Access control method based on policy review and authorization extension
An access control and policy technology, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of only permission and rejection, insufficient fine-grainedness, etc., to achieve the effect of increasing flexibility and ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] It is easy to understand that according to the technical solutions of the present invention, without changing the essential spirit of the present invention, those skilled in the art can imagine various implementations of the access control method based on policy review and authorization extension of the present invention. Therefore, the following specific embodiments and accompanying drawings are only exemplary descriptions of the technical solutions of the present invention, and should not be regarded as the whole of the present invention or as limitations or restrictions on the technical solutions of the present invention.
[0029] The technical solutions of the present invention will be described in detail below with reference to the accompanying drawings.
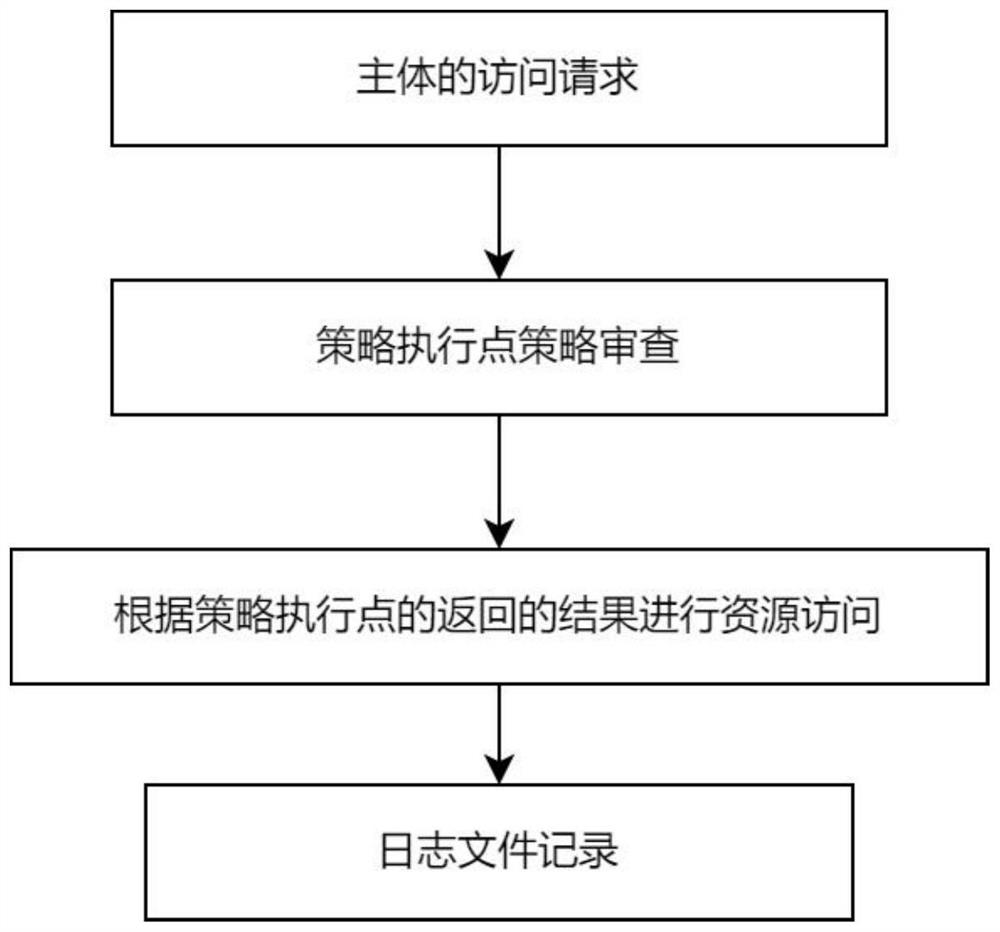
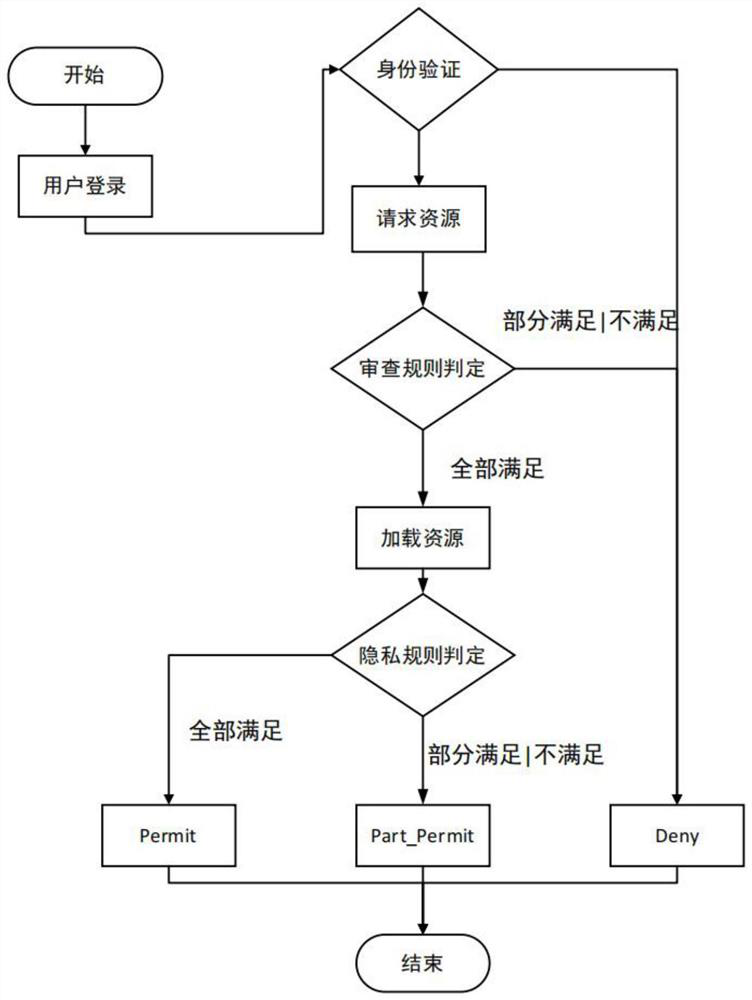
[0030] The basic idea of the present invention is to expand the service type of resource authorization, in addition to permission and rejection, the concept of partial permission is added. Define a policy revie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com