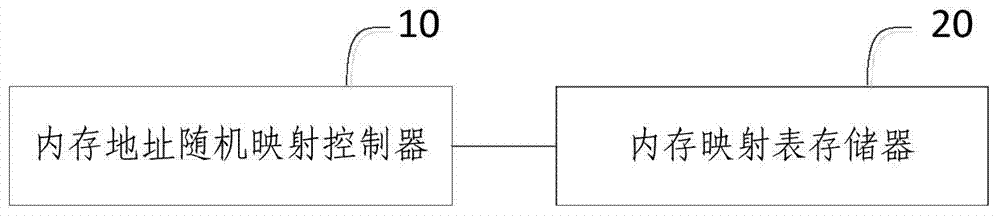
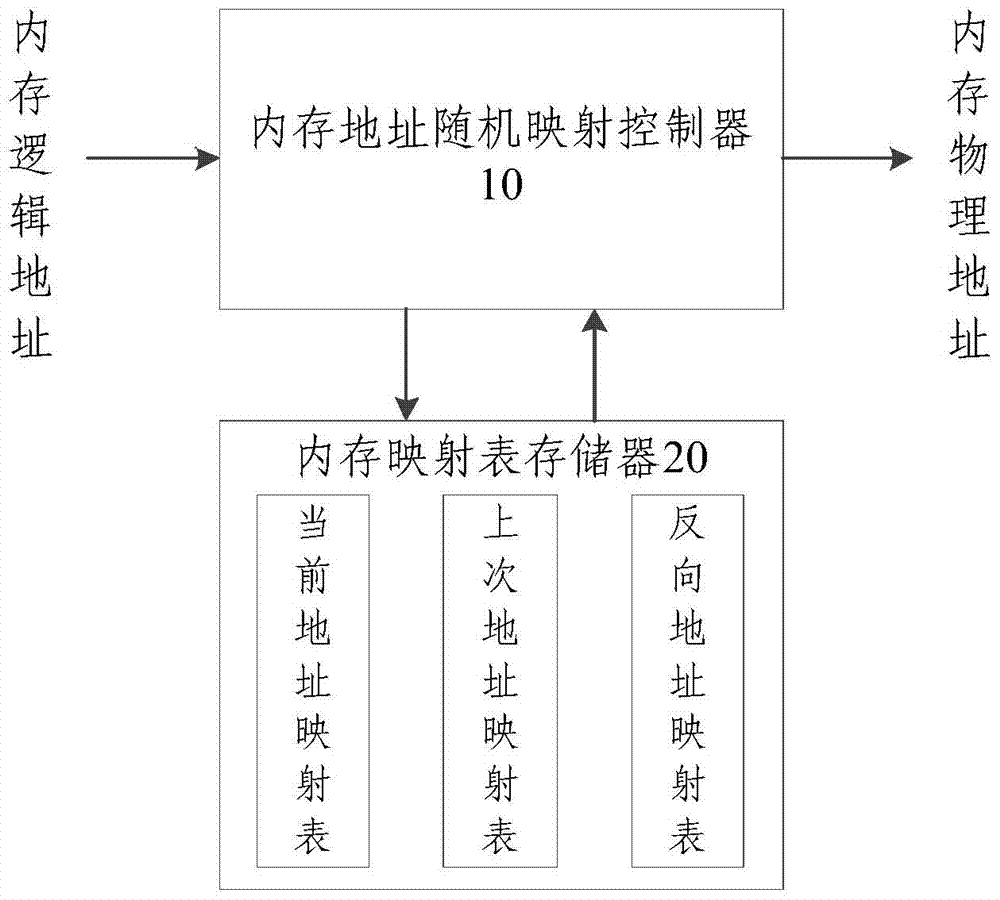
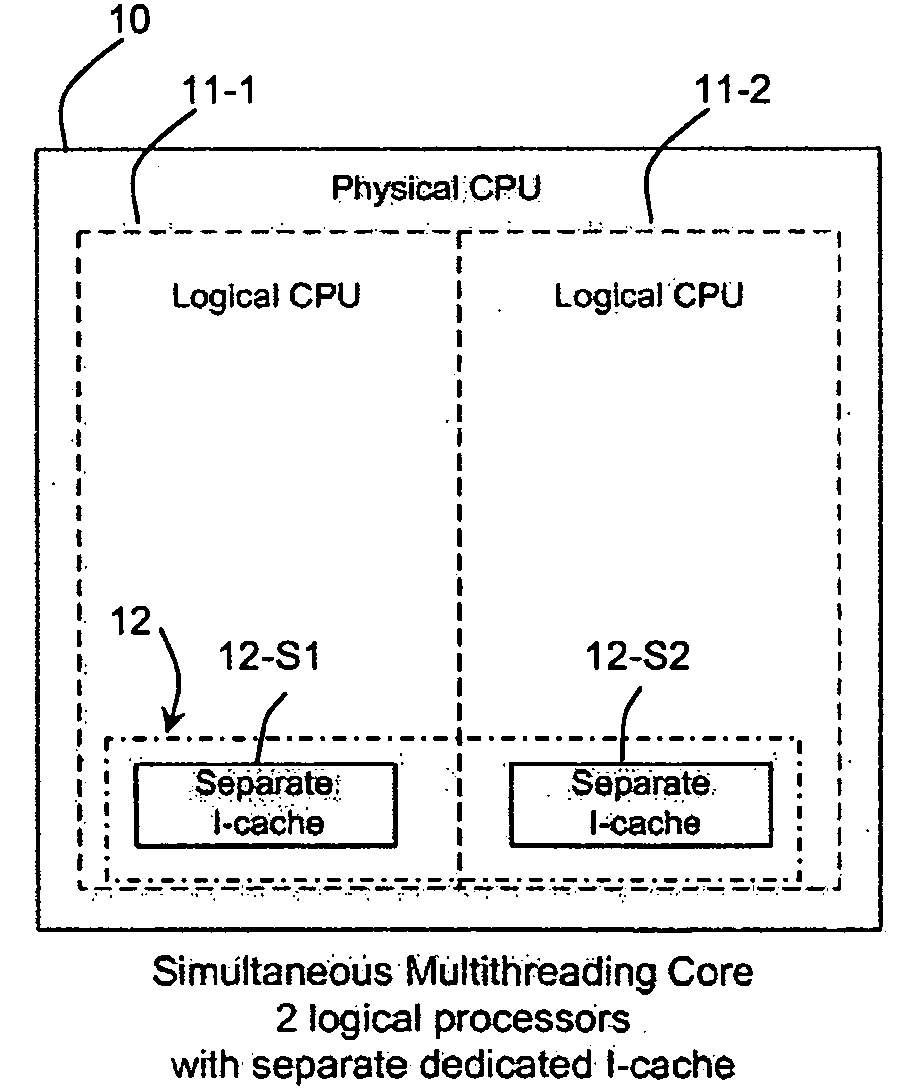
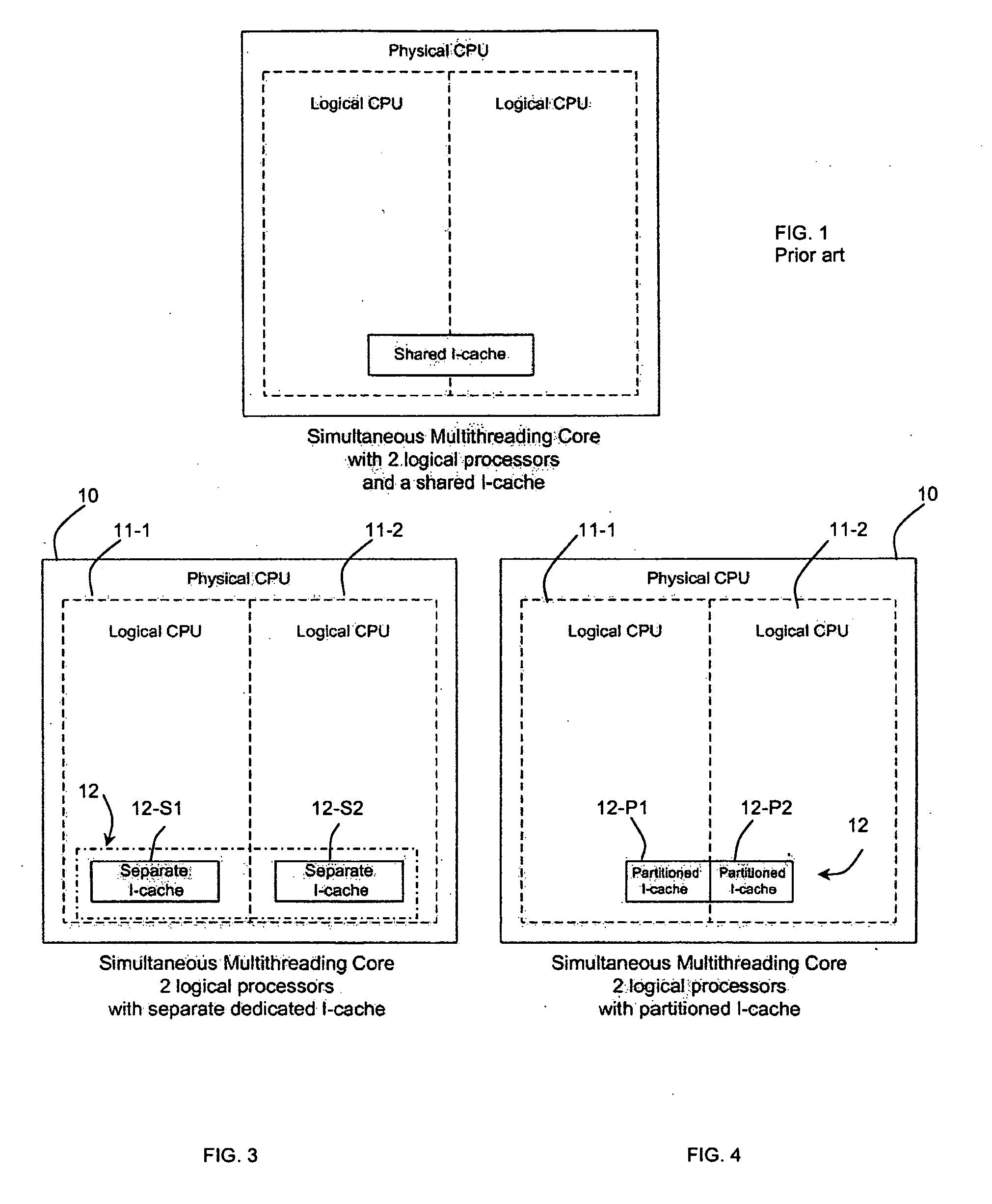
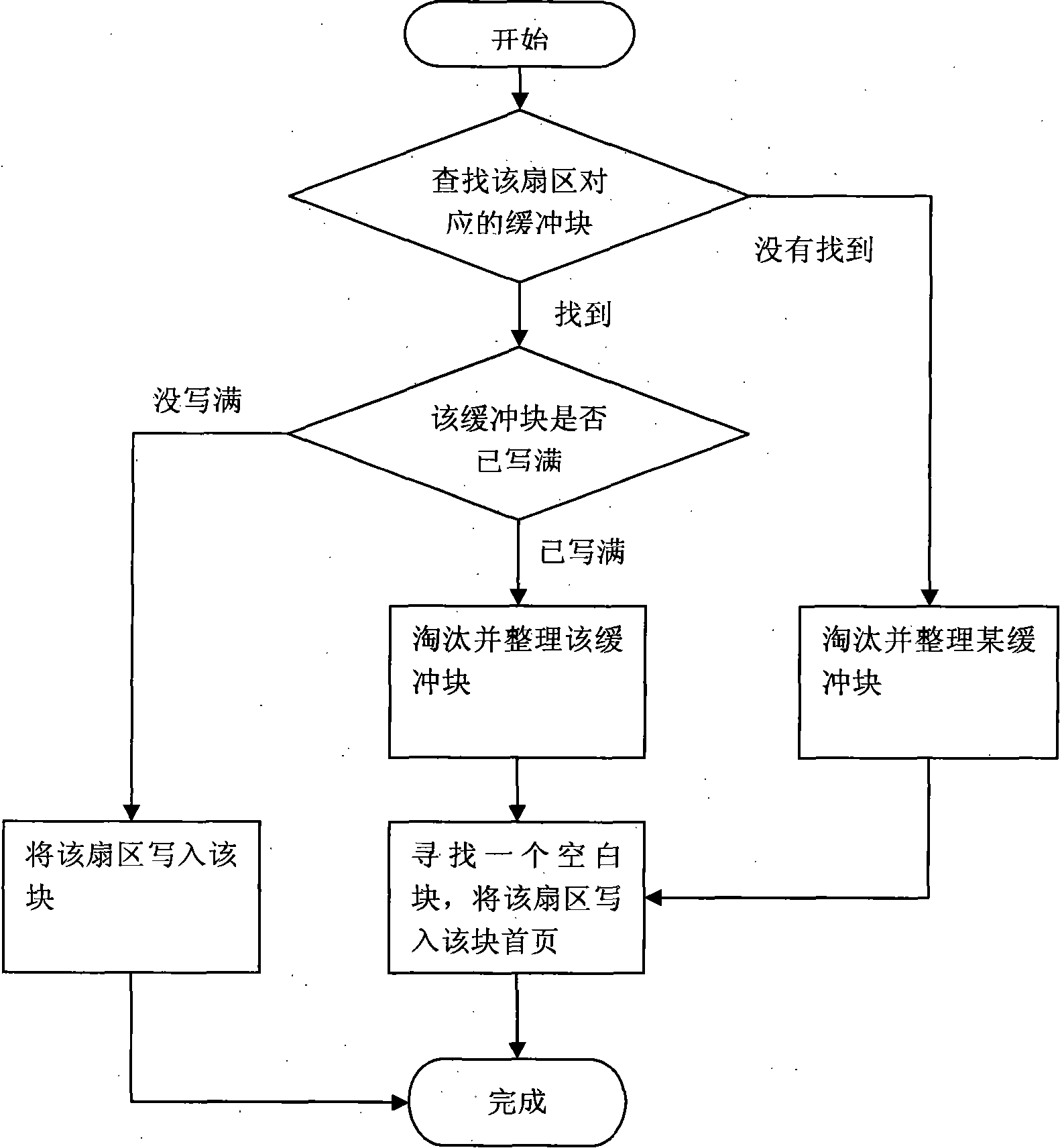
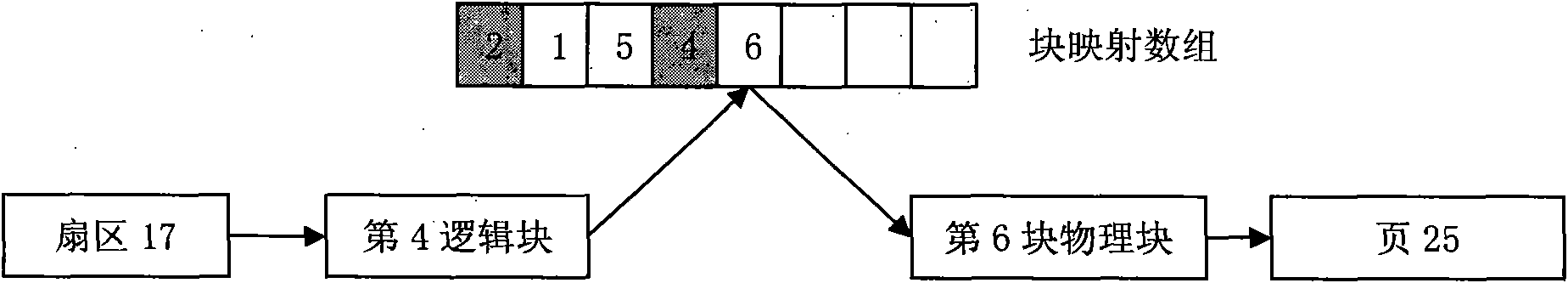
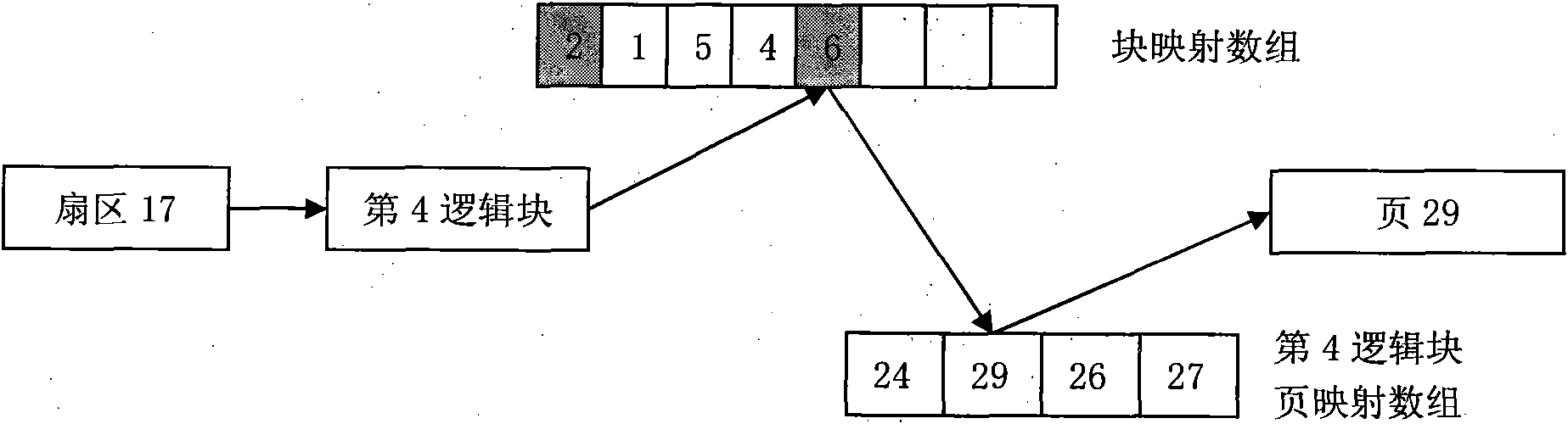
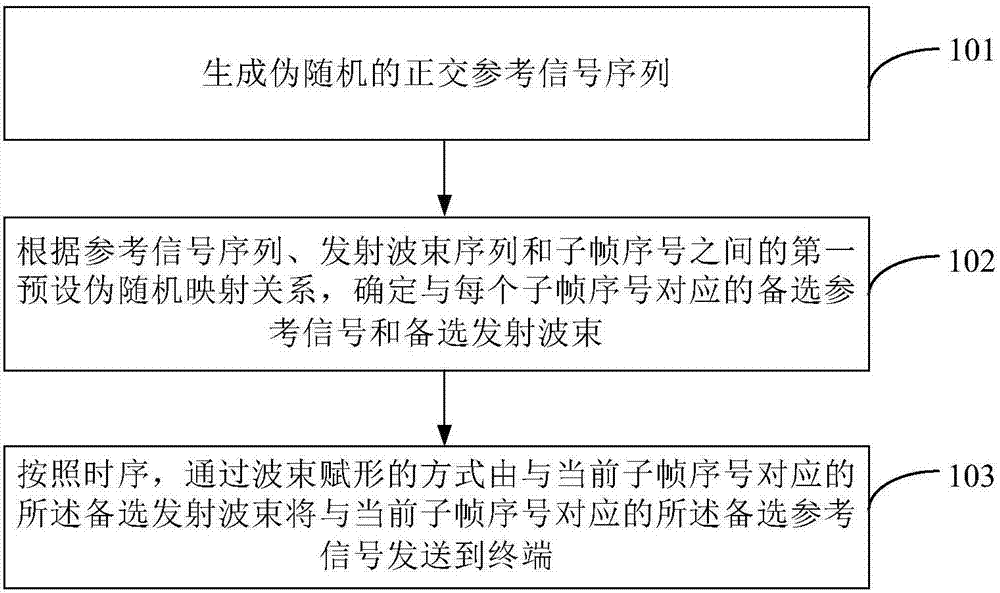
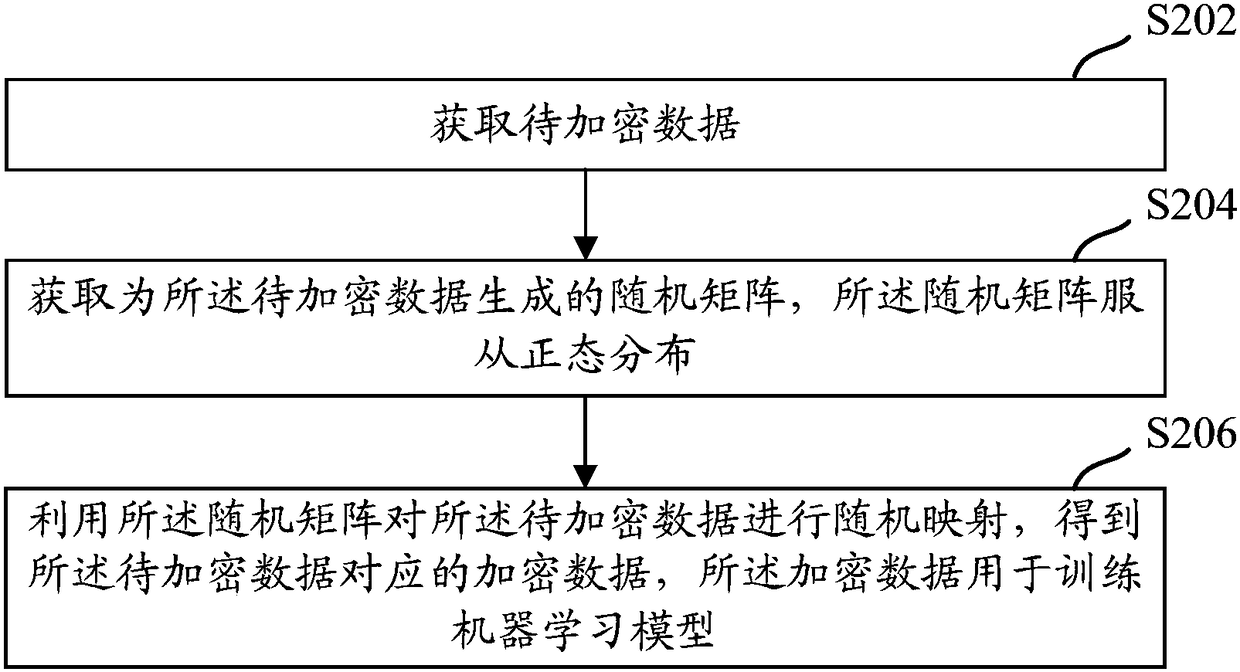
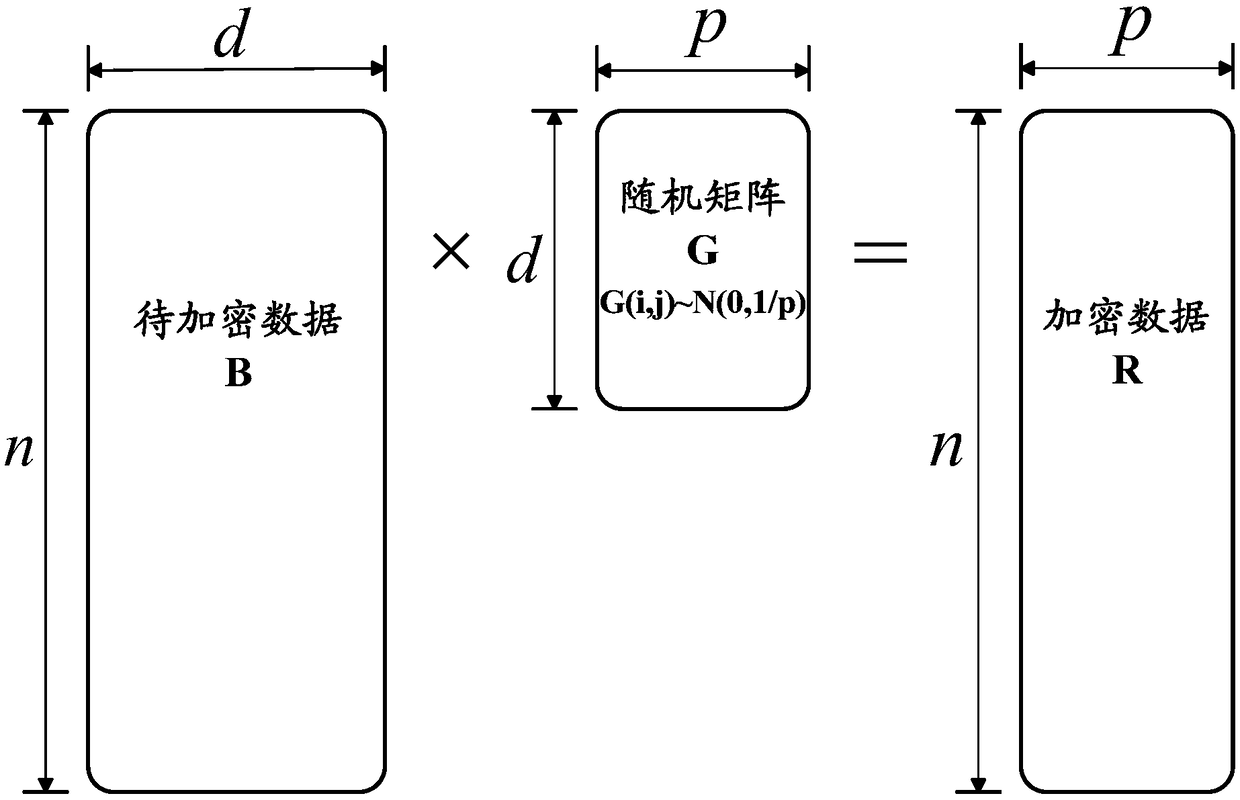
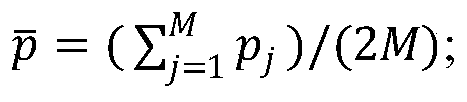Patents
Literature
77 results about "Random mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
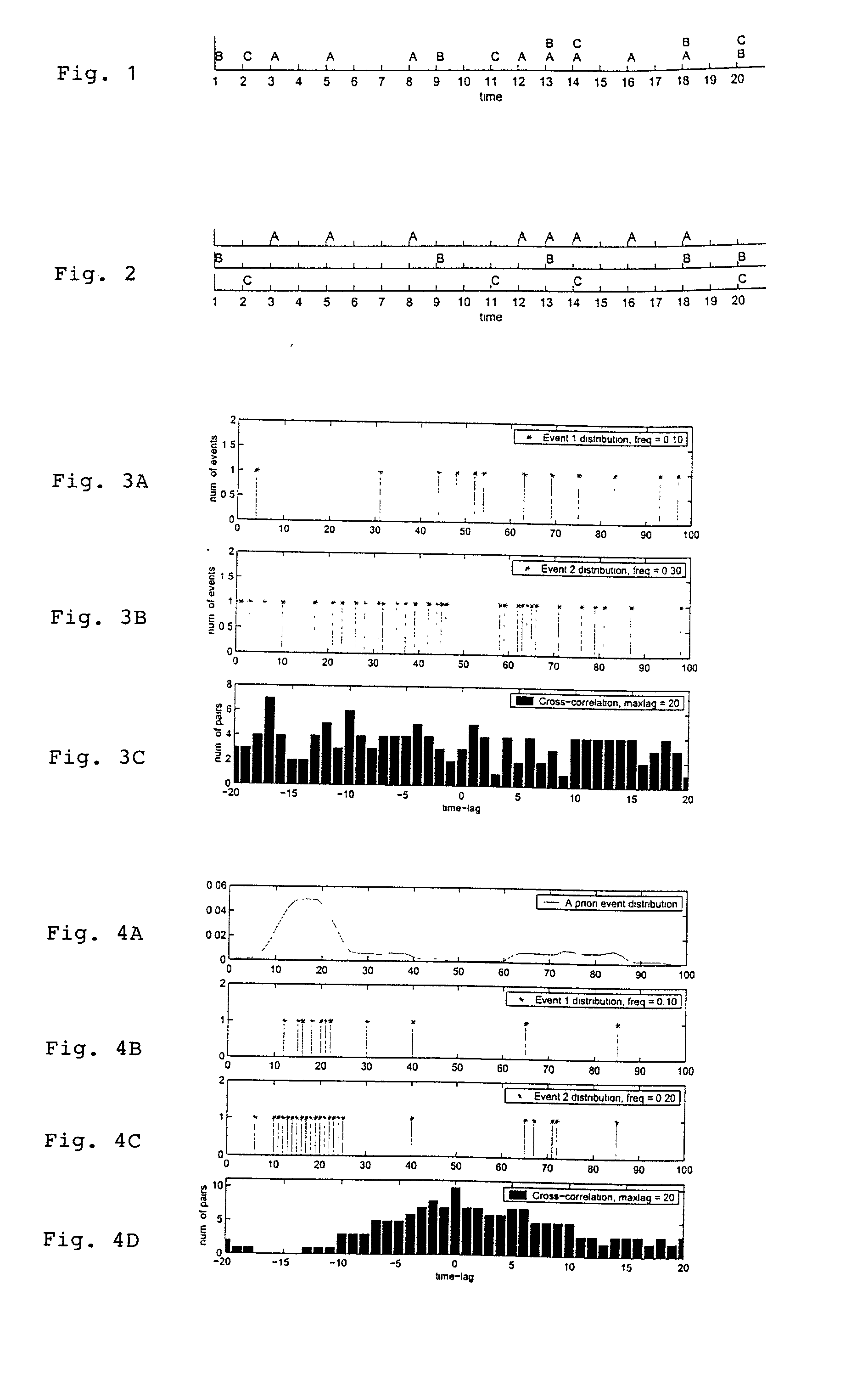
When the data vectors are high-dimensional it is computationally infeasible to use data analysis or pattern recognition algorithms which repeatedly compute similarities or distances in the original data space. It is therefore necessary to reduce the dimensionality before, for example, clustering the data. Random Mapping (RM) is a fast dimensionality reduction method categorized as feature extraction method. The RM consists in generation of a random matrix that is multiplied by each original vector and result in a reduced vector. In Text mining context, it is demonstrated that the document classification accuracy obtained after the dimensionality has been reduced using a random mapping method will be almost as good as the original accuracy if the final dimensionality is sufficiently large (about 100 out of 6000). In fact, it can be shown that the inner product (similarity) between the mapped vectors follows closely the inner product of the original vectors.
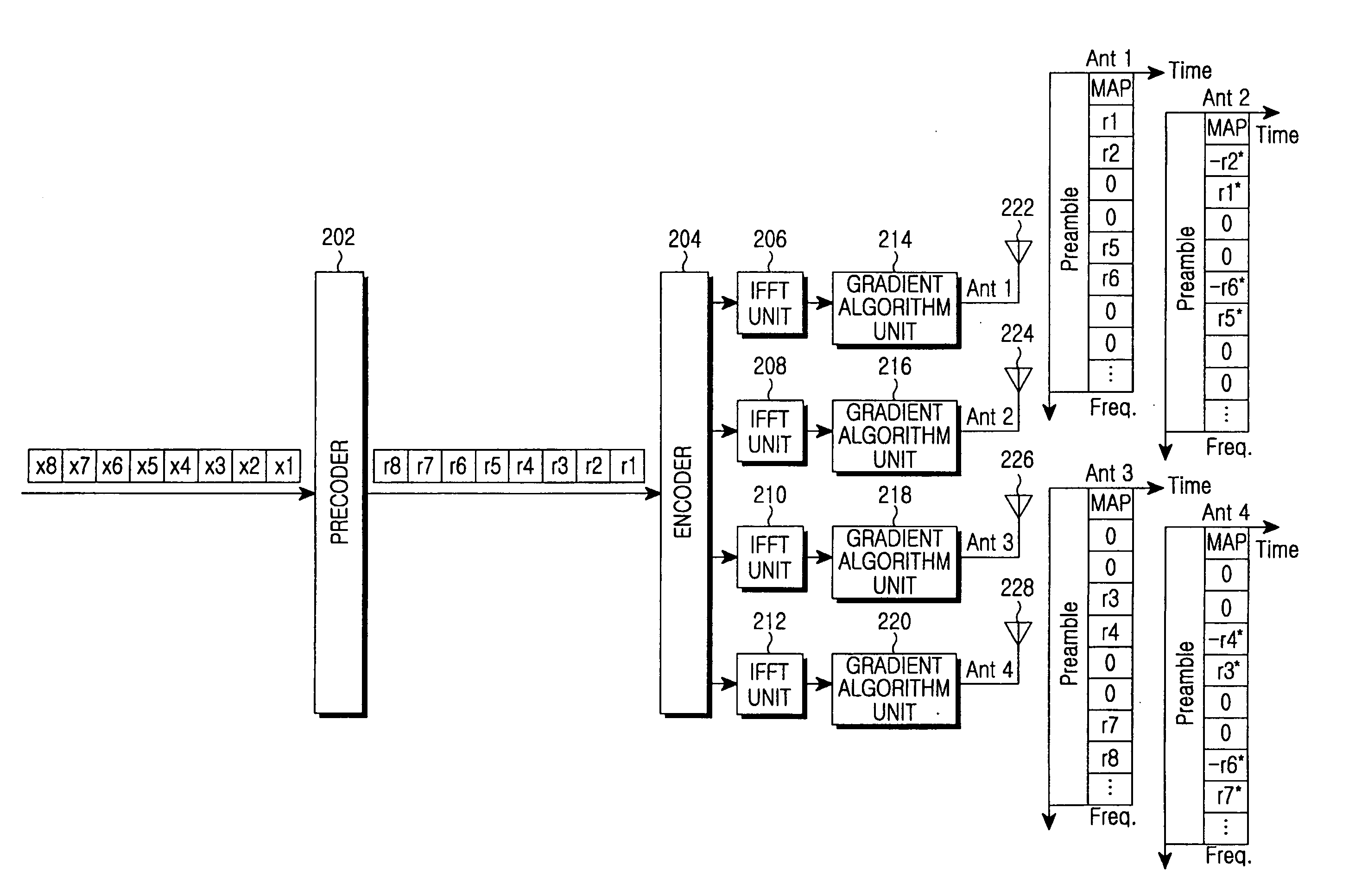
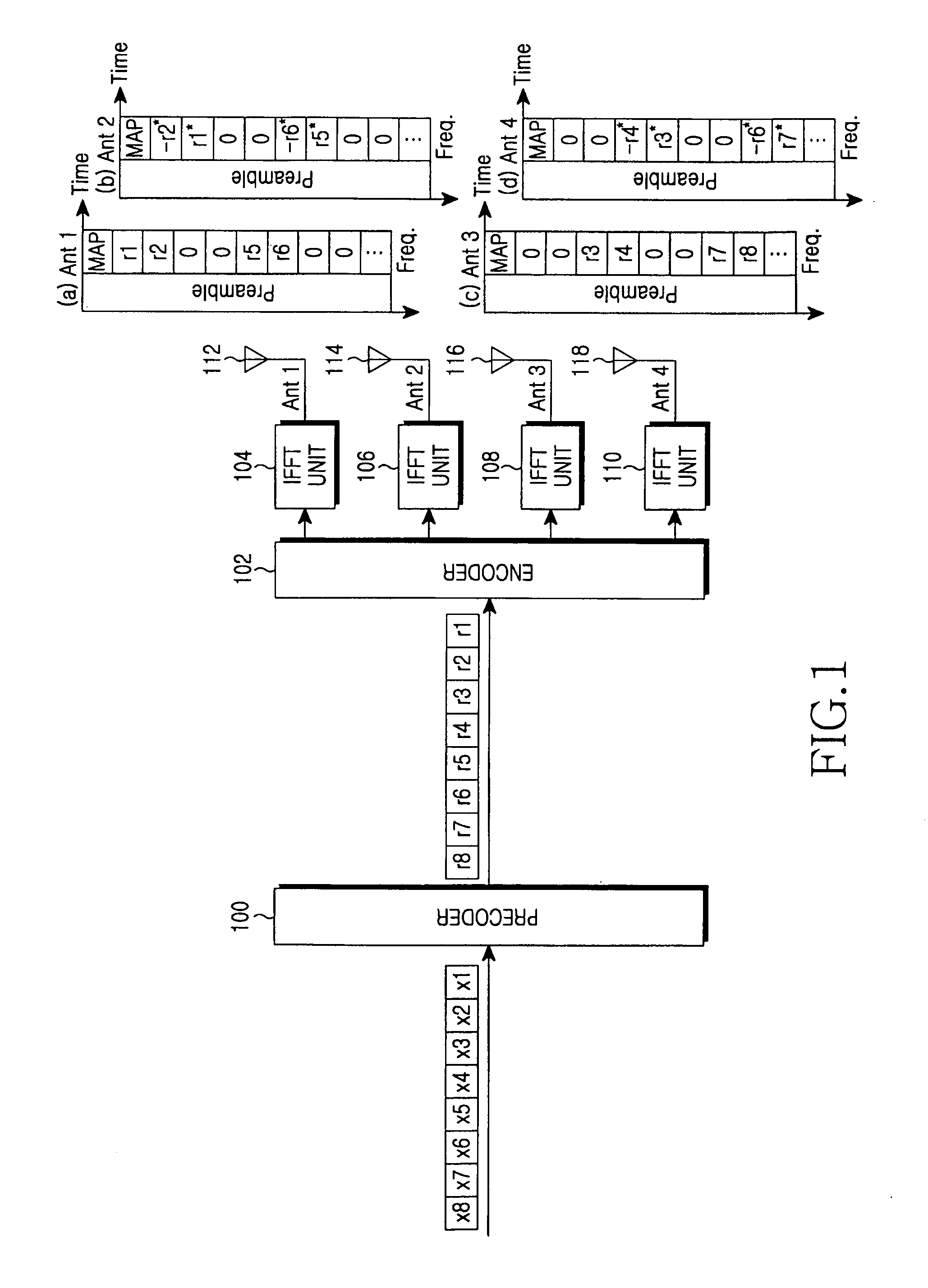
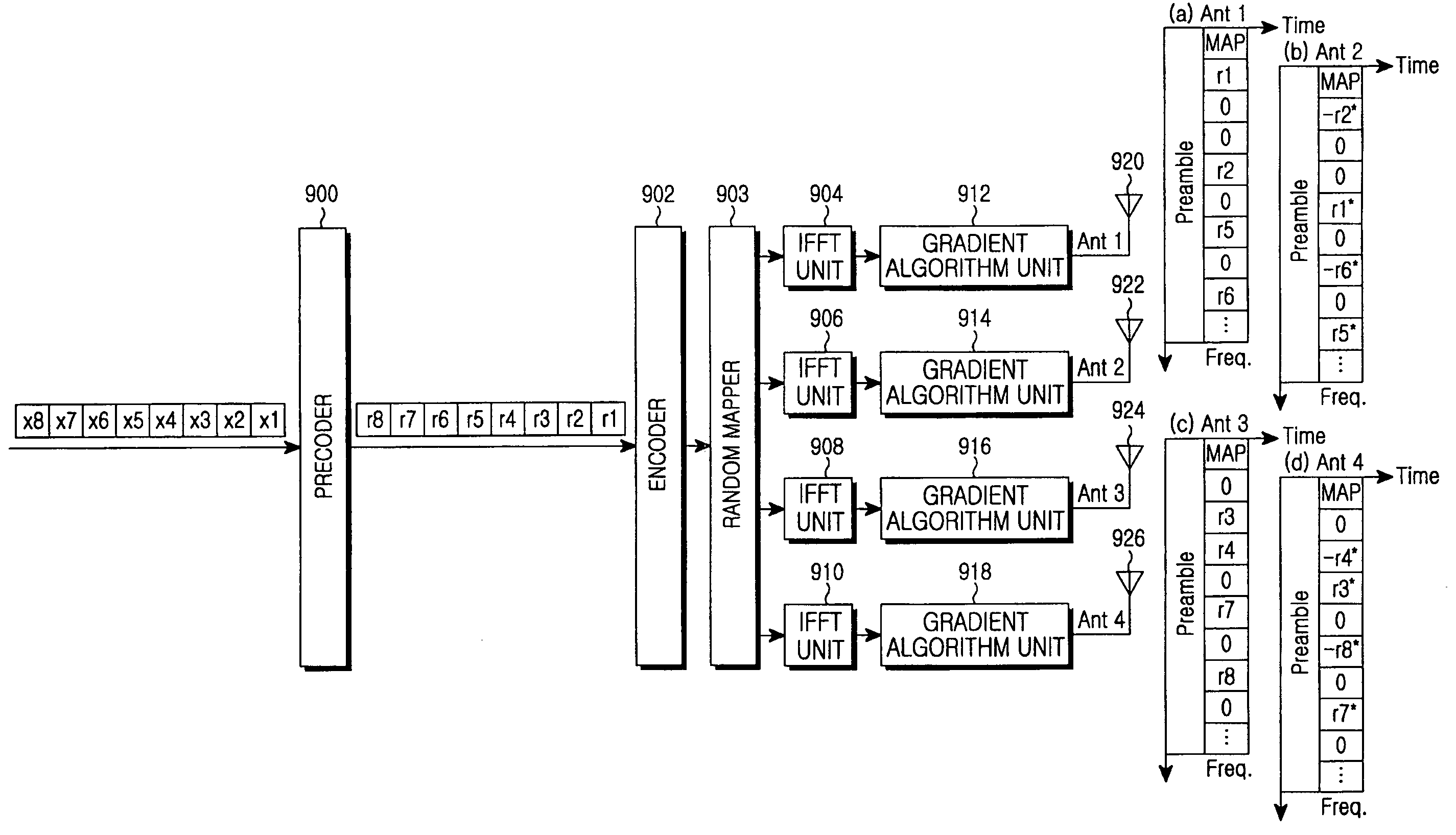
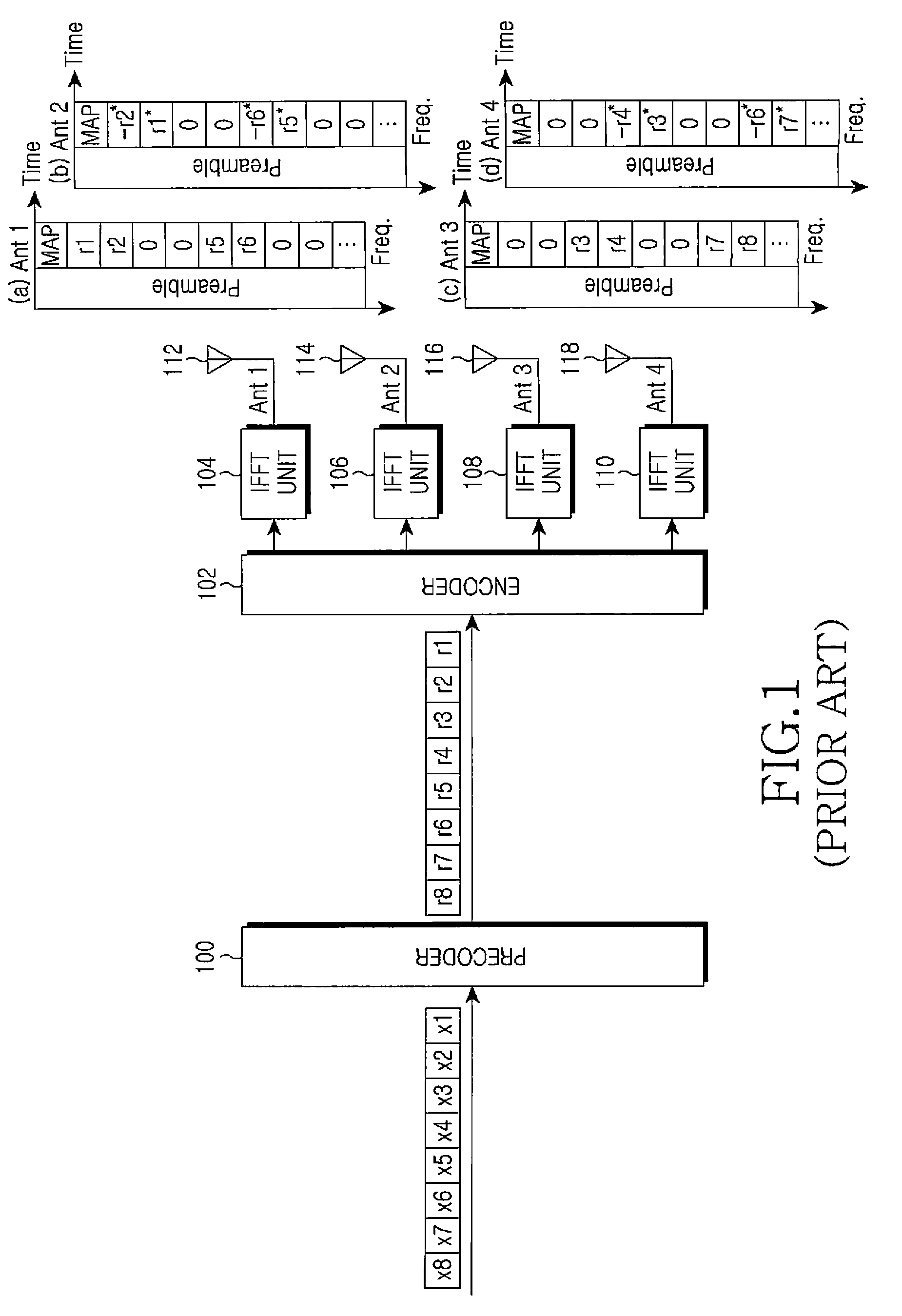
Apparatus and method for minimizing a PAPR in an OFDM communication system
InactiveUS20060078066A1Reduce PAPRMinimizes power ratioSpatial transmit diversityPolarisation/directional diversitySpatial mappingFourier transform on finite groups
A transmitter for minimizing a PAPR in OFDM communication system. The transmitter includes: a precoder for coding input symbols so that a signal rotation is generated, and generating a complex vector including the coded symbols; an encoder for performing a frequency-space mapping for the symbols generated as the complex vector according to a predetermined scheme; a random mapper for randomly mapping the symbols for which the frequency-space mapping has been performed on a frequency plane through at least one transmit antenna; an Inverse Fast Fourier Transform (IFFT) unit for performing an IFFT for the symbols for which the frequency-space mapping has been performed; and a gradient algorithm unit for receiving IFFTed signals from the IFFT unit and reducing the PAPR.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for finding a query-subset of events within a master-set of events
A method and system for determining similarity between a first event set, the first event set including a first plurality of event types, and a second event set, the second event set including a second plurality of event types, is provided. Observed events are randomly mapped to a multidimensional vector-Q and query events are mapped to a multidimensional query vector-q. Comparison of the vectors for a predetermined similarity according to: ∥Q−q∥≦SV, where SV=a predetermined similarity value determines similarity.
Owner:NOKIA TECH OY
Method and device for pre-encoding based on hybrid multiplex demodulation reference symbols
ActiveCN102158319AAvoid interferenceHigh precisionChannel estimationMulti-frequency code systemsRandom mappingData transmission
Owner:G+ COMMUNICATIONS LLC
Method based on linear programming for locating near-field targets and system thereof
InactiveCN101644774AIncrease profitReduce energy consumptionAcoustic wave reradiationResource utilizationTarget signal
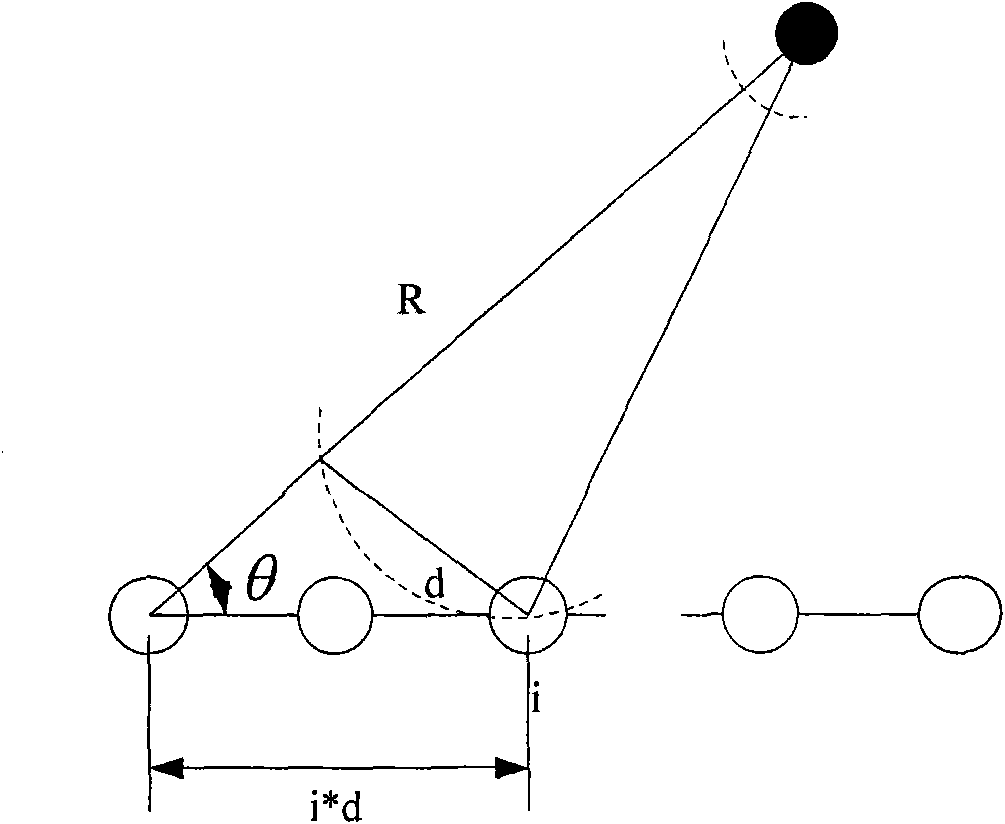
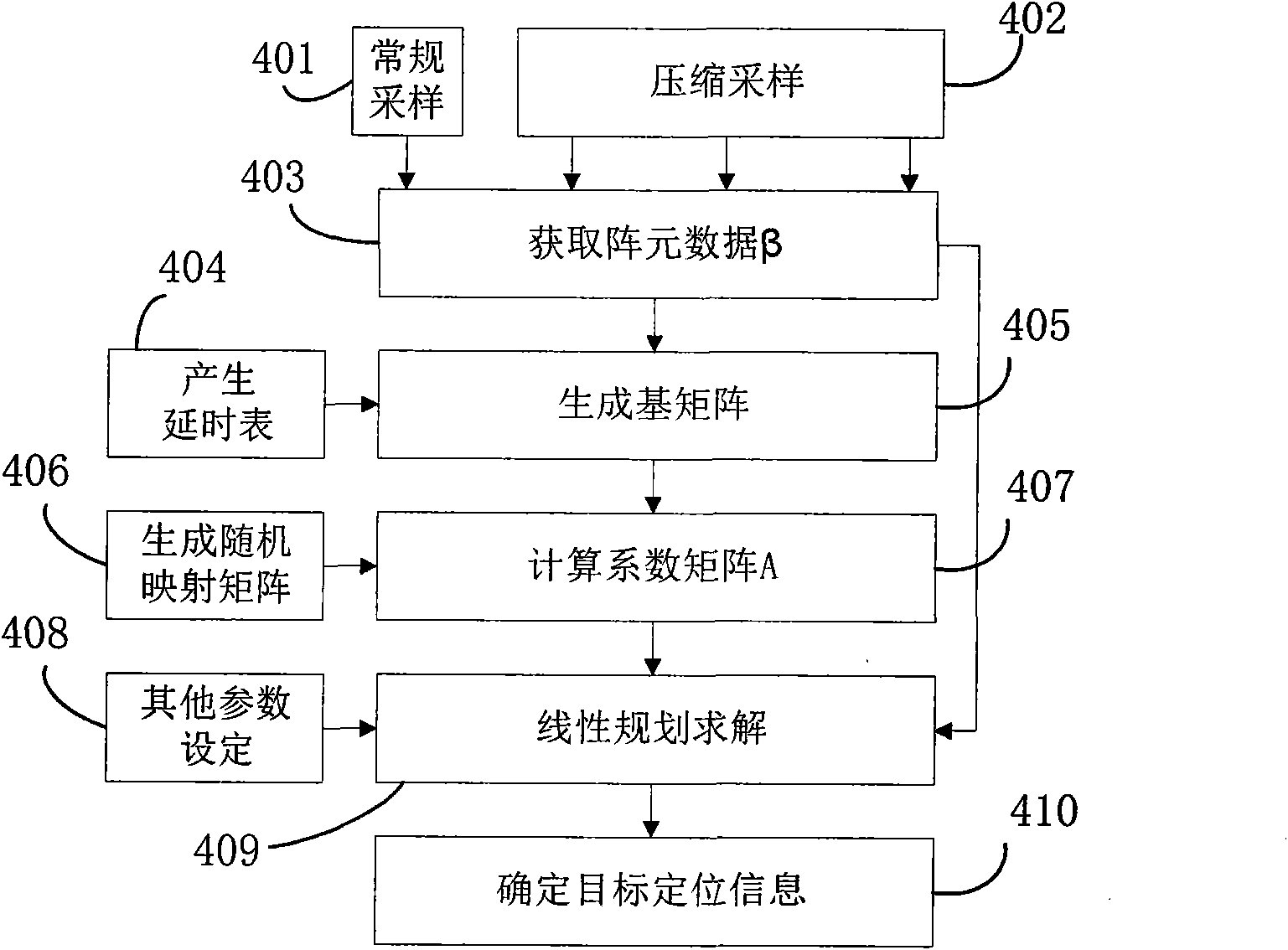
The invention provides a method based on linear programming for locating near-field targets and a system thereof, particularly a method for locating near-field targets on the basis of the compressivesensing theory. The method comprises the following steps: selecting a reference array element under the condition that the signal form is unknown, allowing the reference array element to work at the normal sampling frequency, and the other array elements to work at far below the Nyquist sampling frequency; taking the output signal of the reference array element as the reference target signal, to acquire the sample data of all the array elements; generating a time-delay table and a sparse basis array; generating a random mapping array and obtaining a coefficient array; obtaining a sparse vectorby linear programming solution; and acquiring the location information of the near-field target from the predetermined location-distance collection on the basis of the acquired estimation results ofthe sparse vector. According to the invention, the sensor does not need to work beyond the Nyquist sampling frequency, thereby greatly reducing the sampling rate, reducing the operating energy consumption of the sensor and improving the resource utilization rate of the system; and the method has no limits to the target bandwidth, so that the method is applicable to the target location of both narrowband and wideband, and the method is further applicable to non-Gaussian target location.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
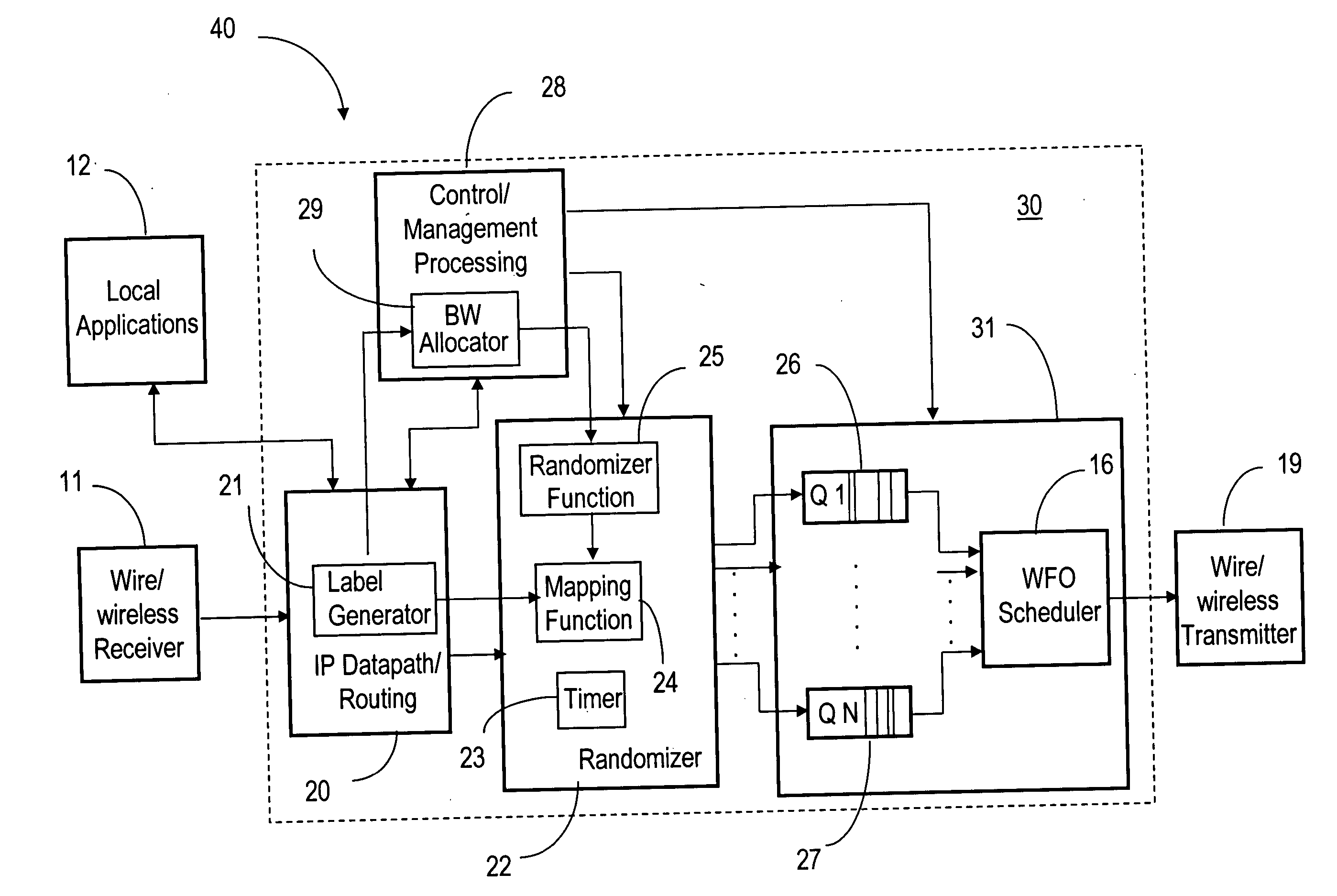
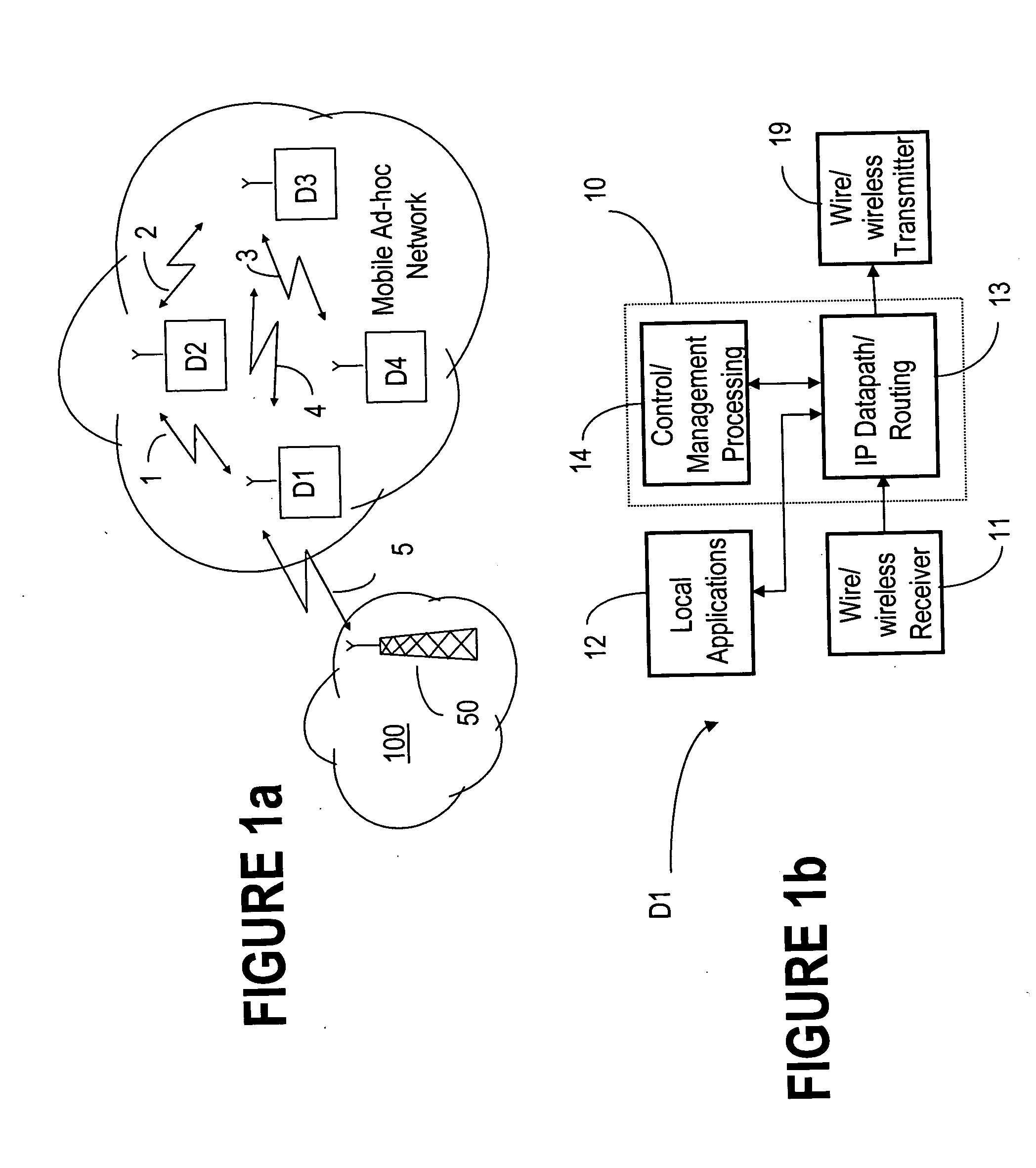
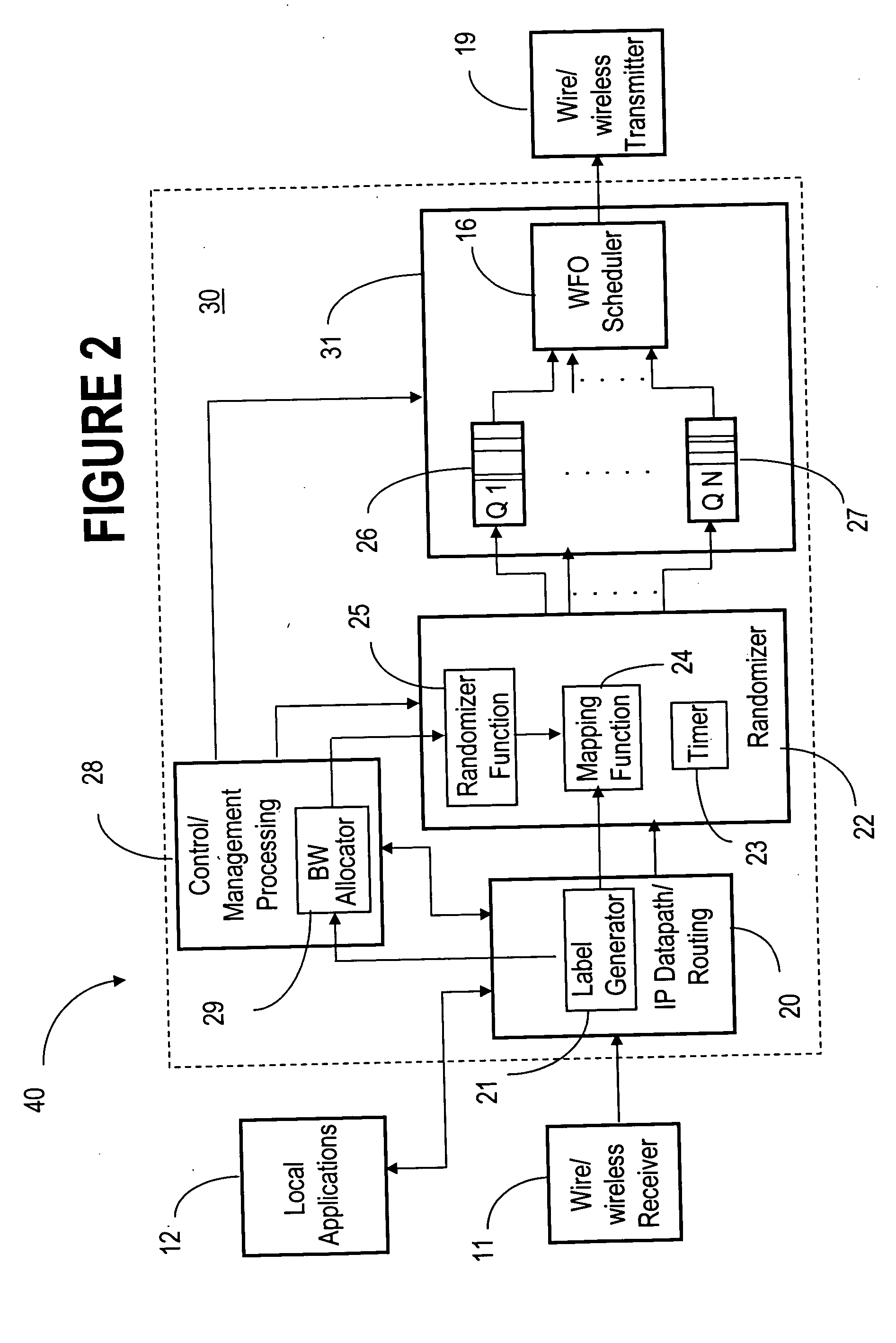
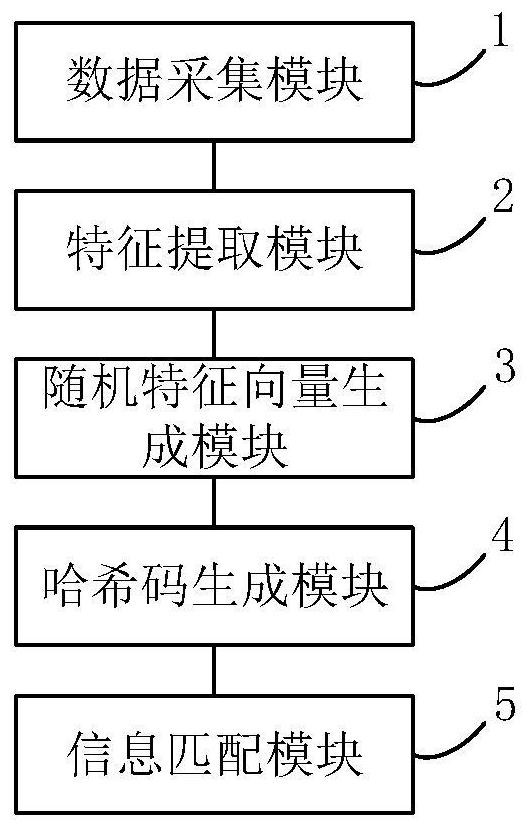
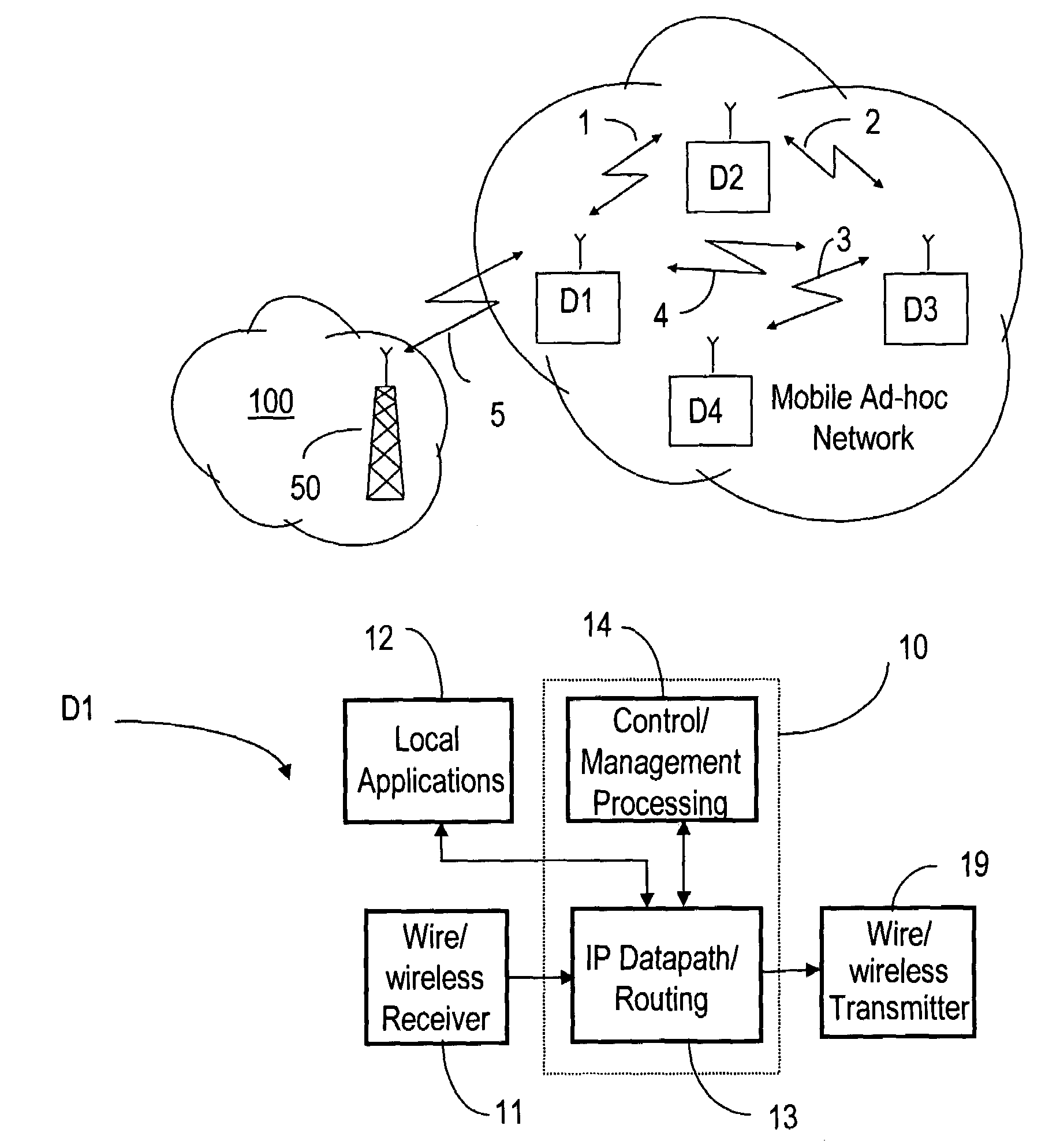
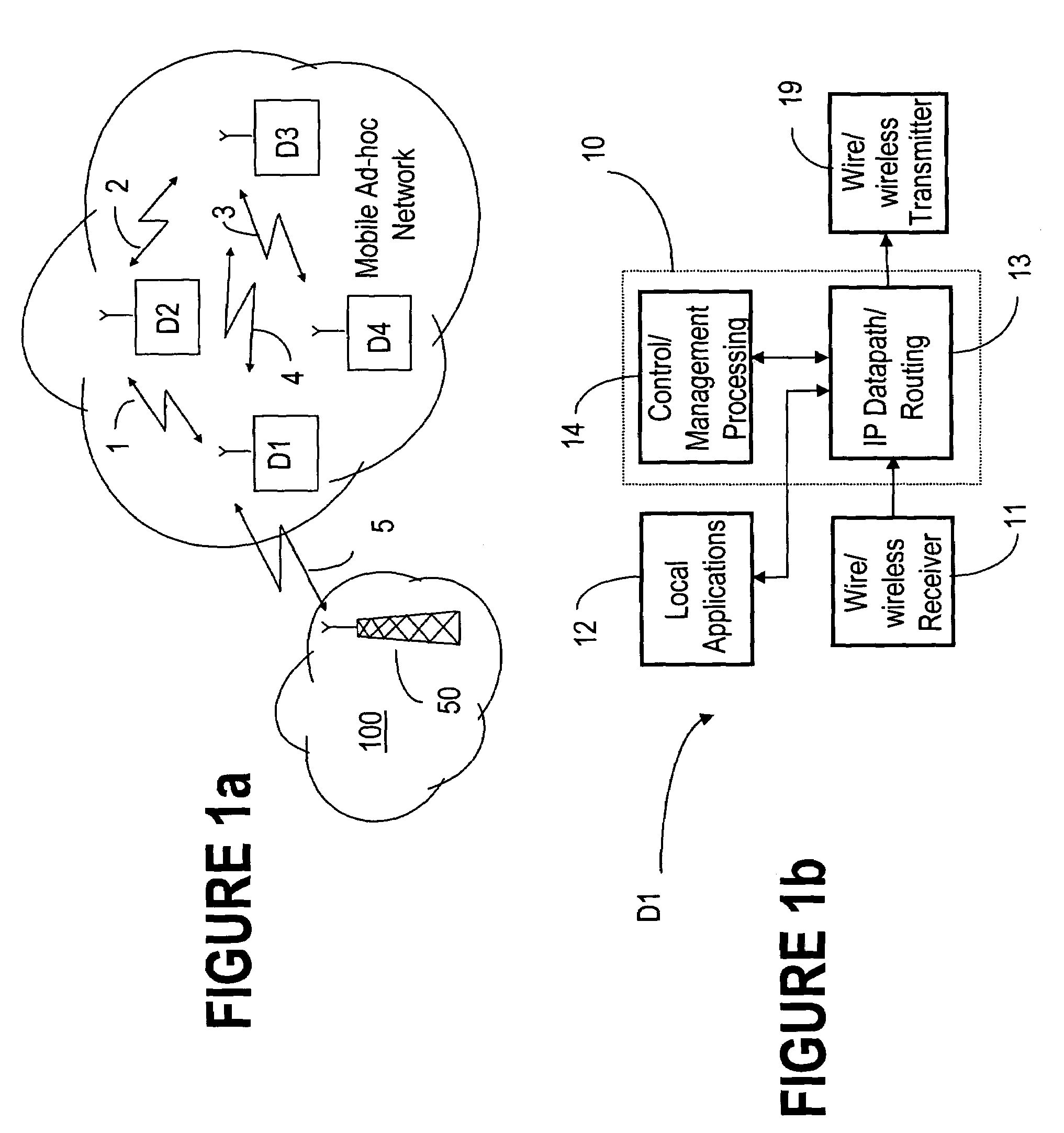
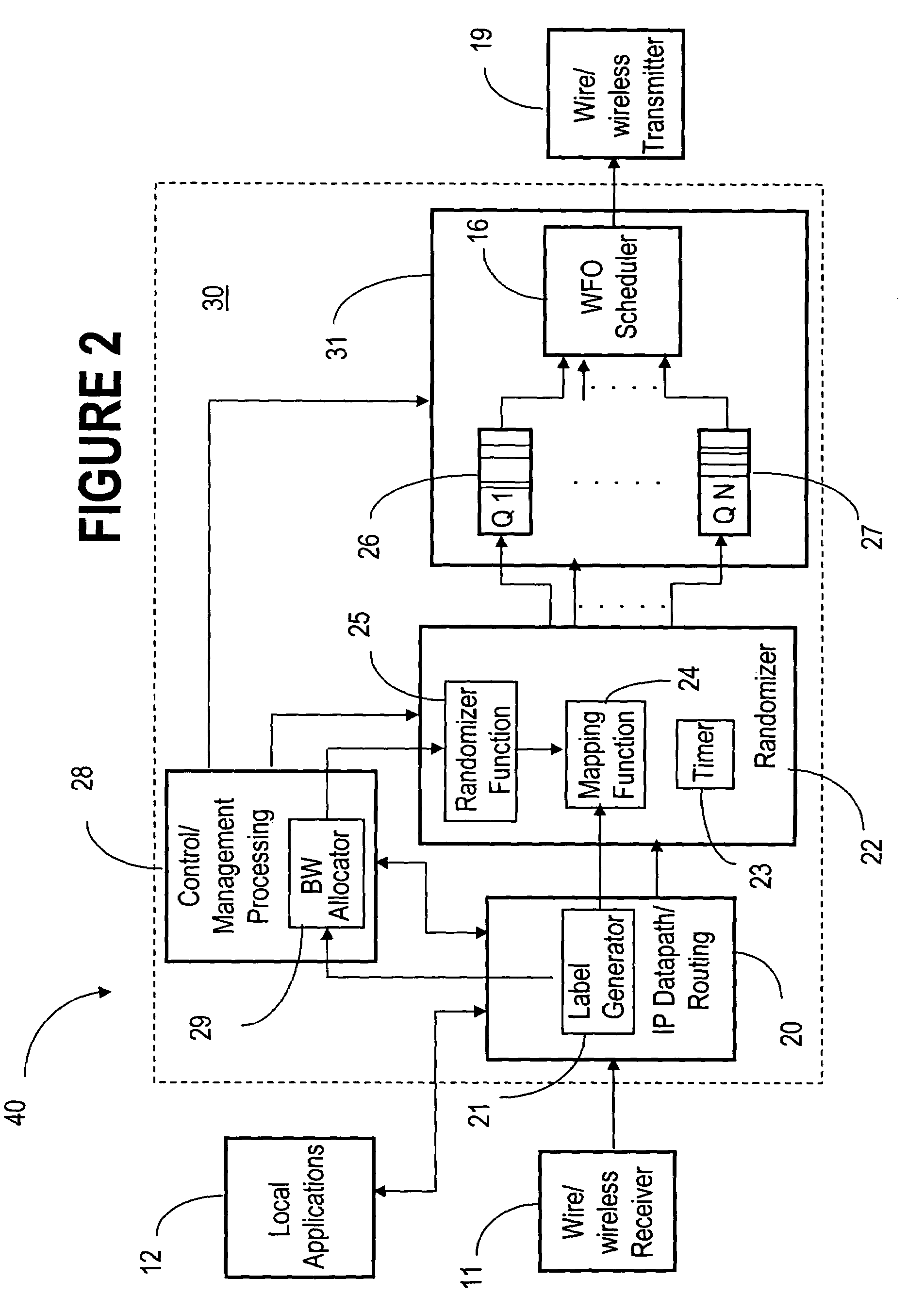
QoS capable mobile ad-hoc network device
ActiveUS20060056353A1Low costFair distribution of network bandwidthError preventionFrequency-division multiplex detailsQuality of serviceRandom mapping
The ad-hoc router enables a decentralized IP routing network (mobile of fixed) amongst a set of network devices, and can offer quality of services for voice, video and data applications. The ad-hoc router is divided into a receiving, control / management processing, IP datapath / routing, randomizer, scheduler and transmission blocks. The IP datapath / routing block provides, in addition to the standard datapath routing functionality, per packet labels that uniquely identify the source device of the packet in the network. The scheduler maintains a plurality of QoS queues, which are then dequeued with a WFQ scheduler, which can be based on standard technology or a simplified low-cost implementation. The randomizer uses the labels to route the packets to a queue such that all packets from the source device, indicated by the label, enter the same queue. For greater security, the randomizer uses a random mapping function that is re-computed periodically.
Owner:ALCATEL LUCENT SAS
Method and system for finding a query-subset of events within a master-set of events
A method and system for determining similarity between a first event set, the first event set including a first plurality of event types, and a second event set, the second event set including a second plurality of event types, is provided. Observed events are randomly mapped to a multidimensional vector-Q and query events are mapped to a multidimensional query vector-q. Comparison of the vectors for a predetermined similarity according to: ∥Q-q∥<=SV, where SV=a predetermined similarity value determines similarity.
Owner:NOKIA TECHNOLOGLES OY
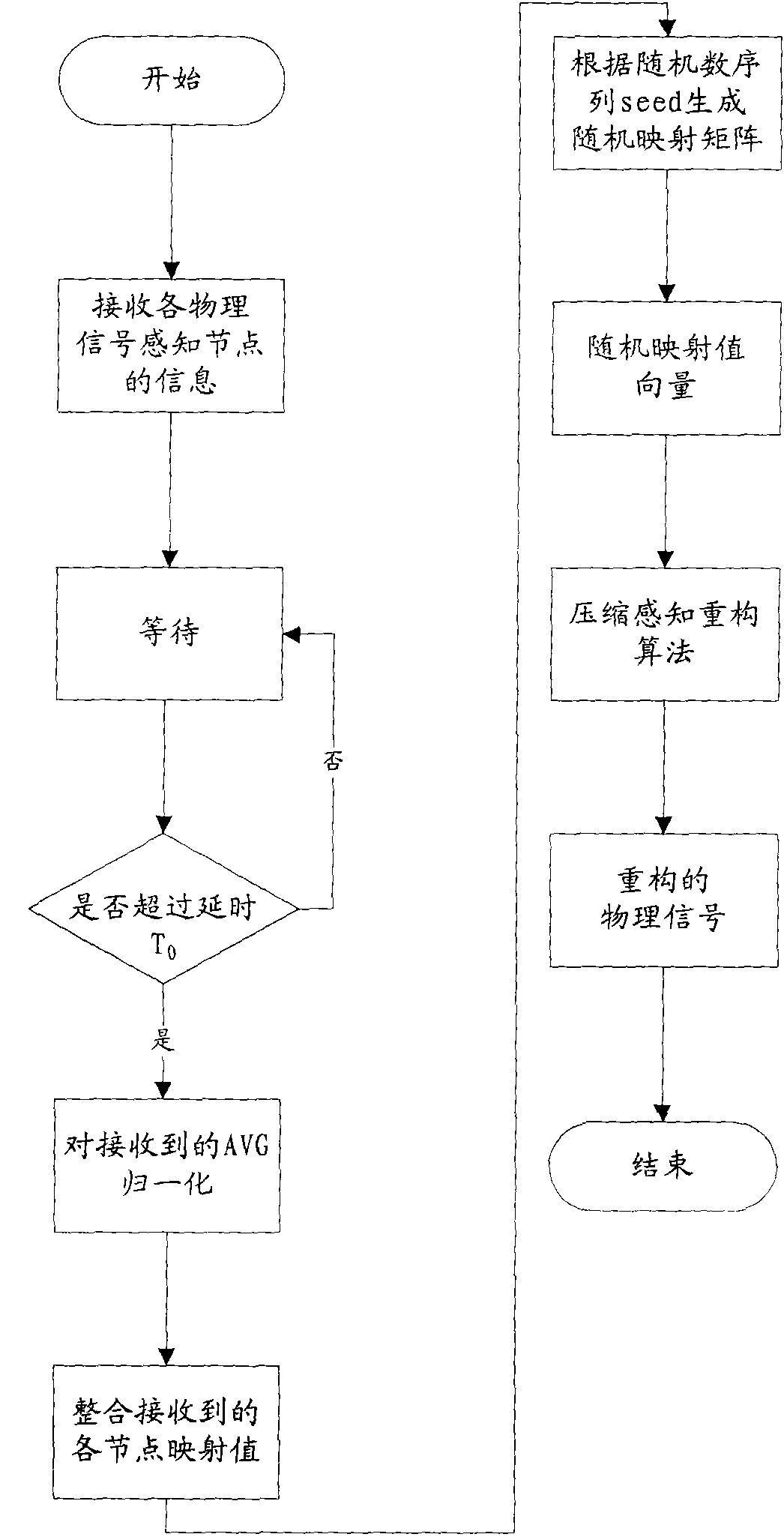
Physical signal collaborative compression sensing system and method for sensor network
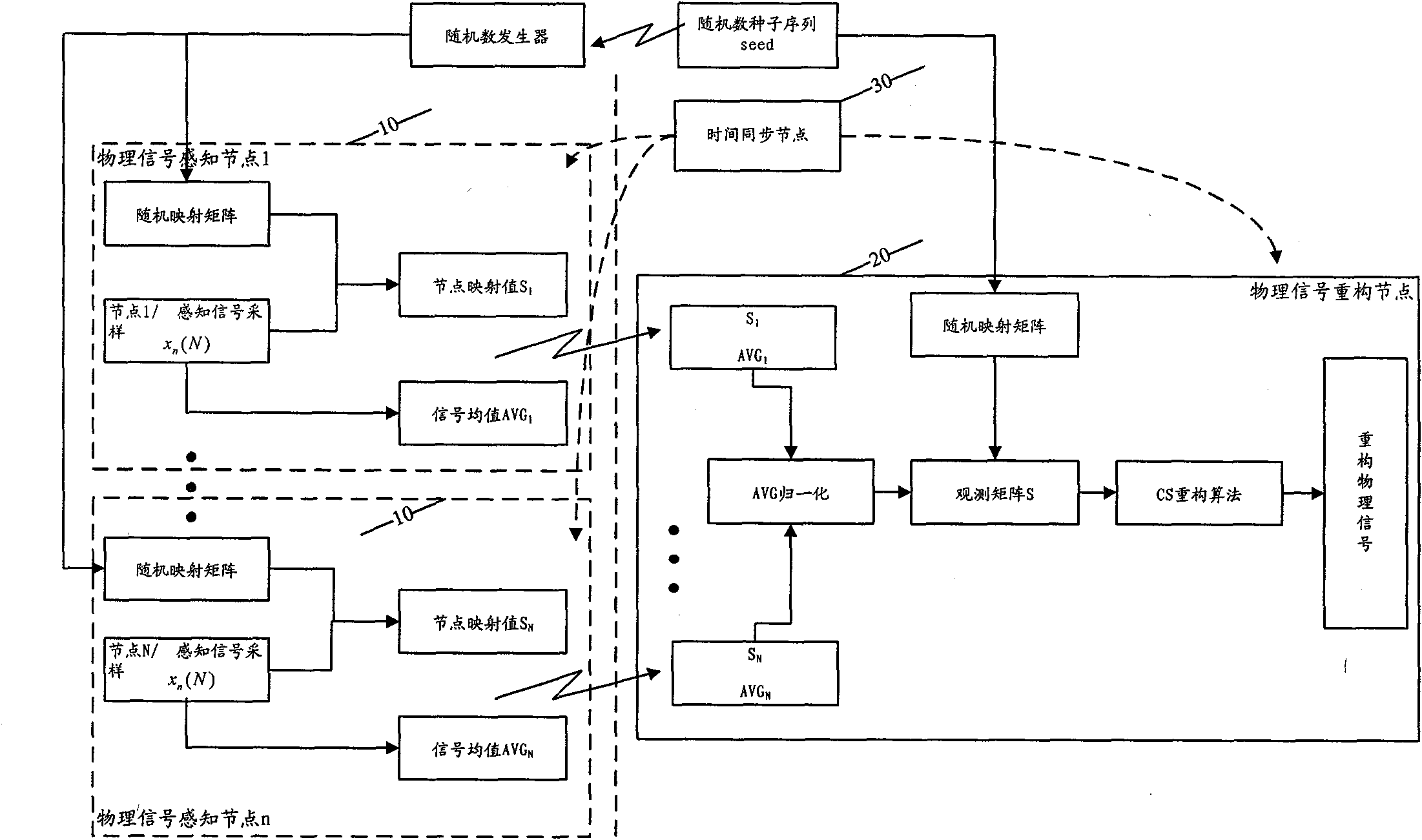
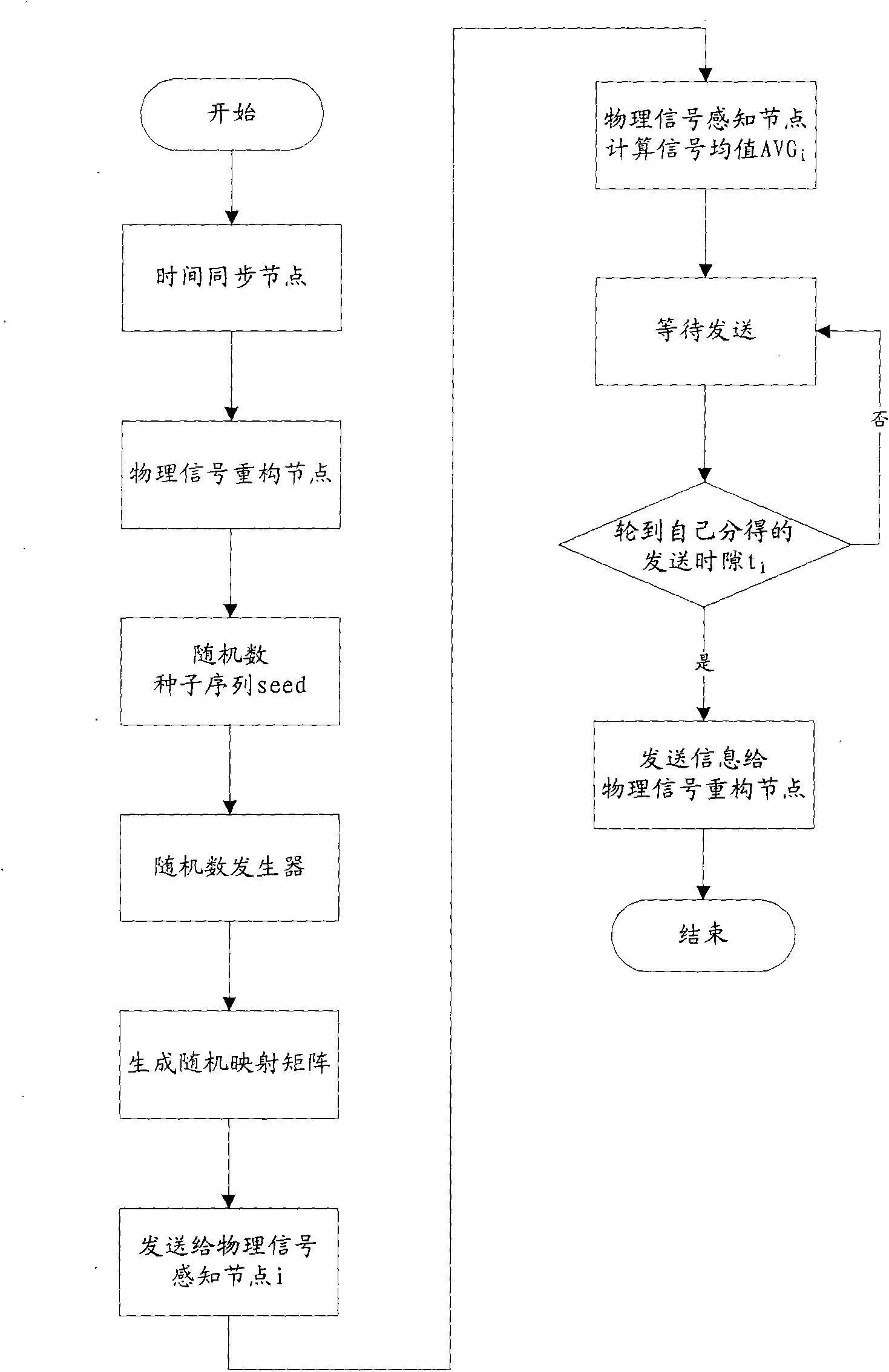
ActiveCN101795501AExtend your lifeReduce data trafficNetwork topologiesRandom mappingPacket loss rate
The invention discloses physical signal collaborative compression sensing system and method for a sensor network. The system comprises physical signal sensing nodes, a physical signal reconstruction node and a time synchronization node; wherein all physical signal sensing nodes are used for sampling physical signals, carrying out random mapping on sampled signal vectors to obtain a random mapping value, simultaneously carrying out statistic calculation on sampled signals to obtain a statistic value and transmitting the random mapping value and the statistic value into the physical signal reconstruction node; and the physical signal reconstruction node is used for collecting the random mapping value and the statistic value from the physical signal sensing nodes, finishing the matrix normalization of the random mapping value and realizing the physical signal reconstruction on the basis of a compression sensing reconstruction algorithm. The invention can reduce the data communication volume of each node, prolongs the service life of the whole wireless sensing network and simultaneously realizes the reconstruction and the effective sensing of the physical signals under the conditions of deep fading channel environment, local node failure and high data packet loss rate.
Owner:上海中科赛思信息工程有限公司
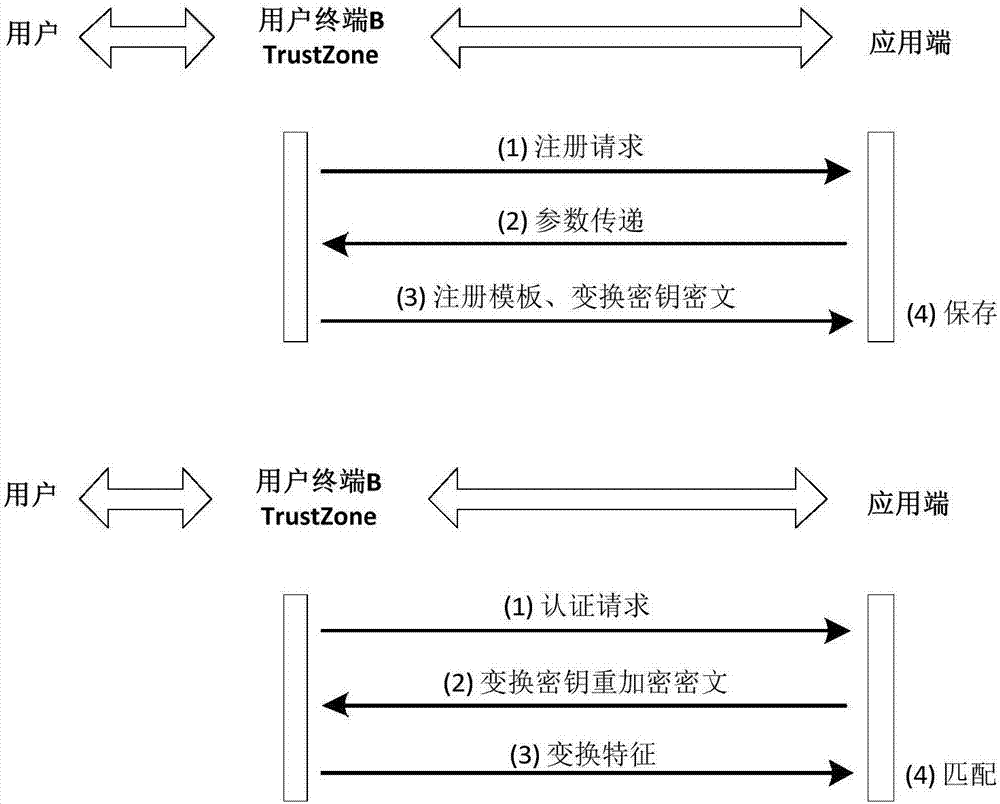
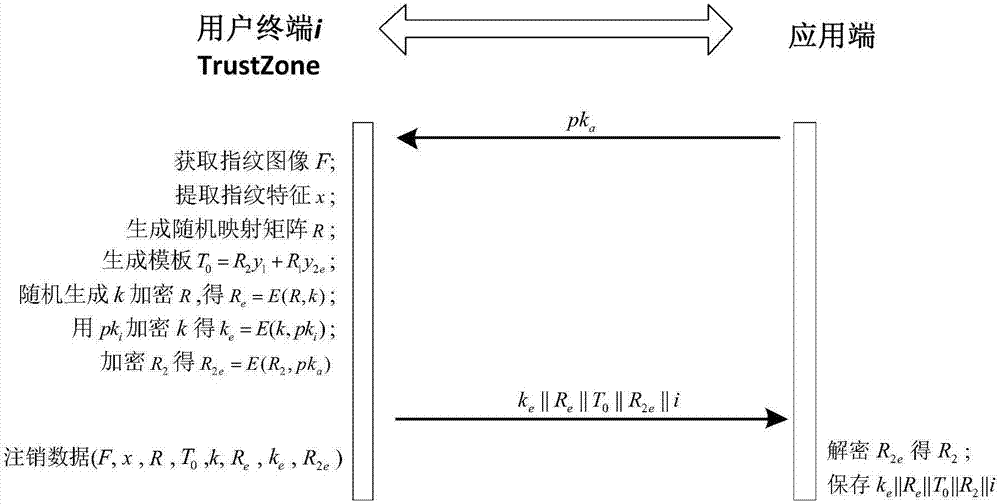
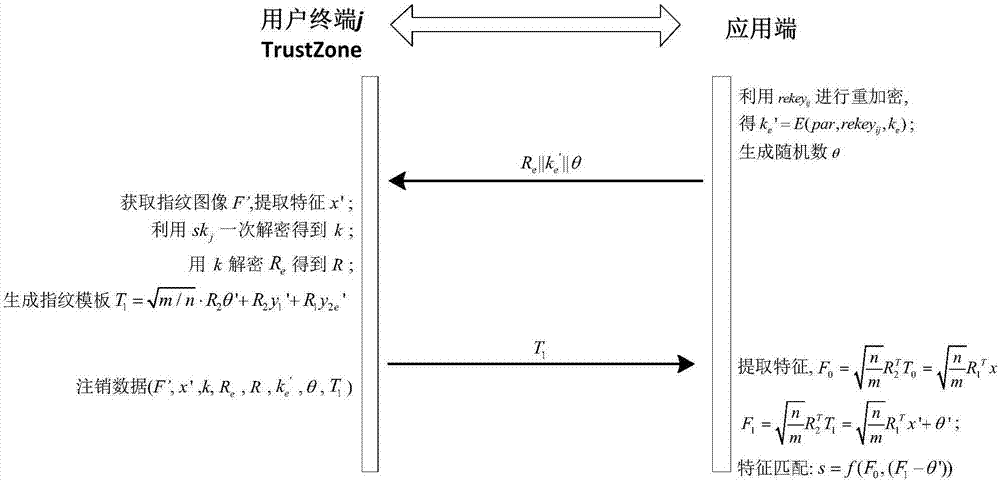
Remote biological feature identity authentication method for strengthening privacy protection
ActiveCN107196765AImprove securityResist attackKey distribution for secure communicationUser identity/authority verificationTrusted ComputingPrivacy protection
The invention provides a remote biological feature identity authentication method for strengthening privacy protection. The method comprises a preprocessing stage, a registration stage and an authentication stage, wherein the preprocessing stage comprises the following steps: inputting a safety parameter, generating a user terminal private key and an application-side public-private key pair, obtaining a transform key for each user terminal to prestore at an application-end; the registration stage comprises the following steps: transmitting the public key to the user terminal through the application-side, generating a saving template for the input biological feature in a TrustZone trust computing zone of the user terminal by using the improved random mapping algorithm, and performing encryption protection on the random mapping matrix; the authentication stage comprises the following steps: generating the transform feature for the input biological feature by using the improved random mapping algorithm, and performing the feature matching by the application-side to realize the identity authentication. By using the technical scheme provided by the invention, the privacy protection of the user fingerprint can be strengthened, and the technical scheme has high attack resistance and the universality of the application.
Owner:WUHAN UNIV
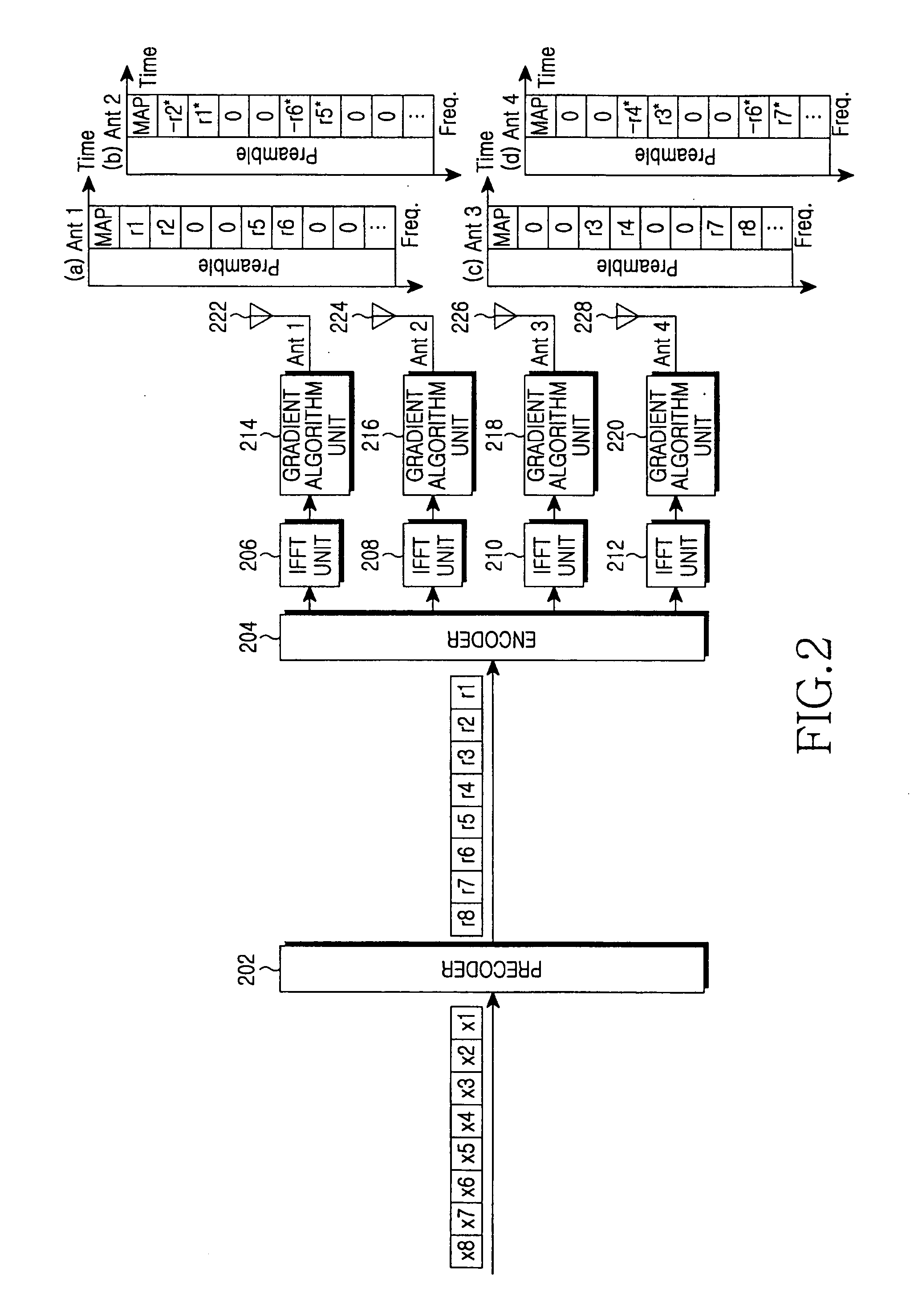
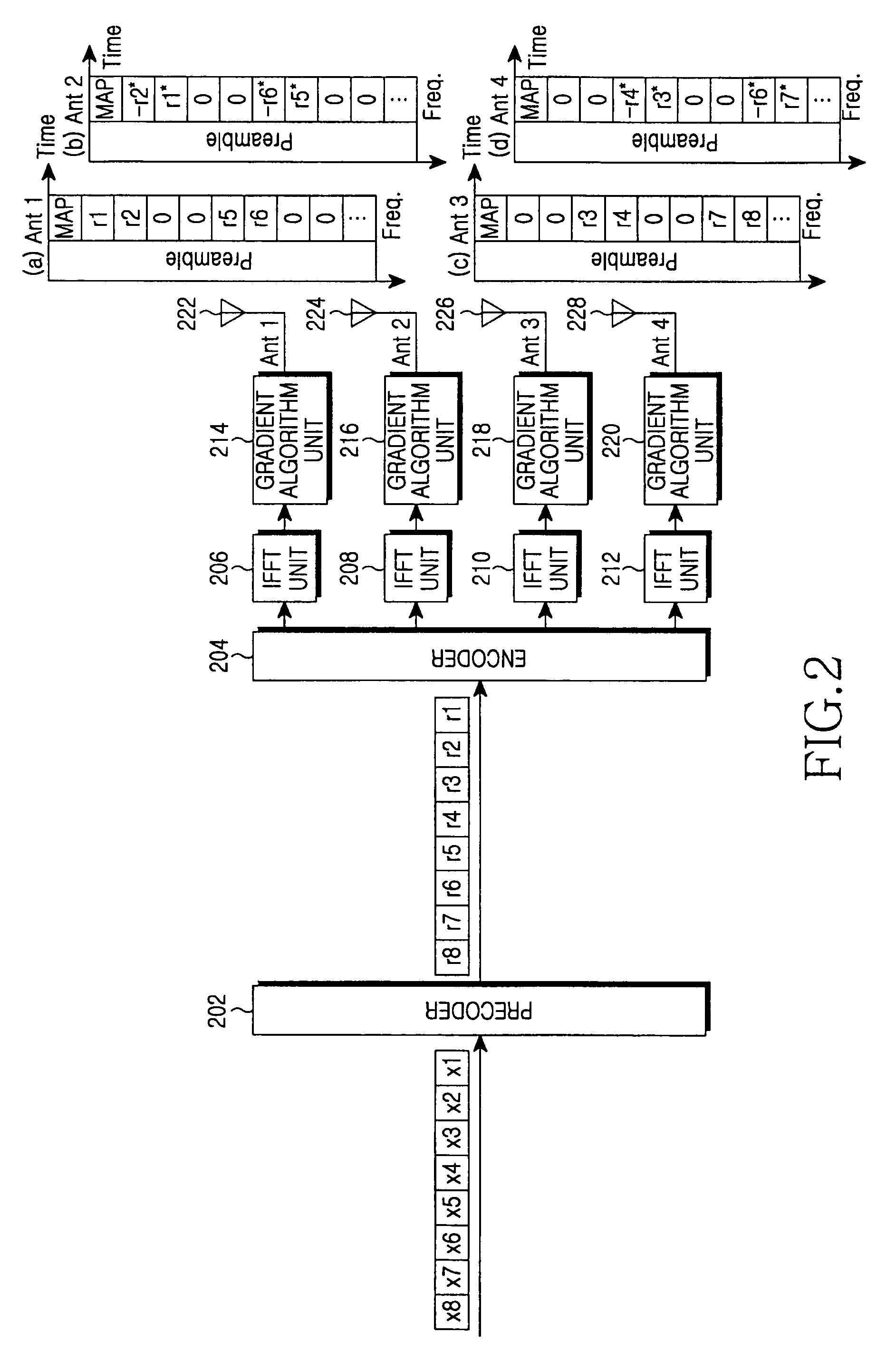
Apparatus and method for minimizing a PAPR in an OFDM communication system
InactiveUS7664192B2Minimizing PAPRPolarisation/directional diversitySecret communicationFast Fourier transformCommunications system
A transmitter for minimizing a PAPR in OFDM communication system. The transmitter includes: a precoder for coding input symbols so that a signal rotation is generated, and generating a complex vector including the coded symbols; an encoder for performing a frequency-space mapping for the symbols generated as the complex vector according to a predetermined scheme; a random mapper for randomly mapping the symbols for which the frequency-space mapping has been performed on a frequency plane through at least one transmit antenna; an Inverse Fast Fourier Transform (IFFT) unit for performing an IFFT for the symbols for which the frequency-space mapping has been performed; and a gradient algorithm unit for receiving IFFTed signals from the IFFT unit and reducing the PAPR.
Owner:SAMSUNG ELECTRONICS CO LTD
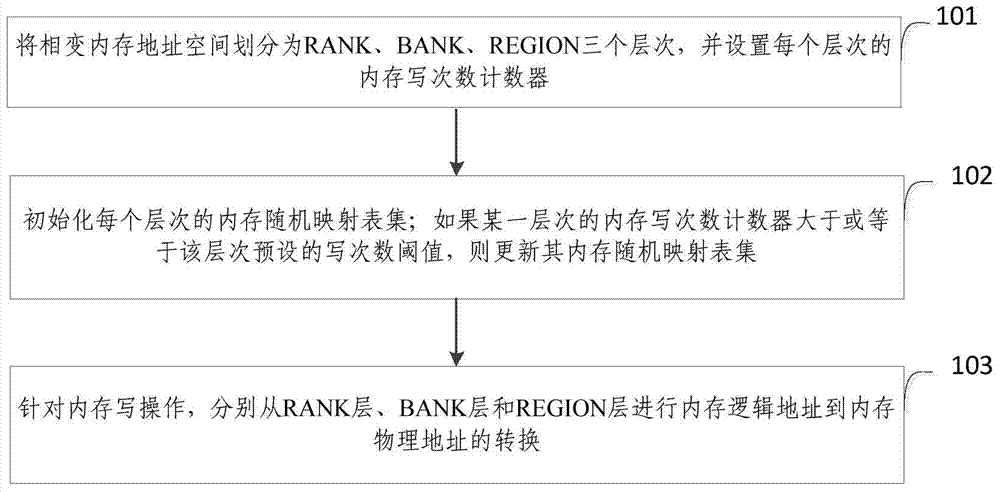
Layered phase-change memory abrasion equilibrating method and system based on random mapping
ActiveCN104714894AExtend your lifeEliminate leaksMemory adressing/allocation/relocationPhase-change memoryFrequency counter
The invention provides a layered phase-change memory abrasion equilibrating method based on random mapping. The layered phase-change memory abrasion equilibrating method based on random mapping comprises the steps that S1, the address space of a phase-change memory is divided into an RANK layer, a BANK layer and an REGION layer, and memory writing frequency counters of all the layers are arranged; S2, a memory random mapping table set of each layer is initialized, wherein if the memory writing frequency counter of a certain layer is equal to or larger than a preset writing frequency threshold valve of the layer, the memory random mapping table set of the layer is updated; S3, conversion from memory logic addresses to memory physical addresses is conducted on the RANK layer, the BANK layer and the REGION layer respectively according to memory writing operation. According to the layered phase-change memory abrasion equilibrating method, the phase-change memory abrasion equilibrating effect ca be improved, the purpose of prolonging the service life of the phase-change memory is realized, and the influence on the performance is minimized.
Owner:TSINGHUA UNIV
Method and system for securing instruction caches using substantially random instruction mapping scheme
InactiveUS20100030967A1Memory adressing/allocation/relocationMicro-instruction address formationProcessing InstructionComputer architecture
A method and system is provided for securing micro-architectural instruction caches (I-caches). Securing an I-cache involves maintaining a different substantially random instruction mapping policy into an I-cache for each of multiple processes, and for each process, performing a substantially random mapping scheme for mapping a process instruction into the I-cache based on the substantially random instruction mapping policy for said process. Securing the I-cache may further involve dynamically partitioning the I-cache into multiple logical partitions, and sharing access to the I-cache by an I-cache mapping policy that provides access to each I-cache partition by only one logical processor.
Owner:SAMSUNG ELECTRONICS CO LTD
Phase change memory abrasion balancing method and system based on random mapping
ActiveCN104731713AExtend your lifeEliminate leaksMemory architecture accessing/allocationMemory adressing/allocation/relocationMemory addressPhase-change memory
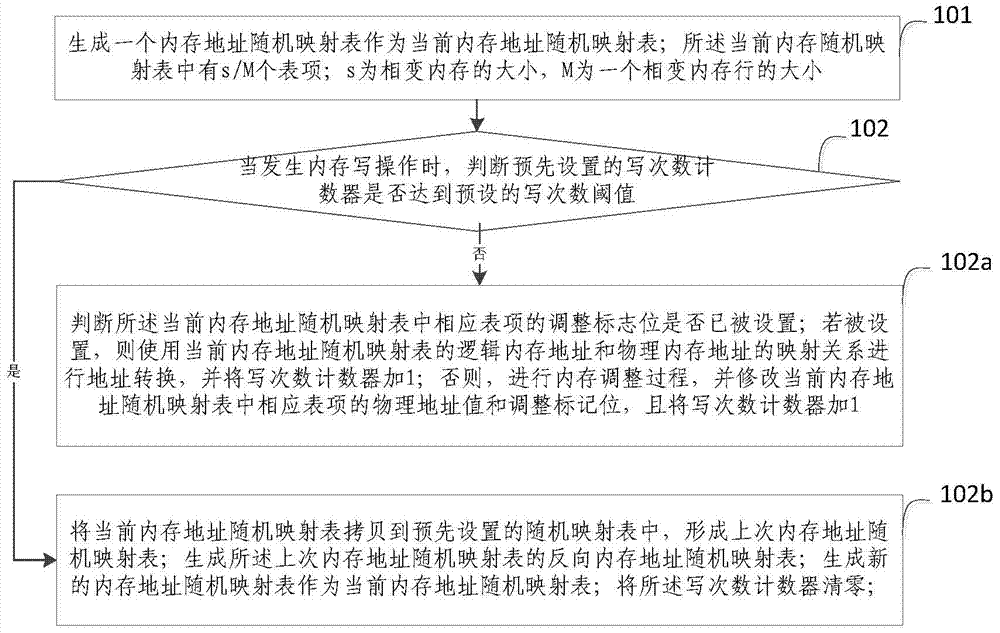
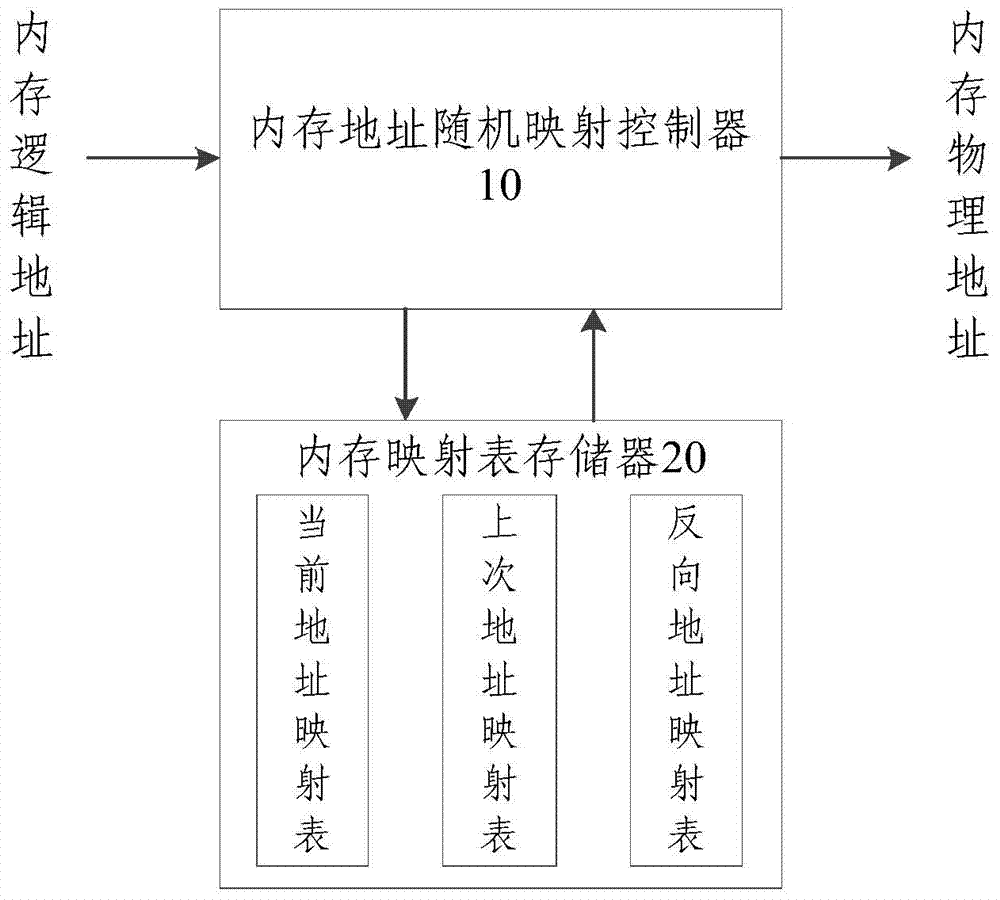
The invention provides a phase change memory abrasion balancing method based on random mapping. The method includes the steps that a memory address random mapping table is generated to serve as a current memory address random mapping table; s / M table items are included in the current memory address random mapping table; s represents the size of a phase change memory, and M represents the size of a phase change memory row; when memory writing operation occurs, if a writing time counter does not reach a preset writing time threshold value, whether adjustment zone bits of corresponding table items in the current memory address random mapping table have been set is judged; if the adjustment zone bits of corresponding table items in the current memory address random mapping table have been set, a mapping relation between a logical memory address and a physical memory address of the current memory address random mapping table is utilized for address conversion; otherwise, a memory adjustment process is conducted, and physical address values and the adjustment zone bits of corresponding table items in the current memory address random mapping table are corrected. According to the method, the phase change memory abrasion balancing effect can be improved, the service life of a phase change memory is prolonged, and influences on performance are reduced to minimum.
Owner:TSINGHUA UNIV
Nand writing balance processing method
ActiveCN102339255AReduce memory usageImprove read performanceMemory adressing/allocation/relocationWrite bufferMemory footprint
The invention discloses a Nand writing balance processing method which comprises the following operating processes: (1) a certain logic block is in a buffer state, the logic block corresponds to two physical blocks, wherein the first physical block is used as an old data block to be read in firstly; a page mapping relationship between the logic block and the first physical block is one-to-one mapping; the second physical block is used as a buffer block to be read in later, and a page mapping relationship between the logic block and the second physical block is random mapping; (2) according to a write buffer algorithm, the page mapping relationship is established; (3) in the write operation process of the physical blocks, if the buffer block which corresponds to the physical block is overwritten, the housekeeping operation process is triggered; the write operation on the physical operation is finished; meanwhile, the corresponding relationship between the logic block and the buffer block is released. According to the Nand writing balance processing method, the two algorithms of page mapping and block mapping are combined so that the high efficiency of read-write performance is ensured while the occupied memory is substantially reduced.
Owner:ANYKA (GUANGZHOU) MICROELECTRONICS TECH CO LTD
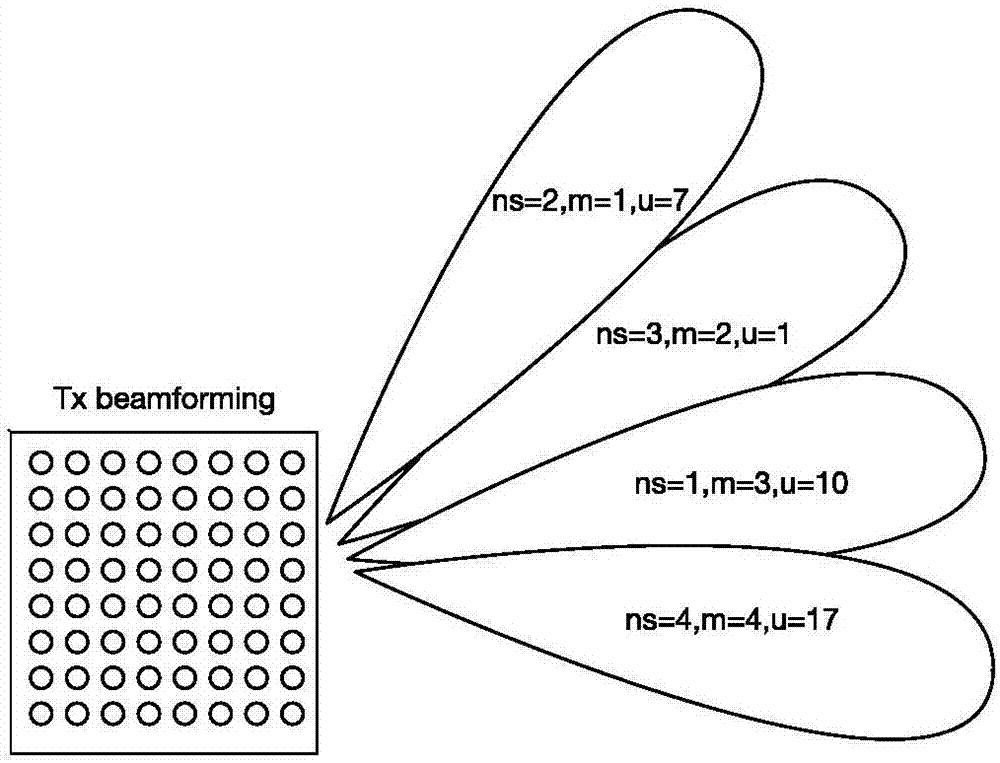
Beam selection method and device based on beam forming, base station and terminal
ActiveCN106888042AReduce distractionsReduce selection errorsSpatial transmit diversityCommunications systemFrame sequence
The invention provides a beam selection method and device based on beam forming, a base station and a terminal. The method comprises a step of generating a pseudo random orthogonal reference signal sequence, a step of determining an alternative reference signal and an alternative emission beam corresponding to each sub frame sequence according to a first preset pseudo random mapping relation among a reference signal sequence, an emission beam sequence and a sub frame number, a step of sending the alternative reference signal corresponding to the current sub frame number to the terminal by the alternative emission beam corresponding to the current sub frame number through a mode of beam forming according to a time sequence, and a step of carrying out beam selection through a target emission beam and the target reception beam of the terminal according to the beam information of the target emission beam returned by the terminal. According to the beam selection method and device based on beam forming, the base station and the terminal, the inter-cell interference can be greatly reduced, a flash effect is effectively overcome, a problem of the wrong selection of the target emission beam and the target reception beam caused by reference signal collision is reduced, and the performance of the communication system is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
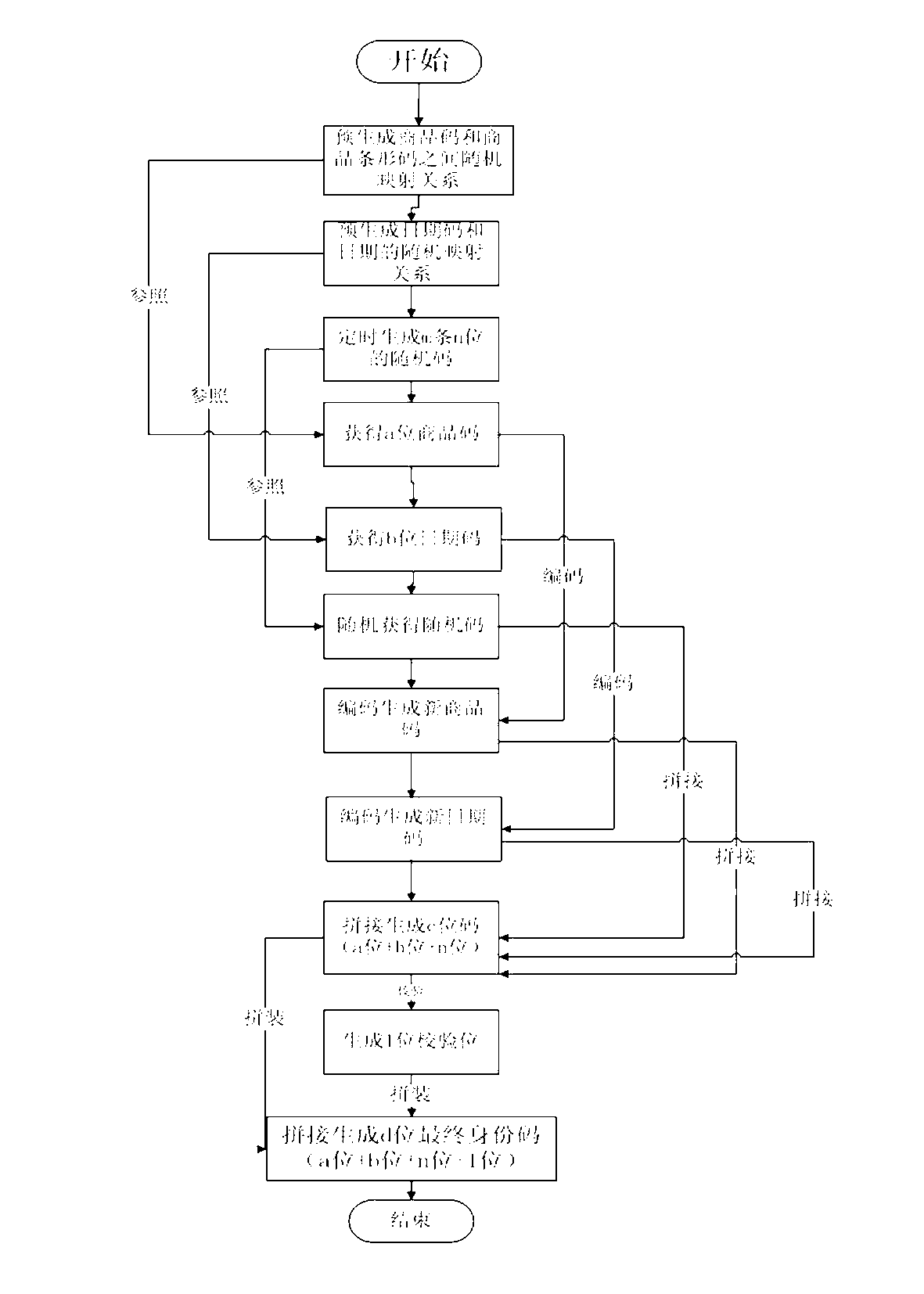
Identity code generation method
ActiveCN102842052AImprove relevanceFor physical storageRecord carriers used with machinesAlgorithmTheoretical computer science
The invention discloses an identity code generation method. The identity code sequentially comprises a product code, a data code, a random code and a check code; the method comprises the following steps of: (1) pre-generating a random mapping relation between the product code and a product barcode; (2) pre-generating the random mapping relation between the data code and the date of every day; (3) pre-generating the data of the random code; (4) acquiring the corresponding product code from the mapping relation according to the product barcode; (5) acquiring the corresponding date code; (6) acquiring the random code and recording the beginning, the destination, the number of the applied code and the product ID; (7) encoding and generating a new product code and encoding the product code; (8) encoding and generating a new date code; (9) jointing the code into a temporary identity code; (10) calculating one check code; (11) jointing the identity code obtained from the step (9) and the check code obtained from the step (10) into a final required identity code.
Owner:南京华博科技有限公司
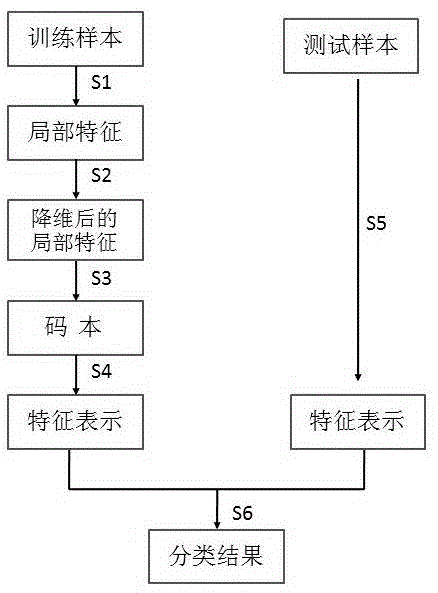
Foundation cloud atlas classification method based on spatial pyramid random mapping
InactiveCN103605988AShow wellImprove efficiencyCharacter and pattern recognitionCurse of dimensionalityFeature set
The invention discloses a foundation cloud atlas classification method based on spatial pyramid random mapping. The method comprises the following steps of firstly, extracting local features from each training foundation cloud atlas sample in a denseness sampling manner; then, carrying out dimensionality reduction on each local feature by applying random mapping, and mapping an original high-dimensionality feature set to a low-dimensionality subspace; then, clustering features which are subjected to dimensionality reduction in the low-dimensionality subspace, so as to obtain a codebook; then, dividing a sample image into different areas according to a spatial pyramid model, obtaining area features of the different areas according to the codebook, combining the area features, and taking the combined area features as final feature representation of the sample image; finally, obtaining a classification result of a tested foundation cloud atlas by applying a support vector machine classifier. According to the method, spatial information of the image can be obtained through applying the spatial pyramid model, so that information in the cloud atlas can be better represented; meanwhile, the local features of the image are subjected to dimensionality reduction by adopting random mapping, so that the efficiency of a foundation cloud atlas classification system can be increased, the time expense is reduced, and the dimensionality disaster can be avoided.
Owner:康江科技(北京)有限责任公司
Bearing fault diagnosis method based on hierarchical extreme learning machine
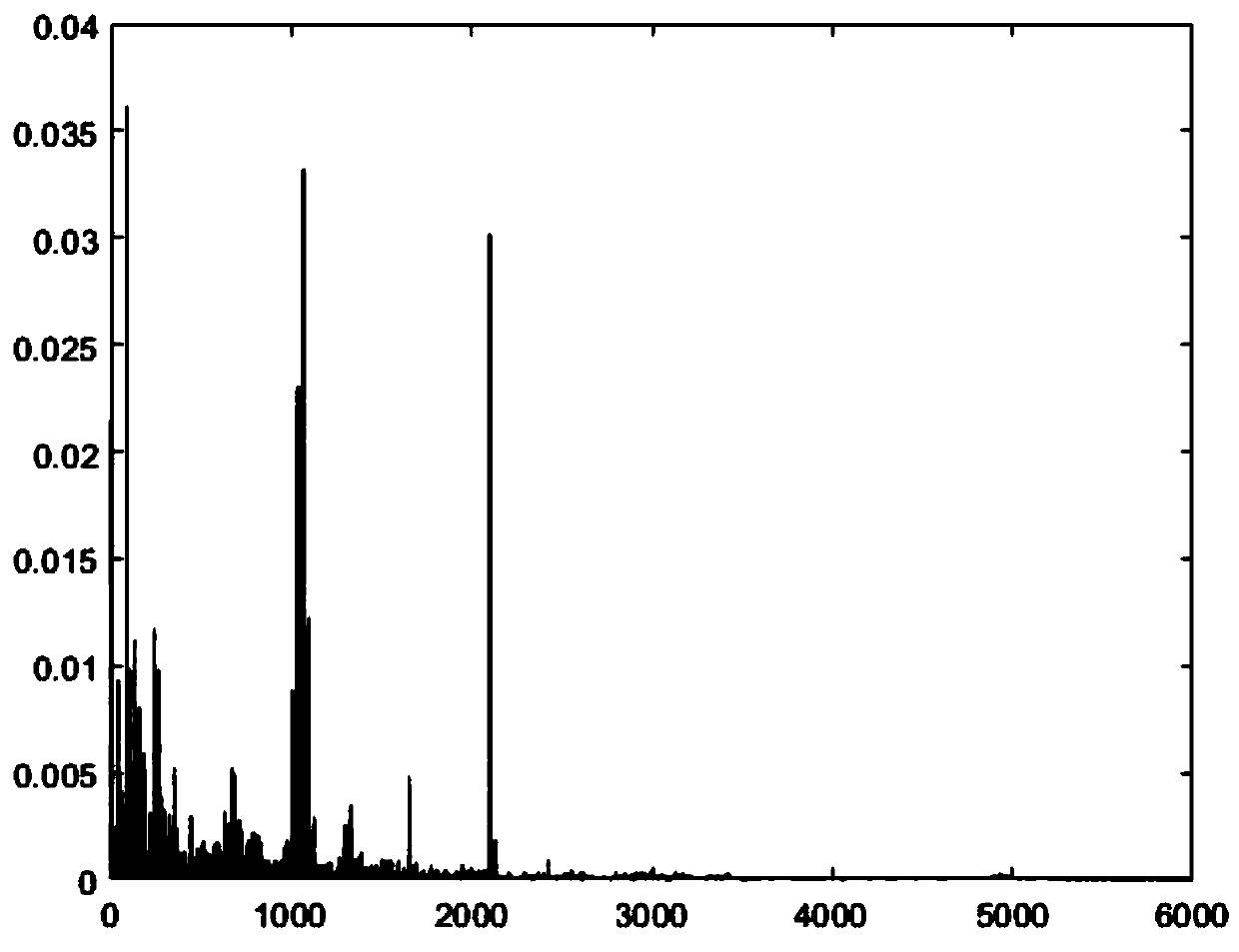
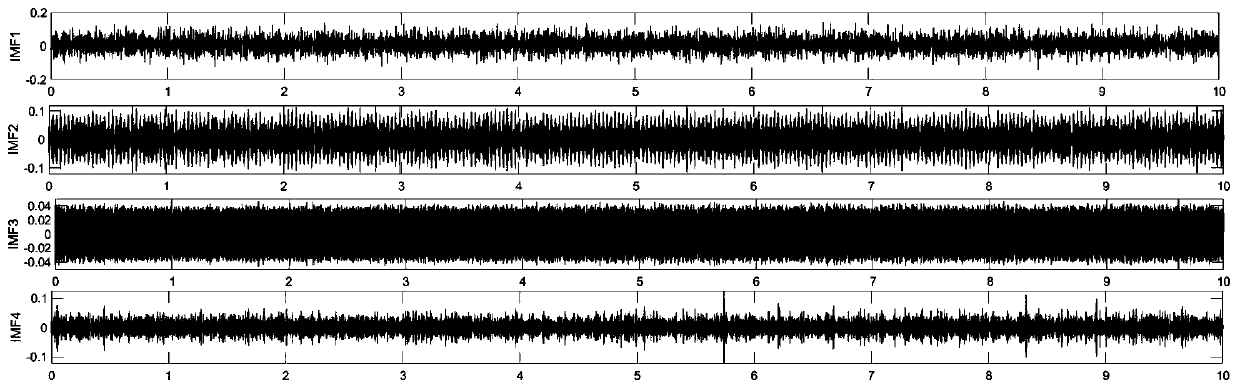
InactiveCN110907177AAccurate classificationIncrease usageMachine part testingLearning machineVibration acceleration
The invention provides a bearing fault diagnosis method based on a hierarchical extreme learning machine, and belongs to the technical field of mechanical part fault diagnosis, and the method comprises the steps: decomposing a vibration acceleration signal into a plurality of modal components through a VMD algorithm; selecting the first four modals sorted according to the size of the center frequency, carrying out feature extraction through an SVD algorithm, mapping input feature data into a random sparse hidden layer space, obtaining hidden information between training samples, and carrying out random mapping again on the feature data processed by the previous layer by each hidden layer through a sparse automatic encoder; and obtaining an optimal neural network weight through a fast iterative shrinkage algorithm (FISTA), so that the actual output is close to the specified label data. According to the method, noise reduction and accurate classification are realized at the same time, and the recognition accuracy and the feature information utilization rate can be improved under the condition of a hierarchical extreme learning machine; compared with an original extreme learning machine, higher recognition precision and higher training speed can be achieved in fault diagnosis of rolling bearing signals.
Owner:BEIJING JIAOTONG UNIV
SCMA resource dynamic optimal distribution method
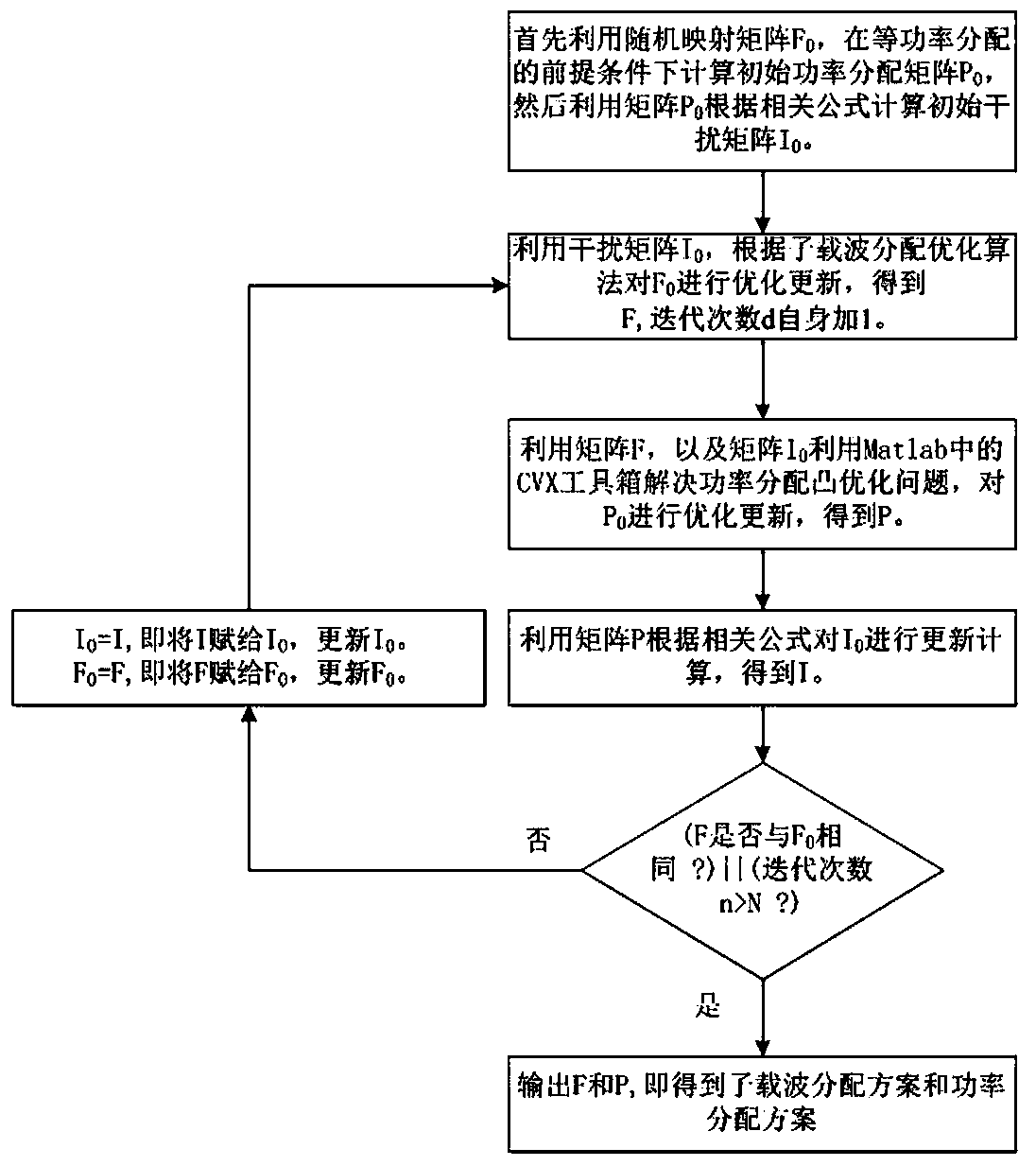
ActiveCN108770054ASignificantly progressiveIncrease capacityPower managementDistribution matrixDistribution method
The invention discloses a SCMA resource dynamic optimal distribution method. For an uplink grouping user accessing to a base station by applying SCMA technology, the sub-carrier distribution and the power distribution of the in-group user are optimized, thereby establishing an optimization model based on the maximized uplink SCMA system and rate. The method comprises the following steps: initializing a random mapping matrix F0 and an equipower distribution matrix P0, and computing to obtain an interference matrix I0; optimally updating the mapping matrix F by using a sub-carrier distribution optimal algorithm according to the obtained interference matrix I0; solving the power distribution of the sub-carrier according to the obtained interference matrix I and the optimized mapping matrix F,namely obtaining a power matrix P; and updating the interference matrix I, and accomplishing multi-turn iterative optimization and corresponding power distribution on the mapping matrix F by using the sub-carrier optimal algorithm until the iteration is reasonably terminated, namely obtaining a sub-carrier distribution scheme and a power distribution scheme. The total system volume is effectivelyimproved.
Owner:NANJING UNIV OF POSTS & TELECOMM
DSSAE-based intermittent process fault diagnosis method
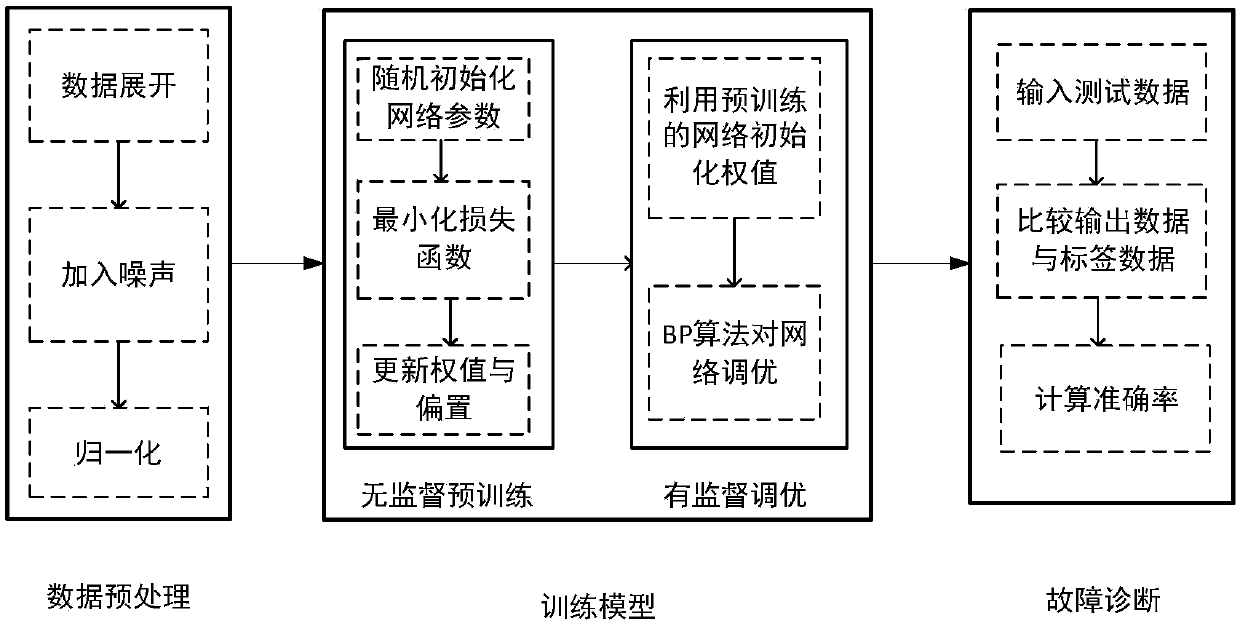
InactiveCN109614992AImprove accuracyRobustCharacter and pattern recognitionNeural architecturesDiagnosis methodsThree stage
The invention discloses a DSSAE-based intermittent process fault diagnosis method, and relates to the technical field of fault diagnosis of machine learning. The method comprises three stages of datapreprocessing, model training and fault diagnosis, wherein the'data preprocessing 'comprises the step of unfolding three-dimensional data in the fermentation process along the variable direction; secondly, corroding input data into a damaged data sample by utilizing random mapping, namely adding a noise reduction code; and finally, carrying out normalization processing on the corroded damaged datasample. And the model training comprises two processes of unsupervised pre-training and supervised tuning. And the fault diagnosis comprises the steps of inputting the collected test data into a trained network for fault diagnosis, outputting a fault category, and counting the accuracy. According to the DSSAE fault diagnosis method and device, only the data in the fault time period are filled, and the influence on the accuracy of DSSAE fault diagnosis due to the fact that too many unknowned data are manually filled is reduced. And meanwhile, the noise reduction codes are added, so that the robustness of the network is improved.
Owner:BEIJING UNIV OF TECH
Arithmetic domain bit interleaved code modulation method
ActiveCN103346863AAchieve adaptiveGuaranteed performanceError preventionBaseband system detailsSignal-to-noise ratio (imaging)Pulse-code modulation
The invention relates to an arithmetic domain bit interleaved code modulation method. The method includes the following steps that 1) the structure of a code is analyzed through an extrinsic information transfer graph, and a superior weight set is selected to construct a mapping matrix; 2) code modulation is carried out at a transmitting end according to the mapping matrix; 3) demodulation and decoding are carried out after a receiving end receives modulated signals. Compared with the prior art, an arithmetic domain bit interleaved code modulation method is put forward on the basis of a random mapping code and is combined with system channel coding, design of self-adaption of a link of the receiving end is achieved, performance of a high signal to noise ratio and performance of a low signal to noise ratio are balanced, and performance of the system can be kept under the condition of coding complexity without increase of the high signal to noise ratio and is improved through using of a coding method under the condition of the low signal to noise ratio.
Owner:TONGJI UNIV
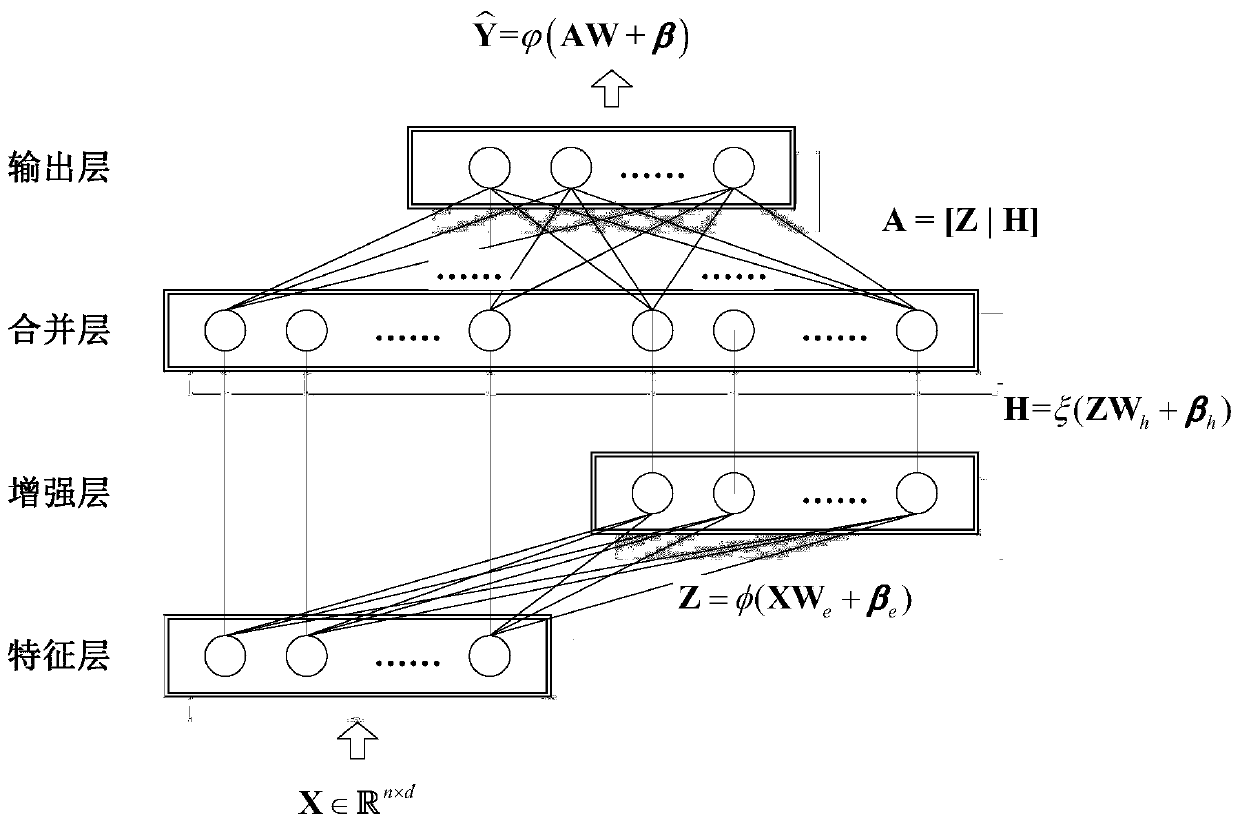
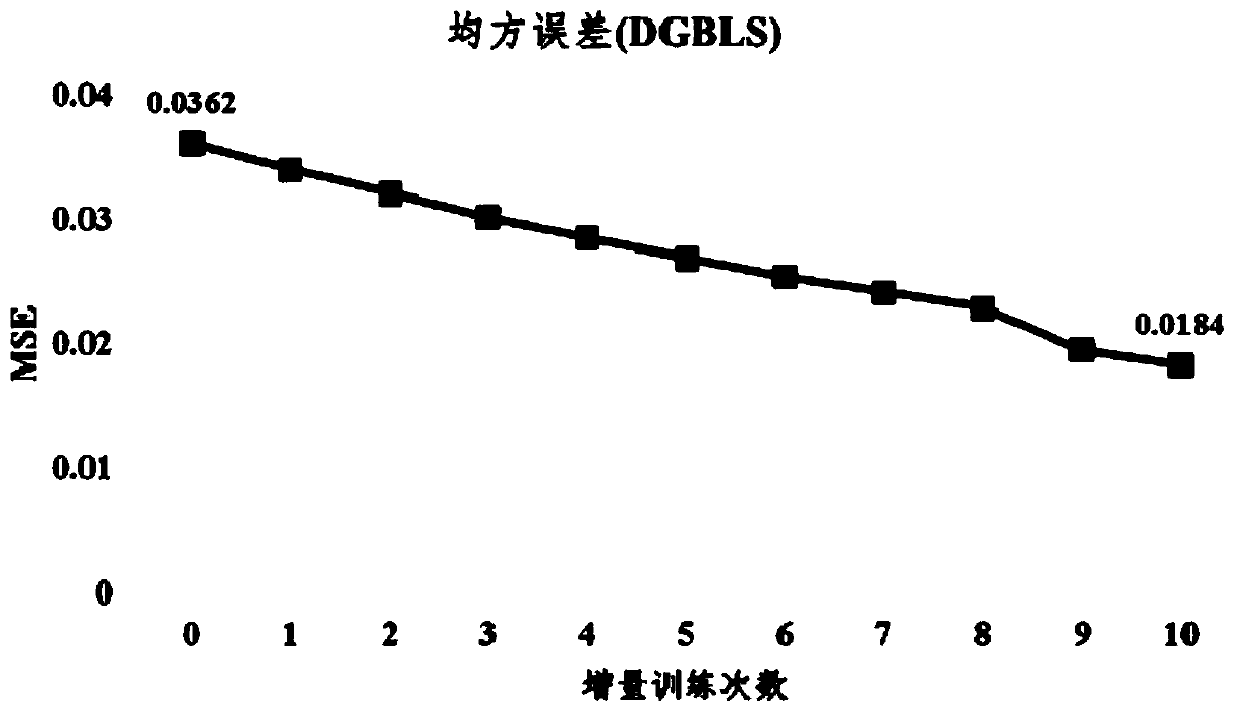
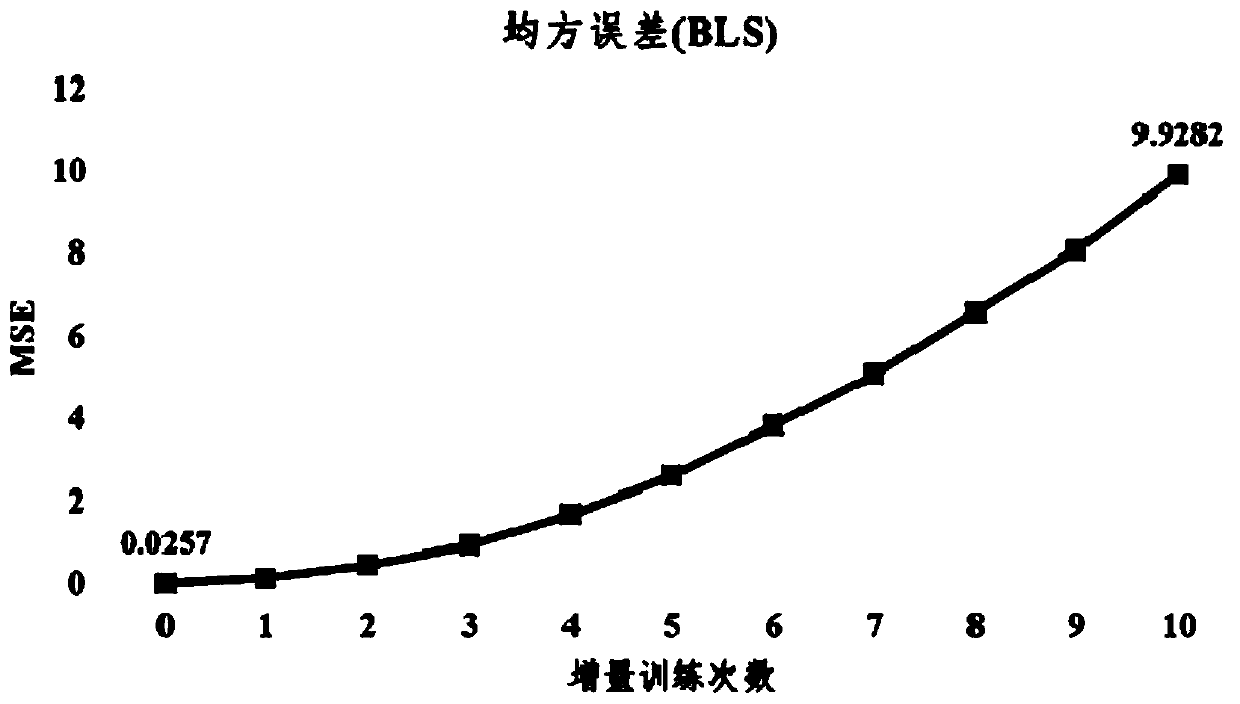
Implementation method of gradient descent width learning system
The invention provides an implementation method of a gradient descent width learning system. The gradient descent width learning system is composed of three dense layers, namely a feature layer, an enhancement layer and an output layer, and a merging layer. The feature layer maps the input data into mapping features by using random mapping to form feature nodes; the enhancement layer enhances themapping features output by the feature layer to form enhancement nodes; the merging layer merges the outputs of the feature nodes and the enhancement nodes and inputs the merged outputs into the output layer as a whole; and the output layer maps the output of the merging layer into the final output of the network, a small batch of training samples are continuously input into the gradient descent width learning system during training, and the gradient descent width learning system adopts a gradient descent method to update the weight of the network, so that the loss of a mean square error MSE loss function is gradually reduced. When the gradient descent width learning system implemented by the method continuously performs small-batch training sample training, the regression performance during batch training can be obviously improved, and the method can be applied to regression tasks.
Owner:CHONGQING UNIV
Human body posture recognition method based on convolutional neural network
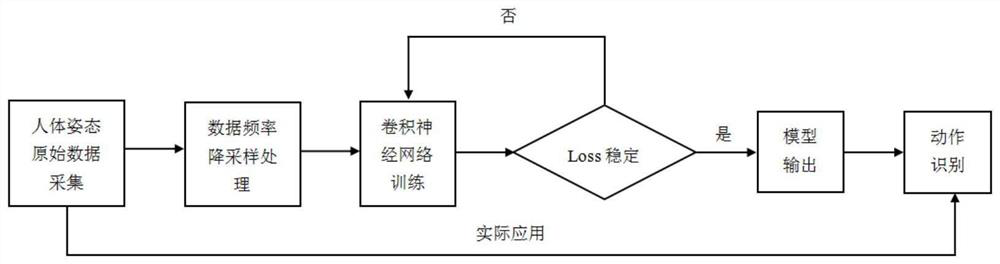
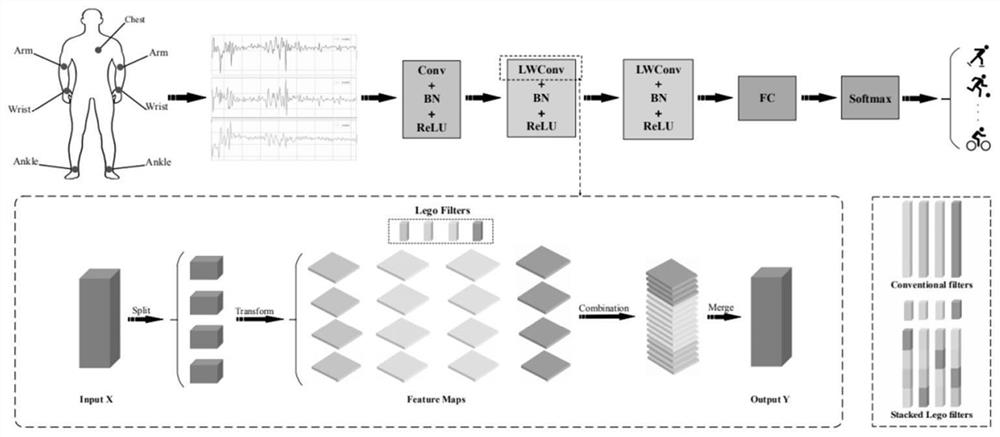
ActiveCN111723662AReduce training timeFast preprocessingCharacter and pattern recognitionNeural architecturesHuman bodyOriginal data
The invention discloses a human body posture recognition method based on a convolutional neural network. The method comprises the steps that original data of a mobile sensor are collected and labeled,data frequency down-sampling and normalization processing are conducted, a training set and a test set are divided, the convolutional neural network is trained, and a model is transplanted to an Android terminal for human body posture recognition. The method is used for human body posture recognition according to a convolutional neural network. According to the method, a Spit-Transform-Merge strategy is introduced into the implementation of the method; a group of Lego convolution kernels with a smaller channel number is provided, the convolution kernels are stacked according to a random mapping and cyclic matrix method so as to realize convolution operation, and finally, generated Lego feature maps are vertically combined and sent to a classifier through a full connection layer for sensordata identification. The method has the advantages of being high in recognition speed, high in recognition accuracy, small in calculation amount, high in generalization capacity and the like, and meanwhile the method plays a very important role in smart home, health detection, motion tracking and the like.
Owner:NANJING NORMAL UNIVERSITY
Biological feature template protection method and device based on deep learning
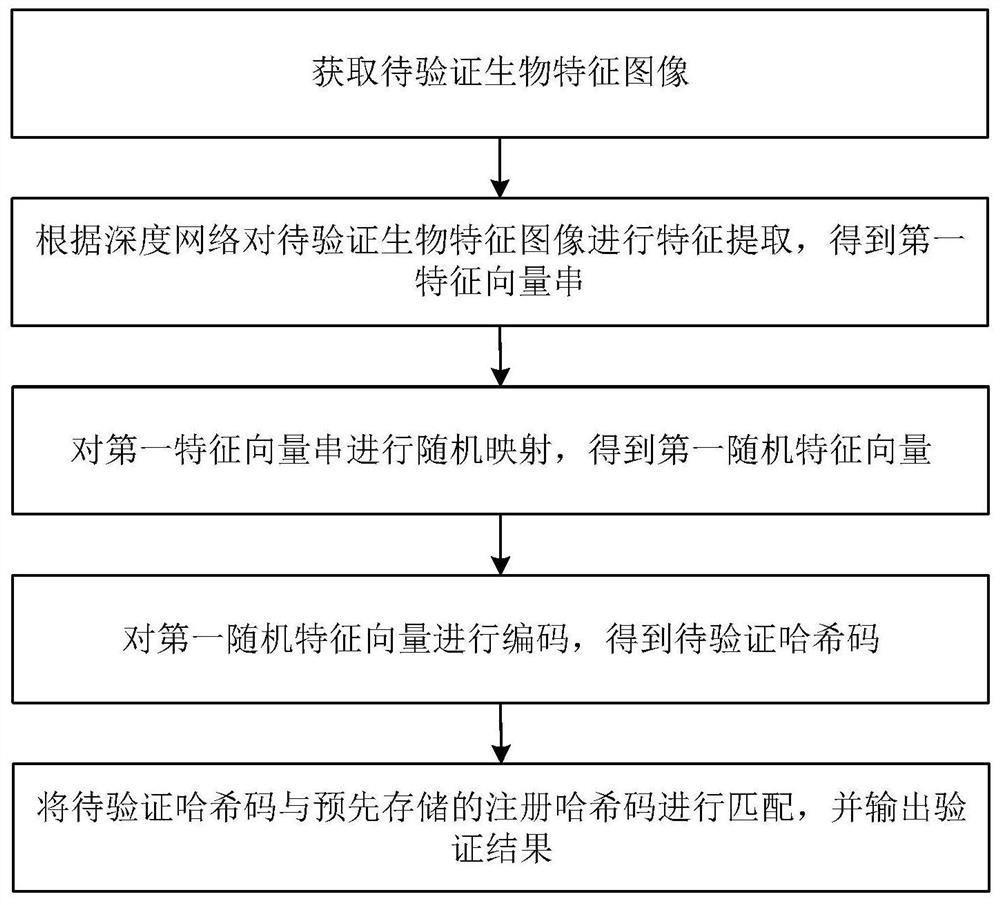
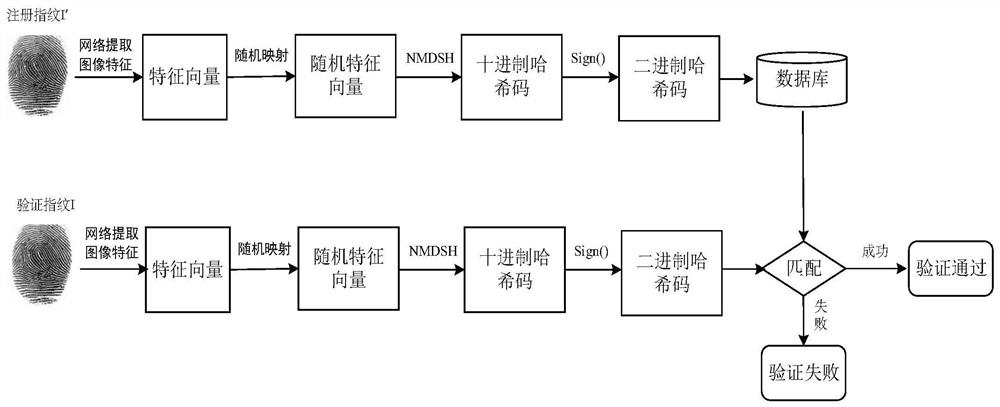
PendingCN112347855AStrong irreversibilityImprove efficiencyBiometric pattern recognitionFeature vectorFeature extraction
The invention discloses a biological feature template protection method and device based on deep learning. The method comprises the steps of obtaining a to-be-verified biological feature image; performing feature extraction on the to-be-verified biological feature image according to the deep network to obtain a first feature vector string; performing random mapping on the first feature vector string to obtain a first random feature vector; performing nonlinear multidimensional spectrum hash encoding on the first random feature vector to obtain a hash code to be verified; and matching the hashcode to be verified with a pre-stored registration hash code, and outputting a verification result. The biological feature template protection method based on deep learning provided by the invention has relatively high precision and safety.
Owner:西安电子科技大学青岛计算技术研究院 +1
QoS capable mobile ad-hoc network device
ActiveUS7417962B2Low costFair distribution of network bandwidthError preventionTransmission systemsQuality of serviceRandom mapping
The ad-hoc router enables a decentralized IP routing network (mobile of fixed) amongst a set of network devices, and can offer quality of services for voice, video and data applications. The ad-hoc router is divided into a receiving, control / management processing, IP datapath / routing, randomizer, scheduler and transmission blocks. The IP datapath / routing block provides, in addition to the standard datapath routing functionality, per packet labels that uniquely identify the source device of the packet in the network. The scheduler maintains a plurality of QoS queues, which are then dequeued with a WFQ scheduler, which can be based on standard technology or a simplified low-cost implementation. The randomizer uses the labels to route the packets to a queue such that all packets from the source device, indicated by the label, enter the same queue. For greater security, the randomizer uses a random mapping function that is re-computed periodically.
Owner:ALCATEL LUCENT SAS
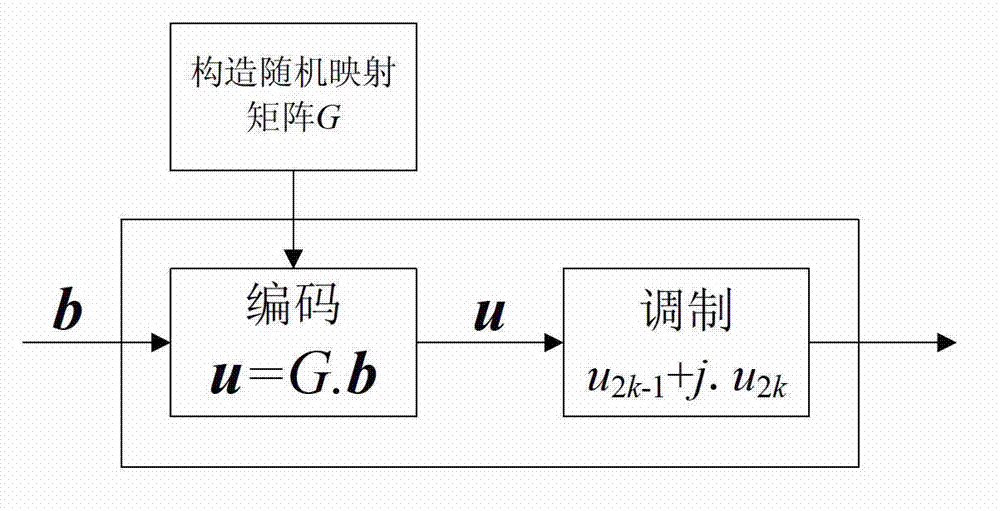
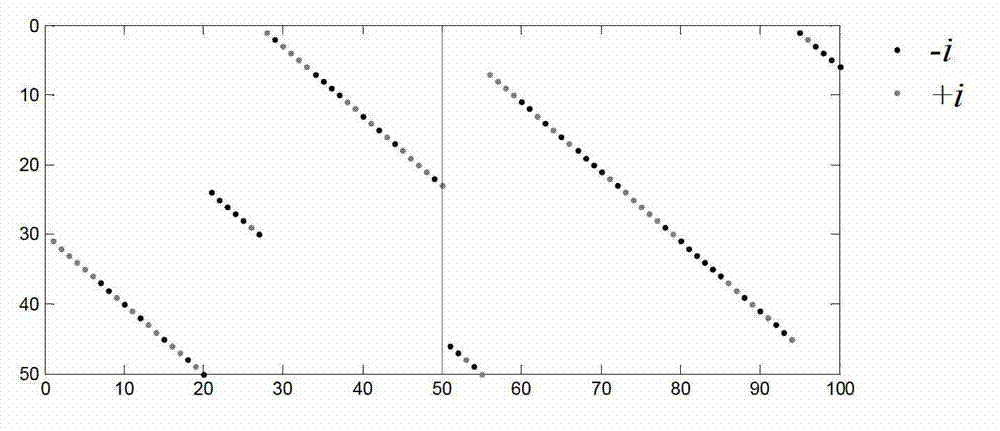
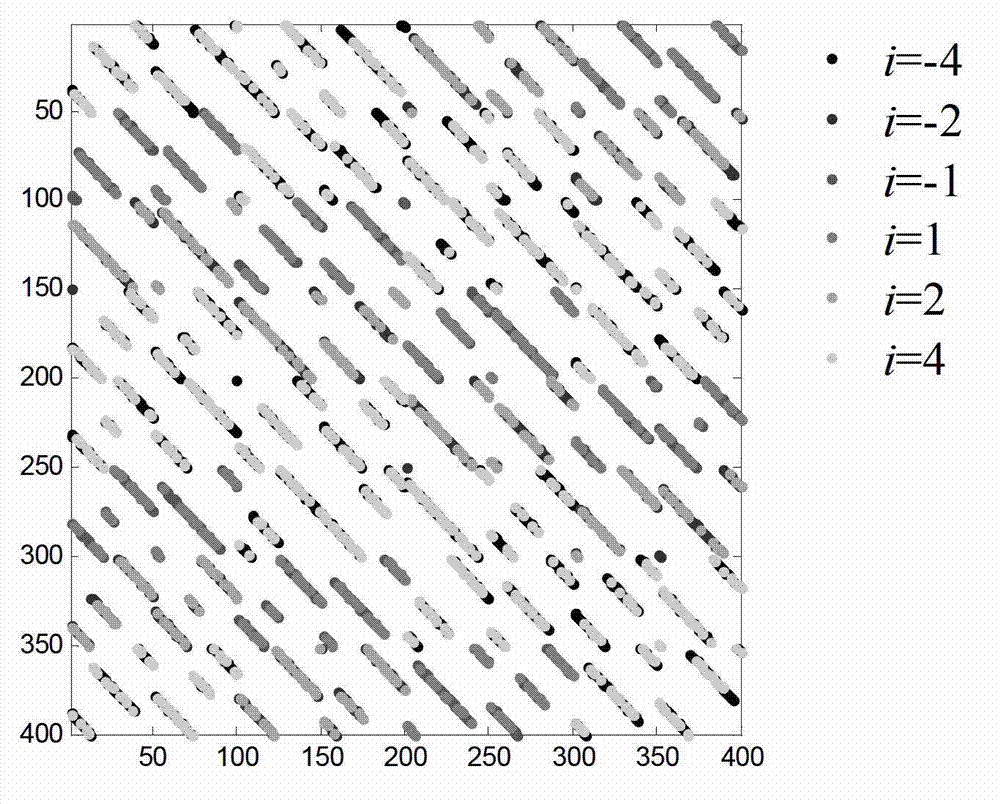
Random mapping code construction method
ActiveCN102891688AEasy to implementAvoid memory access conflictsError correction/detection using multiple parity bitsTheoretical computer scienceRandom mapping
The invention relates to a random mapping code construction method. The method comprises (1) constructing an N*N random mapping matrix G by multilayer random cycle method or multilayer random arrangement method; (2) coding a group of baseband signals b={bi, i=1, 2, ..., N} according to the random mapping matrix G obtained in step (1) to obtain u; and (3) modulating two adjacent coded character to one IQ character, and transmitting the signal. In comparison with the prior art, the random mapping code construction method provided by the invention is stable in performance and easy for hardware implementation, and can obviate memory access conflict.
Owner:TONGJI UNIV
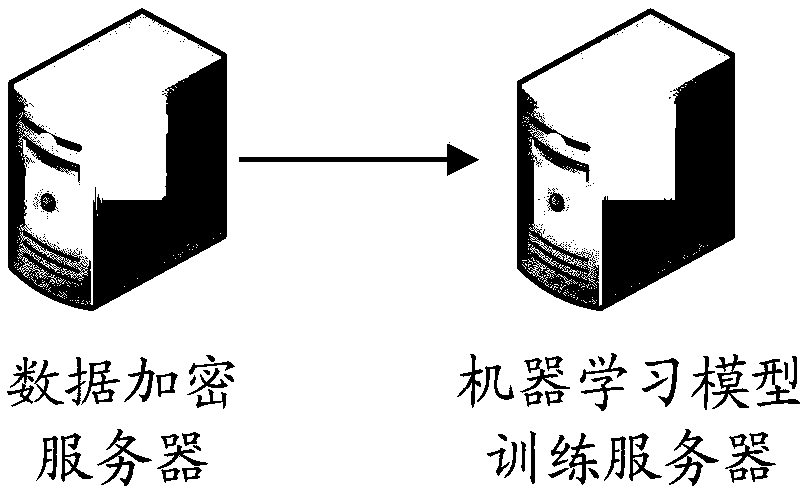
Data encryption, machine learning model training method, apparatus and electronic apparatus
InactiveCN109241749AReduce the risk of privacy breachesTraining does not affectDigital data protectionMachine learningPattern recognitionRandom mapping
Embodiments of the present specification disclose a data encryption, machine learning model training method, apparatus, electronic apparatus, and data encryption system. The data encryption method comprises the following steps: the encrypted data to be encrypted is randomly mapped by a random matrix to obtain the encrypted data corresponding to the data to be encrypted, and the encrypted data is used for training a machine learning model.
Owner:ADVANCED NEW TECH CO LTD
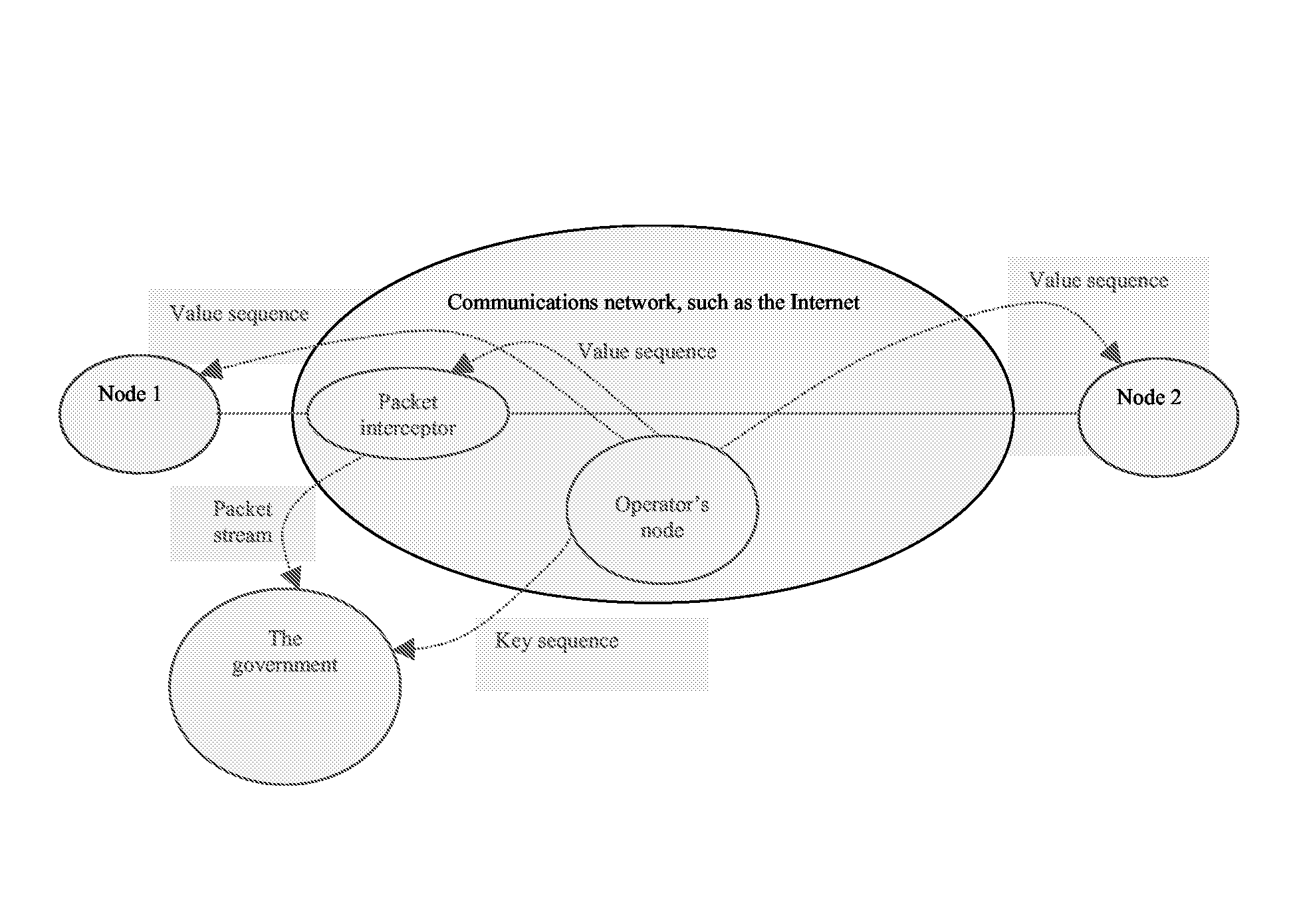
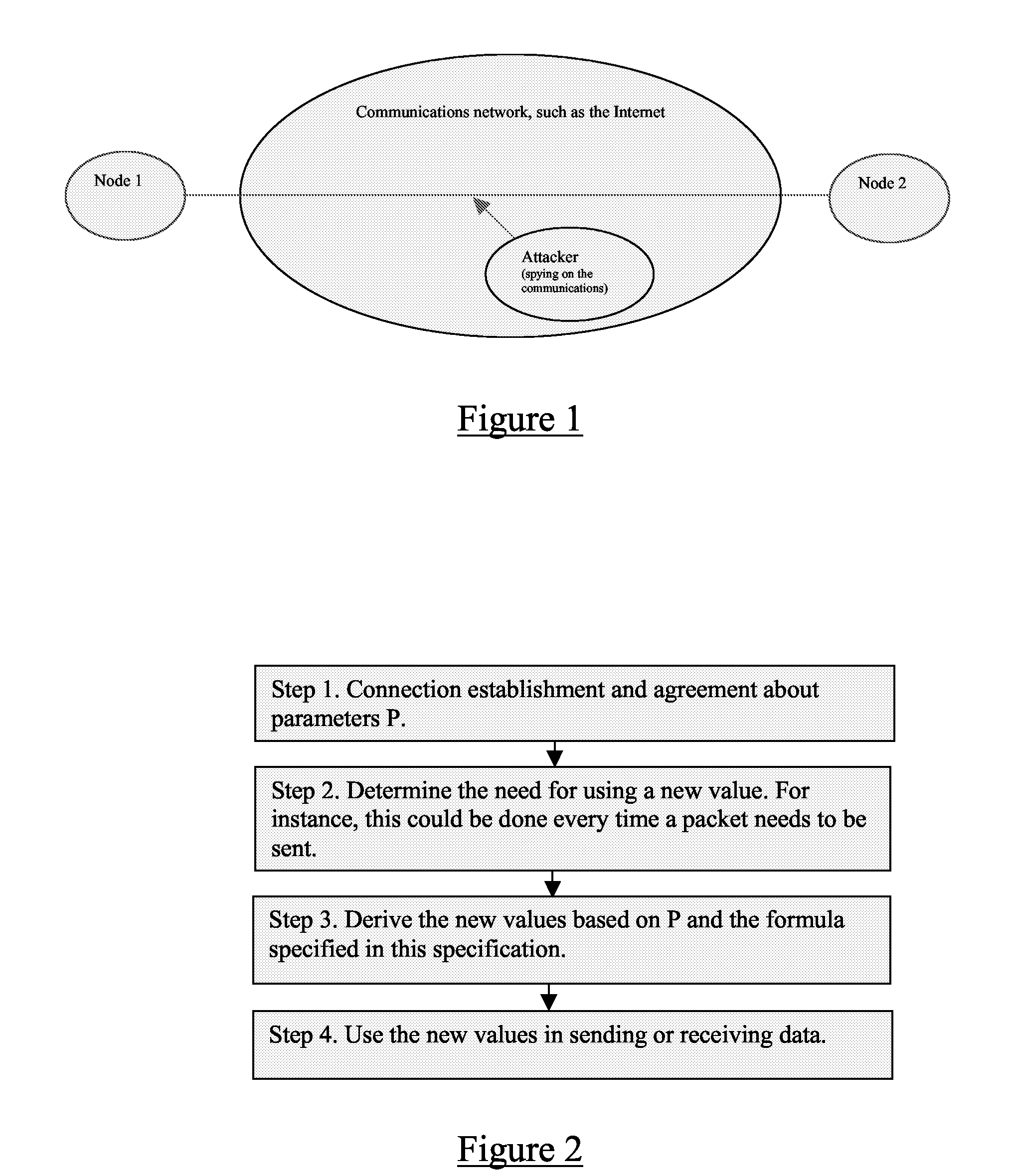
Method and apparatus for ensuring privacy in communications between parties
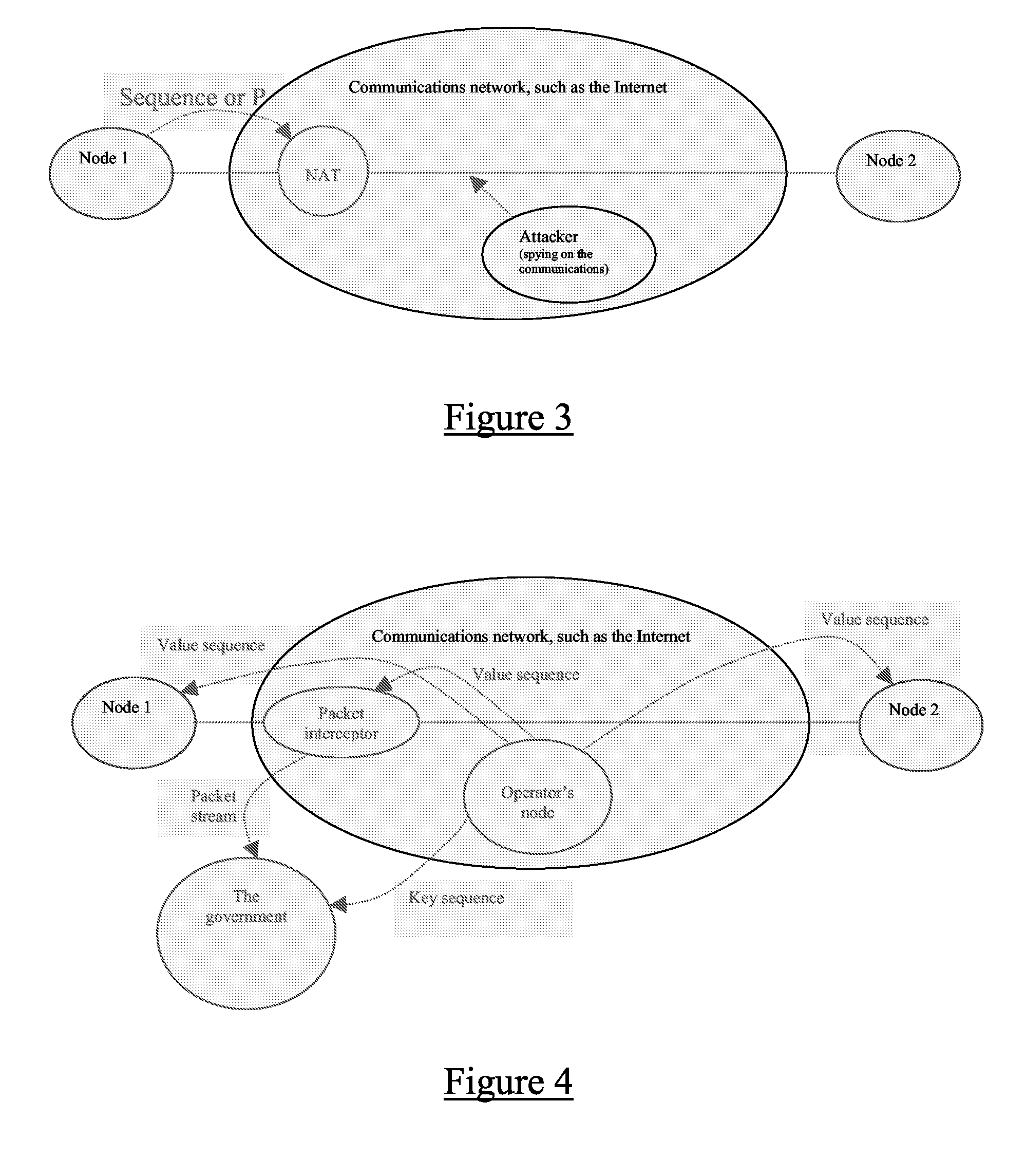
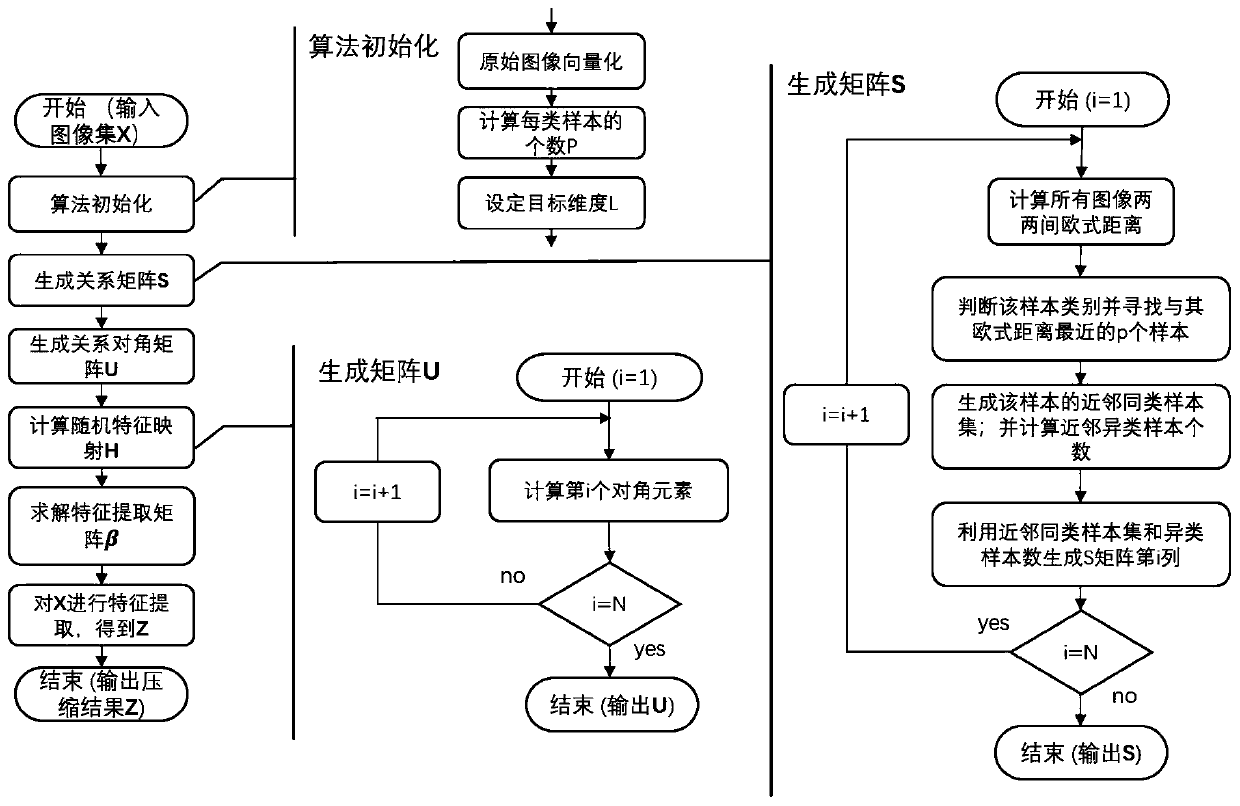
ActiveUS8837729B2Key distribution for secure communicationSecret communicationInternet privacyRandom mapping
A method of improving privacy by hiding, in an ordered sequence of messages M[x(1), D(1)], M[x(2), D(2)], etc, communicated between a first and at least one second party sharing a key k, metadata x(i) descriptive of message processing, wherein D(i) denotes payload data. The method comprises the first and the second party agreeing on a pseudo random mapping depending on a shared key k, Fk, mapping at least x(i) to y(i), and the first party modifying the messages by replacing x(i) by y(i) in each message M(x(i), D(i)). The first party then transmits the modified messages maintaining their original order, and on reception of a message M(y(m), D), the second party uses a mapping Gk to retrieve position m of received value and the original value x(m).
Owner:TELEFON AB LM ERICSSON (PUBL)
Image dimension reduction method of extreme learning machine based on graph embedding
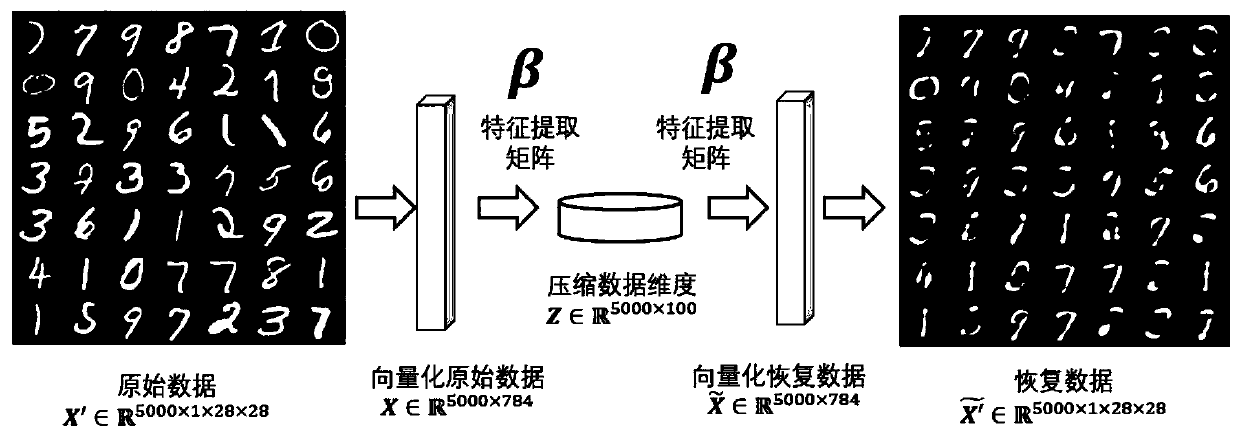
ActiveCN110473140AImprove compression performanceStrong Class DiscriminationGeometric image transformationCharacter and pattern recognitionData dredgingLearning machine
The invention provides an image dimension reduction method of an extreme learning machine based on graph embedding, and belongs to the field of machine learning and data mining. The method comprises the following steps: firstly, selecting an original image sample set, and constructing a sample relation matrix by utilizing inter-sample distances and label information of original image samples; secondly, according to the constructed sample relation matrix, firstly, carrying out random mapping on an input vectorized image sample, and then, learning a feature extraction matrix by minimizing a weighted sample reconstruction error; and finally, performing data dimension reduction on vectorized image data by using the learned feature extraction matrix. The method is short in training time and efficient in data compression, and the compression quality and dimension reduction stability of the data are effectively improved.
Owner:TSINGHUA UNIV
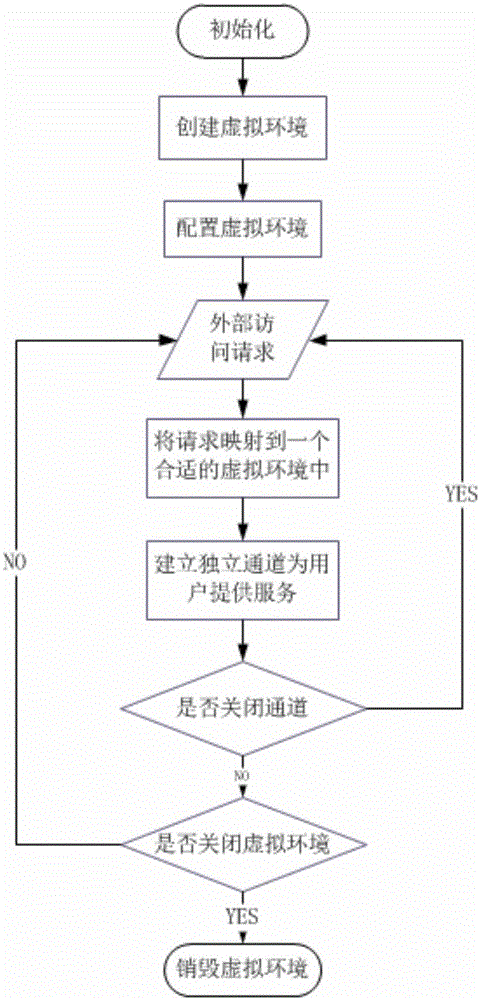
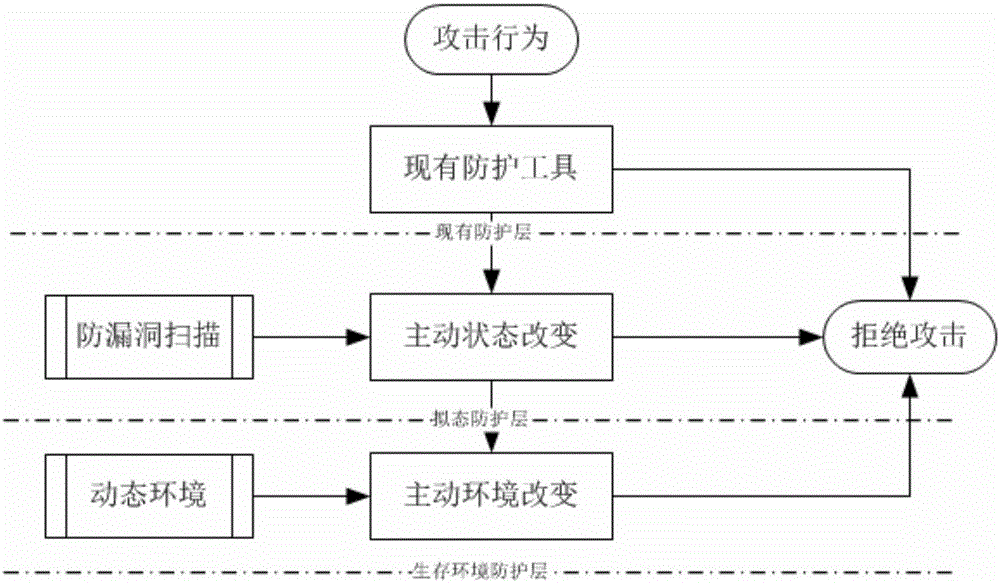
Method for actively defending against Trojan horse based on virtual environments
InactiveCN105847248AIncrease the difficultyChange the operating environmentPlatform integrity maintainanceTransmissionRandom mappingNetwork service
The invention discloses a method for actively defending against Trojan horses based on a virtual environment. For the first time, the invention deploys a protected network server in a virtual heterogeneous system in a dynamically changing heterogeneous configuration environment. When an access request is generated, it is randomly mapped to different virtual systems, so that the environment of each access is different. Encapsulating multiple virtual systems into one network server node increases the difficulty for attackers to exploit environmental vulnerabilities. At the same time, by changing the system and configuration structure, the Trojan horse loses its living environment, so as to achieve the purpose of active Trojan horse defense.
Owner:ZHEJIANG UNIV
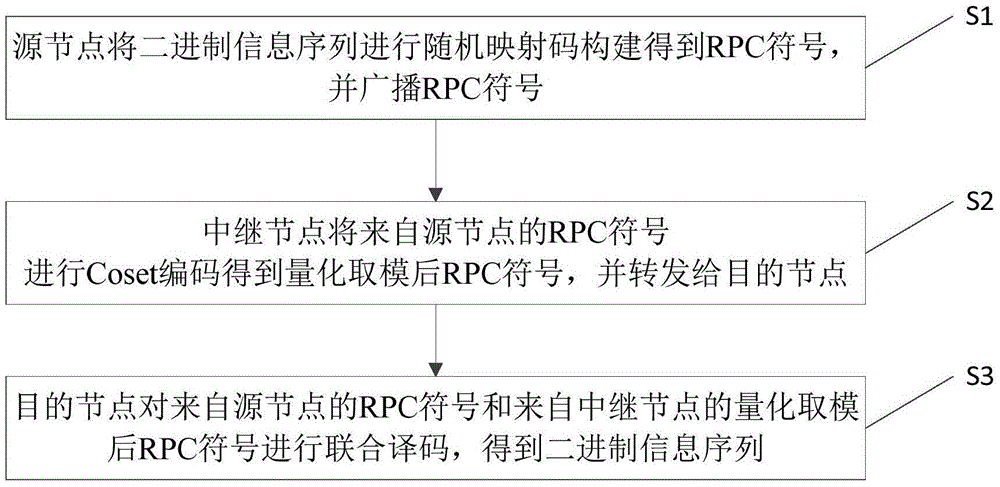
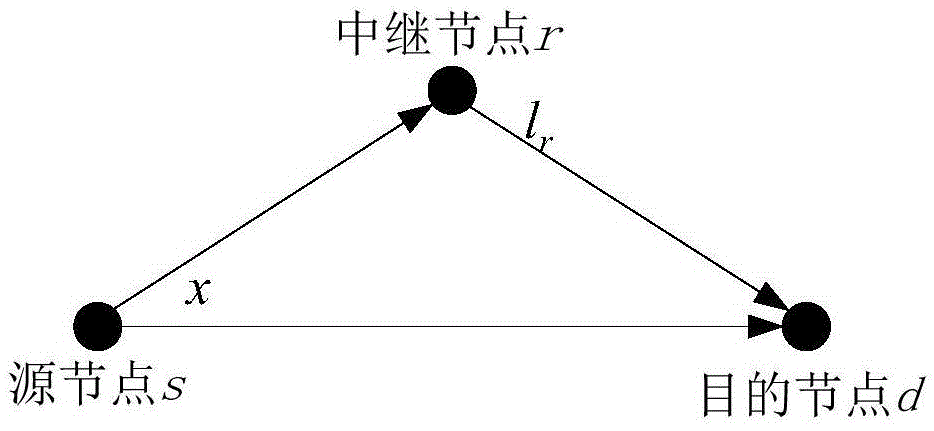
Random mapping code-based data transmission method in wireless relay system
ActiveCN105554813AAchieve adaptiveReduce peak signal-to-noise ratioNetwork traffic/resource managementRadio transmissionBinary informationRandom mapping
The invention relates to a random mapping code-based data transmission method in a wireless relay system. The method includes the following steps that: S1, a weight vector w is given, a source node obtains RPC symbols through adopting a random mapping mode establishing method and based on w and a binary information sequence, and broadcasts an RPC symbol x; S2, a relay node receives an RPC symbol ysr which is broadcasted by the source node through a channel and performs Coset encoding on the RPC symbol ysr so as to obtain an RPC symbol lr which has been subjected to quantized modulo operation, and forwards the RPC symbol lr to a destination node; S3, the destination node receives an RPC symbol ysd which is broadcasted by the source node through a channel and an RPC yrd which is broadcasted by the relay node through a channel, and performs joint decoding on the RPC symbol ysd and the RPC yrd to obtain the binary information sequence. Compared with the prior art, and according to the method of the invention, the peak signal to noise ratio of signals can be decreased through quantized compression at the relay node, a random mapping code-based receiving end link adaptive relaying strategy can be realized, and the throughput of a system can be obtained.
Owner:TONGJI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com