Two-tiered wireless sensor network range query method capable of verifying privacy protection
A sensor network and query method technology, applied in the field of two-layer sensor network range query, can solve the problems of affecting the network life cycle and high communication cost of sensing nodes, achieving high verifiability and ensuring privacy and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
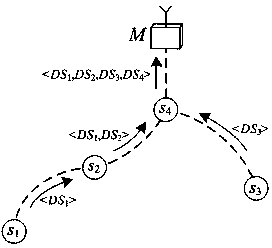
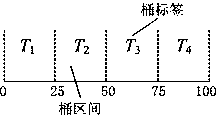
[0050] The invention realizes the privacy protection of sensitive data based on the bucket division mechanism and symmetric encryption technology; based on the Hash message identity authentication code (HMAC) mechanism, by adding relevant verification codes in the transmission data, the consistency verification of the query results is realized. In order to further explain the technical solution, the present invention first provides the definitions and assumptions of relevant symbols, and then provides the detailed process of the technical solution.
[0051] 1. Definitions and assumptions of related symbols
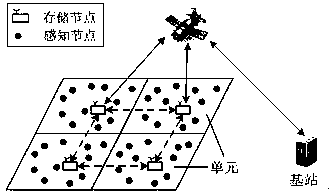
[0052] The invention is based on figure 1 The two-layer wireless sensor network model shown focuses on the range query technology scheme to obtain the sensing data value in the range [lb, ub] in a unit. For a complex range query covering mult...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com