Multi-authorization access control system and method based on attribute encryption
A technology of authorized access and attribute encryption, which is applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as security loopholes, security risks, and single authorization center mode, and achieve the effect of improving encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
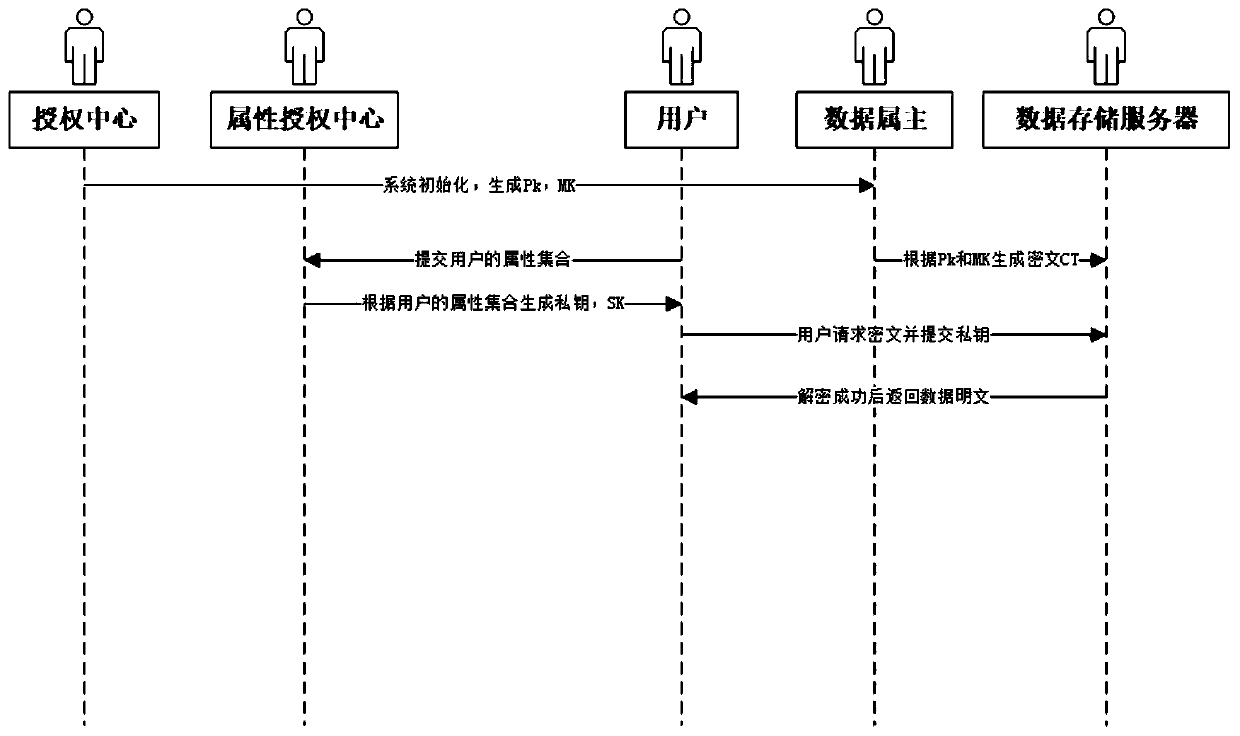
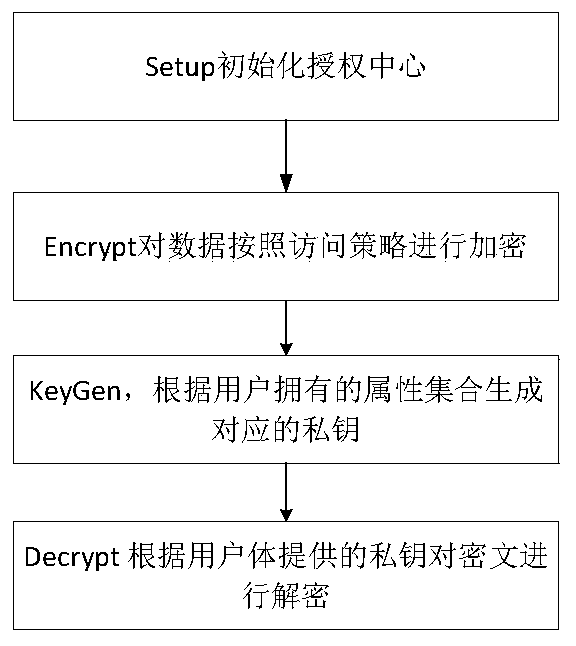
[0031] Example: such as figure 1 As shown, a multi-authorization access control system based on attribute encryption includes: authorization center, attribute authorization center, data owner, data storage server, and access user; wherein, the authorization center: represented as CA (CenterAuthority), is responsible for setting the system Parameters to generate public key PK and master key MK;
[0032] Attribute authorization center: represented as AA (Attribute Authority), responsible for generating private keys for the attributes it is responsible for;
[0033] Data owner: represented as DO (Data Owner), responsible for expressing the policy set of data access and encrypting data;
[0034] Data cloud storage service: denoted as DSM (Data System Manager), responsible for storing the data ciphertext encrypted according to the access policy customized by the policy customizer, and providing decryption services for users;
[0035] Access user: denoted as User, each user has an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com