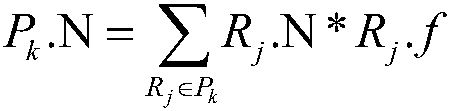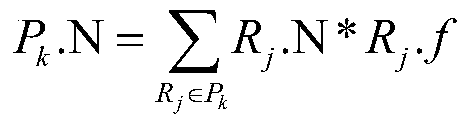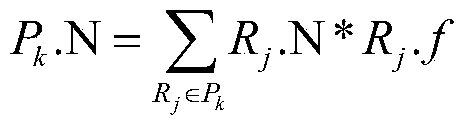An evaluation and optimization method of xacml security policy
A security policy and optimization method technology, applied in the field of optimization, can solve the problems of high system resource overhead, many remote communication interactions, and the inability to meet the high business throughput of commercial applications, so as to achieve the effect of enhancing system availability, flexibility and usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be described in further detail below.
[0050] An evaluation and optimization method of a XACML security policy of the present invention is characterized in that: the method comprises the following steps:
[0051] Step 1: Eliminate redundant rules;
[0052] Step 2: Establish the judgment result cache pool and the XACML security policy cache pool;
[0053] Step 3: Dynamically change the location of the XACML security policy / rule.
[0054] In the step, the redundant rules existing under different merging algorithms are judged first, and then the redundant rules are eliminated.
[0055] Rudang rule R i Applies to requests, rule R j Bound to apply to the request, said R i cover R i , denoted as ; i · effect means R i The judgment result of , the value is Permit or Deny; it is divided into the following three situations:
[0056] (1) Under the permission-first merging algorithm, there are
[0057] 1) and R j · effect=Permit, then R ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com