Internet surfing log recording system and method capable of protecting personal privacies of users
A personal privacy and recording system technology, applied in the field of personal privacy recording system, can solve the problems of high risk of password leakage and poor security of user privacy information, and achieve the effect of convenient organization, data security and security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
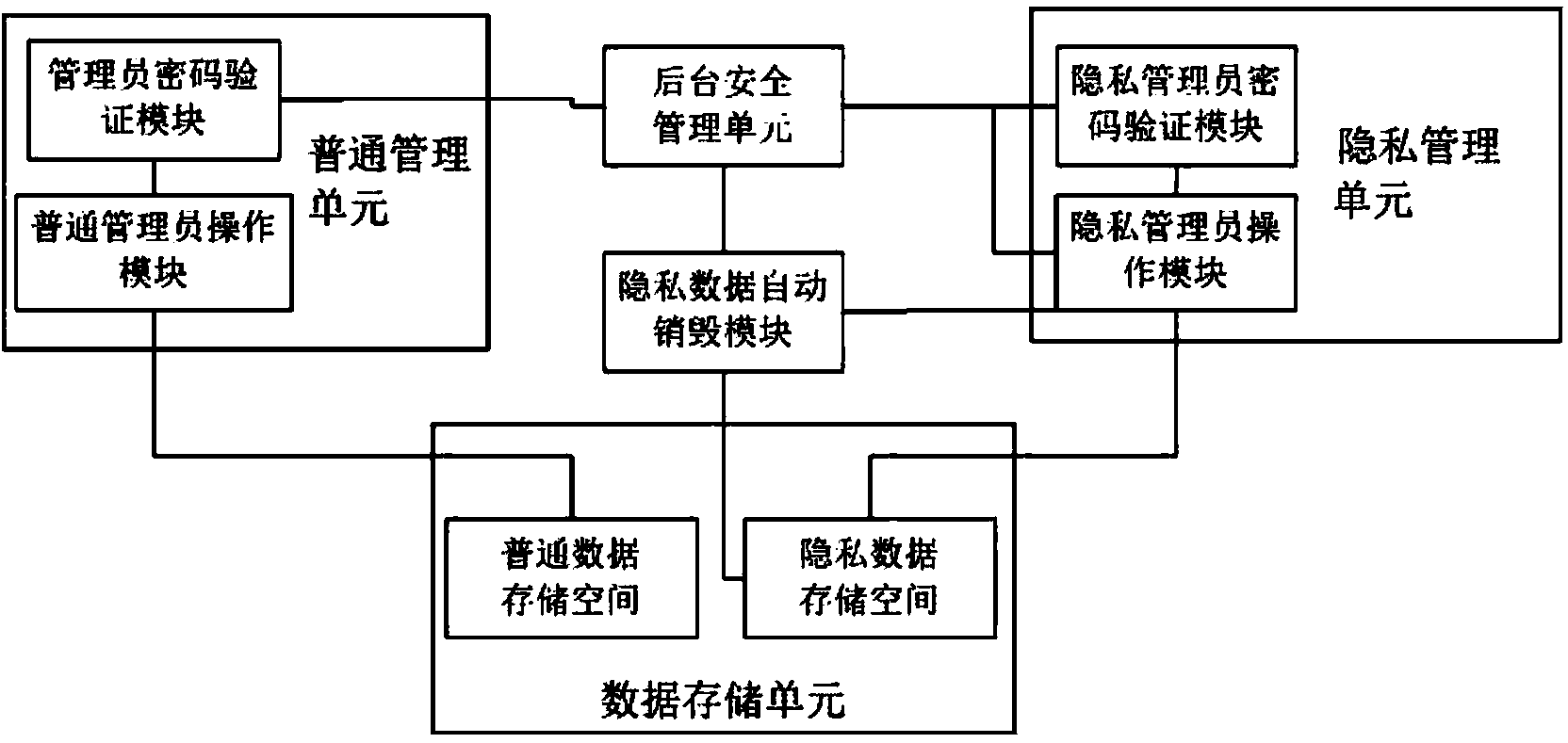
[0070] The technical scheme of the invention provides an online logging system and method for protecting user privacy. Such as figure 1 As shown, an online logging system that protects users' personal privacy mainly includes:
[0071] 1. An ordinary management unit for realizing verification and operation of ordinary administrators, the ordinary management unit may be provided with a plurality of different ordinary administrator accounts, and the ordinary management unit further includes:
[0072] (1.1) An administrator password verification module used to verify the identity and operation authority of ordinary administrators. The password verification device of the administrator password verification module can be identified by static password input or dynamic password input or through USB peripherals. One or more combinations of hardware encryption devices are formed.
[0073] (1.2) Ordinary administrator operation module, which is used for ordinary administrators to opera...
Embodiment 2
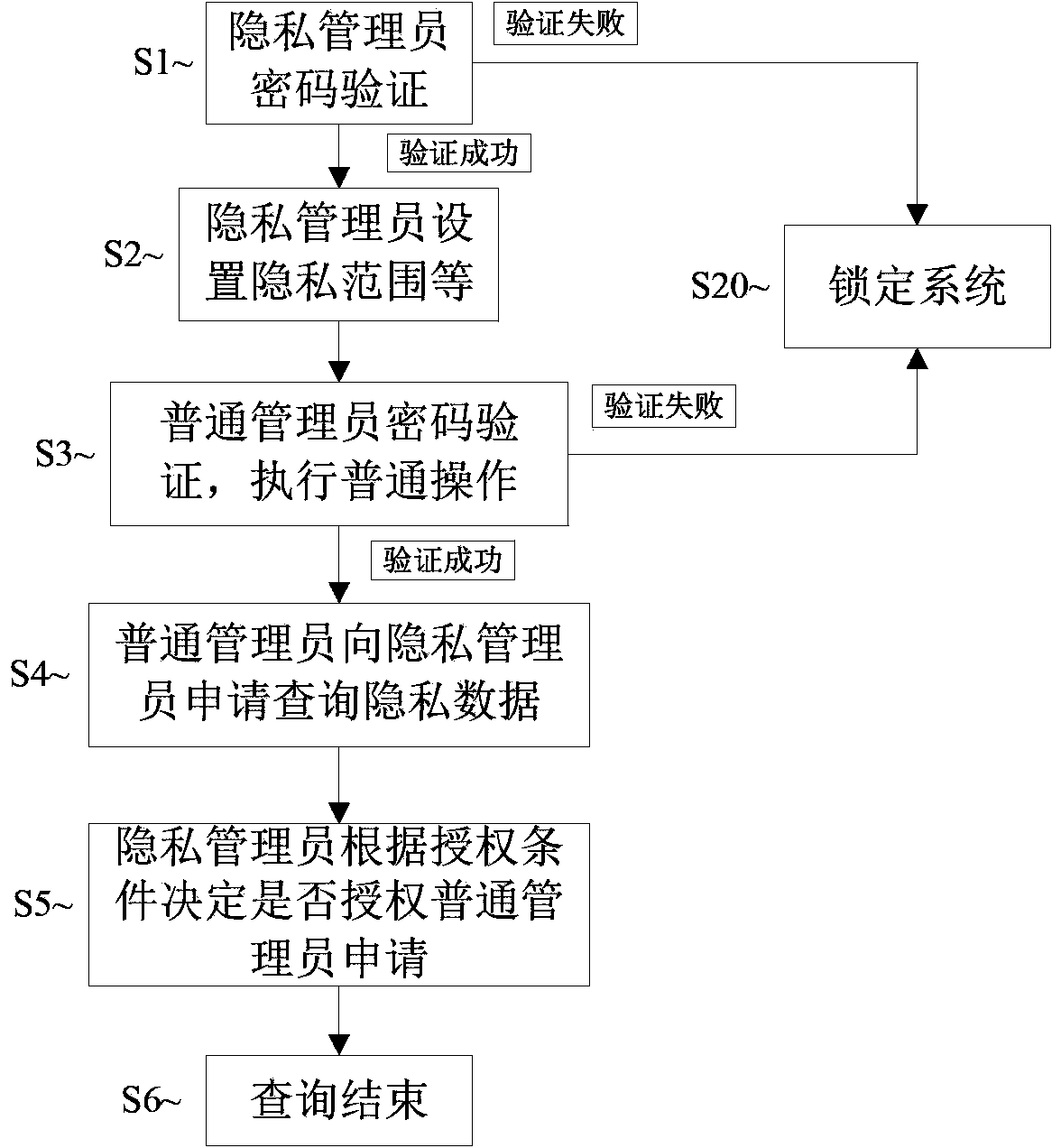
[0085] Such as figure 2 As shown, a log recording method for protecting user personal privacy mainly includes the following steps:
[0086] S1: The privacy manager performs password verification through the privacy manager password verification module of the privacy management unit, and the required number of privacy managers in the online logging system is at least 2. The administrator password verification step includes firstly the privacy administrator login identity verification and the privacy administrator's operation authority verification after the identity authentication is passed. Data operation authority, the privacy administrator does not have the authority to query the specific data content of the user's personal privacy data, such as consulting detailed user log records. If the verification fails, re-verify. When the background security management unit monitors that the privacy administrator has failed more than 3 password verifications (including the sum of lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com