Safety transaction method and system based on policy identity
A secure transaction and identification technology, applied in the field of mobile transactions and information security, can solve the problems of insufficient security, NFC transaction technology is easy to be stolen, inconvenient operation, etc., and achieve the effect of preventing counterfeiting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
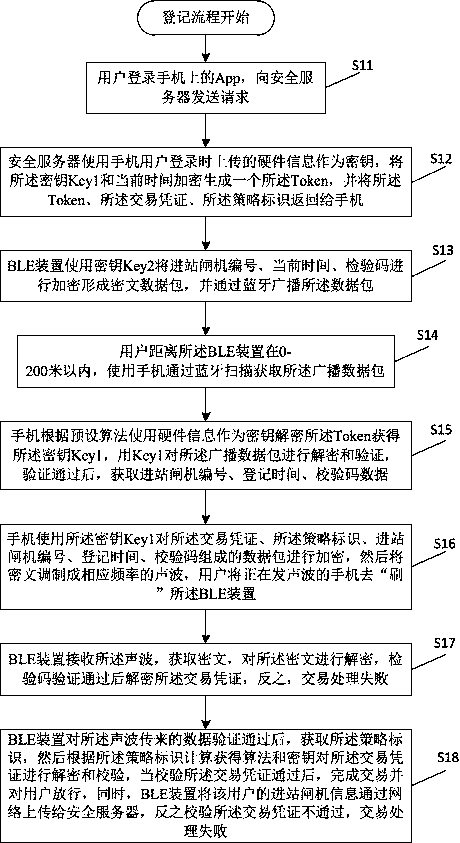
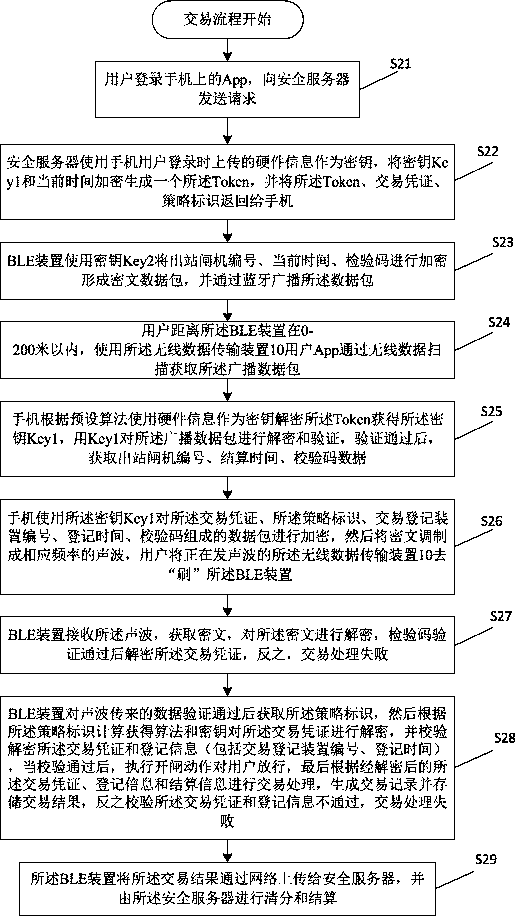
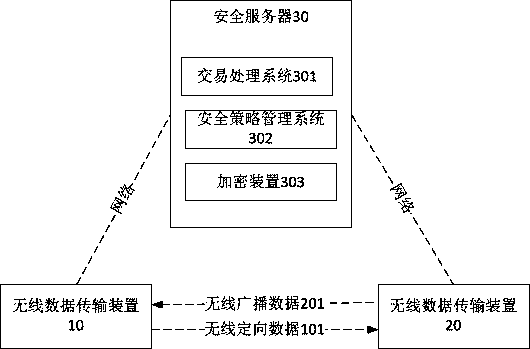
[0031] The present invention will be further described below in conjunction with the accompanying drawings and embodiments, but the protection scope of the present invention is not limited to the following specific embodiments.
[0032] In this embodiment, in order to further clearly understand the technical solution of this embodiment, the following takes a subway station as an example to provide a specific transaction process of a secure transaction method based on the policy identification. Whether it is mileage billing or one-ticket billing, the technical solution of this embodiment can be applied. In this specific implementation, the wireless data transmission device 10 is mapped to a mobile phone, and the wireless data transmission device 20 is mapped to be installed in a gate The BLE device in the machine, the transaction registration device is mapped to an entry gate, the transaction settlement device is mapped to an outbound gate, the security server 30 is mapped to a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com