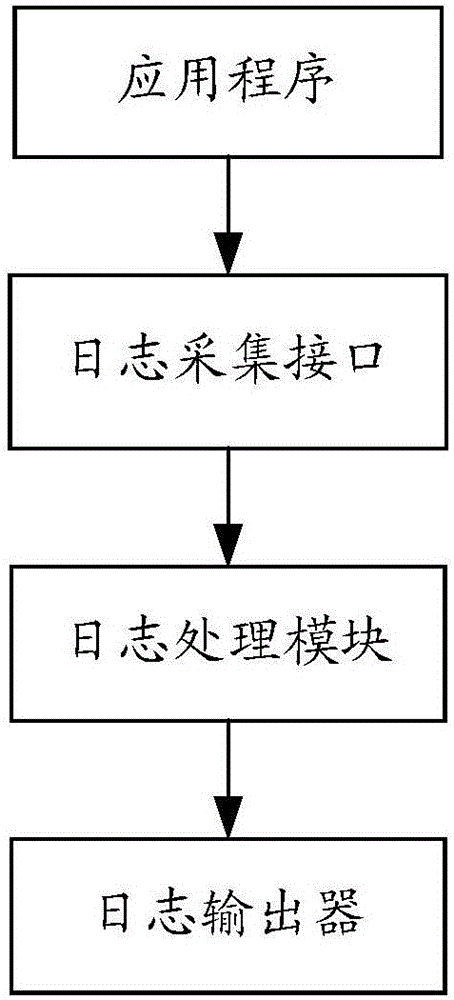
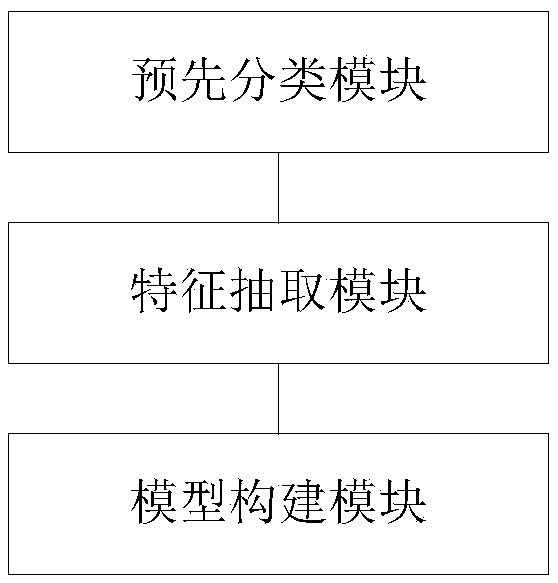
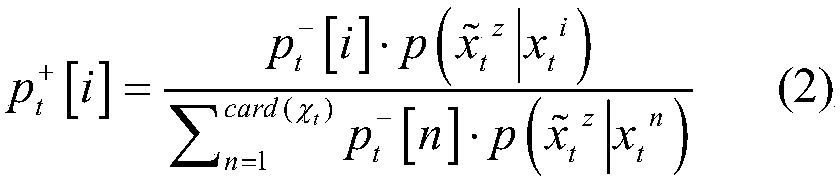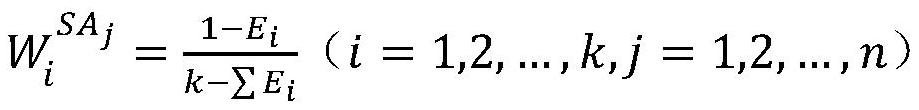Patents
Literature
116results about How to "Reduce the risk of privacy breaches" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for switching working mode of mobile terminal and mobile terminal
ActiveCN102932542AReduce the risk of privacy breachesImprove privacySubstation equipmentTransmissionUser inputUser privacy
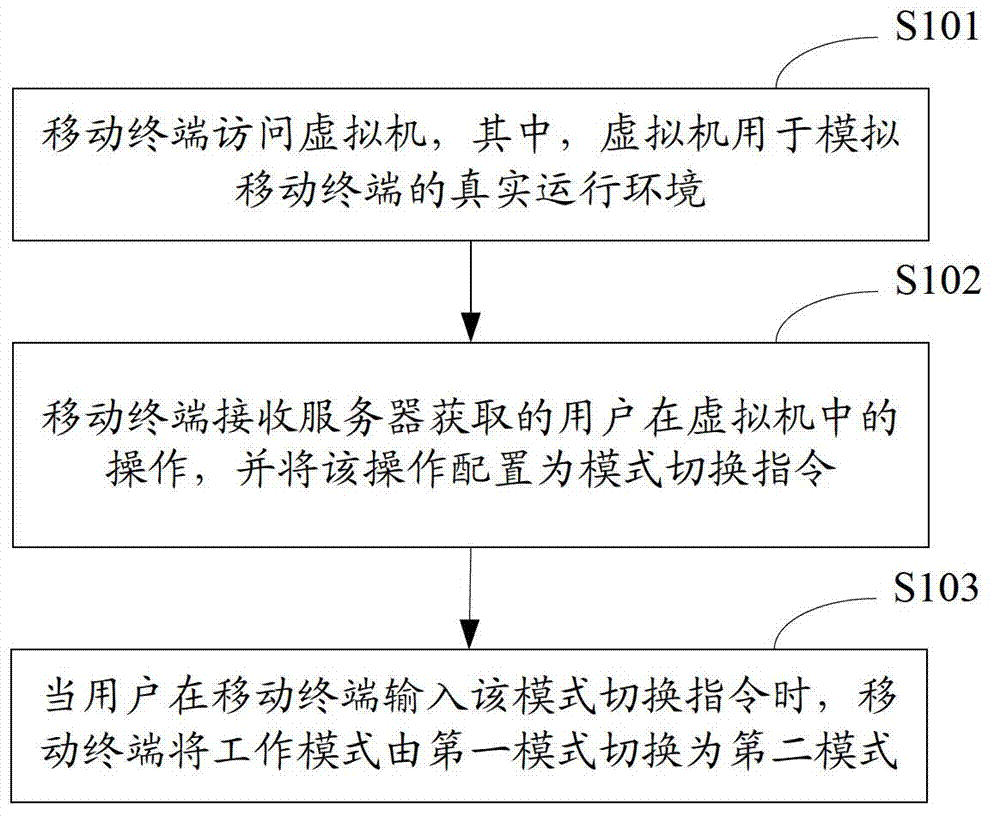
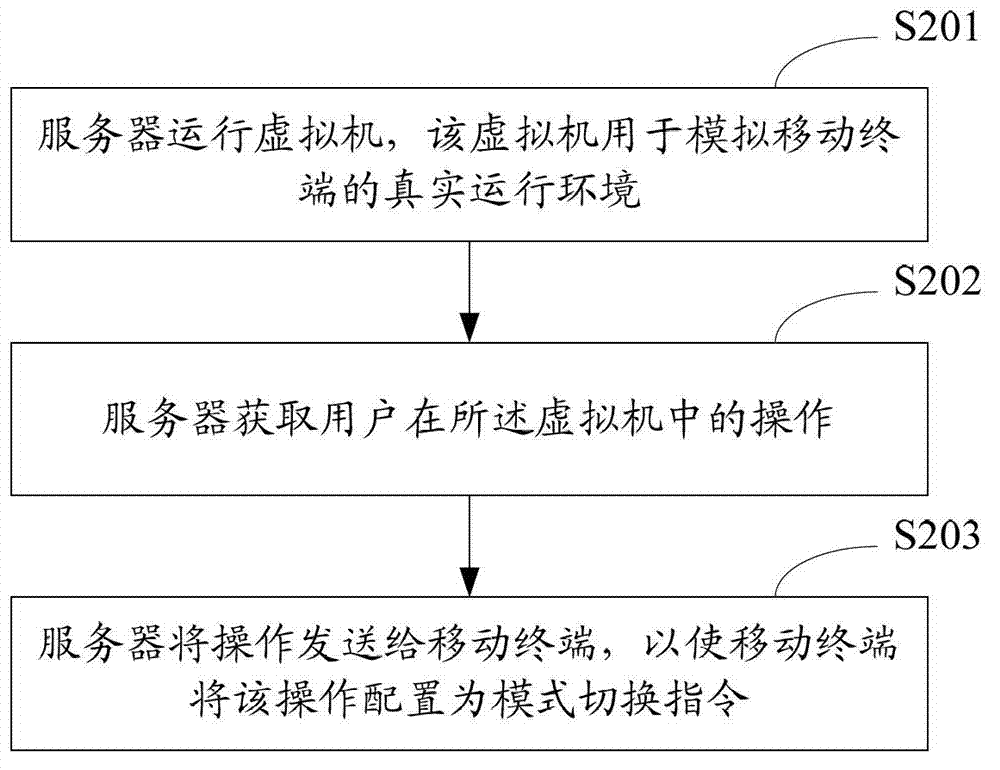
The invention is suitable for the technical field of mobile terminals and provides a method for switching a working mode of a mobile terminal and the mobile terminal. The method comprises the steps of: S101, accessing a virtual machine by the mobile terminal, wherein the virtual machine is used for simulating a real operating environment of the mobile terminal; S102, receiving operation which is acquired by a server and is carried out in the virtual machine by the user, by the mobile terminal, and configuring the operation into a mode switching command; and S103, when the user inputs the mode switching command in the mobile terminal, switching the working mode from a first mode to a second mode by the mobile terminal. According to the invention, by means of accessing the virtual machine by the mobile terminal, the user can set an operation command on the virtual machine so as to customize a private mode inlet of the mobile terminal according to personal operation habits, so that the privacy of the private mode is enhanced, and the risk of disclosing user privacy is reduced.
Owner:DONGGUAN YULONG COMM TECH +1
Method and device for protecting privacy
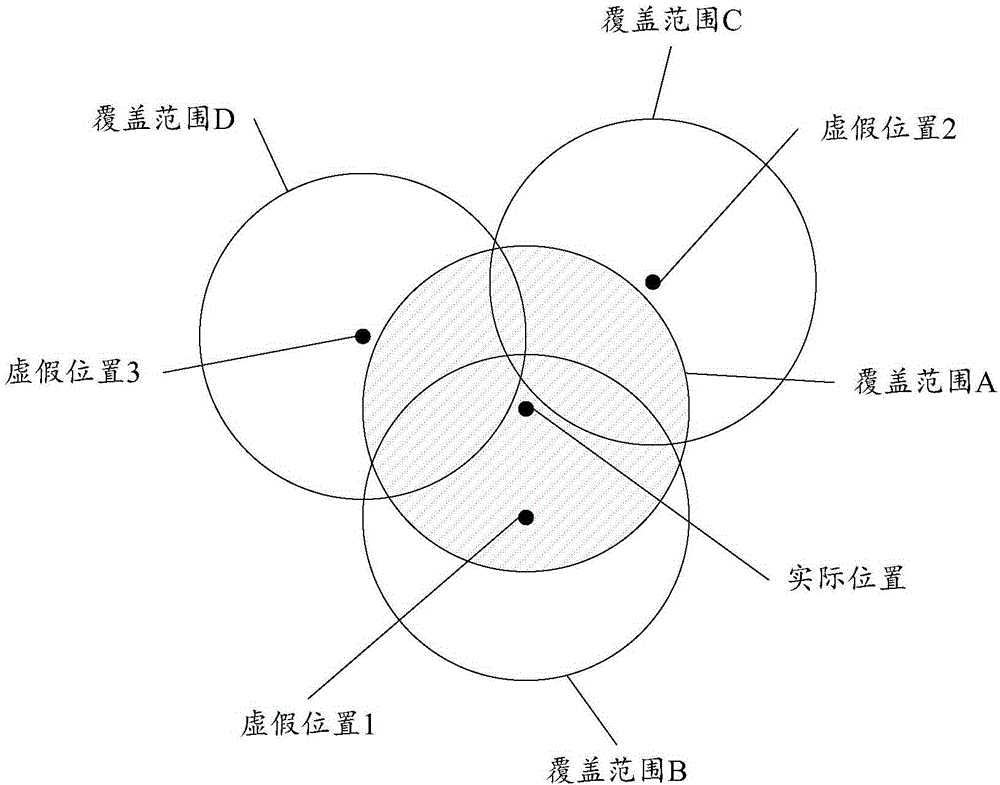
InactiveCN104010272AProtect privacy and securityReduce the risk of privacy breachesLocation information based serviceSecurity arrangementInformation technologyElectronic information
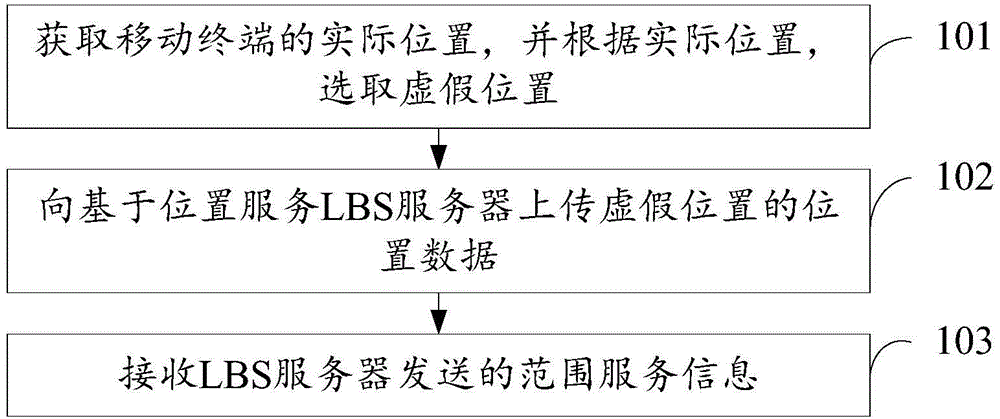
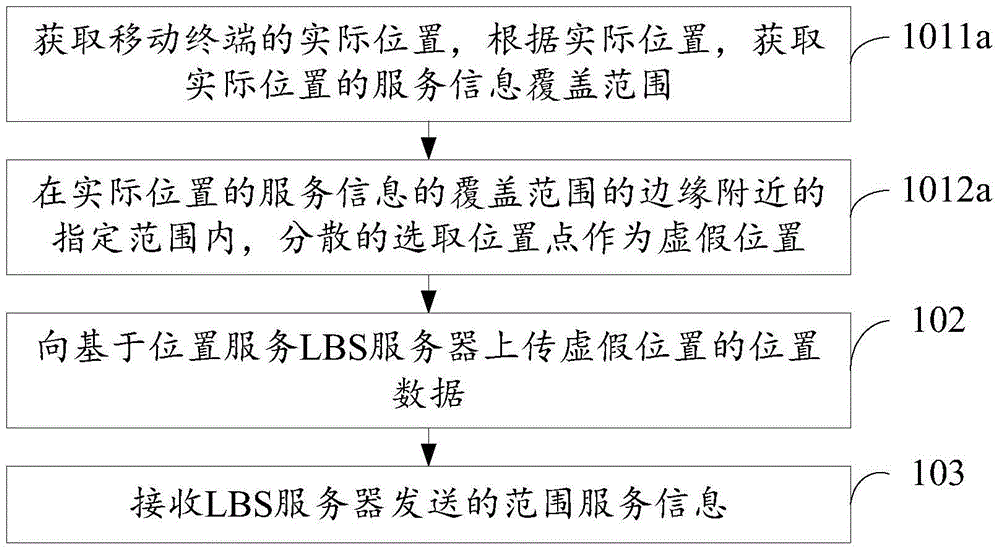
The embodiment of the invention discloses a method and device for protecting privacy and relates to the technical field of electronic information. According to the method and device, position information and privacy leakage of a user can be reduced. The method includes the steps that the actual position of a mobile terminal is obtained, a false position is selected according to the actual position, and the coverage range of service information of the actual position is within the coverage range of service information of the false position; data of the false position are uploaded to an LBS server; the range service information sent by the LBS server is received and at least includes the service information of the false position, and the service information of the false position is obtained through the LBS server according to the data of the false position. The method and device are suitable for scenes where the privacy of the user is protected in LBS.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
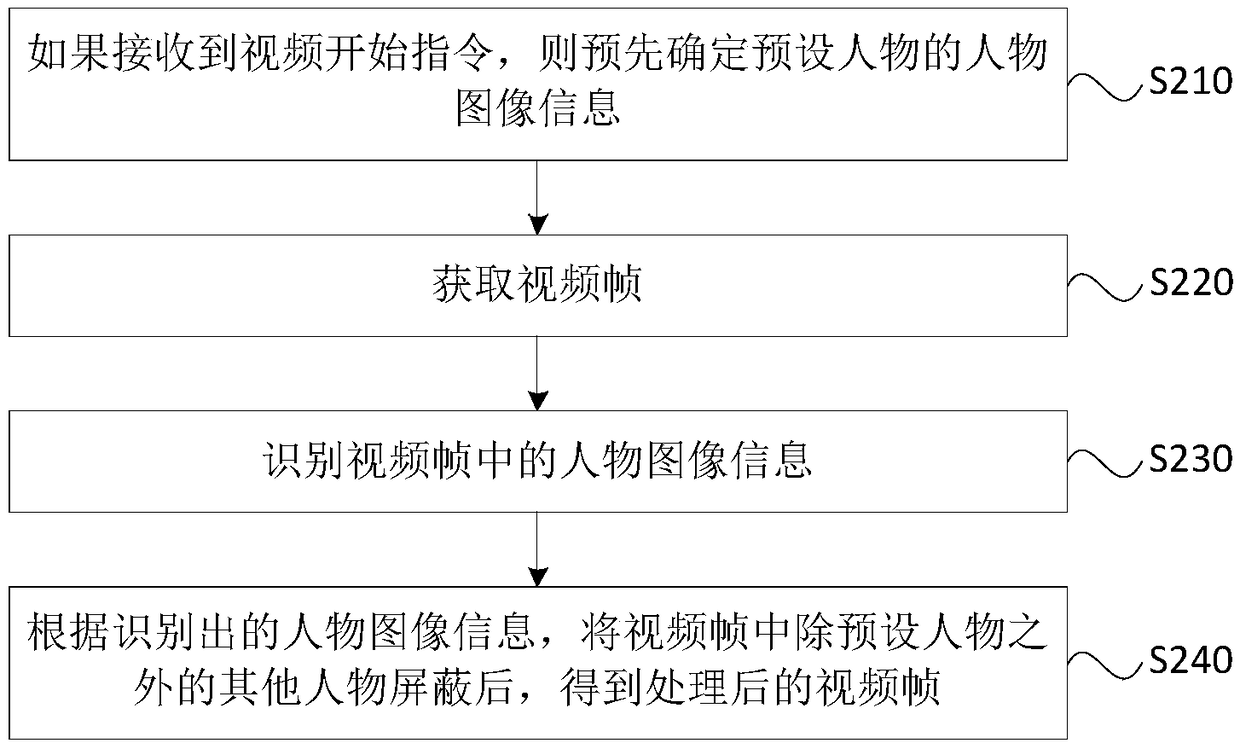
Video processing method and apparatus, terminal and storage medium
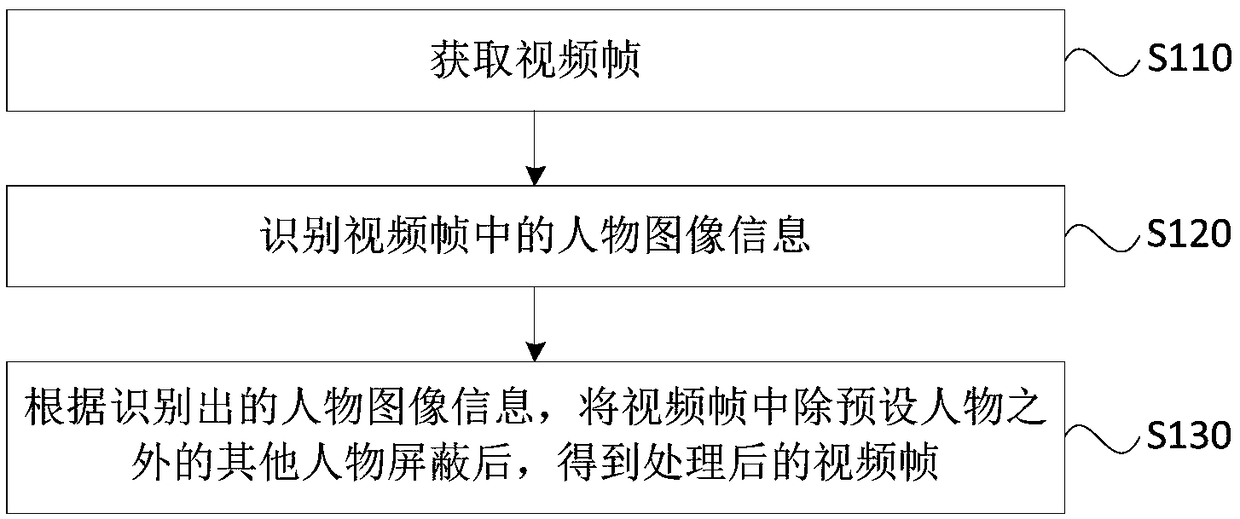
InactiveCN108848334AProtect private informationReduce the risk of privacy breachesTwo-way working systemsSelective content distributionComputer graphics (images)Video processing
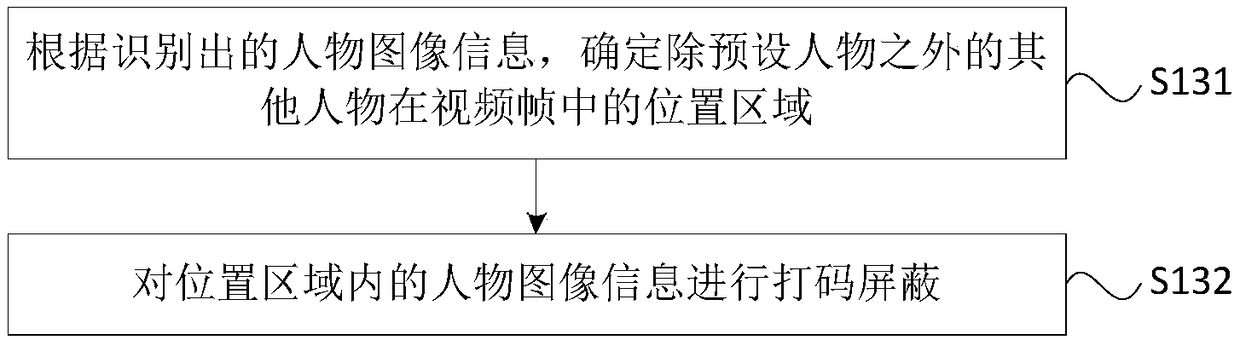
The embodiment of the invention discloses a video processing method and apparatus, a terminal and a storage medium. The method comprises the following steps: obtaining a video frame; identifying character image information in the video frame; and shielding other characters excluding a preset character in the video frame according to the identified character image information to obtain a processedvideo frame. By adoption of the technical scheme provided by the embodiment of the invention, by shielding the other characters excluding the preset character in the video frames in a video process, the information of the other characters who do not participate in a video in the surrounding environment of the video is shielded, thereby protecting the privacy information of the other characters, reducing the risks of accidental privacy leakage and improving the privacy security.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
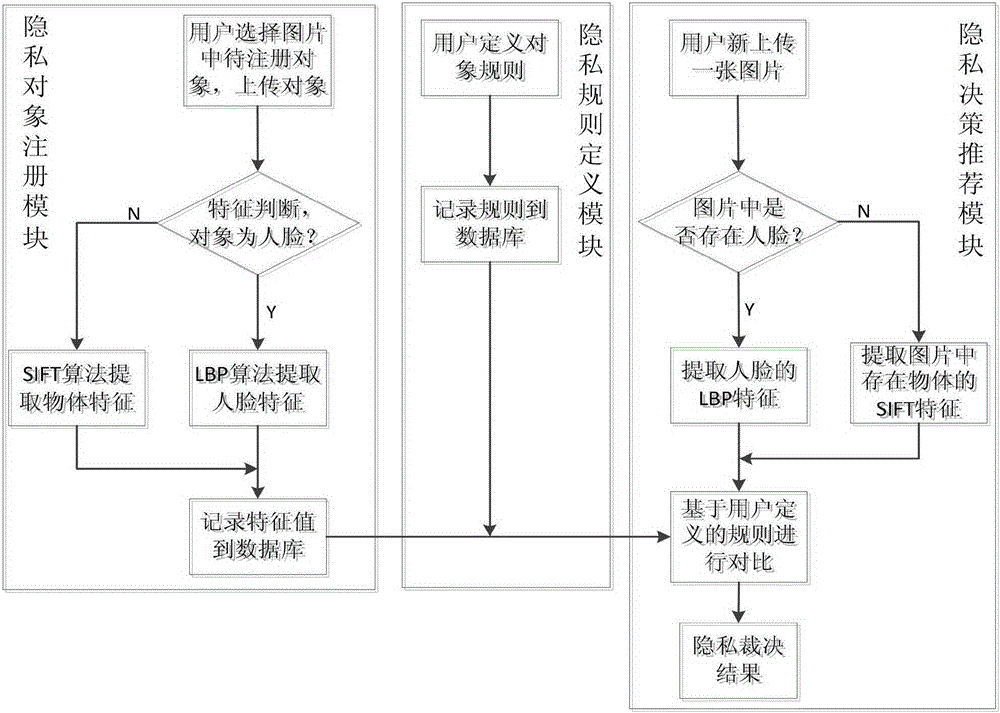
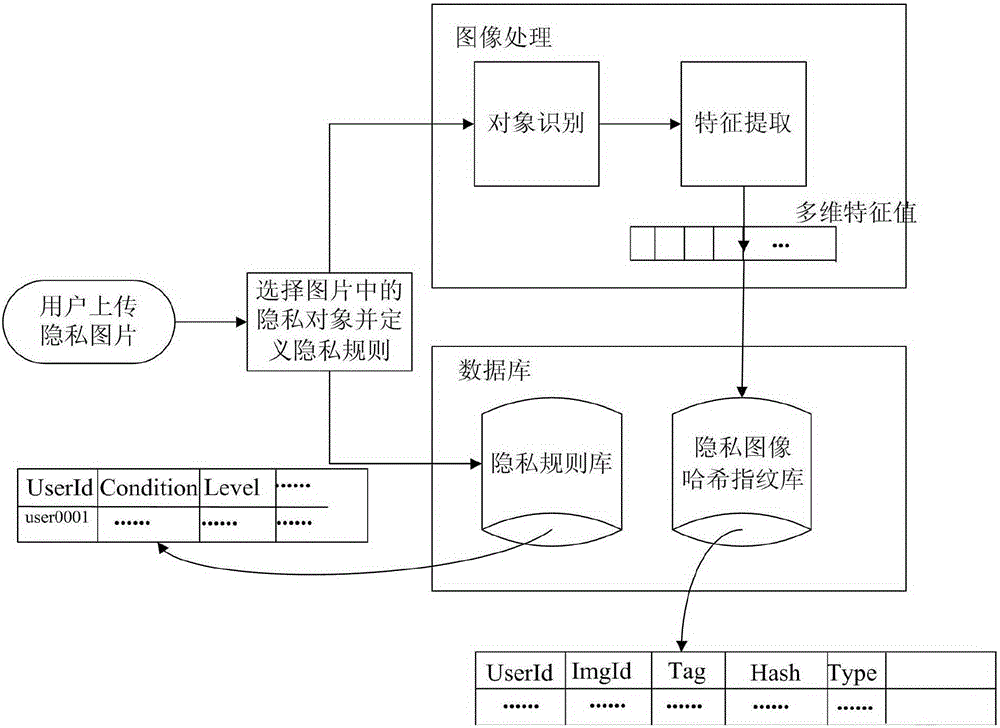
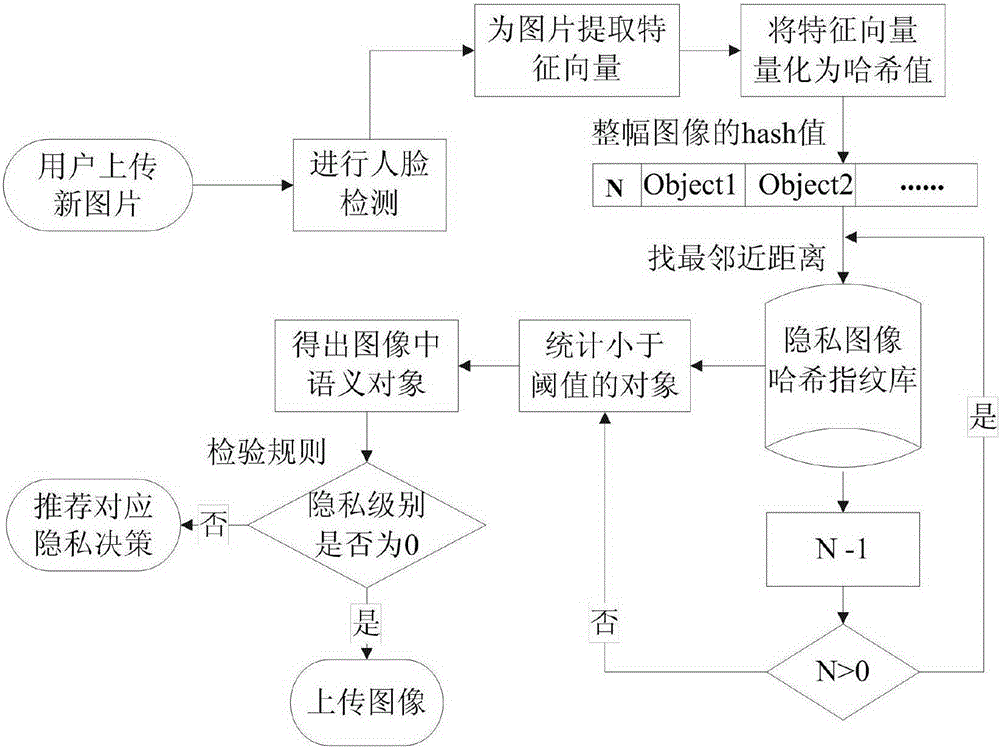
Image privacy decision recommendation system and method under social network on the basis of privacy rule and perceptual Hash
ActiveCN105260676AReduce the risk of privacy breachesSuitable for personalizationData processing applicationsWeb data indexingInternet privacyPrivacy rule
The invention discloses an image privacy decision recommendation system and method under a social network on the basis of a privacy rule and perceptual Hash. The invention is characterized in that the system comprises a privacy object registration module, a privacy rule definition module and a privacy decision recommendation module, wherein the privacy object registration module provides a registration function of an object to be protected for a user; the privacy rule definition module defines a privacy security level for a to-be-protected objet of the user; and the privacy decision recommendation module identifies a to-be-uploaded object of the user, compares the to-be-uploaded object of the user with a protected object in a Hash fingerprint database and a privacy rule in a privacy rule base, and finally submits the privacy security level of the to-be-uploaded object to the privacy decision recommendation module of the user. The quick and convenient automatic calculation of the privacy level and decision recommendation can be realized, and the leakage risks of individuals and the families of the individual can be effectively lowered so as to greatly improve the protection safety of user individual image privacy.
Owner:HEFEI UNIV OF TECH
Anonymous area generation method and location privacy protection method
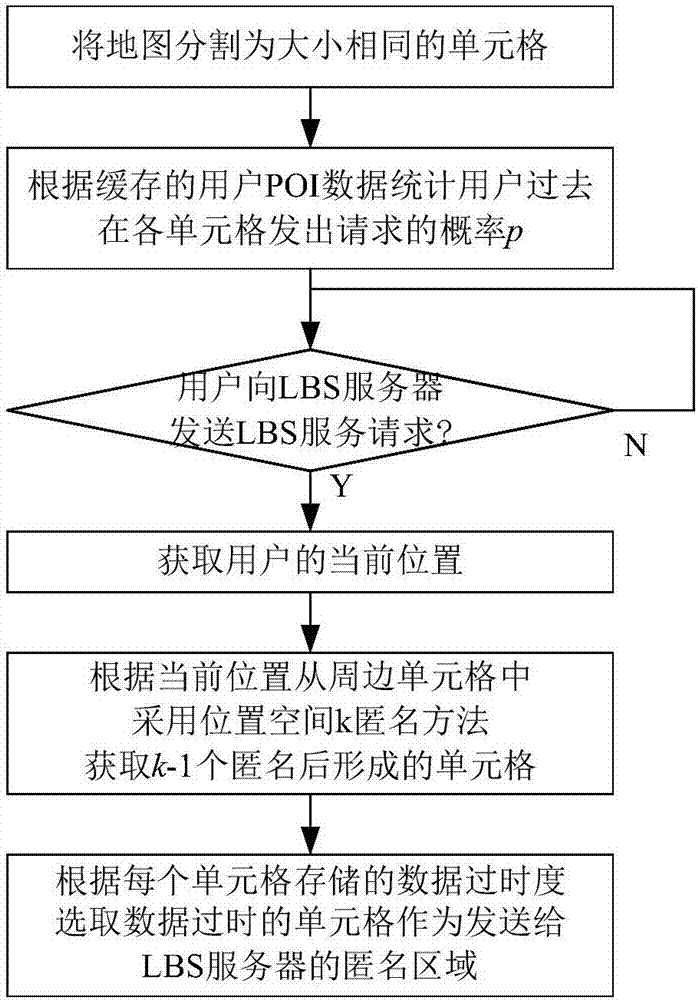
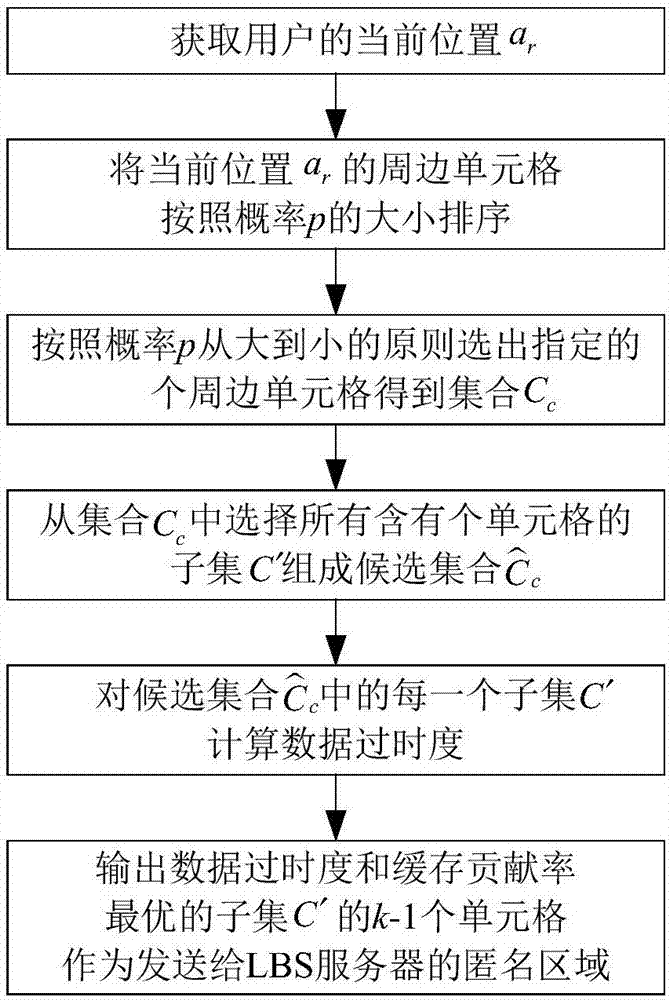
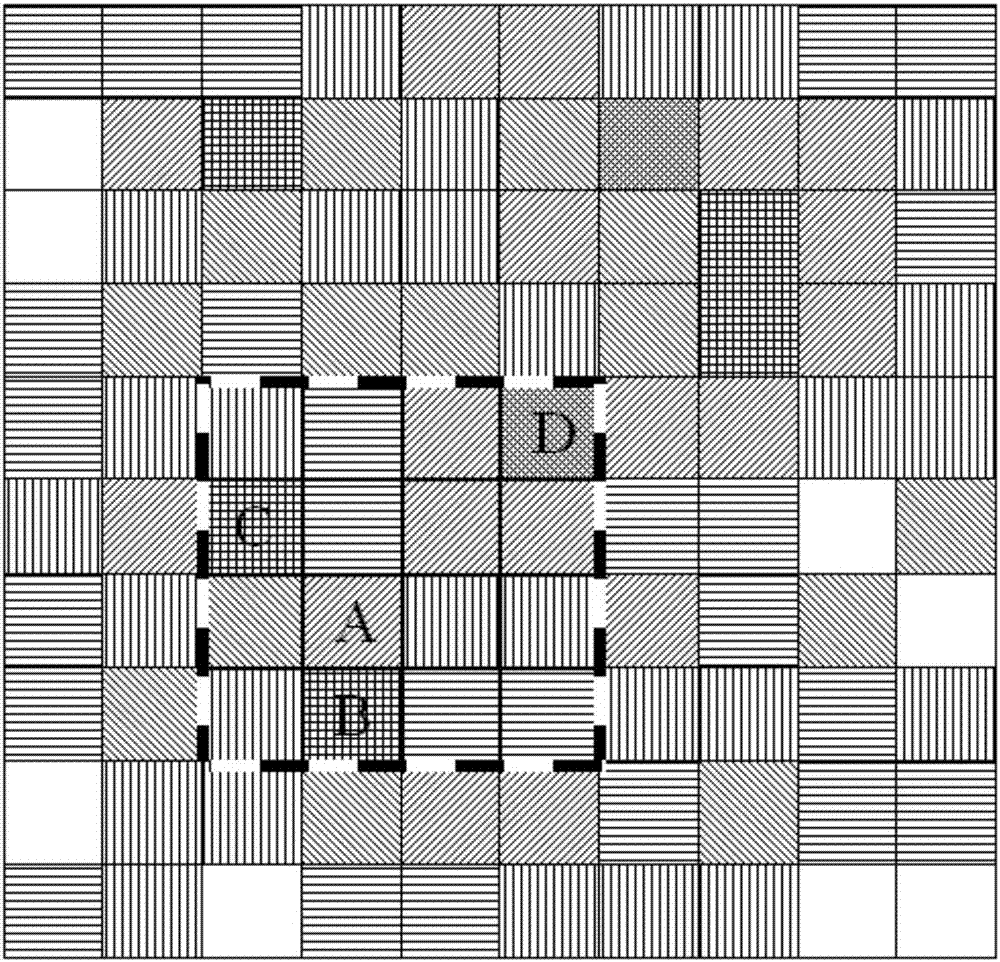
InactiveCN106954182AEfficient use ofReduce overheadTransmissionLocation information based serviceProtection mechanismPrivacy protection
The invention discloses an anonymous area generation method and a location privacy protection method. The anonymous area generation method is used for generating an anonymous area based on a spatial K anonymous method; a multi-level access protection mechanism is adopted in the location privacy protection method; the location privacy protection method performs cache normalization; when a target user sends a LBS request, POI data is obtained according to the priority levels of a target user local, a neighbour user in a network and a LBS server; furthermore, when the POI data is obtained from the LBS server, generation of the anonymous area is carried out by adopting the anonymous area generation method; the LBS request is sent to the LBS server based on the anonymous area as the anonymous location of the user; and furthermore, the POI data returned by the LBS server is output. By means of the anonymous area generation method and the location privacy protection method disclosed by the invention, the location privacy of users is protected in combination with a cache method and the spatial K anonymous method; therefore, inquiry requests sent by users can be reduced to the most extent; furthermore, the privacy protection level of the users can be improved; and thus, the problems that the burden of the server and a channel is too heavy and the information repetition utilization rate is low can be well solved.
Owner:步步高电子商务有限责任公司
Balance management method, system and device and storage medium
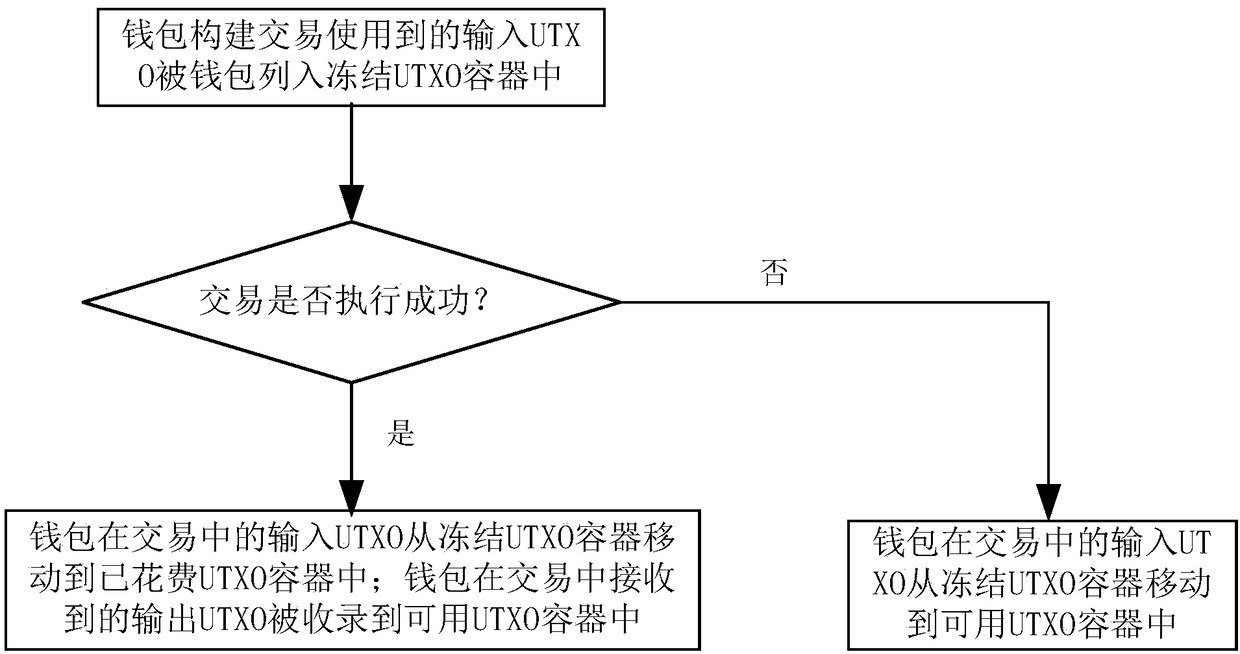
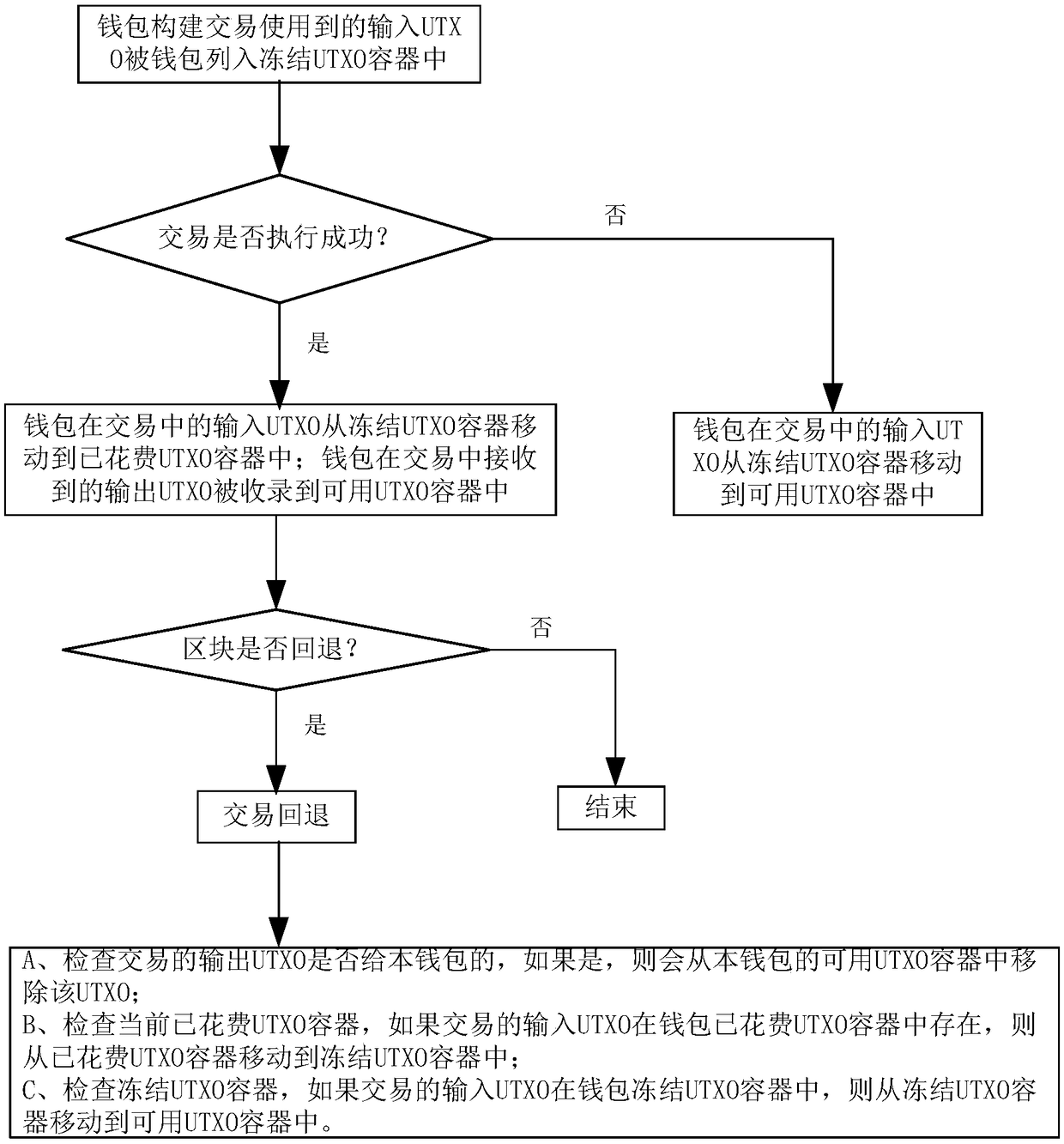
InactiveCN108876335ASolve scalabilityAddress flexibilityPayment protocolsPayment circuitsOperating systemBlockchain
The invention discloses a balance management method, system and device and storage medium, and belongs to the technical field of block chains. The method comprises the steps that a wallet constructinginput UTXO used in transaction and assigned to a frozen UTXO container by the wallet; if the transaction is successfully executed, moving the input UTXO of the wallet in the transaction from the frozen UTXO container to a spent UTXO container; and recording the output UTXO received by the wallet in the transaction into a usable UTXO container; if the transaction is executed unsuccessfully or thetransaction is overtime due to the fact the transaction is not executed for a long time, moving the input UTXO of the wallet in the transaction from the frozen UTXO container to a usable UTXO container. The method can improve the expansibility and flexibility of an account balance management mode. The privacy safety of a user can be improved, and the risk of privacy leakage is reduced.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Internet of Things service unloading decision-making methods based on edge computing and deep reinforcement learning
PendingCN111641681APowerful resource management and orchestration capabilitiesMinimize delayResource allocationTransmissionResource managementDecision-making models
Owner:STATE GRID CORP OF CHINA +1
Method for obtaining behavioral data and device thereof
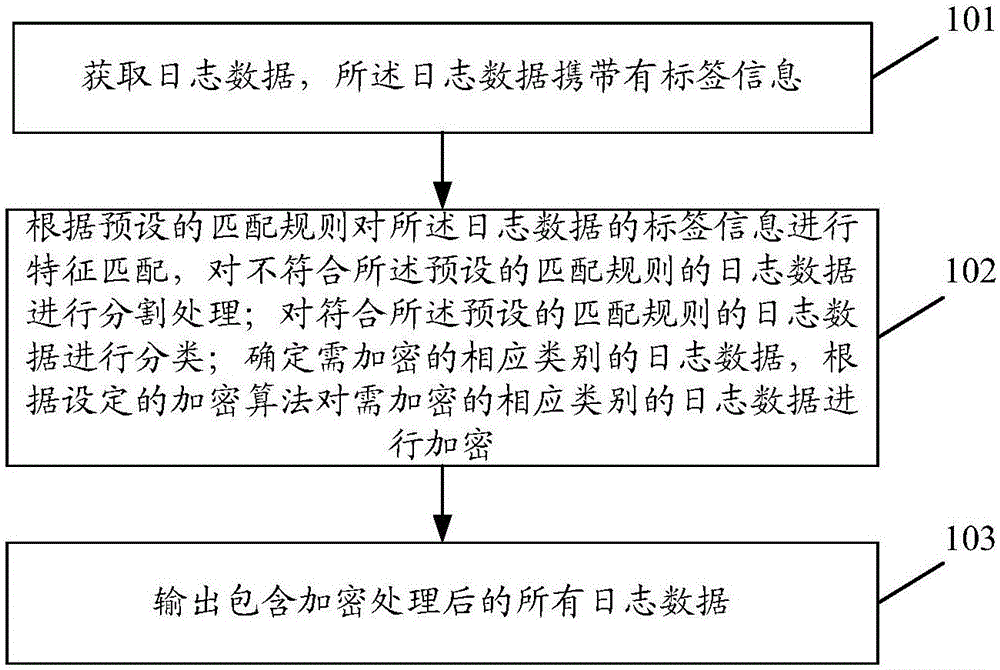
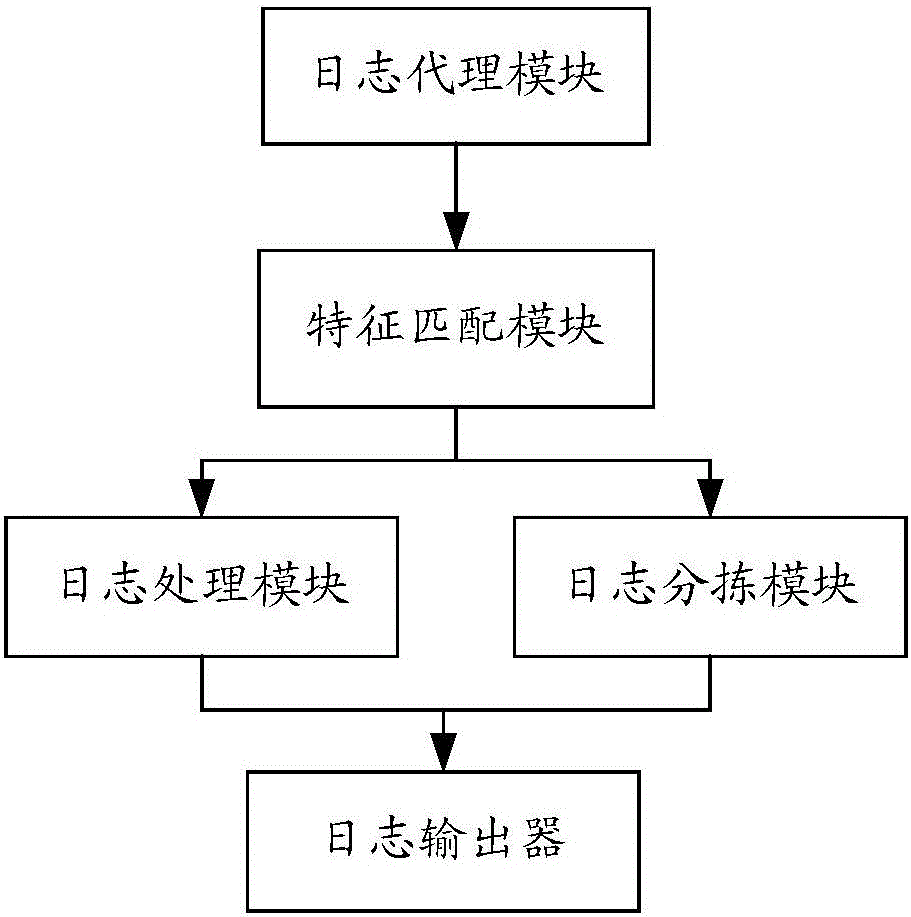
ActiveCN106650493AReduce the risk of privacy leakageReduce the risk of privacy breachesDigital data protectionFeature matchingData export
The invention discloses a method for obtaining behavioral data. The method for obtaining the behavioral comprises log data obtaining, wherein the log data carries with tagged information. The method for obtaining the behavioral data also comprises feature matching for the tagged information of the log data according to the matching rule preset, segmentation processing for the log data that meets the matching rule preset and classification processing for the log data that is unmet, the relevant log data defining and the relevant data encrypting according to the encryption algorithm preset, the encrypted data exporting. The invention further discloses a device for the behavioral data.
Owner:MIGU CO LTD
Information protection method and terminal device
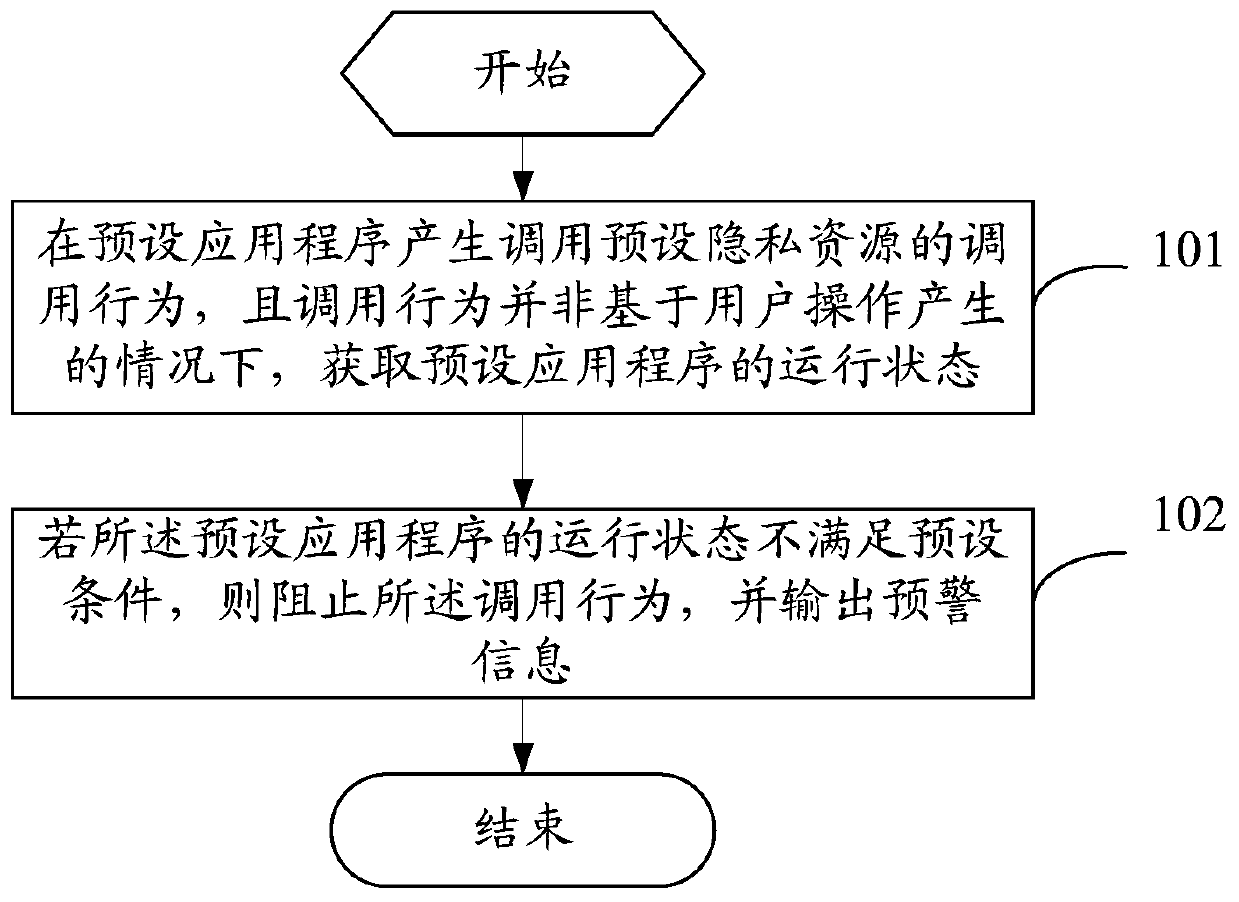
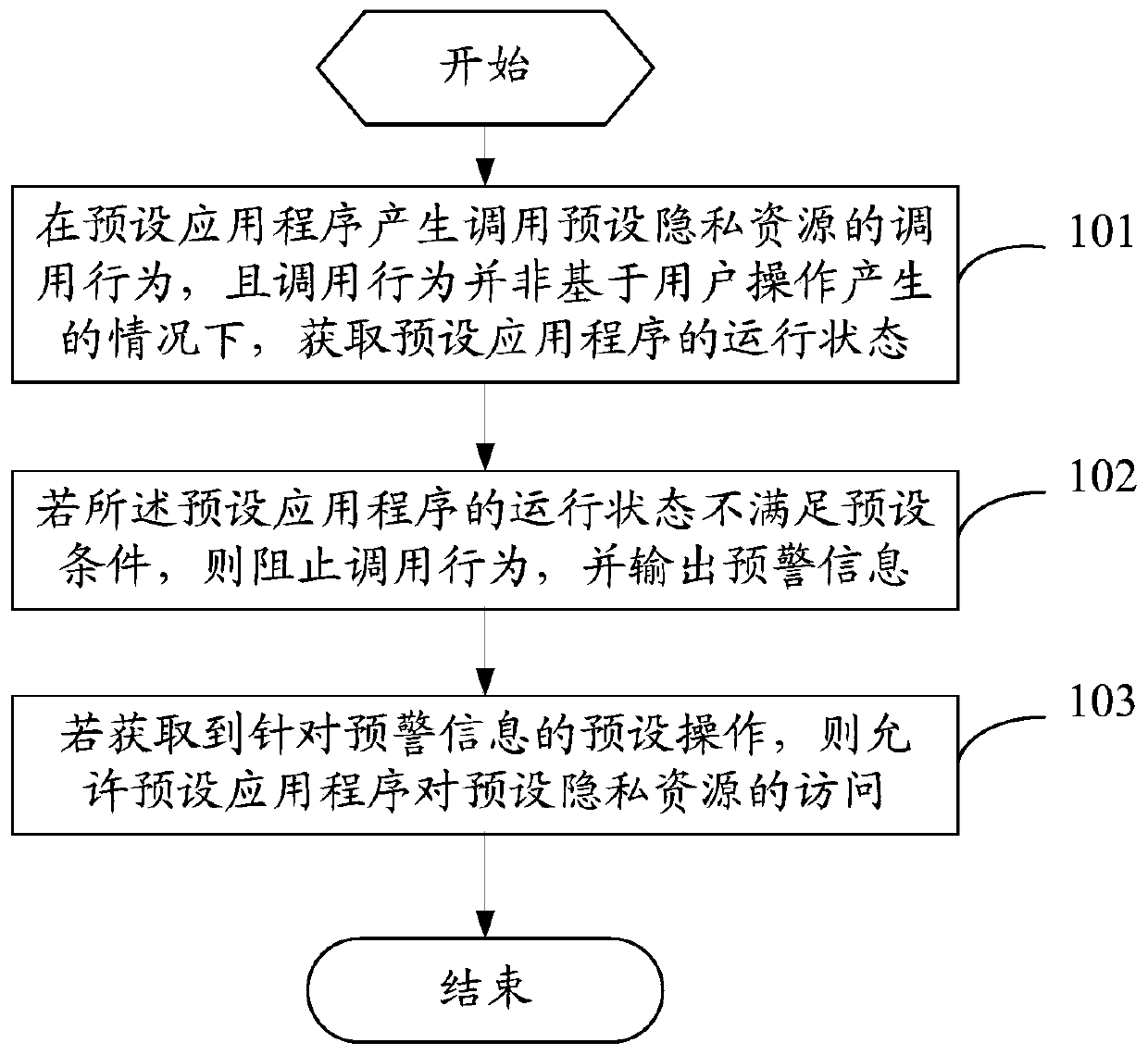
PendingCN109918930AReduce the risk of privacy breachesImprove securityDigital data protectionInternet privacyUser privacy
The embodiment of the invention provides an information protection method and a terminal device. The method comprises the steps that under the condition that a preset application program generates a calling behavior for calling preset privacy resources and the calling behavior is not generated based on user operation, the running state of the preset application program is obtained, and the privacyauthority of terminal equipment allows the preset application program to call the preset privacy resources; and if the running state of the preset application program does not meet the preset condition, the calling behavior is stopped and early warning information is outputted. According to the method, for the preset application program that is allowed by the privacy permission of the terminal equipment to call the preset privacy resource, the preset privacy resource cannot be called under all conditions. And under the condition that the running state does not meet the preset condition, the user can still control the calling behavior of calling the preset privacy resource by the preset application program, so that the risk of user privacy information leakage is reduced, and the security of user privacy information protection is improved.
Owner:VIVO MOBILE COMM CO LTD
Remote hosting system, method and device for mobile terminal
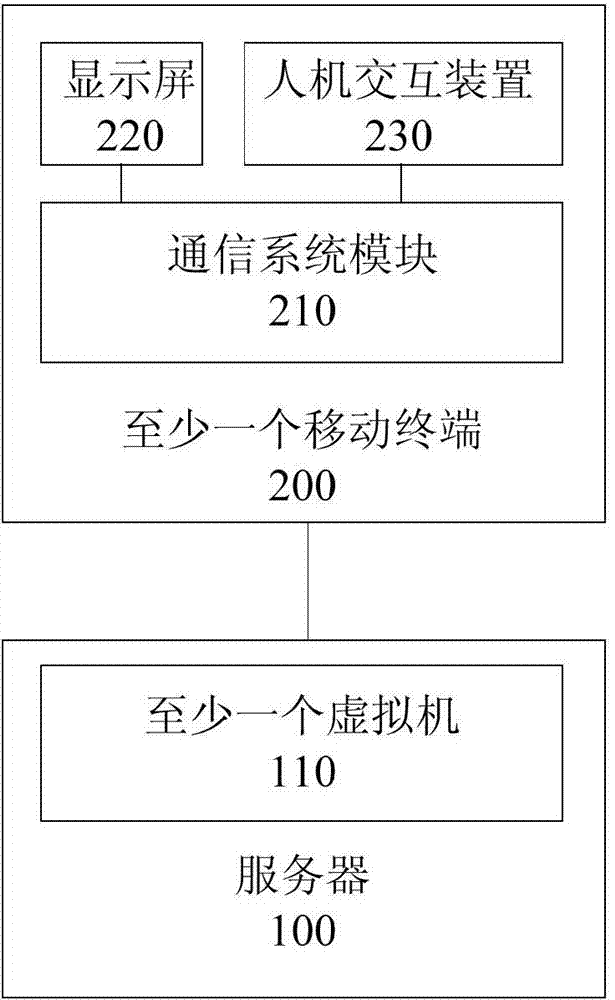
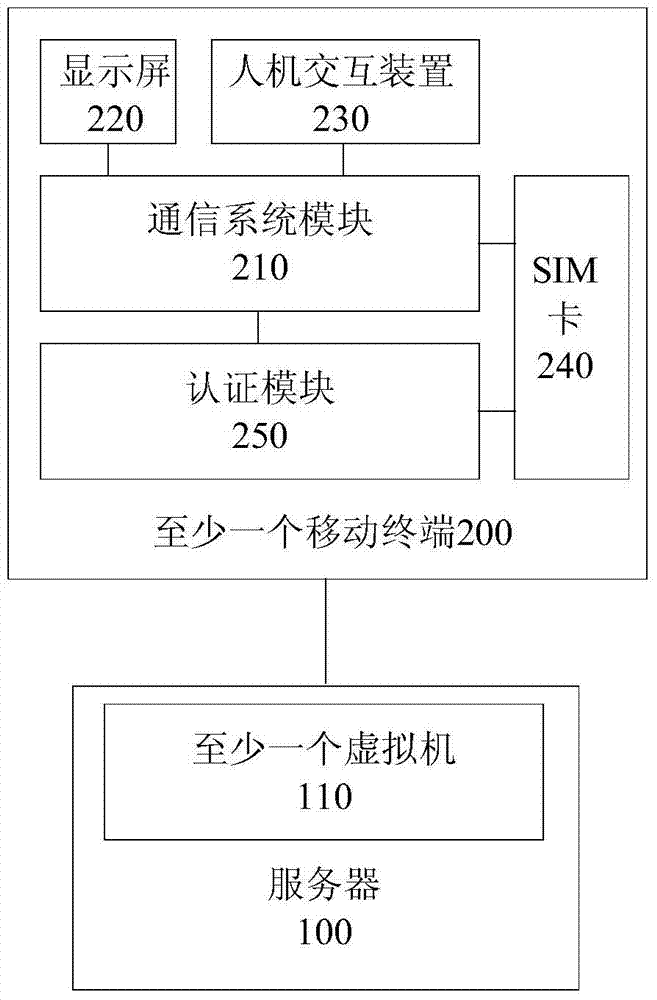
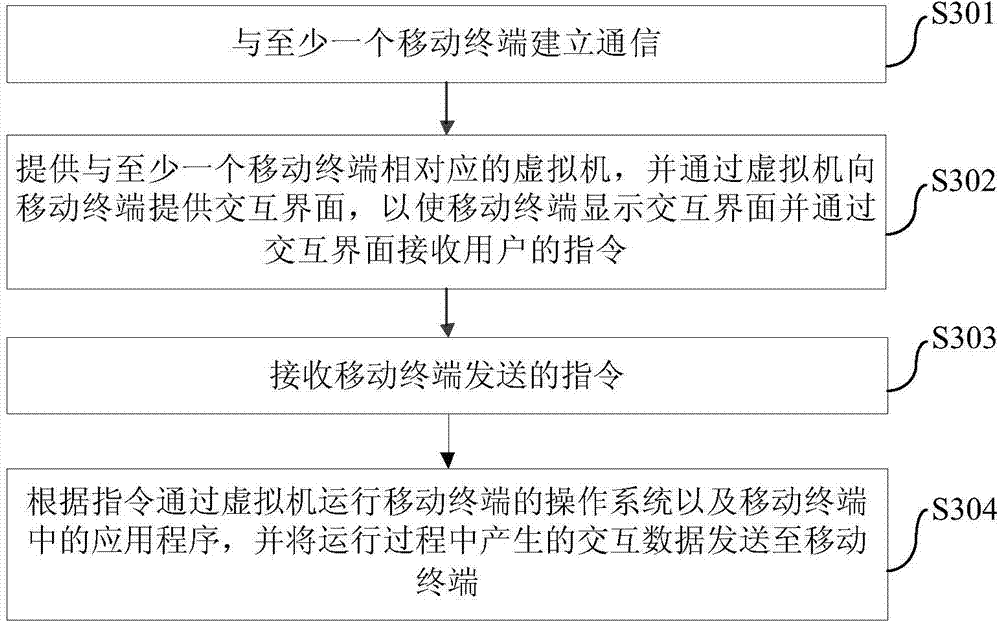
InactiveCN104753996ALow hardware requirementsImprove operational efficiencyTransmissionOperational systemHuman–computer interaction
The invention discloses a remote hosting system, method and device for a mobile terminal. The system comprises a server and at least one mobile terminal, wherein the server is used for providing at least one virtual machine, each virtual machine is corresponding to one mobile terminal, the virtual machine is used for running the operating system of the mobile terminal and the application programs in the mobile terminal, when the server communicates with the mobile terminal, the virtual machine provides interactive interface and interactive data for the mobile terminal; the at least one mobile terminal comprises a communication module which communicates with the server, a display screen used for displaying the interactive interface and interactive data received from the server, and a man-machine interaction module used for receiving the commands of a user and sending the commands of the user to the server through the communication module. The remote hosting system is capable of improving the running efficiency of the operating system and application programs, simplifying the necessary structure of the mobile terminal, improving the safety and improving the user experience.
Owner:BYD CO LTD
Research on privacy protection mechanism based on user behavior
InactiveCN109271806AProtection securityImprove service qualityData processing applicationsCharacter and pattern recognitionUser needsPrivacy protection
Research on privacy protection mechanism based on user behavior. With the development of mobile Internet technology, social network has gradually become an important part of people's daily life. Usersdisclose personal information and share real-time dynamic in various social network platforms at the same time, but also brings the risk of privacy disclosure. Users need a privacy protection mechanism to more effectively protect their personal information on mobile social platforms from abuse. The invention aims at the problem that the current privacy protection method can not protect the privacy data of users in the mobile Internet very well, be combined with the characteristics of user behavior in mobile Internet, a privacy protection mechanism based on user behavior in mobile Internet isproposed and applied to mobile social APP, which provides better data protection for users, reduces the risk of privacy disclosure and improves the quality of service of mobile Internet.
Owner:TONGJI UNIV
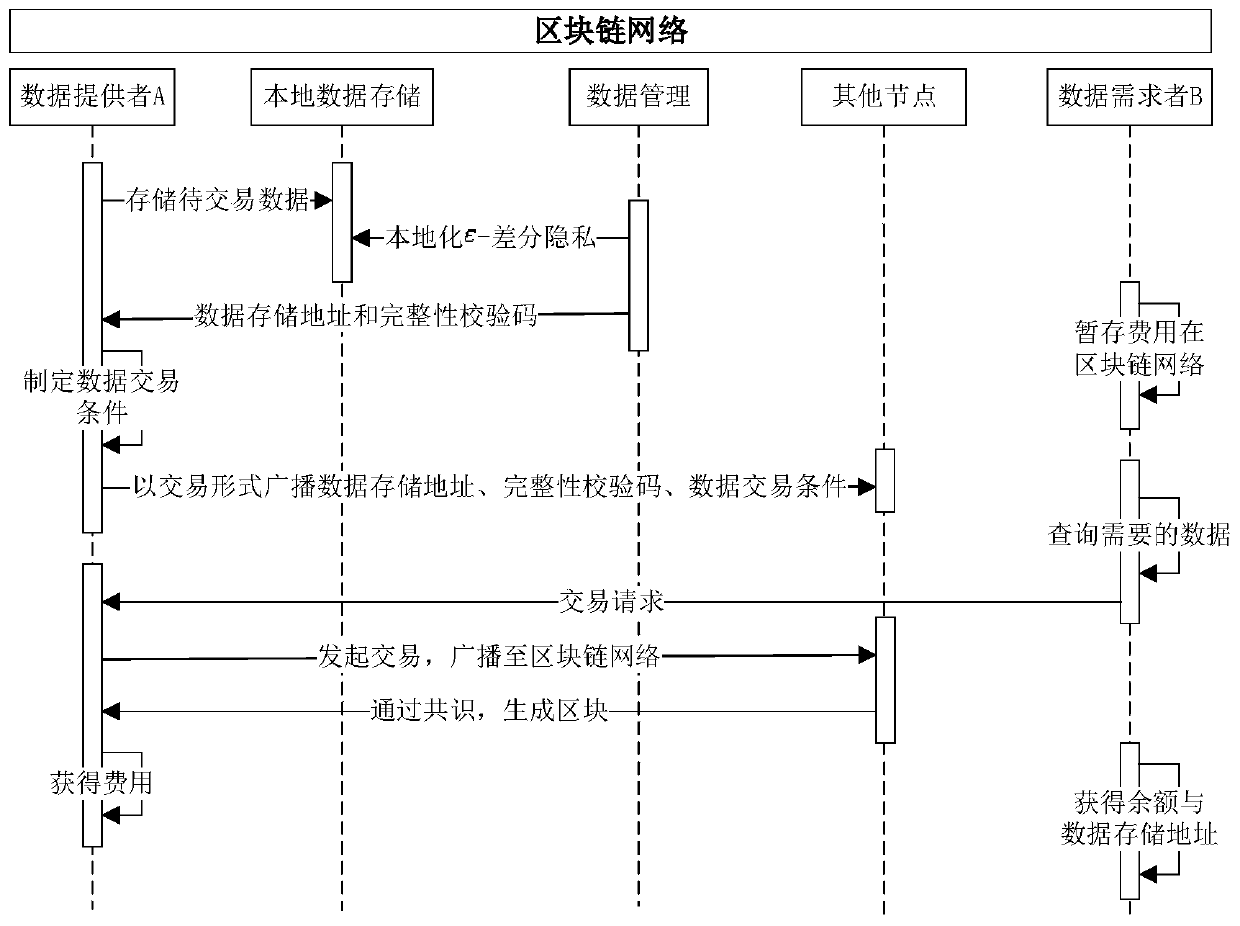
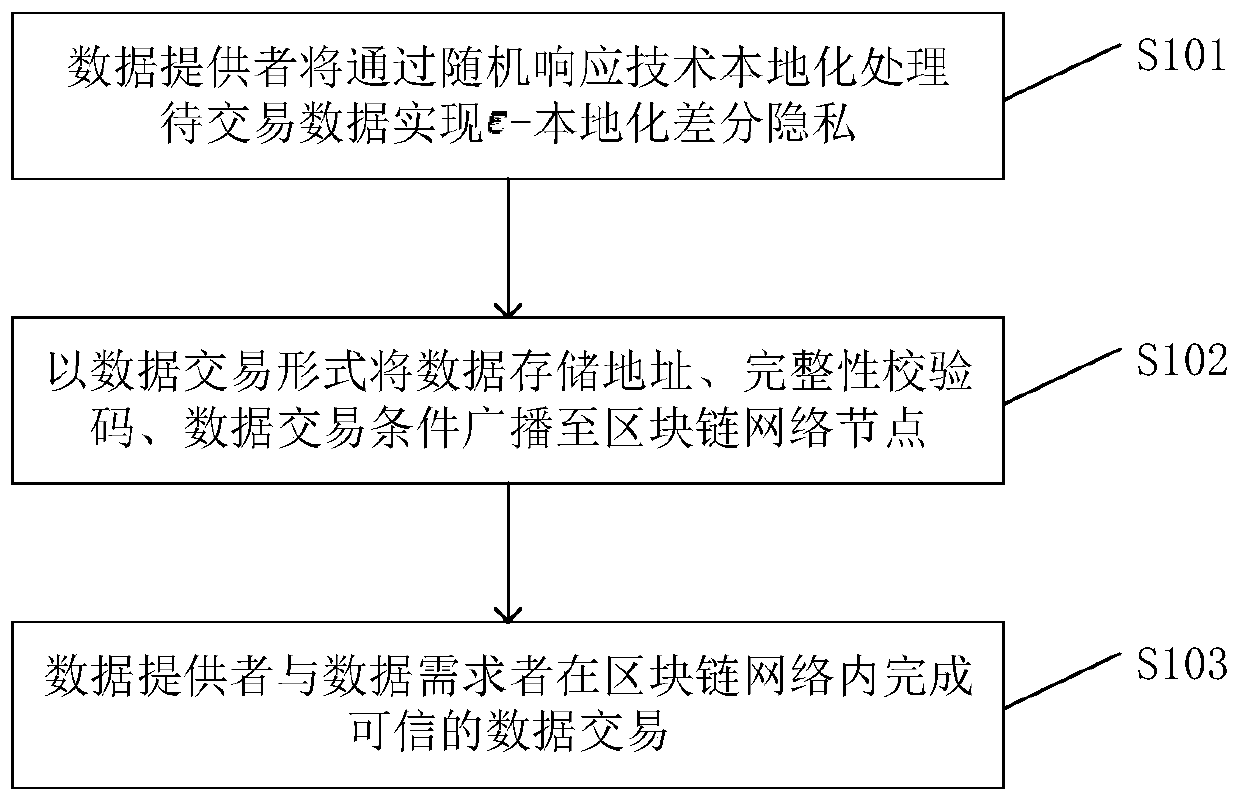
Data transaction localized differential privacy protection method and device based on block chain
InactiveCN110147996ATiming cannot be tampered withAddress privacy breachesPayment protocolsData providerTransaction data
The invention discloses a data transaction localized differential privacy protection method and device based on a block chain, and mainly solves the problem of privacy leakage of an existing centralized data transaction platform. The method comprises the steps that a data provider locally processes to-be-transacted data through a random response technology to achieve Epsilon-local differential privacy; the data storage address, the integrity check code and the data transaction condition are broadcasted to a block chain network node in a data transaction form; and the data provider and the datademander complete credible data transactions in the blockchain network. The privacy disclosure problem in a large number of data transaction scenes with high relevance and various requirements can besolved, and meanwhile the defects that an existing block chain-based data transaction method is poor in flexibility, high in calculation expenditure, low in practicability and the like are overcome.
Owner:CENTRAL UNIVERSITY OF FINANCE AND ECONOMICS
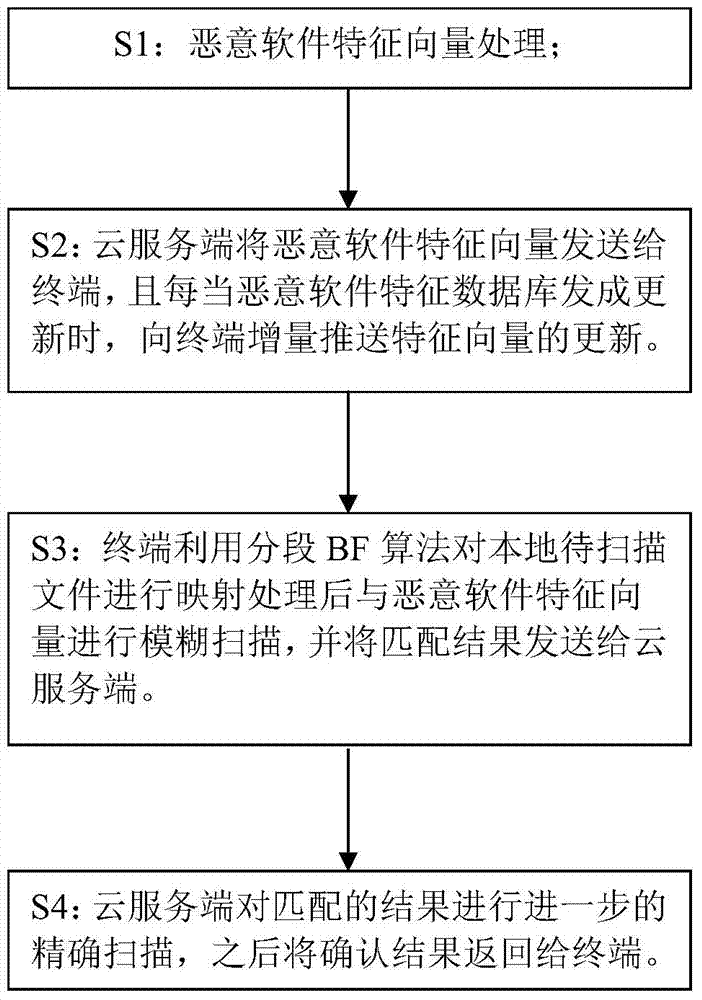
Method and system for cloud detection of malicious software based on Hash characteristic vector
ActiveCN104850784AReduce the number of featuresAccurately locate suspect featuresPlatform integrity maintainanceFeature vectorCloud detection
Owner:NAT UNIV OF DEFENSE TECH
Privacy protection table data sharing algorithm based on clustering anonymity
ActiveCN110555316AEasy to useImprove usabilityDigital data protectionCluster algorithmPrivacy protection
The invention relates to a privacy protection table data sharing algorithm based on clustering anonymity, and the method comprises the steps: firstly carrying out the clustering of records in a tablethrough a k-medios clustering algorithm, and obtaining a plurality of data tables; performing anonymous processing on each data table in combination with the information loss amount to generate an anonymous data table; finally, adding noise to the sensitive attribute values in the anonymous data table, carrying out algorithm verification through example analysis and comparison with a classic k-anonymous algorithm MDAV. The availability and privacy of the algorithm are proved, and the algorithm has high application and popularization value.
Owner:SHIJIAZHUANG TIEDAO UNIV
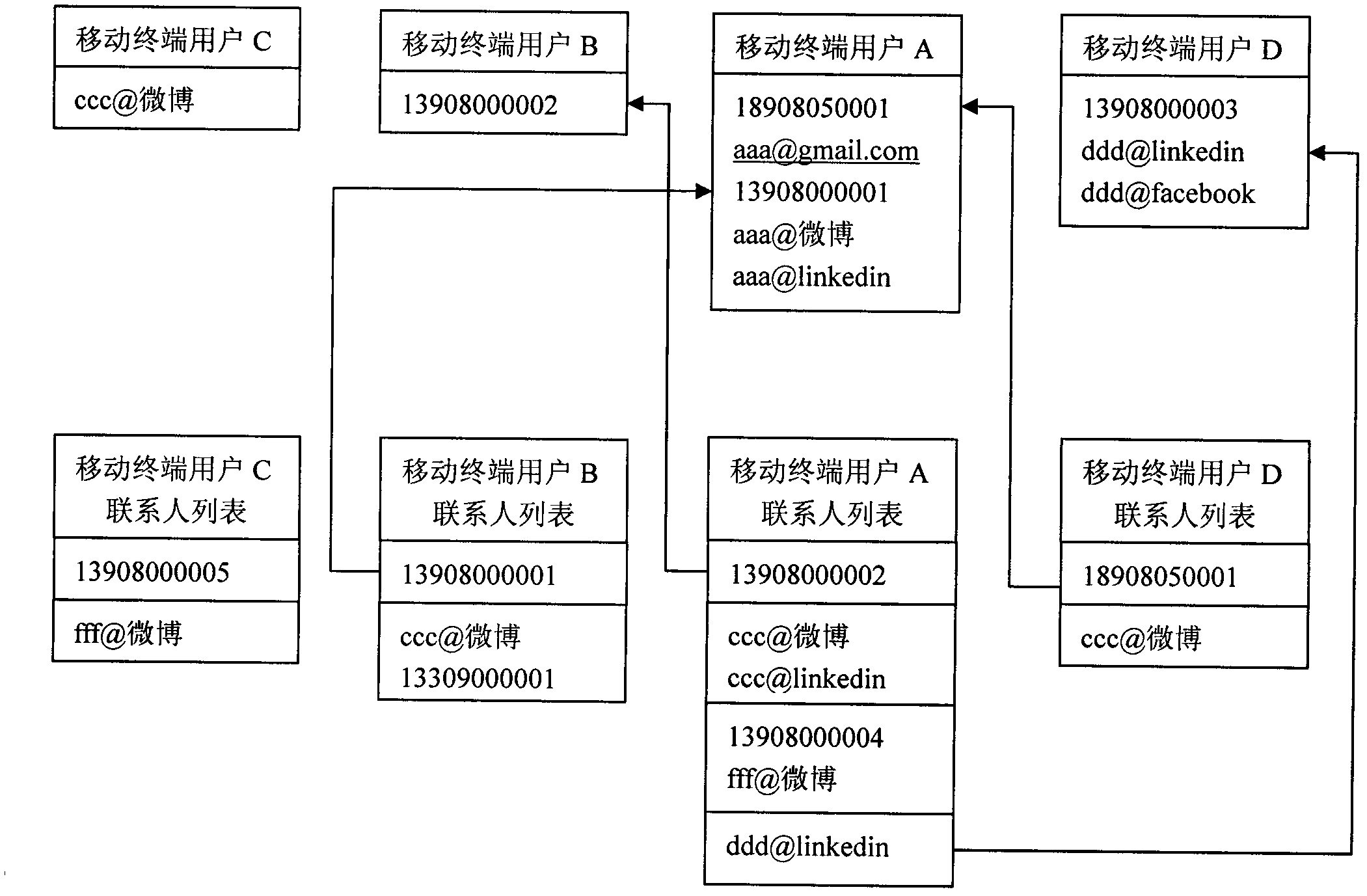
Method and system for friend relation authentication through contacts on mobile terminals
InactiveCN102664994AReduce the risk of privacy breachesSubstation equipmentTransmissionContact methodComputer science
The invention discloses a method and a system for friend relation authentication through contacts on mobile terminals. Contacts in the mobile terminals are stored as distributed data and dynamically submitted friend lists are matched by a server to confirm friend relation. For people being friends realistically (each of the both sides has the contact of the opposite side in mobile terminals), a redundant authentication process is omitted; and for people not in the friend relation in reality, harassment can be prevented.
Owner:PHICOMM (SHANGHAI) CO LTD
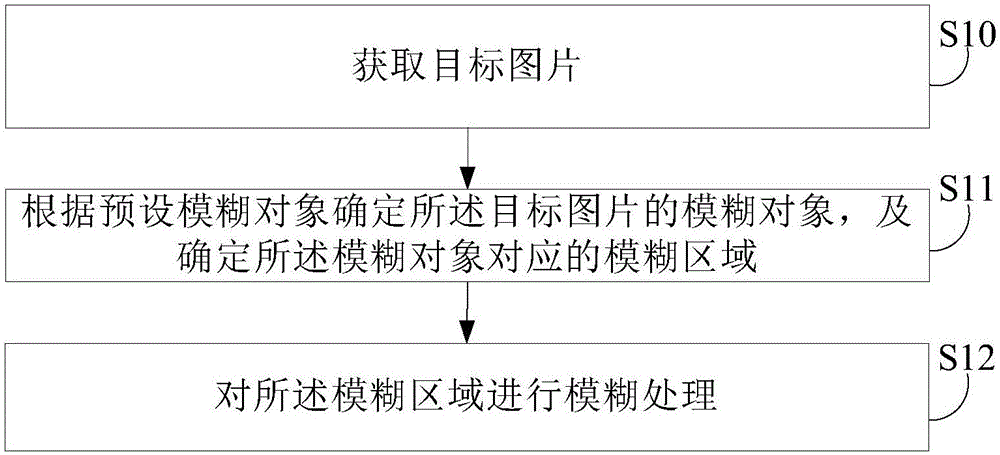
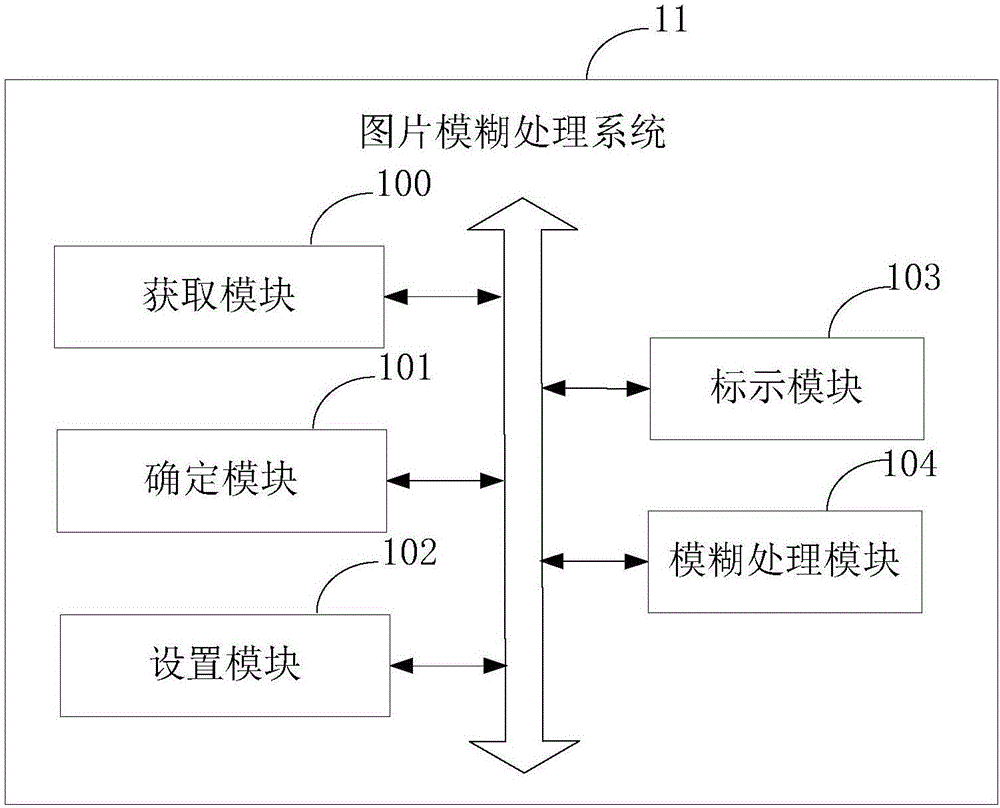
Picture fuzzy processing method and system
InactiveCN106600525AGuaranteed aestheticsReduce the risk of privacy breachesGeometric image transformationFuzzy objectData mining
The invention provides a picture fuzzy processing method and system. The picture fuzzy processing method includes obtaining a target picture; determining a fuzzy object of the target picture according to a preset fuzzy object and determining a fuzzy area corresponding to the fuzzy object; and performing fuzzy processing on the fuzzy area. The picture fuzzy processing method provided by the invention can automatically identify the fuzzy area corresponding to the fuzzy object in the picture, does not need a user to operate for multiple times, and reduces the risk of privacy leakage on the premise of ensuring that the picture is beautiful.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Track privacy protection method based on buffering and position predicating mechanism
ActiveCN107707566AReduce the risk of privacy breachesReduce interactionTransmissionCache hit ratePrivacy protection
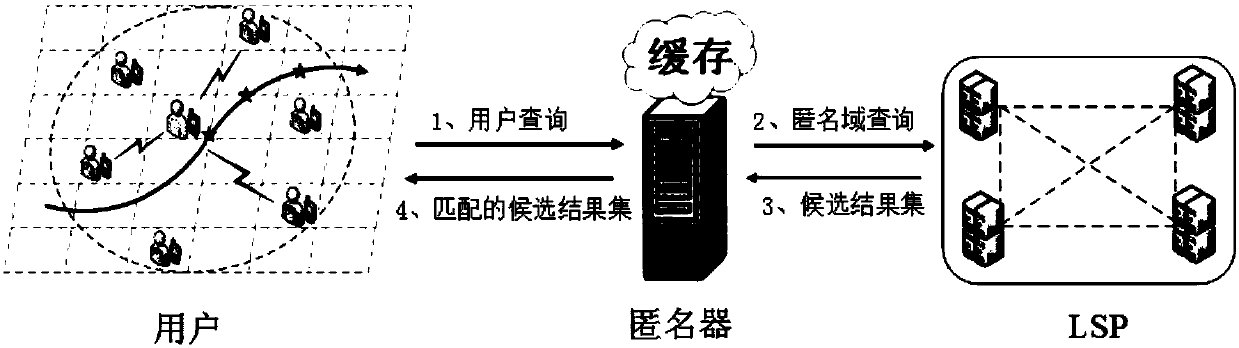
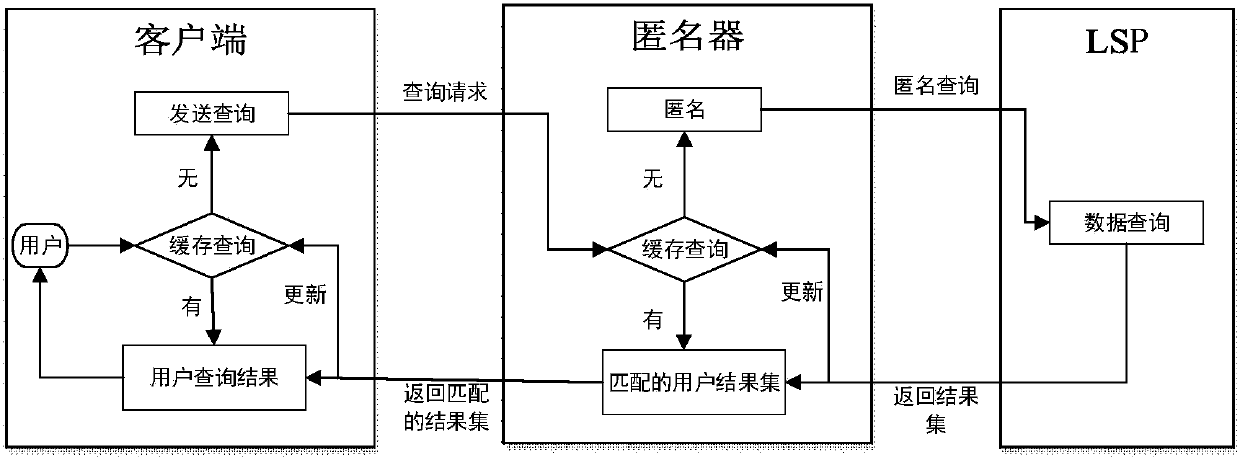
The invention discloses a track privacy protection method based on a buffering and position predicating mechanism. According to the method, a multistage buffering mechanism is used in a client and ananonymous device; and a candidate result set which is obtained through searching by a user is buffered, thereby supplying the candidate result set for use by the user at the subsequent searching pointin continuous LBS searching or use by other users, reducing interaction between the user and an LSP, and reducing risk of user information exposure to the LSP. Furthermore through a movement positionpredicating method based on Markov, an anonymous domain is formed according to data timeliness and user searching probability, thereby improving buffering hit rate and user track privacy protection,and reducing searching expenditure of the LBS server.
Owner:HUNAN UNIV OF SCI & TECH
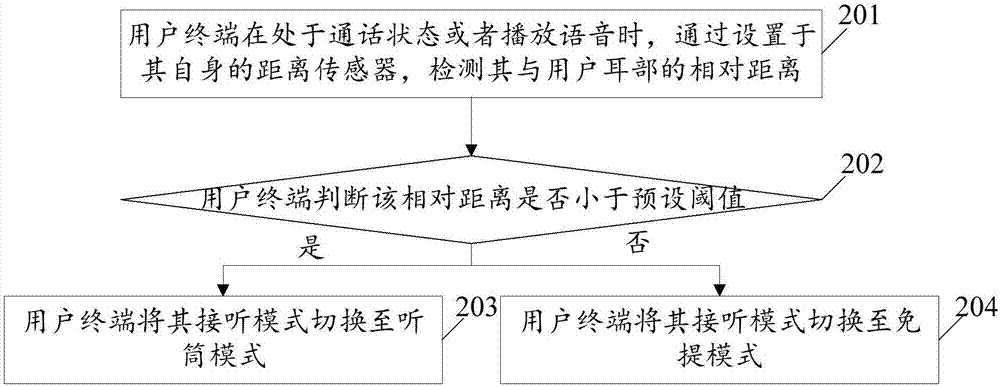
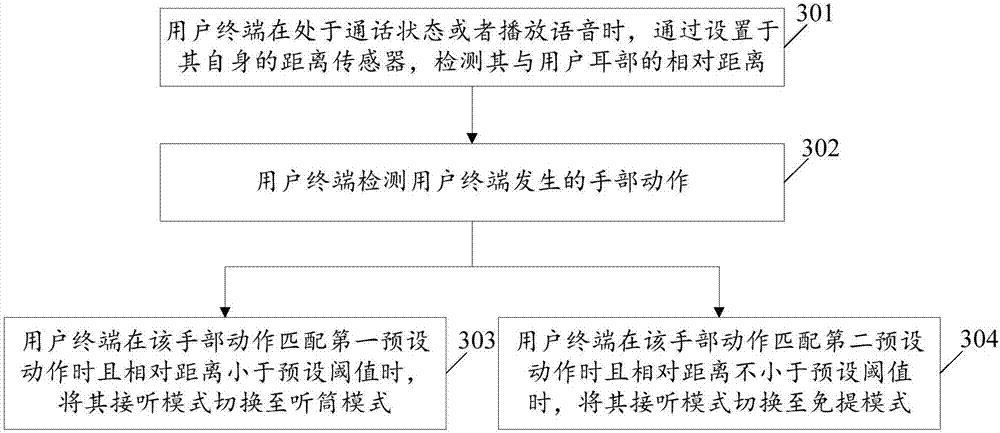
Switching control method and device for answering mode of user terminal and user terminal
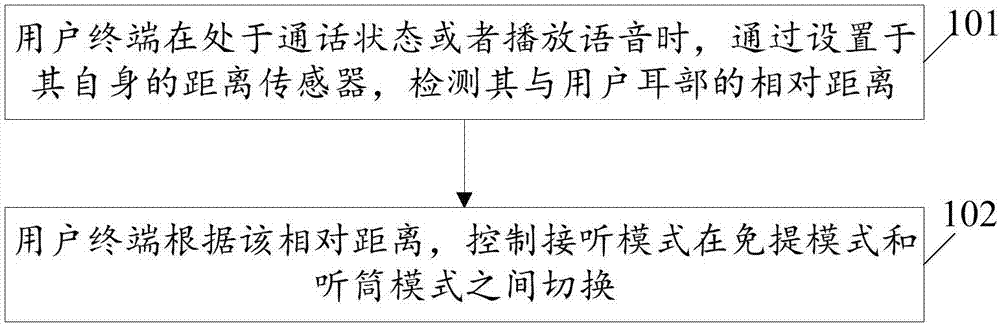
InactiveCN107026938APrevent eavesdroppingReduce the risk of privacy breachesSubstation equipmentComputer terminalHands free
The embodiment of the invention relates to the technical field of communication and discloses a switching control method and device for an answering mode of a user terminal and the user terminal. The method comprises the steps of when the user terminal is in a call state or plays a voice, detecting the relative distance between the user terminal and an ear of a user through a distance sensor arranged at the user terminal; and controlling the answering mode of the user terminal to be switched between a hands free mode and a telephone receiver mode according to the relative distance. Through application of the embodiment of the invention, the answering mode is smartly switched, the voice is prevented from being eavesdropped by others when a call is carried out or when the voice is played, a risk of leaking privacy is reduced, and the privacy of a user is protected.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Intelligent wristband equipment
ActiveCN111150189AAchieve hiddenAchieve exposureBraceletsWrist-watch strapsCamera lensPrivacy protection
The invention provides an intelligent wristband device, which can realize hiding and exposing of a camera lens so as to improve the privacy protection performance of the device and reduce the risk ofprivacy leakage of a user. The intelligent wristband equipment comprises an equipment main body and a camera module, and the camera module comprises a lens; a telescopic receding hole is formed in theside face of a shell of the equipment main body, the camera module is provided with a first position enabling the lens to be kept exposed out of the shell and a second position enabling the lens to be kept hidden in the shell, a telescopic mechanism is further installed on the equipment main body, and the camera module is switched between the first position and the second position by operating the telescopic mechanism so that the camera module can extend out of or retract into the telescopic receding hole. The camera lens can be hidden and exposed, the lens is exposed when the camera needs tobe used, and the lens is hidden in the shell when the camera does not need to be used, so that the privacy protection performance of the device is improved, and the privacy leakage risk of the user is reduced.
Owner:GEER TECH CO LTD
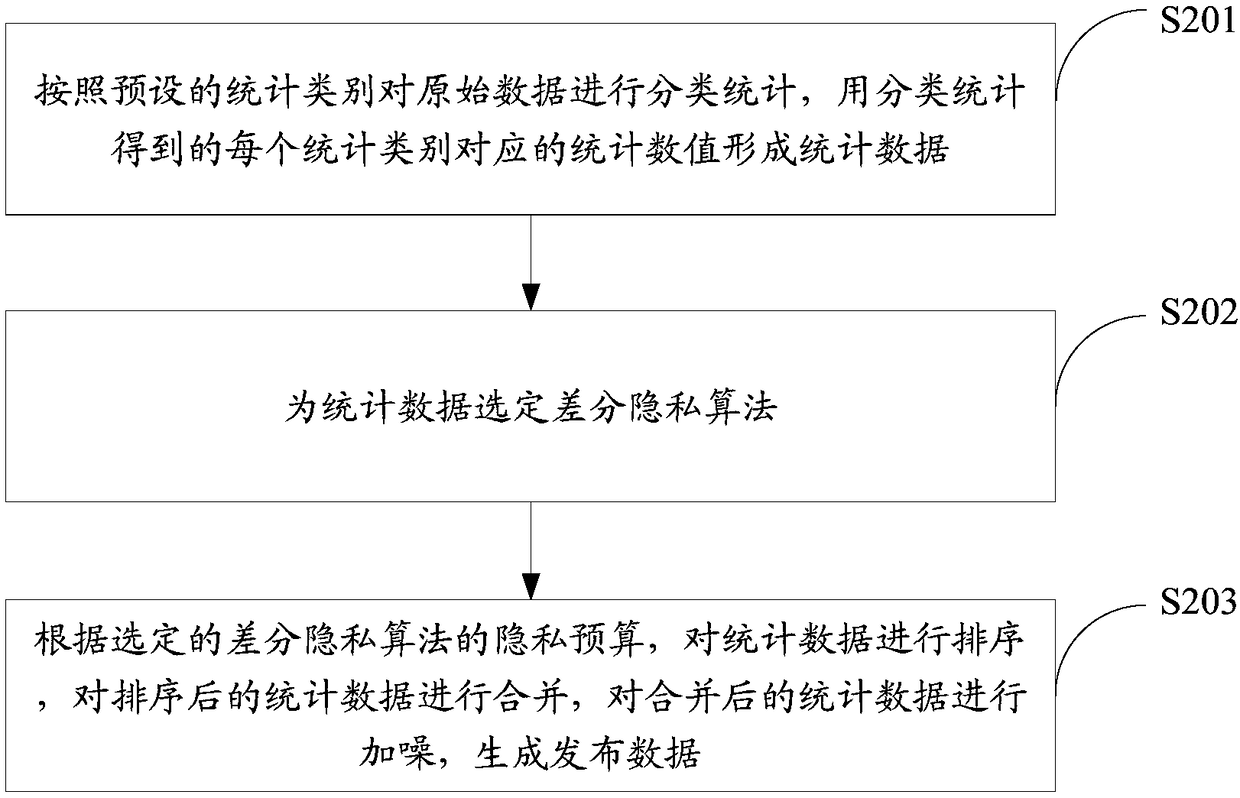
Published data generating method, device and server
InactiveCN109284620AReduce the risk of privacy breachesImprove usabilityDigital data protectionOriginal dataDifferential privacy
The embodiment of the invention discloses a published data generating method. The method comprises the following steps: classifying and counting the original data according to a preset statistical category, and forming statistical data by using the statistical values corresponding to each statistical category obtained by classification and statistics; Selecting a differential privacy algorithm forstatistical data; according to the privacy budget of the selected differential privacy algorithm, the statistical data are sorted, the sorted statistical data are merged, and the merged statistical data are noised to generate published data. The embodiment of the invention also discloses a generating device and a server for publishing data.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD +1
Training method and device of service prediction system
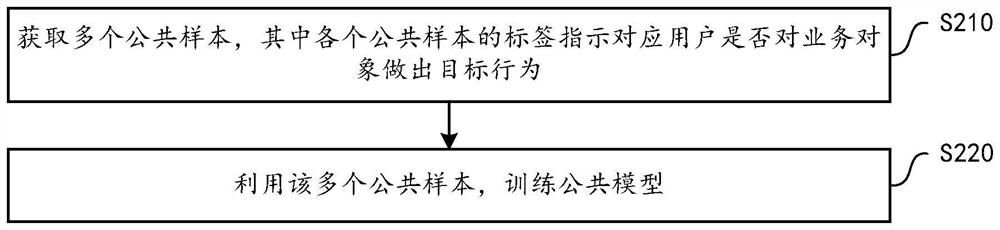
PendingCN113902473AImprove accuracyReduce the risk of privacy breachesCharacter and pattern recognitionDigital data protectionPrediction systemData mining
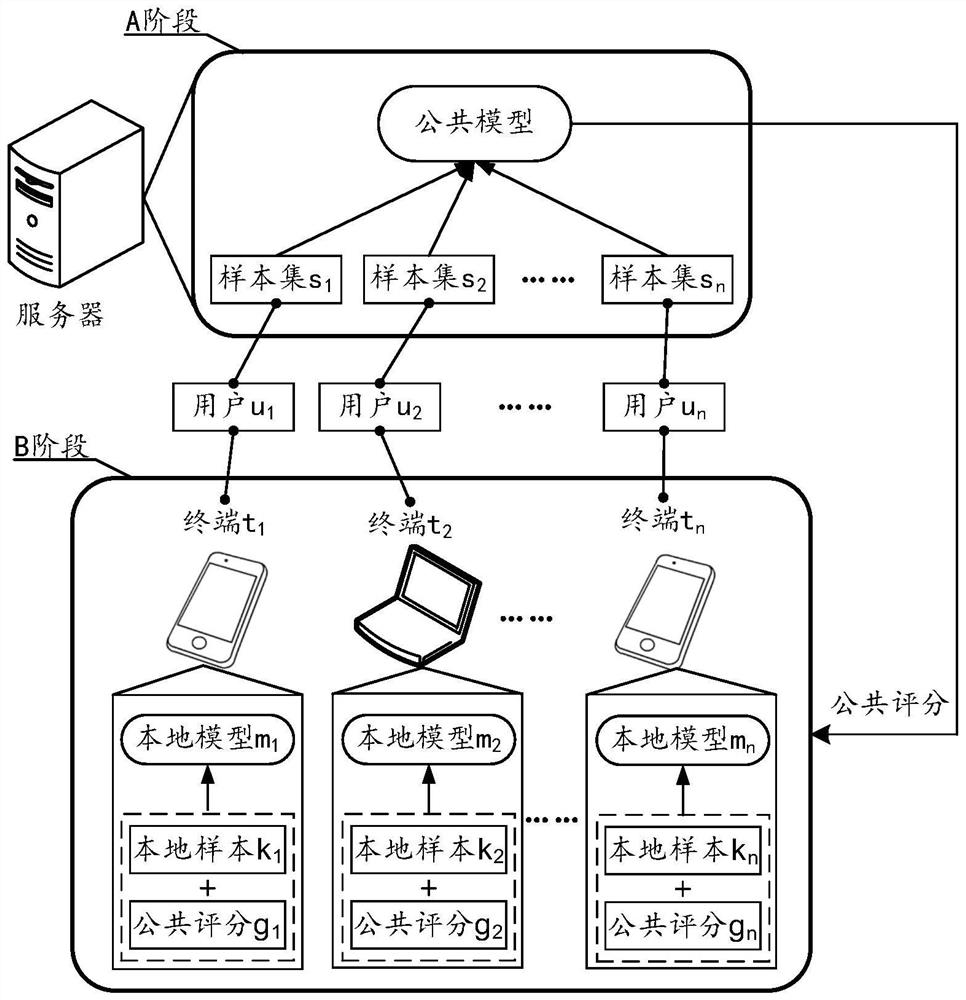
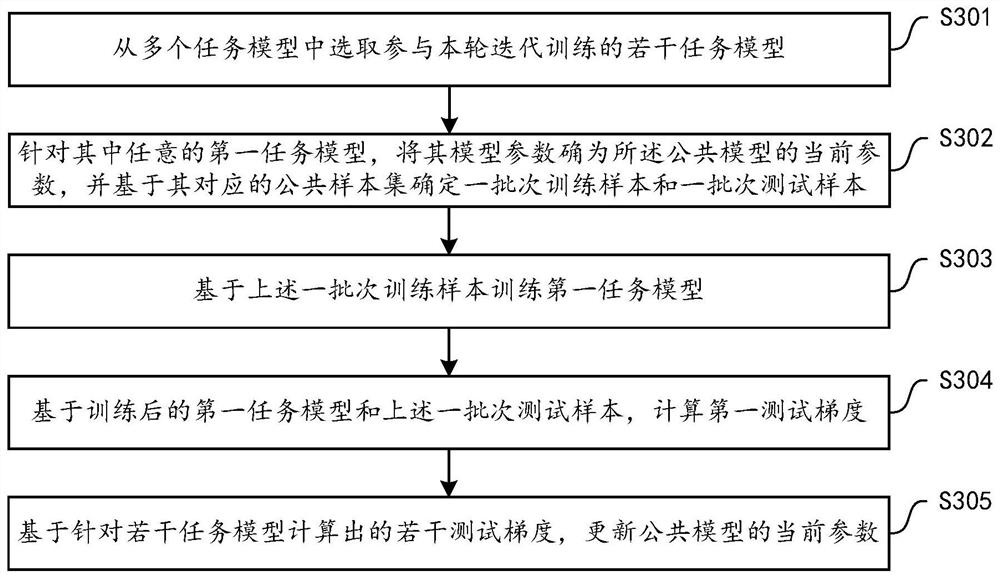
The embodiment of the invention provides a training method of a service prediction system. The service prediction system comprises a public model maintained by a server and a plurality of local models deployed in a plurality of user terminals. The method is executed by a server, and comprises the following steps: acquiring a plurality of common sample sets corresponding to a plurality of users, and training a common model by using the common sample sets; then, based on the trained public model, joint training including multiple rounds of iteration is carried out on the multiple local models, any round of iteration comprising the steps that for any first user, the public model is used for processing a public sample corresponding to the first user, a public prediction result is obtained, and the public prediction result is sent to a corresponding first terminal; then, receiving parameter update data of the first local model from the first terminal, which is determined based on the public prediction result and a local sample of the first terminal; and then, on the basis of a plurality of parameter update data received from the plurality of terminals, determining the parameters subjected to the joint update in the round, and providing the parameters to the plurality of terminals.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
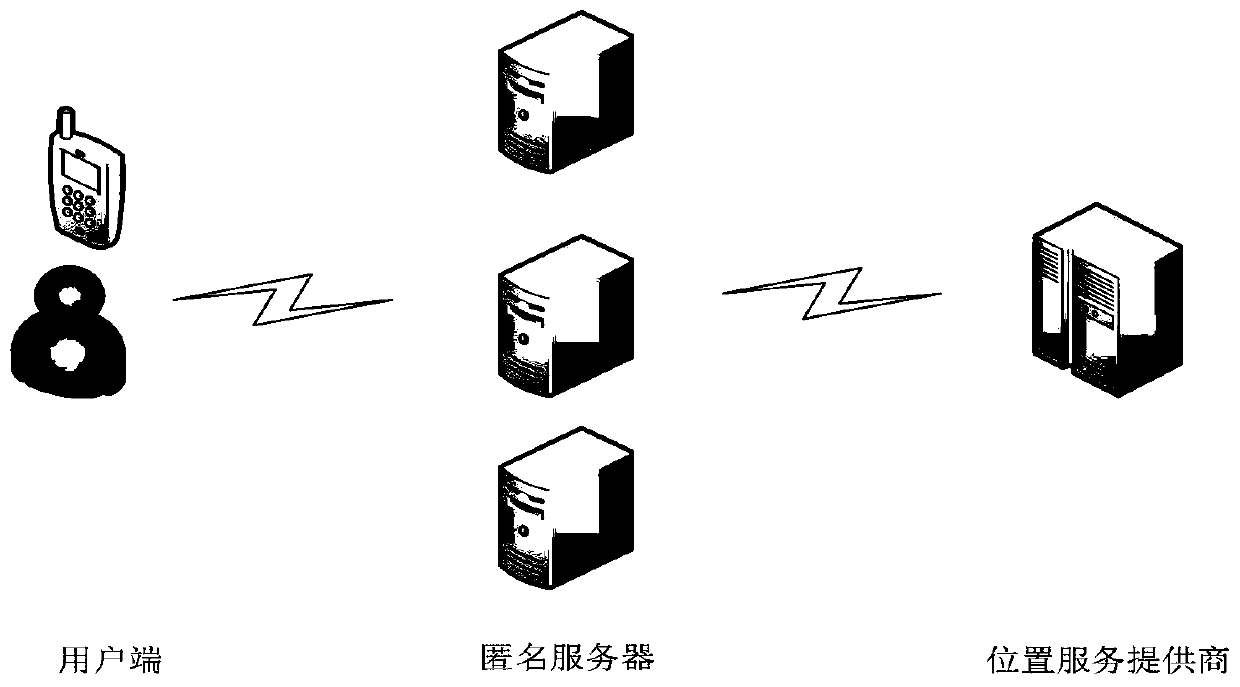
Track privacy protection method based on position service
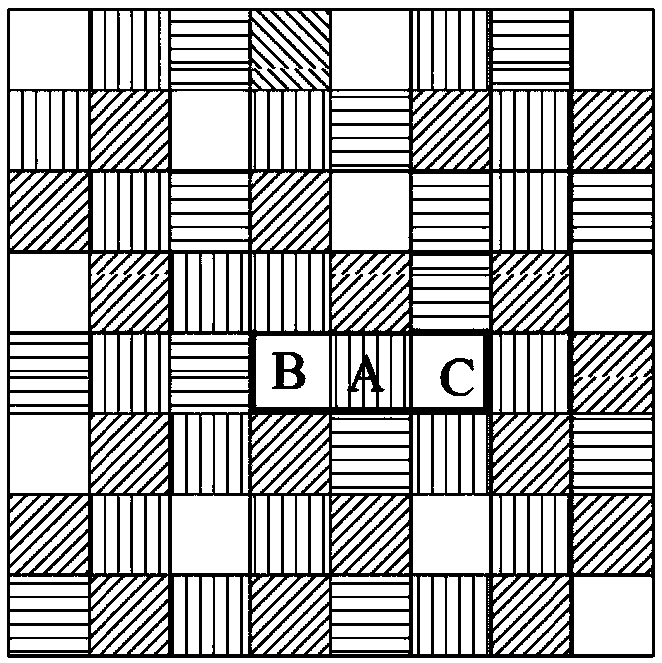
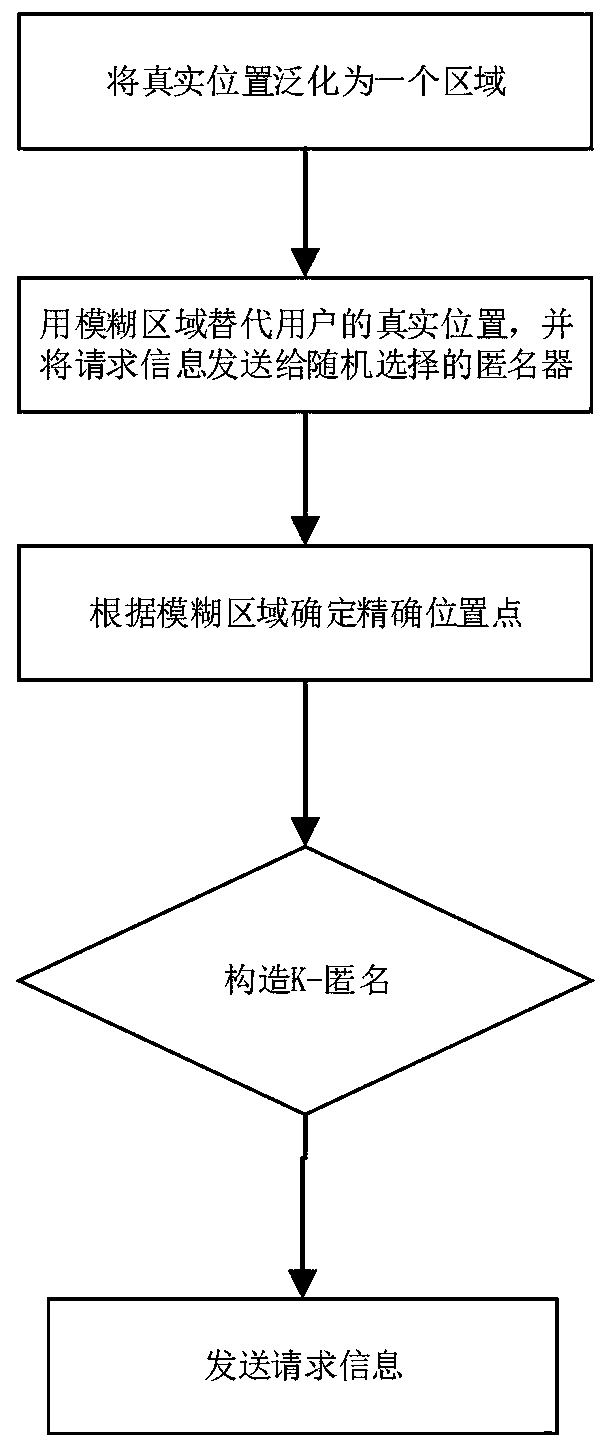
ActiveCN110602145AAvoid gettingReduce the risk of privacy breachesTransmissionK-anonymityRoad networks
The invention discloses a track privacy protection method based on position service. The method comprises the following steps: step 1, generating a fuzzy region BA according to a real position location of a user; 2, replacing the real position location of the user with a fuzzy region BA, randomly selecting an anonymous server from a plurality of anonymizers, and sending a query request (id, BA, t,query, k) to the anonymous server; 3, after the anonymous server receives the request information sent in the step 2, a selecting position point Li in a fuzzy area BA according to a road network; 4,enabling the anonymous server to generate an anonymous query request according to the Li generated in the step 3; and step 5, sending an anonymous query request to the location service provider. The real-time trajectory privacy protection method is researched on the basis of a multi-anonymizer system structure privacy protection model, and a method of combining location ambiguity and K-anonymity is provided, so that the purposes of enhancing trajectory privacy protection and ensuring data availability are achieved.
Owner:HARBIN ENG UNIV
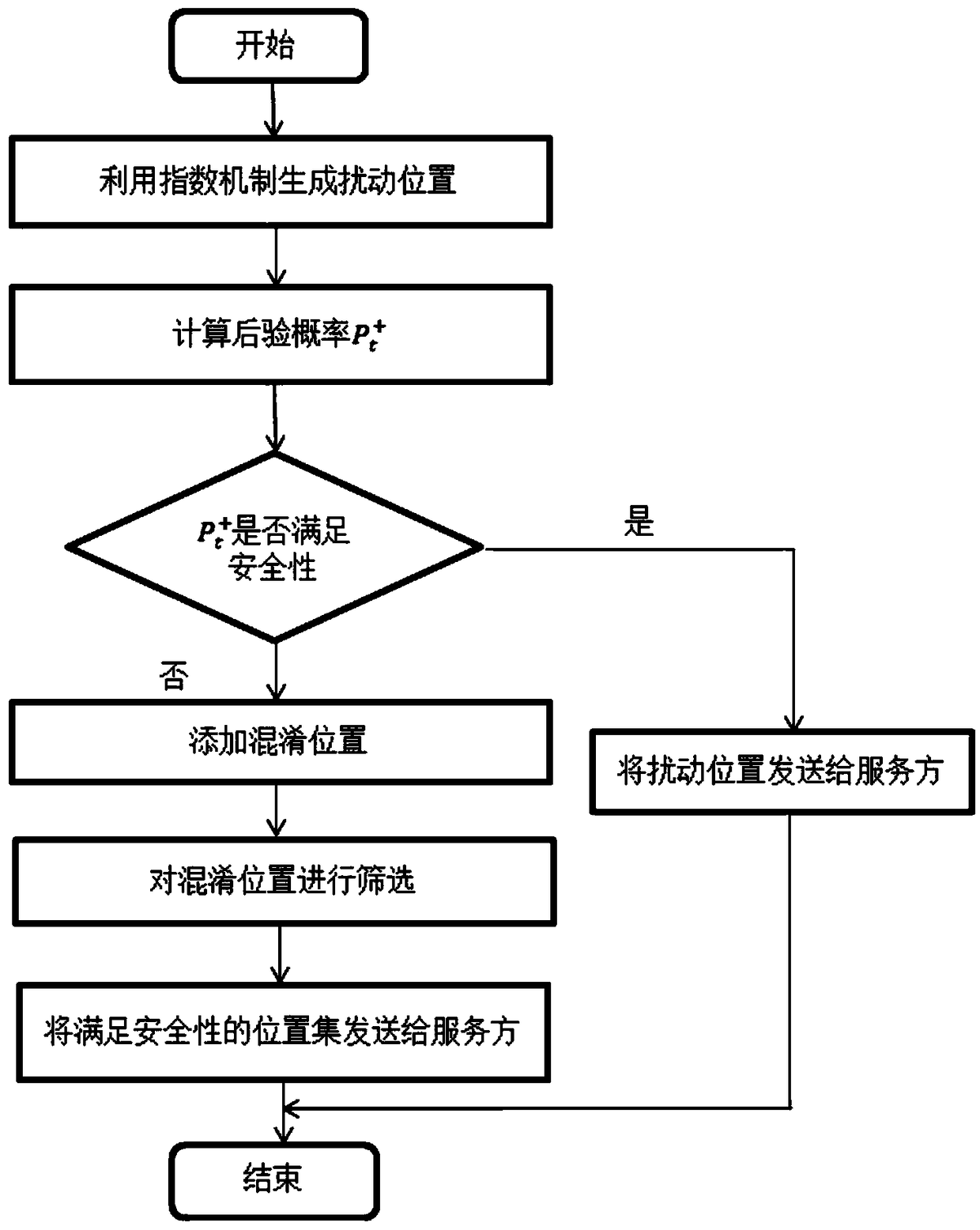
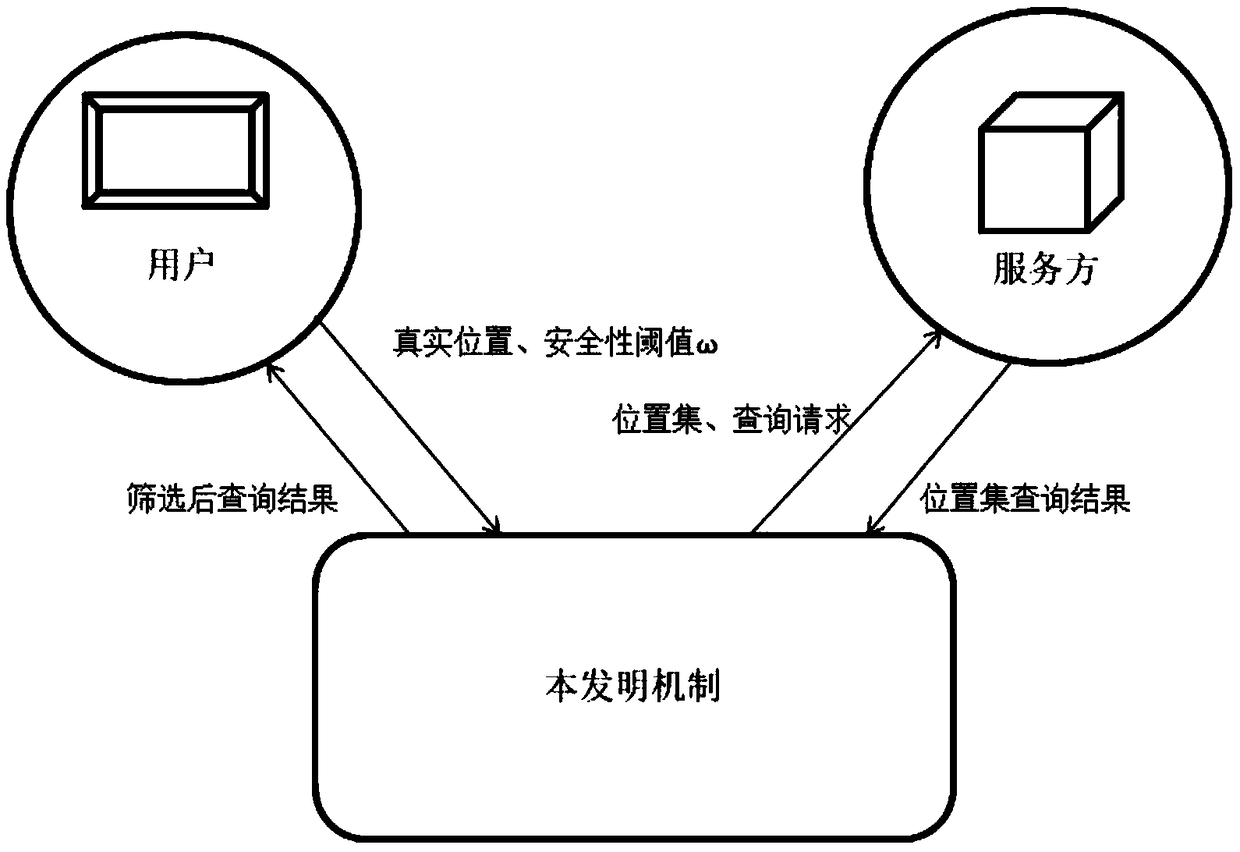
User location personalized differential privacy protection method for location-based service
ActiveCN109362032AReduce the risk of privacy breachesSolve the problem of attackLocation information based serviceSecurity arrangementPersonalizationDifferential privacy
The invention discloses a user location personalized differential privacy protection method for location-based service. The method comprises the steps of 1, generating a disturbance location through utilization of an index mechanism; 2, obtaining a posterior probability of an opponent for a location of a user at time t according to a prior probability of the opponent for the location of the user at time t, index mechanism probability distribution and the generated disturbance location; 3, judging whether the posterior probability of the opponent for the location of the user at time t satisfiesa security requirement or not, sending the disturbance location and a query request to a service provider if the posterior probability of the opponent for the location of the user at time t satisfiesthe security requirement, and adding a confusion location if the posterior probability of the opponent for the location of the user at time t does not satisfy the security requirement; 4, adding theconfusion location, and sending a location set composed of the confusion location and the disturbance location to the service provider after the security requirement is satisfied; and 5, screening query results returned by the service provider. According to the method, the problem that user location privacy is leaked due to unreliability of the service provider can be solved, and moreover, a Bayesian attack can be effectively coped with, so security of the user location privacy in the location-based service can be improved.
Owner:ANHUI UNIVERSITY
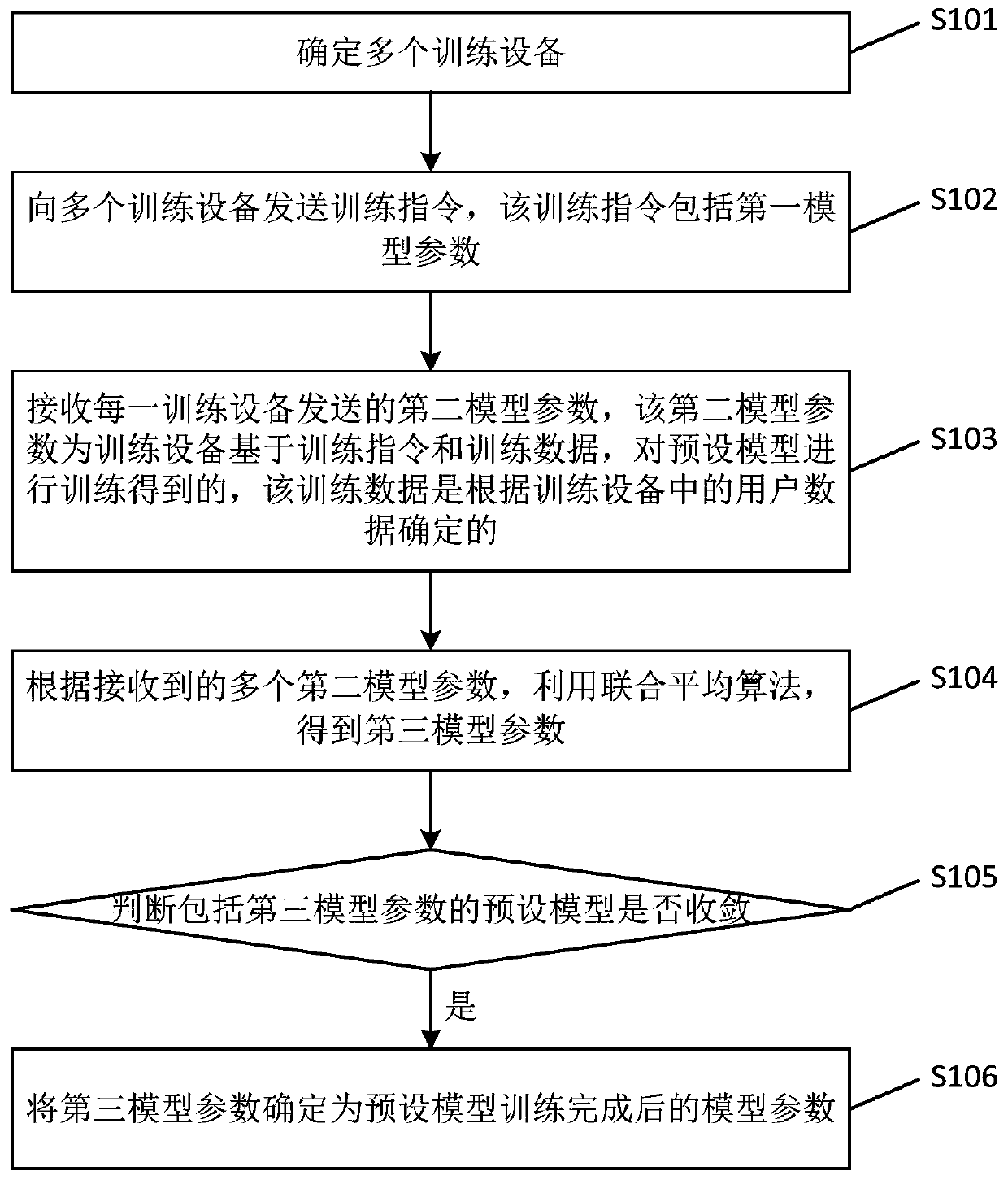
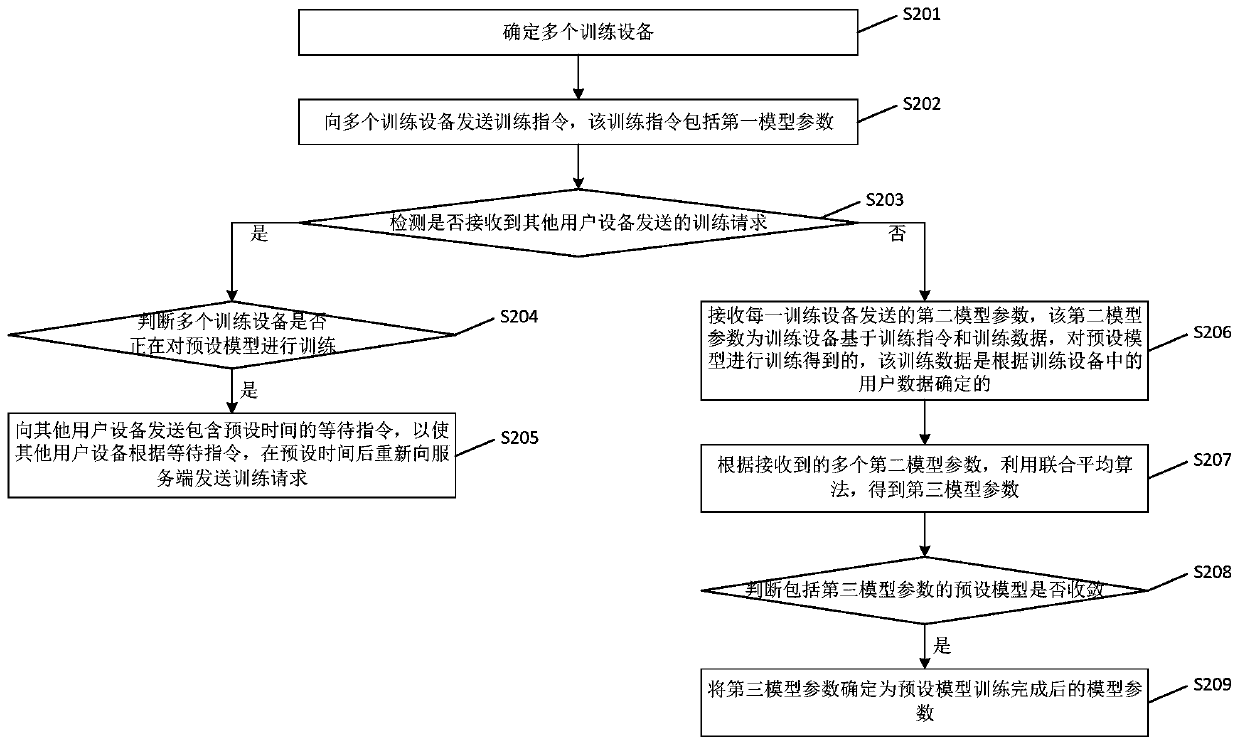
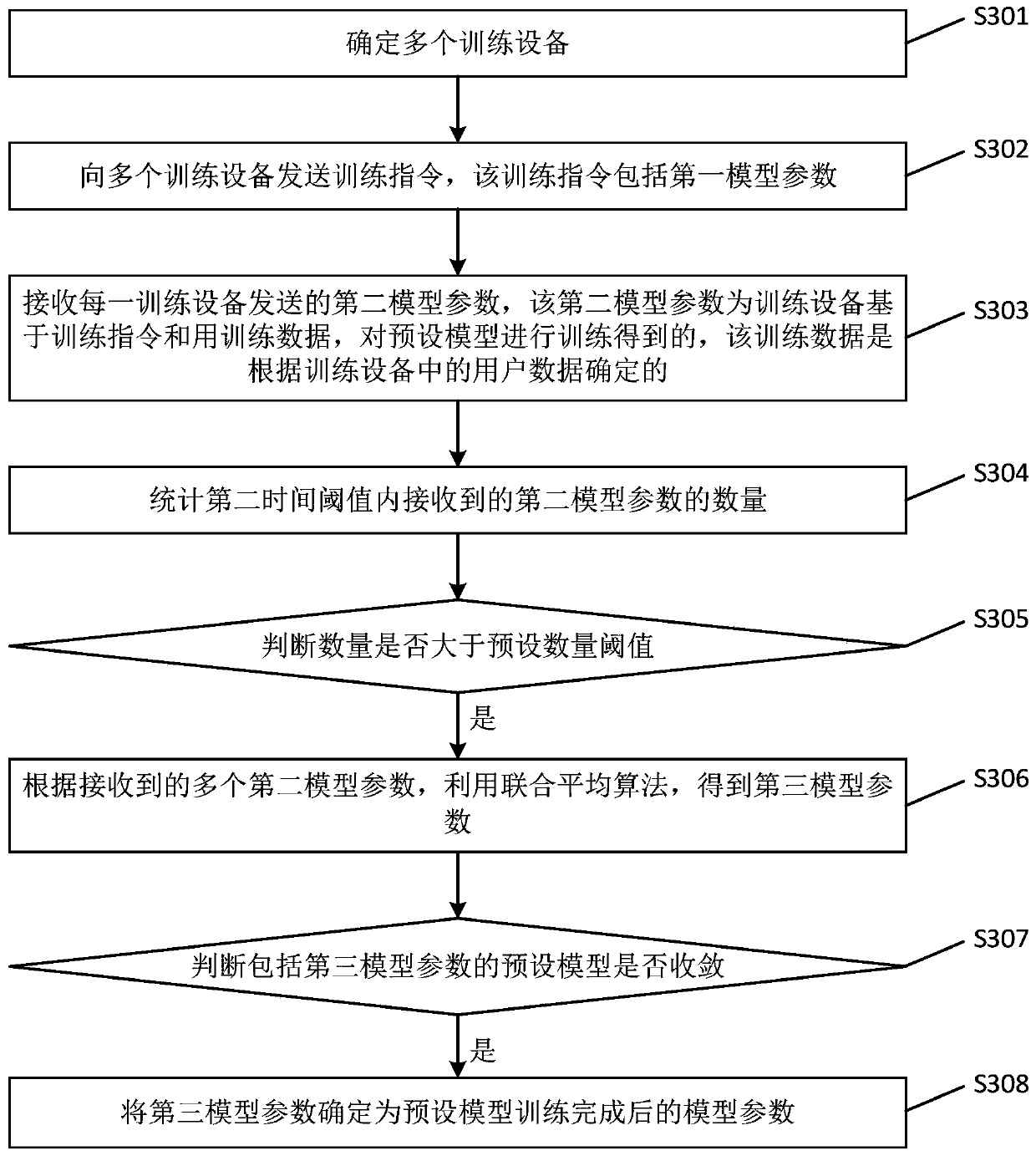
Model training method and device, electronic equipment and storage medium
InactiveCN110298185AReduce risk of leakageReduce the risk of privacy breachesDigital data protectionAlgorithmUser privacy
The embodiment of the invention provides a model training method and device, electronic equipment and a storage medium. The scheme is as follows: the server determines a plurality of training devices,sends a training instruction to a plurality of training devices, wherein the training instruction comprises a first model parameter; a second model parameter sent by each piece of training equipmentis received, wherein the second model parameter is obtained by training preset model by training device based on training instruction and training data, the training data is determined according to user data in the training equipment; obtaining a third model parameter by utilizing a joint average algorithm according to a plurality of received second model parameters, judging whether a preset modelcomprising the third model parameter is converged or not, and if yes, determining the third model parameter as the model parameter after training of the preset model is completed. Through the technical scheme provided by the embodiment of the invention, the risk of user privacy disclosure is reduced.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
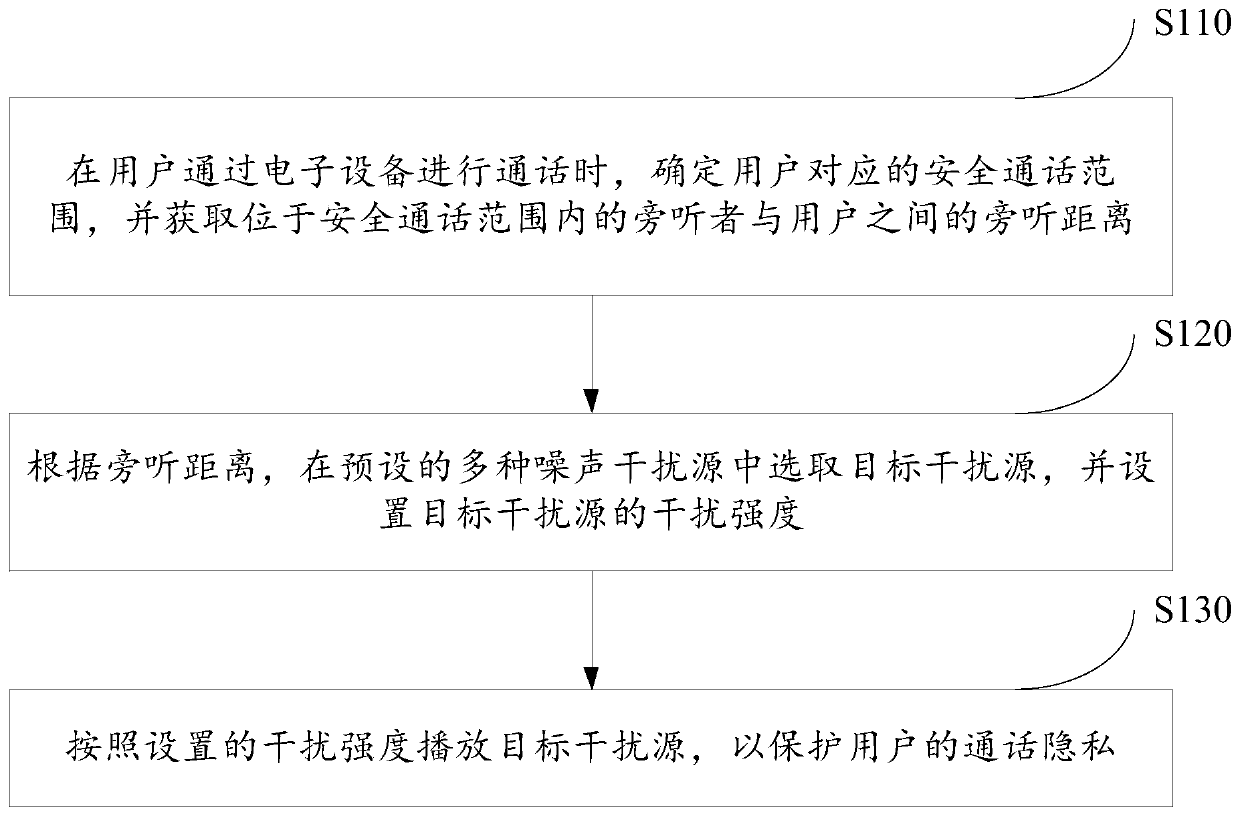
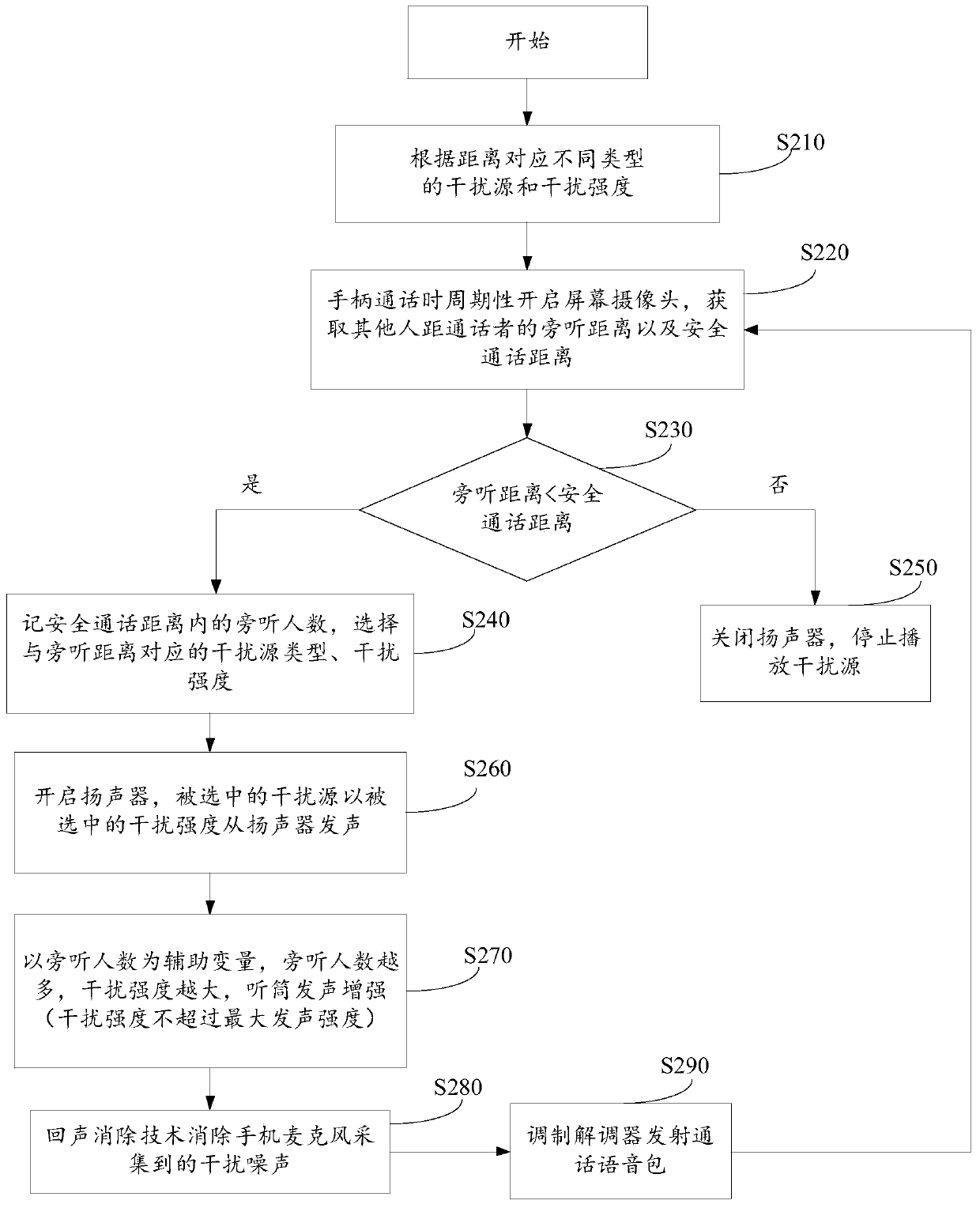
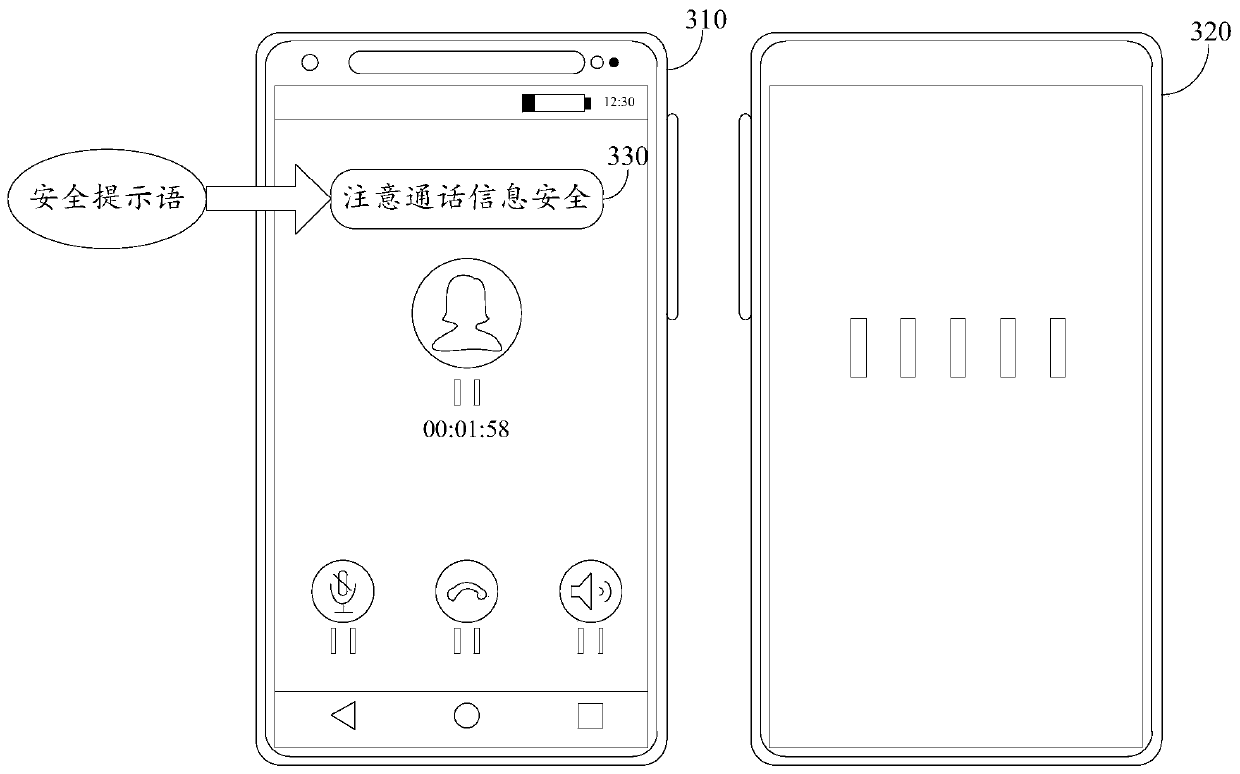
Call privacy protection method and electronic equipment
PendingCN110602696AProtect call privacyAlleviate the problem of privacy leakageSecret communicationCommunication jammingPrivacy protectionElectronic equipment
The embodiment of the invention provides a call privacy protection method and electronic equipment, and the method comprises the steps: determining a safety call range corresponding to a user when theuser carries out the call through the electronic equipment, and obtaining an auditory distance between an audience in the safety call range and the user; selecting a target interference source from aplurality of preset noise interference sources according to the auditory distance, and setting the interference intensity of the target interference source; and playing the target interference sourceaccording to the set interference intensity so as to protect the call privacy of the user. According to the technical scheme provided by the embodiment of the invention, the interference noise can beemitted according to the distance between the audience and the call user, so that the problem of privacy leakage in the call process caused by the sound leakage phenomenon is relieved, the risk of privacy leakage in the call process is reduced, and the effect of protecting the call privacy is achieved.
Owner:VIVO MOBILE COMM CO LTD
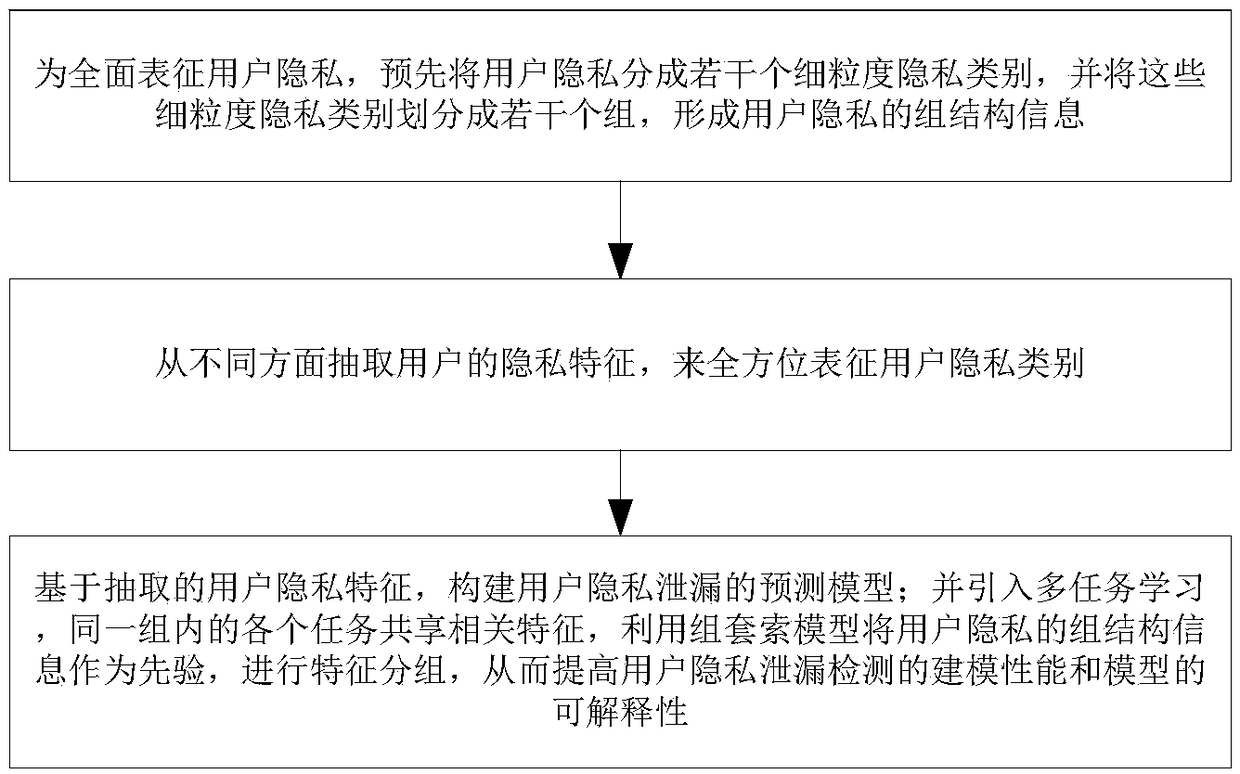
Method for detecting privacy leak of user based on multi-task learning, server and system
ActiveCN108830100AImprove modeling performanceImprove interpretabilityDigital data protectionUser privacyInternet privacy
The invention discloses a method for detecting privacy leak of a user based on multi-task learning, a server and a system. The method for detecting privacy leak of the user based on multi-task learning comprises the following steps: for comprehensive representation of privacy of the user, dividing the privacy of the user into a plurality of fine-grained privacy categories in advance, and dividingthe fine-grained privacy categories into a plurality of groups to form group structural information for privacy of the user; extracting privacy characteristics of the user from different direction torepresent the privacy categories of the user in an all-round manner; constructing a prediction model based on the extracted privacy characteristics of the user; and introducing multi-task learning, enabling each task in the same group to share related characteristics, and performing characteristic grouping by taking the group structural information of the privacy of the user as a priori by use ofa group lasso model. Therefore, the modeling performance for detection of privacy leak of the user and interpretability of the model are improved.
Owner:SHANDONG UNIV
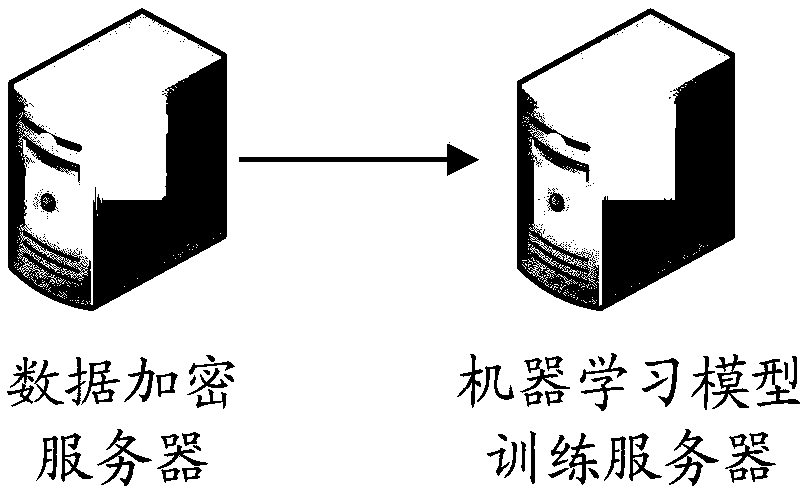
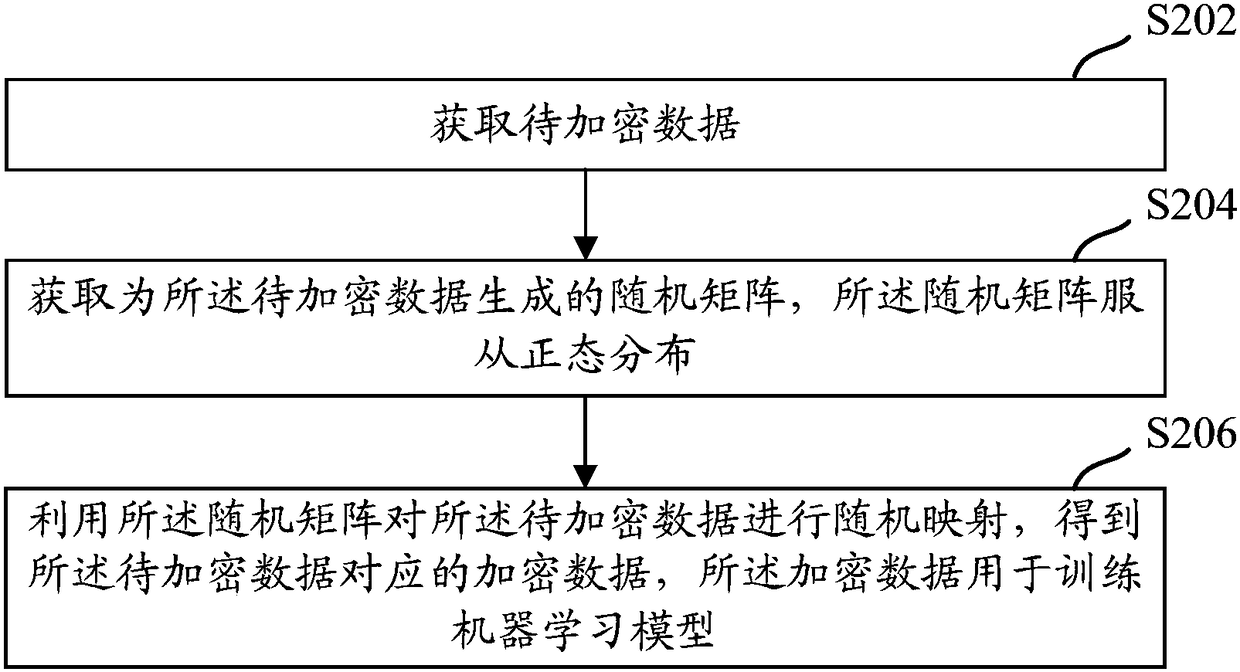
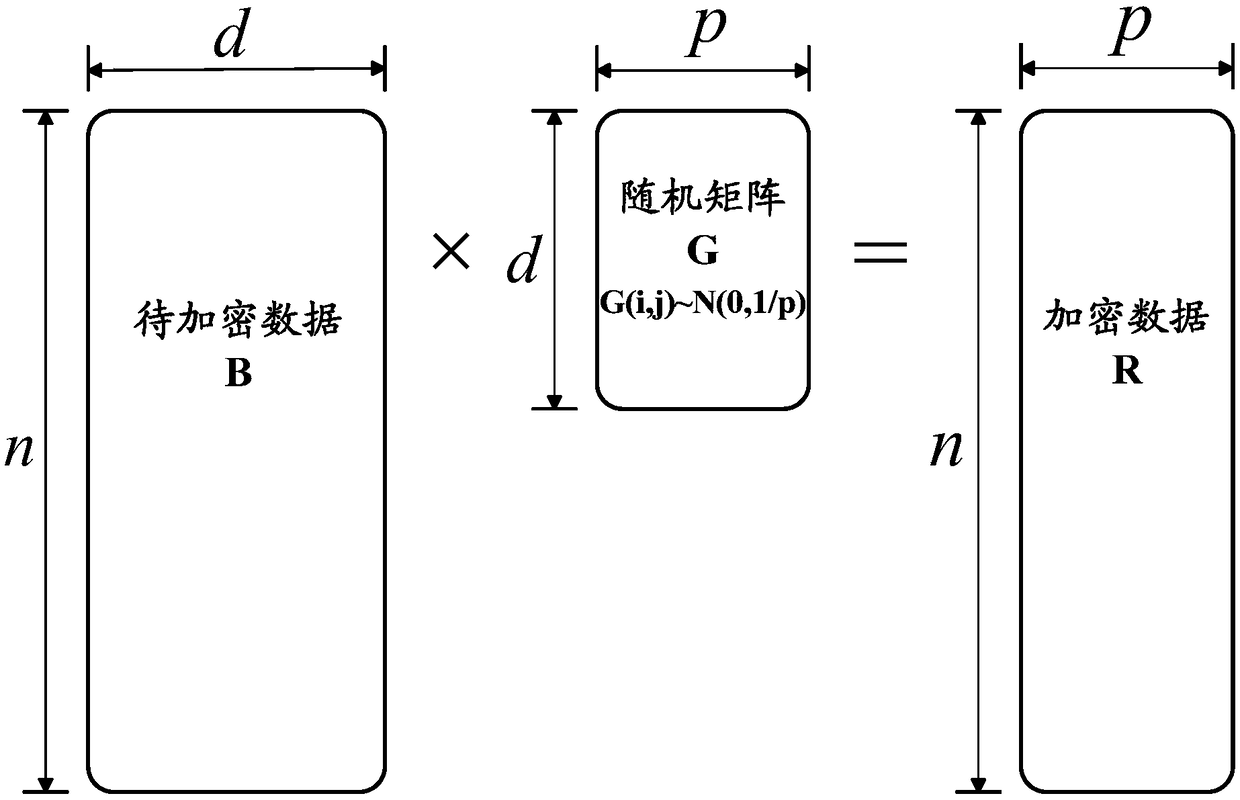
Data encryption, machine learning model training method, apparatus and electronic apparatus
InactiveCN109241749AReduce the risk of privacy breachesTraining does not affectDigital data protectionMachine learningPattern recognitionRandom mapping
Embodiments of the present specification disclose a data encryption, machine learning model training method, apparatus, electronic apparatus, and data encryption system. The data encryption method comprises the following steps: the encrypted data to be encrypted is randomly mapped by a random matrix to obtain the encrypted data corresponding to the data to be encrypted, and the encrypted data is used for training a machine learning model.
Owner:ADVANCED NEW TECH CO LTD
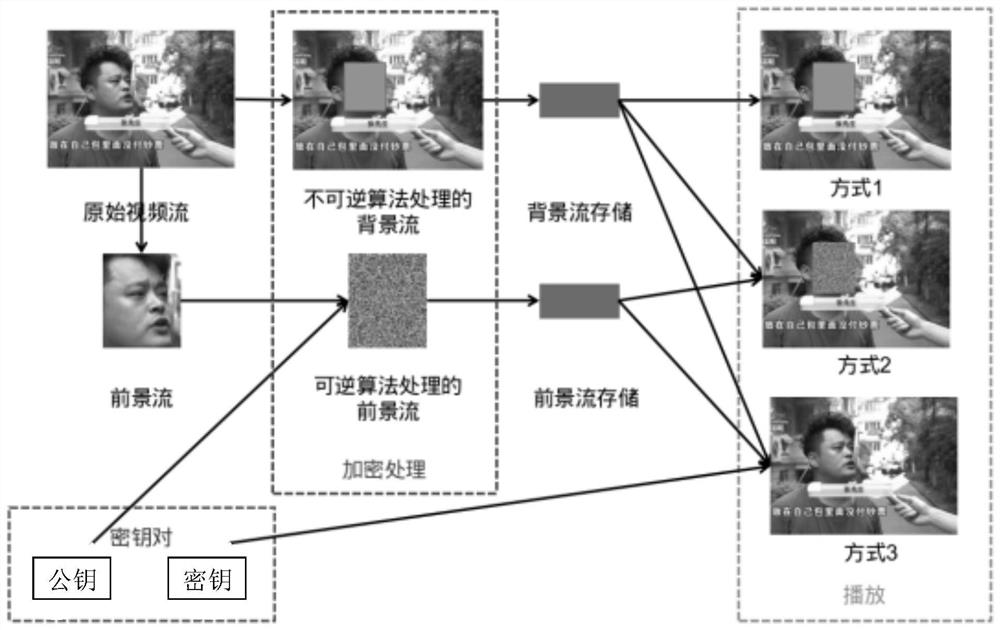
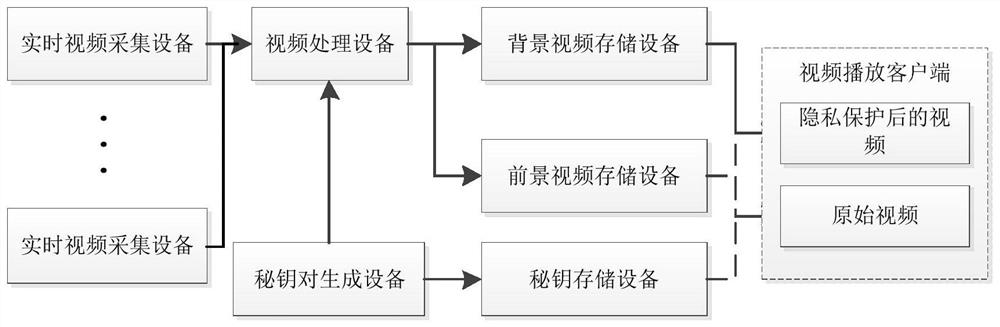
Real-time video sensitive information protection system and method
PendingCN113630587AEasy to play directlyHigh degree of encryptionGeometric image transformationDigital data protectionTemplate matchingData expansion
The invention provides a real-time video sensitive information protection system and method. The real-time video sensitive information protection method comprises the following steps: S1, collecting a real-time video stream; S2, separating the video stream, separating the video stream by an equal interval, adopting a detection algorithm to extract a preset foreground stream in each segment of video stream, and hiding privacy and sensitive information in the foreground stream through a reversible algorithm, wherein the reversible algorithm refers to a public key generated in a corresponding time interval, the detection algorithm comprises target detection and template matching algorithms, the reversible algorithm comprises a scrambling algorithm and a password book translation algorithm, and a scrambling algorithm performs data encryption through image splitting, data expansion and image combination; S3, adopting an irreversible algorithm to erase sensitive information in the video stream so as to obtain a background stream, wherein the irreversible algorithm comprises a mosaic method, a color block covering method and a frosted glass effect; and S4, restoring the original video stream. The encryption degree of the video stream can be improved, encryption is reversible, and the protection degree of personal privacy is greatly improved.
Owner:北京朗达和顺科技有限公司
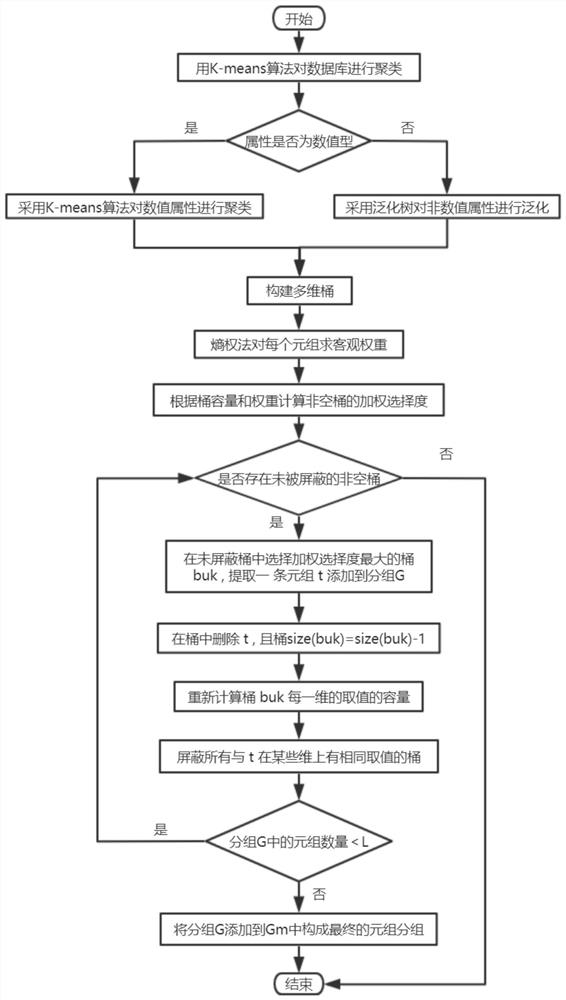
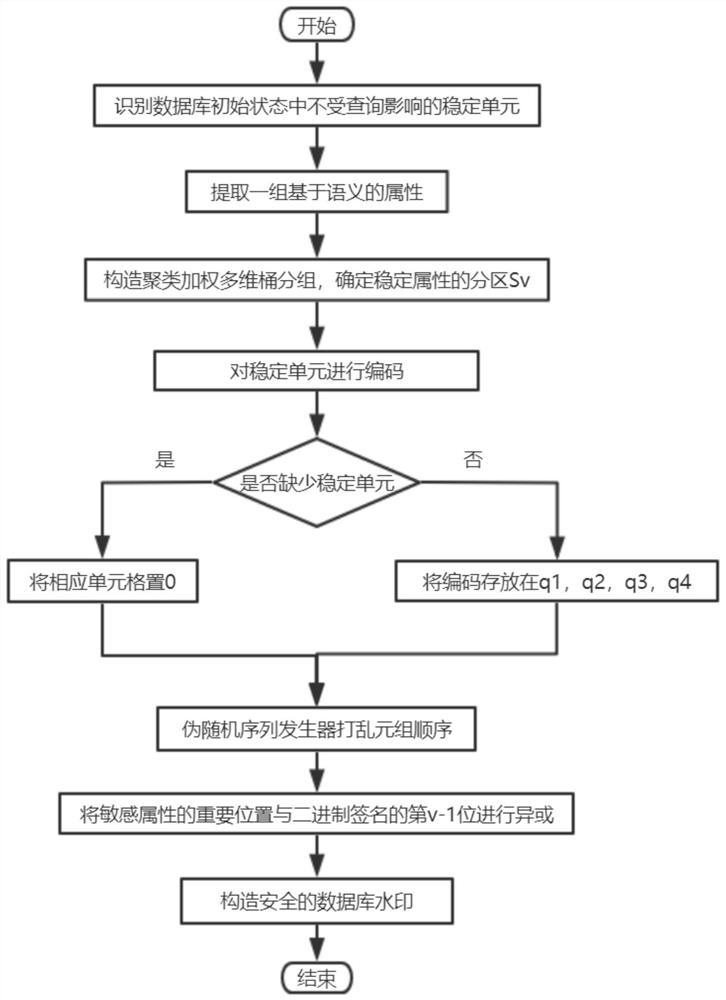
Secure database watermark construction method based on clustering weighted multi-dimensional bucket grouping
ActiveCN112800394AImprove robustnessReduce the risk of privacy breachesCharacter and pattern recognitionDigital data protectionOriginal dataEngineering
The invention provides a secure database watermark construction method based on clustering weighted multi-dimensional bucket grouping. The method is carried out by selecting a proper abstract domain, expressing a stable unit of a database by using an invariant generated by the abstract domain, grouping the database by using a multi-dimensional bucket grouping technology, and constructing a safe database watermark according to the grouped stable units and the extracted invariant attributes. The method particularly includes: selecting database stabilization units and attributes according to an abstract domain, carrying out a data clustering step; establishing a weighted multi-dimensional bucket group; and constructing a secure database watermark. According to the method, the weighted multi-dimensional bucket grouping is adopted, the data quality is improved, meanwhile, the privacy of sensitive attributes is protected, an attacker is difficult to obtain sensitive information, and then the robustness of watermarks is improved; therefore, the weights of the sensitive attributes calculated according to different scenes may be different, the usability of users is improved, the application scene of watermarks is expanded, original data are not modified, and it is ensured that the data are not distorted.
Owner:NANJING UNIV OF POSTS & TELECOMM
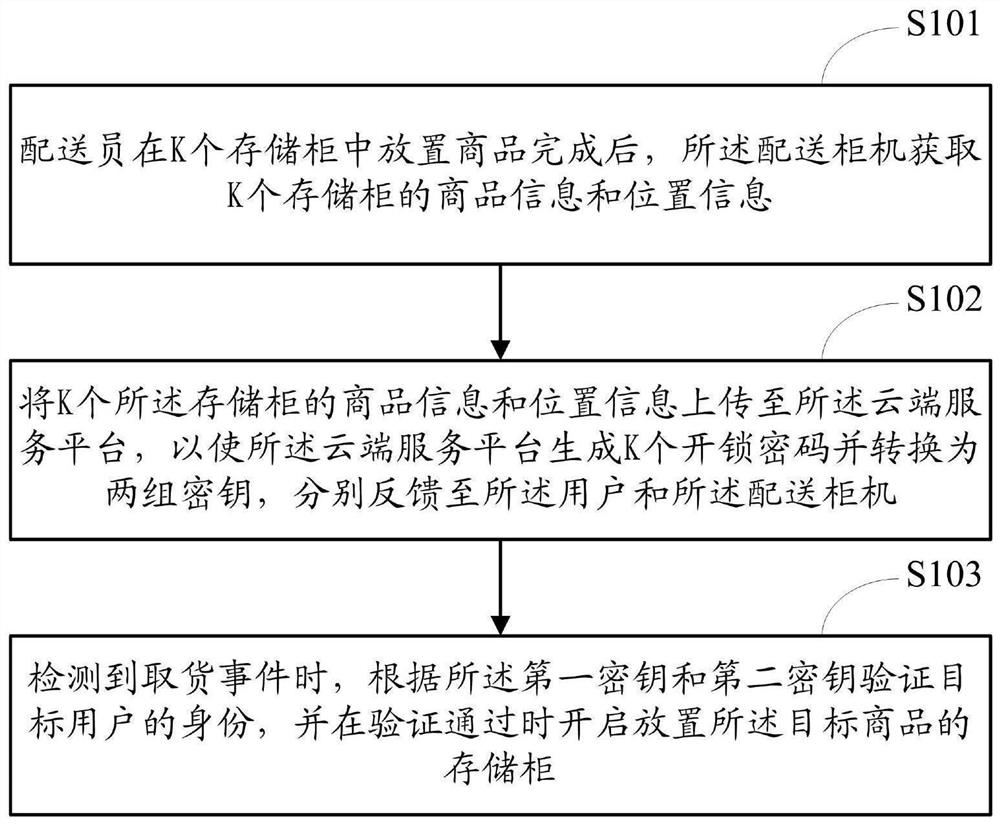
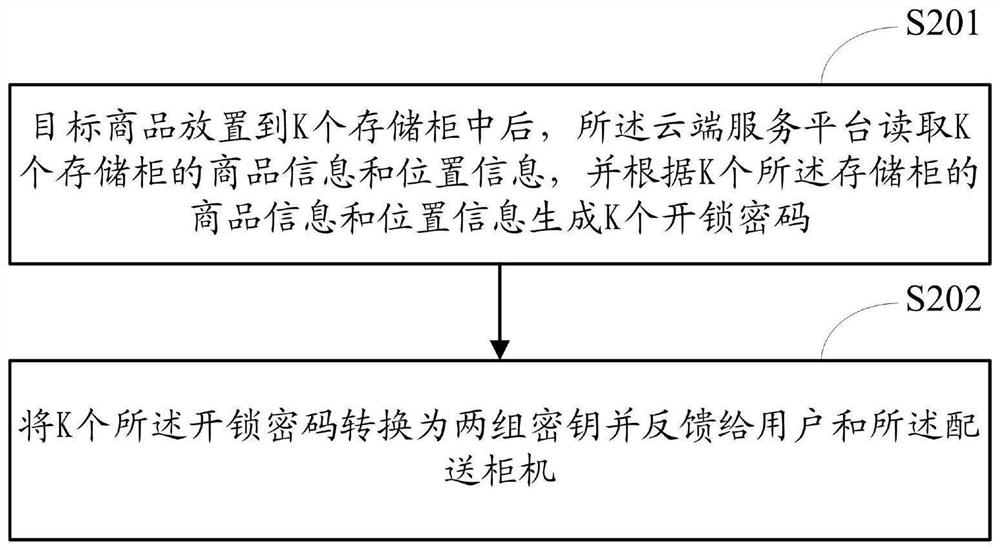
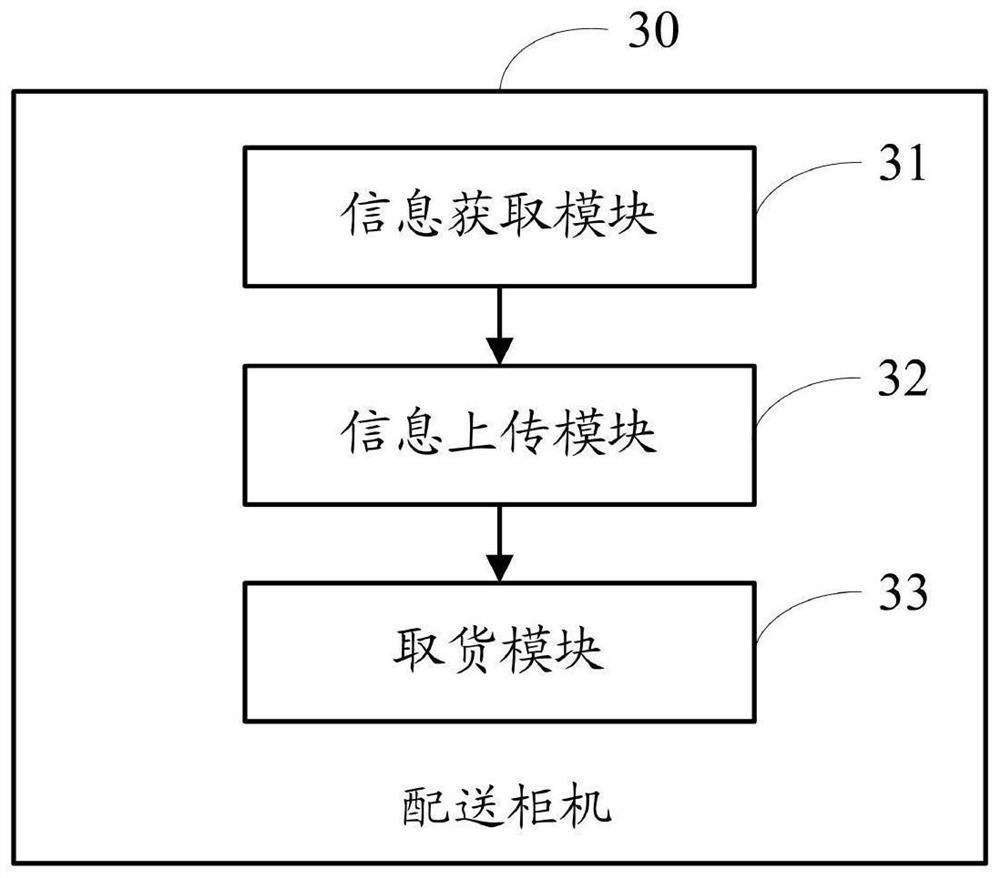
Order delivery method, device and system
PendingCN112651682AAvoid the problem of low delivery efficiencyReduce the risk of privacy breachesDigital data protectionDigital data authenticationLogistics managementPassword
The invention is suitable for the technical field of logistics management, and provides an order delivery method, device and system, the method is applied to an order delivery system composed of a delivery cabinet and a cloud service platform, the delivery cabinet comprises N storage cabinets, the cloud service platform is bound with multiple users, a target user purchases a target commodity through the cloud service platform. The method comprises the steps that after a deliveryman places commodities in K storage cabinets, the delivery cabinet obtains commodity information and position information of the K storage cabinets, and the commodity information comprises user identity codes; the commodity information and the position information of the K storage cabinets are uploaded to a cloud service platform, so that the cloud service platform generates K unlocking passwords and converts the unlocking passwords into two groups of secret keys, and the two groups of secret keys are fed back to the user and the delivery cabinet respectively; and when a goods taking event is detected, the identity of the target user is verified, and the storage cabinet for placing the target goods is opened when the verification is passed. According to the invention, the risk of user privacy leakage can be reduced, and the delivery efficiency is improved.
Owner:重庆华宜佳热能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com