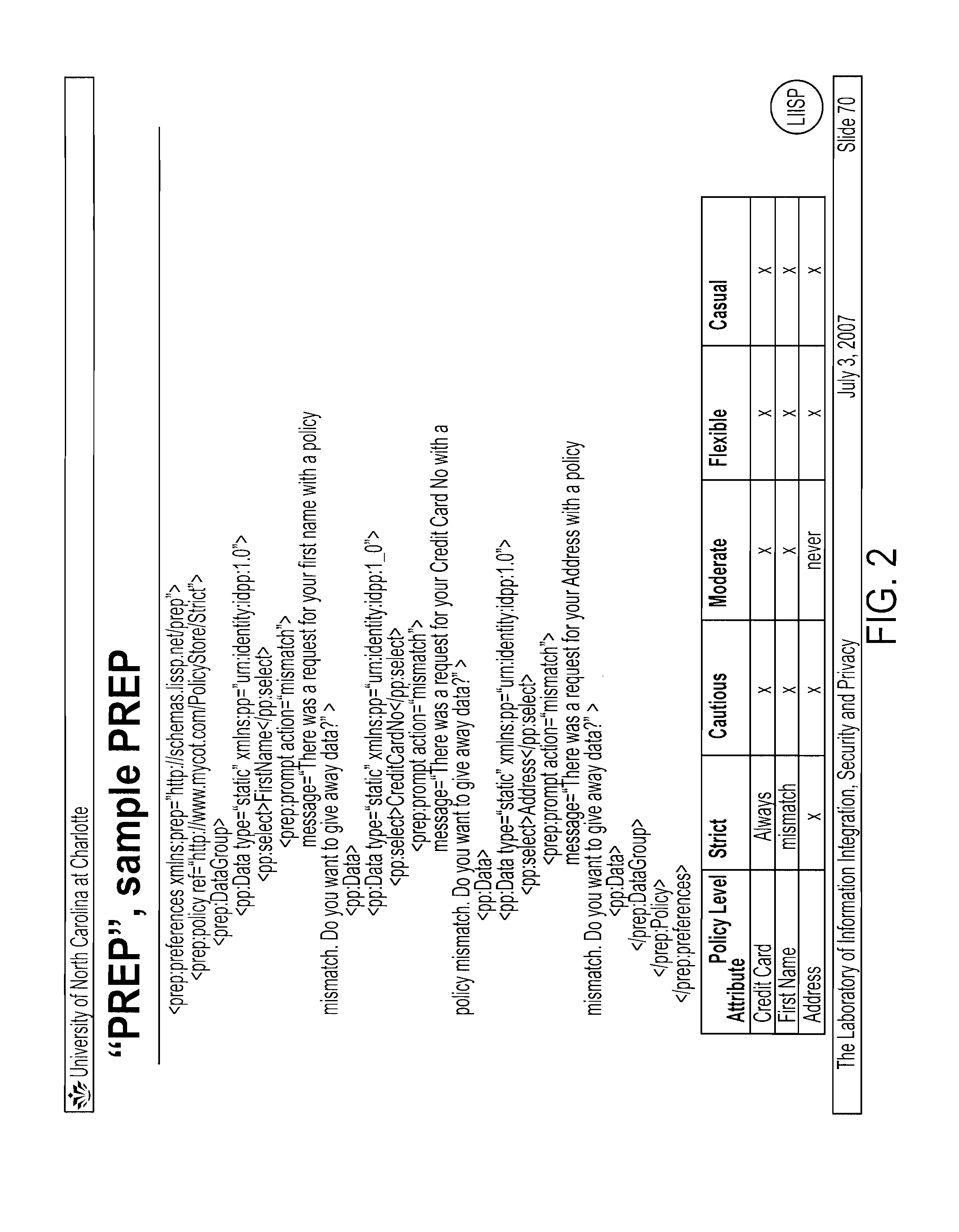
Patents
Literature
90 results about "Privacy management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Communication privacy management (CPM), originally known as communication boundary management, is a systematic research theory designed to develop an evidence-based understanding of the way people make decisions about revealing and concealing private information.CPM theory suggests that individuals maintain and coordinate privacy boundaries (the limits of what they are willing to share) with ...
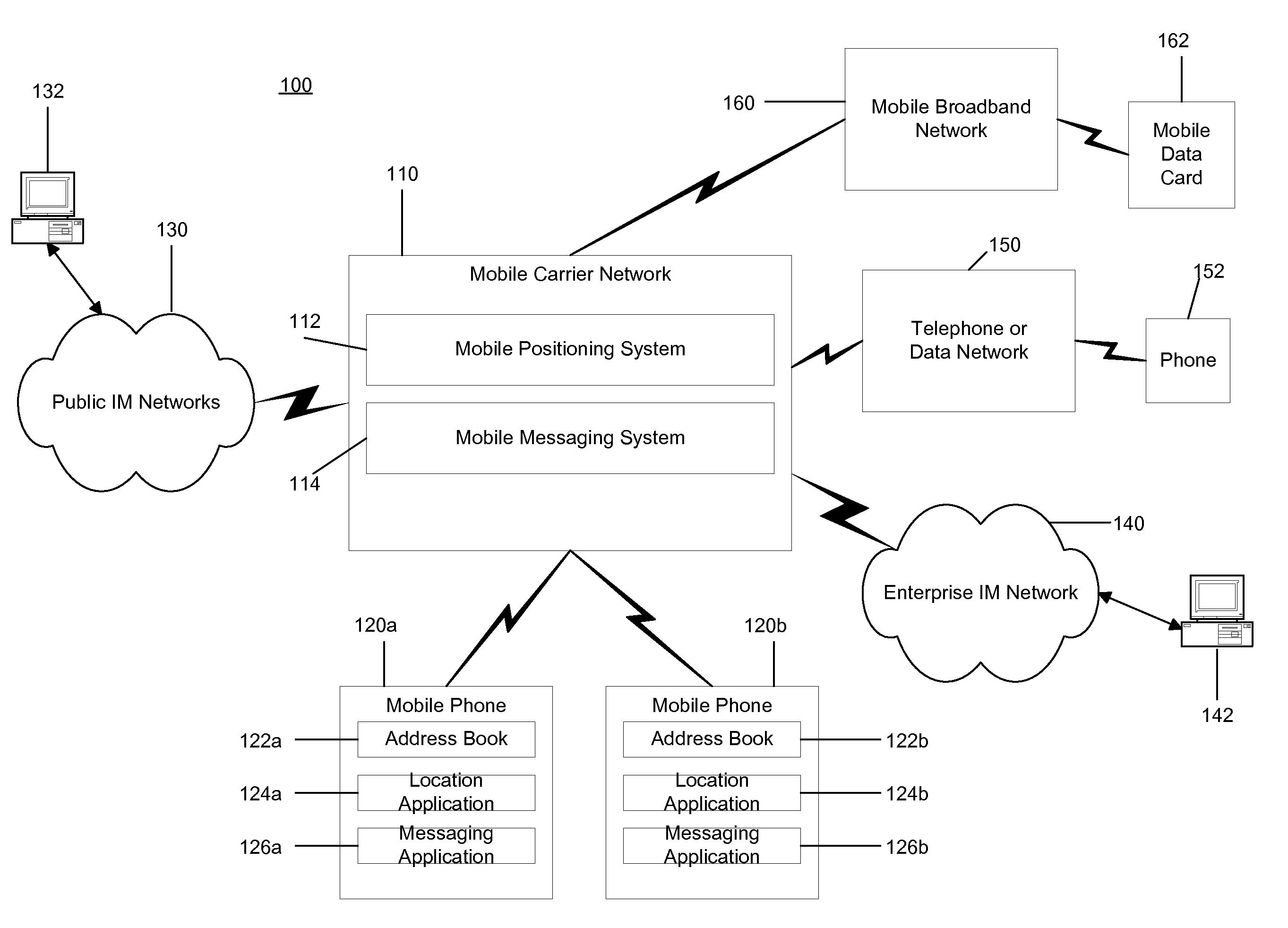
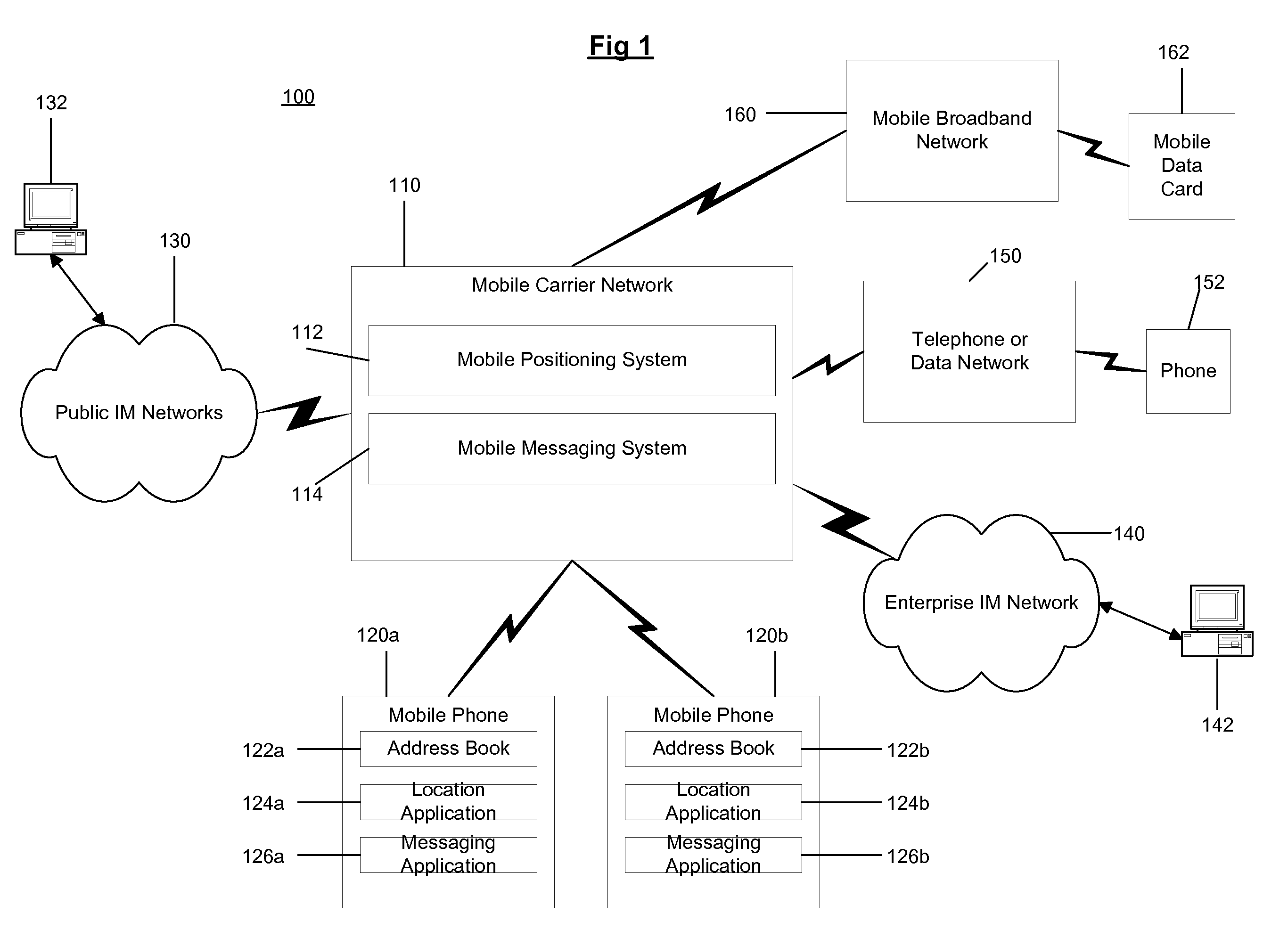
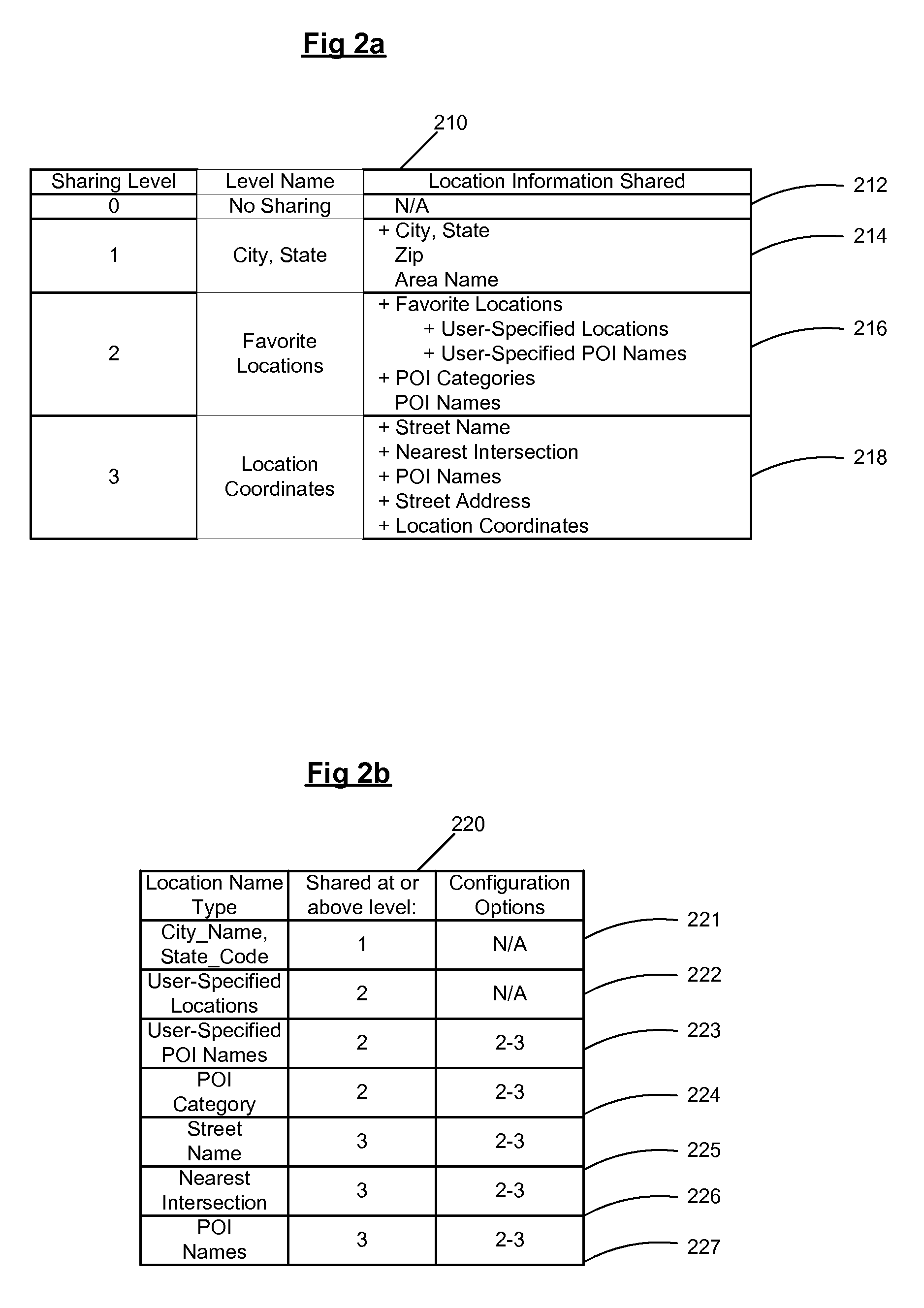
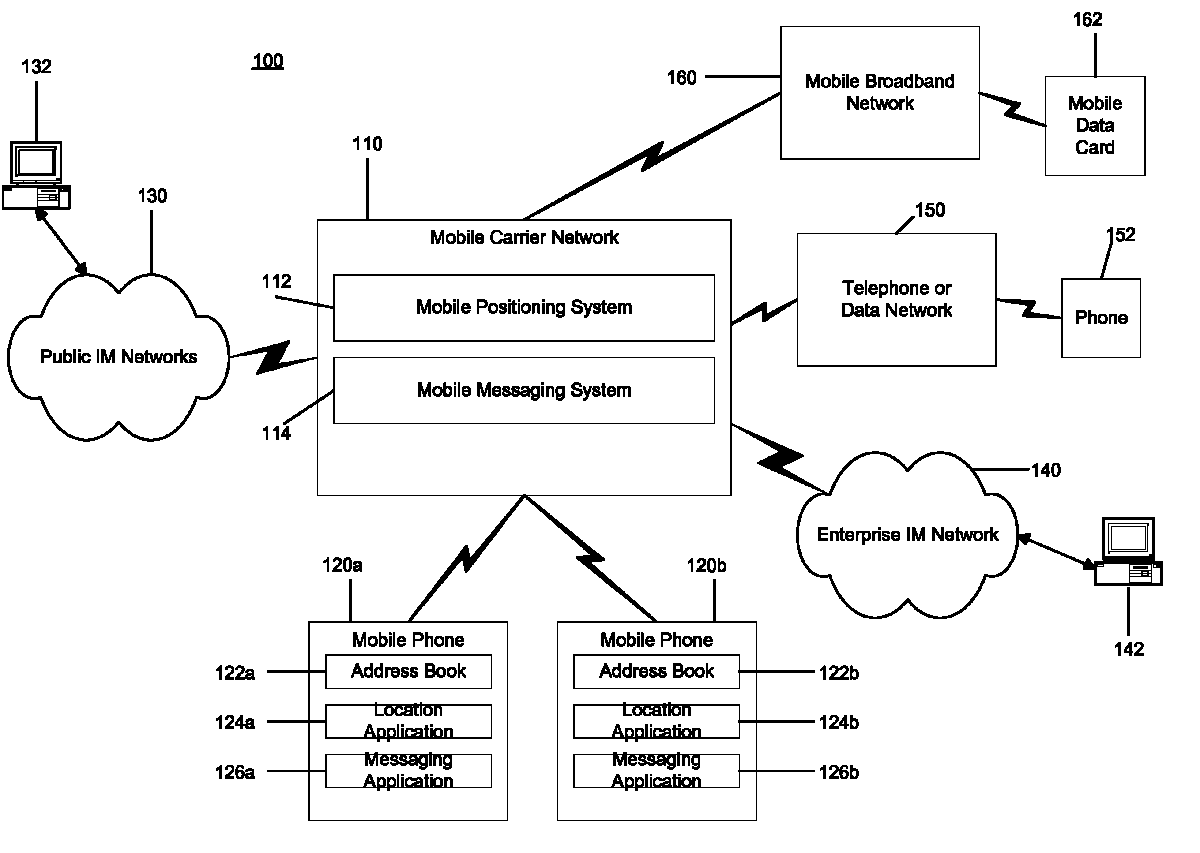
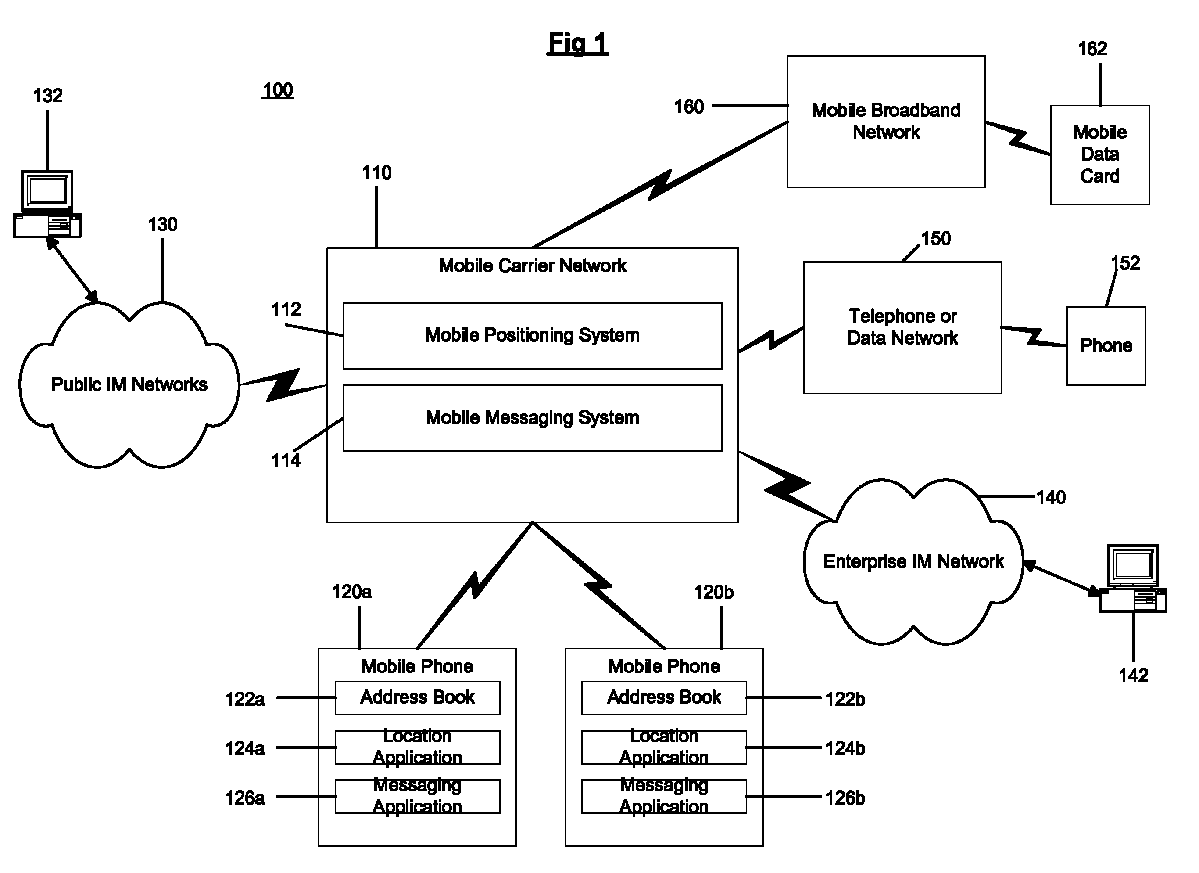
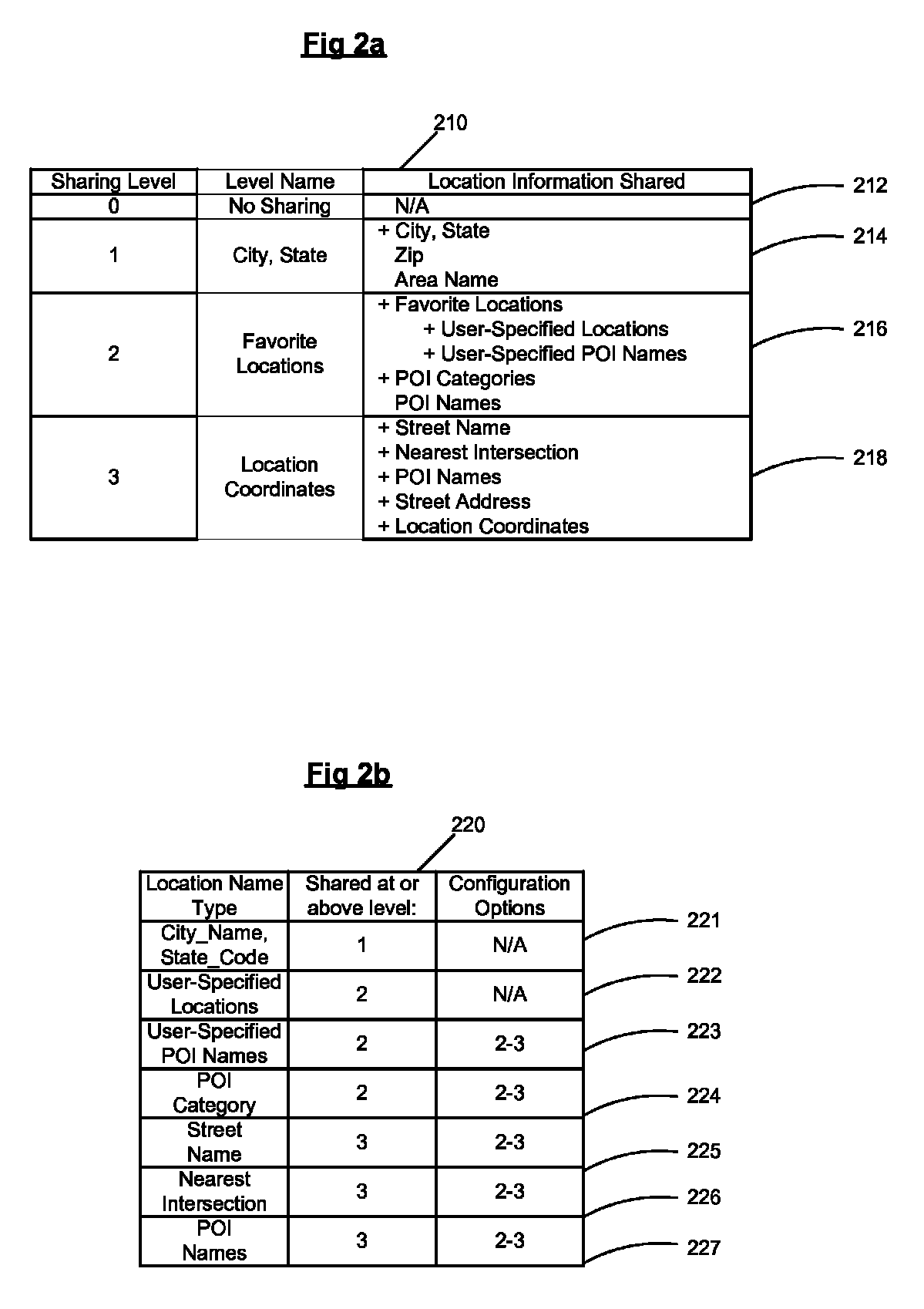
Location based presence and privacy management
ActiveUS20090047972A1Share widelyMitigating liabilityInformation formatServices signallingInternet privacySocial web
A method and system for providing location based presence status and enhancing location privacy management in a mobile, instant messaging or social networking environment. A user specifies or saves their favorite locations (e.g. home, work, school, or particular business or point of interest locations), and specifies or selects names and / or categories to be shared for each user-specified location. In addition, the system provides multiple sharing levels for sharing multiple types of location contextual information. When user's current location corresponds to user-specified locations, location based presence status is provided to specified contacts according to the sharing level settings, and provides user the option to share location contextual information without sharing location coordinates of the user. When user is driving, location based presence status is updated accordingly, and when user is at other business or POI locations, corresponding location contextual information is shared based on user's settings for each sharing level.
Owner:MPANION
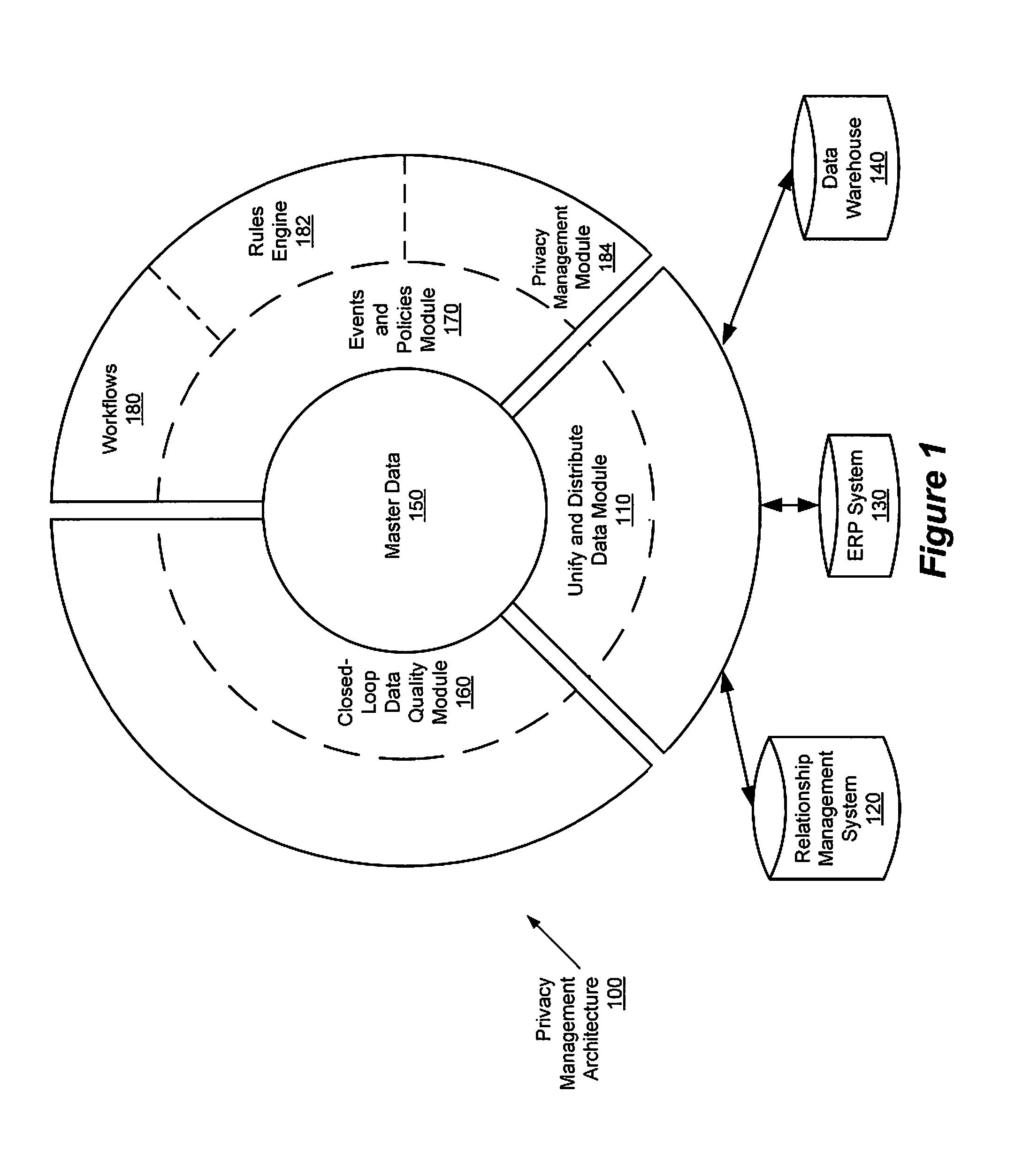
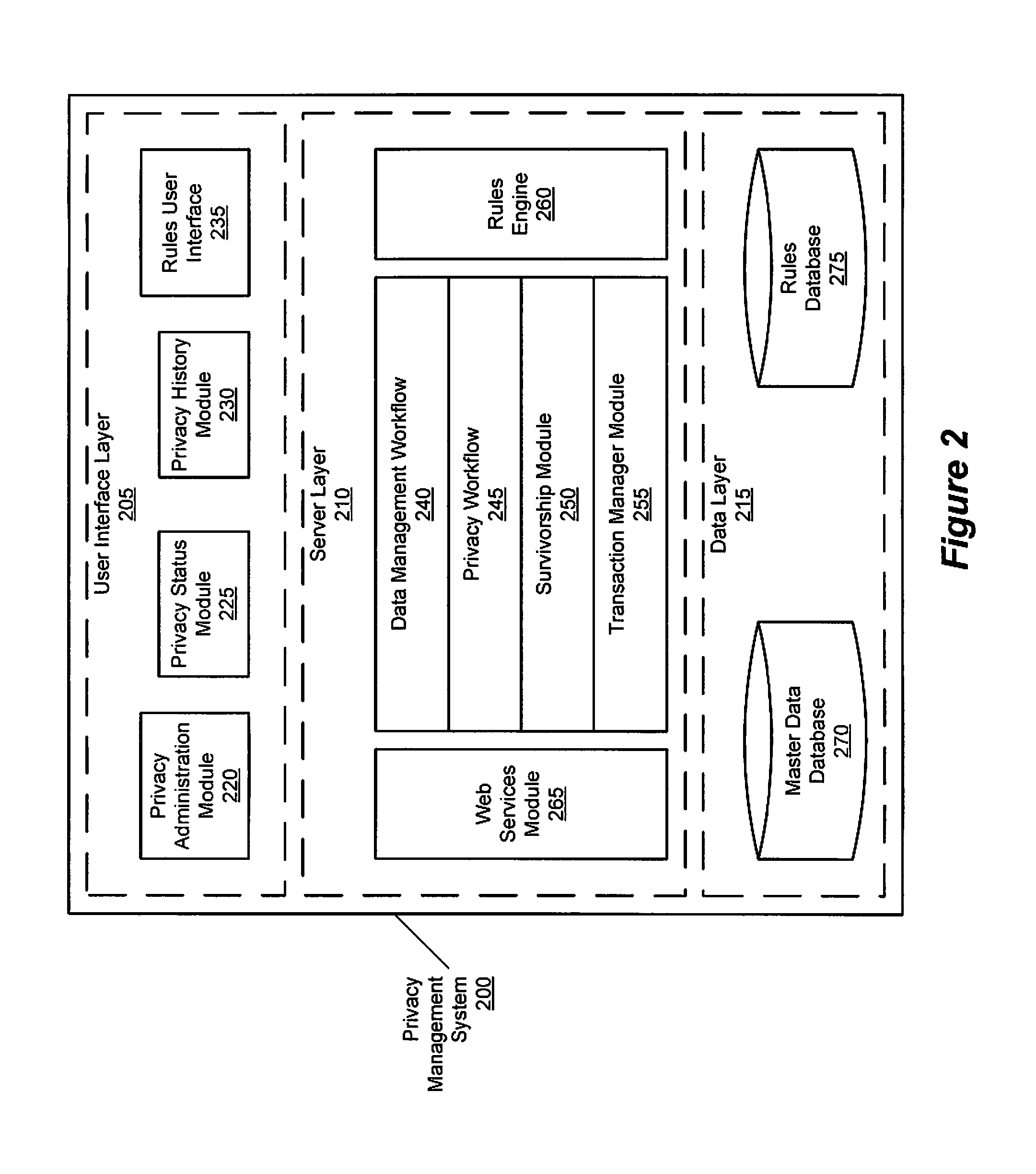
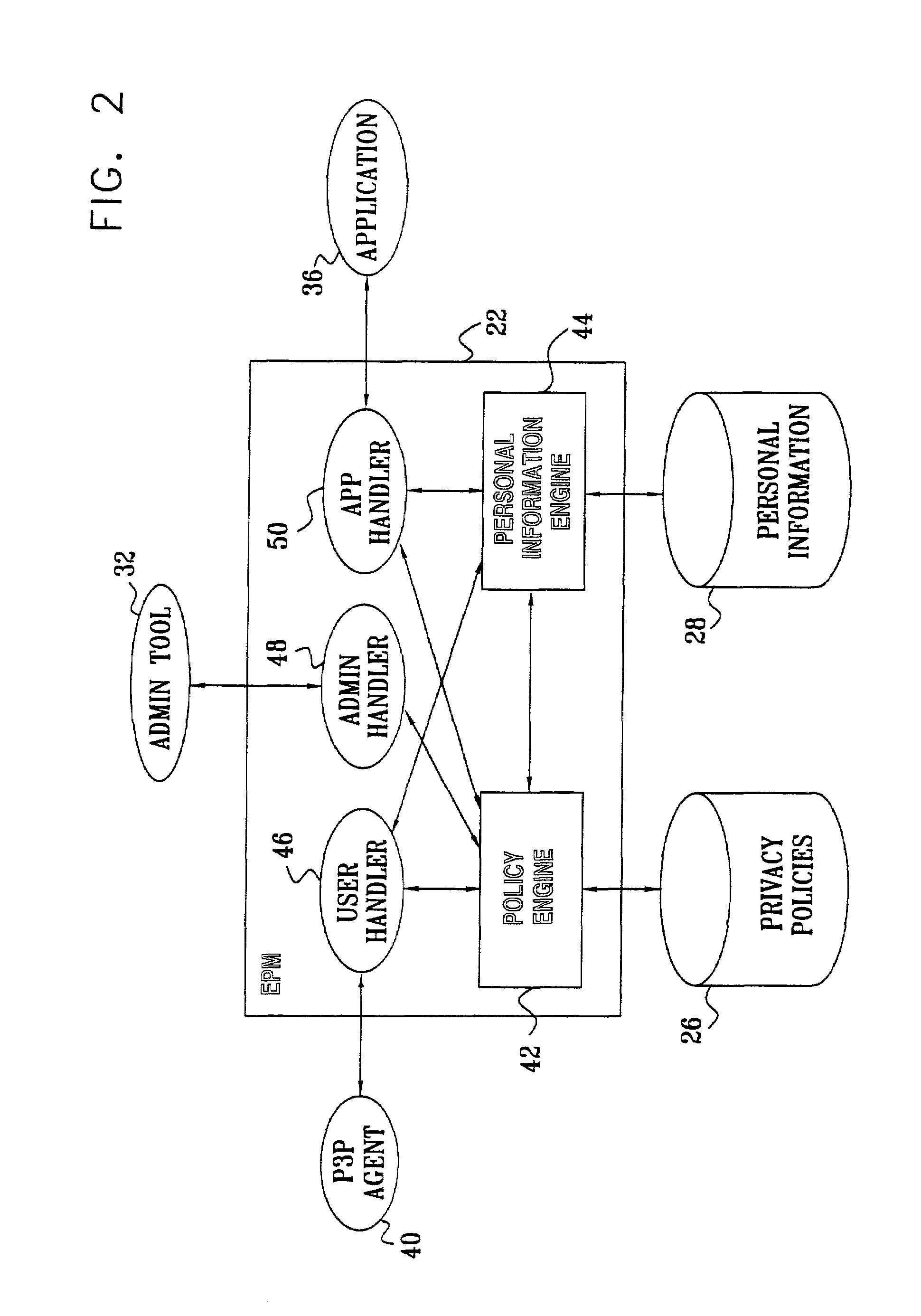
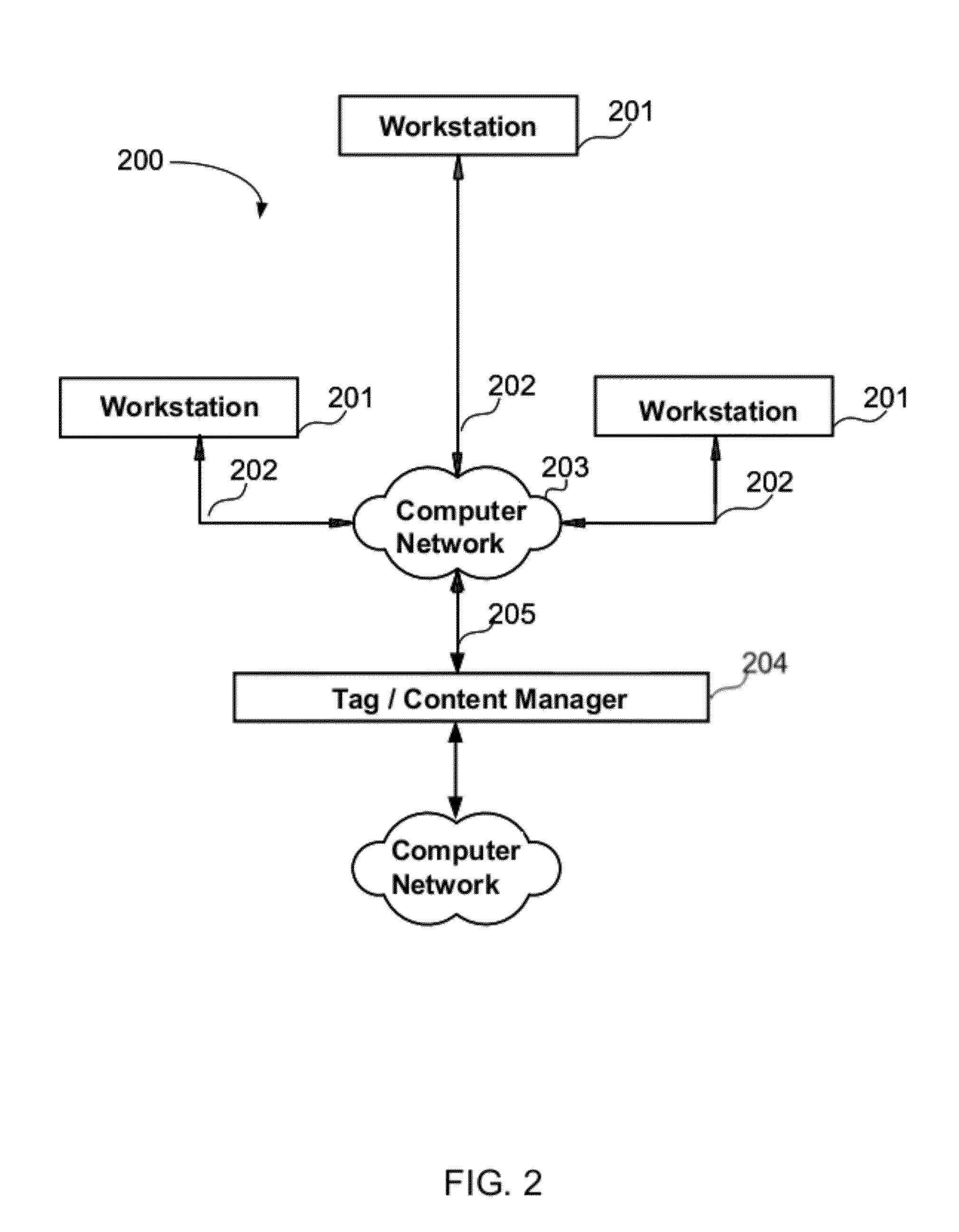
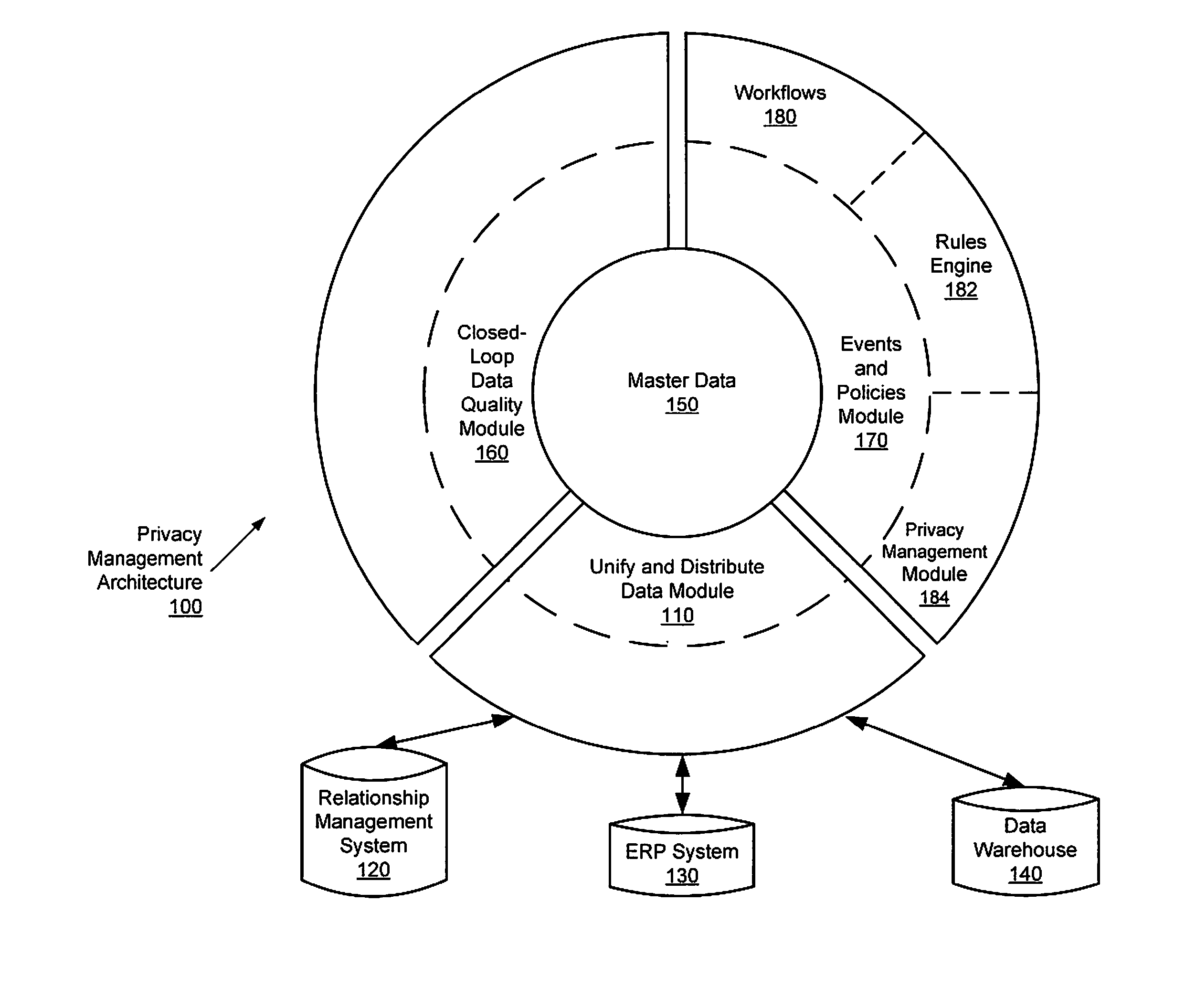
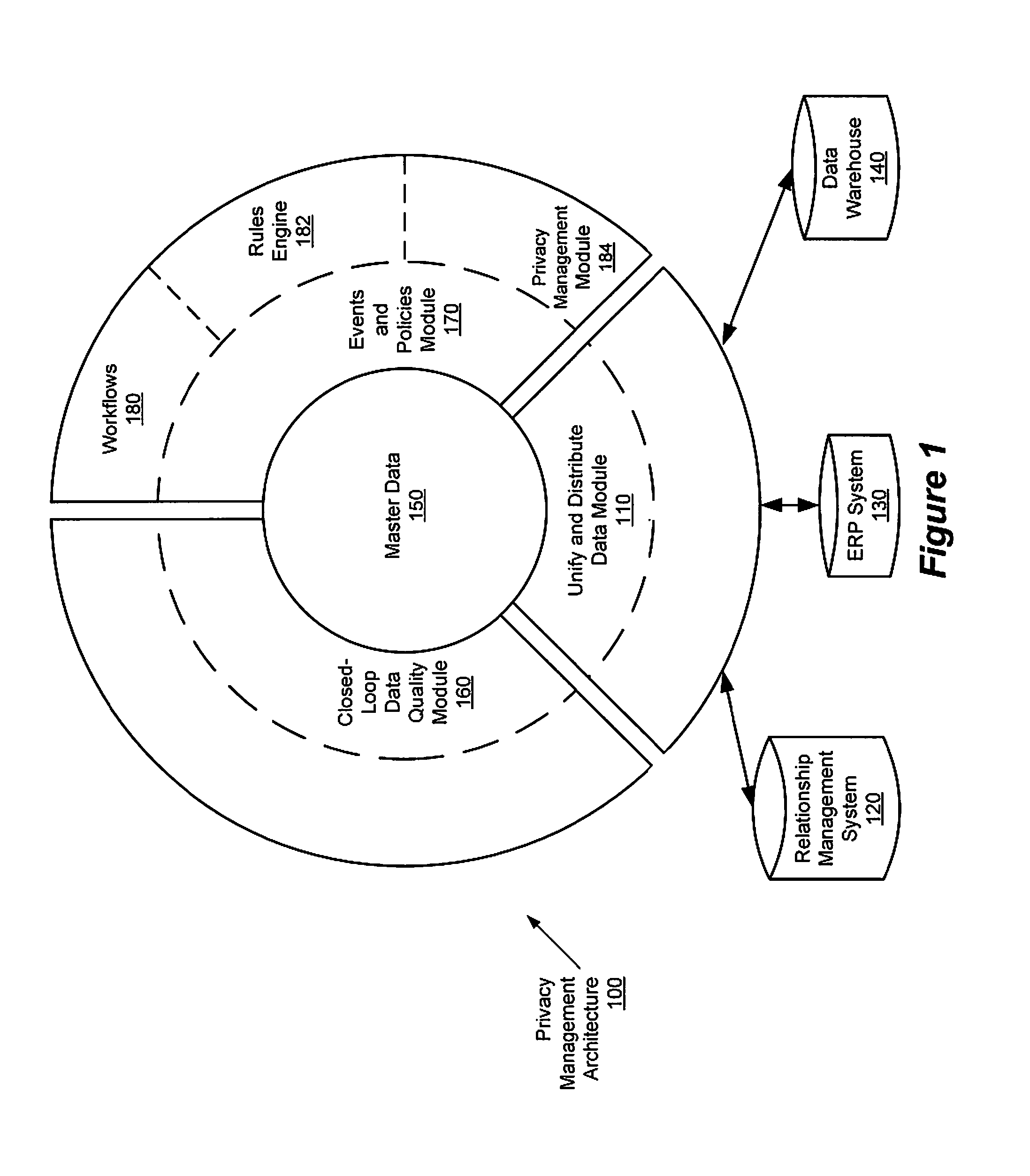
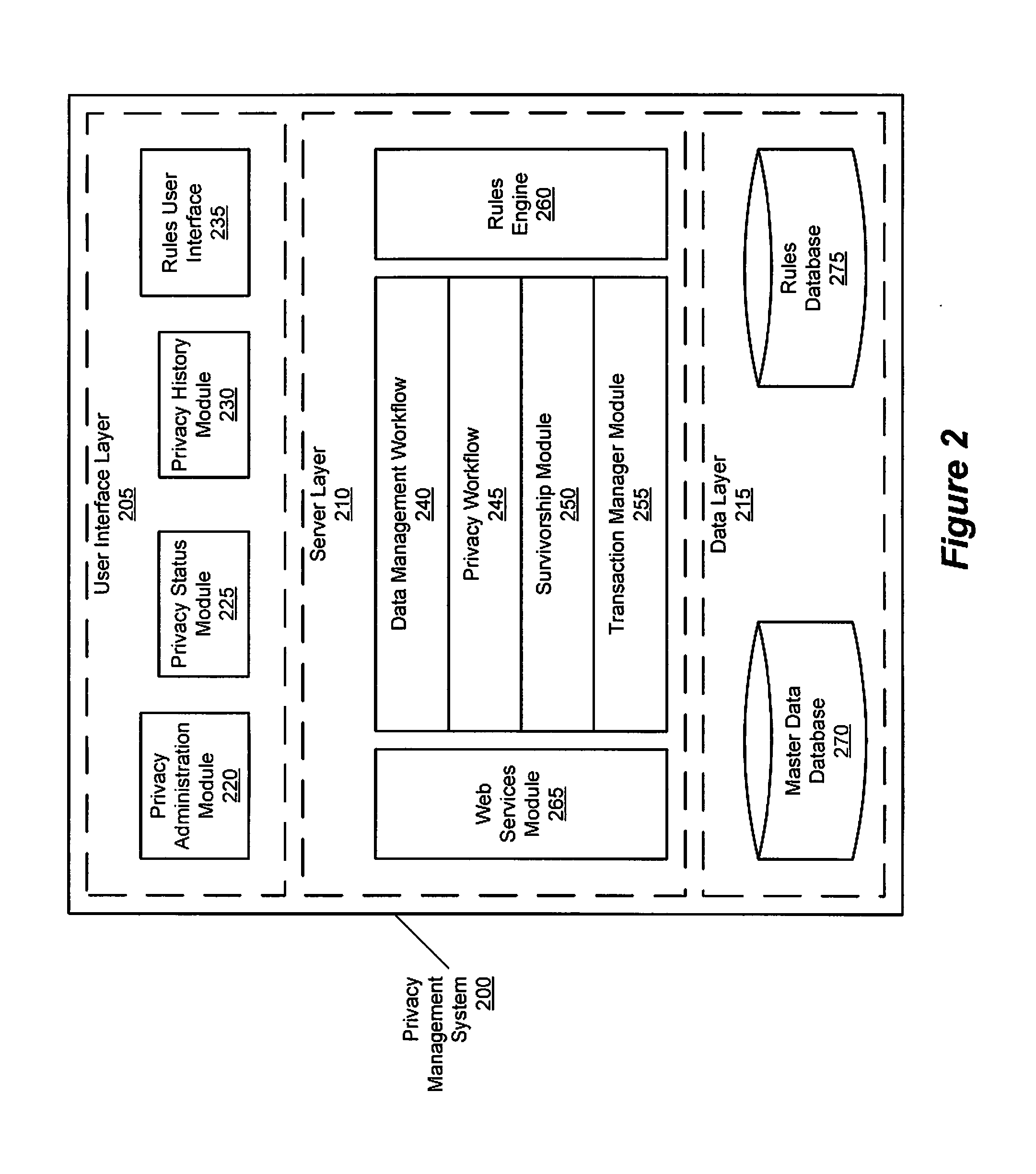
Privacy management policy hub
A system architecture is disclosed that includes a privacy management system. In particular, the privacy management system provides a policy hub for maintaining and managing customer privacy information. The privacy management system maintains a master data database for customer information and customer privacy preferences, and a rules database for privacy rules. The privacy management system captures, synchronizes, and stores customer privacy data. Privacy rules may be authored using a privacy management vocabulary, and can be customized for an enterprise's privacy policies.
Owner:ORACLE INT CORP
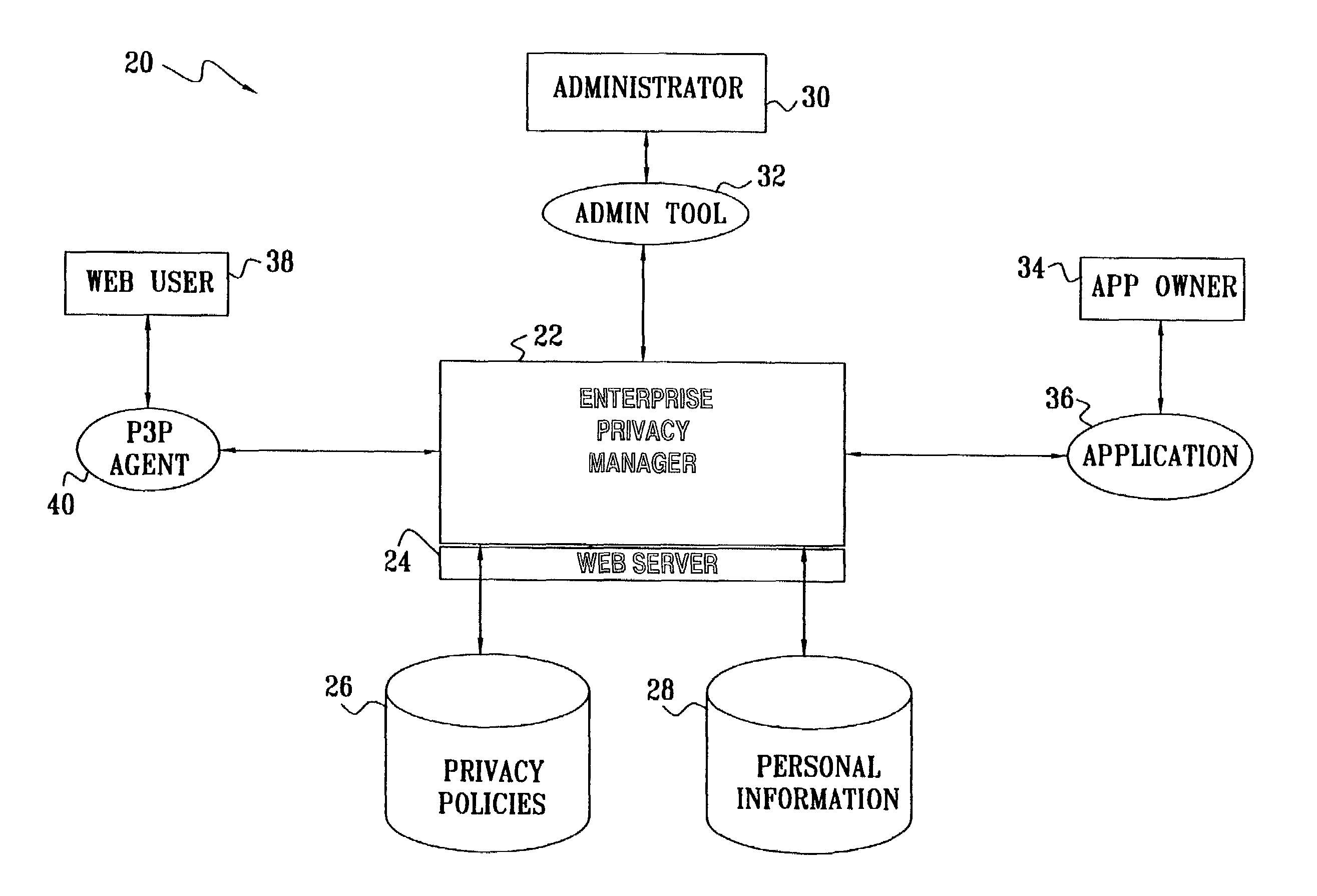
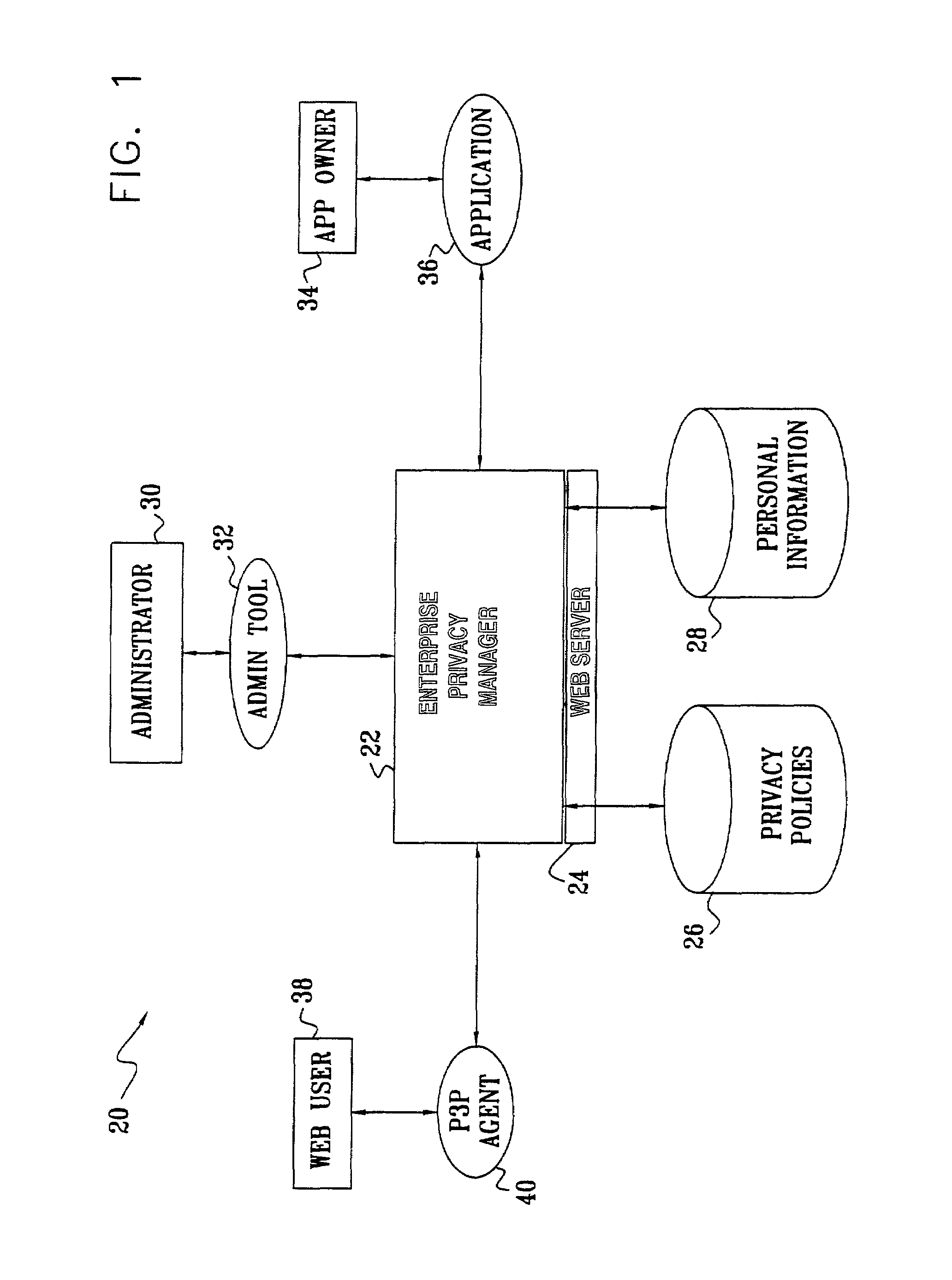
Enterprise privacy manager
InactiveUS7225460B2Remarkable effectEasy maintenanceUnauthorized memory use protectionComputer security arrangementsInternet privacyPrivacy policy
A method for privacy management includes providing a linked collection of interactive resources through which a user is able to exchange information with an enterprise that provides the resources, and assigning respective, non-uniform privacy policies to at least some of the resources regarding use of the information that is exchanged through the resources. The user, accessing a given one of the resources, is provided with the respective privacy policy for that resource. At least a portion of the information that is associated with the given one of the resources is exchanged with the user subject to the provided privacy policy.
Owner:IBM CORP
Location based presence and privacy management
ActiveUS8050690B2Mitigating liabilityMitigating privacyInformation formatServices signallingInternet privacySocial web
Owner:MPANION
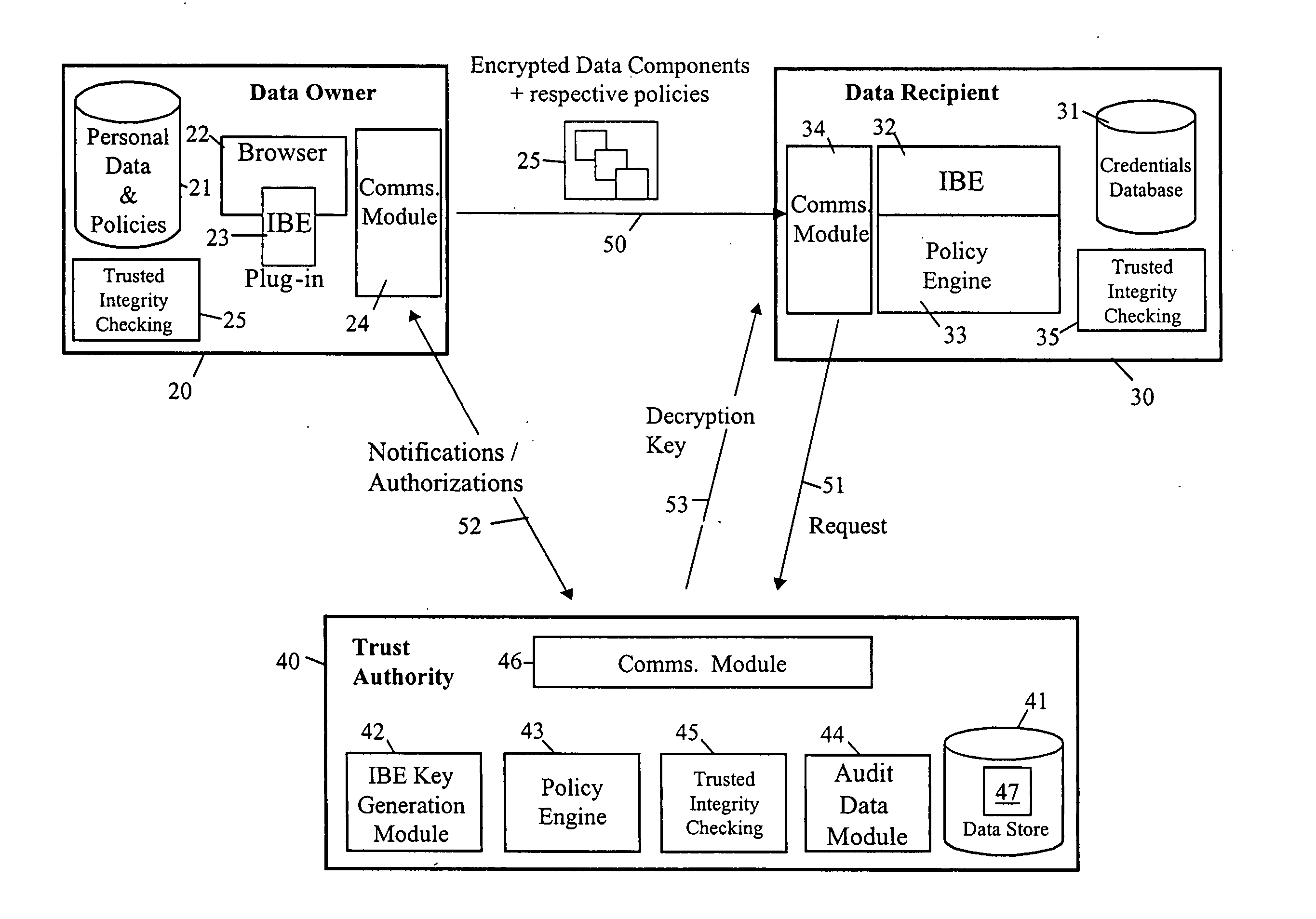
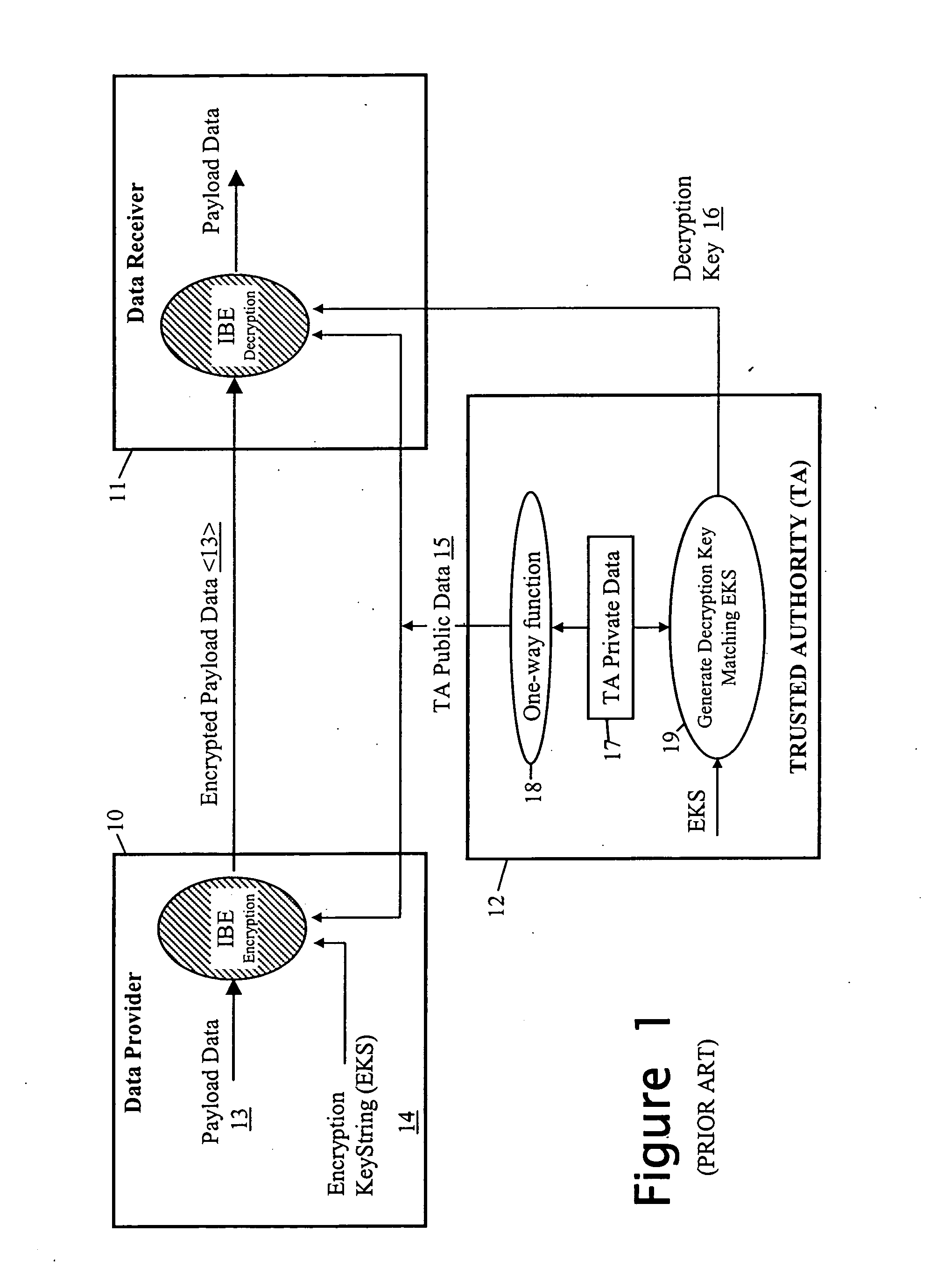
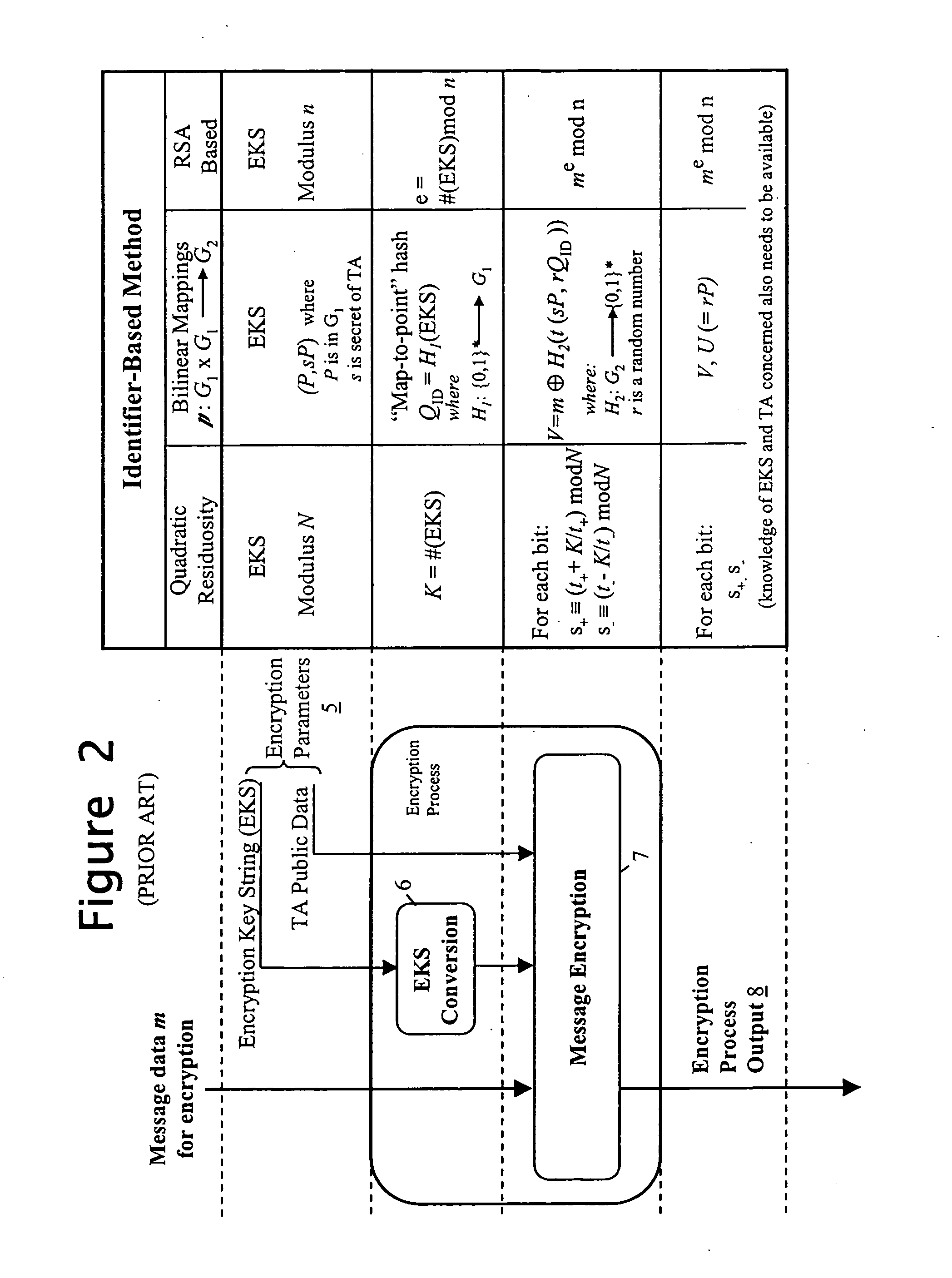
Privacy management of personal data
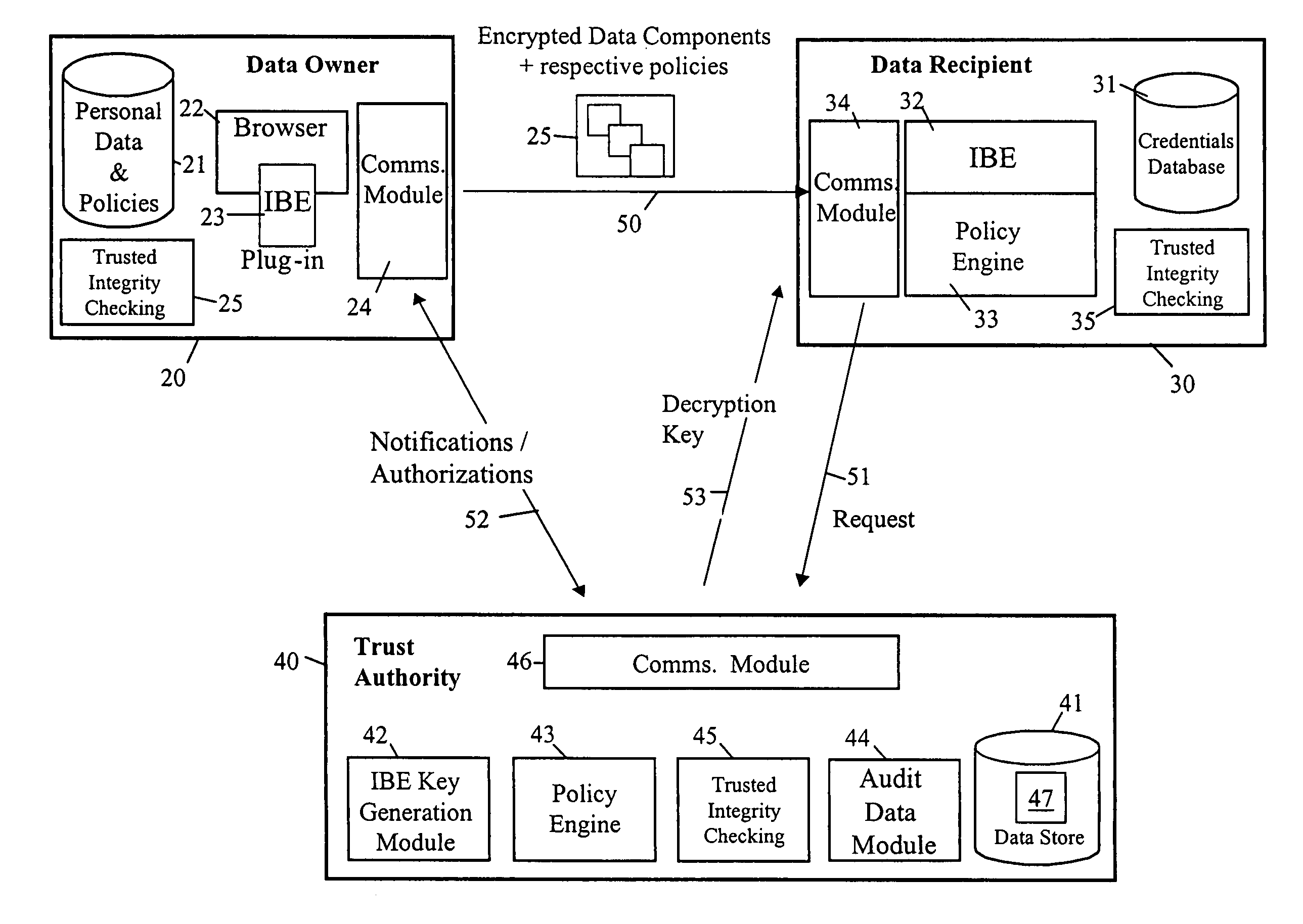
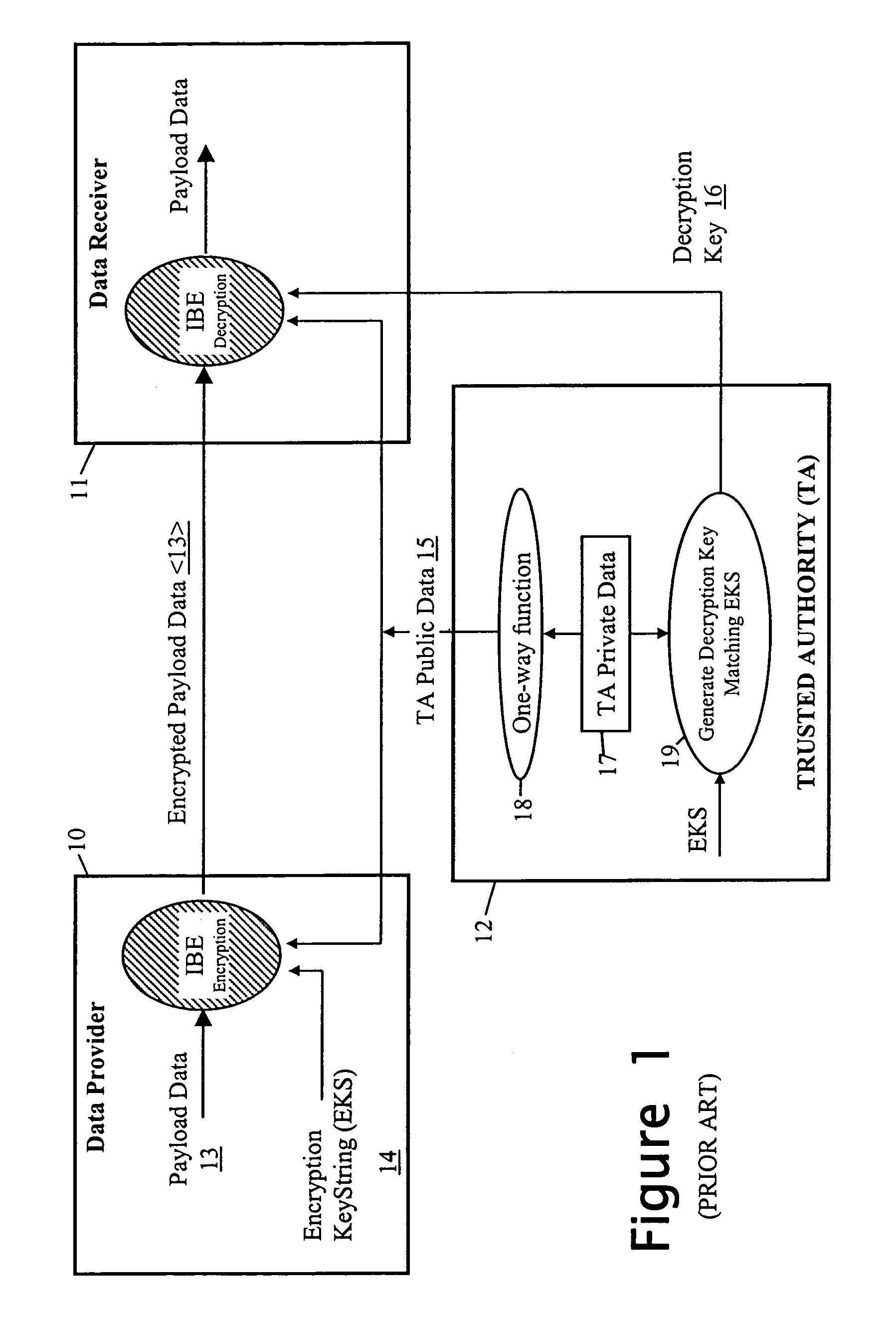
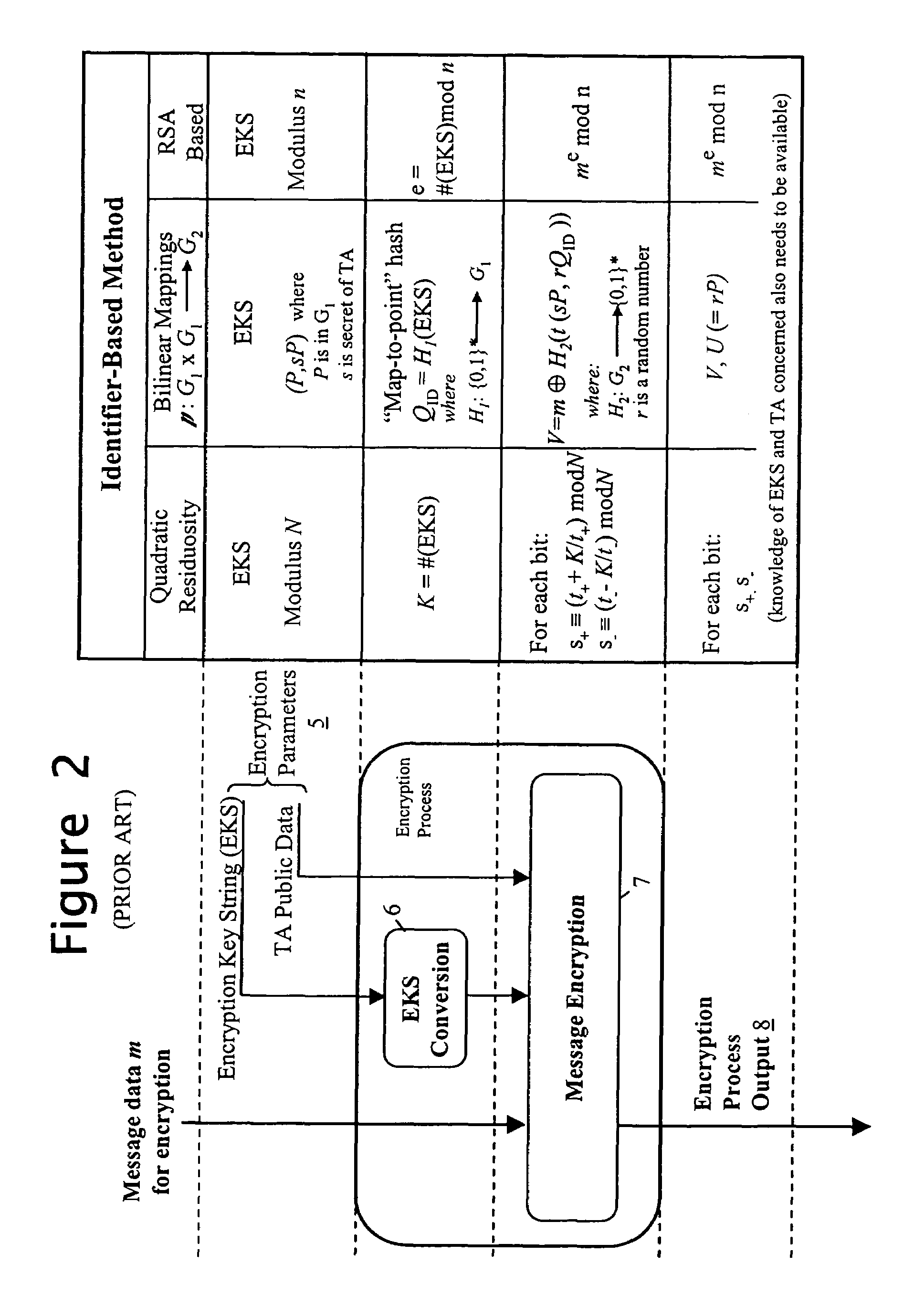
InactiveUS7398393B2Public key for secure communicationUser identity/authority verificationEncryptionPrivacy management
When sending personal data to a recipient, the data owner encrypts the data using both a public data item provided by a trusted party and an encryption key string formed using at least policy data indicative of conditions to be satisfied before access is given to the personal data. The encryption key string is typically also provided to the recipient along with the encrypted personal data. To decrypt the personal data, the recipient sends the encryption key string to the trusted party with a request for the decryption key. The trusted party determines the required decryption key using the encryption key string and private data used in deriving its public data, and provides it to the requesting recipient. However, the decryption key is either not determined or not made available until the trusted party is satisfied that the associated policy conditions have been met by the recipient.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
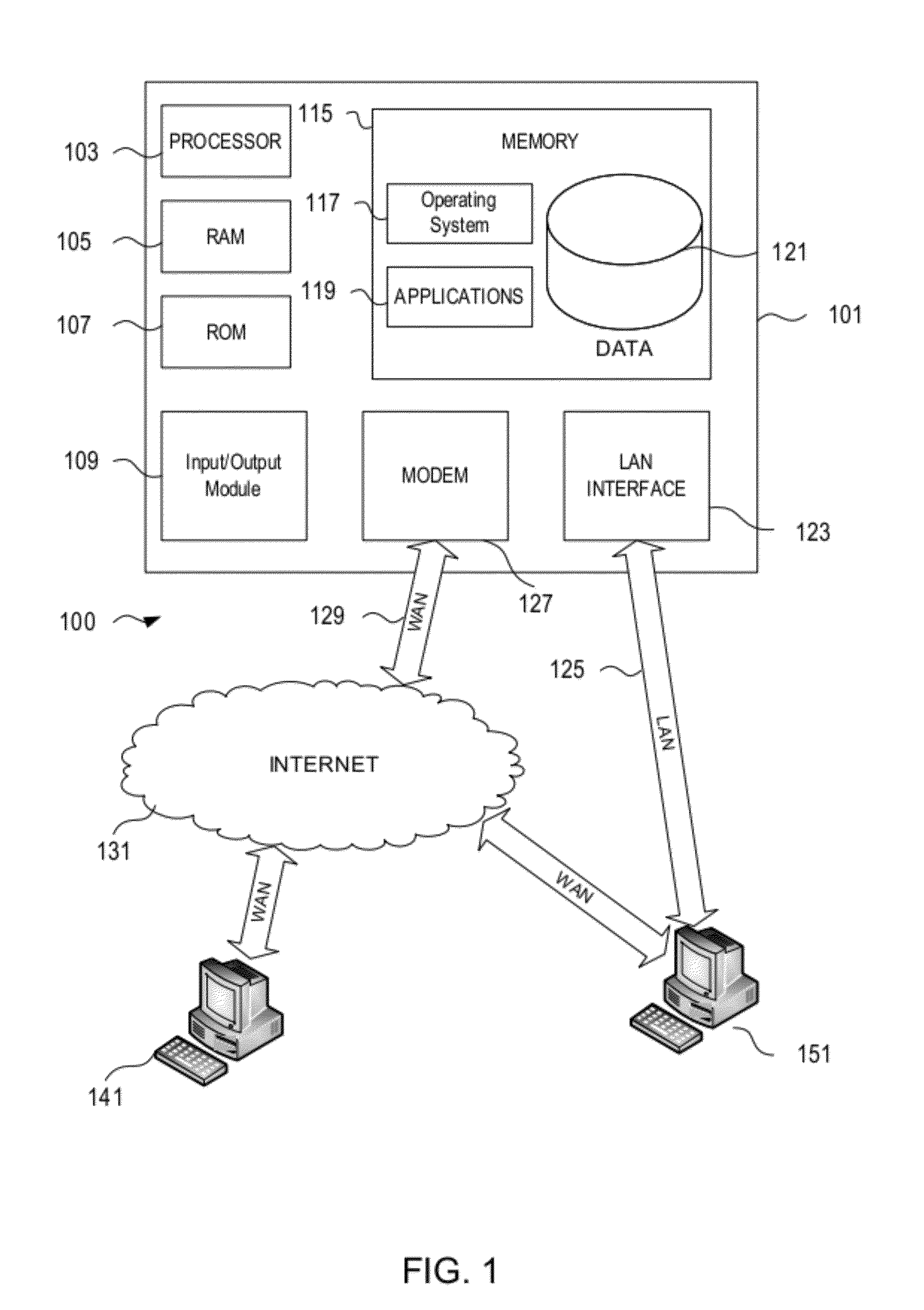
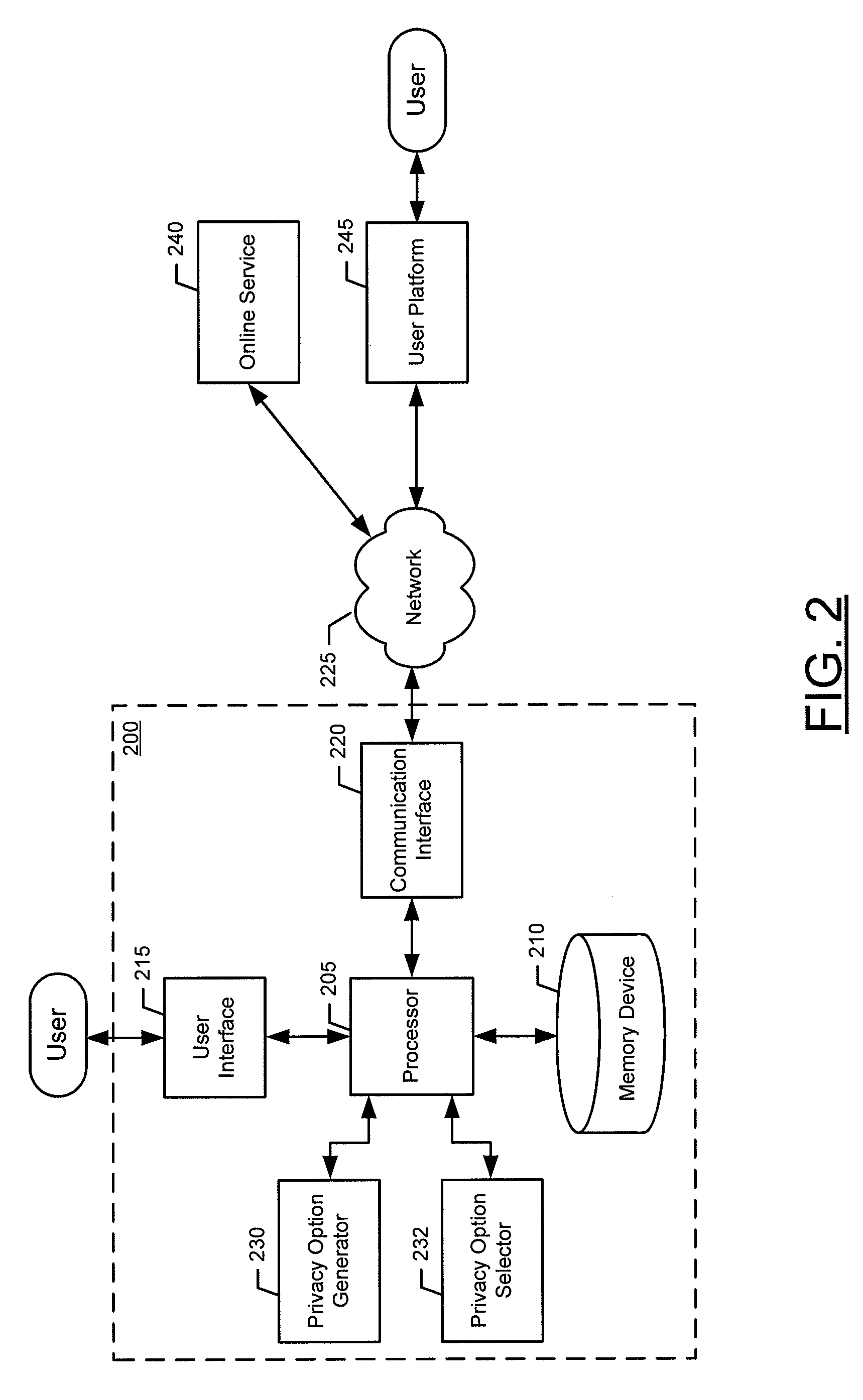
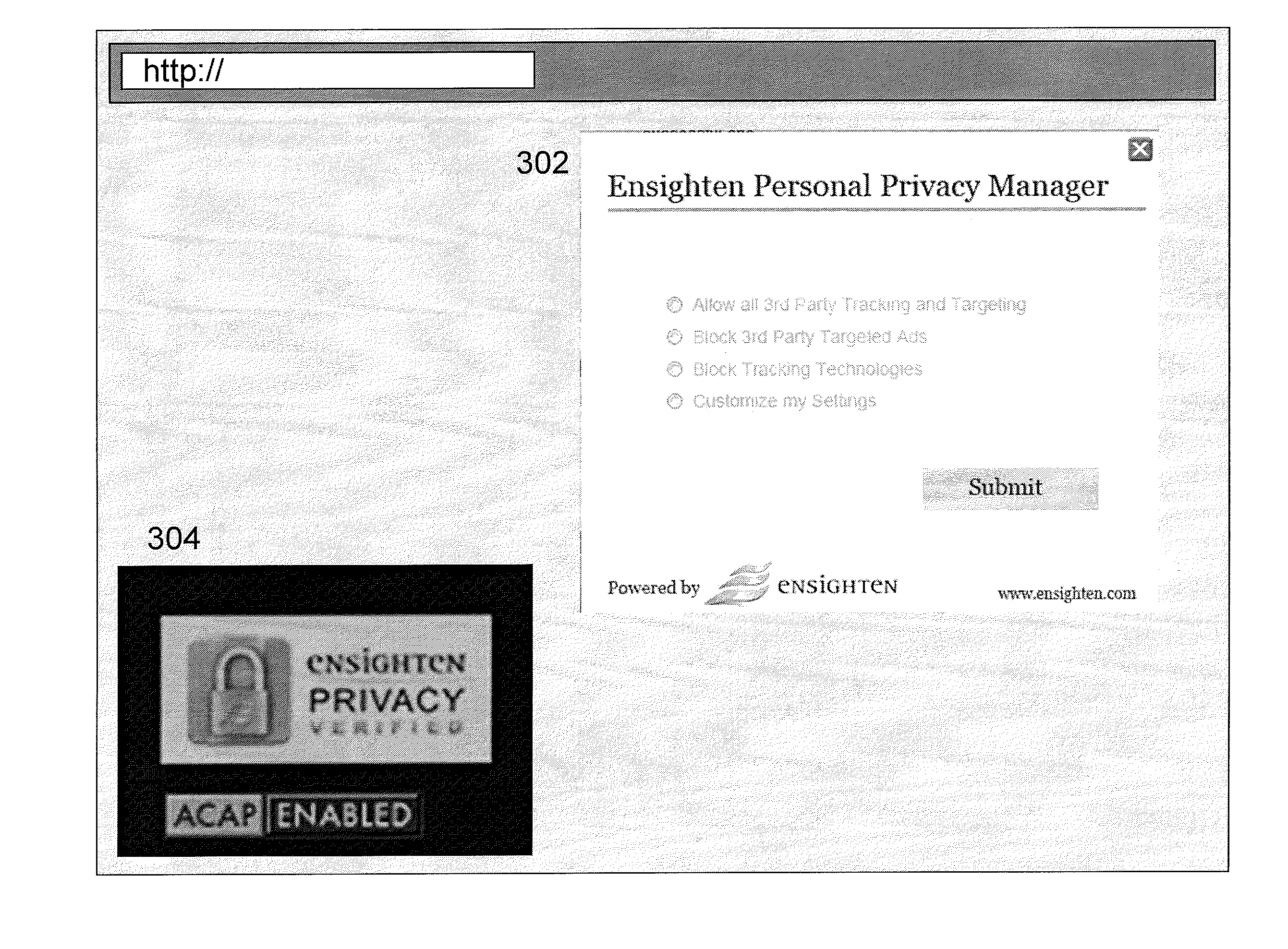
Online privacy management
ActiveUS9003552B2Simple processDigital data processing detailsDigital computer detailsDashboardClient-side scripting
A privacy management system (PMS) is disclosed for a Chief Privacy Officer (CPO) or other user to use in monitoring and / or controlling in realtime the flow of data (e.g., outflow) about the user and his / her online experience. The PMS may employ pattern recognition software to evaluate analytics data and potentially block private information from being sent within the analytics data. The PMS may provide a dashboard displaying a whitelist and / or blacklist indicating what destinations / sources are blocked or allowed as well as private information settings indicating what types of private information should be blocked. The PMS includes browser-client scripting code and may also include a PMS-certified verification icon and / or lock and unlock icons for display on webpages being monitored / controlled in realtime by the PMS.
Owner:ENSIGHTEN
Privacy management system using user's policy and preference matching
By applying a privacy policy, which describes and manages a policy for disclosure of preference information, to the preference information, it is determined whether or not to disclose some or all of the information to a third party based on classification as a result of matching by a matching system. The description of a privacy policy makes it possible to achieve a meaningful communication by disclosing preference information to others within a detailed range while keeping the preference information undisclosed if the user does not wish disclosure thereof, such as disclosing only preference information including preferences matching those of the other user or disclosing only preference information including preferences shared in a certain user group.
Owner:IBM CORP
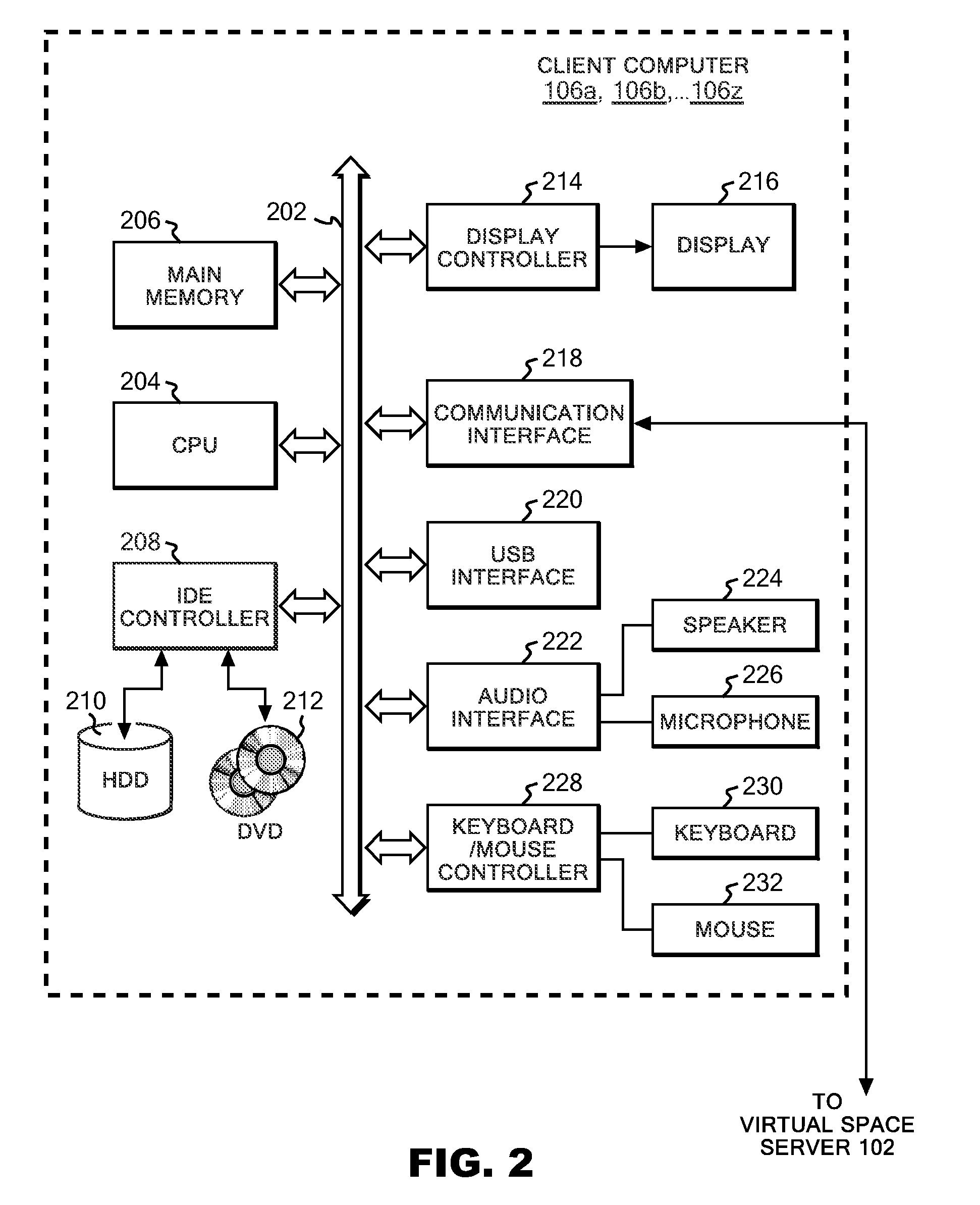
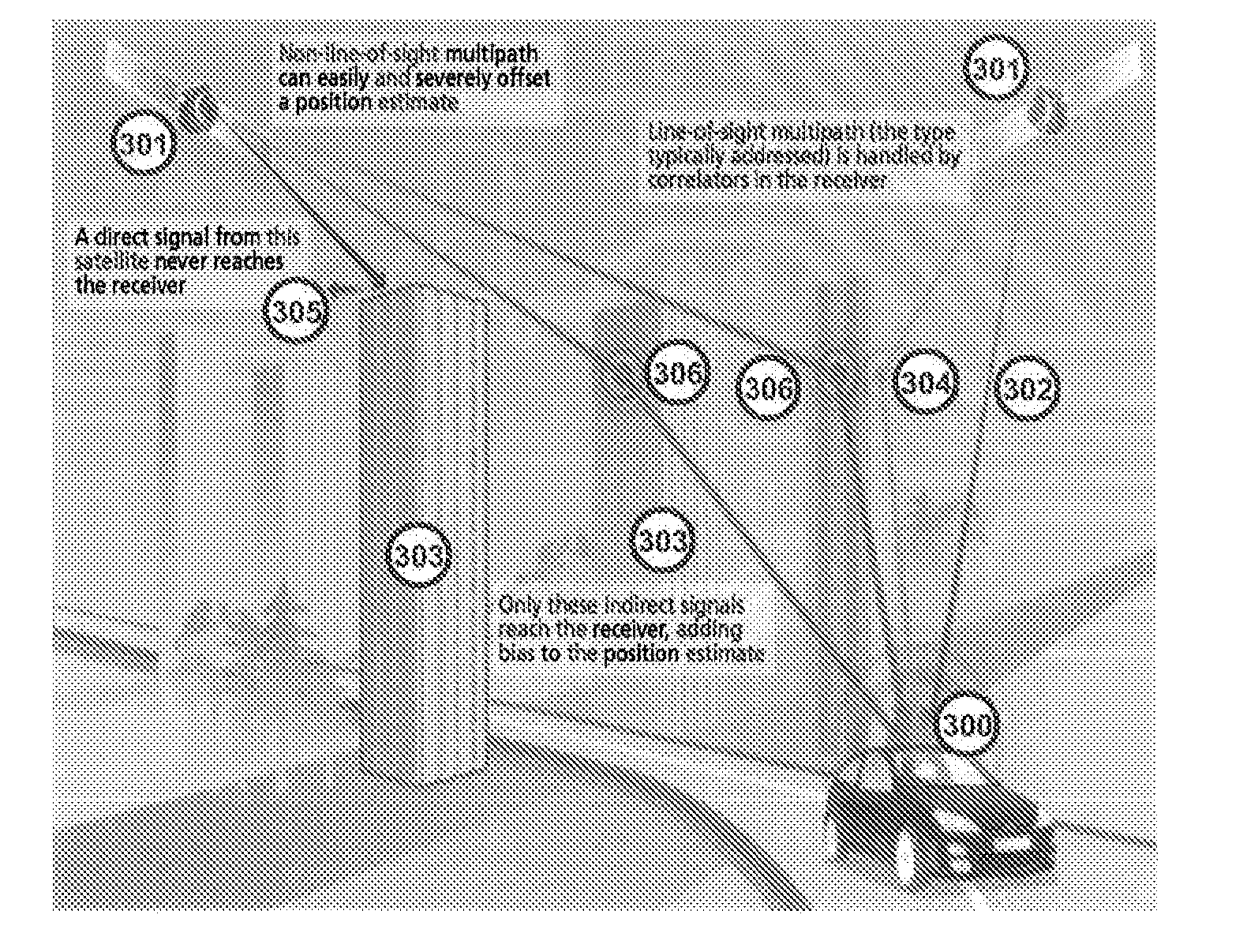
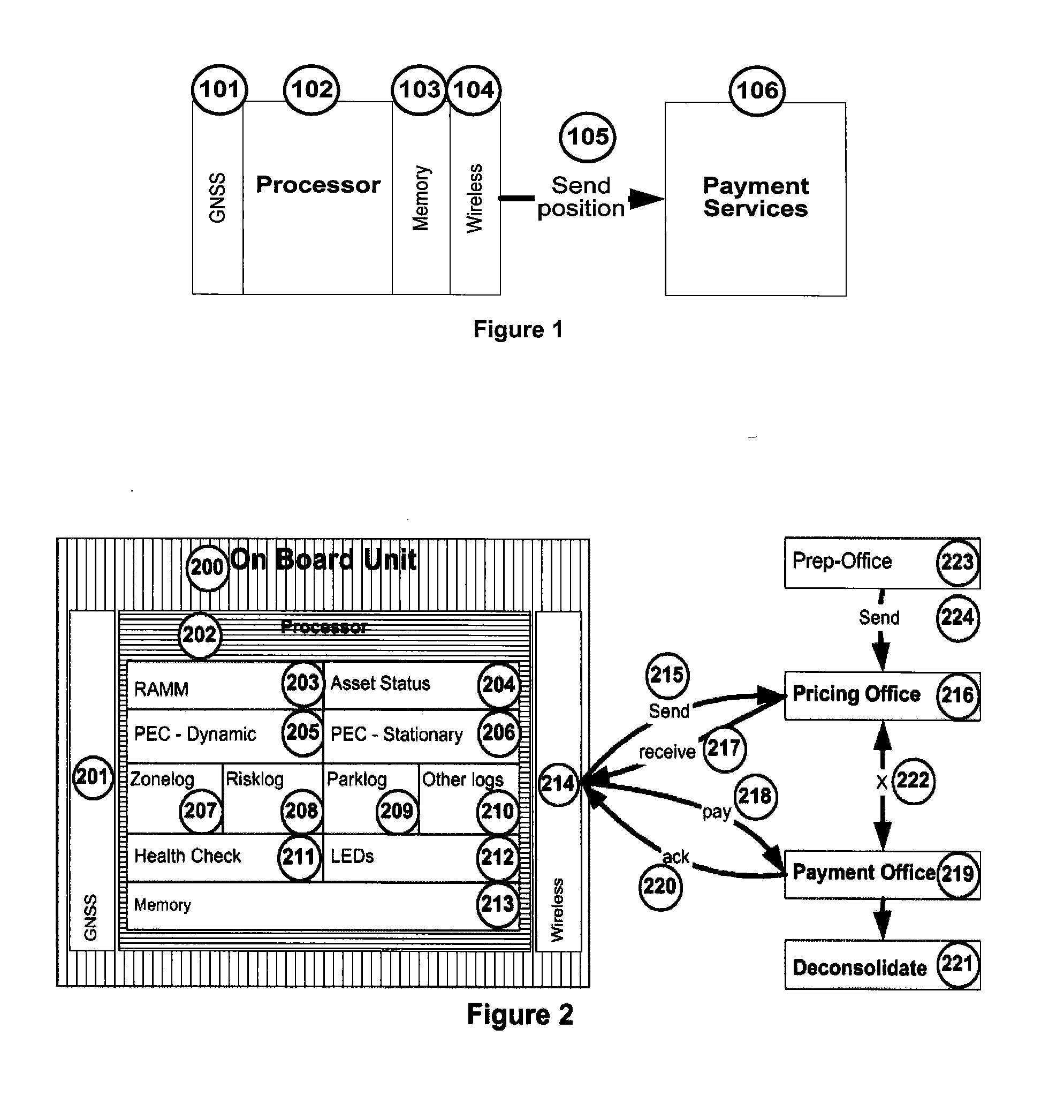
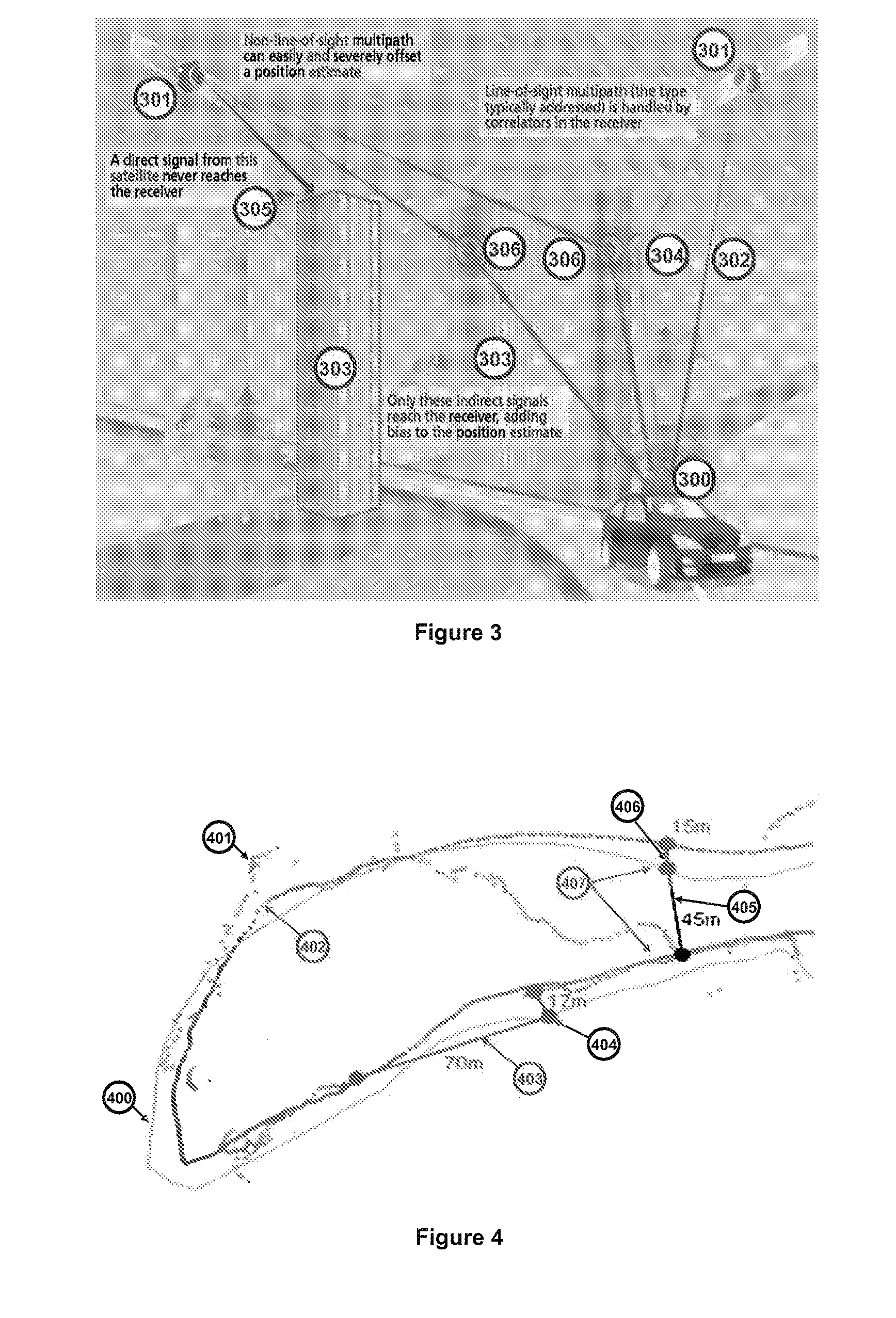
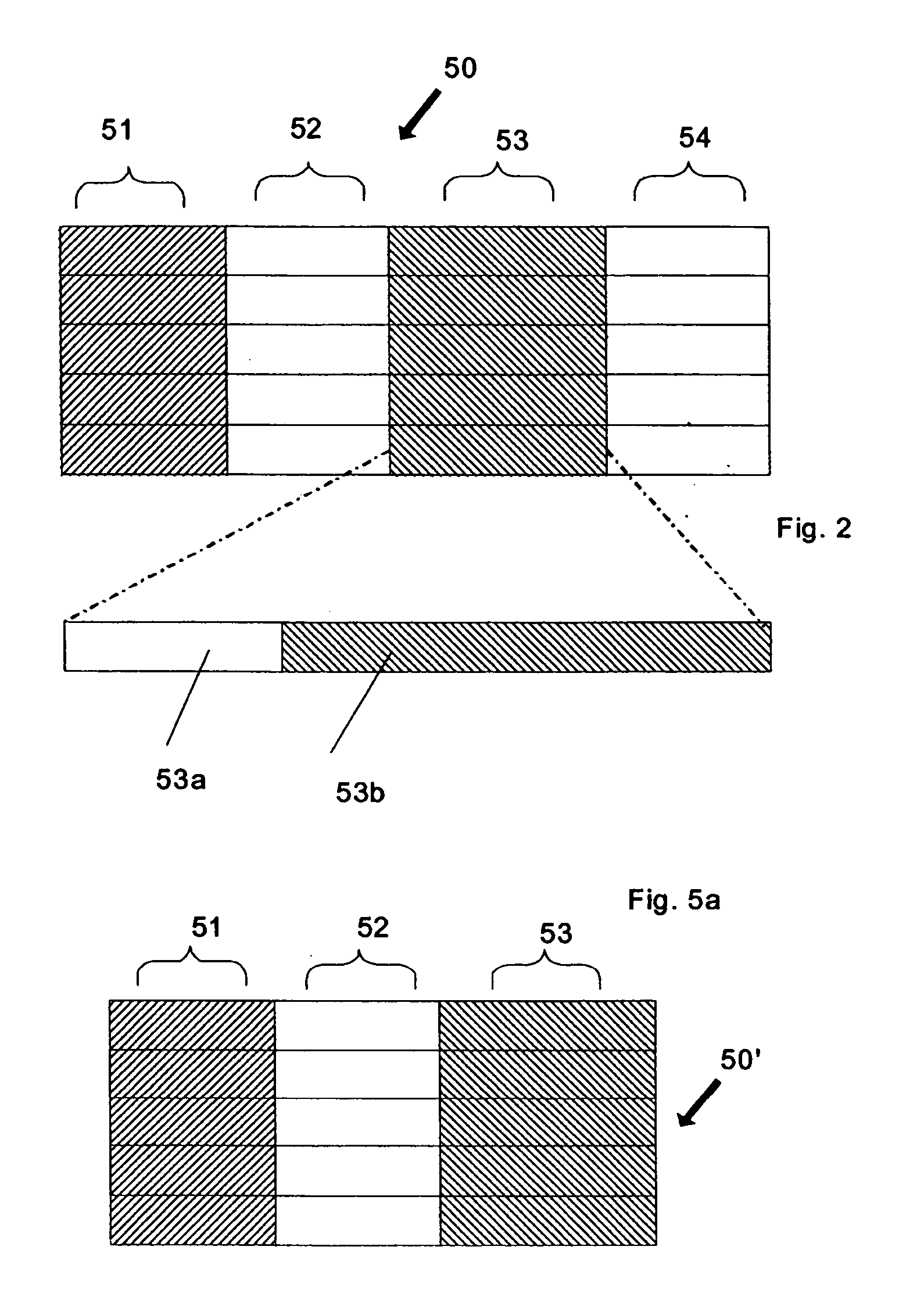
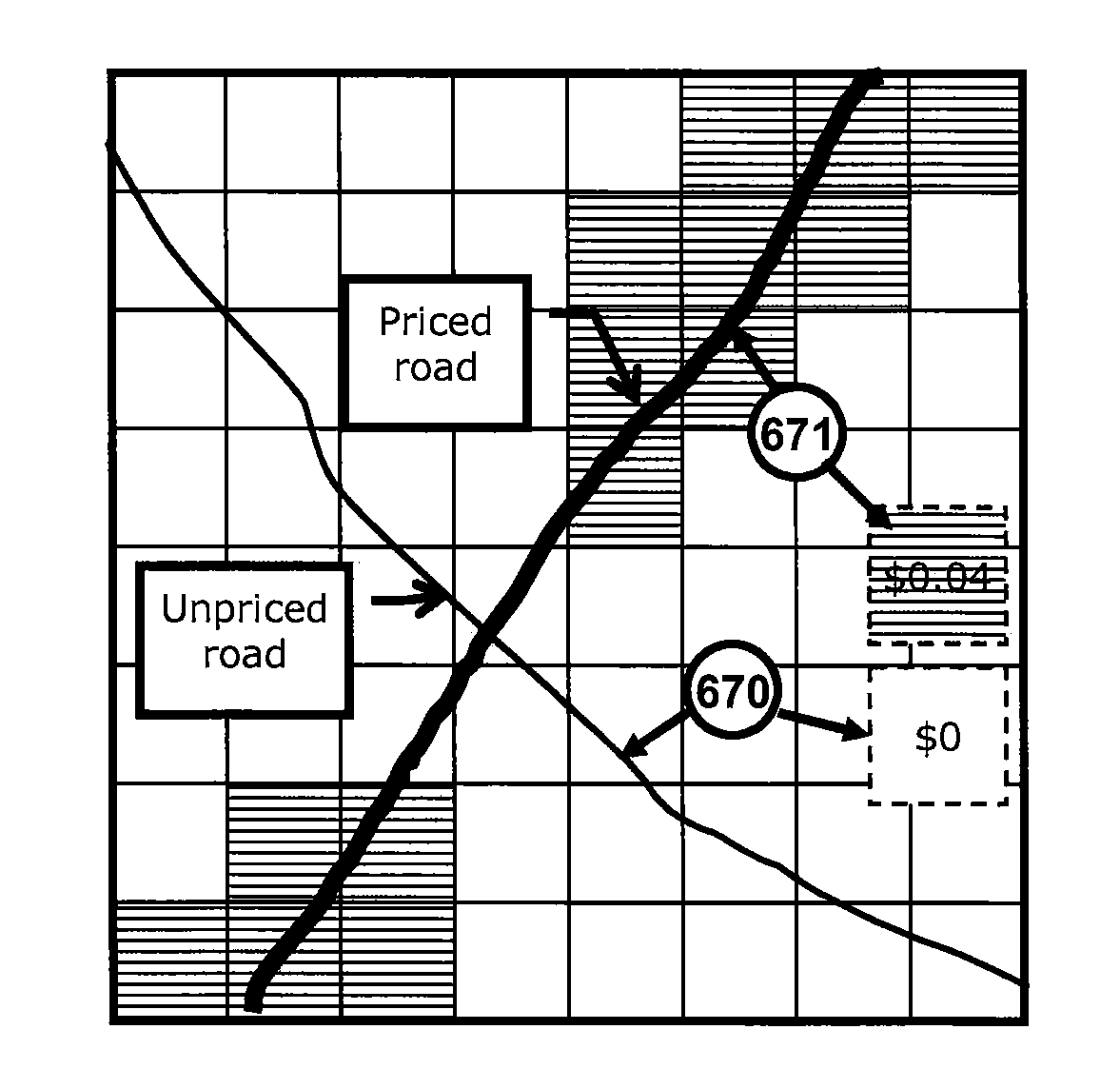
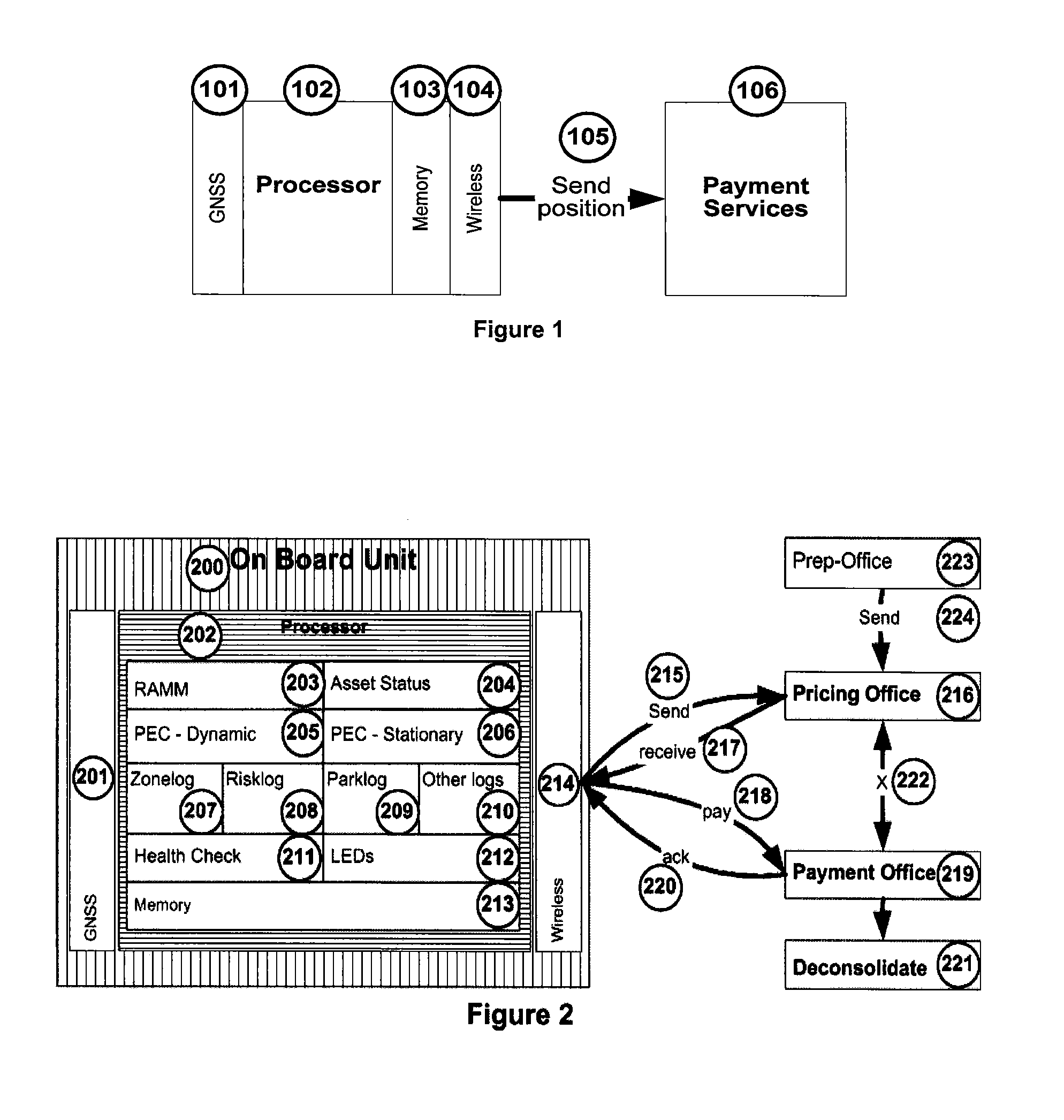
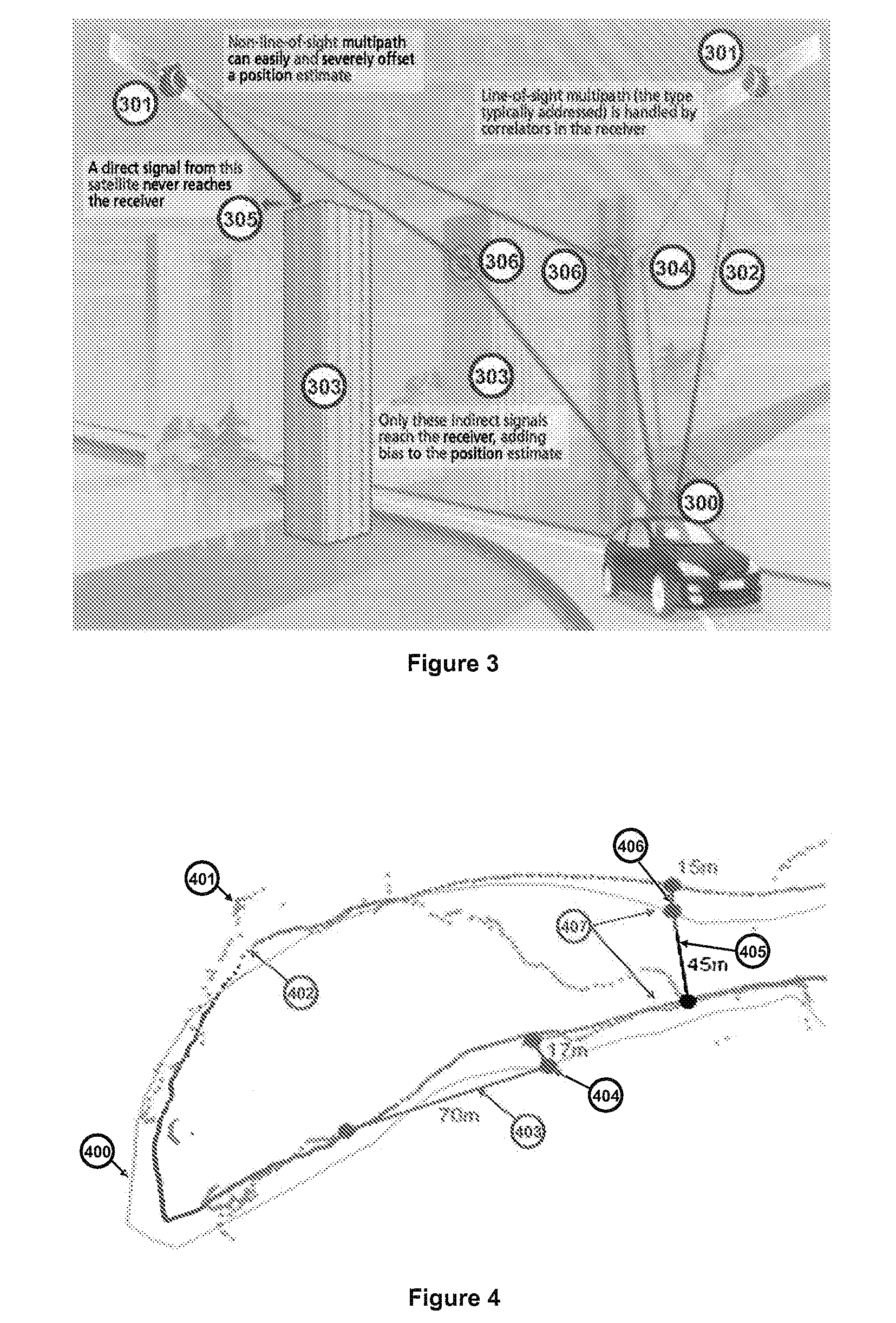
Private, auditable vehicle positioning system and on-board unit for same
ActiveUS20070225912A1Improve position estimateReduce errorsInstruments for road network navigationTicket-issuing apparatusPaymentCost effectiveness
This invention relates to a system and method to generate a private, auditable, evidentiary quality record of the location-history of an asset or person. This invention addresses ten critical improvements over existing systems that are proposed or used for metering for payment services for tolling roads, parking or pay-as-you-drive insurance, namely, cost-effective location accuracy in harsh signal environments, evidentiary assurance of location estimation, handling of dynamic and stationary positioning in a single device, high-ratio compression for a set of stationary positions in urban canyon, high-ratio compression for a dynamic tracklog in urban canyon, high-ratio compression for a set of asset motion behaviors, a method of remote device health check, including anti-tampering, removal of residual price assignment errors, anonymous use without on-board maps, and a method of deconsolidating payments to multiple payees with multiple payment regimes. This system can be applied to road-pricing, congestion-pricing, metered-by-the-minute parking and pay-as-you-drive insurance, incorporating privacy management, and legal admissibility of the evidentiary record. This same device can also be applied to vehicular fleets, military ordinance, or other location audits for assets whether motorized or not, as might be needed in evidence of contract fulfillment or other forms of non-realtime geofencing audits.
Owner:SKYMETER
Method and system for digital privacy management
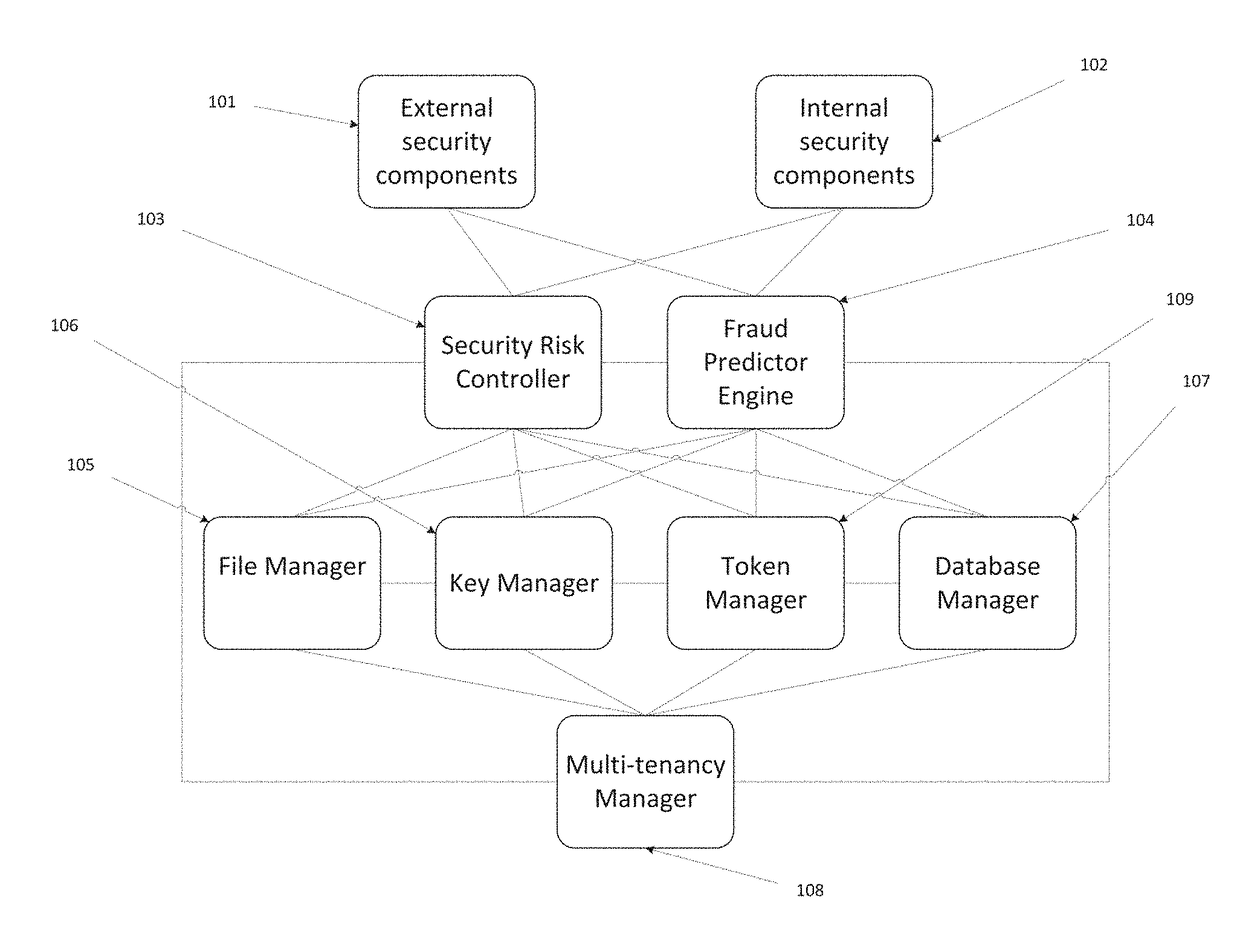
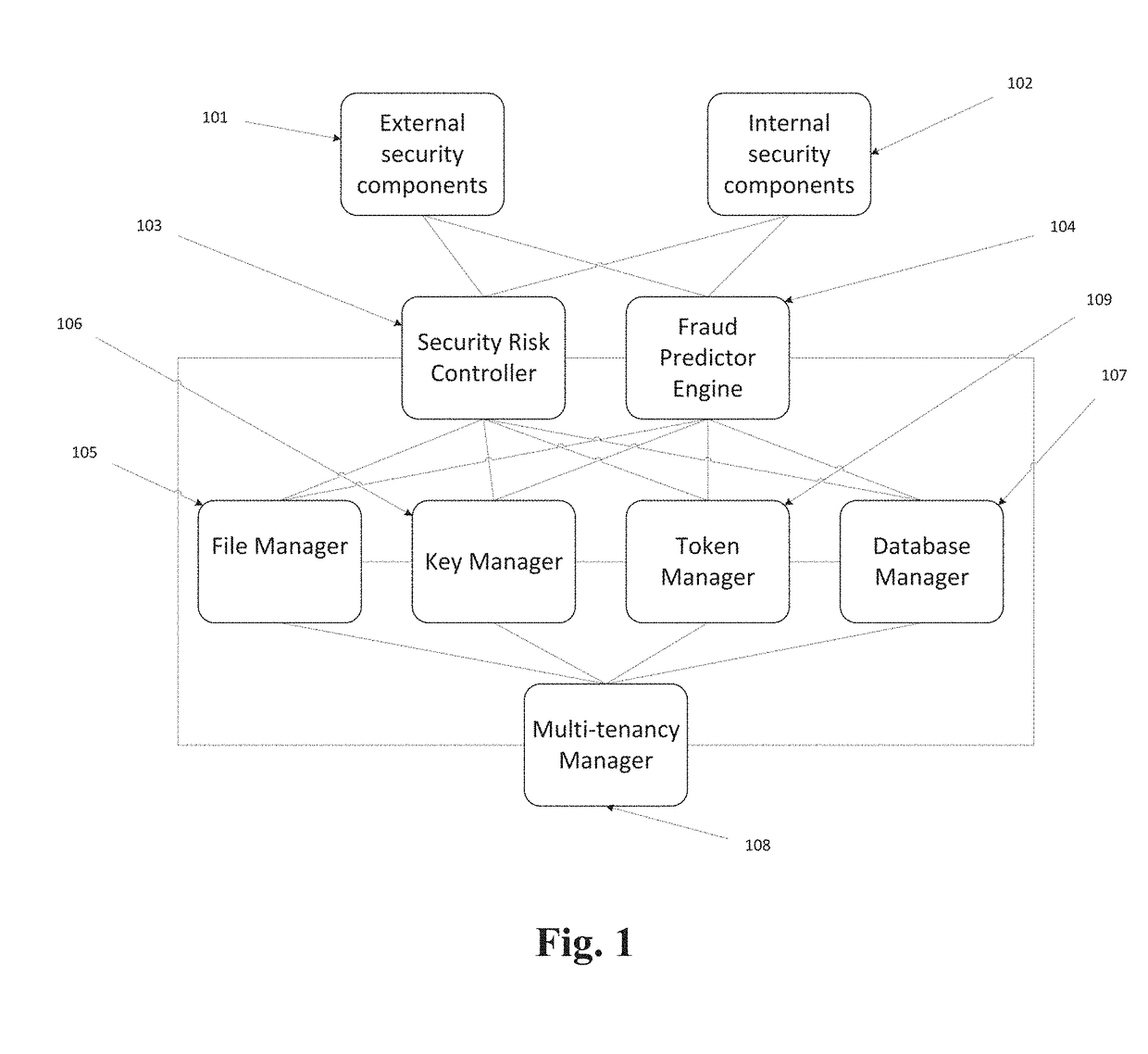
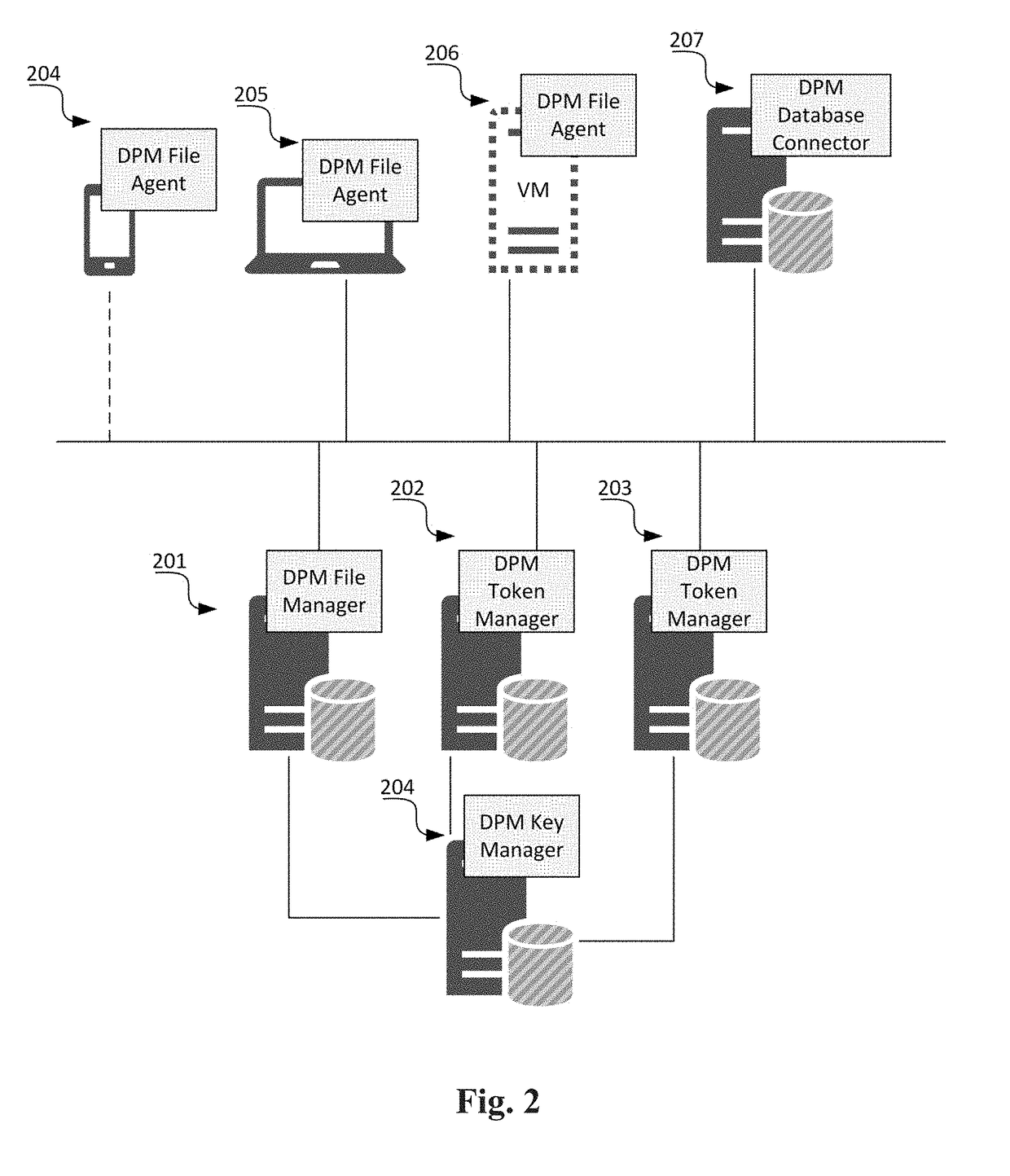
Data Privacy Manager (DPM) solution includes a number of different components performing data security procedures (encryption, masking, tokenization, Anonymization, etc.) at the folder, file, email, application, database and column levels. These include components such as Key Manager, File Manager, File Agent, Email Agent, Database Manager, Database Connector, the Token Manager, Security Risk Controller and Fraud Predictor. All these components can be managed through a management console.
Owner:ADHAR VIRESHWAR K
Online privacy management
ActiveUS8261362B2Simple processDigital data processing detailsAnalogue secracy/subscription systemsData streamClient-side scripting
A privacy management system (PMS) is disclosed for a Chief Privacy Officer (CPO) or other user to use in monitoring and / or controlling in realtime the flow of data (e.g., outflow) about the user and his / her online experience. The PMS may provide a dashboard displaying a whitelist and / or blacklist indicating what destinations / sources are blocked or allowed. The PMS includes browser-client scripting code and may also include a PMS-certified verification icon for display on webpages being monitored / controlled in realtime by the PMS.
Owner:ENSIGHTEN
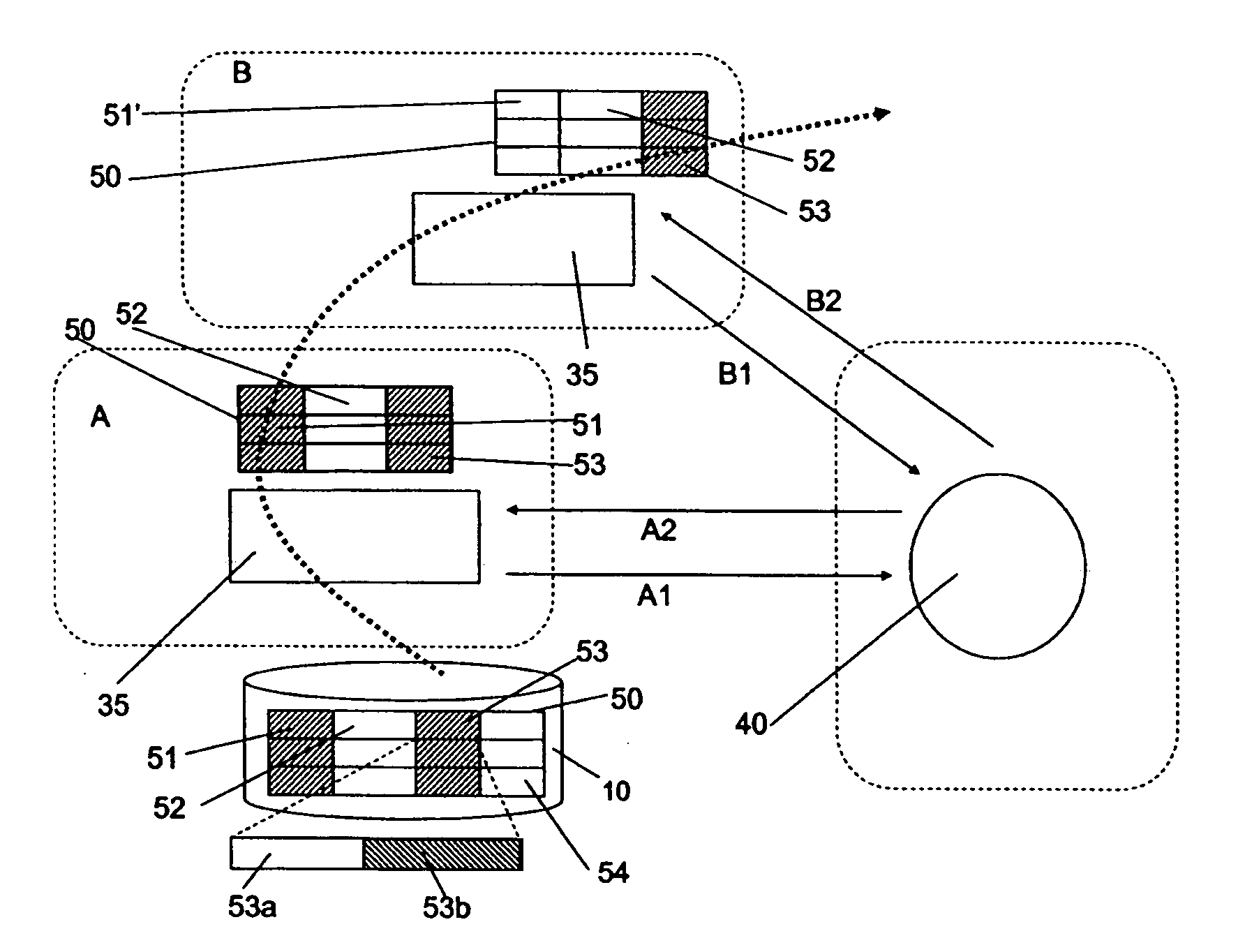
Data privacy management system and method
InactiveUS20050251865A1Minimize impactKey distribution for secure communicationPublic key for secure communicationObfuscationInternet privacy
A data privacy management system includes a data repository, a private data mediating system and a privacy manager. The data repository stores private data items in an obfuscated form. Each private data item has associated privacy policy data a defining conditions to be met to ensure the privacy of the data item. A private data mediating system communicates with the privacy manager to obtain de-obfuscated private data items that are extracted from the data repository 10. De-obfuscation of the data 51, 53 is subject to satisfaction of the privacy manager that the respective conditions ensuring privacy of the data item are met.
Owner:HEWLETT PACKARD DEV CO LP
Private, auditable vehicle positioning system and on-board unit for same
ActiveUS8140265B2Reduce errorsImprove positionInstruments for road network navigationTicket-issuing apparatusPaymentToll road
This invention relates to a system and method to generate a private, auditable, evidentiary quality record of the location-history of an asset or person. This invention addresses ten critical improvements over existing systems that are proposed or used for metering for payment services for tolling roads, parking or pay-as-you-drive insurance, namely, cost-effective location accuracy in harsh signal environments, evidentiary assurance of location estimation, handling of dynamic and stationary positioning in a single device, high-ratio compression for a set of stationary positions in urban canyon, high-ratio compression for a dynamic tracklog in urban canyon, high-ratio compression for a set of asset motion behaviors, a method of remote device health check, including anti-tampering, removal of residual price assignment errors, anonymous use without on-board maps, and a method of deconsolidating payments to multiple payees with multiple payment regimes. This system can be applied to road-pricing, congestion-pricing, metered-by-the-minute parking and pay-as-you-drive insurance, incorporating privacy management, and legal admissibility of the evidentiary record. This same device can also be applied to vehicular fleets, military ordinance, or other location audits for assets whether motorized or not, as might be needed in evidence of contract fulfillment or other forms of non-realtime geofencing audits.
Owner:SKYMETER
Privacy management method and apparatus
InactiveUS20060047605A1Computer security arrangementsPayment architectureInternet privacyAuthorization
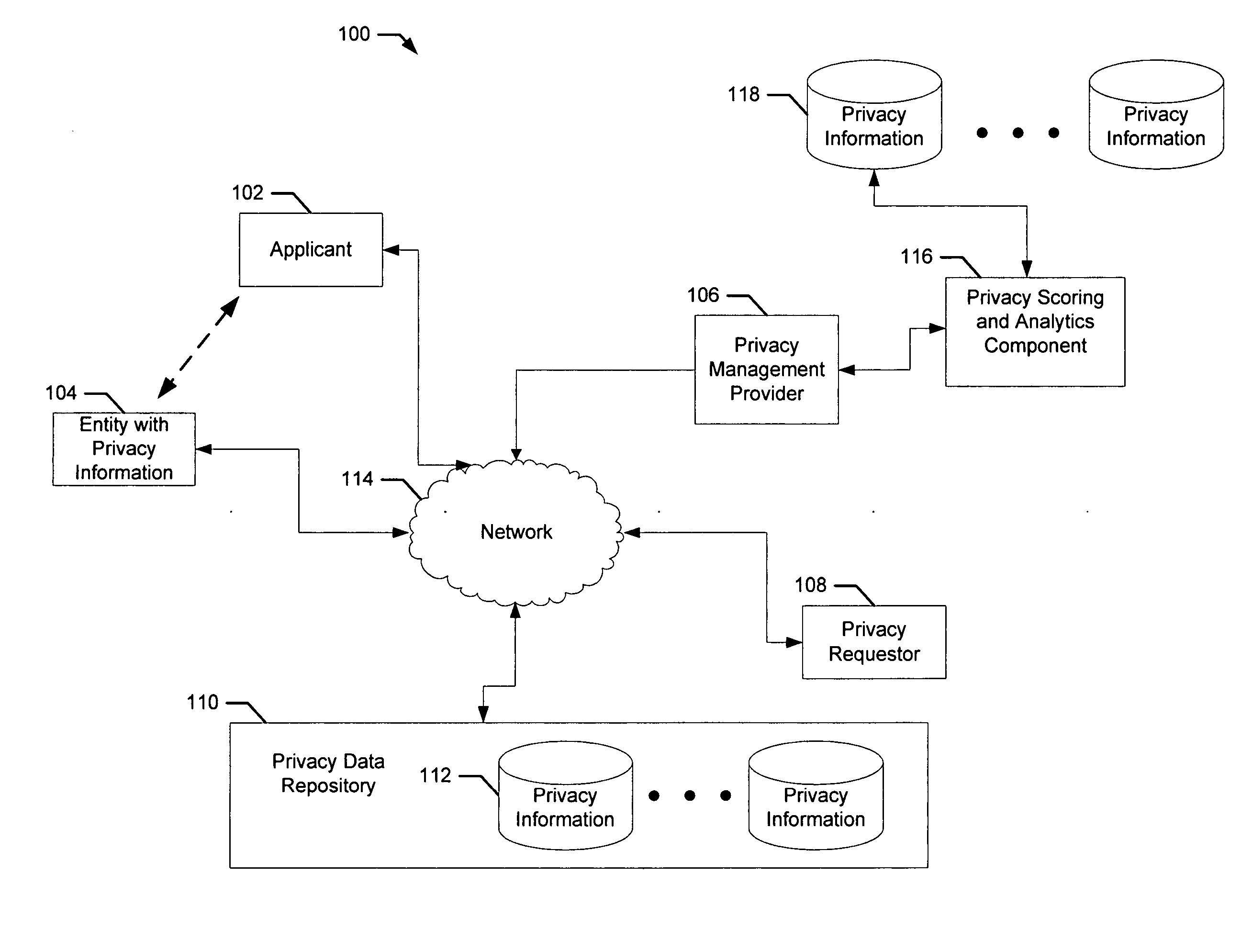
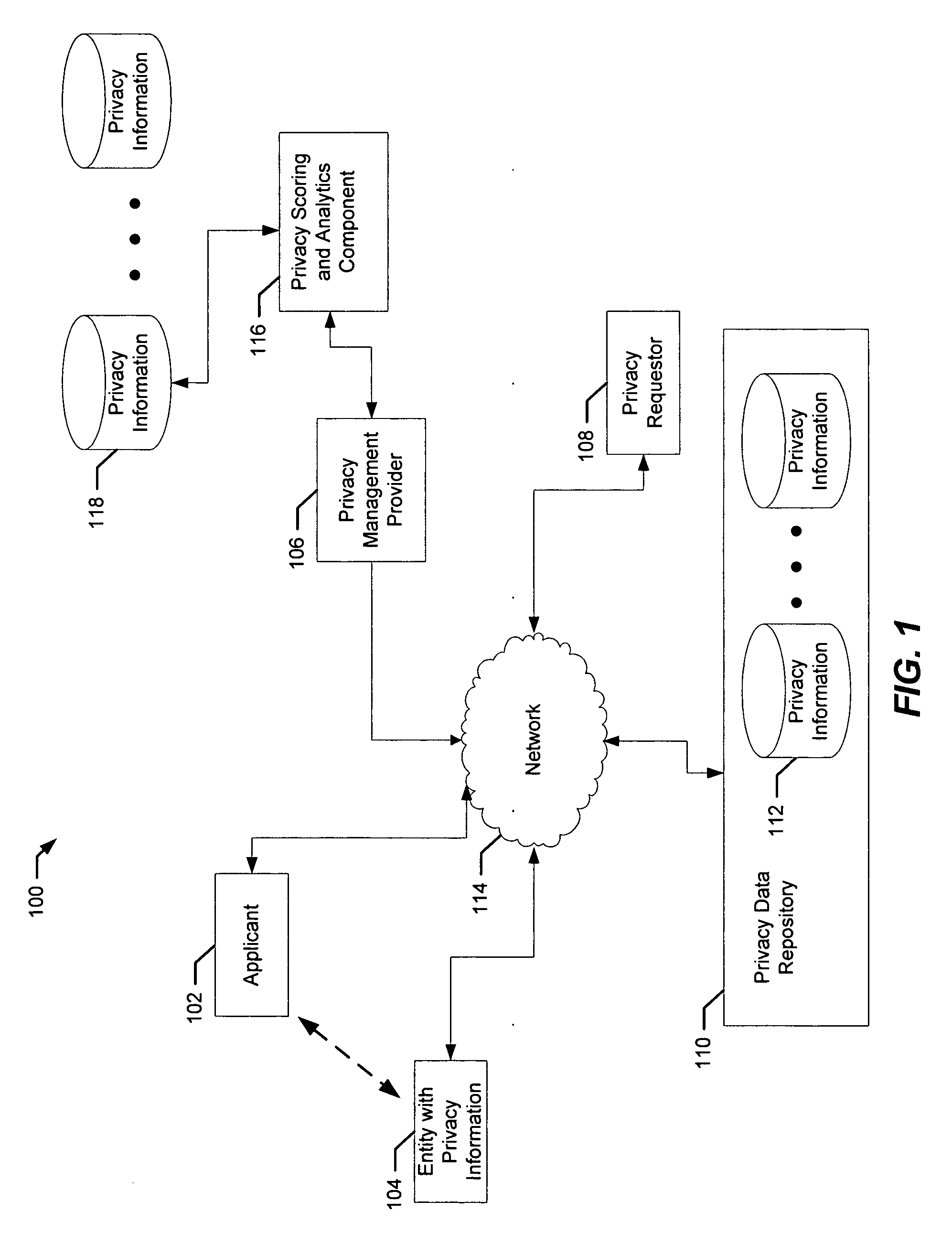
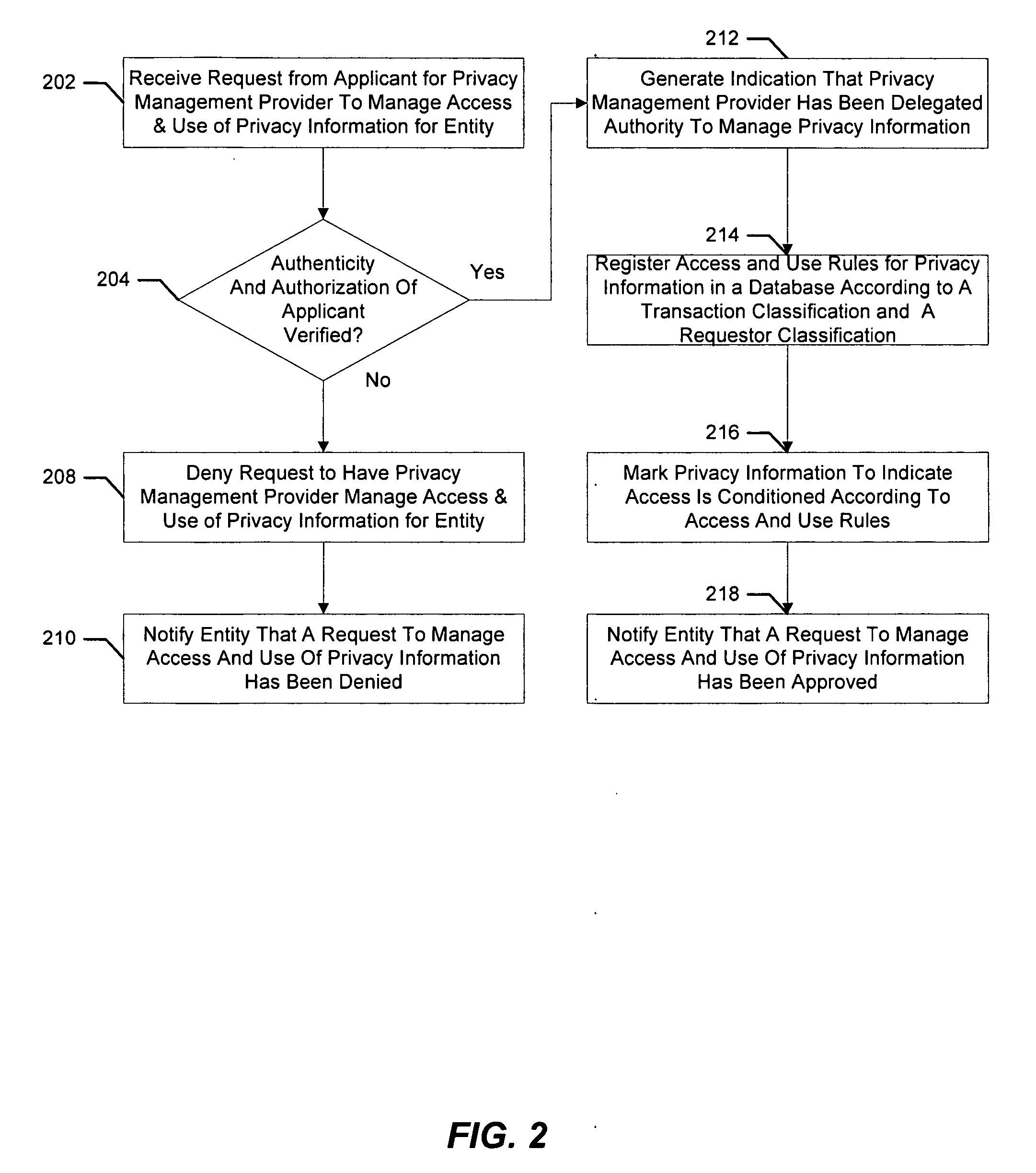
A computer implemented method describes managing privacy information. Initially, a request is received from a requester for the privacy information of an entity. The request is often the result of an applicant submitting a form or application to the requester. Next, implementations of the present invention create a privacy transaction in a database for the privacy information including one or more identity qualities from the applicant and one or more characteristics for the submission. These identity qualities, characteristics for the submission and other pieces of information are used to score the privacy transaction according to the one or more identity qualities from the applicant and the one or more characteristics for the submission. The score provides a confidence level indicative of the authenticity and authorization associated with the submission.
Owner:TRUSTEDID INC
Online Privacy Management
ActiveUS20130276136A1Simple processDigital data processing detailsAnalogue secracy/subscription systemsDashboardAnalysis data
A privacy management system (PMS) is disclosed for a Chief Privacy Officer (CPO) or other user to use in monitoring and / or controlling in realtime the flow of data (e.g., outflow) about the user and his / her online experience. The PMS may employ pattern recognition software to evaluate analytics data and potentially block private information from being sent within the analytics data. The PMS may provide a dashboard displaying a whitelist and / or blacklist indicating what destinations / sources are blocked or allowed as well as private information settings indicating what types of private information should be blocked. The PMS includes browser-client scripting code and may also include a PMS-certified verification icon and / or lock and unlock icons for display on webpages being monitored / controlled in realtime by the PMS.
Owner:ENSIGHTEN
Data privacy management systems and methods
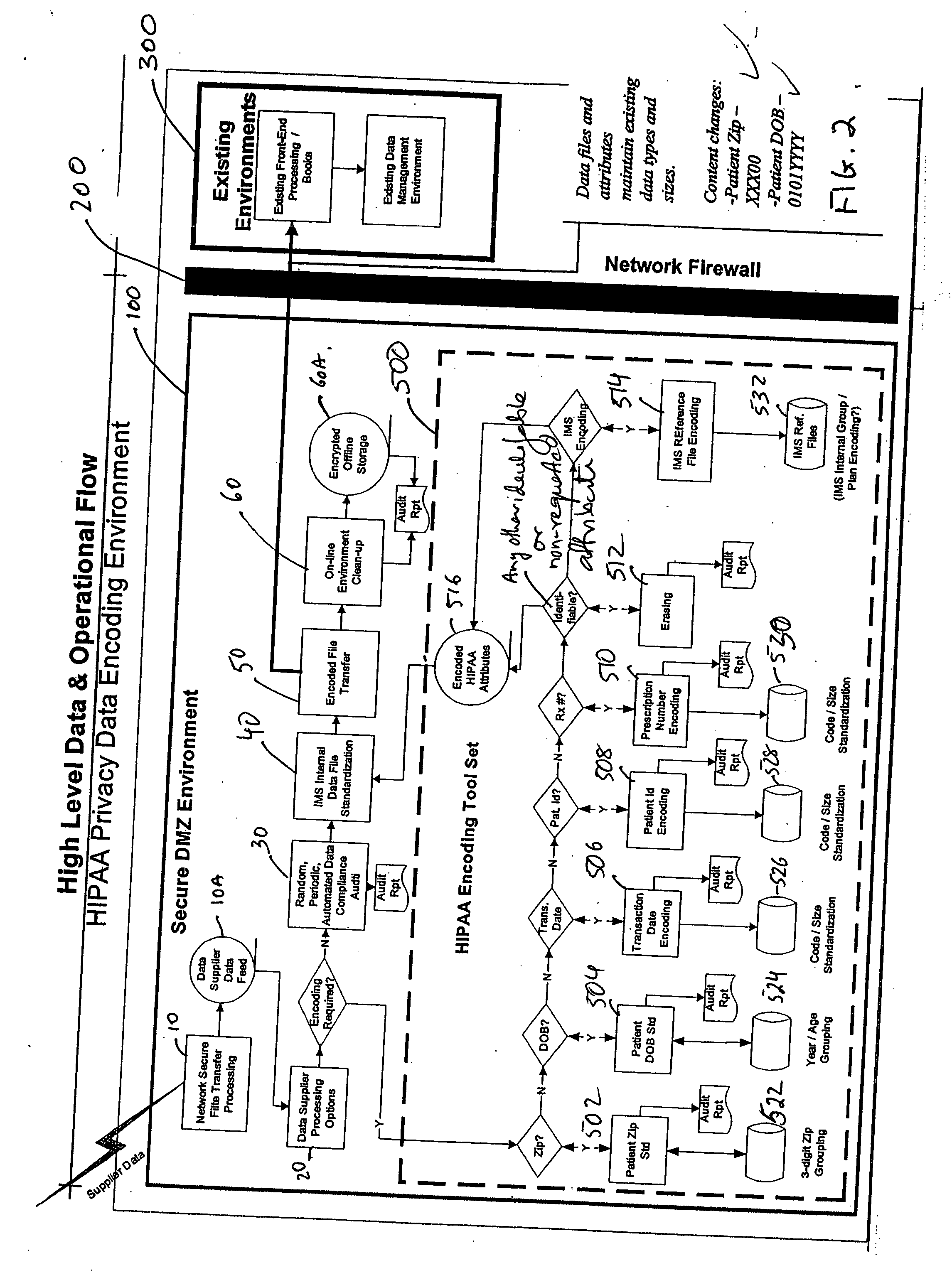
InactiveUS20050065824A1Ensure compliancePatient personal data managementOffice automationInternet privacyManagement process
Owner:IMS SOFTWARE SERVICES
Privacy management of personal data
InactiveUS20050039031A1Public key for secure communicationUser identity/authority verificationComputer scienceEncryption
When sending personal data to a recipient, the data owner encrypts the data using both a public data item provided by a trusted party and an encryption key string formed using at least policy data indicative of conditions to be satisfied before access is given to the personal data. The encryption key string is typically also provided to the recipient along with the encrypted personal data. To decrypt the personal data, the recipient sends the encryption key string to the trusted party with a request for the decryption key. The trusted party determines the required decryption key using the encryption key string and private data used in deriving its public data, and provides it to the requesting recipient. However, the decryption key is either not determined or not made available until the trusted party is satisfied that the associated policy conditions have been met by the recipient.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Privacy management for well-being monitoring
InactiveUS20080294018A1Efficient captureData processing applicationsDiagnostics using lightInternet privacyData management
A method for monitoring physiological conditions of a particular individual, while providing unobtrusively implemented controls for managing the privacy of the particular individual and their physiological data, including providing a set of personal data regarding the particular individual, the personal data including privacy settings data, wellness parameter data, or semantic data; determining initial values for the wellness parameters for the particular individual; unobtrusively acquiring physiological data of the particular individual from an image captured during an image capture event, wherein the image capture and image data management is in accordance with a privacy setting; analyzing the physiological data using wellness parameters to assess physiological conditions of the particular individual; and providing a report of the physiological conditions of the particular individual, where the reporting access is limited by privacy controls based on the privacy setting.
Owner:EASTMAN KODAK CO
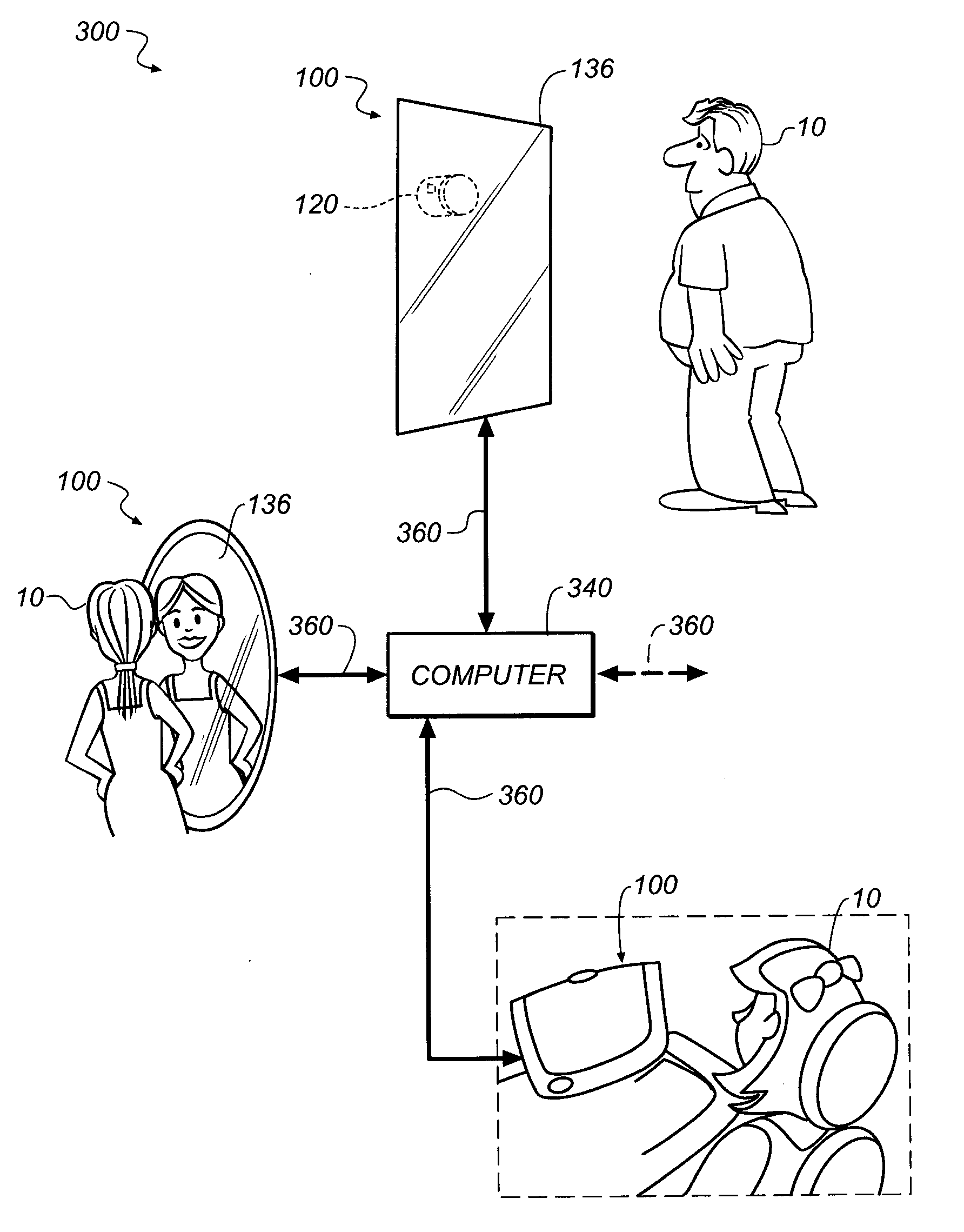
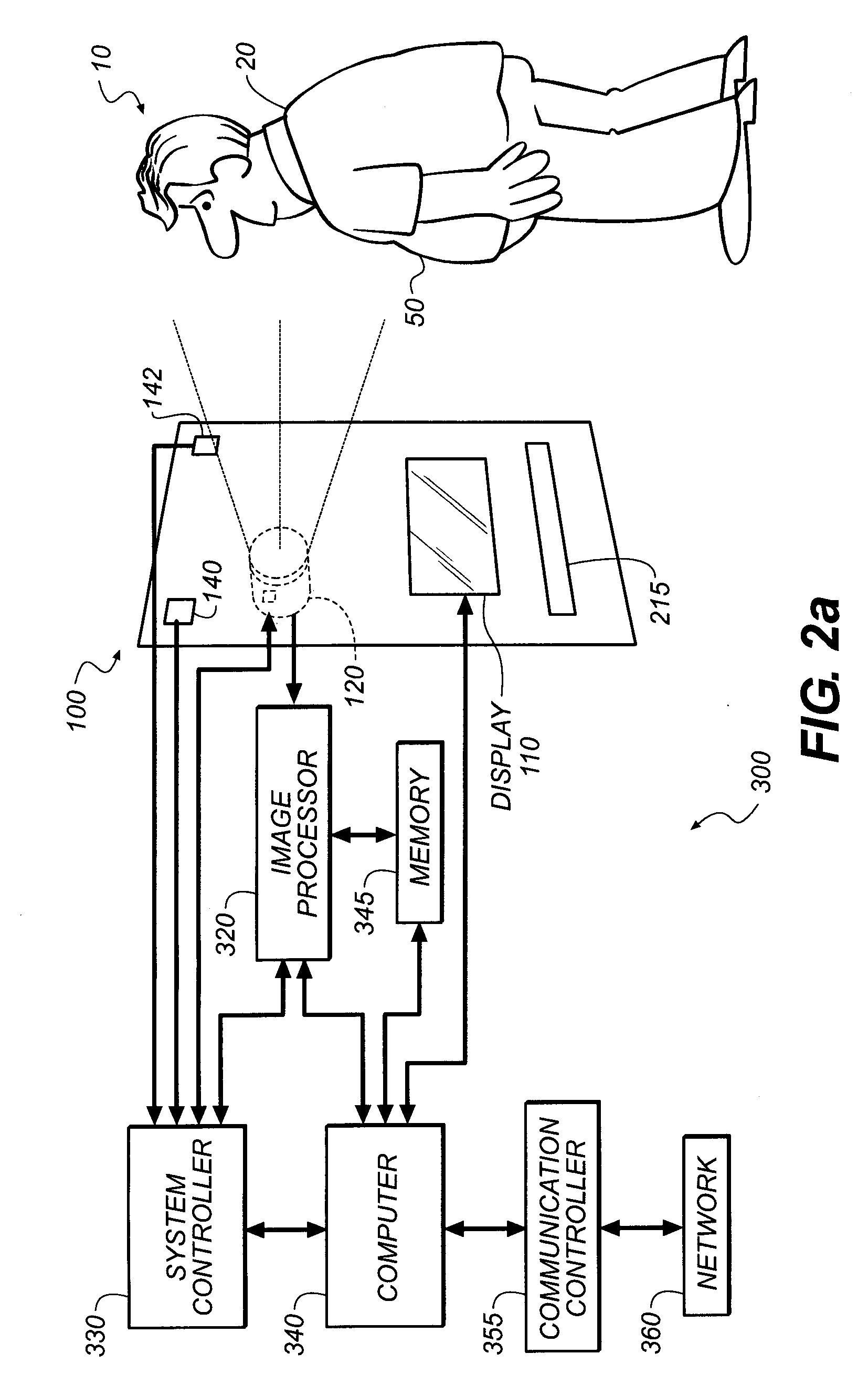
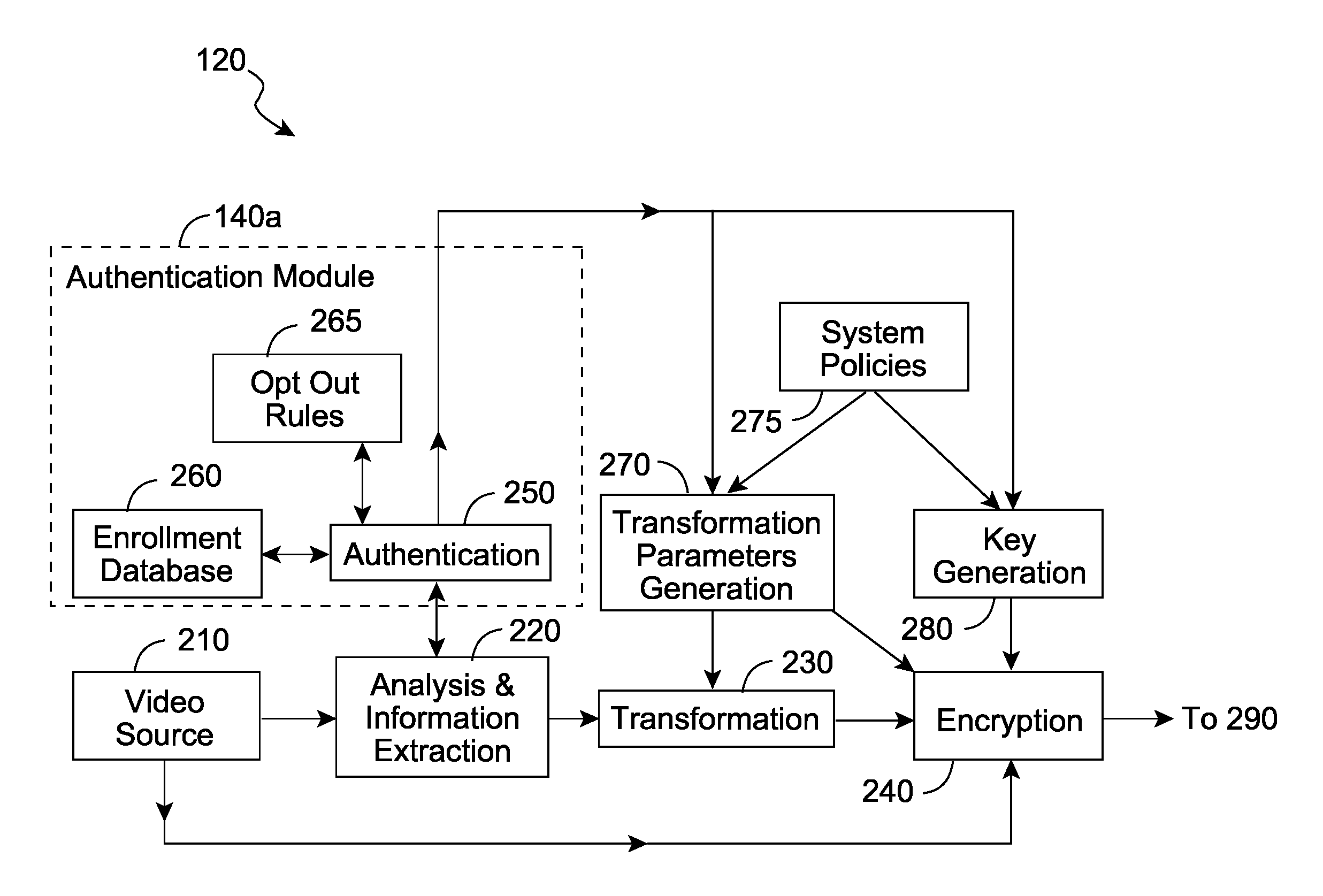
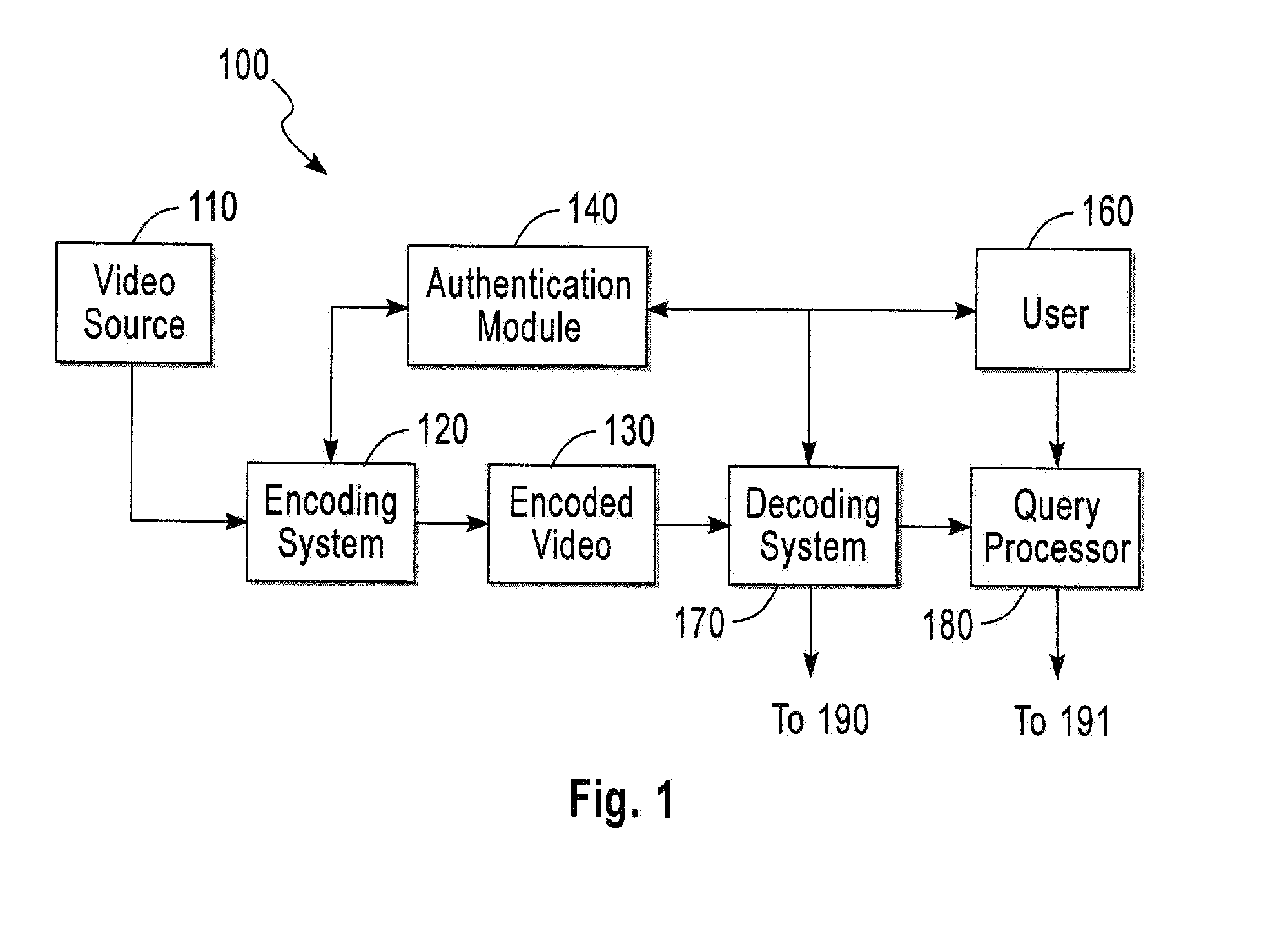
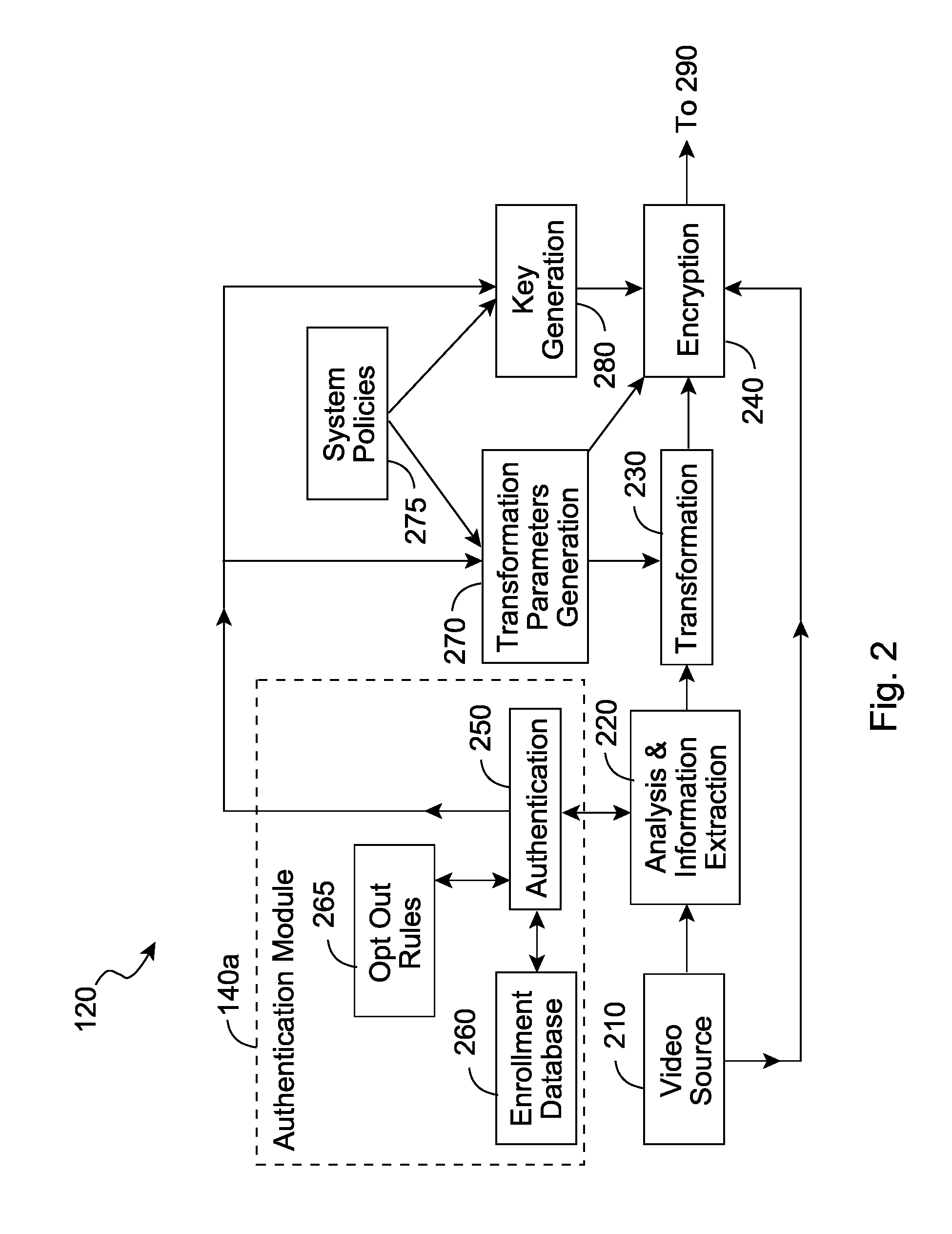
Privacy management in imaging system
The system and method obscures descriptive image information about one or more images. The system comprises a selector for selecting the descriptive image information from one or more of the images, a transformer that transforms the descriptive information into a transformed state, and an authorizer that provides authorization criteria with the image. In a preferred embodiment, the transformed state is the respective image encoded with the descriptive information. The descriptive information can be obscured so that the descriptive information in the transformed state can be decoded only if one or more authorization inputs satisfy the authorization criteria.
Owner:IBM CORP
Privacy Management Policy Hub
ActiveUS20090254511A1Customer relationshipDigital data processing detailsInternet privacyPrivacy management
Owner:ORACLE INT CORP
Privacy management
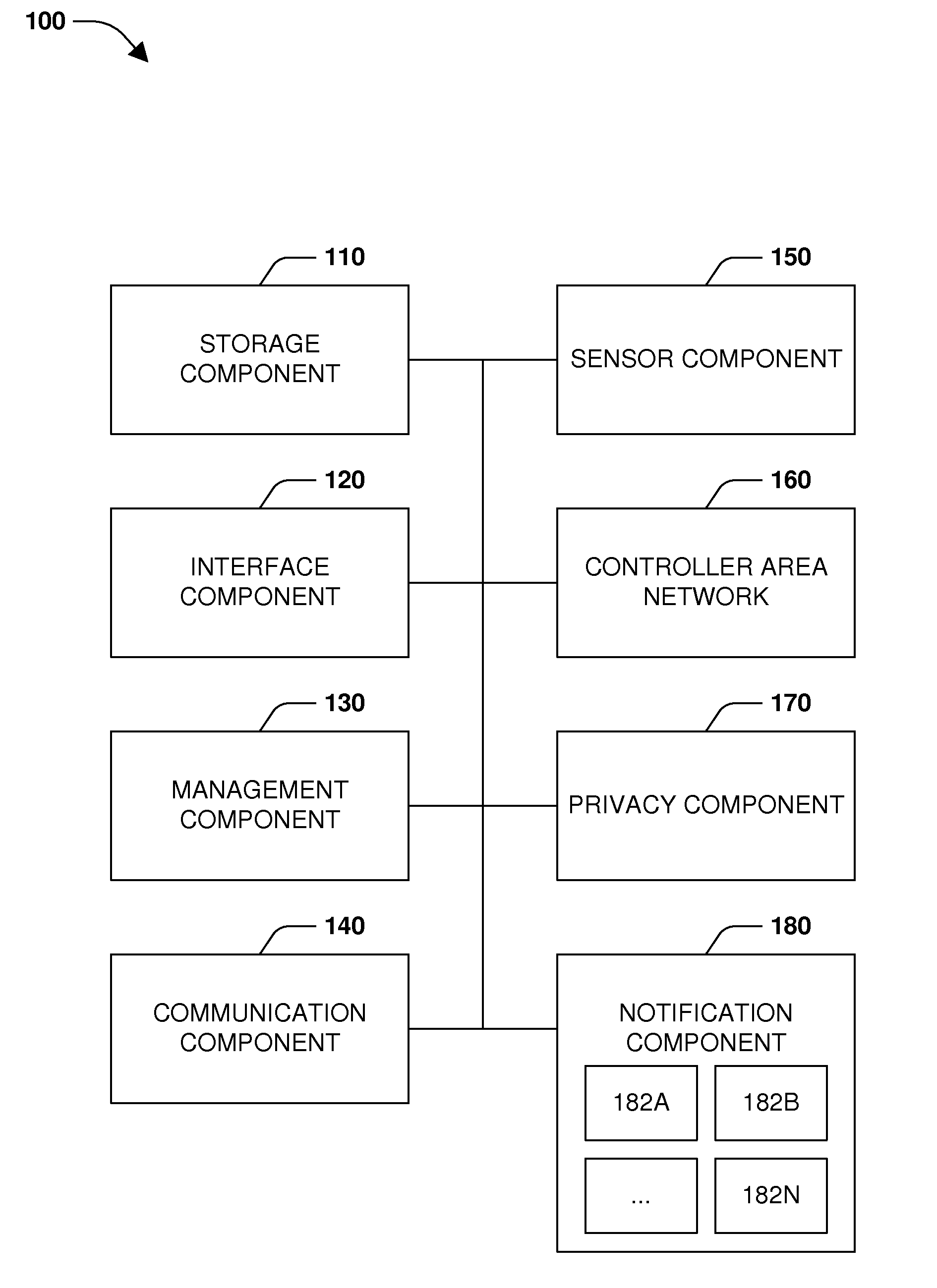
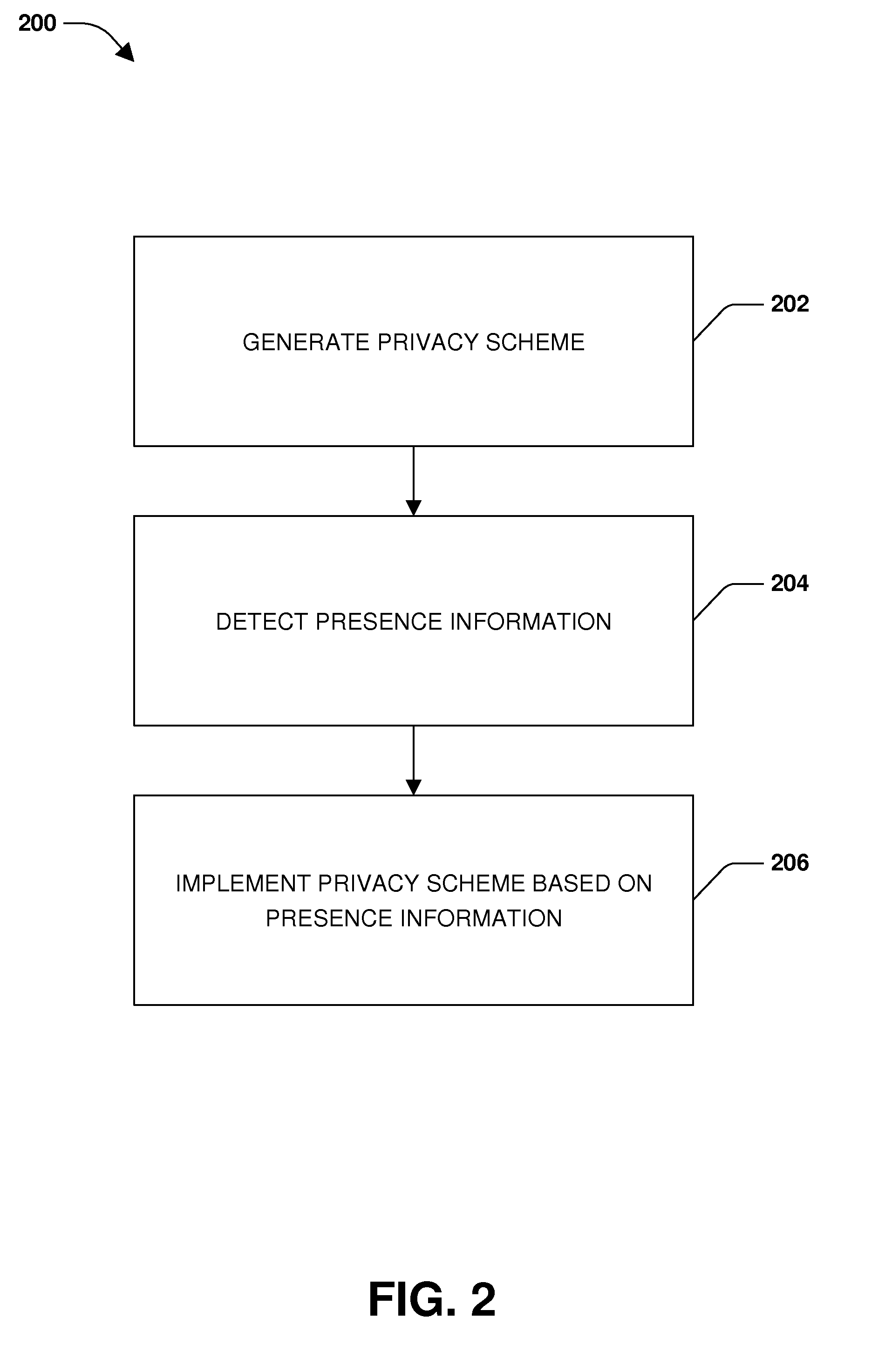
ActiveUS20160059864A1Improve securityDigital data processing detailsSubstation equipmentInternet privacyPrivacy management
One or more embodiments of techniques or systems for privacy management are provided herein. In one or more embodiments, privacy management may be provided by adjusting the way a system provides notifications, handles communications, or executes applications based on the presence or positioning of one or more occupants within a vehicle. In other words, a vehicle may provide notifications in a first manner when merely a driver is present but provide notifications in a second manner (e.g., different than the first manner) when an additional occupant is detected. Sensors may be utilized to detect the presence or positioning of occupants and communications or applications may be managed accordingly. In this manner, privacy management is provided, thus enhancing security of applications or communications utilized by occupants of a vehicle, such as a driver, for example.
Owner:HONDA MOTOR CO LTD
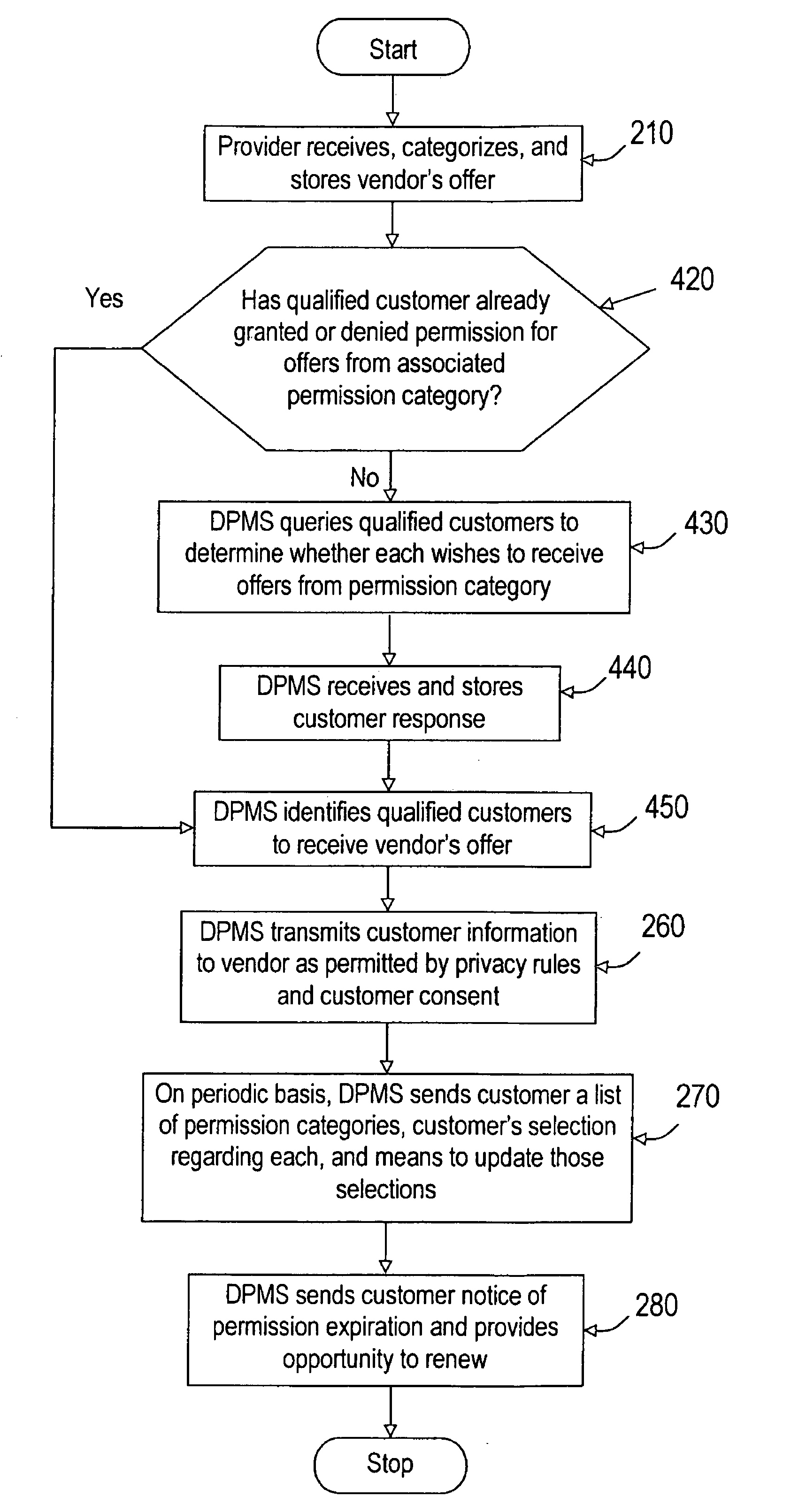
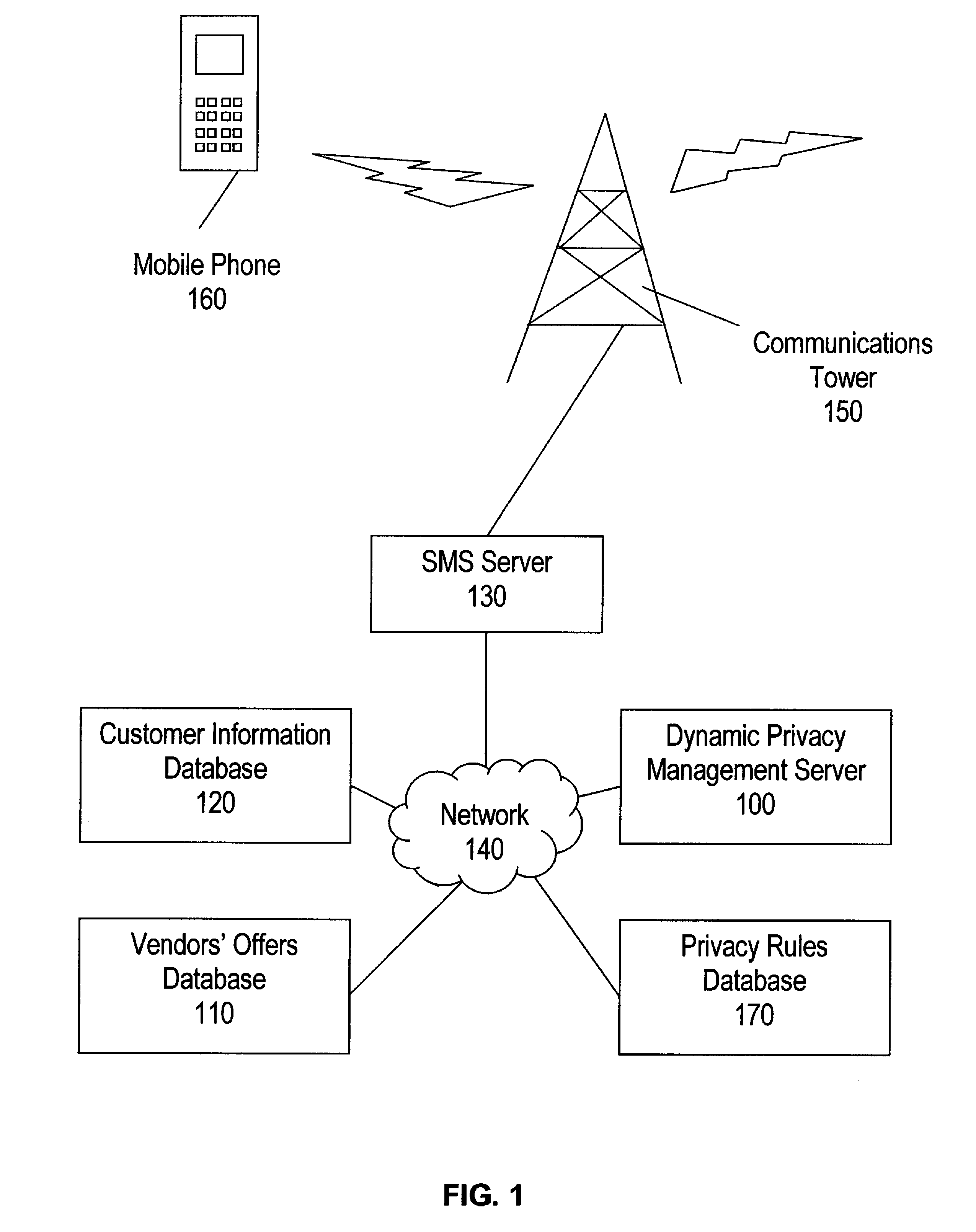
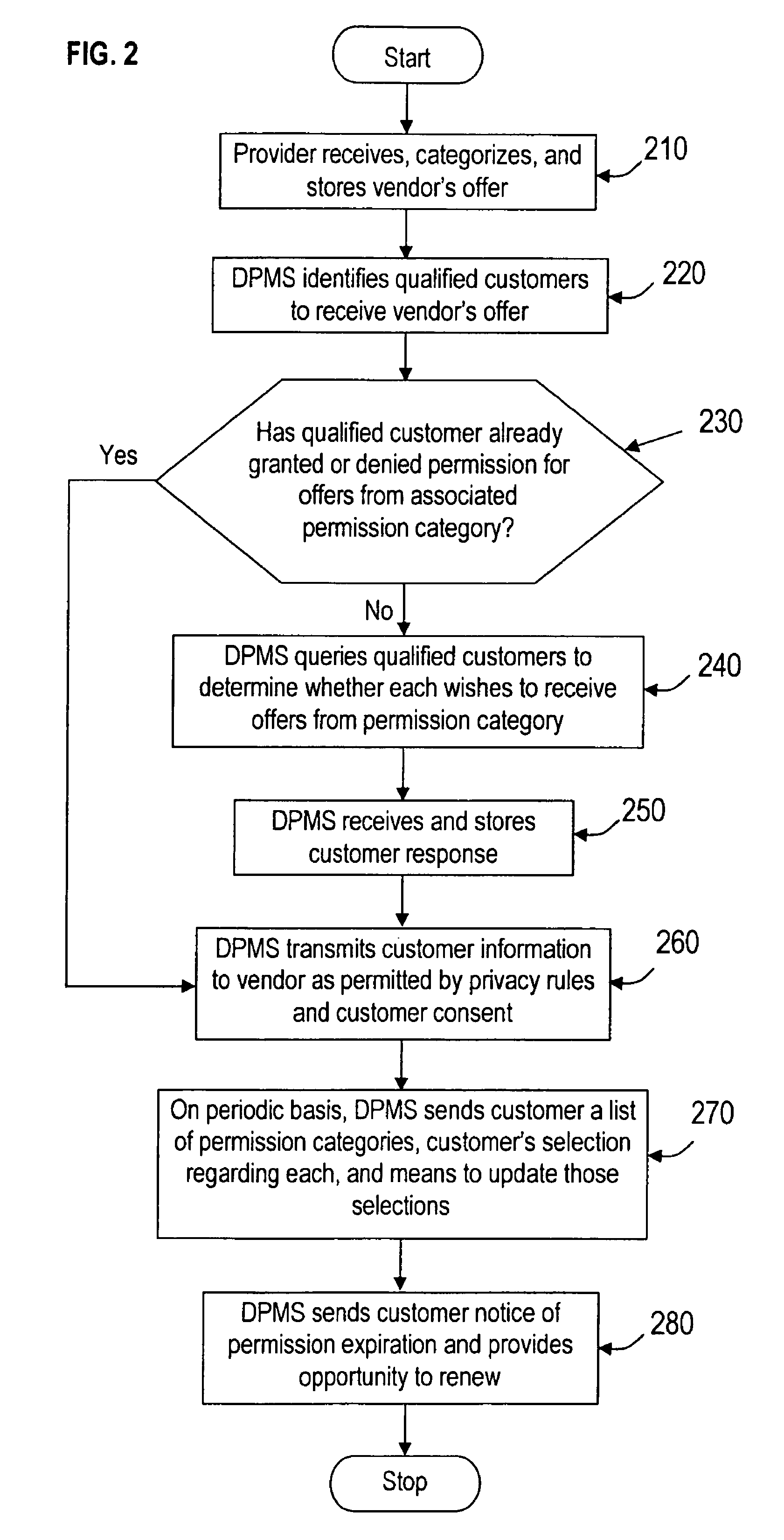
Systems and methods for dynamic privacy management
Systems and methods for dynamic privacy management are disclosed. In some embodiments, a customer may accept or reject using the text-messaging feature of his mobile phone offers of discounted goods or services from a partner in exchange for the customer's consent allowing the vendor to release the customer's personal information to the vendor. By controlling dissemination of his personal information in this way, a customer may tailor his own dynamic privacy agreement with the provider in an informal manner and with very little effort. The customer may also control the amount of spam he receives from vendors by specifying the types of offers he is or is not receptive to.
Owner:T MOBILE INNOVATIONS LLC
Method, Apparatus, and Computer Program Product for Privacy Management
InactiveUS20090328135A1TransmissionProgram/content distribution protectionInternet privacyPrivacy management
An apparatus for privacy management may include a processor. The processor may be configured to access one or more privacy options. In this regard, each privacy option may be configured to provide members of one or more groups access to content. The processor may also be configured to provide for selection of a privacy option in association with the content. Associated methods and computer program products may also be provided.
Owner:CORE WIRELESS LICENSING R L
Online Privacy Management
ActiveUS20120284801A1Simple processDigital data processing detailsAnalogue secracy/subscription systemsData streamClient-side scripting
Owner:CHEQ AI TECH (2018) LTD
Telephone system, apparatus, and method for providing enhanced privacy features
InactiveUS20150023485A1Improve privacySpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingThe InternetApplication software
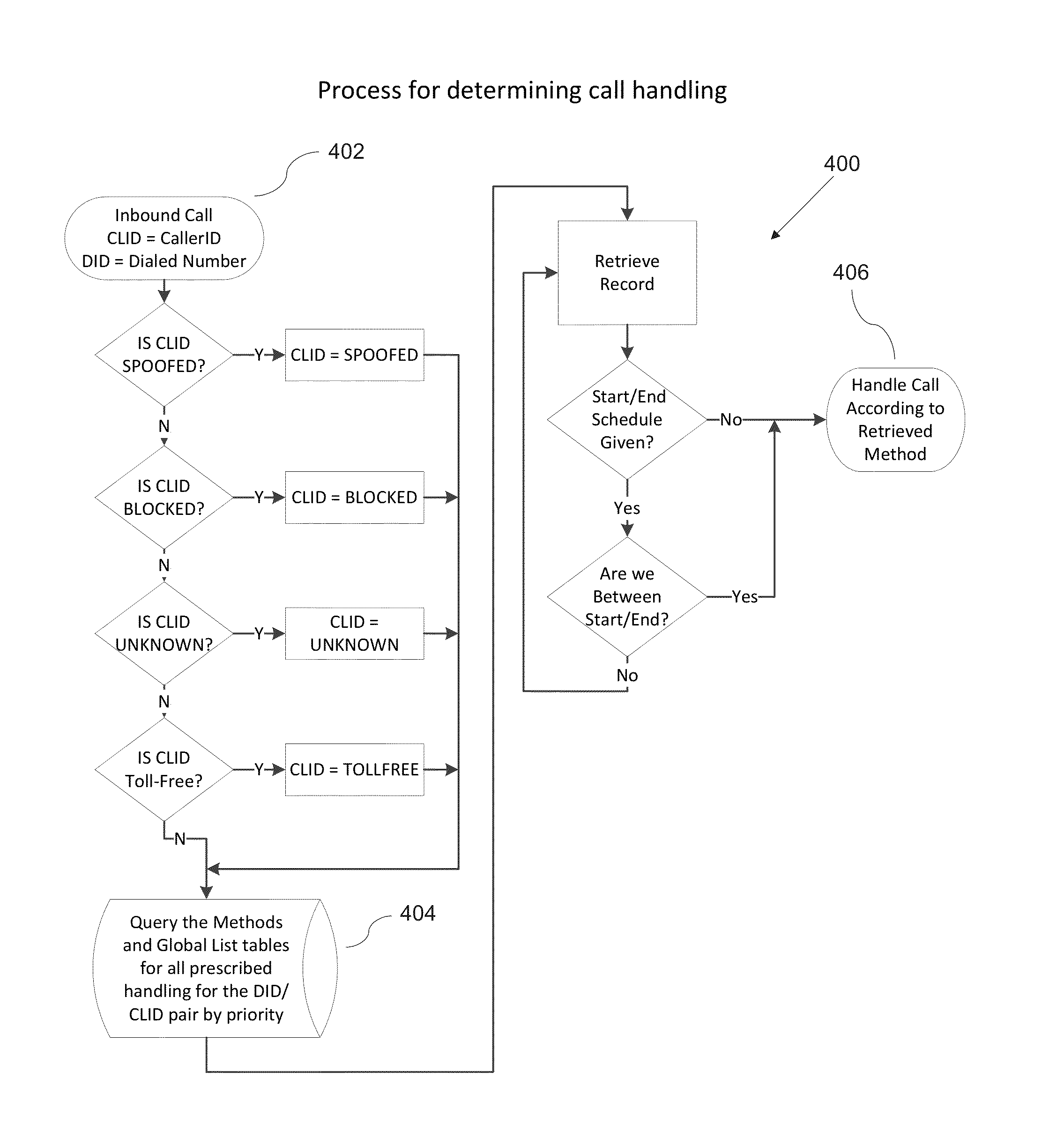
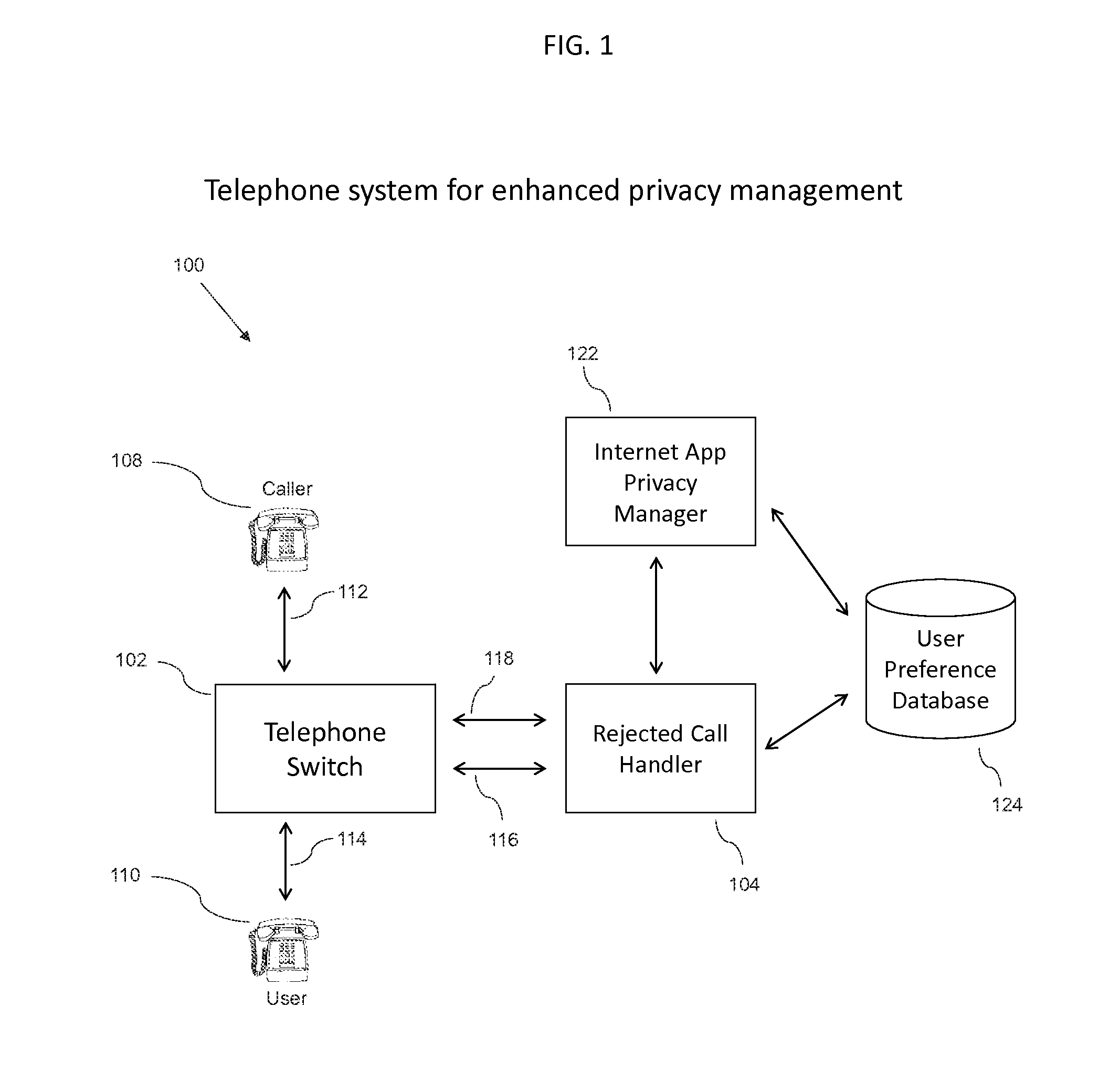
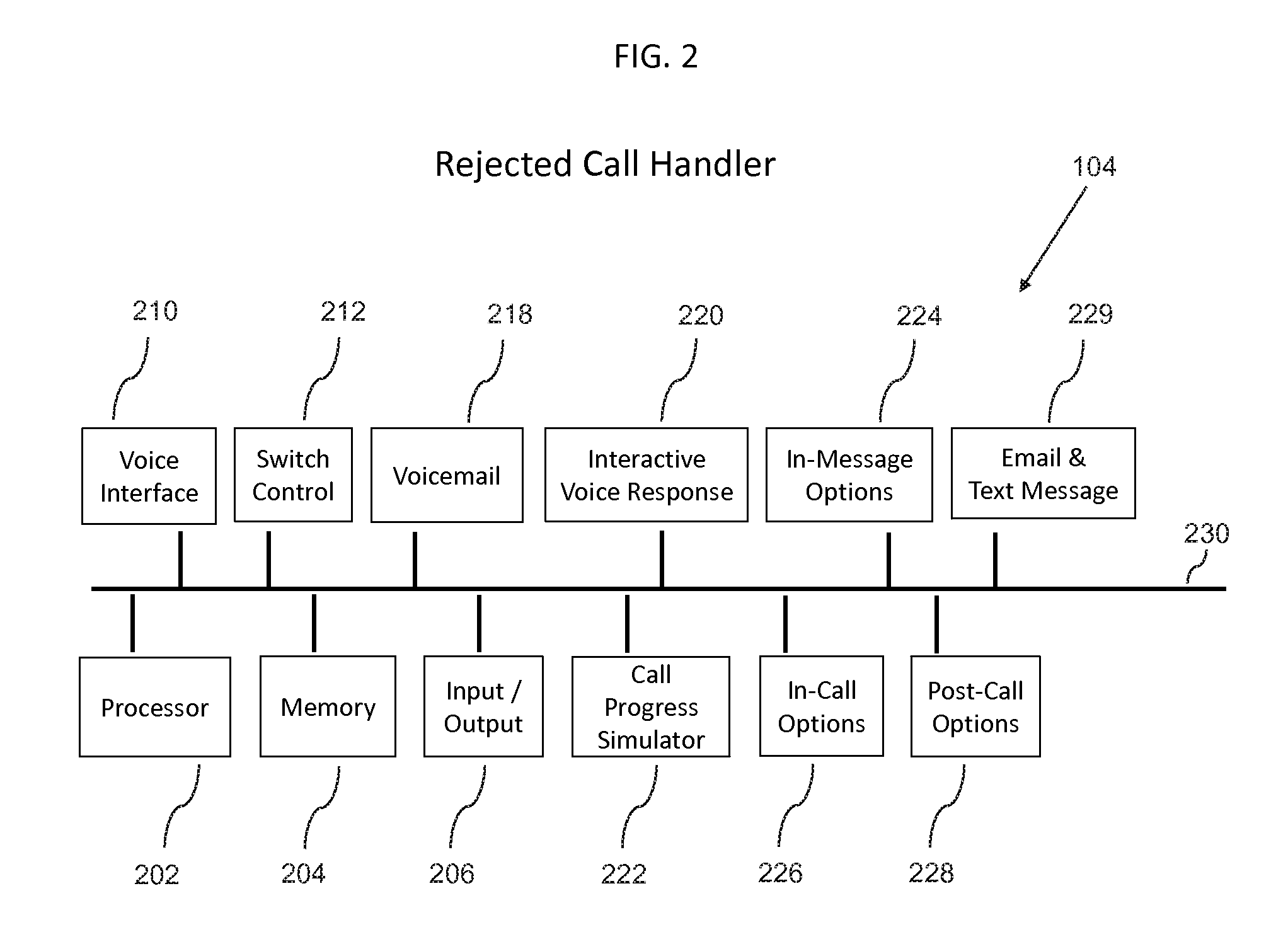
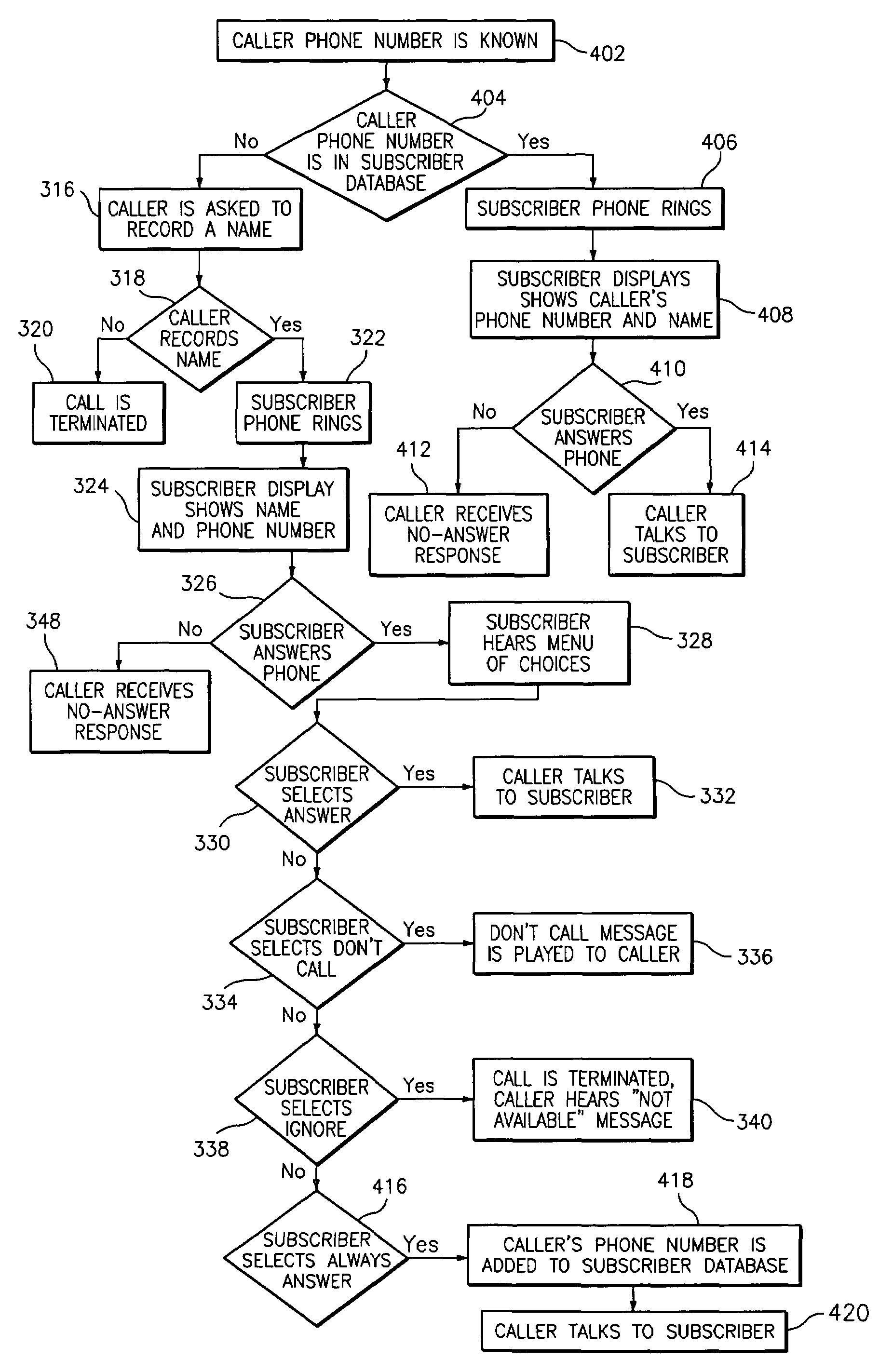
A telephone system for enhanced privacy management includes a telephone switch, a rejected call handler, a user preference database, and an internet app privacy manager, whereby an incoming call can be assigned to a calling class, and routed according to a calling rule associated with the calling class. Using an interactive voice response menu or an application portal, the user can assign callers to calling classes and specify call handling rules and schedules. A rejected call handler includes a voice interface, a switch control, a voicemail, interactive voice response, call progress simulator, in-message options, in-call options, post-call options, and other components. Further disclosed is a method for determining a calling rule, including determining the caller id status, querying a calling rules table, and determining a calling rule.
Owner:GUARRIELLO THEODORE J
Sender managed message privacy
ActiveUS20070022165A1Multiple digital computer combinationsOffice automationData processing systemInternet privacy
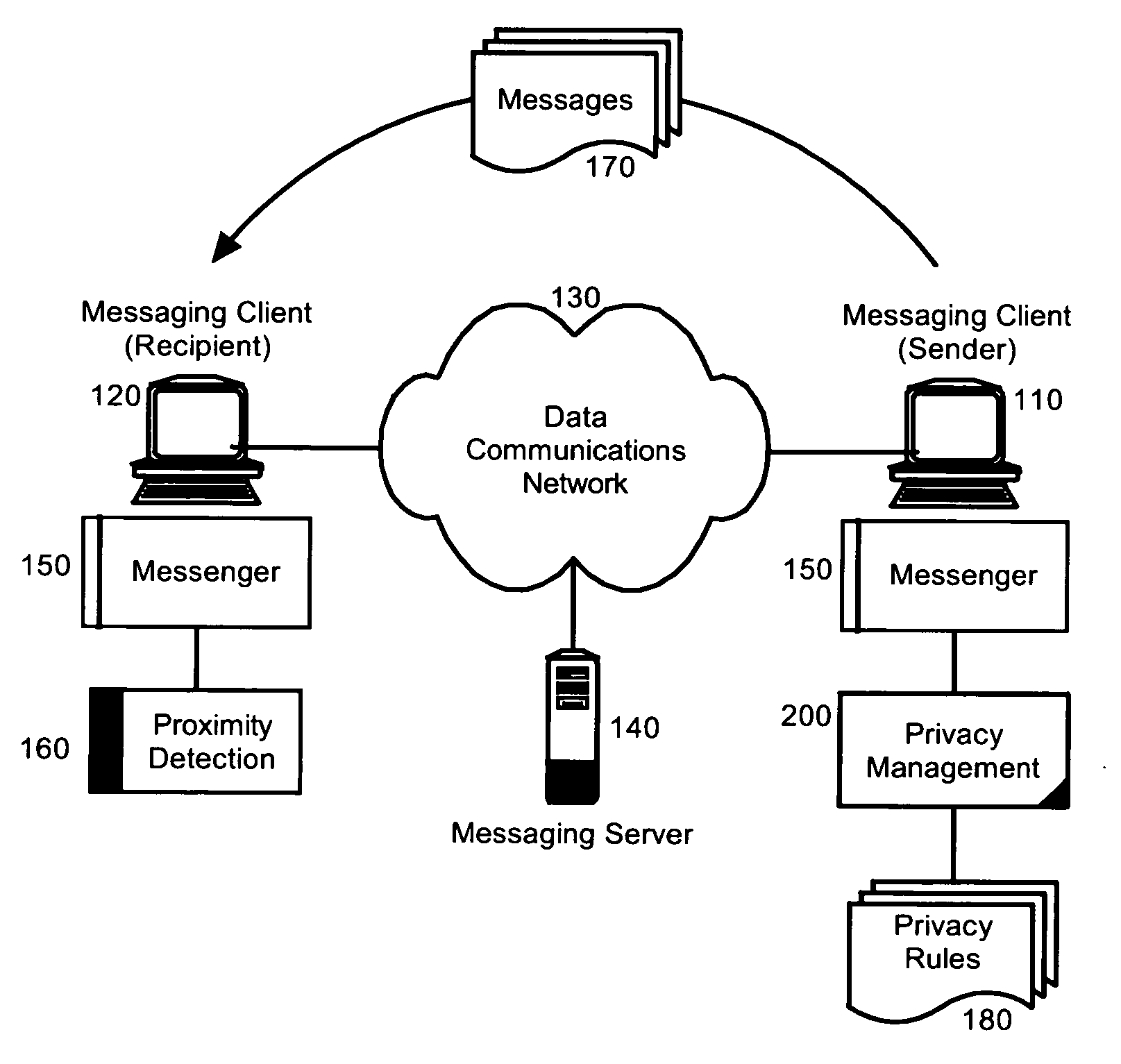
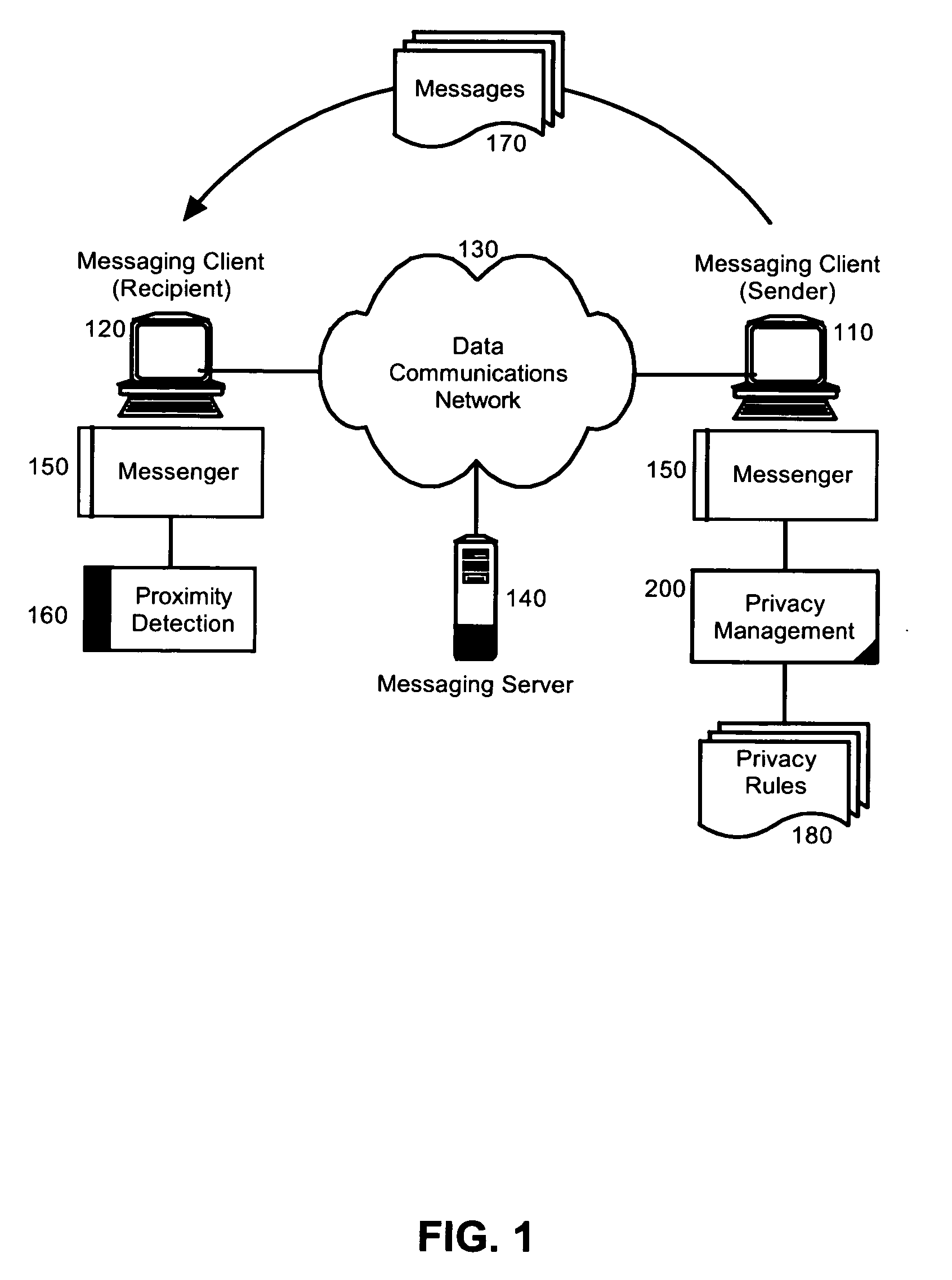
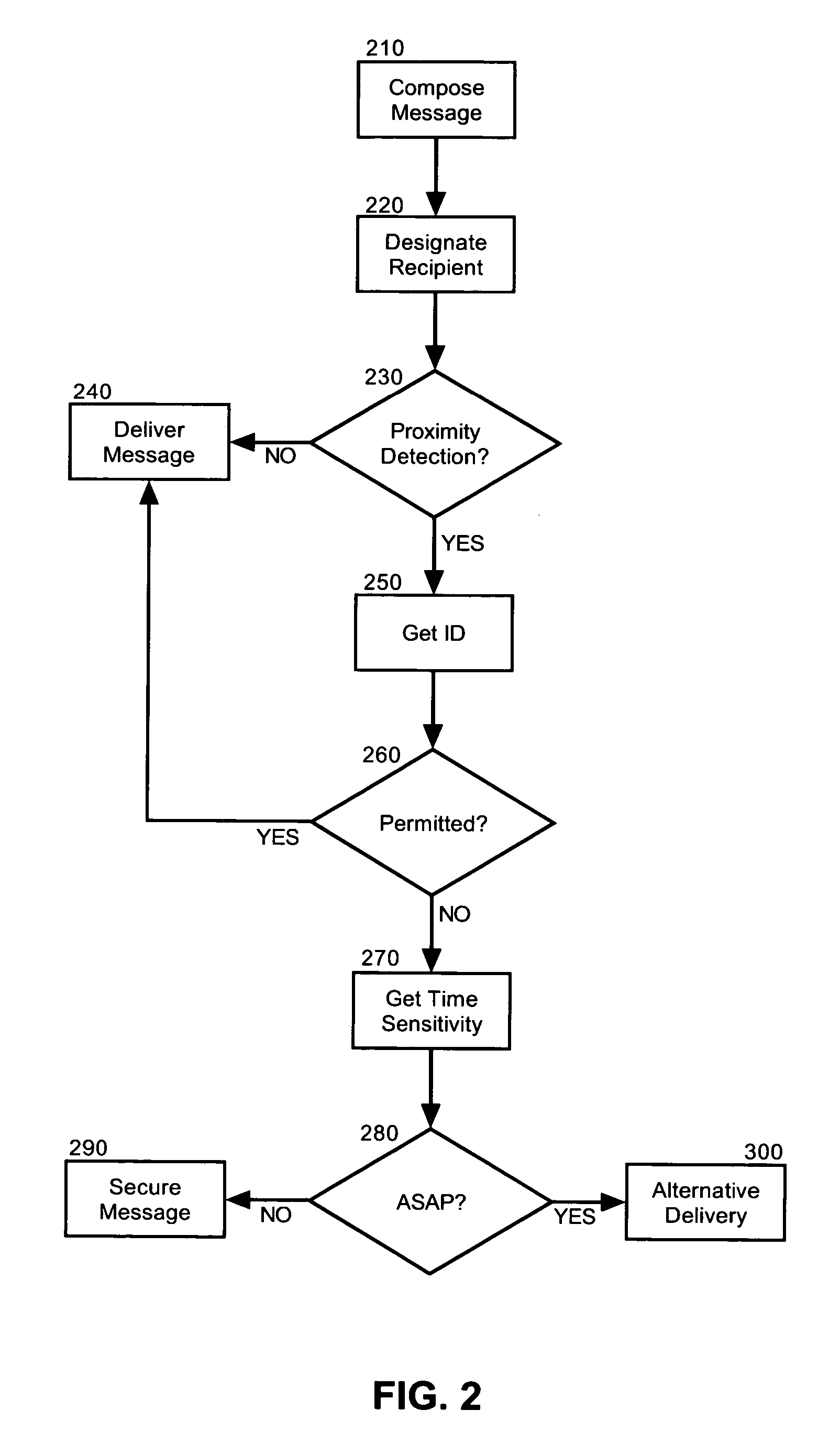
Embodiments of the present invention address deficiencies of the art in respect to securing the privacy of messages and provide a method, system and computer program product for sender managed message privacy. In an embodiment of the invention, a data processing system for sender managed privacy can include a sender messaging client coupled to privacy management logic and configured for communicative linkage to a recipient messaging client coupled to proximity detection logic over a data communications network. The privacy management logic can include program code enabled to secure a message designated for delivery in the recipient messaging client responsive to the proximity detection logic.
Owner:IBM CORP
Internet surfing log recording system and method capable of protecting personal privacies of users
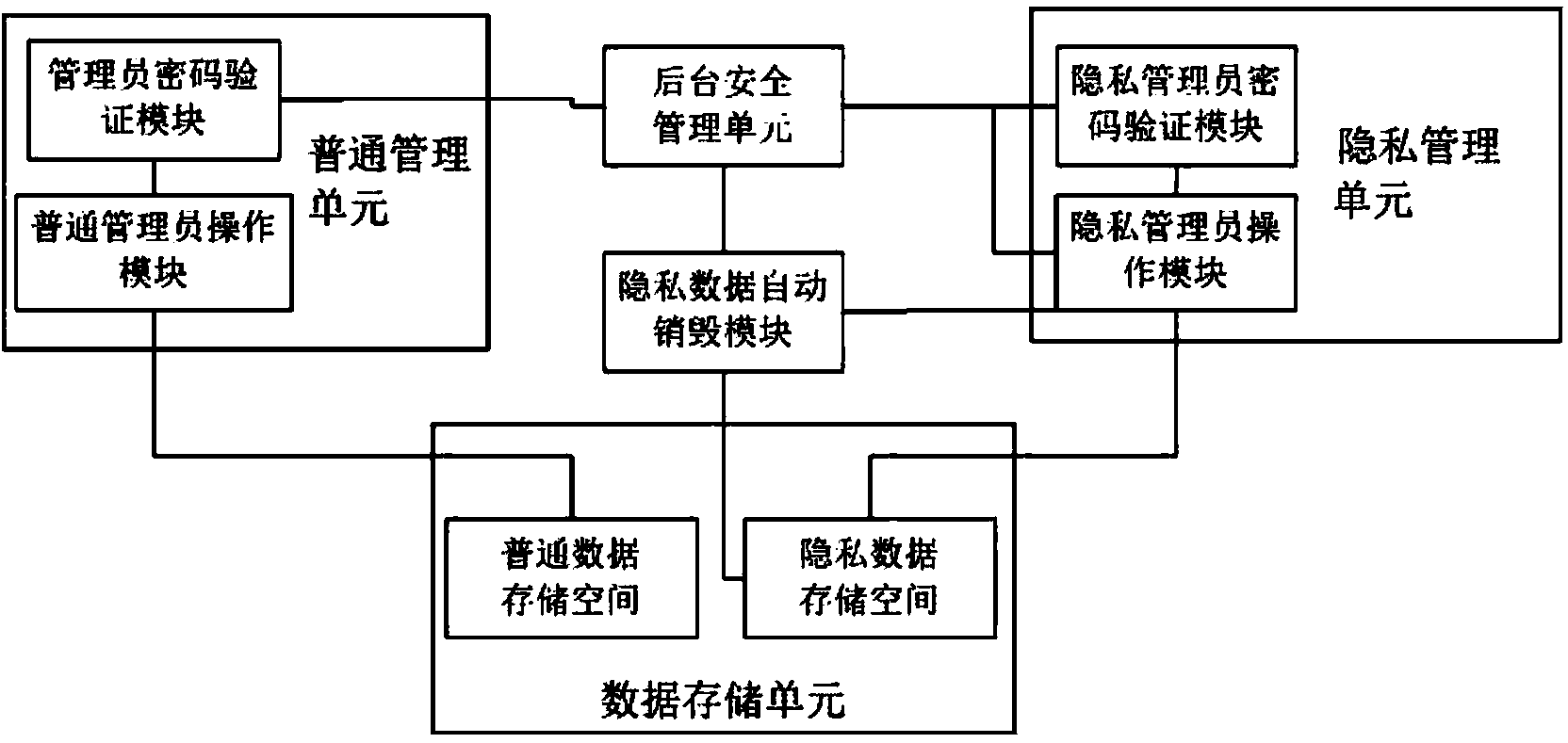
InactiveCN103455763AImprove confidentialityAchieve securityDigital data protectionDigital data authenticationManagement unitInternet privacy
The invention discloses an Internet surfing log recording system and method capable of protecting personal privacies of users. The system comprises a general management unit responsible for general management operation, a privacy management unit responsible for authorization and operation, a background safety management unit connected with the general management unit and the privacy management unit and responsible for safety of a monitoring system, and a data storage unit used for storing data. Therefore, the method is good in safety and less prone to data leakage of the personal privacies of the users, and can achieve joint administration by administrators in different levels through combination of software encryption and hardware encryption.
Owner:孙伟力
Method and system for providing a privacy management service
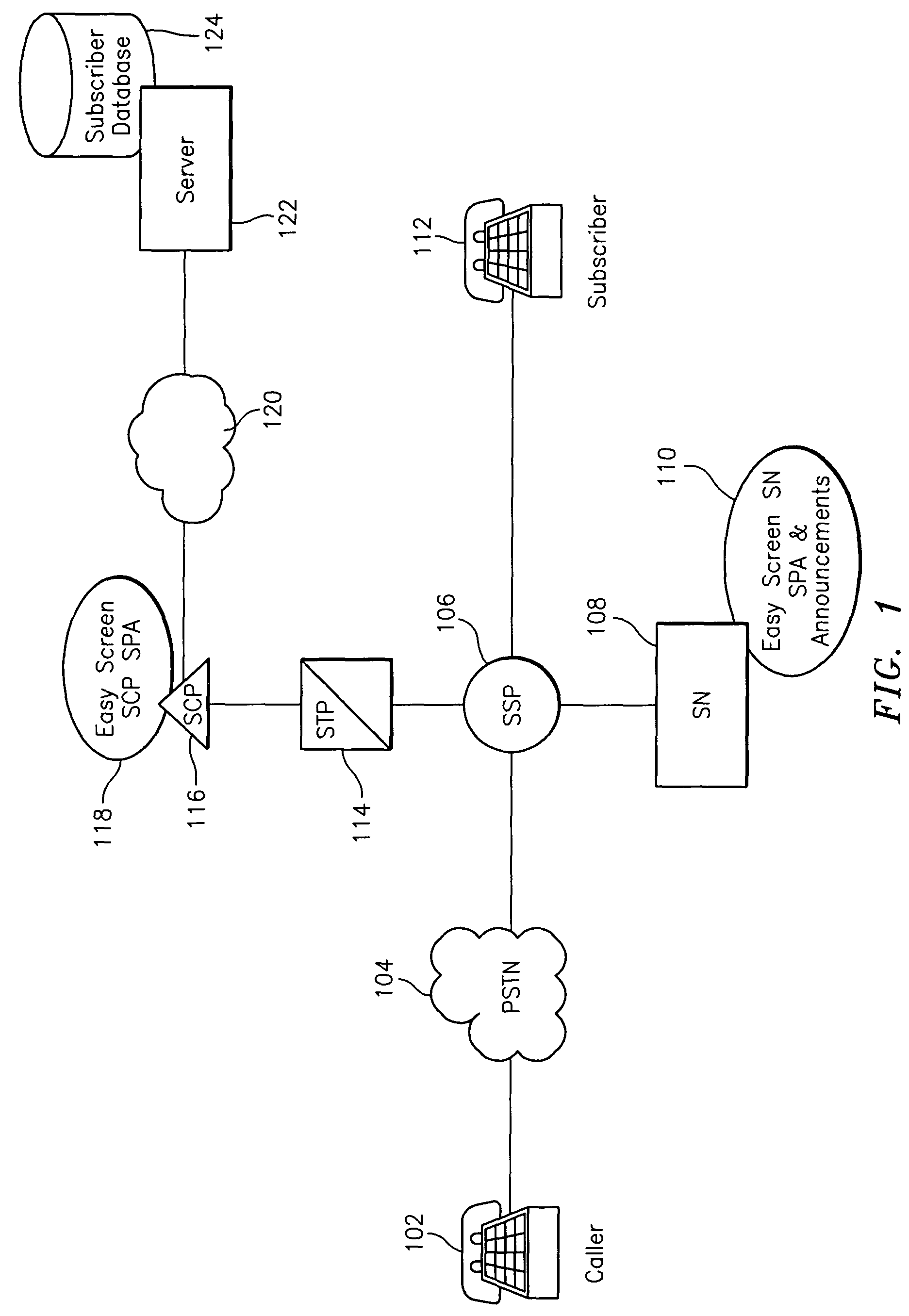
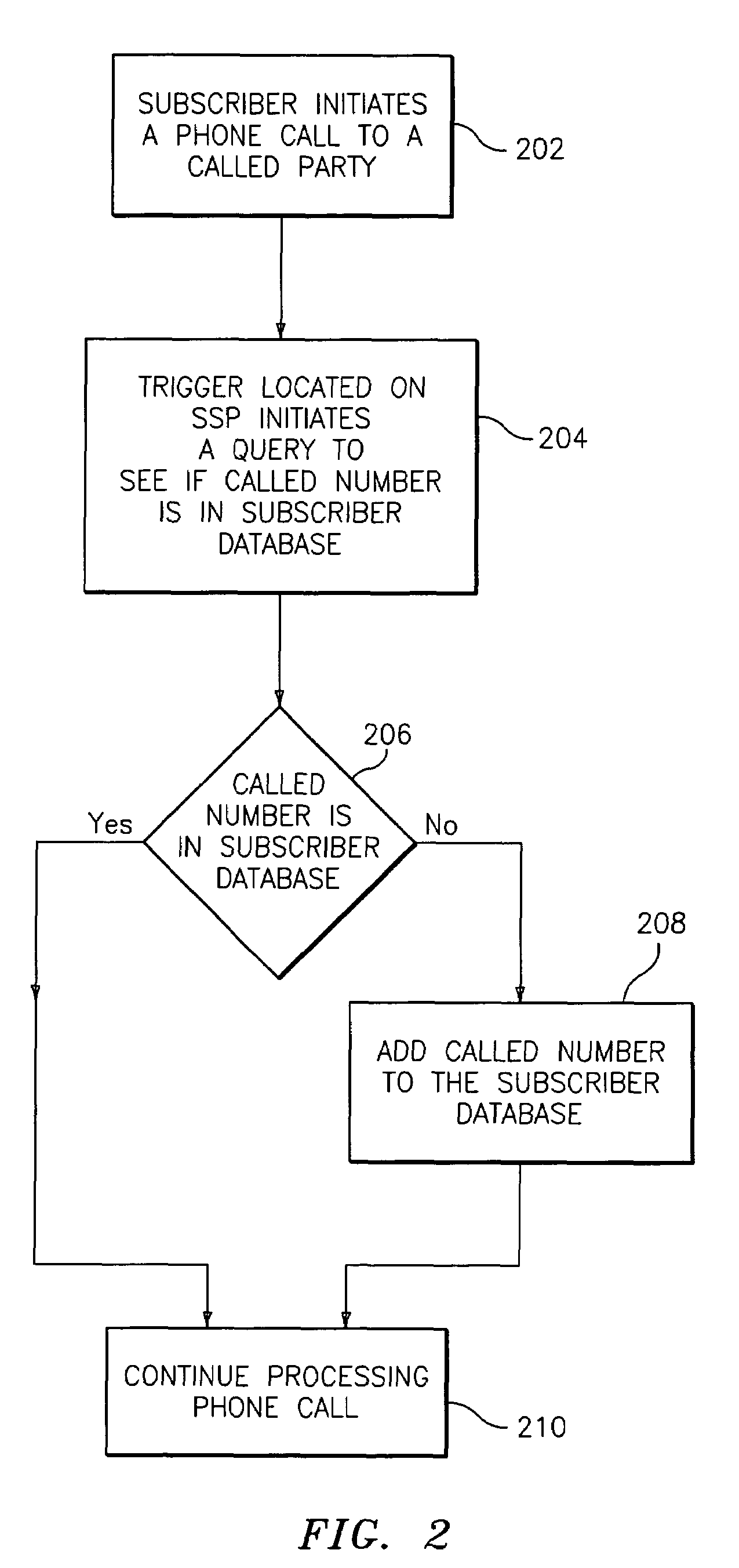
InactiveUS7352855B2Special service for subscribersCalled number recording/indicationComputer sciencePrivacy management
A method for providing a privacy management service in a telephone system including initiating a telephone call from a subscriber telephone number to a called party telephone number. The initiating is performed by a subscriber. It is determined if the called party telephone number is located in a subscriber database corresponding to the subscriber. The called party telephone number is added to the subscriber database in response to the determining resulting in not locating the called party telephone number in the subscriber database. The telephone call between the subscriber telephone and the called party telephone number is connected.
Owner:BELLSOUTH INTPROP COR
A third party remoistening method and realization system
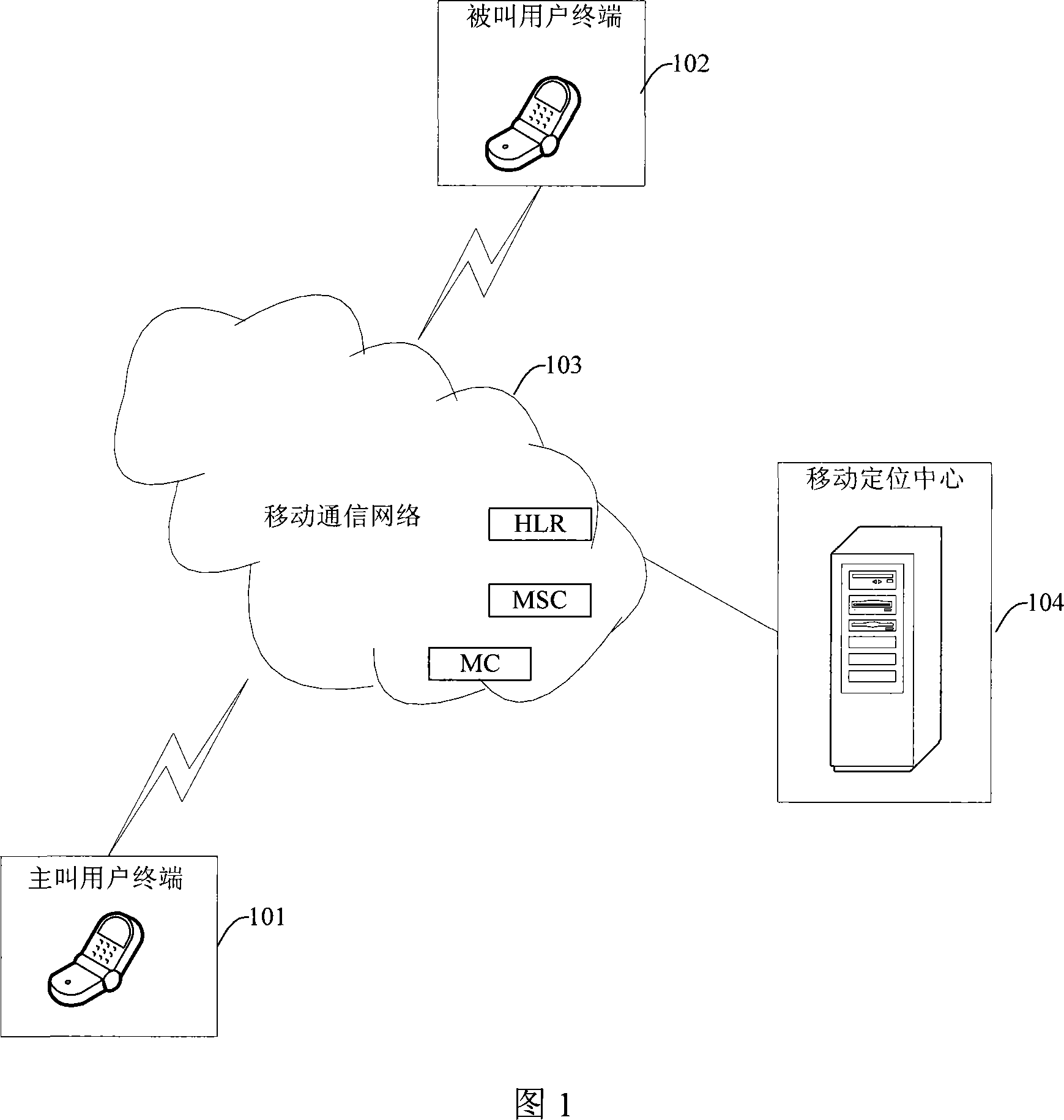
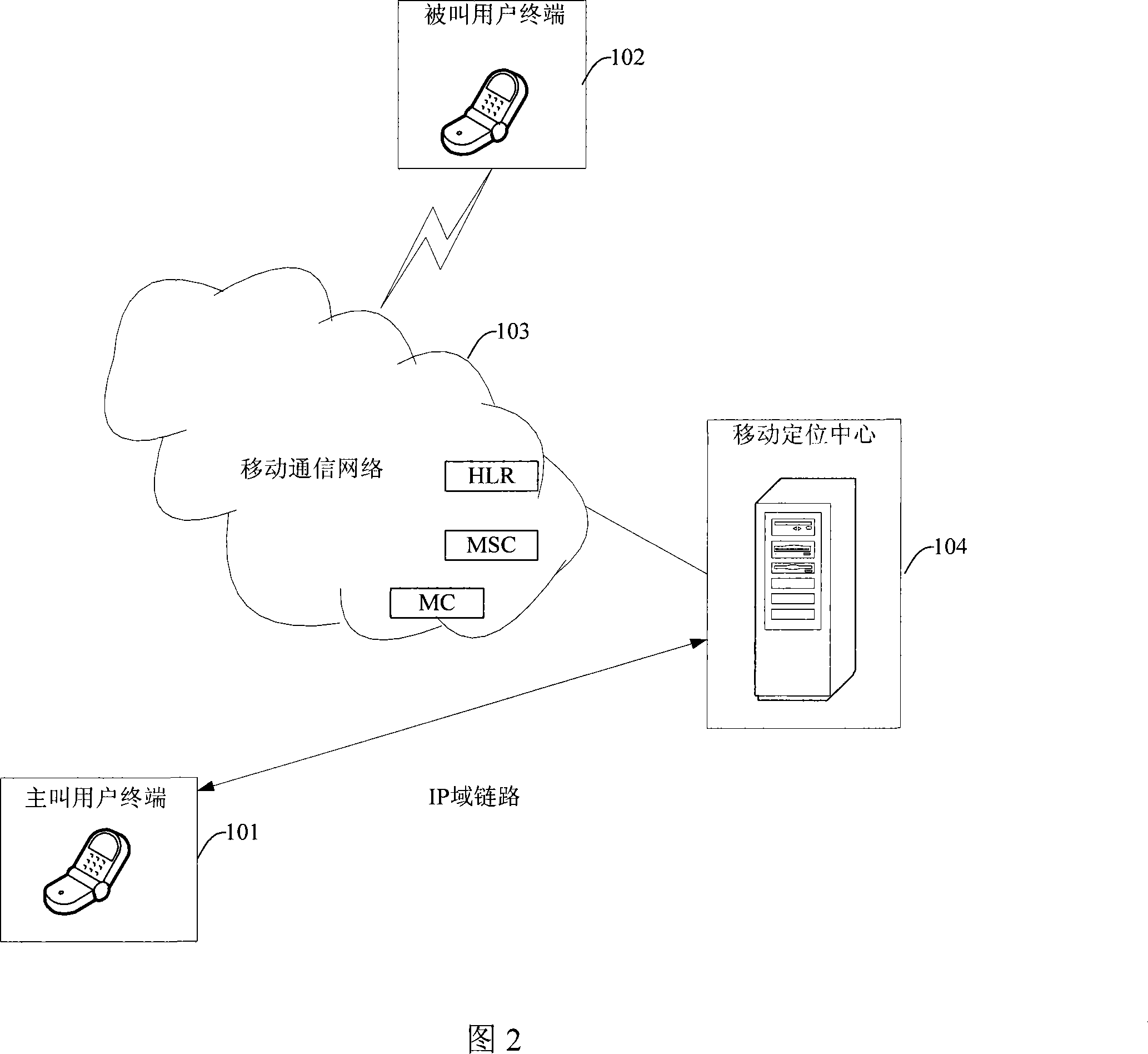
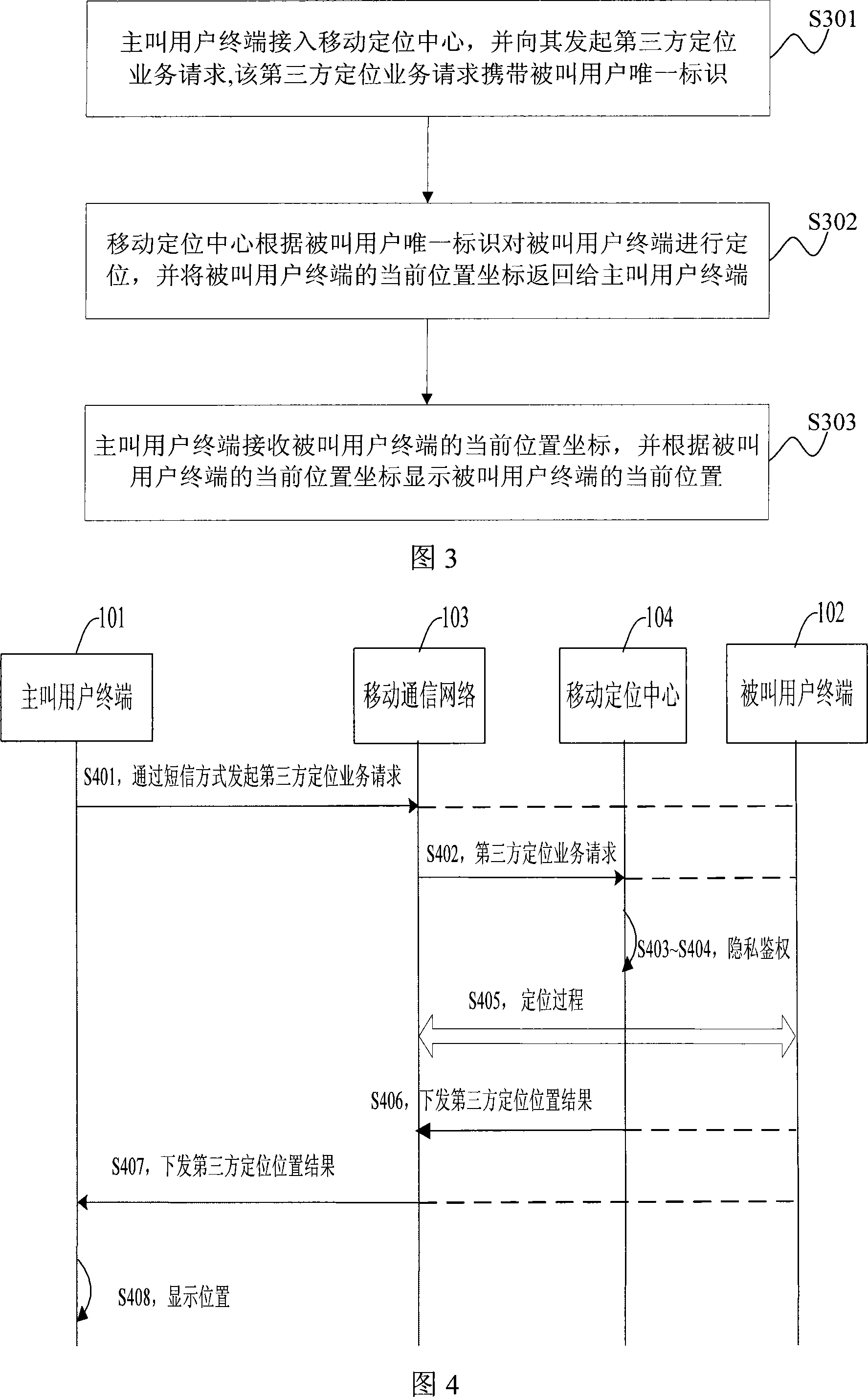
InactiveCN101217570AMultiple Privacy Management InitiativesImprove service qualityUser identity/authority verificationRadio/inductive link selection arrangementsQuality of serviceThird party
The invention discloses a realization method of a third party positioning business, which comprises the steps: a dialing user terminal is accessed to a mobile positioning center and initiates a third party positioning business request carrying an unique mark of a called user terminal to the mobile positioning center; the mobile positioning center positions the called user terminal according to the unique mark of the called user terminal, and returns the coordinate of the current position of the positioned called user terminal to a calling user terminal; the calling user terminal displays the current position of the called user terminal according to the coordinate of the current position of the called user terminal. Meanwhile, the invention correspondingly discloses a realization system of the third party positioning business. Therefore, in the process of executing the third party positioning business, the invention can independently launch the business without depending on SP or CP; the mobile positioning center saves the management of the SP or the CP, and pays closer attention to the management of the authority and privacy of the user, thus leading the user to have more initiative of privacy management and improving the service quality to the user.
Owner:ZTE CORP
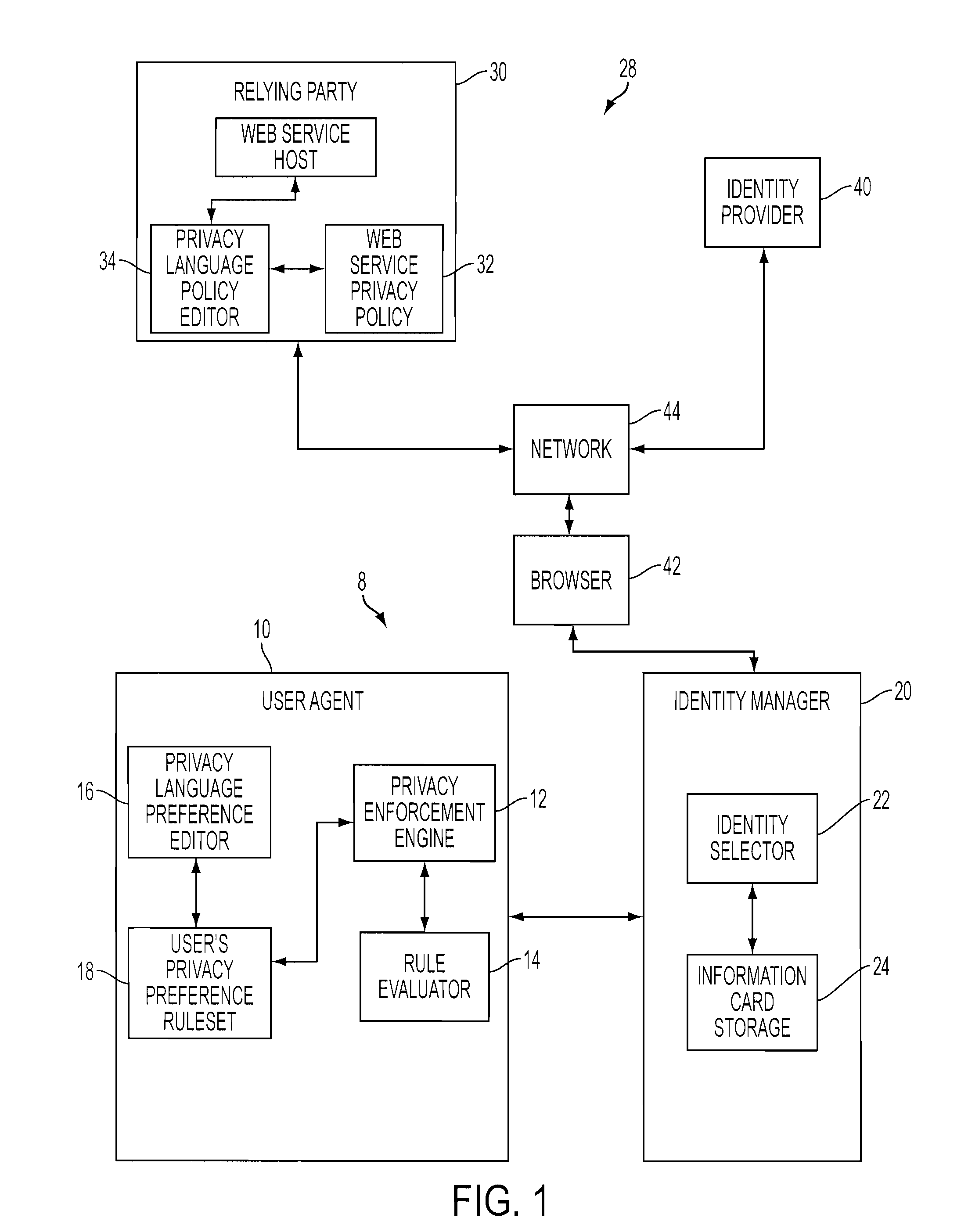
User-directed privacy control in a user-centric identity management system
An identity management system incorporates privacy management processes that enable the user to exercise privacy controls over the disclosure of user identity information within the context of an authentication process. A combination includes an identity selector, a privacy engine, and a ruleset. The identity selector directs the release of a user identity in the form of a security token to satisfy the requirements dictated by a security policy. Prior to release of the user identity, the engine conducts a privacy enforcement process that examines the privacy policy of the service provider and determines if it is acceptable. The engine evaluates a ruleset against the privacy policy. A preference editor enables the user to construct, in advance, the ruleset, which embodies the user's privacy preferences regarding the disclosure of identity information. Based on the evaluation results, the user can either approve or disapprove the privacy policy, and so decide whether to proceed with disclosure of the user identity.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com