Patents
Literature
182results about How to "Improve privacy and security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Binding, unbinding and binding updating method for third-party application account and mobile phone number
ActiveCN103746792AImprove privacy and securityEasy to moveSpecial data processing applicationsSecuring communicationMobile Telephone NumberThird party
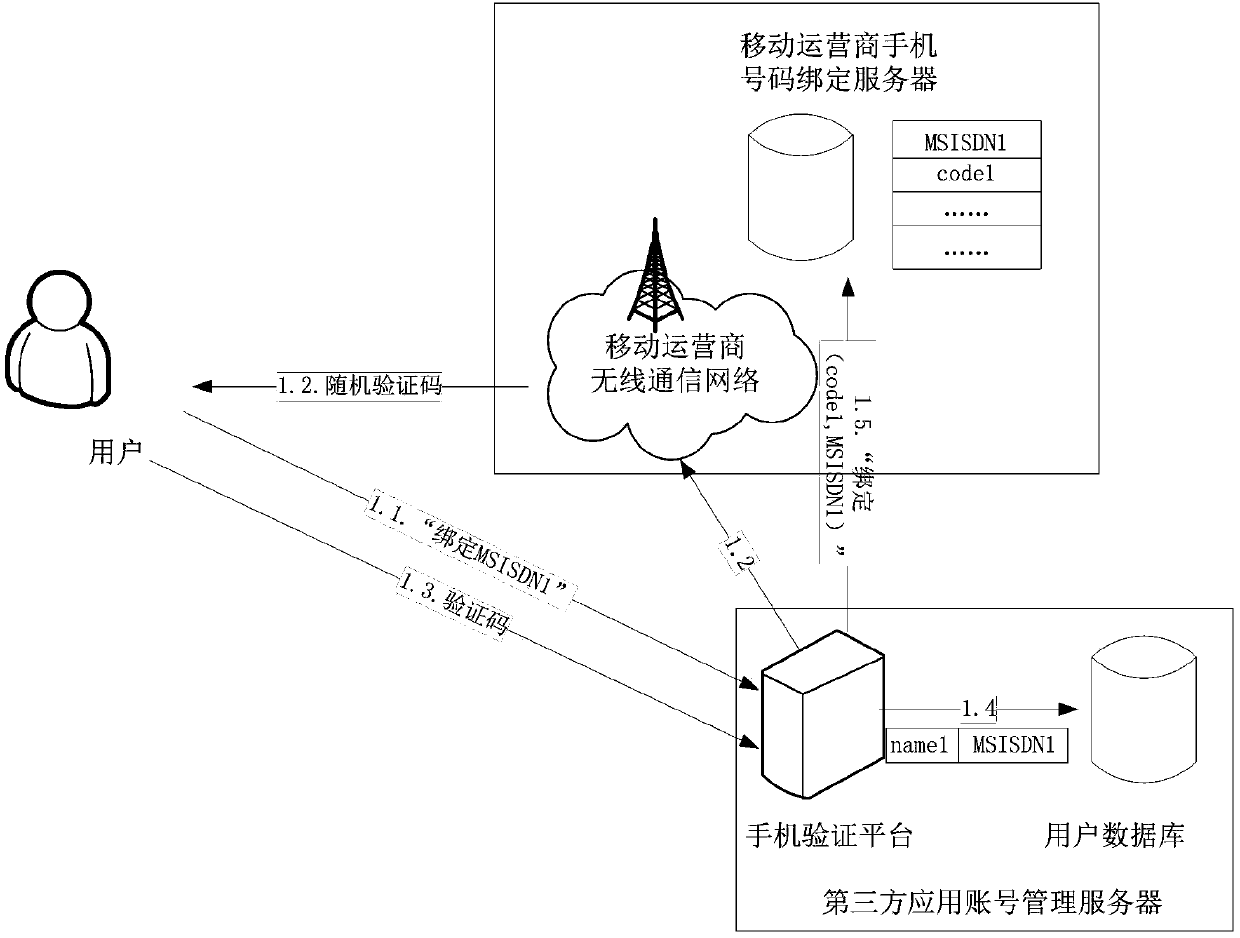
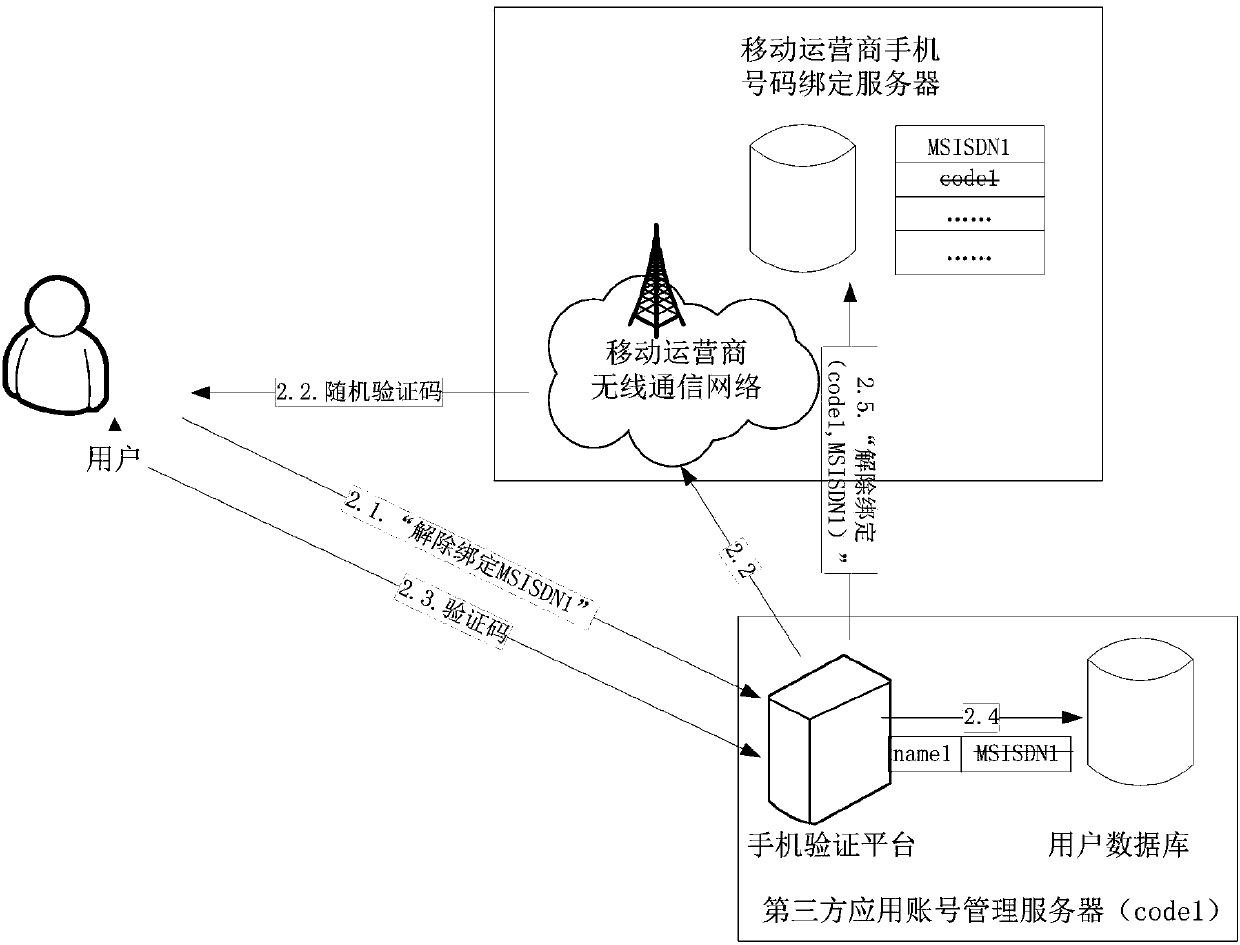
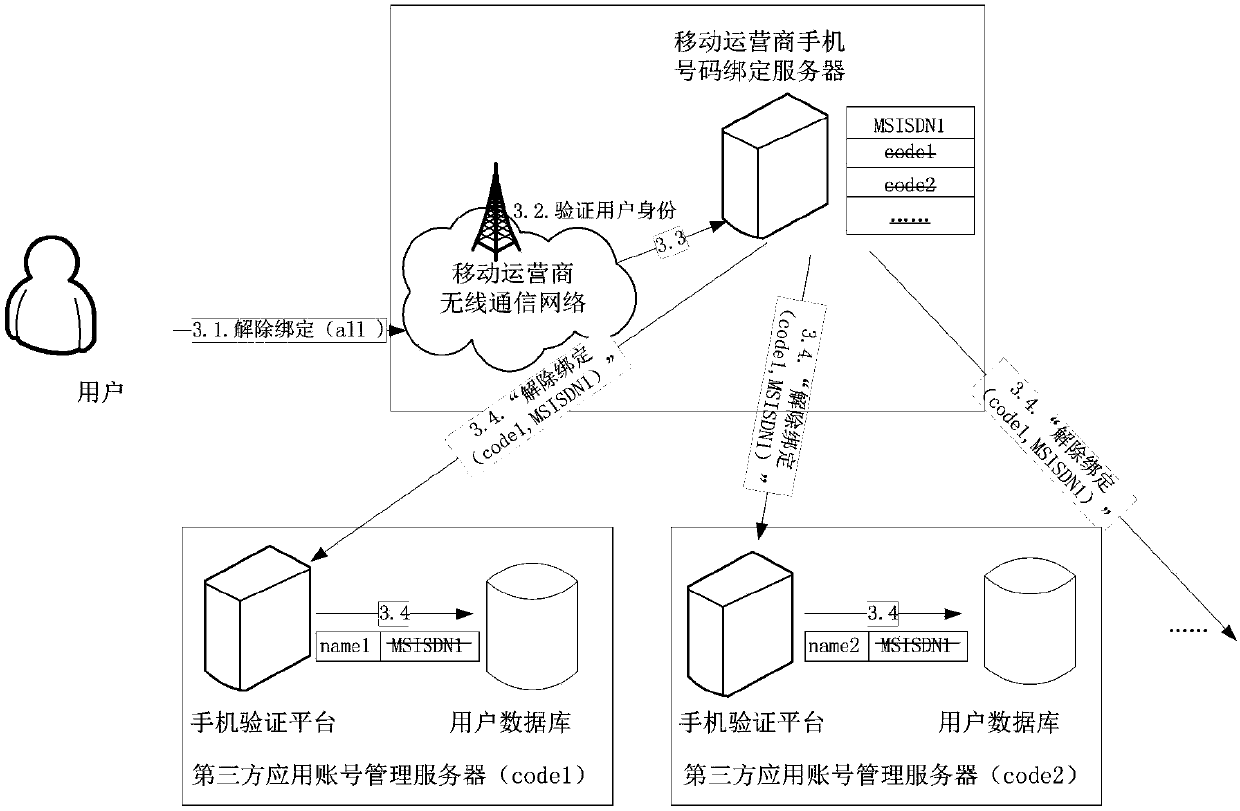
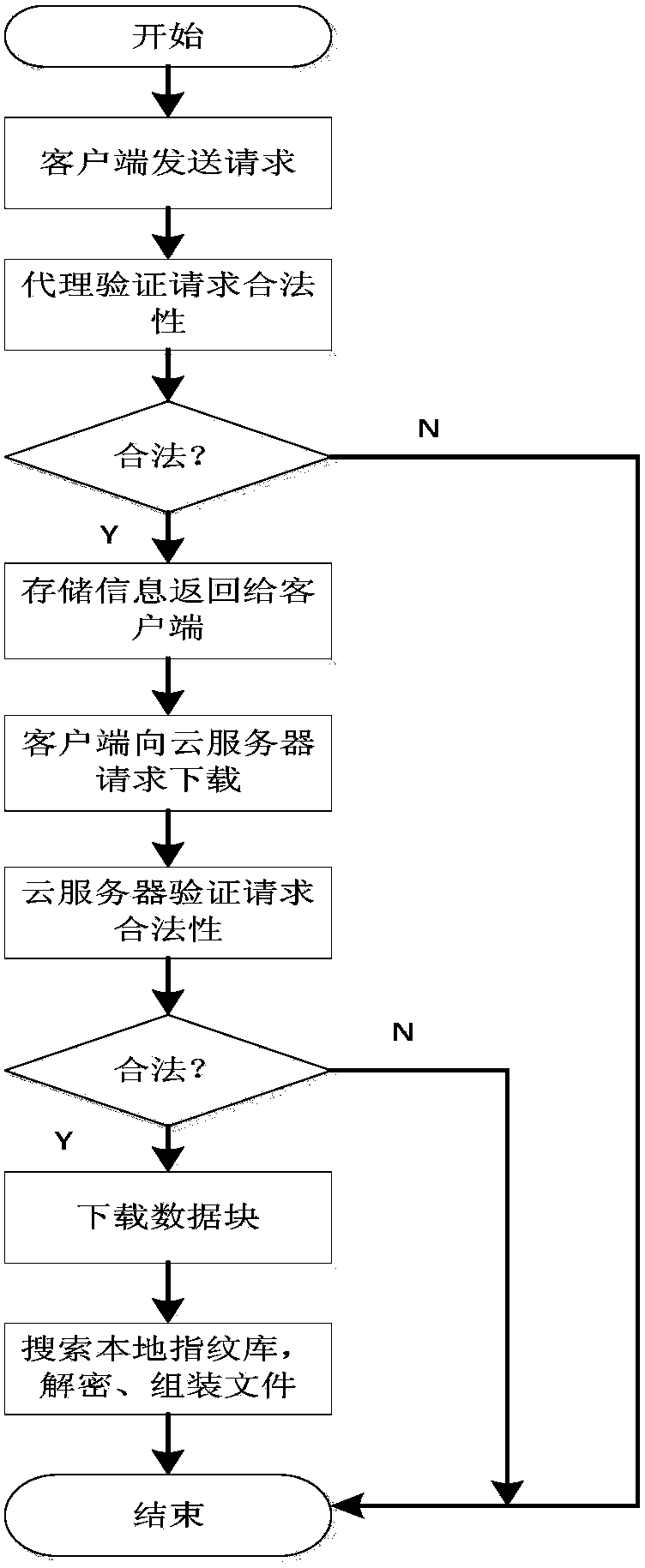
The invention discloses a binding method, an unbinding method and a binding updating method for a third-party application account and a mobile phone number. The binding method comprises the following steps that (1) a user transmits a mobile phone number to be bound to a mobile phone verification platform of a third-party application account management server; (2) the mobile phone verification platform of the third-party application account management server generates a random verification code, and transmits the random verification code to the user of the mobile phone number to be bound through a mobile operator network; (3) the user receives a verification short message, and transmits the verification code back to the mobile phone verification platform of the third-party application account management server; (4) a user database of the third-party application account management server records an association relationship between an account of the user and the mobile phone number; (5) the mobile phone verification platform of the third-party application account management server transmits a service name code and the mobile phone number to a mobile phone binding server of the mobile operator through a binding message, and associates the mobile phone number of the user and the bound third-party application service name code.
Owner:郑盈盈
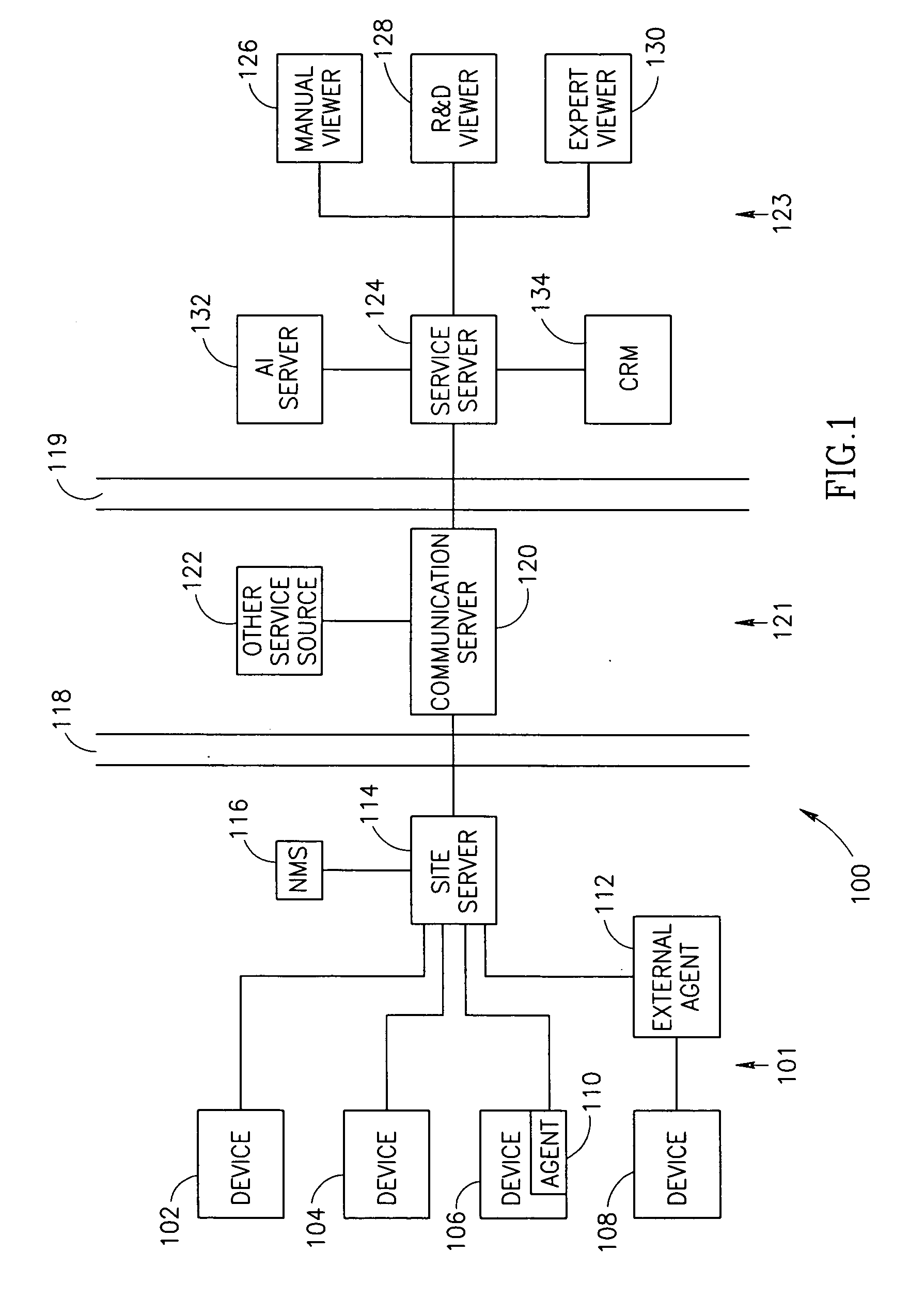
Support network
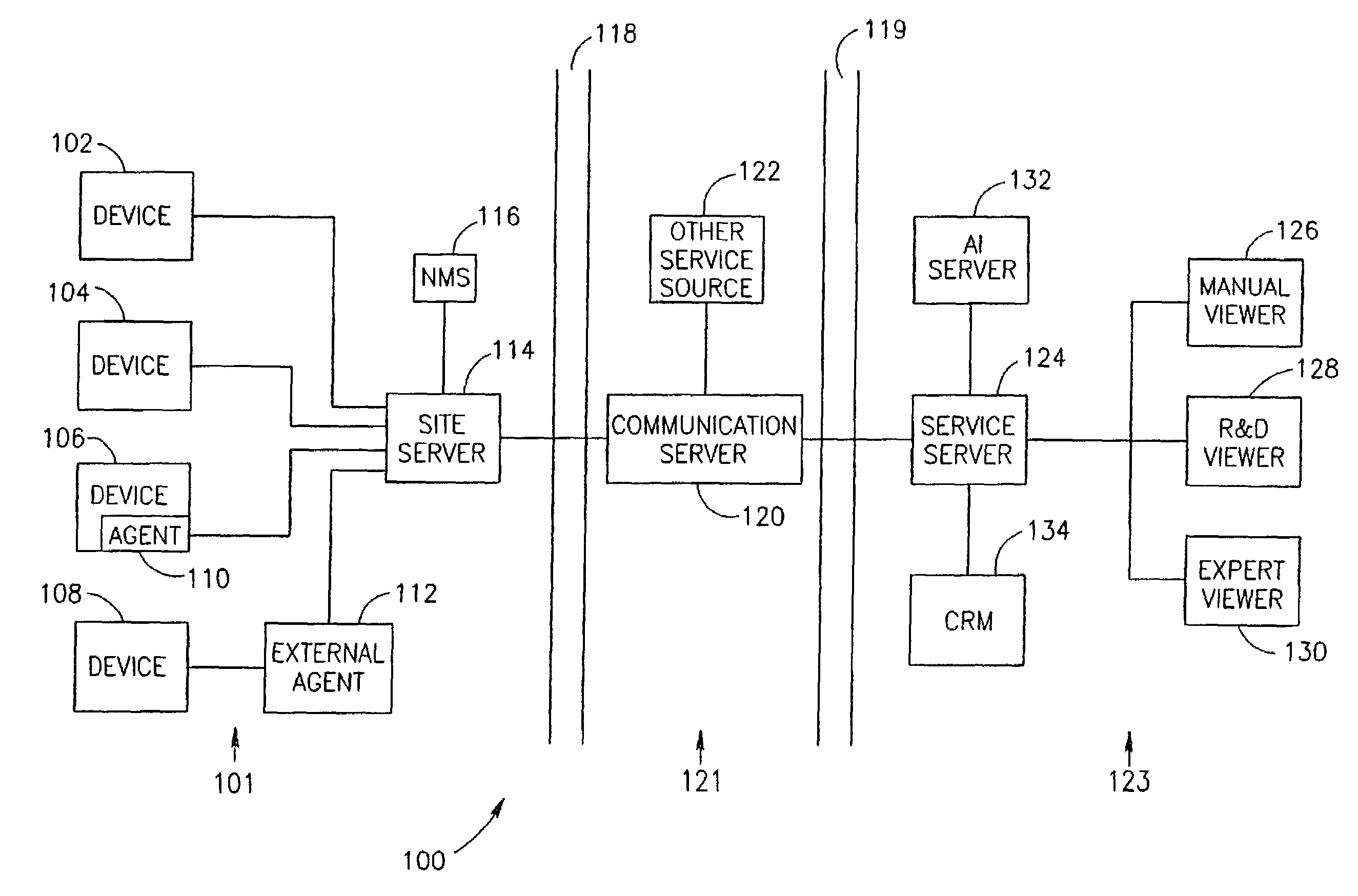
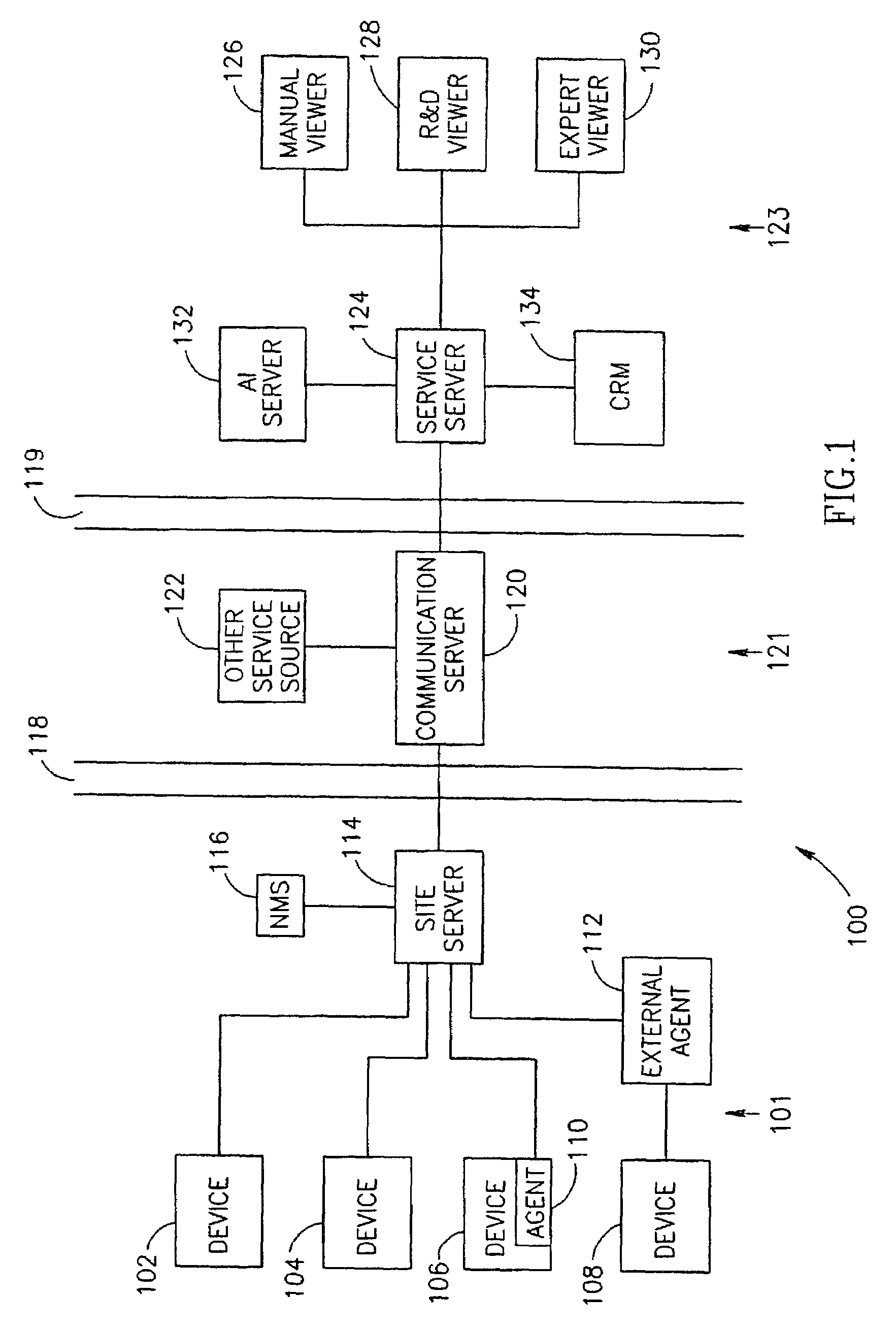
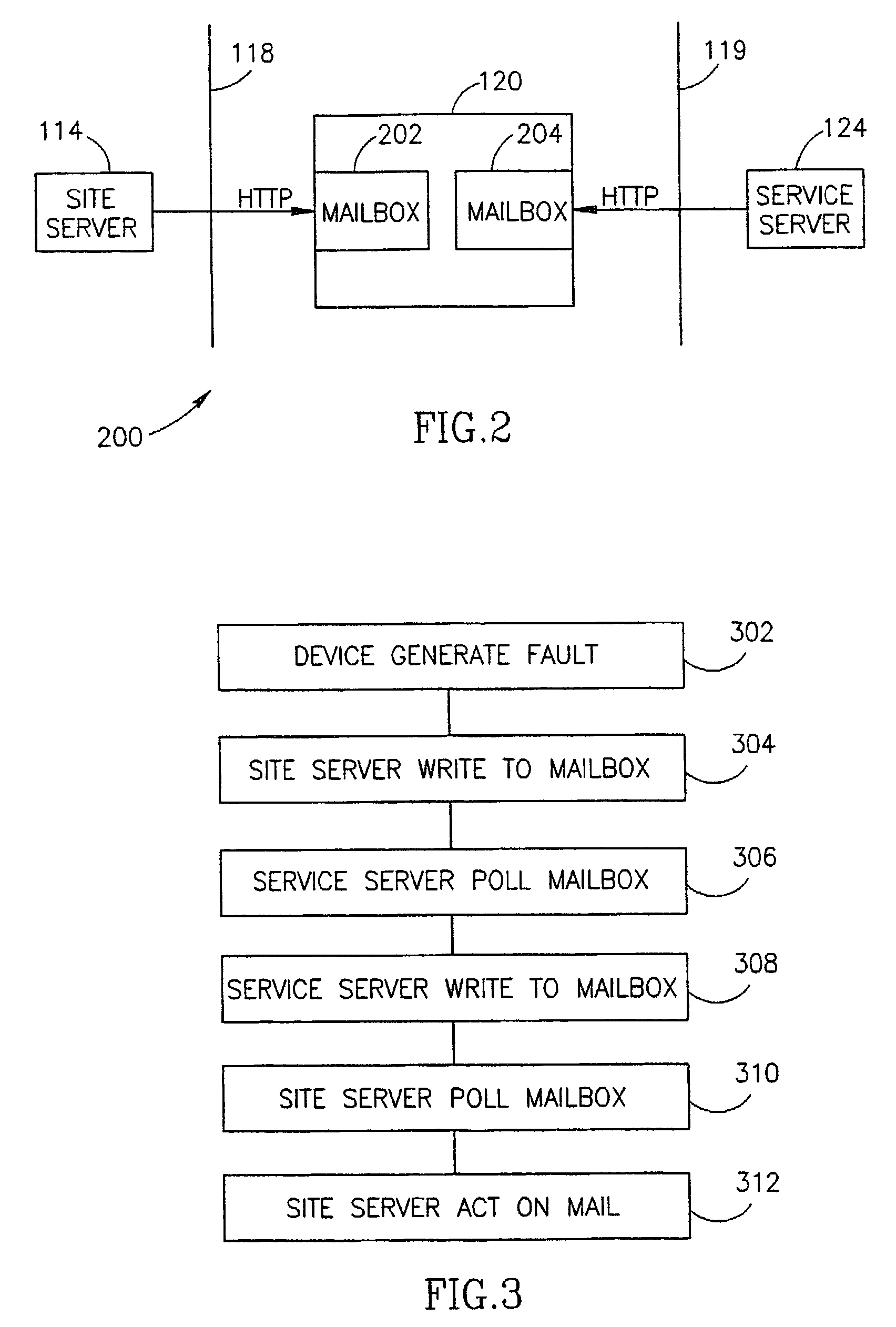
InactiveUS20060161394A1Reduce the amount requiredReduce the numberDetecting faulty hardware by remote testDigital computer detailsComputer scienceReal-time computing
Owner:NEXTNINE
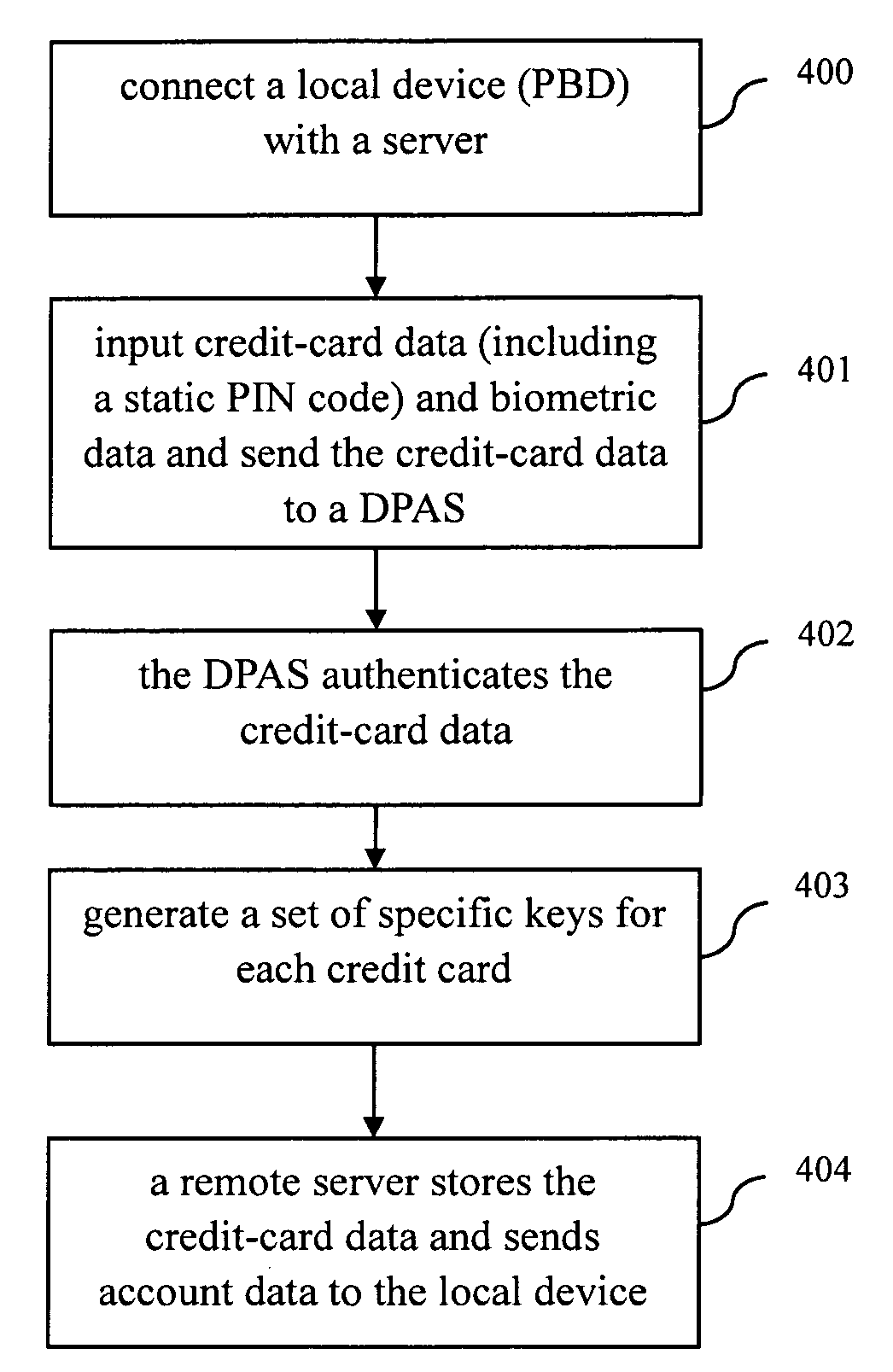
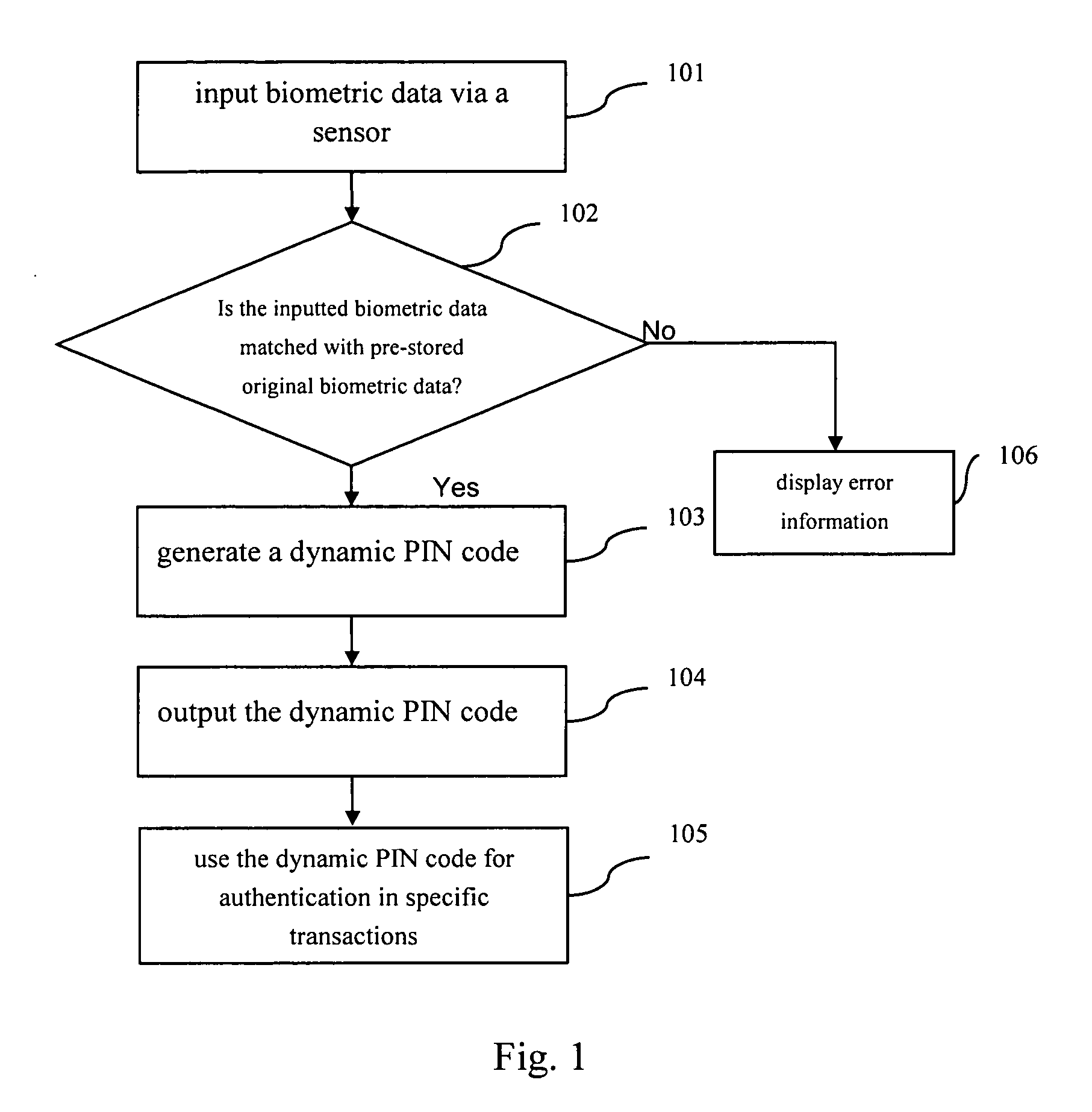
Method, device, server and system for identity authentication using biometrics
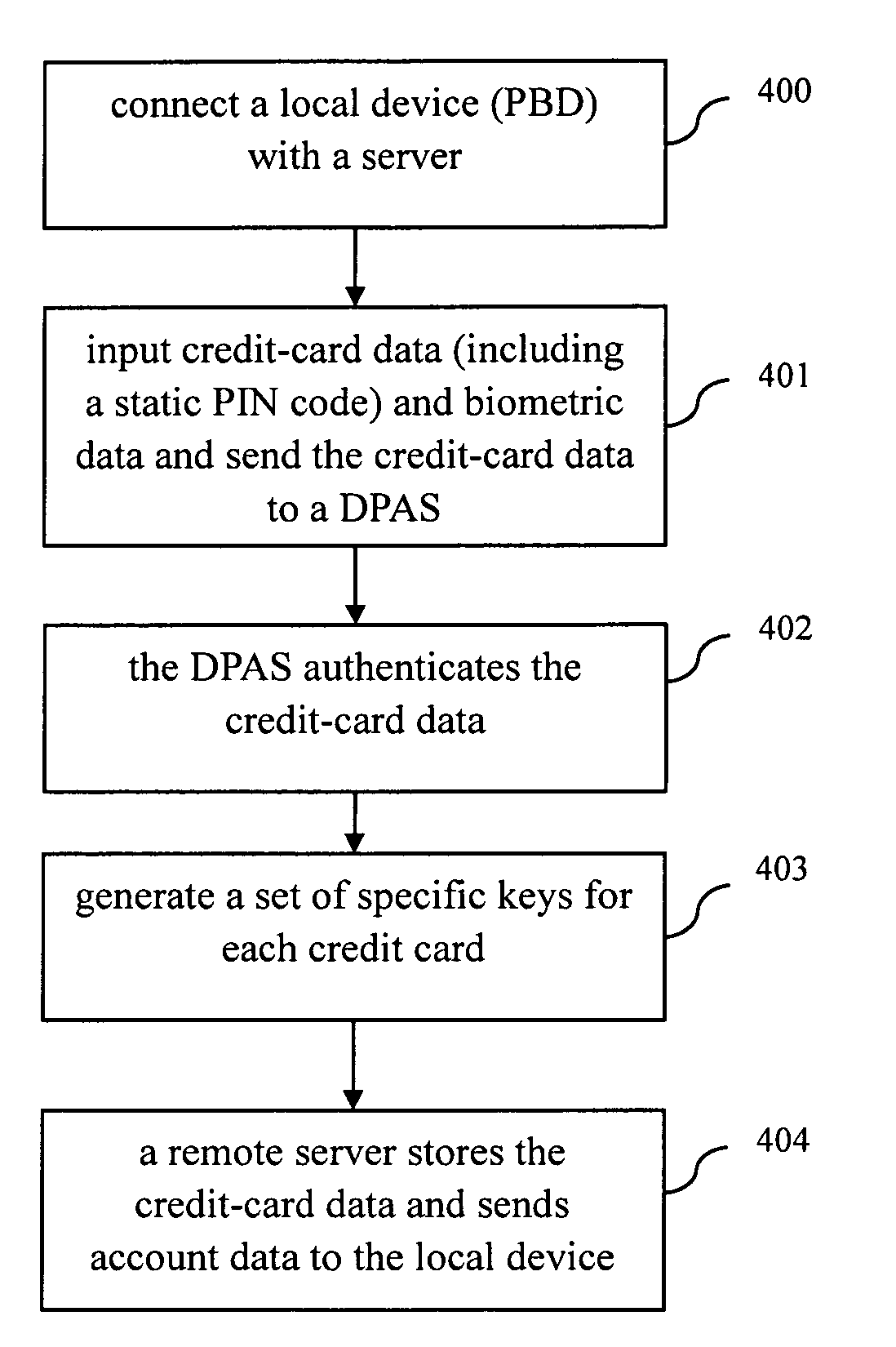
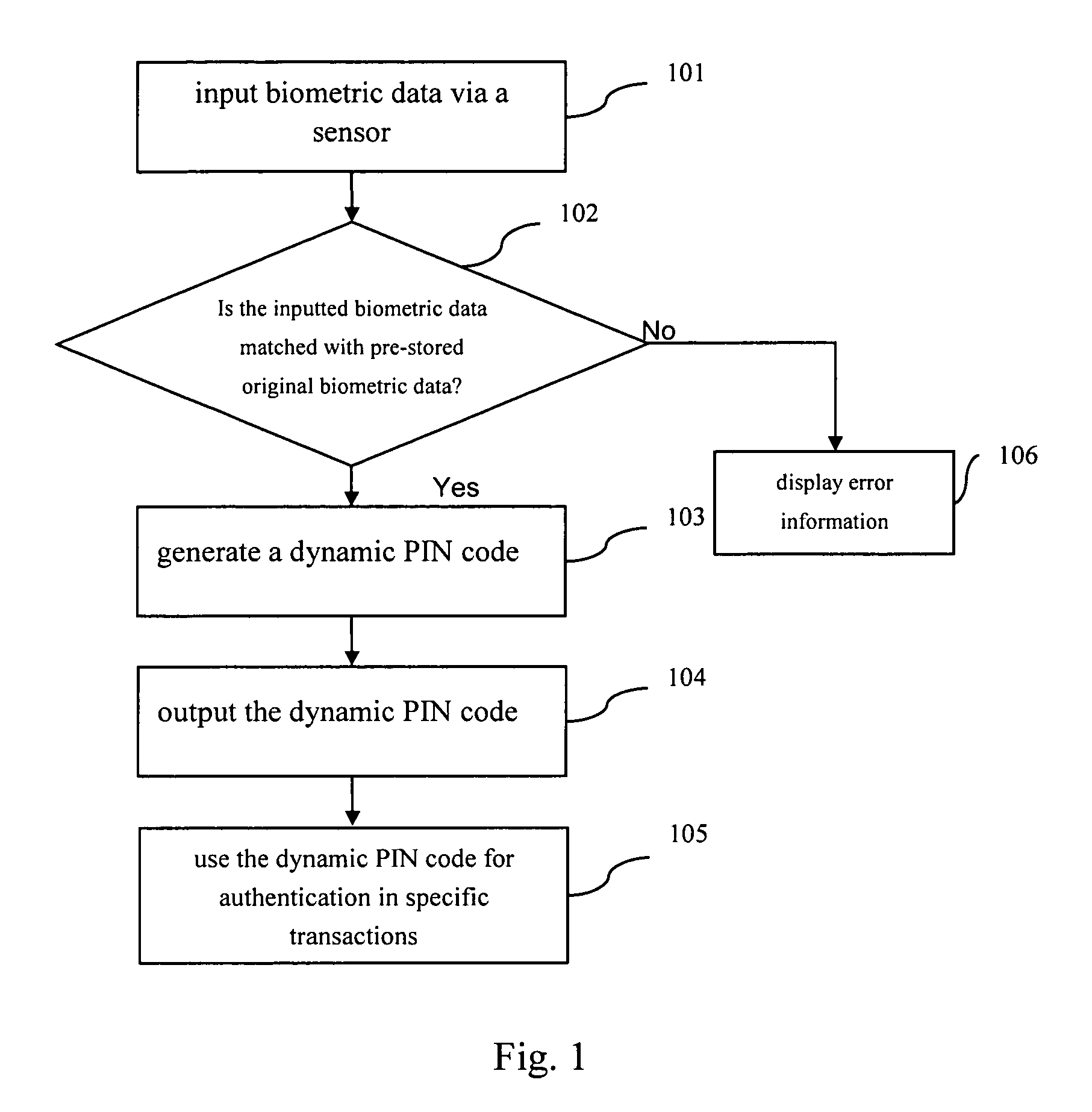
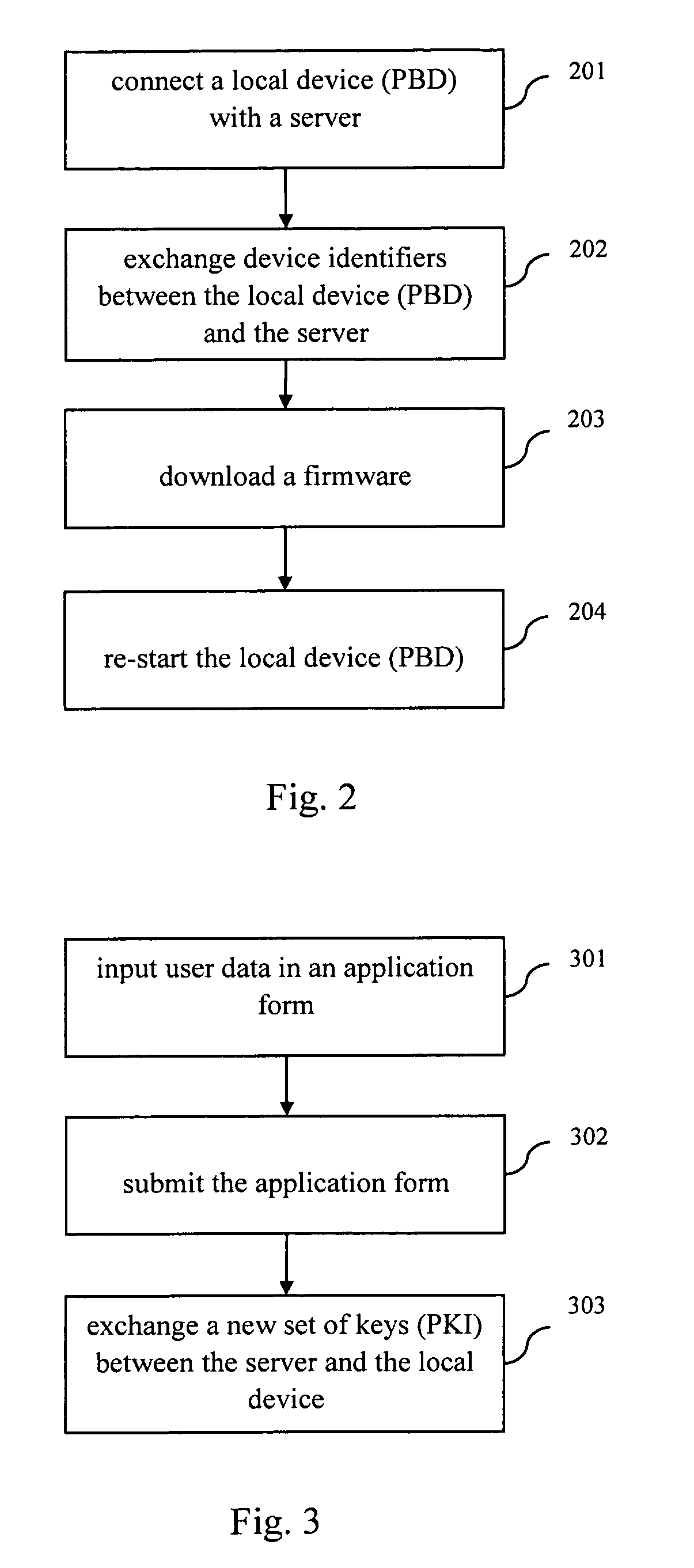
InactiveUS20100049659A1Improve privacyImprove securityElectric signal transmission systemsDigital data processing detailsBiometric dataAuthentication server
A method, a device, a server and a system for authenticating the identity with the biological character in an authenticating system, the authenticating system at least includes a local device and an authenticating server, wherein the method comprises the following steps: inputting step, inputting the biological character data in the local device by a biological character sensor; matching step, matching the input biological character data with the original biological character data pre-stored in the memory of the local device; first identification code producing step, producing the first identification code in the local device if the input biological character data is matched with the original biological character data pre-stored in the memory; and authenticating step, sending the first identification code to the authenticating server, authenticating the first identification code by the authenticating server in order to authorize the system to perform the authorized operation.
Owner:VALLEY TECH
Support Network
InactiveUS20070100585A1Less interferenceFew connectionsDetecting faulty hardware by remote testNuclear monitoringReal-time computing
Owner:NEXTNINE
Support network
InactiveUS7076400B2Reduce the amount requiredReduce the numberAmplifier modifications to reduce noise influenceDigital data processing detailsReliability engineering
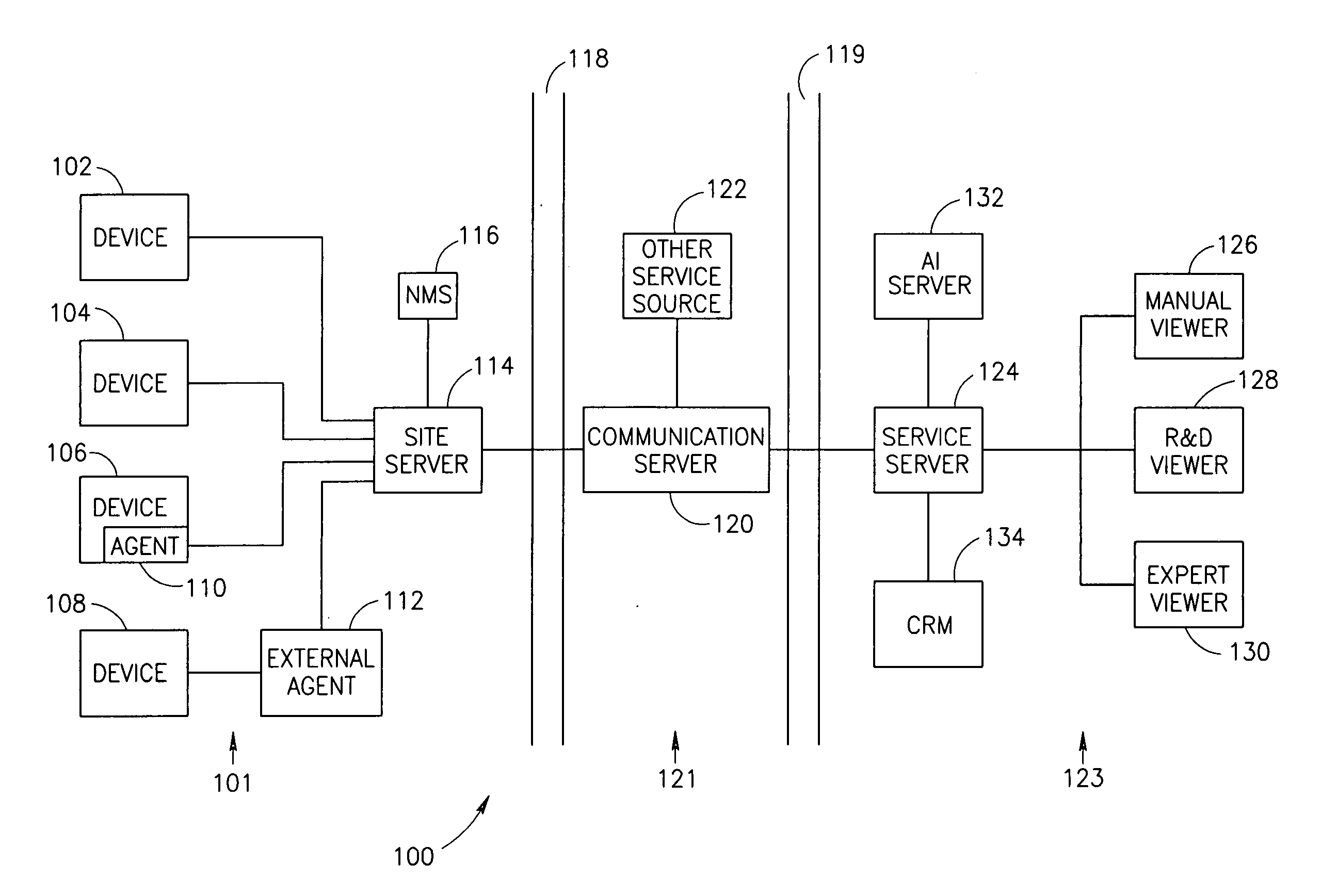
A method of device maintenance including determining that maintenance should be performed on a target device, automatically selecting a maintenance process including at least one maintenance task to effect said maintenance, automatically managing said maintenance process on a maintenance server separate from said target device, said maintenance server adapted to manage maintenance processes for a plurality of devices, said managing including at least monitoring the execution of said process and automatically performing at least one said maintenance-related task to effect at least a portion of said maintenance of said target device.
Owner:NEXTNINE
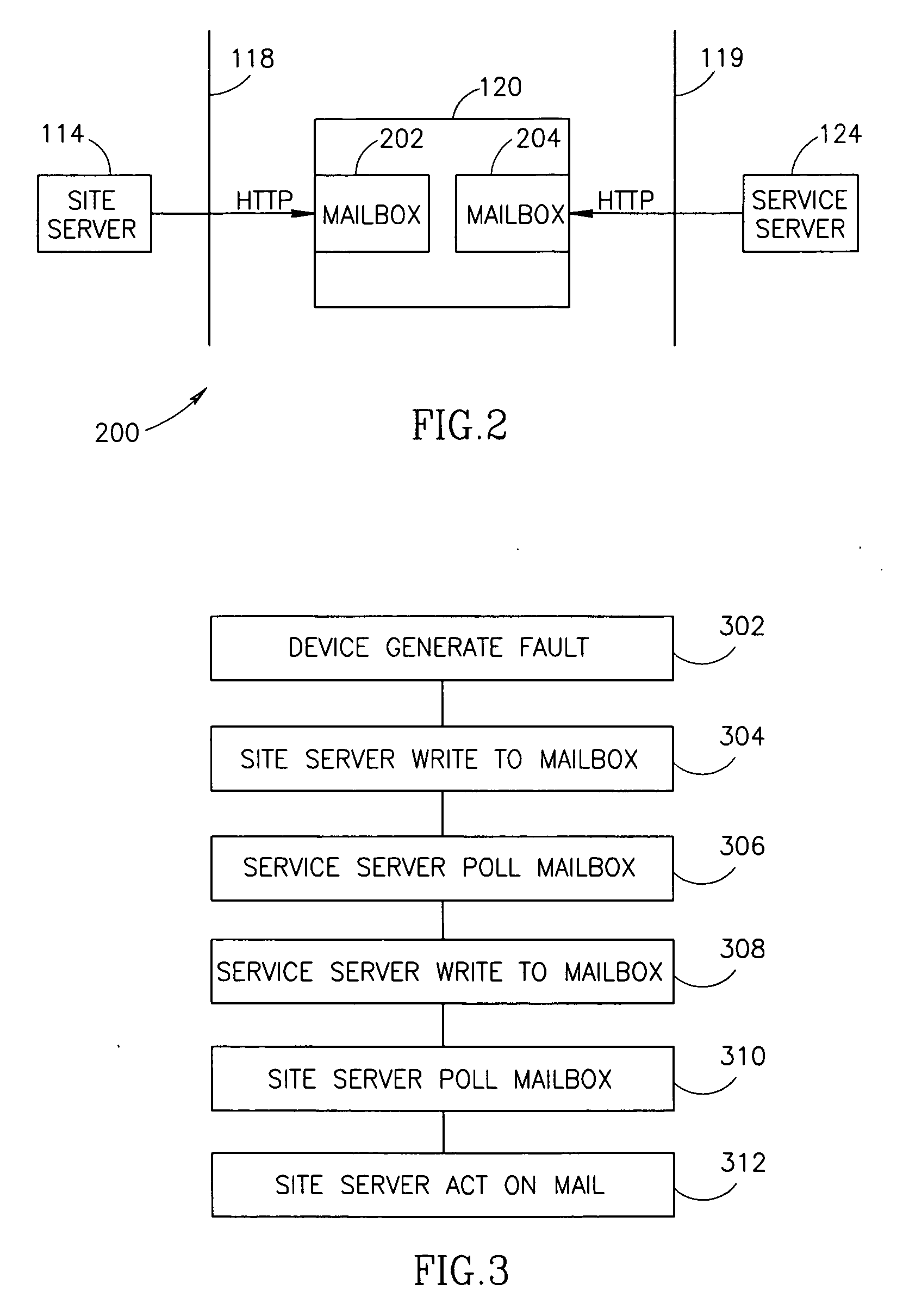
System and Method for Making a Data Silo to Distribute Electronic Data
InactiveUS20070208823A1Avoid restrictionsEasy to useMultiple digital computer combinationsSpecial data processing applicationsNetwork addressReverse proxy
We have a method of making a Web Service and a website, which we call a Silo, that lets a sender upload a file (or directory) of arbitrary size, that she wants distributed electronically to one or more recipients. The uploading can be done via a standard web browser. The Silo associates a token with that file and gives that to the sender. The token is some random bit sequence. The sender can then send that token and the Silo's URL, to her recipients. Who can then use a browser to go to that Silo, present the token, and get the file. A simple usage for sender and recipient. It lets the sender compartmentalize access to various files, and avoids the limitations of using email or ftp to transfer the files. E-commerce can be enabled by having the Silo act as a recognized financial intermediary, and by the sender selling items. With a recipient paying the Silo, who acts as an escrow. The seller can also conduct public or private auctions, using the Silo to host them. We make a Reverse Anonymizer (RA), which is a computer on the Internet that lets two parties connect and interact electronically, where the initiating party does not know the network address of the other party. Optionally, the latter might not also know the address of the former. One or both of the two parties might be a computer program, or a human. The RA mediates messages between the parties. We describe how the RA differs significantly from a reverse proxy server or an Instant Messaging server. The RA can be used to enhance the privacy and security of Internet communications and data transfer.
Owner:SHANNON MARVIN +1
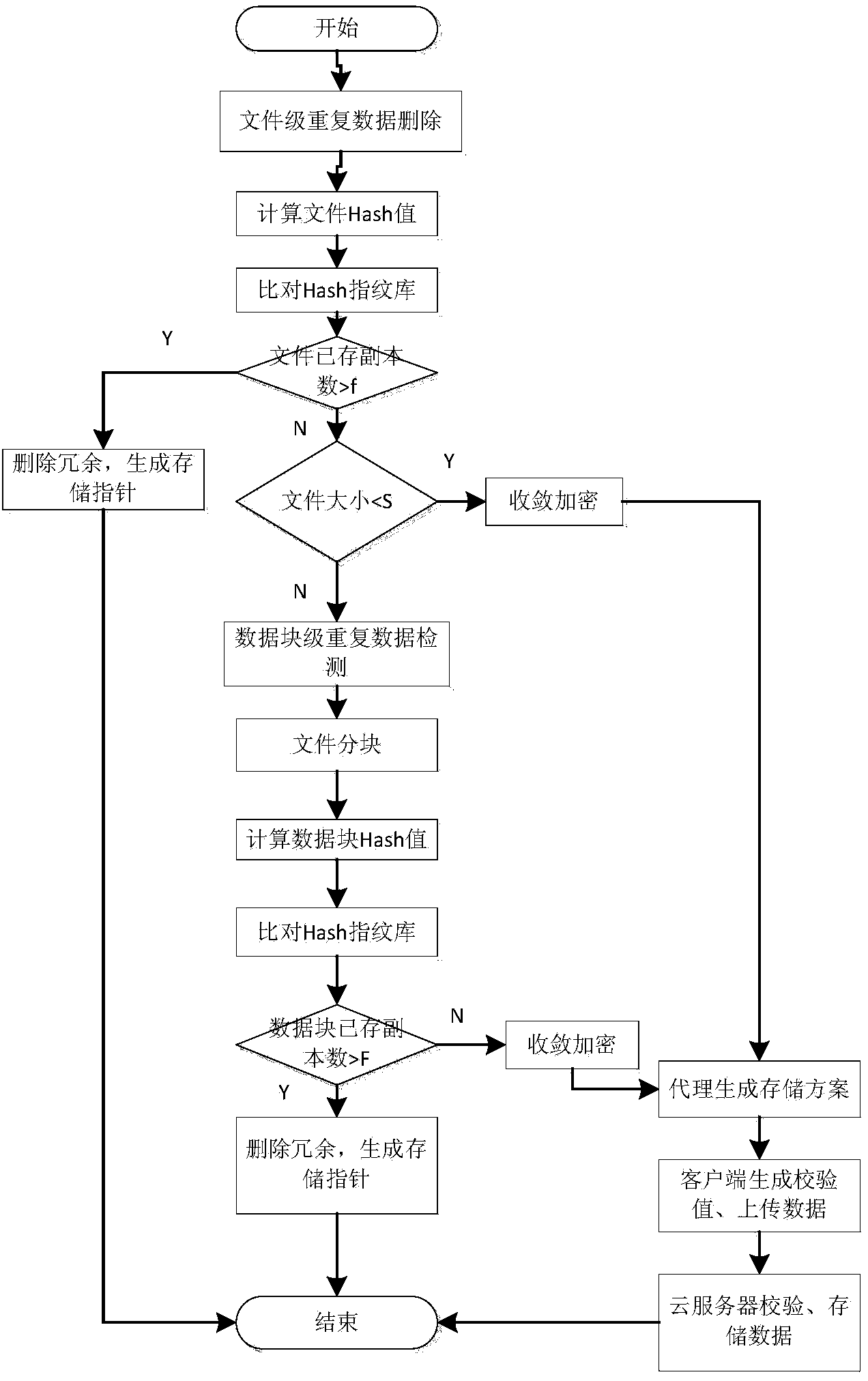
Repeating data deleting system and method applicable to cloud storage
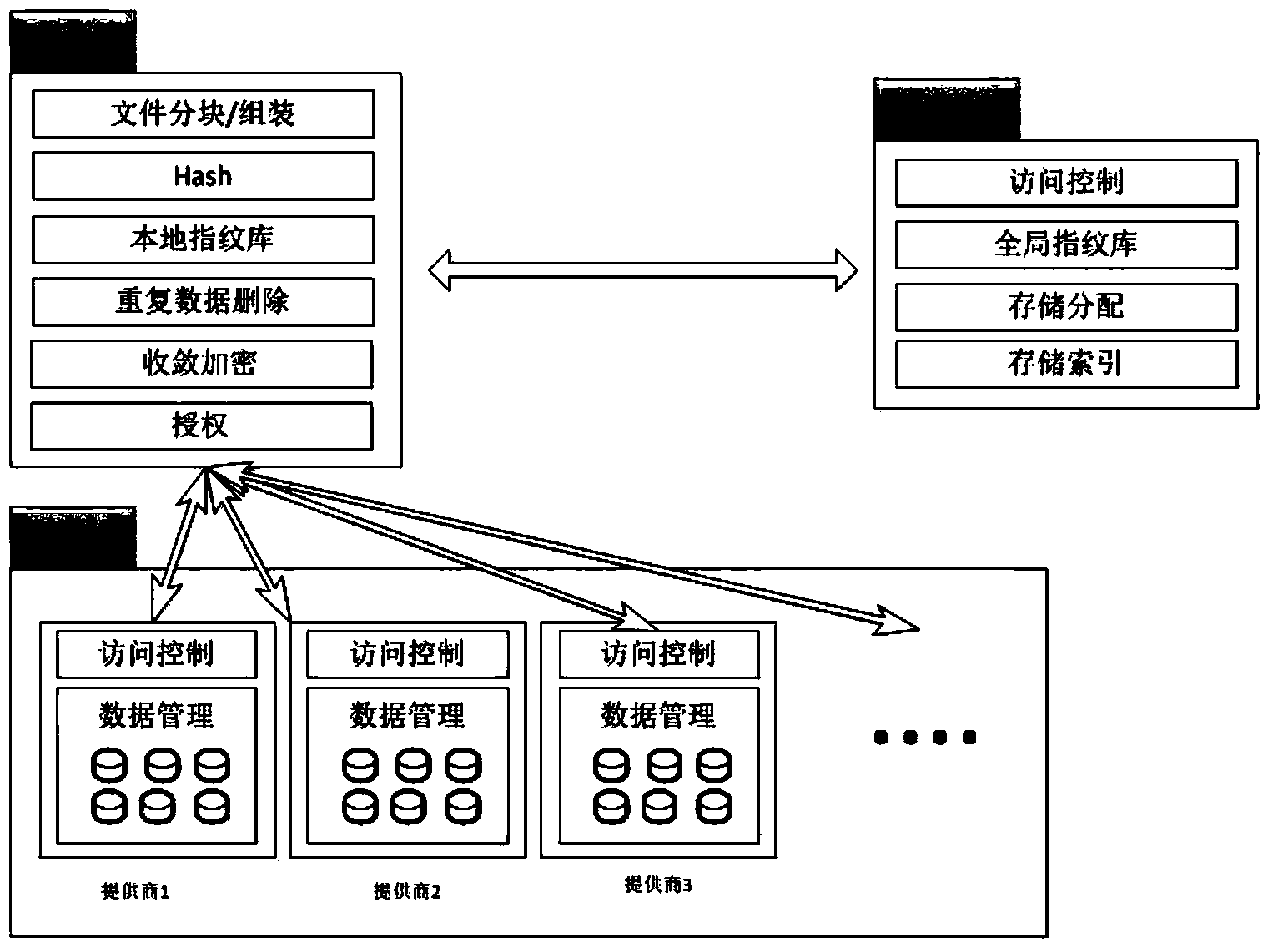
The invention discloses a repeating data deleting system and method applicable to cloud storage. The repeating data deleting system is based on strategies, a security agent and a random storage mechanism are adopted, a storage service is separated from a security service, the space utilization rate of cloud storage is improved, bandwidth occupation of redundant data is reduced, and security of user data and privacies is improved at the same time. The system is mainly composed of a client, the security agent and the cloud storage, wherein the security agent is the most secure core and is mainly used for ensuring the security of the user data and privacies. The repeating data deleting system and method applicable to cloud storage have the advantages of being high in security, system efficiency, bandwidth utilization rate and the like, and can resist replay attack, impersonation attack and security threats brought by partially trusted cloud storage providers.
Owner:NANJING UNIV OF POSTS & TELECOMM
Digital certification analyzer
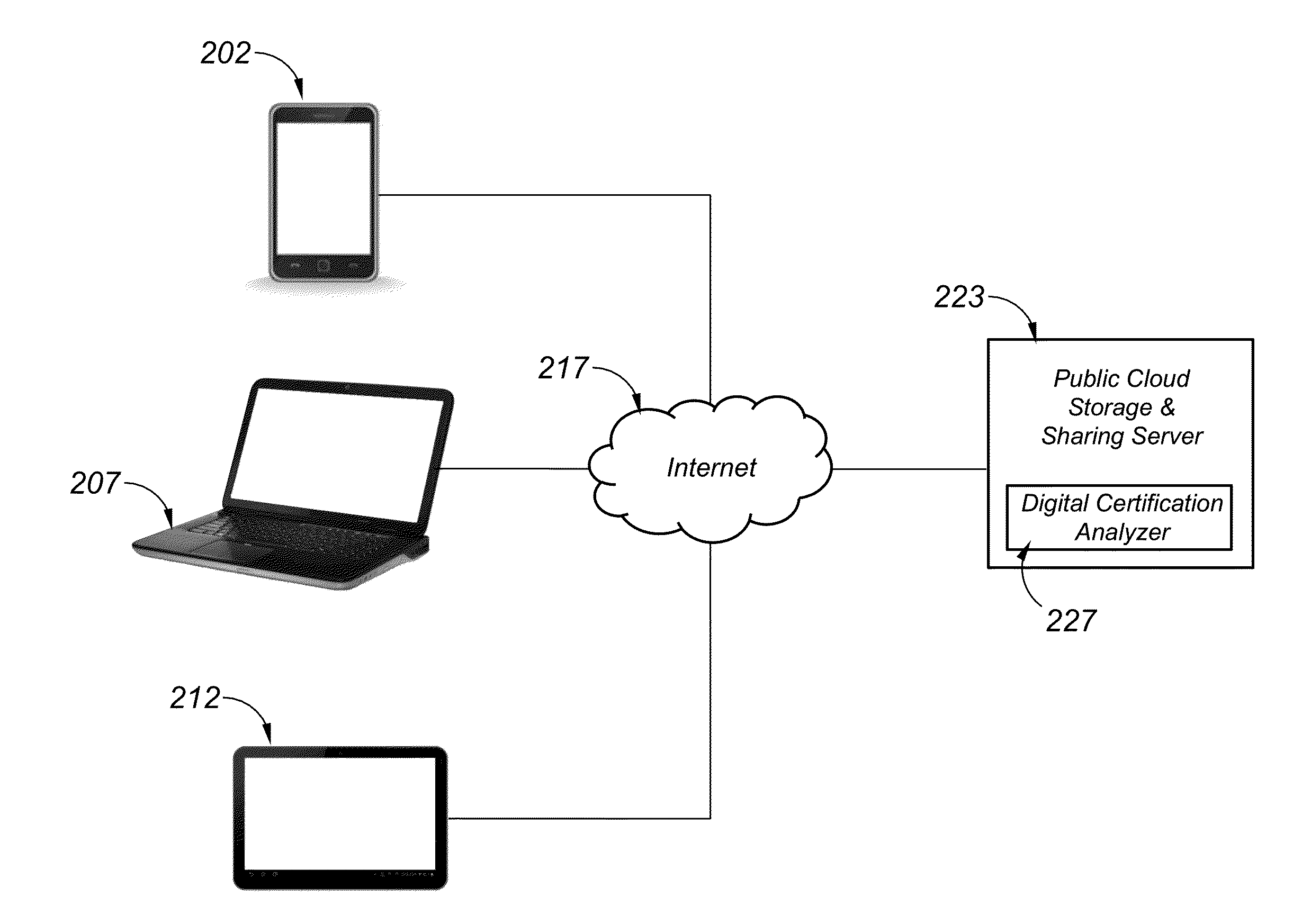
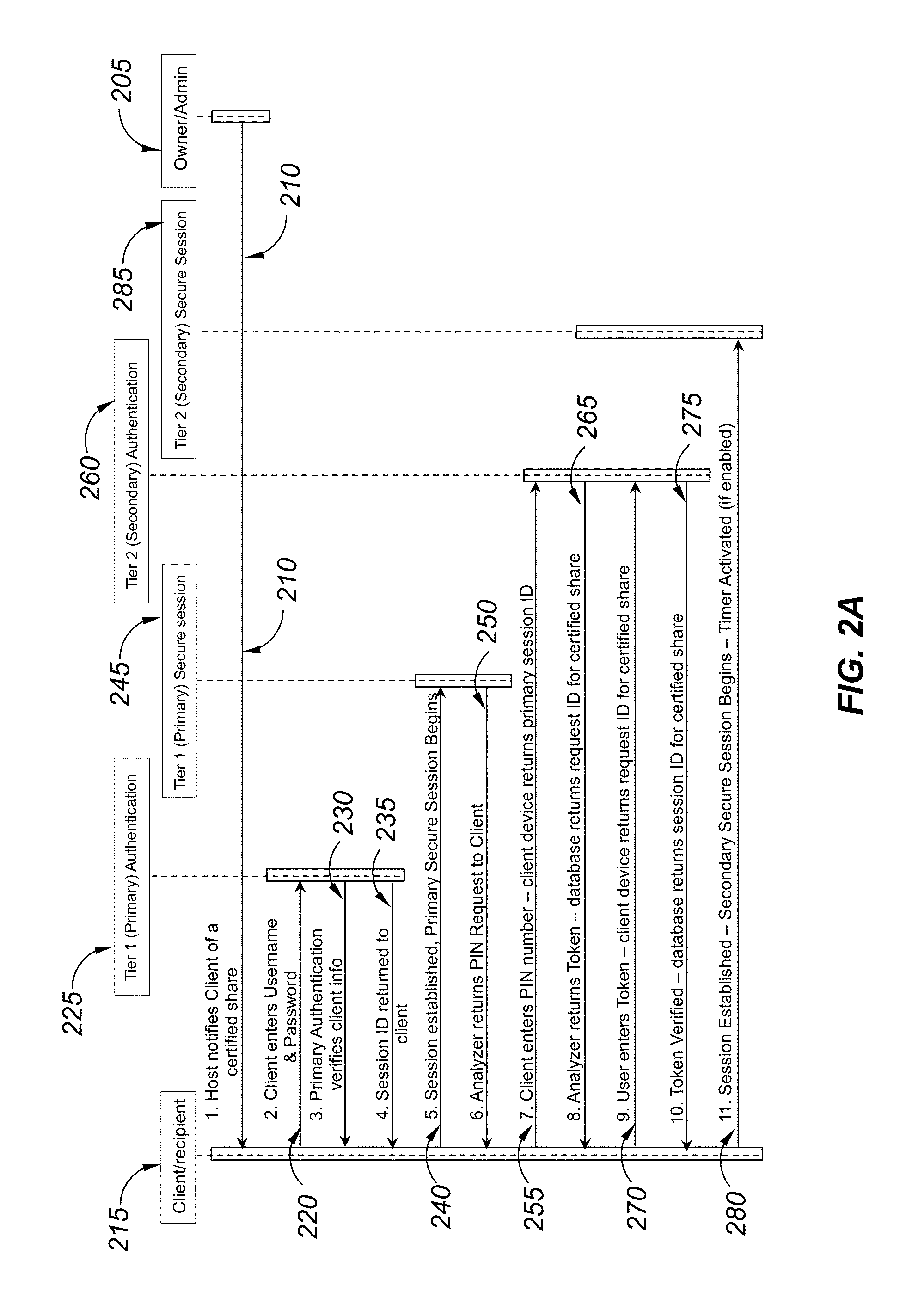
ActiveUS20160094541A1Improve securityImprove privacyProgram/content distribution protectionSecuring communicationHard disc driveDigital content
A digital certification analyzer (or “analyzer”) provides protection for digital content stored on servers, file sharing systems, hard drives and USB enabled external drives or other digital repositories. The analyzer prevents unauthorized access from both owners / administrators and recipients of digital content being shared through a web based or file sharing type service. The analyzer protects the owner of the shared digital content from unauthorized access, while allowing multiple protection instances to be applied to multiple digital content shares within a digital file hosting and sharing environment. Timers are provided to limit access to digital content at the discretion of the owner of the digital content.
Owner:TAN ANTHONY
A user authentication device and an authentication method based on a physically non-clonable technology PUF
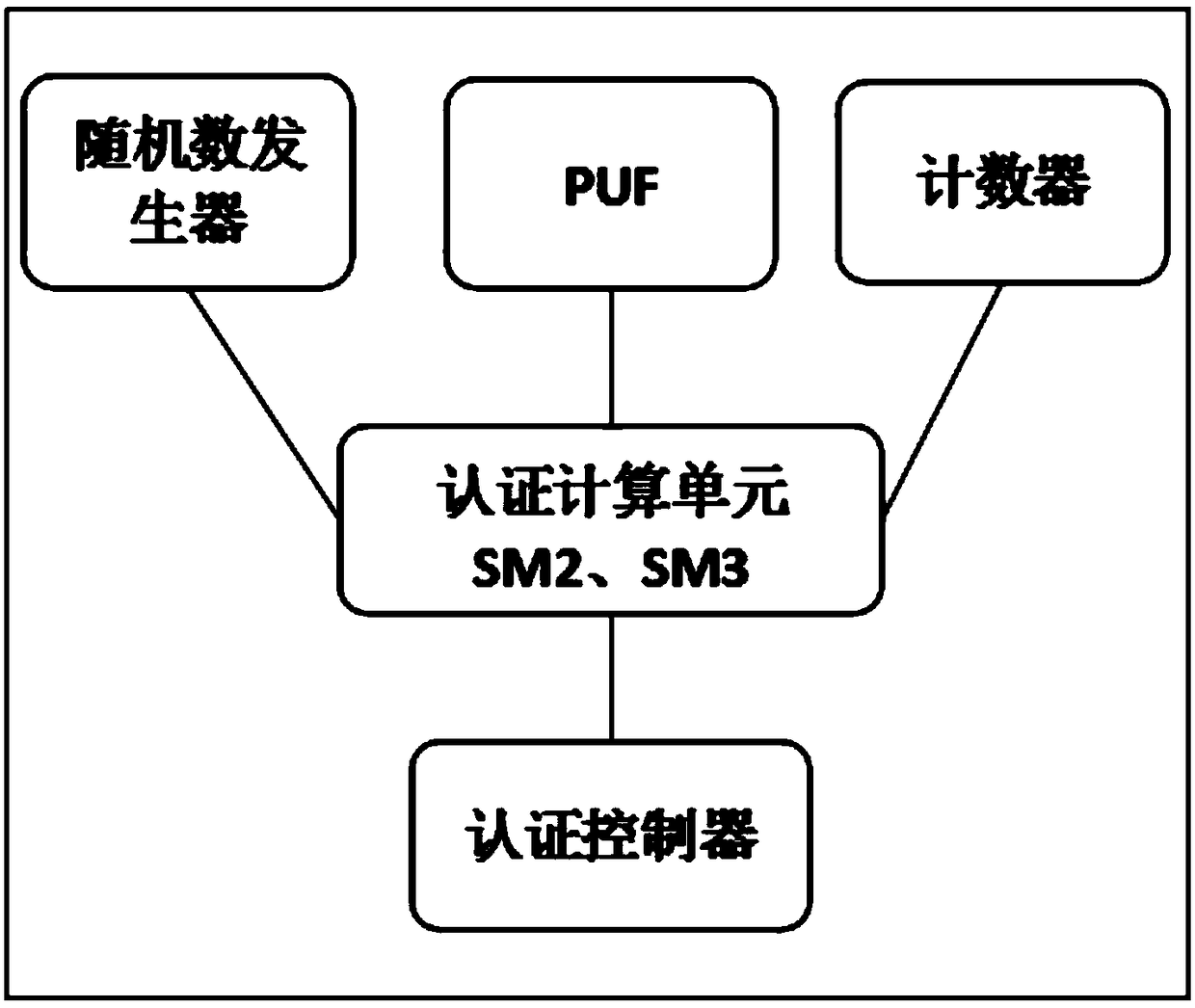
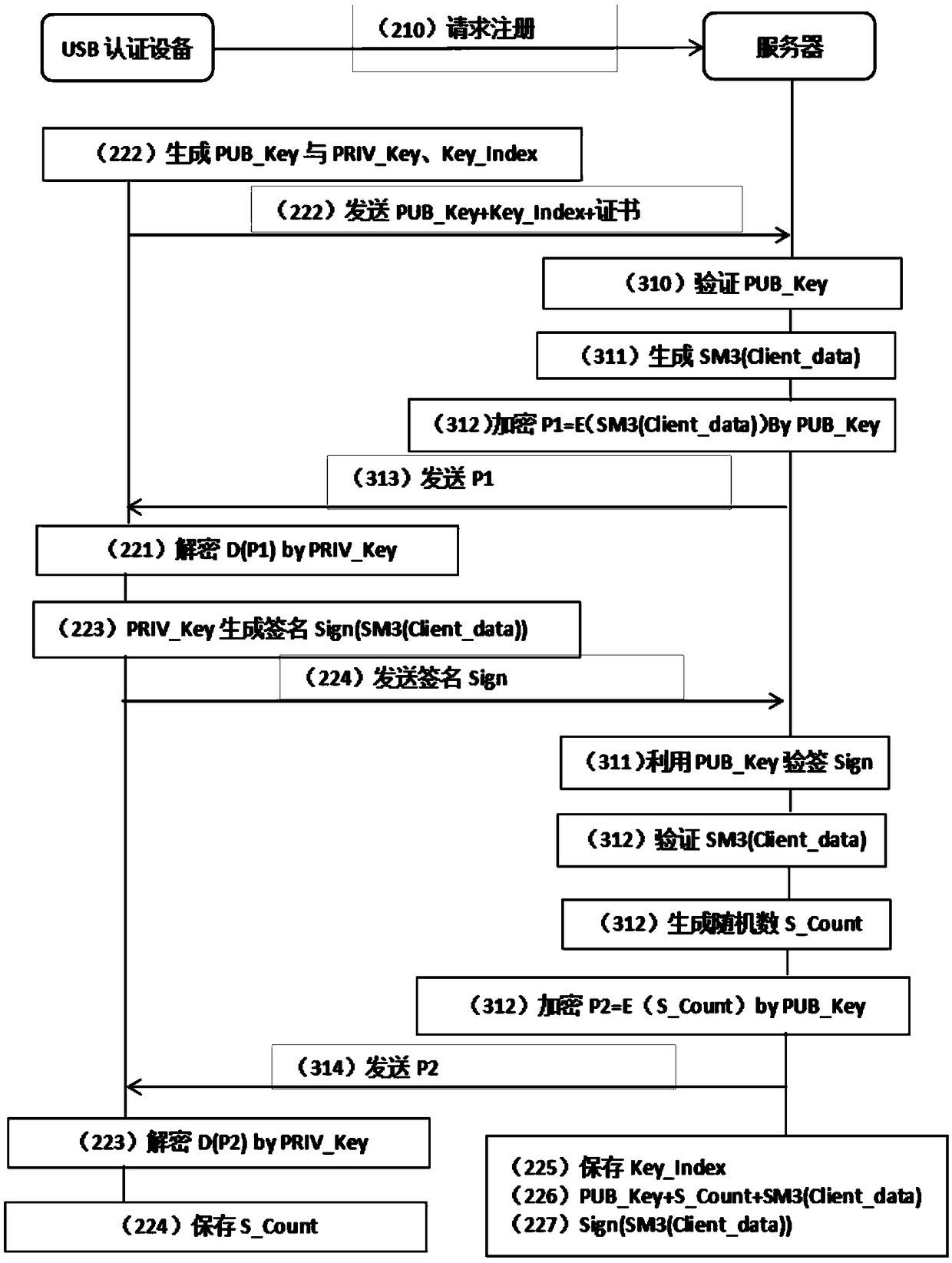
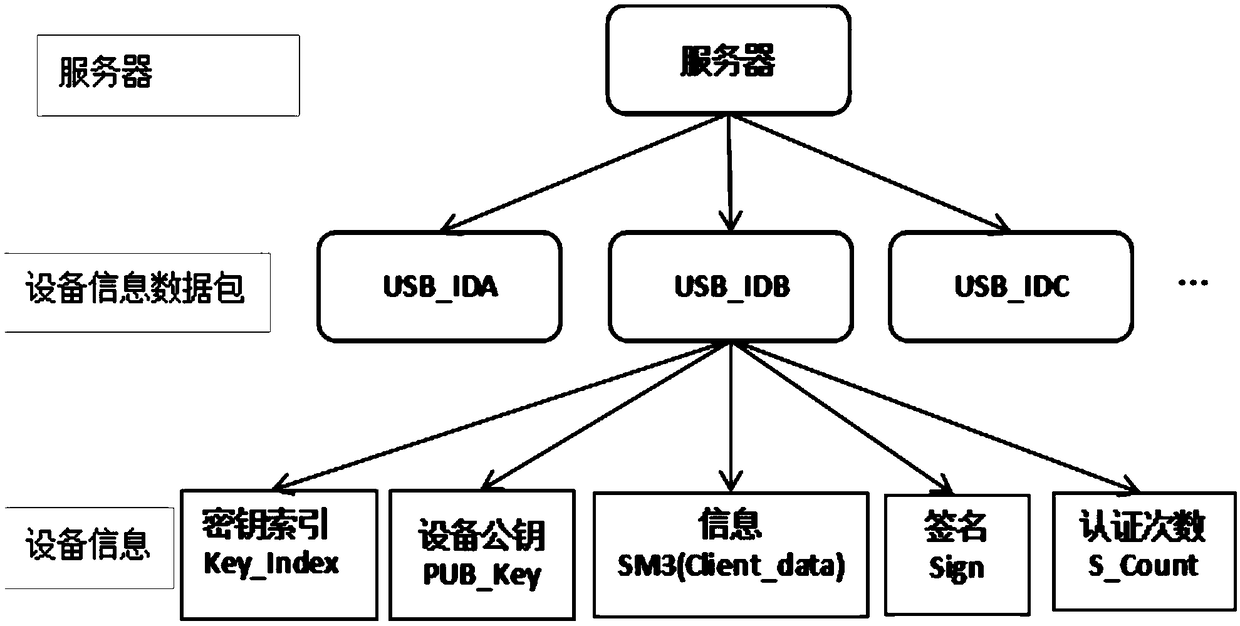
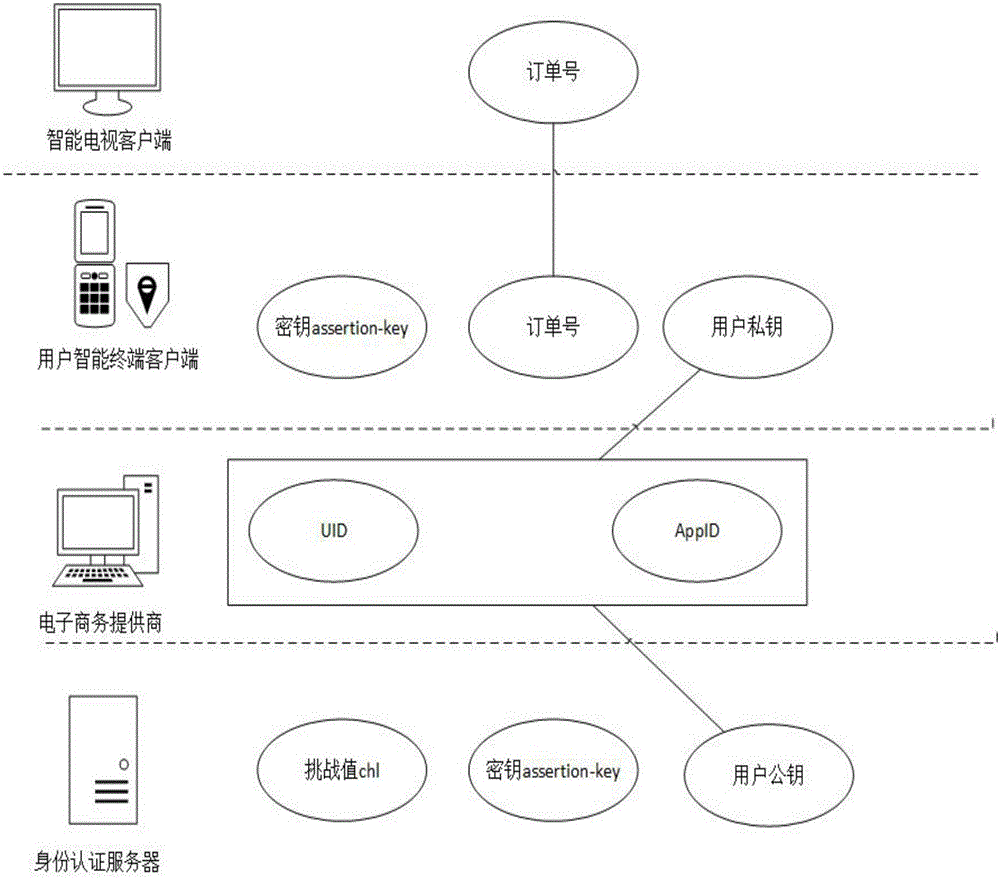
ActiveCN109040067AImprove privacy and securityUniqueness guaranteedPublic key for secure communicationUser identity/authority verificationUser authenticationNumber generator
The invention discloses a user authentication device based on a physically non-clonable technology PUF, comprising a physically non-clonable module PUF, an authentication module, an authentication control module, a random number generator and a counter, wherein, the physically non-clonable module PUF is embedded in the authentication device for generating authentication-related key pairs; The authentication module is embedded with an asymmetric algorithm and a digest algorithm to complete the operation to be executed by the authentication; The user can manually control sending authentication request and sending authentication information through the authentication control module; The invention is based on the three principles of simplicity, privacy security and compatibility, and meets therequirements of simplicity, high security and compatibility with a plurality of network servers. The chip inside the device adopts the non-clone technology PUF to ensure the uniqueness of the device,and meets the characteristics of non-clone replication and privacy security of the device.
Owner:GUANGDONG UNIV OF TECH +1
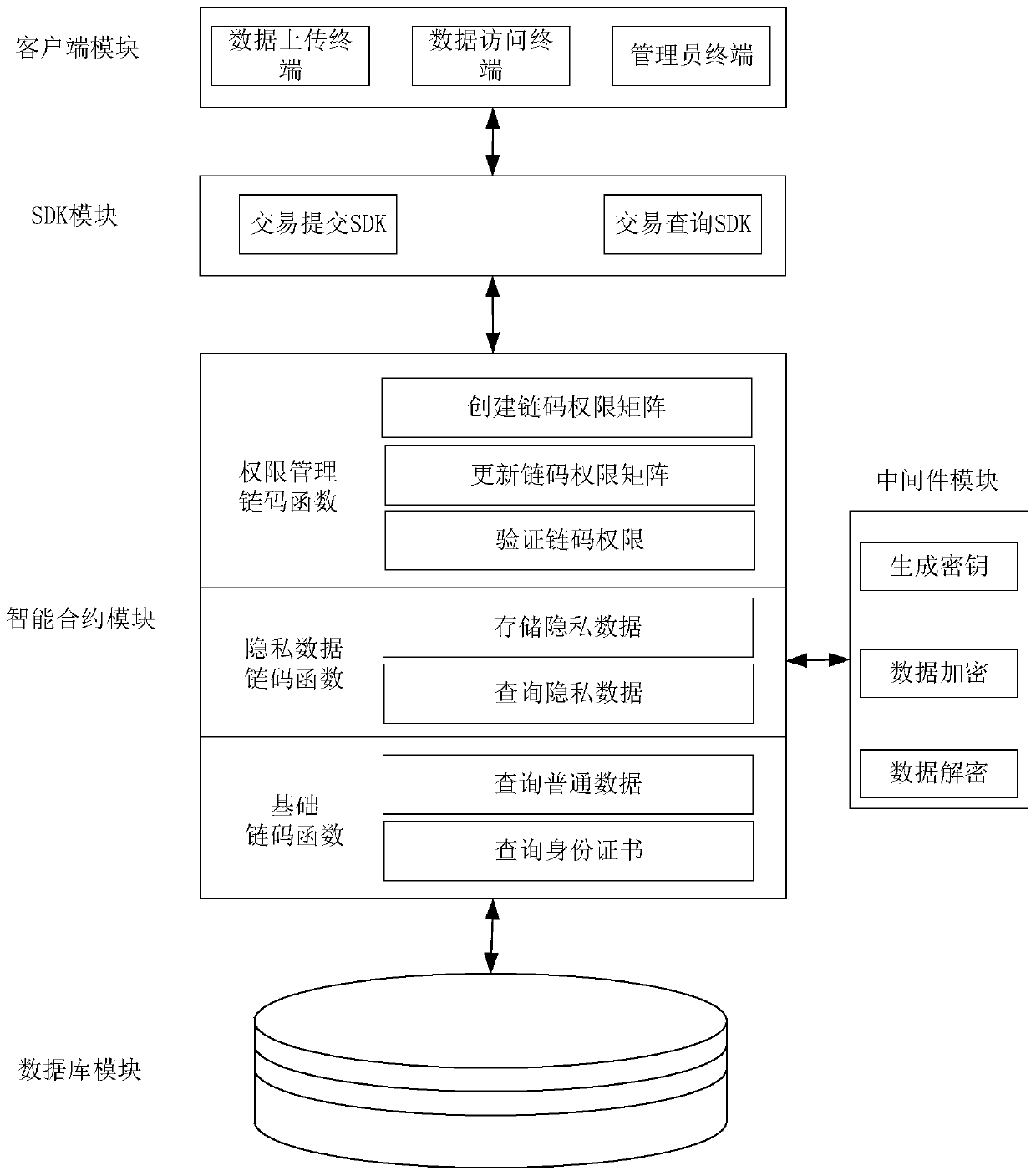
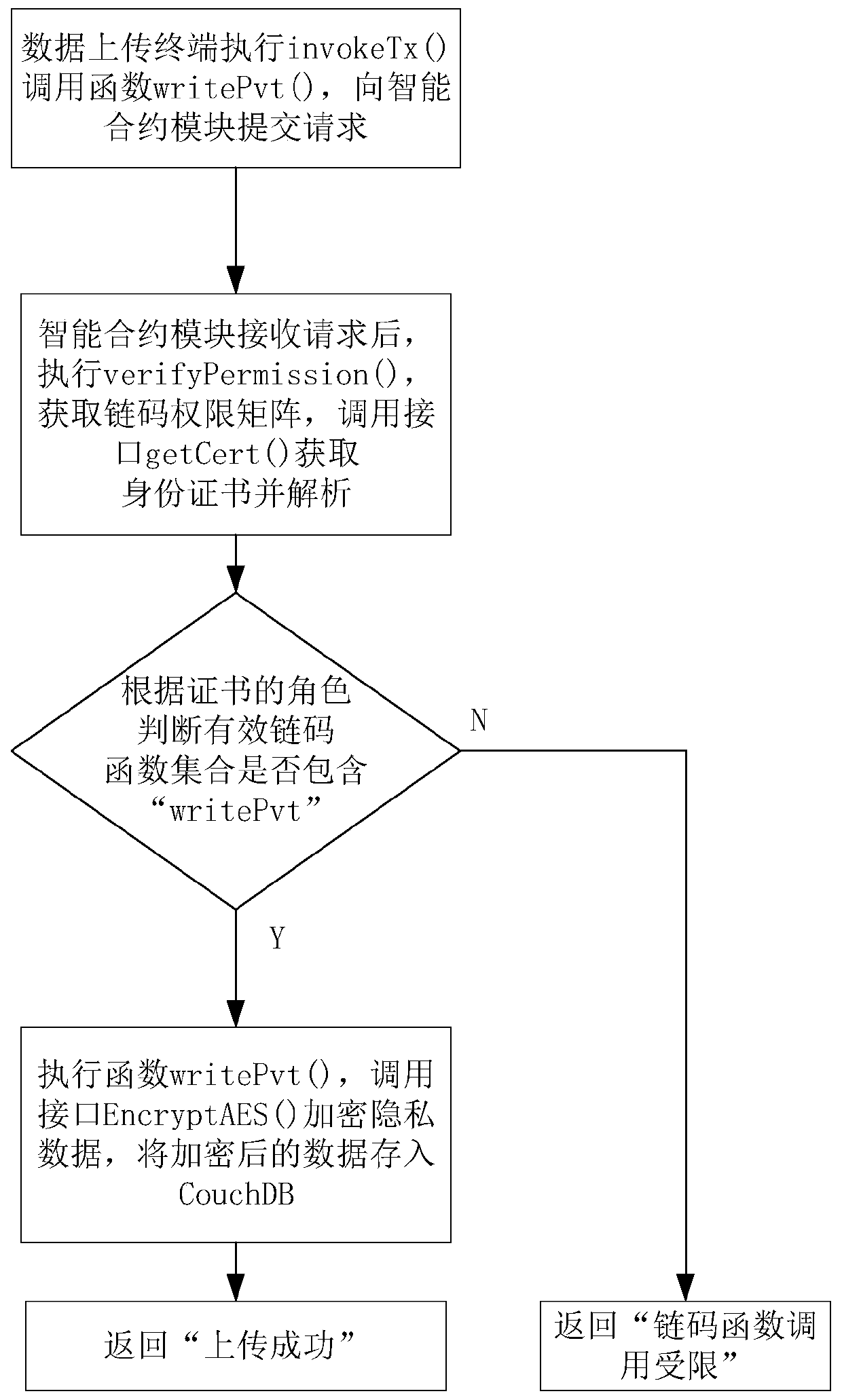
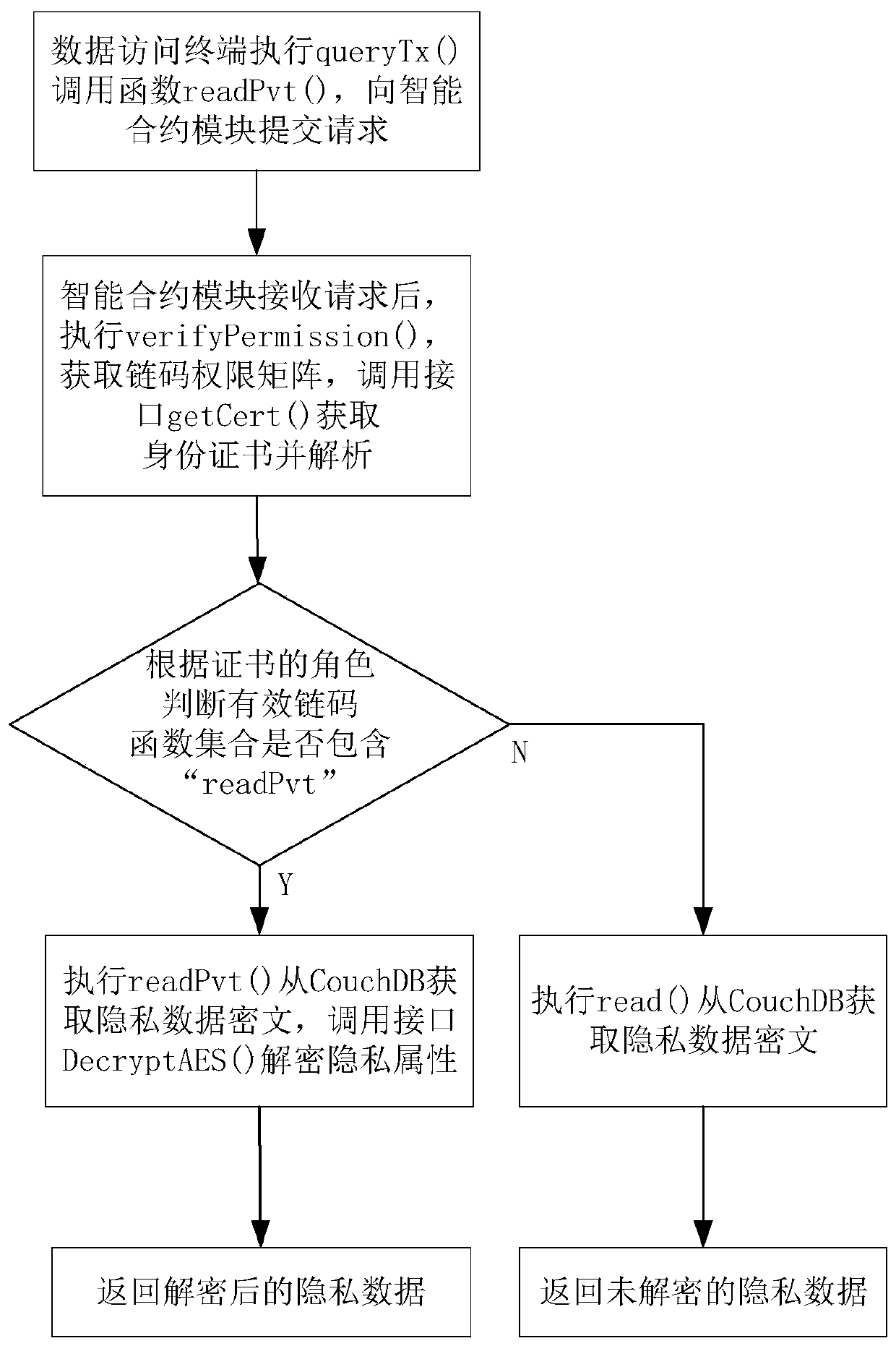
Hyperledger Fabric block chain private data storage and access system and method thereof
ActiveCN111191286AImprove personal privacy securityNot easy to degrade performanceFinanceDigital data protectionData querySmart contract
The invention discloses a Hyperledger Fabric block chain private data storage and access system and a method thereof. The system comprises a client module, an SDK module, an intelligent contract module and a database module, the client module calls a private data storage chain code function through the SDK module, the intelligent contract module judges whether an effective chain code set containsthe private data storage chain code function or not according to role information in a certificate of the client module, and if the effective chain code set contains the private data storage chain code function, the private attribute of the encrypted data and the non-private attribute are stored in a database together; the client module calls the private data query chain code function through theSDK module; and the intelligent contract module judges whether the effective chain code set contains a private data query chain code function or not according to role information in a certificate of the client module, if so, decrypts a query result of the database module and returns real data to the client module, and otherwise, directly returns ciphertext data to the client module. According to the method and the system, the personal privacy security in Hyperledger Fabric data storage can be effectively improved, and the method and the system have the advantages of confidentiality and security.
Owner:NANJING UNIV OF SCI & TECH
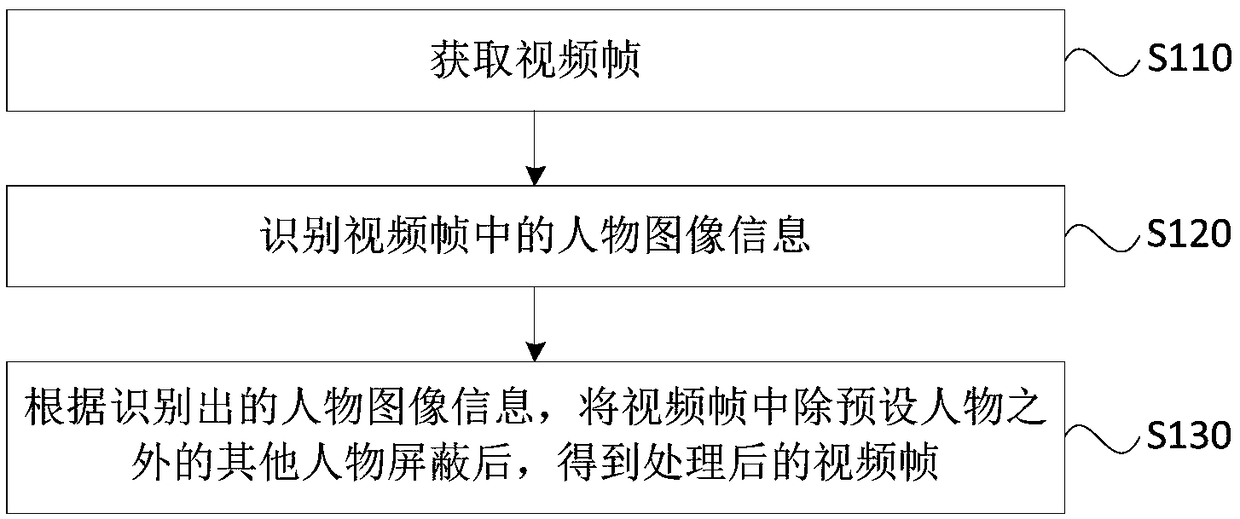
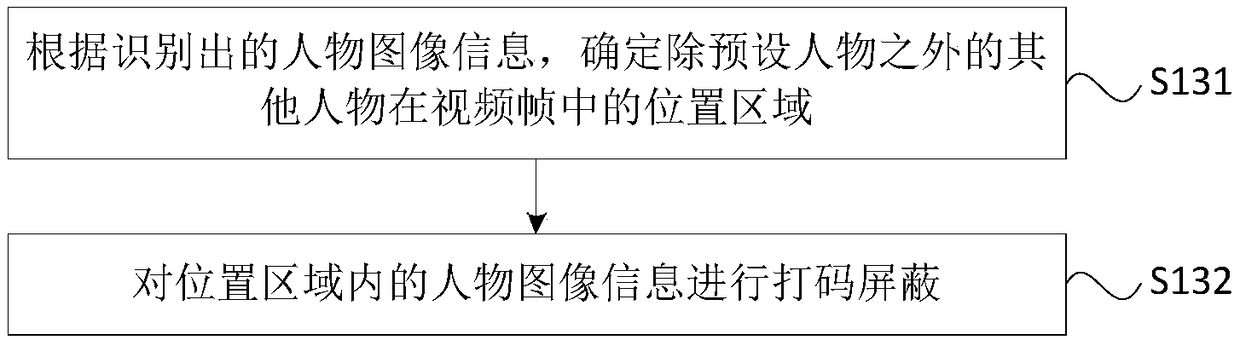
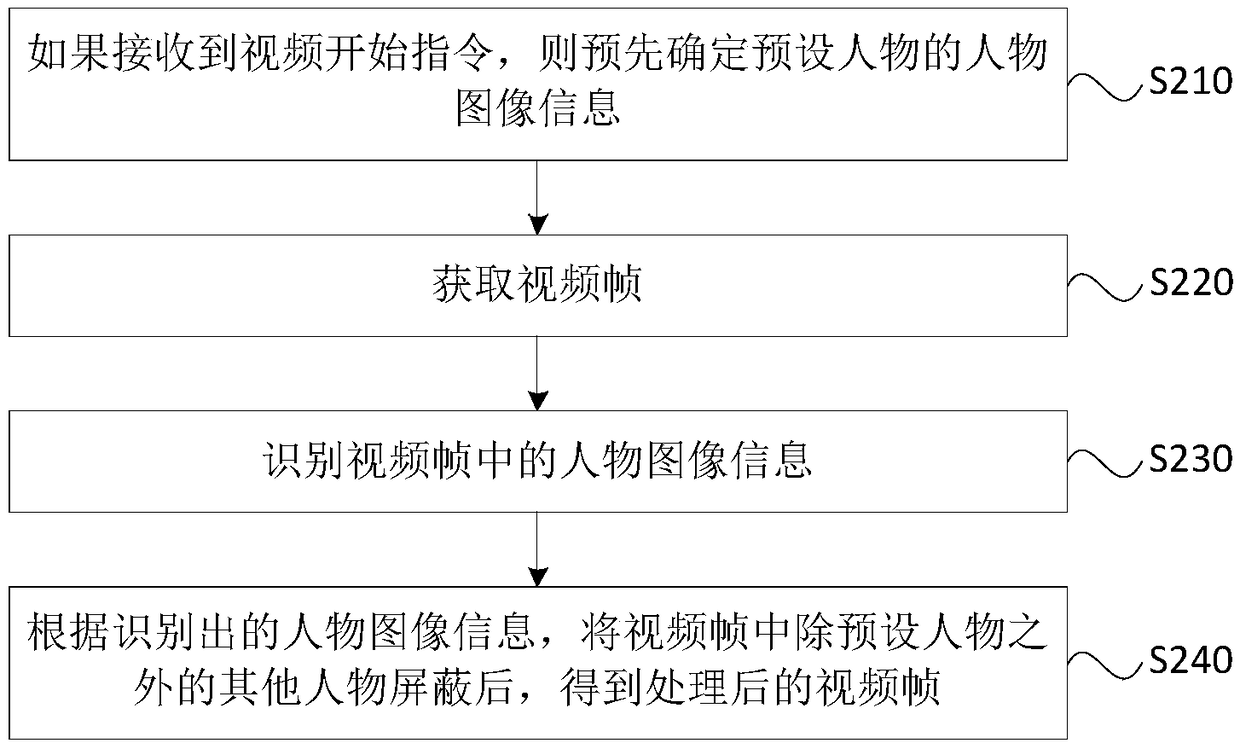
Video processing method and apparatus, terminal and storage medium
InactiveCN108848334AProtect private informationReduce the risk of privacy breachesTwo-way working systemsSelective content distributionComputer graphics (images)Video processing
The embodiment of the invention discloses a video processing method and apparatus, a terminal and a storage medium. The method comprises the following steps: obtaining a video frame; identifying character image information in the video frame; and shielding other characters excluding a preset character in the video frame according to the identified character image information to obtain a processedvideo frame. By adoption of the technical scheme provided by the embodiment of the invention, by shielding the other characters excluding the preset character in the video frames in a video process, the information of the other characters who do not participate in a video in the surrounding environment of the video is shielded, thereby protecting the privacy information of the other characters, reducing the risks of accidental privacy leakage and improving the privacy security.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
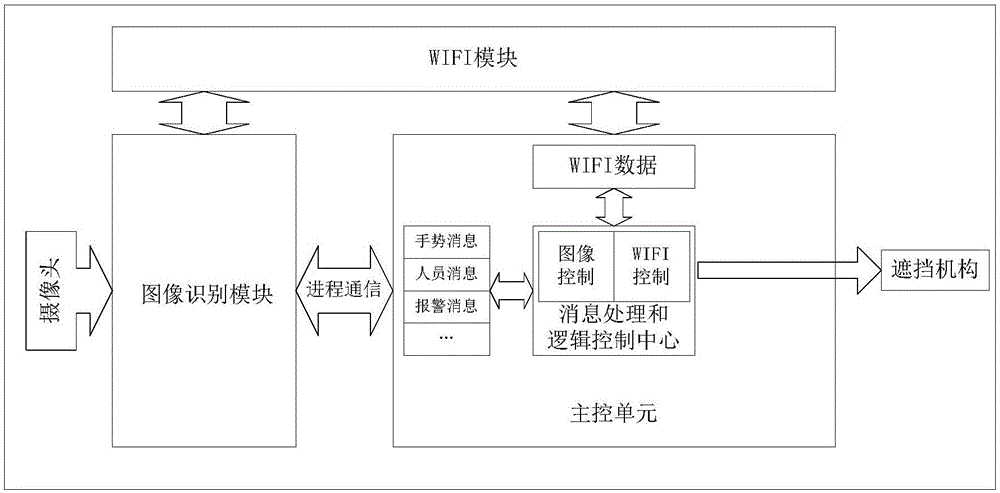
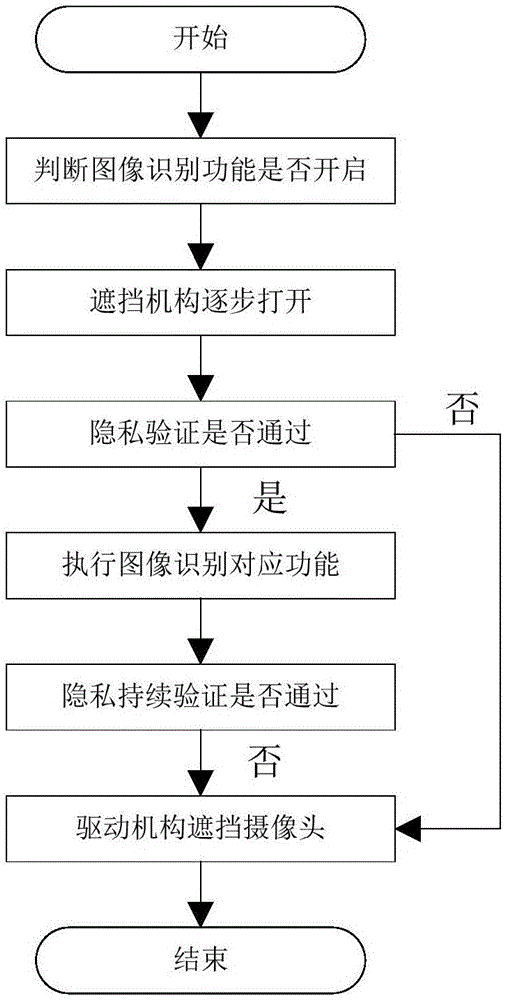
Control method and device of air conditioner
ActiveCN106440199AImprove privacy and securityImprove securityMechanical apparatusSpace heating and ventilation safety systemsUser privacyPrivacy protection
The invention discloses a control method and device of an air conditioner. The air conditioner comprises a camera and a shielding device used for shielding the view of the camera. The method includes the steps of responding to a triggered starting command, starting the camera to collect images and controlling the shielding device to carry out first movement at the preset rate to gradually expand the view range of collecting the images by the camera; in the process of gradually expanding the view range of collecting the images by the camera, carrying out first judgment on whether the user privacy safety passes a standard according to the images collected by the camera; and controlling the shielding device to shield the view range of the camera when the judgment result of first judgment does not pass the standard. According to the control method and device, the problem that the safety of the intelligent air conditioner in the prior art is low is solved, the safety of the intelligent air conditioner is improved, and privacy protection of users is improved.
Owner:GREE ELECTRIC APPLIANCES INC
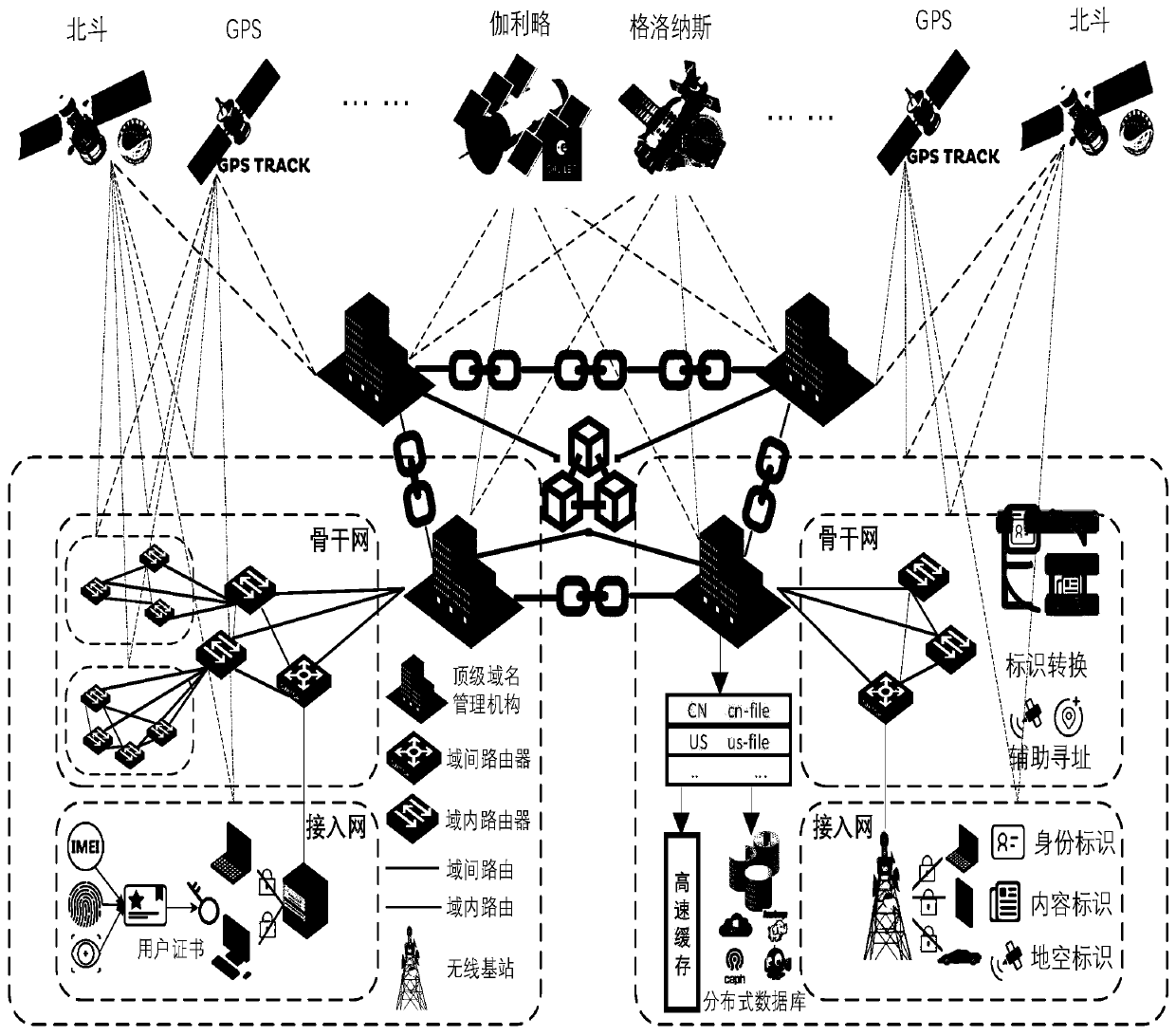
Method and system for supporting multi-mode identification network addressing to gradually go to IP, and storage medium
ActiveCN111373704AAchieve securityRealize immutabilityUser identity/authority verificationData switching networksNetwork addressIp layer
The present invention provides a method and system for supporting multi-mode identification network addressing to gradually go to IP, and a storage medium. The present invention proposes a set of newnetwork multi-mode identification generation management and routing addressing system that integrates blockchains. The multi-mode identification dynamic adaptation and intercommunication technology isused to break through all existing network performance and security bottlenecks based on the IP layer, and the distributed blockchain consensus algorithm is used to achieve the original wish of Internet co-management and co-governance. All network resources on the network are locked on the blockchain to ensure that network resources are authentic and not tampered; the high-performance and low-overhead distributed storage technology is used to achieve the security of multi-mode identification addressing and tamper-proof modification, and, at the same time, the introduction of user real-name registration and network login management strategies combined with biometric identity information and signature strategies for privacy protection are introduced to reduce system management costs and improve the privacy and security of access node information.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +3
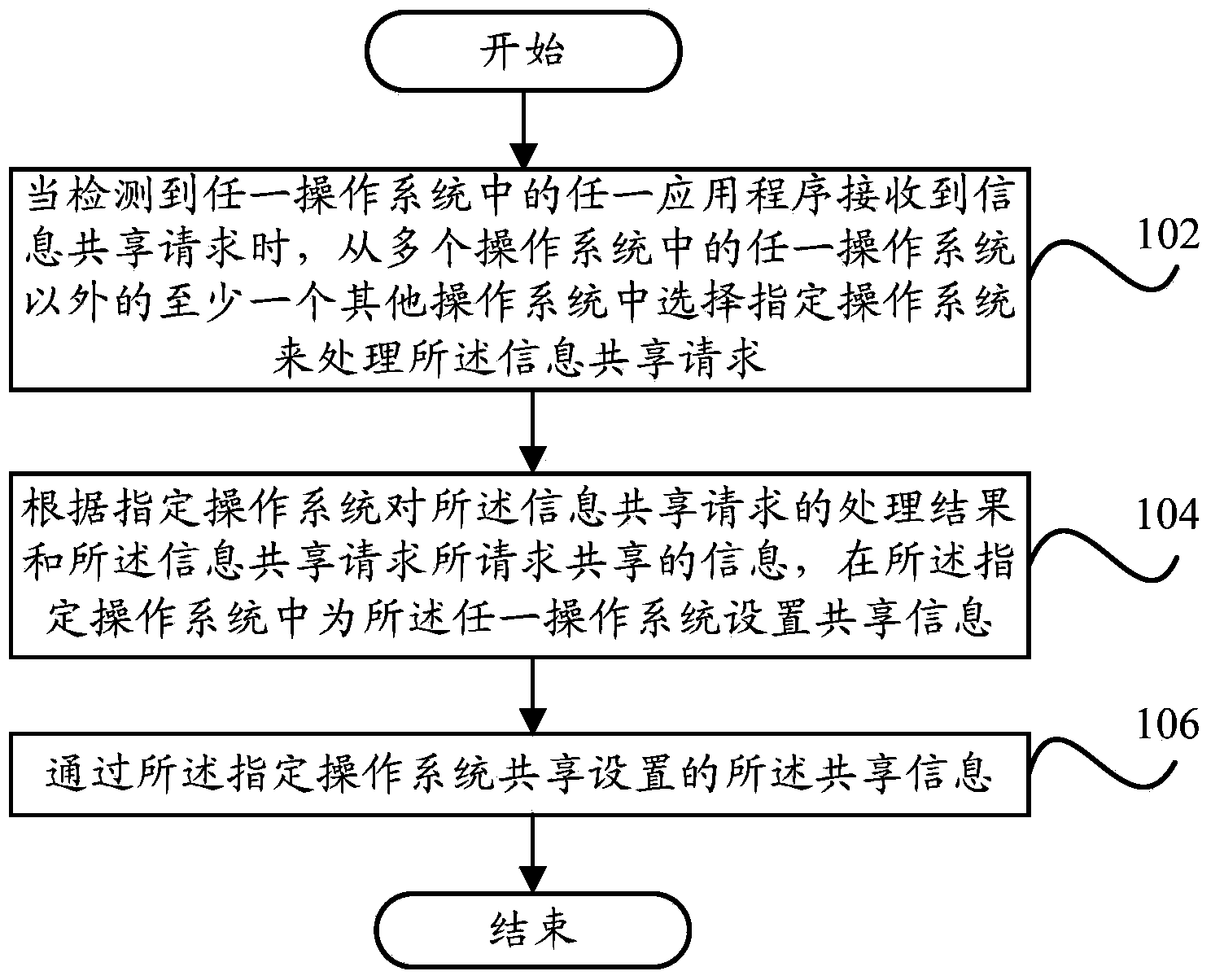
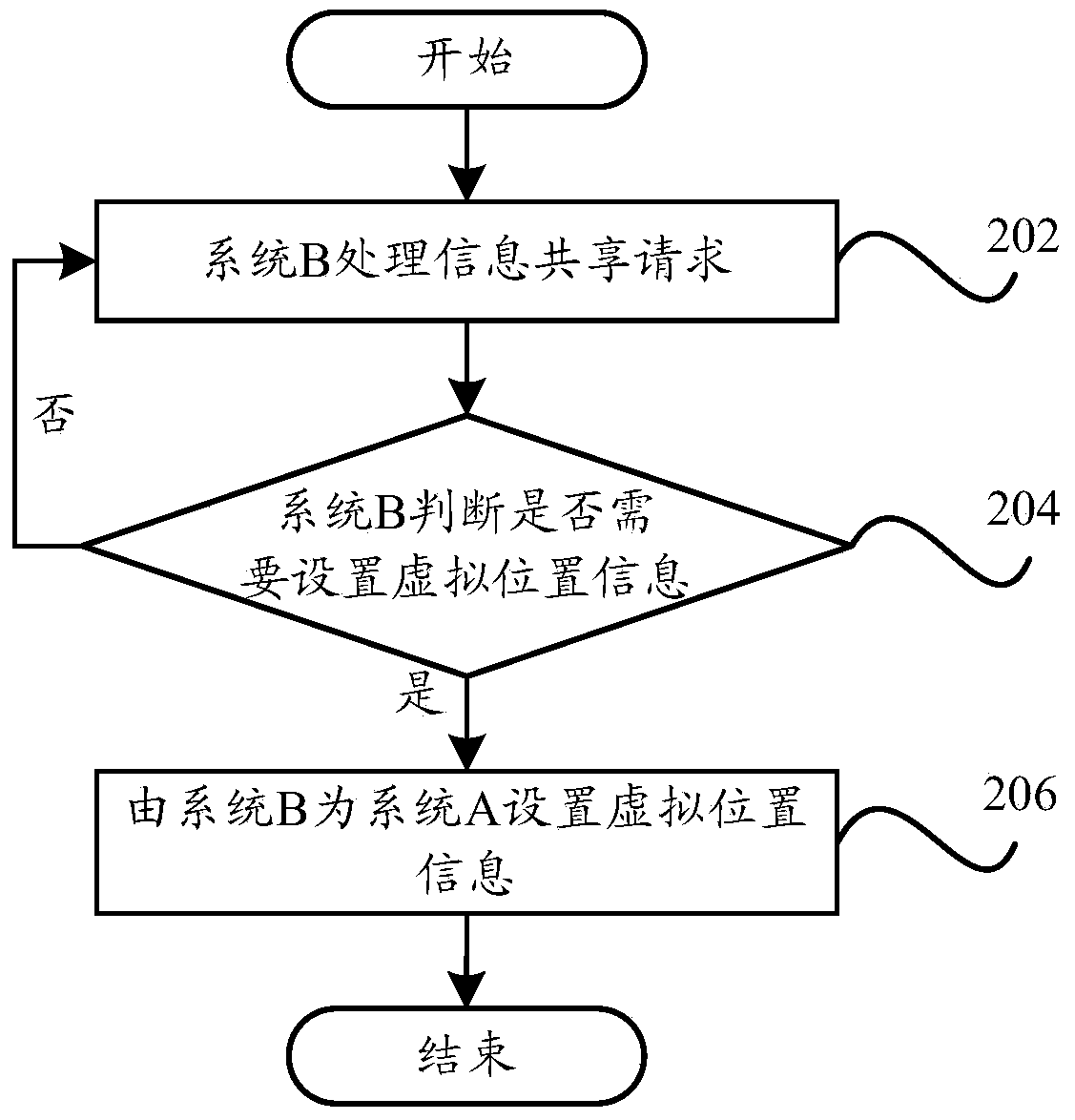
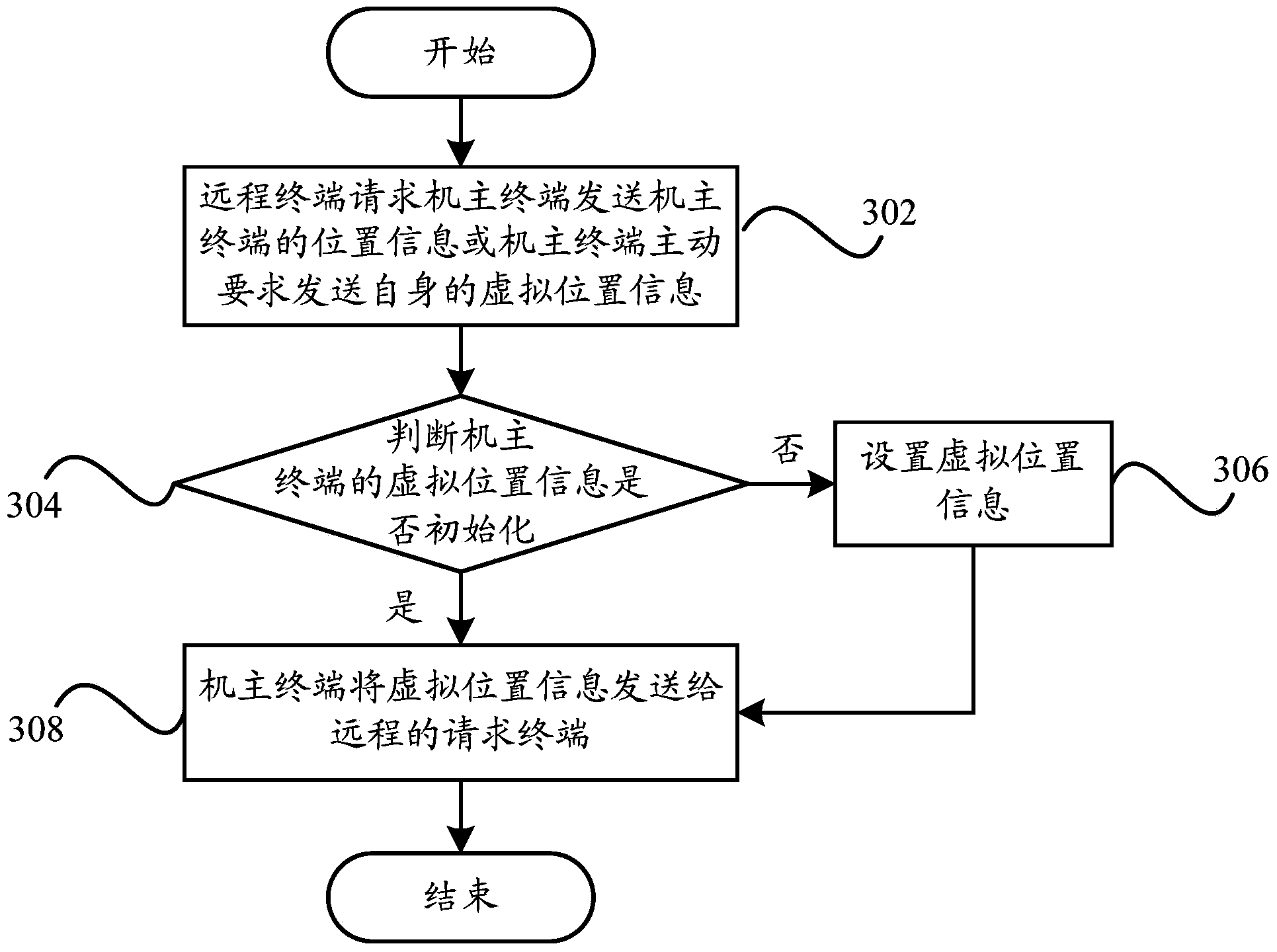
Information sharing method and information sharing device of terminal and terminal
ActiveCN104184738AImprove privacy and securityImprove experienceTransmissionInformation sharingOperational system
The invention provides an information sharing method and an information sharing device of a terminal and the terminal. The information sharing method of the terminal comprises the steps of selecting a designated operating system from at least one of other operating systems of multiple operating systems except any one operating system to handle an information sharing request when detecting any one operating system receives the information sharing request; setting shared information for any one operating system in the designated operating system according to a handling result of the designated operating system handling the information sharing request and information required by the information sharing request to be shared; sharing the set shared information through the designated operating system. By means of the technical scheme, the control ability on personal information of a user is improved, the information security of the terminal is effectively ensured, the privacy security of the user is improved, and the user experience is enhanced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
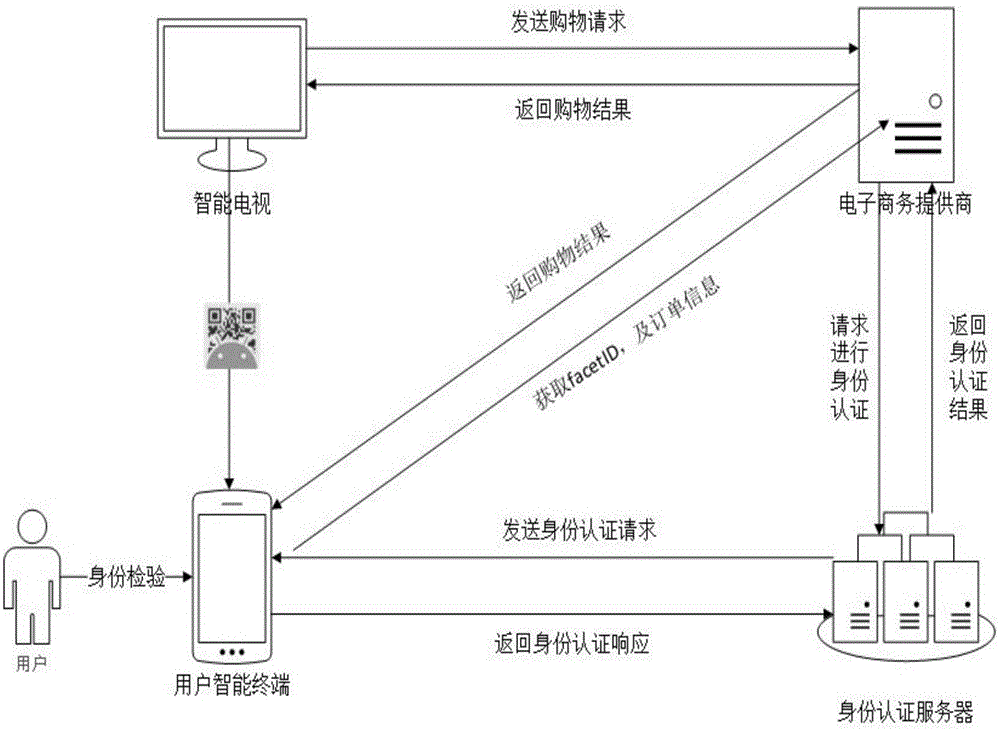
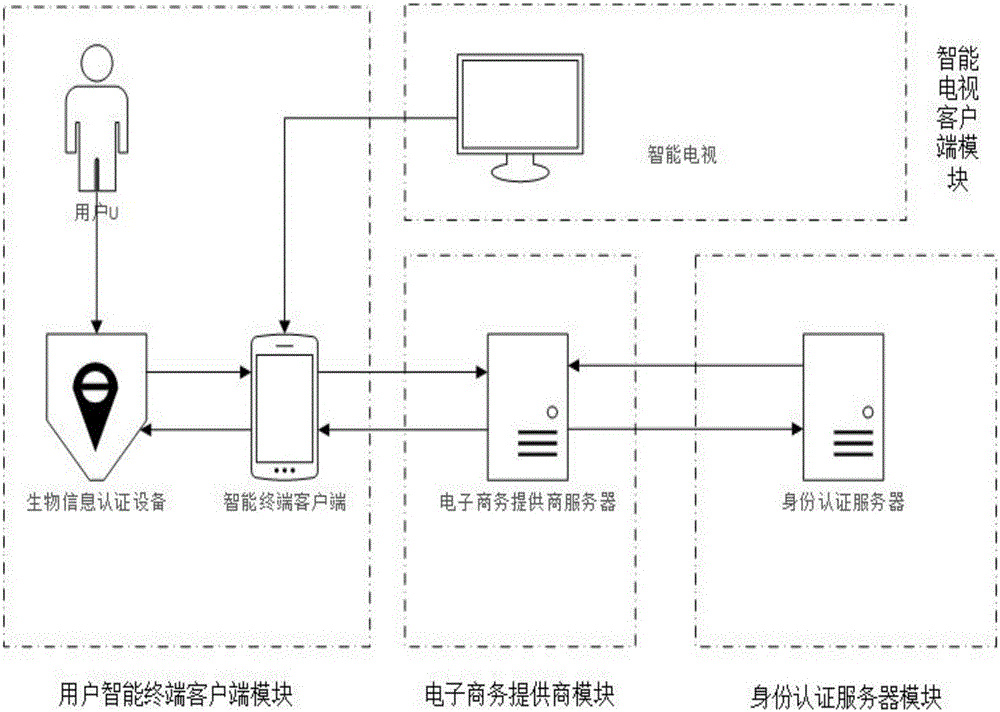
Safety payment system and method based on smart TV multi-screen interaction
InactiveCN105049945AImprove securityGuaranteed experienceTransmissionSelective content distributionPasswordAuthentication server
The invention discloses a safety payment system and method based on smart TV multi-screen interaction. A business delegate method is introduced to relegate an identity authentication requirement at a smart TV terminal to a user smart terminal, which is higher in security and supports a plurality of physiological information authentications, to process through a multi-screen interaction concept, and a processing result is finally returned to the smart TV terminal. Through the adoption of the user smart terminal, a built-in or external physiological information authentication device and an identity authentication server are combined through an asymmetrical secret key mode to perform the negotiation authentication, thereby realizing the safety payment system at the smart TV terminal. Through the adoption of the method disclosed by the invention, a user can finish the identity authentication and the affair confirmation of the smart TV terminal by means of the convenient and safe physiological information authentication device at the smart terminal, and the traditional user name password identity authentication mode is substituted. The information security in the authentication process is greatly improved while the user experience is guaranteed.
Owner:INST OF INFORMATION ENG CAS
Balance management method, system and device and storage medium
InactiveCN108876335ASolve scalabilityAddress flexibilityPayment protocolsPayment circuitsOperating systemBlockchain
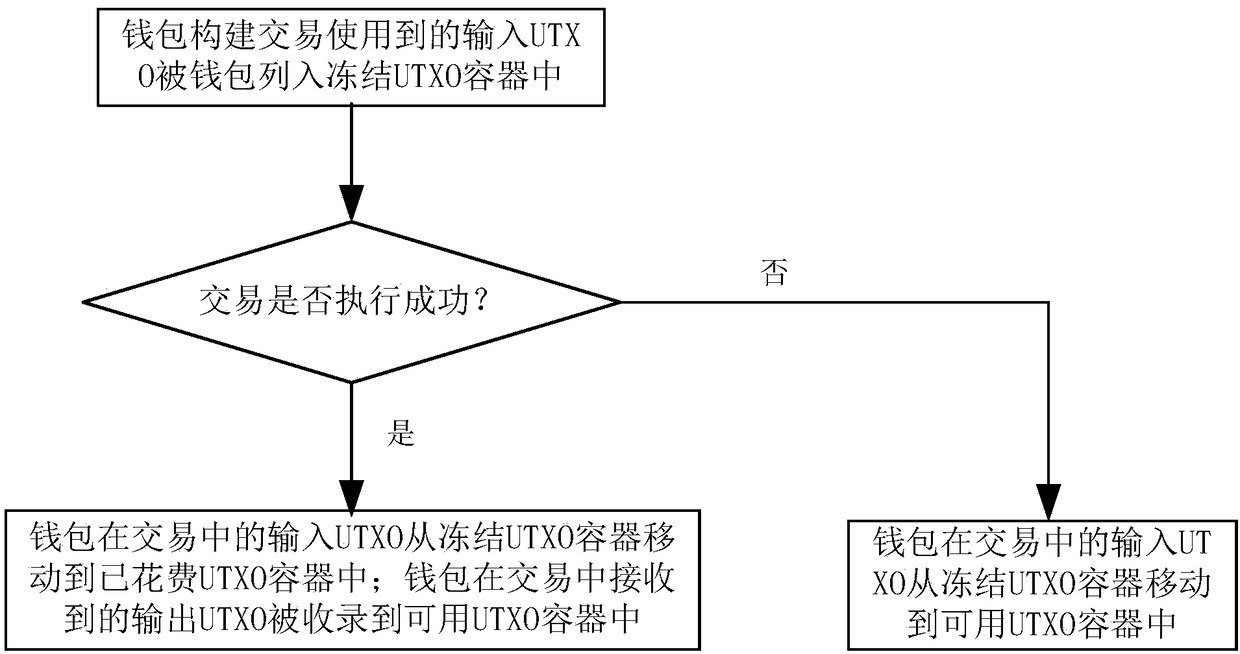
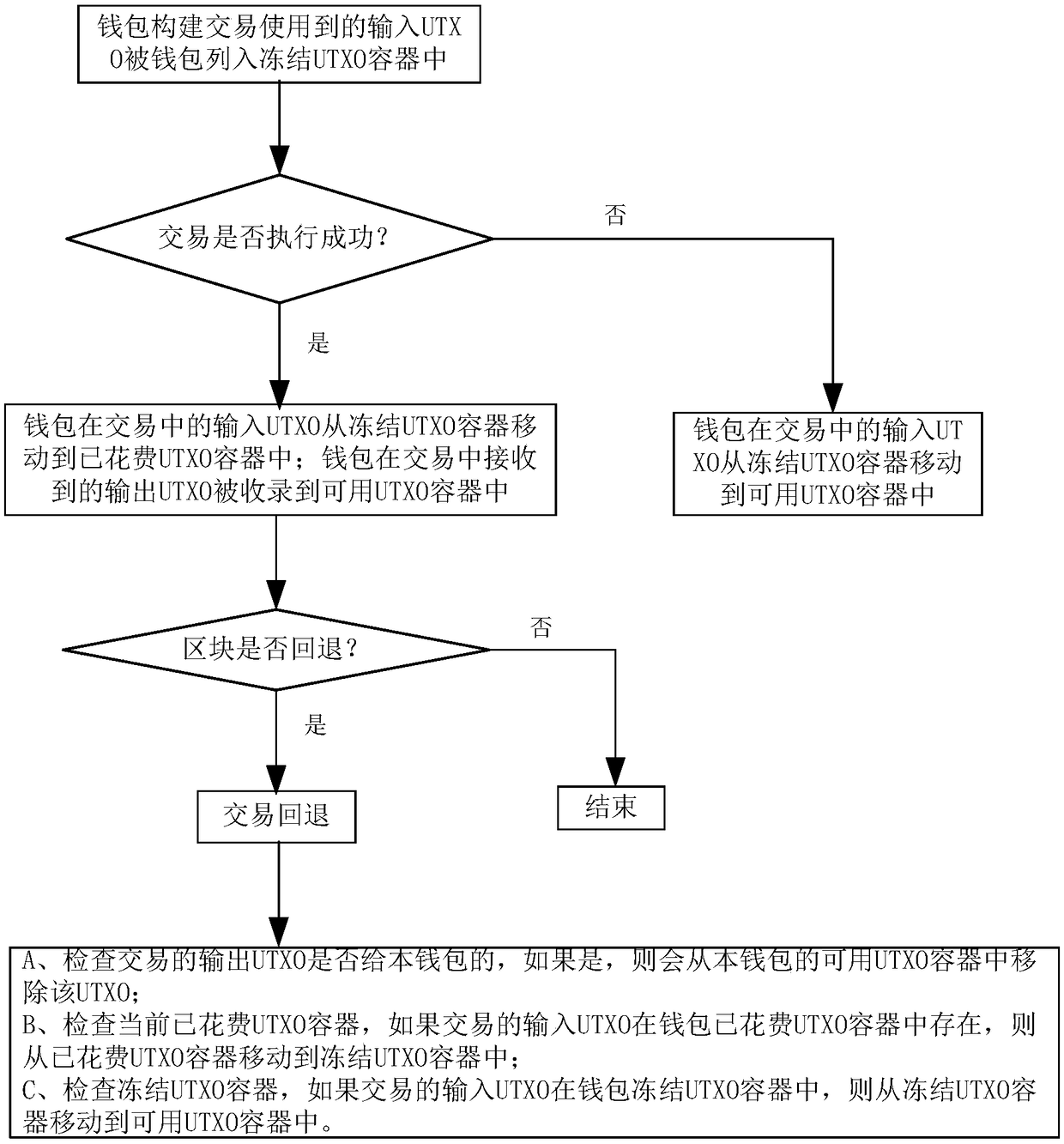
The invention discloses a balance management method, system and device and storage medium, and belongs to the technical field of block chains. The method comprises the steps that a wallet constructinginput UTXO used in transaction and assigned to a frozen UTXO container by the wallet; if the transaction is successfully executed, moving the input UTXO of the wallet in the transaction from the frozen UTXO container to a spent UTXO container; and recording the output UTXO received by the wallet in the transaction into a usable UTXO container; if the transaction is executed unsuccessfully or thetransaction is overtime due to the fact the transaction is not executed for a long time, moving the input UTXO of the wallet in the transaction from the frozen UTXO container to a usable UTXO container. The method can improve the expansibility and flexibility of an account balance management mode. The privacy safety of a user can be improved, and the risk of privacy leakage is reduced.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Two-tiered wireless sensor network range query method capable of verifying privacy protection
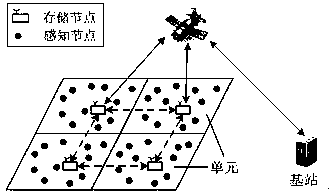
ActiveCN104717644AGuaranteed privacy and securityAchieving verifiabilityNetwork traffic/resource managementData switching networksPrivacy protectionNetwork communication
The invention discloses a two-tiered wireless sensor network range query method capable of verifying privacy protection. The two-tiered wireless sensor network range query method capable of verifying privacy protection includes the data collection protocol step and the query execution and verification protocol step. The data collection protocol step includes the procedures that sensor data are periodically collected by sensor nodes and subjected to bucket partitioning, data buckets are encrypted, verification code information of redundant buckets is worked out, corresponding data messages are constructed and uploaded to storage nodes, and the data messages are collected and then stored through the storage nodes. The query execution and verification protocol step includes the procedures that query instructions containing minimum tag sets corresponding to target zones are constructed by a base station and sent to the storage nodes, the storage nodes execute query processing and return corresponding query feedback messages, the base station decrypts the feedback messages and works out final query results, and finally query result consistency is verified. The protocol steps of the method are simple, privacy security of sensitive data can be guaranteed, and the query results can be verified; the in-network communication cost of the sensor nodes is low, and prolonging of the life cycle of a whole network is facilitated.
Owner:NANJING UNIV OF POSTS & TELECOMM
Position privacy protection method based on road network in continuous position service
ActiveCN105516190AImprove privacy and securityImprove rationalityWireless commuication servicesLocation information based serviceShortest distanceRoad networks
The invention relates to a position privacy protection method based on a road network in continuous position service. The realization steps mainly include two stages: an initialization stage: during the system initialization, an anonymous server firstly performs zoning processing on a service area, and then, a public track library is constructed for each zone according to the road network information; an anonymous processing stage: when a user performs continuous inquiry, firstly, l-1 tracks with the shortest distance are picked out from the track library to form an optimum l- covering track; then, each track in the optimum l- covering track is subjected to sampling processing according to the position of the inquiry in each time; a minimum covering region capable of covering all the tracks is constructed; in addition, the inquiry user ID (identification) is subjected to anonymous mapping. The method has the advantages that the position and track association speculation attack of a typical position k- anonymous mechanism in the continuous position service can be resisted; in addition, the track l diversity protection can be provided under the condition of using the minimum inquiry region.
Owner:FUJIAN NORMAL UNIV
Method and system for commerce with full anonymity
InactiveUS7225169B1Improve privacy and securityEasy to understandPublic key for secure communicationUser identity/authority verificationThird partyInternet privacy
A method (and system) of conducting business electronically between a first party and a second party, includes providing a third party who knows the identity of the first party but no privacy-compromising information regarding a proposed electronic business transaction between the first and second parties, and conducting the electronic business transaction between the first and second parties through the third party such that the identity of the first party is kept from the second party.
Owner:IBM CORP
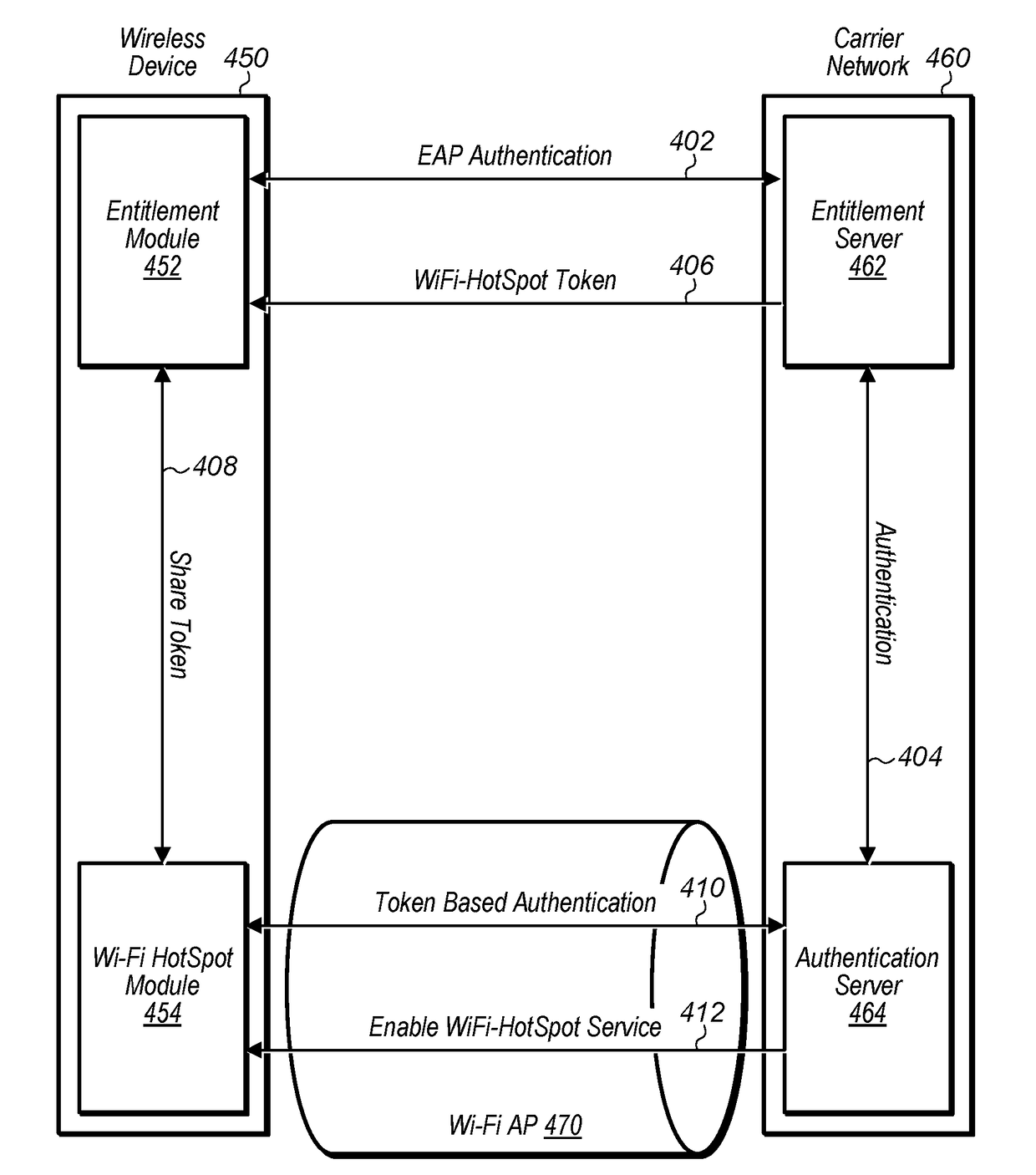
Entitlement Based Wi-Fi Authentication
ActiveUS20180063111A1Improve privacy and securityTransmissionSecurity arrangementWi-FiCommunications system
This disclosure relates to techniques for performing Wi-Fi authentication using an entitlement server in a wireless communication system. A wireless station may perform authentication with a carrier network entitlement server, using a protocol other than Wi-Fi. The wireless station may receive a Wi-Fi service token as part of the authentication with the carrier network entitlement server. The wireless station may perform Wi-Fi authentication with a Wi-Fi access point associated with the carrier network using the Wi-Fi service token. After performing Wi-Fi authentication using the Wi-Fi service token, the wireless station may communicate with the carrier network by way of the Wi-Fi access point.
Owner:APPLE INC
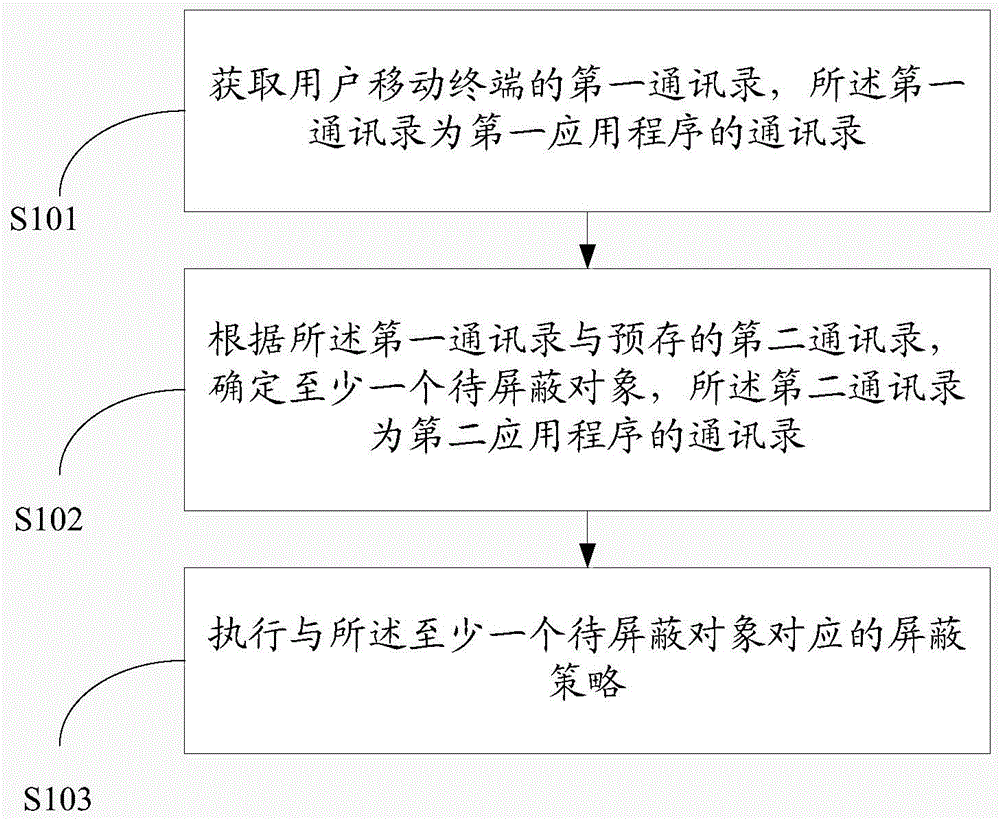
Friend message shielding method and device based on address list
InactiveCN104994009AImprove privacy and securityProtect privacy and securityData switching networksComputer engineering
The invention provides a friend message shielding method and device based on an address list and belongs to the network field. The method comprises the following steps: obtaining a first address list of a user mobile terminal, wherein the first address list is the address list of a first application program; determining at least one object to be shielded according to the first address list and a pre-stored second address list, wherein the second address list is the address list of a second application program; and executing a shielding strategy corresponding to the at least one object to be shielded. The technical scheme can realize bidirectional message shielding between friends, thereby simplifying operation of a user, protecting privacy safety of the user and enhancing user experience.
Owner:GUANGZHOU IAROUND NETWORK TECH CO LTD
Query track privacy protection method
ActiveCN109413067AReduce the number of queriesImprove privacy and securityLocation information based serviceTransmissionPrivacy protectionDifferential privacy
The invention discloses a query track privacy protection method, which is used for solving the privacy problem of continuous location service queries. Firstly, two query strategies of random locationsand suppression are designed on the basis of a service similarity principle, the problem of contradiction between quality of location services and privacy protection is solved, that is, service similarity is introduced for partitioning a map, when a user firstly requests a service in an area, a location is randomly selected in the same area to replace a real location thereof for requesting the service from a location server, then all subsequent queries in the same area are suppressed, and a result of a first query is directly utilized as a current query result; and secondly, a differential privacy protection method is introduced for controlling time intervals of cross-region queries, location privacy security of the cross-region queries is ensured, and the location correlation problem caused by short-time cross-region queries is solved.
Owner:FUJIAN NORMAL UNIV
Registration and login system based on block chain zero knowledge proof and application thereof
ActiveCN110581768AImprove privacy and securityProtect private informationFinanceEncryption apparatus with shift registers/memoriesZero-knowledge proofTamper resistance
The invention discloses a registration and login system based on blockchain zero knowledge proof and an application of the registration and login system in a registration method given by minimizationof information amount, a token number issuing method of a node and a login method with a hidden login state. The registration and login system comprises a token issuing module, an account address generation module, an account registration module and an account login application module. According to the invention, the registration and login system is integrated into the blockchain, and based on thecharacteristics of anonymity, decentration, tamper resistance and the like of the blockchain, and zero knowledge range is added to prove that personal information such as a user account is effectively protected, so that the privacy security of the user is improved, and the privacy information of the user is protected.
Owner:SHANGHAI INSTITUTE OF TECHNOLOGY
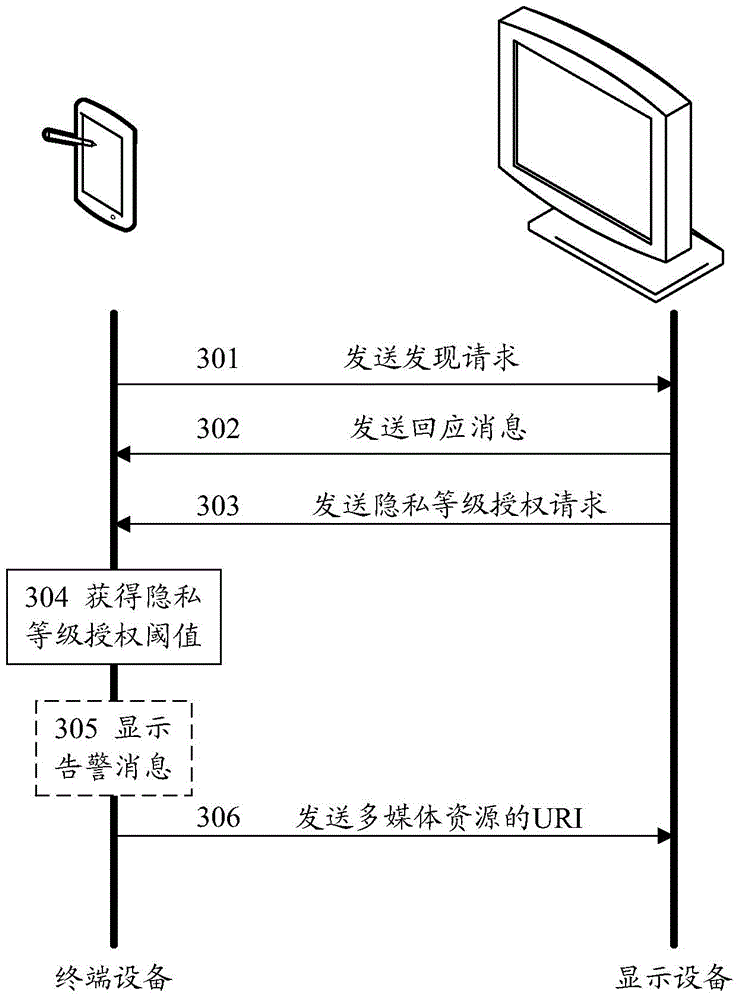
Method and device for multi-screen interaction of multimedia resource
InactiveCN105095770AImprove privacy and securityDigital data protectionInternal/peripheral component protectionTerminal equipmentUser privacy
A multi-screen interaction method of a multimedia resource and a terminal device are disclosed. With the method, security grades of multimedia resources to be shared and a security grade authorization threshold are set for a terminal device, and a display device plays a multimedia resource stored on the terminal device according to the security grade authorization threshold.
Owner:HISENSE
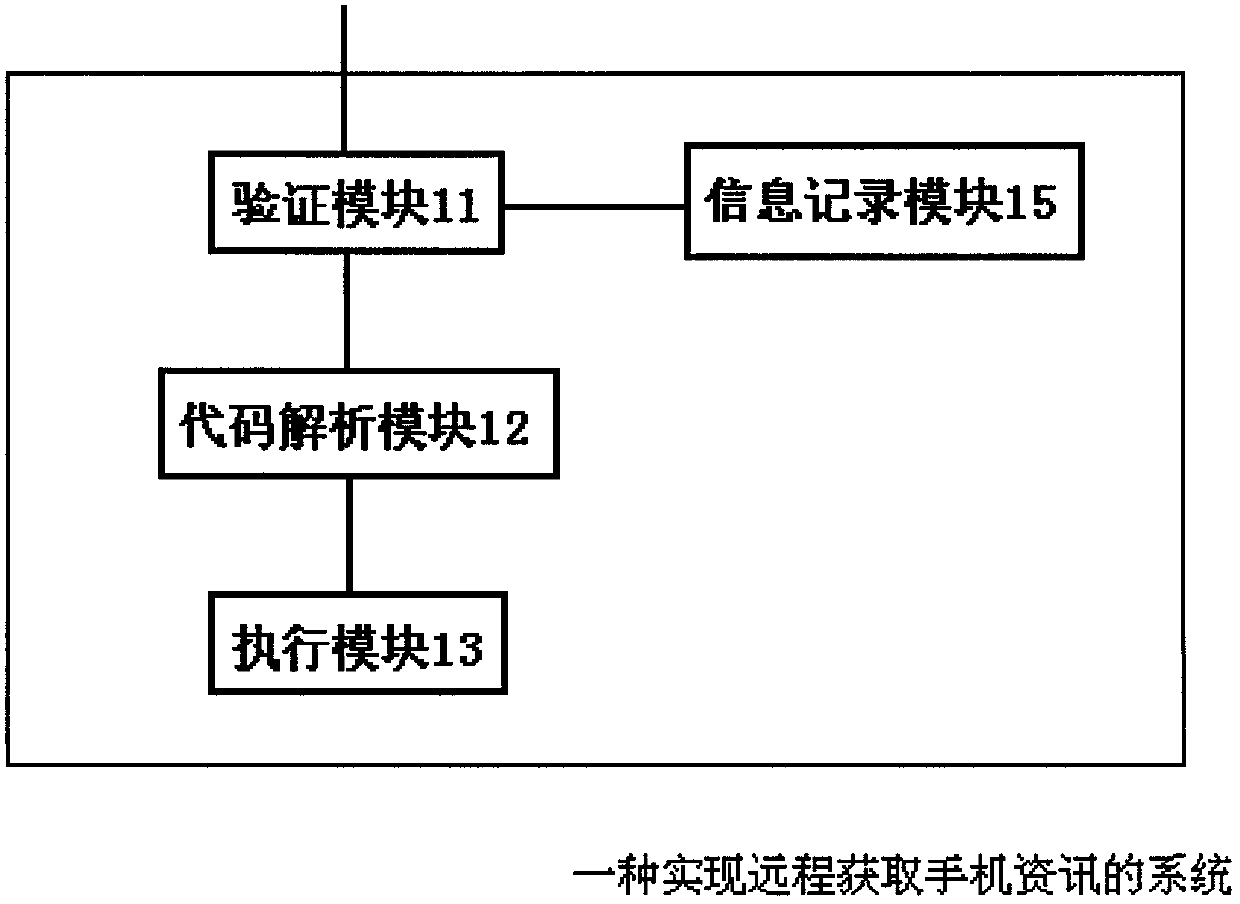
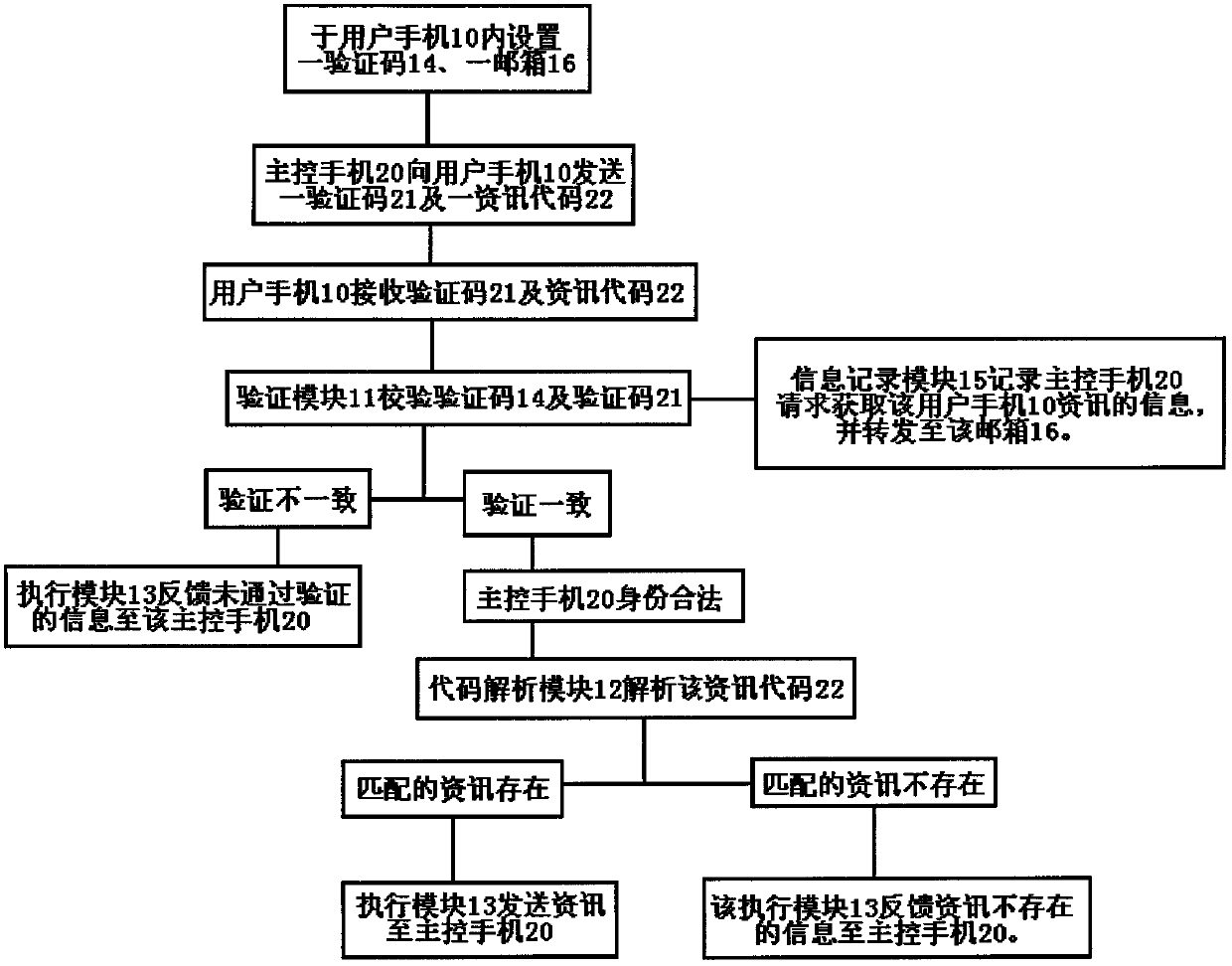
System for remotely acquiring mobile phone information
InactiveCN103002408AImprove privacy and securityConvenient lifeMessaging/mailboxes/announcementsSecurity arrangementComputer hardwareRelevant information
The invention relates to a system for remotely acquiring mobile phone information. The system is applied to a user's mobile phone and is capable of remotely acquiring missed calls, unread messages and contacts' phone numbers in the user' mobile phone by transmitting a verification code and an information code to the user's mobile phone through a master control phone. The system is characterized by comprising a verification module, a code analysis module, an executive module and an information recording module, wherein the verification module is used for verifying validity of identity of the master control phone, the code analysis module is used for analyzing the information code, the executive module is used for executing processing results from the verification module and the code analysis module, and the information recording module is used for recording and forwarding information of requested access, to the user's mobile phone. Even if the user's mobile phone is not carried, the missed calls, short messages and contacts' phone numbers can be acquired, so that life convenience is brought to people. Even if the verification code to the mobile phone is cracked by other people, the user can be informed of whether the mobile phone is remotely accessed for information or not through email boxes and can be informed of related information of the master control phone to take corresponding measures, so that privacy security in mobile phones can be improved to a certain degree.
Owner:LITE ON ELECTRONICS (GUANGZHOU) LTD +1
Method, device, server and system for identity authentication using biometrics
InactiveUS8421595B2Improve privacy and securityImprove convenienceElectric signal transmission systemsDigital data processing detailsBiometric dataAuthentication server
A method, a device, a server and a system for authenticating the identity with the biological character in an authenticating system, the authenticating system at least includes a local device and an authenticating server, wherein the method comprises the following steps: inputting step, inputting the biological character data in the local device by a biological character sensor; matching step, matching the input biological character data with the original biological character data pre-stored in the memory of the local device; first identification code producing step, producing the first identification code in the local device if the input biological character data is matched with the original biological character data pre-stored in the memory; and authenticating step, sending the first identification code to the authenticating server, authenticating the first identification code by the authenticating server in order to authorize the system to perform the authorized operation.
Owner:VALLEY TECH
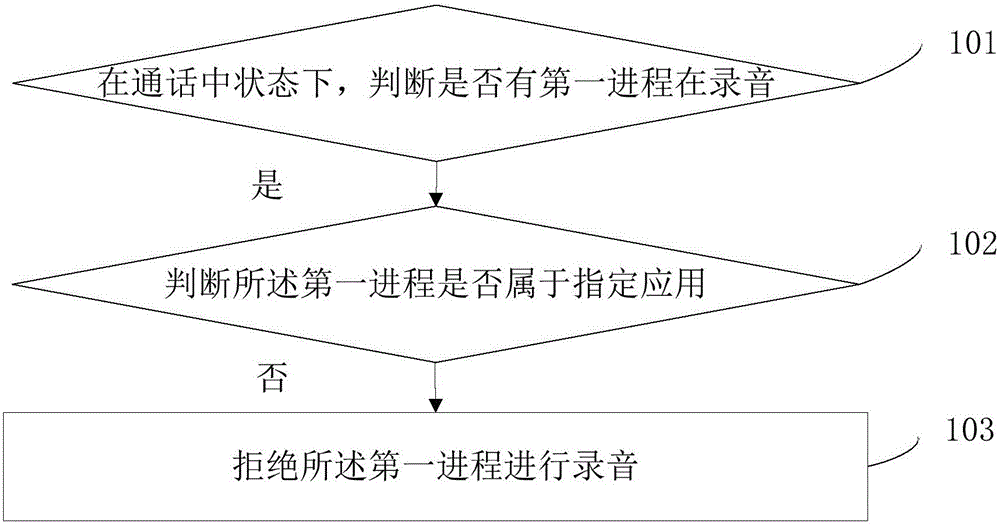
Recording security control method, device and equipment
InactiveCN106210285AImprove privacy and securityAvoid gettingSubstation equipmentThird partyInternet privacy
The embodiment of the invention provides a recording security control method, a recording security control device and a piece of recording security control equipment, relating to the technical field of communication. The method comprises the steps of: in an in-call state, judging whether a first process which records exists; if the first process which records exists, judging whether the first process belongs to a designated application; and if the first process does not belong to the designated application, refusing the first process to record. According to the recording security control method, the recording security control device and the recording security control equipment provided by the invention, the problem that a call process of a user is exposed possibly so that privacy information of the user is unsecure and the privacy security of the user is threatened is solved; the call of the user can be prevented from being obtained by the process of a malicious third party application; and the privacy security for the call process of the user is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
Application program privacy authority management method and device
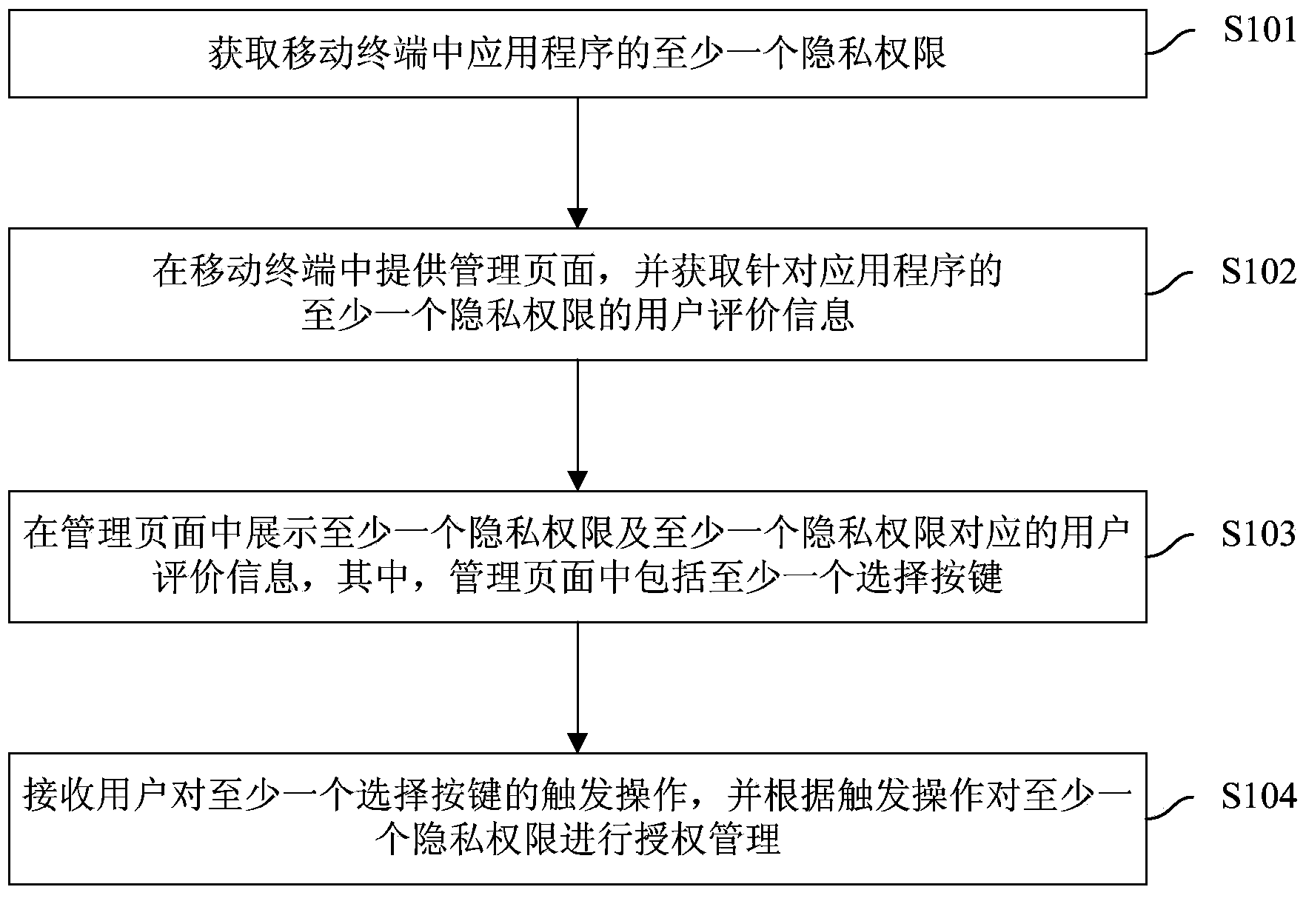
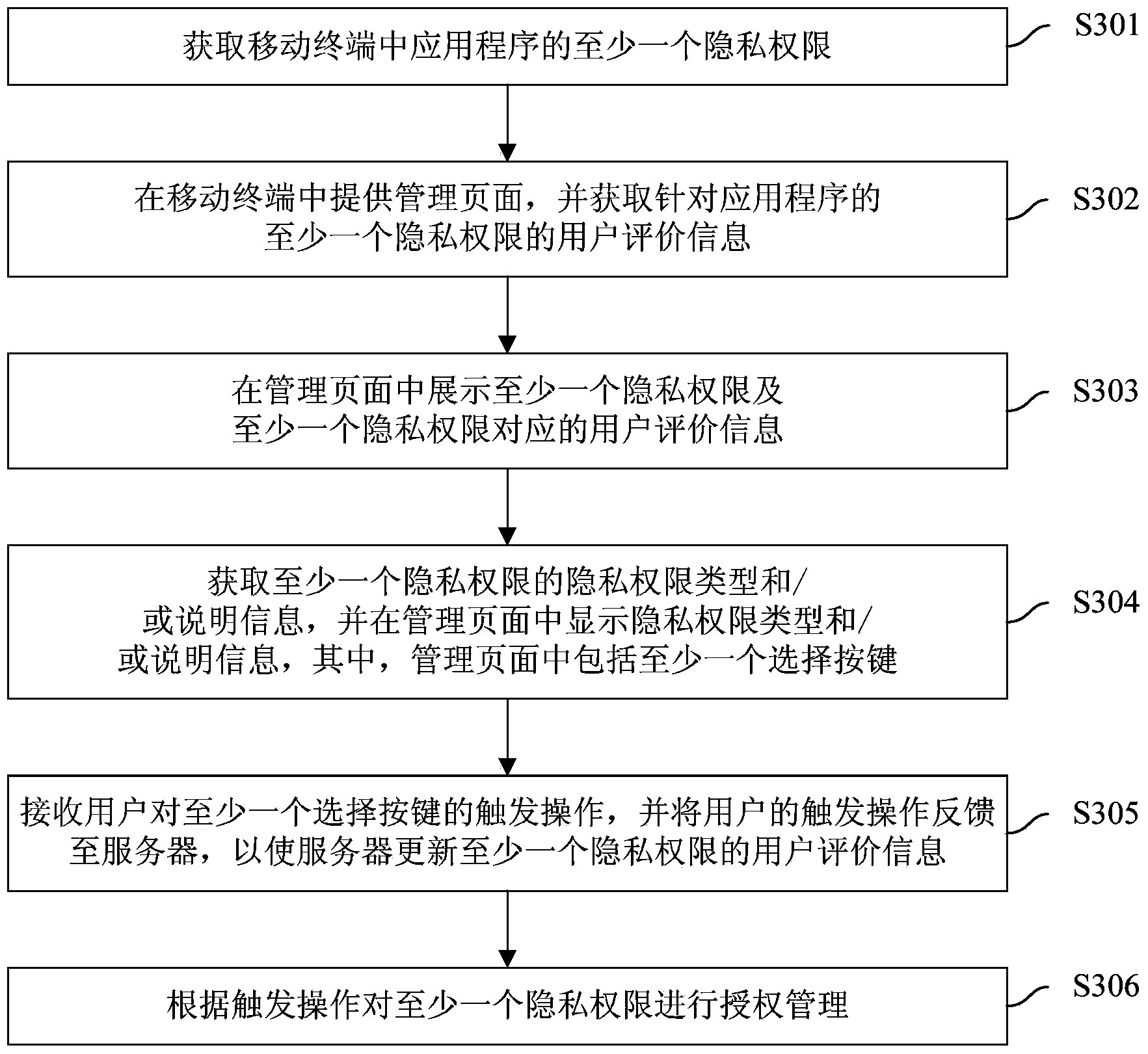
ActiveCN103886255AEasy to manageImprove privacy and securityDigital data protectionPlatform integrity maintainanceApplication softwareAuthorization
The invention discloses an application program privacy authority management method and device. The method comprises the steps that at least one privacy authority of an application program in the mobile terminal is obtained; a management page is provided in the mobile terminal, and user assessing information of the at least one privacy authority corresponding to the application program is obtained; the at least one privacy authority and the user assessing information corresponding to the at least one privacy authority are shown in the management page, wherein at least one selecting key is included in the management page; and triggering operation on the at least one selecting key of a user is received, and according to the triggering operation, authorization management is carried out on the at least one privacy authority. According to the management method, the user can clearly know which application programs obtain the privacy authority excessively, the user can conveniently manage the privacy authority, the privacy safety of the user is improved, user experience is improved, manual analysis is of no need, and labor cost is greatly lowered.
Owner:KENIU NETWORK TECH BEIJING
Privacy protection methods and privacy protection apparatuses in vehicle communication
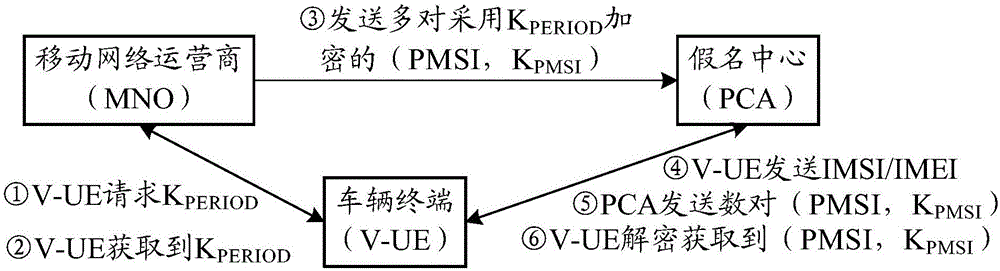
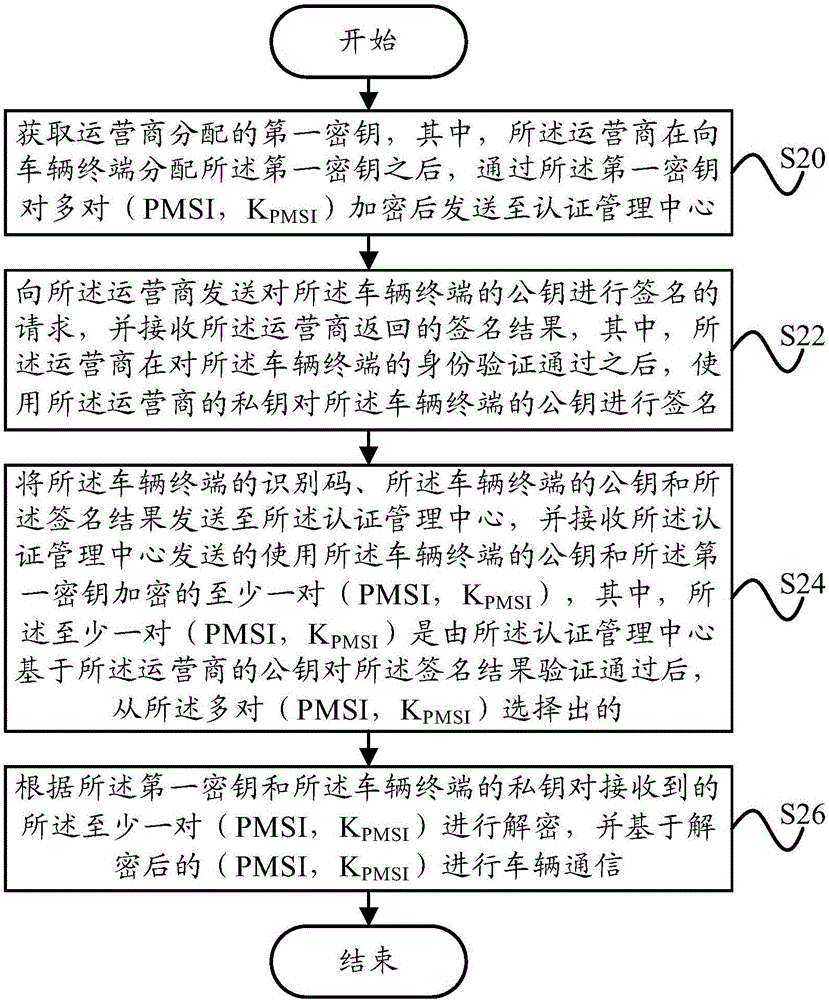
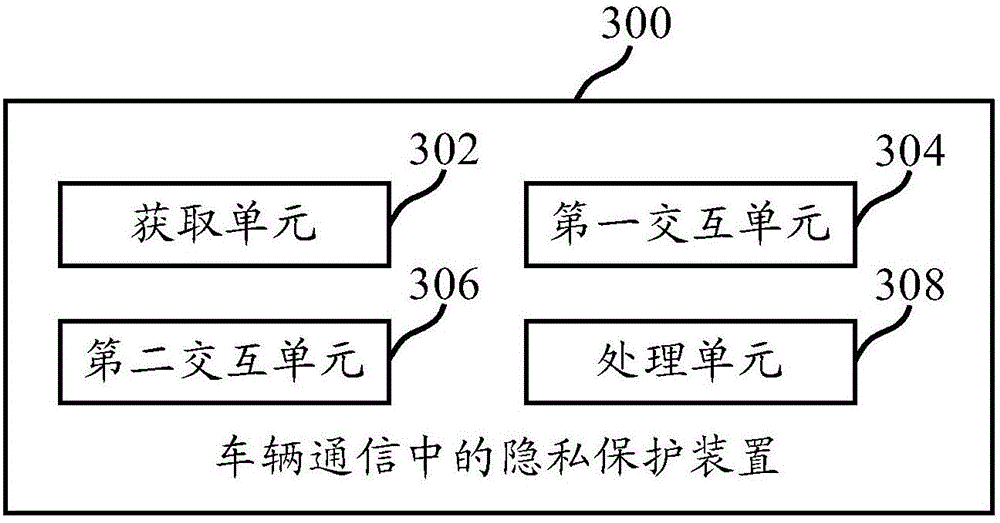
PendingCN106506161AGet real identity informationImprove privacy and securityPublic key for secure communicationUser identity/authority verificationIn vehiclePrivacy protection
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Safety transaction method and system based on policy identity
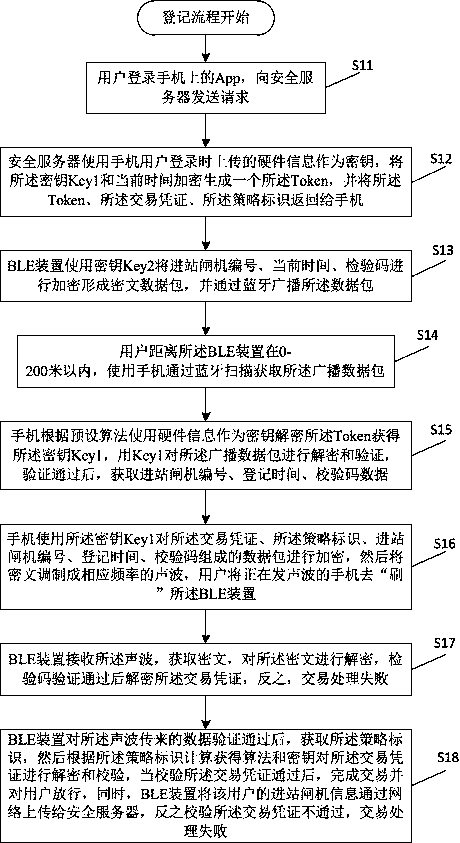
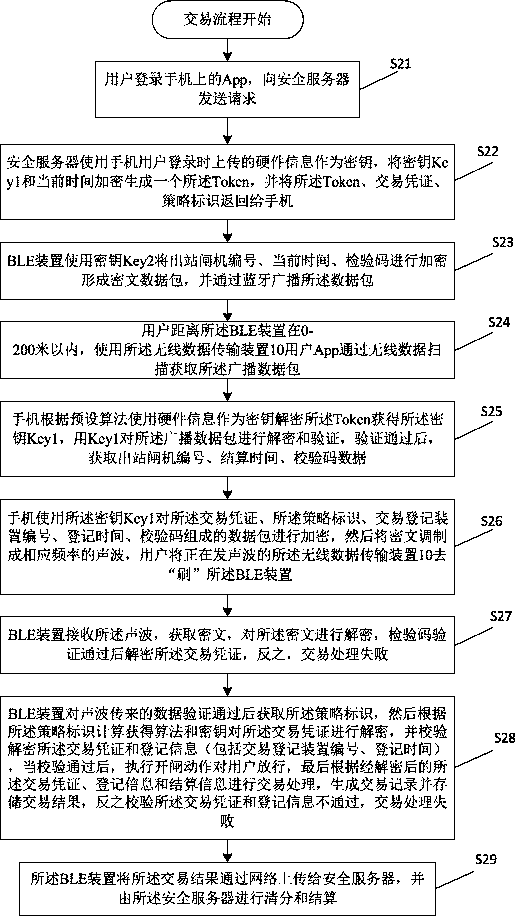
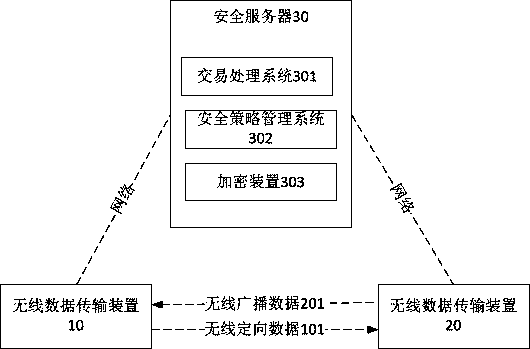
PendingCN108537536APrevent counterfeitingRealize offline transactionsElectronic credentialsProtocol authorisationBroadcast packetCiphertext
The present invention provides a safety transaction method and system based on policy identity. The method comprises the steps that: a wireless data transmission device 10 accesses a safety server toobtain Token, transaction documents and police identity; a wireless data transmission device 20 performs encryption and broadcast of information of a transaction device; the wireless data transmissiondevice 10 performs scanning to obtain a data packet, decodes the Token to obtain a secret key Key1 and perform decoding verification of the broadcasted data packet through adoption of the Key1; afterverification is passed, the wireless data transmission device 10 performs encryption of data formed by the transaction documents, the police identity and the information of the transaction device byemploying the secret key Key1, modulate ciphertext to wireless orienteering data and send the wireless orienteering data to the wireless data transmission device 20; and the wireless data transmissiondevice 20 receives the wireless orienteering data, then calculate a secret key Key2 to perform decoding verification of the ciphertext, perform decoding verification of the transaction documents after the verification is passed, and performs transaction processing logic after the verification is passed. The safety transaction method and system based on policy identity achieves wireless both-way identity verification of the safety transaction data so as to avoid that the transaction documents are counterfeited and the fun is stolen and improve the safety.
Owner:咪付(广西)网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com