Method for optimizing protocol IPsec ESP in single-tunnel mode and device
An optimization method and single-tunnel technology, applied in the computer field, can solve problems such as low decryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
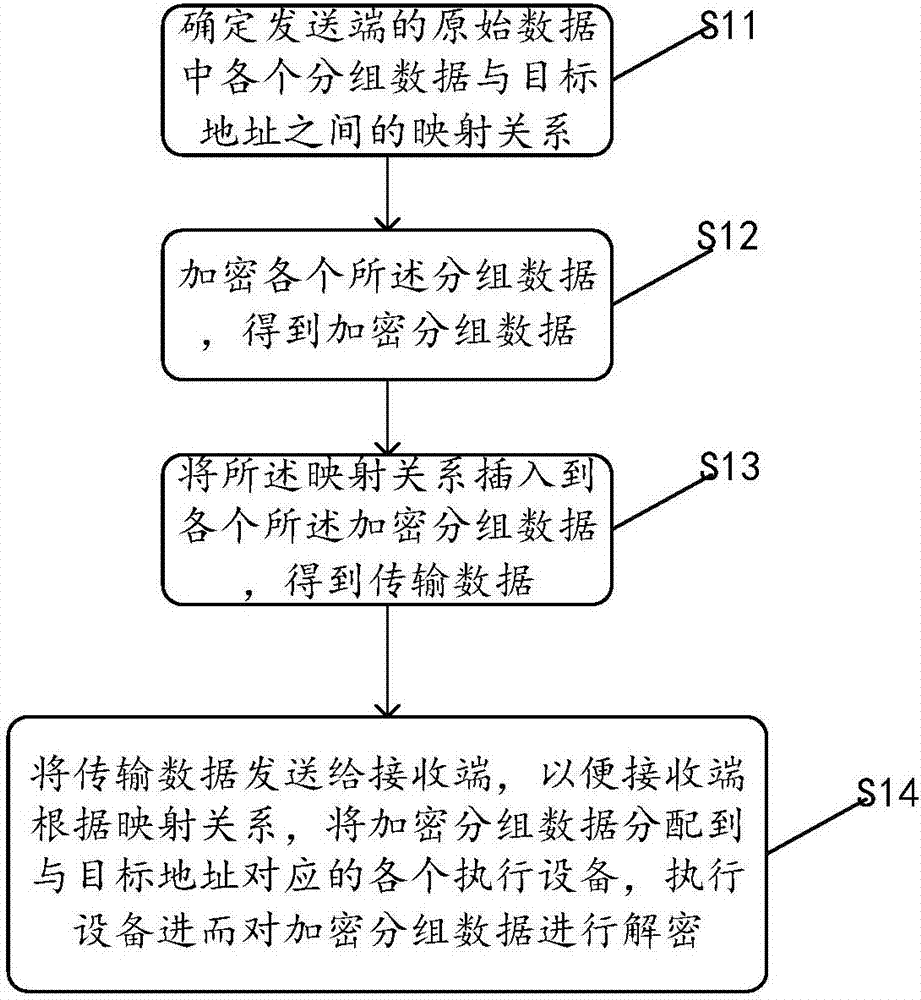
[0047] Begin to introduce the optimization method embodiment one of IPsec ESP protocol under the single tunnel mode provided by the present invention in detail below, refer to figure 1 , Embodiment 1 specifically includes:
[0048] Step S11: Determine the mapping relationship between each packet data in the original data at the encryption end and the target address.
[0049] The encryption end refers to the end that encrypts the original data, and the target address refers to the address to which the original data is finally transmitted.
[0050] Specifically, determining the mapping relationship between each packet data in the original data at the encryption end and the target data may be, using a hash algorithm to calculate the hash between each packet data in the original data at the sending end and the target address Value, the hash value reflects the mapping relationship between the packet data and the target address. Wherein, the packet data may be tuple data.
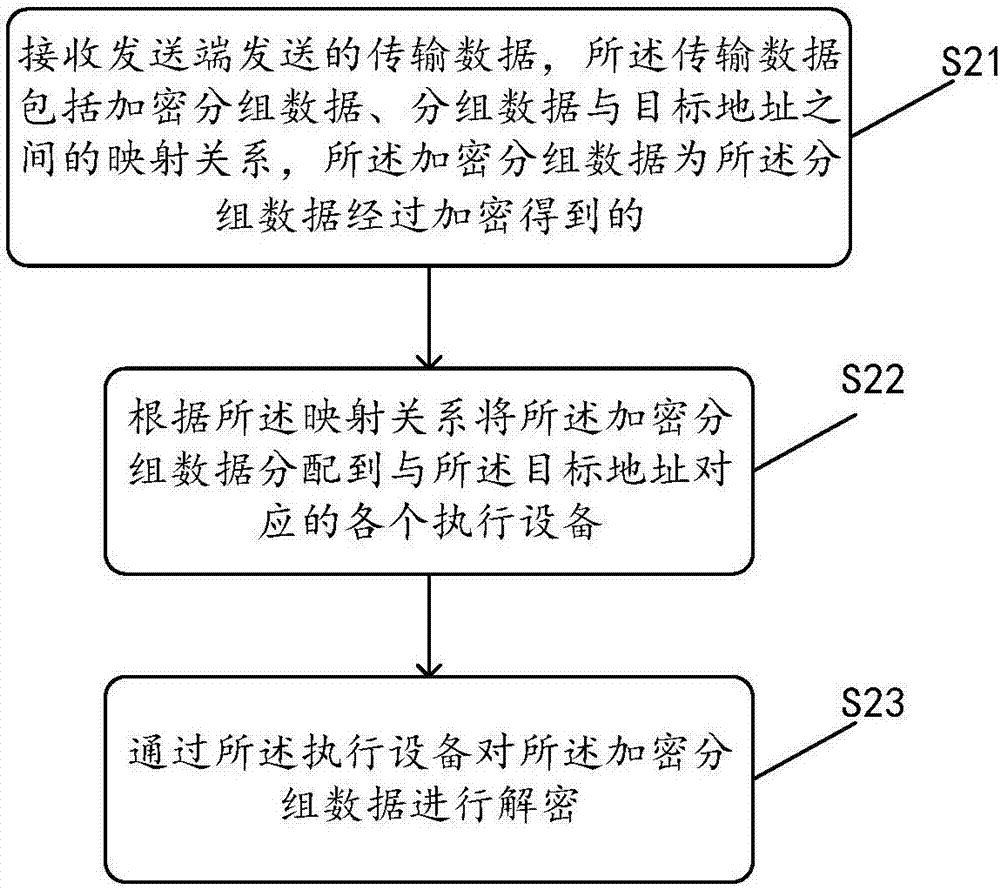
[0051] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com