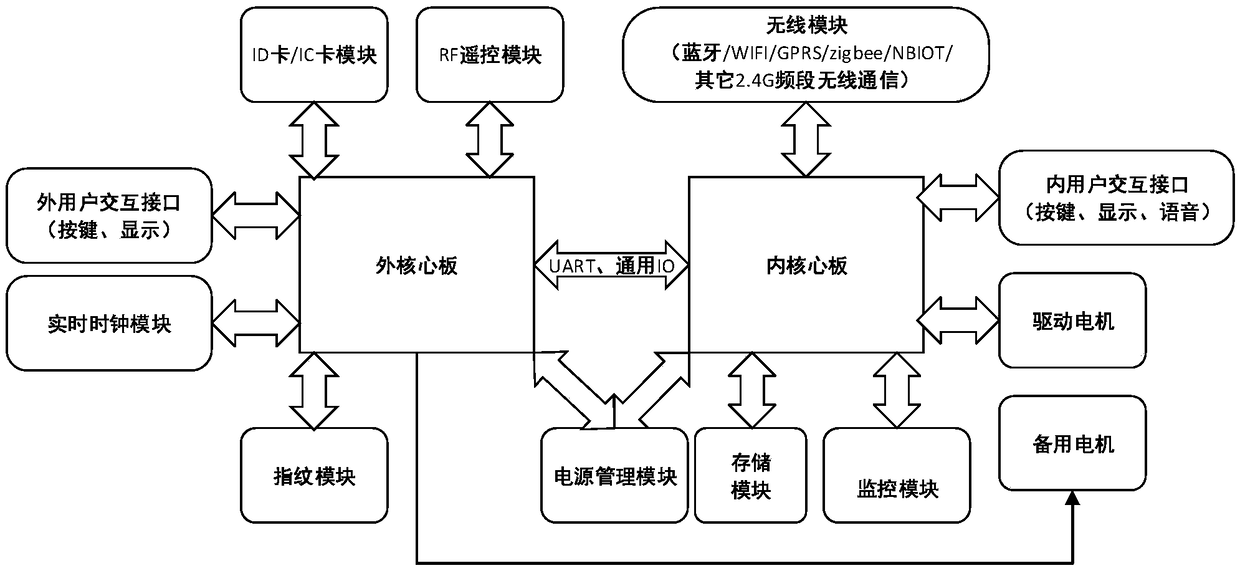
Intelligent lock data encrypted transmission method and leasing equipment applying same
ActiveCN109410396AIncrease the difficultyDetailed planIndividual entry/exit registersCurrent timeServer-side
The invention relates to an intelligent lock data encrypted transmission method and leasing equipment applying the same and belongs to the technical field of intelligent locksets. A complicated encryption algorithm is very difficult to realize through a calculation capability of an existing intelligent lock microcontroller and has certain safety risks. An initial value is solved by utilizing current time of a server side, a key (KEY) of data can be changed at any time and the difficulty of cracking the encrypted data is enhanced; meanwhile, two initial values are solved by the intelligent lockset according to local time and the encrypted data is decrypted; effective data is determined through comparing decrypted verification codes; the scheme is detailed and feasible; a locket key does notneed to be distributed; the encryption and decryption efficiency of the data can be extremely improved; the method is easily realized on the microcontroller and has the advantages of small occupationof microcontroller RAM (Random Access Memory) and FLASH resources, rapid calculation speed and the like, and the safety of the intelligent lock in the aspect of communication is improved.
Owner:ZHEJIANG HONGLI LOCKS
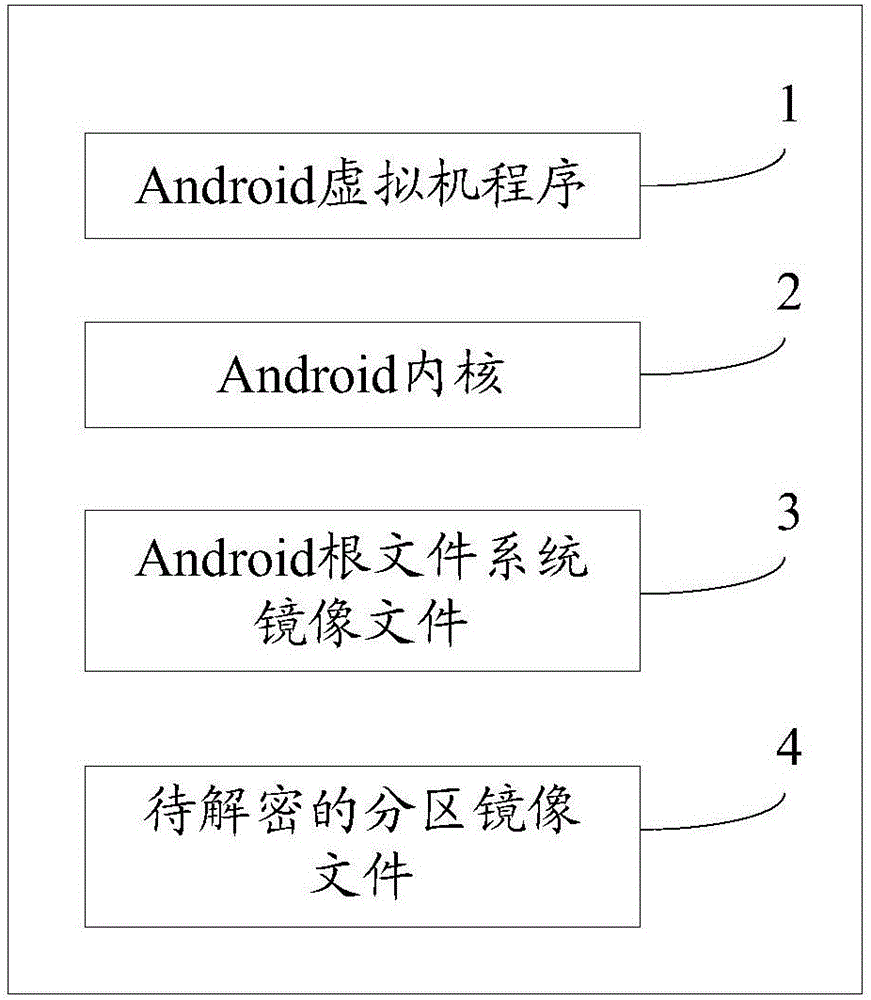
Reduction method and device for Android terminal full-disk enciphered data
The invention provides a reduction method and device for Android terminal full-disk enciphered data. The method comprises the following steps of: constructing an Android virtual machine program used for starting an Android kernel; starting the Android virtual machine program; initializing the Android kernel by the Android virtual machine program; loading an Android root file system mirror image file; operating a program in the Android root file system mirror image file; on the basis of a configuration script in the Android root file system mirror image file, loading a partitioning mirror image file to be decrypted; starting corresponding system basic service; on the basis of the system basic service, reading the partitioning mirror image file to be decrypted; on the basis of a user encryption secret key corresponding to the partitioning mirror image file to be decrypted, generating a middle secret key by the Android kernel; and on the basis of the middle secret key, decrypting the read partitioning mirror image file to be decrypted.
Owner:XIAMEN MEIYA PICO INFORMATION
Rainbow table parallel system design method and device based on MapReduce
InactiveCN104281816AControl overlap problemImplement parallel readsProgram initiation/switchingDigital data protectionData vectorRainbow
The invention discloses a rainbow table parallel system design method and device based on MapReduce. The design method includes a rainbow table data generation step and a rainbow table decryption step; the method includes aiming to each rainbow chain of a rainbow table, allowing a map module to acquire a chain head node data vector and chain end node data vector of the rainbow chain, recording the chain head node data vector as (img file = 'DDA0000586158180000011.TIF' wi = '88' he = '72' / ), recording the chain end node data vector as (img file = 'DDA0000586158180000012.TIF' wi = '95' he = '66' / ), adopting EPi as Key, adopting SPi as Value, and transmitting <EPi, SPi> data to a Reduce module of the rainbow chain; allowing the Reduce module of the rainbow chain to reorganize the <EPi, SPi> data, acquiring a data structure that (img file = 'DDA0000586158180000013 .TIF 'wi =' 400 'he =' 72 ' / ), presenting a chain table as (img file =' DDA0000586158180000014.TIF 'wi =' 238 'he =' 68 ' / ), and allowing the value of the chain table to be a set of chain head node data vectors of the rainbow table with all chain end node data vectors serving as the EPi; inserting all reorganized rainbow table data and fresh & lt; Key, Value & gt; data into a database NoSQL; analyzing Hash H0 to be decrypted, and mapping the H0 as nodes Nodei of the rainbow chain; converting the Nodek as the chain end node data vectors EP'i; adopting the EP'i as the key to read the reorganized rainbow chain data from the database NoSQL, and analyzing and acquiring the H0 passwords.
Owner:XIAMEN ZHIXIN TONGCHUANG NETWORK TECH
Method for scheduling decryption machines
ActiveCN103530929AImprove utilization efficiencyImprove decryption efficiencyPaper-money testing devicesData informationCiphertext
The invention relates to a method for scheduling decryption machines. The method comprises: step 1, a receiver receiving invoice data information comprising invoice ciphertexts; step 2, the receiver querying the working state table of the decryption machines, determining whether there are decryption machines at idle working states, and if there are such idle decryption machines, selecting one as a specified decryption machine, wherein the decryption machine working state table comprises the working states of all the decryption machines, and the working states of the decryption machines comprise an idle state and a busy state; step 3, the server sending the invoice ciphertexts to the specified decryption machine and changes the working state of the specified decryption machine from the idle state to the busy state in the decryption machine working state table; step 4, the specified decryption machine decrypting the invoice ciphertexts and sending obtained invoice decryption information to the server; and step 5, the server, after receiving the invoice decryption information, changes the working state of the specified decryption machine from the busy state to the idle state in the decryption machine working state table. By using the method provided by the invention, the utilization efficiency of the decryption machines can be enhanced and the decryption efficiency can be improved.
Owner:AEROSPACE INFORMATION
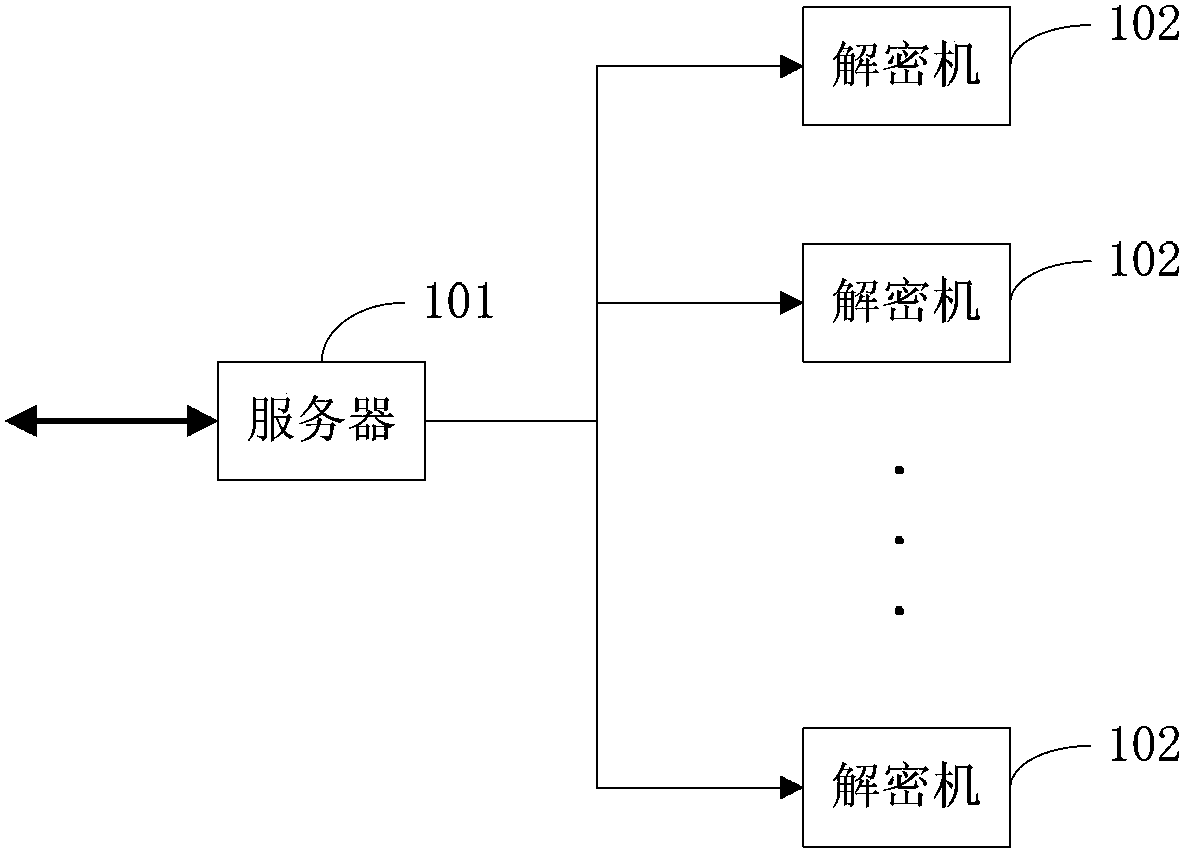
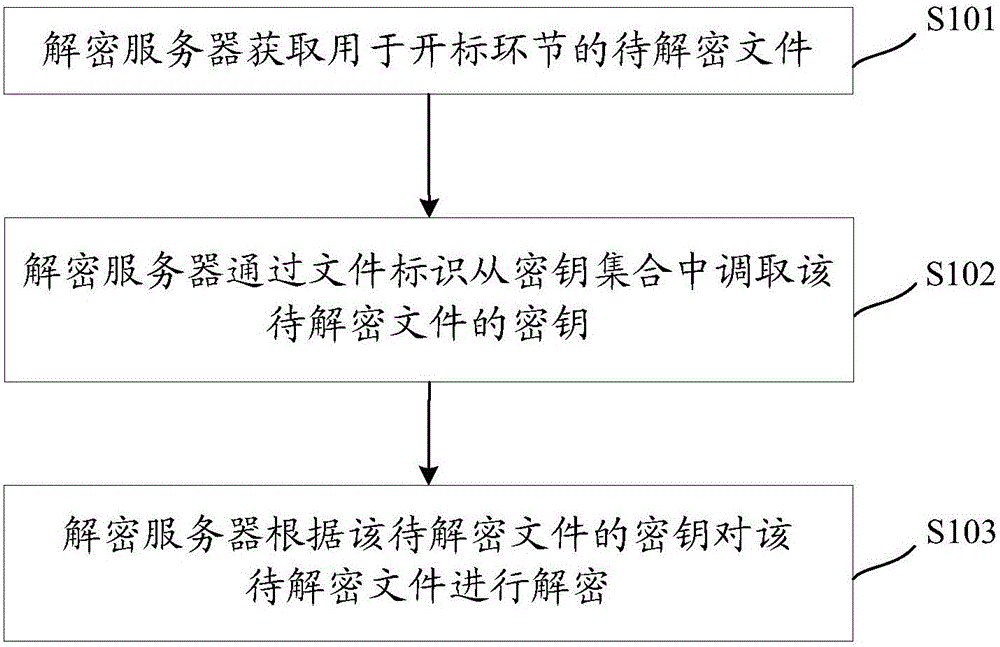
File decryption method and device
The embodiment of the invention discloses a file decryption method and device. A secret key used for decryption is pre-stored in a secret key set configured in a decryption server. The decryption server can schedule the secret key of a file to be decrypted from the secret key set according to the file identifier of the file to be decrypted when the batch file decryption process is performed in the bid opening link, and the file to be decrypted is decrypted so that file decryption of the bid opening link does not depend on participation of client sides, unified file decryption is performed through the decryption server directly and thus the file decryption efficiency of the bid opening link can be greatly enhanced.
Owner:BEIJING GUODIANTONG NETWORK TECH CO LTD +2
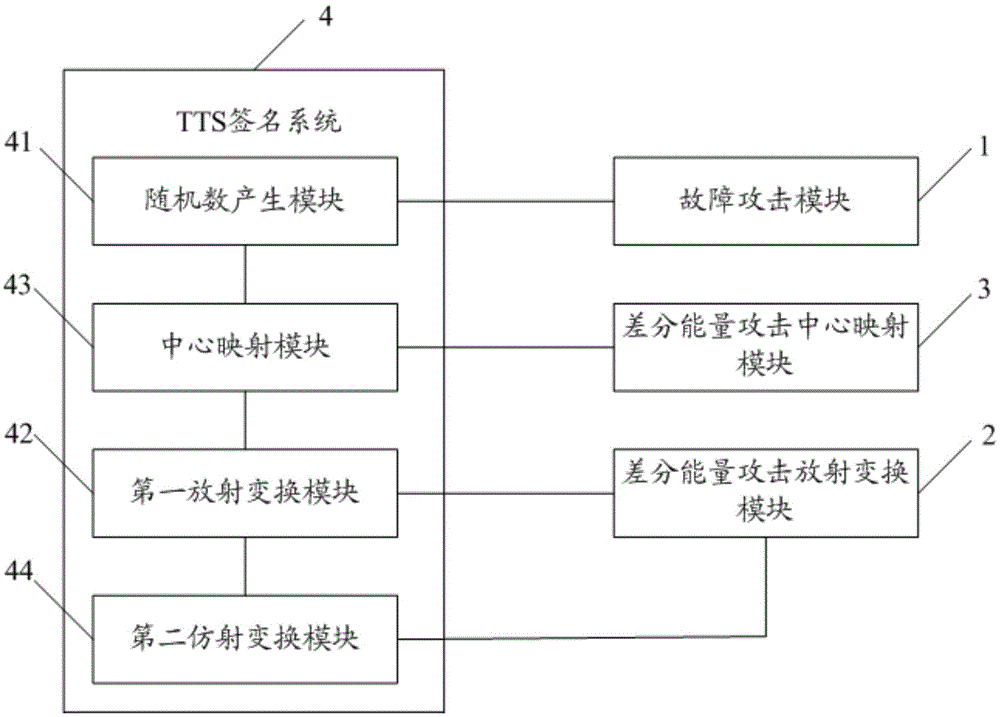
Decryption method for TTS signature
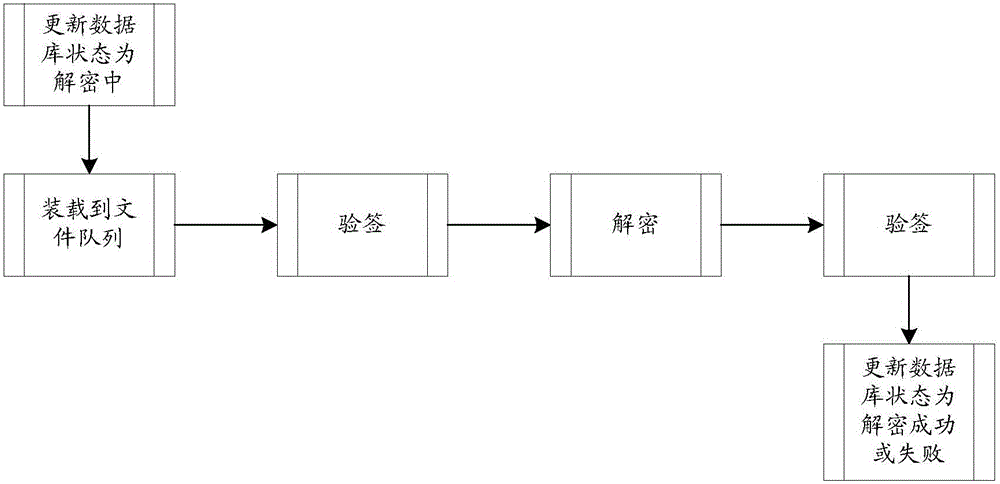
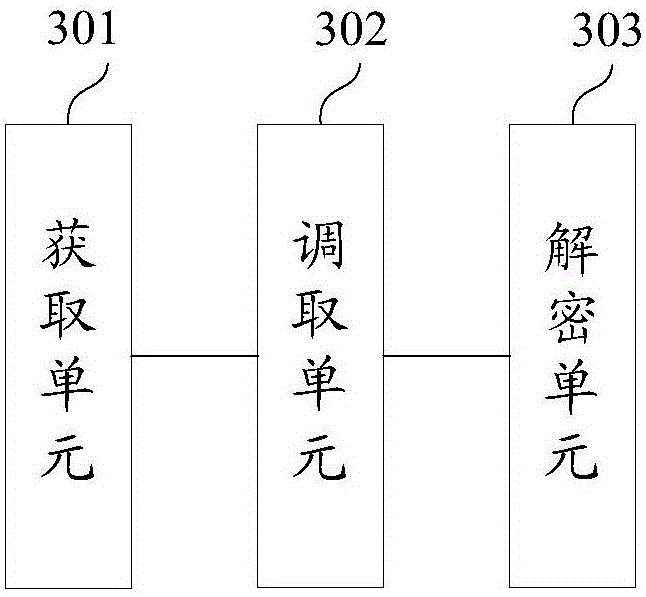
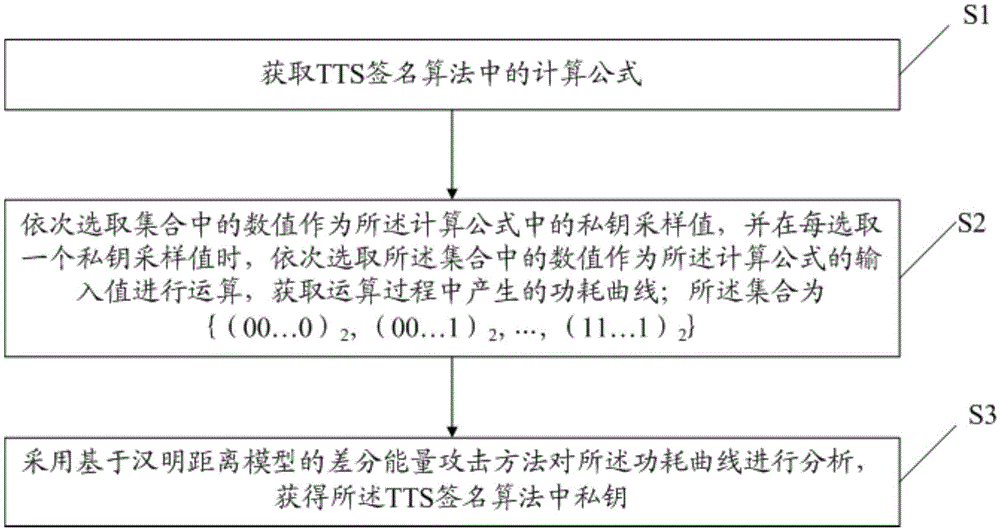
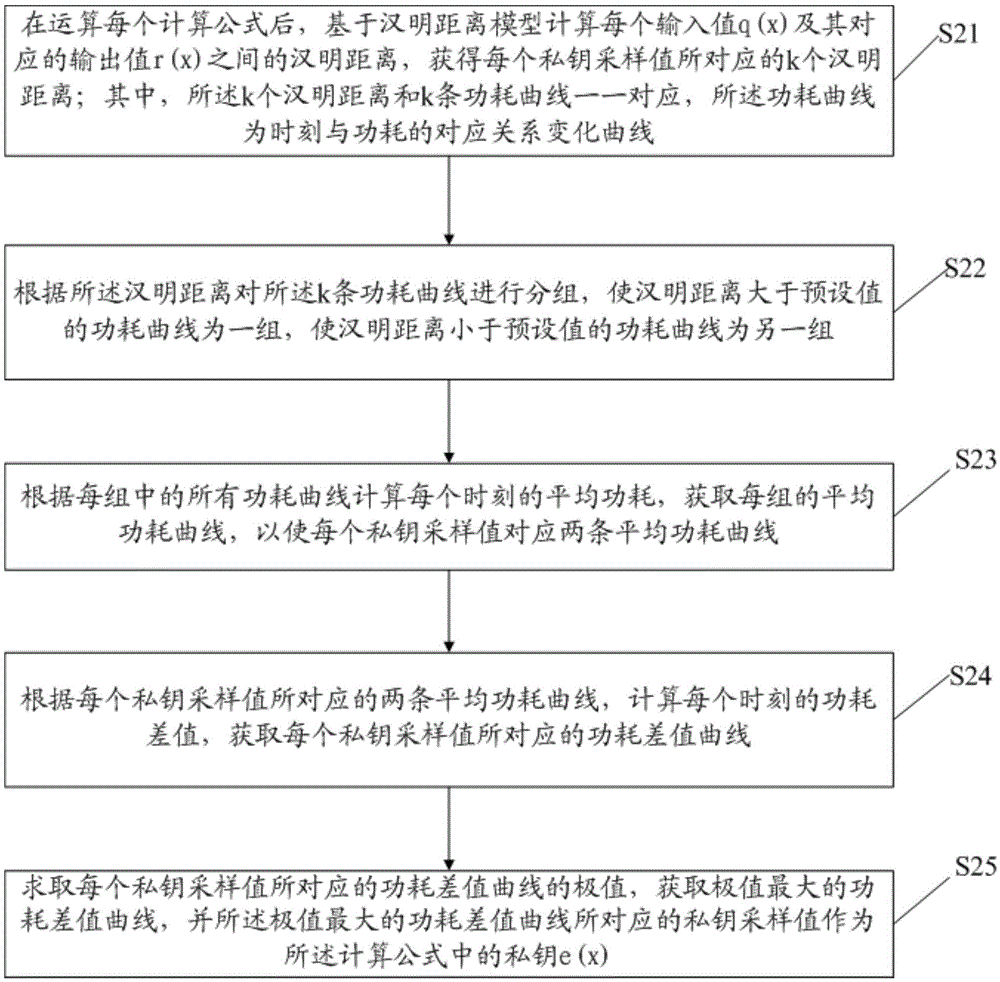
InactiveCN105530091ADecryption implementationImprove decryption efficiencyKey distribution for secure communicationTheoretical computer scienceHamming distance
The invention discloses a decryption method for a TTS signature, comprising steps of obtaining a calculation formula in the TTS signature algorithm, successively choosing numerical values in a set as private key sampling values in the calculation formula, successively choosing the numerical value from the set as an input value of the calculation formula to perform operation when each private key sampling value is chosen so as to obtain the power consumption curve generated during the operation process, wherein the set is ((00...0)2, (00...1)2, ...,(11...1)2), and adopting a differential energy attack method based on a Hamming distance model to perform analysis on the power consumption curve to obtain the private key in the TTS signature algorithm. The embodiment of the invention can improve the decryption efficiency of the TTS signature.
Owner:易海博
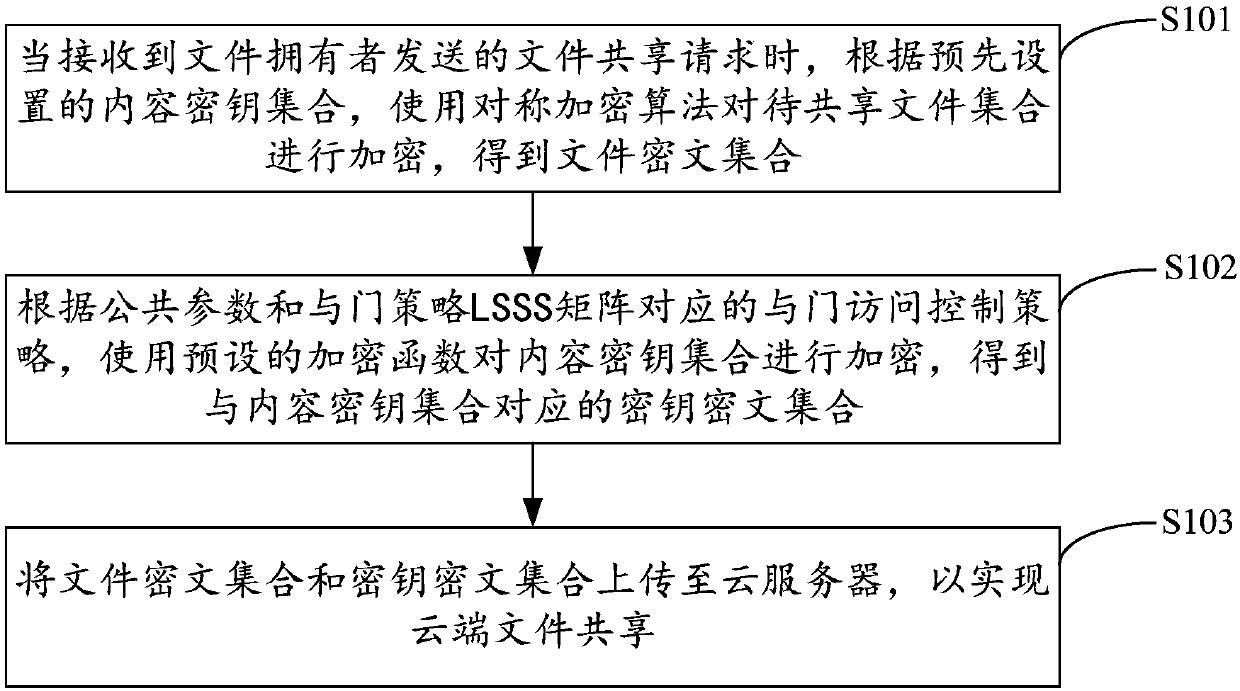
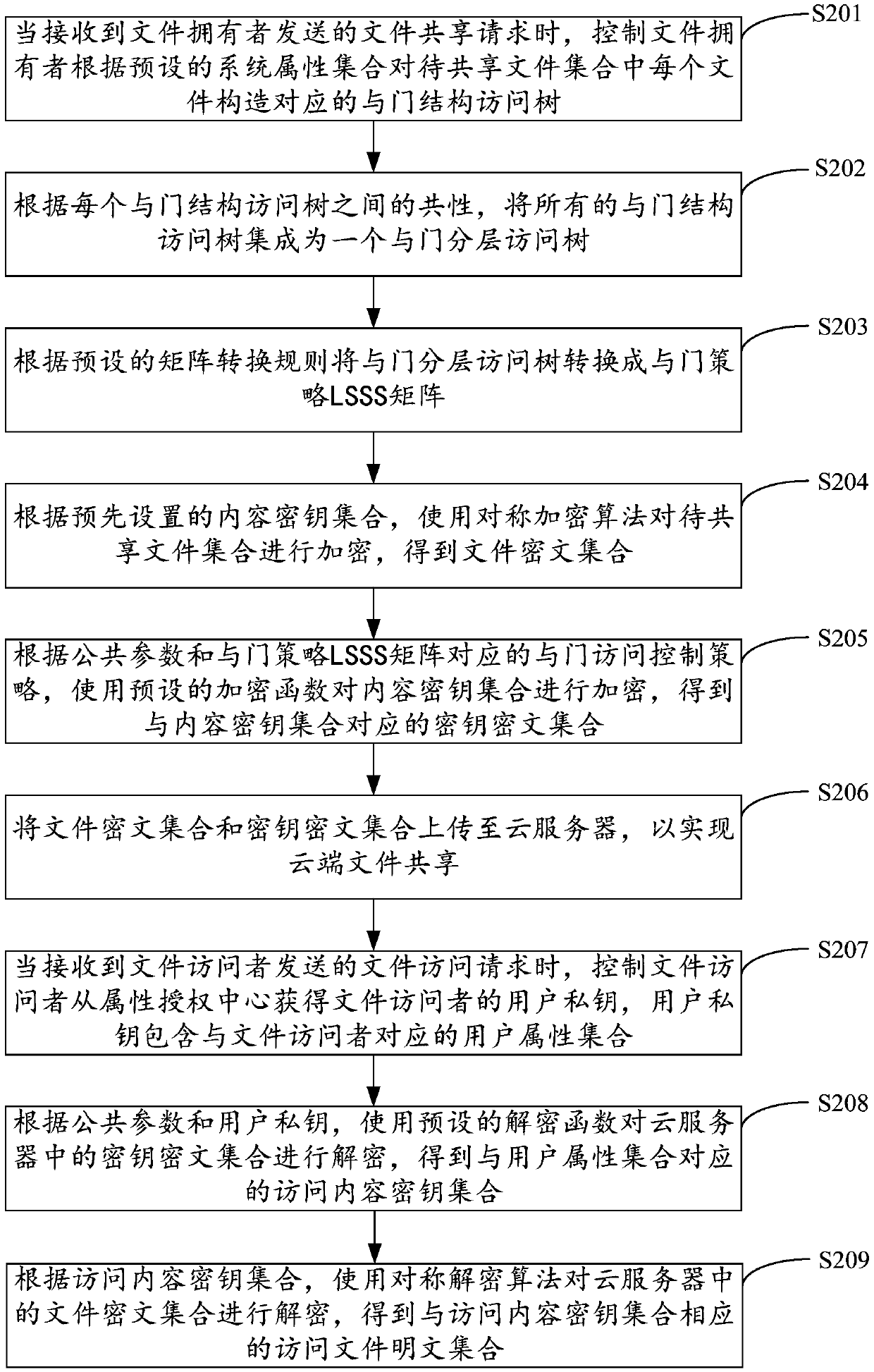
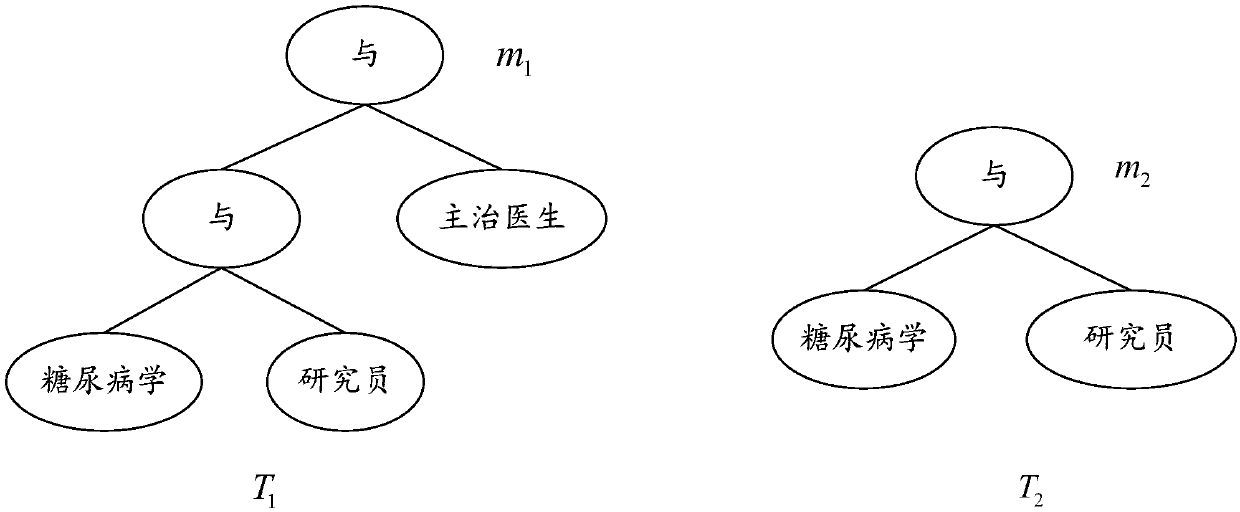
File sharing methods and devices based on CP-ABE (Ciphertext Policy-Attribute Based Encryption) layered access control, equipment and medium
ActiveCN109617855AReduce storage overheadImprove encryption efficiencyTransmissionAttribute-based encryptionMedia access control
The invention applies to the technical field of ciphertext access control and provides a file sharing methods and devices based on CP-ABE (Ciphertext Policy-Attribute Based Encryption) layered accesscontrol, equipment and a medium. A method comprises the steps of when a file sharing request sent by a file owner is received, according to a content key set, encrypting a to-be-shared file set through utilization of a symmetric encryption algorithm, thereby obtaining a file ciphertext set; according to public parameters and an AND gate access control policy corresponding to an AND gate policy LSSS (Linear Secret Sharing Scheme) matrix, encrypting the content key set through utilization of an encryption function, thereby obtaining a key ciphertext set corresponding to the content key set; ad uploading the file ciphertext set and the key ciphertext set to a cloud server, thereby realizing cloud file sharing. Ciphertext layered access is realized through CP-ABE, moreover, storage cost, communication cost and decryption computing complex of ciphertexts are reduced, and encryption efficiency, decryption efficiency and data sharing security degree are improved.
Owner:SHENZHEN TECH UNIV
Color image quick encryption method
InactiveCN104077739AChange positionImprove securityImage data processing detailsPattern recognitionColor image
The invention discloses a color image quick encryption method implemented on the basis of Arnold transform. The method includes the steps that an image is chunked according to the size of the image before encryption, then positions and gray levels of three primary color components of an image pixel are scrambled at the same time by means of Arnold transform to achieve encryption of the color image, and inverse transformation is carried out on transform in the preceding steps to decrypt the encrypted image. Through improvement of the prior art, the encryption effect is improved, encryption efficiency is improved, and the application range is widened.
Owner:APPLIED TECH COLLEGE OF SOOCHOW UNIV
Aggregation method for multi-dimensional data encryption and decryption in intelligent power grid
ActiveCN110110537AImprove production efficiencyLighten the computational burdenData processing applicationsDigital data protectionCiphertextPassword
The invention discloses an aggregation method for multi-dimensional data encryption and decryption in an intelligent power grid. The aggregation method comprises the following steps: 1, respectively generating an encrypted public key and a decrypted private key of power utilization data by utilizing a Chinese remainder theorem; 2, generating a public key and a private key of the password system; 3, encrypting the power utilization data; 4, respectively aggregating the ciphertext and the ciphertext decryption parameters; 5, decrypting the aggregated ciphertext; 6, solving a discrete logarithm for the intermediate ciphertext; and 7, decrypting the mixed ciphertext. In the key generation process, the encrypted public key and the decrypted private key of the power consumption data are generated by utilizing the Chinese remainder theorem, so that the key generation efficiency is improved, and the calculation burden of a control center and the risk of data leakage are reduced. In the decryption process, only one discrete logarithm needs to be obtained for the intermediate ciphertext, the decryption efficiency of the aggregated ciphertext is improved, and finally the efficiency of the whole data aggregation process is improved.
Owner:XIDIAN UNIV
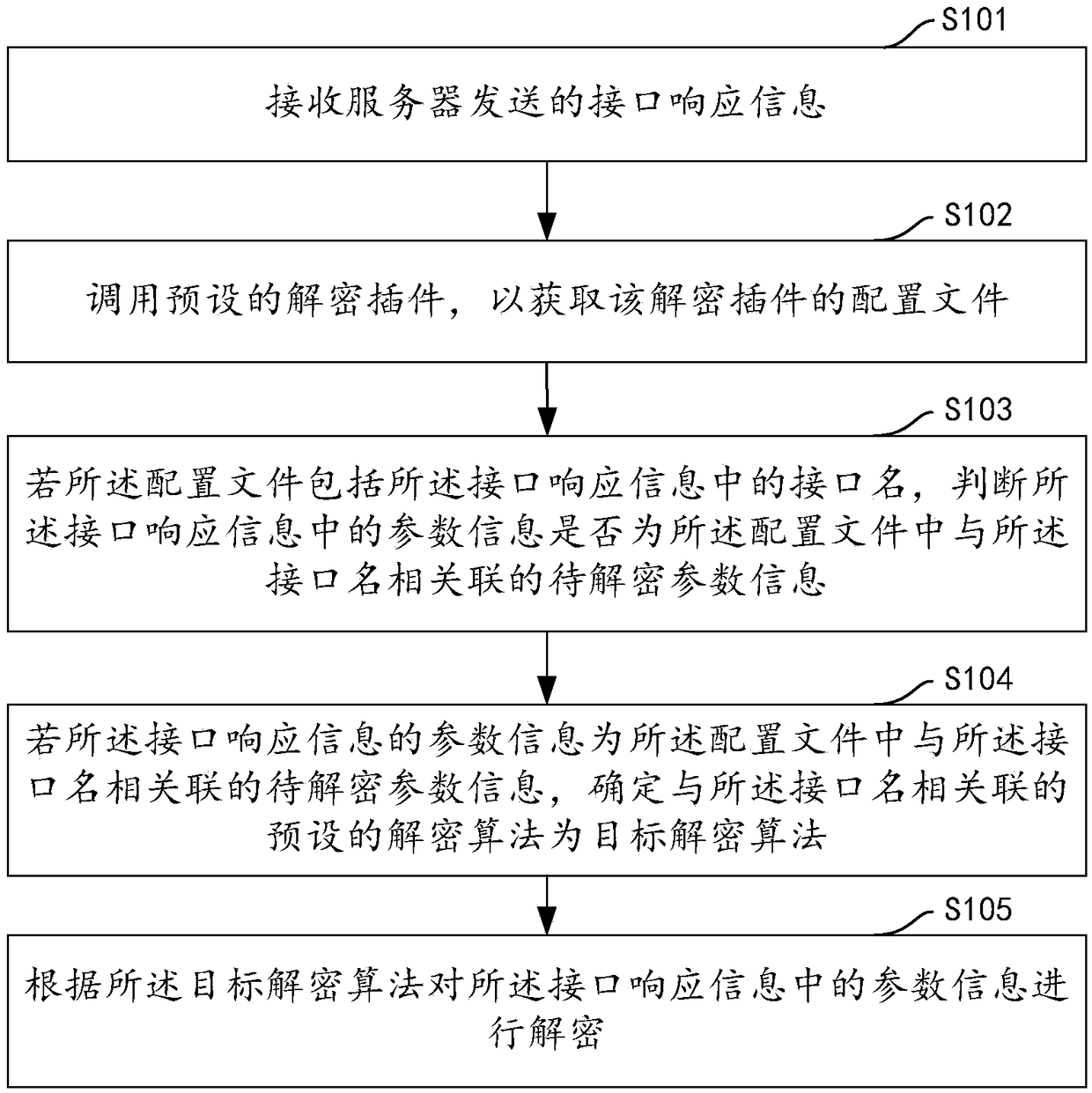
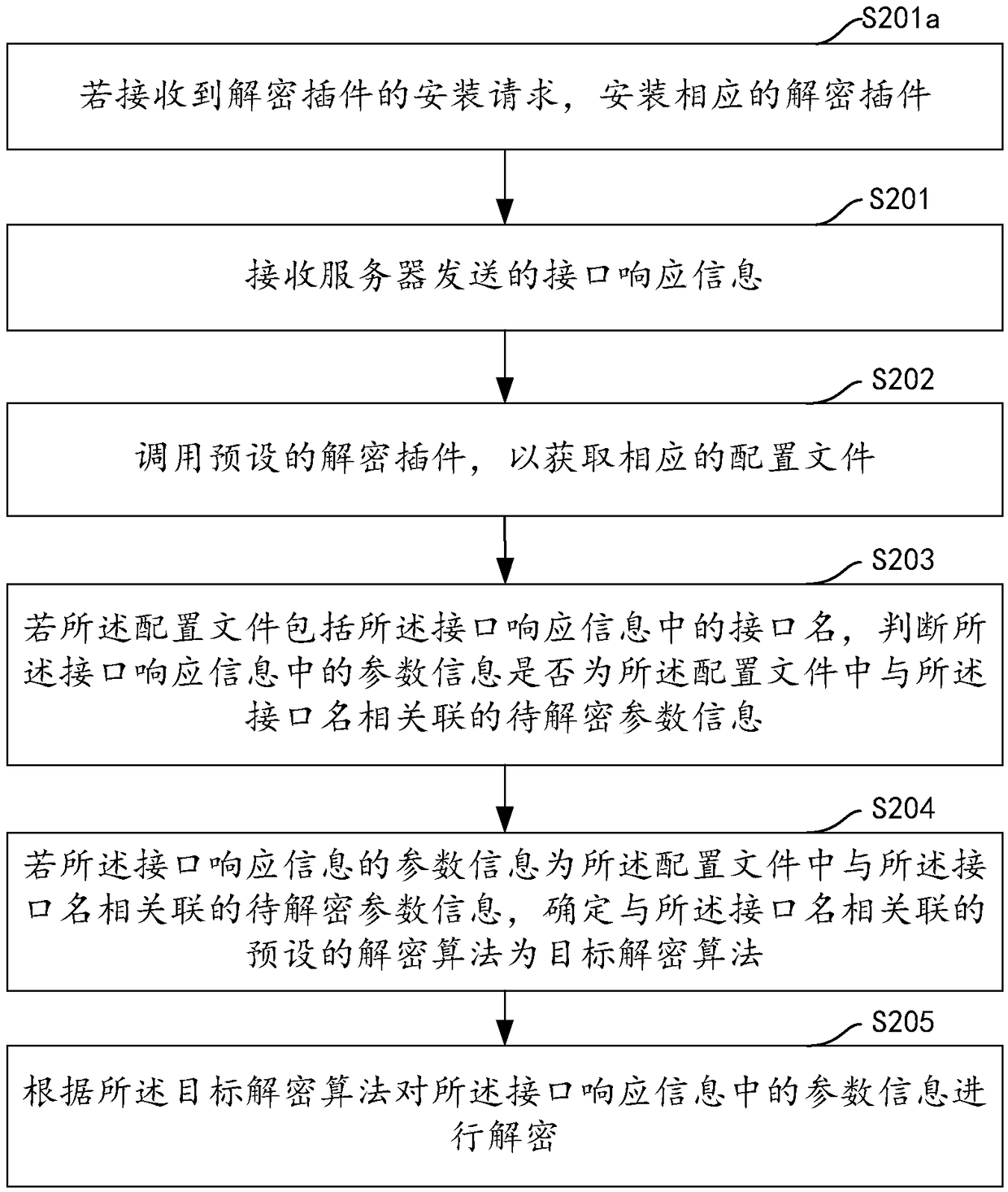
Interface parameter decryption method and device, computer device and storage medium
ActiveCN109274656AImprove decryption efficiencyDecryption is fast and accurateTransmissionSoftware engineeringComputer device
The embodiment of the invention discloses an interface parameter decryption method and device, a computer device and a storage medium, wherein, the method comprises receiving interface response information sent by a server; calling a preset decryption plug-in to obtain a configuration file of the decryption plug-in; if the configuration file includes an interface name in the interface response information, judging whether parameter information in the interface response information is parameter information to be decrypted associated with the interface name in the configuration file; if parameter information of the interface response information is parameter information to be decrypted associated with the interface name in the configuration file, determining a preset decryption algorithm associated with the interface name as a target decryption algorithm; decrypting the parameter information in the interface response information according to the target decryption algorithm. The inventioncan improve the accuracy and efficiency of parameter decryption, and greatly improves the user's use experience and work efficiency.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Multi-authorization access control system and method based on attribute encryption
InactiveCN110830473AImprove encryptionImprove decryption efficiencyKey distribution for secure communicationUser PrivilegeCiphertext
The invention relates to a multi-authorization access control system and method based on attribute encryption, and the system and method employ an LSSS linear secret sharing model to replace an NAND gate model of shamir, and effectively improve the encryption and decryption efficiency of information. According to the method and the system, a secret key generation mode of multiple authorization centers is realized, a user collusion attack mode can be well defended, ciphertext encryption of data information is realized in DO, and the purpose of performing data encryption on the data informationis achieved. In each AA, an attribute set which is more owned by each independent user is generated to generate an independent corresponding secret key, and fine grit management of user permission control is realized.
Owner:ZHEJIANG UNIV OF TECH
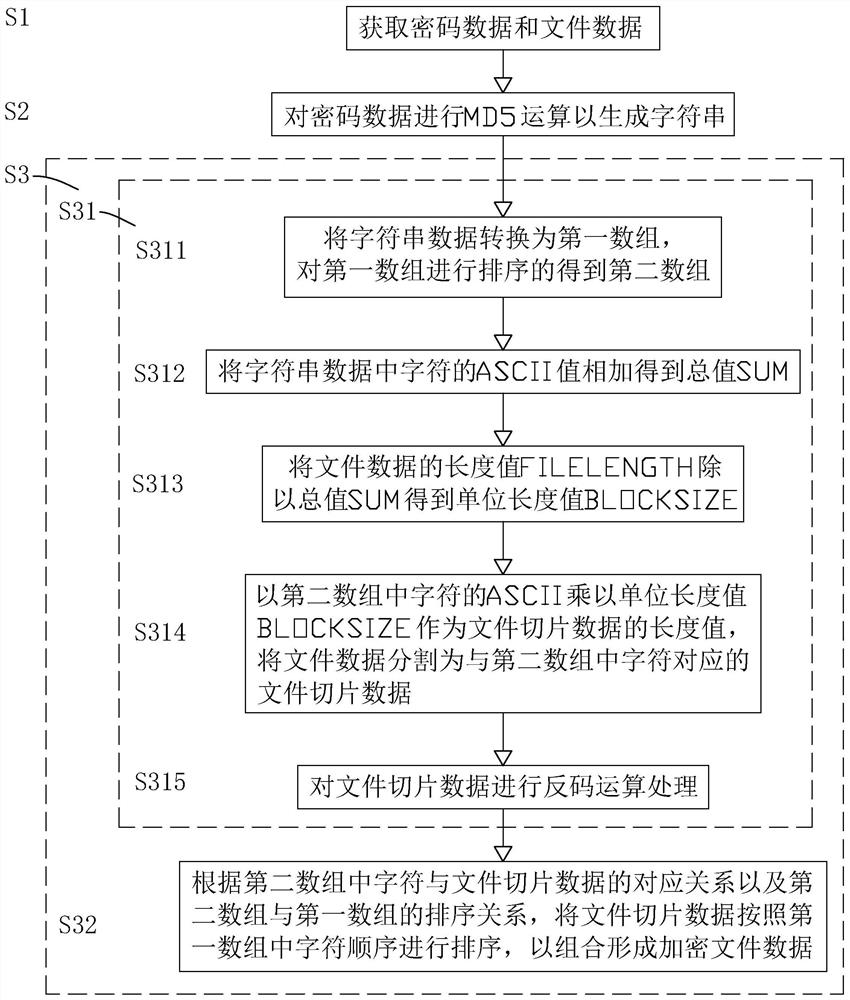
Slice file encryption method and decryption method, storage medium and electronic equipment
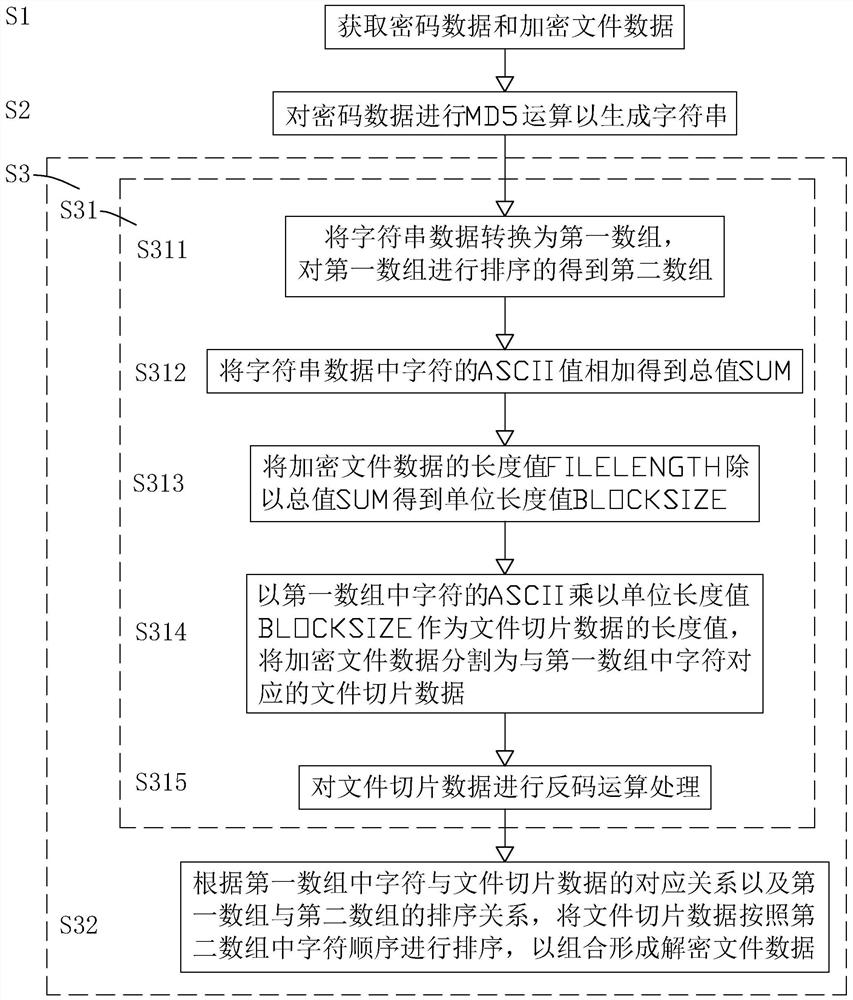
PendingCN114168976AImprove encryption efficiencyImprove decryption efficiencyDigital data protectionNatural language data processingComputer hardwareAlgorithm
The invention discloses a slice file encryption method, a slice file decryption method, a storage medium and electronic equipment. The slice file encryption method comprises the following steps: acquiring password data and file data; performing algorithm operation on the password data to generate character string data; and segmenting the file data according to the character string data to form multiple pieces of file slice data, and sorting and combining the multiple pieces of file slice data according to the character string data to form encrypted file data. The character string data is generated by performing algorithm operation on the password data, and the file data is segmented, sorted and recombined according to the character string data so as to form the encrypted file data, so that only algorithm operation is required to be performed on the password data, encryption algorithm operation is not required to be performed on the whole file data, and the encryption efficiency is improved.
Owner:GUANGDONG NENGLONG EDUCATION
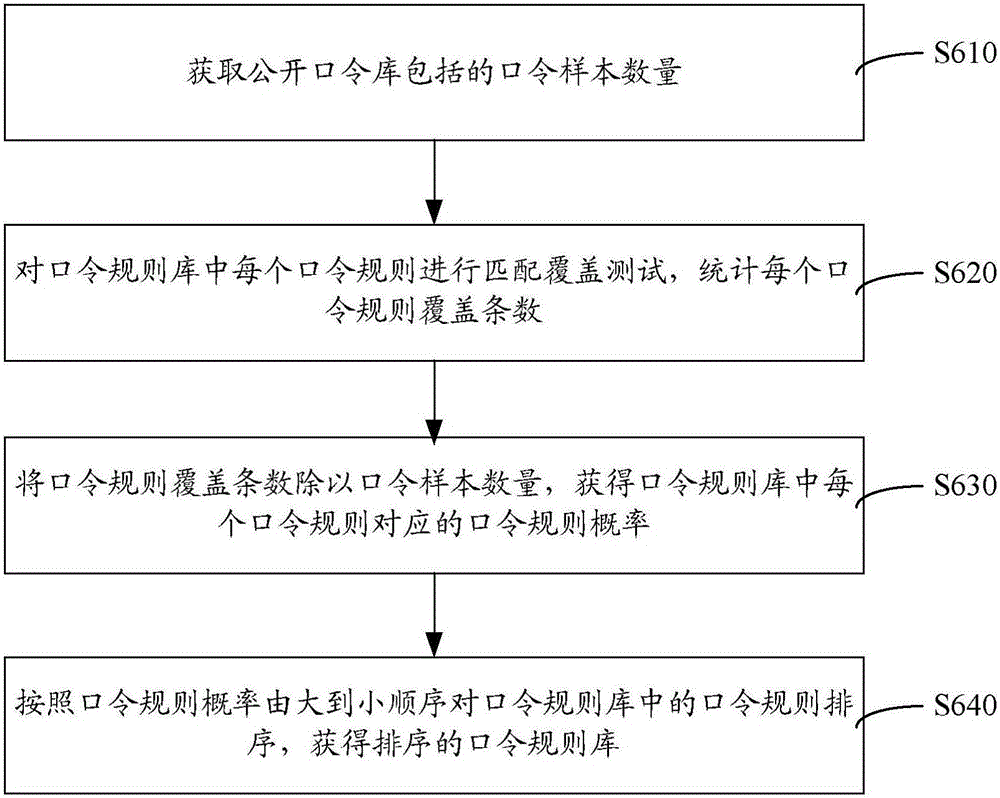
Statistics and analysis method and statistics and analysis device for computer passwords
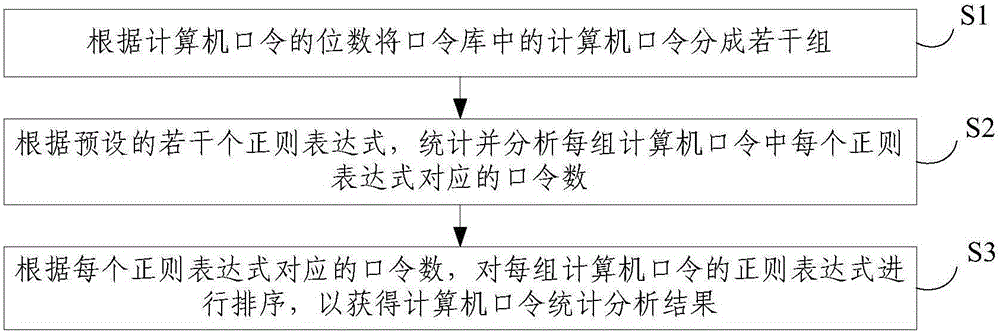
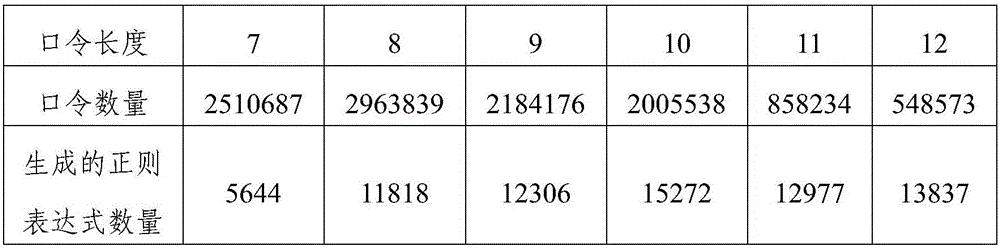
InactiveCN105760769AImprove decryption efficiencySupport analysis jobsDigital data protectionDigital data authenticationPasswordStatistical analysis
The invention discloses a statistics and analysis method and a statistics and analysis device for computer passwords. The method comprises the following steps: dividing the computer passwords in a password library into multiple groups according to the digits of the computer passwords; carrying out statistics and analysis on the password quantity corresponding to each regular expression in each group of computer passwords according to the preset regular expressions; sorting the regular expressions of each group of computer passwords according to the password quantity corresponding to each regular expression to obtain the statistics and analysis result of the computer passwords. According to the statistics and analysis method and the statistics and analysis device, the regular expressions sorted according to the statistical quantity of the computer passwords can be obtained by grouping the computer passwords and carrying out statistics and analysis on each group of passwords through the regular expressions, so that the hit rate of decrypting the computer passwords is improved; and analysis operation on a large-scale password library is supported.
Owner:寇陶陶
Method for optimizing protocol IPsec ESP in single-tunnel mode and device
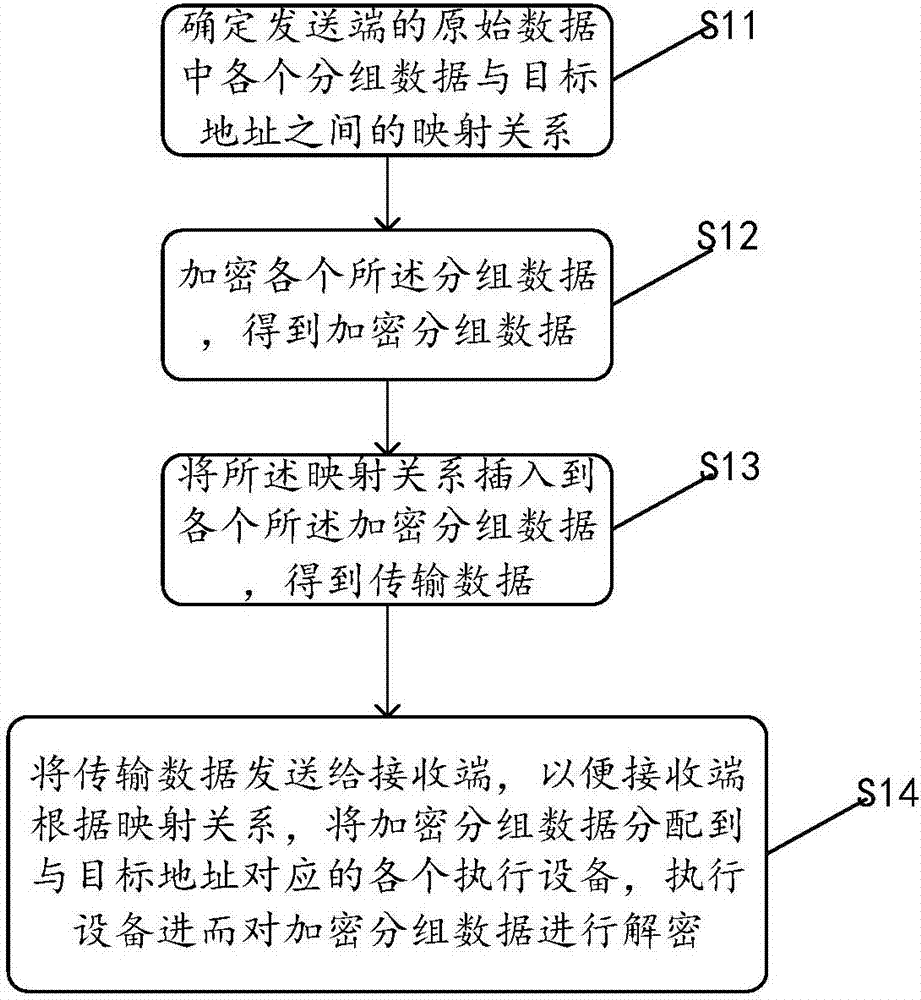
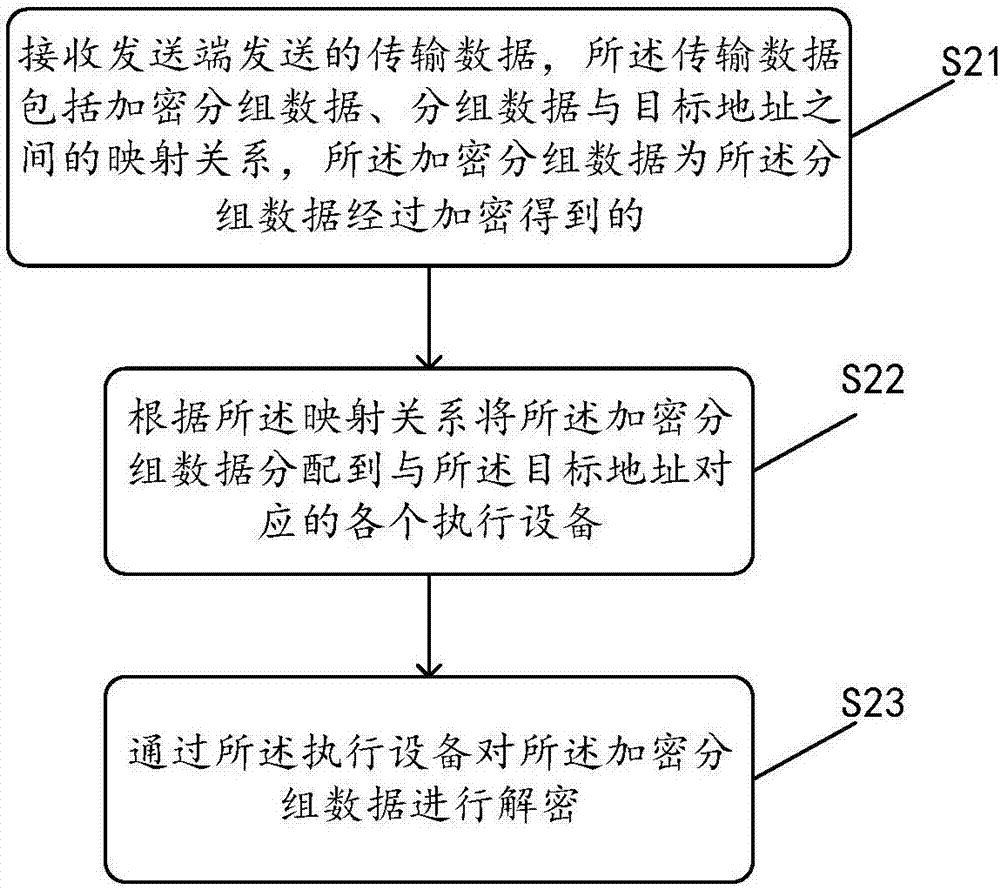
InactiveCN107454116AImprove decryption efficiencyEncryption apparatus with shift registers/memoriesComputer hardwareOriginal data
The invention discloses a method for optimizing a protocol IPsec ESP in a single-tunnel mode. The method is applied to an encryption terminal and comprises the steps: a mapping relationship between all grouped data among raw data and a target address is determined, then, the grouped data are encrypted to obtain encrypted grouped data, then, the mapping relationship is inserted into the encrypted grouped data to obtain transmitting data, finally, the transmitting data are sent to a decryption terminal, the decryption terminal allocates the encrypted grouped data to each execution device according to the mapping relationship, and the execution devices decrypt the encrypted grouped data. By the method, the decryption terminal allocates the encrypted grouped data to a plurality of execution devices for decryption, the execution devices decrypt the encrypted grouped data, and thus, the decryption efficiency in the single-tunnel mode is greatly increased. The method for optimizing the protocol IPsec ESP in the single-tunnel mode, provided by the invention, is applied to the decryption terminal. The invention further provides two devices corresponding to the two methods. The devices correspond to the methods.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com