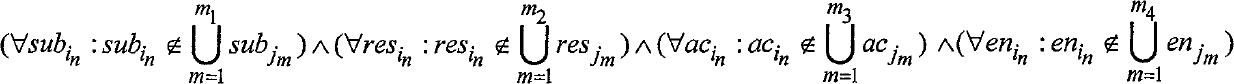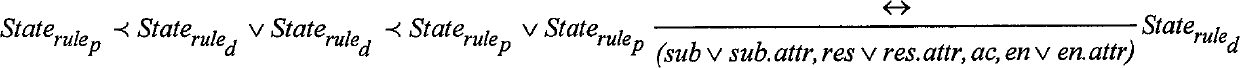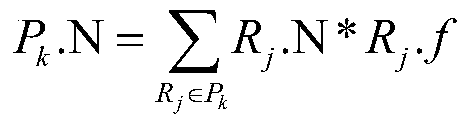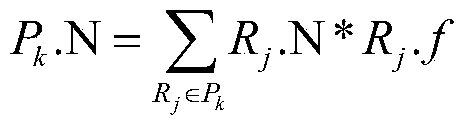Patents
Literature
37 results about "XACML" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
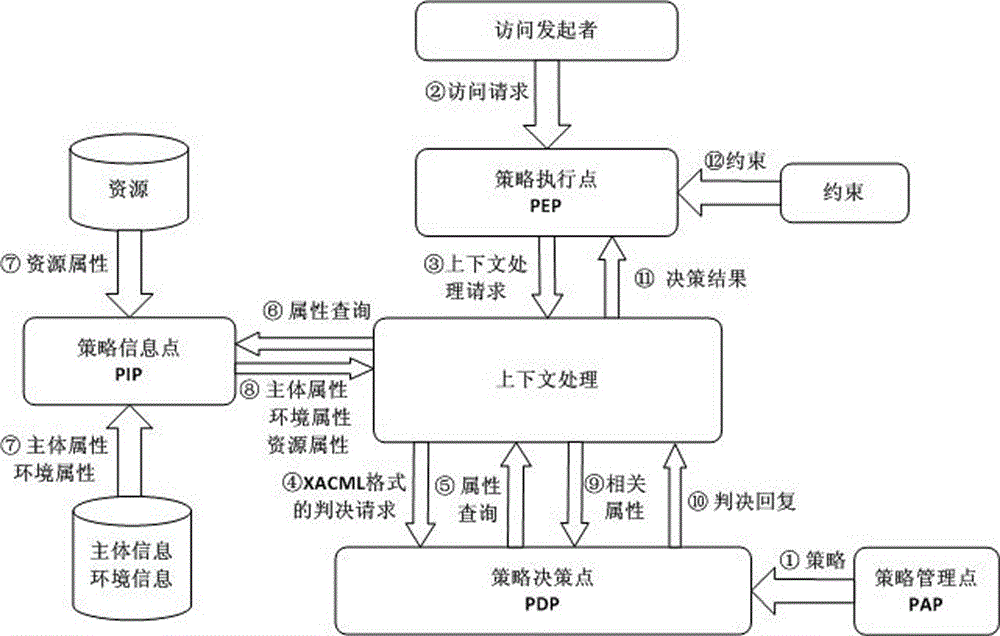
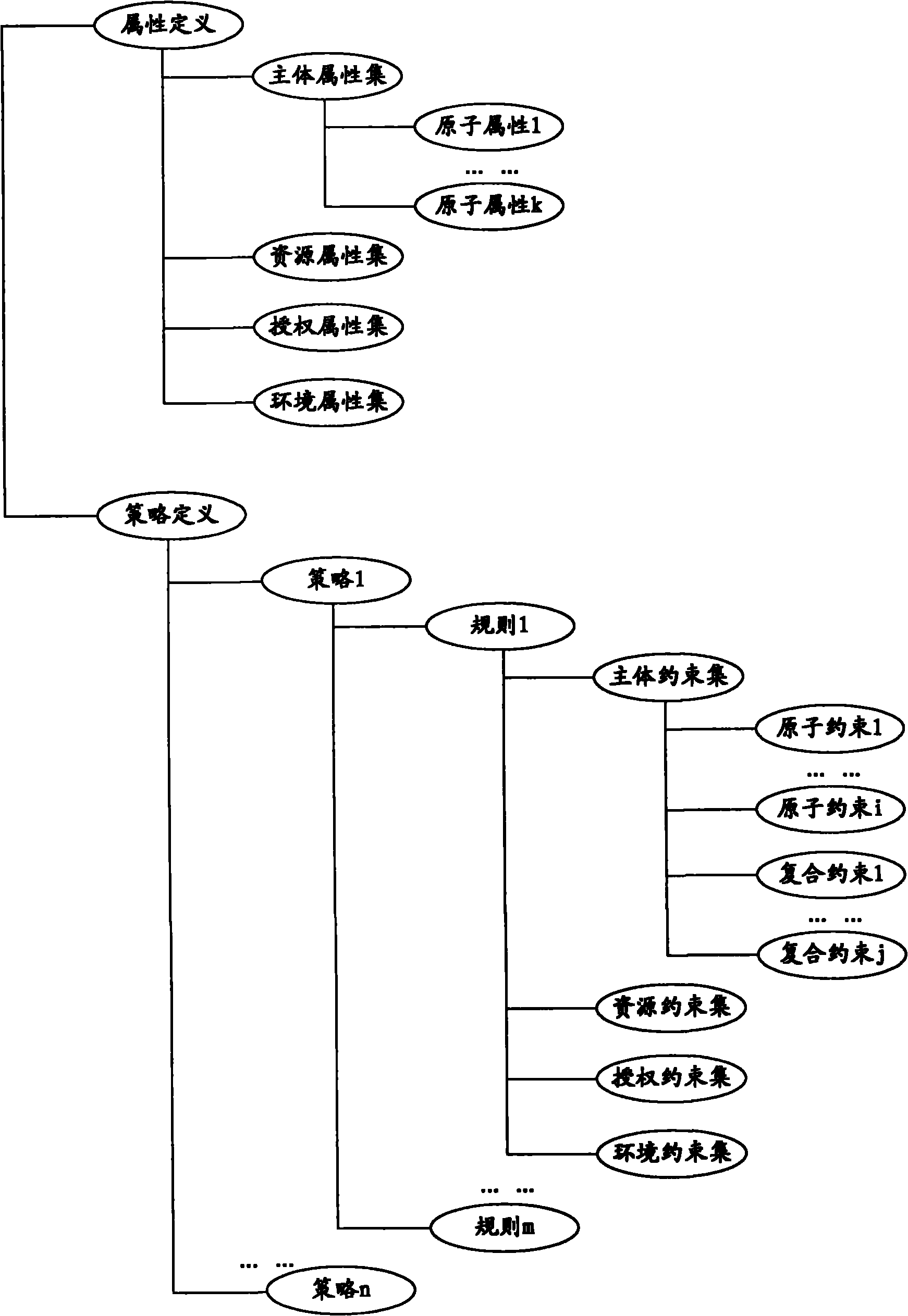
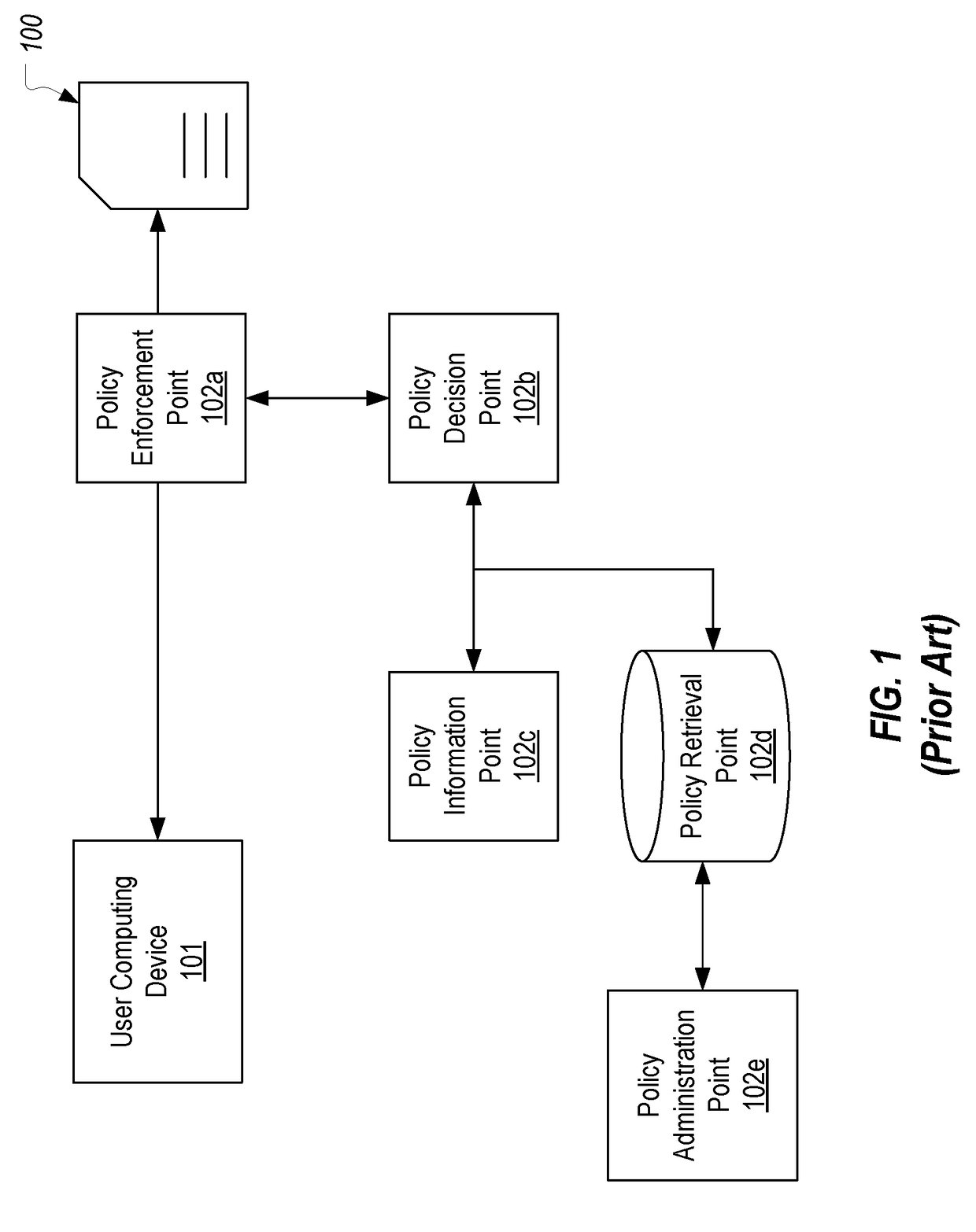
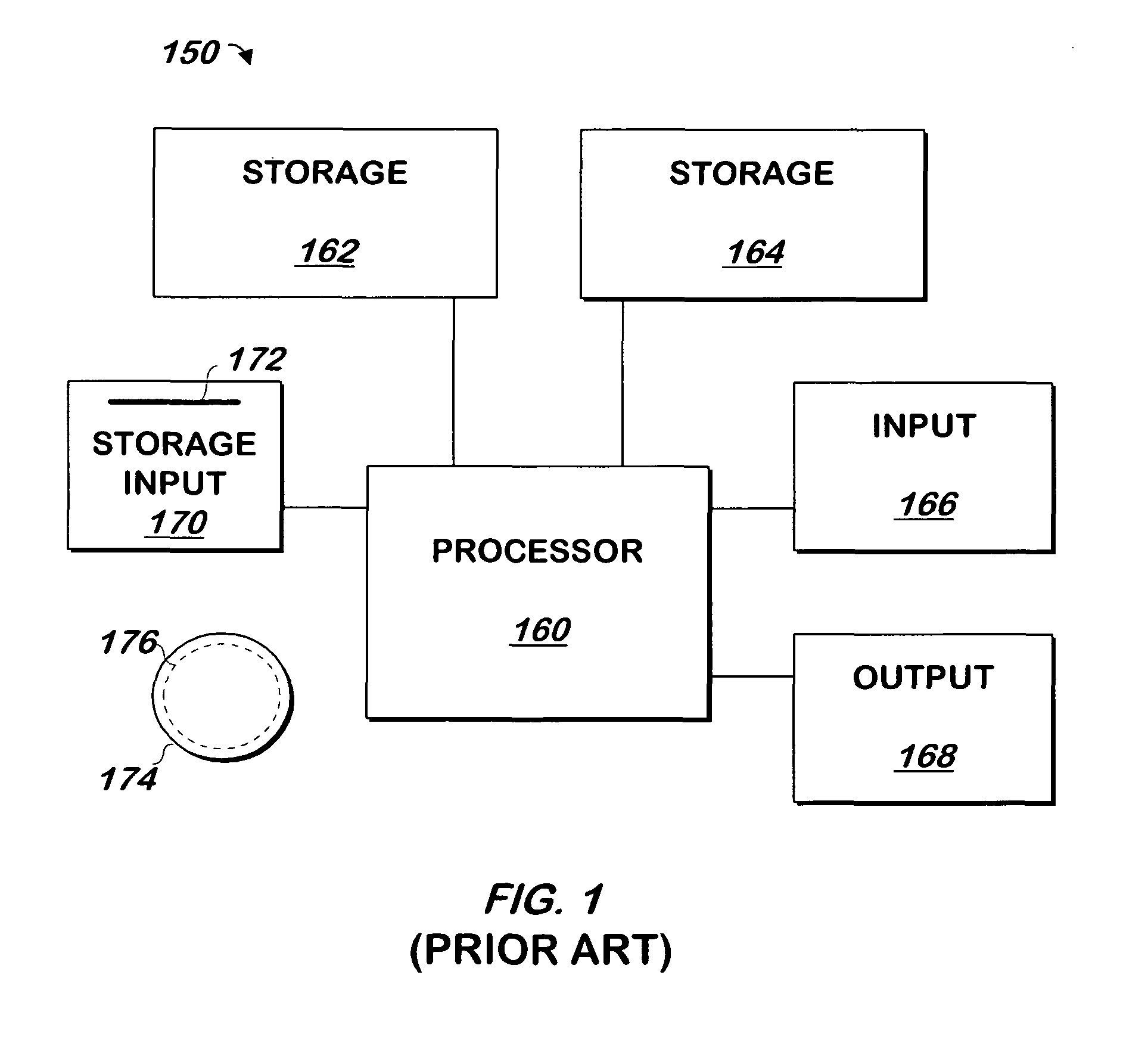
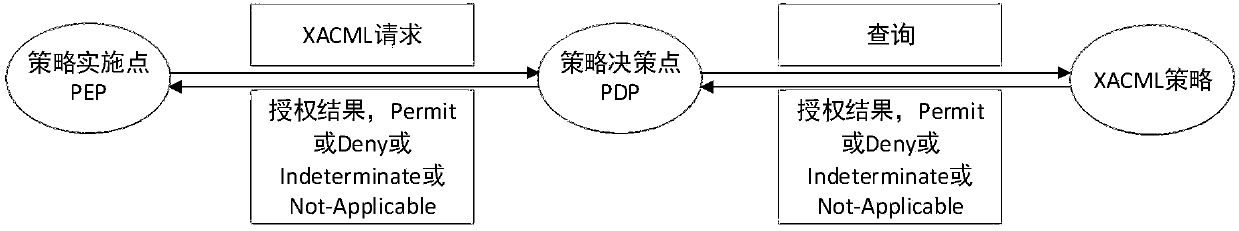
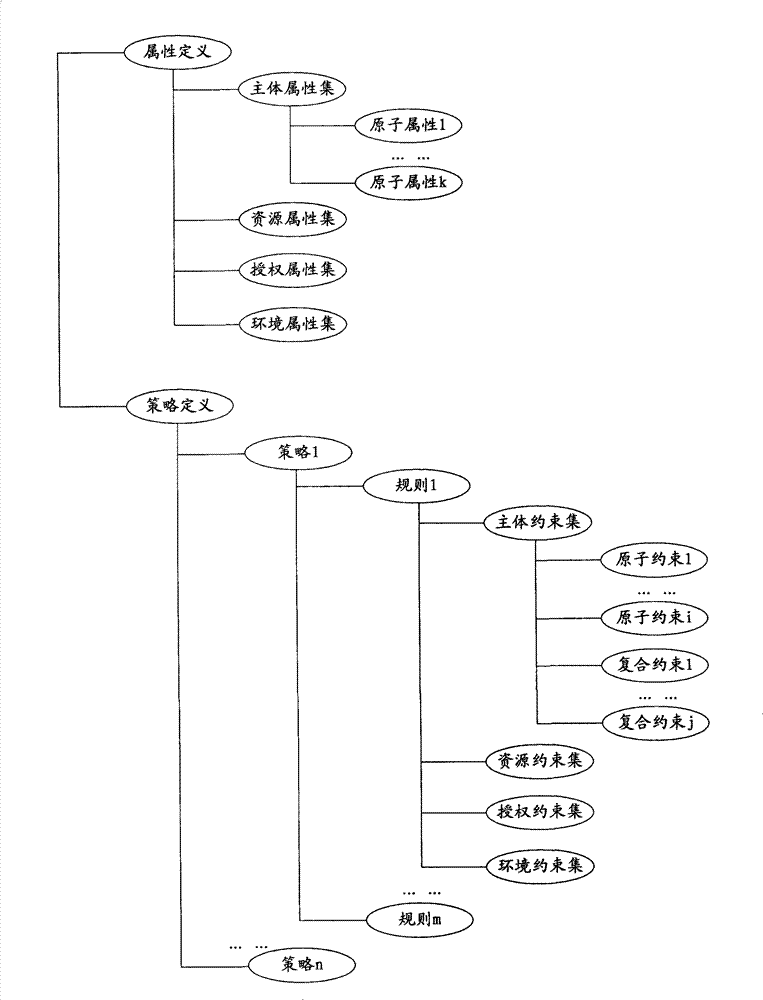
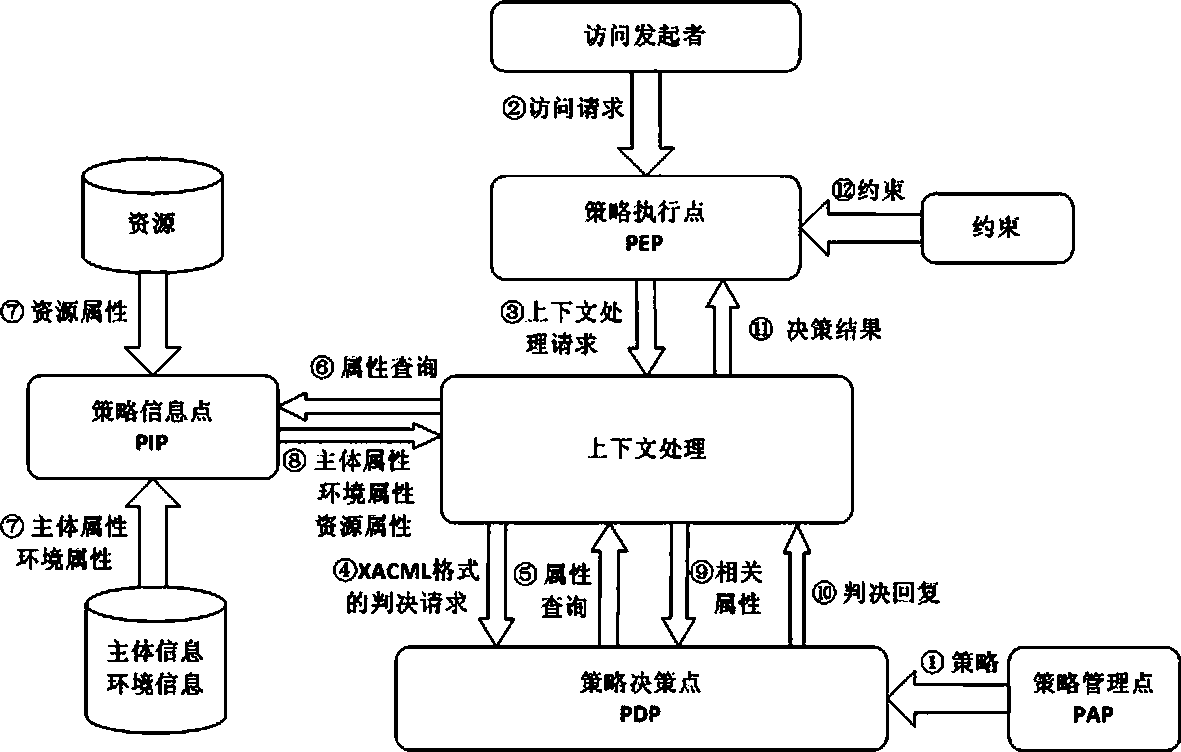
XACML stands for "eXtensible Access Control Markup Language". The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies.
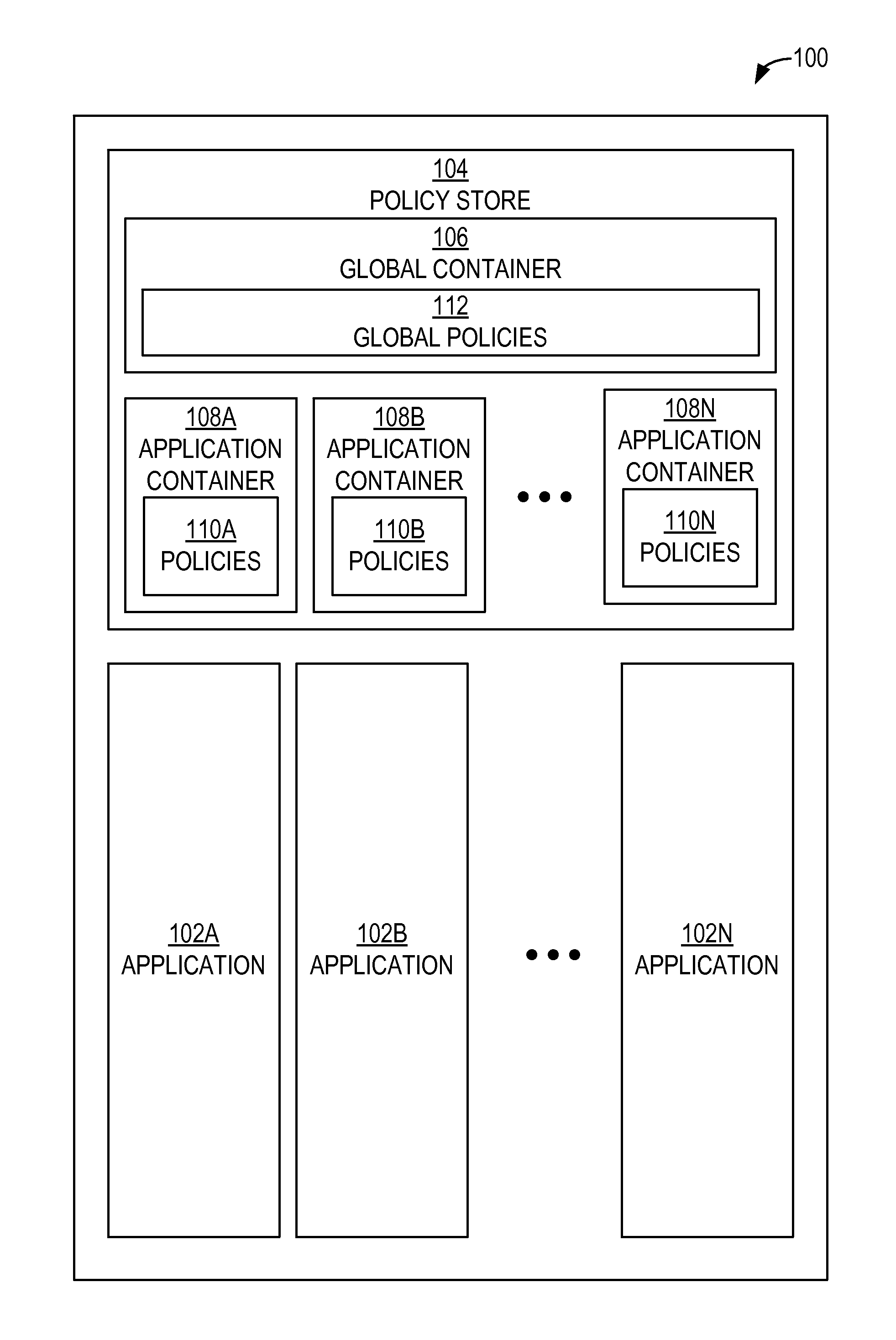
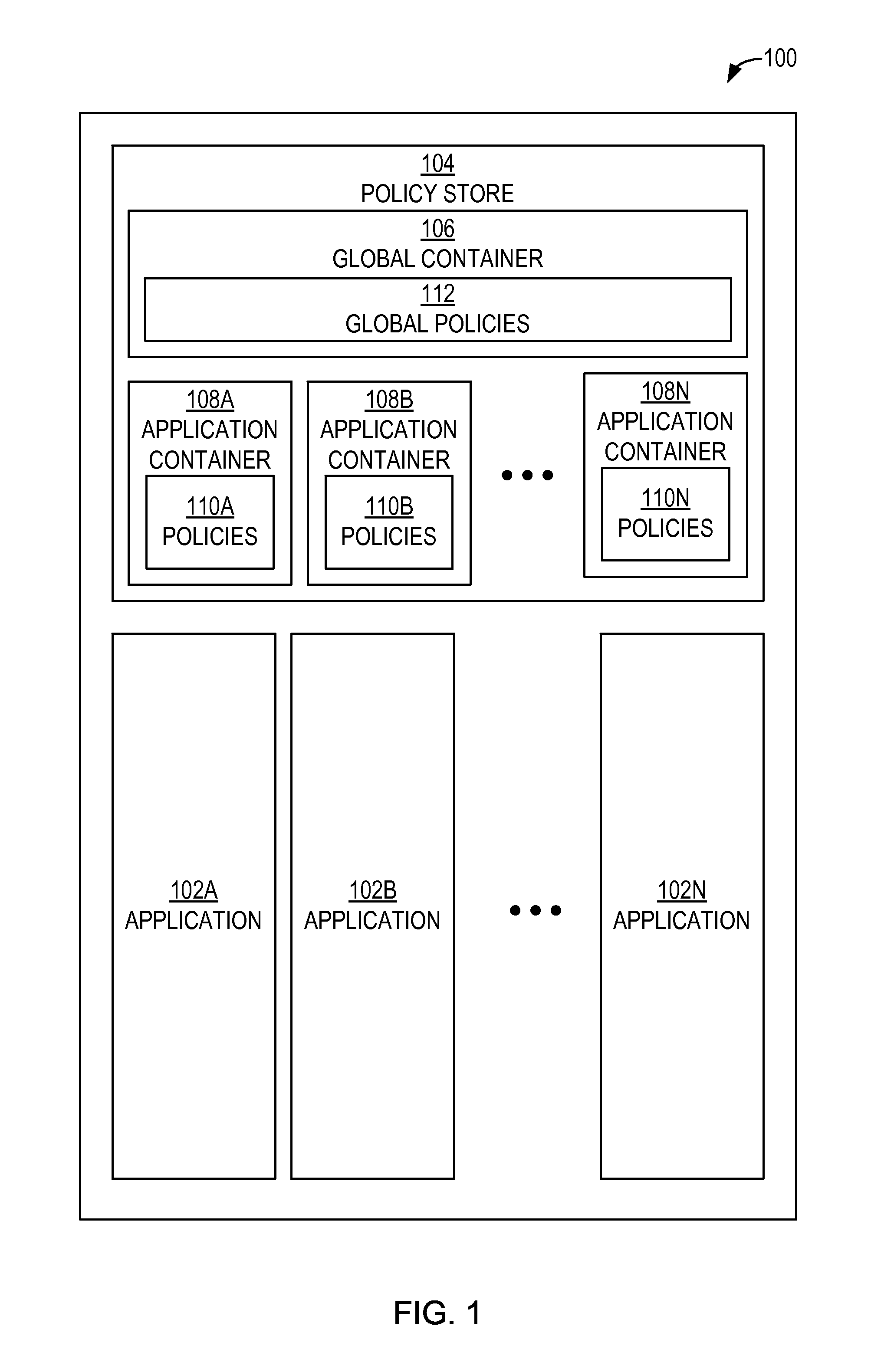
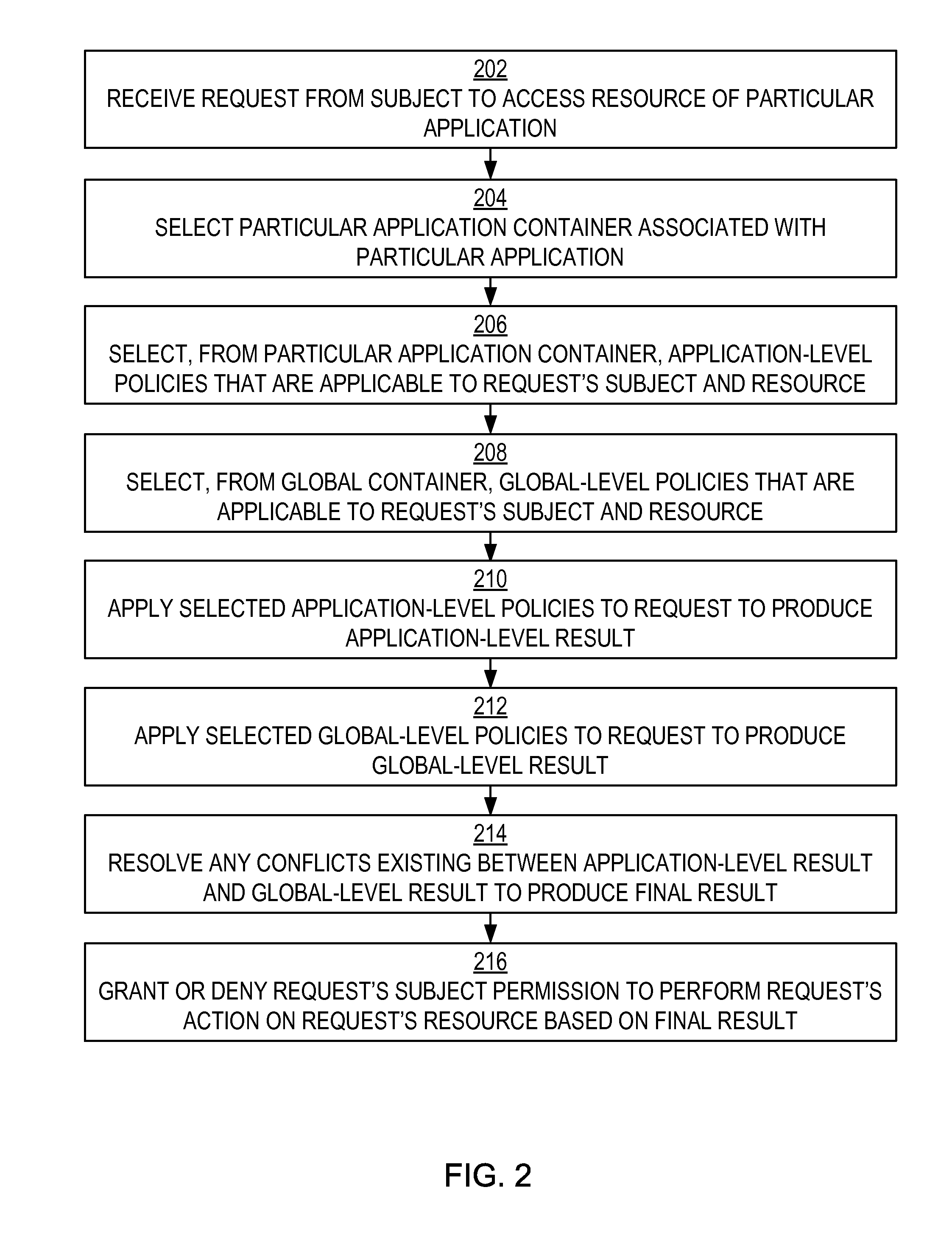
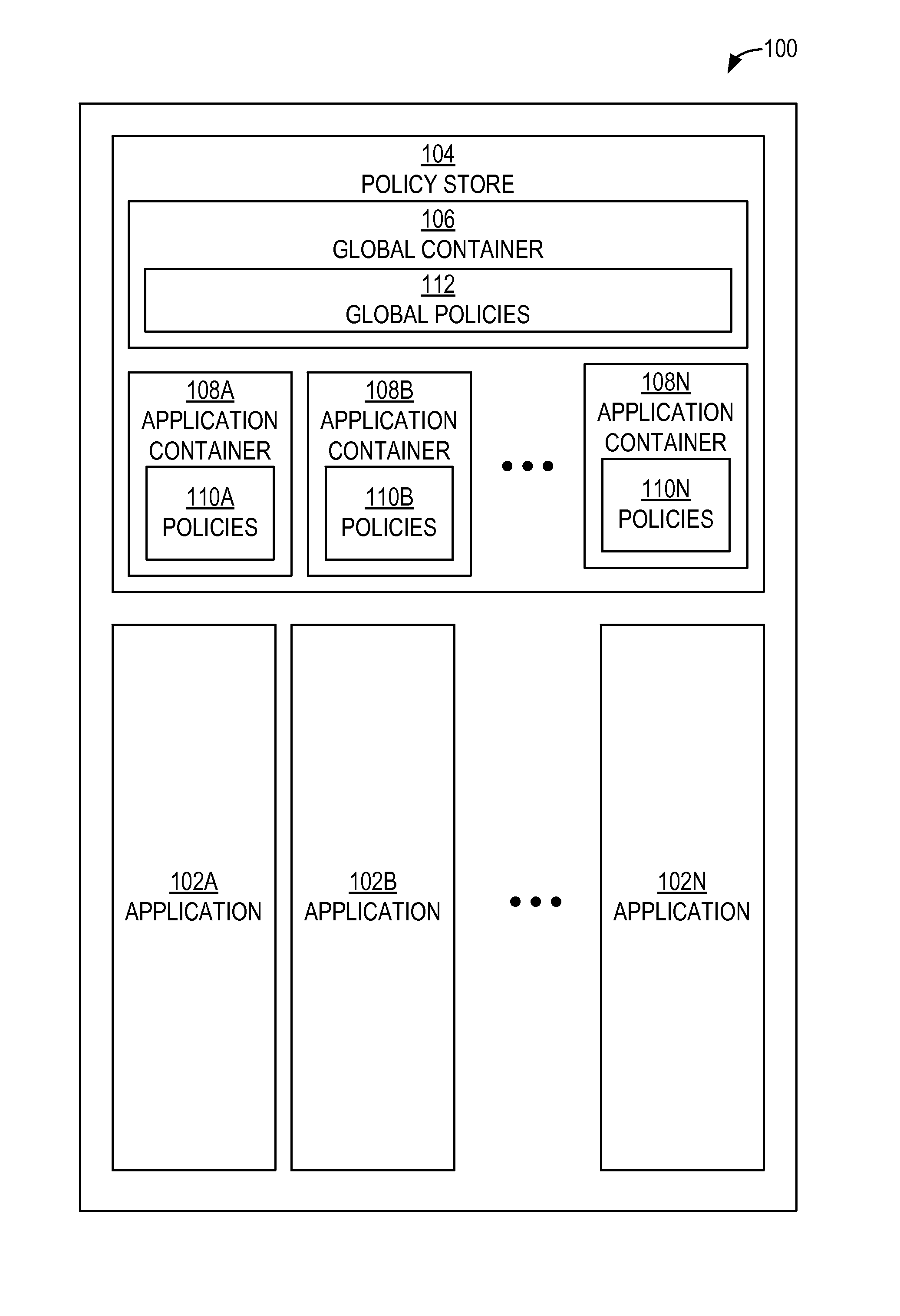
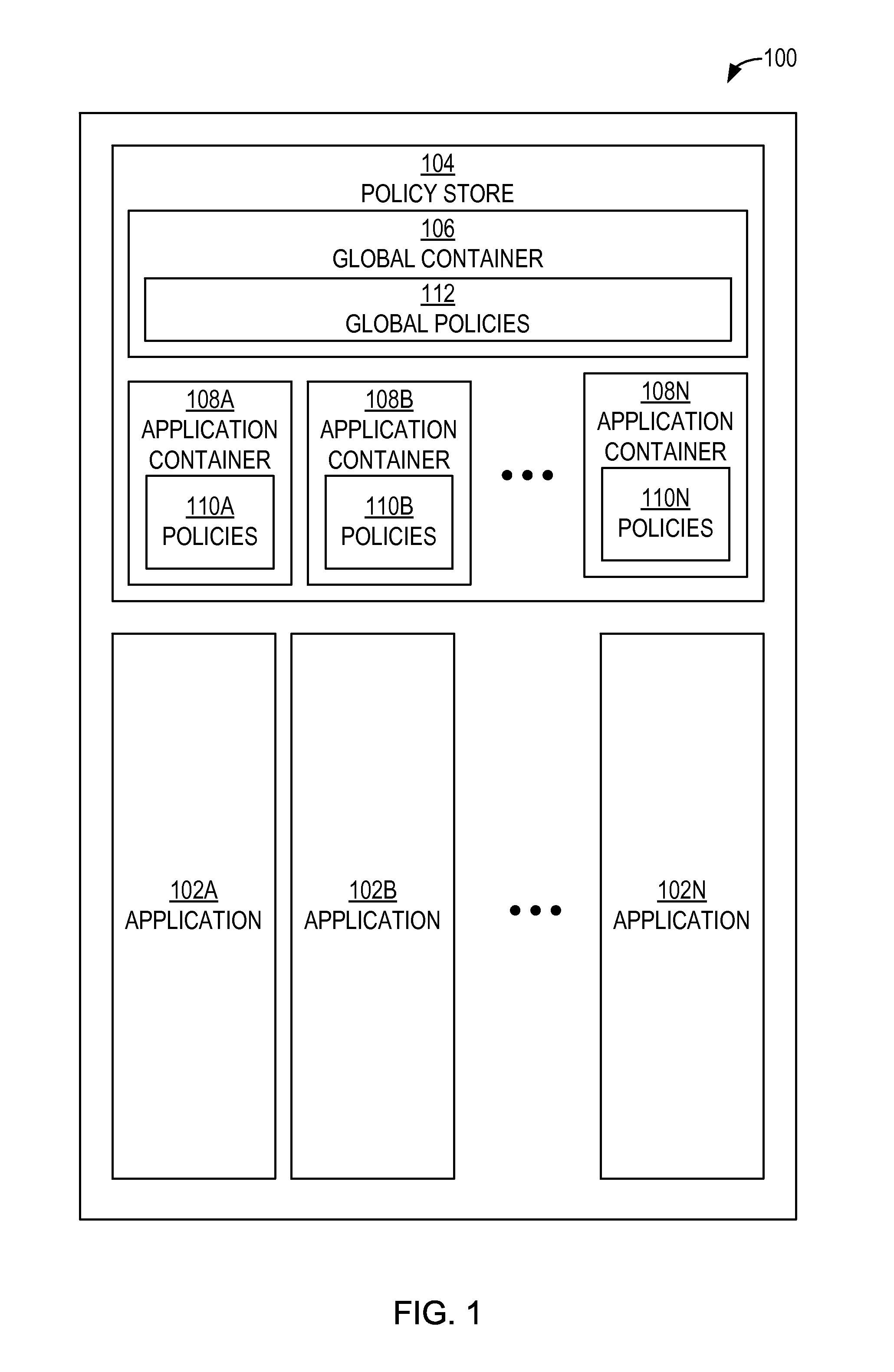
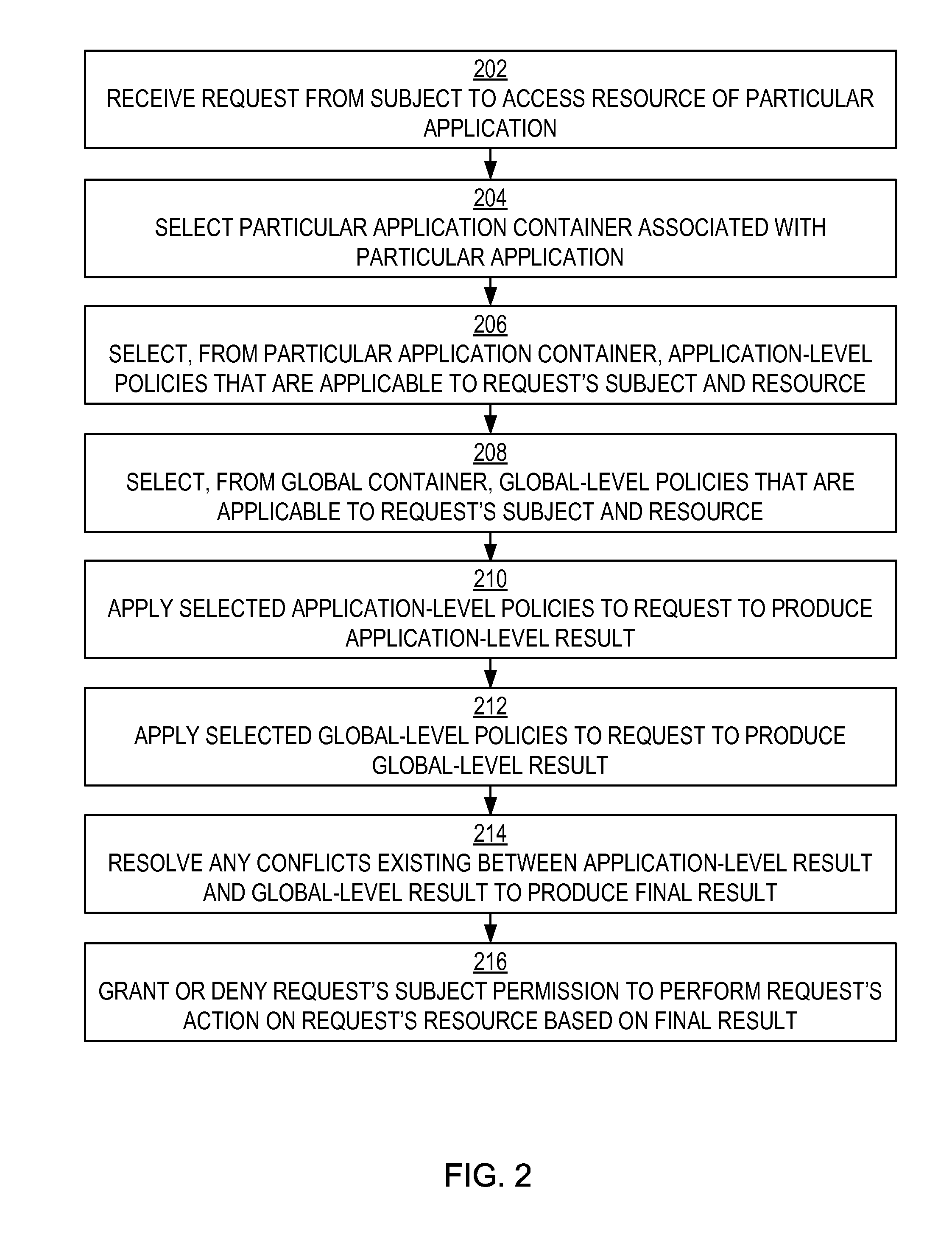
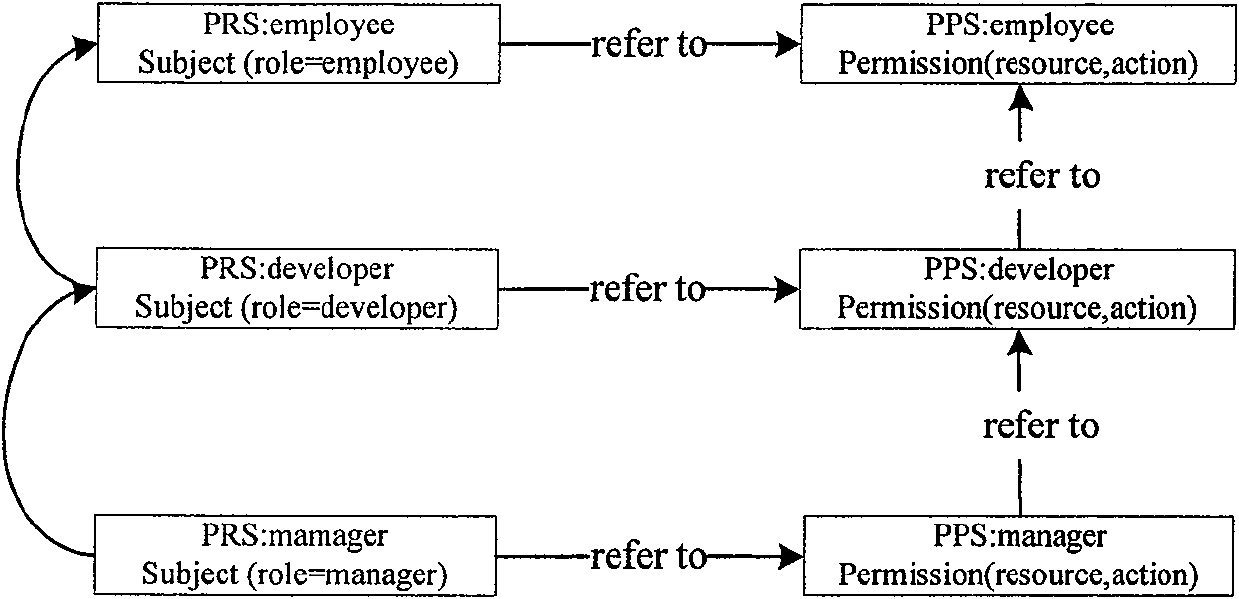
Authorization policy objects sharable across applications, persistence model, and application-level decision-combining algorithm
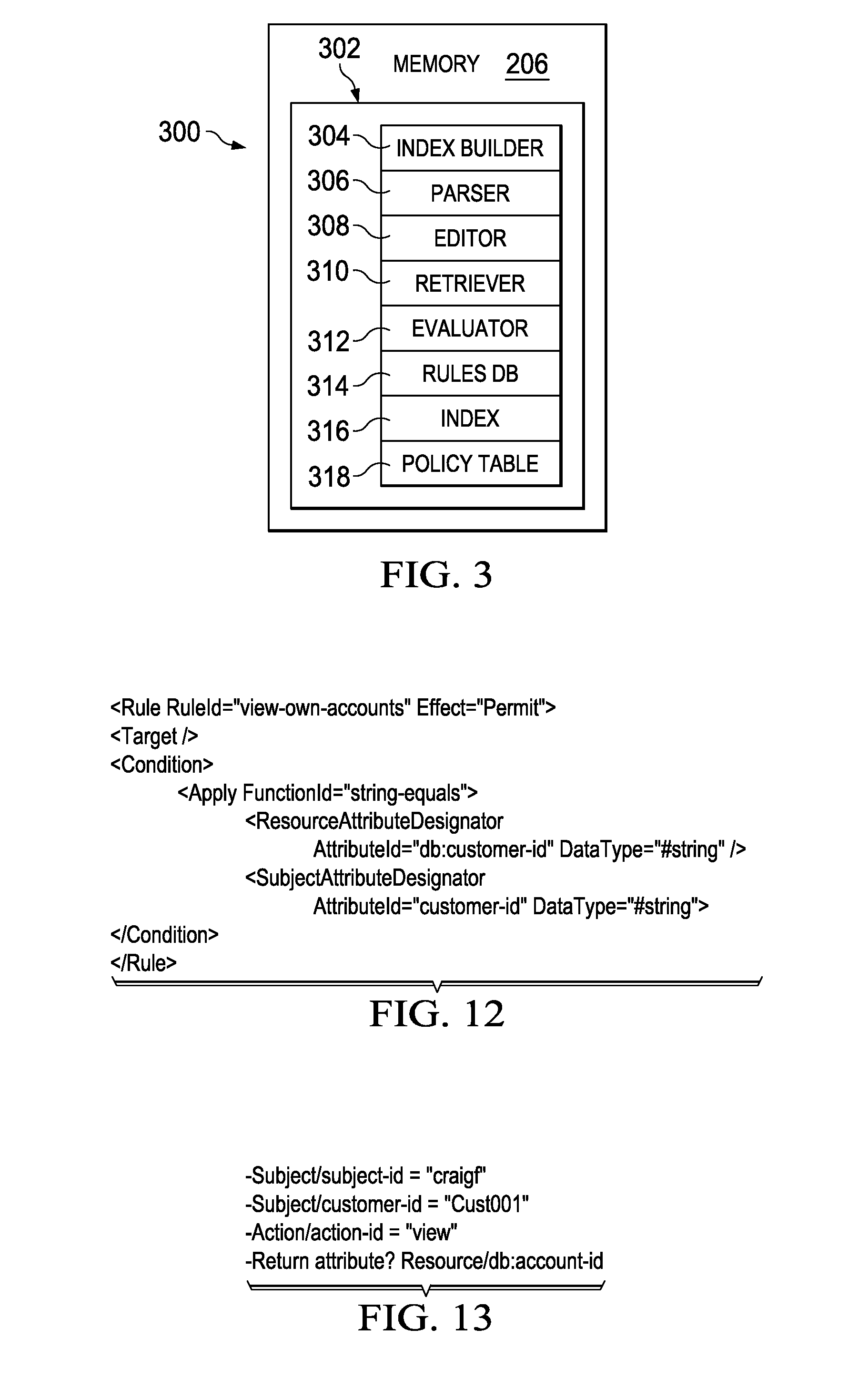
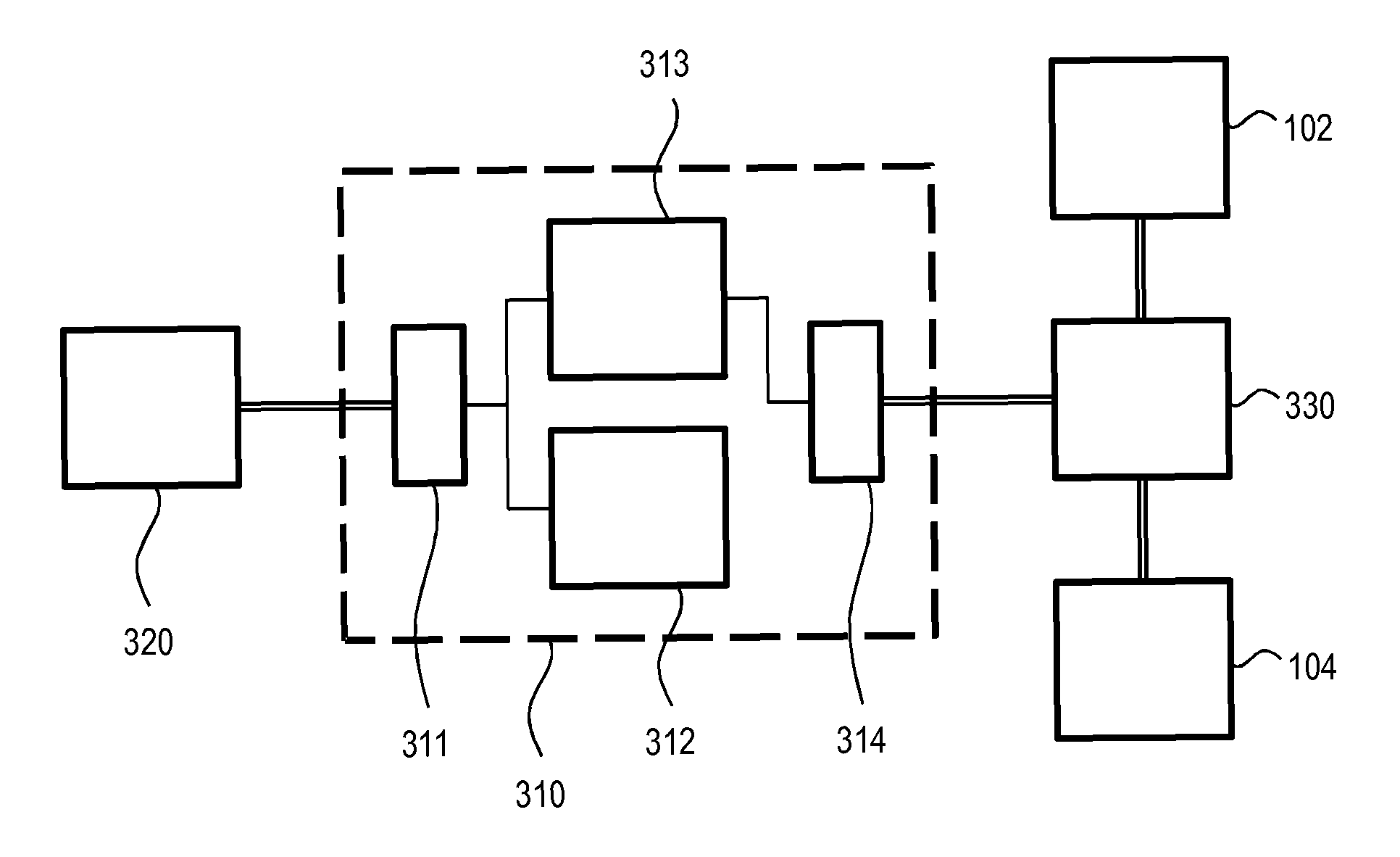
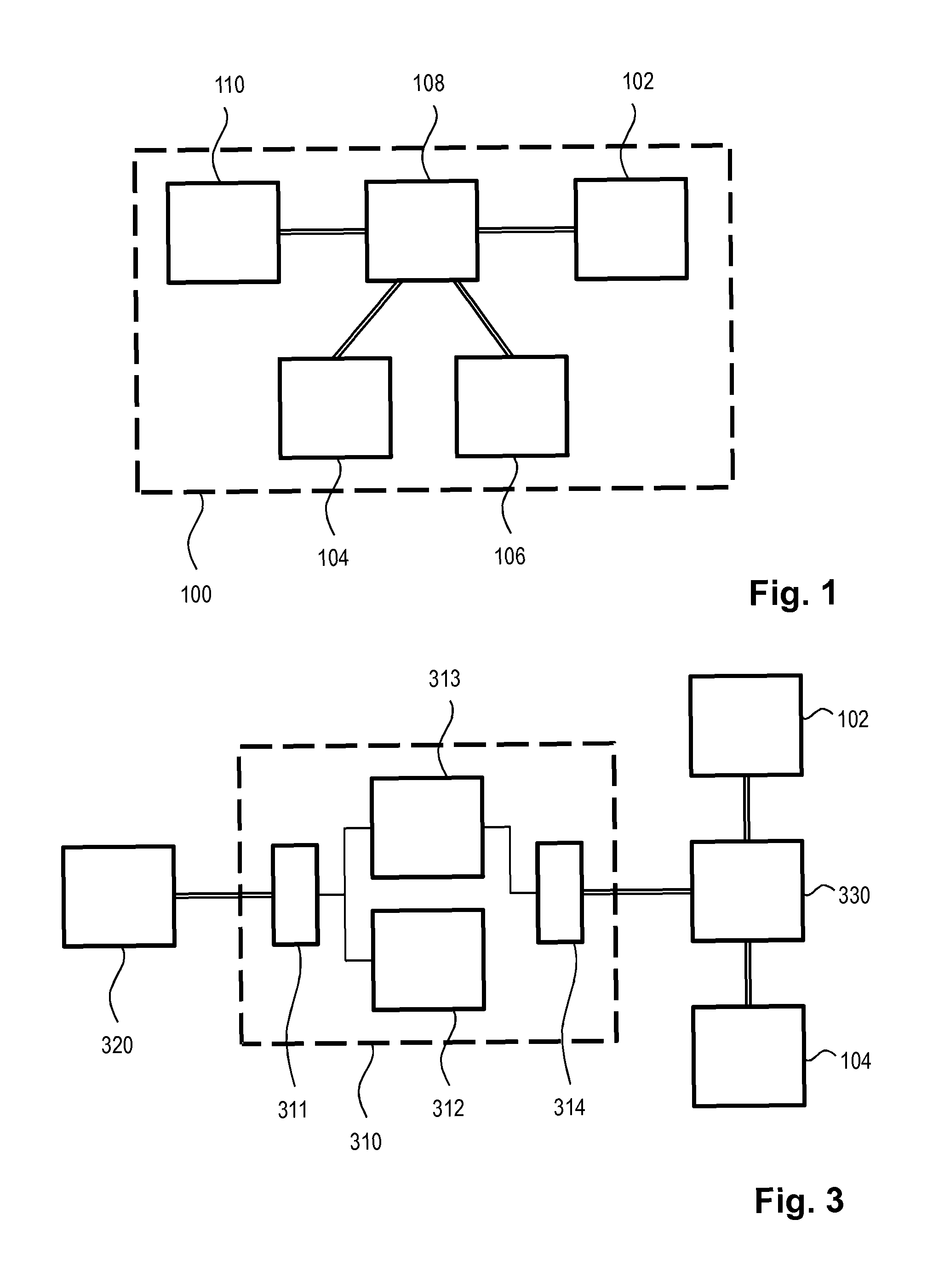
ActiveUS20150089575A1Avoid wasteful duplicationDigital data protectionTransmissionBusiness enterpriseApplication procedure
A global policy store, in which policies applicable to multiple applications in an enterprise environment can be stored, can be stored in association with that environment. An application-level policy combining algorithm can be associated with a specific application to resolve conflicts between the results of evaluating policies that pertain to that application's resources. A persistent model is defined for an Extensible Access Control Markup Language (XACML) target definition.
Owner:ORACLE INT CORP
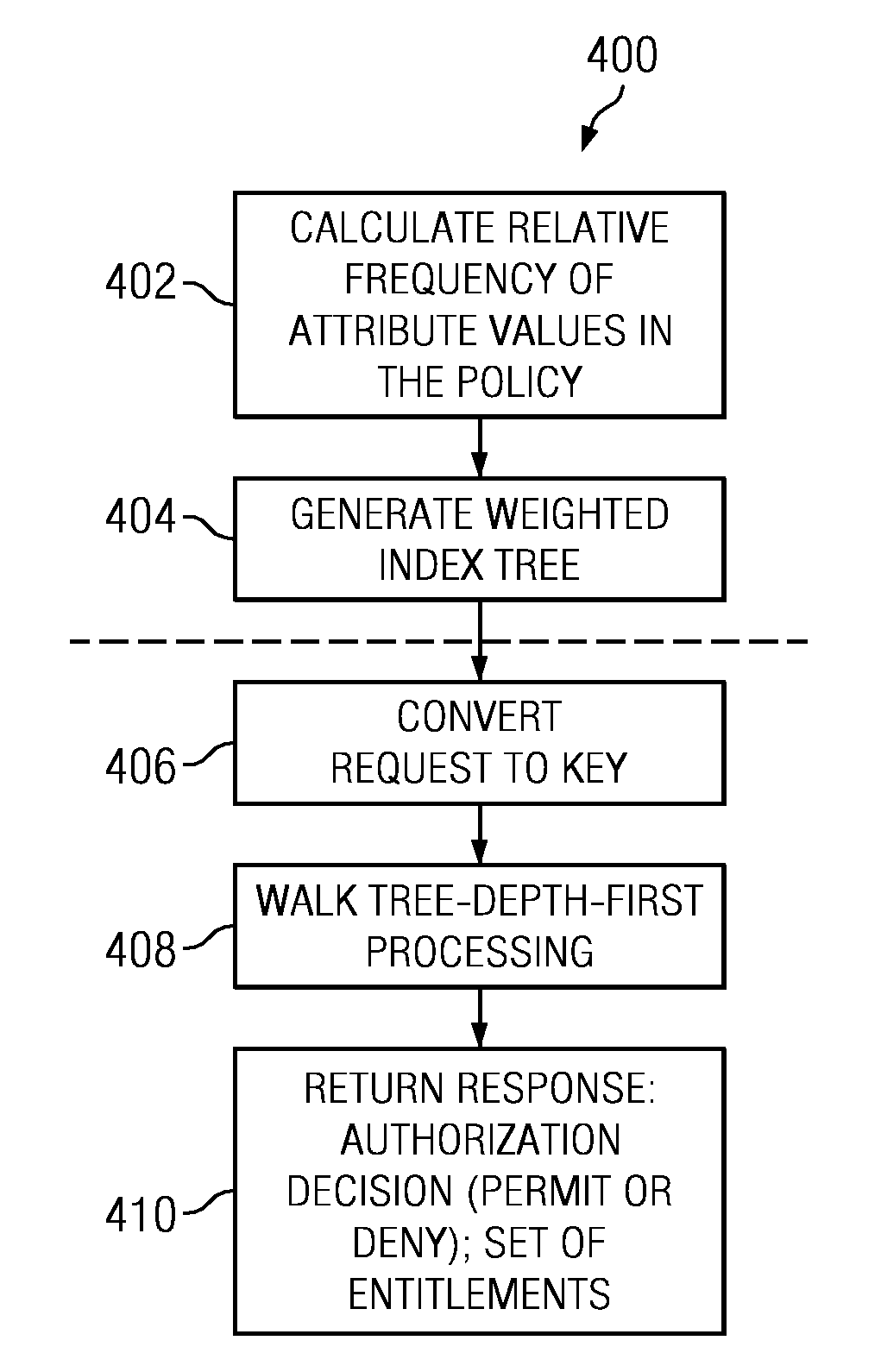
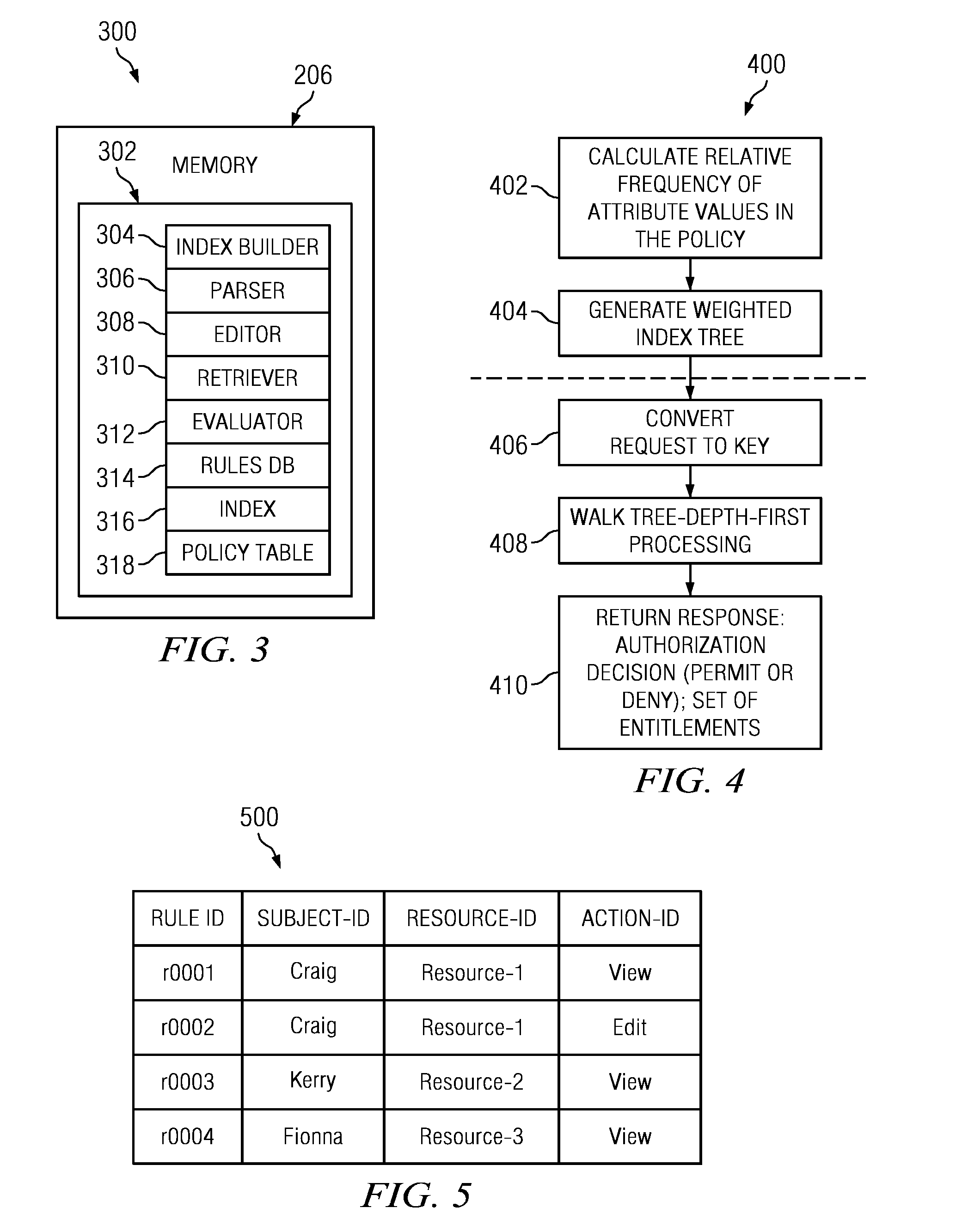
Context-based security policy evaluation using weighted search trees
A method, apparatus and computer program product for evaluating a context-based (e.g., XACML) policy having a set of attributes using a weighted index tree having one or more leaves extending from a root node. Each leaf of the tree represents a policy rule. A depth-first path down the leaf represents one or more attributes of the set of attributes that must be present in a request for the rule to be applicable. An input is evaluated against the weighted index tree to generate a response. One type of input is an authorization request, in which case the response is an authorization decision (e.g., permit or deny). Another type of input is a query for a set of entitlements, in which case the response is a set of entitlements.
Owner:INT BUSINESS MASCH CORP
XACML policy rule checking method
InactiveCN101339591AOptimize strategy structureImprove the efficiency of strategy judgmentDigital data authenticationSemantic treeState dependent
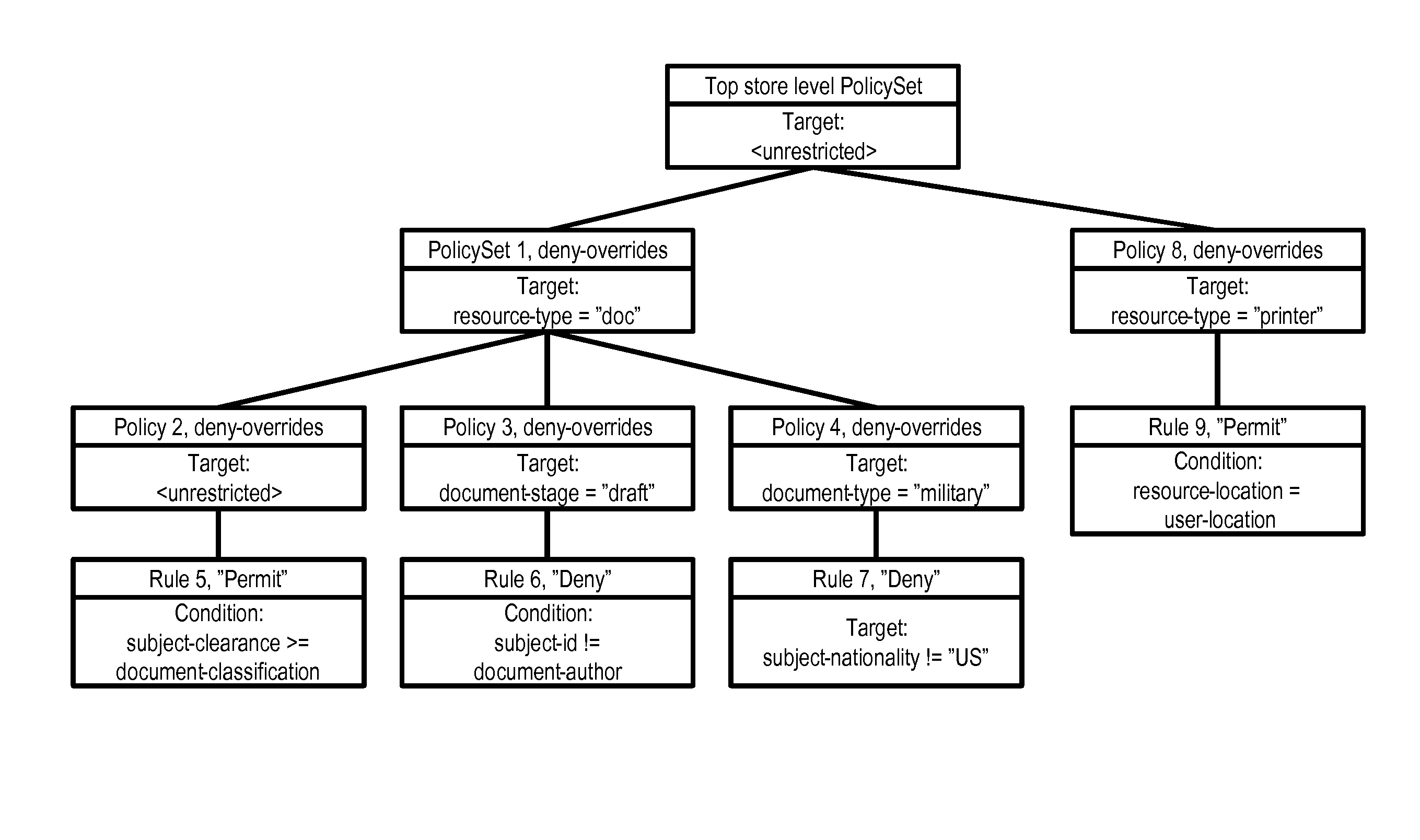
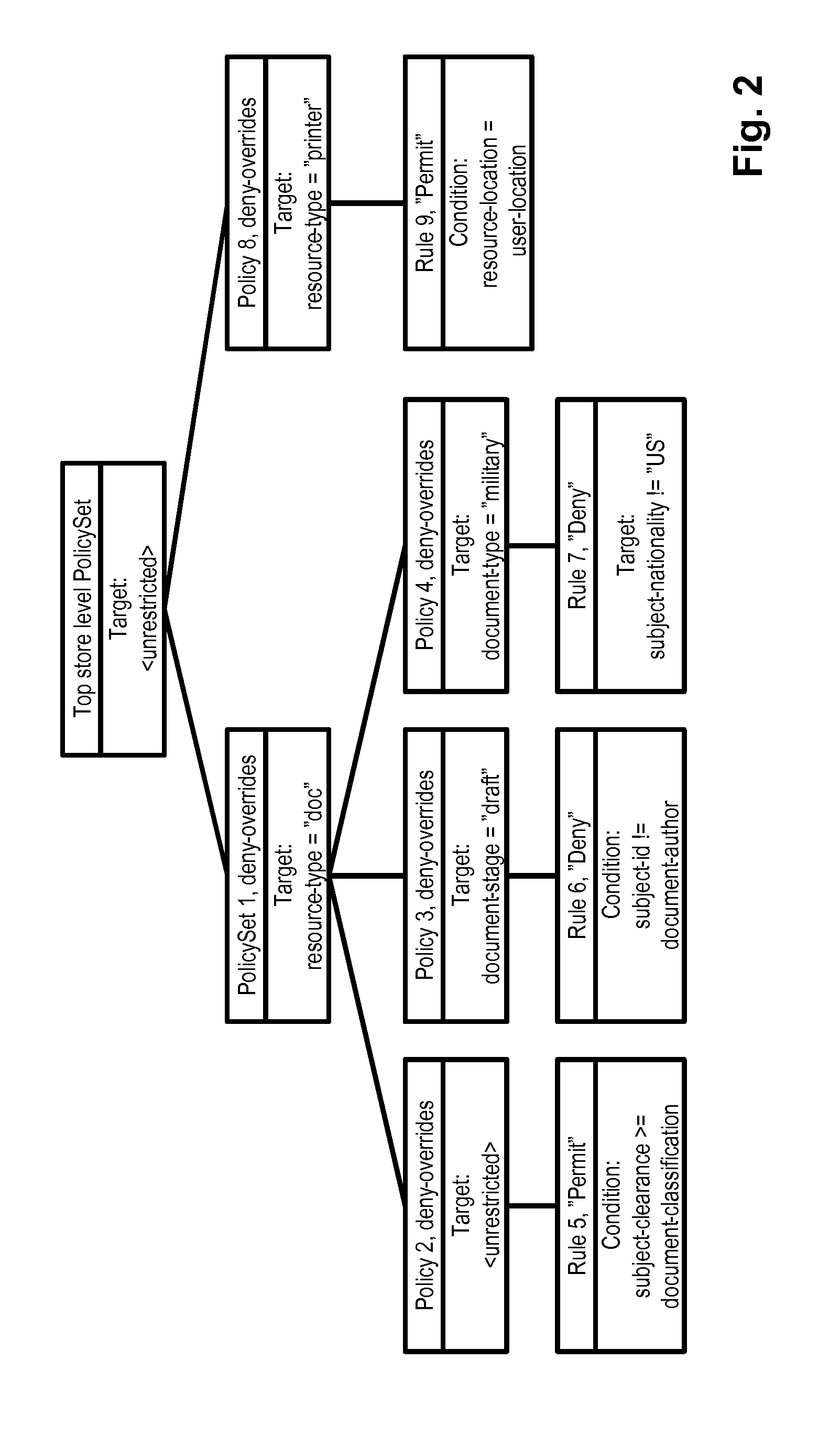
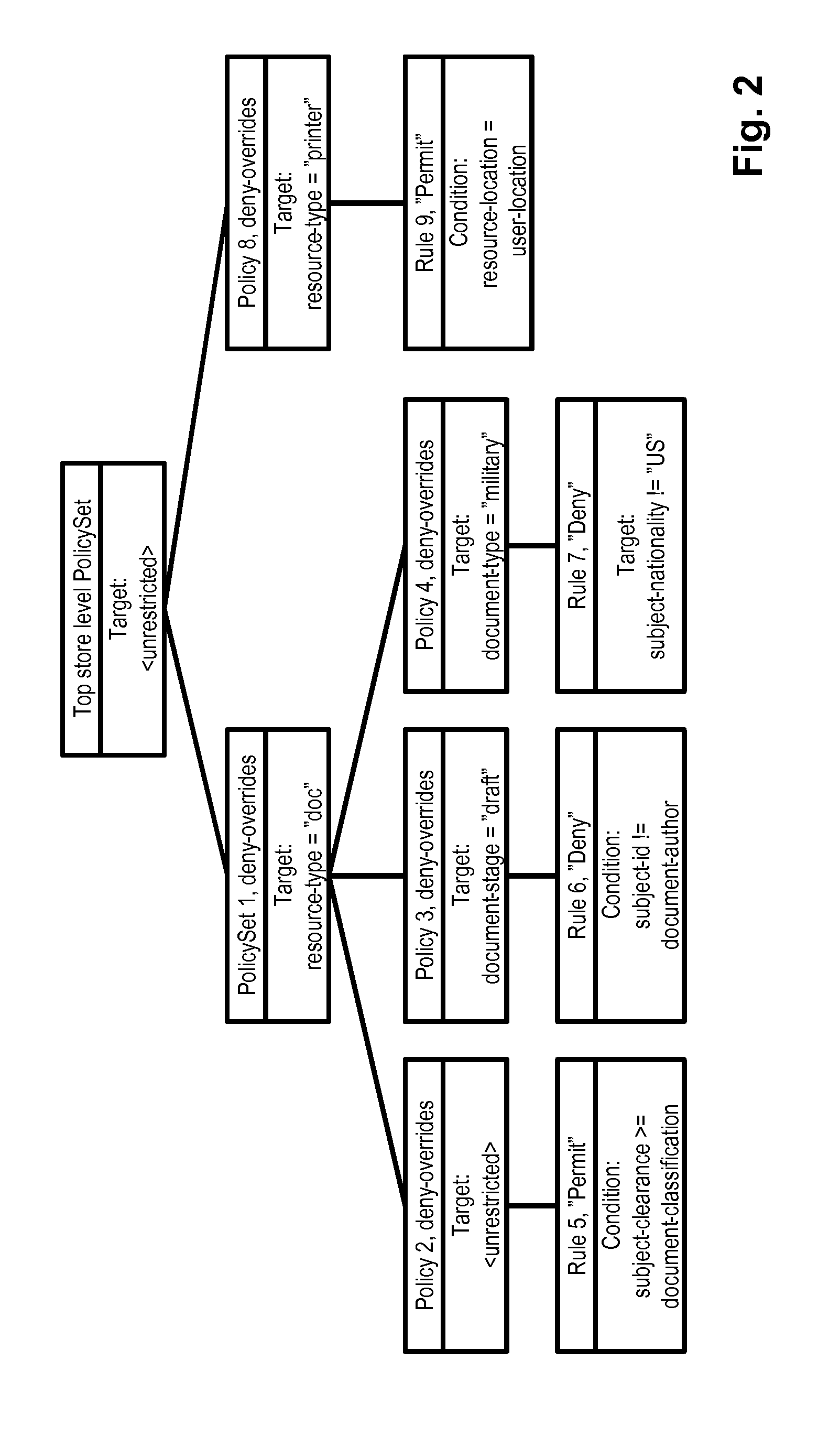
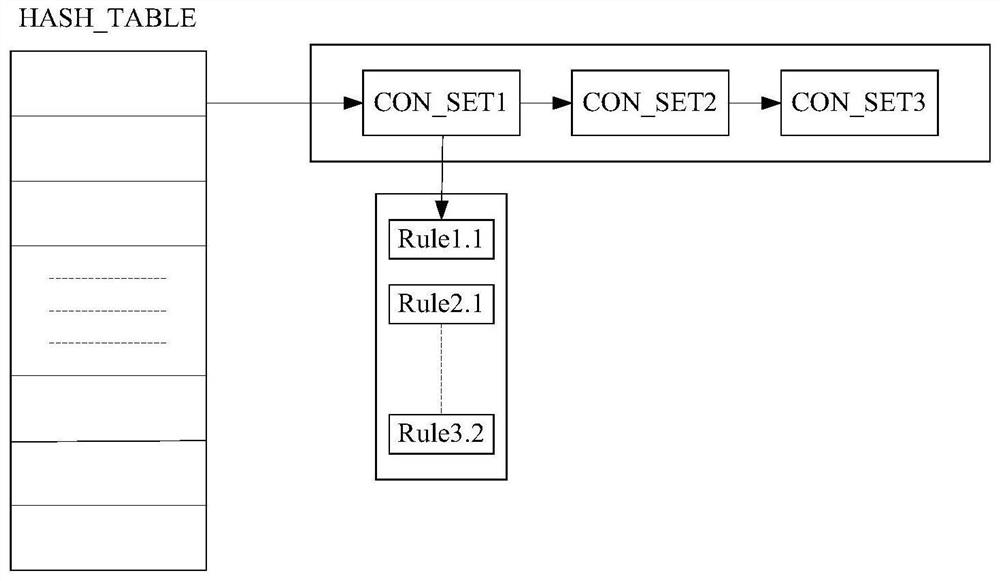
The invention provides an XACML strategy rule detecting method, belonging to the field of authorized strategy analysis in information safety. According to the XACML strategy rule, the method has a rule status definition, a rule status correlation definition and a conflict type analysis; on the basis, a strategy index based on a semantic tree is established, a concrete XACML strategy rule detection is carried out and the rule conflict and the rule redundancy are analyzed; the detection method comprises two types: a conflict detection method based on a property level operation correlation and a detection method for other typed conflicts based on the status correlation. In the redundancy analysis, the analysis determining method of the rule redundancy is given respectively in the algorithms of allowing priority, refusing priority and the first-time application dispelling. By adopting the detection method, the strategy manager can precisely locate the rules causing the conflict and the reasons for the conflict; in the redundancy analysis, according to the analysis result, the strategy structure can be optimized and the redundancy rules which has no influence on accessing the determining result can be deleted, therefore, the strategy determining efficiency is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Highly parallel evaluation of xacml policies
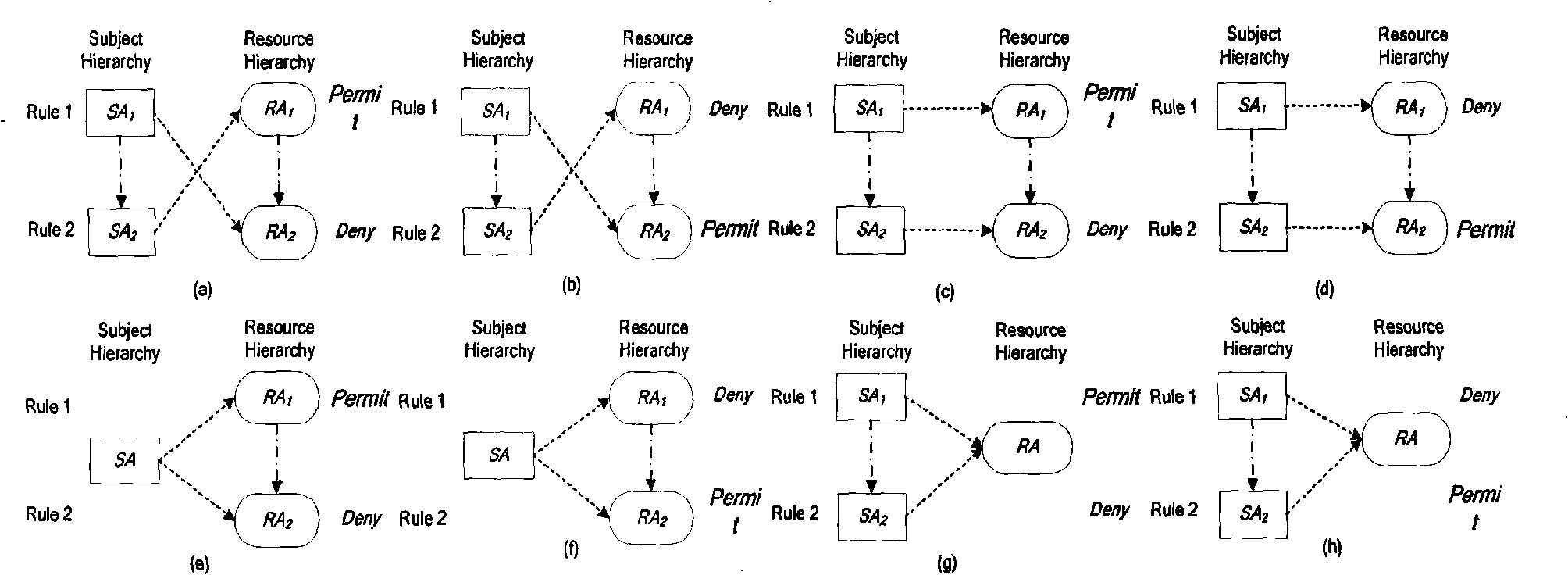
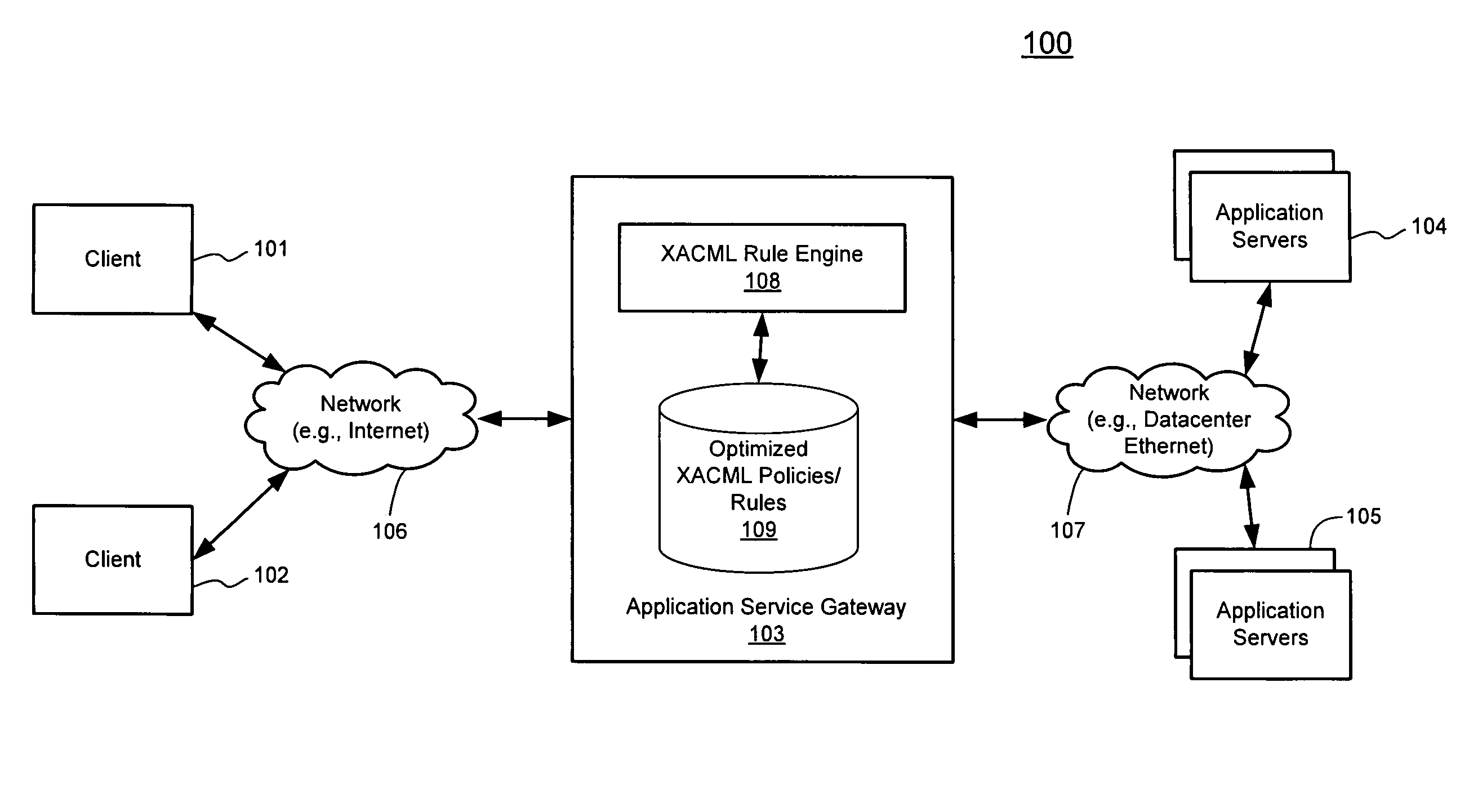
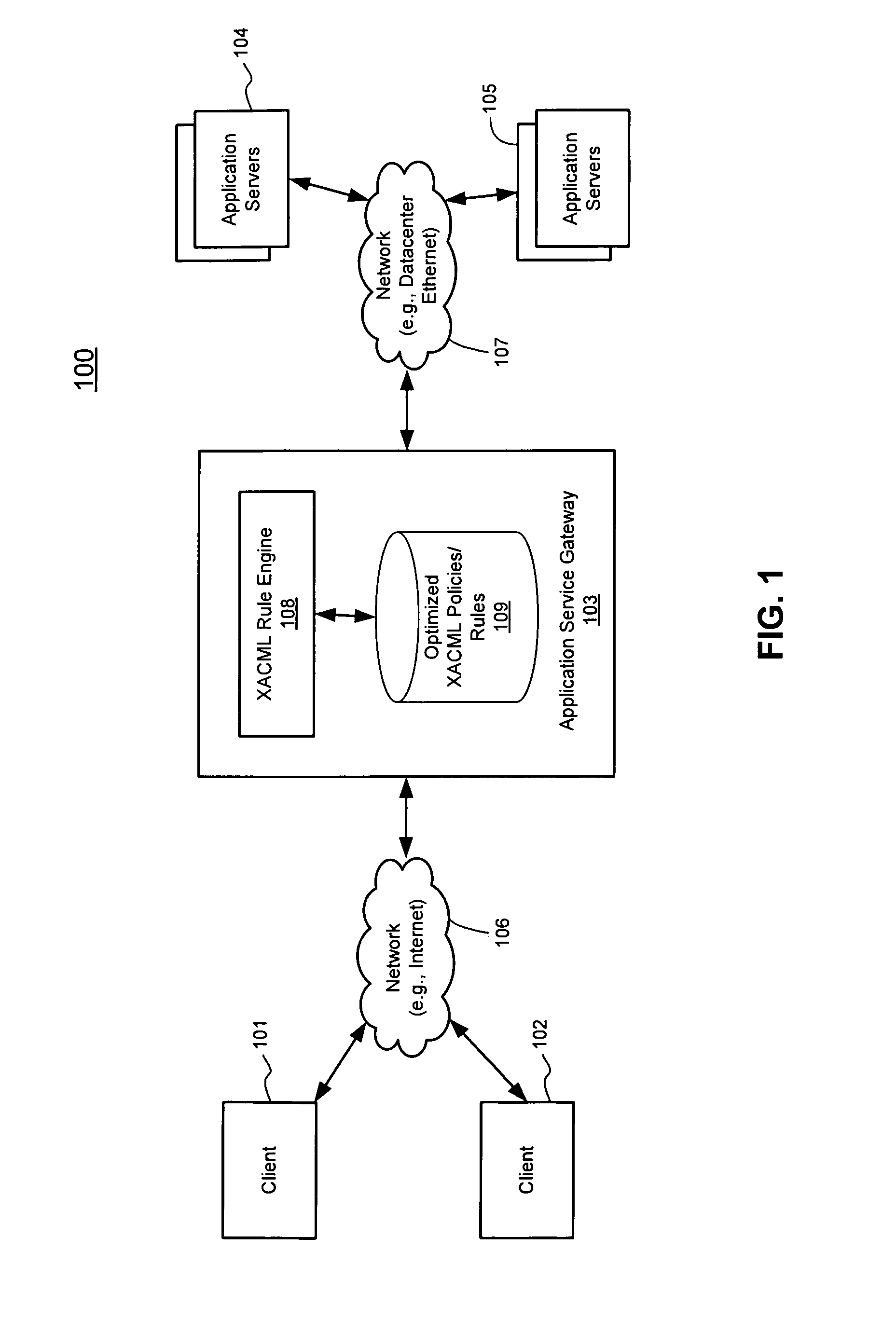
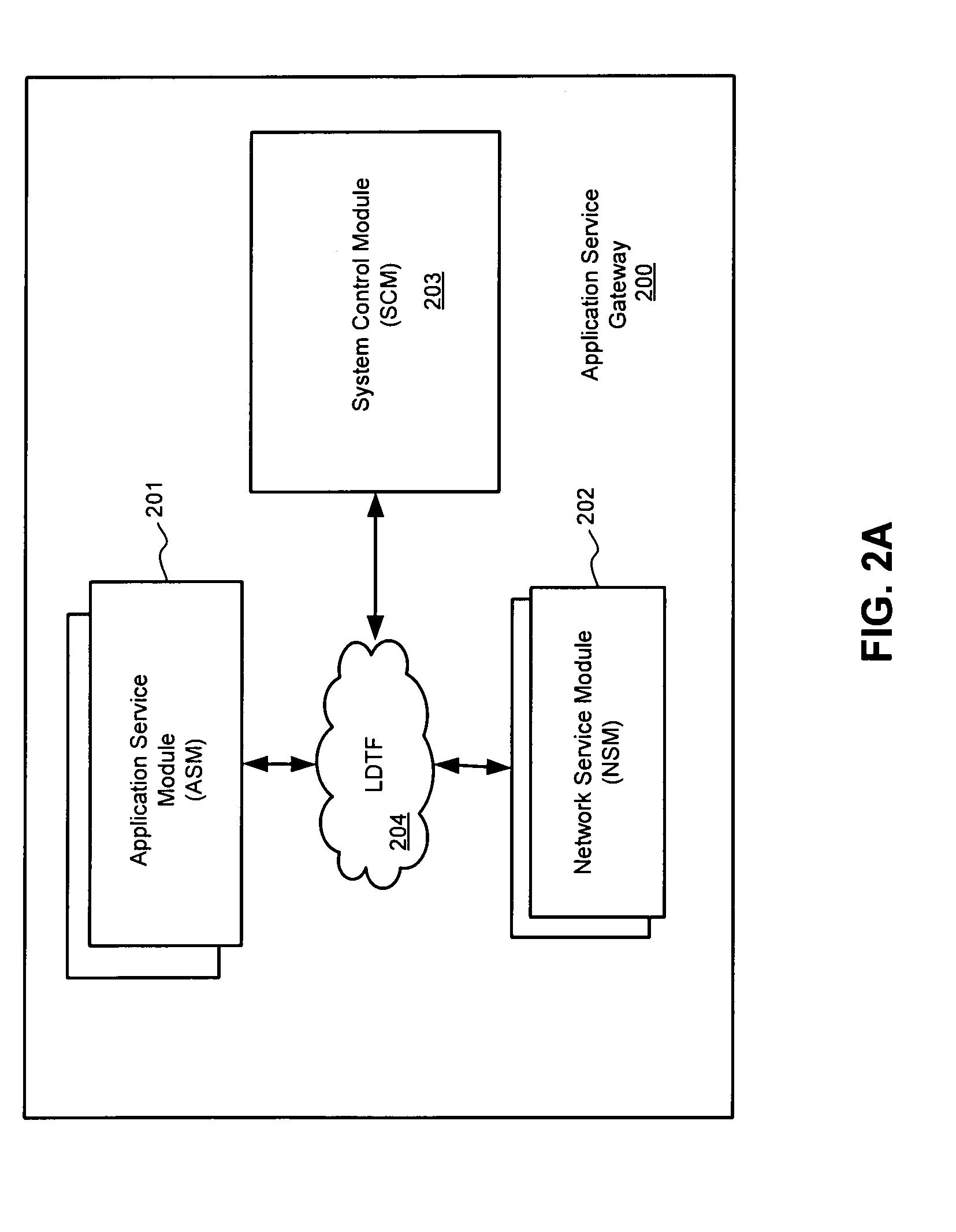
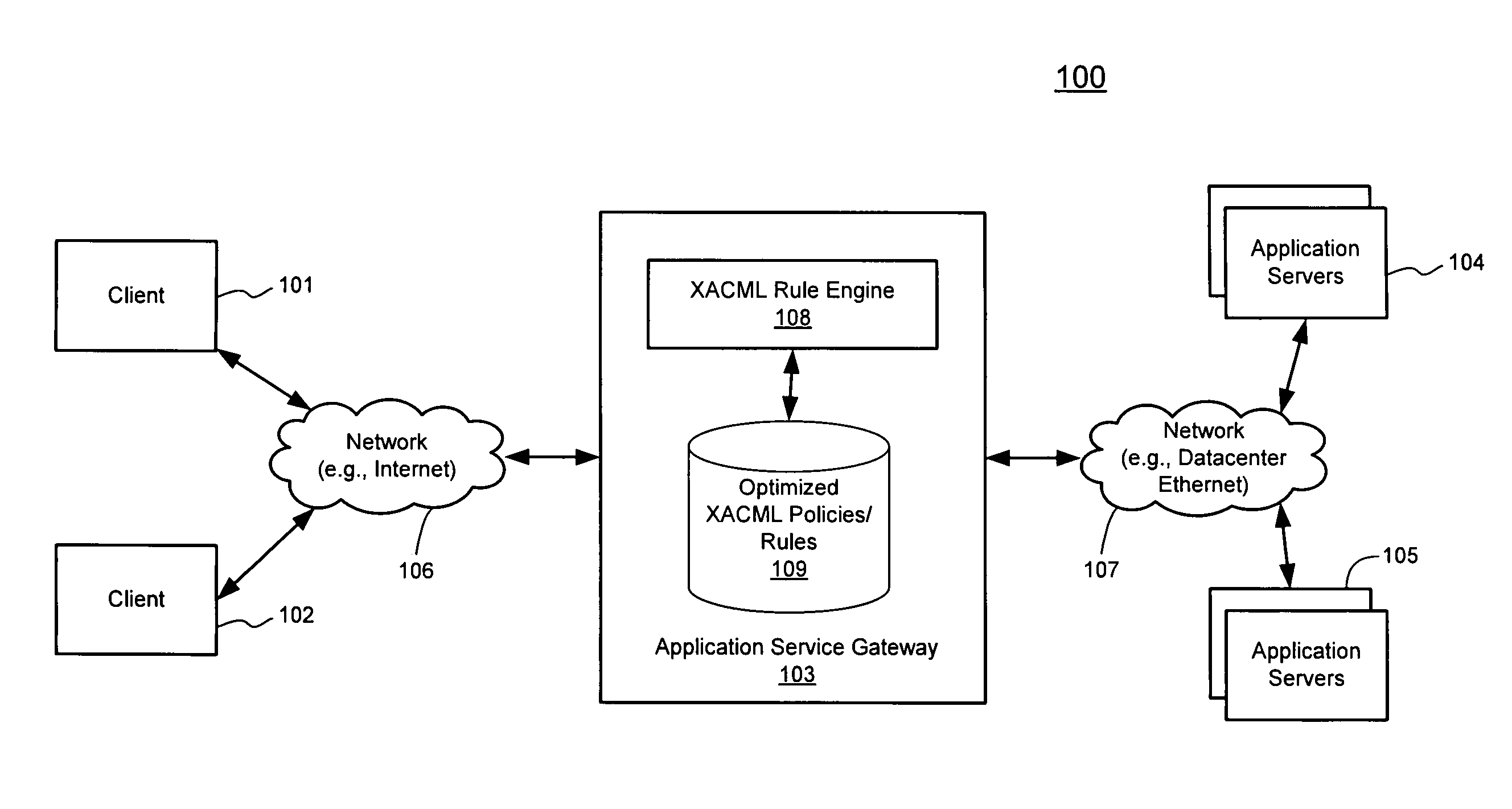
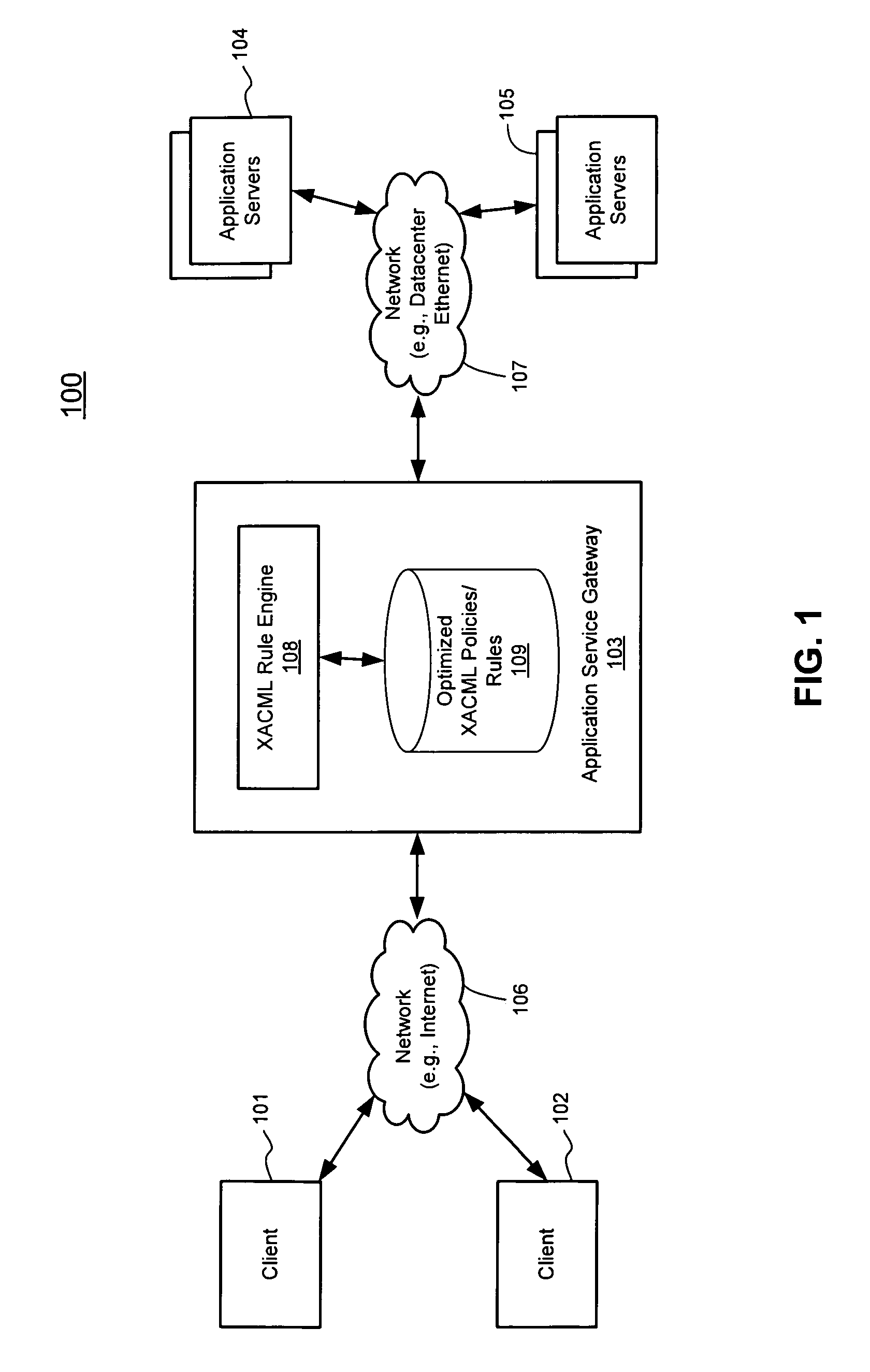
Techniques for highly parallel evaluation of XACML policies are described herein. In one embodiment, attributes are extracted from a request for accessing a resource including at least one of a user attribute and an environment attribute. Multiple individual searches are concurrently performed, one for each of the extracted attributes, in a policy store having stored therein rules and policies written in XACML, where the rules and policies are optimally stored using a bit vector algorithm. The individual search results associated with the attributes are then combined to generate a single final result using a predetermined policy combination algorithm. It is then determined whether the client is eligible to access the requested resource of the datacenter based on the single final result, including performing a layer-7 access control process, where the network element operates as an application service gateway to the datacenter. Other methods and apparatuses are also described.
Owner:CISCO TECH INC
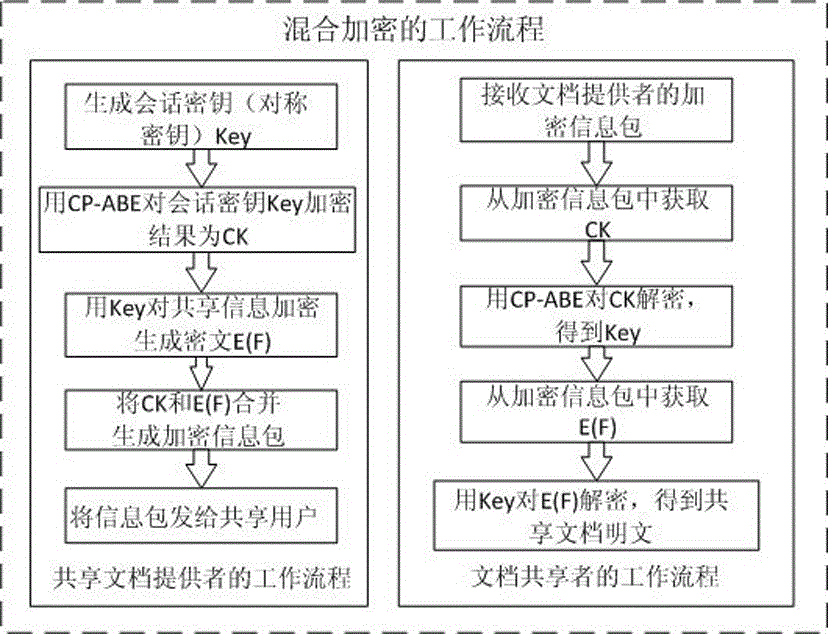
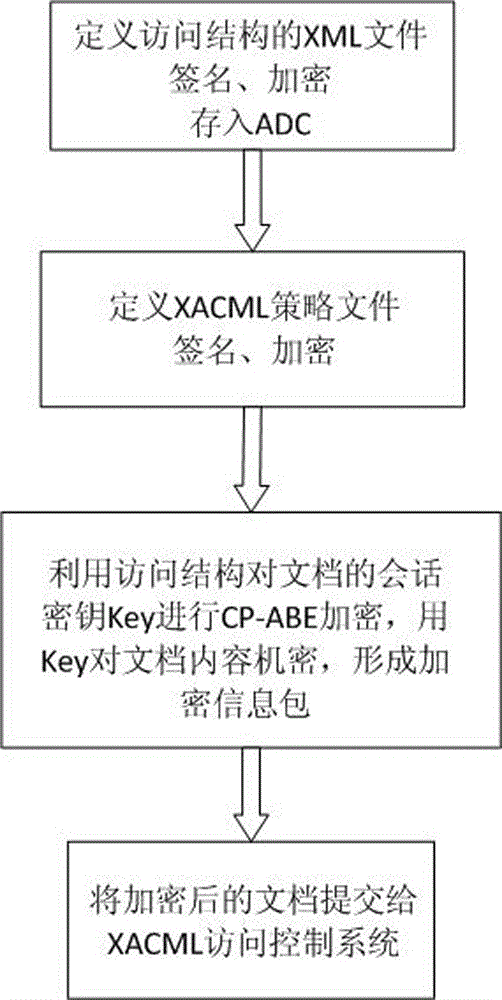
Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption)
ActiveCN105991278AEnsure safetyKey distribution for secure communicationAccess structureControl system
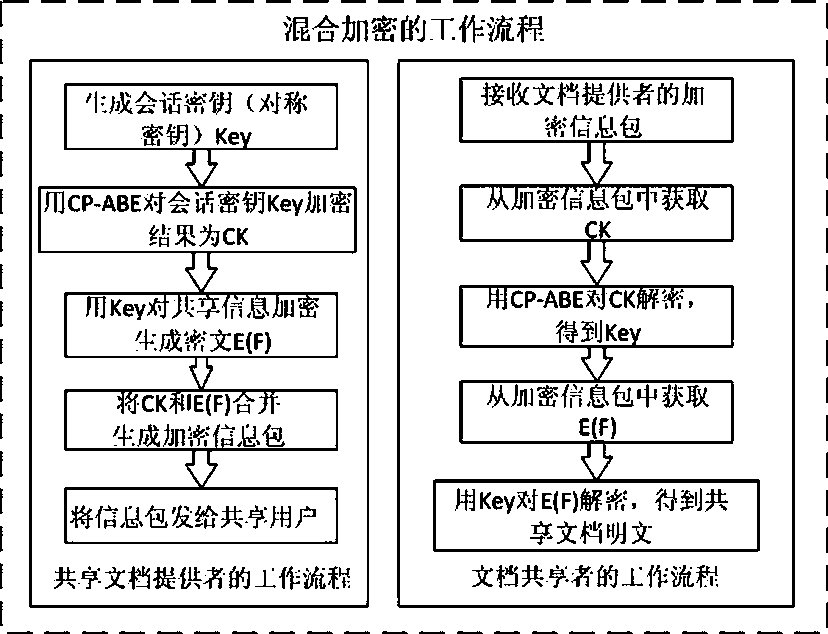
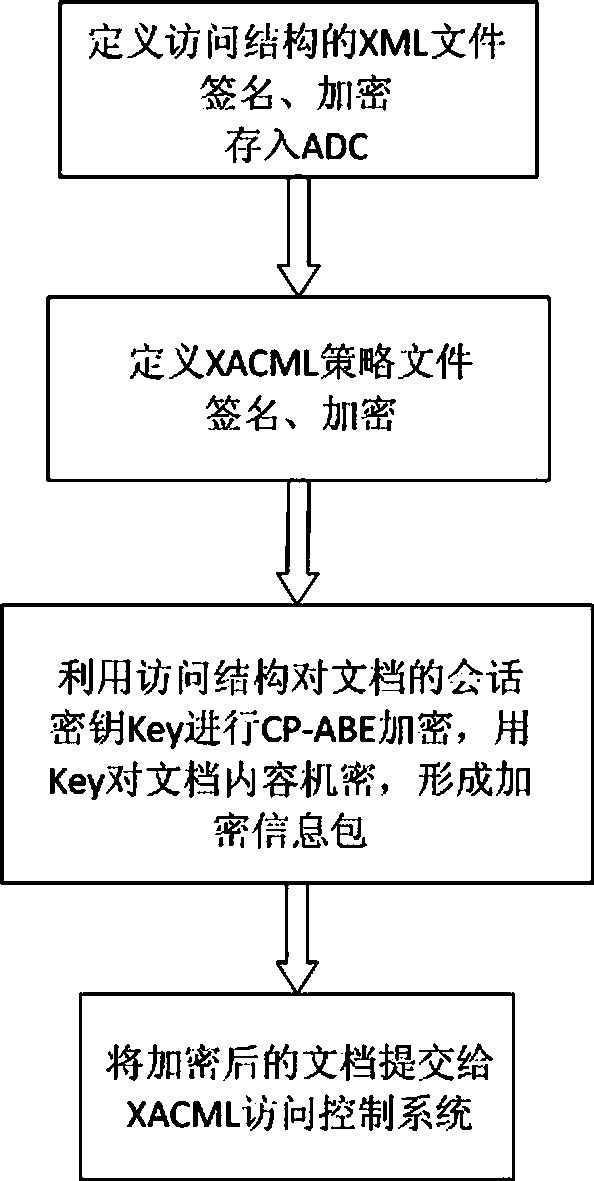
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Authorization policy objects sharable across applications, persistence model, and application-level decision-combining algorithm
ActiveUS9471798B2Digital data protectionData switching networksApplication softwareCombination algorithm
A global policy store, in which policies applicable to multiple applications in an enterprise environment can be stored, can be stored in association with that environment. An application-level policy combining algorithm can be associated with a specific application to resolve conflicts between the results of evaluating policies that pertain to that application's resources. A persistent model is defined for an Extensible Access Control Markup Language (XACML) target definition.
Owner:ORACLE INT CORP
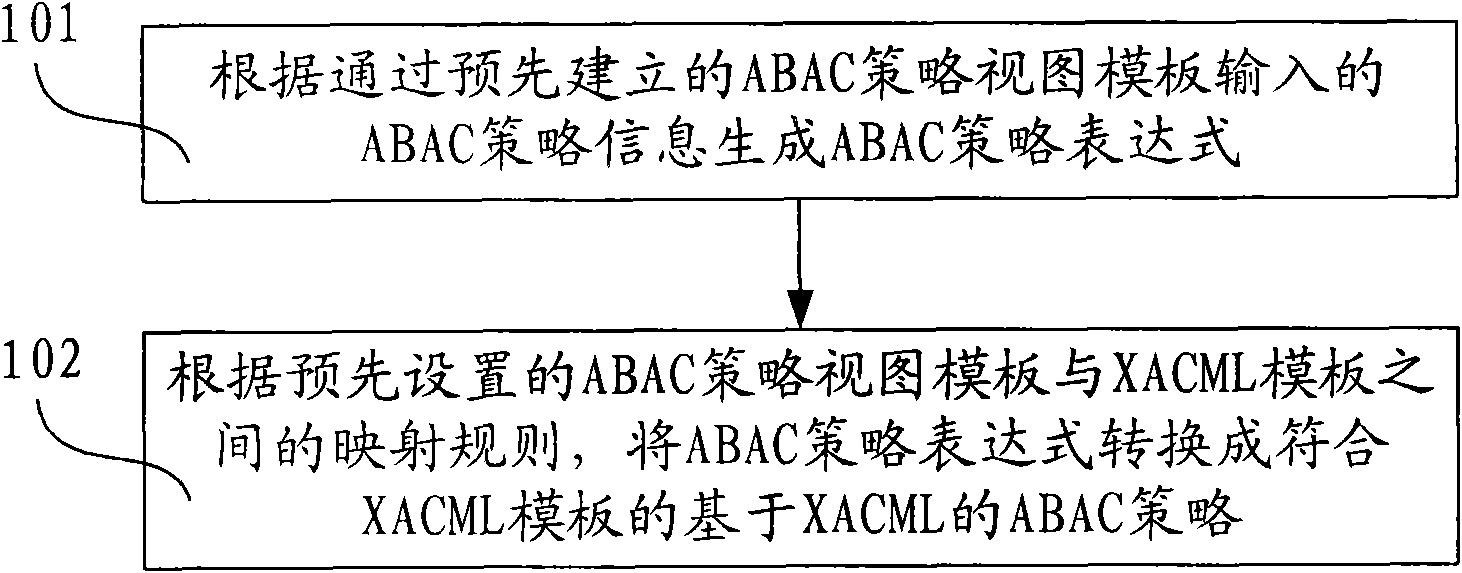
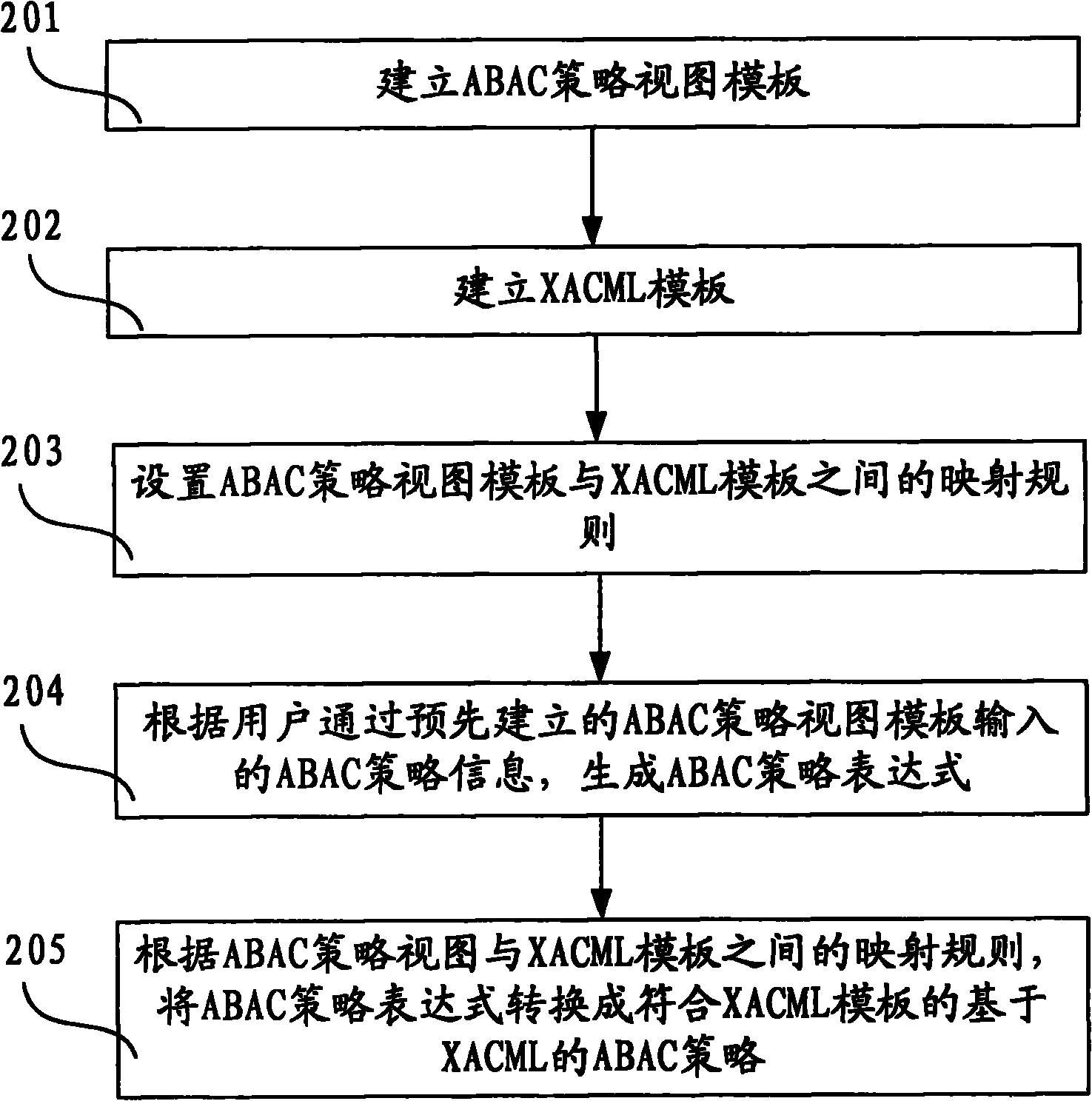
Method and device for generating access controlling policy
InactiveCN101771683AGuaranteed accuracyReduce the burden onData switching networksSpecial data processing applicationsXACMLWorld Wide Web
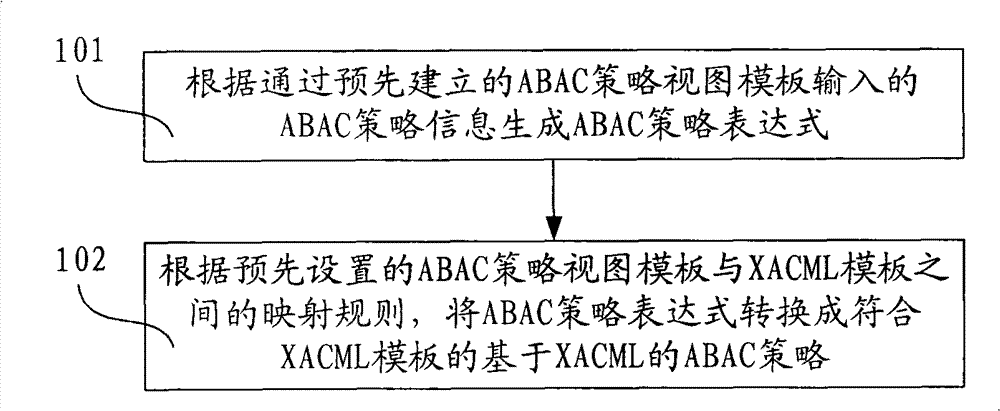
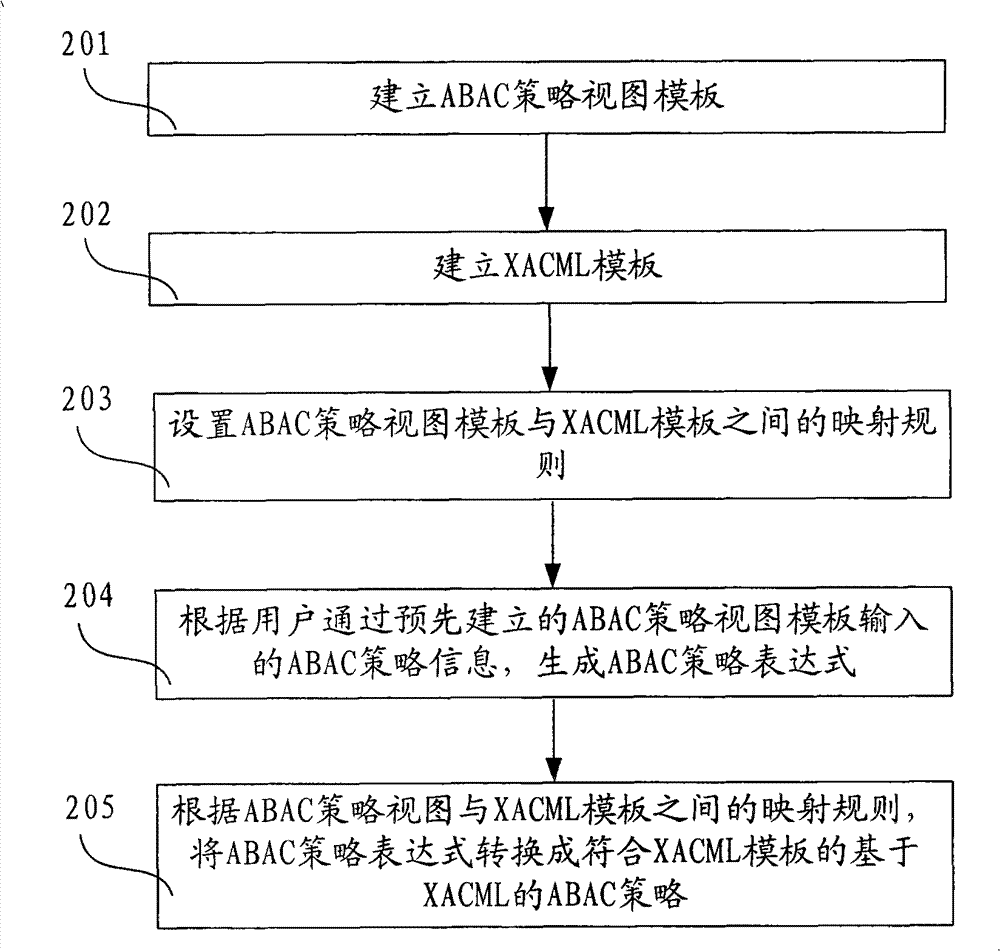
The invention discloses method and device for generating an access controlling policy. The method comprises the following steps of: generating an ABAC policy expression according to ABAC policy information input by a user through a pre-established attribute-based access control (ABAC) policy view template; and converting the ABAC policy expression into an ABAC policy which is based on XACML and conforms to the XACML template according to mapping rules of the preset ABAC policy view template and an extensible access control markup language (XACML) template. In the invention, the user only needs to input some simple ABAC policy information through the ABAC policy view template and does not need to write a complicated ABAC policy based on XACML in a manual mode, therefore, the problem that the user difficultly defines the ABAC policy based on XACML is solved, the problem that errors are made in the process of writing the complicated ABAC policy based on XACML in a manual mode by the useris avoided, and the accuracy of the ABAC policy based on XACML is ensured.
Owner:BEIHANG UNIV
Provisioning user permissions using attribute-based access-control policies
InactiveUS20130081105A1Computational savingImprove variationDigital data authenticationTransmissionUser PrivilegeTheoretical computer science
An attribute-based access control policy (e.g., XACML policy) for a set of elements depends on attributes carried by elements in one of several predefined categories. In order to evaluate such policy for a set of elements, the invention provides a method including the steps of (I) selecting a primary category; (II) partitioning the elements in the primary category into equivalence classes with respect to their influence on the policy; and (III) using the equivalence classes to replace at least one policy evaluation by a deduction. The result of the evaluation may be represented as an access matrix in backward-compatible format. The efficiency of the policy evaluation may be further improved by applying partial policy evaluation at intermediate stages, by forming combined equivalence classes containing n-tuples of elements and / or by analyzing the influence of each element by extracting functional expressions of maximal length from the policy.
Owner:AXIOMATICS
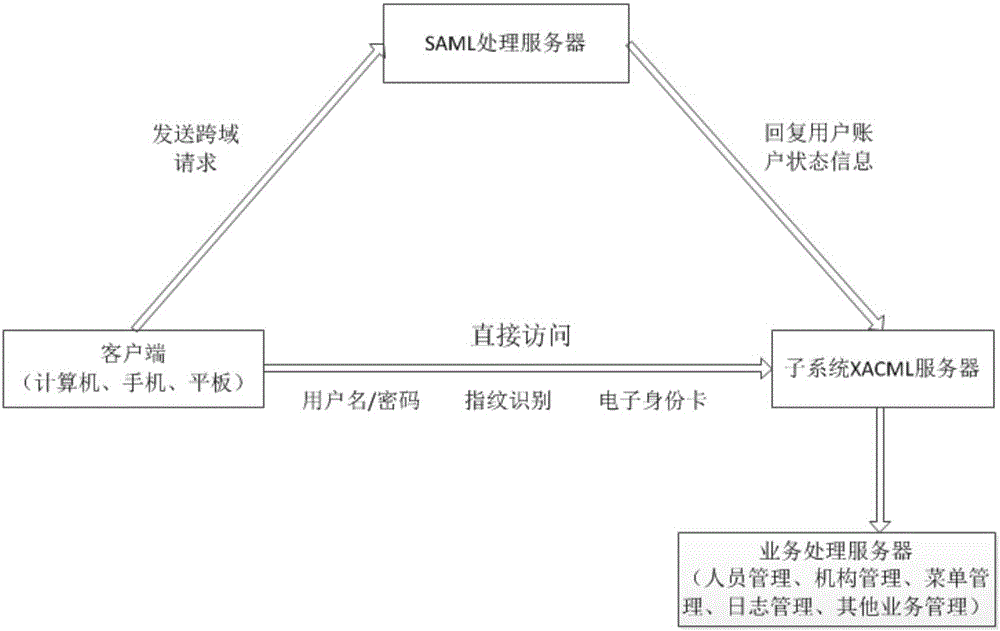
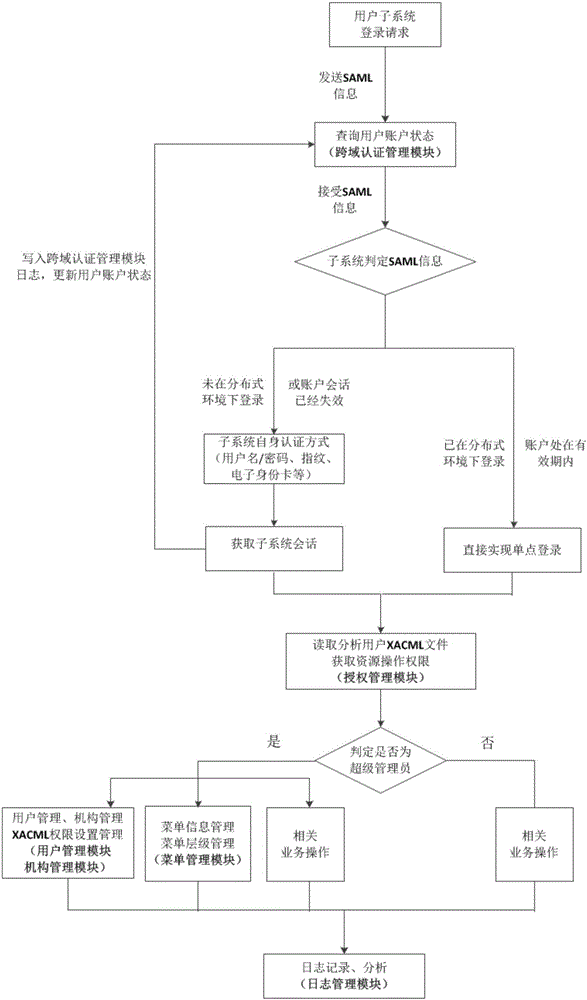
Distributed system authentication and permission management platform based on XACML and SAML under big data environment
ActiveCN106534199AImprove scalabilityMake up for security issuesTransmissionUser PrivilegeFrame based
The invention discloses a distributed system authentication and permission management platform based on XACML and SAML under a big data environment. The platform comprises a cross-domain authentication management module, an authorization management module, an organizational management module, a personnel management module, a menu management module and a log management module, wherein the cross-domain authentication management module is arranged on an SAML processing server, the authorization management module is arranged on a sub-system XACML server, and the organizational management module, the personnel management module, the menu management module and the log management module are all arranged on a business processing system server. The platform utilizes the XACML to perform authorization and access control on a user, and authenticate the identity of the user by using cross-domain data interaction of the SAML. User permission is limited by reading an XACML file of the user and using an XACML frame based on a RBAC access control module, and thus authorization on user granularity is greatly enhanced. In a distributed system, the different platform provides assertion by exchanging SAML information, so that information transmission between the platforms is safer, and the data transmission quantity is less.
Owner:东台城东科技创业园管理有限公司
Dynamic policy-based entitlements from external data repositories
ActiveUS20140282831A1Narrow search spaceTransmissionSpecial data processing applicationsPolicy decisionValue set
A machine-implemented method for evaluating a context-based (e.g., XACML) policy having a set of attributes formulates a search against one or more existing external repositories using a query that is dynamically-generated based on the security policy being evaluated. The approach shifts the building of a candidate set of potentially-allowable resources to the authorization engine (e.g., a Policy Decision Point (PDP)). In operation, an application calls the PDP using an entitlement request and, in response, the PDP builds the candidate set of values based on the defined security policy by generating a query to an external data repository and receiving the results of that query. This approach enables a policy-driven entitlement query at runtime.
Owner:IBM CORP
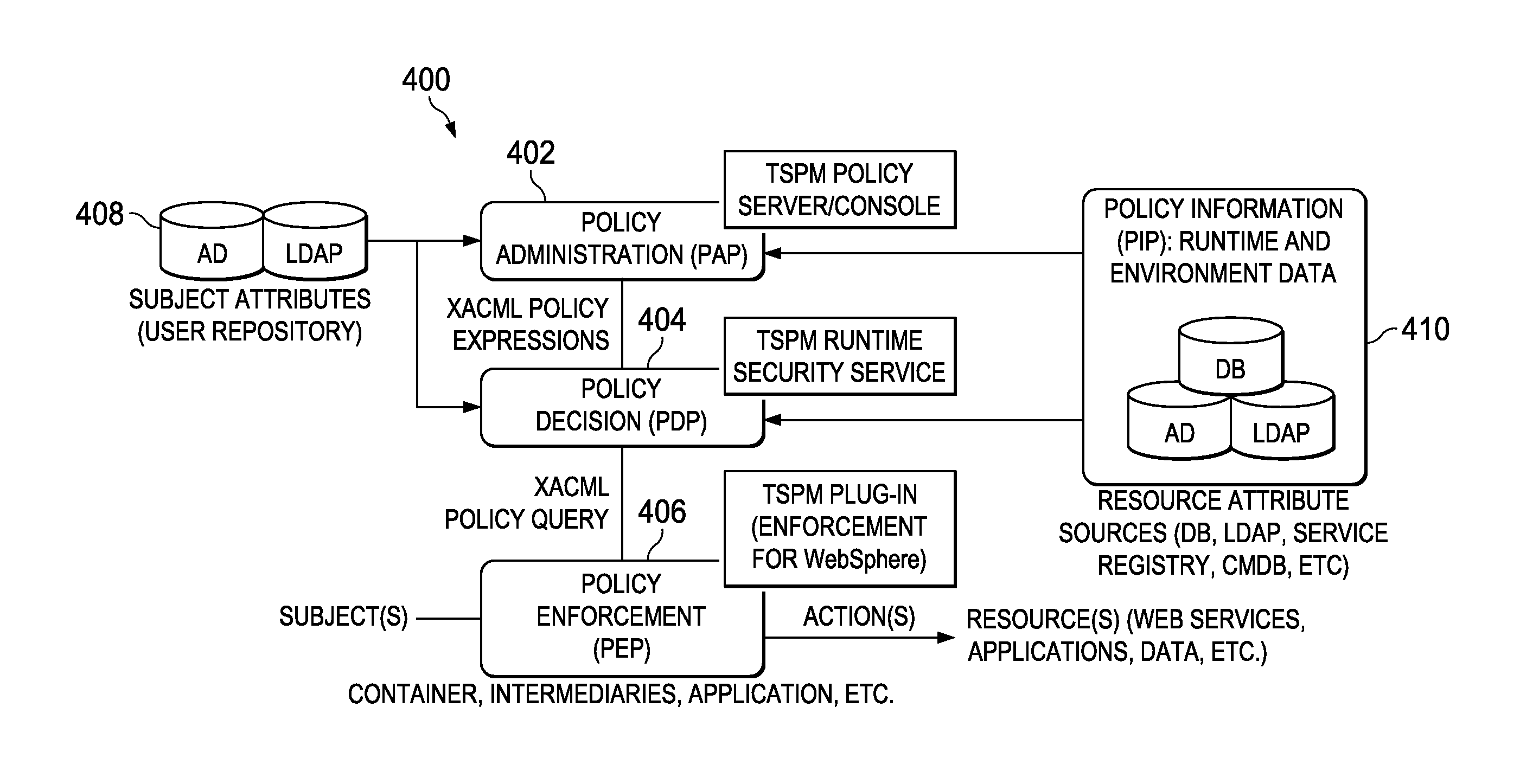
Extensible access control markup language (XACML) strategy assessment engine system based on various optimization mechanisms
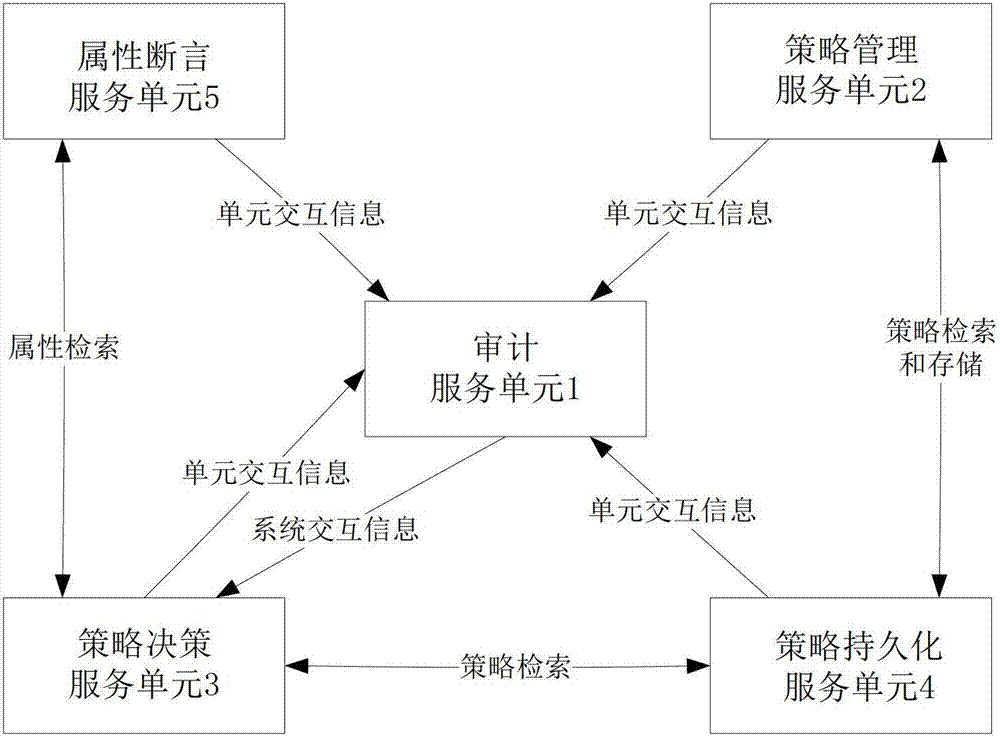
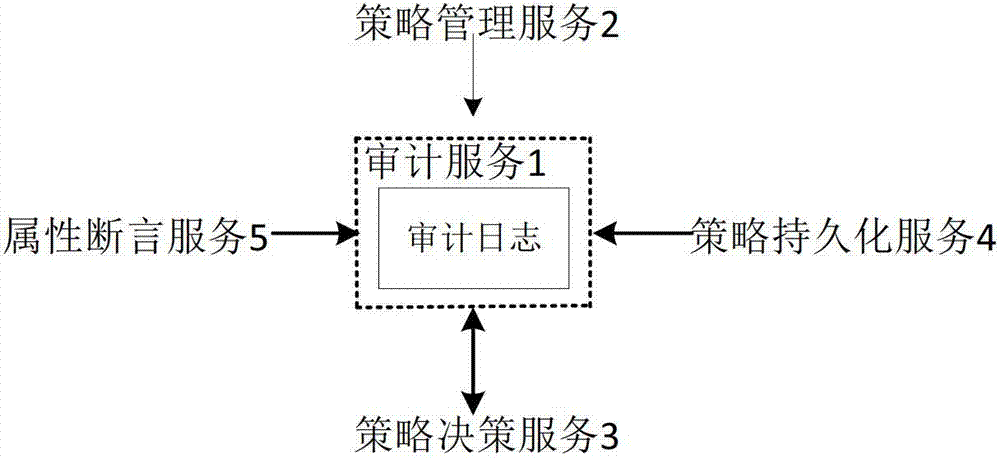
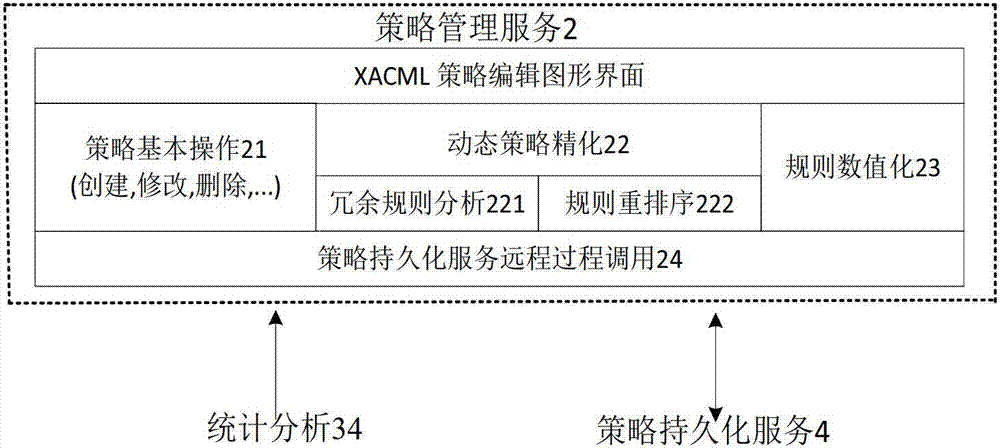
ActiveCN103198361AImprove evaluation efficiencyImprove efficiencyForecastingPolicy decisionDecision taking
The invention provides an extensible access control markup language (XACML) strategy assessment engine system based on various optimization mechanisms. The problem that an existing XACML strategy assessment engine system cannot make a correct decision on access requests sent by a large number of users at the same time is solved. The system comprises an audit service (1), a strategy management service (2), a strategy decision service (3), a strategy persistence service (4) and an attribute assertion service (5). The audit service (1) records mutual information of the system. The strategy management service (2) provides a centralization type patterned strategic management platform. The strategy decision service (3) decides a user request. The strategy persistence service (4) provides a strategy storage function and a strategy search function. The attribute assertion service (5) provides an attribute storage function and an attribute search function. The system has the advantages of being high in assessment efficiency, small in matching computing amount, quick in matching speed and easy to integrate, the system can be used in distributed environment and can make the correct decision on the access requests sent by the large number of users.
Owner:XIDIAN UNIV
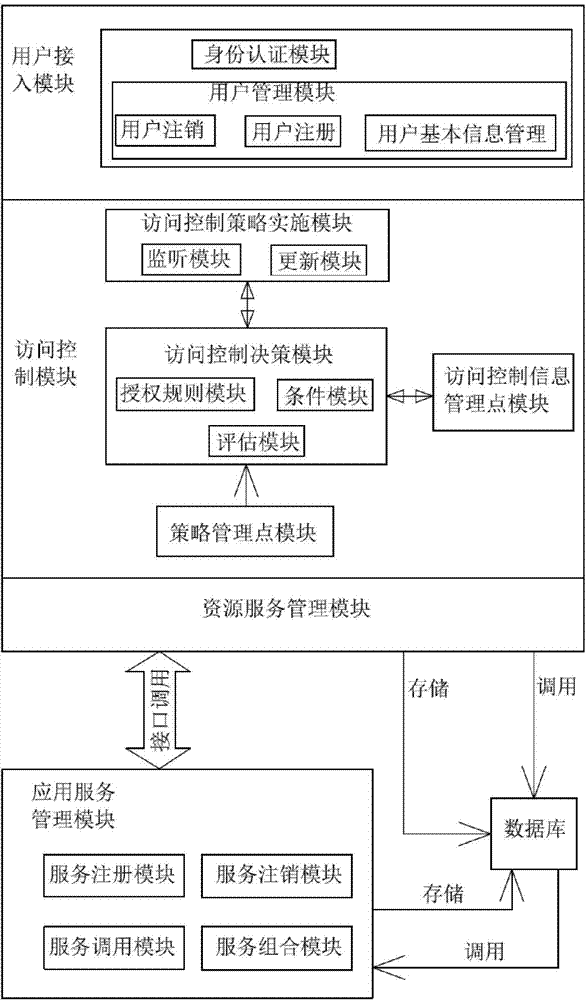
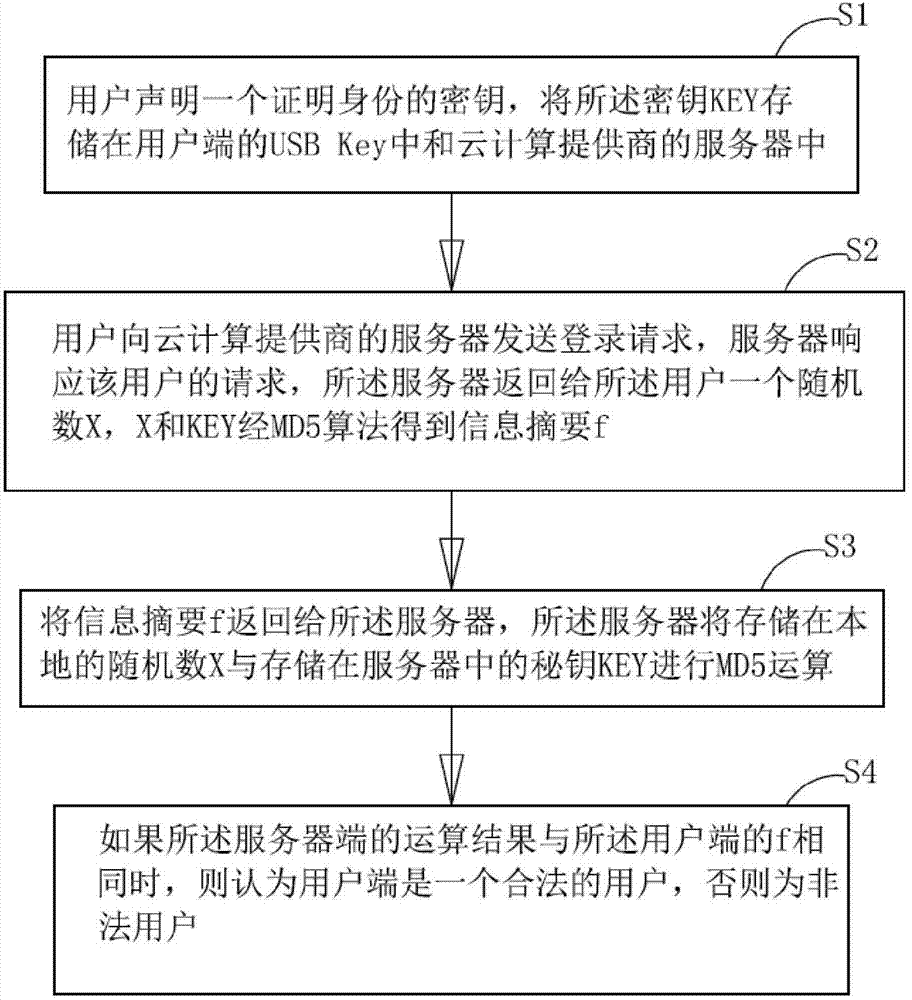
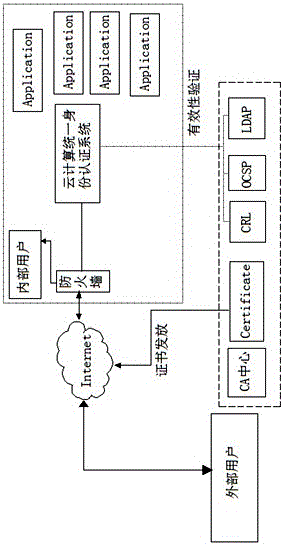
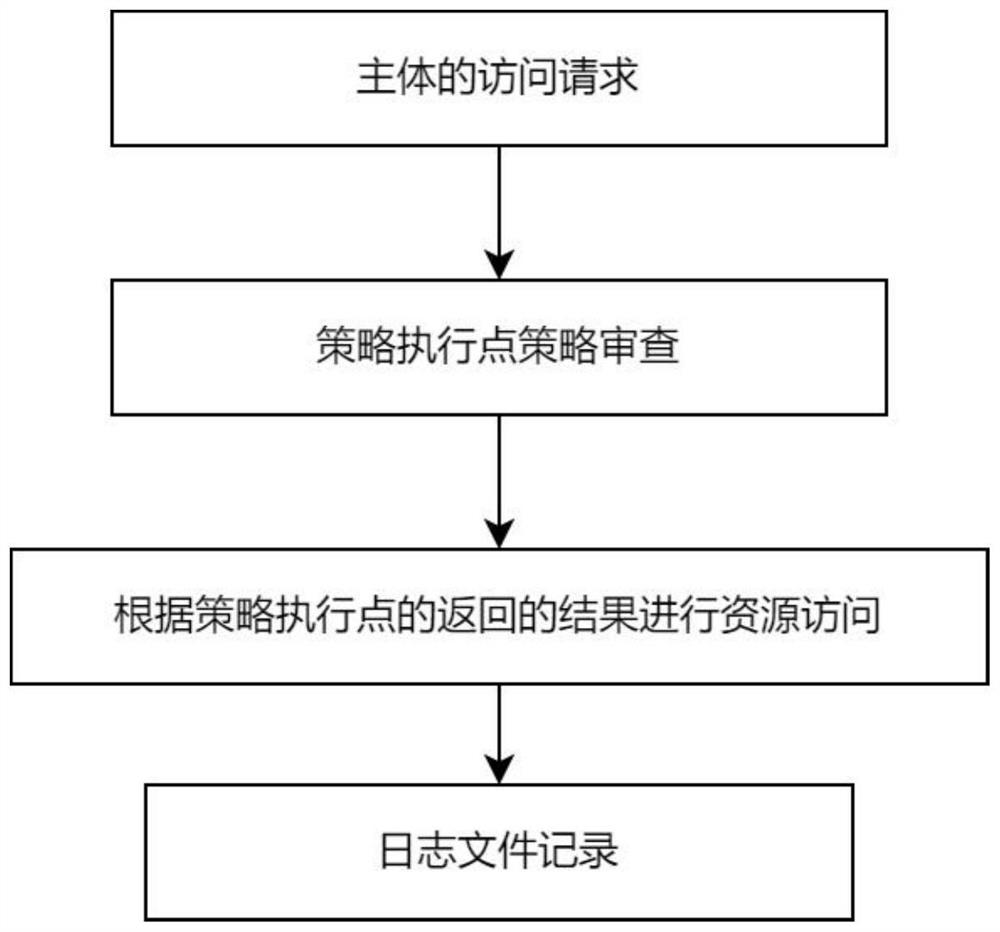
Cloud computing access control system and method
The invention relates to a cloud computing access control system and method. The cloud computing access control system comprises a user access module which is used for realizing that a user sends a login request to a server of a cloud computing provider, the server responding to the login request of the user, and comprises an identity authentication module and a user management module; an access control module which is used for converting the login request of the user into an XACML format request and controlling and managing access right; a resource service management module which is used for managing different user access resources and monitoring and recording information of the user in the using process for log management; and an application service management module which is for initiating a call request to the resource service management module through a public interface, and comprises a resource service login module, a resource service deleting module and a resource service calling module. Through the organic integration of the monitoring mechanism and the XACML, flexibility of the authorization is enhanced; and the cloud computing access control system has fine grain performance, dynamic nature, extendibility and more security.
Owner:张勇平
Ciphertext data sharing system in cloud computing environment
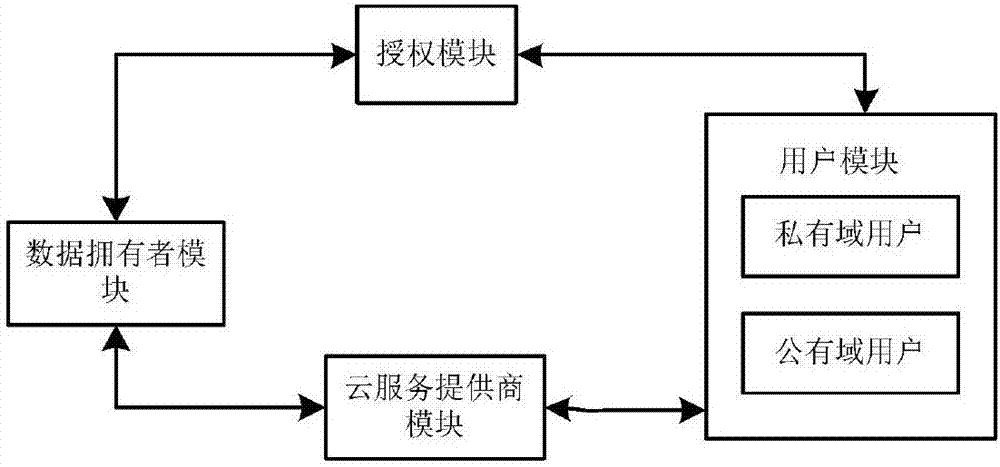
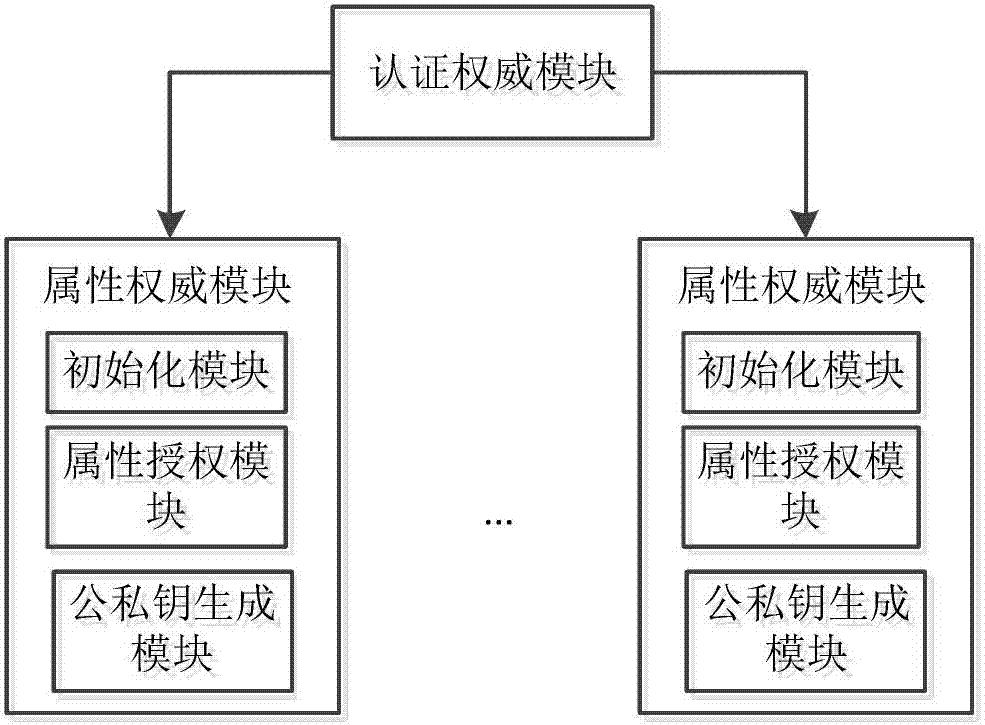
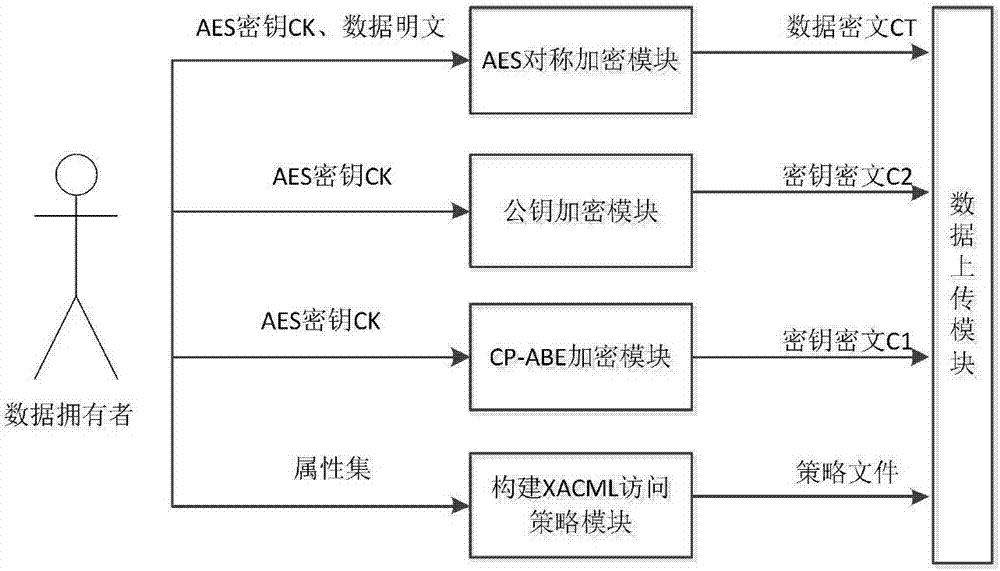
ActiveCN107302524AImprove sharing efficiencyNo bottlenecksTransmissionInformation sharingMultiple attribute
The invention provides a ciphertext data sharing system in a cloud computing environment, used for solving the technical problems of high attribute cancellation cost and low user data sharing efficiency in the existing ciphertext data sharing system. The ciphertext data sharing system comprises an authorization module, a data owner module, a user module and a cloud service provider module, wherein the authorization module comprises multiple attribute authority modules; the various attribute authority modules have the hierarchical or parallel relationship; the data owner module comprises a construction XACML access strategy module used for generating a strategy file; the user module comprises a private key decryption module and a CP-ABE decryption module; the private key decryption module is used for decrypting AES key cyphertext data of private domain users; and the CP-ABE decryption module is used for decrypting AES key cyphertext data of public domain users. The ciphertext data sharing system provided by the invention can be used for information sharing in the data exchange field in the cloud computing environment.
Owner:XIDIAN UNIV
Highly parallel evaluation of XACML policies
InactiveUS8677453B2Digital data processing detailsComputer security arrangementsData centerService gateway
Owner:CISCO TECH INC
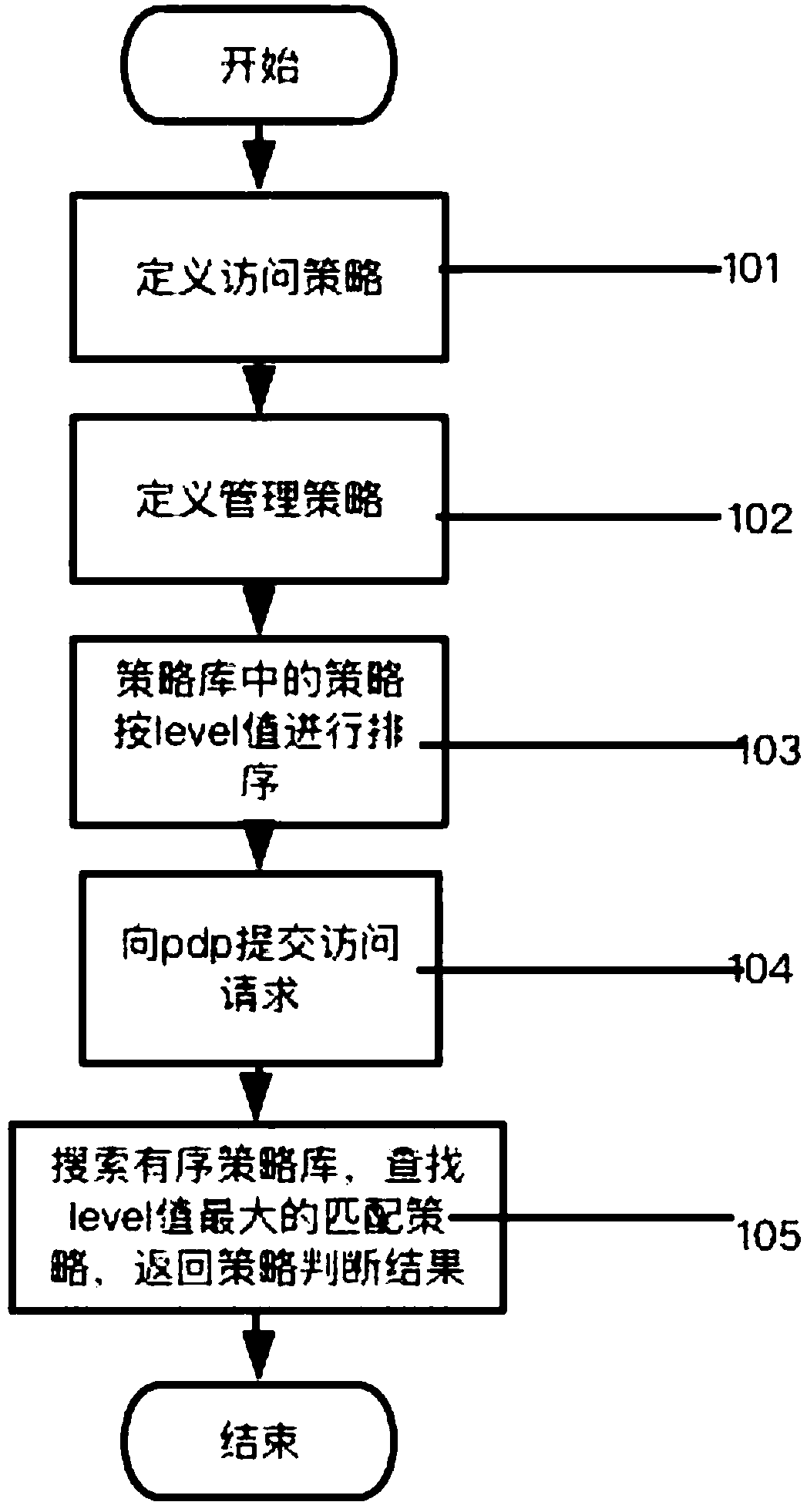
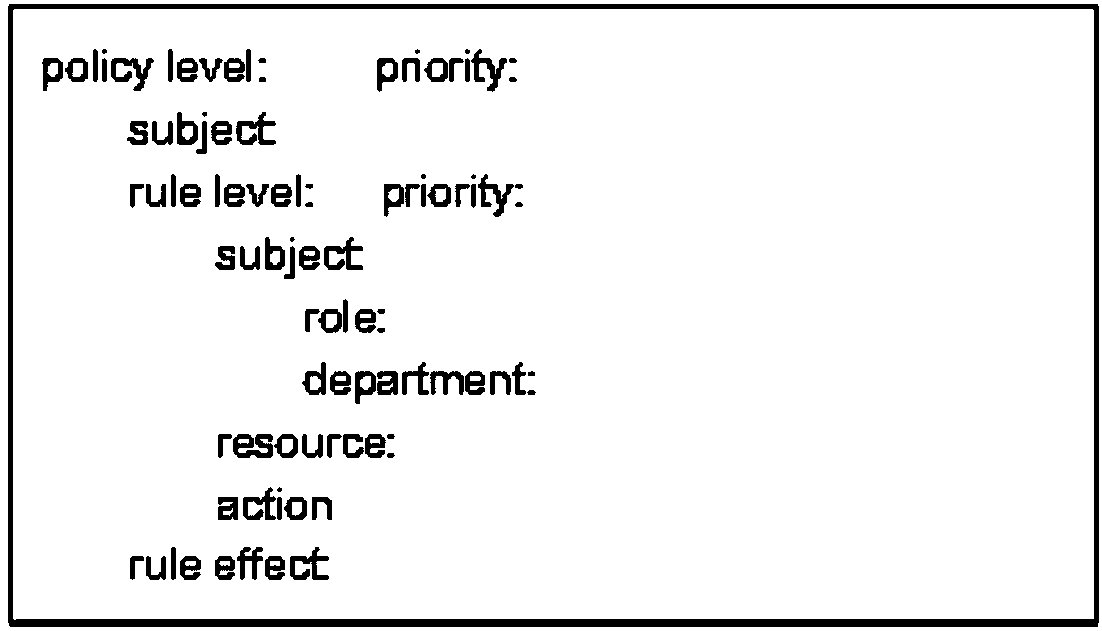
Ordering policy authorization method and system for extended xacml access control
The invention discloses an ordering policy authorization method and system for extended xacml access control. The method comprises the following steps of: S1, defining and generating an access policy;S2, defining and generating a management policy and obtaining a policy library; S3, carrying out ordering on policies in the policy library according to level values from big to small; S4, submittingan access request to a pdp (Policy Determination Point) of an xacml access framework; and S5, searching the ordered policy library, and returning a determination result of a policy with the maximum level value. By the ordering policy authorization method and system disclosed by the invention, search efficiency of the authorized policy can be improved.
Owner:SUN YAT SEN UNIV
Distributed security information and event management system with application-injected remote components
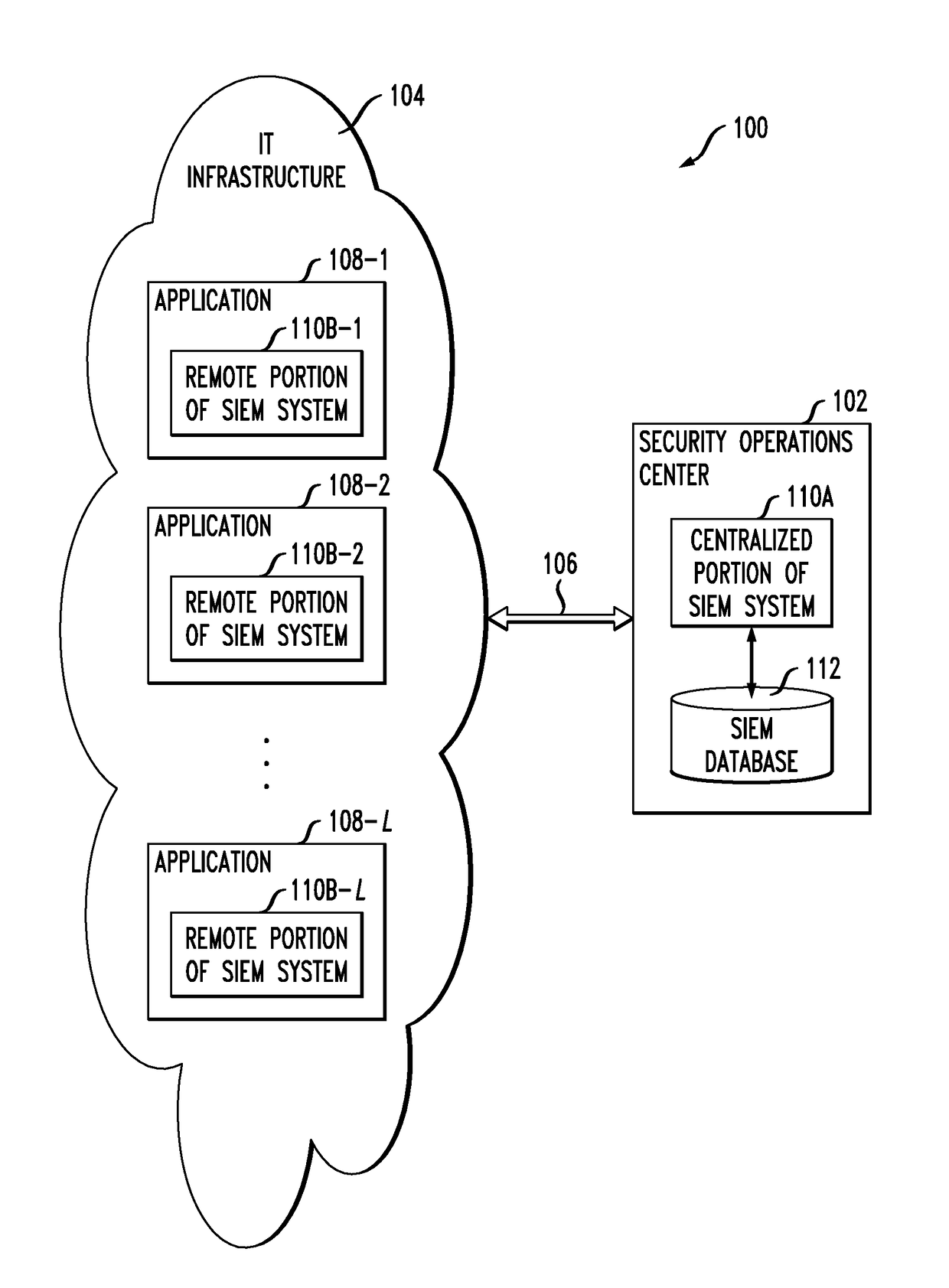
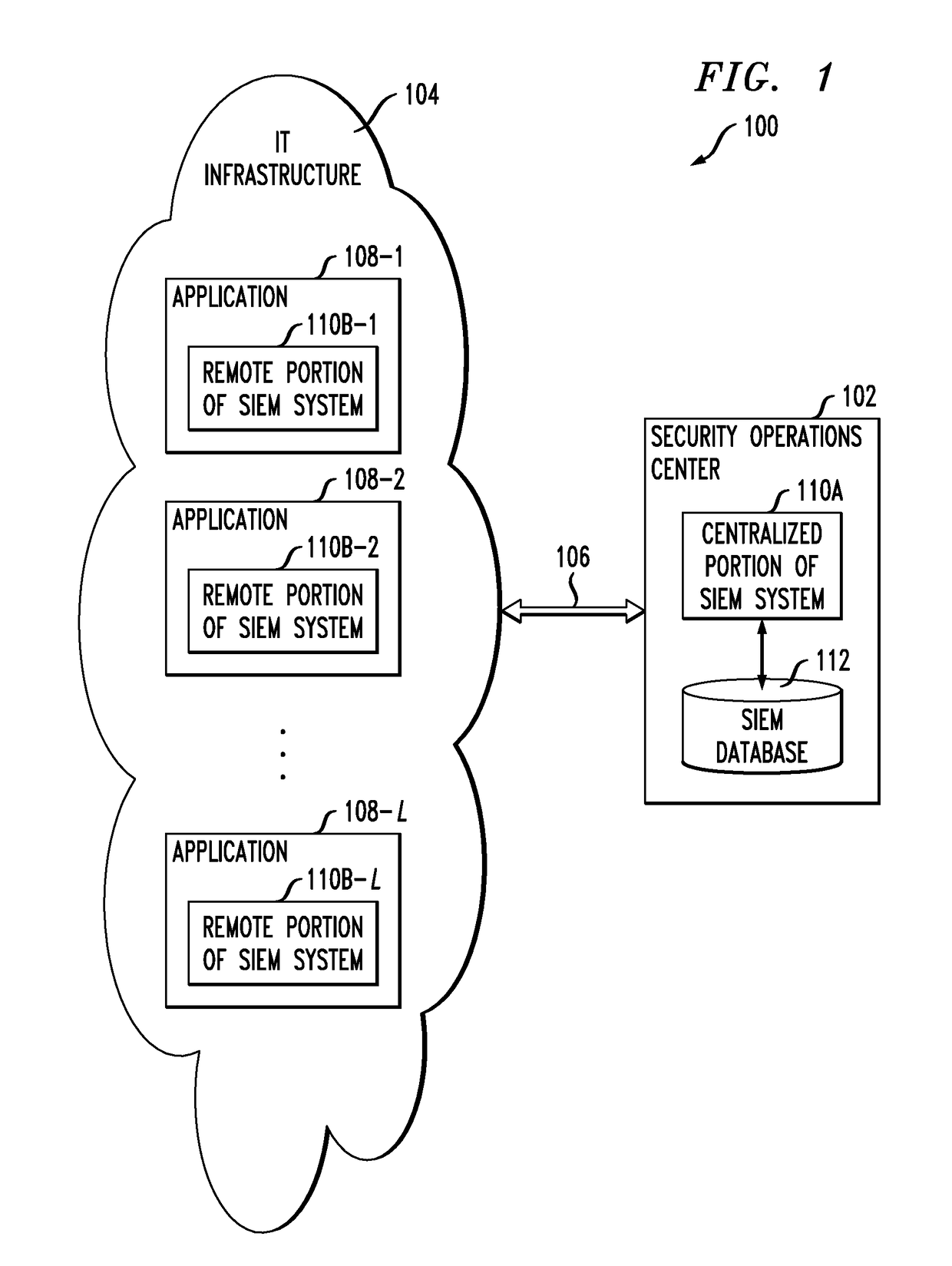
ActiveUS10129072B1Avoid lostTo offer comfortData switching networksSecurity information and event managementDistributed security
A distributed security information and event management system comprises a centralized portion and a plurality of remote portions, with the remote portions being implemented in respective applications within information technology infrastructure. Each of the remote portions comprises one or more remote components inserted into the corresponding application. At least a subset of the remote components of the remote portion are configured for interaction with one or more corresponding centralized components of the centralized portion of the system. The remote components may each be configured to process one or more specified eXtensible Access Control Markup Language (XACML) Obligations or other constructs.
Owner:EMC IP HLDG CO LLC
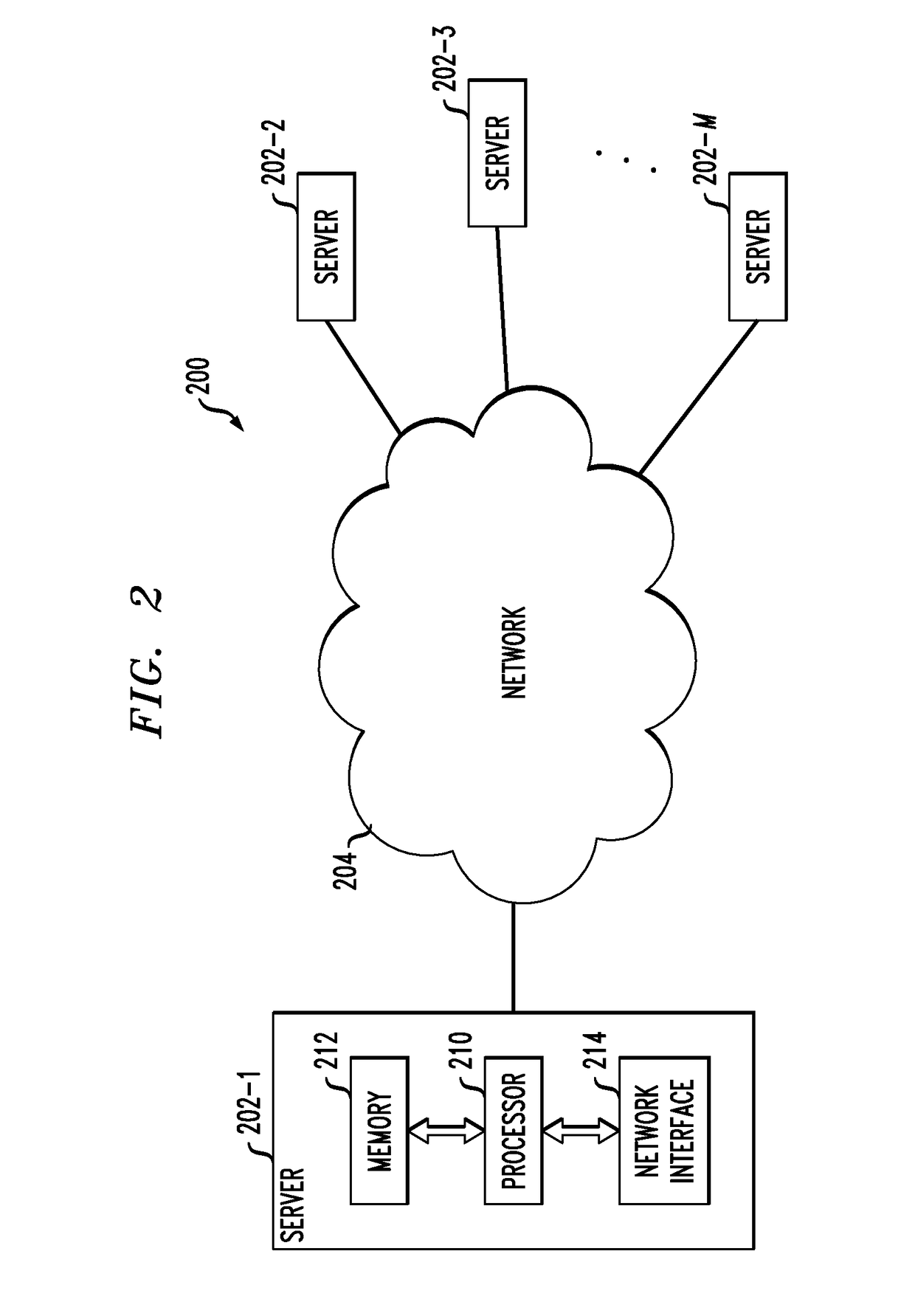
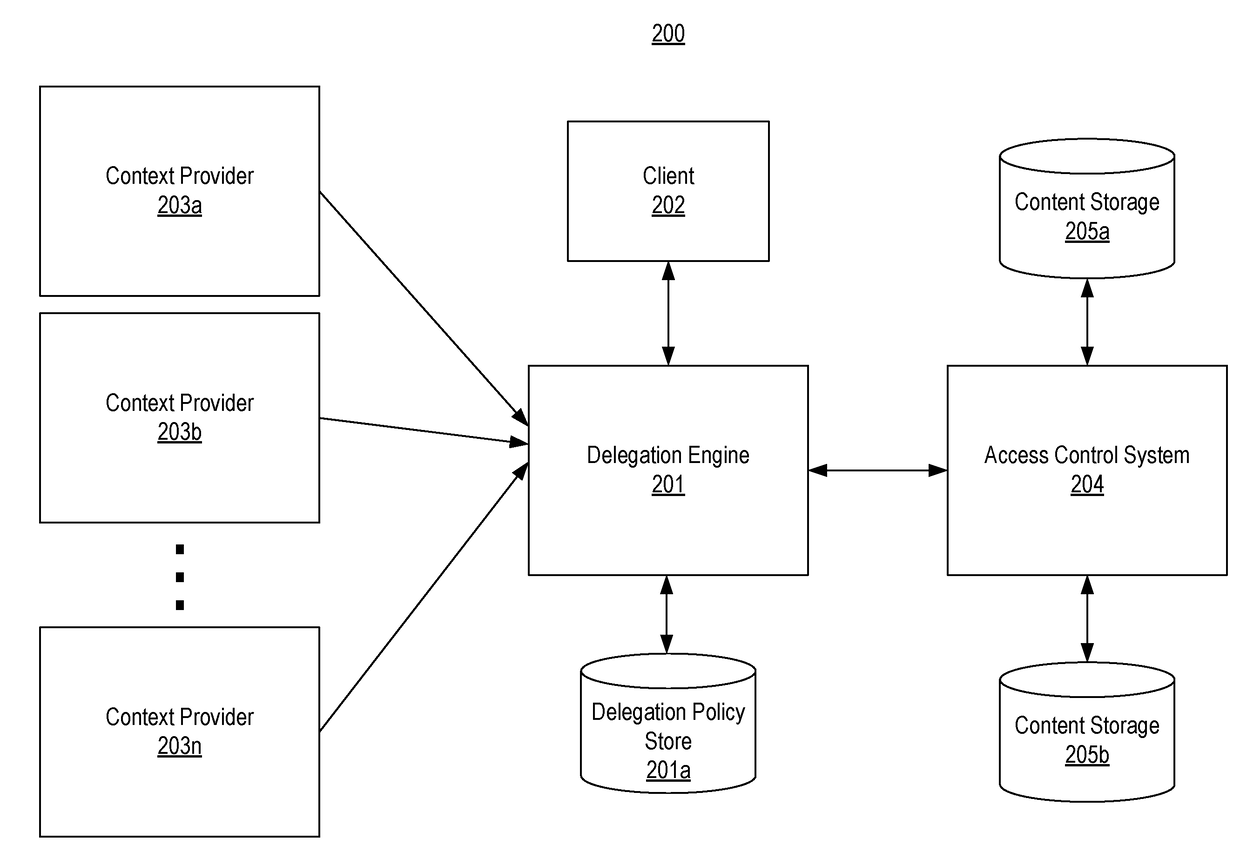
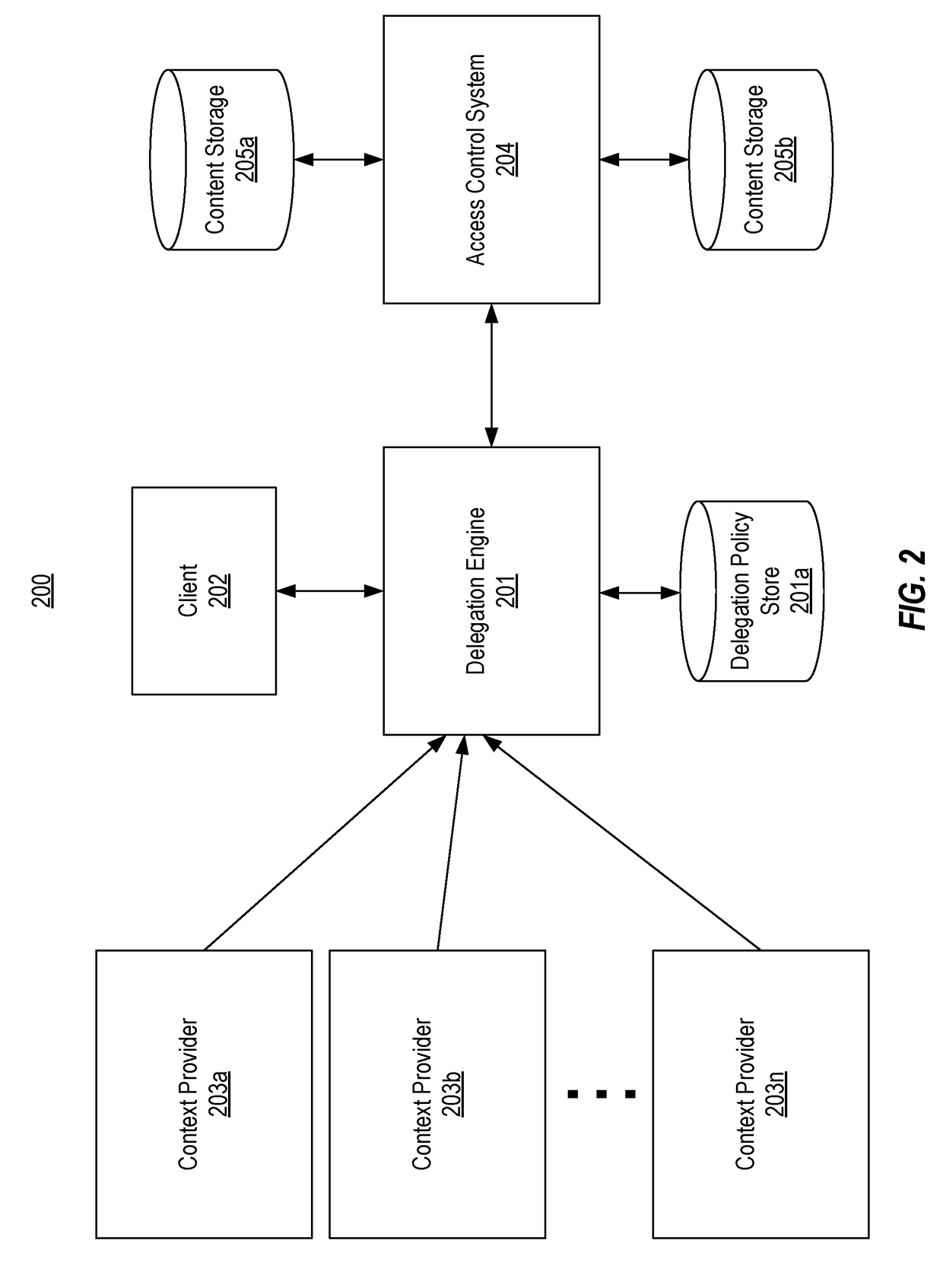
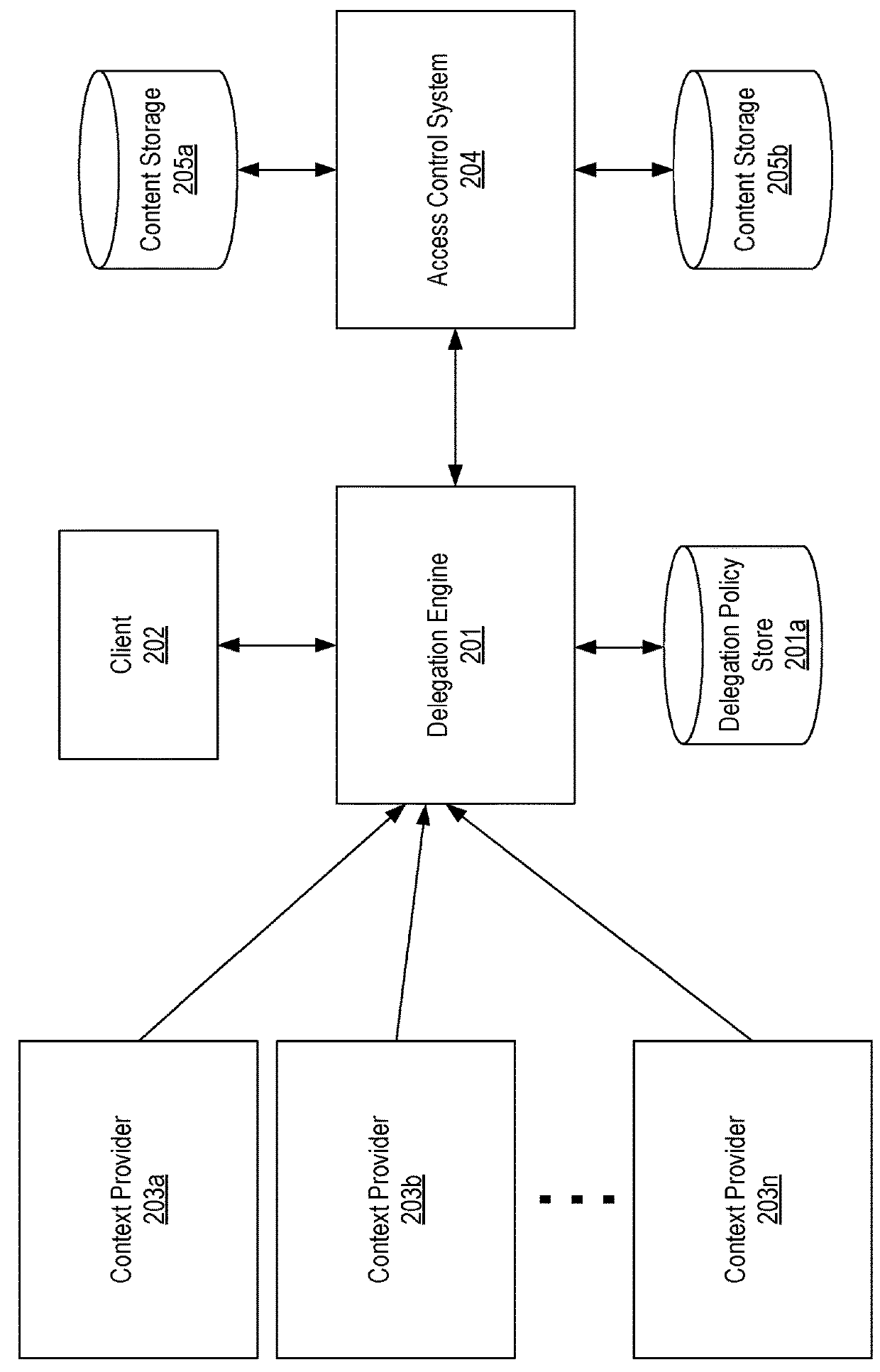
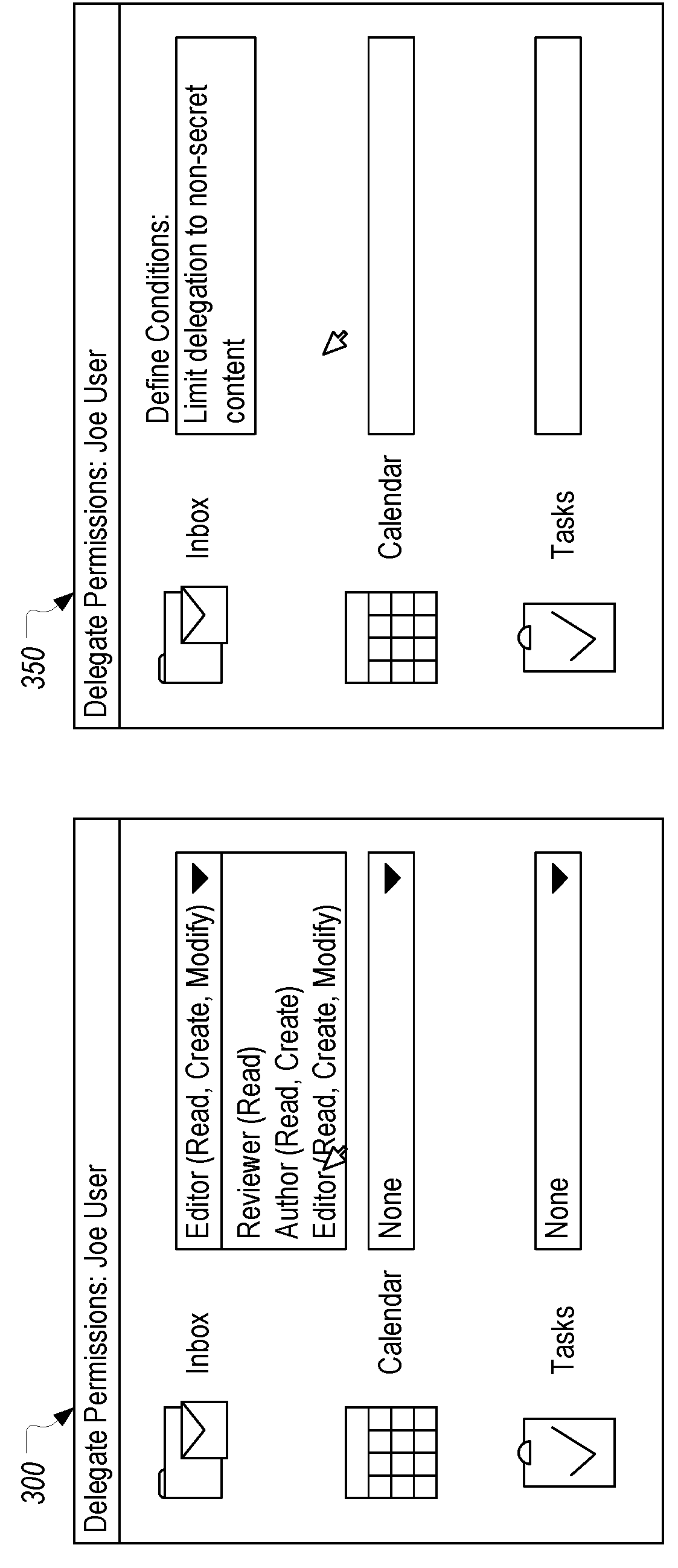
Context-aware delegation engine
A context-aware delegation engine can enable an account owner to identify granular criteria (or context) that will be used to determine what content a delegate will have access to. The account owner can therefore leverage a wide range of information to dynamically determine whether a delegate will receive access to particular content. The delegation engine can be configured to provide a delegation policy to be evaluated to determine whether a delegate should receive access to particular content. Such a delegation policy can be generated based on input provided by the delegator thereby providing the delegator with fine-grained control over which content will be accessible to a particular delegate. The delegation policy can be structured in accordance with an authorization protocol schema such as XACML, SAML, OAuth 2.0, OpenID, etc. to allow the evaluation of the delegation policy to be performed by a policy decision point in such authorization architectures.
Owner:QUEST SOFTWARE INC
Provisioning user permissions using attribute-based access-control policies
InactiveUS8881226B2Computational savingImprove variationDigital data processing detailsUnauthorized memory use protectionUser PrivilegeTheoretical computer science
An attribute-based access control policy (e.g., XACML policy) for a set of elements depends on attributes carried by elements in one of several predefined categories. In order to evaluate such policy for a set of elements, the invention provides a method including the steps of (I) selecting a primary category; (II) partitioning the elements in the primary category into equivalence classes with respect to their influence on the policy; and (III) using the equivalence classes to replace at least one policy evaluation by a deduction. The result of the evaluation may be represented as an access matrix in backward-compatible format. The efficiency of the policy evaluation may be further improved by applying partial policy evaluation at intermediate stages, by forming combined equivalence classes containing n-tuples of elements and / or by analyzing the influence of each element by extracting functional expressions of maximal length from the policy.
Owner:AXIOMATICS
Cloud computing unified identity authentication method based on SAML and XACML
InactiveCN106506500ALow costAvoid using effectsUser identity/authority verificationSecurity domainIdentity provider
The invention discloses a cloud computing unified identity authentication method based on SAML and XACML. According to the method, an identity provider and a service provider are defined by using the SAML standard so that different security domains can be formed, and authentication exchange and data authorization between different security domains can be realized; besides, a framework of a general access control strategy and a performing authorization strategy of the request / response can be realized by using the XACML so that performing of the access control strategy in the cloud computing environment can be realized, and unified identity authentication and authority access control of cloud computing can be realized. According to the unified identity authentication method, the management control problem of unified identity authentication and access control authority of multiple application platforms under cloud computing can be effectively solved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
XACML policy rule checking method
InactiveCN100592315COptimize strategy structureImprove the efficiency of strategy judgmentDigital data authenticationSemantic treeState dependent
The invention provides an XACML strategy rule detecting method, belonging to the field of authorized strategy analysis in information safety. According to the XACML strategy rule, the method has a rule status definition, a rule status correlation definition and a conflict type analysis; on the basis, a strategy index based on a semantic tree is established, a concrete XACML strategy rule detectionis carried out and the rule conflict and the rule redundancy are analyzed; the detection method comprises two types: a conflict detection method based on a property level operation correlation and adetection method for other typed conflicts based on the status correlation. In the redundancy analysis, the analysis determining method of the rule redundancy is given respectively in the algorithms of allowing priority, refusing priority and the first-time application dispelling. By adopting the detection method, the strategy manager can precisely locate the rules causing the conflict and the reasons for the conflict; in the redundancy analysis, according to the analysis result, the strategy structure can be optimized and the redundancy rules which has no influence on accessing the determining result can be deleted, therefore, the strategy determining efficiency is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
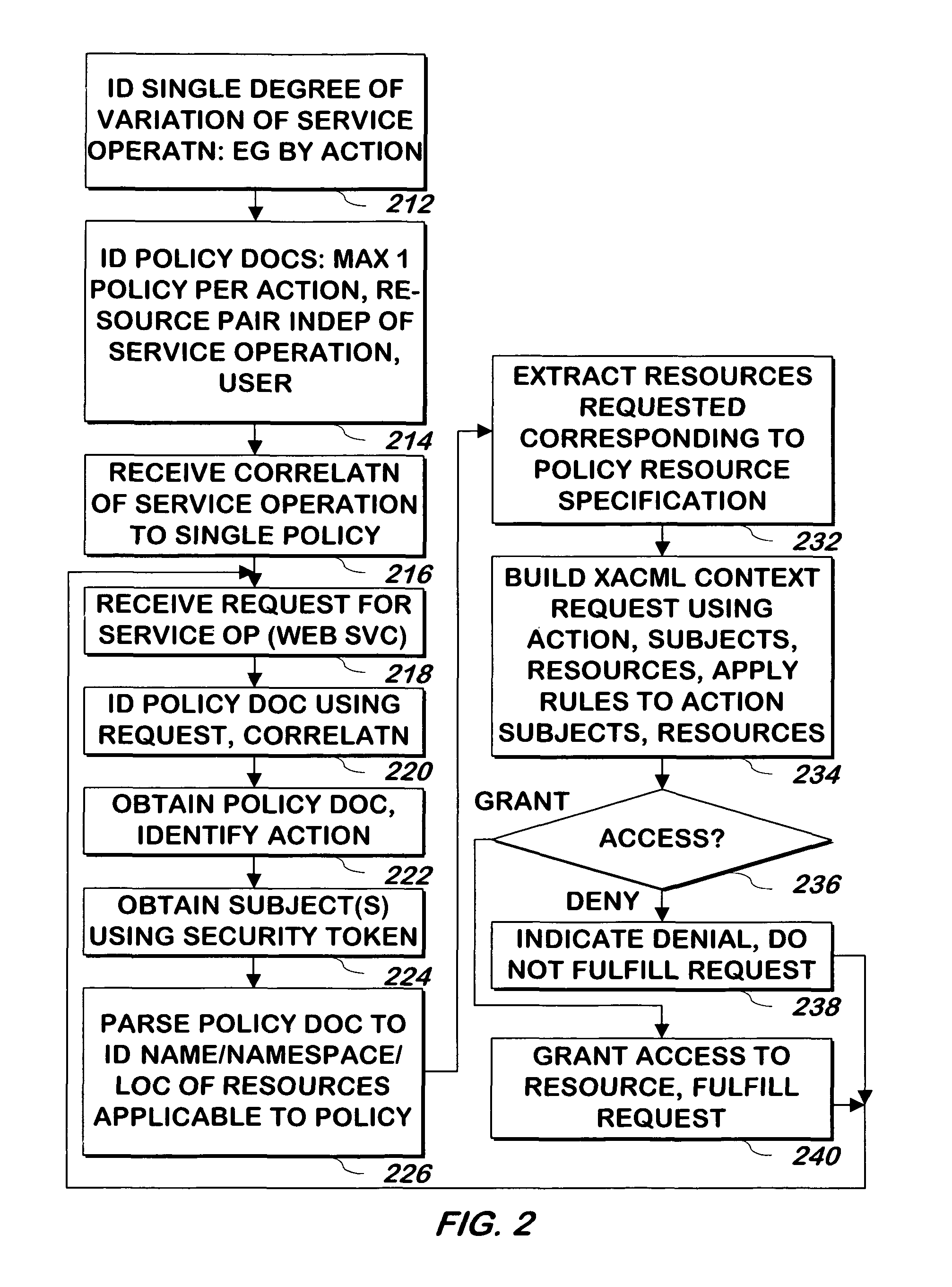
Method and apparatus for simplified, policy-driven authorizations
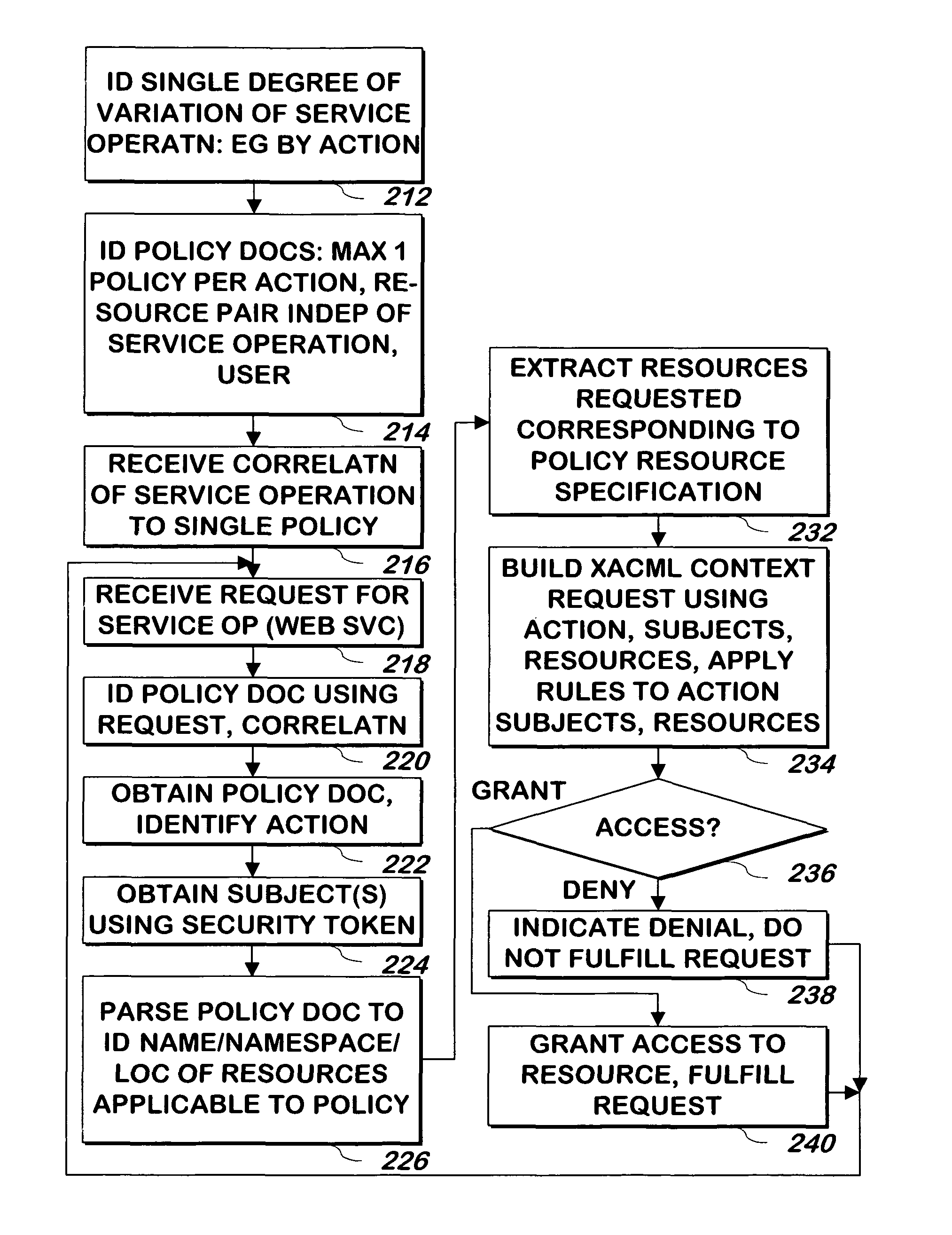
ActiveUS9185090B1Simpler and easy to manageSimpler and easy to and useDigital data processing detailsComputer security arrangementsSubject specificXACML
A system and method uses a set of XACML policies to identify an action or other single degree of variations of various entities that may be called using requests, and uses information from the policy that is useful for obtaining one or more XACML subjects and resources from a request to access the resource, and then builds an XACML policy request using the action or other single degree of variation, and the one or more subjects and resources to determine if authorization for performing the action or other single degree of variation on the one or more resources on behalf of the one or more subjects is granted. Only if the authorization is granted is the action or other single degree of variation performed on the one or more resources.
Owner:CHARLES SCHWAB & CO INC
Access control method based on policy review and authorization extension
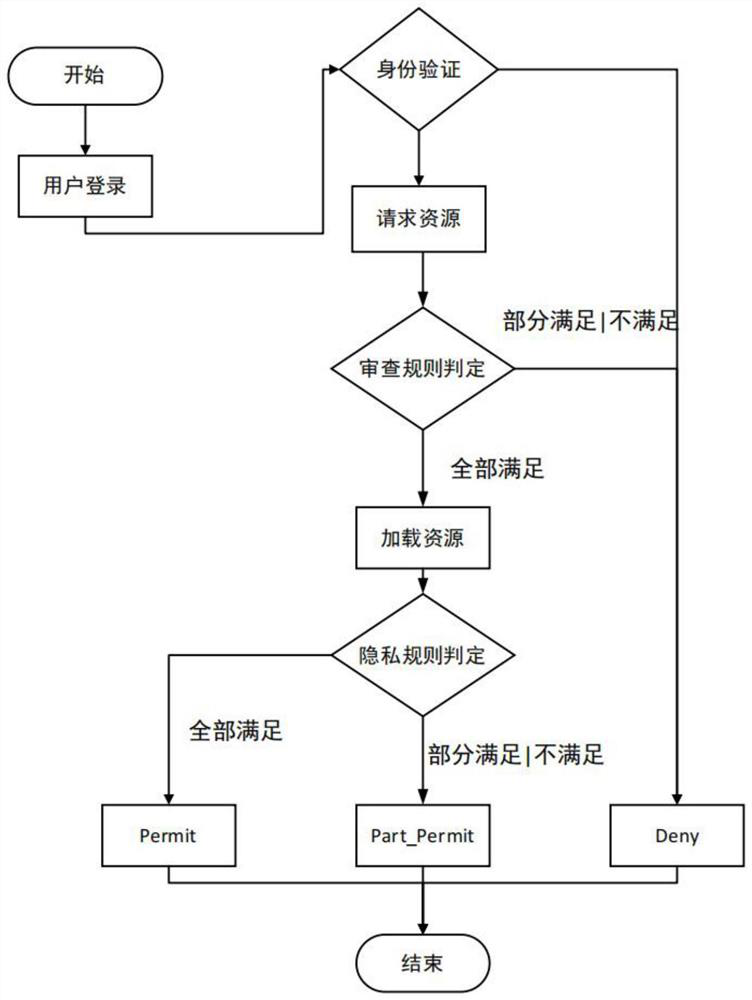
PendingCN114844702AThe realization of the phenomenon that the granularity is not enoughGuaranteed privacySecuring communicationPrivacy ruleXACML
The invention discloses an access control authorization method based on policy review and authorization extension, which comprises the following steps: firstly, expanding the service type of traditional ABAC model resource authorization, and adding the concept of partial permission except permission and rejection; defining a strategy review module, checking whether the attributes of the user meet a review rule set and a privacy rule set in the strategy review module, checking rules in the review rule set firstly, and rejecting the service as long as one rule is not met; and after all the review rule sets are met, checking the privacy rule set, and displaying part of data or all data according to the matching condition of the user attribute and the privacy rule set. After an access control strategy of resources is formulated, all participated attributes in the system are uniformly described by applying an XACML (Extensible Access Control Markup Language). Fine-grained management of resources is realized, and flexibility is increased while privacy is guaranteed.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Dynamic policy-based entitlements from external data repositories
A machine-implemented method for evaluating a context-based (e.g., XACML) policy having a set of attributes formulates a search against one or more existing external repositories using a query that is dynamically-generated based on the security policy being evaluated. The approach shifts the building of a candidate set of potentially-allowable resources to the authorization engine (e.g., a Policy Decision Point (PDP)). In operation, an application calls the PDP using an entitlement request and, in response, the PDP builds the candidate set of values based on the defined security policy by generating a query to an external data repository and receiving the results of that query. This approach enables a policy-driven entitlement query at runtime.
Owner:IBM CORP
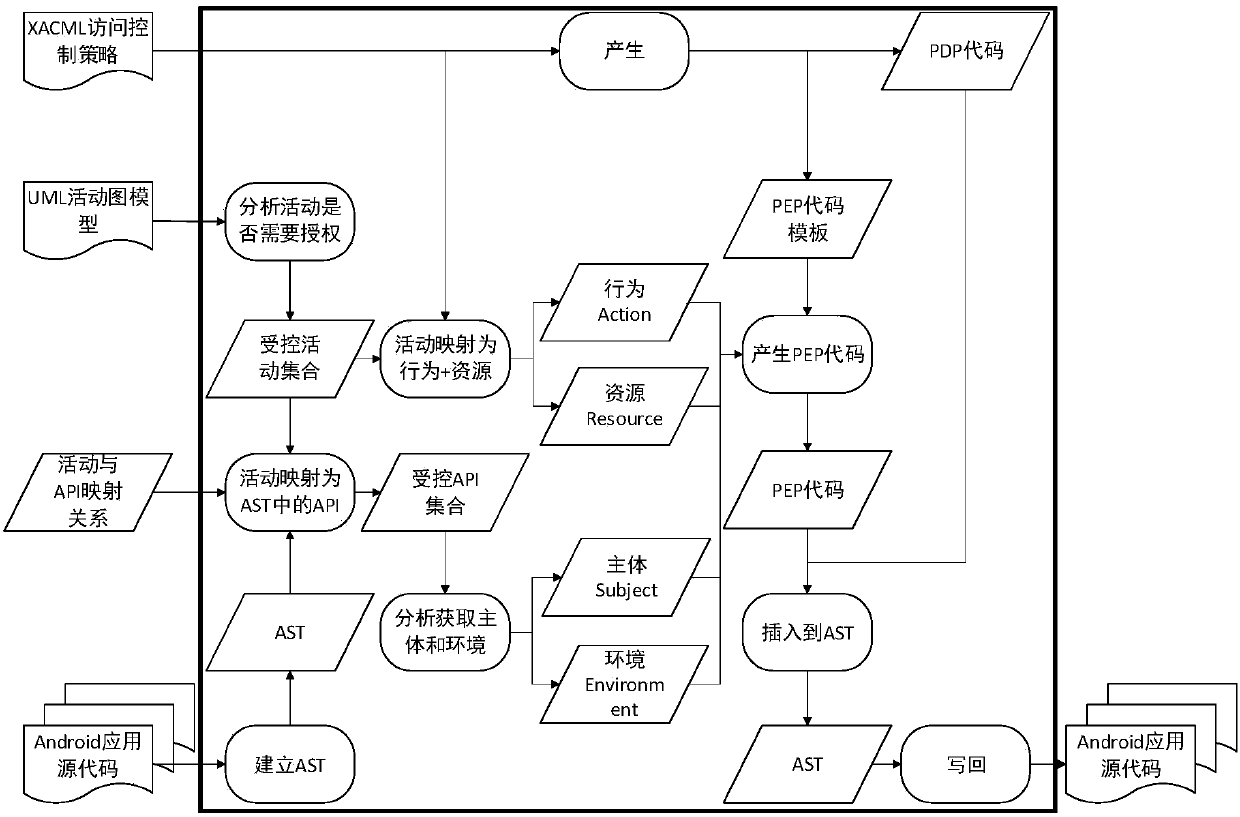
Android application access control code generating method based on XACML access control mechanism
ActiveCN108021362ANarrow the scope of the analysisRealize producePlatform integrity maintainanceModel driven codeWorkloadDEVS
The invention discloses an Android application access control code generating method based on an XACML access control mechanism. A function achievement code of an Android application, an XACML strategy for describing the access control requirement of behaviors and resources of the Android application, and a UML activity graph model for describing the activities of the Android application are provided, codes for satisfying the access control strategy can be generated for behaviors and resources for accessing control authorities and inserted to corresponding positions in codes of the Android application, so that the Android application becomes an entire Android application system. By means of the Android application access control code generating method, an XACML language description accesscontrol strategy is utilized, the access control strategy can be defined with more fine grits, and the access control requirement of the application system can be described more specifically. By generating the access control codes, production and reuse of access control logic are achieved, and the workload and the error rate of developers of the application system are lowered.
Owner:NANJING UNIV
Method and device for generating access controlling policy
InactiveCN101771683BGuaranteed accuracyReduce the burden onData switching networksSpecial data processing applicationsXACMLWorld Wide Web
The invention discloses method and device for generating an access controlling policy. The method comprises the following steps of: generating an ABAC policy expression according to ABAC policy information input by a user through a pre-established attribute-based access control (ABAC) policy view template; and converting the ABAC policy expression into an ABAC policy which is based on XACML and conforms to the XACML template according to mapping rules of the preset ABAC policy view template and an extensible access control markup language (XACML) template. In the invention, the user only needs to input some simple ABAC policy information through the ABAC policy view template and does not need to write a complicated ABAC policy based on XACML in a manual mode, therefore, the problem that the user difficultly defines the ABAC policy based on XACML is solved, the problem that errors are made in the process of writing the complicated ABAC policy based on XACML in a manual mode by the useris avoided, and the accuracy of the ABAC policy based on XACML is ensured.
Owner:BEIHANG UNIV
A Method for Optimizing Access Control Policy
ActiveCN107547549BEncryption apparatus with shift registers/memoriesAlgorithmTheoretical computer science
The invention discloses an access control strategy optimization method, and belongs to the field of network safety. The method mainly comprises the steps of defining rule conflicts and redundancy, andbefore a rule is found, newly defining conflicts of an XACML rule; splitting multiple attributes of the rule to reduce granularity of the rule to the lowest level; splicing main body, resource and behavior rule element character strings to form a new triple rule information character string based on the finding of the rule conflicts and redundancy sets of the XACML triple Hash, calculating a Hashvalue of the rule information character string, wherein if the Hash values of the different character strings are conflicted, this is the conflict or the redundancy set; selectively deleting the ruleconflict or redundancy based on the Maximum number of matching times of the rule: selectively deleting the rule by calculating engine performance cost of the rule after the conflict or redundancy iseliminated; and inversely compressing the split rule.
Owner:HARBIN ENG UNIV
An evaluation and optimization method of xacml security policy
The invention provides an evaluation and optimization method for an XACML (Extensible Access Control Markup Language) security strategy. The method comprises the following steps of: eliminating a redundancy rule; establishing a judgment result buffer pool and an XACML security strategy buffer pool; and dynamically changing the position of an XACML security strategy / rule. Specific to the performance defects and functional defects along with increase in the complexity of the strategy scale and strategy semantics in an existing XACML standard, the XACML security strategy evaluation and optimization method based on strategy redundancy elimination, caching and reordering is provided. Through adoption of the method, relevant optimum processing methods such as strategy analysis, rule matching and judgment response can be provided for performing fine-grained access control on resources; the efficiency during solving of the problems of strategy information retrieval, multi-strategy matching and the like with an XACML security strategy evaluation engine is increased effectively; and the system availability is enhanced. Moreover, the method can adapt to various strategy merging algorithms, and has high flexibility and availability.
Owner:CHINA ELECTRIC POWER RES INST +3
Context-aware delegation engine
A context-aware delegation engine can enable an account owner to identify granular criteria (or context) that will be used to determine what content a delegate will have access to. The account owner can therefore leverage a wide range of information to dynamically determine whether a delegate will receive access to particular content. The delegation engine can be configured to provide a delegation policy to be evaluated to determine whether a delegate should receive access to particular content. Such a delegation policy can be generated based on input provided by the delegator thereby providing the delegator with fine-grained control over which content will be accessible to a particular delegate. The delegation policy can be structured in accordance with an authorization protocol schema such as XACML, SAML, OAuth 2.0, OpenID, etc. to allow the evaluation of the delegation policy to be performed by a policy decision point in such authorization architectures.
Owner:QUEST SOFTWARE INC
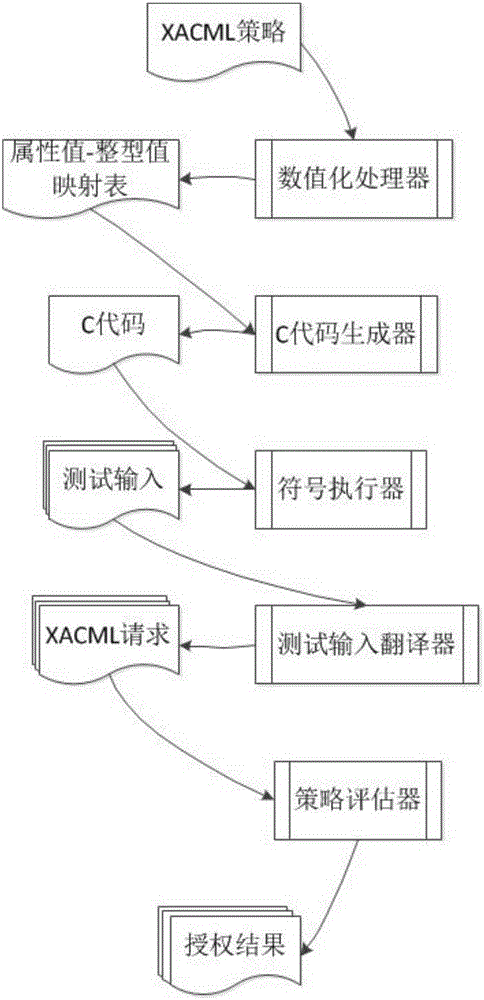
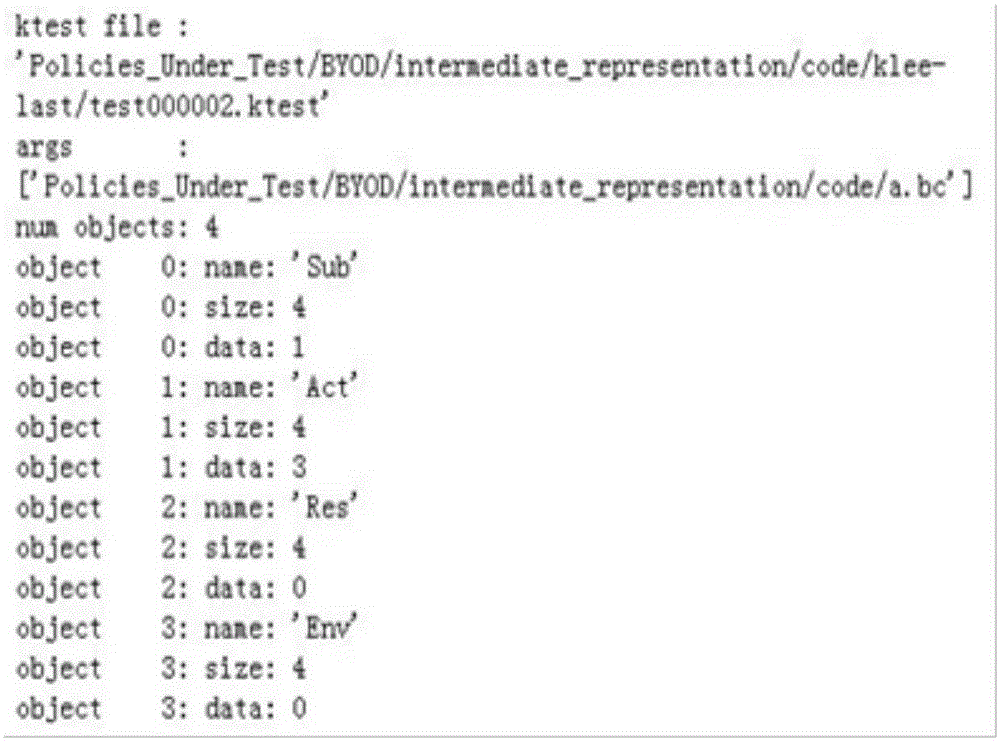
Access Control Policy Test Automatic Generation Method Based on Code Generation and Symbolic Execution
ActiveCN103645987BGood for finding bugsLow number of test requestsSoftware testing/debuggingProgramming languageTest input
The invention provides an automatic generation method of access control policy test on the basis of code generation and symbolic execution and makes up for deficiencies of the existing XACML (eXtensible Access Control Markup Language) policy test technologies and tools according to the actual demand of XACML policy test. The automatic generation method comprises the following steps: firstly, conducing numeralization processing on a to-be-tested XACML policy appointed by a user; then, converting the to-be-tested XACML policy into a C code expression form with equivalent semantics; generating test input of the C code through a symbolic execution tool; translating the generated test input into an XACML request; finally, using the generated XACML request as input of a policy evaluator, and transmitting the input to the XACML policy for evaluation to obtain an authorization result. According to the automatic generation method, the test request fully covering the XACML policy can be efficiently generated through the symbolic execution test technology; the automatic generation method is conductive to finding out errors in the XACML policy.
Owner:NANJING UNIV
A ciphertext access control method based on cp-abe
ActiveCN105991278BEnsure safetyKey distribution for secure communicationAccess structureControl system
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com