Recording security control method, device and equipment
A security control and audio technology, applied in the field of communication, can solve problems such as stealing recordings and insecure user privacy information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
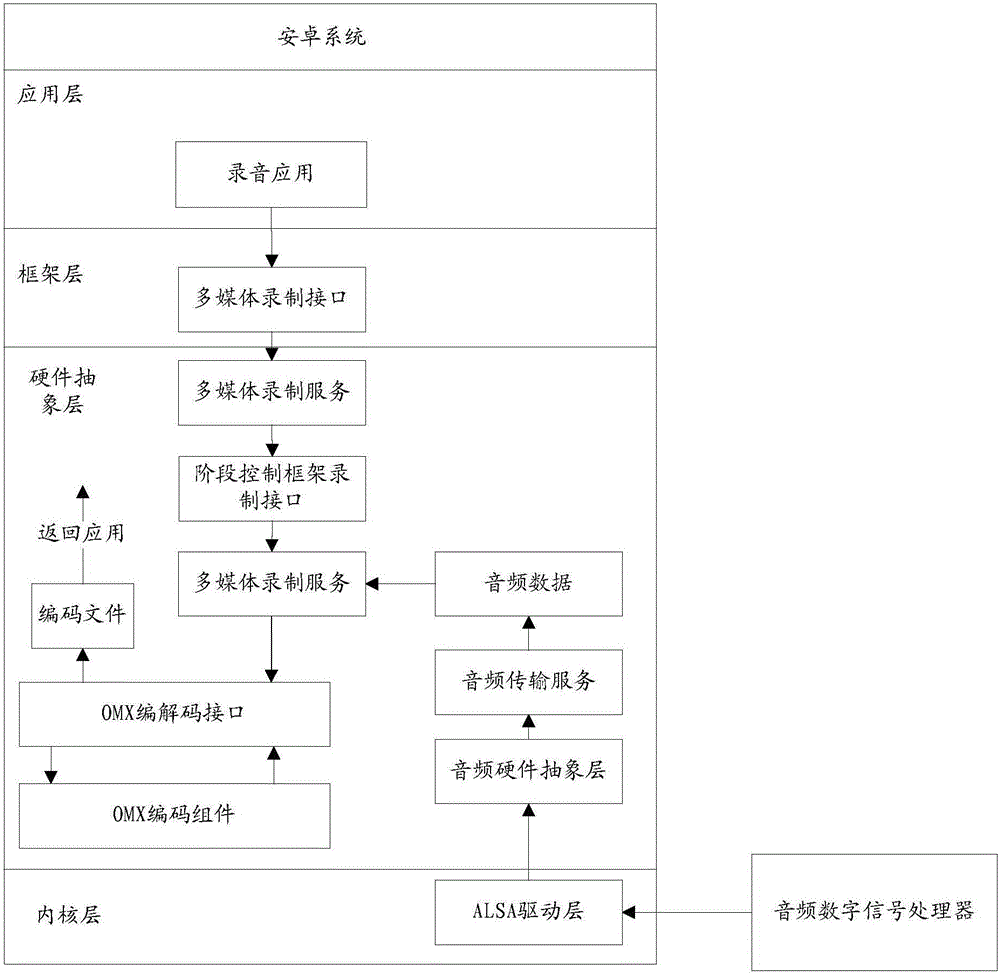
[0070] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a recording security control method according to an embodiment of the present invention, which may specifically include the following steps:
[0071] Step 101, in the state of talking, judge whether there is a first process recording, if there is a first process recording, then enter step 102;
[0072] In the embodiment of the present invention, when the user uses the mobile terminal to make a call, the mobile terminal can judge whether there is a certain first process in the system that is recording in the state of a call.
[0073] The mobile terminal is, for example, a mobile phone, or other mobile terminals that can make and receive calls, and this embodiment of the present invention does not limit it.
[0074] In the embodiment of the present invention, after it is determined that the mobile terminal is in the state of a call, the invocation of the recording interface is monitored. If the...
Embodiment 2
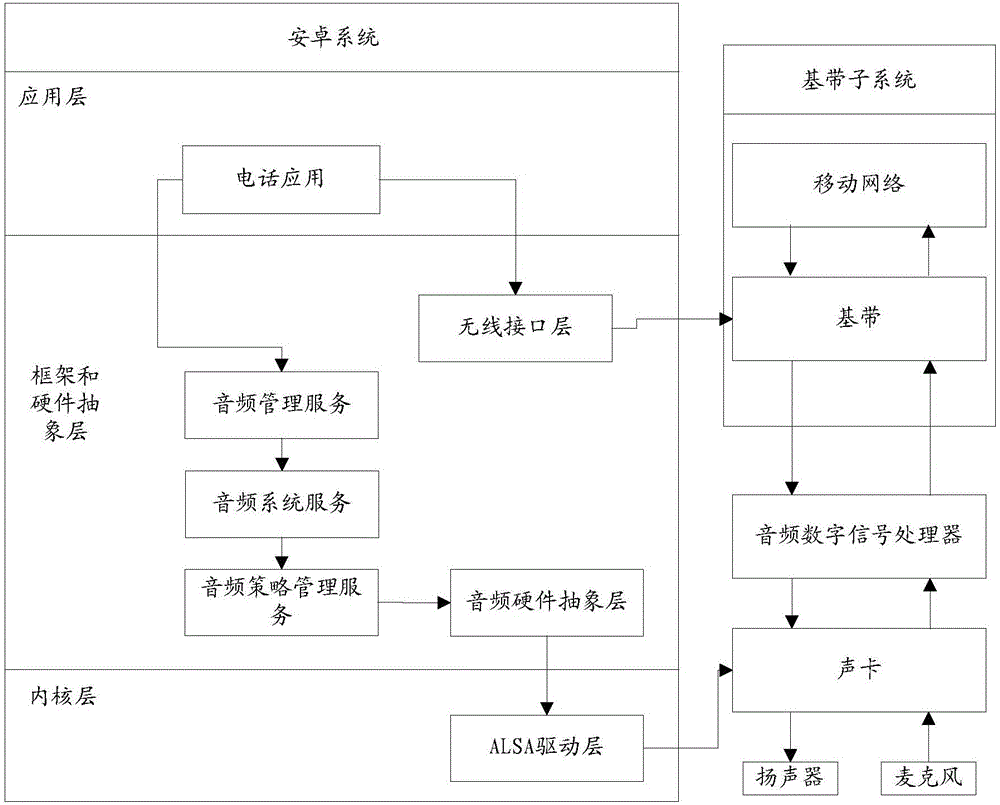
[0086] refer to figure 2 , which shows a flow chart of the steps of an embodiment of a recording security control method according to an embodiment of the present invention, which may specifically include the following steps:
[0087] Step 201, in the state of talking, determine whether there is a first process recording; if there is a first process recording, then enter step 202;
[0088] This step is similar in principle to step 101 in Embodiment 1.
[0089] Preferably, in another embodiment of the present invention, before step 201, it also includes:
[0090] Step 200, judging whether the in-call state written in the audio call state setting interface AudioManager.setMode is received; if the in-call state written in the audio call state setting interface AudioManager.setMode is received, then enter step 201;
[0091] Such as Figure 1B As described in , when the phone application makes a call, it will pass the call state MODE_IN_CALL to the framework and hardware abstra...
Embodiment 3
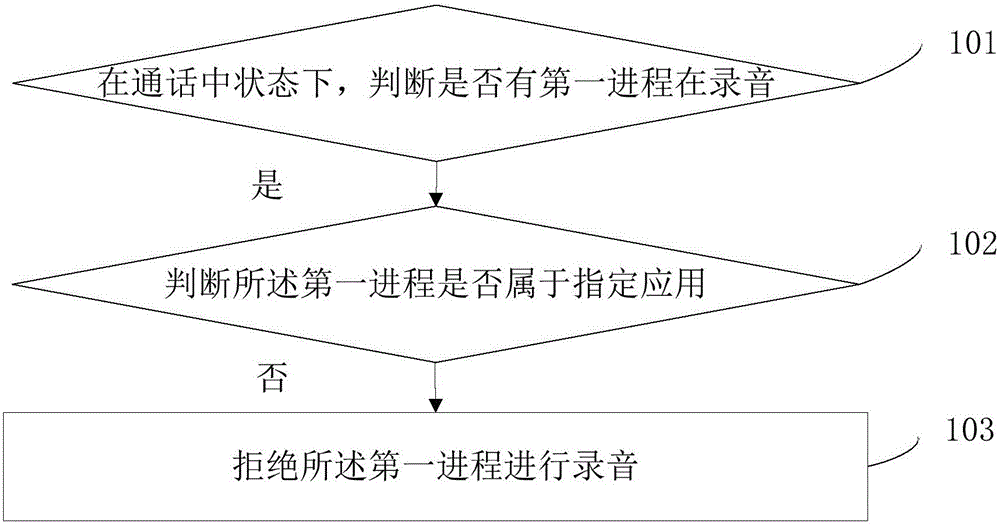
[0133] refer to image 3 , which shows a flow chart of the steps of an embodiment of a recording security control method according to an embodiment of the present invention, which may specifically include the following steps:
[0134] Step 301, in the state of talking, judge whether there is a first process recording, if there is a first process recording, then enter step 302;
[0135] Step 302, judging whether the first process belongs to a designated application, and if the first process does not belong to a designated application, proceed to step 303;
[0136] Step 303, after the first process stores the recording data, delete the recording storage file at the corresponding location according to the storage path of the recording data.
[0137] In the embodiment of the present invention, it is possible to find the storage path where the recording data is stored by the first process, and then monitor whether the recording of the first process is finished, and if it is finish...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com