Patents
Literature
53 results about "Privacy rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
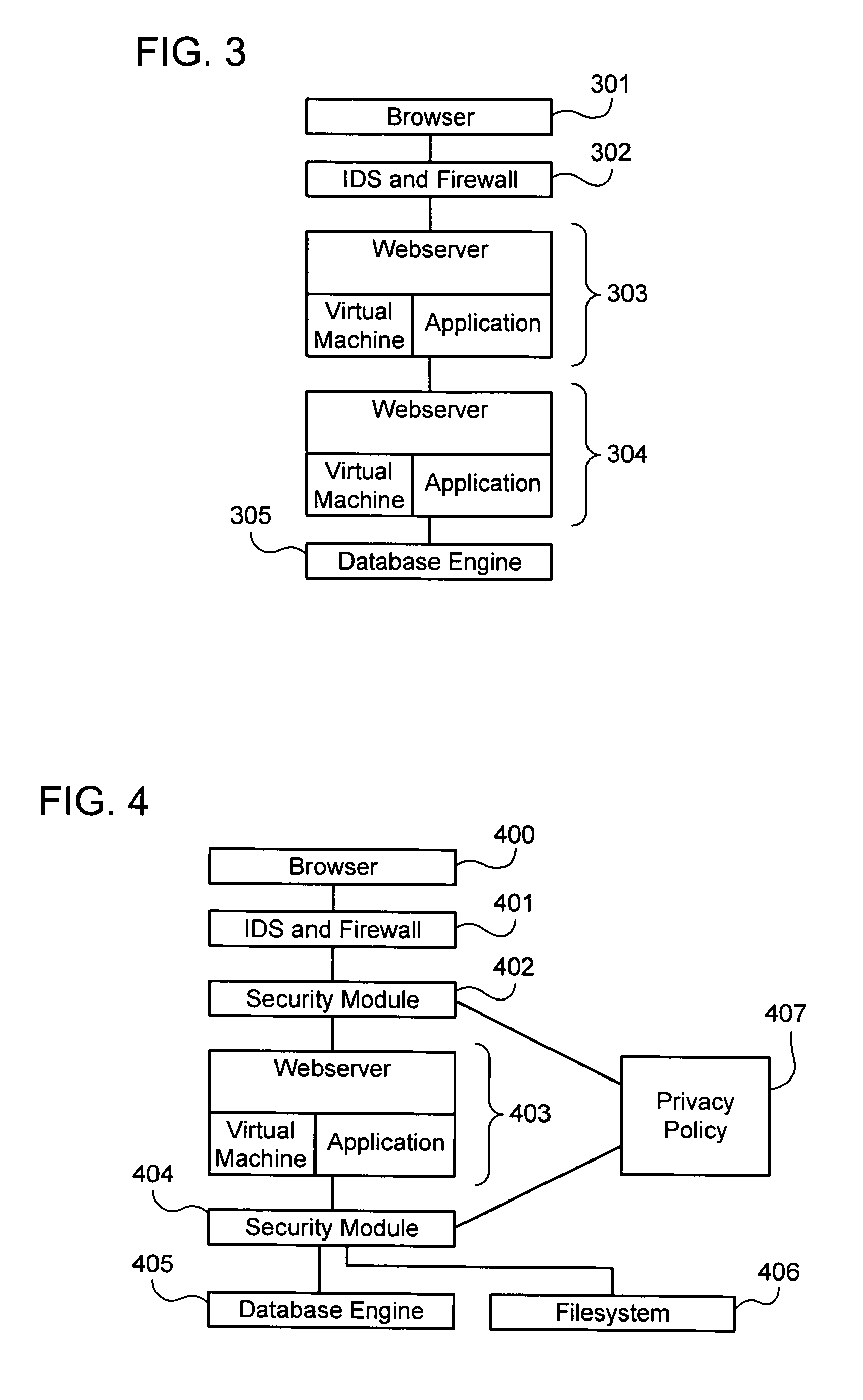
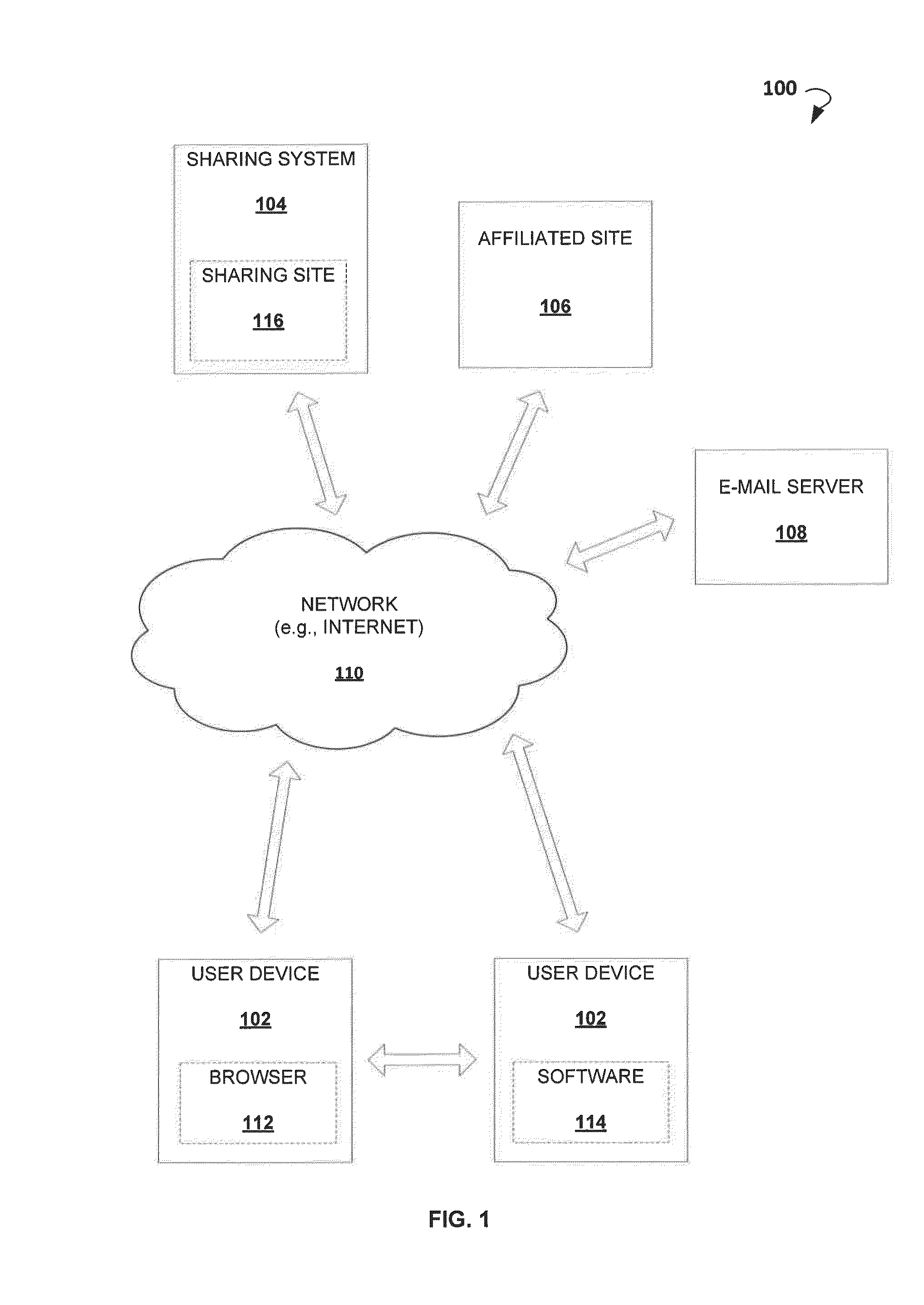
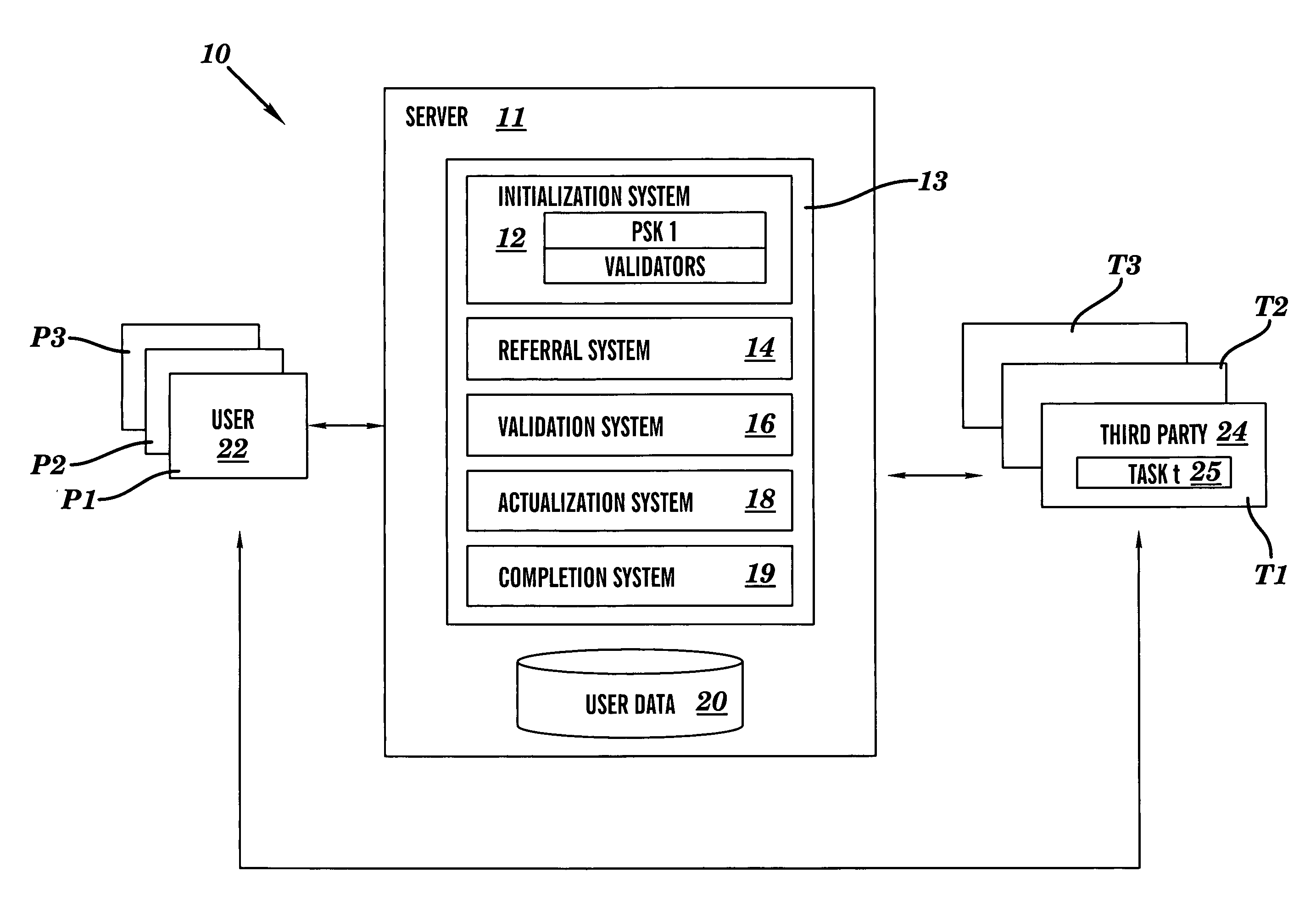
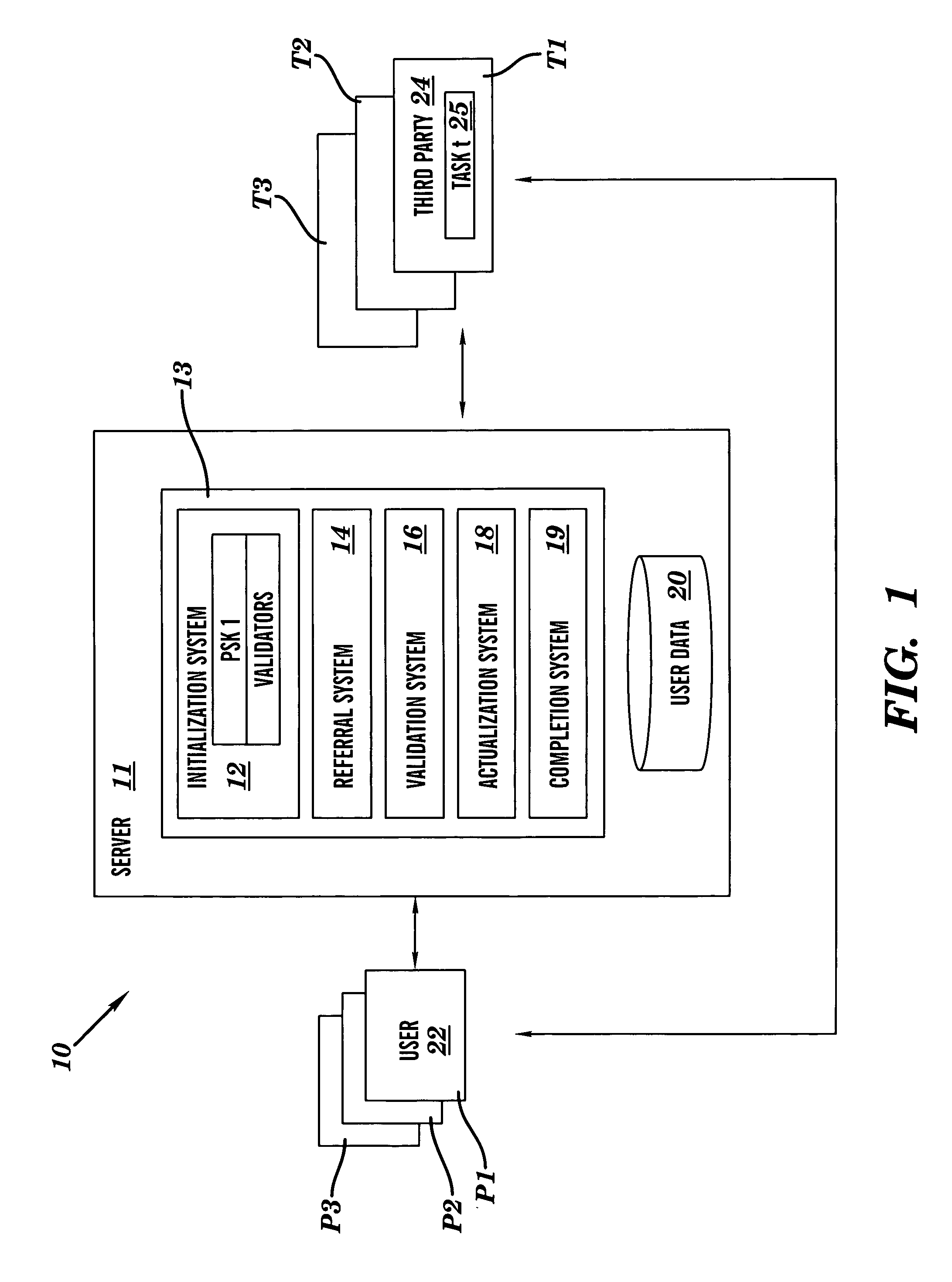
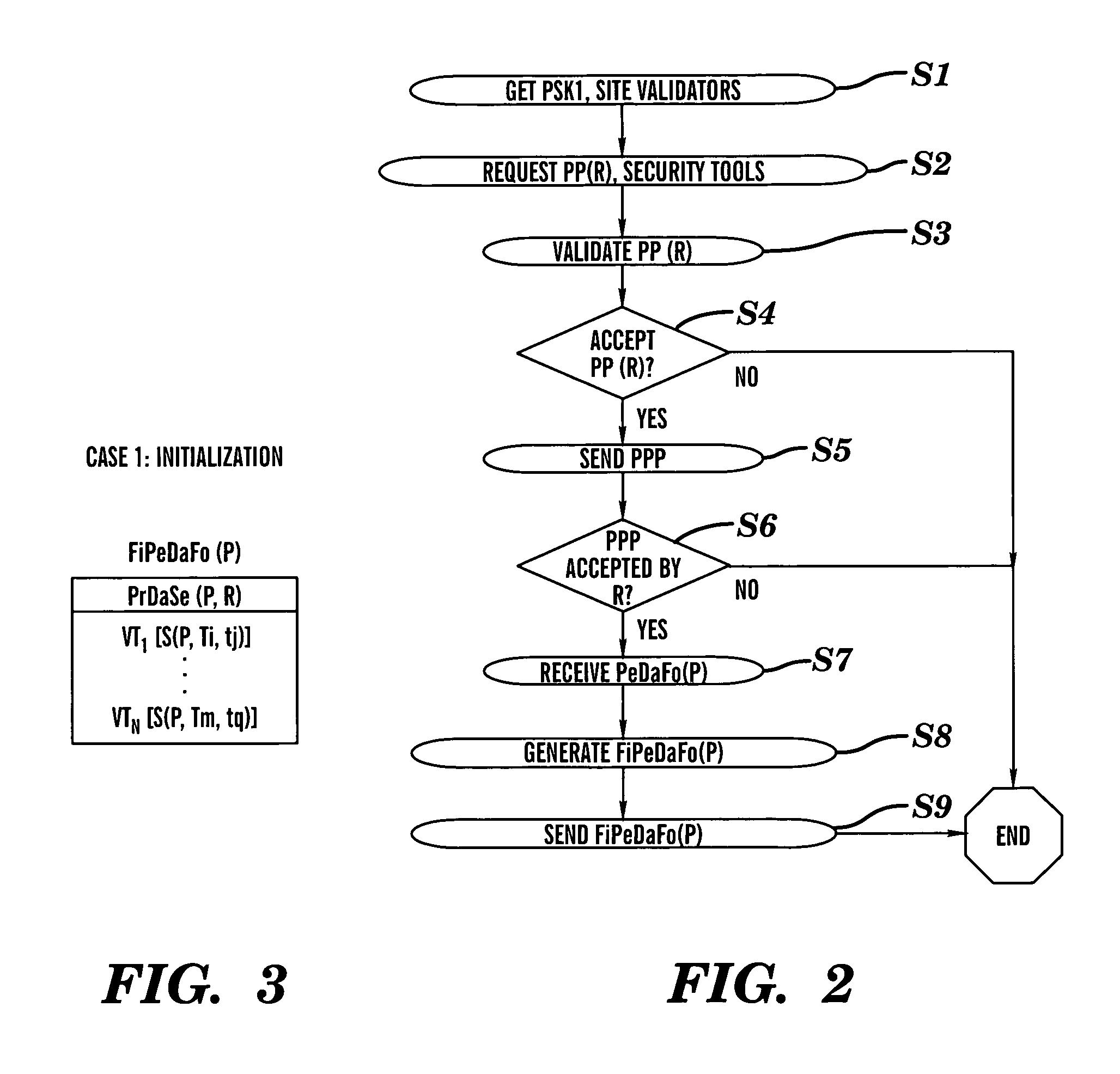
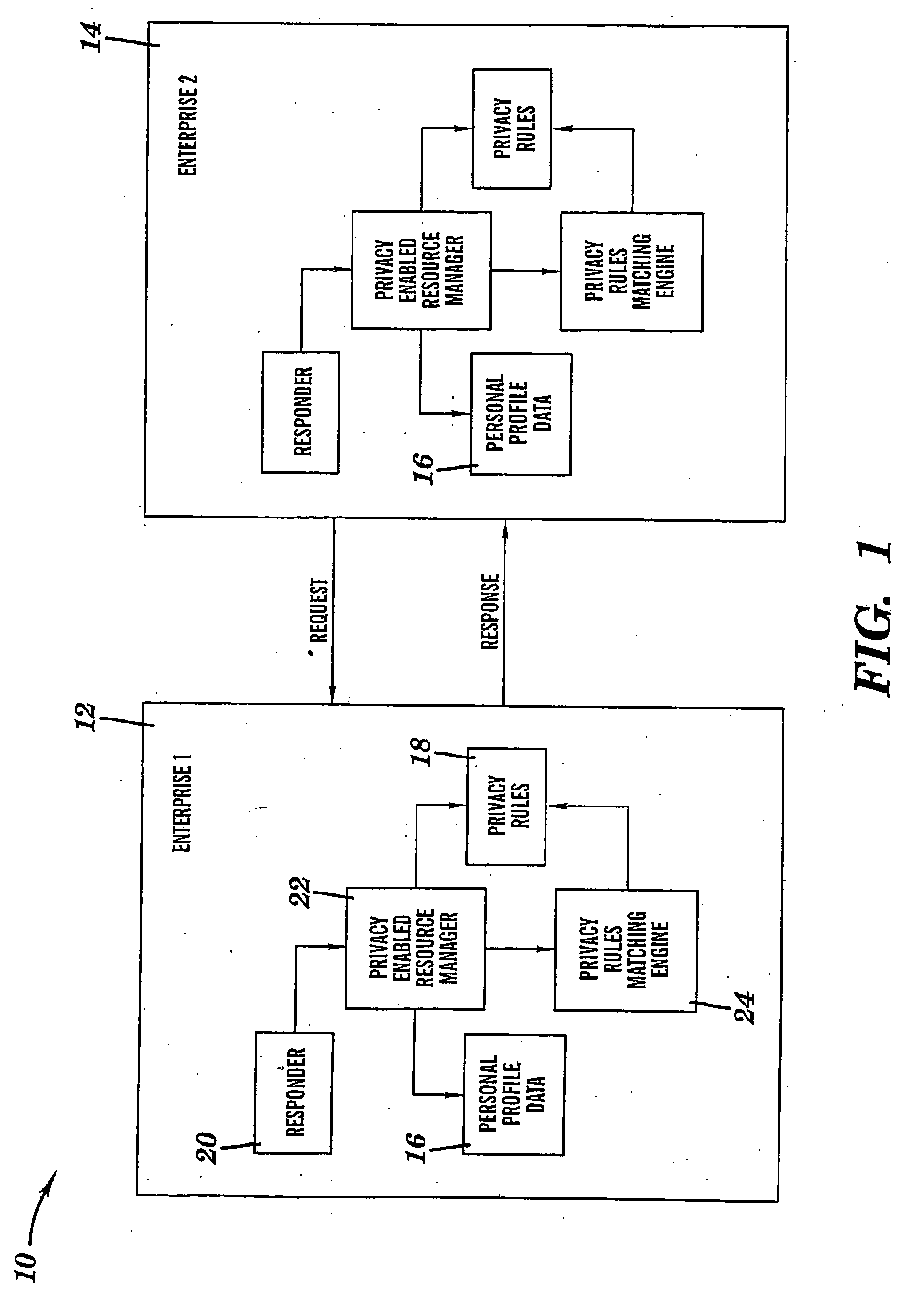
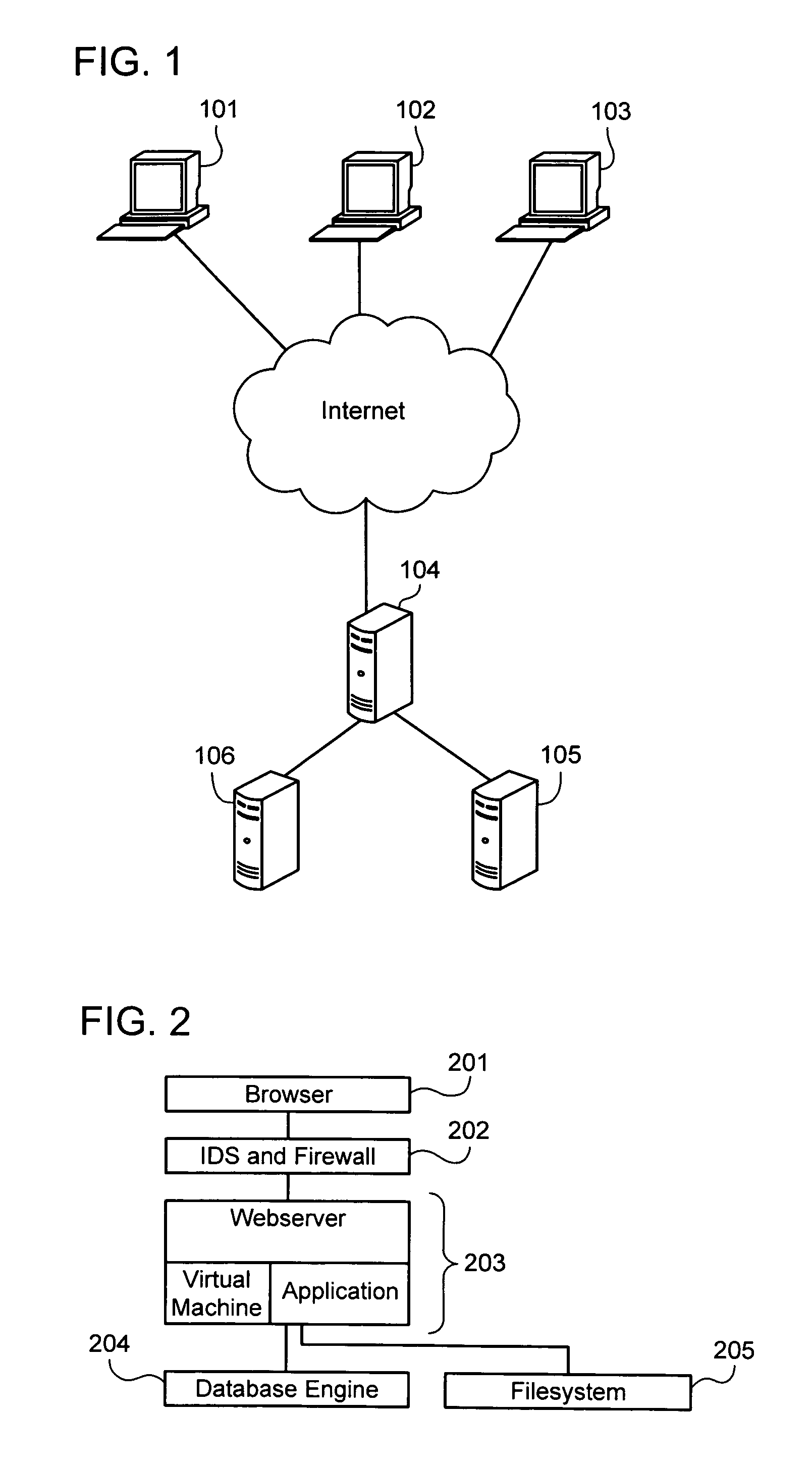
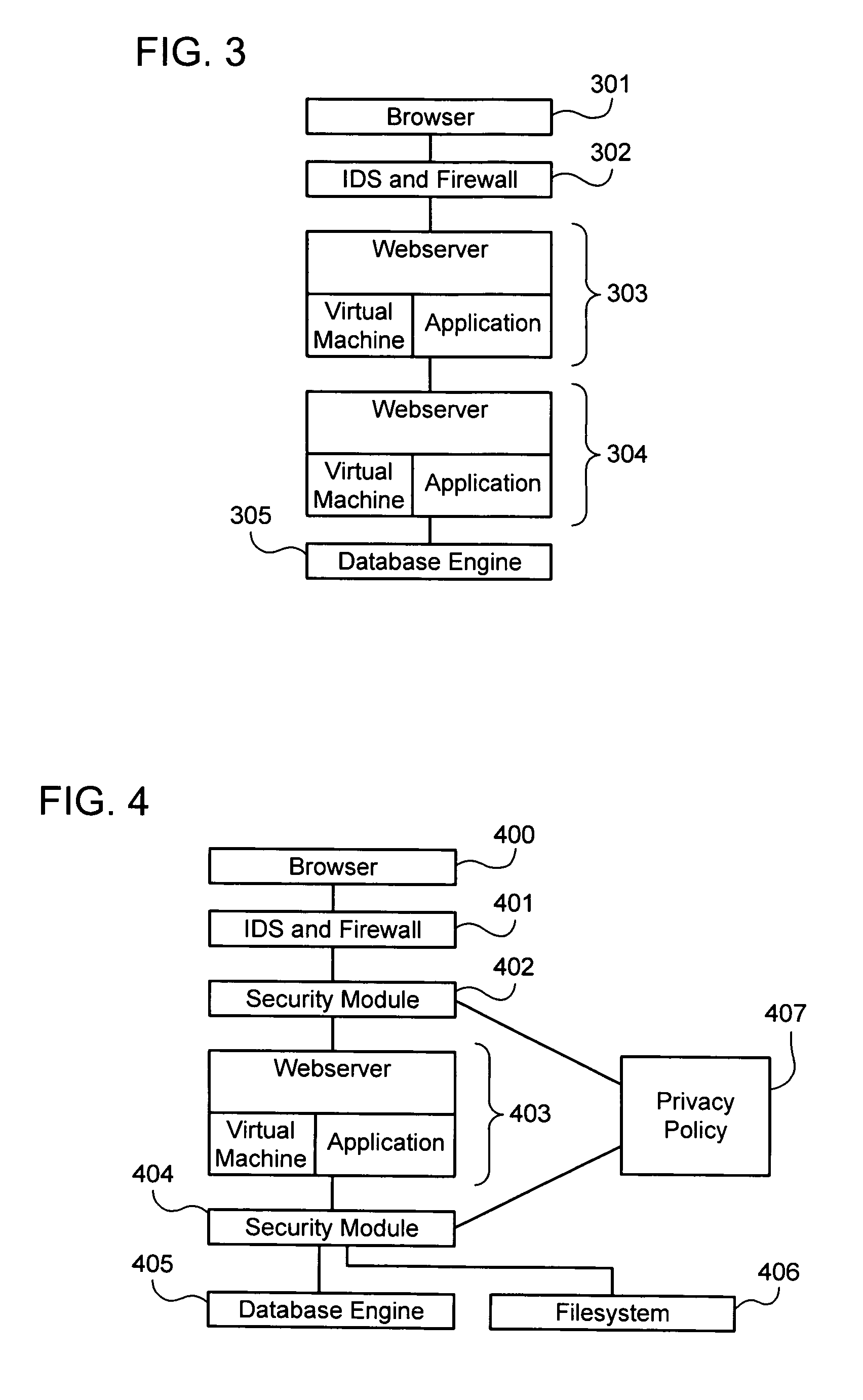
Privacy firewall
ActiveUS20140047551A1Impact efficiencyImpact performanceDigital data processing detailsRelational databasesSupplicantInternet privacy
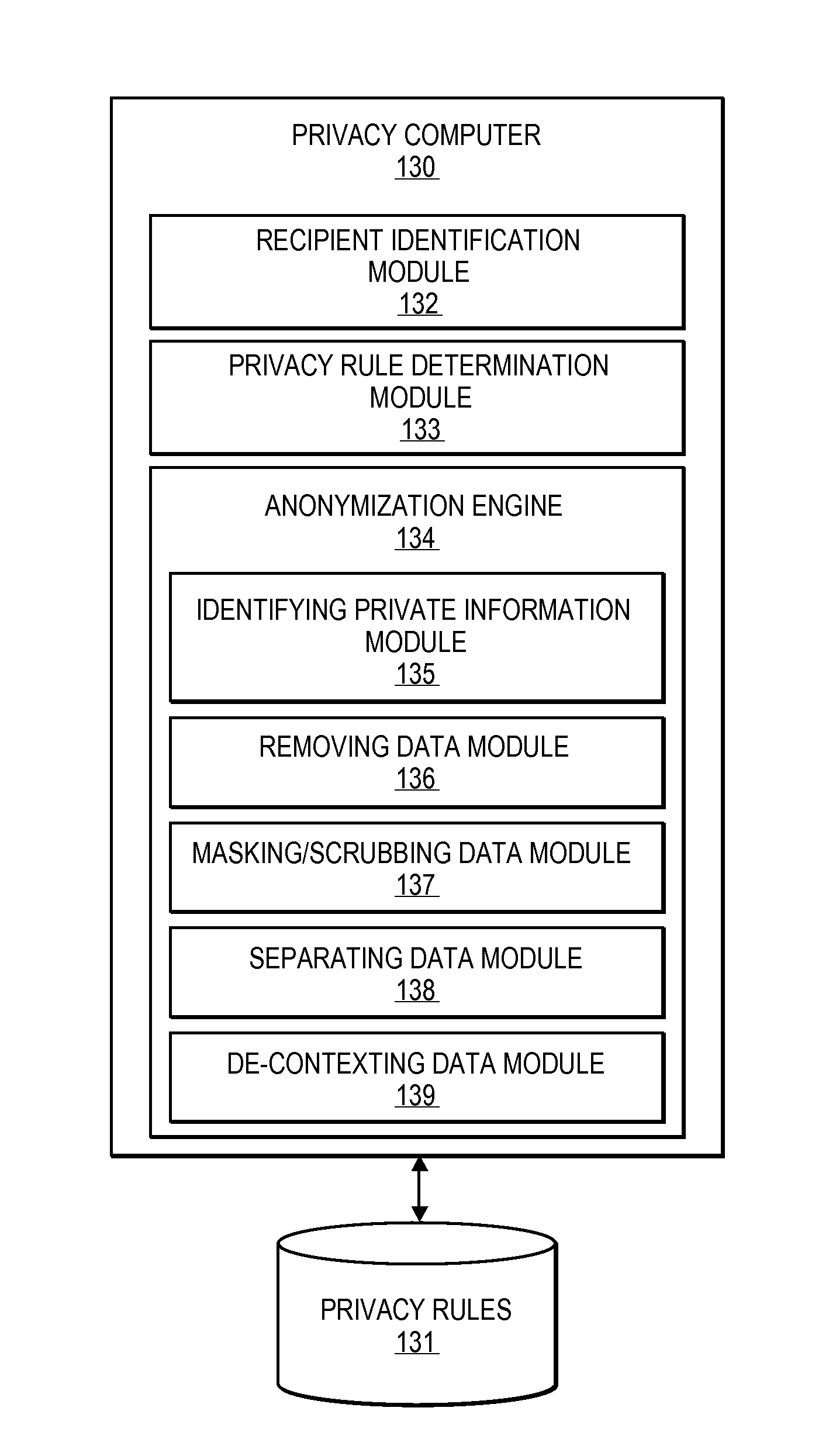
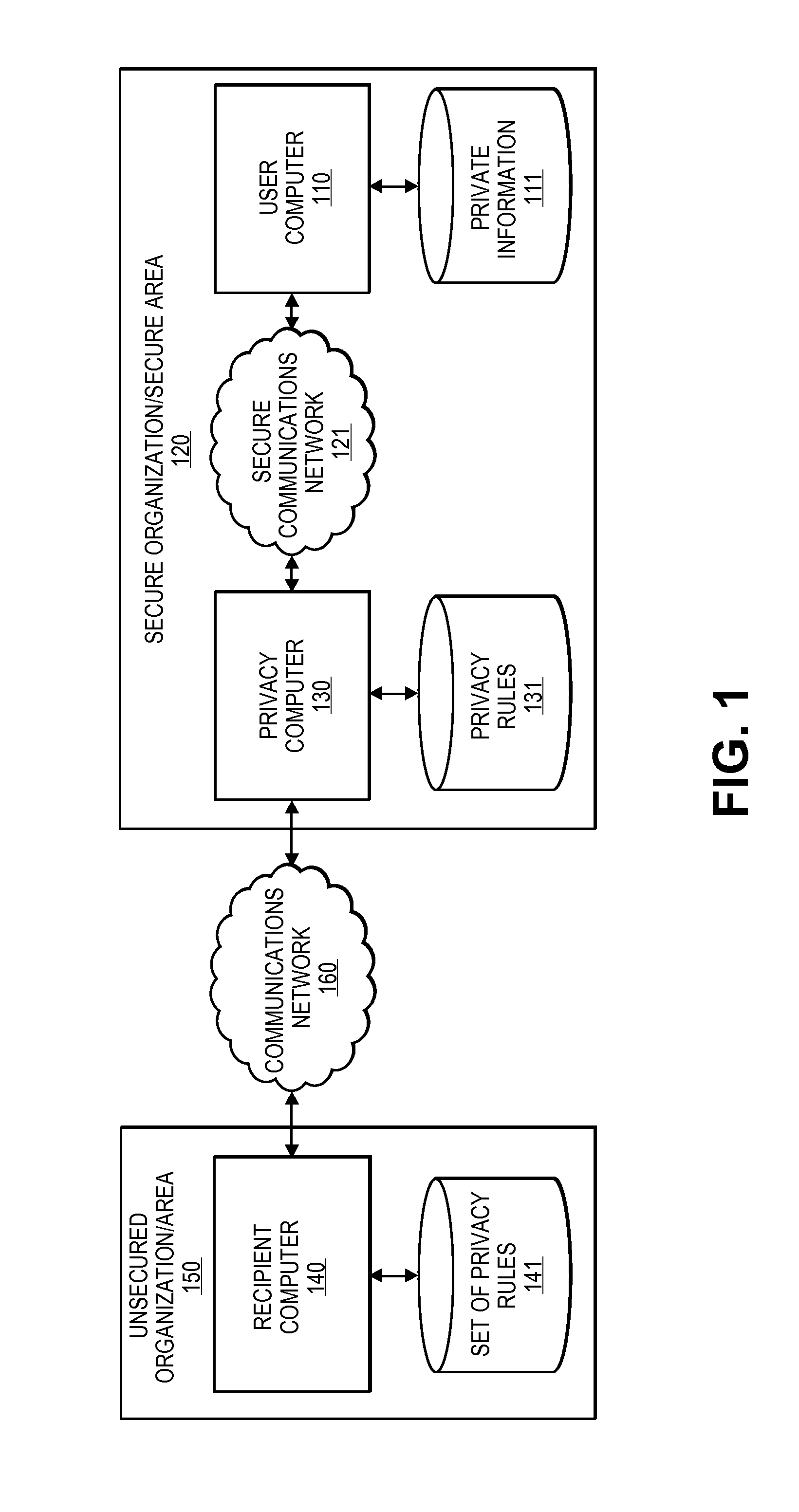
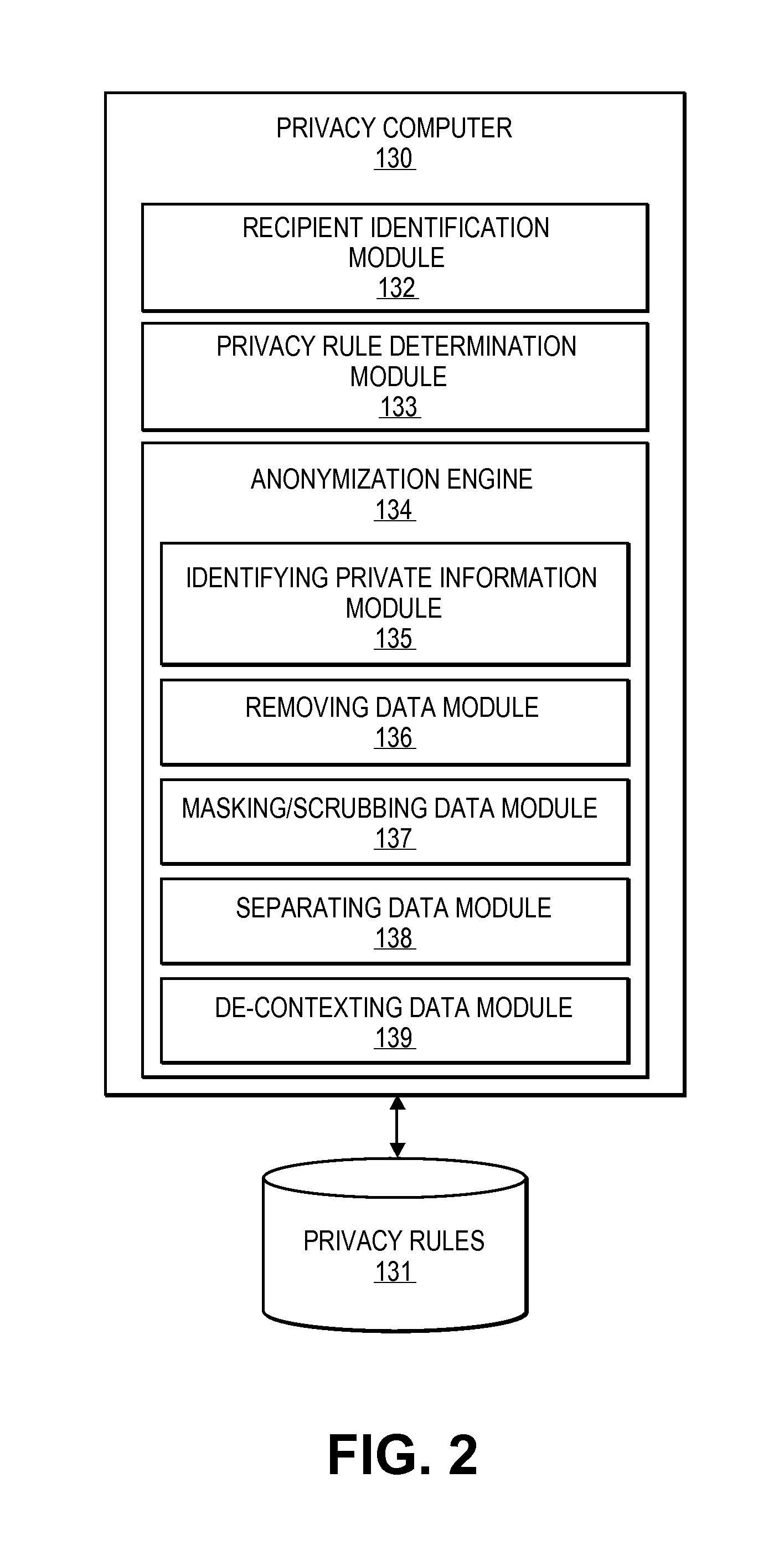
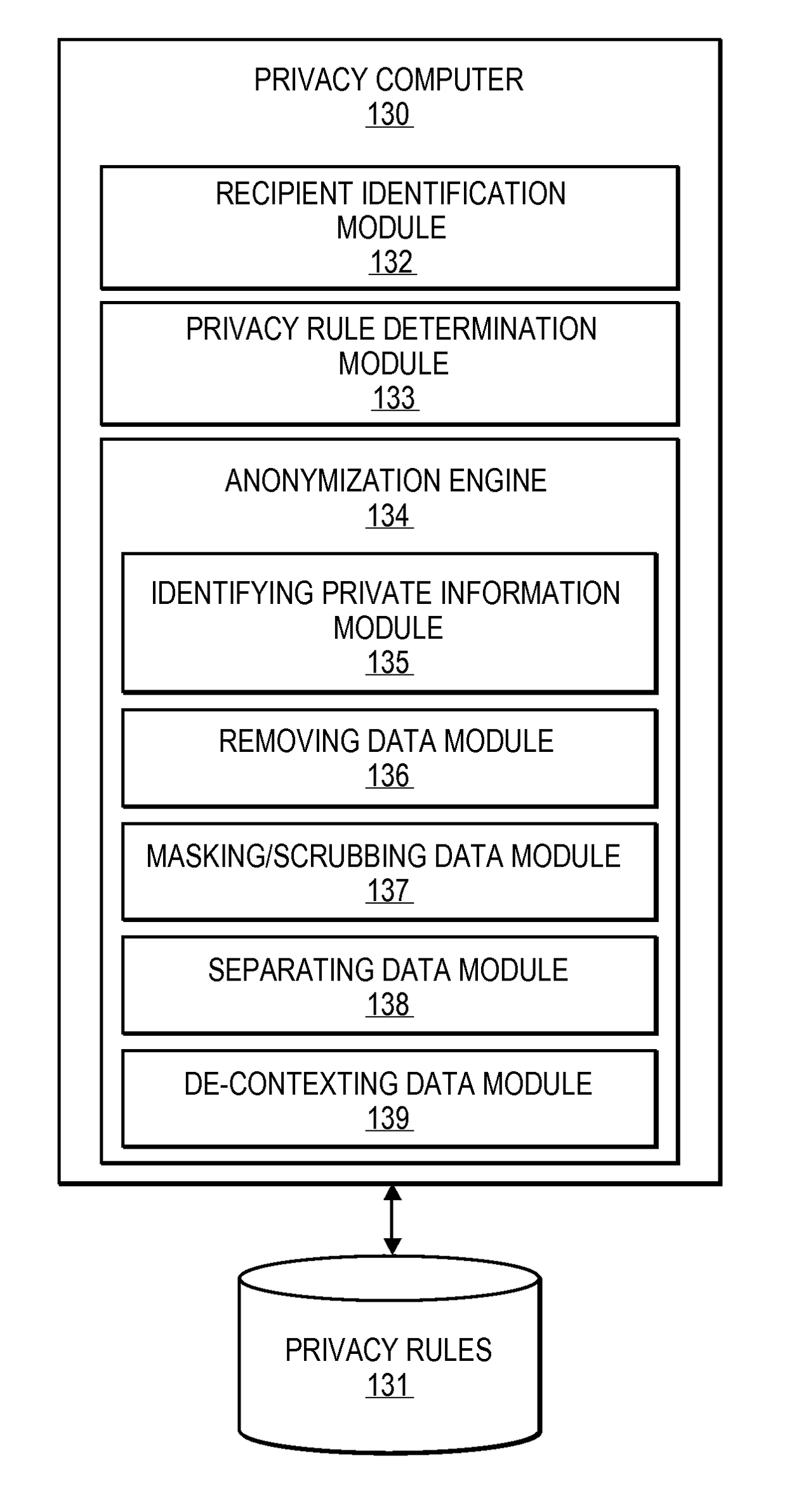
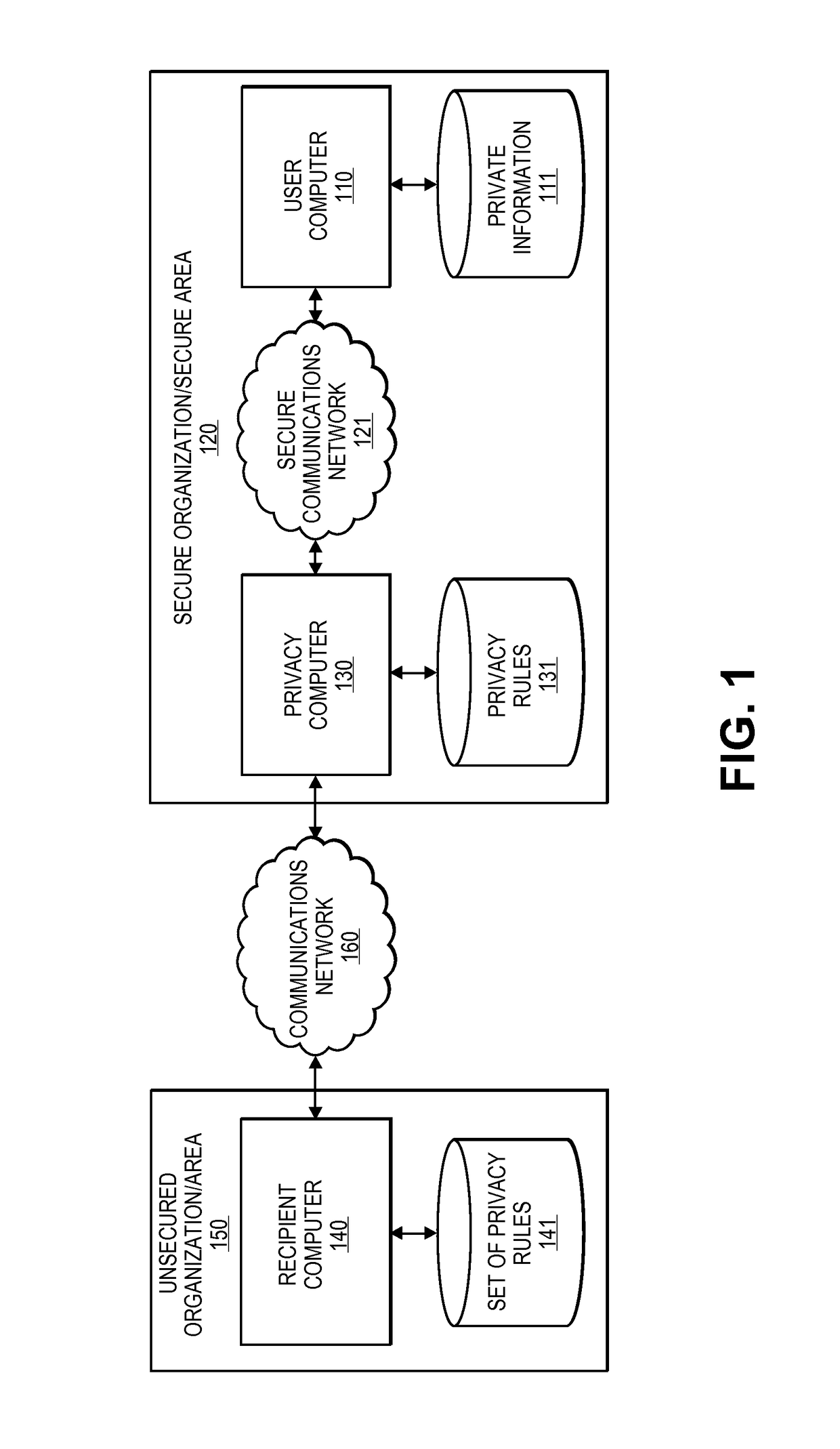
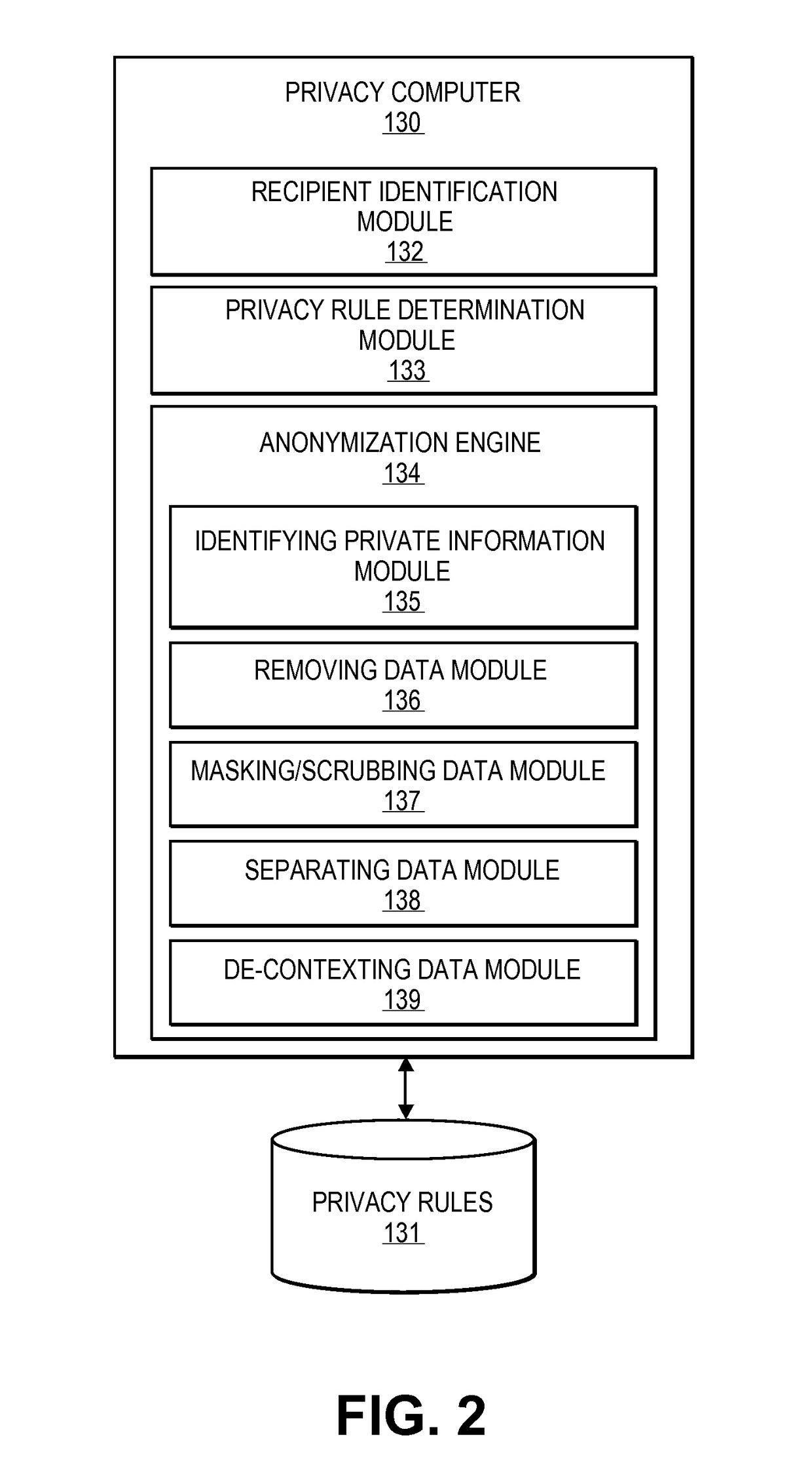
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
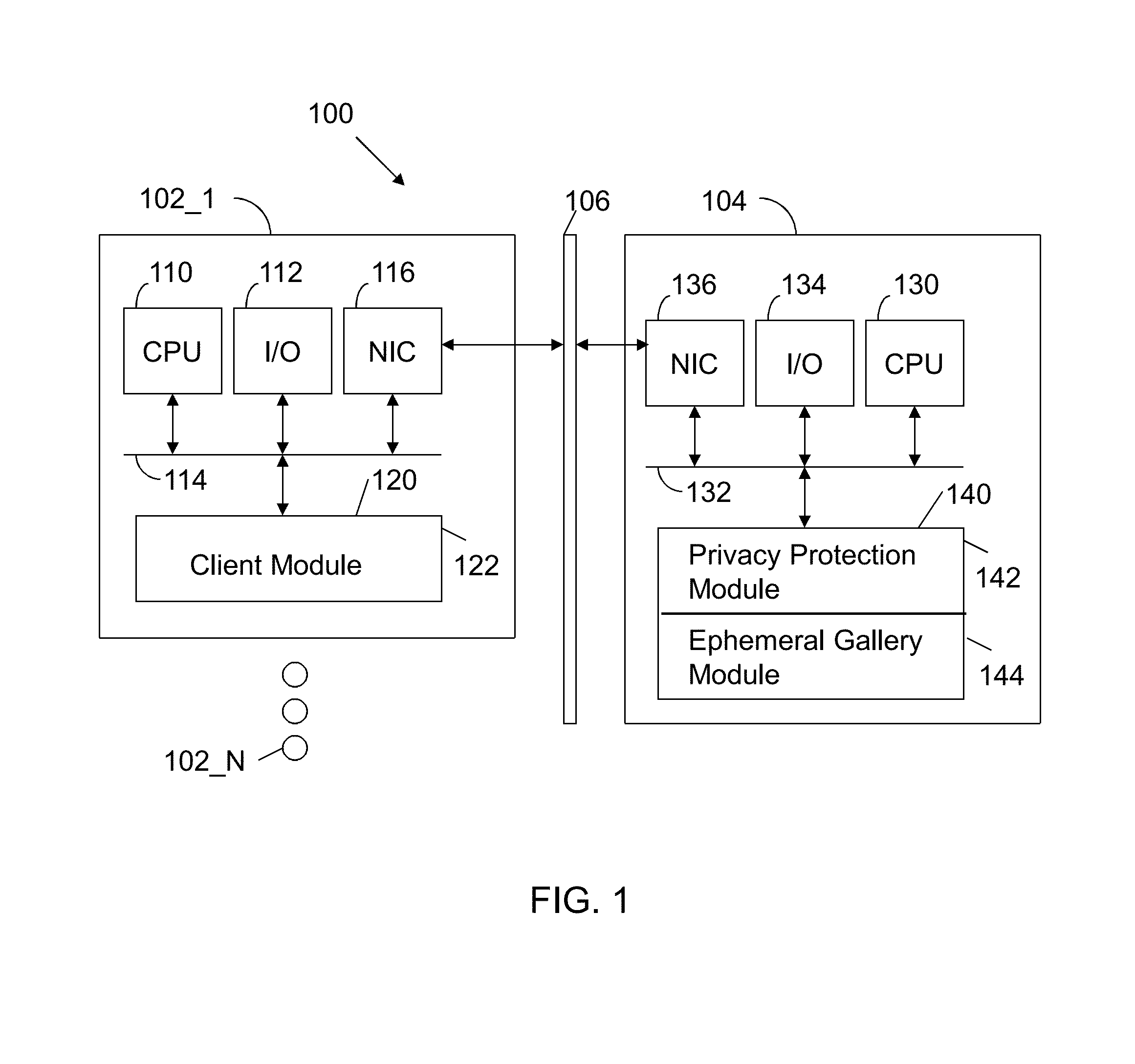
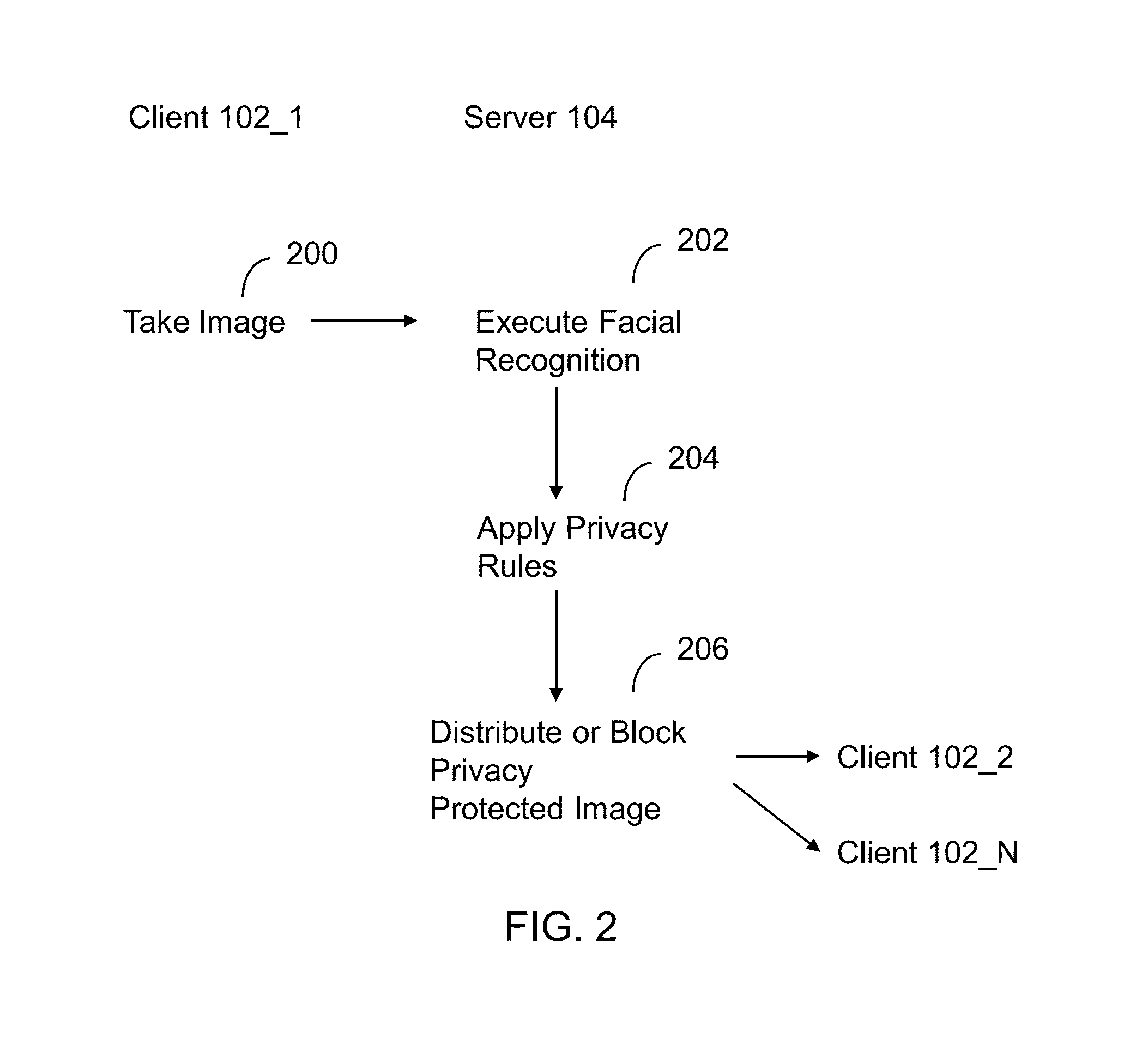
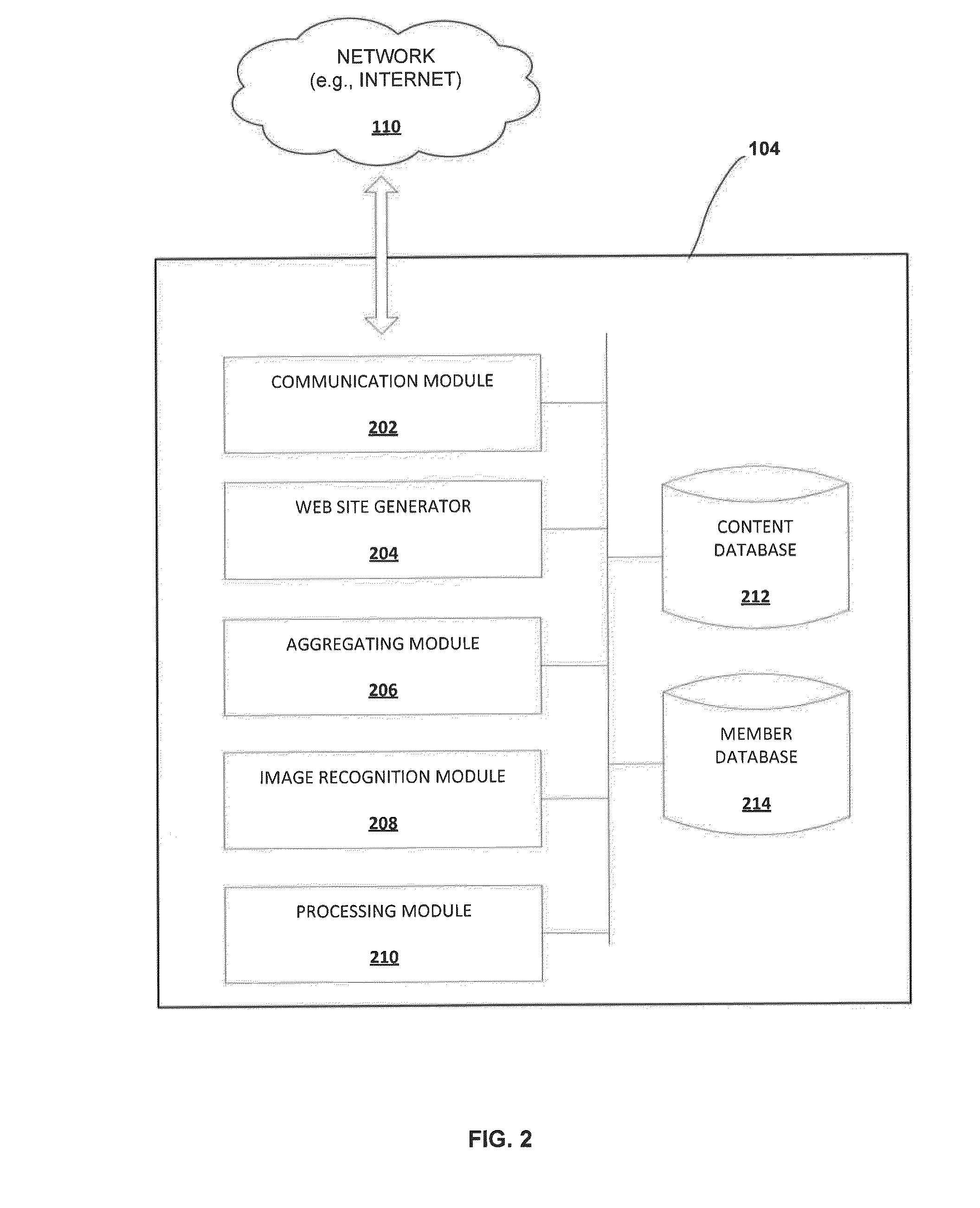
Apparatus and method for automated privacy protection in distributed images
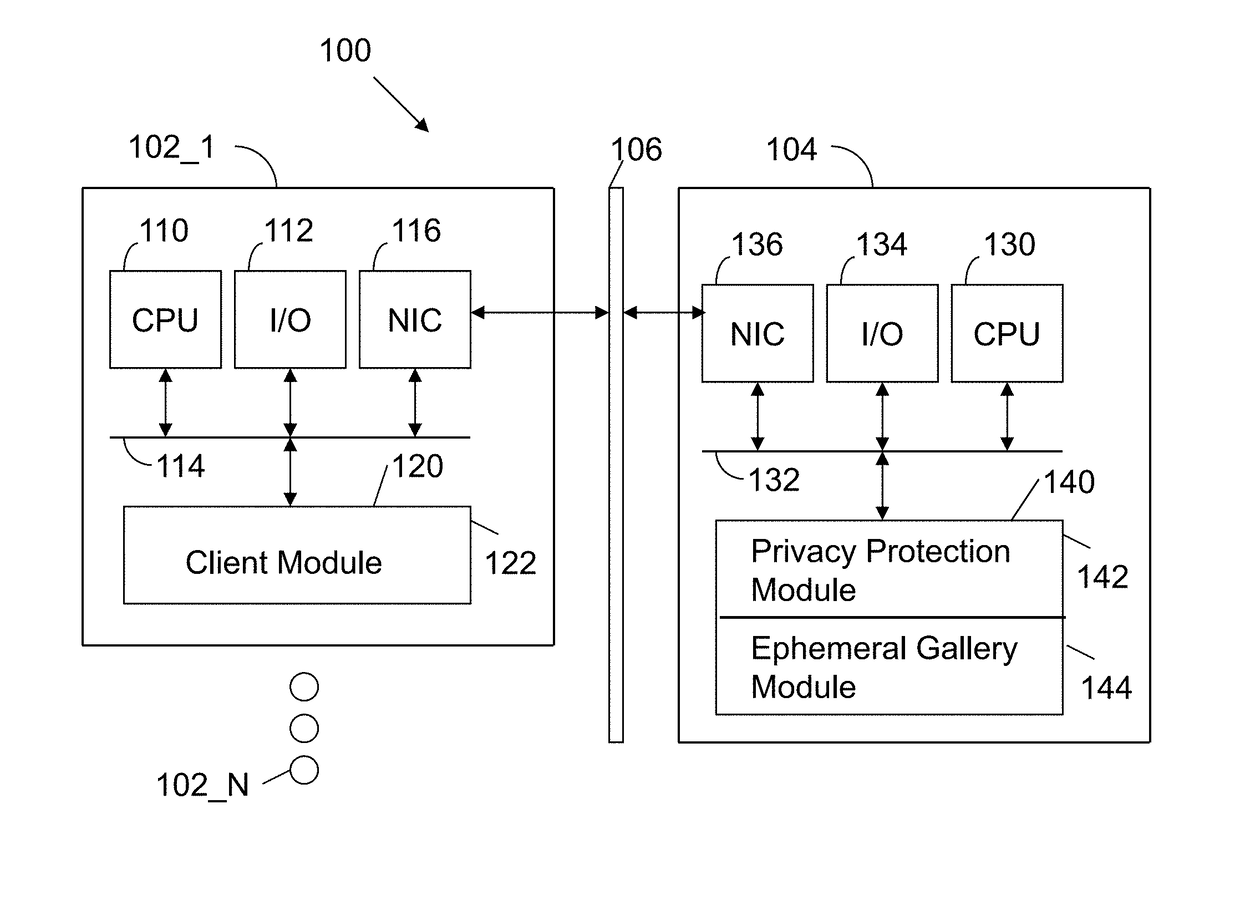
ActiveUS9396354B1Data processing applicationsCharacter and pattern recognitionPrivacy rulePrivacy protection
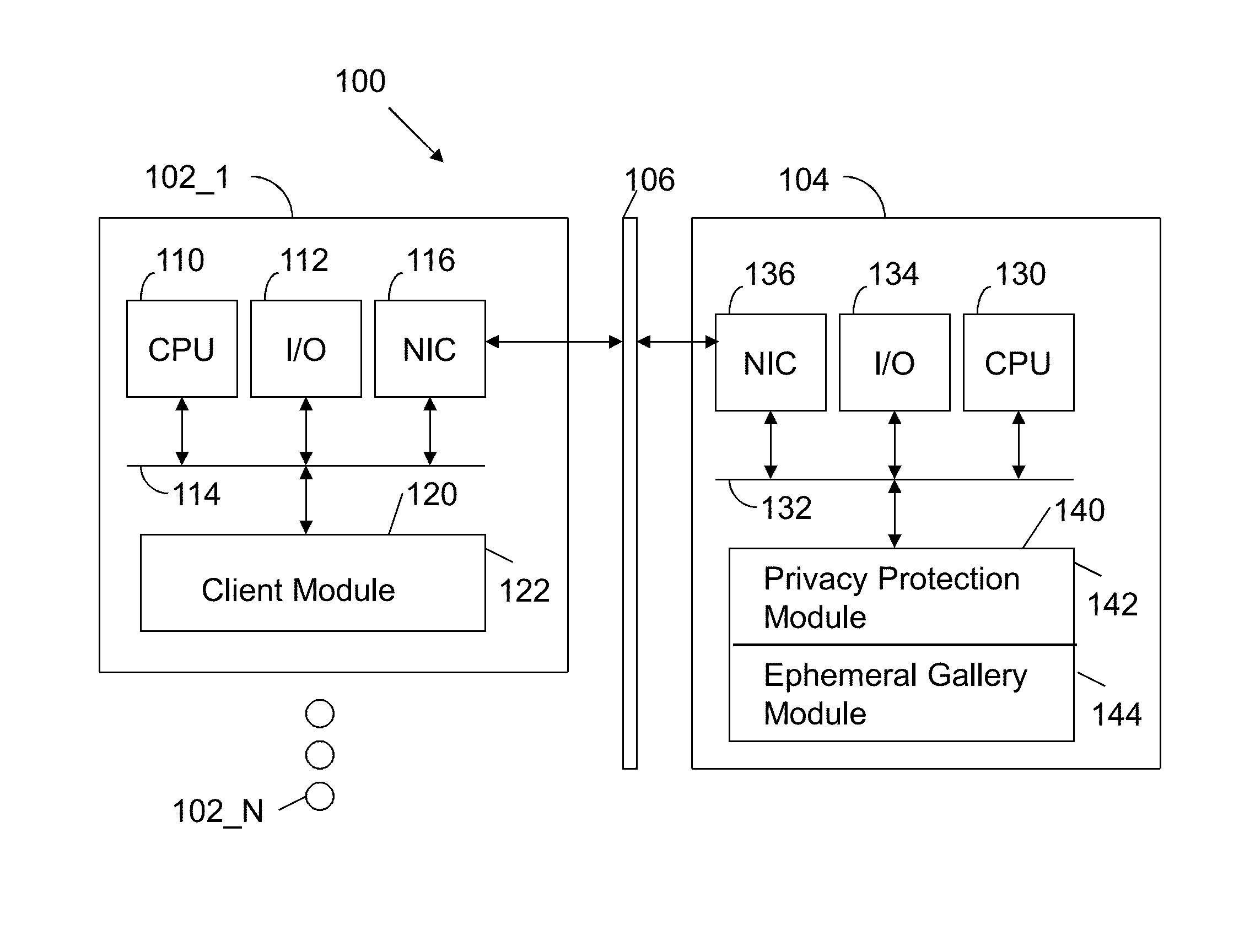
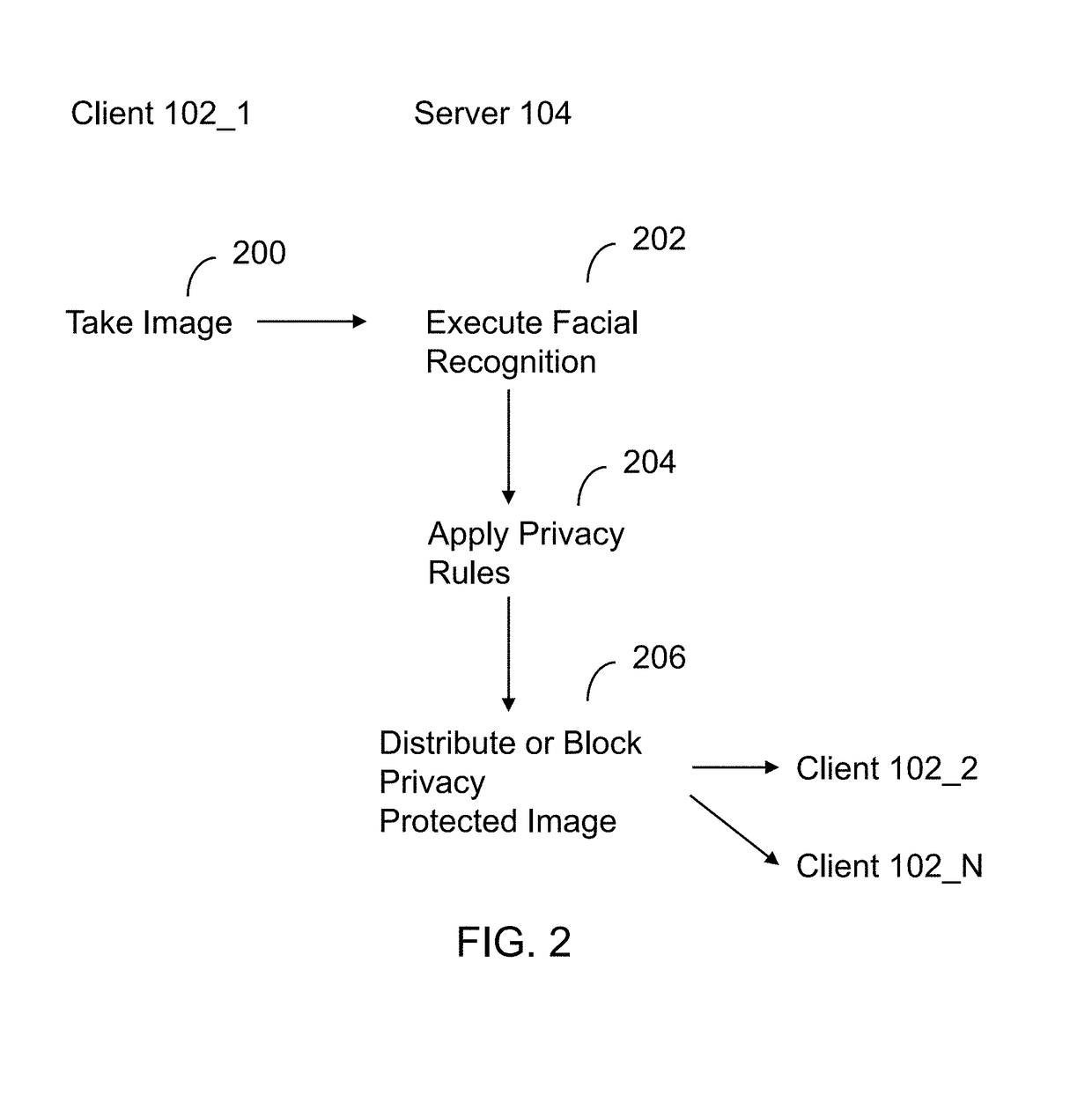
A method executed by a computer includes receiving an image from a client device. A facial recognition technique is executed against an individual face within the image to obtain a recognized face. Privacy rules are applied to the image, where the privacy rules are associated with privacy settings for a user associated with the recognized face. A privacy protected version of the image is distributed, where the privacy protected version of the image has an altered image feature.
Owner:SNAP INC
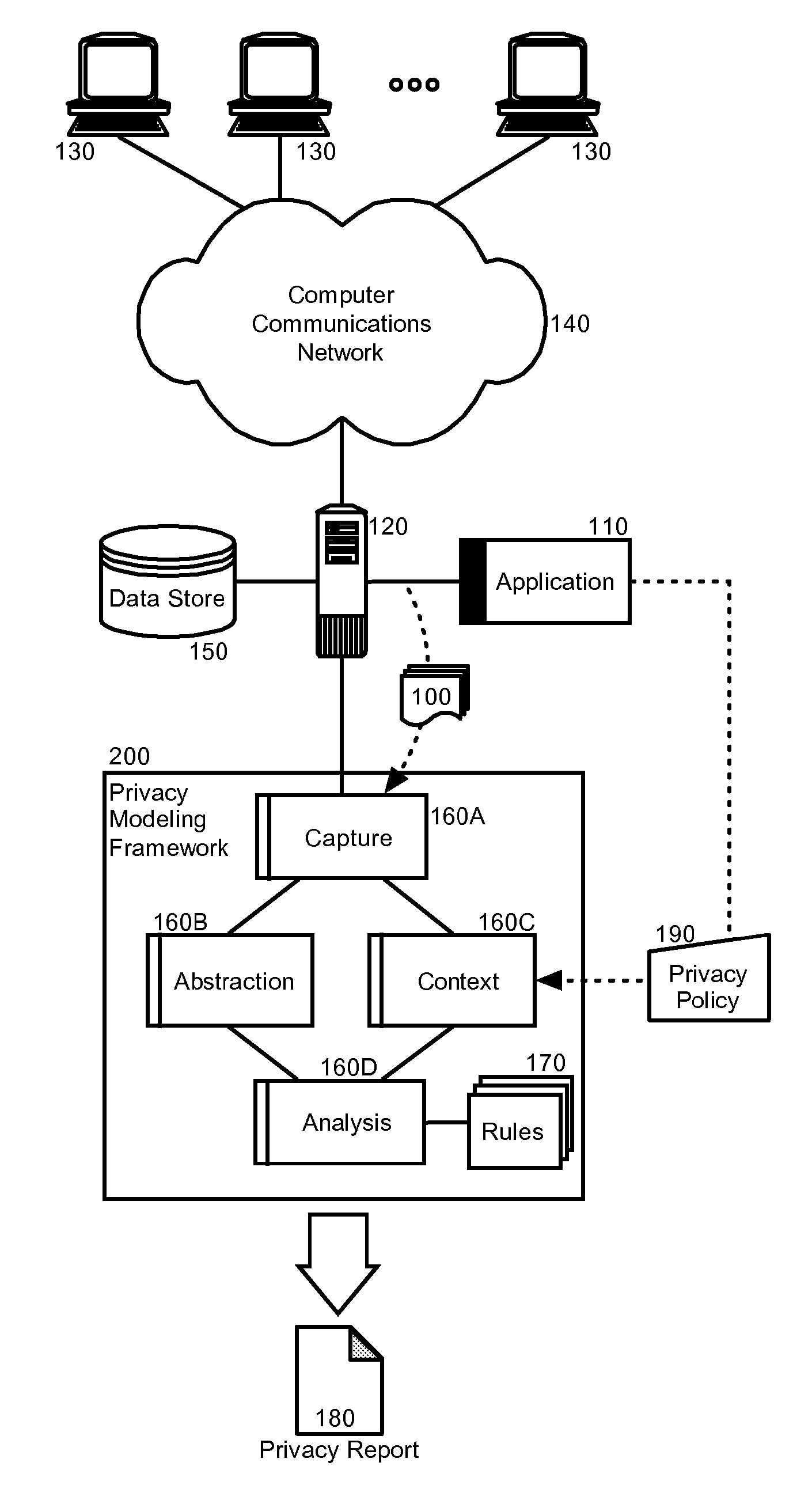
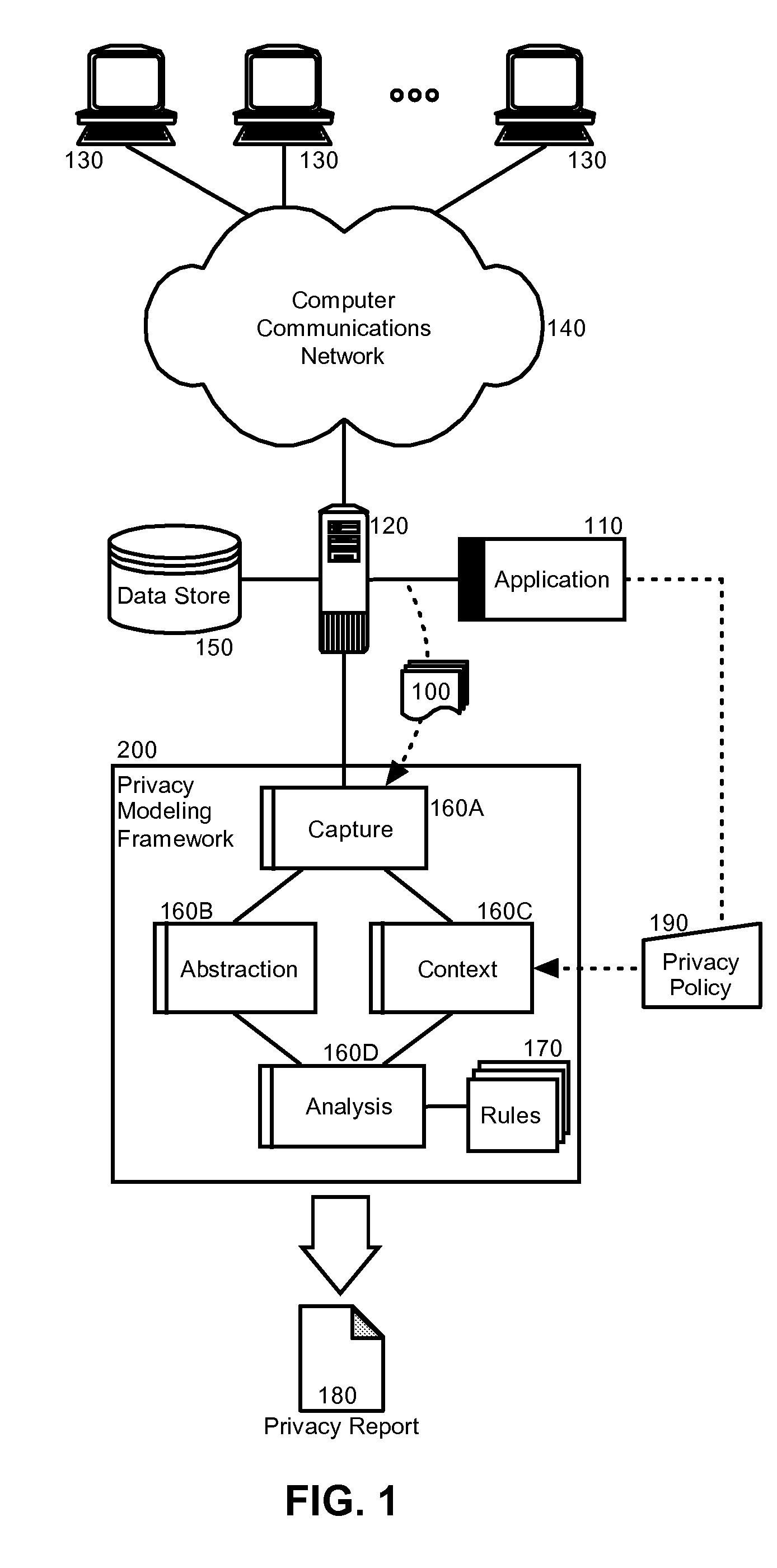
Privacy modeling framework for software applications
InactiveUS20070266420A1Computer security arrangementsOffice automationData processing systemCoupling
Embodiments of the present invention address deficiencies of the art in respect to privacy compliance assessment for computer software and provide a method, system and computer program product for a privacy model framework for software applications. In one embodiment, a privacy modeling data processing system can be provided. The privacy modeling data processing system can include a modeling framework configured for communicative coupling to a software application. The modeling framework can capture information flows from requests to and responses from a coupled software application, and can rules-based process the captured information flows for privacy rules to generate a privacy compliance report for the software application.
Owner:IBM CORP
Privacy management policy hub
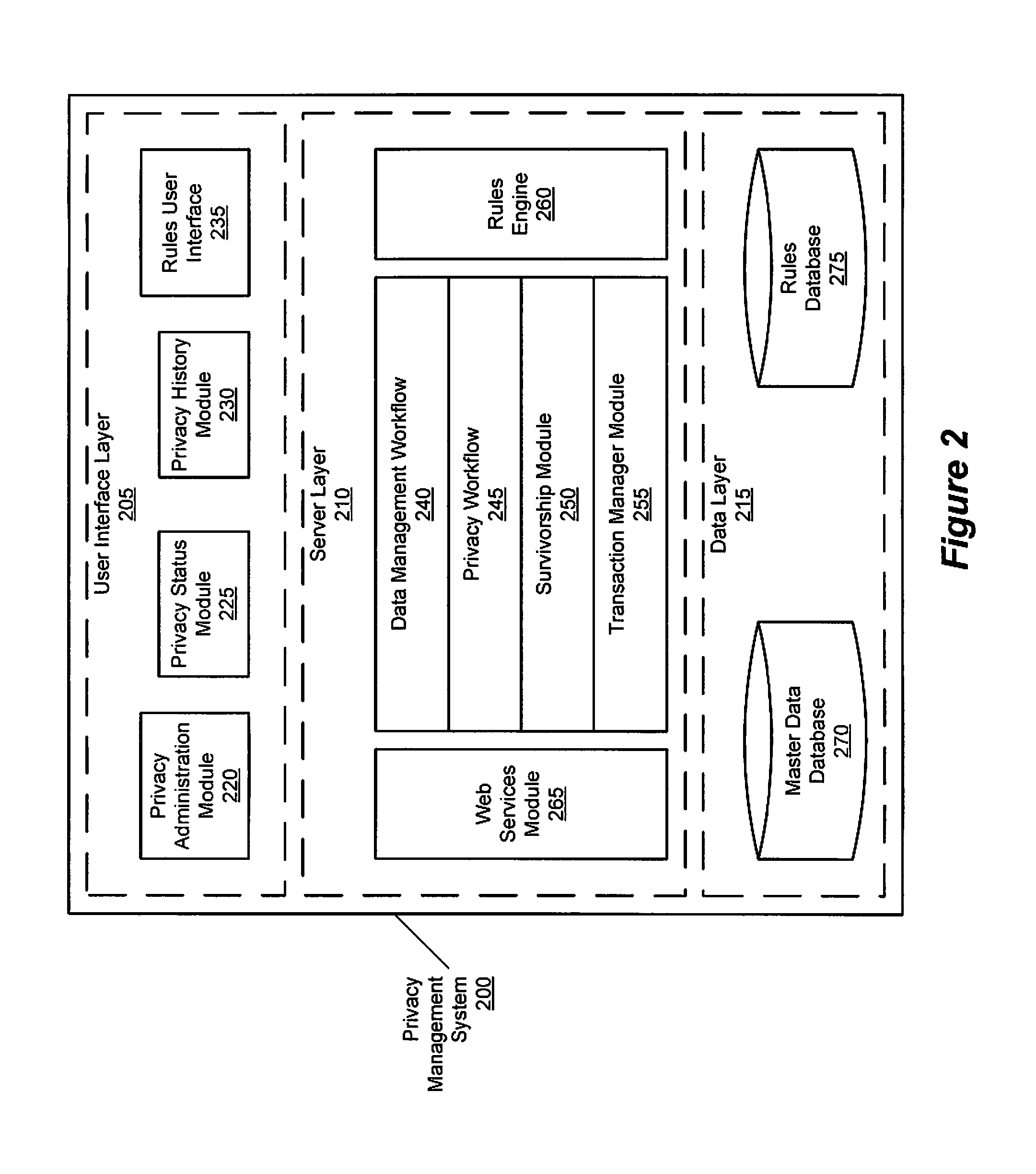
A system architecture is disclosed that includes a privacy management system. In particular, the privacy management system provides a policy hub for maintaining and managing customer privacy information. The privacy management system maintains a master data database for customer information and customer privacy preferences, and a rules database for privacy rules. The privacy management system captures, synchronizes, and stores customer privacy data. Privacy rules may be authored using a privacy management vocabulary, and can be customized for an enterprise's privacy policies.
Owner:ORACLE INT CORP
Privacy firewall
ActiveUS9665722B2Protect normal useAvoid identificationRelational databasesDigital data protectionSupplicantInternet privacy
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
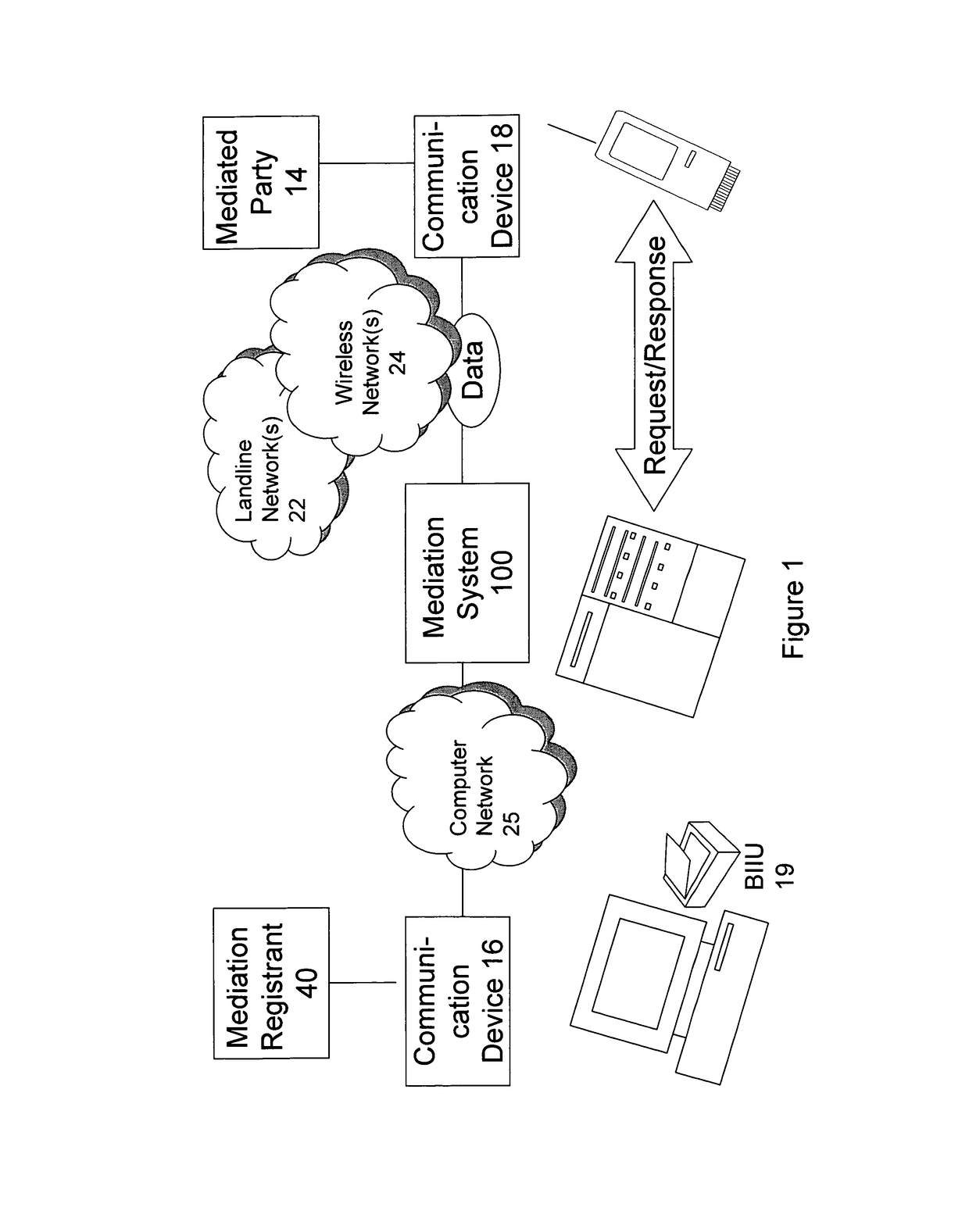
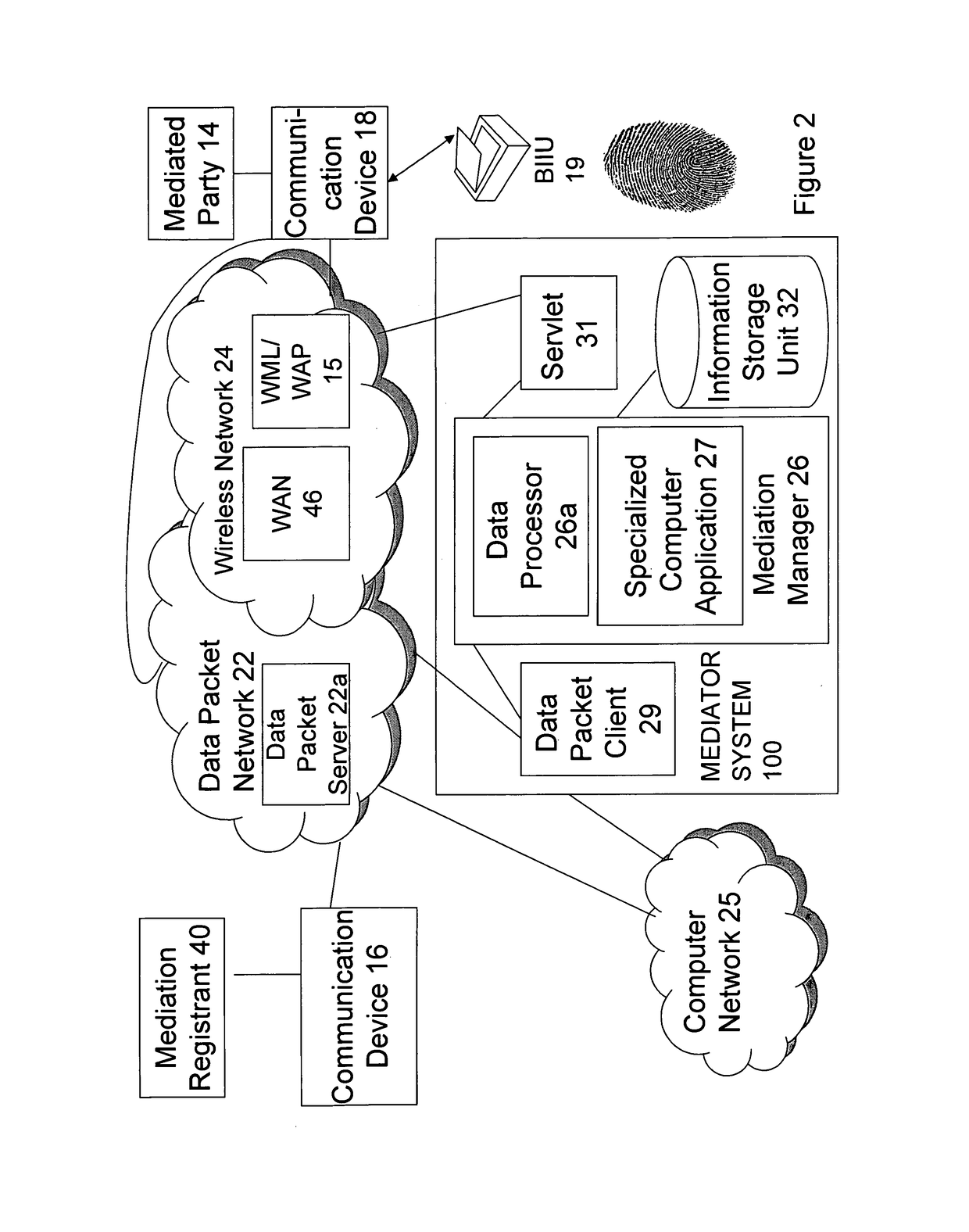
Methods using mediation software for rapid health care support over a secured wireless network; methods of composition; and computer program products therefor
ActiveUS9928379B1Increased riskImprove privacyMedical data miningWeb data indexingBiometric dataPrivacy rule
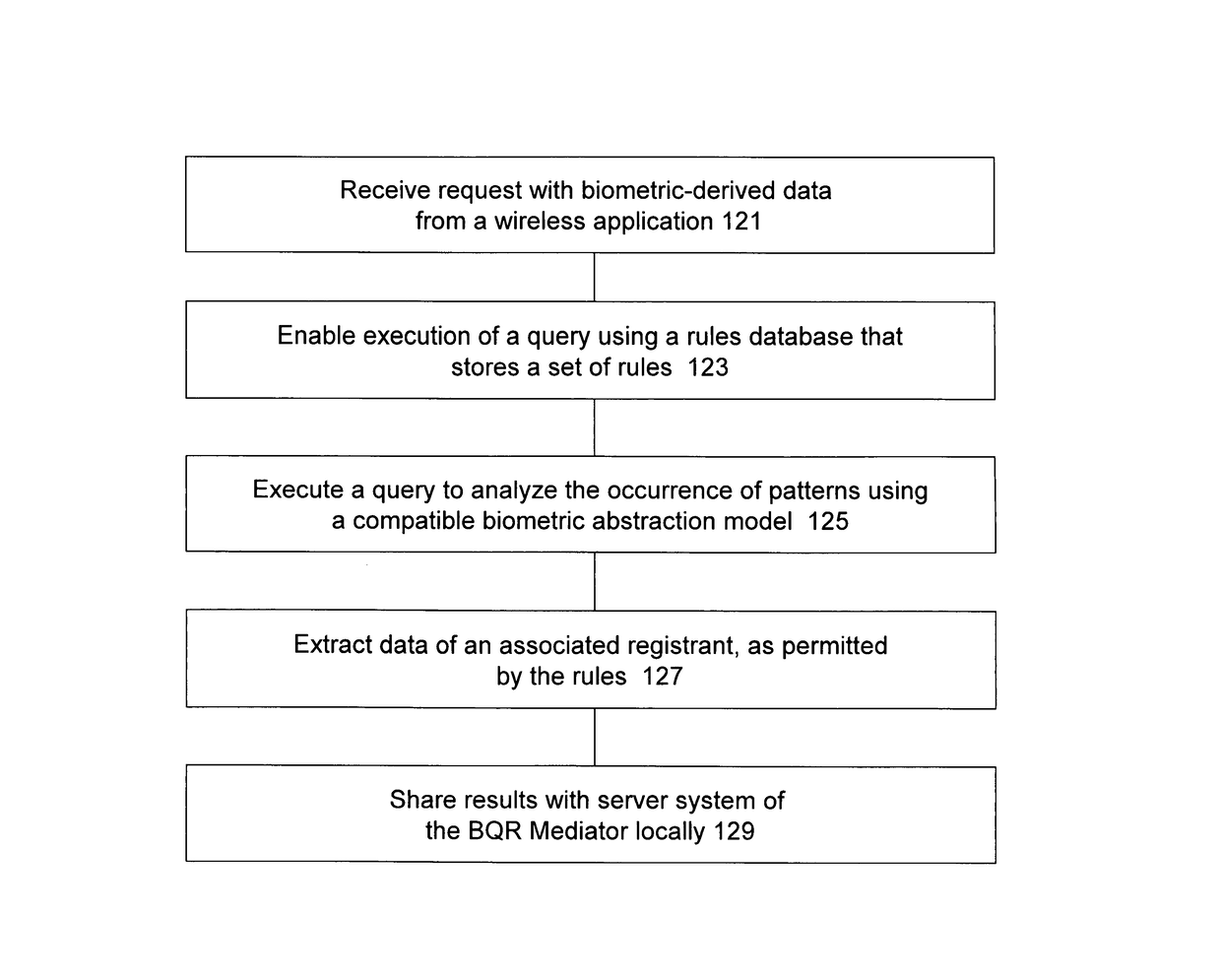
Some of these new methods harness distributed computing capabilities to integrate biometric abstraction processes, wireless network connectivity, and specialized software for mediation, to produce a unified result set. A mediator that enables rapid health care support is used in a computer system having a database of information to be shared with authorized requesters, under privacy rules or other pre-defined constraints. The methods, using specialized software for mediation, are preferably enabled to process a securely transmitted remote data request as a query to verify or identify an individual, whether it is sent via a network that is wireless in any part, or not. Upon receiving a remote request, typically sent by a requesting application other than one operated by the individual who is the subject of the request, the mediator uses the individual's transformed biometric data of the request to rapidly advance query resolution, under all query preprocessing rules, and query results post-processing rules, that apply.
Owner:HOFFER STEVEN M
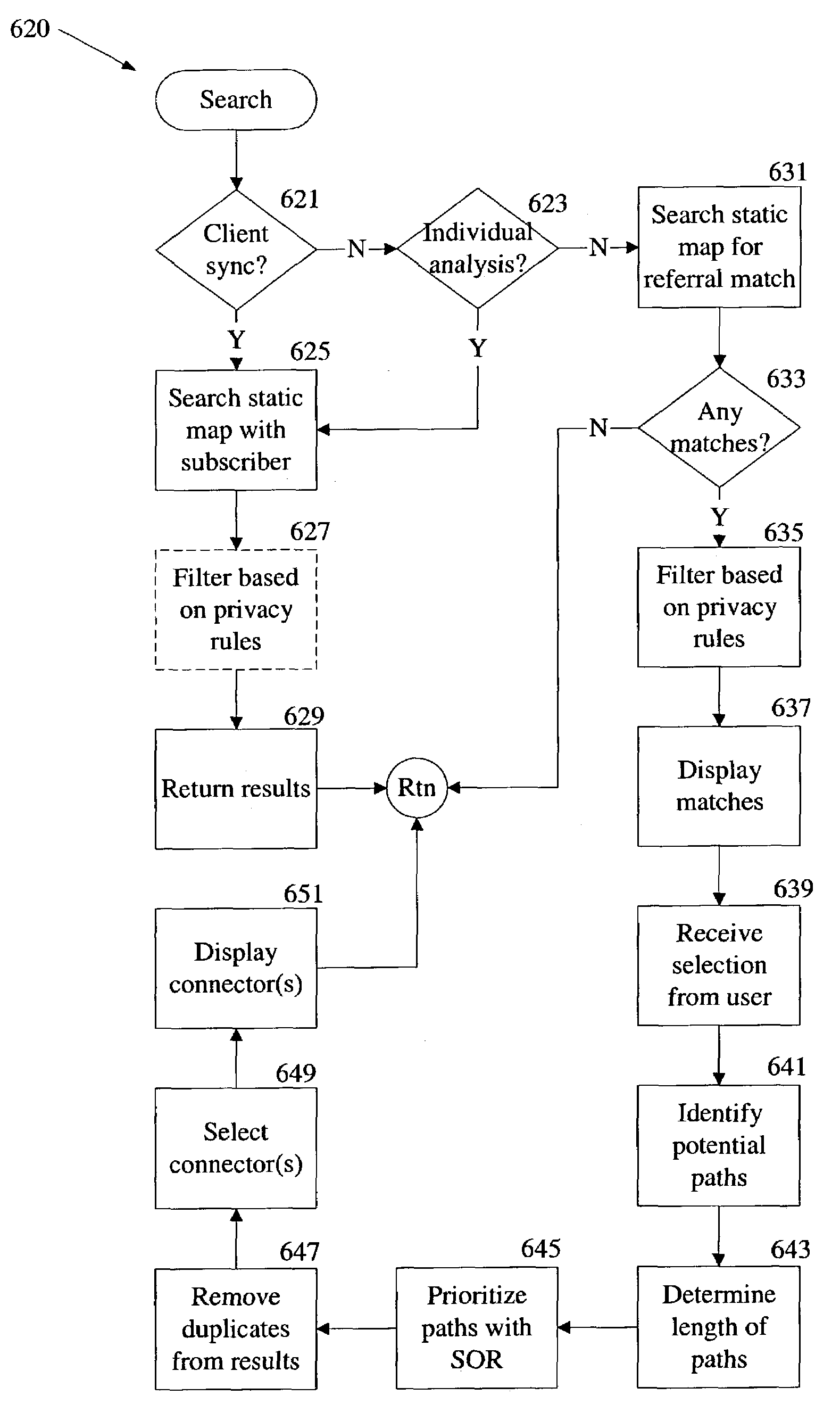
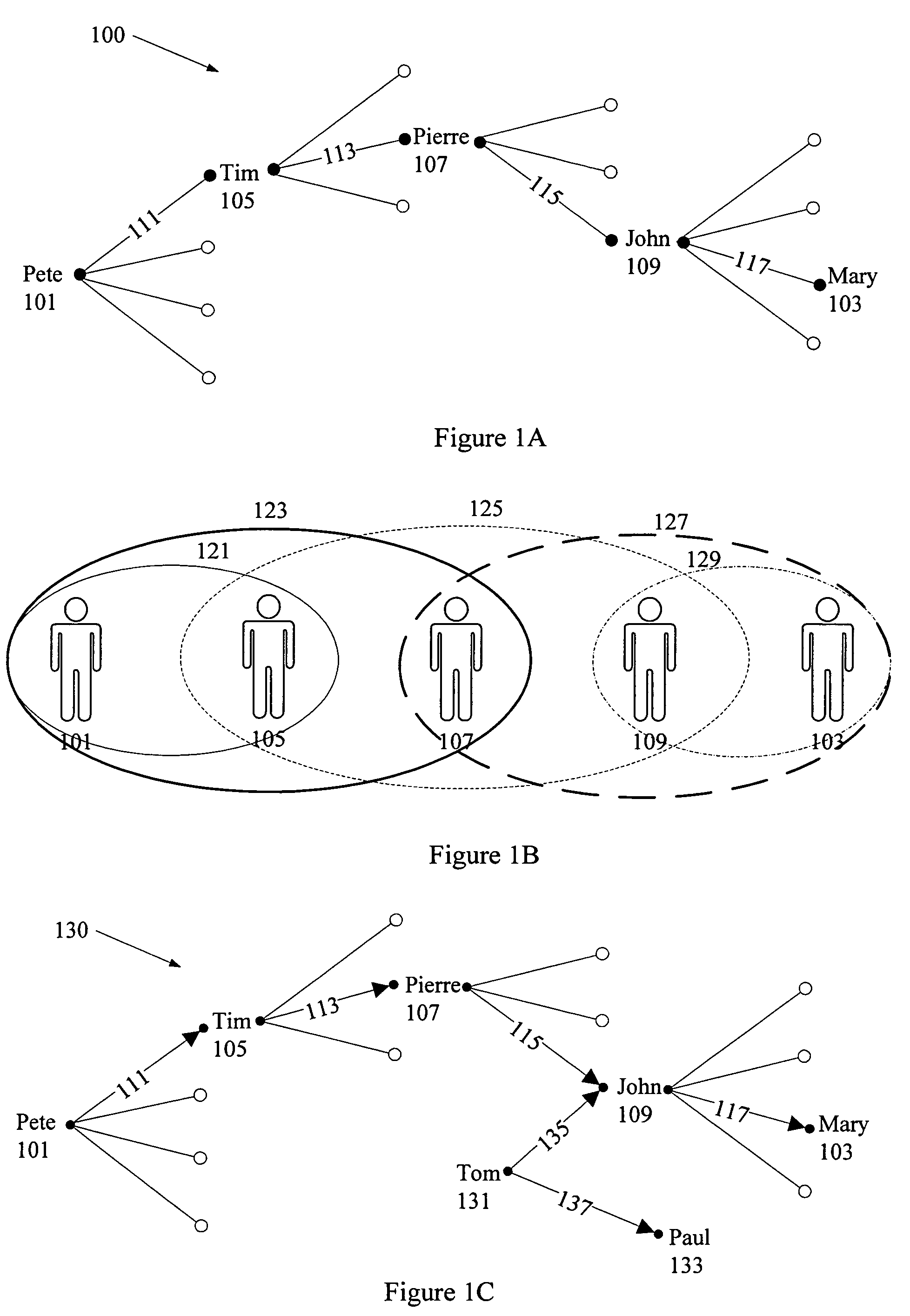
Selecting an optimal path through a relationship graph
InactiveUS7512612B1Data processing applicationsDigital data information retrievalPrivacy ruleData mining
Owner:SPOKE SOFTWARE
Apparatus and method for automated privacy protection in distributed images
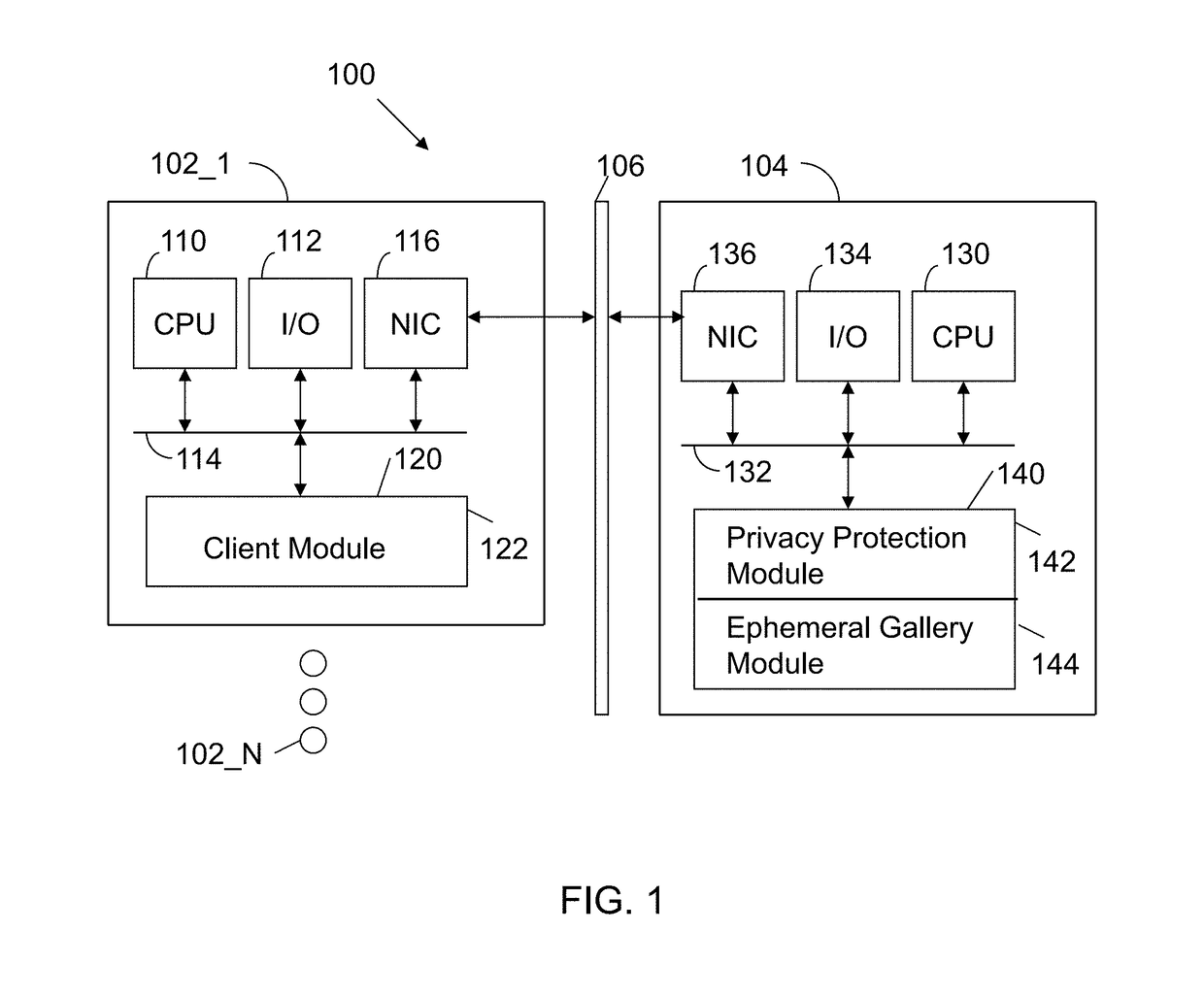
ActiveUS9785796B1Data processing applicationsCharacter and pattern recognitionPrivacy rulePrivacy protection
A method executed by a computer includes receiving an image from a client device. A facial recognition technique is executed against an individual face within the image to obtain a recognized face. Privacy rules are applied to the image, where the privacy rules are associated with privacy settings for a user associated with the recognized face. A privacy protected version of the image is distributed, where the privacy protected version of the image has an altered image feature.
Owner:SNAP INC
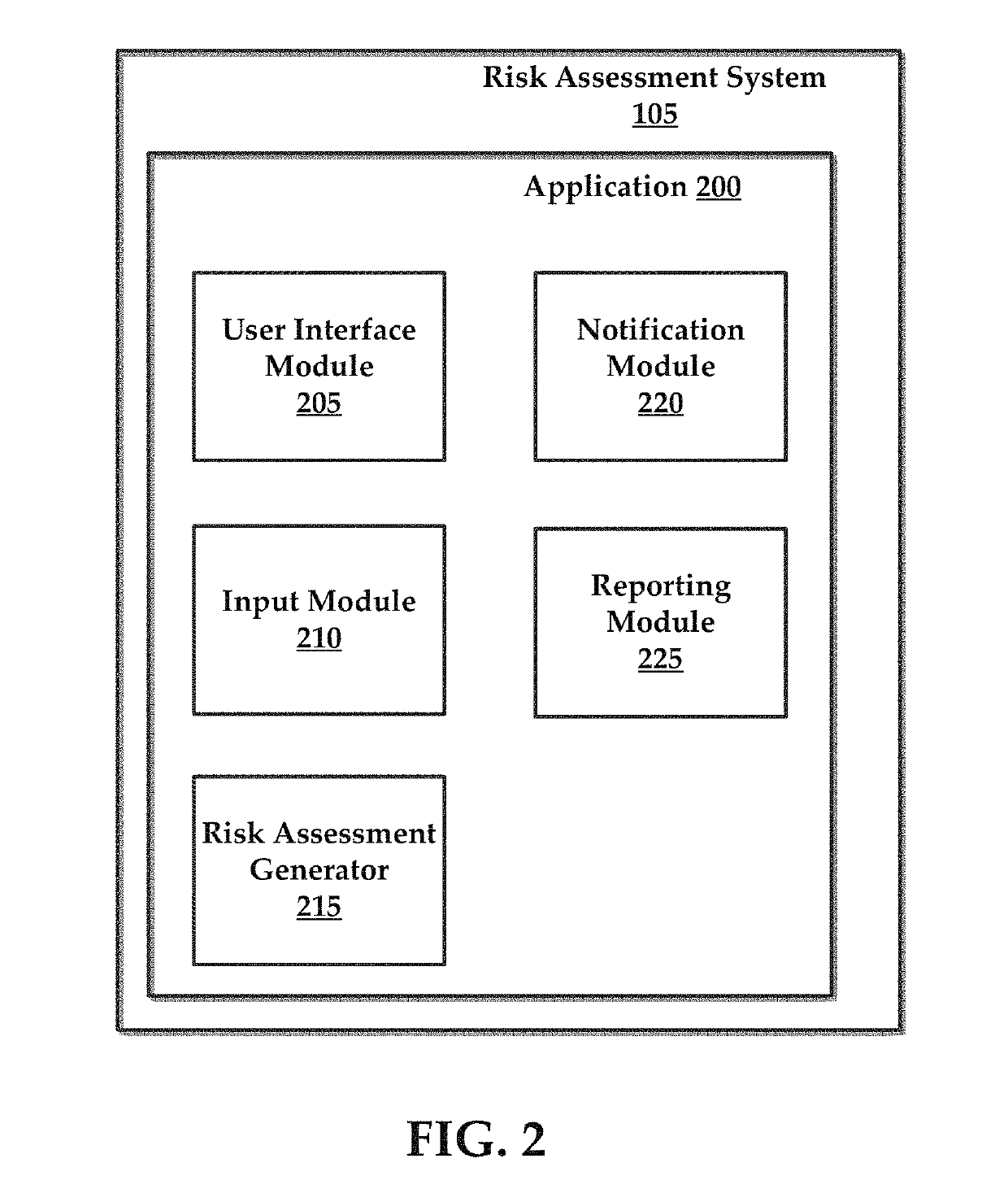
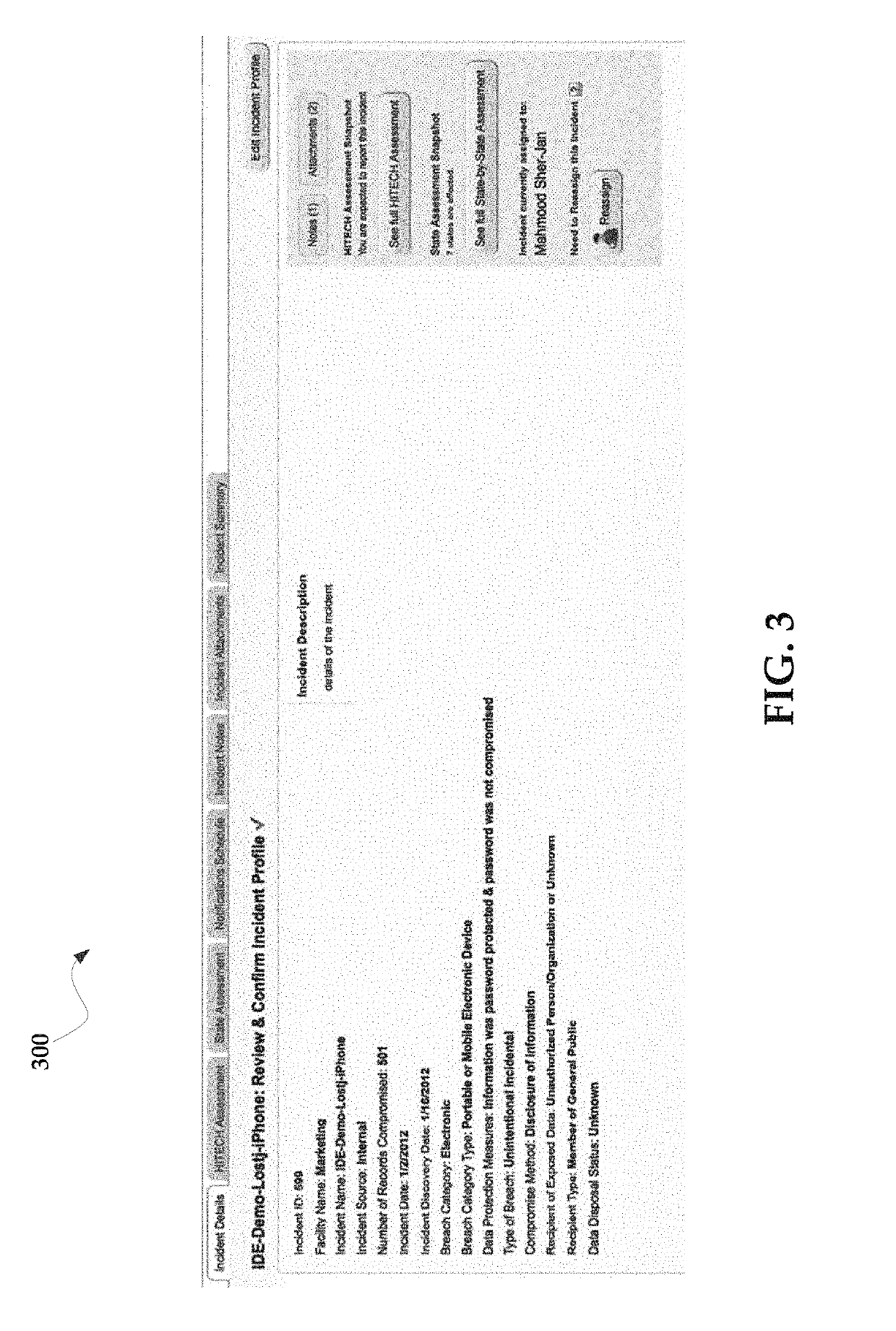
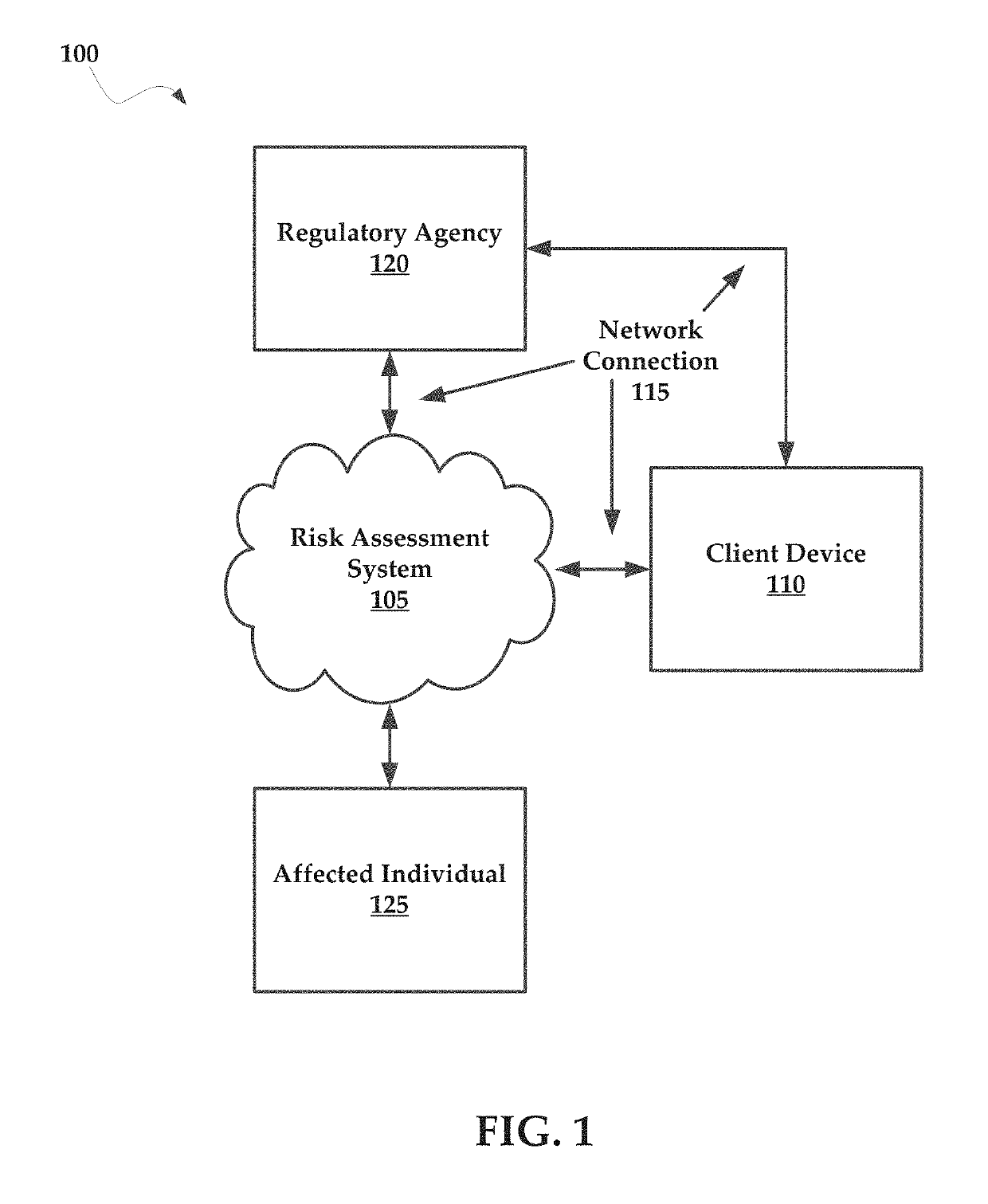
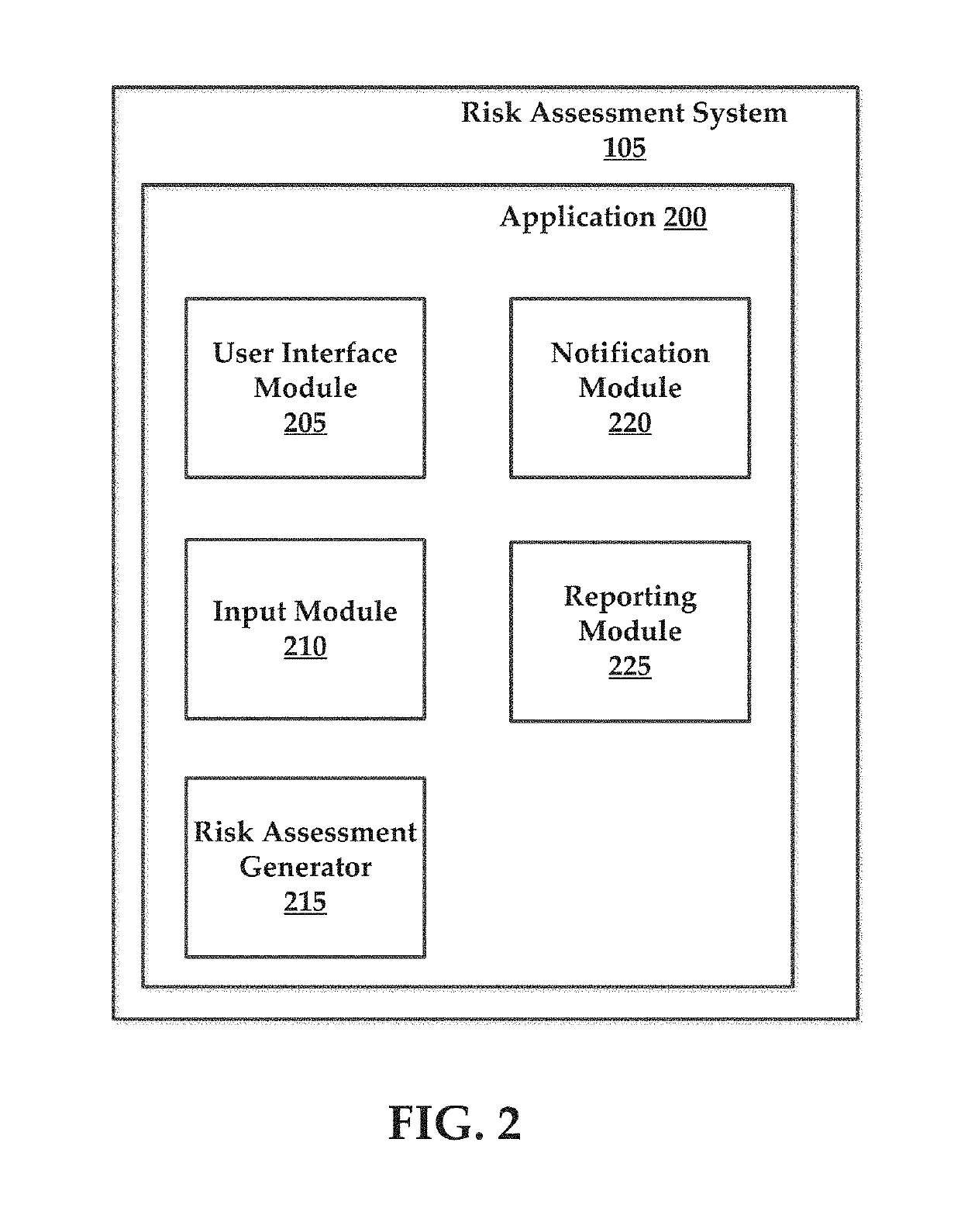
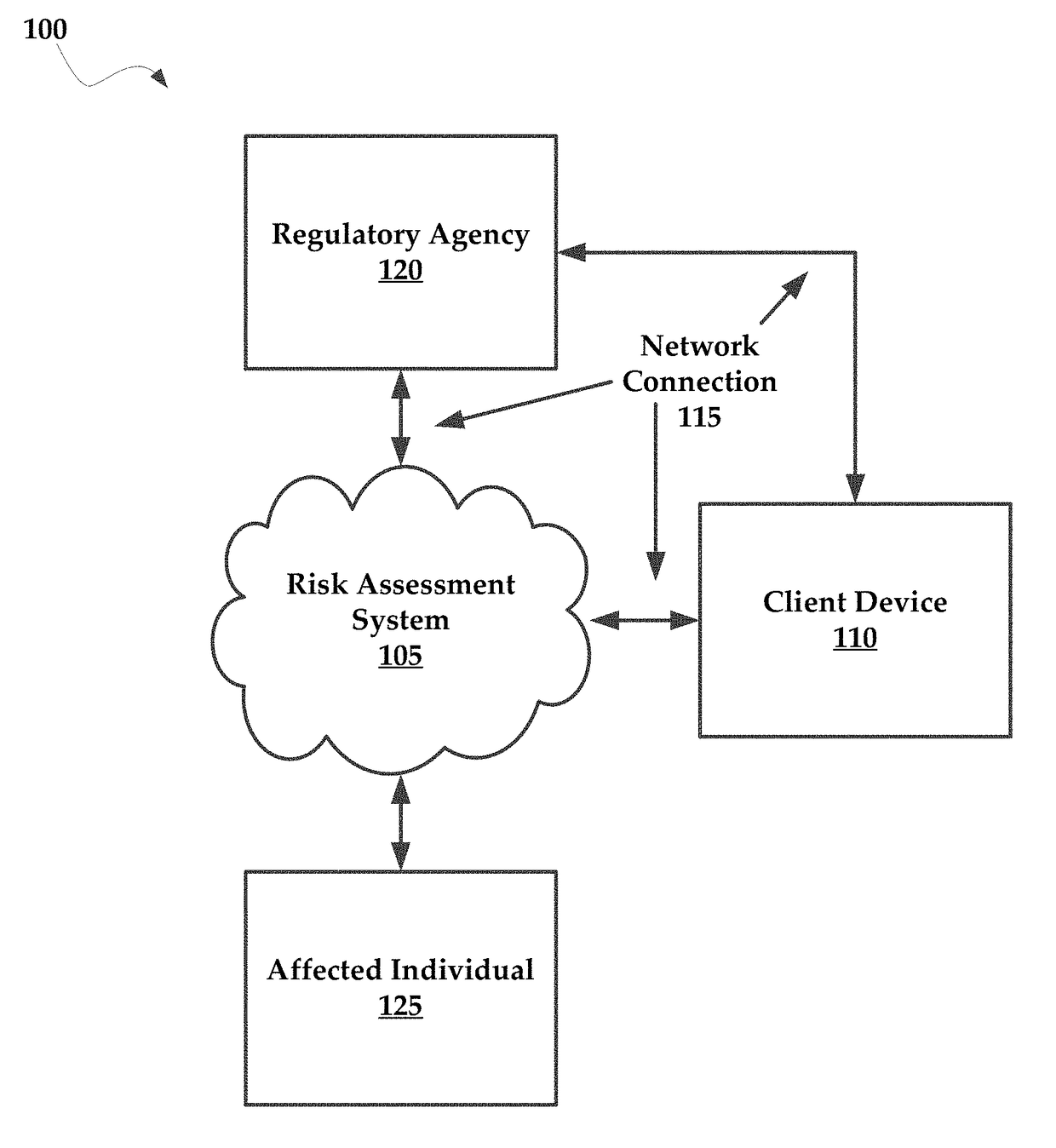
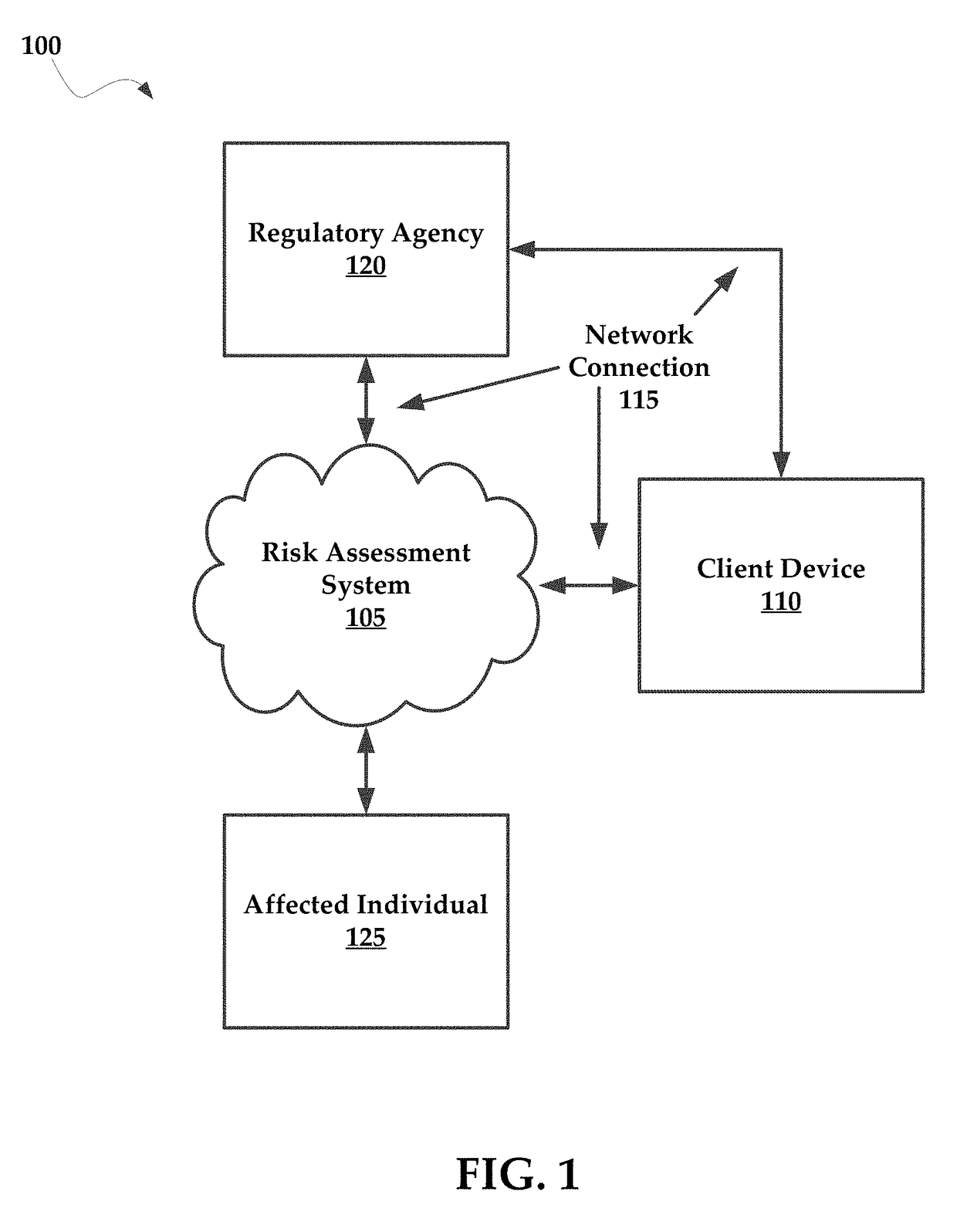
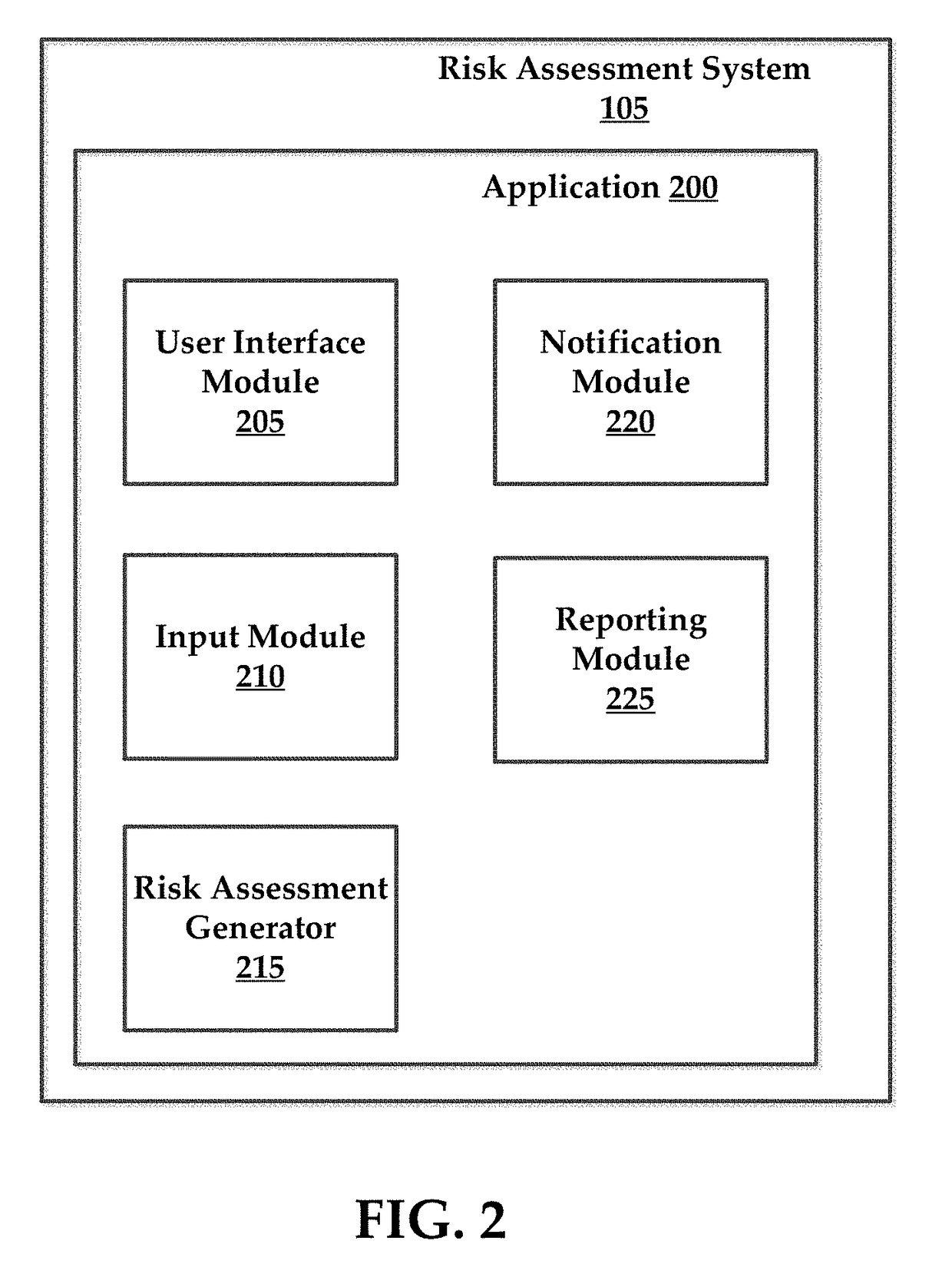
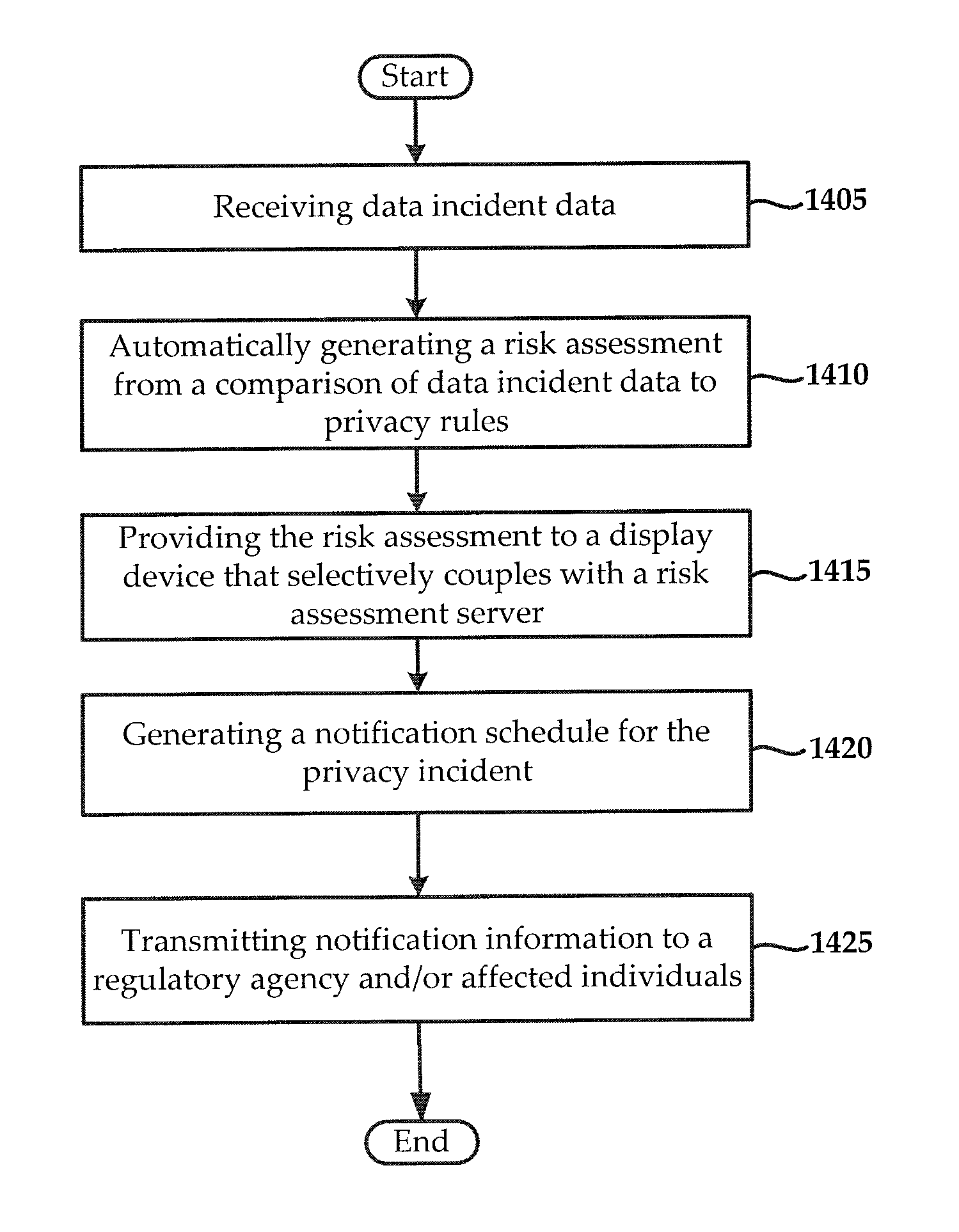
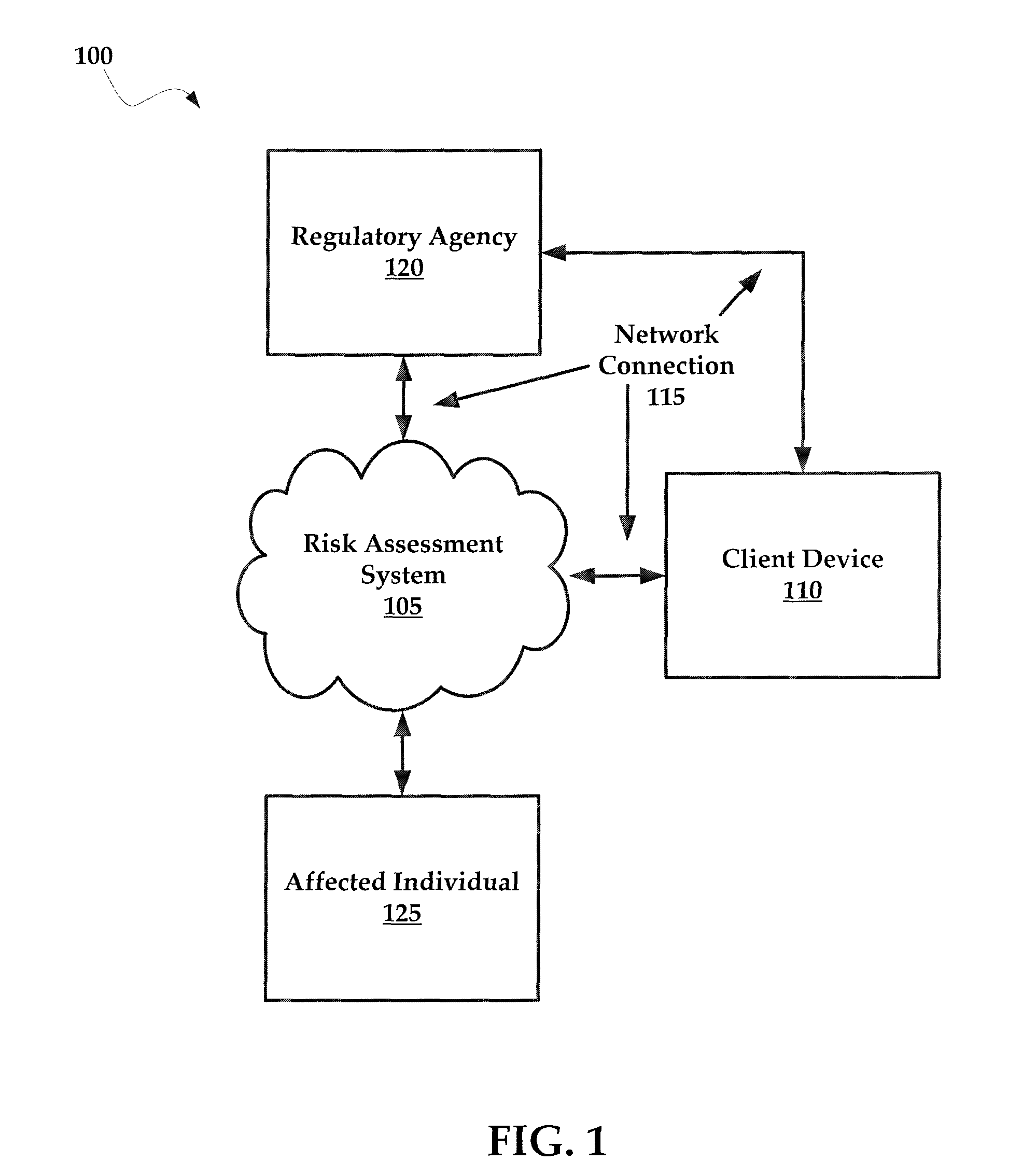
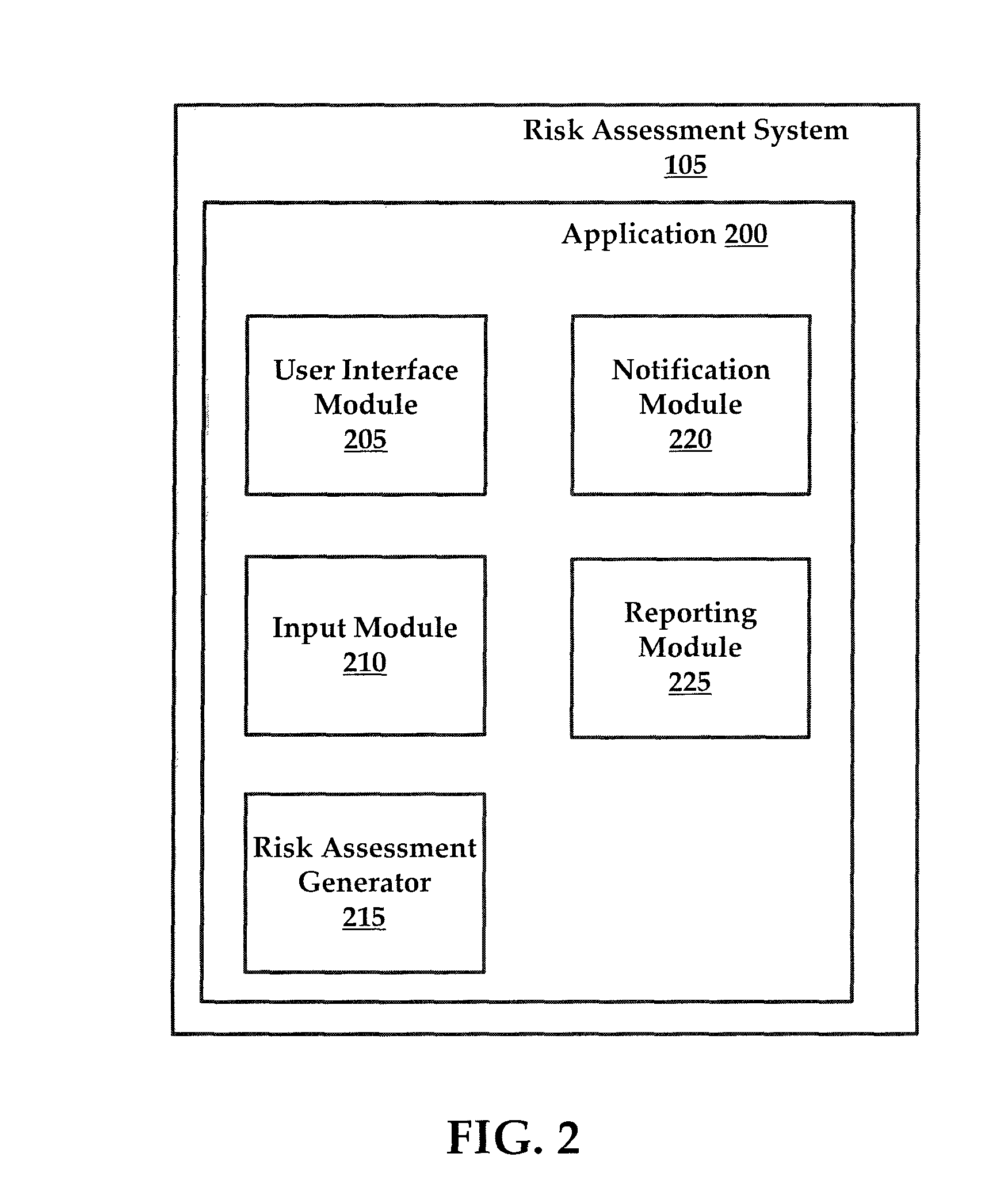
Systems and methods for managing multi-region data incidents
ActiveUS10445508B2Digital data protectionPlatform integrity maintainanceInternet privacyPrivacy rule
Systems and methods for managing a multi-region data incident are provided herein. Example methods include receiving, via a risk assessment server, in response to an occurrence of the data incident, data incident data that including information corresponding to the data incident, wherein the data incident has a plurality of facets with each facet having any of unique and overlapping set of privacy data and media type and associated risk factors requiring facet specific incident risk assessment, automatically generating, via the risk assessment server, a risk assessment and decision-support guidance whether the facet is reportable, from a comparison of the facet to privacy rules, the privacy rules define requirements associated with data incident notification obligations, and providing, via the risk assessment server, the risk assessment to a display device that selectively couples with the risk assessment server.
Owner:RADAR LLC
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS20060143688A1Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
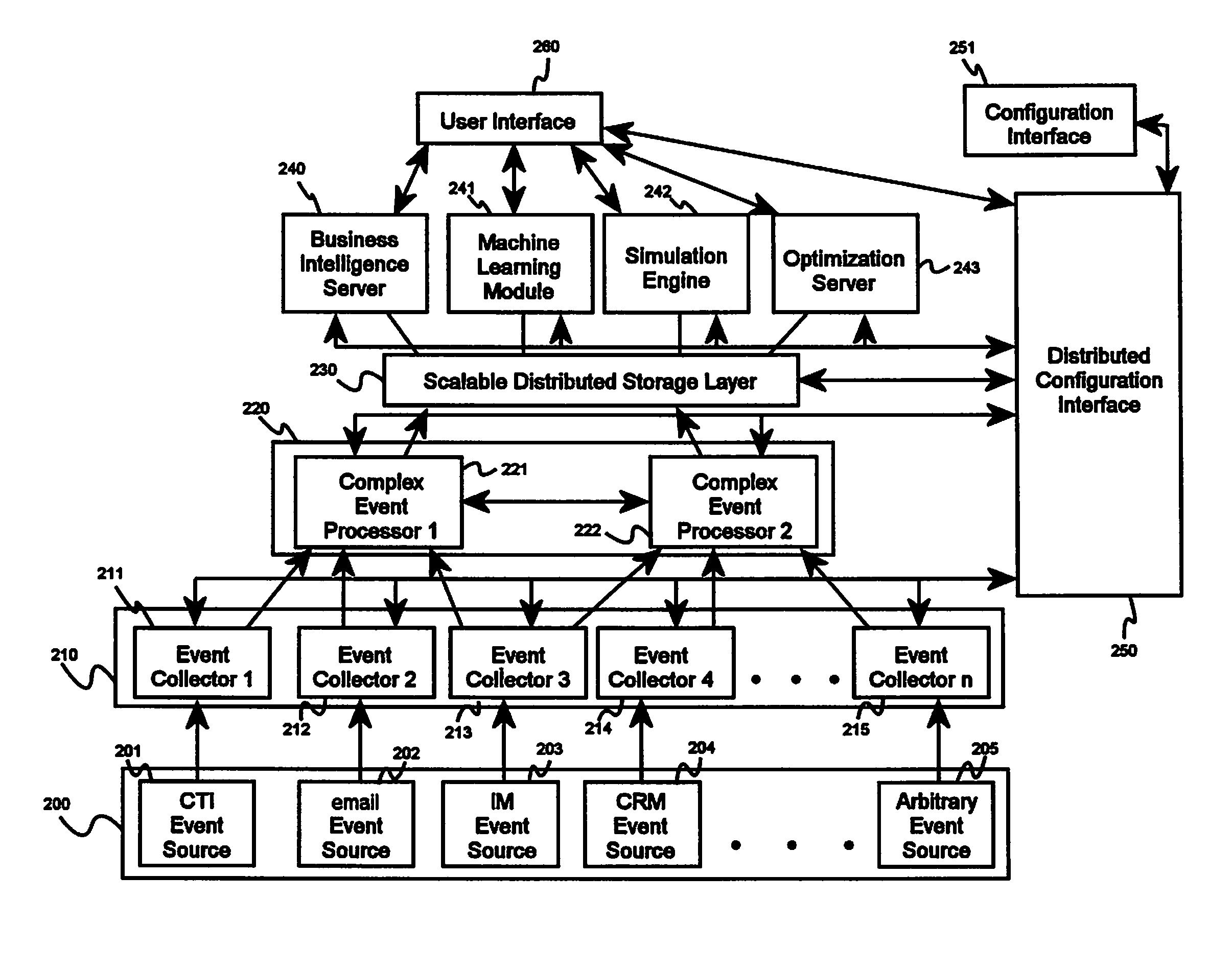
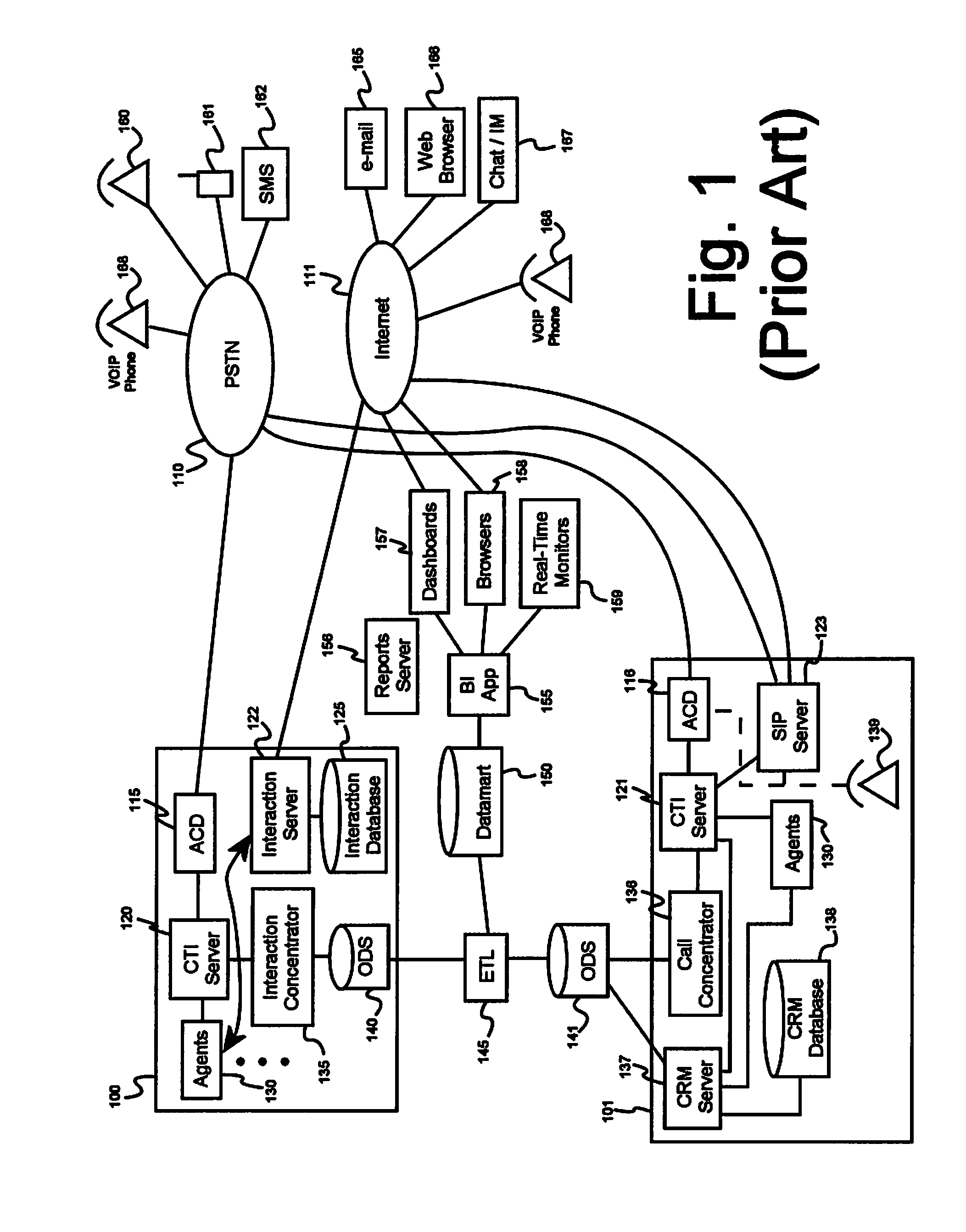
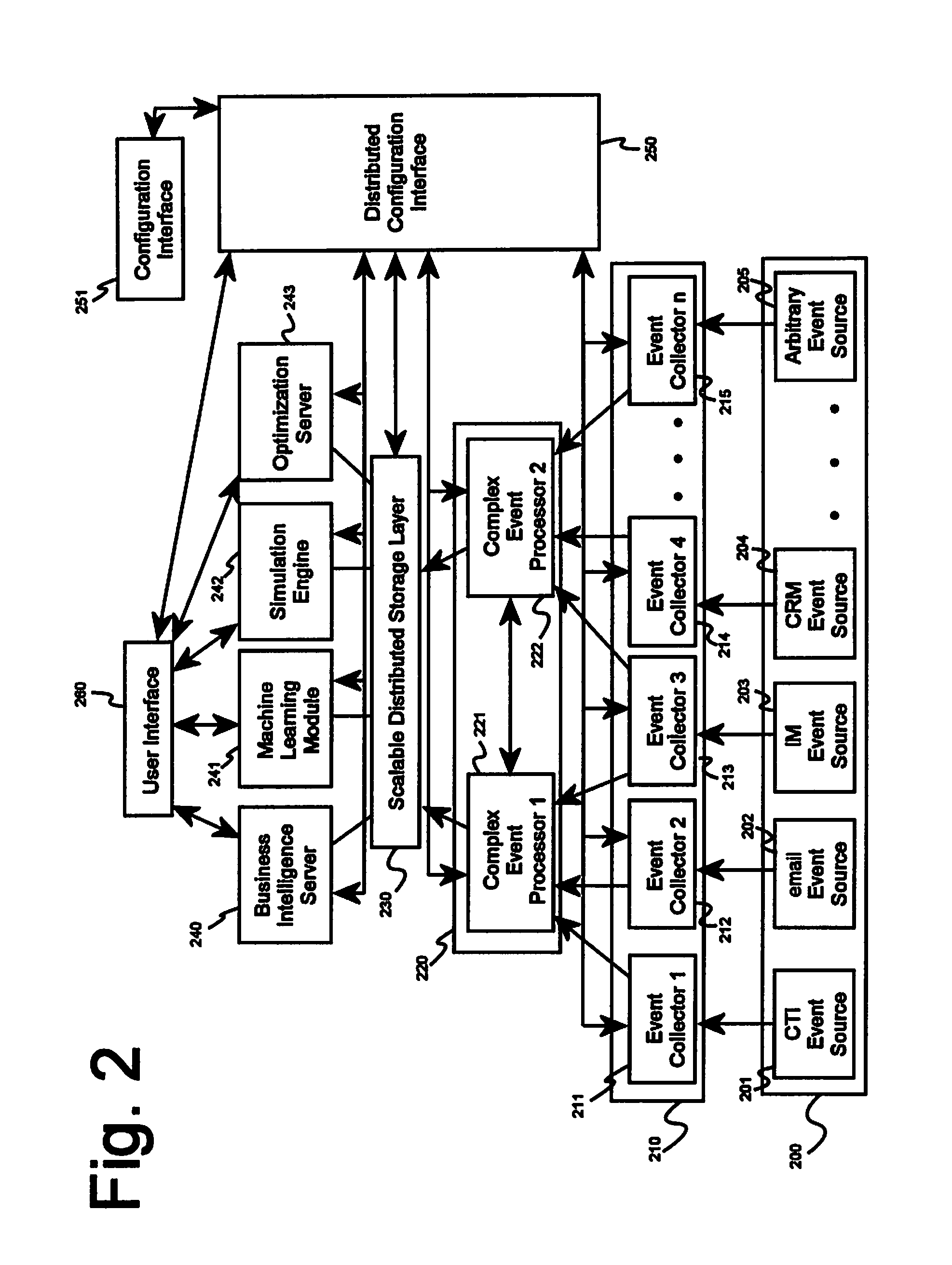
System and method for conducting real-time and historical analysis of complex customer care processes
A system for conducting real-time and historical analysis of complex customer care processes, comprising an event collector software module, a complex event processing software module adapted to receive events from the event collector software module, a distributed data storage layer, a business analytics software module adapted to receive and process data from the distributed data storage layer, a distributed configuration software module, and a user interface software module adapted to receive analytics results from the business analytics software module.Upon receiving an event from an event source, the event collector software module at least converts the event into a standard event data format suitable for use by the complex event processing software module and extracts or masks sensitive data from the event based on privacy rules maintained by the distributed configuration software module.
Owner:NEW VOICE MEDIA LIMITED
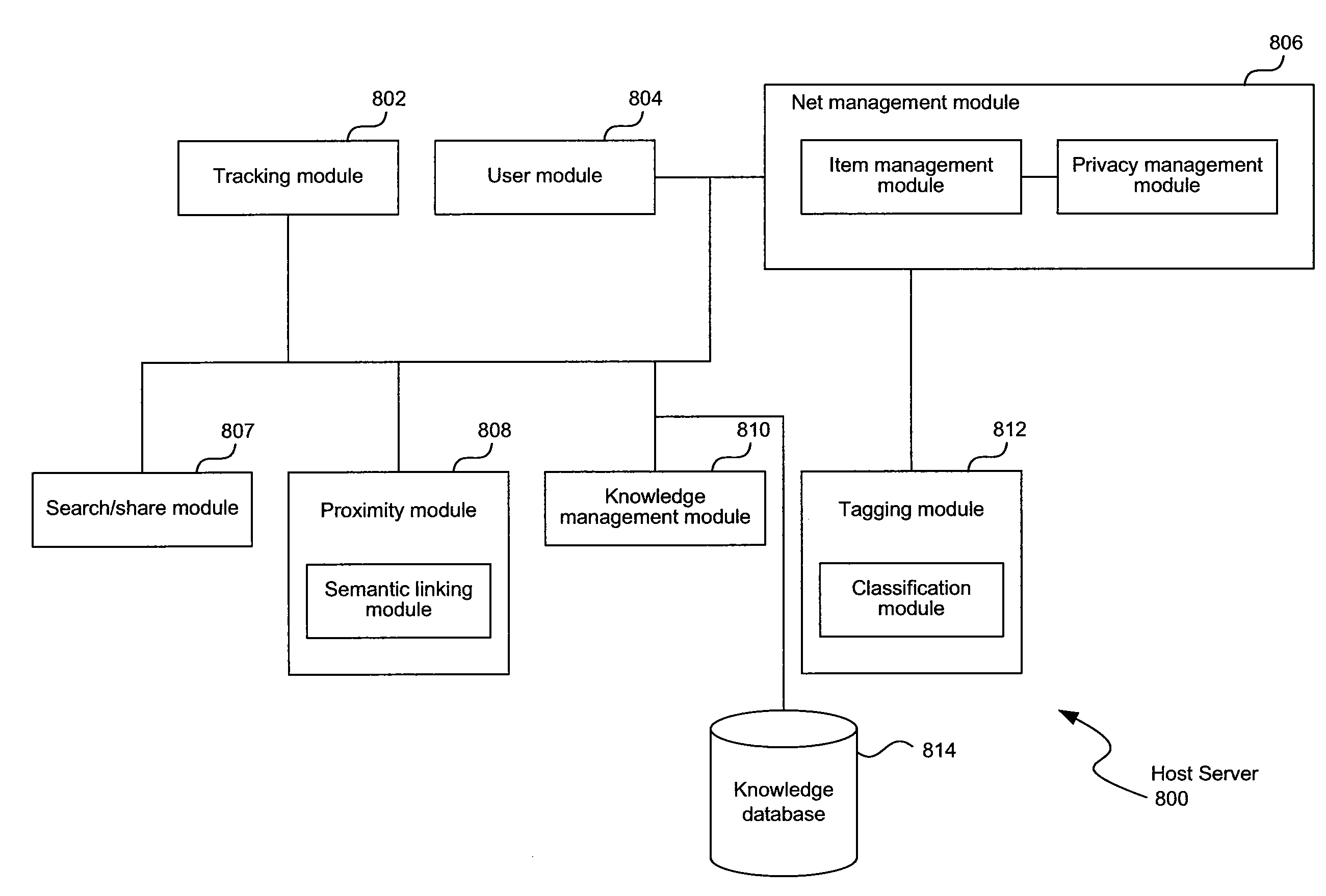
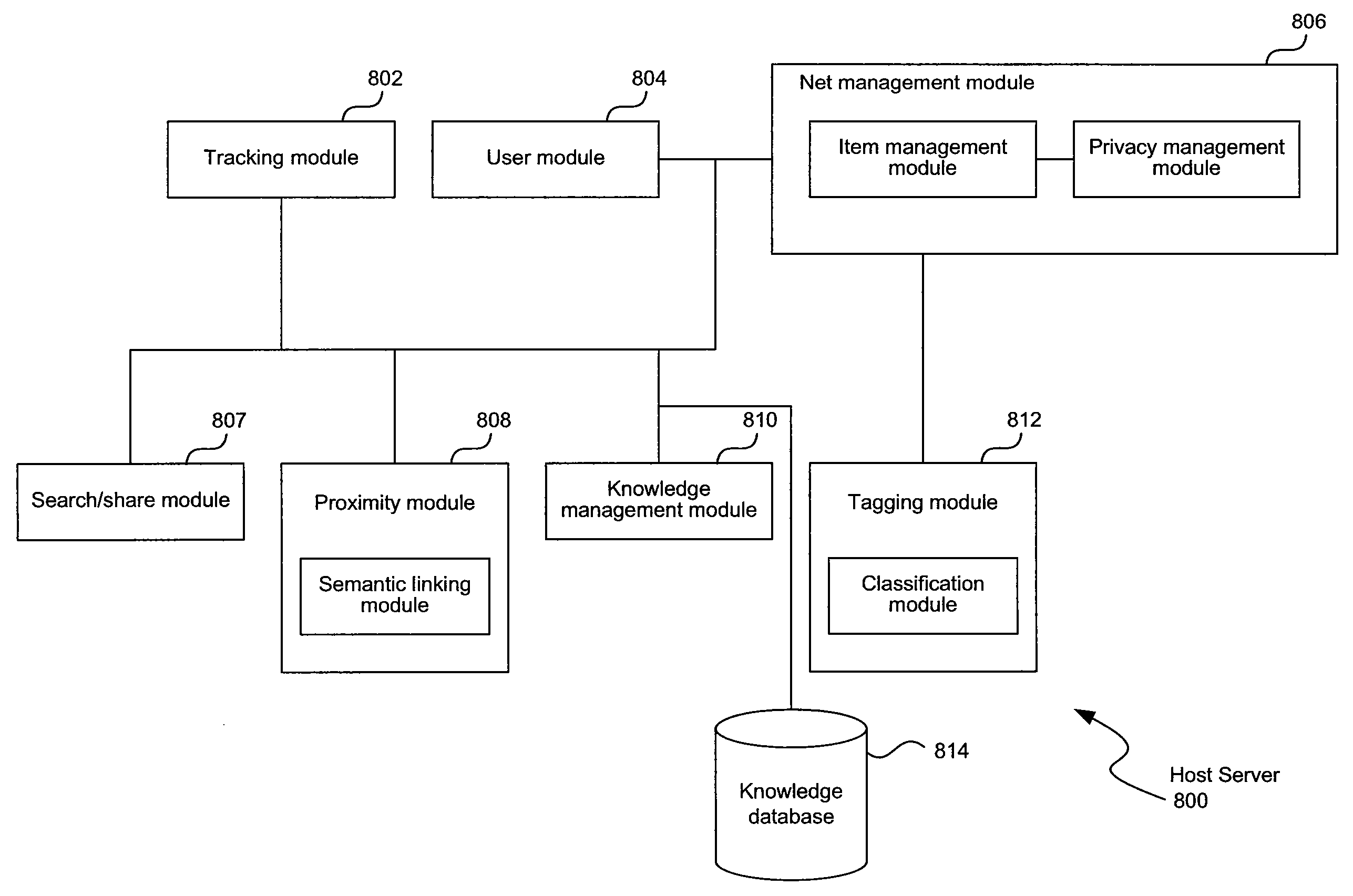
System and Method of a Knowledge Management and Networking Environment
Systems and methods of a knowledge management networking are disclosed here. In one aspect, embodiments of the present disclosure include a method, which may be implemented on a system, of hosting a web-space having a plurality of objects, the plurality of objects to include one or more of, representations of a set of users, a set of web-items, and a set of nets; wherein a net of the set of nets is a subset of the web-space comprising a sub-plurality of the plurality of objects. One embodiment can include, tracking an explicit relationship between a first set of at least two objects of the set of objects; the explicit relationship to be pre-determined by a user of the set of users, identifying an implicit relationship between a second set of at least two objects of the set of objects; the implicit relationship to be identified based on a semantic relationship between the at least two objects, and determining a default set of privacy rules governing access between the at least two objects based on one or more of the identified explicit relationship and the implicit relationship.
Owner:FIVER LLC
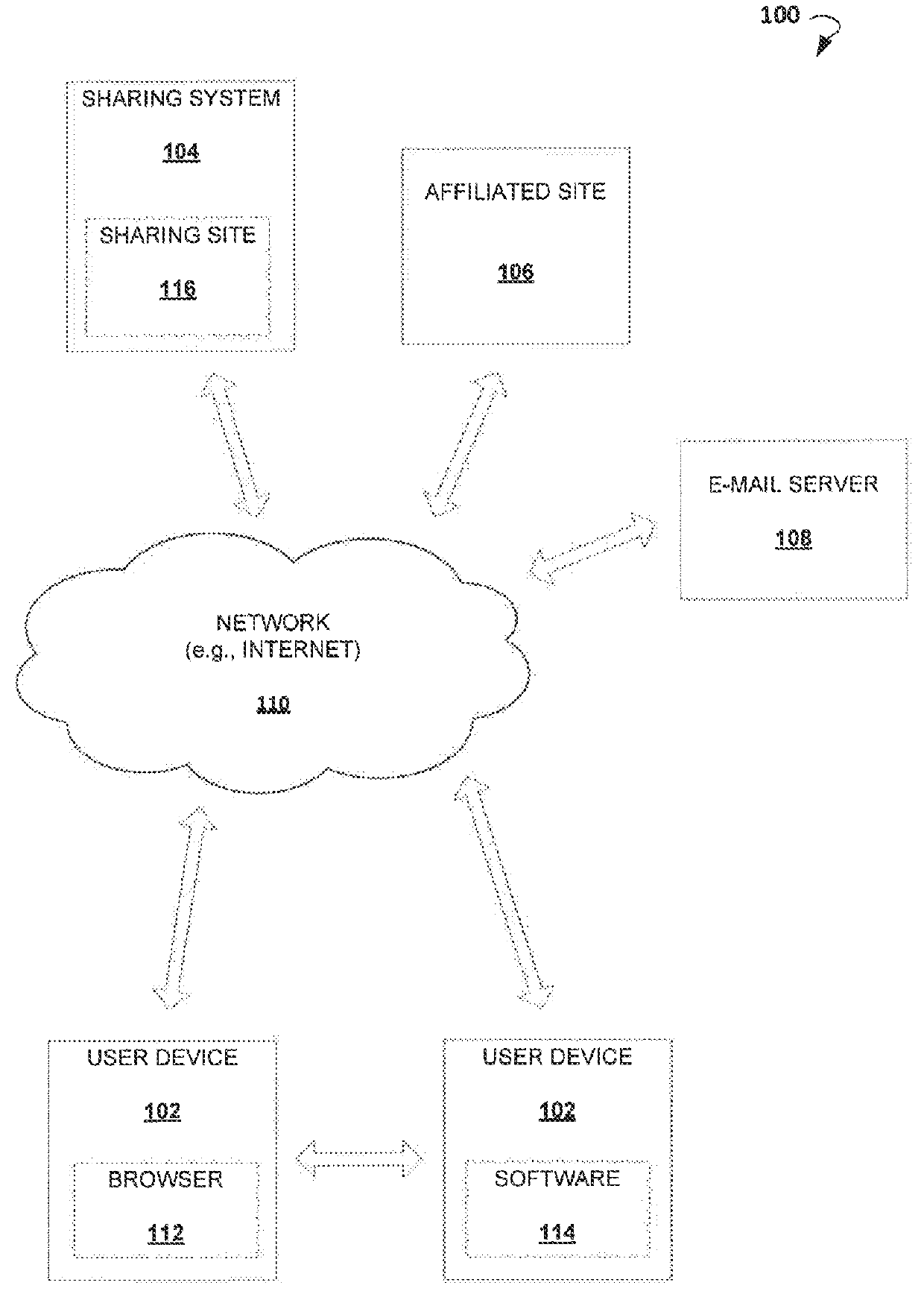
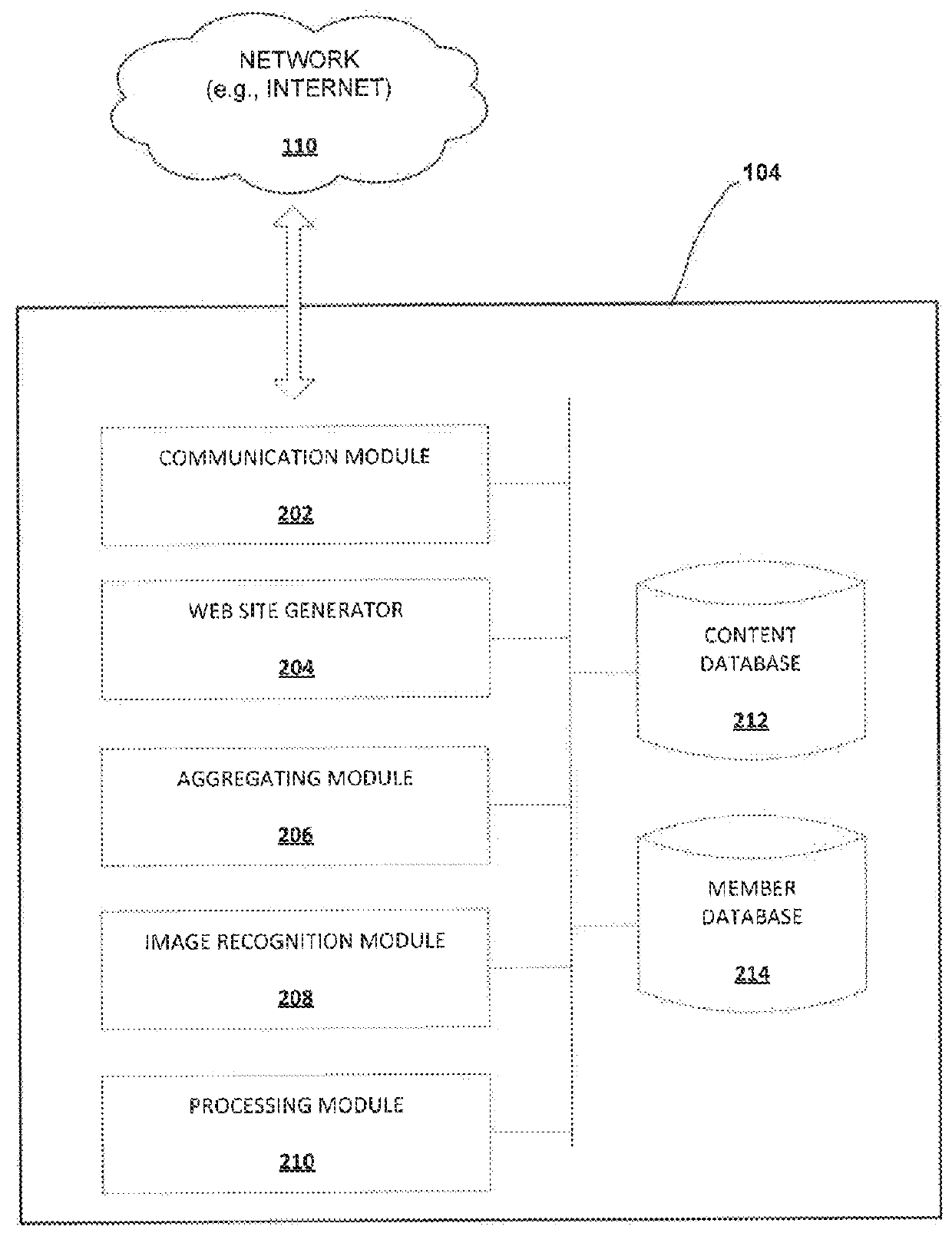
Auto-creating groups for sharing photos
ActiveUS20130013683A1Easy accessData processing applicationsMetadata multimedia retrievalDigital contentPrivacy rule
Methods and systems for aggregating and sharing digital content associated with social events via a network are provided. In one example embodiment, a system for aggregating and sharing digital content associated with social events via a network facilitates the aggregation and sharing of digital content, such as photos and videos. The aggregation may be performed with respect to the digital content received from different sources associated with the same social event. The digital content may also be subjected to an image recognition process to identify one or more individuals appearing in the photos or videos. The shared content may also be filtered to display only those photos or videos with specific individuals. In addition, users may be allowed to set privacy rules with respect to the photos and videos within which they appear.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Systems and methods for managing multifaceted data incidents
ActiveUS10331904B2Digital data protectionPlatform integrity maintainancePrivacy ruleInternet privacy
Systems and methods for managing a multifaceted data incident are provided herein. Example methods include receiving, via a risk assessment server, in response to an occurrence of the data incident, data incident data that including information corresponding to the data incident, wherein the data incident has a plurality of facets with each facet having any of unique and overlapping set of privacy data and media type and associated risk factors requiring facet specific incident risk assessment, automatically generating, via the risk assessment server, a risk assessment and decision-support guidance whether the facet is reportable, from a comparison of the facet to privacy rules, the privacy rules define requirements associated with data incident notification obligations, and providing, via the risk assessment server, the risk assessment to a display device that selectively couples with the risk assessment server.
Owner:RADAR LLC
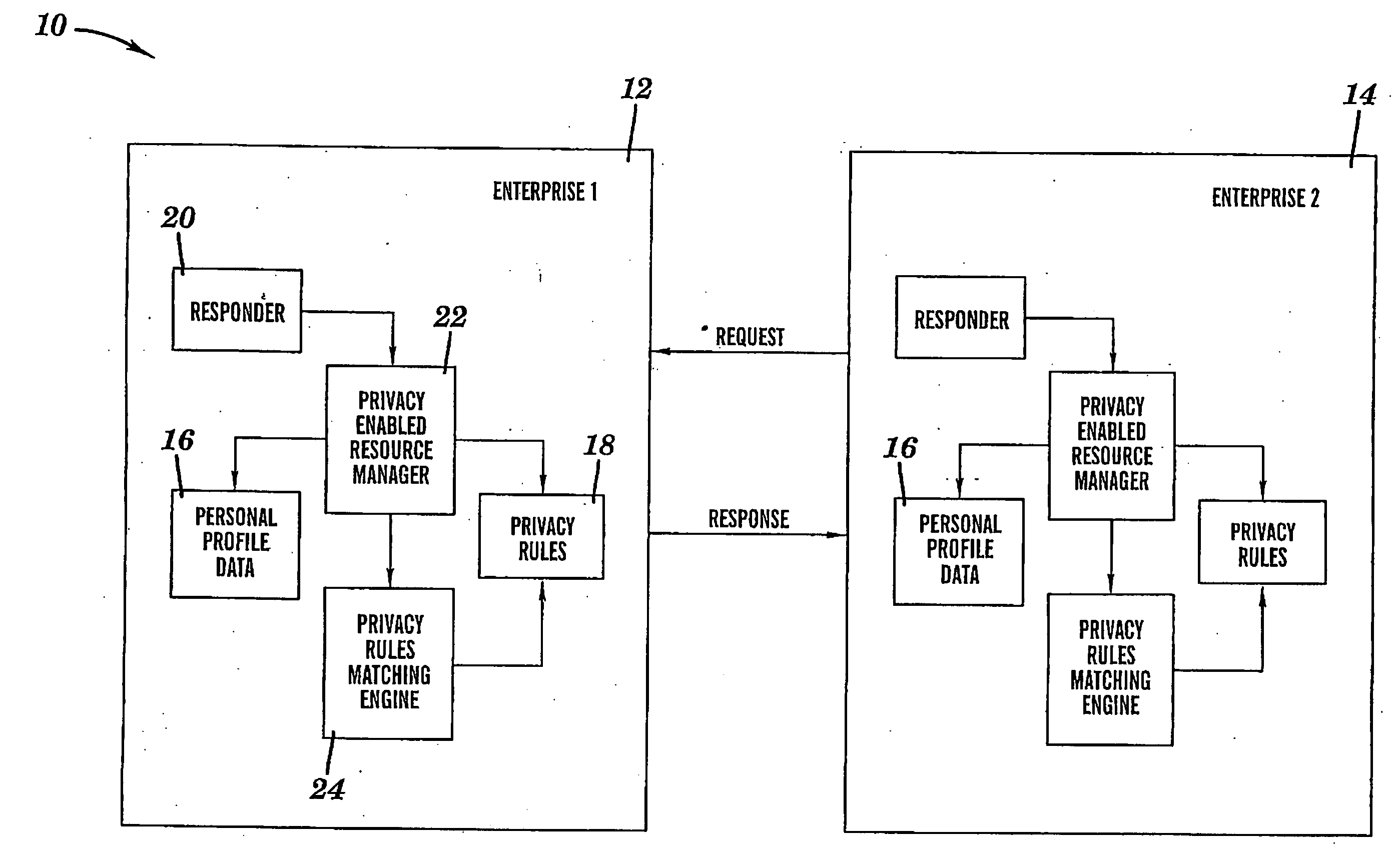
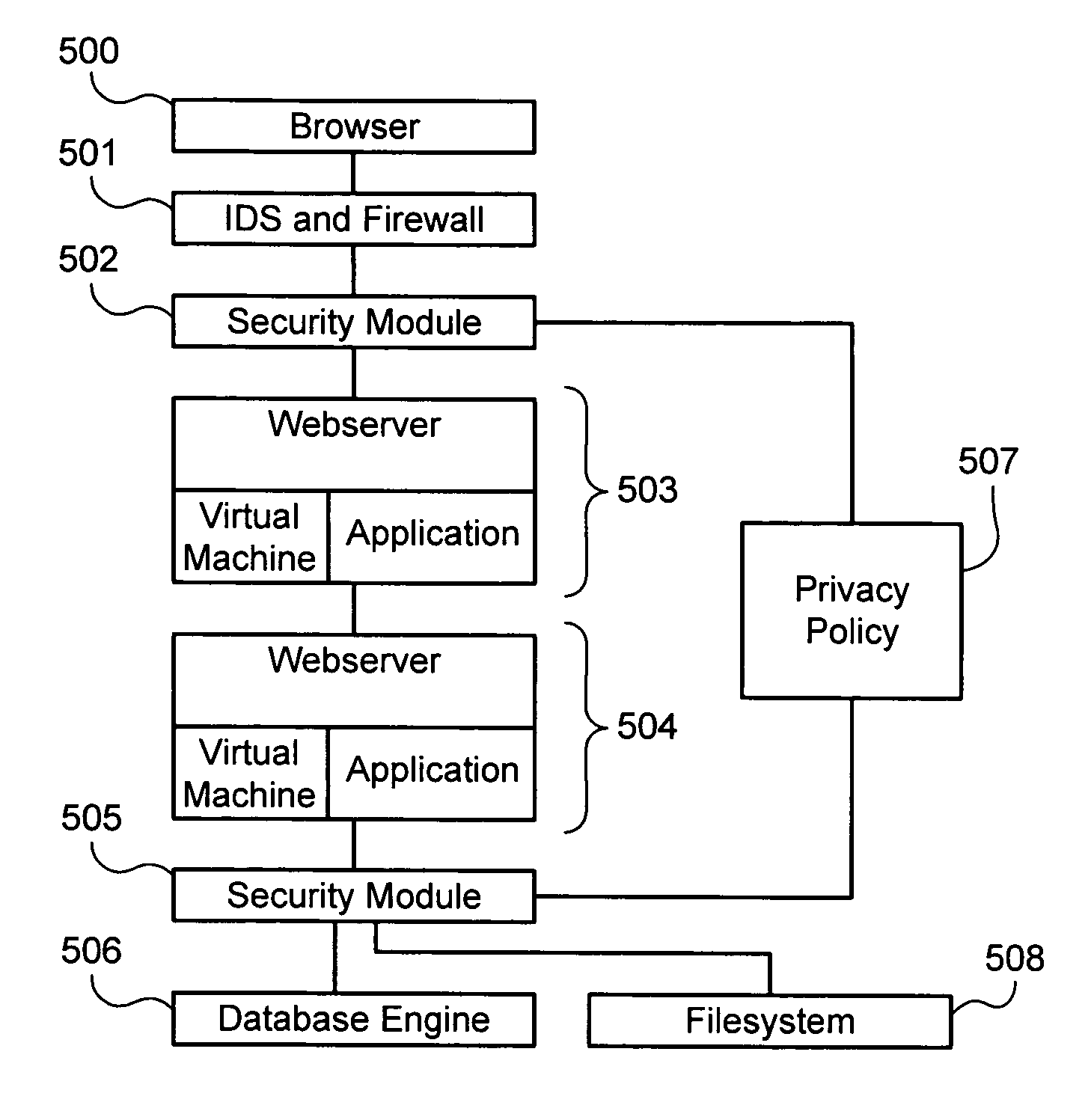
Secure system and method for enforcement of privacy policy and protection of confidentiality
ActiveUS7353532B2Effective protectionFinanceDigital data processing detailsThird partyTamper resistance
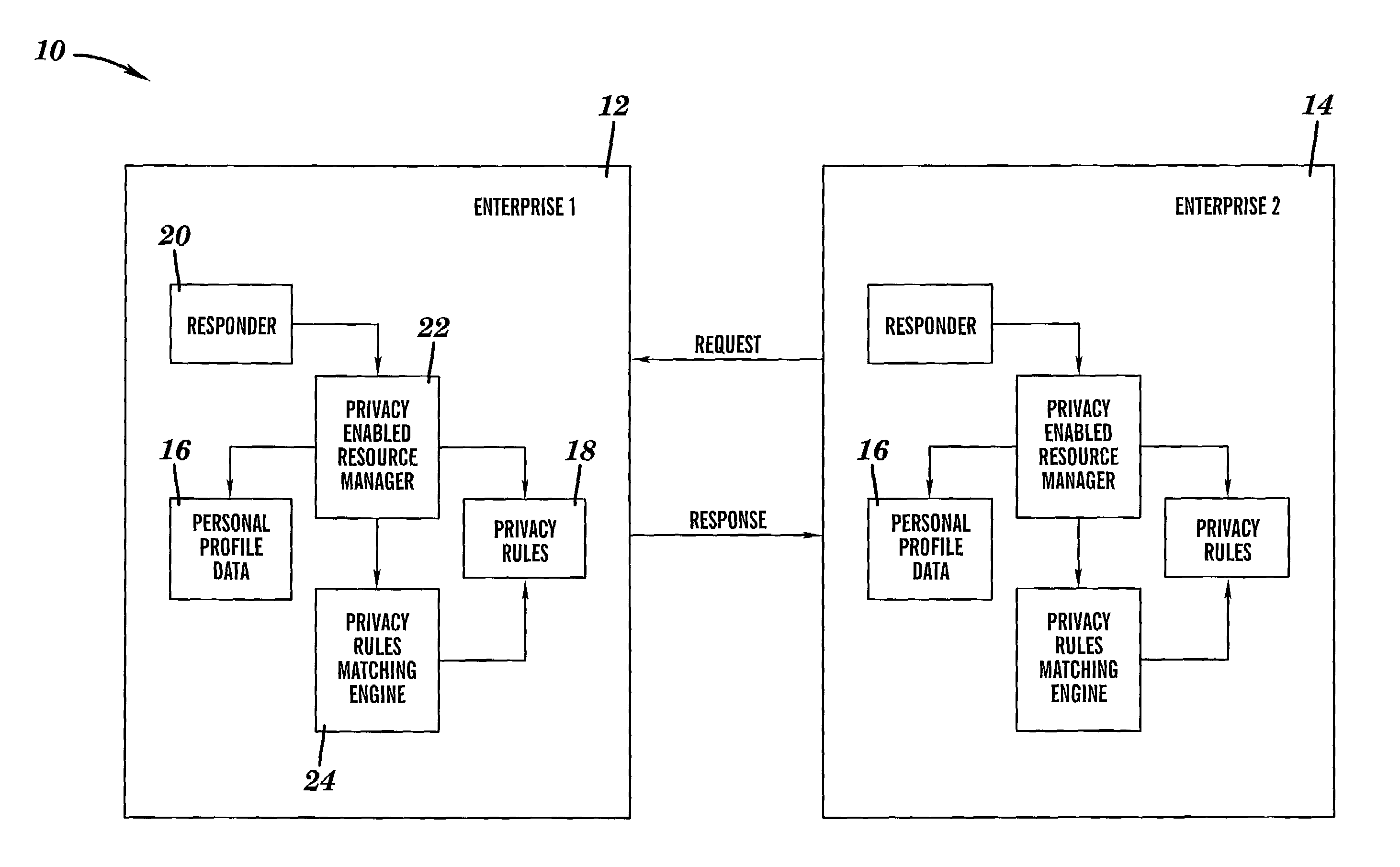
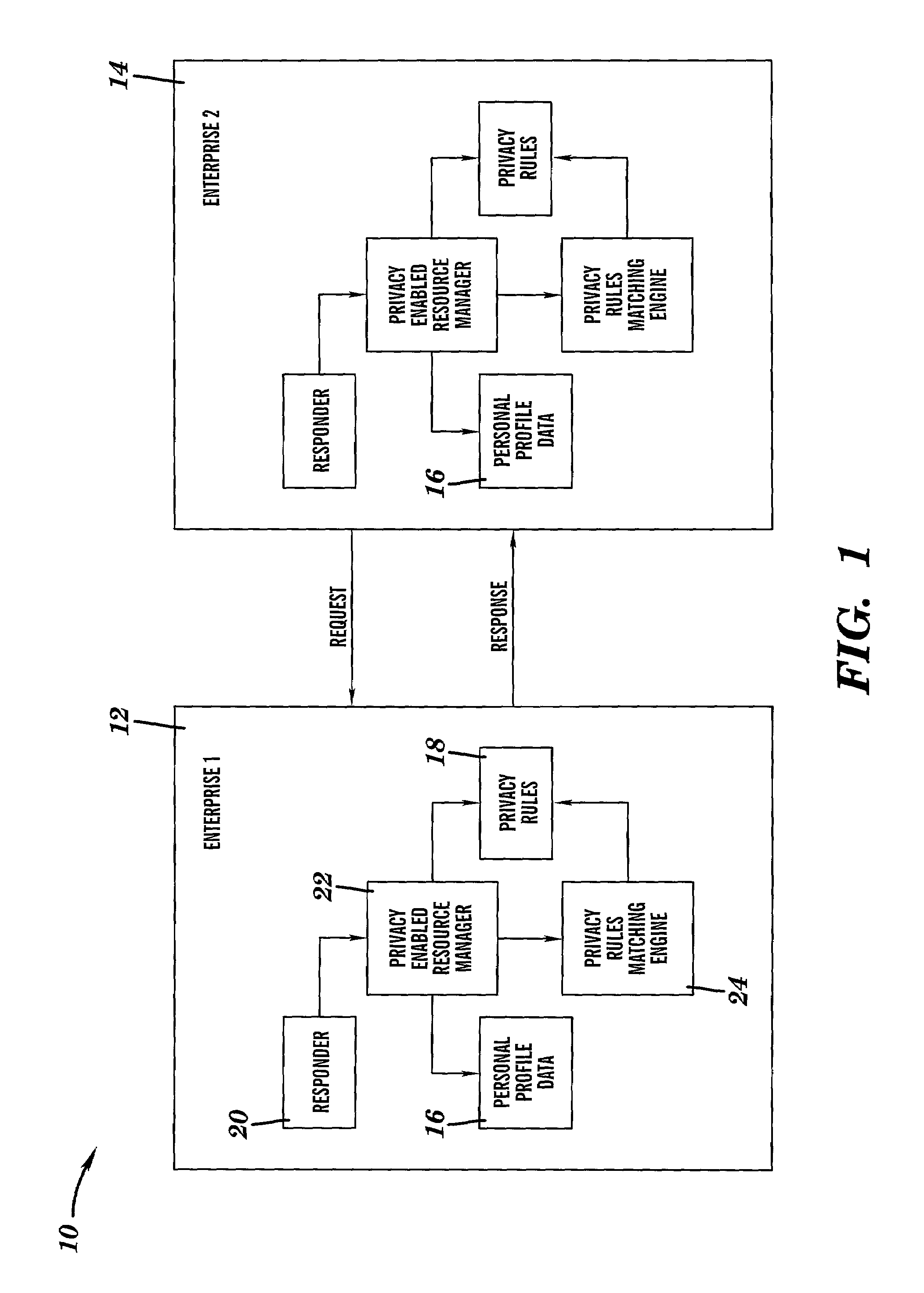
The invention includes various systems, architectures, frameworks and methodologies that can securely enforce a privacy policy. A method is include for securely guaranteeing a privacy policy between two enterprises, comprising: creating a message at a first enterprise, wherein the message includes a request for data concerning a third party and a privacy policy of the first enterprise; signing and certifying the message that the first enterprise has a tamper-proof system with a privacy rules engine and that the privacy policy of the first entity will be enforced by the privacy rules engine of the first enterprise; sending the message to a second enterprise; and running a privacy rules engine at the second enterprise to compare the privacy policy of the first enterprise with a set of privacy rules for the third party.
Owner:GOOGLE LLC
Secure system and method for enforcement of privacy policy and protection of confidentiality
ActiveUS20080307491A1Digital data processing detailsUser identity/authority verificationThird partyTamper resistance
The invention includes various systems, architectures, frameworks and methodologies that can securely enforce a privacy policy. A method is included for securely guaranteeing a privacy policy between two enterprises, comprising: creating a message at a first enterprise, wherein the message includes a request for data concerning a third party and a privacy policy of the first enterprise; signing and certifying the message that the first enterprise has a tamper-proof system with a privacy rules engine and that the privacy policy of the first entity will be enforced by the privacy rules engine of the first enterprise; sending the message to a second enterprise; and running a privacy rules engine at the second enterprise to compare the privacy policy of the first enterprise with a set of privacy rules for the third party.
Owner:SLINGSHOT IOT LLC
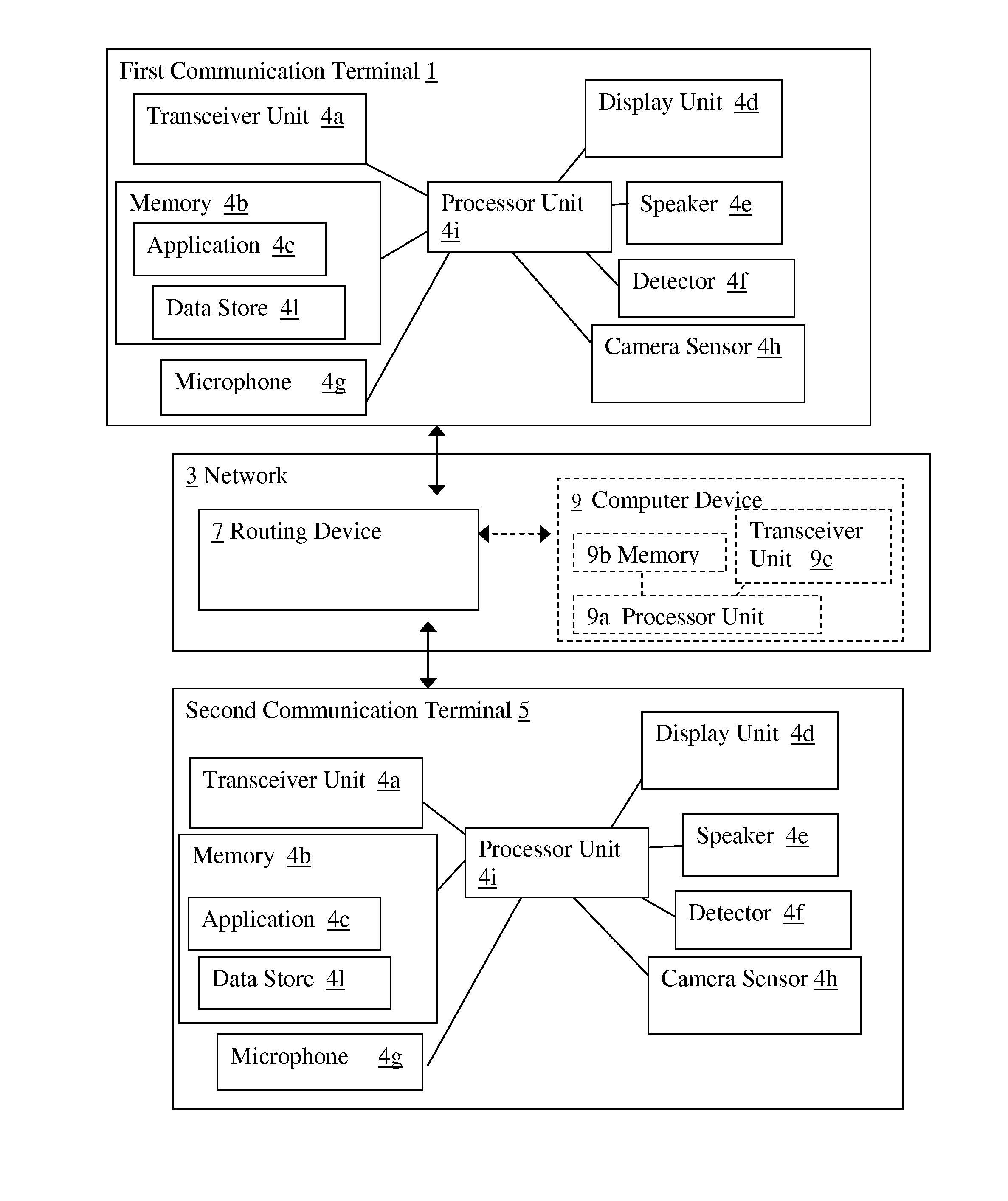
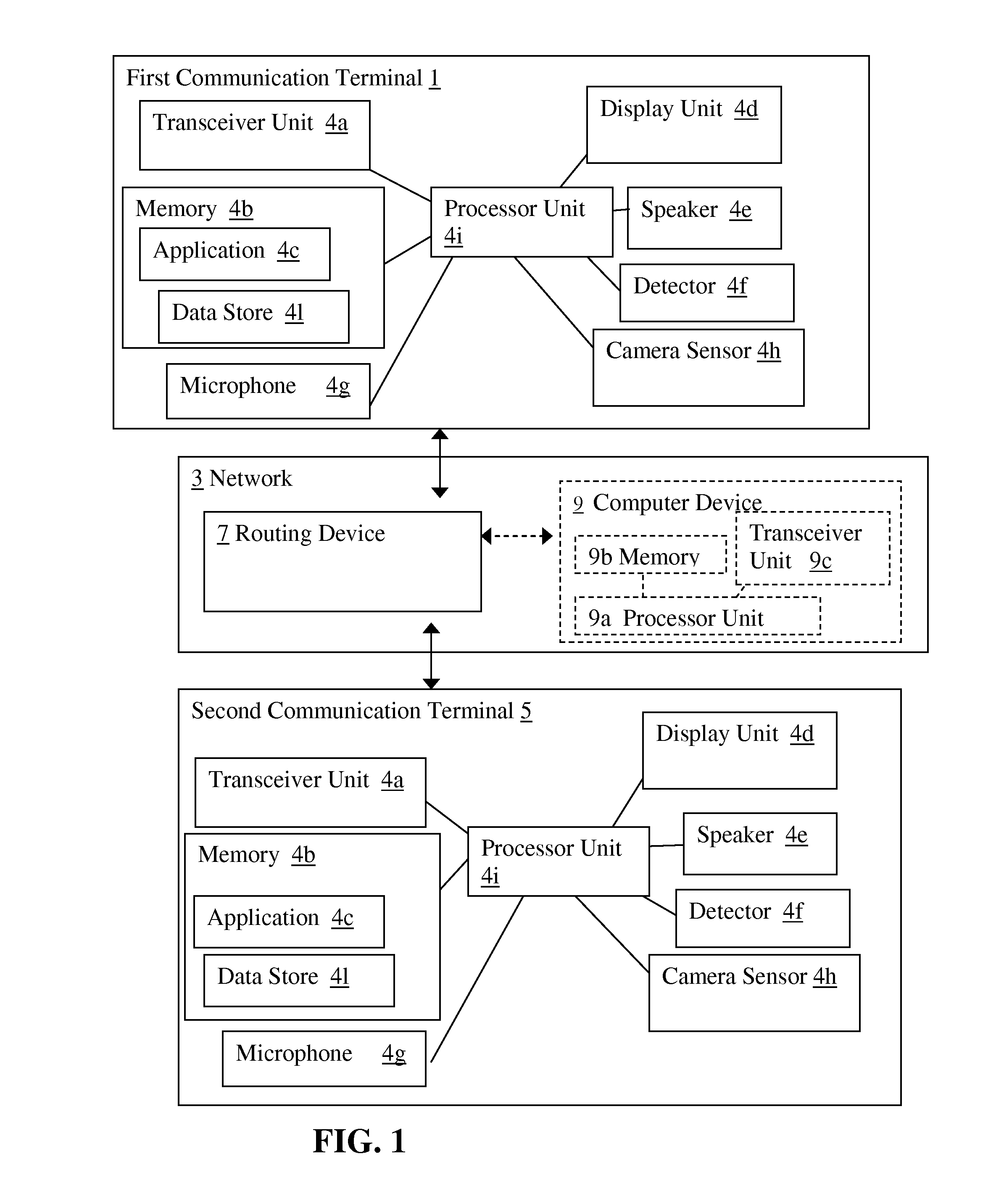
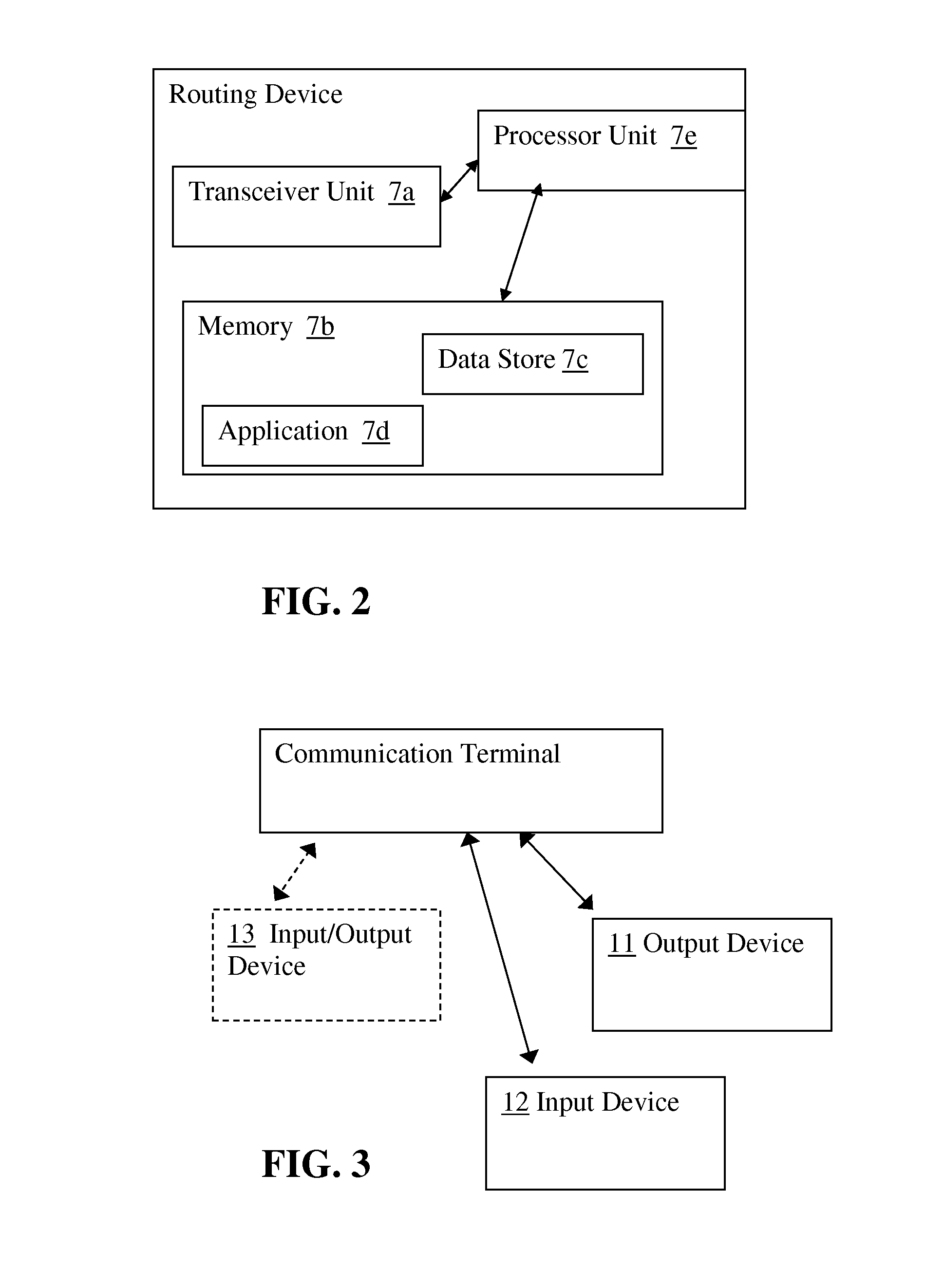
Method, Device, and System for Providing Privacy for Communications
ActiveUS20160261532A1Suppress functionUnauthorised/fraudulent call preventionData switching networksCommunications systemInternet privacy
A communication system, method and communication terminal are configured to facilitate private outputting of content of a message or communication session. A communication terminal can be configured via data included in a message or via a privacy setting to output content of data from a communication session or message in accordance with a pre-selected privacy setting or one or more privacy rules. For instance, a communication terminal may be configured to suppress a text to speech function for certain text messages, email messages, instant messages, or social networking messages that it receives having the privacy parameter set therein. As another example, a user may set the privacy parameter in his or her terminal so that any such message received by that terminal is output in accordance with the privacy setting or rules. A detection of nearby people can affect how certain content may be output via a terminal.
Owner:RINGCENTRAL INC
System and method of a knowledge management and networking environment
Systems and methods of a knowledge management networking are disclosed here. In one aspect, embodiments of the present disclosure include a method, which may be implemented on a system, of hosting a web-space having a plurality of objects, the plurality of objects to include one or more of, representations of a set of users, a set of web-items, and a set of nets; wherein a net of the set of nets is a subset of the web-space comprising a sub-plurality of the plurality of objects. One embodiment can include, tracking an explicit relationship between a first set of at least two objects of the set of objects; the explicit relationship to be pre-determined by a user of the set of users, identifying an implicit relationship between a second set of at least two objects of the set of objects; the implicit relationship to be identified based on a semantic relationship between the at least two objects, and determining a default set of privacy rules governing access between the at least two objects based on one or more of the identified explicit relationship and the implicit relationship.
Owner:FIVER LLC
System and method for communication based on an availability of a user
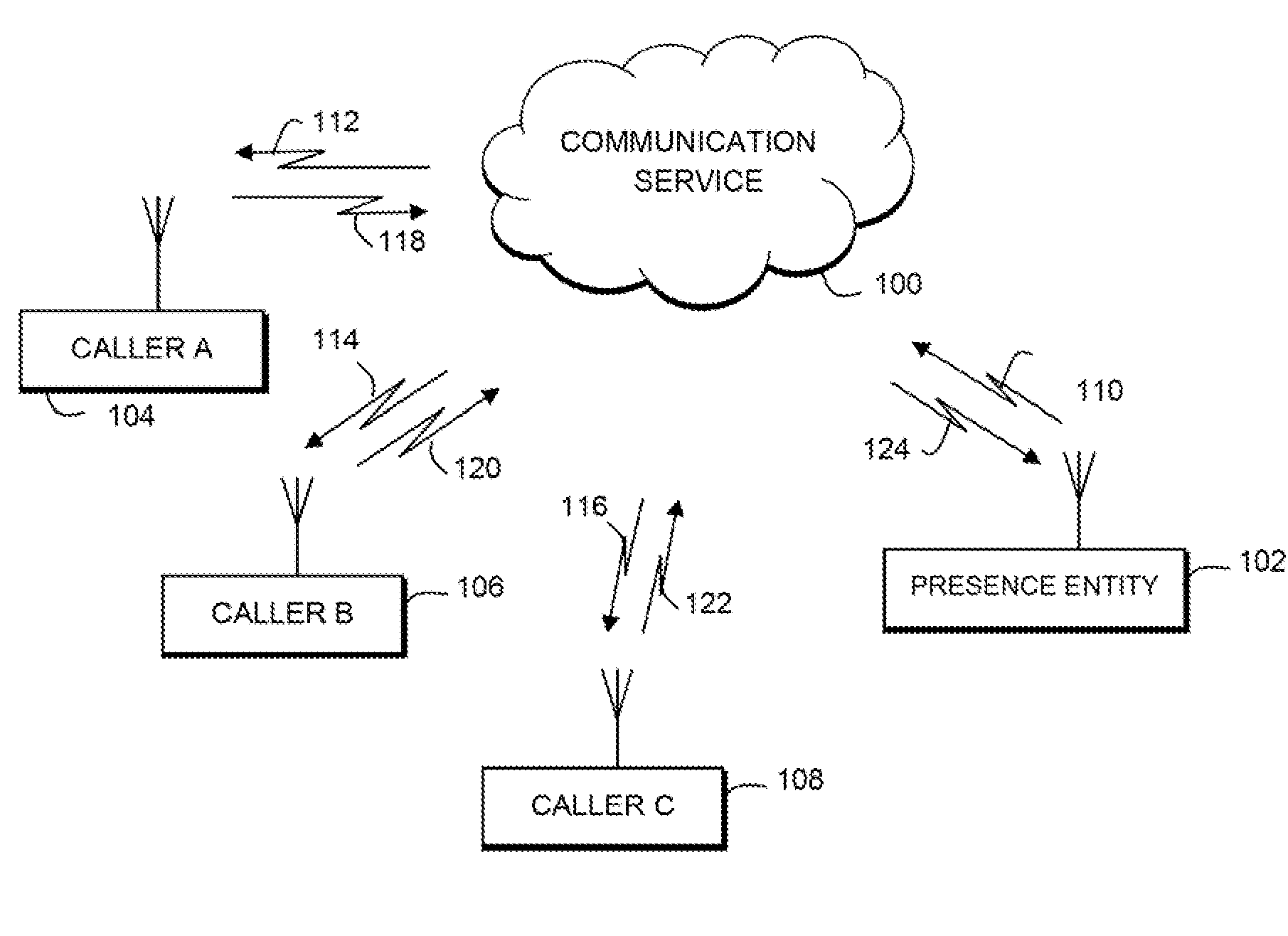
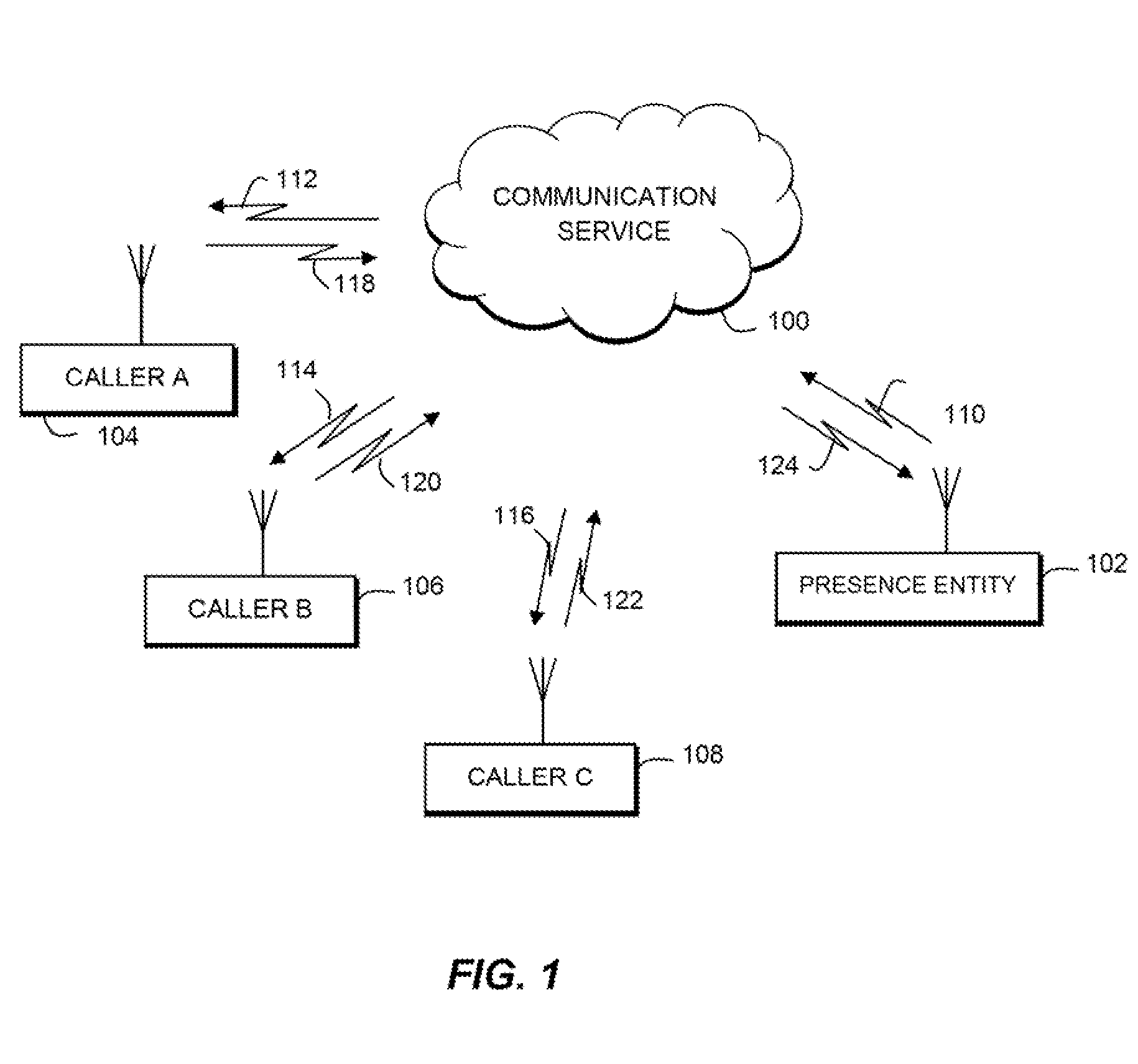
The present invention provides a system and method for communication based on an availability level of a presence entity in a communication network that includes a first step (400) of configuring at least one privacy rule for a communication service, wherein the at least one privacy rule is associated with the presence entity and assigns a potential caller to a prioritized group. A next step (402) includes receiving an indication of availability of the presence entity. A next step (404) includes controlling communication access with the presence entity based on the at least one privacy rule, wherein communication access between the presence entity and the caller is controlled by the priority for that caller and the availability indication of the presence entity.
Owner:MOTOROLA MOBILITY LLC
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS7831995B2Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
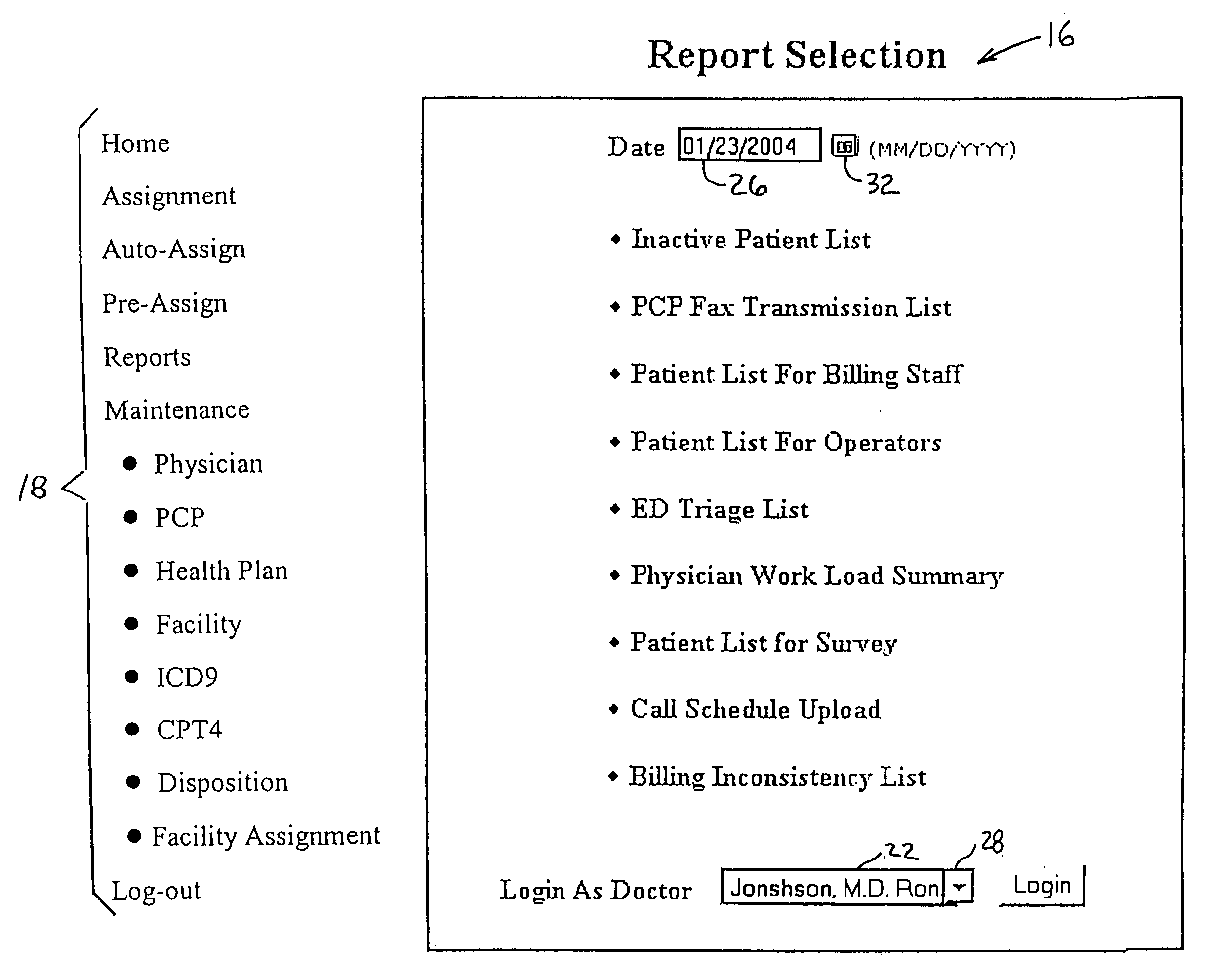
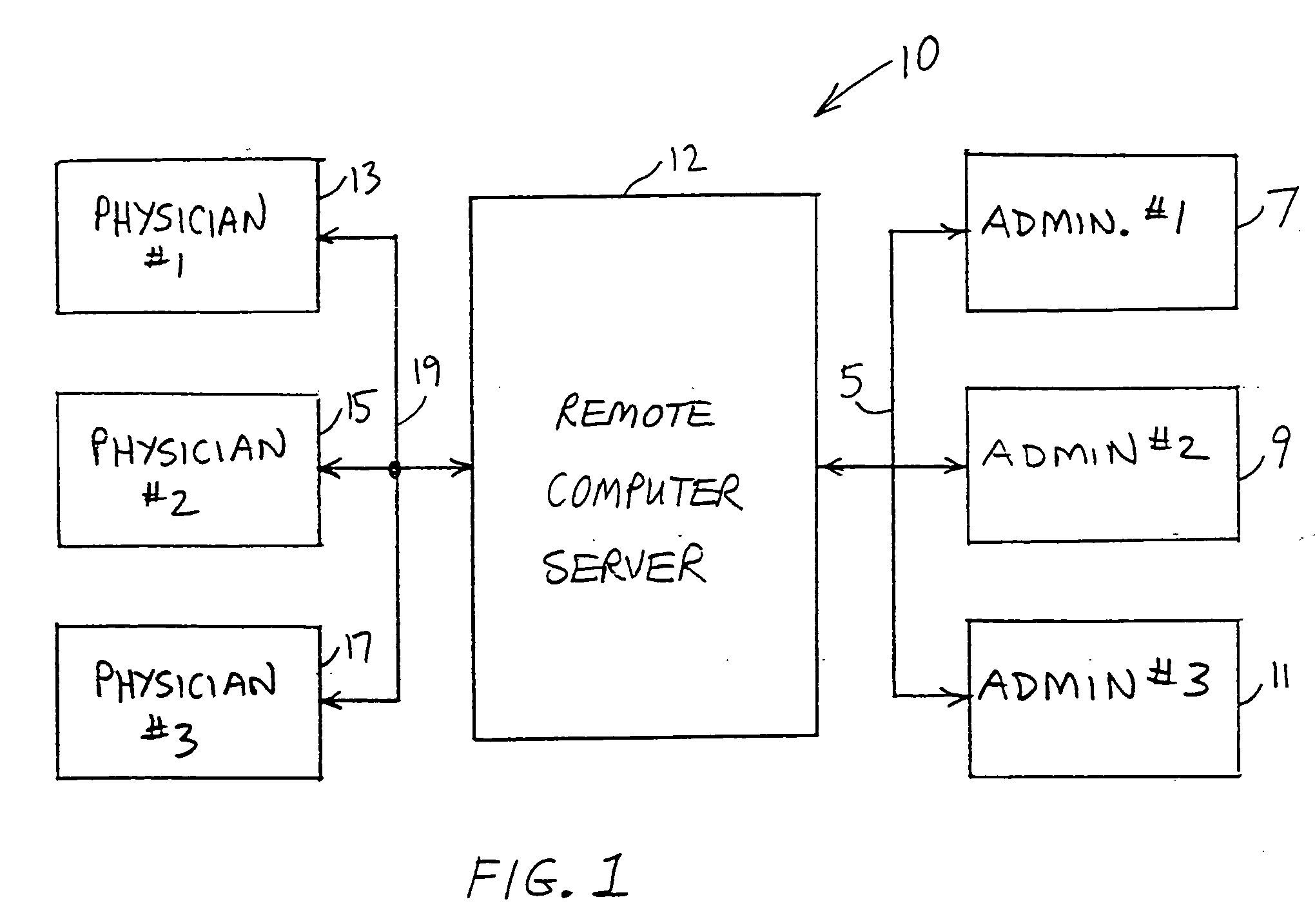
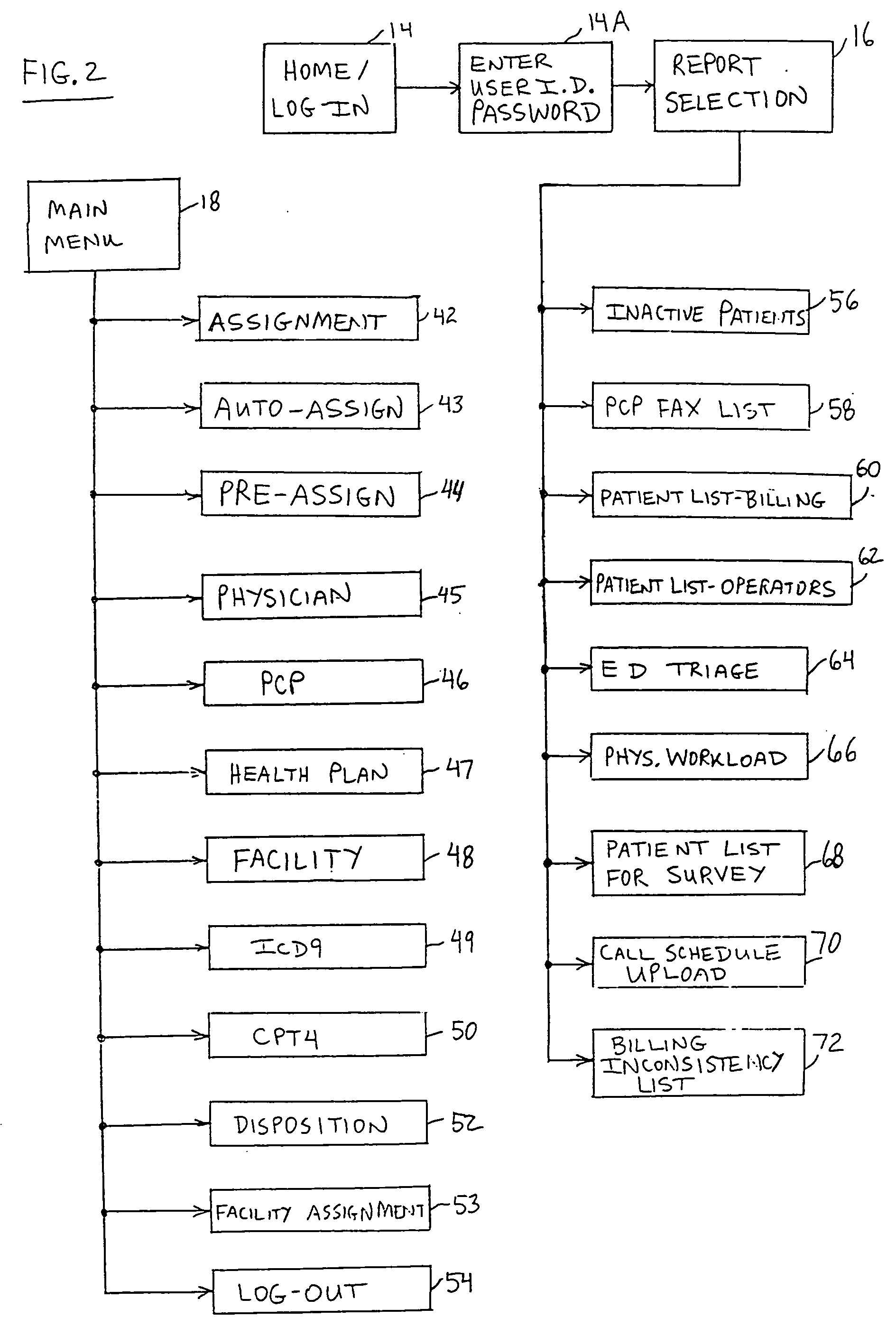
Physicians' remote charge capture system
InactiveUS20050251417A1Facilitates organization and managementReduce laborFinanceOffice automationPatient managementComputer access
A patient management method for hospital-based physicians includes a remote computer server storing certain minimal information regarding patients of one or more physicians. The remote server is linked over a computer network to one or more physician-accessible computers remote from the computer server. Physicians can access such patient information over the network via the physician-accessible computer to view information regarding their patients. Following patient visits, the physician can update patient status information, such as diagnosis, treatment codes, and patient disposition, by entering such information into the server over the network. An administrator in the physician's office can also access the server over a computer network to capture updated patient status information for purposes of workload distribution and / or billing. The interposition of the server between the physician-accessible computer and the physician's office helps ensure compliance with the federal HIPAA Privacy Rule.
Owner:INDUS INVESTMENTS LTD PARTNERSHIP +1
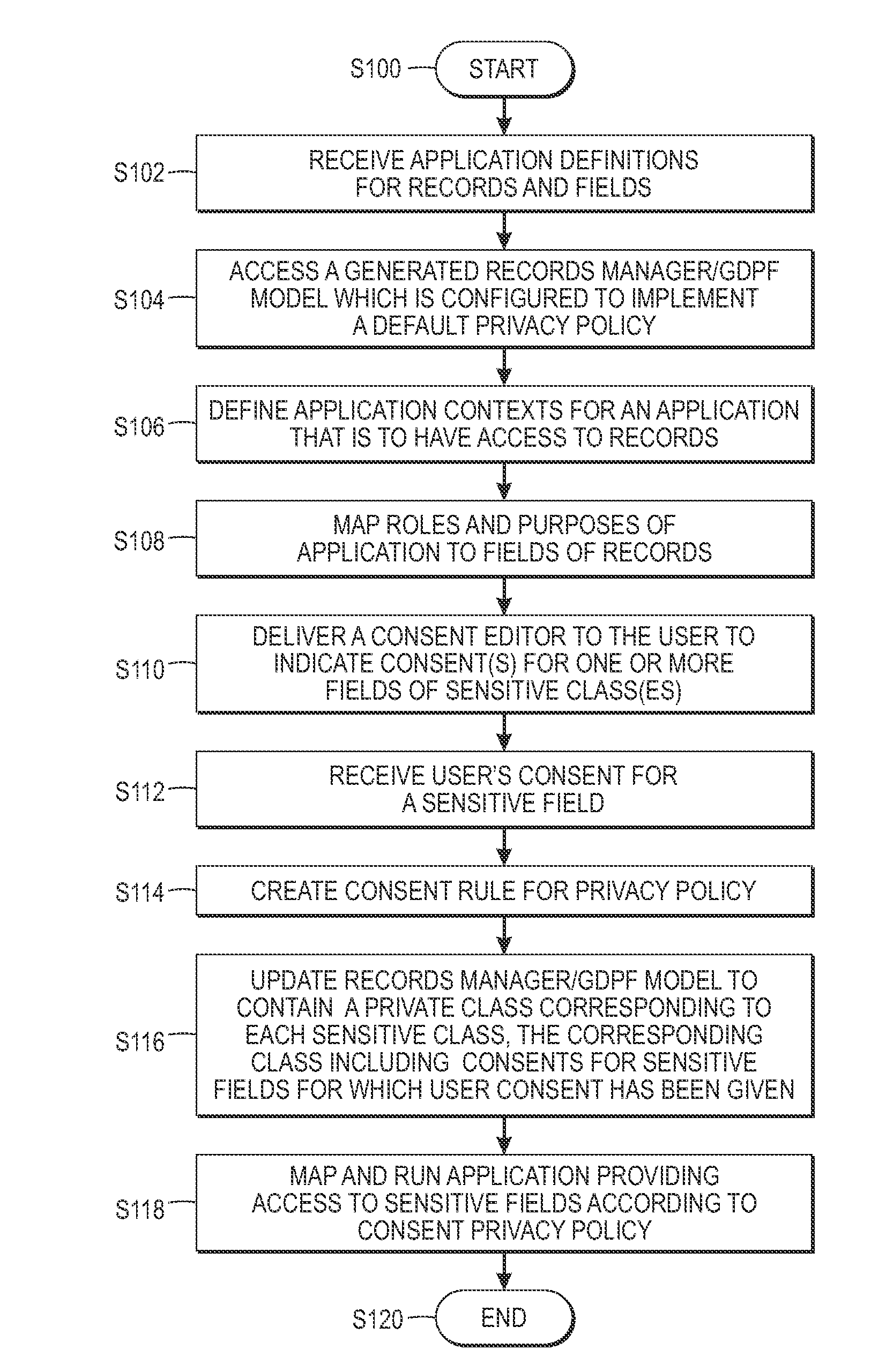
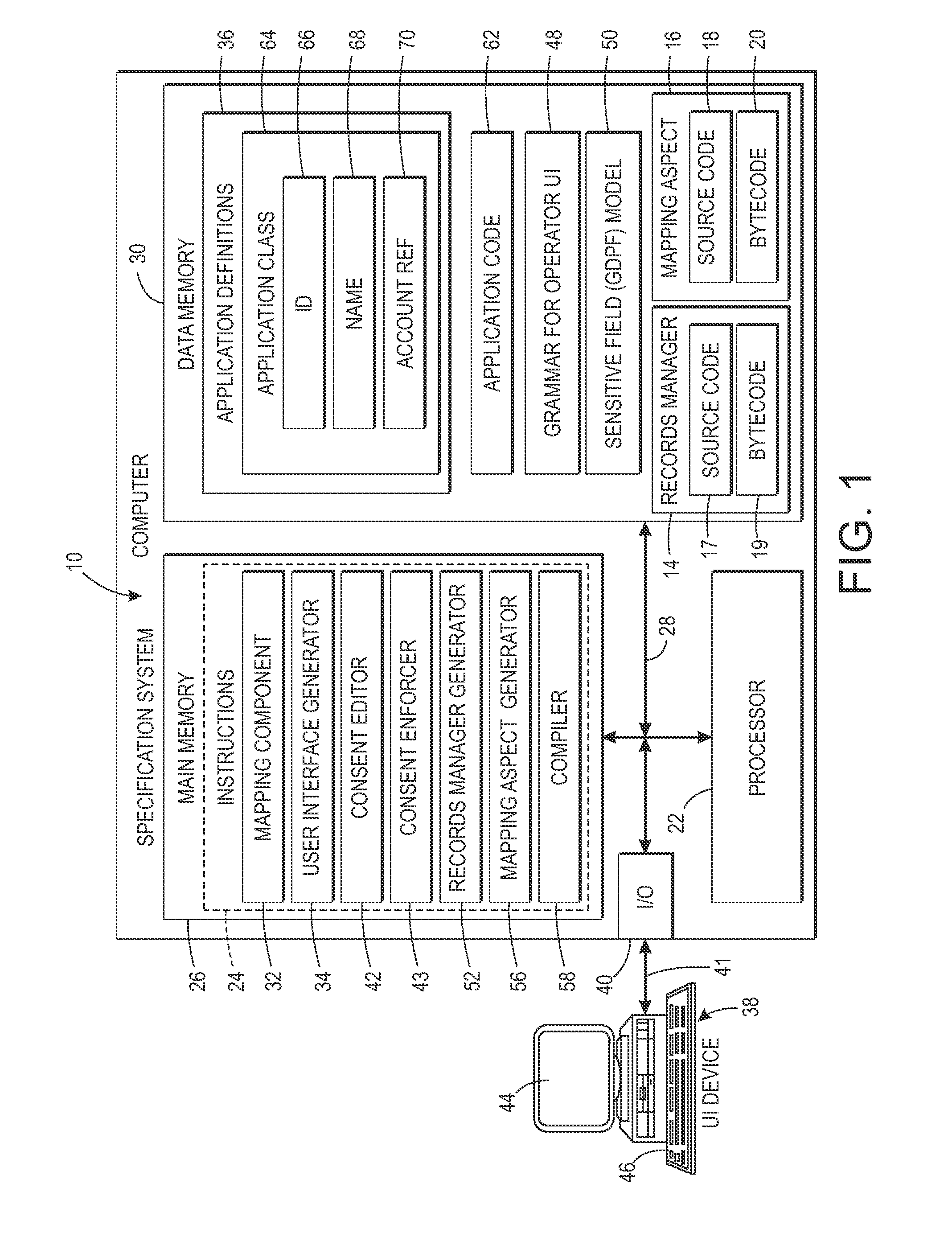
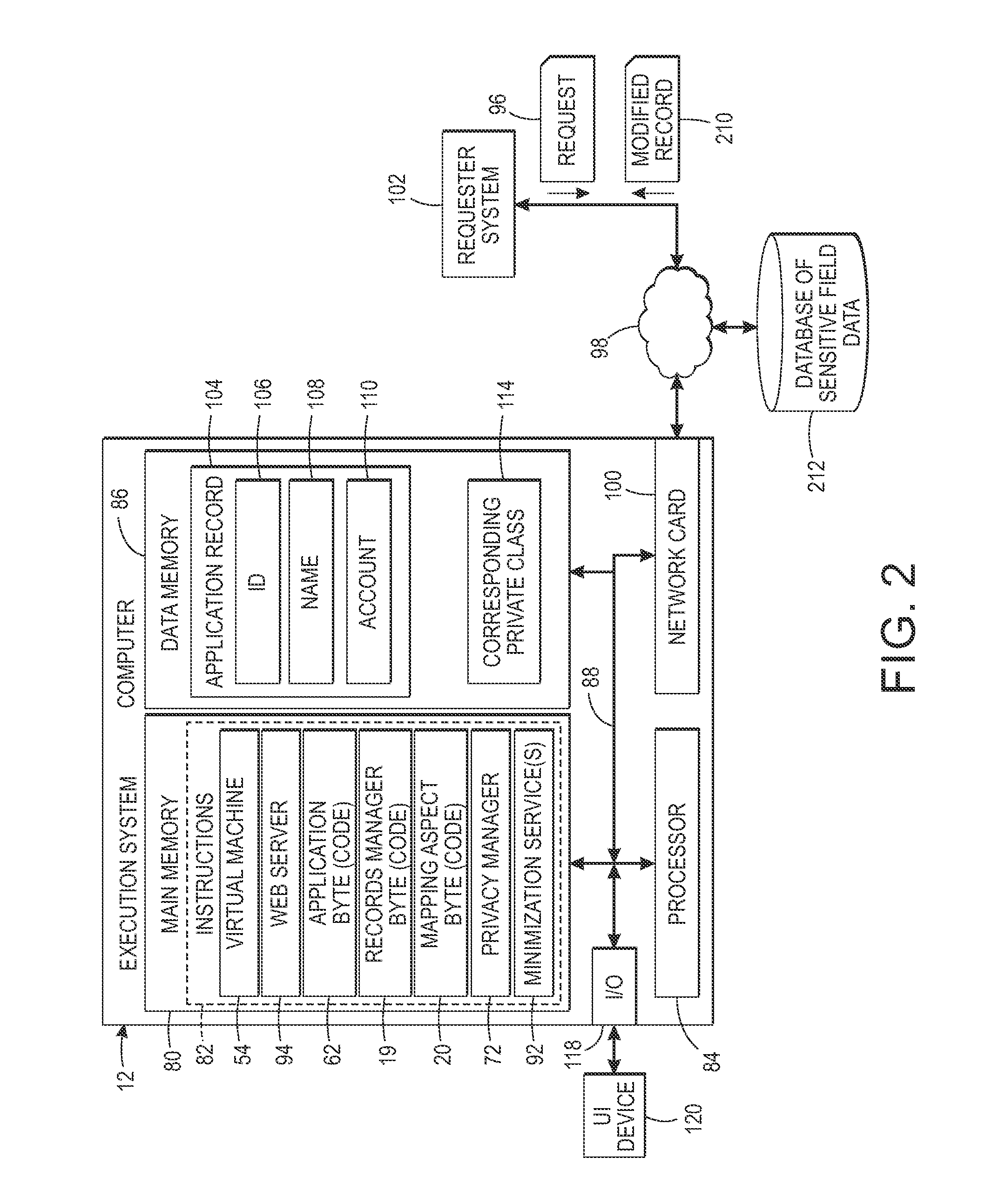
Low-cost specification and enforcement of a privacy-by-consent- policy for online services
ActiveUS20150254456A1Digital data protectionPlatform integrity maintainancePrivacy ruleInternet privacy
A system and method for implementing a privacy policy in an application to be run are provided. Definitions are received for a set of fields. At least one of the fields is designated as sensitive by a default privacy policy. A user is provided with a consent editor whereby the user can consent to relaxing the default privacy policy for at least one of the sensitive fields. A consent privacy rule is generated based on the received consent. A mapping aspect is provided which identifies joins at which code of the application is to be augmented by calling a minimization service to apply the default privacy policy by generating a minimized value of data in each of the designated sensitive fields used by the application unless there is a generated consent privacy rule which authorizes relaxation of the default privacy policy for the user's data in a respective sensitive field.
Owner:XEROX CORP
Method of controlling sharing of participant identity in a group communication session
A system and methods for increasing the granularity of privacy control in a group communication session are presented. A privacy rule is established for a participant in the session. The privacy rule specifies for different identity sharing triggers whether the participant identity is to be shared with other participants in the session. The privacy of the participant is able to be different dependent on the particular identity sharing trigger. The privacy rule is set by participant initiating the session, a separate server, or the participant. In the last case, the participant is able to specify privacy for a media or data stream when requesting the floor to transmit the stream. The identity of the participant is automatically modified dependent on session context information.
Owner:MOTOROLA SOLUTIONS INC
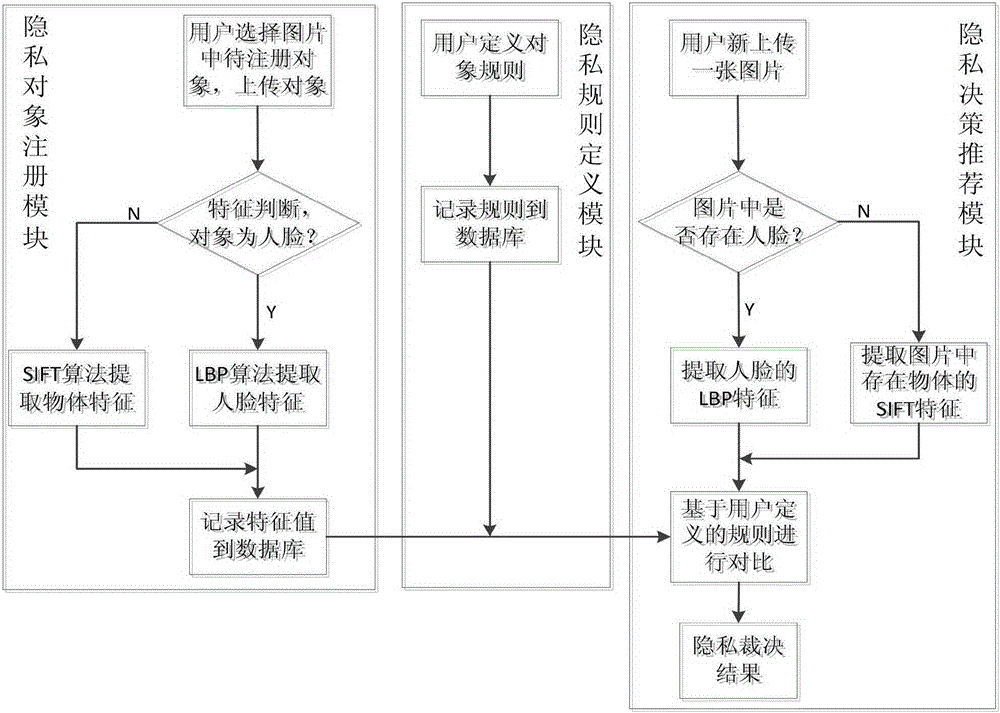
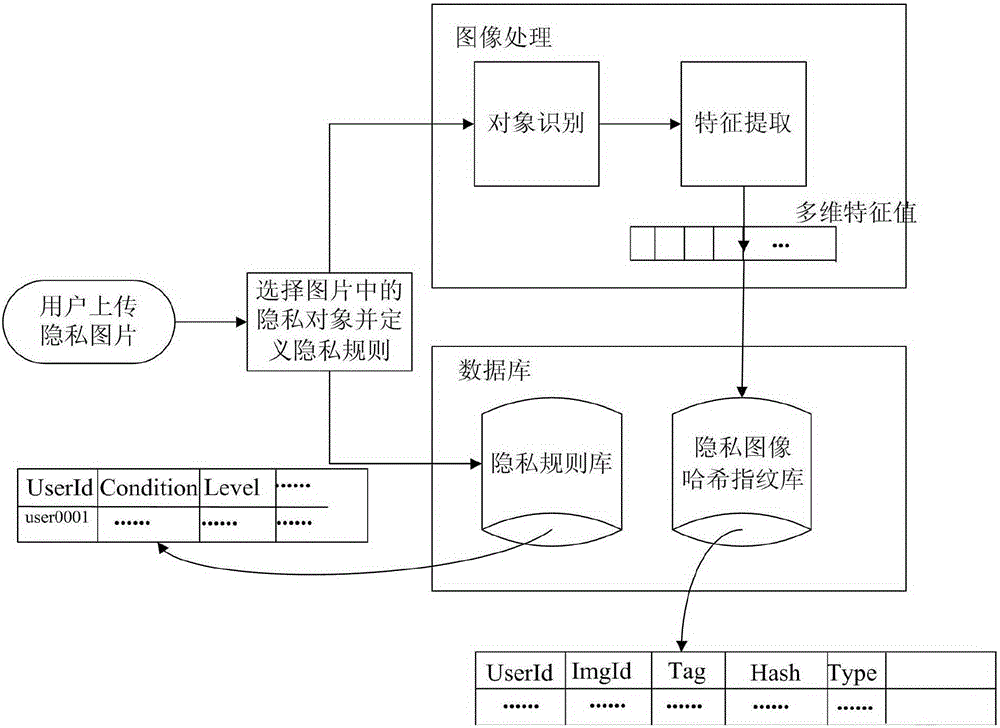
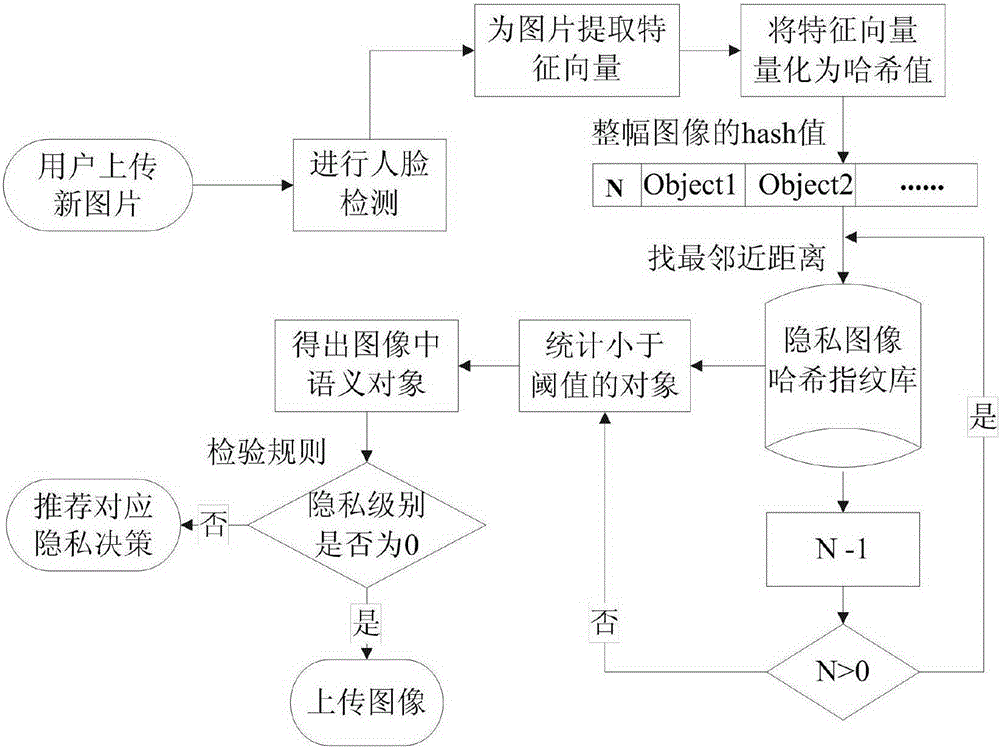
Image privacy decision recommendation system and method under social network on the basis of privacy rule and perceptual Hash
ActiveCN105260676AReduce the risk of privacy breachesSuitable for personalizationData processing applicationsWeb data indexingInternet privacyPrivacy rule
The invention discloses an image privacy decision recommendation system and method under a social network on the basis of a privacy rule and perceptual Hash. The invention is characterized in that the system comprises a privacy object registration module, a privacy rule definition module and a privacy decision recommendation module, wherein the privacy object registration module provides a registration function of an object to be protected for a user; the privacy rule definition module defines a privacy security level for a to-be-protected objet of the user; and the privacy decision recommendation module identifies a to-be-uploaded object of the user, compares the to-be-uploaded object of the user with a protected object in a Hash fingerprint database and a privacy rule in a privacy rule base, and finally submits the privacy security level of the to-be-uploaded object to the privacy decision recommendation module of the user. The quick and convenient automatic calculation of the privacy level and decision recommendation can be realized, and the leakage risks of individuals and the families of the individual can be effectively lowered so as to greatly improve the protection safety of user individual image privacy.
Owner:HEFEI UNIV OF TECH
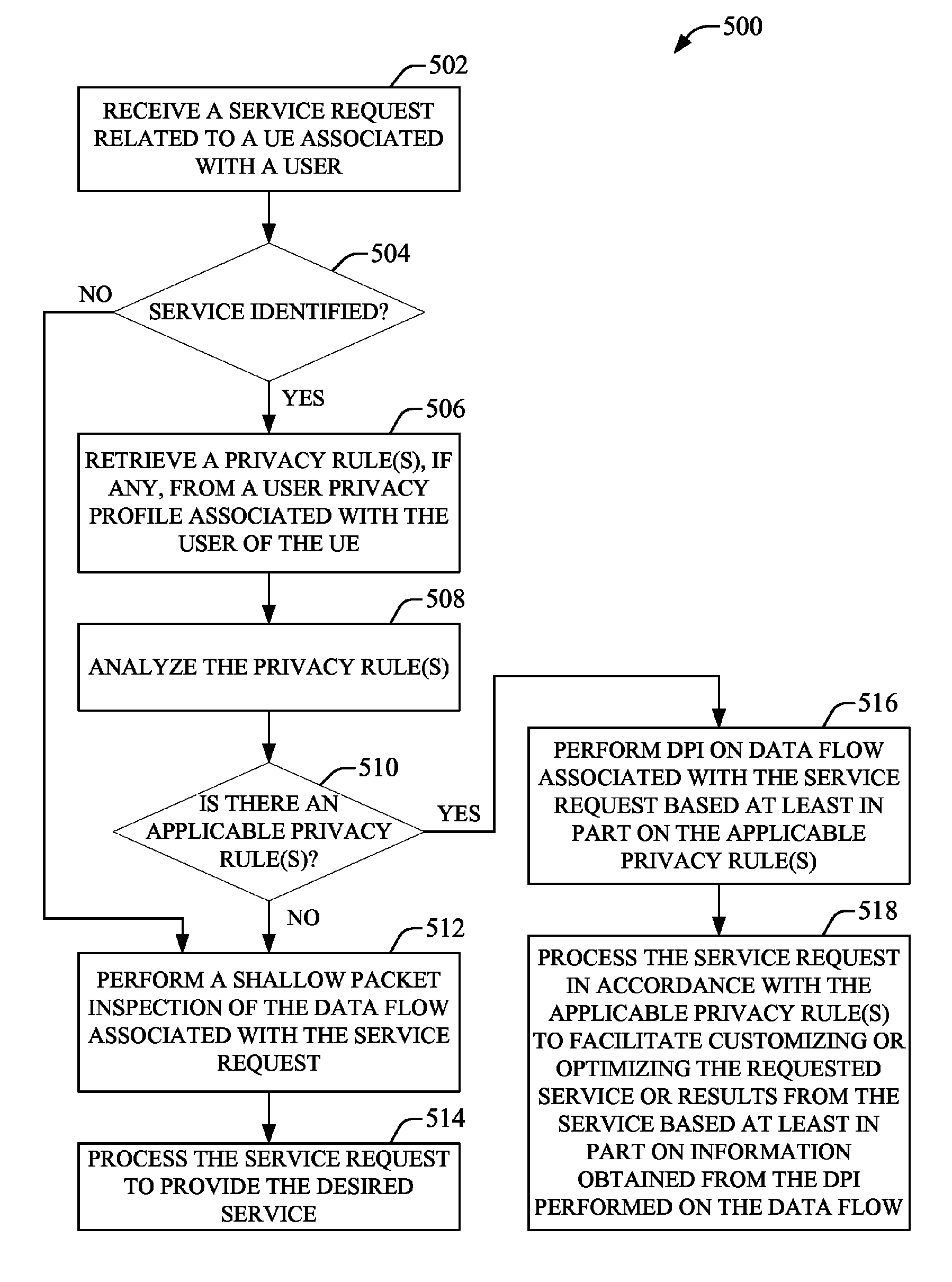
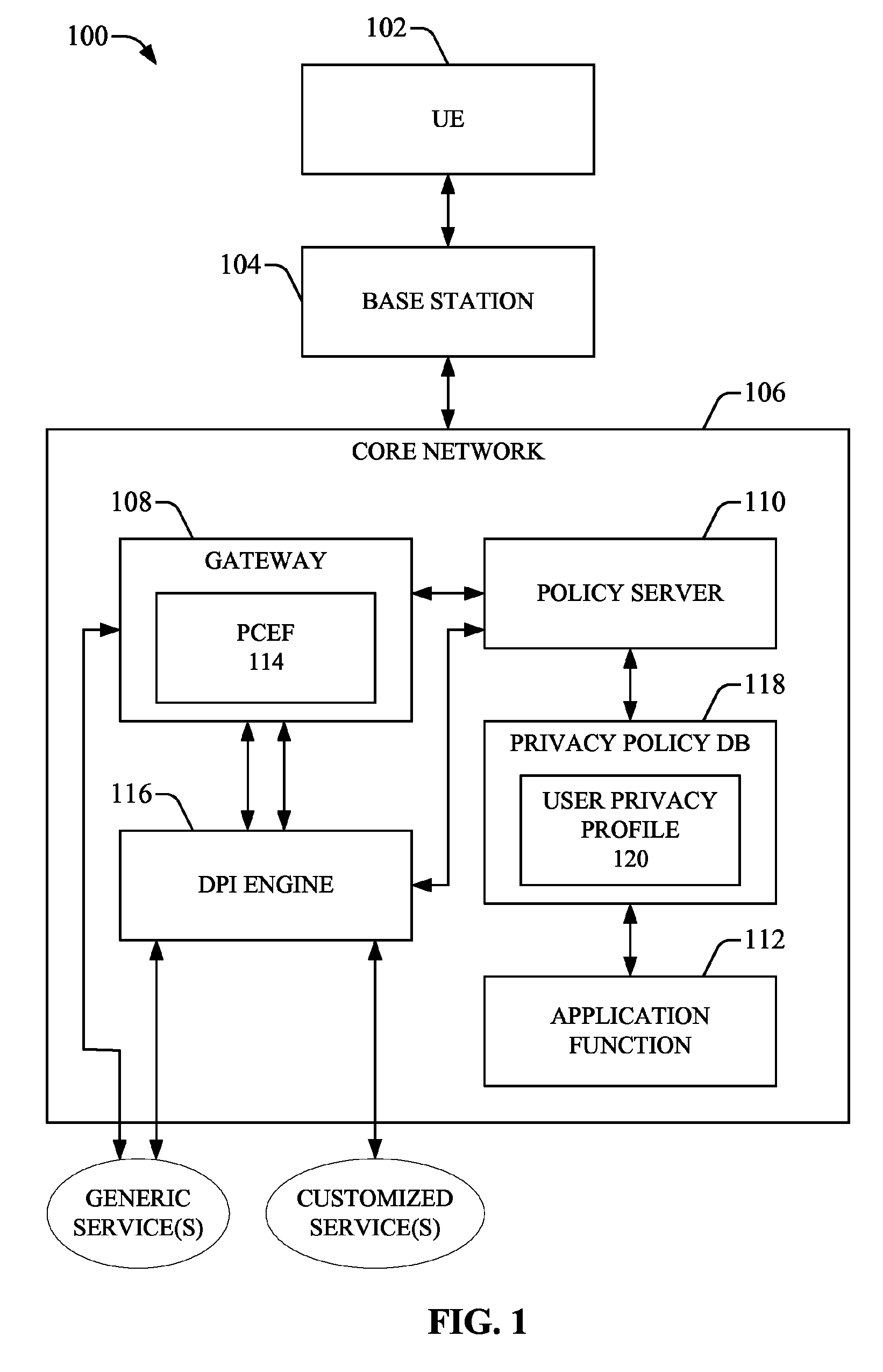
Policy-based privacy protection in converged communication networks
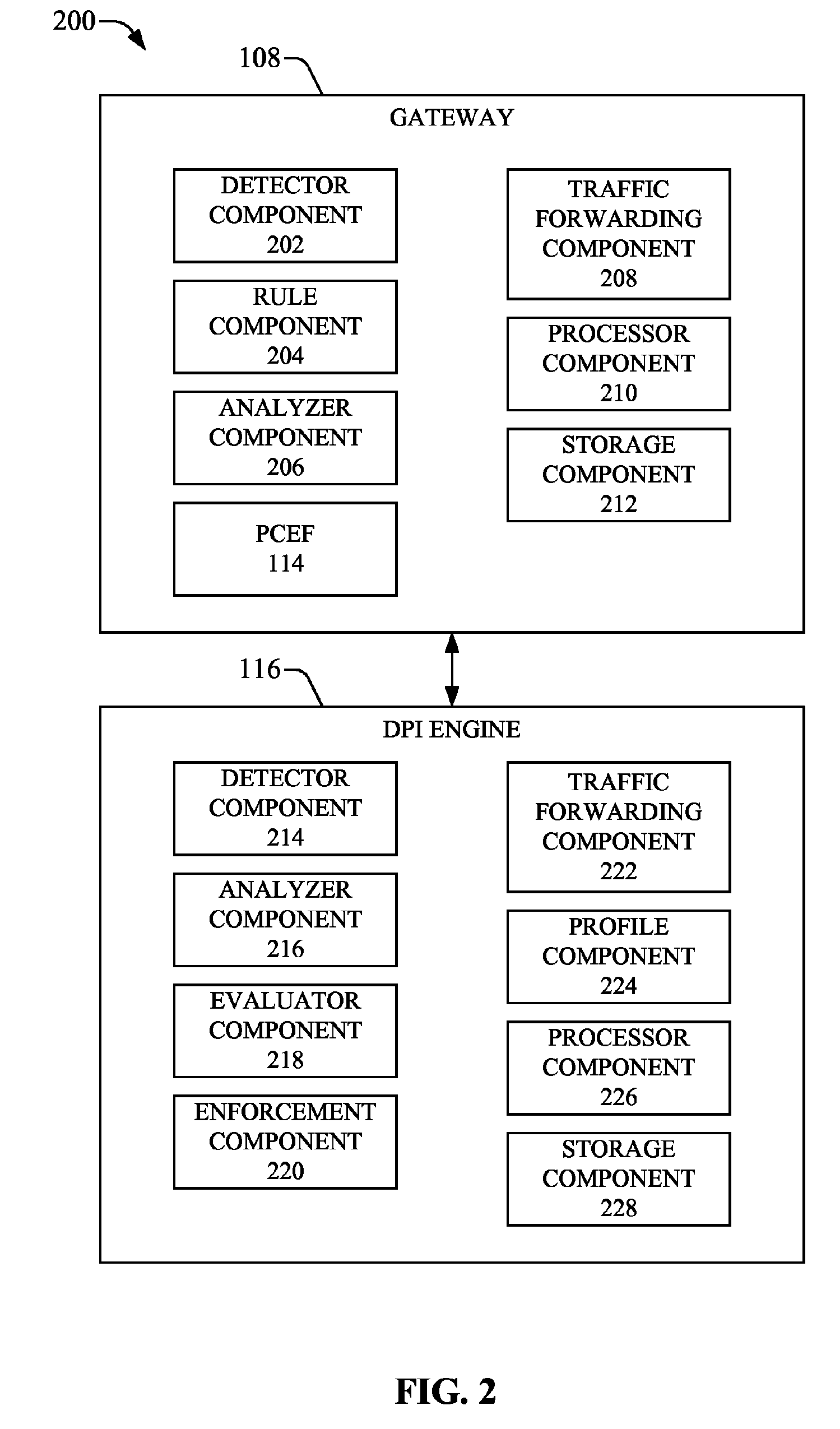
System(s) and method(s) that employ deep packet inspection (DPI) of data flow relating to a requested service associated with a communication device to facilitate customizing the service or results provided by the service are presented. A service request can be received by a gateway identification of the service is attempted. If the service is identified, a privacy rule(s), which is contained in a user privacy profile of a user associated with the communication device, is analyzed to determine whether the privacy rule(s) applies to the service. If the privacy rule(s) is applicable, a DPI engine performs DPI on the data flow, in accordance with the privacy rule(s), to obtain information that can be used to customize the service or results provided by the service. The user can specify the level of DPI to be applied. A default rule can specify that no DPI is performed on the data flow.
Owner:AT&T MOBILITY II LLC
Secure system and method for enforcement of privacy policy and protection of confidentiality
ActiveUS7401352B2User identity/authority verificationComputer security arrangementsThird partyTamper resistance
The invention includes various systems, architectures, frameworks and methodologies that can securely enforce a privacy policy. A method is include for securely guaranteeing a privacy policy between two enterprises, comprising: creating a message at a first enterprise, wherein the message includes a request for data concerning a third party and a privacy policy of the first enterprise; signing and certifying the message that the first enterprise has a tamper-proof system with a privacy rules engine and that the privacy policy of the first entity will be enforced by the privacy rules engine of the first enterprise; sending the message to a second enterprise; and running a privacy rules engine at the second enterprise to compare the privacy policy of the first enterprise with a set of privacy rules for the third party.
Owner:SLINGSHOT IOT LLC
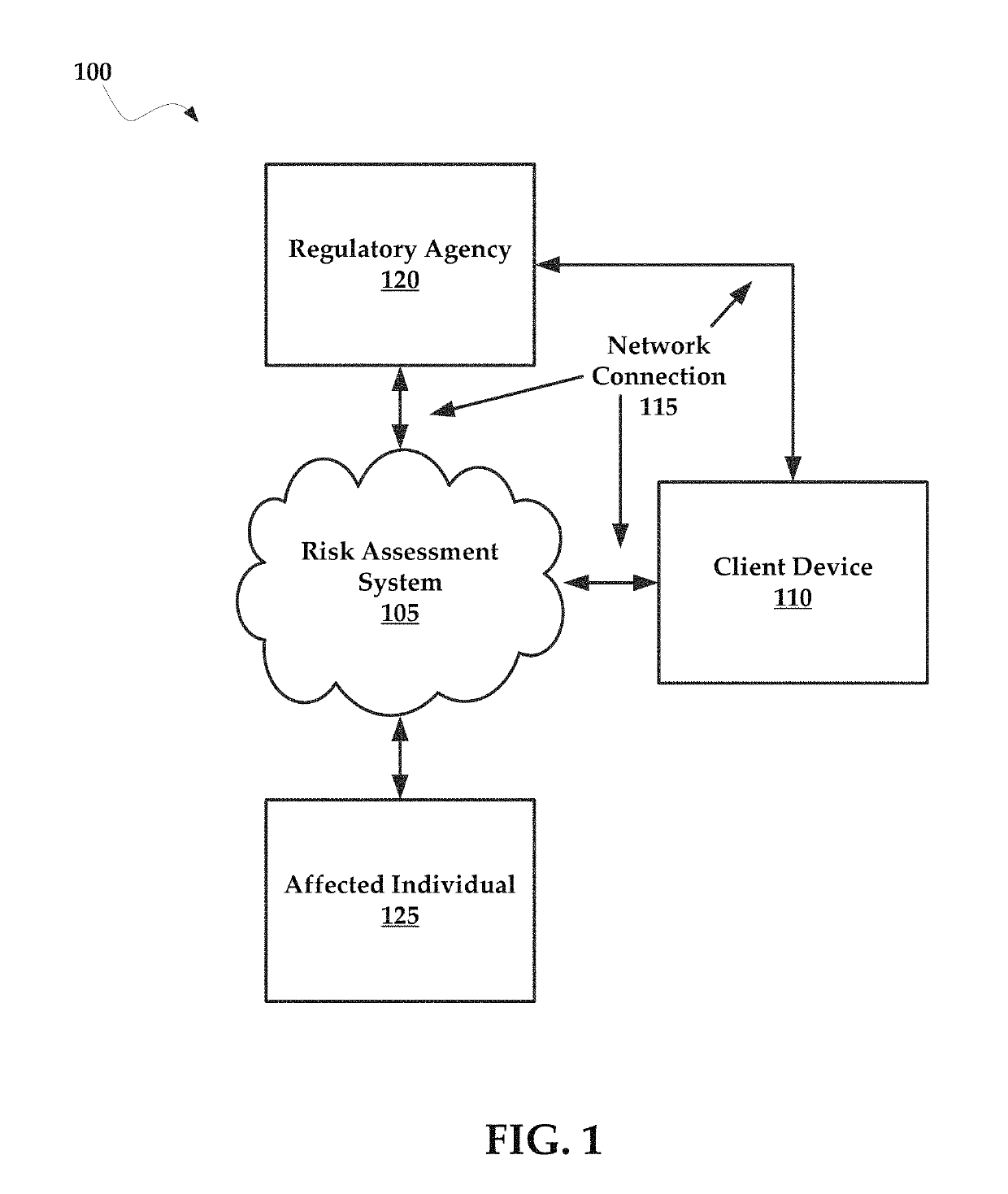
Systems and Methods for Managing Data Incidents
According to some exemplary embodiments, the present technology is directed to methods for managing a data incident, including receiving, via a risk assessment server, in response to an occurrence of the data incident, data incident data that comprises information corresponding to the data incident, the data incident further comprising intentional or unintentional compromise, disclosure or release of personal data or personally identifiable information to an untrusted or unauthorized environment, automatically generating, via the risk assessment server, a risk assessment and decision-support guidance whether the data incident is reportable from a comparison of the data incident data to privacy rules, the privacy rules comprising at least one European General Data Privacy Regulation (GDPR) rule, each rule defining requirements associated with data incident notification obligations, and providing, via the risk assessment server, the risk assessment to a display device that selectively couples with the risk assessment server.
Owner:RADAR LLC
Systems and methods for managing data incidents
Systems and methods for managing a data incident are provided herein. Exemplary methods may include receiving data breach data that comprises information corresponding to the data breach, automatically generating a risk assessment from a comparison of data breach data to privacy rules, the privacy rules comprising at least one federal rule and at least one state rule, each of the rules defining requirements associated with data breach notification laws, and providing the risk assessment to a display device that selectively couples with the risk assessment server.
Owner:RADAR LLC
Auto-creating groups for sharing photos
ActiveUS9342817B2Easy accessMetadata multimedia retrievalComputer security arrangementsDigital contentPrivacy rule
Methods and systems for aggregating and sharing digital content associated with social events via a network are provided. In one example embodiment, a system for aggregating and sharing digital content associated with social events via a network facilitates the aggregation and sharing of digital content, such as photos and videos. The aggregation may be performed with respect to the digital content received from different sources associated with the same social event. The digital content may also be subjected to an image recognition process to identify one or more individuals appearing in the photos or videos. The shared content may also be filtered to display only those photos or videos with specific individuals. In addition, users may be allowed to set privacy rules with respect to the photos and videos within which they appear.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com