A user authentication device and an authentication method based on a physically non-clonable technology PUF
An authentication device and user authentication technology, applied in user identity/authority verification, public key for secure communication, digital transmission system, etc., can solve problems such as easy to be stolen, difficult to maintain, and difficult for users to create and remember. Satisfy the effect of non-cloning and copying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Hereinafter, the present invention will be further described in detail with reference to the examples and drawings, but the implementation of the present invention is not limited thereto.
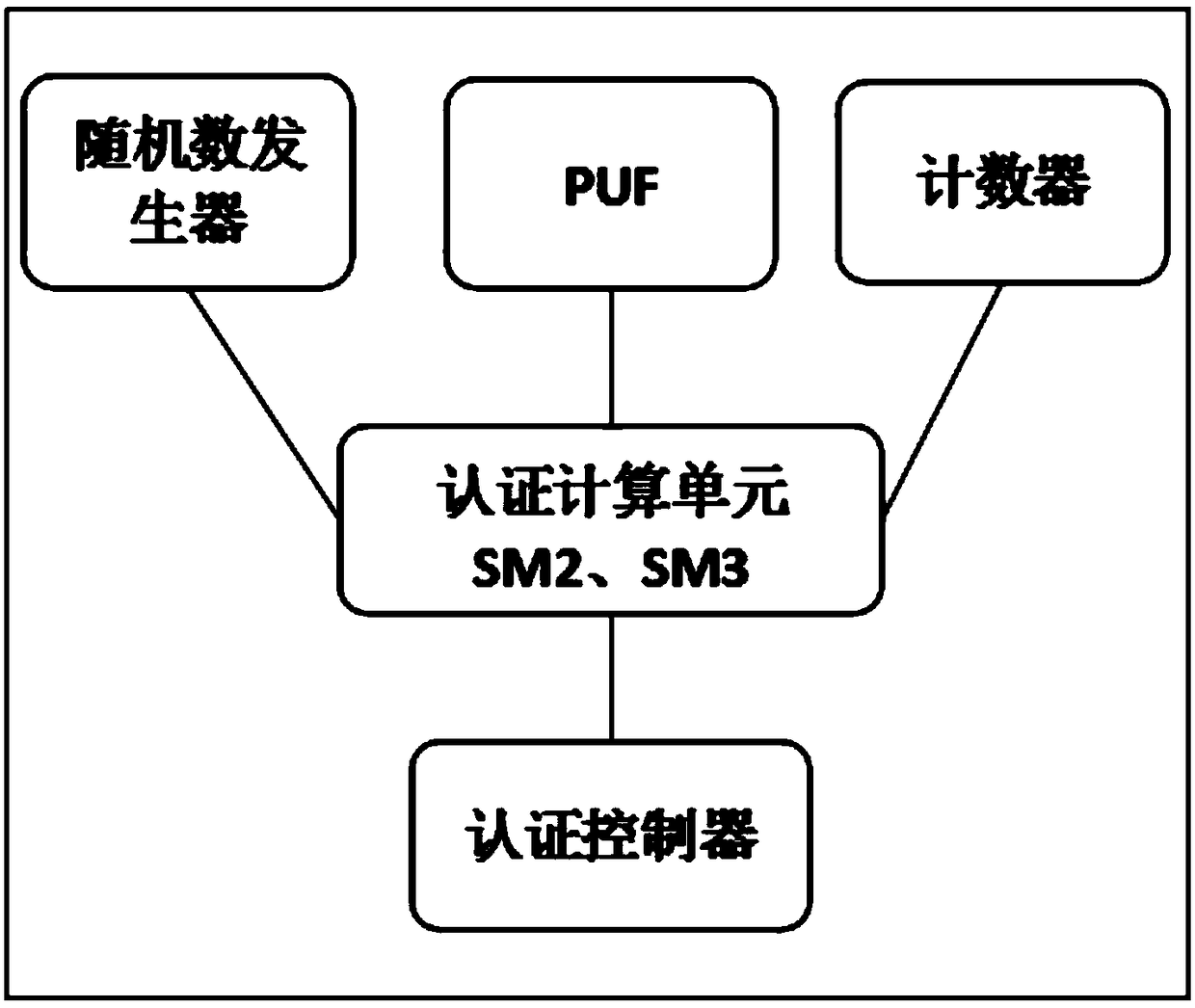
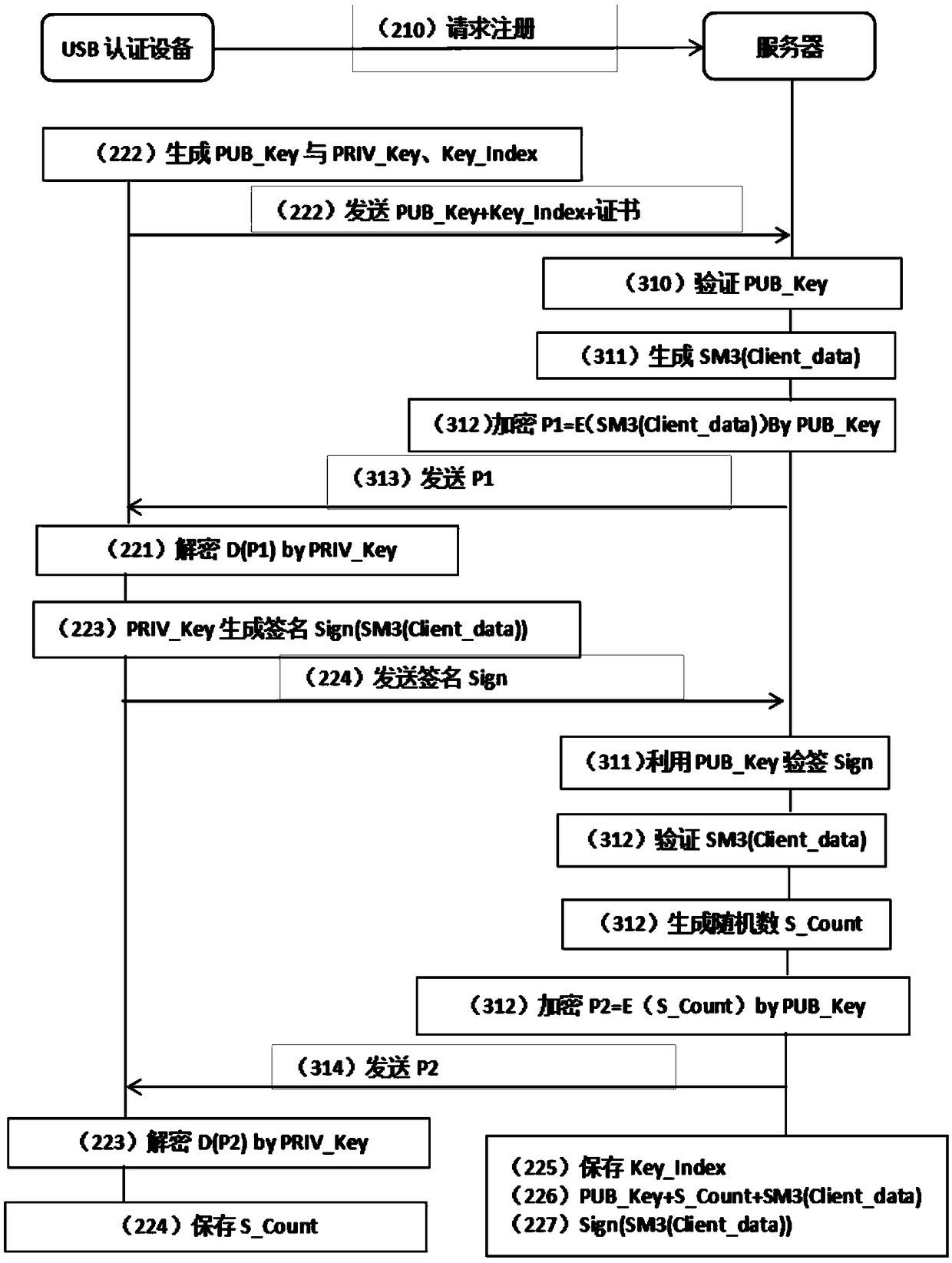
[0050] Such as Figure 1~6 As shown, a user authentication device based on physical unclonable technology PUF includes a physical unclonable module PUF, an authentication module, an authentication control module, a random number generator, and a counter, where:
[0051] The physical unclonable module PUF is embedded in the authentication device for generating authentication-related key pairs;
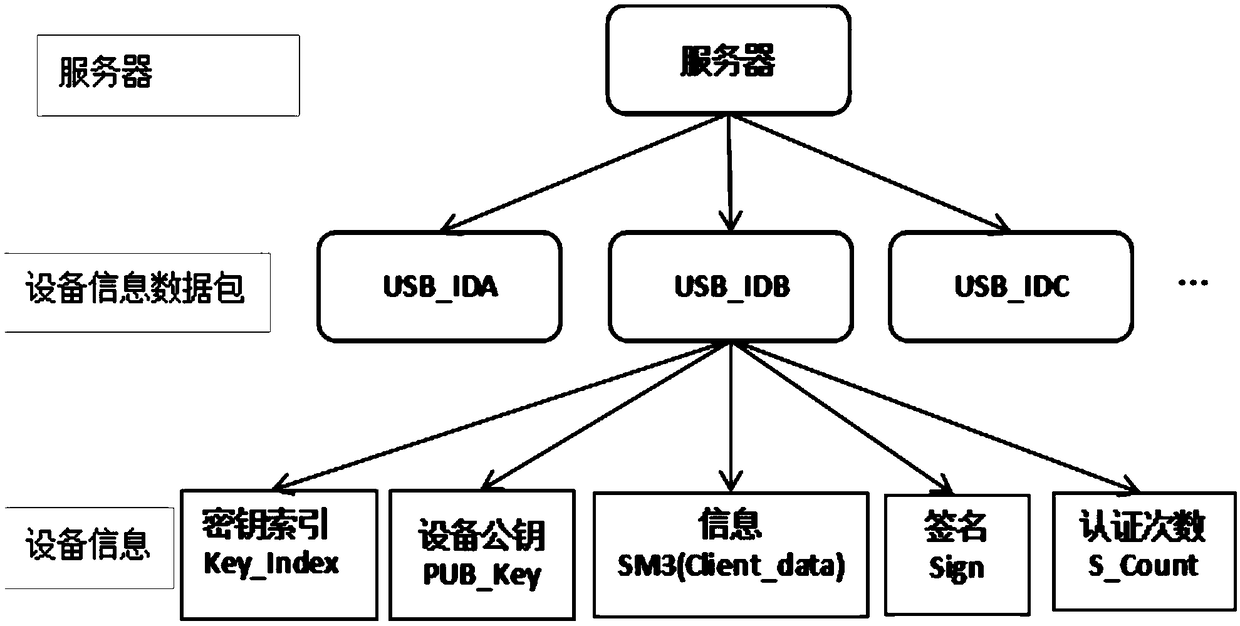
[0052] The authentication module embeds an asymmetric algorithm and a digest algorithm to complete the operations required for authentication; the authentication module includes a public key generation module that uses the "response" of the physical unclonable module PUF to generate a public key, And transmit the public key to the server;
[0053] The user can manually control sending authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com